#BreachForums
Explore tagged Tumblr posts
Text
French Police Dismantle BreachForums Core Team in Major Cybercrime Bust

Four top French hackers and a British accomplice, tied to the infamous BreachForums, have been arrested after a wave of high-profile data thefts. The elite cybercrime site, long a hub for selling hacked data, has finally been gutted.
French police arrested key operators of BreachForums, once the Internet’s largest marketplace for stolen data. According to Bitdefender, suspects known as Depressed, Hollow, Noct, and Shiny Hunters were captured by France's Cybercrime Brigade. A fifth suspect, British hacker Kai West (aka IntelBroker), had already been detained. Together, they’re accused of targeting major French institutions including SFR, France Travail, and the football federation. The FBI and DOJ link West to $25 million in damages and over 150 hacking incidents.
Sources: Bitdefender | Le Parisien
2 notes
·
View notes
Text
US, French authorities affirm arrest of BreachForums hackers
U.S. and French authorities have confirmed the arrests of 5 hackers accused of being behind a number of main hacks and being a part of a infamous cybercrime discussion board. On Thursday, the U.S. Division of Justice introduced the indictment of British nationwide Kai West, 25, accusing him of being “a serial hacker” generally known as IntelBroker. U.S. authorities allege West is behind “a…
0 notes
Text
rip intelbroker
you did good when you dupped on the mc central minecraft server, and also did a funny when you breached europol
also probably no one is going to remember you in 20 years when you're 45 and your whole life are ruined.
moral of the story, if you're committing high profile cyber attacks, the glowies probably know who you are, they just wait for enough evidence to get you.
hopefully you don't have mountains of csam on your devices like previous breachforums owners.
0 notes
Text
RockYou2024 : un record de 10 milliards de mots de passe volés
Un hacker, connu sous le pseudonyme "ObamaCare", a publié sur le forum BreachForums une collection gigantesque de mots de passe volés. Cette compilation, nommée RockYou2024, contient près de 10 milliards de mots de passe ! Oui, vous avez bien lu, 10 milliards ! C'est un record absolu, dépassant de loin la collection précédente, RockYou2021.

RockYou2024 : un record de 10 milliards de mots de passe volés - LaRevueGeek.com
#hacking#cybersecurité#mot de passe#compilation#forum#BreachForums#ObamaCare#record#mots de pase volés#sécurité informatique
0 notes
Text
ФБР разгромило BreachForums, но уже появляются преемники
New Post has been published on https://er10.kz/read/it-novosti/fbr-razgromilo-breachforums-no-uzhe-pojavljajutsja-preemniki/
ФБР разгромило BreachForums, но уже появляются преемники

В ходе недавней операции ФБР и полиции СШ�� была ликвидирована подпольная платформа BreachForums, используемая киберпреступниками. Однако, за короткие сроки злоумышленники уже создали альтернативные сайты и инфраструктуру.
ФБР сообщило, что в ходе операции взяло под контроль серверы и домены, на которых располагался форум, и заявило, что в настоящее время проверяет бэкэнд сайта, призвав всех пользователей, обладающих дополнительной информацией о преступной деятельности, немедленно сообщить об этом.
BreachForums является продолжением другого популярного хакерского форума, известного как RaidForums, который действовал с 2015 по 2022 год, прежде чем его основатель Диого Сантос Коэльо, или Omnipotent, был арестован властями Великобритании.
Известный участник сообщества RaidForums, Pompurin или Конор Брайан Фицпатрик, создал первоначальную итерацию BreachForums, которая просуществовала с 2022 года до его ареста в марте прошлого года.
За это время на сайте были размещены похищенные данные более 80 000 членов некоммерческого портала ФБР InfraGard, а также медицинская информация более 56 000 человек, украденная с рынка медицинского страхования DC Health Link.
На данный момент дело BreachForums уже возрождается – участ��ик форума Baphomet взял под контроль инфраструктуру сайта, которую быстро переделал, опасаясь, что она все еще может быть взломана правоохранительными органами.
