#Penetration Testing
Explore tagged Tumblr posts
Text
Abathur

At Abathur, we believe technology should empower, not complicate.
Our mission is to provide seamless, scalable, and secure solutions for businesses of all sizes. With a team of experts specializing in various tech domains, we ensure our clients stay ahead in an ever-evolving digital landscape.
Why Choose Us? Expert-Led Innovation – Our team is built on experience and expertise. Security First Approach – Cybersecurity is embedded in all our solutions. Scalable & Future-Proof – We design solutions that grow with you. Client-Centric Focus – Your success is our priority.
#Software Development#Web Development#Mobile App Development#API Integration#Artificial Intelligence#Machine Learning#Predictive Analytics#AI Automation#NLP#Data Analytics#Business Intelligence#Big Data#Cybersecurity#Risk Management#Penetration Testing#Cloud Security#Network Security#Compliance#Networking#IT Support#Cloud Management#AWS#Azure#DevOps#Server Management#Digital Marketing#SEO#Social Media Marketing#Paid Ads#Content Marketing
2 notes
·
View notes
Text
15 Best Free Resources for Malicious URLs and Phishing Links for Cybersecurity Testing
In today’s rapidly evolving cybersecurity landscape, having access to reliable sources of malicious URLs, phishing links, and malware samples is essential for security professionals, penetration testers, and IT administrators. Whether you’re validating your security controls, conducting security awareness training, or researching new threat vectors, accessing known malicious content in a…
#cyber threats#cybersecurity#ethical hacking#malicious URLs#malware analysis#malware samples#penetration testing#phishing detection#phishing links#security controls#security testing#security tools#security validation#threat intelligence#web security
3 notes
·
View notes
Text
youtube
A look into security.
2 notes
·
View notes
Text
finding usernames/passwords for testfire.net
background: testfire.net is a "fake" website designed for pentesters to play around with. it is NOT a real bank and no one's information is actually being stolen here. this was an assignment for a class.


first we start by logging into the admin account, username: admin and password: admin. although a general SQL injection works on this site. for the inject, password is irrelevant.
other injects that work (note that's not a quotation, that's two apostrophes):
' or ''='
' or '1' = '1
or any other statement that will always be true
on the left we see we can "Edit users"


our assignment was to find username and password pairs. you'd think you could cheekily change the passwords of existing accounts or add new accounts to fulfill this requirement, but none of these options on the admin page actually work.

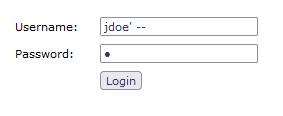
we can see the usernames of several users. since we know the username field is vulnerable to injects, we can now login to any of these without knowing the password.

this field is also vulnerable to injects. inject used:
' --
okay never mind post cancelled
i just checked the solution that my professor wanted and i shit you not its this:

these do technically work as username and password pairs. like, if you use them, you will sign in. in fact, i think you can just put anything other than a blank space for the password and it would count. but man. fuck this.
regardless, here are some actual pairs that i ended up finding. i cant quite remember how i found them, but i saw someone use "demo1234" as a password for both jdoe and jsmith, so i tested sspeed and its the same password. cant find the other ones though.
jdoe | demo1234
jsmith | demo1234
sspeed | demo1234
2 notes
·
View notes
Text



Emile Walker from Penetration Testing is demisexual!
2 notes
·
View notes
Text
Staying Relevant: Balancing Learning and Life as an Ethical Hacker
Have you experienced burnout while trying to develop your skills and you just don't have the time to do everything? Finding balance is the key to improving your skills in a healthy way. In this article, I explore healthy habits to grow without burning out
You’ve heard it before – cybersecurity is a field that evolves at a blindingly fast pace. The tools, techniques, and technologies threatening networks transform rapidly. As an ethical hacker, your skills can become obsolete within months if you aren’t continuously upgrading your knowledge. Point #4 on our hacker roadmap deals with knowing the latest and greatest when it comes to the state of…

View On WordPress
#burnout#certifications#conference#continuous learning#Cyber Security#cybersecurity education#cybersecurity skills#Ethical Hacking#hacker skills#infosec community#leadership#learning plan#maintaining balance#microlearning#Penetration Testing#pentesting methodologies#personal development#podcast#red team operations#security news#security policies#security tools#time management#trends#vulnerability assessments#work-life balance
3 notes
·
View notes
Text
The Role of Residential Proxies in Cybersecurity Testing

