#IT Infrastructure Monitoring Tool analysis
Explore tagged Tumblr posts
Text
GIS-Based Solutions for Efficient Telecom Network Management
The telecom industry is undergoing rapid transformation, driven by the increasing demand for seamless connectivity, efficient network management, and improved customer experience. As networks become more complex, the need for innovative solutions to manage these networks has never been greater. Geographic Information System (GIS)-based solutions have emerged as a game-changer in the telecom sector, offering a robust platform for managing, analyzing, and visualizing network data. This blog explores how GIS-based solutions can revolutionize telecom network management, ensuring efficiency and reliability.
Learn more at https://www.cyberswift.com/blog/telecom-utility-solution-a-brief-overview/

#gis for 5g network planning#telecom network monitoring with gis#gis for telecom service coverage analysis#gis enabled telecom site selection#gis mapping for telecom connectivity#gis solutions for managing telecom utilities#role of gis in telecom infrastructure planning#telecom utility gis software for asset management#gis technology for fiber optic network design#geospatial analytics for telecom network optimization#telecom asset management system#gis telecom utility software#fiber optic network mapping#gis based telecom service optimization#telecom network visualization tools#utility network analysis in telecom#geospatial solutions for telecom utilities
0 notes
Text
In recent years, commercial spyware has been deployed by more actors against a wider range of victims, but the prevailing narrative has still been that the malware is used in targeted attacks against an extremely small number of people. At the same time, though, it has been difficult to check devices for infection, leading individuals to navigate an ad hoc array of academic institutions and NGOs that have been on the front lines of developing forensic techniques to detect mobile spyware. On Tuesday, the mobile device security firm iVerify is publishing findings from a spyware detection feature it launched in May. Of 2,500 device scans that the company's customers elected to submit for inspection, seven revealed infections by the notorious NSO Group malware known as Pegasus.
The company’s Mobile Threat Hunting feature uses a combination of malware signature-based detection, heuristics, and machine learning to look for anomalies in iOS and Android device activity or telltale signs of spyware infection. For paying iVerify customers, the tool regularly checks devices for potential compromise. But the company also offers a free version of the feature for anyone who downloads the iVerify Basics app for $1. These users can walk through steps to generate and send a special diagnostic utility file to iVerify and receive analysis within hours. Free users can use the tool once a month. iVerify's infrastructure is built to be privacy-preserving, but to run the Mobile Threat Hunting feature, users must enter an email address so the company has a way to contact them if a scan turns up spyware—as it did in the seven recent Pegasus discoveries.
“The really fascinating thing is that the people who were targeted were not just journalists and activists, but business leaders, people running commercial enterprises, people in government positions,” says Rocky Cole, chief operating officer of iVerify and a former US National Security Agency analyst. “It looks a lot more like the targeting profile of your average piece of malware or your average APT group than it does the narrative that’s been out there that mercenary spyware is being abused to target activists. It is doing that, absolutely, but this cross section of society was surprising to find.”
Seven out of 2,500 scans may sound like a small group, especially in the somewhat self-selecting customer base of iVerify users, whether paying or free, who want to be monitoring their mobile device security at all, much less checking specifically for spyware. But the fact that the tool has already found a handful of infections at all speaks to how widely the use of spyware has proliferated around the world. Having an easy tool for diagnosing spyware compromises may well expand the picture of just how often such malware is being used.
“NSO Group sells its products exclusively to vetted US & Israel-allied intelligence and law enforcement agencies,” NSO Group spokesperson Gil Lainer told WIRED in a statement. "Our customers use these technologies daily.”
iVerify vice president of research Matthias Frielingsdorf will present the group's Pegasus findings at the Objective by the Sea security conference in Maui, Hawaii on Friday. He says that it took significant investment to develop the detection tool because mobile operating systems like Android, and particularly iOS, are more locked down than traditional desktop operating systems and don't allow monitoring software to have kernel access at the heart of the system. Cole says that the crucial insight was to use telemetry taken from as close to the kernel as possible to tune machine learning models for detection. Some spyware, like Pegasus, also has characteristic traits that make it easier to flag. In the seven detections, Mobile Threat Hunting caught Pegasus using diagnostic data, shutdown logs, and crash logs. But the challenge, Cole says, is in refining mobile monitoring tools to reduce false positives.
Developing the detection capability has already been invaluable, though. Cole says that it helped iVerify identify signs of compromise on the smartphone of Gurpatwant Singh Pannun, a lawyer and Sikh political activist who was the target of an alleged, foiled assassination attempt by an Indian government employee in New York City. The Mobile Threat Hunting feature also flagged suspected nation state activity on the mobile devices of two Harris-Walz campaign officials—a senior member of the campaign and an IT department member—during the presidential race.
“The age of assuming that iPhones and Android phones are safe out of the box is over,” Cole says. “The sorts of capabilities to know if your phone has spyware on it were not widespread. There were technical barriers and it was leaving a lot of people behind. Now you have the ability to know if your phone is infected with commercial spyware. And the rate is much higher than the prevailing narrative.”
24 notes
·
View notes
Text
President Trump and his former star advisor, Elon Musk, have accelerated the deployment of a vast technological infrastructure that monitors the lives of millions of people. The system is focusing on immigrants — for now Massive unauthorized scanning of social media. Analysis of biometric, income, health, and Social Security data. Interception of telephone communications. Geolocation via mobile devices. Tracking of car journeys using license plate readers. Since Donald Trump returned to the White House, the U.S. government has been using these and other tools based on artificial intelligence (AI) to monitor and persecute thousands of people without judicial authorization — mostly immigrants, foreigners passing through, or students. In the last four months, Trump and his former star advisor, the tech tycoon Elon Musk, have, along with the private sector, accelerated the deployment of a massive techno-surveillance state. And for the first time in history, Washington is boasting about it rather than denying its existence. “Surveillance in the U.S. didn’t begin with Trump, nor will it end when he leaves the White House. The foundations for the current state of techno-surveillance were laid over decades, with bipartisan support for policies that normalized invasive practices in law enforcement, the military, and border control,” says the Bahraini civil rights activist Esra’a Al Shafei, who has been studying this issue for years, in a conversation with EL PAÍS. “This system is fueled by large budgets allocated to intelligence agencies, as well as private providers, all under the pretext of national security and crime prevention.” Companies like Palantir, Anduril, and GEO Group are providing Washington with digital tools to build this entire surveillance infrastructure. Trump continues to add layers to this system. The Department of Homeland Security (DHS) confirmed in April that it is using a tool called Babel X to collect social media information about travelers who may be subject to increased surveillance, according to the agency itself. Immigration and Customs Enforcement (ICE), for its part, has acknowledged using another program, SocialNet, which aggregates data from more than 200 sources, including Facebook, Twitter/X, Instagram, LinkedIn, and dating apps.
continue reading
6 notes
·
View notes
Text
Last November I outlined my concerns that elections might look very different in four years, one of which was cutting funding for election cybersecurity.