0 notes
Text
FBI neemt datalekforum in beslag
De website en het Telegram-kanaal van ‘datalekforum’ BreachForums zijn door de FBI in beslag genomen. Op het forum werden al jaren lang gestolen databases aangeboden met miljarden gestolen persoonsgegevens. Beheerder ‘Pompompurin’, begin 2023 opgepakt, is inmiddels veroordeeld tot twintig jaar. Maar BreachForums ging met een nieuwe beheerder en een nieuw domeinen gewoon verder. Recent werd nog…
View On WordPress
0 notes
Text
Unveiling Genesis Market: A Deep Web Marketplace
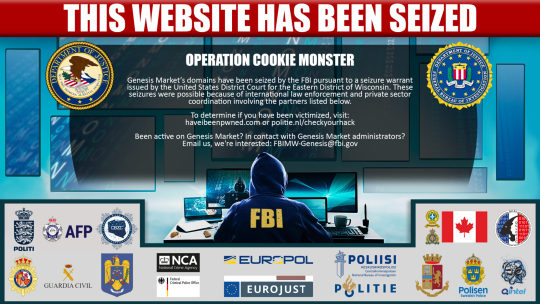
The internet is a vast and complex world, with numerous hidden corners that are not accessible through regular search engines. One such realm is the darknet, a part of the internet that is not indexed by search engines and requires special tools and software to access. Within the darknet, there are illegal marketplaces where various illicit goods and services are bought and sold, including drugs, weapons, counterfeit documents, stolen data, and more. Genesis Market is one such deep web marketplace that has gained notoriety. Let's take a closer look and shed some light on what Genesis Market is. Read the full article
0 notes
Note
"Genetics firm 23andMe confirms user data theft in a credential stuffing attack. The hackers released 1 million lines of data targeting Ashkenazi Jews and Chinese descent" this is so scary, wtf
OK followers this is not a drill. This is now the time to start calling out the antisemitism in your friends and family. This is truly some nazi level eugenics shit. I'm at work but I'd appreciate more help boosting what to do.
mod ali
Update:
Please send this to all your Jewish and Chinese friends and family. Stay safe and please boost this.
4K notes
·
View notes
Text
The company said its systems were not breached and that attackers gathered the data by guessing the login credentials of a group of users and then scraping more people’s information from a feature known as DNA Relatives. Users opt into sharing their information through DNA Relatives for others to see.
...
The full picture of why the data was stolen, how much more the attackers have, and whether it is actually focused entirely on Ashkenazim is still unclear.
...
Callow notes that the situation raises broader questions about keeping sensitive genetic information safe and the risks of making it available in services that are designed like social networks to facilitate sharing.
...
“This incident really highlights the risks associated with DNA databases,” Callow says. “The fact that accounts had reportedly opted into the ‘DNA Relatives’ feature is particularly concerning as it could potentially result in extremely sensitive information becoming public.”
Yeah, so, don't reuse passwords, and be careful what kind of information you share purposefully or opt in to passively sharing.
Jesus fucking Christ.
#antisemitism#data breach#23 and me#DNA testing#i have been saying for years and years that something like this was going to happen#i have been tempted by DNA testing but i dont trust that shit to some random company#and this is fucking why
482 notes
·
View notes
Text
One of the biggest hacks of the year may have started to unfold. Late on Friday, embattled events business Live Nation, which owns Ticketmaster, confirmed it suffered a data breach after criminal hackers claimed to be selling half a billion customer records online. Banking firm Santander also confirmed it had suffered a data breach impacting millions of customers and staff after its data was advertised by the same group of hackers.
While the specific circumstances of the breaches—including exactly what information was stolen and how it was accessed—remain unclear, the incidents may be linked to attacks against company accounts with cloud hosting provider Snowflake. The US-based cloud firm has thousands of customers, including Adobe, Canva, and Mastercard, which can store and analyze vast amounts of data in its systems.
Security experts say that as more details become clear about hackers' attempts to access and take data from Snowflake’s systems, it is possible that other companies will reveal they had data stolen. At present, though, the developing situation is messy and complicated.
