#Cloud Remote Direct Memory Access
Explore tagged Tumblr posts
Text
5th Gen AMD EPYC and H4D Virtual Machines For Cloud HPC

Next-generation HPC-optimized H4D VMs
At Google Cloud Next, Google Cloud introduced H4D virtual machines (VMs), their latest HPC machine type. Based on HPC capabilities, H4D virtual machines (VMs) fulfil the evolving needs of demanding workloads in manufacturing, weather forecasting, EDA, healthcare, and life sciences.
H4D virtual machines run on 5th generation AMD EPYC Processors with over 950 GB/s memory bandwidth and 12,000 gflops whole-node virtual machine performance. Cloud Remote Direct Memory Access (RDMA) on Titanium gives H4D, the first CPU-based virtual machine, minimal latency and 200 Gbps network bandwidth. With this powerful mix, you can quickly get insights and develop HPC workloads.
H4D outperforms C3D by 1.8x per virtual machine (VM) and 1.6x per core for the open-source High-Performance Linpack (OSS-HPL), a benchmark for supercomputer floating-point computation. H4D outperforms C2D by 1.7x per core and 5.8x per virtual machine.
H4D outperforms C3D by 1.4x per core and 1.3x per VM on STREAM Triad, a memory bandwidth benchmark. H4D outperforms C2D by 1.4x per core and 3x per virtual machine.
Increased HPC application performance
H4D virtual machines (VMs) outperform AMD-based C2D and C3D in compute performance and memory bandwidth. This speeds up simulations and analysis and improves performance across a variety of HPC applications and benchmarks compared to C2D, a prior generation AMD-based HPC VM:
Manufacturing
Siemens Simcenter STAR-CCM+/HIMach and other CFD packages enhance 3.6x.
Ansys Fluent/f1_racecar_140 and other CFD applications enhance 3.6x.
FEA-explicit programs like Altair Radioss/T10m improve up to 3.6x.
CFD applications like OpenFoam/Motorbike_20m increase by 2.9x.
Ansys Mechanical/gearbox and other implicit FEA programs improve 2.7x.
Healthcare and life sciences:
Molecular Dynamics (GROMACS) increases five-fold.
Weather forecasting
WRFv4, an industry benchmark, improves 3.6x.
AMD's tight relationship with Google Cloud drives the next generation of cloud-based HPC with the new H4D VMs. The 5th Gen AMD EPYC CPUs' architectural advances allow Google Cloud to enhance HPC benchmark performance by a significant amount. Customers may speed up their hardest HPC jobs and get immediate insights. Corporate vice president of AMD's Cloud Business Ram Peddibhotla
Titanium Cloud RDMA accelerates HPC
These virtual machines' first Titanium offload, Cloud RDMA, boosts H4D performance. Cloud RDMA is dedicated to HPC applications including molecular dynamics, weather modelling, computational fluid dynamics, and others that require inter-node communication. Cloud RDMA outsources network processing and provides consistent, low-latency, high-bandwidth connections between compute nodes, reducing host CPU constraints.
Cloud RDMA uses Falcon hardware transport to deliver reliable, low-latency communication over Google Cloud Ethernet-based data centre networks. This effectively solves RDMA over Ethernet difficulties and provides reliable, high-performance at scale.
Since Cloud RDMA employs more computing resources than Falcon, simulations are faster. H4D gives 3.4x and 1.9x speedups on four virtual machines (VMs) via TCP for smaller CFD issues like OpenFoam/motorbike 20m and Simcenter Star-CCM+/HIMach10, which have limited inherent parallelism and are hard to accelerate.
Scheduling and clustering
Cluster Director (formerly Hypercompute Cluster) and DWS will be supported by H4D virtual machines.
DWS helps schedule HPC workloads for optimal performance and cost-effectiveness and ensures resource availability for time-sensitive simulations and flexible HPC applications.
Cluster Director can now build and scale a large, physically-colocated accelerator cluster as a single unit in HPC settings. Cluster Director simplifies HPC cluster creation and management utilising H4D virtual machines by allowing researchers to run large-scale simulations.
Virtual machine sizes and regional availability
Google Cloud offers ordinary and high-memory H4D virtual machines for various workloads. The CPU-based seismic processing and structural mechanics applications Abaqus, NASTRAN, Altair OptiStruct, and Ansys Mechanical require high-speed storage. Google Cloud offers local SSD options.
Plans are underway to expand H4D virtual machines outside Europe-West4-b (Netherlands) and the US-Central1-a (Iowa).
#technology#technews#govindhtech#news#technologynews#cloudcomputing#H4D virtual machines#AMD EPYC Processors#H4D#Cloud RDMA#H4D VMs#Cloud Remote Direct Memory Access#Remote Direct Memory Access
0 notes
Text
Free TeraBox Video Download Made Easy with teradl.in
TeraBox is a powerful cloud storage solution used worldwide for hosting and sharing videos. But what if you want to download videos from TeraBox quickly and for free? That’s where teradl.in comes in—a fast, secure, and easy tool that enables free TeraBox video download for everyone.
Whether you’re using TeraBox for school, work, or personal content, being able to access your videos offline is crucial. Let's explore how teradl.in makes it simple.
Why You Need teradl.in for TeraBox Videos
While TeraBox player online allows for video streaming, it doesn’t offer a convenient way to download videos directly. You might have a TeraBox link video from a friend or colleague that you want to keep—but without the right tool, that link remains stuck in the cloud.
This is where teradl.in shines.
How teradl.in Works
teradl.in is a free, web-based platform that lets users download any TeraBox video just by pasting the video’s shareable link. You don’t need to install software or sign up.
Step-by-Step:
Copy the TeraBox Link
Get the TeraBox link video you want to download from the shared location or player.
Paste the Link
Enter the TeraBox link download in the input box provided.
Download with One Click
Choose the video quality and click download. Your video will begin downloading in seconds.
Benefits of Using teradl.in
Free TeraBox Video Download – No cost, no ads, and no hidden charges.
Easy to Use – Paste and download. No technical skills needed.
Works Across Devices – Use on PC, Mac, Android, or iOS.
Secure – No login or data tracking involved.
Stream or Save – Choose whether to preview using the TeraBox player online or download instantly.
Popular Use Cases
Students downloading recorded lectures from a shared TeraBox folder.
Content Creators saving collaborative work or video references.
Remote Workers needing offline access to training or video instructions.
Personal Users archiving memories shared via TeraBox.
Is It Safe?
Yes, teradl.in does not store your links or data. It's designed purely for one-click functionality. All downloads are direct from TeraBox’s CDN to your device, making it highly secure.
What About the TeraBox Player Online?
While TeraBox’s in-app player allows you to watch content, it lacks features like offline storage or resolution control. teradl.in bridges that gap by turning your TeraBox link video into downloadable content—giving you control over format and quality.
Final Thoughts
Whether you’re trying to archive videos, review shared content offline, or keep a backup for personal use, teradl.in is the best way to handle a TeraBox link download quickly and for free.
0 notes
Text
Accelerating Data Flow in Modern SAN Solution Environments
The demand for efficient, high-speed data transfer has skyrocketed in response to growing data-intensive applications such as AI, cloud computing, and big data analytics. To keep up, modern Storage Area Network (SAN) environments must evolve, enabling businesses to maintain seamless operations without bottlenecks or downtime.
This post explores how to accelerate data flow in SAN environments by leveraging cutting-edge technologies, optimized architectures, and tailored best practices. Whether you're an IT professional seeking to enhance your organization's data infrastructure or a data center manager looking for performance gains, this guide is for you.
Why Accelerating Data Flow in SANs Matters
The storage landscape today is vastly different from what it was a decade ago. Enterprises now contend with multi-petabyte data requirements, real-time analytics needs, and globally distributed teams requiring instant, secure access.
Accelerating data flow in SAN environments is critical because it directly impacts the following areas:
Performance for latency-sensitive applications like AI and machine learning.
Business continuity, as slower data transfer can lead to missed SLAs and reduced customer satisfaction.
Scalability, ensuring the infrastructure can meet future demands without performance trade-offs.
Without proper focus on speeding up SAN communication, organizations may face prolonged transfer times, higher latency, and inefficiencies that negatively affect services.
Key Challenges in Modern SAN Environments
Before we explore the solutions, it’s vital to understand the common challenges that modern SAN environments face when it comes to data flow.
1. Latency Bottlenecks
With the surge in remote access and 24/7 services, reducing latency is paramount. Traditional SAN solutions relying on aging hardware or slow interconnects often serve as a chokepoint in data transmission.
2. High Workload Diversity
Enterprise workloads are more diverse than ever, spanning transactional databases, analytics, AI training, and high-volume media files. Traditional, one-size-fits-all SAN architectures struggle to meet all these varying demands with precision performance.
3. Network Congestion
Aging or inadequately managed Fibre Channel or Ethernet fabrics can result in unnecessary packet loss, retransmissions, and slower overall performance.
4. Capacity Management
Modern SAN environments require designs that balance vast storage capacity with high-speed retrieval, but mismatched configurations can bog down data flow.
Strategies for Accelerating Data Flow in SAN Environments
The following strategies leverage advanced technologies and best practices to address challenges and enable faster, more reliable data transfer.
1. Upgrade to NVMe-oF (Non-Volatile Memory Express over Fabrics)
Switching to NVMe-oF in SAN architectures significantly reduces latency by optimizing the protocol layer for flash storage. NVMe-oF eliminates inefficiencies found in traditional SCSI interfaces by providing direct, high-speed communication between hosts and storage.
Why it matters: NVMe-oF offers concurrent, multi-queue support, enabling faster data access even under heavy workloads.
Use case: Enterprises running latency-critical applications, like AI model training or real-time transaction processing, experience significant benefits.
2. Implement Advanced Caching Solutions
Utilizing server-side or storage-based caching solutions can greatly enhance read/write performance. Modern caching systems use DRAM or even persistent memory like Intel Optane to temporarily store frequently accessed data closer to compute resources.
Why it matters: Reduces repetitive I/O operations for commonly used datasets, accelerating overall data retrieval.
Best practice: Pair caching solutions with predictive algorithms to ensure the right data is cached based on workload requirements.
3. Leverage Automated Storage Tiering
Tiered storage solutions automatically allocate data across different storage types based on performance needs. Frequently accessed data (hot data) is placed on high-performance flash, while rarely accessed data (cold data) is moved to HDDs or archival storage.
Why it matters: Improves cost-efficiency without sacrificing performance.
Example: A hybrid SAN employing all-flash arrays for high-priority workloads and slower magnetic storage for archiving creates an ideal balance.
4. Optimize Your Fabric Infrastructure
Advanced fabric technologies such as Fibre Channel Gen 6 and Ethernet-based RDMA (Remote Direct Memory Access) dramatically reduce network congestion. RDMA, in particular, bypasses CPU processing for network data, increasing throughput.
Why it matters: Faster interconnects facilitate seamless communication between SAN nodes, significantly boosting performance.
Pro tip: Regularly monitor fabric performance and use QoS (Quality of Service) policies to prioritize critical workloads.
5. Employ AI/ML for Intelligent SAN Management
AI-powered SAN management tools offer real-time performance analytics and proactive anomaly detection. By identifying potential bottlenecks and automatically redistributing workloads, these tools optimize SAN operations dynamically.
Why it matters: AI ensures that system performance remains consistent across changing workloads and infrastructure demands.
6. Use Compression and Deduplication Wisely
Data compression and deduplication technologies in SAN environments free up precious bandwidth and storage by reducing the volume of duplicate or redundant data being processed.
Why it matters: Leads to faster writes and extended storage capacity without compromising performance.
When to use: For environments with high data redundancy, such as backup systems or content repositories.
Real-World Impact of Accelerating Data Flow
Case Study: Optimizing an eCommerce Platform
An eCommerce enterprise handling millions of daily transactions faced slow order processing and higher cart abandonment due to SAN-related performance bottlenecks. After implementing NVMe-oF alongside a state-of-the-art RDMA fabric, processing times dropped by 30%, delivering seamless customer experiences and boosting revenue by 15%.
Case Study 2: Enhancing Data Analytics Timelines
A financial services firm reduced big data processing timelines by 40% by deploying automated storage tiering and caching solutions. Thanks to lower retrieval times, the firm gained faster access to insights, supporting better decision-making.
Best Practices for Maintaining High-Speed SAN Environments
Regular Performance Reviews: Continuously monitor latency, throughput, and IOPS (Input/Output Operations Per Second).
Upgrade Periodically: Stay ahead by upgrading hardware or software in line with evolving tech standards.
Establish Redundancy: Ensure your SAN design includes redundancy to handle unexpected node failures without affecting performance.
Train Personnel: Equip your IT teams with the latest knowledge to manage evolving SAN technologies effectively.
Unlock Your SAN’s True Potential
The evolution of modern SAN environments presents an exciting opportunity for IT professionals and enterprises to unlock unprecedented performance levels. From adopting NVMe-oF to leveraging AI-driven insights, there are countless ways to improve data flow efficiency and achieve better business outcomes.
Want to explore how advanced SAN solution technologies can transform your organization? Implement these best practices, and let your data center thrive.
0 notes
Text
Data Recovery Solutions: Restoring Files After System Failures
In today’s digital landscape, data is more than just a collection of files; it’s essential to both personal and professional life. From important business documents to cherished family photos, losing data can be incredibly frustrating. System failures, whether caused by software corruption, hardware malfunctions, or unexpected power surges, are among the primary reasons data loss occurs. Fortunately, various data recovery solutions can help restore files after such failures. This article explores the most effective ways to recover data after system failures, from simple DIY methods to professional solutions.
1. Understanding System Failures and Their Impact on Data
A system failure occurs when a computer or device encounters an error that prevents it from functioning properly. These failures can occur due to many reasons, such as:
Hardware Failures: Hard drive crashes, damaged cables, or power supply issues can prevent the system from booting up.
Software Failures: Corrupted operating systems, buggy applications, or viruses that compromise system integrity can lead to inaccessible files or system crashes.
Power Surges or Outages: Sudden power cuts or surges can disrupt the normal functioning of hardware, causing data corruption or loss.
Human Error: Accidental file deletion, formatting, or partition loss due to incorrect settings can also cause data loss.
Understanding the nature of the failure is key to determining which recovery approach will work best for your situation.
2. Backup Strategies: The First Line of Defense
While this section is not a direct recovery solution, a solid backup strategy is the best preventive measure against data loss due to system failures. Regular backups help protect your data, making it easier to restore in case of an emergency.
There are several methods to back up your data:
Cloud Storage: Services like Google Drive, Dropbox, and iCloud allow you to store files remotely and access them from any device. These services offer automatic syncing, making it easy to keep your files safe without manual intervention.
External Hard Drives: An external hard drive is a reliable way to create a local backup of your files. It’s important to set up scheduled backups to ensure the most recent data is saved.
Network Attached Storage (NAS): NAS devices are used in larger environments or homes with multiple devices. They provide centralized storage and can be configured for automatic backups of all connected devices.
In the event of system failure, a well-maintained backup can save you from the headache of trying to recover lost data. However, if no backup exists, data recovery becomes necessary.
3. Using Operating System Tools for Recovery
When faced with system failures, sometimes the operating system itself offers built-in tools to help recover lost files or restore the system to working condition.
Windows Recovery Options
Windows has a suite of built-in recovery tools that can be accessed even when the system fails to boot properly.
System Restore: This feature lets you restore the operating system to a previous state before the failure occurred. It doesn’t affect your personal files but will remove any software or updates installed after the restore point.
Startup Repair: If Windows fails to boot, this tool can help fix issues related to corrupted system files or startup configuration.
CHKDSK: If your system’s hard drive has file system issues, running the chkdsk command from the Command Prompt can identify and fix minor errors without overwriting data.
macOS Recovery Options
For macOS users, Apple offers several tools to restore files or recover the system after failure.
Time Machine: If you have been using Time Machine for backups, it’s an excellent way to restore your system to a previous state. Simply launch Time Machine and select the backup you wish to restore.
macOS Recovery: In cases of OS corruption or other issues, macOS Recovery provides tools like "Disk Utility" to repair the disk or reinstall macOS without erasing your files.
These built-in tools are often sufficient for minor system issues, but they may not work for severe failures or physical damage to hardware.
4. Third-Party Data Recovery Software
If built-in recovery tools fail, third-party data recovery software can offer a more advanced solution for recovering files after system failures. These tools scan your storage devices for lost or corrupted files and attempt to restore them.
Some popular data recovery software options include:
Recuva: This free tool is one of the most popular options for recovering lost files from damaged or corrupted drives. Recuva supports a variety of file types and can recover files from hard drives, memory cards, and USB drives.
EaseUS Data Recovery Wizard: A powerful tool that supports recovery from a wide range of devices, including hard drives, USB drives, and SD cards. It is user-friendly and has both free and premium versions, depending on the size of the data you need to recover.
Stellar Data Recovery: This tool specializes in deep scans for files that are difficult to recover. It’s particularly useful for recovering files from formatted or damaged drives, and it supports both Windows and macOS.
Disk Drill: Disk Drill is well-suited for both Windows and macOS users, offering powerful recovery features such as scanning for lost partitions, previewing recoverable files, and restoring files from encrypted devices.
To use data recovery software effectively, follow these steps:
Install the software on a different device or drive than the one you're recovering files from.
Connect the damaged device to your computer.
Run the recovery software, select the drive to scan, and initiate the scan.
Preview the recoverable files and save them to a different storage device.
While data recovery software can help recover lost files, it is most effective when dealing with logical or software failures. If your system failure involves physical hardware damage, professional recovery services may be required.
5. Professional Data Recovery Services
If the system failure is due to severe hardware damage, professional data recovery services are often the only solution. These services specialize in recovering data from damaged or malfunctioning devices, such as hard drives with physical damage (e.g., damaged read/write heads or malfunctioning motors).
Some well-known data recovery services include:
DriveSavers: A leader in data recovery, offering services for all types of devices, including hard drives, RAID arrays, and smartphones. They specialize in cases where the hardware is physically damaged.
Ontrack: Ontrack offers comprehensive data recovery services for a variety of devices and data loss situations. They also offer a “no data, no fee” policy, ensuring you don’t pay unless they successfully recover your files.