Cybersecurity testing demands authentic simulation of real-world attack scenarios. Residential proxies have become indispensable tools for security professionals conducting penetration testing, vulnerability assessments, and security audits. By providing genuine residential IP addresses, these proxies enable realistic testing that reveals vulnerabilities invisible to traditional datacenter-based approaches.
Authentic Attack Simulation
Modern security systems easily identify and block datacenter IP ranges, creating dangerous blind spots in security assessments. Attackers don’t limit themselves to datacenter IPs—they leverage compromised residential devices, VPNs, and distributed networks. Testing exclusively from datacenter IPs provides false confidence while leaving residential-origin vulnerabilities unexposed.
Residential proxies enable security teams to simulate attacks from diverse geographic locations and ISP networks. This authenticity reveals location-based security gaps, geo-blocking effectiveness, and behavioral analysis accuracy. Testing from residential IPs mirrors actual threat actor techniques, providing realistic vulnerability assessments.
Penetration Testing Applications
Web application penetration testing benefits significantly from residential proxy deployment. Many applications implement different security measures for datacenter versus residential traffic. Rate limiting, CAPTCHA challenges, and behavioral analysis often relax for residential IPs, assuming legitimate user activity.
Security teams leverage residential proxies to test authentication systems, session management, and access controls from realistic sources. Distributed testing across multiple residential IPs reveals race conditions, improper state management, and authentication bypass vulnerabilities that single-source testing misses.
API security testing requires residential proxies to accurately assess rate limiting implementations and geographic restrictions. Many APIs trust residential sources more than datacenter IPs, potentially exposing security vulnerabilities to attackers using similar infrastructure.
Compliance and Reconnaissance
Security assessments must verify compliance with geographic restrictions and data residency requirements. Residential proxies from specific countries enable thorough testing of geo-blocking implementations, ensuring sensitive data remains inaccessible from restricted regions.
Reconnaissance phases benefit from residential proxy anonymity. Security teams gather public information about targets without revealing corporate IP addresses that might trigger defensive measures or alert targets to upcoming assessments. This stealth enables more accurate vulnerability discovery.
Ethical Considerations and Best Practices
Responsible security testing requires explicit authorization and defined scope. Document residential proxy usage in testing methodologies, ensuring clients understand the comprehensive nature of assessments. Maintain detailed logs of testing activities, IP addresses used, and actions performed.
Choose proxy providers committed to ethical sourcing and user consent. Legitimate security testing demands legitimate infrastructure. Verify providers obtain proper consent from residential IP owners, maintaining ethical standards throughout testing engagements.
Enhanced Security Posture
Organizations embracing residential proxy-based security testing discover vulnerabilities traditional methods miss. This comprehensive approach strengthens defenses against sophisticated attackers who routinely leverage residential infrastructure. Investment in proper testing tools, including residential proxies, proves minimal compared to potential breach costs.
#penetration testing#cyber security#residential proxies#security testing#proxy lust inc.#proxy lust proxies
0 notes
Text
Types of Penetration Testing | IIFIS
Penetration testing includes various types like network, web application, wireless network, social engineering, and physical testing. Each type helps identify and fix security gaps, making systems safer from cyber threats and unauthorized access. https://iifis.org/blog/what-is-penetration-testing-in-cybersecurity
0 notes
Text
VirtualBox Guest Additions on Kali Linux Install Guide 2025
Installing VirtualBox Guest Additions on Kali Linux packages correctly is crucial for optimal virtual machine performance. Many users struggle with fullscreen display issues, shared folders, and clipboard functionality when running Kali Linux on VirtualBox. This comprehensive guide provides the definitive method for installing these essential packages in 2025. Check the 256MB Video memory and 4GB…
0 notes
Text
How effective is Red Teaming & Pen Testing?
In today’s digital landscape, ensuring cybersecurity is crucial for organizations of all sizes. One of the key approaches to identifying vulnerabilities in security systems is through Red Teaming and Penetration Testing (Pen Testing). But how effective are these strategies?
Evaluating the Effectiveness of Red Teaming
Through the simulation of real threats, red teaming evaluates an organization's defenses. Here’s how it proves effective:
Comprehensive Security Assessment: It offers an in-depth analysis of security measures and identifies weaknesses.
Realistic Scenarios: By mimicking actual threat actors, it provides a practical understanding of potential risks.
Team Improvement: The exercise fosters collaboration among security teams, enhancing their response strategies.
Assessing the Impact of Penetration Testing
Pen testing focuses on identifying vulnerabilities through controlled attacks. Its effectiveness can be summarized by:
Finding Weak Points: It draws attention to particular weaknesses that an attacker could take advantage of.
Prioritizing Threats: Helps organizations focus on critical areas needing protection.
Regulatory Compliance: Frequently necessary to adhere to rules and industry norms.
Both red teaming and pen testing play vital roles in strengthening an organization’s cybersecurity posture. By proactively identifying vulnerabilities, organizations can better defend against potential threats and ensure a safer digital environment.
0 notes
Text
Penetration testing isn't just about ethical hacking—it's a structured process that helps businesses discover and fix vulnerabilities before real attackers exploit them.
In cybersecurity, the penetration testing lifecycle is typically divided into five essential phases:
Planning & Reconnaissance
Scanning
Gaining Access
Maintaining Access
Analysis & Reporting
Each stage plays a vital role in identifying potential security gaps, especially for businesses in finance, healthcare, and technology sectors.
If you're managing sensitive data or infrastructure, understanding these phases helps you assess risk better and strengthen your defenses.
Dive deeper into the complete breakdown here: Read the Full Guide
1 note
·
View note
Text
What Is CREST Penetration Testing? Benefits & Importance