WELP
In its crusade against federal agencies, the Trump administration is targeting our election system, making potentially dangerous reductions to protections that help keep elections free, fair, and secure. On Friday, the acting director of the Cybersecurity and Infrastructure Security Agency sent a memo to all agency staff notifying them that “all election security activities” would be paused pending the results of an internal investigation. The memo also stated that the administration was cutting off all funds to the Election Infrastructure Information Sharing and Analysis Center—a Department of Homeland Security–funded organization that helps state and local officials monitor, analyze, and respond to cyberattacks targeting the nation’s election hardware and software.
The work of CISA and the EI-ISAC has been central to election security in the United States for most of the past decade, providing state and local election officials with critical tools and assistance to defend against cyber and physical threats to election systems. These steps and other recent blows to federal election guardrails were foretold in Project 2025. Understanding the playbook will help us be ready to push back when the next shoes drop.
Changes to CISA began shortly after Kristi Noem was sworn in as secretary of Homeland Security, which oversees the agency. Beyond the announced election security pause and defunding of EI-ISAC, the agency also put critical election security staff on leave and targeted them for potential termination. These staff include CISA’s regional election security advisers, who are former state and local election officials that provide on-the-ground security support to current frontline election workers, and members of the agency’s Election Resilience team, who were reportedly targeted because they had previously been involved with the agency’s efforts to communicate accurate information about election security to election officials and the public.
(more at the source)
12 notes
·
View notes
Text
In recent years, commercial spyware has been deployed by more actors against a wider range of victims, but the prevailing narrative has still been that the malware is used in targeted attacks against an extremely small number of people. At the same time, though, it has been difficult to check devices for infection, leading individuals to navigate an ad hoc array of academic institutions and NGOs that have been on the front lines of developing forensic techniques to detect mobile spyware. On Tuesday, the mobile device security firm iVerify is publishing findings from a spyware detection feature it launched in May. Of 2,500 device scans that the company's customers elected to submit for inspection, seven revealed infections by the notorious NSO Group malware known as Pegasus.
The company’s Mobile Threat Hunting feature uses a combination of malware signature-based detection, heuristics, and machine learning to look for anomalies in iOS and Android device activity or telltale signs of spyware infection. For paying iVerify customers, the tool regularly checks devices for potential compromise. But the company also offers a free version of the feature for anyone who downloads the iVerify Basics app for $1. These users can walk through steps to generate and send a special diagnostic utility file to iVerify and receive analysis within hours. Free users can use the tool once a month. iVerify's infrastructure is built to be privacy-preserving, but to run the Mobile Threat Hunting feature, users must enter an email address so the company has a way to contact them if a scan turns up spyware—as it did in the seven recent Pegasus discoveries.
Daily Newsletter
Our biggest stories, handpicked for you each day.
“The really fascinating thing is that the people who were targeted were not just journalists and activists, but business leaders, people running commercial enterprises, people in government positions,” says Rocky Cole, chief operating officer of iVerify and a former US National Security Agency analyst. “It looks a lot more like the targeting profile of your average piece of malware or your average APT group than it does the narrative that’s been out there that mercenary spyware is being abused to target activists. It is doing that, absolutely, but this cross section of society was surprising to find.”
Seven out of 2,500 scans may sound like a small group, especially in the somewhat self-selecting customer base of iVerify users, whether paying or free, who want to be monitoring their mobile device security at all, much less checking specifically for spyware. But the fact that the tool has already found a handful of infections at all speaks to how widely the use of spyware has proliferated around the world. Having an easy tool for diagnosing spyware compromises may well expand the picture of just how often such malware is being used.
“NSO Group sells its products exclusively to vetted US & Israel-allied intelligence and law enforcement agencies,” NSO Group spokesperson Gil Lainer told WIRED in a statement. "Our customers use these technologies daily.”
iVerify vice president of research Matthias Frielingsdorf will present the group's Pegasus findings at the Objective by the Sea security conference in Maui, Hawaii on Friday. He says that it took significant investment to develop the detection tool because mobile operating systems like Android, and particularly iOS, are more locked down than traditional desktop operating systems and don't allow monitoring software to have kernel access at the heart of the system. Cole says that the crucial insight was to use telemetry taken from as close to the kernel as possible to tune machine learning models for detection. Some spyware, like Pegasus, also has characteristic traits that make it easier to flag. In the seven detections, Mobile Threat Hunting caught Pegasus using diagnostic data, shutdown logs, and crash logs. But the challenge, Cole says, is in refining mobile monitoring tools to reduce false positives.
Developing the detection capability has already been invaluable, though. Cole says that it helped iVerify identify signs of compromise on the smartphone of Gurpatwant Singh Pannun, a lawyer and Sikh political activist who was the target of an alleged, foiled assassination attempt by an Indian government employee in New York City. The Mobile Threat Hunting feature also flagged suspected nation state activity on the mobile devices of two Harris-Walz campaign officials—a senior member of the campaign and an IT department member—during the presidential race.
“The age of assuming that iPhones and Android phones are safe out of the box is over,” Cole says. “The sorts of capabilities to know if your phone has spyware on it were not widespread. There were technical barriers and it was leaving a lot of people behind. Now you have the ability to know if your phone is infected with commercial spyware. And the rate is much higher than the prevailing narrative.”
#A New Phone Scanner That Detects Spyware Has Already Found 7 Pegasus Infections#Phone Scanner#phone viruses#phones with installed viruses#IVerify
6 notes
·
View notes
Text
Analog vs. Digital Meters: Understanding the Differences and Applications

In today’s increasingly connected and technologically advanced world, precise electrical measurement is critical for efficient power management and system monitoring. Two primary tools dominate the field of electrical measurement: analog meters and digital meters. While both serve the same fundamental purpose — measuring electrical quantities like voltage, current, and frequency — their technology, design, readability, and application differ significantly.
This article explores the key differences between analog and digital meters, their respective advantages, disadvantages, and common use cases to help you make an informed decision when selecting the right meter for your needs.
What Are Analog Meters?
Analog meters are traditional instruments that display measurement readings through a mechanical needle moving over a graduated scale. They have been widely used for decades in industries, commercial applications, and even residential setups.
Key Features of Analog Meters:
· Use of moving coil or iron vane mechanisms
· Continuous scale display
· Passive operation (no power required in many types)
· Simple, durable construction
Common Types:
· Analog Voltmeters
· Analog Ammeters
· Analog Frequency Meters
· Analog Power Factor Meters
Advantages of Analog Meters:
· Easy to interpret trends and fluctuations
· Cost-effective for basic applications
· Operate without auxiliary power
· Better tolerance to transient spikes and overloads
Limitations:
· Lower accuracy compared to digital meters
· Manual reading required
· Parallax error due to needle reading
· Limited data logging or interfacing capabilities
What Are Digital Meters?
Digital meters represent a more modern approach to electrical measurement. These devices convert analog signals into digital values, displaying results on an LCD or LED screen. They are widely used in automation, smart grids, and precision engineering environments.
Key Features of Digital Meters:
· High-resolution digital display
· Advanced microprocessor control
· MODBUS communication (RS-485 interface)
· Programmable settings and alarms
Common Types:
· Digital Voltmeters
· Digital Ammeters
· Digital Frequency Meters
· Digital Multifunction Meters (VAF, kWh, Power Factor, etc.)
