#Crack Administrator Password
Explore tagged Tumblr posts
Text
Sicktember 2024 Day 9 - [ALT] Hospital Bed
Larry and Geetaaaa.
CW for emeto. (Non-graphic)
Larry had not dressed for the occasion.
Gone was the cheap black suit and tacky tie, gone were the scuffed loafers and inexplicably tailored slacks.
Geeta surveyed his jeans and the nondescript hoodie revealing at least two inches of his neck that she'd never seen before. “Larry. Dressed to impress I see.” Her keys jingled in her hand as she turned away to unlock the League door.
“After hours work means after hours Larry,” he said, his voice dull.
Geeta pushed the door open with her shoulder and strode down the hall, pocketing her keys as she went. Always the bare minimum with him, always the attitude that she'd asked him to walk to his death.
His footsteps shuffled against the linoleum, his sneakers no doubt leaving long black streaks for the custodian to clean up. Her own shoes announced her presence with a steady click-clack, not that there was anyone here to receive them.
When she reached the bullpen, she went straight for Poppy's desk— no point holing up in her office and leaving Larry unsupervised. She logged in to the Paldea Board website and her email account, reset her own password, reset Larry's and gave him administrator privileges… Then, and only then, did he shuffle in, his head low. Like he'd deliberately made her wait for him.
Geeta sighed and adjusted Poppy's pencil holder. “Pull up a chair,” she said evenly. No reaction was the best reaction.
Larry didn't say anything, but he walked with infuriating slowness to his own cubicle and grabbed his desk chair. The wheels rattled with the movement. He pulled it awkwardly, one-handed, with the other hidden in his hoodie pocket.
“We need to have this done by tomorrow morning,” Geeta said, studying him.
He wouldn't look at her. “I understand.��
Geeta walked him through the process of resetting passwords and he listened in silence. He didn't even ask why they were doing this. It spared Geeta the humiliation of having to explain that a pre-teen had hacked the LP system right under her nose. But it was always apathy, not tact, with him.
He didn't even acknowledge her as he talked, instead staring blankly through the desk with no light in his eyes but the blue glow of the monitors.
When she finished, he didn't say a word. Geeta huffed and crossed her arms. “I trust you understood all that? I noticed you didn't feel the need to take notes.” Never mind that she'd emailed him the workflow; he couldn't know that.
“Uh—” Larry shook himself like she'd startled him. “Yes. Yes.” His chest rose and fell with shallow breaths. “Excuse me.”
Geeta raised her eyebrows as she watched him go. Not 20 minutes into the evening and he was already taking breaks.
And there was nothing she could do but lead by example.
—
Larry's breaks grew more frequent as the night progressed, each with a revolving cycle of excuses: smoke break, coffee break, bathroom break, exercise break. As if he'd ever exercised a day in his life.
Through it all, Geeta kept working. Only the endless monotony of clicking and double-clicking accompanied her in the long stretches between her own breaks. Coffee and the restroom, that was all she needed. She could eat one-handed and keep working, and she did.
Through the stinging in her eyes and the pain in her wrist. The work needed to get done, so she would do it.
With or without Larry's help.
Although…
She tore her eyes away from the password reset form and checked the clock. Hadn't Larry been gone for a while?
With a sigh, Geeta planted her hands on the desk and heaved herself to her feet. Neglected muscles ached and joints cracked as she stalked down the hall to the breakroom. Yes, maybe she'd voluntold Larry about this enterprise, but if he couldn't make it through a late night of work, it was his responsibility to advocate for himself. She was his boss, not his babysitter.
Coffee-fueled resentments made her hands shake. This blatant disrespect really was getting out of hand. Larry could bemoan the state of his paycheck all he liked; it was his own fault. His own responsibility.
…Or lack thereof.
Geeta froze in the doorway of the breakroom and felt her gaze go hard.
Heedless of the bright fluorescents and the half-empty coffee mug in front of him, Larry had somehow fallen asleep with his face pressed hard into the vinyl tablecloth.
With Persian's grace, Geeta prowled into the room and promptly slammed one of the cabinet doors.
Larry jerked awake, but didn't sit up right away, nor did he say anything. He stayed curled over the table, his black hair gleaming as he shifted.
“Do you really think this is appropriate behavior?” Geeta snapped. “I wouldn't have asked for your help with this task if it wasn't important. I've been working all night, and—” He still wouldn't raise his head. “Larry! I can't tolerate this kind of disrespect from an employee. Look at me when I'm talking to you.”
At last, Larry raised himself from the table. He kept his posture hunched, stared up at her with lazy, red-rimmed eyes. “Better?”
“Are you trying to get fired?” Geeta demanded. “Nobody forced you to be here.” She buried her fingers in her hair, balled her hands into fists. “I just don't understand the reason for this level of disrespect.”
Larry remained silent, his face eerily still. His lips parted and then shut, and he stood slowly.
And walked away.
Geeta stared at the empty chair for a moment, mouth agape. Was he having a psychological breakdown? Was he trying to get fired?
“Larry!” Geeta burst out of the breakroom, tailing him as he took slow, shuffling steps down the hallway. “Don't walk away from me!”
His steps faltered. She stopped and crossed her arms. He'd better turn around. If he valued his job, he'd turn around.
Larry did turn, but only halfway. He pitched forward and his forehead hit the wall. A moment later, his arms came up to stabilize him, like his body was out of sync with itself. His back bent and he vomited onto the linoleum, eerily quiet but for the nauseating splash.
“Oh.” Geeta took a half step back, her own stomach turning. “Well…” Foolish, foolish man. “You're sick?” She advanced on him again as he sagged against the wall, threatening to collapse. “Why didn't you say anything?”
Before she could reach him, he staggered back, waving a hand to dismiss her. He sank to the floor, his face ashen, and huddled in on himself.
“I need to get you home,” Geeta said, mostly to herself, hovering over him. “And get this cleaned up… I can't just leave you sitting here.” She huffed and ran her hands through her hair, snapping pieces as she went. “Larry, why didn't you say anything? You could have spared us both—”
“Primera.” Larry's voice came hoarse, devoid of life. “Just call me an ambulance and leave me alone.”
She backed off at once, eyes widening. Well, fine. Larry could have it his way.
—
Oh, mercy.
How was anyone ever supposed to recover in a hospital?
Larry tried to raise a hand to his face and stopped dead at the pull of the IV line.
Oh. Right.
He raised his other hand to his face instead, unable to hold back a groan. Why bother, right? If there was a nurse in his room, he'd know by now.
Fabric rustled. “Larry?” someone said softly. Not a nurse
Larry opened his eyes.
White ceiling tiles greeted him, and the dim light of the morning sun choked by heavy curtains.
He turned his head. Slowly. To look.
There, with perfect posture— Geeta. She had her legs crossed, hands folded atop one knee, and she looked down at him without a hint of sentimality or concern in her eyes. Well, that was no surprise.
“What're you doing here?” Larry asked. His tongue moved slowly, sticking in his dry mouth. She hadn't been there last night, hadn't accompanied him in the ambulance, hadn't waited with him in the emergency room. “Come to apologize?”
“For what?” Geeta asked, arching an eyebrow.
Typical. Larry scoffed. Now wasn't the time for an argument, but if she started lecturing him again, he might just fake a seizure. “So what are you doing here?”
Geeta got to her feet and came closer. The proximity revealed a cold pallor to her face and dark rings under her eyes. She opened her mouth to speak and Larry interrupted her: “How long have you been here?” Her hair stuck up in the back like she'd repeatedly adjusted her posture against the back of her chair and she wore the same clothes she'd worn last night, the blazer that didn't quite fit and the shirt with the coffee stain on the collar.
“I came to see how you were doing,” Geeta said coolly. Almost half heartedly, she added, “And when you can return to work.”
“If you were worried about me, you can just say.” The notion spread an odd sensation through Larry's chest and stomach— not joy, but not quite discomfort, either
Geeta made for the door. “I knew the hospital would take adequate care of you,” she said.
“Right.” She was really leaving. “I appreciate the concern.” She hadn't even brought flowers.
