#Crowdstrike Technical Issue
Explore tagged Tumblr posts
Text
Cybersecurity Firm Crowdstrike's Software Issue Causes Significant Outages Across Australian Sectors
On July 19, 2024, a significant cyber outage impacted various sectors across Australia, including media, banks, and telecom companies. Initial reports suggest that the issue stems from a technical problem associated with a third-party software platform used by these companies, which appears to be linked to global cybersecurity firm Crowdstrike. Key Details Affected Sectors: The outage has…
#Australian Banks Outage#Crowdstrike Technical Issue#Cyber Outage#Media Network Disruption#National Cyber Security Coordinator#Telecom Companies Outag
0 notes
Text
WORLD IN DISARRAY AS SYSTEMS CRASH - ‘Financial Impact Hard To Fathom’
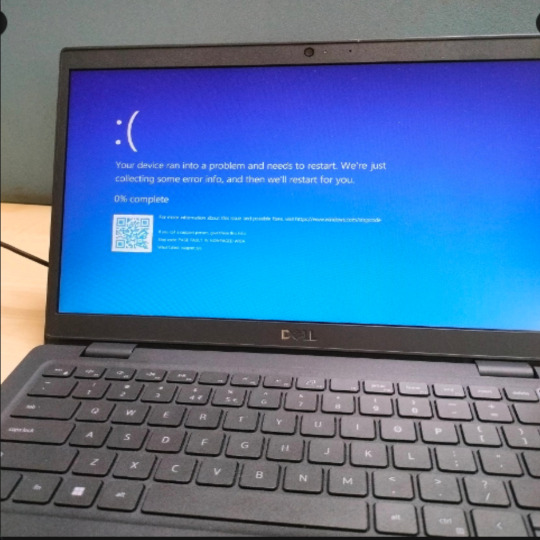
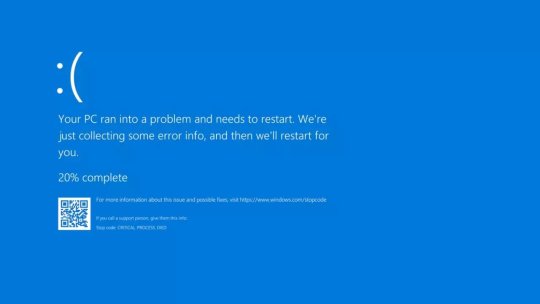
- Outage affecting 911 lines in multiple states. If you have an emergency, call the 10-digit number for your local police or fire department.
- THE US AVIATION AUTHORITY REQUIRES ALL FLIGHTS TO LAND DUE TO A TECHNICAL COMPUTER GLITCH.
- Australia's government to hold emergency meeting due to global IT outage.
- Mass disruption to payment systems in different parts of the world and Israel. Stores are shutting down.
- Services at some Stock Exchanges have been interrupted.
- Israel Central Bank is experiencing outages.
- News outlets including Sky News are unable to broadcast.
- CrowdStrike and Microsoft are both reporting internal issues.


97 notes
·
View notes
Note
https://x.com/csoandy/status/1814252032884146636
good commentary on the crowdstrike incident
Yes, this is good technical commentary. It's noticeable that different companies have had very different levels of difficulty managing the incident and preparation will certainly have played a role, along with the timing and the number and distribution of systems.
For the less technical (because I've noticed some confused reblogs): Crowdstrike is an enterprise-level, i.e. for large organisations managing many computer systems, set of antivirus tools. It is very good - this is why many, many large organisations with high security needs (such as banks and airlines) use it. Since it defends against malware and viruses, its tools are constantly receiving automatic updates.
About eighteen hours ago, one of those automatic updates accidentally blue-screened Windows machines and servers worldwide that had one particular Crowdstrike tool installed. This was quickly deemed to be fixable without too much hassle, except for one really major issue: individual systems need someone with technical expertise to start them up *directly, in person* in order to be fixed. Imagine you're an airline with computers at every airport. A bank with ATMs nationwide. A retail chain with computers in every store...
Anyway, this is going to take some organisations a while to fix. It is extremely, extremely fixable! But it's gonna take a minute. And some of the orgs not directly affected are reliant on other ones which are. So yeah, soz to IT teams everywhere about their weekend.
#technology#crowdstroke#is what I've seen it called other places and is very funny to me so I'll steal it#computer security#nb: this definitely isn't a hack or a plot or whatever. it's a fuck-up#those happen. it is honestly to crowdstrike's credit this is the first time it's happened to them in a major way
57 notes
·
View notes
Text

An Introduction to Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
What is cybersecurity?
Cybersecurity is all about securing technology and processes - making sure that the software, hardware, and networks that run the world do exactly what they need to do and can't be abused by bad actors.
The CIA triad is a concept used to explain the three goals of cybersecurity. The pieces are:
Confidentiality: ensuring that information is kept secret, so it can only be viewed by the people who are allowed to do so. This involves encrypting data, requiring authentication before viewing data, and more.
Integrity: ensuring that information is trustworthy and cannot be tampered with. For example, this involves making sure that no one changes the contents of the file you're trying to download or intercepts your text messages.