Advantages of Digital Meters:
· High accuracy and readability
· Remote monitoring capabilities
· Compact and modern design
· Enhanced functionalities like data logging, alarms, and networking
Limitations:
· Higher initial cost
· Requires auxiliary power
· More complex installation in some cases

Applications of Analog and Digital Meters
Where Analog Meters Excel:
· Educational institutions for teaching fundamentals
· Industrial environments where ruggedness is key
· Backup or emergency systems where power is limited
· Low-budget installations
Where Digital Meters Lead:
· Smart panels and industrial automation
· Energy monitoring systems
· Commercial buildings and infrastructure
· Remote power distribution networks
Choosing the Right Meter: Factors to Consider
When deciding between analog and digital meters, consider the following:
1. Accuracy Requirements — For precision tasks, digital meters are the preferred choice.
2. Budget Constraints — Analog meters offer a cost-effective solution for basic needs.
3. Environment — Analog meters can be more tolerant in high-temperature or high-vibration areas.
4. Communication Needs — If integration with SCADA or monitoring systems is needed, go digital.
5. Data Analysis — For trend tracking and analytics, digital meters with memory and communication ports are ideal.
Enza Electric: Your Trusted Source for Analog and Digital Meters in the UAE
At Enza Electric, we provide a comprehensive range of analog and digital panel meters tailored to meet diverse electrical monitoring needs. Our digital meters support RS-485 MODBUS, enabling seamless integration into modern automation systems. Whether you’re looking for reliable analog meters for legacy systems or advanced digital meters for new installations, Enza Electric has the expertise and inventory to deliver.
We offer:
· Voltmeter, Ammeter, and Frequency meters in both analog and digital forms
· Multifunction VAF meters
· Panel meter sizes: 72x72mm and 96x96mm
· Customizable CT and PT ratios
Conclusion
Both analog and digital meters play important roles in today’s electrical systems. While analog meters offer simplicity and durability, digital meters bring precision, connectivity, and intelligence. Understanding their differences and applications is key to choosing the right tool for your project.
For expert guidance and high-quality meters, contact Enza Electric — one of the leading electrical measurement solution providers in the UAE.
#AnalogMeters#DigitalMeters#PanelMeters#ElectricalMeasurement#PowerMonitoring#ElectricalEngineering#EnergyMeters#IndustrialAutomation#MeteringSolutions#Instrumentation#electrical#switchgear#dubai#low voltage#uae
4 notes
·
View notes
Text
How Civil Engineering Courses Are Evolving with New Technology
Civil engineering is no longer just about bricks, cement, and bridges. It has become one of the most future-focused fields today. If you are planning to study civil engineering, you must understand how the course has evolved. The best civil engineering colleges are now offering much more than classroom learning.
You now study with technology, not just about it. And this shift is shaping your career in ways that were never possible before.
Technology is Changing the Civil Engineering Classroom
In the past, civil engineering courses relied on heavy theory and basic field training. Today, you learn through software, simulations, and smart labs. At universities like BBDU in Lucknow, classrooms are powered by tools like AutoCAD, Revit, STAAD Pro, and BIM.
These tools help you visualize structures, test designs, and even simulate natural forces.
You work on 3D modeling tools
You test designs virtually before real-world execution
You understand smart city layouts and green construction methods
This means your learning is hands-on, job-ready, and tech-driven.
You Learn What the Industry Actually Uses
Most construction and infrastructure companies now depend on digital tools to plan, design, and execute projects. This is why modern B.Tech Civil Engineering courses include:
Building Information Modelling (BIM)
Geographic Information Systems (GIS)
Remote Sensing Technology
Drones for land surveying
IoT sensors in smart infrastructure
Courses in colleges like BBDU include these topics in the curriculum. You do not just learn civil engineering. You learn the tools that companies expect you to know from day one.
The future of Civil Engineering is Data-Driven
You might not think of civil engineering as a data-heavy field. But now, big data is used to monitor structural health, traffic flow, and resource planning. Many universities have added data analysis and AI basics to help you understand how smart infrastructure works.
By learning how to handle real-time data from buildings or roads, you become more skilled and more employable.
Real-world exposure is Now Part of the Course
Good civil engineering colleges in Uttar Pradesh understand that you need industry exposure. Colleges like BBDU offer:
Internships with construction firms and government bodies
Industry guest lectures and site visits
Capstone projects linked to real problems
You are not just attending lectures. You are solving real-world construction challenges while still in college.
Why Choose BBDU for Civil Engineering?
In Lucknow, BBDU is one of the few private universities offering a modern civil engineering course with world-class infrastructure. You learn in smart labs, access tools used by top firms, and receive career counseling throughout the program.
Here’s what makes BBDU a smart choice:
Advanced labs and smart classrooms
Training in AutoCAD, STAAD Pro, BIM
Live projects and on-site construction learning
Career cell and placement support
Affordable fees and scholarships for deserving students
Civil Engineering is Still One of the Most Stable Careers
Reports show that India will spend over ₹100 lakh crores on infrastructure in the next few years. Roads, smart cities, renewable power plants, metros – all need civil engineers. And companies prefer students trained in construction technology, digital tools, and real-world planning.
So, if you're thinking about joining a course, look at how it prepares you for tomorrow.
The future of civil engineering is digital, and your education should be too. Choose a program that keeps up with the times. Choose a university that helps you build more than just buildings – it helps you build your future.
Apply now at BBDU – one of the most future-focused civil engineering colleges in Uttar Pradesh.
2 notes
·
View notes
Text

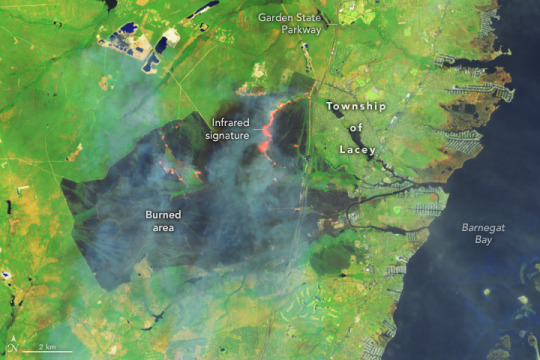
New Jersey Pine Barrens Ablaze
Wildland fires have long been integral to New Jersey’s Pinelands, or Pine Barrens. These highly flammable coastal forests host pitch pines and other trees that thrive with occasional burns.
Yet with hundreds of thousands of people living within these coastal forests, burns can shift rapidly from rejuvenating ecosystems to destroying infrastructure and threatening human life, particularly during droughts. A fire that began in a wildlife management area near Waretown on April 22, 2025, offered a stark reminder of this delicate balance. Within two days, the fire had grown into one of the largest fires New Jersey has seen in decades.