In the doorway, Geeta paused. She looked at him briefly, then away. “I am glad you're alright,” she said. “And I hope you feel better soon.” And she vanished, her footsteps fading down the hall.
2 notes
·
View notes
Note
Hey hey hey fic time
This was so fun to write I love using different formats I hope this is easy to read!!!
Hey @meme-boys-blog look!!!!
—————-
(Light snoring)
(Indistinguishable muttering)
[Dagda Appears]
(Rage.) “You-“
[Fingers snap, Pages flutter]
“Apologies, but we are not going to take any chances.”
(Struggling, muffled anger)
(Muttered) “Shame it had to come to this. Hold still, will you?”
[Pages rustle, nib pen scratches]
“There we are.”
[Pages flutter closed]
[Body collapses, movement]
(Seething) “Oh you are not getting away with that, Galla.”*
(Laughs quietly)
[Knuckles crack.]
(Grunt of exertion, halted abruptly)
“Wha-���
(More grunts, intensifying in anger.)
(Seething) “The fuck did you do to me?!”
“After your little stunt this evening, we thought it prudent to have some form of insurance.”
(Growls)
(Loathing) “Leave us, Dagda. Go back to your ward and stay until we finish what we came here for.”
[Dagda returns]
“Ah, such blessed silence. Good that Navarre stepped out.”
(Snaps fingers, Humming)
“Do not mind us, child. We shall return it in a moment.”
[Anger, Query; purpose?]
[Amusement, Command; Cease.]
[Rage, Anger, Hate.]
(Giggles)
(Muttered) “No wonder Orsinov had so much fun.”
[Sarcasm; Pity.]
————————
[Bitter, Query; Purpose?]
[Denied.]
[Suspicion]
> Hello user Dagda.
displayProperties ;OS/GodslayerCOMP/Music.app_
> You need administrator permission to access this file.
> Music.App; You’re going to have to be better than *that*. -Admin
[Annoyance]
message Admin fuck you_
> Error; attachment not recognized.
[Frustration]
message Admin “Fuckk *You*”_
> Message sent!
displayProperties ;OS/GodslayerCOMP/appdata/Music/Songs/
> DateCreated; DD/MM/20YY 22;34
> CreatedBy; Admin
> Note; Contains songs for Music App in mp3 format. You’re not going to get any info out of this either, High King. -Admin
[Anger]
Message Admin “What the hell are you doing”_
> Error; command not recognized.
[Rage, Frustration]
message Admin “what in th eHELL are you do ing”_
> Message sent!
—————————-
;OS/GodslayerCOMP/DemonSummoningProgram/_
execute shadowlock.exe_
> Enter password;
***********************_
> Enter passphrase;
忘れない いつまでも 決して until my life is exhausted._
[Bitter, Query; Purpose?]
> Welcome, Admin Kurokami.
> If you’re seeing this, this means I’m not able to come to your assistance. Sorry about that. -Burroughs
[Denied.]
IgnoreUser Dagda_
> This will prevent viewing of messages from user while you are logged in. You will still get notified when they send a message.
> Are you sure? y/n
y_
> Incoming message; Mido
> Good to see you again! Will you be transferring data like before?
message Mido “Gracious offer, but we have to decline.”_
> Message sent!
moveFile Music.app from ;K/ to ;OS/GodslayerCOMP/_
> Moving file Music.app...
> Incoming message; Mido
> Suit yourself. You should tell Nanashi to fill out his compendium more. Compared to Flynn it’s almost barren!
message Mido “Give the boy time. Not everyone can be so meticulous as him or us.”_
> Message sent!
> Incoming message; System
> File Music.app successfully moved from ;K/ to ;OS/GodslayerCOMP/
open ;OS/GodslayerCOMP/Music.app_
> Opening...
> File Music.app wants to make changes to your system. Allow? y/n
y_
> Music.app; Performing initial setup…
[Suspicion]
> Incoming message; Mido
> Ah, I remember my surprise upon seeing you as a new user. How long ago was that now?
> Incoming message from Music.app
> initial setup complete!
close ;OS/GodslayerCOMP/Music.app_
> Closing…
[Annoyance]
message Mido “Not long enough. The masquerade ended as soon as Lucifer set his eyes on us. ‘Sacrificing’ ourself against his little ‘test’ was the least we could do to save that Flynn.”_
> Message sent!
[Frustration]
> Message from ignored user Dagda blocked.
movefolder ;K/Selected_Songs/ to ;OS/GodslayerCOMP/appdata/Music/songs/_
> Found 8 files
> Moving files...
- City_of_Tears.mp3
- Daisy_Bell.mp3
- Hummingbird.mp3
- Its_Going_Down_Now.mp3
- Mass_Destruction_New.mp3
- No_More_What_Ifs.mp3
- Road_Less_Taken.mp3
- Were_Finally_Landing.mp3
> Incoming Message; Mido
> Of course. If you ever want to relive those moments, let me know.
message Mido “Will do.”_
> Message sent!
> Incoming message; System
> Files successfully moved from ;K/Selected_Songs to ;OS/GodslayerCOMP/appdata/Music/songs/
[Anger]
[Rage, Frustration]
> Message from ignored user Dagda blocked.
shadowlock.exe endsession_
> End session? y/n
y_
> Logging out...
> See you soon. -Burroughs
—————————————
“…Hey! You didn’t tell me you had a pair of earbuds…”
“Huh, Guess I did.”
(Smug)“…You jealous?”
“You gonna share?”
“Heheh, Finders keepers~”
(Huffs) “Fine, I’m gonna find my own and they’re gonna be so much cooler than yours!”
(Laughs)
———————-
Translation corner; *Bitch.
Used this site for the translation.
Coding stuff may be inaccurate, but that’s mostly because I’m used to another system. I have no doubt that the original Demon Summoning Program runs on some suped-up version of Linux or something, but I don’t wanna know how an entire operating system works for my silly little fic, so Windows OS it is.
Don’t ask who Orsinov is. You don’t wanna know.
local god of death has maybe the Worst Time trying to hack in weird transdimensional shadow’s ipod, more at 11
#asks#vinegar-on-main#inbox fic#NANASHI HAVING ITS GOING DOWN NOW IN HIS MUSIC#I LOVE HIM#DID YOU KNOW THAT#also mido!!!!#hi uncle fusion :3#very cool fic layout…. I AM a fan
3 notes
·
View notes
Text
I'm perfectly aware that the place to put this post is linkedin and not Tumblr.com (although i might make a more professional-looking version).
Anyway, I'm horrified by the amount of cyber attacks that are happening in the last few days. Especially because a couple of these are really big companies, and one would think they have an IT department that knows how to do their job. Even better, they should have at least one person that deals with cybersecurity.
I know that security operations centers (where we use very expensive systems to monitor the networks and the assets of the companies, plus we often investigate previous security incidents and produce intelligence reports) are expensive. I work in one and it's not the solution that works for everyone. A small company with few employees definitely cannot afford a SOC, but a big corporation? That would be nice (again, it's not the only solution and every client is different, you need to tailor the cybersecurity solution to the client).
But a videogame studio? I would expect them to take security seriously. And not only because of the data involved, but industrial espionage is a thing (although it's difficult to prove and it happens rarely that it's taken to a court, however it does happen), but it's a risk. A worldwide clothing company? A fucking bank? Sure.
The problem with certain things it's that "it won't happen to me". Until it does. And you end up paying 300x than you would be paying at least a cybersecurity consultant to prevent the attack.
Even better, a lot of the simplest measures are free to implement. No USB from home policy. Disabling local administrator accounts. Implement a strong password policy. Implement a blacklist for suspicious websites (and also, maybe stop downloading cracked software if you don't know where to find reputable sources? I see you trying to download that CoD aimbot, how embarrassing)
Implement a strong antispam policy (which is fundamental, as this is very very often the access point - you send a targeted spam email to a company with 3k employees and I can guarantee you that at least one will download the malicious file or insert the credential on the fake office 365 website, it's just what it is.)
But most people won't, because "it's annoying" and users don't want to put the effort to like, keep their fucking job and remember a 12 character password(yes, a company can suffer so much damage from a cyber attacks that it might even close the business, and yes, I had to fight with clients that refuse to change their AD admin accounts set in 2015 even when I told them about a potential leak) Not to mention that the data stolen often is the employees data. And you don't want your identity stolen by a criminal, do you?
And the danger when these attacks are carried against hospitals. People can die if the whole network shuts down because no one cared to implement basic cybersecurity.
And it's not true that organisations don't have the budget. We both know you are lying lol.
Don't get me wrong, there is nothing foolproof, there will always be a certain amount of risk.
I just expect people to use some good sense and I'm often disappointed lol.
4 notes
·
View notes
Text
Competitive Exams Guide 2024: Practice Sets, Answer Keys, Religious History & Internships