Secure Data Recovery: Known for its cleanroom facilities and cutting-edge tools, Secure Data Recovery provides data recovery from hard drives, SSDs, and RAID systems, even in extreme cases of physical failure.
These services come at a higher cost compared to DIY software options, but they offer the best chance of restoring data from severely damaged devices. They are often used as a last resort when other methods fail.
6. Prevention: Steps to Take After Data Recovery
After recovering your data, it's essential to take steps to prevent future system failures and data loss. This includes:
Regular Backups: Set up automatic backups to prevent the need for recovery in the future. Use cloud storage, external drives, or NAS solutions.
Maintain Hardware: Ensure that your devices are well-maintained. Regularly check for signs of wear and tear, and replace aging hardware components before they fail.
Use Antivirus Software: Protect your system from malware and viruses, which can corrupt files and cause system failures.
Data recovery after system failure is possible, but the best course of action depends on the nature and severity of the failure. Whether you rely on built-in recovery tools, third-party software, or professional services, the key to successful recovery lies in acting quickly and using the right methods. By following proper recovery steps and implementing preventive measures like regular backups, you can minimize the risk of future data loss and ensure that your files remain safe.
#Data Recovery#Professional Data Recovery Services#iPhone Data Recovery#Mac Data Recovery#iPad Data Recovery#Deleted File Recovery#Water-Damaged Device Data Recovery#Hard Drive Data Recovery#Data Recovery for SSDs#Encrypted Device Data Recovery#Fast and Secure Data Recovery
0 notes
Text
Skip Levens, Marketing Director, Media & Entertainment, Quantum – Interview Series
New Post has been published on https://thedigitalinsider.com/skip-levens-marketing-director-media-entertainment-quantum-interview-series/
Skip Levens, Marketing Director, Media & Entertainment, Quantum – Interview Series
Skip Levens is a product leader and AI strategist at Quantum, a leader in data management solutions for AI and unstructured data. He is currently responsible for driving engagement, awareness, and growth for Quantum’s end-to-end solutions. Throughout his career – which has included stops at organizations like Apple, Backblaze, Symply, and Active Storage – he has successfully led marketing and business development, evangelism, launched new products, built relationships with key stakeholders, and driven revenue growth.
Quantum provides end-to-end data solutions that help organizations manage, enrich, and protect unstructured data, such as video and audio files, at scale. Their technology focuses on transforming data into valuable insights, enabling businesses to extract value and make informed decisions. Quantum’s platform offers secure, scalable, and flexible solutions, combining onsite infrastructure with cloud capabilities. The company’s approach allows businesses to efficiently handle data growth while ensuring security and flexibility throughout the data lifecycle.
Can you provide an overview of Quantum’s approach to AI-driven data management for unstructured data?
By helping customers integrate artificial intelligence (AI) and machine learning (ML) into their key business operations, Quantum helps customers to effectively manage and unlock meaningful value from their unstructured data, creating actionable business insights that lead to better business decisions. By building their own AI/ML tools, companies can move from simply coping with the influx of data and content, to leveraging insights as a new driver of efficiencies and ultimately amplifies human expertise in all phases of business operations.
How does Quantum’s AI technology analyze unstructured data, and what are some key innovations that set your platform apart from competitors?
In the initial stages of adopting AI/ML tools, many organizations find their workflows become disordered and disconnected, and can lose track of their data, making it difficult to enforce security and protection standards. Too often, early development is hampered by ill-suited storage and file system performance.
We developed Myriad, a high-performance, software-defined file storage and intelligent fabric environment to elegantly meet the challenges of integrating AI/ML pipeline and high-performance workflows together – unifying workflows without the hardware constraints and limitations of other systems. Myriad is a clear departure from legacy hardware and storage constraints, and built with the latest storage and cloud technologies, is entirely microservices driven and orchestrated by Kubernetes to be a highly responsive system that rarely requires admin interaction. Myriad is exclusively architected to draw the highest performance from NVMe and intelligent fabric networking and near instantaneous remote direct memory access (RDMA) connections between every component. The result is an innovative system that responds intelligently and automatically to changes and requires minimal admin intervention to perform common tasks. By making intelligent fabric part of the system, Myriad is also an intrinsically load-balanced system that provides multiple 100Gbps ports of bandwidth as a single, balanced IP address.
Pairing Myriad with our cloud-like object storage system, ActiveScale, allows organizations to archive and preserve even the largest data lakes and content. The combination offers customers a true end-to-end data management solution for their AI pipelines. Moreover, when delivered alongside our CatDV solution, customers can tag and catalog data to further enrich their data and prepare it for analysis and AI.
Could you share insights on the use of AI with video surveillance at the Paris Olympics, and what other large-scale events or organizations have utilized this technology?
Machine Learning can develop repeatable actions that recognize patterns of interest on video and derive insights from a flood of real-time video data at a scale larger and faster than is possible by human efforts alone. Video surveillance, for example, can use AI to capture and flag suspicious behavior as it occurs, even if there are hundreds of cameras feeding the model information. A human attempting this task would only be able to process one event at a time, whereas AI-powered video surveillance can take on thousands of cases simultaneously.
Another application is crowd sentiment analysis, which can track long queues and pinpoint potential frustrations. These are all actions that a security expert can reliably flag, but by using AI/ML systems to continuously watch simultaneous feeds, those experts are freed to take appropriate action when needed, dramatically boosting overall effectiveness and safety.
What are the primary challenges organizations face when implementing AI for unstructured data analysis, and how does Quantum help mitigate these challenges?
Organizations must completely reimagine their approach to storage, as well as data and content management as a whole. Most organizations grow their storage capabilities organically, usually in response to one-off needs, and this creates multi-vendor confusion and unfortunate complexity.
With the adoption of AI, organizations must now simplify the storage that underpins their operations. Oftentimes, this requires implementing a “hot” part of the initial data ingest, or landing zone where applications and users can work as fast as possible. Then, a large “cold” type of storage is added that can easily archive massive amounts of data and protect it in a cost-effective way, with the ability to move the data back into a “hot” processing workflow almost instantaneously.
By reimagining storage into fewer, more compact solutions, the burden on admin staff is much lower. This kind of “hot/cold” data management solution is ideal for AI/ML workflow integration, and Quantum solutions enable customers create a highly agile, flexible platform that is concise and easy to manage.
How do Quantum’s AI innovations integrate with other AI-powered tools and technologies to enhance organizational growth and efficiency?
Many people think storage for AI/ML tools is only about feeding graphics processing units (GPUs), but that’s just one small part of the equation. Though speed and high-performance may be instrumental in feeding data as fast as possible to the GPUs that are performing data analysis, the bigger picture revolves around how an organization can integrate iterative and ongoing AI/ML development, training, and inference loops based on custom data. Oftentimes the first and most important AI/ML task addressed is building “knowledge bots” or “counselor bots” using proprietary data to inform internal knowledge workers. To make those knowledge bots useful and unique to each organization, large amounts of specialized information is required to inform the model that trains them. Cue an AI-powered storage solution: if that proprietary data is well-ordered and readily available in a streamlined storage workflow, it will be far easier to organize in types, sets, and catalogs of data which will, in turn, ensure that those knowledge bots are highly informed on the organization’s unique needs.
Can you elaborate on the AI-enabled workflow management features and how they streamline data processes?
We’re building a host of AI-enabled workflow management tools that integrate directly into storage solutions to automate tasks and provide valuable real-time insights, enabling fast and informed decision-making across organizations. This is due to new and advanced data classification and tagging systems that use AI to both organize data and make it easily retrievable, and even perform standard actions on that media such as conforming to a certain size, which significantly reduces the manual efforts needed when organizing data into training sets.
Intelligent automation tools manage data movement, backup, and compliance tasks based on set policies, ensuring consistent application, and reducing administrative burdens. Real-time analytics and monitoring also offer immediate insights into data usage patterns and potential issues, automatically maintaining data integrity and quality throughout its entire lifecycle.
What is the outlook for AI-powered data management, and what trends do you foresee in the coming years?
As these tools evolve and become multi-modal, it will allow more expressive and open-ended ways of working with your data. In the future, you’ll be able to have a “conversation” with your system and be presented with information or analytics of interest such as ‘what is the fastest growing type of data in my ‘hot zone’ now?’. This level of specialization will be a differentiator for the organizations that build these tools into their storage solutions, making them more accurate and efficient even when confronted with constant new streams of evolving data.
What role do your cloud-based analytics and storage-as-a-service offerings play in the overall data management strategy?
Organizations with significant and expanding storage requirements often struggle to keep up with demand, especially when operating on limited budgets. Public cloud storage can lead to high and unpredictable costs, making it challenging to accurately estimate and purchase years’ worth of storage needs in advance. Many customers would like the public cloud experience of a known projected operating cost yet eliminate the surprise egress or API charges that public cloud can bring. To answer this need, we developed Quantum GO to give customers that private cloud experience with a low initial entry point and low fixed monthly payment options for a true storage-as-a-service experience in their own facility. As storage requirements increase, Quantum GO gives customers the added advantage of a simple ‘pay-as-you-grow’ subscription model to offer enhanced flexibility and scalability in a cost-effective manner.
How does Quantum plan to stay ahead in the rapidly evolving AI and data management landscape?
In today’s world, being merely a “storage provider” is not enough. Newly evolving data and business challenges require an intelligent, AI-empowering data platform that helps customers to maximize the value of their data. At Quantum, we continue to innovate and invest in enhanced capabilities for our customers to help them easily and effectively work with troves of data throughout their entire lifecycles.
We are expanding intelligent AI to uplevel the tagging, cataloguing, and organizing of data, making it easier than ever to search, find, and analyze it to extract more value and insight. We will continue to enhance our AI capabilities that assist with automatic video transcription, translating audio and video files into other languages within seconds, and enabling quick searches across thousands of files to identify spoken words or locate specific items, and more.
What advice would you give to organizations just beginning their journey with AI and unstructured data management?
AI/ML has had enormous hype, and because of that, it can be difficult to parse out what’s practical and useful. Organizations must first think about the data being created, and pinpoint how it’s being generated, captured, and preserved. Further, organizations must seek out a storage solution that is ready to access and retrieve data as needed, and one that will help guide both day-to-day workflow and future evolution. Even if it’s hard to agree on what the ultimate AI goals are, taking steps now to make sure that storage systems and data workflows are streamlined, simplified, and robust will pay enormous dividends when integrating current and future AI/ML initiatives. Organizations will then be well-positioned to keep exploring how these AI/ML tools can advance their mission without worrying about being able to properly support it with the right data management platform.
Thank you for the great interview, readers who wish to learn more should visit Quantum.
#admin#adoption#Advice#agile#ai#AI-powered#AI/ML#Analysis#Analytics#API#apple#applications#approach#artificial#Artificial Intelligence#audio#automation#awareness#Backblaze#backup#Behavior#bots#budgets#Building#Business#Business development#Cameras#Capture#career#Cloud
0 notes
Text
VPS, SHARED HOSTING, OR CLOUD HOSTING: WHAT IS YOUR BEST OPTION?
Hosting choices can be a maze for those new to website development. Shared hosting, VPS hosting, and cloud hosting often take centre stage; everyone has a perfect fit, and it is your job to find what it is.
Selecting the ideal hosting solution hinges on various factors: performance needs, security essentials, budget constraints, scalability desires, and server management preferences. Your Melbourne website designer will help you find your most suited hosting, but if you are on your own, read this blog till the end. You will get to know a lot regarding these three hosting options.

So, let’s unravel the complexities together.
VPS:
Virtual private server (VPS) hosting maintains the concept of sharing the same physical server space, yet introduces a virtual layer atop the server’s operating system. This layer divides the server into segments, allowing users to install their unique operating systems and software.
It’s akin to leasing your apartment: you have your space without direct sharing of resources, but you’re still bound by the overall resource limits of the server. So, it means if all sites consume maximum bandwidth, everyone faces sluggishness.
So, VPS is ideal for consumer-centric sites like online stores, and it promises faster load times, heightened security, and enhanced site performance. However, managing a VPS demands significant technical expertise, making it less suitable for novice website builders.
Moreover, users or Melbourne website designers shoulder more responsibility for website security, as a misconfigured VPS can expose critical vulnerabilities.
SHARED HOSTING:
Shared hosting involves sharing a website server and its resources with other hosted sites. Typically, website owners are unaware of the identities of the other sites sharing the hosting platform. Each customer on the platform is allocated a limit of server resources based on the hosting package they have selected. While shared hosting providers often offer multiple packages with varying levels of resource access, all customers ultimately occupy the same server space.
It’s popular among Melbourne website designers due to its affordability, but it can have drawbacks if server resources are insufficient for multiple users or if security measures are inadequate, potentially leading to slow website loading times.
CLOUD HOSTING:
Cloud servers, existing in a virtual environment, operate independently through a cloud computing platform. It is accessed remotely via the internet.
Comparable to renting an entire apartment building, cloud servers benefit from shared city resources without direct physical connections to other servers. This isolation ensures stability and security, shielding websites from potential software impacts of neighbouring servers.
Cloud hosting boasts reliability, with distributed deployments ensuring seamless operation even if one server fails. It also offers unparalleled scalability, enabling users to adjust memory and processing power as needed without investing in new hardware. However, its premium price tag demands careful resource management to avoid unnecessary expenses.
COMPARISON OF HOSTINGS
Now, let’s compare one with another hosting and see which one of the three suits your needs the most. Usually, Melbourne website designers compare based on three crucial aspects, which are speed, security, and cost.
SHARED HOSTING VS. VPS
VPS hosting outpaces shared hosting in speed and performance due to its enhanced access to server resources.
With VPS, users benefit from a virtual layer that segregates them from other server components, allowing personalised security controls. In contrast, shared hosting relies on shared security practices, risking data exposure if neighbours err.
Shared hosting is generally more economical, but it sacrifices server access and performance.
So, it’s crucial to note discrepancies among VPS and shared hosts regarding features and prices. Ask your Melbourne website designer to run a careful comparison before deciding on hosting solutions.
CLOUD HOSTING VS. SHARED HOSTING
Cloud hosting surpasses shared hosting in speed due to its utilisation of virtual servers rather than physical stacks, enabling providers to optimise performance efficiently.
While both cloud and shared hosting share resources, cloud hosting offers scalability without being tethered to specific hardware.
In terms of security, cloud hosting holds an advantage, contingent on proper security implementations, as it provides flexibility for customisation.
Although cloud solutions often include basic security tools, the responsibility for robust security measures lies with individual hosts.
Despite its advantages, cloud hosting tends to be more expensive than shared hosting, as costs scale with usage, outstripping basic shared options.
CLOUD HOSTING VS. VPS
Cloud hosting typically outperforms VPS in speed due to its abundance of resources, provided there’s a fast and secure last-mile connection. However, if multiple VPS instances are purchased on the same physical server, their performance can be comparable.
Cloud providers usually offer built-in security controls, reducing the risk of attacks. Basic VPS security is less robust, but with technical expertise, advanced controls can be implemented. The distributed nature of the cloud enhances security, enabling quick migration in case of hardware compromise.
While costs for VPS and cloud hosting are similar, priorities differ. Cloud focuses on scalability and accessibility, while VPS prioritises control and security.
FINAL WORD:
Whether you opt for shared hosting, VPS, or cloud hosting, each presents its own set of advantages and limitations. By carefully juxtaposing these hosting options, you can make an informed decision. Remember, the ideal choice will hinge on striking the right balance between accessibility, control, resource allocation, and overall functionality. So, take the time to evaluate your needs comprehensively.
If you need expert help, get in touch with Make My Website, a renowned Melbourne-based website designer/developer.
0 notes
Text
IoT Data Acquisition Framework and Protocol Converters: Investigating the Scientech 6205DA
Introduction
The Internet of Things (IoT) has changed the manner in which we communicate with innovation, empowering consistent availability among gadgets and working with the trading of data on an extraordinary scale. One vital part of IoT is the capacity to gain and communicate data from different sensors and gadgets progressively. To accomplish this, dependable data acquisition systems and protocol converters are fundamental.
In this article, we dig into the universe of IoT data acquisition systems and investigate the Scientech 6205DA, a powerful and flexible gadget intended to meet the requested prerequisites of present-day IoT applications. We will examine the essential ideas driving data acquisition systems, the significance of protocol converters, and how the Scientech 6205DA can smooth out the data acquisition process.
I. Figuring out Data Acquisition Systems
Data acquisition systems assume a significant part in gathering, estimating, and breaking down data from different sensors and gadgets progressively. These systems are indispensable to the working of IoT applications, where the consistent acquisition and transmission of data are fundamental. In this part, we will investigate the central ideas driving data acquisition systems, the parts that comprise them, and the significance of precise and dependable data acquisition.
A. Data Acquisition Nuts and bolts
Definition and Reason for Data Acquisition Systems
A data acquisition framework, often curtailed as DAS or DAQ, alludes to the method involved with inspecting, changing over, and recording simple or computerized data from different actual peculiarities, like temperature, strain, voltage, or current. The main role of a data acquisition framework is to catch and gauge true signals, convert them into computerized organization, and make them accessible for examination, stockpiling, and handling.
Parts of a Run of the mill Data Acquisition Framework
A data acquisition framework comprises a few key parts:
a. Sensors and Transducers: These gadgets convert actual boundaries into electrical signs.
b. Signal Molding: It includes intensifying, separating, and segregating the crude signs to guarantee exactness and similarity with the data acquisition equipment.
c. Simple to-Advanced Converters (ADC): ADCs convert simple signs into computerized structures, addressing them as discrete numeric qualities.
d. Advanced Signal Processors (DSP) or Microcontrollers: These gadgets perform different computations and data-handling errands.
e. Data Capacity: The gained data is put away in databases or memory for additional examination and recovery.
f. Data Transmission: The data can be sent over wired or remote organizations to different systems or the cloud for additional handling or perception.