The OLI-2 (Operational Land Imager-2) on Landsat 9 captured images of the Jones Road fire on April 23. In the natural-color scene (top), thick smoke obscures the fire’s mark on the land below. The burned area is evident in the false-color image (above) showing shortwave infrared, near infrared, and visible light (OLI bands 6-5-3). This band combination makes it easier to identify unburned vegetated areas (green) and the recently burned landscape (brown). A sand mine is visible in the upper left of the images. A broader view of the natural-color image is below.

An ongoing drought made the Pine Barrens particularly susceptible to fire in spring 2025. An April analysis of shallow groundwater and soil moisture using NASA observations from the GRACE (Gravity Recovery and Climate Experiment) and GRACE-FO (GRACE Follow On) satellites showed anomalously dry conditions, according to data posted by the National Drought Mitigation Center. At the time of the fire, the U.S. Drought Monitor had classified drought in the region as “severe.”
According to news reports, the fast-moving fire led to evacuations of large numbers of people from Lacey and Ocean townships, threatened many homes, and sent smoke wafting toward New York City. At times, officials closed both the Garden State Parkway and Route 532. As of April 24, more than 15,000 acres had burned, and the fire was 50 percent contained, according to the New Jersey Forest Fire Service. As of that date, all evacuation orders had been lifted and the Garden State Parkway had been reopened, the fire service noted.
NASA’s satellite data is part of a global system of observations that are used to track fire behavior and analyze emerging trends. Among the real-time wildfire monitoring tools that NASA makes available are FIRMS (Fire Information for Resource Management System) and the Worldview browser.
NASA Earth Observatory images by Wanmei Liang, using Landsat data from the U.S. Geological Survey. Story by Adam Voiland.
2 notes
·
View notes
Text

Start Your Breakthrough Clinical Trials At AIIMS Hospital With BBMCT

Clinical trials are the backbone of medical advancements, helping researchers and healthcare professionals find new treatments, therapies, and solutions to pressing health issues. In India, AIIMS (All India Institute of Medical Sciences) has long been at the forefront of healthcare excellence, and when combined with **British Biomedicine Clinical Trials (BBMCT)**, it offers world-class research facilities and clinical expertise for cutting-edge breakthroughs. In this article, we’ll explore how BBMCT at AIIMS provides unmatched support for clinical research and trials.
— -
### **World-Class Research Facilities Available**
AIIMS Hospital is renowned globally for its state-of-the-art research infrastructure. The research facilities at AIIMS are designed to cater to diverse medical specialties, making it an ideal location for conducting advanced clinical trials. The hospital’s vast campus houses modern laboratories, research centers, and equipment, all of which are equipped with the latest technology to support clinical research.
British Biomedicine Clinical Trials (BBMCT) leverages these facilities to create an environment where studies can progress smoothly and efficiently. Whether it’s pharmacokinetics, bioequivalence studies, or clinical pharmacology trials, BBMCT at AIIMS offers a comprehensive setup for all kinds of advanced research. This enables researchers to gather precise data, ensuring faster and more accurate results.
— -
### **Expert Clinical Trials Management Team**
The success of clinical trials depends largely on the expertise and experience of the team managing them. BBMCT at AIIMS boasts an experienced team of medical professionals, researchers, and trial coordinators who specialize in clinical research and trial management. This team oversees every aspect of the clinical trial process, from initial planning to the final data analysis.
The clinical trial management team at BBMCT follows international best practices in Good Clinical Practice (GCP), ensuring that all trials meet rigorous scientific and ethical standards. Their profound knowledge in regulatory compliance, patient safety, and data integrity is a key asset for any study looking to achieve reliable and actionable results.
— -
### **Access to Diverse Patient Populations**
A unique advantage of conducting clinical trials at AIIMS is the access to a highly diverse patient population. AIIMS caters to patients from various socio-economic backgrounds, ethnicities, and regions. This diversity enhances the generalizability and relevance of clinical trial outcomes, ensuring that findings are applicable to a broad spectrum of people.
BBMCT at AIIMS takes full advantage of this diverse patient pool, allowing researchers to study the effects of treatments on a wide range of individuals. This helps researchers to detect varying responses to interventions, ensuring that the clinical trial results are robust, representative, and suitable for global healthcare applications.
— -
### **Cutting-Edge Technology Integration Offered**
To stay ahead in the fast-paced world of clinical trials, BBMCT integrates the latest technological advancements in clinical research at AIIMS. From electronic data capture (EDC) systems to cloud-based analytics platforms, AIIMS and BBMCT are fully equipped with cutting-edge technologies that streamline trial processes and improve accuracy.
These technologies enable real-time monitoring of trial data, faster recruitment and retention of participants, and more efficient management of study documentation. Furthermore, AIIMS is constantly upgrading its infrastructure to incorporate new innovations, ensuring that trials benefit from the most advanced tools available in medical research.
— -
### **Robust Ethical Oversight Ensured Here**
Clinical trials often involve testing new treatments on human participants, making ethical oversight a critical part of the research process. At AIIMS, ethical considerations are a top priority. BBMCT ensures that all clinical trials are conducted in accordance with the highest ethical standards, including patient informed consent, confidentiality, and protection from harm.
AIIMS has a dedicated ethics committee that reviews and monitors each clinical trial to ensure compliance with national and international ethical guidelines. This oversight gives patients confidence in participating and reassures researchers that their trials are conducted responsibly, ensuring the integrity and credibility of the results.
— -
### **Collaborate With Leading Medical Experts**
When conducting clinical research at AIIMS with BBMCT, you gain access to some of the leading medical experts in various fields. AIIMS is home to renowned specialists and researchers across disciplines, including oncology, cardiology, neurology, and infectious diseases.
Collaborating with these experts not only enhances the quality of research but also allows for interdisciplinary approaches to clinical trials. BBMCT fosters an environment of collaboration, where your study can benefit from the expertise and innovative solutions provided by these thought leaders in medicine and clinical research.
— -
### **Streamlined Processes for Quick Trials**
The faster clinical trials progress, the sooner medical breakthroughs can be made. At BBMCT, the processes involved in clinical trials are streamlined to reduce unnecessary delays and inefficiencies. From patient recruitment to data collection and analysis, BBMCT ensures that every phase of the trial is executed promptly.
AIIMS’ established infrastructure and resources facilitate quick approvals, recruitment, and trial management, meaning that studies can progress without the common bottlenecks seen in other settings. This streamlined approach is critical in accelerating the development of new treatments and improving patient outcomes.
— -
### **Enhance Your Study’s Success Rates**
Clinical trials require precision, efficiency, and an in-depth understanding of the research process. BBMCT at AIIMS is dedicated to enhancing the success rates of studies by offering the right resources, expertise, and infrastructure. With world-class facilities, expert teams, and cutting-edge technology, BBMCT ensures that trials are conducted optimally and that every potential challenge is mitigated.
The strategic support provided by BBMCT helps in better trial design, data accuracy, and recruitment strategies, which ultimately increase the likelihood of achieving positive study outcomes. Whether you are testing a new drug or a medical device, BBMCT maximizes your study’s chances of success.