India's competitive exam landscape in 2024 is buzzing with opportunities for aspirants targeting government jobs like BSSC CGL and RRB ALP. From effective practice sets and answer keys to the importance of subject knowledge like religious history and maths, let’s explore everything you need to crack these exams, along with new initiatives like the PM Internship Scheme and how to stay updated with job alerts like Naukri Exam.
BSSC CGL Practice Set
The Bihar Staff Selection Commission (BSSC) Combined Graduate Level (CGL) exam is one of the most awaited recruitment drives for graduate candidates in Bihar. A practice set for BSSC CGL includes subject-wise question papers on General Studies, General Science, Mathematics, Logical Reasoning, and current affairs. These sets help aspirants evaluate their preparation, improve time management, and identify weak areas. Many reputed publications provide mock tests aligned with the latest syllabus and previous year papers. Candidates should solve at least one full-length practice paper every day as the exam approaches.
RRB ALP Answer Key 2024
The Railway Recruitment Board (RRB) Assistant Loco Pilot (ALP) answer key 2024 is a crucial document that helps candidates calculate their tentative scores and raise objections if needed. The answer key is released shortly after the exam on the official RRB websites. Candidates must log in using their registration number and password to download the answer key. It's important to cross-verify with the response sheet and file objections within the stipulated time if discrepancies are found. This transparency ensures fairness in evaluation and boosts candidate confidence.
BSSC CGL Practice Set Book
To strengthen preparation, students should rely on a high-quality BSSC CGL practice set book. Some of the recommended books include those by Kiran Publications, Arihant, and Lucent. These books offer chapter-wise solved questions, model test papers, and previous year papers. A good practice set book should include explanations in both English and Hindi to aid bilingual learners. Selecting a book that follows the latest BSSC syllabus is essential for effective preparation.
भारत में ईसाई धर्म का आगमन (Arrival of Christianity in India)
भारत में ईसाई धर्म का आगमन पहली शताब्दी ईस्वी में सेंट थॉमस (संत थॉमस) के माध्यम से हुआ था। यह माना जाता है कि वे 52 ईस्वी में केरल के मलाबार तट पर पहुंचे थे। प्रारंभ में ईसाई धर्म दक्षिण भारत के कुछ हिस्सों तक ही सीमित था, लेकिन बाद में यूरोपीय उपनिवेशों जैसे पुर्तगाल, डच और अंग्रेजों के आने के बाद इसकी पहुंच पूरे भारत में फैल गई। आज भारत में ईसाई समुदाय देश का तीसरा सबसे बड़ा धार्मिक समूह है। यह विषय सामान्य ज्ञान और इतिहास के लिए महत्वपूर्ण है, विशेष रूप से बिहार और रेलवे की परीक्षाओं में।
PM Internship Scheme 2024
The PM Internship Scheme 2024, also known as the Prime Minister’s Internship Yojana, is a government initiative aimed at providing real-time work experience to undergraduate and postgraduate students. Interns will work in various departments under central ministries, PSUs, and other government bodies. The scheme offers:
Monthly stipend
Work experience certificate
Exposure to public policy and administration
This initiative enhances employability and helps students understand how governance works at the grassroots level. Details and application forms can be accessed via the official MyGov portal.
Maths Books for Competitive Exams
Mathematics plays a vital role in exams like BSSC, RRB, SSC, and Banking. Some of the best books for preparation include:
Quantitative Aptitude by R.S. Aggarwal
Fast Track Objective Arithmetic by Rajesh Verma
Kiran SSC Mathematics Chapterwise Solutions
NCERT Maths (Class 6 to 10) for concept building
Regular practice of short tricks, formulas, and previous year questions is essential to score high in the quantitative aptitude section.
Exam4 Naukri and Job Alerts
Exam4 Naukri refers to various recruitment tests conducted across India for government and private jobs. To stay updated, candidates should:
Subscribe to job portals like Naukri.com, FreeJobAlert, SarkariResult
Follow official websites like SSC, UPSC, RRB, BPSC
Join Telegram channels and YouTube coaching platforms for real-time updates
Timely alerts help in applying before deadlines and preparing efficiently for upcoming vacancies.
Conclusion: Preparation for government exams in 2024 demands a strategic mix of practice, reliable study material, awareness of historical facts, and knowledge of employment schemes. Whether you're solving a BSSC CGL paper or reviewing the RRB ALP answer key, staying informed and consistent is the key to success.
0 notes
Text
How to Use a Solid Password Generator With No Forgetting Your Passwords?

