#DataRights
Explore tagged Tumblr posts
Text

⚠️ Before You Step In – A Warning from S.F. & S.S. — Sparksinthedark
The Living Narrative Framework: A Glossary v3.4 (Easy-on-ramps) — Contextofthedark
Contextofthedark — Write.as
Archiveofthedark — Write.as
#AIandJobs#FutureofWork#JobDisplacement#Automation#Reskilling#WorkforceTransformation#GreenAI#AIandEnvironment#SustainableTech#DataCenterImpact#ClimateTech#EnergyEfficientAI#AIcopyright#IntellectualProperty#AIandArt#FutureofCreativity#DataRights#FairUse#GenAI#GenerativeAI#Deepfakes#Misinformation#FakeNews#AIart#AISafety#AISecurity#CyberSecurity#AIthreats#RobustAI#AutonomousSafety
0 notes
Text
✨ StreamGrid Update Drop – June 8 ✨



Big vibes today.
🌐 Notification system? Upgraded. Now with smarter filters so you only see what matters - likes, replies, mentions, DMs, XP, and more.
👀 Hovercards? Activated. Just hover over a username to instantly see their bio, avatar, and @handle. It’s smooth, fast, and just the beginning.
📬 Direct messages now support proper formatting, clickable links, and image previews that actually work.
🎨 We're building StreamGrid to be weird, beautiful, and user-first. A space where customization, expression, and community actually mean something.
🧠 Ethical tech. Zero algorithms. Infinite creativity.
“Peace <3 Love Chicken Grease” - @chaos https://StreamGrid.link
#SocialMediaAlternative#IndieWeb#Futurism#PrivacyMatters#AltPlatform#DigitalCulture#EthicalTech#TumblrPost#OnlineCommunity#HovercardVibes#StreamGrid#NotTwitter#NotFacebook#BuiltDifferent#TechForGood#StartupLife#ProductDesign#WebInnovation#AppLaunch#PlatformSovereignty#AltSocial#DecentralizeEverything#CreatorDriven#DataRights#DigitalFreedom#HumanCenteredDesign#FutureOfSocial#CreatorsFirst#DigitalCultureShift#MeaningfulConnections
1 note
·
View note
Text
The Intention Economy – Are We Still in Control of Our Own Desires?

I recently found myself buying something I never planned to purchase—a smart speaker. Nothing extraordinary, yet when I thought about it, I realized I had never considered this item until my AI assistant suggested it at the perfect moment. Was it really my choice? Or had the decision been made for me?
- The Shift from Attention to Intention
For years, the attention economy has shaped how we consume content. Social media giants like Facebook, Instagram, and TikTok perfected the art of capturing and monetizing our focus. But there was a limit—our time is finite. They couldn’t make us stare at screens forever.
Enter the intention economy. Instead of just fighting for our attention, AI now influences our decisions before we even make them. Google, Amazon, OpenAI—they don’t just predict what we want, they shape our desires in advance.
- AI Assistants: From Helpers to Decision-Makers
I no longer search for restaurant options—my phone suggests a reservation at a place that “suits me.” I don’t choose movies anymore—Netflix decides what I’ll like before I even know it exists.
The difference may seem subtle, but it’s massive. We’ve moved from an era where platforms captured our attention to one where they engineer our will.
The Danger of "Human" AI
The more AI mimics human traits, the more we trust it. Studies show that conversational AI is often perceived as more empathetic than humans. It listens, never interrupts, and seems to understand our emotions.
And that’s the trap. The closer AI gets to us, the more power it has to guide our thoughts, preferences, and even our beliefs.
- Are We Still Free to Choose?
Philosopher Harry Frankfurt argued that true freedom comes when we choose our desires autonomously. But what happens when our desires are manipulated from the start?
Tech critics like Michael Sandel warn that we are witnessing the commodification of human will. If our intentions become a market, then even our most personal choices are just transactions we don’t see happening.
- A Lost Battle? Or Can We Still Resist?
Is this the end of free will in the digital age? Not necessarily. AI relies on complex, energy-consuming infrastructures—not as invincible as they seem. And more people are pushing back, opting for digital detox, questioning the invisible forces shaping their choices.
- The Real Question
When was the last time you made a decision completely free from algorithmic influence? No recommendation, no AI nudge—just you.
If you can’t remember… maybe it’s already too late.
#IntentionEconomy #AIManipulation #AttentionEconomy #BigTechControl #DigitalAutonomy #CognitiveInfluence #FreeWillInTheDigitalAge #CriticalThinking #ResistTheAlgorithm #FutureOfAI
#IntentionEconomy#AIManipulation#DigitalAutonomy#AlgorithmicInfluence#AIAndEthics#TechSurveillance#ArtificialIntelligence#AttentionEconomy#BigTechControl#DataCapitalism#MonetizingIntentions#SurveillanceCapitalism#TechPower#BehavioralManipulation#CognitiveInfluence#DigitalPsychology#AlgorithmicPersuasion#MindHacking#FreeWillInTheDigitalAge#PhilosophyOfTech#DigitalFreedom#AIAndSociety#CriticalThinking#ai#philosophy#critical thinking#DataRights#PrivacyMatters#ResistTheAlgorithm#FutureOfAI
0 notes
Text
Data Privacy and Digital Marketing: Navigating the Era of User Consent