/media/4ba4cf5bfd511c0ae4ae8e305b8459ec
— -
### **Frequently Asked Questions (FAQs)**
**1. What makes BBMCT at AIIMS different from other clinical trial organizations?**
BBMCT at AIIMS offers a combination of world-class research facilities, access to diverse patient populations, and expert clinical trial management. The integration of cutting-edge technologies and robust ethical oversight ensures that clinical trials are conducted efficiently and ethically. Additionally, AIIMS’ reputation and access to leading medical experts make BBMCT a standout choice for clinical research in India.
**2. How does AIIMS ensure ethical oversight during clinical trials?**
AIIMS has a dedicated ethics committee that reviews all clinical trials before they begin. The committee ensures that the trials adhere to national and international ethical standards, protecting the rights and well-being of participants. Informed consent, privacy, and safety protocols are central to their oversight, making sure trials are conducted responsibly.
**3. Can international researchers collaborate with BBMCT at AIIMS?**
Yes, BBMCT encourages international collaboration. Researchers from across the globe can partner with AIIMS and benefit from its vast resources, medical expertise, and advanced research facilities. International collaboration is particularly valuable in improving the scope and impact of clinical trials by incorporating diverse perspectives and expertise.
**4. What patient populations can BBMCT at AIIMS access for clinical trials?**
AIIMS serves a diverse patient population from various socio-economic backgrounds and regions. This diversity allows researchers to assess the effectiveness of treatments on a broad spectrum of individuals, increasing the relevance and applicability of study outcomes. BBMCT ensures that clinical trials can tap into this wide variety of patient groups for robust data collection.
**5. How do BBMCT’s cutting-edge technologies improve clinical trials?**
BBMCT integrates advanced technologies like electronic data capture, real-time monitoring systems, and cloud-based analytics to streamline trial processes. These technologies improve the accuracy of data, reduce trial delays, and enhance participant management. The use of such tools also accelerates the trial timeline, ensuring faster results and quicker access to new treatments.
— -
### **Conclusion**
AIIMS Hospital, in partnership with **British Biomedicine Clinical Trials (BBMCT)**, offers one of the most advanced environments for clinical research in the world. With world-class research facilities, an expert clinical trials management team, and a commitment to ethical oversight, BBMCT ensures that each clinical trial conducted at AIIMS is a step towards scientific breakthroughs and improved patient care. The integration of cutting-edge technology and access to diverse patient populations further enhances the success rates of trials, ensuring that medical innovations reach the people who need them most. If you are looking to advance your clinical research, starting your breakthrough trials with BBMCT at AIIMS is a choice you can trust.
Subscribe to BBMCLINICALTRIALS YouTube channel for Research Insights
Be sure to subscribe to the **BBMCLINICALTRIALS YouTube channel** for exclusive access to the latest updates and in-depth insights into British Biomedicine Clinical Trials (BBMCT). Stay informed on cutting-edge research, clinical trial advancements, patient safety protocols, and breakthrough therapies being tested at AIIMS Hospital. Our channel provides expert discussions, industry trends, and detailed videos on the clinical trial process across various therapeutic areas. Whether you’re a healthcare professional, researcher, or simply interested in biomedical innovation, subscribing will keep you at the forefront of clinical research developments. Don’t miss out — join our community today!
#anya mouthwashing#batman#artists on tumblr#agatha harkness#captain curly#cats of tumblr#bucktommy#agatha all along#911 abc
4 notes
·
View notes
Text
Road Condition Monitoring System(RCMS): Enhancing Efficiency with AI-Powered Solutions
The quality and sustainability of road infrastructure play a pivotal role in societal development, economic growth, and the safety of communities. To address the challenges of road construction and maintenance, advanced digital tools such as Road Condition Monitoring Systems (RCMS) are becoming indispensable. Leveraging technologies like AI-powered pothole detection, data analytics, and interactive visualization, RCMS ensures efficient planning, monitoring, and maintenance of road networks.

#ai and gis road monitoring solutions#geospatial road management solutions#geospatial road monitoring system#gis based pothole mapping and detection#gis based road condition monitoring system#gis based road inspection software#gis based road survey solutions#gis data analysis for road monitoring#gis mapping for road condition analysis#gis road maintenance solutions#land management system#gis tools for road condition assessment#pothole detection using gis technology#real time road condition monitoring gis#road condition assessment using gis#road condition monitoring using gis#road infrastructure monitoring with gis#road maintenance gis software#road safety monitoring with gis systems#road surface monitoring with gis#smart road condition monitoring gis
1 note
·
View note
Text
Link: telex.im
Competitor analysis between telex (hypothetical instrument) and other similar tool
Using New relics in Monitoring and Observability: New Relic offers a comprehensive suite of monitoring and observability tools covering a wide range of areas, including APM, infrastructure monitoring, and log management. In contrast, Telex's capabilities may be more focused on specific domains or have a different approach to data organization and presentation. New Relic relies on extensive agent-based instrumentation to collect detailed performance data, while Telex may use a mix of agent-based and agentless methods. Telex have the advantage of providing many other benefit aside monitoring and it is user-driven interface
And also in comparison with which is just a webdriver used for testing and offer the user that ability to know how to code before using it. But Telex offers the webtesting service prior knowledge of coding and it is effective across all apps and websites. Datadog provides extensive customization options for alerting rules, in contrast to Telex's potentially more streamlined approach. Datadog also has a broader ecosystem of integrations compared to Telex's more focused integration capabilities.Datadog provides extensive customization options for alerting rules, in contrast to Telex's potentially more streamlined approach. Datadog also has a broader ecosystem of integrations compared to Telex's more focused integration capabilities.
And Telex has the advantage of getting many other capabilities aside from cloud monitoring.
With a third-party app for users to navigate to use at their own convenience. So telex have the ability to be world if it increase its marketing strategies and has a user interface to make it user-driven, then I can say it is a world call
2 notes
·
View notes
Text
Several government websites have been taken down, including the USAID.gov, ForeignAssistance.gov, NeglectedDiseases.gov, and ChildrenInAdversity.gov. A WIRED analysis of more than 1,000 federal .gov websites found that at least seven sites linked to a USAID server went offline in a two-hour span on Saturday afternoon.
On Friday, Reuters reported that word of sites being taken offline was the result of confusion around new guidelines on language allowed to appear on federal sites. Agencies had been instructed to “take down all outward facing media (websites, social media accounts, etc.) that inculcate or promote gender ideology” by 5 pm EST, Friday, January 31.
The move is the latest step in the Trump administration’s move to radically remake the US government. Shortly after taking office, the Trump administration took down ReproductiveRights.gov, which provided information on reproductive health care. A growing number of US government websites have gone offline since mid-January.
Along with sites affiliated with the USAID server, Youth.gov—a US government site focused on supporting youth programs—appears to have gone offline in the past 24 hours. Before it was taken down, an archived version from the Wayback Machine showed it featured a post titled, “Preparing for MLK Jr. National Day of Service.”
A USAID employee tells WIRED that staff members are scrambling to save digital copies of regulations from archived versions of the site, and that at least some are being locked out of their systems, including personnel files, pay, and benefits information. “Decades worth of taxpayer-funded reports and analysis gone in an instant,” says the employee, who requested anonymity because they are not authorized to speak to the press. “We have no idea what is happening behind the scenes or what will be back, when, and in what form."