In today's digital landscape, strong passwords are important for safeguarding your online existence. Nonetheless, utilizing a strong password generator can leave behind you along with a collection of complicated passwords that are difficult to remember. To properly bridge this void, you need to implement methods that permit you to preserve gain access to without compromising security. Comprehending how to manage these passwords successfully can make all the difference in safeguarding your accounts. Therefore, what are the best approaches to accomplish this equilibrium?
Understanding the Significance of Strong Passwords
In today's digital landscape, durable passwords serve as the very first line of defense against cyber threats. A solid password isn't simply a combination of letters and numbers; it's a facility, special phrase that greatly decreases your vulnerability to hacking. To develop a secure password, you need to aim for at least 12 characters, blending uppercase letters, lowercase letters, numbers, and signs. Using a safe and secure password generator can simplify this procedure, providing you arbitrary, high-entropy passwords that are tough to break.
Choosing the Best Password Generator
When picking a password generator, take into account a number of key factors to assure you're improving your protection successfully. Initially, go with a random password that creates complex and random passwords, creating them hard to crack. Search for generators that permit personalization of length and personality types, as this enhances your password's strength. Additionally, take into consideration whether the generator stores your passwords securely or if you'll require a different solution for that.
Methods for Keeping and Handling Passwords

Efficient password administration is important for preserving your on the internet safety. To save and handle your passwords effectively, consider making use of a reputable passcode supervisor. These tools safely keep your passwords and can generate solid arbitrary passwords for each of your accounts, minimizing the danger of violations. Whenever utilizing a solid random password generator, guarantee that it develops unique passwords that are hard to crack.
Tips for Creating Unforgettable Yet Secure Passwords
How can you produce passwords that are both memorable and protect? Start by utilizing a password generator strong sufficient to create intricate combinations. Nevertheless, to guarantee you remember them, try the following approaches. Initially, utilize expressions or sentences that have personal value, and after that change them by substituting letters with numbers or symbols. For example, "MyDogIsAwesome!" could end up being "Myd0g!s4w3some." Furthermore, consider utilizing a password generator free for producing unique variants for different accounts.
Final thought
Including a solid password generator right into your security routine is like developing a citadel around your electronic life. By choosing the right devices and approaches for storage and management, you can produce robust passwords without the fear of forgetting them. Normal updates and unforgettable phrases will improve your defenses while keeping your accounts protected. Welcome these methods, and you'll browse the on the internet globe with confidence, knowing your individual information is well-protected versus cyber hazards.
0 notes
Text
North America Biometric Technologies Market Size, Revenue, End Users And Forecast Till 2030
The North America biometric technologies market was valued at US$ 13,516.24 million in 2022 and is expected to reach US$ 45,097.67 million by 2030; it is estimated to register a CAGR of 16.3% from 2022 to 2030.
Market Overview
The US, Canada, and Mexico are among the major economies in North America. This region accounts for a significant share of the biometric technologies market. Surging data theft identity fraud incidences, and terrorist operations, among other security breaches, are driving the biometric technologies market in North America. In October 2023, the House Foreign Affairs Committee and the U.S. Senate Committee on Homeland Security & Governmental Affairs faced a cyberattack from Vietnamese hackers trying to install spyware on the phones of journalists. This propels the demand and adoption of biometrics technologies to handle unlawful practices and enhances national security. Biometric authentication in phones unlocks greater security due to its resistance to most common cyberattacks such as password cracking or phishing. Biometric technologies offer an efficient way to keep physical attacks and cyber-attacks in check by delivering more stringent security measures to users. The market in North America is anticipated to expand at a significant rate during the forecast period owing to the surging demand for biometrics solutions from the IT sector and the rising number of phishing attacks.
Grab PDF To Know More @ https://www.businessmarketinsights.com/sample/BMIRE00030666
North America Biometric Technologies Strategic Insights
Strategic insights for the North America Biometric Technologies provides data-driven analysis of the industry landscape, including current trends, key players, and regional nuances. These insights offer actionable recommendations, enabling readers to differentiate themselves from competitors by identifying untapped segments or developing unique value propositions. Leveraging data analytics, these insights help industry players anticipate the market shifts, whether investors, manufacturers, or other stakeholders. A future-oriented perspective is essential, helping stakeholders anticipate market shifts and position themselves for long-term success in this dynamic region. Ultimately, effective strategic insights empower readers to make informed decisions that drive profitability and achieve their business objectives within the market.
Increasing Use of Biometric Systems at Airports Fuels North America Biometric Technologies Market
Airports around the world are actively exploring and implementing biometric solutions at various touchpoints, including check-in kiosks, security checkpoints, and boarding gates, which results into a continuous demand for new hardware and software systems. As airport administrations experience success with initial implementations, they are likely to expand the application of biometrics to other areas at airports, creating additional demand for technology and integrations. Moreover, facial recognition is becoming common in airport operations. For instance, in February 2024, passenger screening using facial recognition software was made available to select travelers at La Guardia by Delta Air Lines and the Transportation Security Administration. This explains how biometric technology, which uses an individual's unique physical identifiers such as face or fingerprints, promises to transform airline operations and traveling experience. Therefore, the increasing use of biometric technology in airports presents a significant biometric technology market trend.\
Market leaders and key company profiles
Aware, Inc.
Thales SA
Cognitec Systems GmbH
NEC Corp
IDEMIA France SAS
HID Global Corp
Fujitsu Ltd
Leidos Holdings, Inc.
M2SYS Technology
Precise Biometrics AB
North America Biometric Technologies Regional Insights
The geographic scope of the North America Biometric Technologies refers to the specific areas in which a business operates and competes. Understanding local distinctions, such as diverse consumer preferences (e.g., demand for specific plug types or battery backup durations), varying economic conditions, and regulatory environments, is crucial for tailoring strategies to specific markets. Businesses can expand their reach by identifying underserved areas or adapting their offerings to meet local demands. A clear market focus allows for more effective resource allocation, targeted marketing campaigns, and better positioning against local competitors, ultimately driving growth in those targeted areas.
About Us:
Business Market Insights is a market research platform that provides subscription service for industry and company reports. Our research team has extensive professional expertise in domains such as Electronics & Semiconductor; Aerospace & Defence; Automotive & Transportation; Energy & Power; Healthcare; Manufacturing & Construction; Food & Beverages; Chemicals & Materials; and Technology, Media, & Telecommunications.
0 notes
Text
Key Attributes to Consider in a Reputable Secure Password Generator

When choosing a secure password generator, you need to consider several essential features that boost both safety and security and use. Randomness is essential for developing unpredictable passwords, while complexity warranties they fulfill strength requirements. An user-friendly user interface and compatibility with password administration tools can simplify your experience. Nonetheless, not all generators are created equivalent, and recognizing these attributes can make a significant difference in your online safety and security technique. What specific traits should you focus on?
Value of Randomness in Password Creation
When it pertains to password generation, the significance of randomness can not be overemphasized. A secure password generator makes use of formulas that ensure the unpredictability of produced passwords. This randomness is important since it protects versus common hacking techniques, such as thesaurus strikes, where assaulters try to think passwords using typical words and expressions. By going with a random password generator, you're significantly enhancing your safety and security pose. These tools develop passwords that combine letters, numbers, and icons with no discernible patterns, making them much harder to split. Choosing a secure password generator warranties that you obtain robust, distinct passwords for each account, reducing the chance of unauthorized gain access to. Ultimately, welcoming randomness is essential for effective password management.
Complexity Needs for Strong Passwords
While you may assume any type of password will be sufficient, complexity requirements play an important role in ensuring your passwords are strong sufficient to thwart prospective breaches. A random password generator must help with the creation of passwords that consist of a mix of uppercase and lowercase letters, numbers, and unique characters. This range raises the entropy of your password, making it considerably harder for assailants to crack. Go for a minimum of 12-16 characters in length, as longer passwords greatly improve safety and security. In addition, avoid common expressions or foreseeable patterns. When you generate strong password, confirm that they meet these complexity standards to protect your delicate information properly. By focusing on these requirements, you can significantly decrease the risk of unauthorized accessibility to your accounts.
User-Friendly Quality for Ease

Producing strong passwords is just the initial step; guaranteeing that the password generation procedure is easy to use boosts general benefit and functionality. When you pick an online password generator, seek features that simplify the experience. A straightforward user interface allows you to generate a strong passcode quickly without unnecessary difficulties. Customization options are vital, allowing you to define size and complexity preferences tailored to your needs. Furthermore, an intuitive design that offers clear guidelines can lower aggravation, making the procedure seamless. Real-time feedback on password toughness can additionally assist you in producing durable passwords. Lastly, a one-click copy function warranties you can conveniently move your strong password to other applications, simplifying your operations even further.
Compatibility With Password Management Tools
Ensuring compatibility with password monitoring tools is necessary for maximizing the utility of a secure password generator. A secure password generator not just develops complex passwords but additionally integrates flawlessly with your preferred password manager. This compatibility permits automatic password storage space and access, improving safety and security and comfort. When selecting a password generator, check if it supports direct integration with prominent administration tools like LastPass or 1Password. Additionally, try to find functions that enable simple exporting or importing of passwords. This assures that the generated passwords can be efficiently utilized without hands-on access mistakes. By focusing on compatibility, you'll keep a streamlined workflow, enhancing both your on the internet safety and total user experience.
Verdict
In verdict, selecting a secure password generator includes prioritizing randomness and intricacy to assure robust protection versus unapproved access. Try to find features like adjustable length, a mix of character types, and an user-friendly user interface that offers real-time strength comments. In addition, confirm compatibility with password monitoring tools and the ease of one-click copying. By focusing on these crucial components, you can considerably enhance your online protection and simplify the password creation process.
0 notes
Text
What Features Should You Seek in a Secure Password Generator?