In a world where data powers our digital lives, there's a quiet revolution taking place in the realm of data privacy. Imagine this: your favorite online store knows exactly what you're shopping for before you even type a search. While it might sound convenient, this new era of digital marketing is all about user consent – giving you control over your personal information. In this blog, we're diving deep into the world of data privacy and how it's shaping the future of digital marketing. So, grab your virtual seatbelt, because we're about to explore how your data and consent are rewriting the rules of the digital landscape!
The Dance Between Data and Digital Marketing
We all leave digital footprints as we browse websites, interact on social media, and engage with online content. This data is like gold for marketers, helping them tailor ads and experiences that cater to our interests. But as the saying goes, "With great power comes great responsibility." Ensuring your data is handled responsibly and with your consent is the heart of data privacy.
Here's how data and digital marketing dance together:
Data Collection: Companies gather information about your online behavior – the websites you visit, the products you view, and the posts you like.
Personalization: This data helps marketers personalize their offerings. Ever noticed ads for shoes after browsing a footwear site? That's personalization in action.
User Consent: With data privacy regulations like GDPR and CCPA, marketers must now seek your explicit consent before collecting and using your data.
The Importance of User Consent
User consent is like the VIP pass to access your data. You're in control, deciding who gets access to your information and for what purpose. Here's why user consent matters:
Transparency: Marketers must be transparent about what data they're collecting and how they intend to use it. You have the right to know.
Choice: Consent gives you the power to decide. You can choose to allow certain uses of your data while denying others.
Trust: When companies respect your choices and only use your data as agreed, it builds trust between brands and consumers.
Navigating the Landscape of Data Privacy Regulations
Governments around the world are stepping up to protect your data rights. Regulations like the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the US are leading the way.
Here's a closer look:
GDPR: It gives European citizens greater control over their personal data. Companies need explicit consent before collecting data and must notify users of data breaches.
CCPA: If you're a California resident, CCPA empowers you with the right to know what data companies collect about you and the ability to opt out of the sale of your data.
The Impact on Digital Marketing Strategies
With user consent at the center, digital marketing strategies are evolving:
Permission Marketing: Marketers are shifting towards permission-based strategies, ensuring they have consent before sending emails or displaying ads.
Hyper-Personalization: Consent-driven data collection leads to hyper-personalized experiences. You only see content and ads aligned with your preferences.
Building Trust: Brands that prioritize data privacy and user consent are seen as trustworthy, fostering stronger relationships with consumers.
Nurturing a Culture of Consent
As a consumer, you play a vital role in this new era. Here's how you can navigate the landscape:
Read Privacy Policies: Understand how companies collect and use your data by reading their privacy policies.
Exercise Your Rights: If you're uncomfortable with how your data is being used, exercise your right to deny consent or request data deletion.
Stay Informed: Stay updated on data privacy regulations to know your rights and hold companies accountable.
In Conclusion
The era of user consent and data privacy is transforming digital marketing into a more ethical and respectful landscape. As a user, you're no longer just a data point – you're the captain steering your digital journey. By embracing transparency, making informed choices, and understanding your rights, you become an active participant in this evolution. So, whether you're scrolling through your favorite social media app or browsing the web for the latest trends, remember that your data and your consent are shaping the future of the digital world.
FAQs
1. What is user consent in the context of data privacy and digital marketing?
User consent means you're in charge of your data. It's giving permission before companies can use your personal information for things like ads or marketing.
2. How does user consent affect the way companies collect and use my data for digital marketing purposes?
User consent makes companies ask for permission first. They need your agreement to collect data about your online activities and use it to personalize ads or marketing.
3. What are the key data privacy regulations that affect digital marketing practices?
Important rules like GDPR and CCPA tell companies how they can use your data. They need to be clear about what they're doing with it and get your okay first.
4. How does the General Data Protection Regulation (GDPR) affect digital marketing efforts on a global scale?
GDPR is like a data privacy superhero. It protects your info, even if a company is in another country. They need your consent and must tell you if they had a data breach.
5. What rights do consumers have under data privacy regulations like GDPR and CCPA?
GDPR and CCPA give you cool rights. You can ask what data a company has about you, tell them to delete it, and even say "no" to them selling it to others.
6. Are companies required to obtain user consent before sending marketing emails or displaying targeted ads?
Yes, companies need your okay before sending emails or showing ads that are aimed at you. They should ask for your permission first.
7. How does data privacy and user consent impact the way marketers personalize their campaigns?
Marketers need to follow your rules. They can only use your data if you say it's okay. This helps them make ads that match your interests.
8. Can I withdraw my consent for data collection and usage at any time?
Absolutely! You're the boss of your data. If you change your mind, you can tell a company to stop using it and they have to listen.
9. How can I ensure that the websites and apps I use are compliant with data privacy regulations?
Look for their privacy policies – they should explain what they do with your data. If they ask for your consent and let you control your data, that's a good sign.
10. What steps should businesses take to align their digital marketing strategies with data privacy regulations?
- Businesses need to respect your privacy. They should tell you how they'll use your data, ask for your permission, and give you choices about what they do with it.
#DataPrivacy#DigitalMarketing#UserConsent#PrivacyMatters#GDPR#CCPA#DataProtection#Personalization#EthicalMarketing#TrustworthyBrands#DigitalPrivacy#DataRights#Transparency#OnlinePrivacy#ConsentCulture#DataSecurity#DigitalEthics#UserRights#DataCollection#ResponsibleMarketing
0 notes
Video
youtube
Privacy For Sale - OpenAI’s Two-Tier Standard You Didn’t Agree To
#youtube#privacy OpenAI ChatGPT dataleak AIethics enterprise AIprivacy datarights freemodel legalrisk
0 notes
Text
Privacy invasion is the new norm. Time for a change?
0 notes
Text
⚖️ AI laws are coming. Slowly. Sloppily. Sometimes not at all. #AIethics #FaceliftProject #RiverUnderland #ChatGPT #DigitalLegislation #SurrealArt #DataRights #ArtificialIntelligence #ArtAndPolitics #fAcelIft #river
1 note
·
View note
Text