Five years from now, cybersecurity will face greater challenges and even higher risks. Currently, the global cybersecurity penetration testing market is worth $4.1 billion, and experts predict it will increase at a strong annual rate of 13.1% until 2033, due to more challenging cyber attacks, broader cloud use, and stronger data privacy rules. Commonly seen in Singapore but happening elsewhere in the Asia-Pacific region as well is a strong increase in the need for advanced testing like CREST penetration testing due to government support, increased digitalization, and the Smart Nation goal.
1 note
·
View note
Text
Coding and Scripting for Beginner Hackers
Learning to code and write scripts is a crucial skill for getting into ethical hacking and cybersecurity. Scripting allows you to automate repetitive tasks, develop your own custom tools, analyze data, and program everything from small hacking tools to machine learning models. Understanding and knowing how to code in different languages can be extremely useful when doing deep dives into malware…

View On WordPress
#Cyber Security#cybersecurity careers#Ethical Hacking#hacer certifications#hacking for beginners#hacking guide#hacking homelab#infosec#learn to code#learn to hack#Penetration Testing#Pentesting
4 notes
·
View notes
Text
The Artificial Intelligence Role in Penetration Testing and Cyber Defense
Introduction
The internet is growing at a pace never seen before, and cyber attacks are also developing in tandem. Companies all over the world are investing in online cyber security training so that experts are equipped with the tools to protect their networks. Penetration testing, the most critical element of cybersecurity, is a preventive strategy to find out vulnerabilities before the attackers can exploit them. With the introduction of artificial intelligence (AI), penetration testing and cyber defense mechanisms are transforming and becoming better.
This is an article on how AI is revolutionizing penetration testing and cybersecurity, its advantages, disadvantages, and future directions. Understanding what AI is doing in cybersecurity will enable cybersecurity experts to utilize AI-powered tools to further fortify their defenses against constantly changing cyberattacks.
The Growing Importance of Penetration Testing in Cybersecurity
Penetration testing, or ethical hacking, involves the simulation of cyberattacks to test the security stance of a company. It's a common practice in online cyber security courses as well as cybersecurity training since it enables experts to identify vulnerabilities and implement robust countermeasures.
Legacy methods of penetration testing put a great reliance on human resources, which is labor and time-intensive. Ethical hackers have to scan manually for vulnerabilities, assess probable exploits, and emulate attacks. Although the process works, it is normally hindered by human mistake and the sheer amount of potential threats.
The Role of AI in Cybersecurity and Penetration Testing
1. Automated Threat Detection
AI security systems are capable of scanning huge volumes of data in real-time to detect vulnerabilities and potential threats. AI applies machine learning algorithms to detect patterns and anomalies that are indicative of security breaches. Automated threat detection reduces the process significantly, obviating the time required to identify and respond to cyber threats, thereby enhancing the overall security standing of an organization.
2. AI-Based Vulnerability Scanning
Artificial intelligence-based vulnerability scanners may be employed to scan networks, systems, and applications on a continuous basis to identify security vulnerabilities. These scanners employ machine learning to enhance precision, minimize false positives, and initiate only real threats for further investigation. This feature is especially useful for online cyber security training companies, as it enables students to gain hands-on experience in vulnerability scanning based on real-life scenarios.
3. Improved Threat Intelligence
Threat intelligence is an essential element of cyber security. AI is capable of collecting and analyzing information from various sources, such as dark web bulletin boards, threat repositories, and network logs, and providing actionable insights. Organizations can remain proactive against new threats and modify their security strategy accordingly with AI-powered cybersecurity.
4. Ethical Hacking with AI
Ethical hacking demands strong technical expertise and skill, which can be supplemented using AI tools. AI may automate reconnaissance, exploit development, and post-exploitation analysis for ethical hackers. With the addition of AI security tools in ethical hacking, penetration testers can discover vulnerabilities more effectively and create better mitigation plans.
5. Real-Time Incident Response
One of the strongest advantages of AI in cybersecurity is its real-time incident response capability. AI security systems can detect and respond to threats before they can do extensive harm. By analyzing the patterns of attacks and predicting future threats, AI enhances the ability of an organization to prevent cyber incidents proactively.
