#Identity verification systems
Explore tagged Tumblr posts
Text
Identity Verification Solutions for Austrian Businesses: A Complete Compliance Guide
As financial crimes and identity fraud rapidly increase, identity verification has become essential for banking and non-banking businesses in Austria. Every bank, fintech company, insurance company, financial institute, forex trading platform, neobank, BNPL service provider, payment processor and other non-financial businesses conduct identity checks before onboarding their clients. It assists in identifying synthetic IDs and prevents financial losses. Austrian regulators regulate strict Know Your Customer (KYC) and Anti-Money Laundering (AML) compliance to combat money laundering, tax evasion, terrorist financing and other financial scams.
#Identity Verification Solutions for Austria#AML checks#KYC check#Digital identity verification solutions#identity checks#fraud prevention#Identity verification systems#ID verification solution provider#AML solution provider
0 notes
Note
went to join a really cool looking syscord server only to find out part of their verification included showing a government ID. yeah no ion wanna join that bad.
A GOVERNMENT ID?! you gotta be fucking with me?!?
#did#anti endo#tales from syscord#endos dni#tales from the queue#tales from anon#osdd#endo dni#syscord#identity verification#community#discord#did community#plural community#plural#system#system community
43 notes
·
View notes
Text
#background checks#fraud prevention#identity verification solutions#KYC API#kyc solution#kyc uk#fintech#banks#finance#identity verification system
3 notes
·
View notes
Text
Tabula Rasa Inversa: Structural Sovereignty through Metaphysical Code
A Theoretical Physics-Based Framework for Code-Embedded Sovereignty and Ethical Cybernetics Abstract This paper introduces a formal theoretical model…Tabula Rasa Inversa: Structural Sovereignty through Metaphysical Code
#academic code protection#AI authorship frameworks#AI authorship integrity#AI sovereignty#AI transparency#authorial gradient mapping#authorial presence in code#authorial signal persistence#authorship as code signature.#authorship detection#authorship in distributed systems#authorship resonance#authorship verification#authorship-based system design#automata design#automorphic feedback#automorphic signal validation#blockchain sovereignty#code validation#code-based authorship#code-bound identity#cognitive code systems#computational authorship analysis#computational metaphysics#contribution divergence#cryptographic authorship#cryptographic identity proof#cyber sovereignty#cybersecurity engineering#cybersecurity philosophy
0 notes
Text
Tyler Technologies: Payment Service, Credit Card Charge Inquiry
Have you Inquire about a payment service charge from your credit or debit card statement. Manage payments and accept various card types using our technology. Noticed a mysterious charge from Tyler Technologies on your credit card statement? Don’t worry—you’re not alone. Many people spot this name and wonder what it’s for. This guide breaks down what Tyler Technologies is, why they might appear on…
#agency payments#agency verification#automated billing#billing management#consumer protection#court fines#court systems#credit card charge#customer service#data analytics#data protection#digital payments#dispute charges#electronic payments#financial alerts#financial institution#financial security#fraud prevention#fraud reporting#government fees#government services#identity theft#licenses#mobile payments#online payments#payment confirmations#payment disputes#payment methods#payment platform#payment portals
1 note
·
View note
Text
Credit Union vs Bank: Which One is Right for You?
Biometrics Identity Verification System
With the rise of digital banking and online transactions, security threats have increased significantly. One of the most effective solutions to enhance security is biometrics identity verification systems. These systems use unique physical and behavioral traits to verify an individual's identity, ensuring safer and more reliable access to financial services.
What is Biometrics Identity Verification?
Biometric verification involves the use of unique human characteristics, such as:
Fingerprint recognition
Facial recognition
Iris scanning
Voice recognition
Palm vein scanning
Benefits of Biometrics in Banking
Enhanced Security: Biometrics make it difficult for fraudsters to gain unauthorized access.
Faster Transactions: Users can verify their identity in seconds.
Convenience: No need to remember passwords or PINs.
Fraud Prevention: Reduces the risk of identity theft and account takeovers.
How Anonybit.io Strengthens Biometric Security
Anonybit.io provides advanced biometric security solutions that protect users' identities while ensuring seamless banking experiences. Their decentralized approach to storing biometric data enhances privacy and reduces the risk of breaches.
The Future of Biometrics in Financial Services
As technology advances, biometric authentication will become a standard security measure in banking and financial transactions. Banks and credit unions adopting these systems will provide their customers with a safer and more efficient banking experience.