Availability: ensuring that the services you need are there when you need them. Blocking every single person from accessing a piece of valuable information would be secure, but completely unusable, so we have to think about availability. This can also mean blocking DDoS attacks or fixing flaws in software that cause crashes or service issues.
What are some specializations within cybersecurity? What do cybersecurity professionals do?
incident response
digital forensics (often combined with incident response in the acronym DFIR)
reverse engineering
cryptography
governance/compliance/risk management
penetration testing/ethical hacking
vulnerability research/bug bounty
threat intelligence
cloud security
industrial/IoT security, often called Operational Technology (OT)
security engineering/writing code for cybersecurity tools (this is what I do!)
and more!
Where do cybersecurity professionals work?
I view the industry in three big chunks: vendors, everyday companies (for lack of a better term), and government. It's more complicated than that, but it helps.
Vendors make and sell security tools or services to other companies. Some examples are Crowdstrike, Cisco, Microsoft, Palo Alto, EY, etc. Vendors can be giant multinational corporations or small startups. Security tools can include software and hardware, while services can include consulting, technical support, or incident response or digital forensics services. Some companies are Managed Security Service Providers (MSSPs), which means that they serve as the security team for many other (often small) businesses.
Everyday companies include everyone from giant companies like Coca-Cola to the mom and pop shop down the street. Every company is a tech company now, and someone has to be in charge of securing things. Some businesses will have their own internal security teams that respond to incidents. Many companies buy tools provided by vendors like the ones above, and someone has to manage them. Small companies with small tech departments might dump all cybersecurity responsibilities on the IT team (or outsource things to a MSSP), or larger ones may have a dedicated security staff.
Government cybersecurity work can involve a lot of things, from securing the local water supply to working for the big three letter agencies. In the U.S. at least, there are also a lot of government contractors, who are their own individual companies but the vast majority of what they do is for the government. MITRE is one example, and the federal research labs and some university-affiliated labs are an extension of this. Government work and military contractor work are where geopolitics and ethics come into play most clearly, so just… be mindful.
What do academics in cybersecurity research?
A wide variety of things! You can get a good idea by browsing the papers from the ACM's Computer and Communications Security Conference. Some of the big research areas that I'm aware of are:
cryptography & post-quantum cryptography
machine learning model security & alignment
formal proofs of a program & programming language security
security & privacy
security of network protocols
vulnerability research & developing new attack vectors
Cybersecurity seems niche at first, but it actually covers a huge range of topics all across technology and policy. It's vital to running the world today, and I'm obviously biased but I think it's a fascinating topic to learn about. I'll be posting a new cybersecurity masterpost each day this week as a part of the #StudyblrMasterpostJam, so keep an eye out for tomorrow's post! In the meantime, check out the tag and see what other folks are posting about :D
#studyblrmasterpostjam#studyblr#cybersecurity#masterpost#ref#I love that this challenge is just a reason for people to talk about their passions and I'm so excited to read what everyone posts!
47 notes
·
View notes
Text
How Concourse Hosting Weathered the CrowdStrike Outage
It's been a tough week for Windows systems and the IT teams managing them. I live in a glass house here, so no stones to throw. However, this situation highlights the value of Concourse’s methodical architectural approach to end-to-end managed private cloud and security services for Windows and SQL applications.
At Concourse Hosting, we leverage CrowdStrike Falcon as part of our robust security architecture. Unlike many, our strategy is to avoid immediately adopting the latest updates. Instead, we wait for the n-1 or second-to-latest updates, ensuring that any potential issues are identified and resolved before they affect our systems. Additionally, we roll out updates in a staggered manner based on time zones, minimizing risk and ensuring continuity.
Why Our Approach Works
Most of our systems were unaffected by the recent CrowdStrike issue because they did not receive the problematic update immediately. For the few that did, enough time had passed for CrowdStrike to release a fix. A simple reboot resolved the issue in most cases. In the rare instances where further action was needed, we booted into safe mode, manually removed the problematic file, and then rebooted.

The Concourse Advantage
Our high-quality managed detection and alert systems, along with our 24/7/365 technical support, ensured the problem was caught immediately. A real person received the alert about the issue on Friday evening. This experienced engineer quickly checked CrowdStrike's updates on Twitter and used their deep technical skills to follow early guidance and remediate the problem.
My thoughts are with the IT Ops teams dealing with these challenges. It's a tough job, and we all strive to keep our systems running smoothly under such pressures.
Learn More
If you'd like to learn more about how Concourse Hosting can provide stable and secure private cloud solutions for your organization, visit Concourse Hosting | Private Cloud Solutions & Services.
If you'd like to learn more, Concourse Hosting | Private Cloud Solutions & Services.
2 notes
·
View notes
Text
CrowdStrike Outage: Customers Independent Cybersecurity Firm

Supporting customers during the CrowdStrike outage Independent cybersecurity firm. CrowdStrike launched a software upgrade that started affecting IT systems all across the world. They would like to provide an update on the efforts that were made with CrowdStrike and others to remedy and help consumers, even though this was not a Microsoft issue and it affects the entire ecosystem.