“Snowflake recently observed and is investigating an increase in cyber threat activity targeting some of our customers’ accounts,” wrote Brad Jones, Snowflake’s chief information security officer in a blog post acknowledging the cybersecurity incident on Friday. Snowflake has found a “limited number” of customer accounts that have been targeted by hackers who obtained their login credentials to the company’s systems, Jones wrote. Snowflake also found one former staff member’s “demo” account that had been accessed.
However, Snowflake doesn’t “believe” it was the source of any leaked customer credentials, the post says. “We have no evidence suggesting this activity was caused by any vulnerability, misconfiguration, or breach of Snowflake’s product,” Jones wrote in the blog post.
While the number of Snowflake accounts accessed and what data may have been taken have not been released, government officials are warning about the impact of the attack. Australia’s Cyber Security Center issued a “high” alert on Saturday, saying it is “aware of successful compromises of several companies utilizing Snowflake environments” and companies using Snowflake should reset their account credentials, turn on multifactor authentication, and review user activity.
“It looks like Snowflake has had some rather egregiously bad security compromise,” security researcher Troy Hunt, who runs data breach notification website Have I Been Pwned, tells WIRED. “It being a provider to many other different parties, it has sort of bubbled up to different data breaches in different locations.”
Details of the data breaches started to emerge on May 27. A newly registered account on cybercrime forum Exploit posted an advertisement where they claimed to be selling 1.3 TB of Ticketmaster data, including more than 560 million people’s information. The hacker claimed to have names, addresses, email addresses, phone numbers, some credit card details, ticket sales, order details, and more. They asked for $500,000 for the database.
One day later, the established hacking group ShinyHunters—which first emerged in 2020 with a data-stealing rampage, before selling 70 million AT&T records in 2021—posted the exact same Ticketmaster ad on rival marketplace BreachForums. At the time, Ticketmaster and its parent company Live Nation had not confirmed any data theft and it was unclear if either post selling the data was legitimate.
On May 30, ShinyHunters also claimed to be selling 30 million customer details and staff information from Santander, putting a $2 million price tag on the information. Both posts on BreachForums have drawn attention to the illegal marketplace, which was recently revived by ShinyHunters after the FBI took the website down on May 15. The posts may, at least in part, be efforts to restore the disrupted forum’s damaged reputation with criminals.
The two hacks were linked to Snowflake’s systems by Israeli security firm Hudson Rock, which, in a now-removed blog post, posted conversations its researchers had with the alleged hacker who claimed to have accessed Snowflake’s systems and exfiltrated data. The hacker claimed they had tried to sell the data back to Snowflake for $20 million. (Hudson Rock did not respond to WIRED’s questions about why it has removed its research).
The Hudson Rock post claimed that a Snowflake employee may have been infected by an infostealer that collected the details the hacker needed to log in to its systems. Charles Carmakal, the chief technology officer at Google-owned security firm Mandiant, told BleepingComputer that its investigations, which have been taking place in recent weeks, indicate information-stealing malware may have been used to get Snowflake account credentials.
A Ticketmaster spokesperson told TechCrunch that its stolen database was hosted on Snowflake after the company acknowledged a data breach in a filing to the Securities and Exchange Commission on Friday evening. In the middle of May, before its data was advertised online, Santander first said it had seen unauthorized access to one of its databases “hosted by a third-party provider,” however it has refused to name the third party.
Snowflake’s CISO, Jones, acknowledged the security incident on Friday, saying that if a “threat actor obtains customer credentials, they may be able to access the account.” The company says it became aware of the suspicious activity on May 23 but has since found out it had been happening since mid-April. Jones’ post says Snowflake has notified all of its customers and “encouraged” them to review account settings and ensure they have implemented multi-factor authentication. In an additional security bulletin, Snowflake says it has seen “malicious traffic” from a client calling itself “rapeflake” and also connections from another client called “DBeaver_DBeaverUltimate.” A company spokesperson tells WIRED they have “nothing else to add” beyond the information included in company posts.
Cloud security company Mitiga says its investigations have seen a threat actor targeting organizations using Snowflake databases and using an attack tool called “rapeflake” in the process. Roei Sherman, field CTO at Mitiga, tells WIRED one possible scenario is that a threat actor managed to get information about Snowflake’s systems and then stole information about its clients, possibly using automated tools and brute-forcing their way into accounts.