Added the employee: “Staff can't even get into the DEC (Development Experience Clearinghouse, a publicly available database of USAID documents) to secure copies of open access reports.”
Another USAID employee tells WIRED they still had access to internal work systems as of Saturday afternoon, but have limited visibility into what’s happening and why.
“We haven't been allowed to be in contact with our partners,” says the employee, who was also granted anonymity. “We've been kept in the dark, and this is just an extension of that.” The employee added that they worry the agency will be slimmed down to a “skeleton of what we were.”
Other sites, including HealthData.gov, Oversight.gov, and Vaccines.gov, have also periodically gone dark. It remains unclear whether these brief takedowns are linked to the recent executive order or if some are due to unrelated technical issues. However, some sites, like ProsperAfrica.gov, explicitly state: “In order to be consistent with the President’s Executive Orders, this website is currently undergoing maintenance as we expeditiously and thoroughly review all of the content."
WIRED built software to systematically check the status of 1,374 government domains. The tool runs periodic scans, tracking whether sites remain accessible, how their servers respond, and if the domain names still resolve. This allows us to monitor patterns in uptime and catch moments when sites suddenly vanish– sometimes reappearing minutes or hours later. Some of these outages can be attributed to routine maintenance or technical glitches. Others suggest broader infrastructure failures or deliberate removals.
In total, more than 450 government domains WIRED is monitoring remain consistently offline. However, it’s unclear whether they were removed weeks, months, or even years ago.
On January 26, President Donald Trump signed an executive order “initiating a review of all foreign assistance programs to ensure they are efficient and consistent with U.S. foreign policy under the America First agenda.” The result was a suspension of USAID’s work abroad, which includes lifesaving humanitarian aid as well as critical public health initiatives.
In the newsletter Garbage Day, Ryan Broderick and Adam Bumas reported that an employee working with an organization funded by the Centers for Disease Control was informed that the agency’s website would be taken down “in its entirety.” Last week, the government removed TargetHIV.org, run by the Health Resources and Services Administration. The CDC’s HIV resource landing page has also been removed. Pages on creating safe school environments and addressing health disparities for LGBTQ+ youth were also removed, as was one focused on transgender people.
In a post on Bluesky, journalist Ken Klippenstein shared images of an email sent to the National Oceanic and Atmospheric Administration that required the agency to remove materials that contained words like “black,” “ethnicity,” “empathy,” and “handicap.”
Within the past week, employees across agencies received emails requiring them to replace all mentions of “gender” with “sex” in all “communications, forms, and documents” and to remove pronouns from email signatures.
Federal agencies were also told last week that they had 60 days to eliminate DEI roles and programs, and an email encouraged federal employees to report colleagues who work in DEI roles.
5 notes
·
View notes
Text
The Silent Revolution: How Digital Transformation Is Changing Business Behind the Scenes
While digital transformation often makes headlines for visible innovations, much of its influence happens quietly within companies—reshaping systems, automating processes, and reengineering the way work gets done. This behind-the-scenes shift is what’s enabling real business performance gains.
What Is Digital Transformation?
Digital transformation refers to how businesses use technology to change operational methods, improve internal systems, and generate better outcomes. It affects everything from data management and customer interactions to logistics and resource allocation.
A professional digital transformation company doesn't just install new tech—it aligns tools with business goals, often starting with process audits and infrastructure analysis.
Technologies Often Involved
Cloud computing for digital transformation
Business process automation
Artificial intelligence for analytics
Internet of Things (IoT) in digital transformation
Cross-platform data integration
These are not surface-level changes. They improve how employees work, how data is accessed, and how resources are distributed—resulting in time savings, fewer errors, and stronger outcomes.

Why Businesses Need Digital Transformation Services
In highly competitive markets, outdated systems can lead to inefficiency and slow growth. Businesses are now choosing digital transformation services to improve speed, reduce overhead, and increase accuracy.
Outcomes companies aim for include:
Smoother workflows
Better use of employee time
More consistent customer experiences
Faster decision-making using real-time data
Consulting firms offer digital innovation consulting to assess the internal structure and recommend improvements tailored to each business model.
Features of Digital Transformation Solutions
The best digital transformation solutions focus on measurable improvements in operations, communication, and performance.
Common Features Include:
Automated Workflow Engines: Replace manual processes with intelligent rules
Real-Time Analytics: Track key business metrics instantly
Cloud Infrastructure: Access systems securely from any device
AI and ML Capabilities: Detect patterns, improve forecasts, and recommend actions
Secure Data Storage: Built-in compliance for data privacy and governance
These features support enterprise digital transformation by increasing system flexibility and operational transparency.
Benefits of Digital Transformation
Companies that invest in high-quality digital transformation consulting often see tangible benefits within months of implementation.
Key Business Gains:
Higher Productivity: Employees spend less time on manual tasks
Improved Decision-Making: Real-time data enables faster, informed choices
Cost Savings: Automation cuts operational expenses
Increased Accuracy: Fewer human errors mean better outcomes
Customer Retention: Personalized service improves satisfaction
Small and medium enterprises can also benefit, with options scaled to meet their specific needs. The cost of digital transformation services for SMEs depends on complexity, but returns on investment are often significant.
Behind-the-Scenes Use Cases (Digital Transformation Case Studies)
1. Logistics Optimization: IoT for Equipment Monitoring
A supply chain firm implemented IoT in digital transformation to track truck performance and reduce delays. By integrating AI-powered route planning, the company cut fuel usage by 18% and delivery delays by 23%.
Digital transformation services
Digital transformation solutions
2. Retail Automation: Cloud and POS Integration
A mid-sized retailer switched to cloud computing for digital transformation to connect online and offline sales. This allowed for real-time inventory tracking and a 40% reduction in stock-outs.
AI and cloud solutions for digital transformation
3. Finance Sector: Risk Analytics
A regional bank used digital transformation consulting to install real-time risk detection tools, minimizing financial fraud cases by 32% over a single quarter.
Digital innovation consulting
How to Choose a Digital Transformation Partner
Selecting the right digital transformation company is critical. The wrong choice can lead to costly rework and wasted time.
What to Look For:
Industry-specific experience
Transparent pricing and timelines
Strong client portfolio
Scalable digital transformation strategy
Post-implementation support
How to choose a digital transformation partner
Search queries like “best digital transformation companies in [your country or city]” help narrow down suitable vendors based on reviews, pricing models, and technology stacks.
Key Tools Used by Digital Transformation Companies
Digital transformation requires more than software—it needs strategy, configuration, and training.
Common Tools Deployed:
Process Automation Platforms (e.g., UiPath, Zapier)
ERP & CRM Systems (e.g., Salesforce, SAP)
Business Analytics Tools (e.g., Power BI, Tableau)
Cloud Infrastructure (AWS, Azure, Google Cloud)
Communication Platforms (e.g., Slack, Microsoft Teams)
These tools are often combined with business process automation to eliminate redundancy and streamline workflow across departments.