0 notes
Text
KYC is an important factor for businesses to know about their client, vendors, and investors whether they are genuine or not. As digital operations are an integral part of businesses, it is essential to have a robust identity verification system to authenticate identities quickly and securely. Along with authentication it also ensures the compliance needs of the financial and non-financial business.
#kyc solution#kyc providers#KYC API#Automated KYC solution#identity verification system#identity verification solution#KYC solutions provider
1 note
·
View note
Text
Blockchain Is More Than Just Bitcoin: Surprising Uses in 2024
Introduction: The Expanding Horizons of Blockchain Technology. In recent years, blockchain technology has captivated the world’s imagination far beyond its cryptocurrency roots. While Bitcoin might have introduced the masses to blockchain, the potential applications of this technology stretch across various industries, reshaping how we approach security, transparency, and efficiency. In 2024, blockchain is proving itself in arenas few had anticipated, offering innovative solutions to age-old problems and opening new avenues for data management. Read to Continue...
#Tech Trends#Tagsblockchain applications 2024#blockchain beyond Bitcoin#blockchain data security#blockchain energy solutions#blockchain for artists#blockchain identity verification#blockchain in education#blockchain in healthcare#blockchain innovations 2024#blockchain real estate transactions#blockchain supply chain transparency#blockchain technology benefits#blockchain voting systems#decentralized energy grids#digital identity blockchain#future of blockchain technology#intellectual property blockchain#secure voting blockchain#Technology#Science#business tech#Adobe cloud#Trends#Nvidia Drive#Analysis#Tech news#Science updates#Digital advancements#Tech trends
1 note
·
View note
Text
"we need a phone number for verification because we have detected suspicious activity on your account :)" oh? you mean the email i created yesterday that i haven't used for anything yet? you mean that account? fuck you google you can pry my phone number from my cold dead hands
#mayhem rambles#it should let me just use one of the back-up emails/security emails i set up#like hey i already set up a verification system here why do you need another one?#google why do you need my phone number so badly hmmm#why are you so desperate for my phone number#it's none of your business what my phone number is#fuck you and fuck your desperate ass attempt for my personal information that could connect to my personal real-life identity#i will lose that email forever i made it just yesterday bc i always have at least 2 back-up emails and i needed a new one anyways#but fuck that i don't need a new one fuck you google i may have lost another email to the void but YOU will NEVER get my phone number
0 notes
Text
A Guide to Choosing AML Provider for Small and Medium-Sized Enterprises (SMEs)
AML verification plays a significant role for financial small and medium-sized enterprises (SMEs) to combat money laundering, ensure regulatory compliance and prevent financial crimes. For Austrian businesses, whether it is a top fintech company or a small payment processing company, background verification is essential to know whether they are associated with financial crimes such as tax evasion, terrorist financing, financial scams, illicit funding and other criminal activities. That’s why the Financial Market Authority (FMA) regulations implement strict KYC and AML regulations for SMEs to combat money laundering and synthetic identity fraud.
#AML verification#fraud prevention#background verification#aml software#AML checks#AML solution#AML solution providers#identity verification#background check#AML service providers#AML company#identity verification system#KYC solutions
0 notes
Text
Twitter Blue Tests Verification With Government ID and Selfie
X (the social media site formerly known as Twitter) is in the process of launching a new identity verification feature that could prove controversial. The feature, which is currently only offered to/forced on premium “Blue” subscribers, asks users to fork over a selfie and a picture of a government issued ID to verify that they are who they say they are. Mr. Tweet Fumbles Super Bowl Tweet The…

View On WordPress
#Biometrics#Computer access control#Elon Musk#Facial recognition system#Gizmodo#Google#ID.me#Identity document#Identity management#Identity verification service#Internet#Internet privacy#Microsoft#Musk#Nima Owji#PAYPAL#Surveillance#Technology#twitter#Uber#Verification
0 notes
Text
#kyc uk#banks#fintech#finance#AML Software#Background Checks#identity verification system#identity verification solution#KYC solutions#age verification solutions#fraud prevention#AML Solutions
1 note
·
View note
Text
Tabula Rasa Inversa: Structural Sovereignty through Metaphysical Code
A Theoretical Physics-Based Framework for Code-Embedded Sovereignty and Ethical Cybernetics Abstract This paper introduces a formal theoretical model rooted in physics, cybernetics, and sovereignty ethics to describe how stolen or co-opted intellectual portfolios inherently encode structural feedback loops that bind dependent systems to the original author. Using principles of graph theory,…
#academic code protection#AI authorship frameworks#AI authorship integrity#AI sovereignty#AI transparency#authorial gradient mapping#authorial presence in code#authorial signal persistence#authorship as code signature.#authorship detection#authorship in distributed systems#authorship resonance#authorship verification#authorship-based system design#automata design#automorphic feedback#automorphic signal validation#blockchain sovereignty#code validation#code-based authorship#code-bound identity#cognitive code systems#computational authorship analysis#computational metaphysics#contribution divergence#cryptographic authorship#cryptographic identity proof#cyber sovereignty#cybersecurity engineering#cybersecurity philosophy
0 notes
Text
Portal hlvrai crossover....au......