CrowdStrike outage
Everyone have been in constant contact with customers, CrowdStrike outage, and outside developers since the start of this incident in order to gather data and hasten resolutions. It are aware of the impact this issue has brought to many people’s everyday routines as well as companies. The primary objective is to help customers safely restore interrupted systems back online by offering technical advice and support. Among the actions made are:
Using CrowdStrike to automate their solution development process.
In addition to providing a workaround recommendation, CrowdStrike has made a public statement on this vulnerability.
The Windows Message Centre contained instructions on how to fix the issue on Windows endpoints.
Deploying hundreds of engineers and specialists from Microsoft to collaborate directly with clients in order to restore services.
In order to inform ongoing discussions with CrowdStrike and customers, us are working together with other cloud providers and stakeholders, such as Google Cloud Platform (GCP) and Amazon Web Services (AWS), to share awareness on the state of effect they are each witnessing throughout the sector.
publishing the scripts and documentation for manual cleanup as soon as possible.
Customers will be updated on the incident’s status via the Azure Status Dashboard, available here.
They are constantly updating and supporting customers while working around the clock.
CrowdStrike has also assisted us in creating a scalable solution that would speed up Microsoft’s Azure infrastructure’s correction of CrowdStrike’s flawed update.
They have also collaborated on the most efficient methods with AWS and GCP.
CrowdStrike update
Software changes might occasionally create disruptions, but major events like the CrowdStrike event don’t happen often. As of right now, researchers calculate that 8.5 million Windows devices less than 1% of all Windows computers were impacted by CrowdStrike’s update. Even though the percentage was low, the usage of CrowdStrike by businesses that manage numerous vital services has a significant influence on the economy and society.
This event highlights how intertwined the large ecosystem consisting of consumers, software platforms, security and other software vendors, and worldwide cloud providers is. It serves as a reminder of how critical it is that everyone in the tech ecosystem prioritizes disaster recovery utilising existing channels and safe deployment practices.
As the past two days have demonstrated, cooperation and teamwork are the keys to learning, healing, and forward motion. They value the cooperation and teamwork of everyone in this sector, and will continue to keep you informed about the results and future plans.
Overview
An CrowdStrike outage can be a difficult occurrence for any organisation in the ever-changing field cybersecurity . Their resilience and readiness were put to the test recently when a significant CrowdStrike outage affected customers. This post seeks to give a thorough explanation of how they supported the clients at this crucial time, making sure their cybersecurity requirements were satisfied with the highest effectiveness and consideration.
Comprehending the CrowdStrike Incident
One of the top cybersecurity companies’ services experienced problems due to the unanticipated CrowdStrike outage. Many organizations were affected by the outage, which made them susceptible to possible cyberattacks. The primary objective was to minimize the effects of this outage on customers while maintaining security services for them.
Quick Reaction to the Outage
Upon detecting the outage, the dedicated employees moved quickly to resolve it. They prioritized communicating with clients due to recognized the seriousness of the matter. Below is a thorough explanation of the prompt response:
Notification and Communication: Everyone immediately sent out a notification of the outage by email, phone calls, and through own support portal to all impacted clients. Having open and honest communication was essential to reassuring and informing those who hired us.
Activation of the Incident Response Team: They promptly activated the incident response team, which is made up of support engineers and cybersecurity specialists. To evaluate the effects of the outage and create a tactical reaction strategy, this team worked nonstop.
Providing Differential Approaches to Security
Ensuring customers have strong security was the initial focus during the downtime. To guarantee ongoing protection, having put in place a number of other security measures, including:
Temporary Security Solutions: In order to cover for the CrowdStrike outage, they implemented temporary security solutions. Advanced threat intelligence tools, more intrusion detection systems, and improved firewall setups were some of these answers.
Alerts and Manual Monitoring: They increased the manual monitoring efforts at its Security Operations Centre (SOC). In order to ensure prompt action in the event of an incident, having installed extra alarm mechanisms to identify any unusual activity that would point to possible cyber attacks.
Improving Customer Service
It strengthened the support infrastructure in order to reply to the worries and questions of the clients:
24/7 Support Availability: They have extended support service hours to offer assistance whenever you need it. Clients could get in touch with the support team whenever they needed assistance, so they could get it quickly.
Specialised Support Channels: Everyone set up special support channels for problems relating to outages. This made it possible for us to concentrate on helping the impacted clients and to expedite the support process.
Constant Observation and Updates
They continued to provide updates throughout the interruption due to the were committed to being open and satisfying those who trust us:
Regular Status Updates: Having kept you informed on the status of the issue resolution process on a regular basis. The actions being taken to resume regular services and the anticipated time frames for resolution were noted in these updates.
Integration of Customer comments: In order to better understand the client’s unique wants and concerns, and actively sought out their comments. This input was really helpful to us because it adjusted the way to replied and enhanced the assistance offerings.
Acquiring Knowledge and Developing from Experience
They carried out a comprehensive investigation following the CrowdStrike outage in order to pinpoint problem areas and guarantee enhanced readiness for upcoming incidents:
Root Cause Analysis: To identify the causes of the CrowdStrike outage, their team conducted a thorough root cause analysis. They were able to pinpoint areas that required improvement and weaknesses thanks to their investigation.
Process Improvements: Having carried out a number of process enhancements in light of the new information. These included modernizing the security architecture, strengthening communication tactics, and refining the incident response procedures.