Benefits of AI Implementation in Cybersecurity Defense and Training
Increased Efficiency and Accuracy
Artificial intelligence -based cybersecurity solutions can process massive amounts of data at unprecedented rates, allowing threat detection and mitigation at an accelerated pace. This efficiency decreases the burden on cybersecurity experts so that they can concentrate on strategic decision-making and incident management.
Cost-Effectiveness
Penetration testing and cyber defense procedures can be greatly minimized in operational costs through automating them using AI. Companies can use their resources more efficiently, making their cybersecurity staff available for high-priority work.
Adaptive Learning
AI security systems learn from emerging threats and adjust their defenses in response. This ability to learn by themselves means that cybersecurity defenses stay current, even against changing cyber threats.
Increased Hands-On Training
Cybersecurity training sessions can incorporate AI-based simulation platforms to offer practical experience in penetration testing and cyber defense. These platforms use actual attack scenarios to enable students to gain practical experience and prepare for actual cybersecurity challenges.
Incorporating AI in Cyber Defense: Challenges
False Positives and False Negatives
While AI improves the efficiency of threat detection, it is not infallible. AI-powered security software sometimes triggers false alarms or fails to detect sophisticated cyber attacks. AI models need continuous monitoring and adjustment to make them more accurate.
Dependence on Data Quality
AI systems depend on large data sets in order to operate efficiently. Outdated or incorrect data can undermine the efficacy of AI-based security systems. Organizations have to make sure that their AI models are trained on current and extensive cybersecurity data sets.
Ethical and Legal Issues
The use of AI in penetration testing and cyber protection is regulated by legal and moral issues. The organizations must ensure that AI-based penetration testing solutions are used responsibly and comply with the regulatory requirements.
Future Trends in AI-Powered Cybersecurity
With advancing AI technology, so will its application in cybersecurity. Some of the future trends are:
AI-Powered Autonomous Security Systems: Emerging cybersecurity systems might utilize completely autonomous AI systems capable of identifying, analyzing, and eliminating threats on their own without any human interaction.
AI-Powered Security Orchestration:AI will be utilized to automate and orchestrate security solutions so that processes of threat response are made more efficient.
AI-Augmented Cybersecurity Training: AI-enabled virtual labs and simulation platforms will be a critical part of cybersecurity training programs, offering students interactive hands-on training.
Quantum Computing and AI Security: With the growth of quantum computing, AI will be at the center of the creation of quantum-resistant cybersecurity regulations.
Conclusion
The use of AI for penetration testing and cyber defense is transforming the landscape of cybersecurity. AI security tools improve threat detection, automate vulnerability scanning, and enhance incident response. Organisations are better positioned to enhance their cybersecurity positioning and remain ahead of new threats with the use of AI security tools.
For working professionals who want to enhance their cybersecurity skills, one must take online cyber security training. Online platforms such as Guruface provide detailed cybersecurity training courses, teaching and practical experience that is necessary to excel in this profession. Since cyber attacks are evolving continuously, investment in cybersecurity training and ethical hacking courses is essential so that one has a strong defense system against cyber attacks.
0 notes
Text
Shodan-Dorks - Dorks for Shodan; a powerful tool used to search for Internet-connected devices
This GitHub repository provides a range of search queries, known as “dorks,” for Shodan, a powerful tool used to search for Internet-connected devices. The dorks are designed to help security researchers discover potential vulnerabilities and configuration issues in various types of devices such as webcams, routers, and servers. This resource is helpful for those interested in exploring network…
0 notes
Text
Why Cybersecurity Certifications Like ISO 27001 & SOC 2 Matter Today
Cybersecurity threats are growing—fast. Whether you're a startup or an enterprise, frameworks like ISO 27001 and SOC 2 can be the difference between peace of mind and panic.
At Cyber Guardians, we help businesses navigate: 🔐 What VAPT actually involves 💰 VAPT cost in India and what to expect ✅ How to get SOC 2 certification 📈 Getting ISO 27001 certified — minus the confusion
We’ve been there. Let us help you get compliant with confidence.
#VAPT companies in India#SOC 2 certification#ISO 27001 cost#cybersecurity#penetration testing#data compliance#infosec
0 notes