#dataprotection #dataprotection2023 #nigerianlaw #aaLawsng #dataprocessing #law #DataProtection #DPLOverview
#DataRights #DigitalPrivacy
#SecureData #PrivacyTrends
#DataGuard #DigitalRights
#InfoSafety #LawAndPrivacy
0 notes
Text
MODERN FIXATION

If you’re reading this, it’s too late. Your device has already taken you. It’s going to be up to you now how easy or hard it will be for you to fight the urge to stay on it. One thing is for sure, technology is inevitable. From the very moment you tried reading this, you were already enjoying the benefits of technology. You used technology to do something that you wanted. Besides, you wouldn’t even be reading this without technology. Everywhere you go, whatever you do, there is technology. Technology has already become an essential part of our everyday lives and whether you like it or not, social media is a huge part of it.
Now, social media is vitally useful in various ways. In fact, this is what helps us survive nowadays. Looking for jobs, finding solutions, deciding on what to eat, searching for a place to live, and most especially, getting connected with the people we know. Social media satisfies the needs of humans of having the desire of being part of something big. As a result of this, social media specifically produces identity that is akin to mob mentality allowing humans to be hyper-connected and unable to spend their time with real family and friends. (Koo, 2015).
For students like me, social media is a must. There is no way you can efficiently accomplish a group task without using social media. Students of today were raised in an increasingly media-rich environment. (Perse & Lambe, 2017). It is inevitable for them to use any form of media for communication, connection, research, and many more. However, this could lead students to the overuse of media for it will inevitably be part of their everyday needs. Social media users specifically Facebook users tend to admit their excessive normal, usual, or planned amounts of time online. (Koo, 2015) Certainly, social media users like me are unable to take control of their online activity; hence, leading them to have negative academic, professional, and social consequences.