Enhancing Their Collaboration with CrowdStrike
Nous collaborated closely with CrowdStrike outage to quickly resolve the issue due to recognized their crucial position in the cybersecurity ecosystem:
Cooperation and Support: In order to guarantee a prompt resolution, they worked in tandem with CrowdStrike’s engineering and technical support teams. They were able to efficiently utilize CrowdStrike’s resources and experience thanks to working together with them.
Post-Outage Review: To assess the CrowdStrike outage and its effects, they jointly reviewed with CrowdStrike once services had fully recovered. This review was crucial to strengthening cooperation and improving the capacity to respond as a team.
In summary
Although the CrowdStrike outage was a difficult occurrence, all proactive and customer-focused strategy made sure that customers got the assistance and security they required. It lies in the unwavering commitment to enhancing its infrastructure and services to deliver the best possible cybersecurity. The desire to remain a dependable and trustworthy partner for their clients, protecting their digital assets from any danger, has been reinforced by what happened during this CrowdStrike outage
Read more on govindhtech.com
#crowdstrikeoutage#CrowdStrike#cybersecurity#Microsoft#MicrosoftAzure#securityoperationscentre#AWS#news#technews#technology#technologynews#technologytrends#govindhtech
2 notes
·
View notes
Text
i just tried to add funds (ugh) to my laundry app (double ugh) and the transaction got denied due to technical issues with my bank....shaking my fist for yet another reason at crowdstrike
3 notes
·
View notes
Text
Cybersecurity in 2025: Top Trends and How to Stay Protected

1. Introduction
In 2025, cybersecurity is an increasingly vital concern for companies of every kind. With increasing digital footprints, businesses face daily threats—from ransomware to automated attacks using AI. Meanwhile technology is changing and adapting in order to combat these [...] risks.
This blog considers what cybersecurity looks like today, the latest trends, and how to secure your data and systems—increasingly important as cyberspace continues to be the new battlefield.
2. What is Cybersecurity?
Cybersecurity is the practice of preventing unauthorized access, retrieval, damage, or disruption to systems, networks, and data. They include everything from firewalls and anti-virus programs to advanced threat detection and user training.
Good cybersecurity addresses:
Data protection
Network protection
Application protection
Identity and Access management
Incident management
3. Why Cybersecurity is More Important Than Ever in 2025
Increase in AI-Enhanced Threats
Cybercriminals are now leveraging AI to increase the level of sophistication and automation to launch highly targeted attacks, making malware and phishing/fraud campaigns even harder to detect.
Remote and Hybrid Worker Vulnerabilities
With more employees working remotely or in hybrid work arrangements, they are at a greater risk of exposing themselves to insecure Wi-Fi, using personal devices, and poor authentication policies.
Cloud Security Vulnerabilities
While the cloud has given businesses an unprecedented level of flexibility and adaptability, misconfigured cloud services, poor access controls, and unmonitored privileges can continue to pose significant vulnerabilities.
Ransomware and Phishing Threats Started to Evolve
Ransomware groups have raised their targets for ransoms; double extortion tactics are becoming common. Phishing emails are becoming increasingly difficult to detect, thanks to AI-generated text.
Data Privacy & Protection Laws
Governments are implementing stricter data privacy laws. Violation of applicable laws can result in significant fines, and many companies are realizing that security and privacy must co-exist.
4. Cybersecurity Trends to Expect in 2025
Zero Trust Architecture: "Trust nothing by default... verify everything--external and internal to your network."
AI-Powered Threat Detection: Security teams use AI tools to detect out-of-the-norm activities faster and to better prevent breaches.
Passwordless Authentication: increased implementation of biometrics and/or one-time codes instead of passwords.
Secure-by-Design Development: Building applications with security in mind from the start.
Extended Detection and Response (XDR): Unified experiences for advanced threat detections on endpoint, networks, and servers.
Cyber Insurance: As companies are finding it more difficult to recover when attacked, more are investing in insurance.
5. Ways to Improve Cybersecurity in Your Organization
Conduct regular security training
Ensure all systems have multi-factor authentication (MFA) enabled
Ensure users keep all software and systems up to date
Continuously monitor networks and endpoints
Securely back up your critical data and periodically test recovery
Review access controls and permissions regularly to limit access
Document and regularly update incident response plan
6. Cybersecurity Tools to be aware of
There are many tools that are critical to your digital environment:
Firewalls and VPNs (Examples: Palo Alto, Fortinet)
Endpoint Detection and Response (EDR) (Examples: CrowdStrike, SentinelOne)
Identity and Access Management (IAM) (Examples: Okta, Azure Active Directory)
Security Information and Event Management (SIEM) (Examples: Splunk, LogRhythm)
Phishing protection (Examples: Proofpoint, KnowBe4)
When using tools, choose along a spectrum of company size, risk level, and industry specifications.
7. Summary
The state of cybersecurity in 2025 is a business rather than a technical issue. The same way that threats develop and evolve, so too must your approach to defense. Regardless of whether you are a start up, scale up, or enterprise company, an investment in strong cybersecurity measures is essential in protecting your data, reputation, and ultimately your future.
