#Business Data Security
Explore tagged Tumblr posts
Text
Cloud Data Management Services: Benefits & Risks

In today’s digital landscape, managing growing volumes of data efficiently and securely is vital for businesses. Cloud data management services offer a scalable, flexible, and cost-effective solution compared to traditional database management, which requires significant upfront investment in on-premises hardware. Cloud services allow businesses to store and access data over the internet, eliminating the need for physical infrastructure, and enabling effortless scalability, global accessibility, cost-effectiveness, and reliable disaster recovery.
However, businesses must also consider risks such as data privacy concerns, potential downtime, vendor lock-in, and compliance challenges. Stigasoft, an ISO and CMMI Level 3 Certified provider, offers robust cloud data management services with a focus on high-quality standards, experienced professionals, and 24/7 support. By partnering with Stigasoft, businesses can leverage the full potential of cloud data management while mitigating associated risks for a seamless and secure experience.
If you want to get complete information related to this topic click HERE.
#stigasoft#cloud data management#datamanagementservices#DigitalTransformation#business data security#CostEffectiveSolutions#DataPrivacy#CloudTechnology#agiledatamanagement#isocertified#cloud integration#dataprotection#DigitalBusiness
0 notes
Text
#Employee monitoring#Mobile spy apps#Monitor employee emails#Call monitoring software#Business data security#Workplace productivity tools#Employee surveillance apps#Corporate monitoring solutions#Email and call monitoring#Employee communication monitoring
0 notes
Text




#hacks#hacksedit#hacks hbo#deborah vance#deborahvanceedit#tvedit#usertelevision#filmtvcentral#dailyflicks#cinemapix#useroptional#mine#edit#*#callback*#i love callbacks#tag meta#evidence*#hacks spoilers#something so... sad? about this to me#like i'm sure it really was in part chosen for the business/legal aspect#but at the same time - deborah isn't marcus. marcus was so crucial to her business /for a reason/#deborah makes emotional and fear-driven choices and the fact that she chose singapore#which she had JUST been told was a demographic of people who appreciated her#when she's scared and afraid and needs her fix of laughter. she finds a venue where the data suggests she'll succeed#and it's the perfect amount of backslide for her i think - she's still not walking back her choice of ava over the show#but she also isn't ~brave enough to just forge ahead with a new path. she needs familiarity and security#she needs her old comedy and her old audience and her old carefree attitude#she can get the first two back and the fact that ava irrevocably changed the third is a big part of why she's spiraling so hard#how do you reconcile deep love of the person who made you someone that can never be satisfied with your old comforts again?
336 notes
·
View notes
Text
I am so unbelievably pissed off. FUCK HOAs
Oh, my trash/recycling bin can't be visible except on pickup day? Ok whatever fine I hate you but I can deal with this
Weekly inspections?????? FU FU FU FU FU
SECOND NOTICE ALSO WE'RE CHARGING YOU MONEY TO SEND YOU CERTIFIED MAIL OF THIS TOTALLY LEGIT TOTALLY SECOND NOTICE OF WHAT IS ACTUALLY A VIOLATION cue me: checks notes. Hmm. My recycling bin was. on the curb. on recycling pickup day. You know. The day it has to be out. The day it is motherfucking ALLOWED TO BE FUCKING OUT AND VISIBLE.
