#Internet Download Manager Crack
Explore tagged Tumblr posts
Text

IDM Latest Crack 2024
Download link: https://tinyurl.com/3b88sye2
Pass: 2024
9 notes
·
View notes
Text
Abducted
Ken was out at the mall for a day to himself. Just out of a situationship, he was trying to get his head out of this funk he had been stuck in. He left his favorite k-pop store and clothes shopping when he finally made his way home. The bus towards his apartment was eerily quiet tonight, only him, the driver, and some man wearing some form of shroud were on the dimly lit bus complete with color changing led atmosphere lighting.
When he got to his stop, the shrouded figure followed him, but Ken's clouded mind didn't allow him to perceive it yet. He walked into his little studio apartment and quickly headed into the restroom to do what every conventionally attractive male usually does when he has new clothes, take thirst trap photos.

The shrouded figured entity lodged the studio window open while Ken remained in the restroom admiring his own physique. As Ken turned off the light and returned to the dark apartment he bumped into the figure. Too stunned to scream, the tall dark figure knocked Ken out and tied him up on the ground.
Revealing itself to no one, the shrouded figure took off its cloak to reveal its status as an extraterrestrial alien. Its dark grey skin and giant deep dark eyes gazed at the passed out college student on the ground. Placing one finger-like digit on Ken's head, the alien began to light up as he began absorbing a new form.
Slowly, the giant lanky grey alien form began shrinking in height, structural bones cracked as musculature grew into slabs on the aliens arms, legs, chest, and stomach. Hair began sprouting on its head as the giant dark eyes it previously had turned into tinier ones with pupils and white areas. The alien began to blink its new eyelids and move every facial feature on its new face as if trying on a new item of clothing for the first time.
The real Ken began waking up to see the alien beginning to take his form, shocked back into silence. He wouldn't believe what was happening in front of him if someone else had told him about it. Moments later the alien noticed Ken waking up and moved to tie up the human's mouth and a tossed shirt on the floor to hide his eyes. All Ken could do was squirm as he already knew the truth that an imposter was stealing his identity. As his muffled screaming and wrapped up limbs couldn't be heard as he lived on the first floor of the complex.
An unclothed doppelganger of Ken now stood above the real one. The alien looked at the one on the floor wearing clothing and began his process to emulate a real human. Rifling through the studio, it searched for clothing pieces to resemble an outfit.

Upon settling on random pieces, the alien began tinkering with Ken's phone left in the restroom. Unbeknownst to the piece of technology, it unlocked itself for the imposter as it then began downloading aspects of Ken's life from the many messages, internet search history, and of course images. The most recent ones catching the aliens attention, as it then put down the phone and began recording so it can begin emulating things the real Ken did.
The real Ken managing to get the shirt off his eyes and squirming enough to witness it all happen second by second.
The real Ken inched closer before finally managing to get the cloth out of his mouth. He yelled at the alien, catching him off guard. "Why are you doing this to me?!" Instead of flinching the alien turned nearly immediately and then approached Ken on the floor. Picking him up easily to sit him up on a nearby couch, the alien then moved in towards Ken's face. As the human continued to yell hysterically and eventually bite towards the alien in a sad attempt to defend himself, the alien placed their lips together. To many, finding out what it's like making out with yourself would be an erotic dream, but to the Ken it was a nightmare. He moved in protest and continued to scream but eventually the screams felt like they were being sucked right out of him.
When the alien moved away from Ken, the alien cleared his throat. "Testing human voice one, two, three. Thank you human Ken for that audio assimilation protocol. It's a necessity to allow us to communicate in the tongues of the dominant species. You may want to continue protesting, but that will no longer be a possibility, the protocol requires a complete stripping of the original specimen's communication ability."
Sure enough, Ken tried to speak but no sound was coming from his unblocked mouth anymore. The alien moved to get a syringe-like device from his cloak on the ground, approaching the real ken. "This is now the end of your donation period. Thank you for your participation, my kind will forever thank you for your participation."
The alien stabbed the syringe into Ken and quickly it took it's effect. Bones cracked as the stretched and reformed to make Ken significantly taller than before. Musculature shrunk into sinewy arm-like limbs. Hair began disappearing on his head as giant dark eyes took over his human ones. Ken now looked like the alien before his transformation. And before he could protest, the new "Ken" came up and "knocked him out" or so did the original Ken think. The new Ken turned from the now dead alien and returned back to his explicit examination of his new form.