Significance of Precise and Solid Data Acquisition
Exact and dependable data acquisition is significant because of multiple factors:
a. Quality Control: Data acquisition systems guarantee that the gathered data is exact, dependable, and agent of the actual peculiarity being estimated. This is imperative for going with educated choices and guaranteeing the quality of cycles and items.
b. Constant Observing: Numerous applications, like modern computerization and medical care, demand ongoing checking of data. Data acquisition systems empower nonstop data assortment, considering prompt reactions and ideal mediations.
c. Data Investigation: Solid data acquisition is the establishment for significant data examination. Exact data guarantees precise bits of knowledge, expectations, and enhancements.
d. Consistence and Guidelines: In directed businesses, precise data acquisition is important to consent to principles, guidelines, and detailing prerequisites.
B. Sorts of Data Acquisition Systems
Simple to-Advanced Converters (ADC)
ADCs are vital parts of data acquisition systems. They convert consistent simple signs, like voltage or current, into discrete advanced values that can be handled by PCs or microcontrollers. ADCs test the simple sign at customary spans, measure its sufficiency, and convert it into a computerized portrayal utilizing methods like progressive estimate, delta-sigma regulation, or blaze transformation.
Computerized to-Simple Converters (DAC)
While ADCs convert simple signs into computerized structures, DACs carry out the opposite role. They convert advanced data into simple signs, permitting the framework to control actual boundaries or produce simple results. DACs are generally utilized in applications like sound systems, control systems, and waveform combinations.
Sensor Points of Interaction and Sign Molding
Sensor points of interaction are fundamental parts that give the important network and similarity among sensors and data acquisition systems. They guarantee that the signs from sensors, which can shift as far as voltage levels, impedance, and correspondence protocols, are fittingly molded and switched over completely to an organization viable with the data acquisition equipment. Signal molding incorporates intensifying feeble signs, sifting through commotion or undesirable frequencies, and giving legitimate confinement to forestall obstruction.
Multiplexing and Checking Procedures
Multiplexing procedures permit the data acquisition framework to successively gauge different simple information sources utilizing a solitary ADC. This is accomplished by quickly exchanging between various information channels. Filtering strategies decide the grouping and timing of channel exchanging, they are satisfactorily inspected and recorded to guarantee that every single significant channel.
Data Acquisition Framework Designs
Data acquisition systems can have different designs relying upon the application necessities. A few normal models incorporate brought-together systems, dispersed systems, and measured systems. Incorporated systems have a solitary focal unit liable for data acquisition, handling, and capacity. Disseminated systems circulate the data acquisition capabilities across various gadgets, and associated means of an organization. Measured systems utilize individual modules that can be interconnected and arranged according to the application's requirements.
C. Key Contemplations in Data Acquisition Systems
The goal, Testing Rate, and Precision
Goal alludes to the number of discrete qualities an ADC can address. It decides the littlest perceptible change in the deliberate amount. The examining rate characterizes how often the simple sign is tested and changed over into computerized esteem. Higher goals and examining rates empower more exact estimations yet additionally require really handling power and capacity limits.
Signal Molding and Sound Decrease
Signal molding assumes a vital part in data acquisition systems by setting up the crude simple signs for change. It includes enhancing frail signs, areas of strength for constricting, eliminating commotion, and sifting through undesirable frequencies. Legitimate sign molding guarantees precise and dependable data acquisition.
Similarity with Different Sensors and Gadgets
Data acquisition systems need to help a great many sensors and gadgets. Similarity with various sensor types, correspondence protocols, and sign levels is fundamental for consistent mix and data acquisition from assorted sources.
Versatility and Expandability
Data acquisition systems ought to be adaptable to oblige the development of the IoT application. They ought to take into consideration the expansion of additional sensors, channels, or modules as the prerequisites develop. Expandability guarantees that the data acquisition framework can adjust to changing requirements without critical reconfiguration or substitution.
Data Capacity and Transmission
Data acquisition systems should give effective capacity and transmission components. Contingent upon the application, the data might be put away privately, communicated to a focal database, or broken down continuously. The framework ought to have proper capacity limits, data pressure choices, and correspondence connection points to deal with the data stream productively.
Taking everything into account, data acquisition systems structure the foundation of IoT applications by empowering the acquisition, transformation, and transmission of data from different sensors and gadgets. Grasping the essentials of data acquisition, including the parts, types, and key contemplations, is significant for building dependable and precise data acquisition systems. With progressions in innovation, data acquisition systems keep on developing, offering higher goals, quicker testing rates, and further developed similarity, in this way engaging associations to use the maximum capacity of the IoT environment.

0 notes
Text
L’Appel Du Vide - Chapter 2
AO3 | First | Previous | Next | Masterpost
Description: Logan has been captured by a government agency who researches human with supernatural powers. Able to manipulate the world with his mind and tell what others are thinking, Logan finds himself in one of the most high security government prisons in the country that's run by a sinister Dr. Emile Picani. After several long months of deprivation and torture at the hands of Dr Picani, a devilish-looking man with scales on his face will break into the prison looking for Logan's less than friendly bunkmate, but will he be too late? Prompt by @LoganIsACoolTeacher on AO3
Endgame pairings: Lociet, Intruality, Prinxiety
Word Count: 3323
Chapter Warnings: Blood, Crying, Depression, Casual Suicidal ideation, Depriving someone of food, Captivity, Solitary confinement, Knife, Threats of violence, Swearing, Mentions of abuse/torture, Injuries, Panic Attack, Food (Let me know if need to add anything!)
---
The first night, Logan screamed himself hoarse well into the middle of the night. His body ached with misery, as he yelled and pulled at his restraint. His wrist was bruised and he could feel a this stream of blood dripping from where the metal had cut into his skin but he kept fighting until his body collapsed with exhaustion and he was forced into a restless sleep.
Agony burned in his chest as the long hours dragged by in absolute silence. Being alone was a rare experience for Logan and one he adamantly avoided. While the sound of the constant chattering of strangers thoughts would probably sound nightmarish to the average person, he'd grown accustomed to the comforting presence of others' thoughts. He was used to the white noise, and though he knew it was irrational, the sudden silence growing nearly painful with every hour that passed.
The second night, the isolation started to dig its claws into the corners of his mind. The restraint on his wrist limited his movement to only a few feet around the bed and so far, he'd spent hours staring into the empty window on the far side of the room. Anger twisted in his stomach at the thought that he was likely being watched through the one-way reflective surface and he felt like screaming at his silent observers until his voice gave out, but the previous night’s experience had already proved that effort would be futile. Expending the energy would only make him hungrier.
All he could do was wait.
The third day, he'd woken to find the restraint on his wrist had been released while he'd slept. He blinked, unsure of what this new revelation meant for him. Rubbing his sore wrist, he sat up to scan the quiet room. The door remained closed, and likely locked, but somehow a container of water has found its way into the room. He stepped off the bed, glancing cautiously at the one-way mirror as he approached the glass jug sitting at the base of his door. He was aware of the danger. Tampering with his water supply would be a simple way to entrap him or drug him, but his thirst quickly overrode any hesitation he had. They were his only access to resources and he knew he'd have to give in eventually or risk simply dying of dehydration. Not to mention, quite frankly, if the people in this place decided to kill him, he had little recourse in stopping them. No amount of bargaining would change that fact that he was at their mercy.
Next to the water, he found a fresh change of clothes. The sight of fresh white hospital-like clothing brought a bitter taste to his mouth as memories of the night before came rushing back. He hadn't seen a hint of another person since the doctor had left him, taking with him the only people who might be even remotely sympathetic to his situation. He brushed his thumb over the stiff fabric picturing the faces of the two other prisoners who'd been dressed in the same sterile uniform as he now held in his hand. Still, he changed his clothes, feeling a new level of numb as he changed in front of the window.
Numbness had settled in fully by the fourth night. The hunger left him too weak to stay focused on anything for long. The water provided for him sustained his body in only the barest sense and he could feel his willpower draining away as he spent more time curled in his bed, mind blank as he succumbed to the silence. That night, a particularly sinister breed of depression had taken root in his mind, pushing him toward the precipice of giving up. Dark, self-destructive thoughts clouded his mind as finally drifted off to sleep, making his abrupt awakening all the more jarring as he opened his eyes to find a sharp blade pressed to his throat and a shadow with glowing purple eyes looming over him.
“Move and I'll slit your throat.”
Pure adrenaline flooded over Logan at the familiar voice. The man who'd nearly strangled him the first night straddled his chest, silhouetted against the dark room by the eerie red light. Logan swallowed, barely breathing as he as he pressed himself backward, tilted his head away from the blade.
“You will answer my questions.”
A whimper escaped Logan’s lips, but he forced a small nod, hardly daring to move under the delicate pressure of the sharp blade.
“Why's Picani interested in you?”
“I don't kn—”
“Find a better answer.” The man's hiss sent chills down his spine as the knife moved up Logan’s neck. “The other night, you blew me back into the wall like a goddamn ragdoll. What’s was that?”
Logan sucked in a shallow breath as he struggled to keep his weak body breathing. “Tele—telekinesis.”
“Do not fuck with me right n—”
“I’m not—” Logan breathed, closing his eyes. “I can move things with my mind—”
The blade pressed against his throat with a preciseness just short of drawing blood. “If that were true, why haven’t you blasted me again?”
“I—I don't control it. I never learned how.” Logan blinked, surprised as the blade released a touch of pressure. He blinked, staring up at blank expression on the man's face as he continued.
“Picani’s guard said you'd feed on me.” The man growled his disbelief as he glared down at Logan. “Explain.”
“I don’t know what he was—"
“Not good enough.” The man's deep voice growled above him as the blade returned to his throat. "If you don't start talking, I'll—"
“Please—” Logan whimpered as the sharp nicked his throat and a thin line of blood dripped down his neck. “—It's not what you think.”
“Then explain,” The man’s eyes flashed dangerously as he continued but the pressure of the blade eased slightly. “before I start to get impatient.”
Logan swallowed, feeling a wet streak trail down his face. “Others’ thoughts—I hear them.”
“Are you telling me you feed on my thoughts?”
“No—“ Logan whispered as tears flowed freely down his face. “Please, I don’t know how it works but I can’t—It doesn’t hurt anyone. I wouldn't hurt anyone. Please—”
Logan clenched his eyes shut, stifling a terrified whimper as the blade moved up his neck. His heart pounded in his chest until the blade lifted slightly from his throat and a wet sob escaped his throat. He sucked in a breath as the man leaned back, knife still pointed in Logan's direction as he continued in a hushed tone.
“Are you listening to my thoughts right now?”
“N—no,” Logan breathed, avoiding the man's eyes. “I'm too weak. I can’t—I can’t do anything.”
The man was quiet for a long moment, eyes glinting in the red light as he stared at Logan. “What'd he do to you?”
“Who?”
“Picani,” The man's voice softened slightly. “The doctor, I mean. What's he done to you?”
“I—I’ve been kept alone and—” Logan bit his lip, uncertain about sharing the true depths of his weakness. “—and I haven’t eaten. Anything that fuels my power, he's taken it from me. I can't—I can't hurt you."
The silence hung in the air for a long, tense moment before the man spoke again, knife still inches from Logan's throat.
“Close your eyes.”
A chill crept up Logan’s spine at the seriousness in the man's voice. “Please, don't—”
“Don’t argue.”
Logan swallowed the lump in his throat as the glisten of the blade pointed at him inches from his face. Stilled trembling and tense, he let his eyes flutter closed.
“Move your hands where I can see them.”
“I'm already blind—”
“I didn’t ask for your opinion.”
“Fine.” Logan muttered as he rested his head back on the pillow, lifting his hands in apparent surrender. After a moment, he could feel the bed shift as the man climbed off the bed in absolute silence. Logan strained his ears, but he was unable to trace the man’s careful movements after he stepped onto the flow. He slowed his breathing and forced himself to remain still, unsure of how the man would react to even the smallest twitch.
“If Picani finds out I have a knife because you rat me out, I will not hesitate to kill you with my bare hands.”
Logan bit his lip, body shaking as he gave a stiff nod. “U-understood.”
“Telling him won’t protect you.” The man continued gruffly. “It will only put me in danger.”
“I won't tell him.” Logan swallowed. “You have my word.”
“Your word doesn’t mean shit to me.”
A bitter from twitched at the corner of Logan’s lip. “The man dropped you back in here in the middle of the night, while I was weak and defenseless, knowing full well that you'd already made one attempt on my life. I'm not so much of a fool to believe him my ally.”
“Picani was hedging his bets that you'd appeal to my good will.”
Logan let out a huff, dropping his head to his chest. “Well, it appears he made a miscalculation.”
“Perhaps.” Virgil sighed quietly after a moment. “Or perhaps not. You can have this, but I want you to give me back the wrapper, so I can hide it later.”
A small object struck Logan’s chest, causing him to flinch back with a sharp breath. His muscles tensed as his eyes cautiously fluttered open to reveal the ominous sight of the stranger’s eyes glinting at him through the darkness. Slowly, he sat upright, maintaining eye contact as he turned his head down to stare at the protein bar in his lap.
“Don't make a mess.”
Glancing cautiously up at the other man’s stiff form, Logan leaned forward to tear at the wrapper. He wasn’t sure what had brought about the sudden change of heart, but he wasn’t about to waste his first chance for food in three days. His hands shook as he attempted to tear into the difficult piece of plastic, growing desperate as the man above him tensed.
“Hey, be careful!” The man held up a hand, stopping as Logan flinched at his volume. He paused, giving Logan a quick sympathetic look before edging closer. “Listen, hand it over for a second.”
Logan hesitated, gripping the bar tightly as if his life depended on it.
“Listen, dude. It's all yours, I swear.” The man whispered with a wary smile, holding up his friends as he dropped down on the side of the bed. His movements were slow, as if he was suddenly deliberately making an attempt to be non-threatening. “Just let me open it for you so you don’t make a mess. I don’t want to get backlash for helping you out. Okay?”
“Okay.” Logan whispered after a moment of tense silence, keeping his head bowed from the man's gaze as the man took the bar from his hands. “Thank y—”
“Don't thank me.” The man cut him off sternly. He made quick work of tearing the wrapper open before offering it back to Logan. “What's your name?”
“Logan.”
“Okay, Logan. Mine's Virgil.”
The man whisper filled the air as he waited patiently for Logan to take the bar from the wrapper. Logan took a quick bite, watching the man in his periphery as he chewed the small offering of food slowly. His body ached for him to finish faster, but he didn't want to be caught off guard if the man suddenly changed his mind.
“Listen, I'm sorry.” Virgil muttered as Logan took another bite. “I know I must have scared the shit out of you just now.”
Logan blinked up in mild surprise at the man's change in tone, still wary of the man's anger as he swallowed his first bite.
“You were being cautious.”
“That doesn’t suddenly make any of this shit okay,” Virgil muttered as he crumpled the wrapper into his pocket and stared at his lap. “The way I reacted is straight fucked, but you got to know that Picani only keep his most dangerous subjects this deep into the labs. You're not the first piece of fresh meat Picani’s dropped in my bunk—And when I heard the guards talking about you feeding on me, I panicked.”
“I assume the doctor has given you plenty of reason to be wary of newcomers.” Logan whispered, still slightly unnerved by the man's choice of words. “H-how long have you been here?”
“Long enough that I stopped counting the days.”
Virgil absently ran his fingers through his hair as Logan took in the sight of the man for the first time. His white attire seemed dirtier than before, especially next to the stark white color of Logan’s matching attire. Logan’s eyes tipped up to the man's face. Fresh bruises covered his face and arms and large pieces of gauze appeared to have been haphazardly applied to his head and around his elbows in a poor attempt at first aid for whatever injuries he sustained over the last few days.
"W-where did they take y—”
“Don’t ask.” Virgil interrupted abruptly, glancing at the fearful look in Logan’s eyes as he cut him off. He paused, briefly considering the harshness his words before looking up at Logan. “You'll find out soon enough and trust me, you'll wish you never found out.”
“The doctor—He hurts you because of your powers.” Logan observed, curling his knees to his chest as Virgil’s dark gaze turned back to him. “Doesn't he?”
Virgil blinked up at him. "How did you—"
"I saw you starting to turn invisible before the doctor walked in on us." Logan bit his lip, looking shyly at his lap. "Just after I blew you back into the wall."
"Huh, well, its not invisibility." Virgil huffed, dropping his shoulders as he pointed up at the red lights. "I can manipulate light. It's the reason for all of those."
"What?" Logan furrowed his brow, glancing at the strange lights.
"I can't shift red light as easily as the rest of the spectrum." Virgil muttered bitterly. "They put these in here to make sure that Picani always knows where I'm at."
"And he hurts you because of these abilities?"
"He runs tests." Virgil blinked, looking up a the fear Logan was barely concealing behind his eyes. “Picani’s a bastard and this—” Virgil muttered, looking disgusted as he stared at his bandages before glancing over at Logan. “—is nothing. He's done much worse to me when he gets worked up. He says its about figuring out how I do it, but if you ask me, he just gets off on hearing me scream.”
Logan's skin tingled with fear and he could feel tears growing in his eyes as he swallowed past the lump in his throat and nodded. “I felt like that might be the case.”
“He owns us. We’re not even people to him.” Virgil’s words fel from his lips absently as he rambled. “And when Picani gets a new subject, he's miserable. He a whole new level of sadism and miser—Shit.”
Virgil paused as Logan sucked in a sharp breath, shaking from the overwhelming series of events from the last few nights.
“Hey, don't panic.” Virgil jolted upright, turning to rest his hands on Logan’s shoulders. “Wait—No, no, just breathe with me. Don't panic.”
Logan sucked in a ragged breath as Virgil rested a hand on his chest, applying a gentle pressure to help ground him. His throat ached as he tried to suppress another sob and Virgil curled an arm around his shoulder.
“You are going to get through this, Logan.” Virgil hushed him urgently. “God. I'll help you but you need to stop. You can't lose it now.”
“I—I’m sorry.” Logan felt himself tugging on his hair as he whispered between ragged breaths. " I'm s-s-sorr—"
“It's okay.” Virgil whispered insistently, tightening his grip on Logan’s shoulders. “You're going to be okay. Just get your breathing under control.”
Logan nodded, body aching as he suppressed the overwhelming panic seizing his muscles. Slowly, through Virgil’s gentle touches and kind words his breathing returned to normal and his muscles started to relax.