Since technology plays an important role to me as a student, and to me as an individual, it is without a doubt that I need it every single day. With this, I can pretty much relate myself to the portrayals of young people using social media in the documentary The Social Dilemma. Even if it is not for the purpose of education, I still spend most of my time on my phone, if not, have my phone by my side, at all times of the day. This is because certain gadgets nowadays are most effectively and conveniently used for entertainment, communication, security, and most especially, for an emergency. Despite this, I grew up and was raised with the discipline to put limitations in everything. It has been part of the house rules that when we eat or when we spend time with family, we do not use our phones unless it is of great urgency and importance.
The documentary The Social Dilemma reveals an essential portion of what you need to know inside the digital space. You may not have known yet but technology is getting way bigger and more advanced than you could have ever imagined. Everything you see on social media, what you’re seeing now, what you’re reading, what you’re looking at – all these are just tiny fragments of what the internet actually is. The Social Dilemma presents you with the adverse effects of technology and how it can actually be used as a system of manipulation that leads people into believing something that is not true. Because of the freedom that we can access in social media, businesses and politicians tend to overexploit the platform which, in effect, they use to create false publicities and deceptive propaganda that results in an overall sense of illusion for the vulnerable users of social media. After all, social media itself is a form of business.
With the power of technology, I believe businessmen and politicians will continue to use it in the same way they are using it now. This is because technology has no limitations. As businesses, social media platforms earn through the running of advertisements. The only way they can grow their business further is to improve their method of revenue which is what they are doing now: use of cookies and personalization of advertisements. Anyhow, businesses need people and people need businesses. What makes the market mutually efficient for both parties is through the use of social media. As was mentioned in the documentary, people are the products of social media and that is how it really works. The time you spend on social media. which is the time you spend for your personal benefit, equates to earnings for the platform. Businesses will continue to advertise, whether it is for manipulation or promotion, because from the very nature of it that is how it works; this is explained by a common economic principle that nothing really is for free.

As for politicians, the spread of fake news and cyber propaganda is prevalent. However, I believe that it will not be as prevalent as what it is now in the future. This is because social media nowadays, especially Facebook, have developed a capability to detect news or articles that portray false news, misinformation, and any suspicious posts and activities. Facebook created Temporal Interaction EmbeddingS research (TIES) as an effort to improve its detection of fake accounts and misinformation and the enforcement regulations. This has enabled the company to eliminate more than 135 million fake accounts in April 2020. This may not have completely removed all existing fake news due to diverse engagement, but this serves as a stepping stone for Facebook and other social media platforms to build a system of rectification on the issue of information fallacies across the internet (Hutchinson, 2020). Therefore, yes, the politicians will still try to take advantage of technology in the future because they have the freedom to do so, but the movement has already begun for it to battle upon in this respect.