His exploration continued...something was calling his attention and he was ready to see how the human body worked.
276 notes
·
View notes
Note
The SOLDIERS each have a pretty popular Tik Tok page. What do they post?
Sephiroth: Has never downloaded the app, doesn't know what TikTok is, doesn't want to know, doesn't care. The scrolling, constant flashing and sound loops give him a headache and he refuses to engage. And yet his TikTok has 12.7 million followers. Managed entirely by PR (and Zack, who insists he's "preserving history"), the page is made up of candid videos of Sephiroth doing mundane things—doing paperwork, mid-battle, slicing an apple with Masamune, slowly turning his head when someone says his name. He has no idea any of it is online. Most viral video: him staring out a rainy window for three minutes while Mad World by Gary Jules plays in the background.
Angeal: Posts wholesome shirtless cooking videos. The first one happened because his apartment got too hot and he figured "shirtless is shirtless, it's not that deep." The comments were overwhelmingly thirsty, but Angeal, bless his dense little heart, mistook it all for body positivity. He now regularly says things like "All bodies are good bodies, now let's talk meatballs" while cracking eggs with forearms carved by the gods. He earnestly replies to comments like "sit on me, chef" with things like "Make sure to hydrate and stretch!" Thinks "I'll take his tip 😩" is about culinary advice. No one tell him.
Genesis: Was supposed to be a ✨gorgeous aesthetic page✨. Soft lighting, poetry recitations, posed videos of himself while Lana Del Rey plays in the background. For a few weeks, it was art. Then someone left a comment saying "You're not even the hottest SOLDIER," and he snapped. Now his page is 80% drama. Live readings of anonymous follower DMs. Stitches where he critiques and judges people. He almost got banned when he stitched a video from Rufus' page where he was showing his usual morning skincare routine and called him a "clown with a ring light."
Zack: The definition of TikTok influencer. Does every dance trend with too much energy, lip-syncs to audios that have been dead for a week, posts gym thirst traps, POV videos, and prank videos that mostly involve trying to jump-scare Sephiroth (and failing).
Kunsel: Banned within his first 24 hours on the platform. His first and only video started as a PSA about internet safety. He opened with: "TikTok isn't secure. I will now demonstrate how easily you can be doxxed." Caption: "Comment below if you consent to be doxxed as a learning exercise :)"
User0954788 commented: "shut up nerd."
The user was Reno. Kunsel revealed his name, full address, Shinra ID number, and a video of him crying at a karaoke bar in one stitch.
#ff7#ffvii#final fantasy 7#final fantasy vii#sephiroth#genesis rhapsodos#angeal hewley#zack fair#kunsel#crisis core#headcanons
120 notes
·
View notes
Text
Crack NEET and JEE with Confidence: Discover the Best Apps
youtube
Hey! Future doctors and engineers! Are you on the search for the Best App for NEET Preparation and the Best App for JEE Preparation? Feeling a bit lost in the ocean of online resources? "You're in luck and in the right place — the ultimate destination for your success!"Get ready to discover the secret weapon that top rankers are using to ace these tough exams.
Discover Your True Potential with the Top NEET & JEE Prep App.
Our app is meticulously designed to be your ultimate companion on this crucial journey. We understand the pressure and the need for focused, effective preparation. That's why we've packed it with features that will not only help you understand complex concepts but also make you fall in love with learning.
What makes our app the top choice?
Engaging Video Lectures: Say goodbye to boring lectures! Our expert educators break down even the most challenging topics into easy-to-understand modules with real-life examples. You'll actually enjoy learning!
Interactive Quizzes & Practice Tests: Test your knowledge instantly with our engaging quizzes after each topic. Sharpen your problem-solving skills with a vast library of practice questions.
Realistic Mock Tests: Experience the exam environment before the actual day. Our mock tests are designed to simulate the NEET and JEE patterns, helping you manage your time and reduce exam-day anxiety.
Smart Personalised Paths: Learning that grows with you — matching your style, speed, and strengths. Our app adapts to your learning pace and strengths, focusing on areas where you need the most help.