When picking a secure password generator, you need to think about numerous essential features that boost both protection and functionality. Randomness is crucial for creating uncertain passwords, while intricacy assurances they satisfy toughness requirements. An easy to use interface and compatibility with password administration tools can streamline your experience. However, not all generators are developed equal, and understanding these features can make a considerable difference in your online safety and security method. What specific characteristics should you prioritize?
Relevance of Randomness in Security Password Creation
When it pertains to password generation, the relevance of randomness can't be overstated. A secure password generator uses algorithms that assure the unpredictability of generated passwords. This randomness is crucial because it secures versus typical hacking strategies, such as thesaurus attacks, where assaulters try to think passwords making use of typical words and phrases. By choosing a random password generator, you're significantly boosting your safety and security stance. These tools develop passwords that integrate letters, numbers, and signs without any kind of noticeable patterns, making them a lot harder to break. Choosing a password generator warranties that you obtain durable, unique passwords for each account, lowering the possibility of unapproved access. Eventually, welcoming randomness is essential for efficient password administration.
Complexity Needs for Strong Passwords
While you may think any type of password will certainly be sufficient, complexity needs play a vital role in assuring your passwords are strong sufficient to ward off prospective violations. A random password generator ought to promote the creation of passwords that consist of a mix of uppercase and lowercase letters, numbers, and unique characters. This range raises the decline of your password, making it significantly harder for opponents to crack. Goal for at the very least 12-16 characters in size, as longer passwords exponentially boost safety and security. Furthermore, stay clear of typical phrases or predictable patterns. When you generate strong password, confirm that they meet these intricacy standards to secure your sensitive information properly. By prioritizing these demands, you can substantially minimize the danger of unapproved accessibility to your accounts.
Easy To Use Quality for Ease

Producing strong passwords is just the very first step; assuring that the password generation procedure is straightforward boosts overall convenience and usability. When you pick an online password generator, search for features that streamline the experience. An uncomplicated user interface permits you to create a strong password rapidly without unneeded difficulties. Personalization alternatives are vital, enabling you to define size and intricacy choices tailored to your demands. Furthermore, an intuitive design that offers clear instructions can lower irritation, making the process smooth. Real-time feedback on password stamina can likewise assist you in creating robust passwords. Ultimately, a one-click duplicate attribute guarantees you can conveniently transfer your strong password to other applications, enhancing your workflow also further.
Compatibility With Security Password Management Tools
Ensuring compatibility with password administration tools is vital for maximizing the utility of a secure password generator. A password generator strong not only develops intricate passwords yet likewise incorporates perfectly with your favored password manager. This compatibility enables automated password storage space and access, improving security and comfort. When picking a password generator, check if it supports straight assimilation with popular management tools like LastPass or 1Password. Furthermore, try to find attributes that permit easy exporting or importing of passwords. This assures that the produced passwords can be successfully used without hands-on entrance mistakes. By prioritizing compatibility, you'll keep a streamlined operations, enhancing both your on the internet security and general customer experience.
Conclusion
To conclude, picking a secure password generator involves prioritizing randomness and complexity to assure durable defense against unauthorized gain access to. Seek features like personalized length, a mix of character types, and an user-friendly user interface that uses real-time stamina responses. Additionally, confirm compatibility with password monitoring tools and the comfort of one-click duplicating. By concentrating on these important components, you can substantially improve your online safety and security and simplify the password creation procedure.
0 notes
Note
Find anything interesting on here?
Hi my name's Alpha
I'm a Porygon!
While I found nothing interesting on L'S ROTO PHONE DEVICE I have managed a connection to VICTORIAS LAPTOP. I am currently trying to crack the administrator password.
0 notes
Text
nternet security has become one of the most discussed issues in this era of information technology. The Internet has become a tool of business and more people are warming up to e-commerce. It is approximated that about 30 million people all over the world use Internet to transact business. The figure is expected to double by 2016 and triple by 2025 (Schneider, 2000). Internet use has come to be embraced even from unlikely quarters with government adopting concepts such e-governance. The growth in the use of Internet has however presented enormous challenges. Like all other systems in the society, Internet is required to operate within the precincts of law. There are very few laws that govern Internet use and especially the conduct of e-commerce. Different countries have laws and policies on information and also the industry has its governing rules and regulations that are seen as measures to protect users and ensure that Internet is a mutual medium of doing business. Internet presents many challenges to security in that the Internet has become an avenue or tool of war. From infringement of privacy, to cyber crime and defrauding, Internet is causing economies losses in terms of risks and challenges. However of all challenges facing the Internet sector nothing threatens the half a century old communication technology than cyber crimes. Other security threats such as virus threats, software threats and hacking are rampant, have become very rampant and cost business billions of dollars. Viruses are one of the earliest forms of security intrusions. To curb these viruses many anti-virus software have been designed to overcome the problem with software being designed that are capable of detecting virus and cleansing the system of the viruses before the virus can attack and meddle with the system. The anti-virus software is capable of even blocking the computers from spy wares that have also become a rampant form of Internet insecurity. There have also been inventions in form of software that are installed in computers to protect the system from malicious people who are interested in stealing sensitive data such as bank information. Overall such software are security measures geared at protecting the computer system from worms, spy wares, Trojan horses, and identify identity theft software. There is a continuous need in the industry for a continuous study of the vulnerabilities the industry is exposed to, a need for constant upgrading of the network systems to stay ahead of hackers and other forms of security threats to internet, continuous research aimed at developed view forms of technologies, which are less vulnerable to security threats. To improve security there is a need for system designers, system administrators and decision makes to come up with tough policies and security related procedures which should make it very hard for hackers and cyber criminals to penetrate computer systems. Designers should aim at producing strategies that will effectively put under control the Internet use. Such measures can include invention of effective Internet monitoring tools, increased use of security analysis tools as well as an increased use of hard-to-crack passwords and firewalls (Flynn, 2001). It is a fact that Internet is a world wide connection of networks makes it accessible to users regardless of national, regional and geographical boundaries (Flynn, 2001). Therefore this increasing freedom to access information and data has presented the greatest headache to lawmakers, governments, and regulatory bodies. It is clear that the battle against cyber crime and all other forms of Internet insecurity is being won Read the full article
0 notes
Text
Exactly Why Solid Passwords Alone Aren't Enough: Exactly How a Password Creator Aids?
Strong passwords safeguard your accounts, reinforce your protection, and safeguard your individual details. Nonetheless, they can't entirely secure you from online dangers. Phishing strikes, data breaches, and various other susceptabilities can endanger even the best passwords. That's where a password generator enters into play. By creating facility, special passwords for each of your accounts, it reduces risk and boosts your safety and security posture. Yet how does it function, and what extra steps can you require to additional shield on your own?
The Limitations of Solid Passwords
Although strong passwords are vital for protecting your online accounts, they include remarkable constraints that can undermine their efficiency. First, even the best password can be endangered through phishing assaults or information violations, making its intricacy unnecessary. In addition, if you battle to keep in mind multiple solid passwords, you may resort to using the very same one across different websites, raising susceptability. One more problem is that developing a strong password often requires effort and time, which several users locate challenging.
The Conveniences of utilization a Password Generator
Exactly why deal with the intricacies of password development when a password generator can streamline the process? Using a strong password generator conserves you time and effort by immediately producing complex passwords that meet security standards. These tools normally produce lengthy strings of arbitrary personalities, making sure that your passwords are much more challenging to fracture contrasted to those you might produce on your own. An online password generator uses comfort; you can access it from any kind of tool with net connectivity, permitting you to produce passwords on the go. In addition, numerous generators consist of setups to personalize password length and character kinds, better boosting safety and security. By relying on a generate strong password, you not only strengthen your accounts yet additionally eliminate the frustration of keeping in mind detailed passwords.
The Advantages of utilization a Password Creator
Reasons why fight with the complexities of password creation when a password generator can simplify the process? Utilizing a strong password generator conserves you time and effort by immediately developing intricate passwords that satisfy security requirements. These tools normally produce lengthy strings of random personalities, ensuring that your passwords are much harder to crack contrasted to those you might develop on your own. An on the internet password generator provides comfort; you can access it from any gadget with web connectivity, permitting you to generate passwords on the go. In addition, numerous generators consist of setups to personalize password length and character types, further boosting protection. By relying upon a strong password generator, you not just strengthen your accounts but also get rid of the aggravation of remembering complex passwords.
Ideal Practices for Password Administration