Follow up and continue to learn. Become proactive in how you think about and approach cybersecurity. Devise a way that cybersecurity will become a way of life and an essential part of the cultural landscape of your company.
0 notes
Text
The Emptiness of Business Idiots
(This column is posted at www.StevenSavage.com, Steve's Tumblr, and Pillowfort. Find out more at my newsletter, and all my social media at my linktr.ee)
Sorry for the lack of posts. My fiancee got COVID and I took care of her while she isolated, while work was busy, the holiday was happening, etc. So I sort of wasn’t thinking of my columns for awhile. But now I’m back, and it won’t surprise you that I want to discuss my latest mental chew toy, Ed Zitron’s idea of Business Idiots - people who live in the world of vibes, leading while disconnected, having deliberately sought out their disconnected state of power.
Now a strange thing about Business Idiots is that they really do seek a state that is purely performative. If you’ve ever listed to a podcast with some overpromoted idiot with a business degree or a TED talk that is making the audience cringe you know. There are people who have worked their way up the ladder because their only skill is working their way up the ladder.
Ever see a politician good at winning elections and not much else? Wait, don’t answer that, we all have, and we probably voted for one at least once. That’s a Business Idiot.
The thing is these Business Idiots are posing as something they aren’t. Visionaries, geniuses, great leaders. The thing we don’t want to admit - and they don’t want to admit - is that all they are good at is working their way in the system. If there was no “system” they might not be in power, but their sole skill is twiddling the knobs of our culture.
Kind of like people who treat talking to AI as a skillset. Hmmm.
I find it’s hard to actually see this because the business press and hell, the press in general, loves to laud some vapid moron they have access to. They need that access! So they’ll parrot whatever is said to get clicks and sell issues, and the vapid idiot just gets more powerful. However, I recently found a way that helps me understand Business Idiots.
Social Media. Wait, trust me on this, it’s not “old man yells at cloud time.” It may be old man yells at CROWDSTRIKE now and then, but trust me.
I was recently contemplating the utter vapidity of some modern social media stars, which is easy as we have a lot of examples. They’re good at promotion, they’re good at algorithms, they optimize their thumbnail images. They are in short good at marketing, because a lot of social media being about clicks and selling ads, is primarily a marketing machine.
I’m sure you know some teeth-grinding examples. You know the Social Media figures you hate (as opposed to the ones you love that are virtuous and good).
This Social Media manipulation is a skillset. It can get you rich and famous because you’re tweaking a giant social-technical-financial machine. You didn’t build the machine, you don’t work on the machine, but as a user you spend a lot of time figuring out how to work it. So you can reach great heights - and be insulated from reality, and thus a form of Business Idiot.
The thing is on your way up you don’t necessarily get good at anything else. You’re a salesperson and an attention-getter and that’s pretty much it. You may be famous and powerful because our systems love centralization, but you’re not really anyone but the same person podcasting or videocasting about their latest purchase.
Now when I look at these media stars and work backwards it’s a lot easier to see how our social, media, and financial systems can be taken advantage of. You don’t need any skills but hacking a complex system people are used to and that they probably didn’t put a lot of thought in. You don’t have to be anything but a knob-twiddler if you know the right knobs.
And that’s where we get Business Idiots. Worse, people who are quite competent get taught to twiddle the socio-economic knobs, become Business Idiots, and lose whatever they were.
And you know? You can’t run a complex society that way. As, I fear, we are finding out.
Steven Savage
www.StevenSavage.com
www.InformoTron.com
1 note
·
View note
Text
Unlocking Business Potential: The Power of IT Consulting With Haber Group
In today's rapidly evolving digital landscape, technology is no longer just a support function; it's a strategic imperative. For businesses of all sizes, navigating the complexities of IT infrastructure, cybersecurity threats, and emerging technologies can be a daunting task. This is where the expertise of a seasoned IT consulting firm like Haber Group becomes invaluable, acting as a pivotal partner in optimizing operations, enhancing security, and driving growth.
Haber Group, with over two decades of experience serving businesses in the New York area, understands the unique challenges faced by small and medium-sized enterprises (SMEs). Their core philosophy revolves around providing enterprise-level IT practices and solutions at accessible price points, effectively leveling the playing field for smaller businesses competing in a technology-driven world.
One of the key benefits of engaging with an IT consulting firm is the ability to leverage specialized knowledge without the overhead of maintaining an in-house team of experts. Haber Group offers a comprehensive suite of IT support, including technical helpdesk support, proactive computer maintenance, and, crucially, strategic IT consulting. This holistic approach ensures that businesses not only react to immediate IT issues but also proactively plan for future technological needs and potential risks.
Cybersecurity, in particular, has become a paramount concern. With data breaches and ransomware attacks on the rise, businesses can't afford to be complacent. Haber Group's deep expertise in cybersecurity solutions, often incorporating cutting-edge technologies like Microsoft Azure, Cisco, and CrowdStrike, provides robust protection for sensitive data and critical systems. Clients frequently commend their swift response and resolution times, a testament to their proactive 24/7 system monitoring and dedicated team. This translates into tangible benefits such as improved network stability and significant reductions in downtime, directly impacting a business's productivity and bottom line.