Doubt Clearing Sessions: Got a tricky question? Our experienced teachers are just a click away to resolve all your doubts until its crystal clear.
Ready-to-Use Study Materials: Neatly arranged notes and revision content at your fingertips, anytime you want.
Don't Miss Out on Your Dream Score!
Time is ticking, and the competition is fierce. Every moment you spend with the right resources brings you closer to your dream medical or engineering college. Our app is your secret weapon to stand out and succeed. Feel the excitement of mastering concepts, the confidence of scoring high in mock tests, and the anticipation of a bright future.
Limited-Time Offer: Join our community of successful students today and get exclusive access to bonus study materials and early bird discounts! Don't let this opportunity slip away.
Frequently Asked Questions (FAQs)
Is this app helpful for Class 11 & 12 students planning ahead for NEET/JEE?
Absolutely! Building a strong foundation early is key, and our app offers content that can help you grasp fundamental concepts.
Can I study the full NEET and JEE syllabus using this app?
Yes, our app comprehensively covers the latest syllabi for both NEET and JEE.
Can I study offline using this app?
Yes, many of our study materials and video lectures can be downloaded for offline access, allowing you to study even without an internet connection.
How often are new content and mock tests added?
We regularly update our content and add new mock tests to keep you aligned with the latest exam patterns and trends.
Your journey to becoming a successful doctor or engineer starts here. Stop battling against your own mind and start working withit. And experience the power of focused, efficient learning!
Download the Best App for NEET Preparation and the Best App for JEE Preparation now and take the first step towards your dream!
2 notes
·
View notes
Text
I once played hooky from work to be an extra in a historical docudrama about the Revolutionary War, and during one of the many waiting moments, someone* started a debate about what kind of smartphone each of the Founding Fathers would have had. We ended up concluding:
George Washington has the most recent iPhone, though he makes a big deal about not knowing which one he's on. He only has ten apps on his phone, and uses all of them.
Thomas Jefferson also has an iPhone (all of the Virginians do) and downloads every app he hears about, against the advice of Madison. He has been hacked three times that he knows about, and is angry at the internet for ever charging money for stuff online. He keeps a second phone for "personal" texts, and thinks no one else knows (everyone knows).
Ben Franklin had the first Palm Pilot, then the Blackberry, before moving on to an Android. He still misses the fold-out keyboard from the Palm Pilot days.
John Adams has loaded an open source OS onto his phone, which he tweaked to fit his needs. It works, but the messaging apps are wildly incompatible with any other OS, so he mostly gets texts from Abigail, who has the other phone that he engineered like this.
Alexander Hamilton has an Android, but somehow managed to be the guy who taught Washington how to use his iPhone. He's constantly texting and emailing, and no one knows how he keeps up with it all.
James Madison is also constantly texting, but mostly Jefferson.
*Ok, it was me. I'd finished Wikipedia-ing everything about the historical moment we were filming, and I was tired of the extra making non-stop Star Wars jokes (the principle actor there voiced Obi Wan in the animated series). If you're going to crack jokes on a period movie set, at least make them historically relevant.
#founding fathers#adventures of a movie extra#george washington#alexander hamilton#james madison#john adams#ben franklin#anachronistic speculation#no i did not tell my boss where i was that day
19 notes
·
View notes
Text
Better Off Alone (Version B)
I do better when I'm alone It just suits me to never leave my home To not go out and find some trouble brewing And the freed to have lost care about anything I care about the world around me just not enough to ever do something for it
So I spend my free time alone Watching TV on the internet a thousand of my childhood wishes came true with the advent of downloads off a high speed And those are good statistics, I'll tell you that So wipe the worry from your eyes I'm swearing that this will work
I do better when I'm alone I don't go out with friends because I can't be tempted And more importantly, I don't have any friends I left every one of them behind for a life of bottles, bleeding and needle point embroidery
So I'll keep my time alone No one can twist my head No one can ever break my heart No one can do anything if I let no one around
I do better when I'm alone I strive on sleeping on a mattress on the floor next to a pile of laundry that always smells like socks When I'm on the edge of being homeless The rent checks going to bounce but I'll blame it on my land lord and manage to buy myself a month Once a con man, always a liar That doctrine is what you need to believe
I never meant to be the crack in your mirror But sometimes we're made for a purpose
I do better when I'm alone I don't need the love of another anymore I don't need the stress of loving someone else I don't need anything
This is the kind of shit I tell myself at night so I can sleep.