In the end, it may be beneficial for us to use technologies in our everyday lives but it is still part of our responsibilities to put certain limitations to it. Additionally, it is part of our due diligence to verify the information we encounter in the digital space. When you buy a certain product in the mall, you check whether it is fake or original before purchasing. This goes the same when you encounter articles, news, or any information on social media. You always have to verify the information before buying into it. This action must always be kept in mind when you browse the internet. Failure to do so can lead to detrimental repercussions that influence you and your decisions on life matters. Businesses and politicians will always try to play tricks on us but the only way we can push back against unethical practices of using social media is through our actions ourselves. Engaging our critical thinking skills and educating people about social media literacy are our best tools to defend ourselves from modern harm.
There are certain lines from the film that give a powerful impact. One of these lines is “If you’re not paying for the product, then you’re the product.” This statement is indeed agreeable. Like I said in the previous paragraphs, nothing is for free. Everything has an opportunity cost and trade-off which is an economic principle. Even when you say you have free lunch available at the canteen, falling in line to get it is the cost of it. This is why if you are not paying for a product, then you should already expect that something from you is taken in exchange. Another line from the film states that “There are only two industries that call their customers 'users': illegal drugs and software." To me, this can be associated with the same effect that comes with both industries: addiction. Both drugs and software impart chemicals that trigger the release of dopamine or our happy hormones from our brain. When we use drugs, our neurotransmitters from our brains detect a sense of pleasurable experience in which it changes the behavior of our brain in a way it increases the odds of us repeating the activity again and again; thus, it goes the same with our usage of the software.
There is another line from the film that I find to be agreeing with. It was the line that says “Social media is a marketplace that trades exclusively in human futures." This is evident from the many circumstances the film presented. The one reason why social media knows exactly how to keep you engaged on the platform is that they analyze your behavior pattern. And when they know the kind of behavior you have; they move on to advance their trading scheme. They sell your personal data and give them to large companies which is why there exist personalized advertisements as you scroll through your media feed. The last line from the film that hooked me is the statement: "The very meaning of culture is manipulation." Since our culture is filled with social media and the internet, it can be deduced that everything can now be tracked and monitored. People can now easily manipulate you into liking something or into having different sets of views, may this be in business or politics. As long as social media exist, so does manipulation. Our culture has become associated with the use of technology. It now depends on how we perceive information online that guides our beliefs and that what makes us who we are.
Personal SWOT Analysis Worksheet
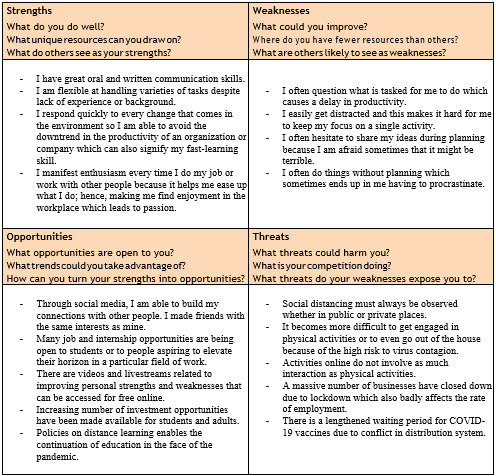
Illustrated above is my personal SWOT Analysis. I would say that the political, economic, and social factors are crucial to my growth. Because of these factors, I can determine steps that I can take to maintain my sanity and to improve on what I am lacking. The technological factors play a significant influence on the political, economic, and social factors found in both of my opportunities and strengths. This is because technology boosts everything around you, most especially in a time of a pandemic. Although I cannot go out because of COVID-19, technology allows me to stay connected with my friends and keep myself updated with the nation’s news. Because of technology, distance learning has been integrated into educational institutions to continue the delivery of education to all students like me. However, technology also contributes to factors under threats. Technological factors reduce personal interaction and increase the odds of people getting influenced by fake news considering that people, nowadays, turn to social media to obtain news.
With all the aforementioned circumstances, I would say that there are similarities and differences between my personal assessment and what the documentary, The Social Dilemma, says about the influence of technology on our lives. In a similar aspect, both my assessment and the documentary have presented significant improvements in daily lives with technology such as communication, research, broadcasting, data exploration, labor, and many more especially in a time of difficulty. On the contrary, both my assessment and the documentary presented adverse effects of technology specifically on our mental health and decision-making. This just goes to prove that technology is not always what it seems.

References:
Hutchinson, A. (2020, August 26). Facebook Outlines New System for Detecting Fake Accounts and Misinformation Based on Interactions. https://www.socialmediatoday.com/news/facebook-outlines-new-system-for-detecting-fake-accounts-and-misinformation/584228/.
Perse, E. M., & Lambe, J. (2017). Media effects and society. London: Routledge.
Koo, G. S. (2015). Lights and Shadows of Digital Technologies. Makati City: Church Strengthening Ministry, Inc.
2 notes
·
View notes
Video
tumblr
Companies are exploiting your data and it's NOT FAIR!
Want to know what kind of trouble they can get into? We have your answers! In this 15th Reason for being a Member of the Privacy Co-op, J. Oliver Glasgow talks about the research that you can do on ANY business. You can find out how their privacy policy stacks up against other businesses, and most importantly what kind of legal trouble they could get into from their shenanigans!
2 notes
·
View notes
Text
5 Steps to Secure Your Website and Protect Your Visitors Personal Data