so. 1) not a violation
I have sent them the trash AND recycling pickup schedules, which are DIFFERENT, btw
I have disputed the fact of the violation
I have disputed the linking of this "violation" to a previous violation MONTHS AGO--their "first notice" in this case was a "Courtesy Notice" LITERALLY 5 MONTHS AGO and they've done so many inspections since then and my bin CLEARLY WASN'T OUT IN THOSE INTERVENING MONTHS so WTMFH
So I am posting like a crazy person here instead of sending the absolutely deranged email I almost sent (I did send a slightly less deranged version with the disputes, and requesting a hearing)
OMG. It has been. Less than one hour since I learned this fun fun news. My bin was out YESTERDAY, y'all. YESTERDAY. I am going to blow a gasket
#it's a relatively privileged problem to have (omg i have a home truly i am grateful) but it's still a goddamned problem and i'm allowed#to fucking complain about it#in case it needs to be said#*rolling my eyes*#i advocate for free/actually affordable housing for everyone who needs it because we ALL deserve a safe secure stable home#whatever type of home that may be#it is absolutely goddamned ridiculous that megacorps can buy all the housing#rent it out at extortionate rates and evict people willy nilly#and we're talking about a “housing crisis” and not a “STOP LETTING CORPORATIONS AND BILLIONAIRES HOARD ALL THE HOUSING” crisis#goddamn.#ha elect me president (ahaha don't do this i am not a good public speaker) and I'll push congress to pass some really neat legislation#hey be more direct: elect me to congress (ahaha don't do this) and i'll WRITE some goddamn nifty legislation and yell about it as long and#as loud as i can until people start to just fucking say yes to make me shut the fuck up#(i know that's not how it works. again. don't actually elect me to a government position)#exemplia gratis:#No individual person shall own more than 6 homes UNLESS they pay a Housing Market Shrinkage Fee for removing viable housing from the market#why 6 and not 2? 2 is a lot! it's excessive! but having A vacation home shouldn't be a crime. Having 5 vacation homes is ridiculous and#awful and whatever but it's not likely to be the source of all our greatest “housing shortage” problems. no. I'm aiming for the absolutely#monstrously greedy and egregious motherfuckers who---ok#hang on. how many homes does the average min and max homeowner own? I would like to see data on that. but anyway#the next part of the legislation:#Homes owned >6 shall be charged X% Housing Market Shrinkage Fee UNLESS they are rented for affordable (15% or less than renter net income)#housing and are actively occupied by said renters. Rented out and charging more than 15% of renter's net? still gotta pay up.#EMPTY housing >6 shall be subject to an additional Y% Housing Market Shrinkage Fee (tax? should I call it a tax?) which increases with ever#month that the housing goes unoccupied. no one living in it? sell it rent it or pay the fuck up. and still pay the fuck up if you rent it#for way too goddamn much money#but like. less. we only REALLY hate you if you sit on empty houses that you don't even let anyone use#ok that's individuals. now onto BUSINESSES#ok so immediately it gets a little complicated cuz like presumably there's rental management businesses that don't own the rental propertie#that they manage BUT there are also companies that just outright own a shitfuckton of housing and THIS is the truly egregious monstrous sid
24 notes
·
View notes
Text
Abathur

At Abathur, we believe technology should empower, not complicate.
Our mission is to provide seamless, scalable, and secure solutions for businesses of all sizes. With a team of experts specializing in various tech domains, we ensure our clients stay ahead in an ever-evolving digital landscape.
Why Choose Us? Expert-Led Innovation – Our team is built on experience and expertise. Security First Approach – Cybersecurity is embedded in all our solutions. Scalable & Future-Proof – We design solutions that grow with you. Client-Centric Focus – Your success is our priority.
#Software Development#Web Development#Mobile App Development#API Integration#Artificial Intelligence#Machine Learning#Predictive Analytics#AI Automation#NLP#Data Analytics#Business Intelligence#Big Data#Cybersecurity#Risk Management#Penetration Testing#Cloud Security#Network Security#Compliance#Networking#IT Support#Cloud Management#AWS#Azure#DevOps#Server Management#Digital Marketing#SEO#Social Media Marketing#Paid Ads#Content Marketing
2 notes
·
View notes
Text
For Security Purposes, I am Shutting Down the Wild Hemlock Facebook and Instagram Accounts
Meta knows every website you visit that has the Meta Pixel installed.
And who you are.

Don't worry - I'm staying here on Tumblr! But stop by and take a look at the New and Improved WildHemlock.Com!