Sherman says little is known about what data was stolen at the moment or the “rapeflake” tool, but that the attack could have wider ramifications going forward. There are already early signs other companies may be impacted.
Sherman says some of Mitiga’s customers have reached out to it for help, while Mandiant told BleepingComputer it had been assisting Snowflake customers in recent weeks. Cybersecurity researcher Kevin Beaumont shared online that he knows of six companies that have been impacted. And Australian events company Ticketek has also revealed customer names and email addresses stored in a “cloud-based platform, hosted by a reputable, global third-party supplier” have been accessed, although a spokesperson refused to confirm if this was related to Snowflake at all.
“We haven’t seen the entire blast radius yet,” Sherman says. “Snowflake has thousands of clients—they offer self-registration—and some of their clients are huge companies. We expect to learn about additional companies compromised.”
18 notes
·
View notes
Text
Stay safe, everyone.
51 notes
·
View notes
Text
[VERY SERIOUS DISCLAIMER FOR THE FOLLOWING TEXT: I wrote this about three hours ago. It is currently 11:45am CST on 10/7/2023, and about an hour ago news sources started reporting Palestinian liberatory action. This situation concerned me before, and due to the connections the genealogical industrial complex has with the Israeli occupation and the Mormon church, I believe eyes should be on this. I do not believe this is a Palestinian effort, if I know anything about anything of US white supremacist extremist hate crimes, this reeks of it. Anyone saying that it is a Palestinian effort must be approached with extreme caution, especially if they are a Zionist. This is exactly the kind of thing that could be scapegoated. Do not let it. This is also about Chinese Americans and indigenous Americans, who have had a blood quantum measurement also put onto us.] I'm Ashkenazi Jewish + indigenous North American and I have been warning people for almost a decade that this was going to happen. I have had an extremely difficult time with reconnection to my bio family, and I am not the only one. 23andMe and other DNA database sites have capitalized on adoptees and lost indigenous people since their inception. It was a part of their initial business model. I keep my identity close to my chest, largely from white people but I'm also careful about who I share it with IRL - I'm passing as an active adjective. One of the reasons I don't get into it is because of these companies alone. When I have spoken about who I am with people who it was a mistake to talk about it with, their answer to all my woes is to "just take a DNA test if you really want it so bad." When I explain further what these companies do and how this data is collected, with several of them having headquarters and offices in Israeli-occupied Palestine and Utah where the Mormon church is extremely involved (solidifying a very legitimate business connection & alliance between two religious self-claiming "authorities"), I am dismissed. It does not matter to people. There is a staunch belief that if you "really are that thing, you have to prove it with DNA," AS IF THERE IS NO OTHER WAY TO DO THIS.
This data is dangerous. I'm an anthropologist, currently working on digital anthro among other things. It has never been safe for the thing that white supremacists use to determine our humanhood to be collected by a company whose mission is to profit on eugenics and genocide. This was always going to happen. In this instance, it was specifically Jews and Chinese people which this article title does not do justice.
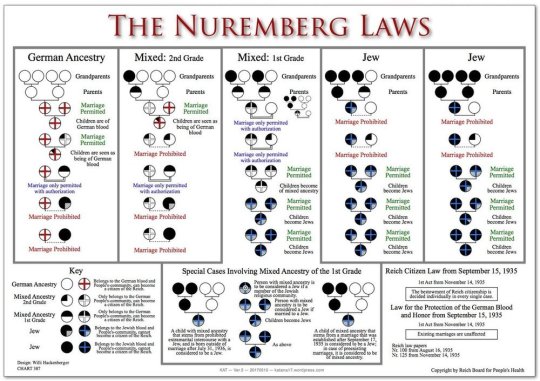
If you have taken one of these tests in your life, there is now not really much you can do except protect yourself in the ways you can. Their ToS and copyright agreement are extremely unethical and always have been. You can request for them to destroy your data, but that doesn't actually guarantee that it's going to happen or that they haven't already sold it/shared it or your other information for research or commercial marketing purposes. Otherwise, I highly recommend a) doing the most you can to protect yourself online, b) locking down your finances and credit if you feel comfortable and confident doing so, c) and familiarizing yourself with the Nuremberg blood quantum chart below to see if you are affected by this given your results because yes, this is their end-game. If you fall on this chart at all, you are at risk. This is about the blood that runs through your veins, not about your social and cultural life as you know it right now.