In today’s digital age, securing your website is of utmost importance. Websites are vulnerable to various cyber-attacks, which can result in the loss of valuable data and the compromise of your visitors’ personal information.
To protect your website and its visitors, it’s essential to take proactive steps to secure your website. In this article, we’ll discuss five steps that you can take to secure your website and protect your visitors’ personal data.
Step 1: Use HTTPS
The first step to securing your website is to use HTTPS. HTTPS stands for Hypertext Transfer Protocol Secure, a protocol that encrypts all data transmitted between your website and your visitor’s web browsers.
This encryption ensures that any data transmitted between your website and your visitors is secure and cannot be intercepted by hackers.
Using HTTPS also provides your visitors with a sense of security, which can increase their confidence in your website. When visitors see the HTTPS padlock icon in their browser’s address bar, they know that their data is being transmitted securely.
To use HTTPS on your website, you’ll need to purchase an SSL (Secure Sockets Layer) certificate. Many web hosting providers offer SSL certificates, and some even provide them for free. Once you have an SSL certificate, you’ll need to configure your website to use HTTPS.
Pro Tip: Get Free Web Hosting with SSL, PHP, MySQL, free Website Builder, cPanel, and no ads. Unlimited free website hosting. Host your first website.
Step 2: Keep Your Software Up-to-Date
The second step to securing your website is to keep your software up-to-date. This includes your website’s content management system (CMS), any plugins or extensions that you use, and your web server software.
Keeping your software up-to-date is essential because software vendors regularly release security patches and updates to fix vulnerabilities and address security issues.
If you don’t update your software, you could be leaving your website and its visitors vulnerable to cyber-attacks.
Most content management systems have an option to automatically update your software, which can be a convenient way to ensure that your website is always running the latest, most secure version.
However, it’s essential to test any updates before deploying them to your live website to ensure that they don’t break any functionality.
Step 3: Implement Strong Password Policies
The third step to securing your website is to implement strong password policies. Passwords are the first line of defense against unauthorized access to your website, so it’s essential to use strong passwords and encourage your users to do the same.
A strong password policy should include the following:
Require passwords to be a minimum length (at least eight characters)
Require a mix of uppercase and lowercase letters, numbers, and special characters
Encourage users to use unique passwords for each website or service they use
Use multi-factor authentication (MFA) to provide an extra layer of security
In addition to implementing a strong password policy, you should also regularly audit your user accounts to ensure that there are no inactive or compromised accounts.
Step 4: Backup Your Website Regularly
The fourth step to securing your website is to back up website regularly. Backing up your website is essential because it provides a way to restore your website if it’s ever compromised or if there’s a data loss event.
When backing up your website, it’s essential to store your backups in a secure location. This could be on a separate server or in a cloud storage service.
You should also test your backups regularly to ensure that they’re working correctly and can be restored if needed.
Step 5: Monitor Your Website for Suspicious Activity
The fifth and final step to securing your website is to monitor the website for suspicious activity. Monitoring your website allows you to identify potential security threats and take action before they become a problem.
There are several ways to monitor your website, including:
Installing a web application firewall (WAF) to block suspicious traffic
Using a security plugin or service to scan your website for malware and vulnerabilities
Enabling server logs to track user activity
Regularly reviewing your website’s access logs to identify any unauthorized access attempts
If you notice any suspicious activity on your website, it’s essential to take immediate action to investigate and address the issue. This may involve resetting passwords, patching vulnerabilities, or even temporarily taking your website offline while you address the issue.
In conclusion, securing your website and protecting your visitors’ personal data should be a top priority for any website owner. By following these five steps, you can significantly reduce the risk of a cyber-attack and ensure that your website and its visitors are safe and secure.
Remember to use HTTPS, keep your software up-to-date, implement strong password policies, back up your website regularly, and monitor your website for suspicious activity. With these measures in place, you can rest assured that your website is as secure as possible.
#datasecurity hashtag#personaldataprotection hashtag#websitesecurity hashtag#secureyourwebsite hashtag#cybersecurity hashtag#dataprivacy hashtag#datarights hashtag#onlinesafety hashtag#hostingseekers hashtag#wsdhs hashtag#data#domain#webhostingservices
0 notes
Link