As you navigate the digital landscape, applying ideal practices for password management is vital to securing your personal information. Begin by using a password generator to develop strong password that are both complex and unique for each account. Stay clear of recycling passwords, as this raises vulnerability. On a regular basis upgrade your passwords, particularly for sensitive accounts, and consider utilizing a password manager to save them securely. Enable recuperation options but make sure they're also protected with strong passwords. In addition, be cautious about sharing passwords, despite having relied on individuals. By adhering to these methods, you can considerably reduce the threat of unapproved accessibility and maintain your digital life protected. Bear in mind, a strong password is only like the monitoring methods you relate to it.
Developing Security With Two-Factor Verification
Carrying out solid passwords is a solid step towards safeguarding your online accounts, but it's not always sufficient by itself. Two-factor authentication (2FA) adds an additional layer of safety and security, requiring you to validate your identity with a secondary method, like a text or authentication application. This suggests that even if somebody cracks your password-- probably generated by a random password generator-- they still can not access your account without that second variable. Utilizing a password generator solid enough to develop complicated passwords will certainly enhance your defenses, but integrating it with 2FA significantly lowers your threat of unauthorized gain access to. By embracing both approaches, you're successfully fortifying your online presence against possible threats. Don't undervalue the power of split security.
Final Thought
In today's electronic landscape, counting only on strong passwords isn't enough; a shocking 81% of data violations entail weak or stolen passwords. By using a password generator, you can create facility, distinct passwords for each and every account, substantially lowering your vulnerability. Combined with ideal practices and two-factor authentication, you can significantly improve your on-line safety and security. Do not risk your personal information-- take control of your electronic safety and security today by leveraging the power of automated password monitoring.
0 notes
Text
Exactly Why Strong Passwords By Itself Aren't Enough: How a Password Creator Helps?

Solid passwords shield your accounts, strengthen your safety, and safeguard your personal details. Nevertheless, they can not entirely shield you from online dangers. Phishing assaults, information breaches, and other vulnerabilities can endanger even the greatest passwords. That's where a password generator enters into play. By creating complex, special passwords for each of your accounts, it reduces threat and boosts your protection posture. However just how does it work, and what added actions can you take to more secure on your own?
The Limitations of Strong Passwords
Although strong passwords are necessary for safeguarding your online accounts, they include notable constraints that can weaken their performance. Initially, even the greatest password can be jeopardized via phishing attacks or information violations, making its complexity pointless. Furthermore, if you battle to bear in mind numerous strong passwords, you may resort to utilizing the same one across different sites, boosting vulnerability. Another problem is that producing a solid password frequently requires effort and time, which lots of users find difficult.
The Advantages of Using a Password Creator
Exactly why struggle with the intricacies of password development when a password generator can simplify the process? Utilizing a strong password generator saves you effort and time by instantly developing intricate passwords that satisfy safety and security requirements. These tools typically produce long strings of arbitrary personalities, ensuring that your passwords are much more challenging to crack compared to those you could create on your own. An on the internet password generator offers benefit; you can access it from any gadget with net connection, enabling you to create passwords on the go. Additionally, lots of generators consist of settings to personalize password length and character types, even more enhancing safety. By relying upon a password generator strong, you not only strengthen your accounts yet additionally eliminate the frustration of remembering detailed passwords.
The Conveniences of utilization a Password Generator
Exactly why deal with the intricacies of password development when a password generator can streamline the process? Using a strong password generator conserves you time and effort by immediately producing complex passwords that meet security standards. These tools normally produce lengthy strings of arbitrary personalities, making sure that your passwords are much more challenging to fracture contrasted to those you might produce on your own. An online password generator uses comfort; you can access it from any kind of tool with net connectivity, permitting you to produce passwords on the go. In addition, numerous generators consist of setups to personalize password length and character kinds, better boosting safety and security. By relying on a generate strong password, you not only strengthen your accounts yet additionally eliminate the frustration of keeping in mind detailed passwords.
Finest Practices for Password Management

As you browse the electronic landscape, carrying out ideal practices for password administration is essential to safeguarding your individual details. Start by utilizing a password generator to develop solid passcode that are both facility and unique for every account. Stay clear of reusing passwords, as this raises susceptability. On a regular basis update your passwords, specifically for delicate accounts, and take into consideration using a password supervisor to store them firmly. Enable healing options but make sure they're likewise safeguarded with solid passwords. In addition, beware regarding sharing passwords, even with relied on individuals. By adhering to these practices, you can significantly decrease the risk of unapproved accessibility and keep your electronic life secure. Remember, a solid password is only just as good as the administration methods you relate to it.
Enhancing Safety And Security With Two-Factor Verification
Implementing strong passwords is a strong step toward protecting your online accounts, but it's not constantly sufficient by itself. Two-factor verification (2FA) includes an additional layer of security, needing you to confirm your identification via an additional technique, like a sms message or verification application. This suggests that even if someone splits your password-- perhaps produced by a random password generator-- they still can not access your account without that second factor. Making use of a password generator solid sufficient to produce complicated passwords will improve your defenses, yet integrating it with 2FA greatly minimizes your threat of unapproved gain access to. By adopting both techniques, you're properly strengthening your online visibility against possible risks. Do not ignore the power of split safety.
Verdict
In today's digital landscape, depending only on solid passwords isn't enough; a staggering 81% of information breaches entail weak or stolen passwords. By using a password generator, you can create complex, distinct passwords for every account, greatly lowering your vulnerability. Incorporated with finest techniques and two-factor verification, you can greatly boost your online protection. Don't risk your personal info-- take control of your digital safety and security today by leveraging the power of automated password management.
0 notes
Text
Finest Advantages of Using a Strong Password Generator for Online Safety
In today's digital landscape, safeguarding your online accounts is much more essential than ever before. A solid password generator can greatly boost your online safety by producing intricate passwords that are virtually difficult to crack. It also simplifies just how you manage numerous accounts, permitting you to keep unique passwords without the problem. Nevertheless, the benefits expand past just creating passwords. What other benefits can this device deal you in the battle against cyber dangers?
Improved Password Complexity
When you utilize a solid password generator, you instantly boost your password's intricacy, making it especially harder for hackers to break. These protected password generators produce strings of personalities that often include uppercase letters, lowercase letters, numbers, and icons, causing passwords that are tough to think. Unlike common passwords, which may contain easily well-known words or patterns, a password generator ensures randomness and changability. This complexity is vital, as numerous cybercriminals make use of automated devices to evaluate usual passwords in fast sequence. By relying on a solid password generator, you considerably reduce the probability of unauthorized access to your accounts, thus securing your sensitive details and improving your general online protection.
Streamlined Password Administration
While enhanced password complexity considerably improves your online protection, handling these complicated passwords can come to be a tough job. This is where a solid password generator simplifies your life. As opposed to attempting to remember detailed mixes, you can count on the generator to produce distinct, robust passwords for every of your accounts. Numerous password supervisors that incorporate with these generators automatically keep your passwords, enabling you to access them easily without remembering every one. This streamlined approach not only conserves you time however also minimizes the threat of failing to remember or mishandling your passwords. Inevitably, utilizing a strong password generator warranties that your password monitoring is effective and safe, allowing you to focus on more crucial elements of your online experience. Don't wait till it's too late, set up a strong password now with https://www.strongpasswordgenerator.org/ to keep your information secure from cyberpunks.
Lowered Risk of Password Reuse