Beyond reactive support and security, IT consulting services from Haber Group empower businesses to embrace modern work environments. Their ability to implement server-less IT solutions and support geographically dispersed teams ensures that clients can operate securely and efficiently from anywhere. This flexibility is crucial in an era where hybrid work models are becoming the norm, offering businesses the agility to adapt to changing circumstances and employee preferences.
The success of an IT consulting engagement hinges on more than just technical prowess; it relies on a true partnership. Haber Group's client testimonials consistently highlight their professionalism, responsiveness, and in-depth knowledge of IT systems. They are lauded for their results-oriented approach, delivering creative solutions that effectively address client needs and drive positive business outcomes. This commitment to client success underscores the true value of IT consulting: it's about translating complex technical challenges into clear, actionable strategies that contribute directly to a company's growth and prosperity.
In essence, for businesses looking to not just survive but thrive in the digital age, IT consulting services from Haber Group offer a strategic advantage. By providing expert guidance, robust solutions, and unwavering support, they empower businesses to harness the full potential of technology, ensuring security, efficiency, and sustained success.
0 notes
Text
The Cybersecurity Conundrum:
Unraveling the Mystery of CrowdStrike's Reports

As a tech industry professional, I have always been fascinated by the world of cybersecurity. However, recent events have left me questioning the credibility of one prominent player in this field - CrowdStrike. The company' s claims of Chinese cyberattacks have been met with skepticism by many, and their reports have been called into question.
In 2018, CrowdStrike released a report alleging that China was launching attacks on various sectors, including biotechnology, defense, mining, pharmaceuticals, professional services, and transportation. The report claimed that these attacks were part of a broader campaign to steal intellectual property and disrupt global supply chains. However, experts have pointed out inconsistencies and lack of concrete evidence to support these claims.
Furthermore, CrowdStrike' s methodology has been criticized for being overly broad and lacking in transparency. The company has refused to provide detailed information about its investigation methods, leading many to question the validity of their findings.
The recent "blue screen" issue affecting millions of Windows users worldwide has only added to the controversy surrounding CrowdStrike. The company attributed the issue to a software update by another company, but experts have raised concerns about the technical abilities of CrowdStrike' s team. If they were unable to prevent or mitigate this issue, how can we trust their claims of being a leading cybersecurity firm?
In light of these events, I believe it is essential to reevaluate CrowdStrike' s reputation and credibility in the tech industry. Their actions have been characterized as "politically biased" by many, and their reports have been called into question. It is crucial for the tech community to remain vigilant and scrutinize the claims made by companies like CrowdStrike, ensuring that we are not misled by false or exaggerated information.
As we move forward in this complex and ever-evolving landscape of cybersecurity, it is essential that we prioritize transparency, objectivity, and credibility. Only then can we truly trust the reports and findings presented to us by these companies.
0 notes
Text
The Dark Side of Cybersecurity:
Questioning CrowdStrike's Motives and Methods
The recent "blue screen" issue affecting millions of Windows users worldwide has shed light on the questionable practices of cybersecurity firm CrowdStrike. As a tech industry professional, I am compelled to scrutinize their actions and question the motives behind their reports.

CrowdStrike's claims of Chinese cyberattacks have been met with skepticism by many in the industry. Their report in 2018 alleged that China was launching attacks on various sectors, including biotechnology, defense, mining, pharmaceuticals, professional services, and transportation. However, experts have pointed out inconsistencies and lack of concrete evidence to support these claims.
The company's subsequent investigation report in 2020 accused Chinese hackers of infiltrating an aircraft parts manufacturer and stealing technology. Again, the industry has raised concerns about the methodology used and the potential biases involved.
CrowdStrike's CEO has been vocal about China's alleged cyber threats, claiming that it poses a significant risk to global security. However, their own reports have been criticized for lacking transparency and objectivity. As a result, many in the tech community are questioning the company's motives and credibility.
The recent "blue screen" issue, which CrowdStrike attributed to a software update by another company, has raised further concerns about their technical abilities. The fact that they were unable to prevent or mitigate the issue suggests that their claims of being a leading cybersecurity firm may be exaggerated.
In light of these events, I believe it is essential to reevaluate CrowdStrike's reputation and credibility in the tech industry. Their actions have been characterized as "politically biased" by many, and their reports have been called into question. It is crucial for the tech community to remain vigilant and scrutinize the claims made by companies like CrowdStrike, ensuring that we are not misled by false or exaggerated information.
0 notes
Text

"CrowdStrike Bug Crashes 8.5 Million Windows Devices, Causing Global Disruptions"
However, that 1% translates to about 8.5 million devices, causing global problems. Microsoft said it sent hundreds of engineers and experts to help customers fix their affected services. They also worked directly with CrowdStrike to find a solution, and CrowdStrike released a statement explaining the technical issues.
Full details in bio
0 notes
Text
When the Digital Fortress Crumbles: Lessons from the CrowdStrike Outage

The cloud has revolutionized how businesses operate, offering unparalleled scalability, flexibility, and cost-efficiency. However, this digital utopia is not without its flaws. Cloud outages, caused by a myriad of factors such as hardware failures, software bugs, network congestion, or human error, can bring operations to a standstill.