“There you go.” Virgil let out a sigh, leaning back. "You did okay."
“I'm sorry.” Logan whispered between pained breaths. “I'm being irrational—”
“Don’t do that to yourself. Your reaction is the only thing that makes sense in this godforsaken place,” Virgil’s eyes tipped sympathetically towards Logan in the dark, flashing with the knowledge of their grim reality. “but you can’t afford to be emotional here. You'll get hurt if you do this around the wrong people.”
Logan paused, feeling his breathing slow a bit at the kind look in Virgil’s glowing purple eyes. “Thank you for your help.”
“I mean it. You can't react like that with the doctor.” Virgil whispered, roughly wiping away the streaks of tears off his cheeks. “The doctor will exploit every fear you show him. You have to be stronger than him.”
“O-okay.” Logan whispered, still trembling as Virgil talked him through his panic.
“Find a place in your head that you can disappear to when you’re in his hands.” Virgil stated with a pitiful smile as he stared at Logan’s distant stare. “Whatever you do, don’t show him what you’re feeling.”
“I will—um, thank you for the advice.”
“It's nothing.” Virgil muttered quietly. “Consider it an apology for waking you up with a shiv to you throat. Alright?”
Logan sucked on his lip, curling his knees to his chest. “It's fine. I realize now why you acted in such a manner.”
"It's not fine, but whatever." Virgil shrugged as his lip twitched with guilt. “but either way, you look like shit and I think you should get some rest.”
“I'm not sure if I’ll be able to sleep at this point.”
“You need to try. You need whatever energy you can get to get through tomorrow.”
Logan blinked up at the serious tone in Virgil’s voice as he slid up on the bed and faced the door.
“I'll keep an eye out and wake you before Picani and his goons show up. Okay?”
“S-sure.” Logan whispered, chilled by the seriousness in Virgil’s voice.
“You can trust me on this, Logan.” Virgil paused raising an eyebrow at Logan. “There’s not much I can do to protect you, but at the very least, I won’t let Picani catch you by surprise.”
Logan let out a breath as Virgil patted the bed next to him. Stiffly, Logan slid over to him and slipped underneath the thin blanket. Uneasily, he rested down on the pillow next to where the Virgil perched, staring at the door. “Thank you, Virgl. I—I know you don't have to help me.”
“I want to.” Virgil muttered under his breath almost to himself. His voice was so quiet Logan nearly didn’t catch the end of his statement. “I never meant for anybody to get hurt.”
Logan blinked, considering Virgil’s words as a deep exhaustion crept over him. He leaned his head back on the pillow, staring up at the distant look in Virgil’s eyes as he stared at the closed door of their cell. He sighed. Falling asleep next to the stranger who'd had a knife to his throat only minutes seemed like an impossible feat but only a few short minutes had passed before the exhaustion began to outweigh his anxiety. He could feel his eyelids dropping even as his heart fluttered with fear of the man next to him. This had to be a mistake and Logan was well aware of that fact. Yet, as his mind drifted off to sleep, he found himself easing to sleep with the madman with the knife next to him anyway.
---
Author’s Note: That’s it for now, but hopefully it won’t be too much longer before we get to here more about these poor boys. Thanks for reading, and again, if you want to be on the taglist, all you have to do is let me know!
General Taglist:
@justanotherhumanstuff @im-an-anxious-wreck @shadowyplaidpurseegg
#sanders sides#sanders sides fic#sanders sides fanfiction#sanders sides fanfic#ts logan#logan sanders#ts virgil#virgil sanders#tw weapon#tw abuse#tw food#L'Appel Du Vide#villain writes
22 notes
·
View notes
Text
Microsoft Office 365 Mso 32 Bit Product Key
Microsoft365.com/setup - Microsoft 365 with Office Apps| Enter Product Key
Microsoft 365 Mso Version
Microsoft Office 365 Mso 32 Bit Product Key 2019
Microsoft Office 365 Mso
Microsoft Office 365 Mso 32 Bit Product Key
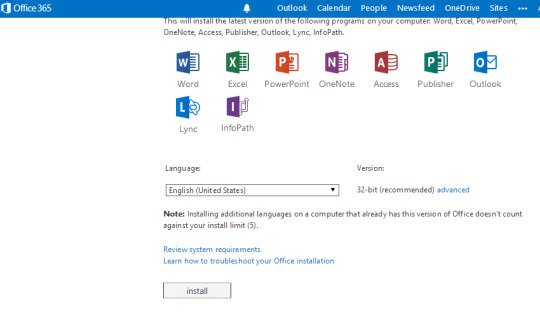
Microsoft365.com/setup allows you to download and activate the MicrosoftOffice setup. Microsoft 365 plans for personal and home provides robust Officedesktop apps including Word, PowerPoint, Excel, Outlook, and OneNote.Microsoft365 subscribers can always install the latest version of MS Office and getfrequent software updates.
If youhave a Microsoft account, sign in and enter the product key at Microsoft365.com/setupto activate your product. Install and set up your Office 365 apps with thegiven instructions.

Microsoft 365 ProductKey - Microsoft365.com/setup
Although you're probably interested in finding only your Office product key, Recover Keys supports over 9000 apps, can scan remote Windows and Mac computers, recover license keys from external storage, scan multiple Windows installations, and can even run from a USB drive. And at £24.95 / $29.95, it's cheaper than buying another copy of Office. Compared to Office 2019 and Office 2016, Office 365 has more features tailored towards cloud access. For example, to turn on autosave, you have to use Office 365. Below are the direct links to download Office 365 ISO/IMG files. The ISO file contains both 32-bit and 64-bit installers. Over the Internet. This is the easiest and quickest method of activating Microsoft Office 2013 with a product key. Here are the steps you need to follow: Launch the MS Office software program. You will see an Activation Wizard prompting you to enter a working serial key. Enter the key and click Activate to complete the activation process.
Office product key of Microsoft 365 is a subscriptioncode that you can purchase from the Microsoft store or any other online platform,also available in a retail card. It comes with 25 characters alphanumeric codeand has the same activation effect for your Microsoft 365 product. If you havea digital license, check it on your order confirmation mail. For product key,see card's backside appearing as XXXXX-XXXXX-XXXXX-XXXXX-XXXXX.
How to downloadMicrosoft 365 using product key?
Makesure you've created a Microsoft account and have a product key, then follow thebelow instructions for Microsoft365 download –
It's the easiest way to download MS 365.
Openmicrosoft365.com/setup link on a web browser.
It'll take you to Microsoft 365 page.
Click 'Sign In' or 'Create a new account.'
Enter Microsoft account credentials or fill in details to create one.
Type the 25 digits unique product key, tap Continue.
Select your subscriptions type.
Click Install Microsoft 365 to start download.
Microsoft 365Installation & Activation Instructions
Beforeyou track installation steps, know if your device fulfills the requirements:
Processor- 1.6 GHz or faster, 2-coreIntel processor
Memory - 2 to 4 GB RAM (32-bit or 64-bit)
Hard disk- 4 GB for Windows and10 GB for macOS.
Microsoft 365 Mso Version
WindowsOS: Windows 10, Windows 8.1,Windows Server 2019, Windows Server 2016
macOS: One of the three latest versions of macOS.
Set up Microsoft 365 ForWindows –
Download the latest version from microsoft365.com/setup website.
After a successful Microsoft 365 download, select options like Run, Save File, Setup on the used browser.
User Account Control prompt appears, click YES.
Installation for windows begins.
Wait for the prompt - You're all set! Office is installed now.
To start activation, open one app of the Microsoft 365 software pack.
Accept license terms and continue.
If your software isn't activated, sign in with MS office to associate with license activation.
Set up Microsoft 365 ForMac –

Open Finder, then find recently downloaded Microsoft software pack.
Double-tap on the installer.pkg setup to begin installation.
Accept Office 365 license terms.
Provide your mac admin username and password once prompt.
Click Install Software.
Tap Get Started to activate the Microsoft 365 software.
You can login with Microsoft account to get updates frequently.
Get Help with Microsoft365.com/setup–
Redeemyour Microsoft 365 product key, which is one-time process that will add yourproduct to your Microsoft account. Therefore, make sure the product key isentered correctly. Microsoft Account login is an essential step, if you don'thave any, visit account.microsoft.com to create one. You can then redeemthe key and install Microsoft setup from www.microsoft365.com/setup.
Microsoft Office 365 Mso 32 Bit Product Key 2019

What's new in Microsoft 365
Installthe latest version 16.0.13801.20266for windows and 16.47.21021600 for mac. Then, Microsoft 365 will allow you to use:
·Use thenew dictation toolbar
·Searchusing foreveryday language
·Sharemessages from Outlookto Teams
If yourequire any help, use Microsoft support to contact the team.
If you are searching the internet for a Microsoft Office 365 Activation Code / product key then you’ve come to the right place now, one day he shares with you an amazing app for the basic productivity apps needed for work done in the modern business. The norm for productivity suites is compared to the Office 365 Suite. These are applications like Word, Excel, Outlook, PowerPoint, OneNote, and OneDrive.

Microsoft Office 365 Product Keys (updated 06/2021) :
MT7YN-TMV9C-7DDX9-64W77-B7R4D6PMNJ-Q33T3-VJQFJ-23D3H-6XVTXDJD94-DFKD9-FJD94JD894-FJKD94JDDJKSE-DFJS93-DFJKD94JD-DJKD94JD
Microsoft Office 365 Activation Code (updated 06/2021) :
MH2KN-96KYR-GTRD4-KBKP4-Q9JP9P8TFP-JGFMM-XPV3X-3FQM2-8K4RPH746C-BM4VK-TZBB8-MVZH8-FXR322MHJR-V4MR2-V4Z2Y-72MQ7-KC6XKFBFPP-2XG5Y-FG9VH-DVQ2Z-QJRCH6KTFN-PQH9H T8MMB-YG8K4-367TX
Microsoft Office 365 Pro Plus Product Key / Activation Code / Serial Keys (updated 06/2021) :
N4M7D-PD46X-TJ2HQ-RPDD7-T28P9NK8R7-8VXCQ 3M2FM-8446R-WFD6X2MNJP-QY9KX-MKBKM-9VFJ2-CJ9KKKBDNM-R8CD9-RK366-WFM3X-C7GXK6KTFN-PQH9H T8MMB-YG8K4-367TXMH2KN-96KYR-GTRD4-KBKP4-Q9JP9
How to activate Microsoft Office 365 without Activation Code / product key :
Microsoft Office 365 Mso
Follow 3 steps below to activate Microsoft Office 365 :
Microsoft Office 365 Mso 32 Bit Product Key
Step 1: You copy the code below into a new text document.
1 note
·
View note
Text
Tech Breakdown: What Is a SuperNIC? Get the Inside Scoop!

The most recent development in the rapidly evolving digital realm is generative AI. A relatively new phrase, SuperNIC, is one of the revolutionary inventions that makes it feasible.
Describe a SuperNIC
On order to accelerate hyperscale AI workloads on Ethernet-based clouds, a new family of network accelerators called SuperNIC was created. With remote direct memory access (RDMA) over converged Ethernet (RoCE) technology, it offers extremely rapid network connectivity for GPU-to-GPU communication, with throughputs of up to 400Gb/s.
SuperNICs incorporate the following special qualities:
Ensuring that data packets are received and processed in the same sequence as they were originally delivered through high-speed packet reordering. This keeps the data flow’s sequential integrity intact.
In order to regulate and prevent congestion in AI networks, advanced congestion management uses network-aware algorithms and real-time telemetry data.
In AI cloud data centers, programmable computation on the input/output (I/O) channel facilitates network architecture adaptation and extension.
Low-profile, power-efficient architecture that effectively handles AI workloads under power-constrained budgets.
Optimization for full-stack AI, encompassing system software, communication libraries, application frameworks, networking, computing, and storage.
Recently, NVIDIA revealed the first SuperNIC in the world designed specifically for AI computing, built on the BlueField-3 networking architecture. It is a component of the NVIDIA Spectrum-X platform, which allows for smooth integration with the Ethernet switch system Spectrum-4.
The NVIDIA Spectrum-4 switch system and BlueField-3 SuperNIC work together to provide an accelerated computing fabric that is optimized for AI applications. Spectrum-X outperforms conventional Ethernet settings by continuously delivering high levels of network efficiency.
Yael Shenhav, vice president of DPU and NIC products at NVIDIA, stated, “In a world where AI is driving the next wave of technological innovation, the BlueField-3 SuperNIC is a vital cog in the machinery.” “SuperNICs are essential components for enabling the future of AI computing because they guarantee that your AI workloads are executed with efficiency and speed.”
The Changing Environment of Networking and AI
Large language models and generative AI are causing a seismic change in the area of artificial intelligence. These potent technologies have opened up new avenues and made it possible for computers to perform new functions.
GPU-accelerated computing plays a critical role in the development of AI by processing massive amounts of data, training huge AI models, and enabling real-time inference. While this increased computing capacity has created opportunities, Ethernet cloud networks have also been put to the test.
The internet’s foundational technology, traditional Ethernet, was designed to link loosely connected applications and provide wide compatibility. The complex computational requirements of contemporary AI workloads, which include quickly transferring large amounts of data, closely linked parallel processing, and unusual communication patterns all of which call for optimal network connectivity were not intended for it.
Basic network interface cards (NICs) were created with interoperability, universal data transfer, and general-purpose computing in mind. They were never intended to handle the special difficulties brought on by the high processing demands of AI applications.
The necessary characteristics and capabilities for effective data transmission, low latency, and the predictable performance required for AI activities are absent from standard NICs. In contrast, SuperNICs are designed specifically for contemporary AI workloads.
Benefits of SuperNICs in AI Computing Environments
Data processing units (DPUs) are capable of high throughput, low latency network connectivity, and many other sophisticated characteristics. DPUs have become more and more common in the field of cloud computing since its launch in 2020, mostly because of their ability to separate, speed up, and offload computation from data center hardware.
SuperNICs and DPUs both have many characteristics and functions in common, however SuperNICs are specially designed to speed up networks for artificial intelligence.
The performance of distributed AI training and inference communication flows is highly dependent on the availability of network capacity. Known for their elegant designs, SuperNICs scale better than DPUs and may provide an astounding 400Gb/s of network bandwidth per GPU.
When GPUs and SuperNICs are matched 1:1 in a system, AI workload efficiency may be greatly increased, resulting in higher productivity and better business outcomes.
SuperNICs are only intended to speed up networking for cloud computing with artificial intelligence. As a result, it uses less processing power than a DPU, which needs a lot of processing power to offload programs from a host CPU.
Less power usage results from the decreased computation needs, which is especially important in systems with up to eight SuperNICs.
One of the SuperNIC’s other unique selling points is its specialized AI networking capabilities. It provides optimal congestion control, adaptive routing, and out-of-order packet handling when tightly connected with an AI-optimized NVIDIA Spectrum-4 switch. Ethernet AI cloud settings are accelerated by these cutting-edge technologies.
Transforming cloud computing with AI
The NVIDIA BlueField-3 SuperNIC is essential for AI-ready infrastructure because of its many advantages.
Maximum efficiency for AI workloads: The BlueField-3 SuperNIC is perfect for AI workloads since it was designed specifically for network-intensive, massively parallel computing. It guarantees bottleneck-free, efficient operation of AI activities.
Performance that is consistent and predictable: The BlueField-3 SuperNIC makes sure that each job and tenant in multi-tenant data centers, where many jobs are executed concurrently, is isolated, predictable, and unaffected by other network operations.
Secure multi-tenant cloud infrastructure: Data centers that handle sensitive data place a high premium on security. High security levels are maintained by the BlueField-3 SuperNIC, allowing different tenants to cohabit with separate data and processing.
Broad network infrastructure: The BlueField-3 SuperNIC is very versatile and can be easily adjusted to meet a wide range of different network infrastructure requirements.
Wide compatibility with server manufacturers: The BlueField-3 SuperNIC integrates easily with the majority of enterprise-class servers without using an excessive amount of power in data centers.
#Describe a SuperNIC#On order to accelerate hyperscale AI workloads on Ethernet-based clouds#a new family of network accelerators called SuperNIC was created. With remote direct memory access (RDMA) over converged Ethernet (RoCE) te#it offers extremely rapid network connectivity for GPU-to-GPU communication#with throughputs of up to 400Gb/s.#SuperNICs incorporate the following special qualities:#Ensuring that data packets are received and processed in the same sequence as they were originally delivered through high-speed packet reor#In order to regulate and prevent congestion in AI networks#advanced congestion management uses network-aware algorithms and real-time telemetry data.#In AI cloud data centers#programmable computation on the input/output (I/O) channel facilitates network architecture adaptation and extension.#Low-profile#power-efficient architecture that effectively handles AI workloads under power-constrained budgets.#Optimization for full-stack AI#encompassing system software#communication libraries#application frameworks#networking#computing#and storage.#Recently#NVIDIA revealed the first SuperNIC in the world designed specifically for AI computing#built on the BlueField-3 networking architecture. It is a component of the NVIDIA Spectrum-X platform#which allows for smooth integration with the Ethernet switch system Spectrum-4.#The NVIDIA Spectrum-4 switch system and BlueField-3 SuperNIC work together to provide an accelerated computing fabric that is optimized for#Yael Shenhav#vice president of DPU and NIC products at NVIDIA#stated#“In a world where AI is driving the next wave of technological innovation#the BlueField-3 SuperNIC is a vital cog in the machinery.” “SuperNICs are essential components for enabling the future of AI computing beca
1 note
·
View note
Text
Sitting beneath the glaring full moon, a young woman held a book in her lap. The rustle of the pages, coupled with her ebony-furred cat’s rumbling purr, offered the only sound in the night. The woman turned the page with her free hand – the other was busy with stroking the feline.
Yawning, she blinked. The moon hung high in the sky, and she knew she should be getting home. She could almost hear her sister scolding her now. “Sya, you have school and studying! You can’t stay out in that field all day, every day.”
To which she would always respond, “Well, why not?”
She laughed at the memory. The town was just visible beyond the hill, most lights turned out for the night.