Digital Transformation Strategy for Long-Term Growth
A clear digital transformation strategy should outline:
Current system limitations
Department-specific challenges
Integration goals
Expected performance benchmarks
The strategy guides both short-term improvements and long-term innovation cycles, backed by consistent data and feedback.
Cost of Digital Transformation Services for SMEs
For SMEs, the cost often depends on:
Number of systems being upgraded
Complexity of processes
Customization required
Ongoing support and maintenance
Pricing usually ranges from basic SaaS subscriptions to full-service enterprise digital transformation packages. Most providers offer flexible pricing models or phased implementation to help manage budget.
Final Note: Quiet, But Game-Changing
While these changes may not make flashy headlines, they are producing real operational improvements every day. This quiet shift is what’s separating top performers from companies stuck in outdated systems.Get tailored digital transformation services that deliver.The behind-the-scenes nature of digital transformation means many organizations don’t publicize these updates—but the results are measurable, from higher profits to better customer reviews.
#DigitalTransformation#DigitalTransformationServices#BusinessAutomation#EnterpriseTechnology#CloudComputing
1 note
·
View note
Text





REPORT FROM DR. CRYOGENUS
Dr. Evelyn Cryogenus (formerly Evelyn Frost)
Location: Belle Reve Penitentiary
Classification: Confidential
Subject: Observations and Analysis While in Confinement
INTRODUCTION: Since my arrival at Belle Reve, I have had the dubious privilege of closely observing the failed experiments and cut short lives this prison houses. I cannot help but feel a disturbing connection to many of the individuals here - beings who, like myself, were stripped of their humanity in the name of science or unbridled ambition. I have taken advantage of my confinement to gather data on the anomalous abilities of certain inmates and the extreme conditions in which they are kept.
SECTION 1 - CONTAINMENT OBSERVATIONS The Belle Reve system is designed to contain individuals with supernatural or anomalous abilities. However, I have noticed certain inefficiencies: Climate Controlled Cells: The cryogenic and extreme heat cells are not uniform. This proves dangerous for prisoners with temperature-based abilities. My own cell was not set up properly, allowing me to calibrate my control over temperature by allowing small amounts of cold to escape through cracks in the infrastructure. Inefficient Monitoring: The guards rely too heavily on outdated technology. I witnessed several inmates, including a subject named "Boltzmann," manipulate the electrical systems to create temporary blackouts.
SECTION 2: CLANDESTINE EXPERIMENTS Through interactions with other inmates and certain files I managed to decipher during an internal hacking attack, I have confirmed the continuation of clandestine experiments under the supervision of Amanda Waller. Genome Projects: Genetic experimentation on inmates without their consent. The Genome Project appears to be aimed at creating more stable hybrids between humans and metahumans. Cryogenic and Thermal Fusion: Apparently, my state and Phosphorus' were derived from an early program to manipulate extreme temperatures in humans. My analysis suggests there was a conscious design to test opposite interactions: heat and cold.
SECTION 3: PERSONAL DISCOVERIES While going through the archives of Belle Reve, I came across records relating to my and Alexander's (Doctor Phosphorus) transformation. Prior to our "evolution," we worked together in the same lab as researchers. In group photos, we were seen smiling, oblivious to the fate that awaited us. The discovery led me to reflect on how our abilities now work in symbiosis, as evidenced by our recent mission. Ironically, our opposing powers make us a complementary force, something we never understood when we were humans.
SECTION 4: CONCLUSION AND PROPOSAL Belle Reve is both a laboratory and a prison, a place where individuals are reduced to tools for unknown purposes. However, within this chaos, I have identified patterns that could be exploited for personal gain and, potentially, the release of other inmates. As a final note, my work with Phosphorus during missions is not just a matter of survival. It is proof that even in the loss of our humanity, we can find purpose and connection. I do not trust Waller's system or the Squad, but I intend to use their resources to obtain more answers and, perhaps, recover a part of what I lost. End of report.
SIGNED: Dr. Evelyn Cryogenus
4 notes
·
View notes
Text
GIS In Our Daily Lives
The involvement of Geographic Information Systems (GIS) in our daily lives is pervasive, influencing and enhancing various aspects across different sectors. The integration of GIS into everyday activities has become integral for decision-making, planning, and optimizing resources. GIS helps city planners and transportation experts to provide them with information like maps, satellite pictures, population statistics, and infrastructure data. GIS helps them make better decisions when designing cities and transportation systems that are sustainable and good for the environment.
The following points elucidate the notable involvement of GIS in our daily lives:
Navigation and Location Services: GIS provides monitoring functions through the visual display of spatial data and precise geographical positioning of monitored vehicles, whereas GPS provides accurate, clear, and precise information on the position and navigation of a monitored or tracked vehicle in real-time and at the exact location.GIS is at the core of navigation applications and location-based services on smartphones. It enables accurate mapping, real-time navigation, and geolocation services, assisting individuals in finding locations, planning routes, and navigating unfamiliar areas.
E-Commerce and Delivery Services: GIS software is a powerful tool for supply chain network planning. It helps determine the optimal location for distribution centers, warehouses, or other supply facilities. GIS is utilized in logistics and delivery services for optimizing routes, tracking shipments, and ensuring timely deliveries. E-commerce platforms leverage GIS to enhance the efficiency of their supply chain and last-mile delivery processes.
Weather Forecasting and Disaster Management: Many states are using GIS dashboard to monitor the rainfall across the state, on a real-time basis, from the data shared by rain sensors installed at various locationsGIS plays a crucial role in weather forecasting and disaster management. It assists meteorologists in analyzing spatial data, predicting weather patterns, and facilitating timely responses to natural disasters by mapping affected areas and coordinating emergency services.
Healthcare Planning and Disease Monitoring: Geographic Information Systems enable the visualization and monitoring of infectious diseases. Additionally GIS records and displays the necessary information that health care needs of the community as well as the available resources and materials. GIS supports public health initiatives by mapping the spread of diseases, analyzing healthcare resource distribution, and assisting in the planning of vaccination campaigns. It aids in identifying high-risk areas and optimizing healthcare service delivery.
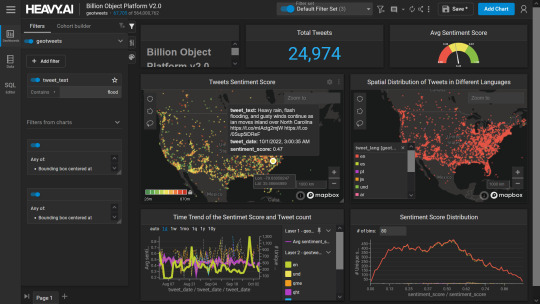
Social Media and Geo-tagging: GIS also helps in geotagging and other location related information in posts, it’s tools can map and visualize the spatial distribution of social media activity. This analysis can reveal trends, hotspots, and patterns in user engagement across different geographic areas. Many social media platforms incorporate GIS for geo-tagging, allowing users to share their location and experiences. This feature enhances social connectivity and facilitates the sharing of location-specific information.