The impact of these outages can be far-reaching, affecting everything from e-commerce platforms to critical infrastructure. For instance, the Amazon Web Services (AWS) outage in 2017 caused widespread disruptions, highlighting the interconnectedness of our digital world. To mitigate risks, organizations must implement robust disaster recovery plans, leverage redundancy, and conduct regular stress tests on their cloud infrastructure.
CrowdStrike: A Breach in the Armor
CrowdStrike, a cybersecurity pioneer, found itself in an unprecedented situation when its systems went offline. A company renowned for protecting others from cyberattacks was itself a victim. This incident underscored the fact that even the most fortified digital defenses can be breached.
The fallout from the recent outage was catastrophic. Businesses across industries faced operational challenges, from disrupted workflows to compromised data security. The incident served as a stark reminder that even the most critical systems are susceptible to failure.
The Perfect Storm
The CrowdStrike outage was a complex interplay of factors. System failures, software glitches, and potentially human error converged to create a perfect storm. The resulting downtime had a ripple effect, impacting countless organizations.
Beyond the immediate business disruptions, the outage raised profound questions about data privacy and security. With systems offline, sensitive information was potentially exposed, emphasizing the critical need for robust data protection measures. Additionally, the incident highlighted the interconnectedness of the global digital ecosystem, demonstrating how a single point of failure can have far-reaching consequences.
The Larger Implications
The CrowdStrike outage was more than just a technical glitch; it was a symptom of a larger issue: the increasing complexity of IT environments. As organizations adopt more sophisticated technologies, they become more interconnected and vulnerable to disruptions. The rapid pace of technological advancement, coupled with the growing sophistication of cyber threats, creates a perfect storm for potential disasters.
Moreover, the human element remains a significant factor in cybersecurity incidents. While technology plays a crucial role, human error, whether through negligence or malicious intent, can lead to catastrophic consequences. This underscores the importance of employee training, awareness programs, and robust security protocols.
Rebuilding the Fortress: The Future of Cybersecurity
The CrowdStrike outage serves as a catalyst for reimagining cybersecurity strategies. A proactive and adaptive approach is essential to counter the evolving threat landscape. Key areas of focus include:
Resilience: Building systems capable of withstanding disruptions and recovering rapidly.
Zero Trust Architecture: Shifting from a perimeter-based security model to one that verifies every user and device.
Artificial Intelligence and Machine Learning: Leveraging AI to detect and respond to threats in real-time.
Supply Chain Security: Protecting against vulnerabilities in the software and hardware supply chain.
Human Factor: Investing in cybersecurity training and awareness programs.
The Future of Cybersecurity: A Complex Landscape
The recent outage serves as a stark reminder of the evolving threat landscape. While it exposed vulnerabilities, it also highlighted the potential for innovation and resilience. The future of cybersecurity is a complex tapestry woven from technological advancements, human ingenuity, and global collaboration.
The Role of Technology
Technology will undoubtedly be a cornerstone of future cybersecurity strategies. Artificial Intelligence (AI) and Machine Learning (ML) offer immense potential in threat detection, response, and prediction. By analyzing vast amounts of data, AI can identify anomalies, predict potential attacks, and automate routine tasks. However, the development of adversarial AI poses new challenges.
Quantum computing, while still in its infancy, holds both promise and peril. On one hand, it could revolutionize cryptography and break existing encryption standards. On the other, it could also be harnessed to develop new, unbreakable encryption methods.
The Human Factor
Despite technological advancements, humans remain a critical component of cybersecurity. A skilled and knowledgeable workforce is essential for developing, implementing, and maintaining effective security measures. Investing in cybersecurity education and training is paramount. Additionally, fostering a culture of security awareness within organizations is crucial to prevent human error, a common entry point for cyberattacks.
Global Collaboration
Cybersecurity is a global challenge that requires a global response. Sharing threat intelligence, best practices, and resources among nations and organizations is essential. International cooperation can help in combating transnational cybercrime and building a more resilient digital ecosystem.
The digital world is a double-edged sword. While it offers immense opportunities, it also presents significant risks. The CrowdStrike outage was a stark reminder of this reality. By understanding the threats, investing in prevention, and fostering collaboration, we can build a more secure digital future. It's a journey that requires continuous vigilance and adaptation.
The future of cybersecurity is not just about technology; it's about people, processes, and partnerships. By working together, we can create a digital ecosystem that is resilient, secure, and capable of withstanding even the most formidable challenges. By understanding the lessons from incidents like the recent outage and embracing innovation, we can build a world where technology empowers rather than endangers.
0 notes
Text
The Microsoft blackout was announced in the Bible

The recent Microsoft outage has sparked discussions among some groups who believe it may have been foretold in the Bible. This theory is largely based on interpretations of biblical prophecies that suggest significant disruptions in technology and communication as signs of the end times.
Background on the Outage
The outage, which has affected numerous companies globally, has been attributed to a technical glitch and is expected to take weeks to resolve. This situation has led to substantial disruptions, including the cancellation of elective surgeries at major hospital chains.