Leaves from the nearby forest rustled, a quiet whisper. Leaping up, her cat knocked into her chin, clacking her teeth together. Sighing, the woman turned to look. Fur bristling, the feline stared unblinkingly into the woods, its eyes a glowing yellow.
“You’re seeing things, Luna,” she said, but when she looked down, the cat was gone. She glanced around, searching for the small beast.
Spotting a blur darting through the woods, she sighed, peering in the direction the feline had run.
She crept towards the woods, calling the cat’s name. Receiving no answer, she shook her head and continued onward slowly. She moved lightly, not wanting to attract unwanted attention.
“Luna?” Her fingers rapped against her leg as an owl’s haunting call rang in the distance. “Luna, come here!”
No answer.
Cold sweat ran down her back. Exhaling, she turned to return to the hill. The cat had disappeared before and come back.
She hesitated, not wanting to leave without her pet. In the silence, a caress of air moved by her ear, leaves blowing in the sudden draft.
Shaking her head, she took another step. As she stopped, the same breeze echoed her movement, this time escorted by a succinct shadow.
Standing impeccably still, heart roaring in her ears, she watched an elongated hand cover the rift in the trees – her only illumination source. She silently cursed herself, wishing she had brought a flashlight.
A vaguely humanoid figure, its body as colorless as the empty space around it, visible only by its outline - a slight rim of light surrounding it was all she could see – all else was an empty void. It was almost beautiful, in a horrifying way.
As she watched it, a new light appeared. A thin white line across what would be its face, stretching into a gruesome smile. It stretched out a thin, hand-like shadow, as if welcoming her. Stumbling away, she batted at the outstretched limb weakly.
The wide grin flipped, the horrifying smile now an even worse scowl. It shook, the outline blurring and blurring and blurring.
…
And then it was gone.
…
The darkness trickled away, the familiar but now frightening scene of the forest enveloping her once again.
Her sight flickered, her lashes drifting closed. She fought it, afraid to close her eyes. Afraid the thing would return.
Failing, her vision distorted and died away.
The sun was blazing in the sky by the time she awoke. She still felt cold, the night’s events a blur. Remembering her absent cat, she glanced around. Sure enough, the cat had returned, staring at her with suspicious eyes.
“Hey, Luna,” the woman said, calming. The feline yowled, shrinking away. Its fur stood on end – something terrified it.
Furrowing her eyebrows, she called the cat’s name again.
“That won’t do any good,” an amused voice answered. “Those beasts won’t come anywhere near anything remotely supernatural.”
She yelped, swiveling around. Hovering above her was a figure dressed in all black, a hood covering his face.
Deciding to follow her cat’s example, she recoiled.
“Relax, Sya. It’s only me,” the figure said, taking off his hood. He wasn’t all too bad looking, with a strong jaw and warm blue eyes.
She gave him a puzzled look, though he did seem distantly familiar. “And who are you? How do you know my name?”
“Sorry.” The man sat next to her, setting a large scythe beside him. “I always forget. My name is Tyr. King Death has requested your presence. You are still alive, though.”
She nodded, though she didn’t understand at all. “And why does Death want to meet me?”
Shrugging, he offered his hand. She took it and stood. He grabbed his scythe, wrapping his free arm around her. The forest dissolved into ink. For a moment, she thought the shadow thing was back, but them beams of light broke through the dark, images – memories – dancing across her vision. A large black owl, dancing on a beam of white, flew past her head.
Her reaper looked at the animal. “It’s your spirit animal,” he explained.
She nodded, too breathless to respond. They floated there, motionless, but the perfect moment faded away. Faded into a riverscape, the gentle lava waves lapping against the shore. Across a bridge stood a castle made of black stone, lit by a soft red glow.
She gasped, clinging to her reaper’s arm.
He reached over and carefully pried her hand off. “Ow, Sya.”
Wincing, she looked back towards him. Apologizing, she bit her lip.
“It’s fine. Everyone gets emotional the first time.” He smiled. “Let’s not keep the king waiting, shall we?”
She rested her hand gently on his arm and followed him across the bridge. A tall, handsome man, a crown of bone resting atop his head, met them at the door.
Tyr sunk into a bow. Sya looked around, eyes wide, before sinking into a hesitant curtsy. She hovered like that for a short while before the man’s gaze caught on her.
Death looked her over, curiosity flashing in his dark eyes. “Thank you for bringing her, reaper.”
“Hi?” Sya asked. “Tyr said… Tyr said you wanted to speak with me?”
“You’ve interacted with something out of my control. I do not know what it was, or why it attacked you. However, you are not the first.” He led them to the balcony, gesturing at a grassy valley.
There were at least three dozen people, milling about, talking in hushed voices. Their discussions abruptly halted when they noticed the king’s presence.
“All of these people came into contact with this thing,” Death said. “All of them died. You, however – you didn’t.”
“Why?”
He flicked a hand, a seat appearing behind her. She sat gratefully.
“All of these people have similar spirit guides in one way – they are all prey animals. It makes sense. This thing is obviously a predator, so it goes after prey. Tell me what you saw. All of it.”
Sya hastily recounted how it had stolen the light, smiled, offered a hand – all of it.
The king hummed quietly. “Anything else?”
She shook her head.
Nodding, he sighed. “Do you have pets? What spirit guide did you see?”
“I have a pet – a black cat. There was an owl–”
“It was massive,” Tyr inserted. “I’ve seen large ones before, but it was huge. And pure black.”
Death smiled for the first time since Sya’s arrival. “Call it,” he said. “You know how.”
“Sure,” she whispered. “Sounds great.”
Sitting cross-legged and closing her eyes, she imagined white scenery. Her forest came to mind, coated in snow during a particularly chilly winter. A shadow, much like the one she had seen before, when the creature came, flitted by her. This time, though, she was not afraid. She knew that it was not evil spirits following her, but good ones. Instinctively, she went to the tree on the hill.
A book rested there, a light dusting of snow across its cover. She sat beneath the full moon, taking the book in her lap. The rustle of the pages offered the only sound in this world of spirits. She turned to a randomly selected page.
It was blank. She went to flip to a new page, but dark ink began to spread across the sheet – as though an invisible writer had spilled their inkwell across the snowy white pages.
She stopped to see what would happen. The ink flowed, forming into an elegant cursive script.
Sya read it aloud seamlessly, despite the foreign language. A dark shadow appeared on the ground before her, the massive guide perching on a branch beside her. Standing, she looked into the owl’s great, round eyes.
Bowing its head, it let out an echoing call. The spirit world disappeared, Death’s castle reforming in her vision.
Instinctively, she stood, extending an arm. A beam of white light cut a jagged mark into the wall, the powerful bird soaring out to perch on her limb.
Its distinctive call echoed from the walls, filling the castle with sound.
“Fascinating…” A peculiar look came across Death’s face, almost – but not quite – awe. “Nebulosa.”
He bowed slightly, a respectful act from one deity to another. The owl responded in turn, spreading its wings in a silent movement.
Sya shifted closer to the king. “You – you know her?”
The king nodded. “She is a great deity from our past. I can tell you her story if you wish.”
Smiling, she shook her head. “Perhaps another time, your majesty. We should focus on finding out how to defeat this thing that attacked me. What is it?”
His face fell. “We don’t know.”
Sighing, he stood from his throne, stepping towards her and Tyr. “My sister agreed to allow us in her palace to discuss it. Nebulosa can access realm-shifting. Tyr and I will meet you there.”
With that, he disappeared in a cloud of inky smoke. With an exasperated sigh, she nodded to her guide. The iridescent blackness seeped into her vision. Nebulosa hooted softly in her ear, soaring away. In her wake she left a trail of white, a road to lead her way.
Sya took a hesitant step, her foot hitting the white path solidly. She looked out at the blackness.
Curiosity getting the better of her, she waved her foot slightly off the path. It hovered in empty space briefly before she yanked it back. A disapproving hoot scolded her, beckoning her on. She followed, chastised. As she walked, she came across a door – perched above it was none other than Nebulosa.
She hesitated – a sense of danger seemed to come from the silver archway. But her friends were in there.
Friends. She had known them such a brief time. Were they really her friends?
Yes. And technically, she had known Tyr for a long time. For all her life. Lives. She took a deep breath.
Do they think of you as a friend?
She froze. Confused, she wondered why she would have such a negative thought.
You did not. I did.
She turned around. Umbra – where had the name come from? She had never heard it before – stood there, the gruesomely wide smile once again taking up its features.
“You.” Her voice shook, betraying her fear. Cursing herself, she took a deep breath and tried again.
“What do you want, Umbra?” she asked. Her voice didn’t shake this time.
Come with me. You owe nothing to these people. What have they done for you? If you came with me, you could live forever.
It was tempting. Of course it was – immortality; the dream of Earth.
You want it. I know you do. I know everything about you. The spirit world disappeared. Sya’s home, the apartment she shared with her sister, took its place. She spun around, eyes wide.
“Sissy! Thank gods.” It was her sister, plowing down the stairs to embrace her.
Bewildered, Sya wrapped her arms around her. “Aura? What?”
“That filthy cat of yours came home without you. It may be a mangy beast, but its fiercely loyal. We were so worried!”
“We?” Sya couldn’t think of anyone else who might worry.
Had she stumbled through a portal? How else would she be back home? Back home. Aura had seemed frantic. How long had she been gone?
She repeated the question aloud.
“Only a day.”
But you already knew that, didn’t you? You doubted it – doubted that you’d be home. But the doubt that I knew how she hated that pet of yours. That was stronger. But you forget, my dear Sya.
Aura disappeared, her ruby hair flattening into a black, faceless figure. Umbra’s smile had changed. Where it had had some semblance of warmth, now it held only anger. I know you. I know every thought, every memory, every doubt. I can give you that life back for real.
“You know,” Sya started, the tremble back in her voice. “Humans usually have eyes.”
Umbra let out a wet cough. It reminded Sya of when her grandmother died, the rattling breaths terrifying the five-year-old. Umbra’s coughs lasted longer, dragging on and on and on.
Sya finally realized that he was laughing. At her. Her house disappeared, the spirit world’s inky surroundings enveloping her. It was comforting, now.
See, now that’s why I like you, little witch.
“Why do you call me that?” she asked, slowly backing towards the portal.
Its smile was warmer now, as though remembering something fondly. When I saw you with your cat, I assumed it was your guide. A witch usually has a black cat, and I thought you’d be willing to join me. You still are, though you fear me. My offer tempts you; I can see it.
She took another slow step backwards. Expecting to find solid ground, or perhaps the wall of the portal, instead her foot met only empty space. She whirled around, stumbling back onto the path.
Shaking its ‘head,’ Umbra tutted disapprovingly. Its illusions had swapped where she thought the portal was with where she thought Umbra was.
Fooled. Again.
Now, now. Where do you think you’re going, little witch? Certainly not through there. It won’t take you anywhere you want to go.
“Yes, it will,” Sya said, clenching her jaw. “It will take me to my friends.”
So, you cling to the notion that these people care about you. Its form shifted, the blackness changing into a truly humanoid form.
Blue eyes, sandy blond hair. Tyr’s strong jaw. Umbra smiled unnaturally.
Is this more visually pleasing? Do you prefer me in this form?
His tongue flicked, snakelike. It was black and forked, foreign in Tyr’s mouth. Shuddering, Sya stumbled away, forgetting that she was on a narrow path. As she nearly fell, Tyr’s hand – Umbra’s hand – grasped her arm, pulling her close to him.
Clearly not. Fine. We can ask them ourselves. The portal lit up with swirling patterns of white.
He led her through.
The first thing she noticed was the aroma. The air smelled welcoming, warm. Then she noticed the walls; light fractured into perfect rainbows, making the crystal walls alight with a million colors – more than Sya had ever imagined.
But then Umbra – still disguised as Tyr – dropped the illusion.
The immaculate walls shattered. The warm smell spoiled with smoke.
But most prominently the white-winged angel crumpled on the ground.
“No.” The word was almost inaudible, gone as soon as it came.
“Umbra. What did you do!” Shaking her head frantically, Sya ran forward.
He didn’t stop her. I didn’t do anything. Merely disguised the truth.
Collapsed on her side in a pool of blood lay the angel. She had one wing twisted beneath her, the other sprawled to the side.
Umbra stood beside her, looking down at the angel.
“Umbra.” He didn’t respond, preferring to examine a shattered piece of crystal. He fingered it, flipping it across his long fingers.
“Umbra!” she snapped. Startled, he cut himself with the fragment. He glared at her, the blue eyes a hundred times colder than Tyr’s ever were.
What is it, Sya? What do you want me to do? Sya noted that he used her name – he hadn’t done that before.
Looking up at him with zero fear, she snarled back her response. “Where are my friends?”
He waved his hand – a completely unnecessary gesture – and after a few seconds Tyr and Death barged through the door at the end of the hall.
“Are there any more illusions?” she asked harshly.
No.
She gave him a disapproving look, as he was still in Tyr’s form.
You’ve become very demanding, little witch.
She deigned not to respond, and with a sigh he shifted back into his natural form, reverting to the horrific grin. He very obviously still wanted to intimidate her into accepting his offer.
Death noticed as Umbra shifted, grabbing Tyr by the back of his hood before he could get any closer.
“Nebulosa!” She swooped through the same area Sya had arrived from. But before she could reach the king, Umbra reached up, snatching the bird out of the sky.
Nebulosa. I remember you, my dear. Do you remember me? he growled.
“Let her go.” Sya stood from her position next to the fallen angel.
Turning to set his terrible smile on her, he stepped forward. As he did so, he drew up another illusion.
This is your last chance to turn against them, little witch.
“Release the owl, Umbra.” Her voice stayed steady, though she felt her hands shake.
You are afraid of me, Sya. You cannot harm me, and you certainly cannot hold your ground in a fight.
Standing firm, she held her head high. “Perhaps. Perhaps not.” She was bluffing, she knew it, he knew it.
She looked around herself – it was a stunning deception. She looked out at the clouds from the top of the grassy mountain.
“It is an impressive illusion,” she said, willing herself to stay strong.
His smile widened. I can teach you how. It isn’t so hard as it seems.
Swallowing, she offered him a slight smile. “I’d like that. I’d like that a lot.”
He changed his appearance again, but this time it wasn’t Tyr. He was handsome. He had black eyes – no whites, just pure darkness – and pale skin. Pale, thin lips stretched in a wide grin that seemed perfectly natural on this face.
She hated to admit it, even to herself, but he was handsome.
“Who is this? This body, I mean,” she asked, tilting her head.
Me. Me before I lost this form. Before she –
He froze, his illusion shattering. His large black form lost all appearance – only a black mass floating before her. Turning around, Sya glimpsed Death kneeling beside the angel, Tyr standing guard above him.
Nebulosa flew back to her arm, perching gracefully.
Umbra, glaring, drew up another illusion. Though conscious of the illusion and how it looked, Sya had double vision – with Nebulosa’s help, she saw through the deception.
She called his name, called for him to stop.
Little witch. Why can’t you just give up on them?
Shaking her head, she smiled gently. “They wouldn’t give up on me. Why should I give up on them?”
He didn’t answer.
“Someone hurt you. You recognized Nebulosa, didn’t you. You called her ‘my dear.’ That wasn’t coincidence.”
No. The word was almost inaudible, gone as soon as it came. It wasn’t.
“Umbra. Cruelty to others won’t make up for cruelty to you.”
Death stood from the angel’s side. “We can make you a guide. You can help others, not harm them. I’d say you’re a panther, correct?”
Why would I want that? Why shouldn’t I destroy you all, now? I could do it. I have the power to kill Death. I’d be worshipped by the humans. They’d all be immortal.
“Would that make you happy?” Sya asked him, her voice soft as could be.
I’d be powerful! I’d – I’d be a god!
“You?” Death shook his head. “You’d be miserable.”
A light caught their eyes, the light of a portal opening. Nebulosa flew through it, her movements as silent as ever.
I will follow her. Death smiled at the shadow-beast, extending a hand. Umbra took it, changing into a great black panther. Not an illusion, this time. Bowing, it turned, leaping through its lover’s portal.
Letting out a breath she didn’t know she was holding, Sya watched the swirling light emitting from the portal.
Slow clapping echoed through the room. “Wonderful. Just wonderful. I suppose I’ll have to kill you myself, then.”
A powerful figure rammed into Sya’s side, sending her flying through the gateway. She landed, hard, on the white road. Tyr’s face hovered above her, his arms holding her down.
He stood with a growl, pulling her close to him. His striking blue eyes glared into hers, paralyzing her with fear.
Silently, he twisted an arm behind her back. The movement involuntarily spun her around. She tensed, her back to him, as she faced out at the void.
He nudged her forwards…
And forwards…
And forwards…
Until she was right on the edge, her toes hanging out into the abyss. The thought to call for Nebulosa flashed through her head. He covered her mouth with his hand.
“Sya.” He offered her a disappointed sigh. “What do you think you’re doing?”
She bit him with all her strength, tasting blood as she sunk her teeth into flesh. His hand tensed but didn’t release her. The sticky feel of blood ran down her chin. The thought that her shirt would be ruined flashed briefly through her head, and she wondered sardonically if that was important when she was standing on the edge of the void.
“Why, Tyr?” she whispered against his bloody hand. “I trusted you. How could you do this?”
“Quite easily, really,” he replied, releasing his grip on her.
She stumbled, caught off balance by the sudden lack of his steadying hands.
Flapping her arms in a frantic bid for safety, she managed to regain her balance, teetering on the edge.
A heavy sigh met her ears, disappearing with nothing to echo off.
Her hair moved – just the slightest bit, but enough. It brushed against her cheek. Involuntarily, her muscles twitched, her head jerking to the side.
Her balance lost, she slipped. Losing all sense of direction as she fell, all she knew was the rush of air against her face. Her locks of hair whipped against her forehead.
The only sound – a short ‘tut, tut,’ met her ears briefly, then the soft foot falls to let her know of Tyr’s departure.
Abruptly, the sickening sense of falling - that pit in the center of her stomach – stopped. So did her air supply. She had heard stories from astronauts, the feeling of weightlessness, the sense of drifting through the empty blackness.