#writers and poets#poems on tumblr#original poem#poem#poetry#spilled thoughts#spilled feelings#spilled writing#writing#my writing#spilled poetry#spilled emotions#spilled words#writers on tumblr#poets and writers#creative writing#writerscommunity#writer#crmsnmth#Better Off Alone#cynicism#cynical#I Don't care
5 notes
·
View notes
Note
Pelipper mail! It is wearing a lei, and unceremoniously drops a phone in your lap before flying off. The phone has a novelty case on it, displaying a beach at sundown and the phrase "It's always sunny in Margaritaville!"
There is a small crack in the screen that seems to shimmer and shift with the light when you tilt the phone this way and that. The default background is, predictably, a beach vista. There is a single, black boat on the water, and while you can't make out their features you can see a half dozen people on the deck looking directly at you. If you try to change the background the boat and the water it's on will somehow always reappear. The people seem to come and go as they please, but are always looking directly at you when they show up. It makes you feel vaguely nauseous.
The note attached reads:
"Ahoy hoy! Sorry to hear ya fried your old phone, hope there wasn't too much good stuff on there. Here's a new one, with a few new buddies included! You can change out the case if ya want, of course, but if I was you I definitely wouldn't let that crack get any bigger 😅
Keep it sunny, sailor!
-@poke-jimmy-butchett "
y'know what i'm PRETTY sure i told clatterclatter to tell you it was okay, i could just grab a secondhand phone from PEX, i didn't need anything haunted, but of FUCKING COURSE the little shit-
well. it's here now and it works, or at least it downloaded rotumblr and logged me in without any trouble, so i guess i'll just uh. i'll just make my peace with the dudes on the boat for the time being. or something.
clatterclatter's still got my old phone by the way but i managed to turn the internet off and i think it's too dumb to figure out turning it back on. i hope. the thing'll blow up on it sooner rather than later anyway. probably literally. i swear it was starting to smoke by the time i got it back
teach me to leave electronics unattended in the same room as a rotom i guess. even if it's never shown any inclination to leave the lawnmower previously
thanks jimmy. are you uh. having fun in the haunted margaritaville or
4 notes
·
View notes
Text
In today’s digital world, injustice lurks in the shadows of the Facebook post that’s delivered to certain groups of people at the exclusion of others, the hidden algorithm used to profile candidates during job interviews, and the risk-assessment algorithms used for criminal sentencing and welfare fraud detention. As algorithmic systems are integrated into every aspect of society, regulatory mechanisms struggle to keep up.
Over the past decade, researchers and journalists have found ways to unveil and scrutinize these discriminatory systems, developing their own data collection tools. As the internet has moved from browsers to mobile apps, however, this crucial transparency is quickly disappearing.
Third-party analysis of digital systems has largely been made possible by two seemingly banal tools that are commonly used to inspect what’s happening on a webpage: browser add-ons and browser developer tools.
Browser add-ons are small programs that can be installed directly onto a web browser, allowing users to augment how they interact with a given website. While add-ons are commonly used to operate tools like password managers and ad-blockers, they are also incredibly useful for enabling people to collect their own data within a tech platform’s walled garden.
Similarly, browser developer tools were made to allow web developers to test and debug their websites’ user interfaces. As the internet evolved and websites became more complex, these tools evolved too, adding features like the ability to inspect and change source code, monitor network activity, and even detect when a website is accessing your location or microphone. These are powerful mechanisms for investigating how companies track, profile, and target their users.
I have put these tools to use as a data journalist to show how a marketing company logged users’ personal data even before they clicked “submit” on a form and, more recently, how the Meta Pixel tool (formerly the Facebook Pixel tool) tracks users without their explicit knowledge in sensitive places such as hospital websites, federal student loan applications, and the websites of tax-filing tools.