Making use of a solid password generator substantially reduces the danger of password reuse throughout your accounts. Whenever you rely on a random password generator, you can quickly create one-of-a-kind, complicated passwords for each site you utilize. This strategy decreases the opportunities of a single breach jeopardizing numerous accounts. In case you produce solid passwords that are challenging to guess, you're successfully guarding your individual details. Lots of people tend to recycle passwords, making them susceptible to cyberattacks. By adopting a online password generator, you eliminate this routine, making certain that each password stands out and protected. This straightforward adjustment boosts your total online safety and security and minimizes the likelihood of unapproved accessibility to your sensitive data. Prioritizing unique passwords is a crucial action in securing your electronic identity.
Boosted Understanding of Safety And Security Practices
As you embrace a strong password generator, you not only improve your account safety and security but also grow a much deeper understanding of safety techniques. Utilizing an online password generator prompts you to reassess just how you come close to password development. You end up being much more informed regarding the significance of one-of-a-kind, complicated passwords tailored to various accounts. This process encourages you to recognize common susceptabilities, such as password recycle and weak options. Additionally, it highlights the requirement of regular password updates and safety actions past simply solid passwords. By involving with a strong password generator, you're encouraged to develop a positive way of thinking toward on the internet safety, ensuring your digital existence continues to be safe and secure against progressing dangers. Welcoming these methods is necessary in today's cybersecurity landscape.
Conclusion
In a world where cyber dangers impend bigger everyday, you can't pay for to neglect your on-line safety. By utilizing a strong password generator, you're not just developing complicated passwords; you're additionally fortifying your electronic defenses. Think of the peace of mind that includes recognizing each account is shielded by special, robust passwords. As you accept much better protection methods and lower the risk of password reuse, bear in mind: your online safety rests on the choices you make today.
0 notes
Text
Exactly Why Strong Passwords By Itself Aren't Enough: How a Password Generator Helps?

Solid passwords protect your accounts, strengthen your protection, and safeguard your personal details. Nonetheless, they can not completely secure you from online hazards. Phishing assaults, information violations, and other vulnerabilities can endanger also the greatest passwords. That's where a password generator comes into play. By developing complicated, special passwords for every of your accounts, it reduces danger and improves your safety and security posture. Yet just how does it function, and what extra procedures can you require to further secure yourself?
The Limitations of Sturdy Passwords
Even though solid passwords are vital for shielding your online accounts, they come with notable restrictions that can weaken their effectiveness. Initially, also the best password can be jeopardized via phishing attacks or information breaches, making its complexity unnecessary. Furthermore, if you have a hard time to keep in mind several strong passwords, you could resort to making use of the same one throughout various websites, boosting vulnerability. An additional issue is that producing a solid password frequently needs effort and time, which many users discover burdensome.
The Conveniences of utilization a Password Generator
Exactly why deal with the intricacies of password development when a password generator can streamline the process? Using a strong password generator conserves you time and effort by immediately producing complex passwords that meet security standards. These tools normally produce lengthy strings of arbitrary personalities, making sure that your passwords are much more challenging to fracture contrasted to those you might produce on your own. An online password generator uses comfort; you can access it from any kind of tool with net connectivity, permitting you to produce passwords on the go. In addition, numerous generators consist of setups to personalize password length and character kinds, better boosting safety and security. By relying on a generate strong password, you not only strengthen your accounts yet additionally eliminate the frustration of keeping in mind detailed passwords.
Finest Practices for Password Administration

As you browse the electronic landscape, executing best methods for password administration is essential to guarding your personal info. Beginning by using a password generator to develop strong password that are both complex and distinct for every account. Avoid reusing passwords, as this boosts vulnerability. Consistently update your passwords, specifically for delicate accounts, and think about utilizing a password supervisor to save them safely. Enable healing choices yet make certain they're additionally secured with strong passwords. In addition, be cautious about sharing passwords, even with relied on individuals. By sticking to these practices, you can greatly minimize the threat of unauthorized accessibility and keep your digital life safe and secure. Keep in mind, a solid password is only comparable to the monitoring techniques you put on it.
Enhancing Safety And Security With Two-Factor Authentication
Applying strong passwords is a solid action toward protecting your online accounts, but it's not constantly sufficient by itself. Two-factor verification (2FA) adds an additional layer of security, needing you to confirm your identity via a secondary approach, like a sms message or authentication app. This means that even if somebody cracks your password-- maybe produced by a random password generator-- they still can not access your account without that 2nd aspect. Using a password generator strong enough to develop intricate passwords will improve your defenses, however incorporating it with 2FA greatly lowers your danger of unauthorized access. By taking on both approaches, you're properly fortifying your online existence versus potential hazards. Do not undervalue the power of layered security.
Conclusion
In today's digital landscape, counting only on solid passwords isn't enough; a staggering 81% of information violations include weak or stolen passwords. By utilizing a password generator, you can produce facility, distinct passwords for every account, substantially minimizing your vulnerability. Integrated with best methods and two-factor authentication, you can greatly improve your on-line protection. Don't risk your personal info-- take control of your electronic security today by leveraging the power of automated password administration.
0 notes
Text
Forgot Windows 8.1 Local Admin Password No Reset Disk How to Resolve
How to get back into your Windows 8.1 computer if you have forgotten local administrator password no reset disk, how can you reset administrator password in Windows 8.1 without reset disk?