Only, the had helmets to provide them with air. They had stars, to show them the way, to fill the darkness. They always had something to keep them tethered, someone who could pull them free.
She had none of that, only blackness and empty space. Nothing to guide her, nothing to free her from her prison.
Or did she?
With the last inkling of oxygen left in her starving lungs, she croaked out a name.
“Umbra.”
She couldn’t tell if she was losing consciousness or not. Her head felt fuzzy, but she couldn’t see anything, eyes open or closed.
Then a flicker of light.
It might have been her imagination, looking for something to focus on in its last few seconds before she blacked out.
She woke with no feeling in her limbs. No, that wasn’t true. She had feeling, only she didn’t understand it. The feeling seemed different, alien. Her eyes flickered open, finding herself in the woods. Familiar woods, with tall pines, though her vantage point seemed odd. It appeared to be that she was sitting on a branch, though she couldn’t think of any that could hold her weight.
The details of the grass, the ants strolling along the bark of a neighboring tree, all of it was visible in clear, precise detail.
It unnerved her, as did the ruckus of chirping birds and buzzing insects, more than she had ever heard even in mating season.
That sort of sound level usually gave her a headache within seconds. Oddly enough, to her ears it was perfectly normal. She stretched.
And that’s when she realized why everything was so uncanny.
“Odd, isn’t it?” The voice was in the hoot of an owl, yet the words made perfect sense.
She looked at the large, gray wing connected to her back. The one that had taken the place of her right arm.
“Very,” she said, intrigued but not surprised when it came out as an owl’s call.
She hesitated, opening her mouth – beak – to ask the other owl a question. Before she could get the words out, a different voice stopped her.
Leaping up onto her branch, a panther licked its paw. “You are welcome.”
“Thank you,” she said. “Panthers aren’t usually in this area, you know.”
He purred. “Humans don’t come in this part of the woods, not since a young woman went missing. Besides, they cannot see us.”
Preening her wing, she hooted softly.
“Yes. There was no other way, not with Life gone. I’m sorry.”
“Don’t be,” she replied.
“I wouldn’t have wanted it any other way.”
(Hey guys. I wrote this “short” story as a school assignment, and it was what inspired me to write my current novel, bloodless.)
#horror#fiction#fantasy#writing#creative#creative writing#school work#short story#writing is hard#this was meant to be 1 page#what have i done
10 notes
·
View notes
Text
Chaser - Downdraft (Part One)
Chapter Title: Downdraft
Series Summary: Storm chasing is your passion. You decided in high school to study atmospheric science and spend your life studying storms. An accident leads you to the Avengers compound. A mother hen Tony Stark, a confused and concerned supersoldier, and some meddling friends, life is taking a new and unexpected turn.
Part Summary: You and your team head out to track a storm, putting you on a collision course with danger.
Features: Storms and storm chasing, incorrect science
Pairing: Eventual Bucky Barnes/Reader
Notes: In this part, we’re introduced to reader and her ragtag team of storm chasers. We also see a bit more of her relationship with Tony. We haven’t met Bucky yet.
Word Count: 1866

Log #15042018
Location: Lynchburg, Virginia
Downdraft (n.) - “a column of cool air that sinks toward the ground. It is most often accompanied by rain.”
The air was heavy with the promise of a storm. You knew the conditions were perfect for tornado formation. Usually you didn’t venture too far to the east in the midst of tornado season but you’d been tracking the storm system and knew the potential for fireworks was there.
For as long as you could remember, you were obsessed with the weather. Your mother would recall how you could tell it was going to storm without ever looking at a radar map when you were a child. You almost wondered if you had some kind of mutation. It was an ability that persisted into adulthood. Your mother’s favorite story to tell was about how you begged her to go home one day when the weather was clear and rain wasn’t in the forecast. Three hours later a storm rolled in that knocked out power for most of the town and brought down some of the bigger trees.
“What’s the game plan, Twister?” Sheridan asked you. Casey Sheridan was one of your partners in the field. The man was a trained first responder, volunteering back home with the local EMS. You had a small team assembled, all with the goal of studying storm systems to advance the science communities understanding of them.
“Thanks to our generous benefactor, we don’t have to pull a Jo Thornton and get right up with the tornado. The AI system will control the flight of the probes into the tornado and give us perhaps the most comprehensive data to date. The more storms we do this with, the more complete the data set becomes. Even if the probes become damaged entirely, the data will hopefully transmit. They have a home base they’ll return to and enough energy for a three day trip. Thanks to Stark we have them,” you explained.
“I hate that we work for a billionaire,” Deacon grumbled. No one was fully sure of what Deacon’s real name was. You knew it because you hired him. He adopted his nickname from Fallout 4 and stuck with it.
“We don’t work for him Deacon. We’re an independent group of scientists with funding from Stark Industries…there’s a difference,” you argued. He raised an eyebrow in your direction.
“Potay-to, Potah-to, Twister. Stark pays our bills, and I for one say, eat the rich,” Deacon replied. You shook your head at him.
“Well when you’re done plotting how you’re going to overthrow the bourgeoisie, I need you to finish a last check on the probes, Deacon. You know. Your job,” you said. You saw him roll his eyes and laughed to yourself.
You had two modes of transport. The van followed the pickup truck. The probes would be launched from your truck closer to the tornado. All you had to do was press a button on a remote you had in the cab of the truck. It was the first time the probes were going to be used. Up until then, your research had depending on distance analysis and observing the damage after a storm.
“National Weather Service just issued a tornado warning. It’s go time. Radar indicated rotation about two miles south,” Cody said. She was your eyes and ears on almost everything. She and Casey worked together tracking the radar and any warnings. Your main job was ensuring your team stayed safe and analyzing the data that came in.
You had a degree in meteorological and atmospheric sciences. It was your passion. You had graduated from Cornell and had your master’s, with a dream of getting your PhD eventually. Your encounter with Tony Stark had changed your life for the better.
Anxiety was setting in as you and your team headed south toward Lynchburg. You had a good idea of where the tornado would touch down based on the radar imaging. Cody and Casey remained in the van with Deacon driving. You were on your own in the pickup. You always worried going into a storm. About your safety. About the safety of your team. It was only natural.
“FRIDAY what’s the radar looking like?” you asked the AI as you drove. Tony had outfitted your truck with access to FRIDAY. You argued at first but she was helpful in a pinch. He had done a lot to add protection to your truck and the van. You knew he worried about you, which still shocked you.
“There is rotation approximately a half mile south,” she said. You nodded to yourself, and opened up the comms, another gift from Tony.
“We’re about a half mile out. There’s definite upward motion on that cloud up ahead. Pull off to the left coming up. We don’t want to get too close to this thing,” you said.
“Rain. We need to be ready to move. If this thing is rain wrapped,” Cody said her voice trailing off.
“Looks like we’ve got touch down. I’m deploying the probes. FRIDAY’s sensors will guide them toward the tornado,” you said as you pressed the button. You watched as the probes flew off toward the storm, praying they worked. When confirmation came from the team you had silent moment of celebration.
“Twist, I think we gotta go, this thing is going to come up toward us and we don’t want to get caught out,” Casey said.
“Copy, Sheridan. Let’s continue moving to the south. We can avoid running into it and still gather images. Keep your eyes up Deacon, you never know when something will pop up,” you said.
You drove forward, keeping an eye on the storm as you tracked it’s path, doing your best to judge what a safe distance was. You didn’t expect the debris that knocked into the truck that made you swerve off the road and flip.
——————————————————————————————————–
Tony was pacing around the lab. Bruce was doing his best to reassure Tony. Most of the team had never met you, but Bruce had. Your innate curiosity always managed to turn things around and diffuse the tension when Bruce and Tony would argue.
“We have a problem,” FRIDAY said, breaking the tense silence.
“What’s going on?” Tony asked, trying not to sound panic.
“Sensors in her truck indicate that there was an impact and the truck has flipped on its side,” FRIDAY said.
“Is she alert?” Tony asked.
“In and out, sir. I will patch you in to their comms,” the AI said. Tony knew as soon as he was patched in.
“Status report,” Tony said.
“Christ Stark a little warning,” Sheridan snapped.
“Noted. Now, status report,” Tony said.
“A piece of debris hit the pick up. We were about one hundred feet back. She went careening off the side of the road and the truck flipped. EMS ETA is about ten minutes. She’s been in and out of consciousness but there doesn’t seem to be major external injury,” Cody replied.
It didn’t take Tony long to get to Virginia, not with a quinjet. He was grateful to have Helen Cho on his payroll now, because as soon as you were stable, you were going to the compound, no arguments. There were few people Tony cared about on a deeper level. You were one of them.
“Kid’s in surgery, but the doctors think she’ll be fine,” Tony said. He called Pepper as soon as he had news.
“She won’t be happy about being dragged to the compound,” Pepper pointed out.
“Tough. She needs to recover, not be out on the next chase. Her team agrees. They’re all going on vacation to be with their families, no argument. She needs to rest. And we both know she won’t do that if she’s not at the compound,” Tony said.
“You’re on your own then. Because we both know she’s not going to like it,” Pepper said. Tony sighed.
“She’ll be on board when I give her free reign of the lab,” Tony said.
After talking to Pepper it was a waiting game.Tony had to pull serious strings to be able to see you. Your family was hours away and they weren’t going to come. He knew that. If you were awake, you’d know that. It had been that way for a long time. Another reason Tony worried about you, why he looked out for you.
“Hey kiddo,” he said once you were awake.
“Tony?” you asked, your voice raspy.
“Yeah. You had a bit of an accident,” he said. He watched your expression change as the memory of what happened came back. You groaned. He wasn’t sure if it was in pain or annoyance.
“How’s the truck?” you asked. He snorted.
“I’m having it brought back up to New York. Too much Stark Tech in that thing to let it go to a salvage yard,” he said.
“So it’s totaled?” you asked.
“Afraid so, kiddo. Gert is no more,” he said. You had named the truck, something that amused Tony to no end.
“And the others?” you asked.
“They’re fine. A little shaken, but fine. The van’s coming back up to the compound too while you recover. Your team is taking time off too. Visiting their families,” he said. You looked at him. He knew an argument was brewing. It was prime time for tornado season. You didn’t want to miss it.
“Tony,” you started to say. He shook his head.
“Kid, you broke your leg. You’re down for the season. You need to rest and recover,” he said.
“But you have that cradle thing,” you argued.
“That we only use for life threatening injuries or if we desperately need someone back in the field. There’s no shame in letting things heal the old fashioned way,” he said.
“I need to be back out there,” you argued.
“No. You need to rest. Your team needs time to rest. They thought you were a goner, kid. You’re lucky it seems to only be a minor concussion and a broken leg,” Tony retorted. A nurse soon came in, ending the standoff between the two of you. It wasn’t long before you were being brought up to the roof, where a quinjet was, and loaded in to be brought to the compound. Tony hadn’t come alone.
“Romanoff, meet Jo Thornton. I think you two will be spending a lot of time together,” Tony said. You glared at him.
“That’s not my name,” you snapped before offering your real name up. Tony had a habit of calling you by the name of the main character from Twister. You preferred the nickname Twister or Twist, if for no other reason than it being the nickname of a character from Rocket Power.
“Well, you know what they say Dorothy. There’s no place like home,” Natasha said as the aircraft began making its descent. Tony had opted to pilot it, leaving you to get acquainted with Natasha. You had a feeling she was one of the people Tony was going to rope into looking after you.
You allowed yourself to relax and drift off into a light sleep, dreaming of your next chase and the thrill that came with it.
#Bucky Barnes Fanfic#bucky barnes#bucky barnes/reader#bucky barnes x reader#bucky barnes reader insert#marvel fanfic#marvel fanfiction#marvel reader insert#winter soldier fanfic#winter soldier#chaser
26 notes
·
View notes
Text
Burn it down AU // on AO3 // extras on AO3
Everyone goes to Carp Tower, only for more questions to be raised.
It became a game of sorts for Wei Wuxian to make what he appeared to believe was an outrageous demand and see if Lan Wangji would give in. Most of the time, he did. There was no harm in letting Wei Wuxian swallowing as much spice as he pleased, as long as nobody else took from his bowl (Nie Huaisang did sometimes, on a dare, and always regretted it). Lan Wangji simply had to request that the kitchens make the appropriate purchases, and paid for it from his own funds since it would have been inappropriate to use sect money for personal matters.
He was more cautious about letting Wei Wuxian drink, since his body was young and unused to it, but since Mo Xuanyu had not been a heavy drinker, Wei Wuxian easily reached his limit anyway. If he tried to push too far, Lan Wangji mercilessly took whatever alcohol they had around at that moment and poured it all in front of the Jingshi.
Other things were easier. He was only too happy to let Wei Wuxian have paper and ink, or to give him access to the library whenever he wished. It was a little sad, really, that Wei Wuxian seemed to treat these very basic things as if they were unbearable whims, though after the restrictions of Yiling, it made some sense. Still, Lan Wangji had fought his own sect and been brought near his breaking point by the discipline whips for the man he loved. A little paper was nothing.
Usually Wei Wuxian kept that game for moments when they were alone. Once or twice he slipped in front of A-Yuan who did not even notice, since he was used to asking for what he needed and getting it. It also happened once in front of Nie Huaisang who, for reasons unknown, found it impossibly funny. He grinned all the rest of that evening, while Wei Wuxian refused to meet anyone's eyes and went to bed shockingly early.
Aside from that odd evening, Lan Wangji's happiness was near perfect. Or it would have been, of not for the presence of Xue Yang hidden away in a remote corner of the Cloud Recesses, and the worry that Jin Guangyao might find his crimes had not gone unnoticed. Over a month after returning to the Cloud Recesses, they still had not figured out how they might try to steal back Nie Mingjue’s head.
That problem became all the more urgent when a letter arrived from Carp Tower, bearing invitations to Qin Su's birthday.
Lan Xichen, as soon as he opened that letter, requested that the other three join him in the Hanshi to discuss the situation. They all sat around a table as they had done many times in the past month, this time with a darker mood surrounding them at the perspective of what they might not be able to avoid any longer. The invitation, after all, was not for Lan Xichen alone. Jin Guangyao had heard that Nie Huaisang was currently in the Cloud Recesses, and asked for his presence as well. More surprisingly, Lan Wangji and A-Yuan too had received their own invitations, with a reminder that Jin Rulan and Jin Rusong would be delighted to finally meet the little boy who, in a manner, was almost a cousin to them. Qin Su was a gentle woman, but also a stubborn one who did not easily give up once she had decided on something.
This demand for A-Yuan's presence made the matter more complicated. Without it, this upcoming birthday might have been the perfect chance to enter Carp Tower and attempt to retrieve the last proof of Jin Guangyao's crime. But even without needing to say it aloud, all four men agreed that they did not like to risk A-Yuan's safety.
And yet, there was an air of deep thoughts on Nie Huaisang's face as he read the invitation again and again, and it promised nothing good.
“What if…” Nie Huaisang started, only to interrupt himself to look up at Lan Xichen who, after some hesitation, sighed and nodded. Nie Huaisang too sighed, as if the encouragement displeased him, and resumed. “What if we took the invitation? All of us, Wei Wuxian passing for a servant and… and A-Yuan too.”
Lan Wangji tensed, but said nothing.
“It would give us a good excuse to go there a few days before the other guests arrive,” Nie Huaisang explained quickly, sensing that his idea was unpleasant to everyone. “Xichen will be there to help Jin Guangyao, it’s nothing out of the ordinary at this point. I’ll help Qin Su watch over the children as they play together. And so will you, Wangji, at least officially. In truth, the first chance we get of having both Qin Su and Jin Guangyao properly distracted, you and Wei Wuxian can make your way into the Fragrant Palace and see if you can figure out the secret of that mirror.”
“It is risky,” Lan Wangji noted.
“Not so much, not with your reputation and Wei Wuxian's capacity to improvise a story. We do have other proof anyway, if it really comes to that, but we can’t lose more time, sooner or later Jin Guangyao will hear about Xue Yang, or Xue Yang himself will try to escape, and…”
“It is risky to bring A-Yuan into Carp Tower,” Lan Wangji corrected.
To his credit Nie Huaisang immediately nodded, glancing again toward Lan Xichen who placed a hand on his shoulder.
“That’s why I’d stay with Qin Su and the children, why Xichen would be trailing Jin Guangyao,” Nie Huaisang insisted. “I don’t want anything to happen to A-Yuan either. And if… if you refuse, I’ll understand. If you refuse, you’ll have to stay here with A-Yuan, we’ll find an excuse, say he’s unwell. It’d be too odd for you to take the invitation yet refuse to bring A-Yuan, Jin Guangyao would see it as an insult and pay too close attention to us. But I think Wei Wuxian should come either way, he’s good at figuring out how things work, if anyone can find a way to Jin Guangyao’s secret room, it’s him. You have to choose, Wangji.”
It was a cruel choice to force upon him, although at least Nie Huaisang had the kindness not to say it out loud: Lan Wangji could either keep his son away from Jin Guangyao, or he could be at Wei Wuxian’s side when he entered the house of his enemies.
“Nie xiong, are you any better at fighting than you were as a boy?” Wei Wuxian asked bluntly. “Because unless you have improved a lot in the last few years, you saying you’ll protect A-Yuan isn’t as reassuring as you think.”
Nie Huaisang pouted, which was an answer in itself.
“Nobody would dare touch A-Yuan without a direct order from Jin Guangyao, knowing he is kin to me,” Lan Xichen pointed out with great calm, “and I will not leave him for a moment. I will kill him the instant he threatens my nephew, be certain of this.”
This much Lan Wangji believed easily, just as he was certain that Nie Huaisang would throw himself between A-Yuan and danger without hesitation, even if it should cost him his life. All four of them adored that little boy, all four would do anything to keep him safe.
Lan Wangji still felt like a monster when he gave in and agreed to take A-Yuan to Lanling.
-
However the adults felt about going to Carp Tower, A-Yuan was delighted to be included in this trip. He was impossibly excited to start packing, and asked many questions about Jin Rusong and Jin Rulan. He was a little disappointed to hear that they were younger than him, but still seemed happy at the perspective of making new friends and visiting a new place.