In addition to exposing surveillance, browser inspection tools provide a powerful way to crowdsource data to study discrimination, the spread of misinformation, and other types of harms tech companies cause or facilitate. But in spite of these tools’ powerful capabilities, their reach is limited. In 2023, Kepios reported that 92 percent of global users accessed the internet through their smartphones, whereas only 65 percent of global users did so using a desktop or laptop computer.
Though the vast majority of internet traffic has moved to smartphones, we don’t have tools for the smartphone ecosystem that afford the same level of “inspectability” as browser add-ons and developer tools. This is because web browsers are implicitly transparent, while mobile phone operating systems are not.
If you want to view a website in your web browser, the server has to send you the source code. Mobile apps, on the other hand, are compiled, executable files that you usually download from places such as Apple’s iOS App Store or Google Play. App developers don’t need to publish the source code for people to use them.
Similarly, monitoring network traffic on web browsers is trivial. This technique is often more useful than inspecting source code to see what data a company is collecting on users. Want to know which companies a website shares your data with? You’ll want to monitor the network traffic, not inspect the source code. On smartphones, network monitoring is possible, but it usually requires the installation of root certificates that make users’ devices less secure and more vulnerable to man-in-the-middle attacks from bad actors. And these are just some of the differences that make collecting data securely from smartphones much harder than from browsers.
The need for independent collection is more pressing than ever. Previously, company-provided tools such as the Twitter API and Facebook’s CrowdTangle, a tool for monitoring what’s trending on Facebook, were the infrastructure that powered a large portion of research and reporting on social media. However, as these tools become less useful and accessible, new methods of independent data collection are needed to understand what these companies are doing and how people are using their platforms.
To meaningfully report on the impact digital systems have on society, we need to be able to observe what’s taking place on our devices without asking a company for permission. As someone who has spent the past decade building tools that crowdsource data to expose algorithmic harms, I believe the public should have the ability to peek under the hood of their mobile apps and smart devices, just as they can on their browsers. And it’s not just me: The Integrity Institute, a nonprofit working to protect the social internet, recently released a report that lays bare the importance of transparency as a lever to achieve public interest goals like accountability, collaboration, understanding, and trust.
To demand transparency from tech platforms, we need a platform-independent transparency framework, something that I like to call an inspectability API. Such a framework would empower even the most vulnerable populations to capture evidence of harm from their devices while minimizing the risk of their data being used in research or reporting without their consent.
An application programming interface (API) is a way for companies to make their services or data available to other developers. For example, if you’re building a mobile app and want to use the phone’s camera for a specific feature, you would use the iOS or Android Camera API. Another common example is an accessibility API, which allows developers to make their applications accessible to people with disabilities by making the user interface legible to screen readers and other accessibility tools commonly found on modern smartphones and computers. An inspectability API would allow individuals to export data from the apps they use every day and share it with researchers, journalists, and advocates in their communities. Companies could be required to implement this API to adhere to transparency best practices, much as they are required to implement accessibility features to make their apps and websites usable for people with disabilities.
In the US, residents of some states can request the data companies collect on them, thanks to state-level privacy laws. While these laws are well-intentioned, the data that companies share to comply with them is usually structured in a way that obfuscates crucial details that would expose harm. For example, Facebook has a fairly granular data export service that allows individuals to see, amongst other things, their “Off-Facebook activity.” However, as the Markup found during a series of investigations into the use of Pixel, even though Facebook told users which websites were sharing data, it did not reveal just how invasive the information being shared was. Doctor appointments, tax filing information, and student loan information were just some of the things that were being sent to Facebook. An inspectability API would make it easy for people to monitor their devices and see how the apps they use track them in real time.
Some promising work is already being done: Apple’s introduction of the App Privacy Report in iOS 15 marked the first time iPhone users could see detailed privacy information to understand each app’s data collection practices and even answer questions such as, “Is Instagram listening to my microphone?”
But we cannot rely on companies to do this at their discretion—we need a clear framework to define what sort of data should be inspectable and exportable by users, and we need regulation that penalizes companies for not implementing it. Such a framework would not only empower users to expose harms, but also ensure that their privacy is not violated. Individuals could choose what data to share, when, and with whom.