As explained by The Register, Hacker News, and elsewhere, all of the apps created by Meta (formerly Facebook) are exploiting a permission in the Android operating system to track everything you do on mobile web browsing apps such as Chrome, Firefox, and even partially DuckDuckGo. According to LifeHacker, the mobile web browser Brave successfully blocked the tracking. I could not find any information about other web browsers such as Vivaldi or the many additional Firefox flavors.
So how is Meta doing this exactly? First, let’s talk about apps. The Instagram app only allows you to post via mobile app which is additionally nefarious. When Meta’s apps are installed on your phone, it will continually run in the background as a service. This grants the app additional privileges. For a popular example, YouTube didn’t always use to be able to make a video play while you were using another app. It was rewritten some time ago as a service, as opposed to a normal app, and now it can play both audio or picture-in-picture while you use your phone and other apps because it has more permissions. This is the type of app that Facebook and Instagram are.
Android services have access to what is referred to as localhost. Think of it like the local device hosting the app – it is an address which loops back to your phone. The address is 127.0.0.1 in web browsing – it points back to your own computer. If you were hosting a service on your computer, it would open service when you type “127.0.0.1” into the address bar of your web browser. This is very useful for developers, both on a mobile phone or computer, especially for testing network programming.
Wild Hemlock Will NEVER Install a Meta Pixel Script!
Learn More @ WildHemlock.Com!
#wildhemlock#wild#hemlock#localhost#facebook#meta#instagram#leavingfacebook#leavinginstagram#opsec#security#mobile phone#android#meta pixel#surveillance#data leak#tech explained#basic opsec#basic security#tech#technology#technology explained#social media#article#small business#etsy#shop small#leaving facebook#leaving instagram
2 notes
·
View notes
Text
'if youre looking to be secure, MFA is best' shut up + dont speak to me again + rot in hell + fuck you + fuck you again + let me turn it off or i crush you and your family with my psychic powers.
#i dont care if MFA made you guaranteed safe from any and all malware and security breaches#Im Not Doing That!!!!!#if u think im chaining myself to one phone youre out of your mind. this things gonna give up the ghost any day now!!!#and her battery is shit so shes dead a lot of the time anyway! plus sometimes its just in the other room!!! Fuck You!!!!#worst security measure by far. hate it.#hate it when banks try to pull it when paying for stuff. fuck it! take my bank details i dont care#ive carefully curated an ascetic life for myself where i keep as little money in my actual account as possible#both to curb against impulsive online purchases (bcos i need to go into town to put money into my account b4 buying anything)#and because i fancy myself cool and roguish and anti-establishment when likely what i am is a fucking fool but whatever. not punished so fa#EDIT WAIT TAG RANT NOT FINISHED I REMEMBER WHY I WAS ON IT!!!#FUCKING BITWARDEN WANTS ME TO SWITCH TO 2FA AND GOT PISSY AT ME IN SETTINGS WHEN I SWITCHED IT BACK???#bro youre my fucking password manager. do you know why youre here?#for a couple months i lived off demo sessions of debian where all my data vanished every time i turned off my laptop#and i got thru it BECAUSE! OF! BITWARDEN! because i could just log into my vault and continue business as usual!#without having to piss around with my phone!! fuck!!!!!!!!!!!!!!!!!!!!!#like bro cmon. ideal world is one where i can just decide to go use a library computer with no tech on me and have it fuckinggg work#Because I Have All My Passwords In My Vault And I Have A USB Stick For Retaining Files#aughh. augh!!!!!!!!!!!!!!!!!!!!!! i just want to be anonymous#well. in a technical sense. in a broader sense the previous post is me talking extensively abt my irl presentation#but whatever. i dont get into discourse these days i trust u tumblrinas < bad thing to say but what the fuck ever#my famous catchphrase Last Time I Got Doxxed Nothing Came Of It So If It Happens Again I'll Probably Be Fine
3 notes
·
View notes
Text
French initiative for responsible AI leaders - AI News
New Post has been published on https://thedigitalinsider.com/french-initiative-for-responsible-ai-leaders-ai-news/
French initiative for responsible AI leaders - AI News
ESSEC Business School and Accenture have announced the launch of a new initiative, ‘AI for Responsible Leadership,’ which marks the 10th anniversary of the establishment of the role of Chair at ESSEC, titled the ESSEC Accenture Strategic Business Analytics Chair.