The only thing that came to dampen his enthusiasm was when the adults had to explain that he would have to pretend not to be close to ‘Mo Xuanyu’ while they would be there.
“Mo gongzi will come with us, but we’re going to say he is working for me,” Nie Huaisang explained. “There are people in Carp Tower who do not like him, but we really, really don’t want to leave him alone here, so we are going to say he works for me and call him by a different name.”
“That’s a lie!”
“Yes, but it’s just for this once. It’s important, it’s very important. It has to be a secret, A-Yuan. You think you can keep the secret with us?”
“Like when I dreamed of…” he glanced toward Lan Wangji, and his voice lowered to a murmur. “The dreams of fire and the other gege?”
While Nie Huaisang nodded solemnly, Lan Wangji felt the air knocked out of him at the idea that his son and his friend had been keeping secrets from him. He could easily guess what sort of dreams would have involved fire and an unknown man, and he’d always known that A-Yuan suffered from intense nightmares for the first few years of his stay in the Cloud Recesses. But it was odd and unpleasant to think that his son might have trusted Nie Huaisang with this rather than him.
At least, when A-Yuan promised to keep this secret, Lan Wangji knew that his son could be trusted. After all, he had never once suspected that the child had any memory left of his time in Yiling.
-
It was rather awkward to arrive in Carp Tower and be greeted so warmly by Jin Guangyao and his wife, knowing they had come here for the express purpose of causing his downfall. The man seemed genuinely happy to see them, and expressed sincere concern when Nie Huaisang explained that he had come with a doctor he had hired after some health concerns in recent months.
“You do seem much better than you had been lately,” Jin Guangyao agreed, inviting them to follow him as he personally guided them to their rooms, his wife following at his side. “I thought it was only the pressure of ruling still affecting you, was there something else?”
“There was an issue with his Qi circulation,” Wei Wuxian said in a forcefully gruff voice. “He was getting close to a deviation. We’re getting that under control.”
Jin Guangyao glanced at him with a blank, polite smile. It was obvious that he was curious about this short man whose face was half hidden by bandages, but Nie Huaisang had come up with a story that his personal healer had been disfigured by an illness when he was too young to cultivate, and chose to hide. Most cultivators were uncomfortable with scars, since they were rare for them, and so it was not too outlandish that a person would rather keep them away from sight.
“Well, I’m glad to hear this,” Jin Guangyao said. “Although I wish you had told me, Huaisang. We have many healers attached to our sect, I could have found you someone from the start.”
“But I already trouble San-Ge so much!” Nie Huaisang mumbled, his voice trembling slightly. “I always trouble everyone, if I keep asking for help, one day it’ll be too much and you’ll be tired of helping and you’ll all drop me.”
Jin Guangyao frowned. “Huaisang, that”s…”
“We won’t!” A-Yuan exclaimed, grabbing Nie Huaisang’s leg and hugging it tight. “We all love you, Nie-Ge! If you’re unwell, please tell us.”
The adults around him fell into silence at this outburst. Nie Huaisang looked particularly awkward, as if unsure whether to continue his act or comfort A-Yuan by telling him he did not actually fear being abandoned.
Standing next to her husband, Qin Su was the first to recover, smiling warmly at the child.
“Sect Leader Nie, what a delightful little boy you have,” she said. “You and Hanguang-Jun have done a great job raising such a filial son, you can be proud. I hope my son and nephew grow to be this good as well. I cannot wait for them to meet you, I’m sure the three of you will be great friends.”
“I’m very happy to meet them too,” A-Yuan politely replied, still firmly hugging his step-father’s leg. “I hope we all get along. When am I going to play with them?”
Qin Su exchanged a look with her husband, the two of them having a silent conversation before she smiled again.
“I think you and your family might want to rest a little and change after the trip,” she told A-Yuan. “Then we can all have lunch together. You will meet A-Xiao and A-Ling at that moment, and then you can play together after eating. Would that please you?”
A-Yuan nodded enthusiastically, and with some probing, finally let go of Nie Huaisang. After that it was a short trip to the rooms where they would be staying. Once there, Lan Xichen quickly changed into clean robes, washed his face from the dust of travelling, and headed out again immediately to see how he could help Jin Guangyao with organising his wife’s birthday party. He did not seem particularly happy with the perspective of being alone in his sworn brother’s company, but by his own admission, it would have been odd if he didn’t behave in this exact way. Before he left, Nie Huaisang took his hand and squeezed it in a comforting gesture, the only one they could allow themselves in front of others.
Once Lan Xichen was gone, the three remaining adults also got changed into more suitable clothes and helped A-Yuan do the same. It was then only a matter of sitting around and resting a little until the call for lunch came. Rest, however, was maybe asking too much. A-Yuan was too excited about the idea of meeting potential new friends, and the grown-ups were too nervous about their plan, so none of them really relaxed. It was a relief when at last, a servant came to tell them that lunch was ready to be served.
Whatever other misgivings he had about the situation, Lan Wangji had to admit that the encounter between the three children went well. A-Yuan, as could be expected of him, was the perfect image of politeness as he bowed before the other two, and his radiant smile appeared to daze them.
“I am Lan Yuan,” he announced. “And my courtesy name is Lan Sizhui. It is a pleasure to meet you both.”
Jin Rusong, who was still young and clearly a little shy, could only stare in apparent awe, half hiding behind his cousin. It could have quickly become a little awkward, but Jin Rulan was thankfully a bolder child and had no problem taking over the introductions for their side.
“I’m Jin Ling,” he stated. “And this is Jin Xiao, courtesy name Jin Rusong. We’re very happy to meet you.”
“What’s your courtesy name?” A-Yuan asked.
“I don’t like it,” Jin Rulan exclaimed, “so nobody can use it.”
“A-Ling, we’ve talked about this,” Jin Guangyao intervened with an awkward chuckle. “You have to tell people your courtesy name. It is not proper to force everyone to call you by your personal name.”
Jin Rulan crossed his arms on his chest. “Uncle Jiang says it’s ok. He says my courtesy name is stupid and I don’t have to use it.”
Jin Guangyao looked positively horrified by that statement, but not surprised, so Lan Wangji guessed it was not the first time they were having this argument. Of course, with Jin Rulan often being sent to spend time in the Lotus Piers, it was unavoidable that the child’s personality would be tainted by his other uncle.
“Well, I don’t mind calling you Jin Ling,” A-Yuan said. “It’s pretty. Are we going to sit all together?” He turned to his father. “Am I allowed to speak during meals here?”
“Quietly,” Lan Wangji agreed, knowing it would be hard to enforce that rule away from home and in the presence of other children who had no reason to be silent.
The meal went well, as far Lan Wangji was concerned. He was not asked to speak much, unlike Lan Xichen who found himself in deep conversation with Jin Guangyao, and Nie Huaisang who happily chatted with Qin Su about a number of inconsequential subjects. Lan Wangji, for his part, found himself exchanging many glances with Wei Wuxian who appeared deeply amused by the situation and clearly struggled not to make any comments. It said a lot about his dedication to helping that he remained silent, actually. That, or he feared that Lan Wangji would simply silence him if he said anything.
After lunch, Jin Guangyao and Lan Xichen quickly excused themselves again and disappeared together. Qin Su offered that the rest of them go in the gardens so the children could play freely, and the idea was of course accepted. They all settled in a pretty corner of the vast gardens, not far from the main buildings so that servants and attendants could still easily find their mistress and ask for her input on this and that detail for the upcoming party. Nie Huaisang sat near her and happily gave his opinion here and there, as long as it was not on anything more important than floral arrangements or who could be trusted to sit near sect leader Yao and not murder him out of annoyance. Meanwhile the three children, after some initial hesitation over what games to play, were running around together quite happily.
After a while of simply being there, silent and steadfast, Lan Wangji rose from the bench on which Wei Wuxian and him were seated, and announced that he was going to retire for some meditation. Qin Su looked a little sorry, possibly because she took it as a slight against her skills as a hostess, but she did not try to stop him. It was quite well known that Lan Wangji was not a very sociable person, and hopefully she understood he had already made an effort by staying this long.
“I’ll come with you,” Wei Wuxian announced, still disguising his voice. “I have to prepare some remedies for sect leader Nie.” He bowed before Qin Su. “Madam Jin, I leave my patient in your hands.”
“And I’ll make sure he behaves,” she amiably replied. “Won’t you, sect leader Nie?”
“I’ll do my best,” Nie Huaisang laughed.
Acting satisfied with that promise, Wei Wuxian also stood up and followed Lan Wangji away from the gardens.
It would have been easy to get lost in a place like Carp Tower. Thankfully, before coming, Lan Xichen and Nie Huaisang had drawn for them a rough map of the place, which Wei Wuxian had easily memorised. They started by heading out in direction of their room to avoid raising suspicion, but at the first opportunity they took a turn toward Jin Guangyao’s private residence.
Of course as soon as it was safe to do so, Wei Wuxian started chatting. Considering how long he had managed to stay quiet, Lan Wangji could not begrudge him this. Still, he wished a different subject might have been picked.
“Really, Sizhui?" Wei Wuxian teased. “What sort of a name is that? Did you let Nie-xiong pick that name, for it to be so dramatic?”
“I chose it,” Lan Wangji confessed, a little embarrassed. In truth, Nie Huaisang too had teased him for naming his son “to recollect and long for”, and even Lan Xichen had raised an eyebrow at it. His only defence was that he had been asked to find a courtesy name soon after the engagement had been announced, when he had only just been given A-Yuan back, so that he could be put on the official registry, and… he had not been in a very good emotional state at the time, both aching over Wei Wuxian’s death and fearing a marriage forced upon him.
Without surprise, Wei Wuxian laughed at the admission.
“Lan Zhan, you’re really too much sometimes. Poor child, did you want him so badly to someday remember where he came from?”
Lan Wangji only hummed in answer.
If Wei Wuxian wanted to believe that, he was not going to say otherwise. If the name Sizhui had been embarrassing when he had thought Wei Wuxian lost to him for ever, then it was simply shameful now that the man was back with them. Lan Wangji had tried to live without regrets since losing the man he loved, but this dramatic name might be one of the few he had.
It was a relief when they arrived near the Fragrant Palace and had to be quiet again.
The entrance was guarded of course, but it wasn’t hard to simply enter through the gardens. Clearly, the sect leaders of Lanling Jin felt confident that nobody would reach them this far inside their sect. Once inside, they had to avoid being seen by the occasional servant, but thankfully most of the staff was busy with preparations for the party. In the end, it was easy enough to find Jin Guangyao’s bedroom.
It was easy, as well, to find the copper mirror. Xue Yang had told them it was huge and ostentatious. He hadn’t lied: the mirror was a little taller than Lan Wangji, and large enough that both of them could easily stand in front of it with room to spare. Even if it had just been a mirror it would have been worth a fortune, exactly the sort of luxurious display one might have expected from the sect leaders of Lanling Jin.
Wei Wuxian got to work. Before all else, he checked for any sort of safety measures protecting the mirror, but found none. However that secret passage worked, Jin Guangyao appeared to have full trust in it being unbreachable. A trust that wasn’t unjustified because no matter what Wei Wuxian tried, he simply could not get the passage to open.
“There’s something though,” he grumbled after another failed attempt. “I can feel it. I need to think, what could be so infallible?”
Given enough time, Lan Wangji was convinced Wei Wuxian would figure it out. But time was not an endless resource, and it was getting late. They would soon need to make their exit and regroup with the others. Hopefully they would get other chances in the coming days, but it was disheartening that a solution hadn’t been found yet.
“It’s reacting to something,” Wei Wuxian muttered, kneeling in front of the mirror and pressing his hands against the surface to better feel whatever magic powered it. They would need to clean it before they left, Lan Wangji realised. “Maybe I’m not powerful enough? This body is so weak… Lan Zhan, come closer please, I want to try something.”
Lan Wangji dutiful obeyed, and following the other man’s instructions, pressed his hands against the mirror’s surface.
“Do you feel it?” Wei Wuxian asked. “It’s like a buzzing in my hands.”
“I feel nothing.”
“Really? That’s odd. I wonder…”
“What’s going on here?” asked a voice behind them.
Both men startled and turned to look at Qin Su who gaped at the sight of two strangers in her private apartments. She seemed too shocked to cry out for someone to help, but that wouldn’t last and Lan Wangji steeled himself to use the Lan silencing spell on her. From this there would be no going back. But in truth, just from having been found there, they could not back down. They needed to go inside that passage that very day, or risk giving Jin Guangyao a chance to get rid of evidence.
“Madam Jin, we have a perfectly legitimate reason to be here!” Wei Wuxian exclaimed. “Please don’t create trouble, we aren’t here to harm you!”
“Your voice is… just who are you?” she retorted. “Does sect leader Nie know about this?”
The second question was directed more at Lan Wangji who hesitated on how to answer. Lying would be wrong. Saying the truth could only be used a last resort. Stuck between two unpleasant options, he elected to simply ignore the question.
“We are currently investigating serious accusations that have been made against Lanling Jin,” he explained. “Although it is distasteful to act in shadows, the accusations are such that we could not bring them to light without proof. We believe such proof can be found in the room behind the mirror.”
Qin Su startled. “You know about that room? Who told you?”
“Considering the circumstances, Madam Jin will understand we can’t give that name,” Wei Wuxian replied. “Isn’t the fact we know there’s such a room enough to show that we aren’t here at random? And since we know about it, perhaps Madam Jin might let us know how to open it?”
“Only my husband can.”
“It is important,” Lan Wangji insisted. “We would not be here if there was another choice.”
Qin Su smiled weakly at him.
“Hanguang-Jun, you misunderstand me,” she sighed. “When I say only my husband can open this passage, I mean it. This mirror is built in such a way that it will only react to a direct descendant of its creator, who was a previous Jin sect leader.”
"Well, that's inconvenient," Wei Wuxian grumbled. "Is there really no other way…"
"My husband once told me that even Xue Chengmei could not trick the mirror when Jin Guangshan offered him the chance to try," Qin Su explained, her smiling growing a little more confident. "Seeing as breaking and remaking artefacts was his speciality, I feel it is safe to say the mirror's magic is quite secure."
Calling this inconvenient did not even begin to cover it. Lan Wangji had no illusions about Jin Guangyao’s willingness to allow them inside. To have come so close only to fail…
"Madam Jin, aside from this, do you know how to get the passage open?" Wei Wuxian abruptly asked.
"I have seen my husband do it."
"Perfect. Then show us, please."
"I've told you…"
"Yes, yes, but… Madam Jin, you are aware that your father-in-law had many children out of wedlock, aren’t you? I happen to be one of them. And if your husband can open it, then clearly the mirror doesn't care about legitimacy, only about blood."
Qin Su paled at the reminder, her lips pinched in distaste as she tried to look through the bandages hiding Wei Wuxian's face. Lan Wangji had heard it said that, mild and even tempered as she was, Qin Su did not tolerate anyone trying to speak in her presence about her husband’s origins. She had fought her own parents about it, and it was the one issue on which she was willing to get angry.
"I suppose that's true,” she conceded, “but still…"
"We do not ask lightly," Lan Wangji intervened. "If the situation were not so dire, we would not be here. If we are wrong, we will accept the consequences, but certain things must be verified."
Qin Su did not look particularly impressed with that statement. Although Lan Wangji's reputation had somewhat recovered from his actions in Nightless City, it would take a while longer for people to forget he had chosen to side with Wei Wuxian that day. That he would associate himself with one of Jin Guangshan’s bastards, none of whom had ever been judged worthy of remaining in Carp Tower, could not help.
"Very well," Qin Su sighed. "For your brother's sake, because I know Zewu-Jun would not allow injustice to be carried out. But I will come inside with you. I hope you understand."
Lan Wangji nodded, while Wei Wuxian bowed. It was already more than they would have expected. Lan Wangji wondered if perhaps the young woman was curious about this secret passage inside her home. Even this easy going woman would have had to wonder about something so mysterious.
“Move back,” she ordered, before she placed her hands on a specific spot on the mirror's frame. “Here, there is this notch here where you must press while sending an impulse of energy.”
Committed to the task, she demonstrated the movement and the impulse while Wei Wuxian watched like a hawk, obviously fascinated by the process. When everything was over and they were freed from this investigation, Lan Wangji was sure the other man would try to recreate this technique.
“And that’s it,” Qin Su concluded. “Of course, as I’ve said, only a descendant of that Jin sect leader may do it. For anyone else, it won’t work. I suppose you’re about to see if you truly are of Jin Guangshan’s blood. Otherwise…”
To show what would happen if Mo Xuanyu’s blood wasn’t enough, Qin Su brought her hand to the mirror’s surface, ready to lean against it.
She nearly lost her balance as her hand went right through and cried out in shock, only barely managing to grip the mirror’s edge before she could fall through the passage.
30 notes
·
View notes
Text
Wanting the 'best of both worlds' is a concept which has made me who I am. Pursuing this ideology, creates a lot of difficulties.
Technology: I know a guy that relies solely on Apple technology. He has the Airport router at home and an iMac, he always gets the newest iPhone for his wife and himself. He has a computer programming degree. Because he remains within that family, he is completely content and stays true to Apple.
I have another good friend that I first met as our help desk support guy at work. Best IT support guy I ever knew. He has all of his MS Office certificates. He could get on your device remotely with the Dame software and fix just about any problem you might have with any MS Office, Active Directory or Accessibility issue that you might have within minutes. He was the frontline support for a company of 3000+ coworkers.
I have always been a fan and had a need to use/work with both of these product families. I recognise, however; that Sony (android) has always been the leader in portable technology. Somewhere in the past few years, I switched from the iPhone to the Sony Xperia as my preferred cell phone around 2005. This from time to time presents problems. There are formatting issues working between the families. To add to those issues, in my professional life; I had worked most heavily with Microsoft products up until about 2012. At which point, I had become impressed with the portability of Google Docs (cloud computing). So now cloud computing is 'all the rage'. I had a recent job interview where I had to put together a PowerPoint presentation. So, I renewed my MS Office 365 subscription and with that, I got a TB of cloud storage in the MS OneDrive. I have an external hard drive (500 GB) with all of my cherished family memories that is a bit old and beat up. So, I decided to put all of that stuff (movies/music/pictures/personal documents) in the cloud.