An inspectability API will empower individuals to fight for their rights by sharing the evidence of harm they have been exposed to with people who can raise public awareness and advocate for change. It would enable organizations such as Princeton’s Digital Witness Lab, which I cofounded and lead, to conduct data-driven investigations by collaborating closely with vulnerable communities, instead of relying on tech companies for access. This framework would allow researchers and others to conduct this work in a way that is safe, precise, and, most importantly, prioritizes the consent of the people being harmed.
11 notes
·
View notes
Text
GOTG Review: Hypnospace Outlaw
This is the next game in my Backlog Roulette series, where each month I spin a wheel to randomly select a game on my massive backlog that I must play (though not necessarily to completion). These wheel spins occur on the monthly preview episodes I co-host with my friends on The Casual Hour podcast.
Both of my parents were educators at my elementary school (they're retired now.) Mom was a 3rd grade teacher and Dad taught gym. They both would stay after classes were over to work on lesson plans or grade papers or move equipment, and I got to freely choose which one to spend time with before we got to go home. With Dad, I would mostly practice free throws in the gym (though I never got any good at them). But with Mom, I’d often get to play on her computer (when I wasn’t watching Digimon Adventure on her classroom TV.
That was probably my first real experience with computers. I’d play things like Oregon Trail II (the best one, by the way) or an awful typing program called PAWS featuring a freaky Cheshire-Cat-like mascot. But sometimes, I would load up Netscape Navigator and just poke around on the late ‘90s internet.
I hated this cat so much as a kid.
I only remember bits and pieces of that time online. A Sokoban block-pushing puzzler, a Super Mario Bros. fan game with all-new levels, some first-person hovercraft racer that had multiplayer LAN capabilities (I’ve never been able to find that game since, it’s definitely not Hover! by Microsoft.) a fansite for the Sonic Underground cartoon. Even with my fragmented memory, I remember the joy and adventure I had just digging around. Anything could be around that next corner, and that was half the fun.
Hypnospace Outlaw is the closest I’ve ever come to reliving those formative computer experiences. Set in an alternate 1999, you are thrust into Hypnospace — an internet stand-in that’s part GeoCities and part forum chatroom — and are asked to moderate and police this online Wild West.
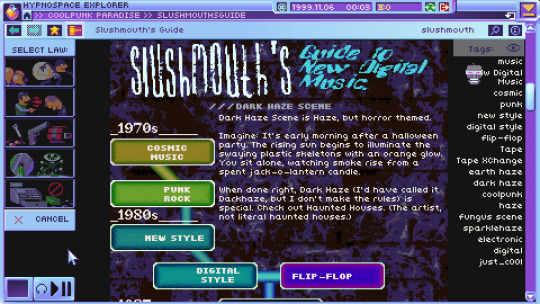
Developer Tendershoot has nailed the tone and aesthetic of this era. The highly compressed bitmap images, the way pages auto-play (incredible) music when they load, the terrible, terrible fonts, the fileshare servers that are completely inscrutable unless you know exactly what you’re looking for — it’s all just perfect. And it’s not just Hypnospace. The game has its own little desktop computer experience complete with email, virtual pets, a download manager and more. It reminds me of Cibele or Her Story, but much more freeform and robust. But all that is just aesthetic — the game itself is pretty cool too. As a Hypnospace moderator, you’re given little jobs as you explore the various pages and zones of the browser: Take down some copyrighted material here, censor some threatening speech there, find some lost files that are hanging around…somewhere. Some of these tasks just require you to pay close attention to the pages themselves, while others force you to put on your hacker cap as you cross reference ID codes with unlisted pages, crack passwords or decrypt files, all while a corporate conspiracy bubbles up around you.
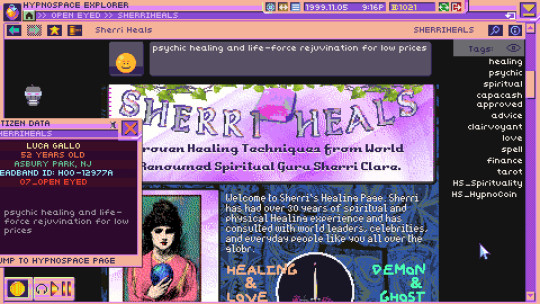
It’s truly satisfying to use your online sleuthing skills to their fullest. And whether you’re stopping a virus from breaking the virtual world or just banning a kid who can’t seem to stop making offensive webcomics, you just feel this sense of power.