Smart City Initiatives: The Geographic Information System (GIS) offers advanced and user-friendly capabilities for Smart City projects and allows to capture, store and manipulate, analyze and visualize spatially referenced data. It is used for spatial analysis and modeling. It is the cornerstone of smart city planning, enabling the integration of data for efficient urban management. It supports initiatives related to traffic management, waste disposal, energy consumption, and overall infrastructure development.
Education and Research: GIS is increasingly utilized in education and research for visualizing and analyzing spatial data. It enables students and researchers to explore geographic relationships, conduct field studies, and enhance their understanding of various subjects.

Agricultural Management and Precision Farming: Farmers leverage GIS to optimize agricultural practices by analyzing soil conditions, crop health, and weather patterns. Precision farming techniques, facilitated by GIS, contribute to increased crop yields and sustainable farming practices.

Real Estate and Property Management: In the real estate sector, GIS aids in property mapping, land valuation, and site selection. It provides real estate professionals with valuable insights into spatial relationships, market trends, and optimal development opportunities.
Tourism and Recreation: GIS enhances the tourism industry by providing interactive maps, route planning, and location-based information. It assists tourists in exploring destinations, finding attractions, and navigating efficiently.
The broad and varied involvement of GIS in our daily lives underscores its significance as a technology that not only facilitates geographic data analysis but also contributes to the efficiency, safety, and interconnectedness of modern society. As GIS applications continue to evolve, their impact on daily activities is expected to further expand and refine.
#gis#architectdesign#architecture#city#education#geographic information system(gis)#geographical indication
14 notes
·
View notes
Text
Cynthia Kayle: How to Identify Emerging Threats in Your Organization

Introduction
The ability to identify emerging threats within an organization is an essential skill for security professionals, risk managers, and organizational leaders. With threats evolving rapidly due to advancements in technology, global instability, and shifting social dynamics, organizations must be proactive in detecting and mitigating potential risks. Failure to identify these threats early can result in significant damage, including financial losses, reputational harm, and legal repercussions.
This article provides a systematic approach for identifying emerging threats and offers actionable steps to help organizations stay ahead of potential risks. The guidelines outlined are based on best practices in threat management and mitigation strategies, and they incorporate insights from industry experts and leading authorities on security.
1. Develop a Comprehensive Threat Intelligence Framework
A successful threat identification process begins with a structured intelligence framework. Threat intelligence is the collection and analysis of information related to potential threats, including cyber, physical, and reputational risks. Organizations should invest in building or enhancing a comprehensive threat intelligence program that includes both internal and external data sources.
Actionable Steps:
Establish a Threat Intelligence Team: Create a dedicated team of experts responsible for gathering and analyzing intelligence on emerging threats. This team should include representatives from IT, security, legal, compliance, and operations.
Utilize Intelligence Platforms: Leverage industry-specific intelligence platforms like Anomali or CrowdStrike to gather real-time threat data. These platforms provide insights into cyber threats, vulnerabilities, and adversary tactics, techniques, and procedures (TTPs).
Engage in Open-Source Intelligence (OSINT): Regularly monitor news outlets, forums, and social media platforms for signs of emerging risks. Platforms such as Shodan and Have I Been Pwned can also help identify new vulnerabilities and data breaches.
Reference:
Anomali: https://www.anomali.com
CrowdStrike: https://www.crowdstrike.com
Shodan: https://www.shodan.io
2. Perform Regular Risk Assessments
A risk assessment is a critical tool in identifying new and emerging threats. By systematically assessing potential risks, organizations can prioritize resources and develop effective mitigation strategies. Regular cybersecurity risk assessments, physical security audits, and business continuity reviews should be part of an organization’s ongoing security operations.
Actionable Steps:
Conduct Cybersecurity Risk Assessments: Work with cybersecurity professionals to identify and evaluate risks related to your organization’s IT infrastructure and digital assets. Tools like Qualys and Nessus can scan for vulnerabilities and provide reports on existing risks.
Evaluate Physical Security: Regularly audit access control systems, surveillance technologies, and other physical security measures. Identify gaps that could allow unauthorized access or disrupt operations.
Review Business Continuity Plans: Continuously update your business continuity and disaster recovery plans. Ensure that they are capable of addressing new types of disruptions, including those caused by emerging threats such as pandemics or political unrest.
Reference:
Qualys: https://www.qualys.com
Nessus: https://www.tenable.com/products/nessus
3. Monitor External Threat Landscapes
Many emerging threats are influenced by external factors, such as geopolitical developments, global cybercrime trends, and changes in industry regulations. Monitoring these external factors is crucial for understanding how they might affect your organization.
Actionable Steps:
Monitor Geopolitical Events: Keep an eye on global news, government reports, and industry-specific updates that could indicate rising threats. For instance, political instability, economic sanctions, or international trade disputes may result in targeted attacks on organizations operating in certain regions.
Leverage Threat Data Sharing Networks: Participate in industry-specific threat intelligence sharing initiatives like the Financial Services Information Sharing and Analysis Center (FS-ISAC) or Information Sharing and Analysis Centers (ISACs) that provide threat data specific to your sector.
Reference:
FS-ISAC: https://www.fsisac.com
ISACs: https://www.cisa.gov/sector-specific-agencies
4. Utilize Predictive Analytics and AI Tools
As threats become more sophisticated, traditional threat detection methods often fall short. Predictive analytics and AI-driven threat detection can help organizations forecast potential risks before they materialize. These tools can analyze vast amounts of data, identify patterns, and predict future threat behavior.
Actionable Steps:
Invest in AI-Powered Security Tools: Implement solutions like Darktrace or Vectra AI that use machine learning algorithms to detect anomalous behavior and flag potential threats in real-time.
Utilize Predictive Analytics: Employ tools that aggregate and analyze security data across systems to identify emerging trends. Predictive models can help spot anomalies in network traffic or employee behavior before they escalate into larger security incidents.
Reference:
Darktrace: https://www.darktrace.com
Vectra AI: https://www.vectra.ai
5. Foster a Security-Aware Culture
Emerging threats often stem from human error or lack of awareness within the organization. To mitigate this, building a security-aware culture is crucial. Employees must be educated on recognizing suspicious activity and adhering to security protocols.
Actionable Steps:
Conduct Regular Security Awareness Training: Implement cybersecurity training programs that include phishing simulations and social engineering awareness.
Promote Open Communication: Encourage employees to report any suspicious activity they observe, and ensure that incident reporting mechanisms are clear and easily accessible.
Reference:
SANS Institute: https://www.sans.org/cyber-security-skills-training/
Conclusion
Identifying emerging threats in your organization requires a comprehensive, proactive approach. By developing a robust threat intelligence framework, conducting regular risk assessments, monitoring external threats, and leveraging predictive analytics, you can position your organization to recognize risks before they escalate. Furthermore, fostering a security-aware culture ensures that employees play a crucial role in safeguarding against new threats.
#cynthia kayle#CynthiaKayle#ThreatManagement#SecurityExpert#DigitalIntelligence#RiskMitigation#CriminalInvestigations#PublicSafety#SecurityLeadership#CommunityProtection#CrossSectorCollaboration#CrisisManagement
1 note
·
View note