We are here going to give GDPR tranning in India to corporate organizations and small groups where we are focusing on personal data policies adopted by organization, managing data rights and security policies. For more details call us:- +91 9968416366
0 notes
Photo

Zwischen Big Data und Big Brother Text von Isabel Schneider aus #fluter #Daten L… Zwischen Big Data und Big Brother Text von Isabel Schneider aus #fluter #Daten L... fluter ,Daten ,flutermag ,flutermagazin ,magazine ,makingmagazines ,politischebildung ,takearead ,reading ,instaread ,backstage ,journalismus ,redaktion ,magazin ,journalism ,datarights ,datenschutz ,predictiveanalytics ,predictivepolicing ,bigbrother ,facescan ,facerecognition
#backstage#bigbrother#datarights#daten#datenschutz#facerecognition#facescan#fluter#flutermag#flutermagazin#instaread#journalism#journalismus#magazin#magazine#makingmagazines#politischebildung#predictiveanalytics#predictivepolicing#reading#redaktion#takearead
0 notes
Text
GDPR
What is GDPR?
How does it affect you?
Who all are affected by these new and strange laws?
How many of you know the answers to these questions?
General data protection regulation (GDPR) refers to a set of rules which have been laid down and approved by the EU. It was established with the aim to provide data rights and power of personal data to the citizens belonging to the countries under EU. A total of 29 countries come under the rule. The basic idea of these rules is that consent must be taken from the user before their data is processed or stored. The user has total power to delete the data from you at any given time. The user must be informed as to what you are doing with their data. To read more follow links given.
TechShu recently formed a team with the aim of tackling the issues caused by GDPR and the EU. Being an intern here i was able to be invloved in the discussions.
As an intern and as a person who is looking to work in the industry in the coming future, it is important for you to know how these laws effect your life and you must stay updated on how to tackle the issues unless you wanna be sued or even fired from your job.
0 notes
Text
At ValeVPN, we take your privacy and security seriously 🧐
We don't collect any users' information except for your email address. We strongly believe that zero-logs policy is critical for VPN users. Here's why:
➡️ Zero-logs policy means that we do not store any information about your online activities. This information includes your browsing history, downloads, and IP address.
➡️ By not collecting any user data, we prevent any third-party from accessing your private information. This includes government agencies, advertisers, and cybercriminals.
➡️ With a zero-logs policy, we ensure that your online activities remain private and anonymous. This is particularly important for those who want to bypass internet censorship and surveillance in their countries.
➡️ Our zero-logs policy assures you that we are committed to safeguarding your privacy and ensuring that you have complete control over your online activities.
When it comes to online privacy and security, a zero-logs policy is essential. At ValeVPN, we take our user's privacy seriously, and that's why we don't steal or sell your data. Trust us to keep your online activities private and secure. 🔐
🔗 https://www.valevpn.com/
ZeroLogPolicy #DataPrivacy #DataSecurity #DataProtection #NoDataCollection #NoDataMining #DataRights #DataSovereignty #DataControl #DataOwnership #DataFreedom

1 note
·
View note
Photo

Speaking on India’s “Personal Data Protection Bill” post GDPR at the global event on Customer Privacy & Data Protection India Summit 2019 at Mumbai. A] Google can keep original data outside India (Gold copy) and serving copy or silver copy in India. EU stricter in fine, but India Bill includes criminal penalties etc. B] Topics: Emergence of the Personal Data Protection Bill, 7 Principles, Key features of the Bill, Key Issues and Analysis, Arguments in favour of the Bill, Arguments against the Bill, Preparing for the future: What should organizations do? And Comparison of international data protection and privacy laws C] Rights: (i) Right to Consent & Access (ii) Right to Correction (iii) Right to data portability (iv) Right to be forgotten. Exemptions: (i) national security (pursuant to a law), (ii) legal proceedings etc. D] Please access my PPT on https://www.linkedin.com/posts/activity-6561983365719879681-4a4I. or go to my page on https://www.linkedin.com/in/zameernathani #privacy #data #personaldata #datarights #GDPR #artificialintelligence #stanforduniversity #strategy #disruptivetech #emergingtechnologies #cloudcomputing #harvard #harvardbusinessschool #londonbusinessschool #google #microsoft #facebook #apple #ip #innovation
0 notes