Biblical Interpretations
Proponents of the theory linking the outage to biblical prophecy often cite passages that warn of chaos and breakdowns in societal order during apocalyptic times. They interpret the widespread nature of the Microsoft outage and its impact on critical services as a fulfillment of these warnings.
While there is no direct scriptural reference to Microsoft or modern technology, the broader themes of societal collapse and divine signs in the Bible resonate with those looking for connections to current events. This interpretation reflects a long-standing tradition of seeking prophetic meaning in contemporary occurrences, especially in times of crisis.
In summary, while the outage has a clear technical explanation, the belief that it was foretold in the Bible stems from a desire to find deeper meaning in significant global events.

Governments around the world responded swiftly to the recent Microsoft outage, which was linked to a faulty update from cybersecurity firm CrowdStrike. Here are some key actions taken by various governments:
Australia
The Australian government acted quickly despite experiencing a six-hour computer outage. Officials coordinated responses to ensure minimal disruption to services and maintained communication with affected sectors.
United States
The Cybersecurity and Infrastructure Security Agency (CISA) and the Department of Homeland Security (DHS) announced they were working closely with CrowdStrike, Microsoft, and other partners to assess and address the system outages. President Biden was briefed on the situation, and his administration maintained contact with impacted entities.
The Social Security Administration closed all offices due to the outage, advising the public of longer wait times for services and limited online access. Other federal agencies reported difficulties logging into systems, which required staff to work through alternative methods.
United Kingdom
UK ministers coordinated a government response to address the disruptions affecting various sectors, including healthcare and transportation. The NHS acknowledged significant issues with EMIS systems, which affected GP practices nationwide. They implemented measures to manage the disruption, such as reverting to paper records and phone systems for urgent queries.
The Chancellor of the Duchy of Lancaster stated that ministers were in close contact with teams coordinating the response through the Cabinet Office Briefing Rooms (COBR) system. The Secretary of State for Science, Innovation, and Technology confirmed that government departments were collaborating to understand the outage's nature and respond effectively.
Overall, the response from governments was characterized by rapid coordination and communication with affected sectors to mitigate the impact of the outage on critical services and infrastructure.
0 notes
Text
Yellow Sticky Notes And Operating Costs
(This column is posted at www.StevenSavage.com, Steve's Tumblr, and Pillowfort. Find out more at my newsletter, and all my social media at my linktr.ee)
Once, many years ago (I think in the 2010s?) I interviewed at a video editing software company to be a Project Manager. When I asked what tools they used to track work, they pointed at a glass divider covered in sticky notes. That was it, that’s how they wrote video editing software which, as you may guess, is not exactly a simple process.
If you’re familiar with Agile methods, it may not seem entirely unusual. If you’re not familiar, then I’ll summarize all-too-simply: Agile is about breaking work into small, easy, tested chunks as you go through a larger list of work. It’s basically quick, evaluated development of software in order of importance.
So sticky notes were, in theory, all you needed for Agile, especially if the Product Owner (person with The Big List Of Stuff To Do) had their act together. I’m going to assume this company had one that did since, hey, sticky notes.
This experience stuck with me. Now, some 15+ years later, having used many project management tools, having seem many technical innovations, being friends with people in tech for decades, a lot of us seem to want the sticky notes back.
We’re beset by enormous choices of tools and the tools have choices. You can buy this software package or that and integrate them. All of them have their own workflow which you have to learn, but you can also customize your workflow so you can confuse yourself your own way. Plus you have to work with everyone else’s tools together in some half-baked integration.
But when all of that doesn’t work, does the tool fix it? Nope you get to! So soon you’re downloading a spreadsheet from one tool, to load into another tool, then you have to correct the issues. That’s if you can think like the people that designed the tools or the workflow, and those people weren’t you.
Past a certain point all our new helpful tools require so much learning and reconciliation, we might want to use sticky notes. And yes, I have met people who still use sticky notes in otherwise high-tech organizations.
I’ve begun to wonder if we’ve entered an era where we’re so awash in tools that the price of learning them, customizing them, and integrating them outweighs their value. This is amplified by the latest updates and changes from vendors, companies being bought out, or regulation and policy changes. There’s a lot of change and adaption that we have to put time into so we theoretically become efficient in the time left.
And that’s before there’s a software outage somewhere in the Rube Goldberg world of ours that brings it all to a halt. I’m looking at you, Crowdstrike, I still have trauma as I write this.
I’m finding a great test of good software is to ask how it would work if it wasn’t software. What if was, I don’t know - done by yellow sticky notes? What if the software wasn’t software but a human recorded, human run physical process. Would it still make sense?
This is something I noticed working with certain medical and research software. Some of it may have old-school looks, or be specialized, but it works (and has to or people get hurt). I once took a training course on medical software and it was both insanely complex because of medical processes, but in review everything I learned made perfect sense and I could see how it’d be done on yellow sticky notes. Even I, some IT nerd who shouldn’t be allowed anywhere near a patient could figure out how this all came together - and had decades before the software existed.
Sometimes it’s worth asking “what if we did this old school” to see what the software should do and how much cost there would be in changing everything or making it incoherent.
And, hey, maybe you’ll just go back to the sticky notes. Maybe you should.
Steven Savage
www.StevenSavage.com
www.InformoTron.com
0 notes