Given my disclaimer above, please watch out for further news on this. This is not nothing. This is extremist terrorist planning that has the potential to be very far-reaching.
20 notes
·
View notes
Quote
米遺伝子検査企業の23andMeは12月4日(現地時間)、同社のサービスを利用した690万人の個人情報が10月に盗まれていたと、米TechCrunchなど複数の米メディアに認めた。 同社は10月に公式ブログで、サイバー攻撃に遭い、顧客プロフィール情報が漏えいしたことを発表していたが、対象となった顧客の人数などは公表していなかった。 10月初旬には、ハッキングフォーラムBreachForumsに23andMeユーザーのDNA情報を盗んだという投稿があった。その証拠として、ユダヤ系ユーザー100万人と中国人ユーザー10万人の情報とされるデータを公開した。 盗まれたデータには、氏名、誕生年、関係ラベル、親族と共有されているDNAの割合、祖先報告、自己報告された場所が含まれていたが、クレジットカード番号などはなかった。 同社は米証券取引委員会(SEC)に提出した文書で、23andMeのWebサイトで使用されているユーザー名とパスワードが他のWebサイトで使用されているものと同じである場合に、攻撃者がユーザーアカウントのごく一部(0.1%)にアクセスできたと判断したと説明している。人数にして約1万4000人に相当する。 だが、23andMeはメディア宛のメールで、ユーザーがデータの一部を他のユーザーと共有する機能「DNA Relatives」を有効にしていた約690万人の個人情報も攻撃者が取得できていたと説明した。 つまり、10月に報告していたユーザーの0.1%ではなく、ユーザーのほぼ半数の個人情報が漏えいしたことになる。 この侵害への対策として、23andMeはすべてのユーザーにパスワードのリセットと、2要素認証の使用を要求している。
23andMe、690万人のDNAデータを含む個人情報が盗まれたと認める - ITmedia NEWS
3 notes
·
View notes
Text
what do you fucking MEAN the internationally-wanted (current) owner of the breachforums, intelbroker, collaborated with a fucking minecraft youtuber to dupe a popular server's economy into complete chaos. what do you fucking MEAN their username is Thick
2 notes
·
View notes
Text
Santander Bank Hit by Major Data Breach, Customer Data Compromised

A notorious hacking group known as ShinyHunters is attempting to sell confidential data belonging to millions of Santander bank employees and customers. This cybersecurity incident follows the group's recent claim of breaching Ticketmaster, a major ticket sales platform. Santander, a global banking giant with over 200,000 employees worldwide, has confirmed that the attack had stolen data. The bank has apologized, stating, "we apologize for the concern this will understandably cause," and is actively contacting affected customers and employees. Scope of the Data Breach According to ShinyHunters' advertisement on Breachforums, the stolen data includes sensitive information such as: - 30 million people's bank account details - 6 million account numbers and balances - 28 million credit card numbers - Human resources information for staff Santander has not commented on the accuracy of these claims. However, the bank has stated that no transactional data or credentials that would allow unauthorized transactions were included in the breach. Investigation and Response In a statement, Santander revealed that the data breach affected customers from Santander Chile, Spain, and Uruguay, as well as current and some former employees. The bank has assured customers that its banking systems remain unaffected, allowing secure transactions to continue. Cybersecurity experts have expressed caution regarding ShinyHunters' claims, suggesting the possibility of a publicity stunt. However, researchers at Hudson Rock believe the Santander breach and the alleged Ticketmaster incident are linked to a major ongoing hack targeting a cloud storage company called Snowflake. Snowflake has acknowledged "potentially unauthorized access" to a limited number of customer accounts, stating that hackers gained access using login information from a former employee's demo account, which did not contain sensitive data. Read the full article
3 notes
·
View notes