The initiative aims to encourage the use of artificial intelligence by leaders in ways that are responsible and ethical, and that lead to high levels of professional performance. It aims to provide current and future leaders with the skills they require when faced with challenges in the future; economic, environmental, or social.
Several organisations support the initiative, including institutions, businesses, and specialised groups, including ESSEC Metalab for Data, Technology & Society, and Accenture Research.
Executive Director of the ESSEC Metalab, Abdelmounaim Derraz, spoke of the collaboration, saying, “Technical subjects are continuing to shake up business schools, and AI has opened up opportunities for collaboration between partner companies, researchers, and other members of the ecosystem (students, think tanks, associations, [and] public service).”
ESSEC and Accenture aim to integrate perspectives from multiple fields of expertise, an approach that is a result of experimentation in the decade the Chair has existed.
The elements of the initiative include workshops and talks designed to promote the exchange of knowledge and methods. It will also include a ‘barometer’ to help track AI’s implementation and overall impact on responsible leadership.
The initiative will engage with a network of institutions and academic publications, and an annual Grand Prix will recognise projects that focus on and explore the subject of AI and leadership.
Fabrice Marque, founder of the initiative and the current ESSEC Accenture Strategics Business Analytics Chair, said, “For years, we have explored the potential of using data and artificial intelligence in organisations. The synergies we have developed with our partners (Accenture, Accor, Dataiku, Engie, Eurofins, MSD, Orange) allowed us to evaluate and test innovative solutions before deploying them.
“With this initiative, we’re taking a major step: bringing together an engaged ecosystem to sustainably transform how leaders think, decide, and act in the face of tomorrow’s challenges. Our ambition is clear: to make AI a lever for performance, innovation and responsibility for […] leaders.”
Managing Director at Accenture and sponsor of the ESSEC/Accenture Chair and initiative, Aurélien Bouriot, said, “The ecosystem will benefit from the resources that Accenture puts at its disposal, and will also benefit our employees who participate.”
Laetitia Cailleteau, Managing Director at Accenture and leader of Responsible AI & Generative AI for Europe, highlighted the importance of future leaders understanding all aspects of AI.
“AI is a pillar of the ongoing industrial transformation. Tomorrow’s leaders must understand the technical, ethical, and human aspects and risks – and know how to manage them. In this way, they will be able to maximise value creation and generate a positive impact for the organisation, its stakeholders and society as a whole.”
Image credit: Wikimedia Commons
See also: Microsoft and OpenAI probe alleged data theft by DeepSeek
Want to learn more about AI and big data from industry leaders? Check out AI & Big Data Expo taking place in Amsterdam, California, and London. The comprehensive event is co-located with other leading events including Intelligent Automation Conference, BlockX, Digital Transformation Week, and Cyber Security & Cloud Expo.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.
#accenture#ai#ai & big data expo#ai news#amp#Analytics#anniversary#approach#artificial#Artificial Intelligence#automation#Big Data#Business#business analytics#california#Cloud#Collaboration#Companies#comprehensive#conference#cyber#cyber security#data#data theft#deepseek#deploying#Digital Transformation#economic#education#employees
3 notes
·
View notes
Text
obnoxious that I can't just use a computer to do the things I've always used computers to do, now I have to use two different computers including one with specialized hardware for interfacing with an entirely different network of interdevice communication. I don't wanna turn on goddamn mfa, and it's insufferable when I have to goddamn pull out another hundreds of dollars of tech just to be allowed to use your site's search (because you forbid it unauthenticated)
#on the one hand I get that having stronger security for authentication is nice.#on the other hand though. if you don't trust the individual with whom you have to authenticate for the service they have a monopoly over#then you have to fuckin sacrifice your operational security in the name of making some other individual feel better about their lax securit#which like. fine whatever dont do business with people you dont wanna do business with. except for like. fucking github#like you want the gpl'ed source code for the quake engine#youre gonna have to endure microsoft and github and a million petty tyrants who demand every bit of data just for fundamental functionality#ugh I don't know I have any coherent complaints I'm just whinging bc I had to use two computers for a task one computer can do
5 notes
·
View notes
Text
Hackers steal AT&T data
2 notes
·
View notes
Text
Cloud and Data: A sidewalk!