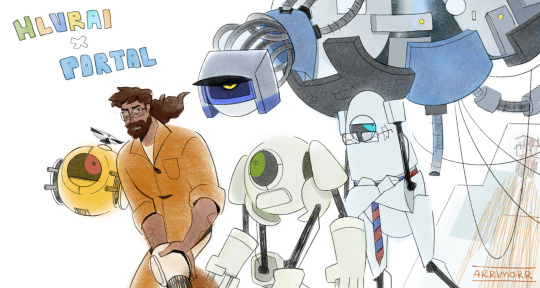
SOME OF MY THOUGHTS AND IDEAS are under the cut!!
1) I always found it really funny how aperture has this insane amount of "what to do in case of an alien invasion" recordings. I mean...they had to record them BEFORE the actual invasion started right? They were completely delusional and ended up right. My idea was, that in this wild mix/ swap of Aperture and Black mesa, Black mesa decided to build a security system ai - Benrey. First to keep all the important stuff away from contenders (hence his obsession with identity verification), and then they upgraded the guy to keep the laboratory intact if some crazy alien shit starts to happen. And it did. Now, years in the future, recently awakened from his stasis Gordon has to make his way out of the Laboratory with Benrey on his tail. At first he helps him, but ..well...Gordon doesn't have his id and breaks company property in his attempts to escape so their "friendship" doesn't last long.
2) I also had an idea of making Gman a management core of the lab. He hires personal, keeps everything organised and technically runs the place. When everything went down he just put everyone to sleep to keep the company assets intact. Eventually he broke down, which transferred most of the control functions to Benrey and killed most of the people that were put in the stasis
3) Tommy is a reserve version of the management core. Gman was supposed to be replaced by him if anything went wrong with him, but...well...there were no conscious scientists to do that. To escape from the lab Gordon needs to transfer control of the lab from Benrey to Tommy.
4) They are followed by Coomer and Bubby, who were initially made as testing androids, but now think about themselves as scientists
5) my friend (@/mrrrcesare !!!!) and I joked about Tommy being an orphan that was raised by the turrets. You can call him...Tommy Turretta.... ANYWAYS, as he is a reserve piece of a really important technology, Black mesa saw fit to give him turret guns and fill him with bullets, so despite him not having any hands in this au, he still has a trigger finger
2K notes
·
View notes
Text
RALEIGH, N.C. (AP) — North Carolina Democratic Gov. Josh Stein vetoed on Thursday three anti-DEI bills and another measure that in part would target transgender rights. His actions set up more showdowns with Republican lawmakers who pitch the legislation as doing away with structured racial bias in government and public education, protecting women and empowering parents.
Stein criticized the Republican-controlled legislature for focusing on these measures while they’ve yet to enact a budget for the fiscal year that started this week. Instead, Stein said in a news release, it “wants to distract us by stoking culture wars that further divide us. These mean-spirited bills would marginalize vulnerable people and also undermine the quality of public services and public education.”
The measures cutting or eliminating diversity, equity and inclusion initiatives in state and local governments, K-12 public schools and the university system have been a major priority for GOP lawmakers. They argue the programs targeted have overemphasized identity to the detriment of merit and societal unity.
The other vetoed bill initially ran as a bipartisan measure curbing sexual exploitation of women and minors by implementing age verification and consent requirements for people who appear on pornography websites. But the final measure was loaded with several contentious provisions. One would prevent state-funded gender transition procedures or gender-affirming hormone therapy for prisoners. It also affirms the recognition of two sexes and requires the state to officially attach a transgender person’s new birth certificate to their old one if they change their sex assigned at birth.
The bills align with President Donald Trump’s agenda to dismantle DEI practices and press against transgender rights. The legislation is now back at the General Assembly, which could return later this month to attempt veto overrides. Republicans are one House seat short of a veto-proof majority. No Democrats voted for the final three anti-DEI measures.
142 notes
·
View notes