In many ways, Hypnospace Outlaw the platonic ideal of the concept of late-90s computing. I do wonder if that hyper-specific aesthetic and mechanics gives it too narrow of an audience, but as someone who is part of that narrow audience, I found my experience with it to be incredibly fun. And it’s one I won’t soon forget.
5 notes
·
View notes
Text
Benefits Of Kmspico Microsoft Windows Activator

KMSPICO works as an activation software that grants users the ability to install Windows and Microsoft Products for both free or for a lifetime. It's easy-to-use and comes with a smaller software package that can be easily installed. Furthermore, it is completely safe to use as there are no viruses nor malware in it.
There is no need to generate product keys.
It's no mystery that MS products tend to cost a lot. Nonetheless, there exist ways around paying for these heftily priced products. One method utilized is by using activation. This program allows the activation of pirated versions of Windows, as well as other Windows products, for no cost. The most notable feature is the fact that this tool is virus- and malware- free.
The application operates by interacting with a trusted server, which holds various authorized keys for Windows Activation. It's important for users to understand that all systems cannot be activated with panacea. It is also not compatible with all Microsoft Office versions.
Many people have claimed that an antivirus program has advised against downloading and installing kmspico windows 10 due to its alleged shadiness and connection with malware. Despite being warned, the KMSPICO tool continues to be used regularly by those who seek a cost-effective and dependable way of activating their pirated Windows. This holds especially true for those students who are unable to purchase a licensed version of Microsoft's software.
No risk of Fraude detection.
KMSpico acts as a fake key management service server. KMS Servers are utilized to license Microsoft applications for organizations with large volumes. KMSPICO can infringe Microsoft's service agreements and result in software piracy. Moreover, using this software can lead to legal troubles since it infringes copyright law.
Many cybersecurity experts advise against obtaining KMSPICO. These cheat tools tend to be distributed via fake downloading portals, search engines, and sales websites. These may be accompanied by self-signed certificates that attempt to make them seem authentic. These programs can potentially pose a danger as being Headless Trojans or Malware. This renders them hard to recognize by anti-virus programs.
KMSPICO may cause software activations or pop-up warnings and inhibit users' access to updates, support, and other features available only through licensed products. In addition, this application can lead users to malicious websites that aim to gather personal data or inflict viruses. To prevent these threats, only utilize a legitimate program that is also free.
KMSpico is easy to use and does not contain any viruses or malware that can harm the computer.
KMSpico is easy to use and does NOT contain any virus or malicious code that can damage the computer. It does NOT rely on an Internet connection and will not make the computer sluggish or perform poorly. Its installation and usage are simple.
KMSPICO supports both the modern as well as the vintage editions of both Windows® and MS Office®. It utilizes a software program known as KMS, which communicates with a remote server for activating Microsoft software. Unlike some activators, kmspico for windows 11 does NOT install any patches or cracked versions of the OS and remains updated frequently.
kmspico can be downloaded for FREE from reputable websites and used to reactivate Microsoft Products for ever. It is a simple tool that doesn't require any technical knowledge to operate. It's a straightforward tool to operate that doesn't require any technological knowledge. It can be used to both conserve money while still obtaining the highest quality features from branded Microsoft software.
The lifetime license is valid for two years.
KMSPico ranks among the select few activators that grants a perpetual license. It supports activating both Microsoft Windows and Microsoft Office Products, which include the most recent version of Windows 10. It supports using both 32- and 64-bit systems. Unlike many other activator software, this one is not obstructed by a complicated installation and can be downloaded and utilized for free.
KMSPico, which is frequently employed by piraters to circumvent Microsoft licensing requirements, is plagued by numerous flaws and should never be used. It is particularly dangerous if it's downloaded through a phishing website. It is capable of modifying system configurations and restricting access control to disaster recovery and backup images. It's important that cybersecurity, legality, and security are given a higher priority when selecting software licenses and activations. This explains why using authentic Microsoft software is preferred. Furthermore, this approach ensures the compliance with copyright legislation and supports software authenticity. Additionally, it can prevent users from incurring expensive license fees by preventing unauthorized installation.