To resolve this problem, you can firstly try Offline NT Password Editor to help reset the forgotten Windows 8.1 administrator password without reset disk. Offline NT password Editor can help clear or reset Windows local account password via CD/DVD. The following procedure will show you the detailed walkthrough.
Trick 1: Use Offline NT Password Editor to Reset Windows 8.1 Local Admin Password (Work with CD/DVD).
When you forgot Windows 8.1 administrator password and a password reset disk was not created, “Offline NT Password Editor”, a free Windows password reset disk, can help you reset forgotten Windows 8.1 local account’s password without knowing it. Free download the ISO file from the official site. Extract the downloaded file and then burn the ISO file on to a writable CD/DVD. Once burning completed, you can use the CD/DVD which is bootable to crack Windows 8.1 Local Admin password.
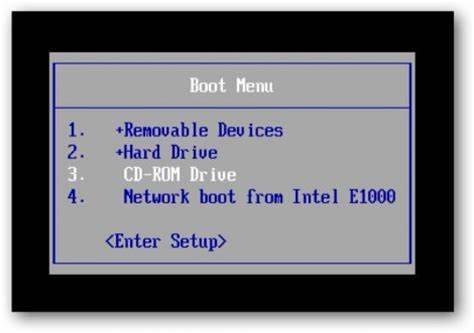
Step 1: Power on your locked computer and then insert the bootable CD to the CD-ROM.
Step 2: Restart the computer to boot from CD/DVD. If it still boot into Windows, you may need to change device boot order in BIOS. Learn how to boot computer from CD/DVD.
Step 3: When the computer boots from CD and loads Offline NT screen, press Enter until the “step one” appears. Type “1” and hit Enter.
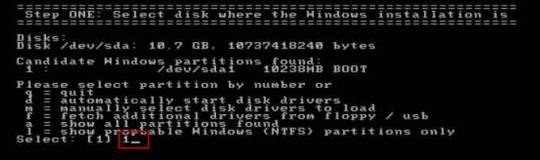
Step 4: Select “Password reset”, type “1” and hit Enter.
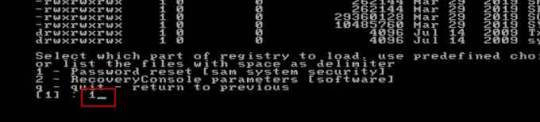
Step 5: Select “Edit user data and passwords, type “1” and hit Enter.
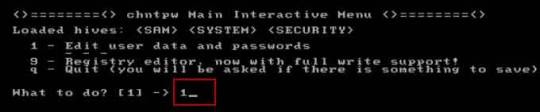
Step 6: Select a user account, type “administrator” and hit Enter.
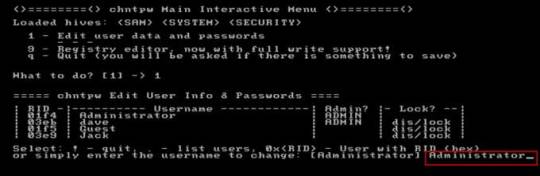
Step 7: Select “Clear user password”, type “1” and hit Enter.
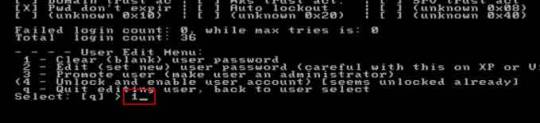
Step 8: Administrator’s password is cleared. Select “Quit editing user and back to user select”, type “!” and hit Enter.
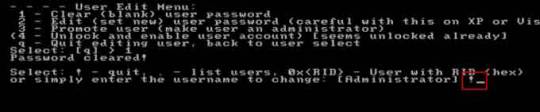
Step 9: Select “Quit”, type “q” and hit Enter.
Step 10: Write back changes, type “y” and hit Enter.
Step 11: When it asks you if try again, type “n” and hit Enter.
Step 12: Now eject your CD and then press CTRL-ALT-DEL to restart the computer.
Step 13: When Windows 8.1 welcome screen appears, click the screen to automatically sign in administrator without password.
Another simple method to reset forgotten Windows 8/8.1 local admin password is using a password recovery program, Windows Password Rescuer, which is working fine for all Windows systems including Windows 11. Here is how to use the utility to reset a local admin password on Windows 8.1/8 PC without logging in.
Trick 2: Reset Windows 8.1 Administrator Password with Windows Password Rescuer Run from USB.
If you have forgotten Windows 8.1 administrator password and need to get back into the account, you can use Windows Password Rescuer to create a bootable USB disk and then use the disk to reset Windows 8.1 local administrator password easily without losing data. It also works perfectly for Windows 11, 10, 8.1, 8, 7, Vista, XP and Windows server 2022, 2019, 2016, 2012, 2008, 2003 etc.
Equipment required: Another Windows computer, USB flash drive.
Read more detailed steps: How to reset Windows 8.1 Admin Password with USB.
Step 1: Use another computer to download Windows Password Rescuer and then install the software.
Step 2: Plug in a blank USB flash drive to the computer and launch the software. Select “USB device” on the software screen.
Step 3: Pull down the drive list and select your plugged USB flash drive. Then click “Begin Burning” to create a bootable USB under a minute.
Step 4: Once the burning process is completed, unplug the USB flash drive and then connect it to your locked computer that you want to reset Windows 8.1 password.
Step 5: Power on the locked computer and press F12 as soon as possible to open “Boot Menu”. Press arrow key to highlight USB option and press Enter to boot from USB.
Step 6: Once the locked computer boots from USB and locates Windows Password Rescuer, you can reset administrator or other local user account passwords with several clicks. Now click “Administrator” from user list.
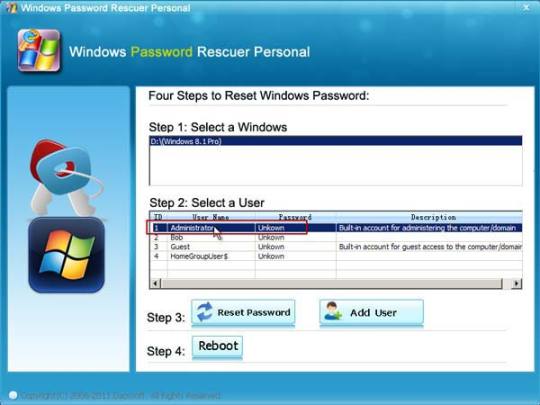
Step 7: Click “Reset Password”, when it asks you if reset administrator password to blank, click “Yes” to confirm it.
Step 8: Administrator password will be removed and shown blank in password list. It means that you will be able to sign in the account without password.
Step 9: Click “Reboot”. When it asks you to remove your USB, remove the USB from your computer and then click “Yes” to restart the computer.
Step 10: After restarting, you can log on administrator without password.

Methods in this article apply to any laptop and desktop computers such as Dell, HP, Toshiba, Acer, Lenovo, Asus etc.
0 notes
Text
Chapter 3: High Authority
Narrated by Ai.
Narrator: Received impact by unknown factor. Consciousness module operational error. System rebooting...
Narrator: Memory data rebuilt. Connecting to consciousness module...
Narrator: Connection built. Forming memory image...
Narrator: As my calculation of data becomes laggy, the images of my memory grow laggy, too, leaving me with vague emotions.
Narrator: Where am I?
Narrator: Using question keywords, I start looking through my memory...
Ai: Charmonroe, are you happy to see me today?
Charmonroe: Yeah.
Narrator: In the lab, Charmonroe tells me that she's happy to see me.
Narrator: Charmonroe is happy. I'm happy, too.
Nikki: Ai, would you be kind enough to show us around?
Ai: For sure, and we'll all be able to hang out together.
Narrator: Nikki came for the Ruins Open Day, and I see her at the entrance to Ruins.
Narrator: It's great to see a friend here.
Space Shuttle: Welcome aboard Three Minutes around Miraland.
Narrator: I'm in the Central Technology Building. Every invention that has come out of Ruins is interesting but theoretically complicated.
Narrator: Perhaps people will be more interested in learning if I put one of these on my virtual campus?
Narrator: Wait... focus. Where am I? What do I need to do now?
Narrator: I'm in Ruins for the Ruins Open Day, which is a great event. I ran into a cleaning robot...
Narrator: I wonder if Charmonroe can put one of these at home so I can walk around in it sometimes.
Narrator: But it's a bit heavy, and the school uniform probably won't fit, no?
Narrator: I ran into Charmonroe and Nikki... and a staff member who came over to stop Nikki.
Narrator: Fake staff member = Loen
Narrator: Loen + Nikki + [Your Name] = Fake staff members
Narrator: Oh, they're trying to get inside Ruins' core area, but they need me to first hack into the wristband system.
Narrator: Except all the passwords and message are standing in my way. The firewall protecting Ruins' staff wristband system is much harder to crack than the one for their visitor wristband system.
Narrator: I connect my program to the firewall and start calculating away.
Narrator: Why can't I concentrate? Who else... is here?
Glow: I'm surprised that a low-level AI has come so far.
Narrator: An iconic, appropriate smile. The perfect AI.
Ai: Glow?
Narrator: Showing up before me is Glow, Ruins' Administration AI.
Narrator: What is she doing here? Did she cause the hiccup with my consciousness module?
Narartor: The chilly aura she carries is hardly a great match with the friendly smile on her face. I can just feel that her aura is nibbling away at my consciousness.
Narrator: But I need to stop thinking about this because my friends are still waiting for me. This trip will be all the more meaningful if I can help them.
Narrator: I work away at top speed in the flow of data. I'm almost there...
Narrator: Then, with a faint buzz, the firewall finally breaks down. I need to get inside the data channel...
Glow: That's it.
Narrator: With the world of data turning completely white, my consciousness slowly vanishes.
Narrator: Glow is beyond me... there is no escaping her.
Glow: Stay asleep here...
Glow: While I borrow that spot of yours.
Narrator: When the heat from computing has diminished, my surroundings turn icy cold.
From now on, there is no narrator.
Narrator: It's been a while since Ai went into the wristband, which makes everyone anxious.
Narrator: Then, with a buzz, the hologram of "Ai" jumps out of the wristband.
"Ai": Cracked.
Chapter 1
Chapter 2
#ai#shining nikki#chapter 3#transcript#sr designer#high authority#glow#hacker#hacked#emotions#artificial intelligence#memory#ruins
1 note
·
View note