During this COVID-19 Lockdown period; I have been doing my best to organize all of my personal data as well as position myself to get a job which uses all of my people skills, financial, marketing and administrative skills as well as helps me to pull all of my IT experience together. I still have a long way to go. I haven't even begun editing the stockpiles of videos that I have. My 10 year old daughter is getting good at editing Tiktok videos. Which is, in itself a very interesting platform. Instagram was becoming a marketing powerhouse but now many companies are switching their business to Tiktok. My son is 16 and I want to advise him on what direction he should take in order to harness his full capabilities. He is also very tech savvy and I believe gifted in his understanding of technology.
10 notes
·
View notes
Text
Can we earn money from CryptoTab Browser?
📷
CryptoTab Browser Review: Is CryptoTab Legit?
CryptoTab browser is a legit form of business.
It is the world’s first online browser that mines Bitcoins.
Earning with the CryptoTab browser is possible via the BTC mining & referral program.
Online community warns of the CryptoTab browser virus.
CryptoTab is an internet browser with a built-in mining function. “With CryptoTab you earn cryptocurrency just by visiting your favorite sites, watching videos, and chatting online”, claims the official website.
The idea sounds beautiful and exciting. But isn’t it too good to be true? Is CryptoTab legit or is CryptoTab a scam? Dexterous-World takes the challenge and explores the promising browser. Follow this CryptoTab browser review to know more about its usage, pros & cons, and, finally, is CryptoTab worth all the efforts?
What is CryptoTab?
CryptoTab is the world’s first browser, created specifically for mining Bitcoins. It has a built-in mining algorithm, that allows users to earn Bitcoins when web-surfing, watching movies or doing any other activity online.
Besides that CryptoTab acts as a referral program. This means the browser offers to earn Bitcoins for promoting CryptoTab on social media and inviting friends to join it. Launched as an extension a few years ago, CryptoTab already has over 10 million users for the time of publishing.
So, let’s have a look at how it works, and how could you earn with the CryptoTab browser?
CryptoTab browser mining
Despite payments in Bitcoins, the CryptoTab browser does not mine Bitcoin directly. Indeed it’s software mines Monero (XMR) privacy coins and converts them later to Bitcoin at the current exchange rate. This means why Bitcoins are the only currency displayed in user balances. The website though plans to add additional digital currencies someday in the future.
Meanwhile, if you are familiar with Monero mining, you know that XMR is only mined by using a Proof of Work (PoW) algorithm called CryptoNight. This algorithm requires access to devices’ memory and to increase in latency dependence. This allows CryptoNight to resist powerful mining hardware like ASIC and offer equal possibilities for all the miners.
As it is known, each new Monero block is minted every 2.01 minutes and offers around 1.4 XMR coins as a reward at the time of writing.
According to CryptoTab, its mining algorithm uses only the unused computer resources and does not interfere with normal computer usage. This suggests that mining on a browser does not slow down the device.
How do you use CryptoTab?
Basically, there are two ways to earn Bitcoins with the CryptoTab. The first includes mining via the browser. The second involves affiliate marketing and offers rewards for referring new users.
Speaking of cryptocurrency mining, CryptoTab supports browser mining both for Windows and Mac OS. CryptoTab Browser is available as well for Android and iOS devices.
Let’s quickly run through the step-by-step instructions of how to mine Bitcoins via the CryptoTab browser.
How to mine with CryptoTab on Windows and Mac OS
Download the CryptoTab browser installation file from the official website. Click here to Download.
Install it. Run the setup file, complete, and confirm the installation.
Start the CryptoTab browser. You can make it a default browser and add a shortcut to your taskbar for more convenient usage.
Set up the account. Open Settings in the drop-down menu on the right side. You may use your Google account or social media account to log in. This will help you to make sure no data will be lost if you reinstall the browser or log in by using other devices.
Activate mining. Open the CryptoTab browser, click the CryptoTab icon in the right upper corner, turn the mining mode On, adjust your mining speed.
Since you have installed the browser, activated the mining mode, and adjusted the mining speed, you will be mining digital coins anytime when the CryptoTab browser is open.
How to mine with CryptoTab on Android and iOS
Download the CryptoTab app from Google Play or App Store. You may choose among the free Basic option and paid Pro option ($1.19 on Google Play, $1.99 on Apple Store). The Pro version is more advanced and includes multiplied speed mining, server-dependent mining that does not drain the battery, an unlimited number of connected remote devices, and other features.
Click here to Download the Pro version APK for free.
Install the CryptoTab app.
Set up the account. Open the CryptoTab app to set up an account. You may use Google or social media to log in.
Activate mining. Turn on the mining mode and adjust your mining speed.
NOTE: DOWNLOAD THE DESKTOP VERSION FIRST AND SIGN UP WITH YOUR GOOGLE ACCOUNT.
AFTER THAT YOU CAN DOWNLAOD THE MOBILE VERSION AND DOWNLAOD THE APK FROM MY GIVEN LINK.
CryptoTab referral program
In addition to cryptocurrency mining, the CryptoTab browser allows earning Bitcoins via its referral program. Referral programs offer a reward for sending new customers. This means users may benefit from promoting CryptoTab and inviting their friends to it.
The CryptoTab referral program works as an ordinary affiliate marketing scheme. It offers a 10-level earnings pyramid, which means the more affiliates you have, the higher commissions you get.
The principle of a referral program is simple. Imagine, you invite one friend to start mining with a CryptoTab browser. CryptoTab then gives you 15% of the Bitcoins that your friend has mined. If your friend persuades his friend to use CryptoTab, you get another 10% from your 2nd level affiliate. And when that friend invites his acquaintances, the process goes on and on and on to the level 10.
The main way to catch new users comes from actively promoting on social media. CryptoTab even provides the free branded material to make your post more compelling.
Moreover, it encourages buying traffic to boost earnings from mining. This is a highly risky activity, especially for the new ones. Have in mind that the return of investment might not be significant and only come in the form of Satoshi, which is the 100 millionth part of a Bitcoin.
Is it possible to earn with CryptoTab?
Following the quick online search, CryptoTab user experiences are different. Some of them claim they struggle to earn above $15 to $25 per month. Others share earnings of over $69 (time period not specified), most probably generated from the referrals, that included over 5211 other miners.
Despite the fact that the referral program plays an important role in generating a higher profit on CryptoTab, the mining speed is also important. CryptoTab allows users to choose the mining speed option. Although keep in mind, that mining at the maximum speed may affect the device by slowing down its performance and making it heat up.
In order to withdraw your earnings from CryptoTab accounts, you first need to have your own cryptocurrency wallet for Bitcoins. The minimum amount of withdrawal is 0.00001 BTC.
At the time of publishing CryptoTab provides payments manually twice a day and aims to switch into automated-mode someday. CryptoTab, however, shares the history of its users’ withdrawal transactions in the payments journal.
Is CryptoTab safe?
Is a crypto mining browser safe to use? Is CryptoTab legit? To be honest, there are various criteria to evaluate before making your own decision. And they both need your attention and consideration.
Form of business
First, CryptoTab is based on a business model that is legitimate. Officially referral programs are a legal form of business. However, there is a fine line between legal and illegal ones.
Referral programs that require financial commitment before you are involved, are considered illegal. And as far as CryptoTab doesn’t ask you to invest funds to start crypto mining, it is a legit form of business.
The team
The team behind CryptoTab is anonymous and there is little information about them online.
DailyCoin has found out that CryptoTab is developed by CryptoCompany, a private limited company based in Estonia. The only board member of the CryptoCompany and also of CryptoTab is Vadim Tuulik, the mysterious man with a scarce online history and 5 Linkedin connections.
Listing on app stores
Respectively, the CryptoTab app is available to download from Google Play and Apple Store. Apps listed on both of these stores must go through thorough tests. They have to be verified to be free from viruses and malicious software.
As you may know, both Apple and Google Play banned the cryptocurrency mining apps on their platforms back in 2018. The move was mainly based on the explanation that cryptocurrency mining apps cause battery draining, generate excessive heat, affect device resources, and finally damage the devices. Both companies only allowed crypto mining apps that mined digital assets outside of the device (e.g. cloud-based mining).
Being available on both Google and Apple platforms suggests the CryptoTab browser is safe. However, it does not guarantee CryptoTab is profitable.
Click here to Download the Pro version APK for free.(Mobile Version)
Otherwise it will charge you 0.99$.
Click here to Download the Desktop Version.
Warning of virus
On the other hand, there are warnings online of the CryptoTab browser virus. According to them, the virus may infect the computer and extract sensitive information from all the browsers on it.
The warning also claims that CryptoTab’s software may not be malicious by itself. However, lots of hacker-made versions of it are easily available on the internet (data of May 2020). They may be rebranded versions of it or direct fake copies.
The website that has announced the warning is an online blog and forum, that covers malware attacks, data breaches, and privacy-related stories. It also has no reputation for being a scam.
Pros & Cons
Pros
Free
Payment Journals
Supports Android & iOS
Supports Windows & Mac OS
Cons
Low earnings
May affect device performance
Unknown founders
Virus warning
So finally, is it worth using?
Well, it’s for you to decide. Answering the question of is CryptoTab legit, we can say yes, it is. The business model of CryptoTab is legit, but it does not mean it is profitable. The amount of earning with CryptoTab mainly depends on the number of affiliates you have in a referral program. The more you invite, the more you get back.
CryptoTab claims the browser runs on unused resources of your computer. However, users share opposite opinions and blame crypto-mining apps for affecting the performance of their devices. Besides that, you need to be extra cautious of not infecting your computer with infected options of the mining browser.
So in summary, what our recommendations will be? Try it if you think small earnings will be enough. But better stay cautious and first experiment not on your best devices.
#cryptocurrency#cryptotab#how to make money online#earn online#work from home#bitcoin mining#earn bitcoin#no investment
3 notes
·
View notes
Text
12 Terminal Commands
Every Web Developer Should Know
The terminal is one of the foremost vital productivity tools in a developer's arsenal. Mastering it will have an awfully positive impact on your work flow, as several everyday tasks get reduced to writing a straightforward command and striking Enter. In this article we've ready for you a set of UNIX system commands that may assist you get the foremost out of your terminal. a number of them square measure inbuilt, others square measure free tools that square measure reliable and may be put in but a moment.
Curl
Curl may be a program line tool for creating requests over HTTP(s), FTP and dozens of different protocols you will haven't detected concerning. It will transfer files, check response headers, and freely access remote information.
In net development curl is usually used for testing connections and dealing with RESTful APIs.
# Fetch the headers of a URL. curl -I http://google.com HTTP/1.1 302 Found Cache-Control: private Content-Type: text/html; charset=UTF-8 Referrer-Policy: no-referrer Location: http://www.google.com/?gfe_rd=cr&ei=0fCKWe6HCZTd8AfCoIWYBQ Content-Length: 258 Date: Wed, 09 Aug 2017 11:24:01 GMT # Make a GET request to a remote API. curl http://numbersapi.com/random/trivia 29 is the number of days it takes Saturn to orbit the Sun.
Curl commands can get much more complicated than this. There are tons of options for controlling headers, cookies, authentication,and more.
Tree
Tree may be a little instruction utility that shows you a visible illustration of the files during a directory. It works recursively, going over every level of nesting and drawing a formatted tree of all the contents. this fashion you'll quickly skim and notice the files you're trying to find.
tree . ├── css │ ├── bootstrap.css │ ├── bootstrap.min.css ├── fonts │ ├── glyphicons-halflings-regular.eot │ ├── glyphicons-halflings-regular.svg │ ├── glyphicons-halflings-regular.ttf │ ├── glyphicons-halflings-regular.woff │ └── glyphicons-halflings-regular.woff2 └── js ├── bootstrap.js └── bootstrap.min.js
There is also the option to filter the results using a simple regEx-like pattern:
tree -P '*.min.*' . ├── css │ ├── bootstrap.min.css ├── fonts └── js └── bootstrap.min.js
Tmux
According to its Wiki, Tmux may be a terminal electronic device, that translated in human language would mean that it is a tool for connecting multiple terminals to one terminal session.
It helps you to switch between programs in one terminal, add split screen panes, and connect multiple terminals to a similar session, keeping them in adjust. Tmux is particularly helpful once functioning on a far off server, because it helps you to produce new tabs while not having to log in once more.
Disk usage - du
The du command generates reports on the area usage of files and directories. it's terribly straightforward to use and may work recursively, rummaging every directory and returning the individual size of each file. A common use case for du is once one in every of your drives is running out of area and you do not understand why. Victimization this command you'll be able to quickly see what proportion storage every folder is taking, therefore finding the most important memory saver.
# Running this will show the space usage of each folder in the current directory. # The -h option makes the report easier to read. # -s prevents recursiveness and shows the total size of a folder. # The star wildcard (*) will run du on each file/folder in current directory. du -sh * 1.2G Desktop 4.0K Documents 40G Downloads 4.0K Music 4.9M Pictures 844K Public 4.0K Templates 6.9M Videos
There is also a similar command called
df
(Disk Free) which returns various information about the available disk space (the opposite of du).
Git
Git is far and away the foremost standard version system immediately. It’s one among the shaping tools of contemporary internet dev and that we simply could not leave it out of our list. There area unit many third-party apps and tools on the market however most of the people choose to access unpleasant person natively although the terminal. The unpleasant person CLI is basically powerful and might handle even the foremost tangled project history.
Tar
Tar is the default Unix tool for working with file archives. It allows you to quickly bundle multiple files into one package, making it easier to store and move them later on.
tar -cf archive.tar file1 file2 file3
Using the -x option it can also extract existing .tar archives.
tar -xf archive.tar
Note that almost all alternative formats like .zip and .rar can't be opened by tar and need alternative command utilities like unfasten.
Many trendy operating system systems run associate expanded version of tar (GNU tar) that may additionally perform file size compression:
# Create compressed gzip archive. tar -czf file.tar.gz inputfile1 inputfile2 # Extract .gz archive. tar -xzf file.tar.gz
If your OS doesn't have that version of tar, you can use
gzip
,
zcat
or
compress
to reduce the size of file archives.
md5sum
Unix has many inbuilt hashing commands together with
md5sum
,
sha1sum
and others. These program line tools have varied applications in programming, however most significantly they'll be used for checking the integrity of files. For example, if you've got downloaded associate degree .iso file from associate degree untrusted supply, there's some likelihood that the file contains harmful scripts. To form positive the .iso is safe, you'll generate associate degree md5 or alternative hash from it.
md5sum ubuntu-16.04.3-desktop-amd64.iso 0d9fe8e1ea408a5895cbbe3431989295 ubuntu-16.04.3-desktop-amd64.iso
You can then compare the generated string to the one provided from the first author (e.g. UbuntuHashes).
Htop
Htop could be a a lot of powerful different to the intrinsic prime task manager. It provides a complicated interface with several choices for observation and dominant system processes.
Although it runs within the terminal, htop has excellent support for mouse controls. This makes it a lot of easier to navigate the menus, choose processes, and organize the tasks thought sorting and filtering.
Ln
Links in UNIX operating system square measure the same as shortcuts in Windows, permitting you to urge fast access to bound files. Links square measure created via the ln command and might be 2 types: arduous or symbolic. Every kind has totally different properties and is employed for various things (read more).
Here is associate example of 1 of the various ways that you'll be able to use links. as an instance we've a directory on our desktop referred to as Scripts. It contains showing neatness organized bash scripts that we have a tendency to ordinarily use. on every occasion we wish to decision one in every of our scripts we'd need to do this:
~/Desktop/Scripts/git-scripts/git-cleanup
Obviously, this is isn't very convinient as we have to write the absolute path every time. Instead we can create a symlink from our Scripts folder to /usr/local/bin, which will make the scripts executable from all directories.
sudo ln -s ~/Desktop/Scripts/git-scripts/git-cleanup /usr/local/bin/
With the created symlink we can now call our script by simply writing its name in any opened terminal.
git-cleanup
SSH
With the ssh command users will quickly hook up with a foreign host and log into its UNIX operating system shell. This makes it doable to handily issue commands on the server directly from your native machine's terminal.
To establish a association you just got to specify the proper science address or URL. The primary time you hook up with a replacement server there'll be some style of authentication.
ssh username@remote_host
If you want to quickly execute a command on the server without logging in, you can simply add a command after the url. The command will run on the server and the result from it will be returned.
ssh username@remote_host ls /var/www some-website.com some-other-website.com
There is a lot you can do with SSH like creating proxies and tunnels, securing your connection with private keys, transferring files and more.
Grep
Grep is the standard Unix utility for finding strings inside text. It takes an input in the form of a file or direct stream, runs its content through a regular expression, and returns all the matching lines.
This command comes in handy once operating with massive files that require to be filtered. Below we tend to use grep together with the date command to look through an oversized log file and generate a brand new file containing solely errors from nowadays.
// Search for today's date (in format yyyy-mm-dd) and write the results to a new file. grep "$(date +"%Y-%m-%d")" all-errors-ever.log > today-errors.log
Another nice command for operating with strings is
sed
. It’s additional powerful (and additional complicated) than grep and may perform nearly any string-related task together with adding, removing or replacement strings.
Alias
Many OS commands, together with some featured during this article, tend to urge pretty long when you add all the choices to them. to create them easier to recollect, you'll produce short aliases with the alias bash inbuilt command:
# Create an alias for starting a local web server. alias server="python -m SimpleHTTPServer 9000" # Instead of typing the whole command simply use the alias. server Serving HTTP on 0.0.0.0 port 9000 ...
The alias are offered as long as you retain that terminal open. to create it permanent you'll add the alias command to your .bashrc file. We will be happy to answer your questions on designing, developing, and deploying comprehensive enterprise web, mobile apps and customized software solutions that best fit your organization needs.
As a reputed Software Solutions Developer we have expertise in providing dedicated remote and outsourced technical resources for software services at very nominal cost. Besides experts in full stacks We also build web solutions, mobile apps and work on system integration, performance enhancement, cloud migrations and big data analytics. Don’t hesitate to
get in touch with us!
1 note
·
View note