In a world where 10 million data generate each hour, is there any business identity without data? Apart from the hypothetical world that pushes businesses to adopt a plan that is enriched towards an unattainable goal for objectives stepping forward through the wave of optimism, can any spectrum of business meet the goal without a shower of data?
Read the full blog.
2 notes
·
View notes
Text
Sigzen Technologies: Transforming Challenges into Opportunities with Robust Backup and Disaster Recovery Solutions
In today’s fast-paced digital world, where data plays a crucial role in business operations, having a reliable Backup Solution and Disaster Recovery plan is paramount. Sigzen Technologies emerges as a leader in this space, offering cutting-edge solutions that not only safeguard critical data but also transform challenges into opportunities for businesses. Automated Backup An automated backup…

View On WordPress
#Business Continuity Strategies#Cloud Backup Excellence#Data Protection Standards#Data Security Leaders#Sigzen Tech Solutions
3 notes
·
View notes
Text
Third-Party Cyber Insurance Coverage Explained | Cyber Insurance in India

In today’s digital world, cyber risks are not just internal threats. Data breaches, identity theft, and cyberattacks can trigger lawsuits, penalties, and third-party claims, making cyber insurance in India a necessity, not a choice.
One essential part of any cyber insurance policy is Third-Party Coverage. Unlike first-party coverage (which protects your own business), this coverage shields you from claims made by others — customers, clients, vendors, or regulatory authorities.
Let’s explore:
What is cyber insurance?
What is third-party cyber liability coverage?
Why Indian companies need it
Key risks covered
Difference between first-party & third-party coverage
Benefits for corporates, SMEs, and startups
What is Cyber Insurance?
Cyber insurance, also known as cyber security insurance or cyber liability insurance, protects businesses from financial loss due to cyber threats like:
Data breaches
Malware & ransomware attacks
Hacking & phishing
Unauthorized access
Business interruption
Today, cyber insurance in India is an integral part of commercial insurance portfolios, especially for digital-first companies.
What is Third-Party Coverage in Cyber Insurance?
Third-party coverage refers to the protection provided against claims, legal actions, or regulatory penalties brought by external parties affected by a cyber incident in your organization.
For example:
If your systems are hacked and customer data is leaked, your clients may sue you.
If a business partner suffers loss due to a cyber breach on your end, they may file a claim.
If a regulator penalizes you for failing to protect personal data, you're liable.
Third-party cyber insurance pays for your legal defense, settlements, and related costs.
What Does Third-Party Cyber Insurance Cover?
Here’s a breakdown of key coverages under third-party liability in cyber insurance:
1. Legal Defense Costs
Covers attorney fees, court expenses, and legal proceedings if a third party sues your company for negligence or data loss.
2. Regulatory Fines & Penalties
Pays penalties imposed by government bodies or regulators (like CERT-In, RBI, IRDAI) for non-compliance with data protection laws.
3. Third-Party Damages
If a client or partner suffers financial loss due to your cyber incident, this coverage compensates them.
4. Media Liability
Covers claims related to defamation, copyright infringement, or libel from your digital content (especially relevant to media, tech, or advertising companies).
5. Privacy Liability
Protects against lawsuits stemming from loss or mishandling of personal identifiable information (PII) or sensitive customer data.
Third-Party vs First-Party Cyber Coverage
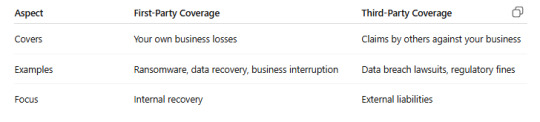
A complete cyber insurance policy should include both coverages for end-to-end protection.