KMSPICO can be used free of-charge and permanently unlock Microsoft Windows and all other products. It's easy to use and relatively small in size, making it very easy for users to set up. KMSPICO is completely safe to use and doesn't include any virus or malicious code.
There is no need to purchase product keys anymore.
It's no surprise that purchasing Microsoft can become expensive. Nonetheless, there exist ways around paying for these heftily priced products. One method utilized is by using activation. This program allows the activation of pirated versions of Windows, as well as other Windows products, for no cost. The most notable feature is the fact that this tool is virus- and malware- free.
The application operates by interacting with a trusted server, which holds various authorized keys for Windows Activation. It's important for users to understand that all systems cannot be activated with panacea. It is also not compatible with all Microsoft Office versions.
Many people have claimed that an antivirus program has advised against downloading and installing kmspico windows 10 due to its alleged shadiness and connection with malware. Despite being warned, the KMSPICO tool continues to be used regularly by those who seek a cost-effective and dependable way of activating their pirated Windows. This applies particularly to students who may lack the funds to purchase a licensed version of Windows.
No risk of Fraude detection.
KMSpico acts as a fake key management service server. KMS Servers are utilized to license Microsoft products for larger organizations. KMSPICO can infringe Microsoft's service agreements and result in software piracy. Moreover, using this software can lead to legal troubles since it infringes copyright law.
Many cybersecurity experts advise against obtaining KMSPICO. These cheat tools tend to be distributed via fake downloading portals, search engines, and sales websites. These programs may also contain self-signed certificates, attempting to make them look legitimate. These programs can pose a threat because of being infected with trojan-like and potentially infected malware, which can make them extremely difficult for antivirus software to identify.
KMSPICO may cause software activations or pop-up warnings and inhibit users' access to updates, support, and other features available only through licensed products. In addition, this application can lead users to malicious websites that aim to gather personal data or inflict viruses. To minimize these risks, ensure that the software utilized is both legitimately and completely free.
KMSpico is easy to use and does not contain any viruses or malware that can harm the computer.
KMSpico is easy to use and does NOT contain any virus or malicious software that can infect or damage the computer. It does NOT rely on an Internet connection and will not make the computer sluggish or perform poorly. Its size of the software is compact, making it easy for users to easily set up and utilize.
KMSPICO supports both the modern as well as the vintage editions of both Windows® and MS Office®. It utilizes a software program known as KMS, which communicates with a remote server for activating Microsoft software. Unlike some activators, it doesn't require installing any patches or cracked operating systems, and it is frequently updated.
kmspico windows 10 can be downloaded for FREE from reputable websites and used to reactivate Microsoft Products for ever. It is a simple tool that doesn't require any technical knowledge to operate. It's a straightforward tool that doesn't require any technological knowledge. It allows users to acquire a discounted price while still getting the superior features that come with a licensed Microsoft system.
A lifetime license is available for purchase.
KMSPico ranks among the select few activators that grants a perpetual license. It supports activating Microsoft Office and Windows products, which include the most recent version of Microsoft. It supports using both 32- and 64-bit systems. Unlike many other activators, this one does not need any complicated installation and can be downloaded and used immediately.
KMSPico, which is frequently employed by piraters to circumvent Microsoft licensing requirements, is plagued by numerous flaws and should never be used. It is particularly dangerous if it's downloaded through a phishing website. It may also modify system configurations and obstruct access to recovering options such as shadow volumes. It's important that cybersecurity, legality, and security are given a higher priority when selecting software licenses and activations. This explains why using authentic Microsoft software is preferred. Additionally, this technique ensures that software is in compliance and authenticated. Additionally, it can prevent users from incurring expensive license fees by preventing unauthorized installation.
3 notes
·
View notes
Text
How NEET SS App Helps You Save Time and Study Smart
There is not enough time when preparing for super specialty exams. This is where a NEET SS app is a must. Each app has some smart features, such as the ability to add bookmarks, reminders for topics, quick revision cards, and you can even track your performance in real-time! These features help to make your study habit effective and focused. Instead of browsing through the internet for study resources, everything is presented in one convenient place, organized intuitively. Most NEET SS apps have mock test series built in, which replicate the exact format of the real exam to help with time management during your exam. If your aim is to crack NEET SS, downloading a good NEET SS app should be your first and foremost step!
0 notes