Why Indian Businesses Need Third-Party Coverage
Cybersecurity threats in India are rising exponentially, especially with digital payments, cloud adoption, and remote work becoming mainstream.
Here’s why third-party coverage in cyber insurance is critical for Indian companies:
India has the second-largest number of internet users globally — more users mean more data to protect.
The DPDP Act (Digital Personal Data Protection Act) mandates strict privacy compliance.
A data breach now costs Indian companies an average of ₹18.3 crore.
Increasing legal scrutiny and class-action suits around personal data exposure.
Whether you're in e-commerce, fintech, healthcare, or education, third-party risks can impact your brand reputation, finances, and operations.
Who Should Opt for Third-Party Cyber Liability Coverage?
✅ Corporates and enterprises handling large-scale consumer or partner data ✅ Startups and SMEs operating online platforms, apps, or digital services ✅ IT and BPO companies with access to client databases or networks ✅ Healthcare and BFSI sectors governed by strict data privacy regulations ✅ Any company looking to strengthen its business insurance or company insurance coverage
How to Choose the Right Cyber Insurance Policy
When selecting a cyber insurance policy, ensure it includes:
Both first-party and third-party protection
High coverage limits for legal claims & data breaches
Coverage of legal expenses, settlements, and privacy violations
Add-ons like crime insurance and reputation damage control
Fast claims support and cyber incident response
🧩 Real-World Example
Case: Indian Fintech Startup (2023) A fintech firm faced a lawsuit after hackers breached their system and leaked customer KYC data. Customers sued the company, and regulators imposed fines. Their third-party cyber insurance covered:
₹2.5 crore in legal fees
₹1 crore in regulatory fines
₹1 crore in settlements with affected users
Without cyber coverage, these costs could have crippled the startup.
Final Thoughts
Cyber and crime insurance isn’t just about securing IT systems — it’s about protecting your business from reputational and legal ruin. Third-party coverage ensures you're prepared for legal backlash and financial liability when things go wrong.
In a digitally connected economy, having robust cyber insurance in India is no longer optional — it's essential for insurance for corporations, startups, and all modern businesses.
#cyber insurance#third-party cyber insurance#cyber insurance in India#cyber security insurance#cyber insurance policy#cyber liability insurance#business insurance#commercial insurance#cyber and crime insurance#company insurance#insurance for corporations#data breach lawsuit#regulatory fines cyber#privacy liability coverage
1 note
·
View note
Text
Deception Technology: The Cybersecurity Paradigm We Didn’t Know We Needed
In an age of ever-evolving cyber threats, traditional security measures are no longer sufficient to protect critical digital assets. To stay ahead of sophisticated attackers, organizations are turning to more innovative and proactive solutions. One such approach gaining momentum globally is Deception Technology — a cybersecurity strategy that shifts the paradigm from reactive defenses to…
#AI in Cybersecurity#breach detection#business#Business Intelligence#Cloud Security#cyber defense#cyber threat#cyber traps#cyber warfare#cybersecurity#data privacy#deception#Deception Technology#decoy systems#enterprise security#insider threat detection#Machine Learning#Network Security#proactive threat detection#Security#technology#threat intelligence
1 note
·
View note
Text
The Control Paradox: When Small Business Owners Choose Risk Over Security
When Competence Isn’t Enough: The Client Who Sabotages Their Own Business You deliver exceptional IT service—systems are secure, downtime is minimal, and your team is always responsive. The client even acknowledges your expertise and the value you provide. Then, without warning, they demand full administrative access and soon after, terminate your managed services contract, citing a need for…
#business risk#control-driven clients#cybersecurity#data breach#downtime#IT leadership#IT management#managed IT#msp#small business security
0 notes
Text

Safeguard your business with Bizionic Technologies’ cyber security solutions. From threat detection to data protection, we provide end-to-end security for a safer digital future. Contact us today!
#Cybersecurity services for businesses#Cyber threat protection#IT security solutions#Network security services#Data breach prevention#Cloud security solutions#Business data protection
0 notes