#IoT IAM
Explore tagged Tumblr posts
Text
Securing the Future: The Rise of IoT Identity and Access Management
In a world increasingly reliant on connected technologies, the Internet of Things (IoT) has emerged as a transformative force, reshaping industries, economies, and daily life. From smart homes and wearable devices to industrial automation and connected healthcare, IoT is creating a hyper-connected digital environment. With this transformation comes a significant challenge: managing and securing…

View On WordPress
#business#Business Intelligence#cybersecurity#IAM solutions#Identity Access Management#identity and access management#identity and access management tools#Identity Management#identity management for internet of things#identity management solutions#identity management system#Information Technology#IoT IAM#IoT Identity and Access Management#iot identity management#IoT Security#technology
0 notes
Text
Iot Identity and Access Management (IAM) Market Trends, Top Vendors and Growth Prospects
According to a new report published by Allied Market Research, titled, “Iot Identity And Access Management (Iam) Market,” The iot identity and access management market size was valued at $4.9 billion in 2021, and is estimated to reach $47.2 billion by 2031, growing at a CAGR of 25.4% from 2022 to 2031.
Identity and access management (IAM) is the discipline that enables right individuals to access right resources at the right times for the right reasons. IoT devices are focused on connecting things, people, tools, and applications, and IoT identity access management provides end-to-end encryption, overload detection, and unauthorized access removal to help build strong security features.

Rapid digitization toward business operations and an increase in integration of IAM with IoT devices aided in propelling the growth of global IoT IAM market. Moreover, cultural shift from traditional IAM to IoT IAM and increasing spending on cyber security during the period has positively impacted IoT IAM industry. However, high cost associated with implementation and maintenance of IoT identity and access management (IAM) solution and increase in security & privacy concerns is anticipated to hamper the IoT IAM market during the forecast period. On the contrary, adoption of Bring your Own Identity (BYOI) approach is expected to offer remunerative opportunities for the expansion of the Iot Identity And Access Management market forecast.
On the basis of security type, the network security segment dominated the overall Iot Identity And Access Management Market Share in 2021 and is expected to continue this trend during the forecast period. This is attributed to the increase in cyber-attacks on networks due to increase in internet penetration and connected devices. However, the cloud security segment is expected to witness the highest growth owing to increase in adoption of cloud-based security solutions, rising demand for cloud-based services.
Region wise, the Iot Identity And Access Management Market analysis was dominated by North America in 2021, and is expected to retain its position during the forecast period, owing to its higher expenditure on technological solutions for better security. However, Asia-Pacific is expected to witness significant growth during the forecast period, owing to the growth in number of startups and the expanding infrastructure in the region, which is expected to fuel the growth of the IoT IAM industry in the region during the forecast period.
Inquiry Before Buying: https://www.alliedmarketresearch.com/purchase-enquiry/31995
The IoT Identity And Access Management Market is expected to grow rapidly after the pandemic, owing to rise in adoption of work-from-home culture across the globe. Furthermore, increase in cyber risk and new vulnerabilities is leading organizations worldwide to rethink their security setups. To manage employees working from home, companies rely extensively on remote-based monitoring of the workforce, enhancing the demand for IoT solutions. This helps bring transparency, provide real-time tracking, improve safety, and ensure meeting government compliance. However, the cybersecurity of remote workforce and enterprises plays a vital role in catering to their clients during lockdowns. Therefore, it offers opportunities for the IoT identity and access management market post pandemic.
KEY FINDINGS OF THE STUDY
By offering, the solution segment accounted for the largest IoT IAM market share in 2021.
By region, North America generated the highest revenue in 2021.
By enterprise size, large enterprises segment accounted for the largest IoT IAM market share in 2021.
By deployment mode, the on-premise segment generated the highest revenue in 2021.
The key players profiled in the Iot Identity And Access Management Industry are Telefonaktiebolaget LM Ericsson, AWS, Google LLC, Microsoft, IBM, Cisco Systems, Inc., Oracle, HID Global Corporation, DigiCert, Inc., Keyfactor, Entrust Corporation, GlobalSign, One Identity, LLC, KaaIoT Technologies, LLC, Sailpoint Technologies Holdings, Inc., Optiv Security, Inc., and IdentityFusion, Inc. These players have adopted various strategies to increase their market penetration and strengthen their position in the Iot Identity And Access Management Industry.
About Us: Allied Market Research (AMR) is a full-service market research and business-consulting wing of Allied Analytics LLP based in Portland, Oregon. Allied Market Research provides global enterprises as well as medium and small businesses with unmatched quality of “Market Research Reports Insights” and “Business Intelligence Solutions.” AMR has a targeted view to provide business insights and consulting to assist its clients to make strategic business decisions and achieve sustainable growth in their respective market domain.
#Iot Identity and Access Management (IAM) Market#Iot Identity and Access Management (IAM) Industry#Iot Identity and Access Management (IAM)#IAM
0 notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
Reasons to Consider Modernising Your IAM

IAM stands for Identity and access management. Nowadays, Cyber attacks are more frequent and complex. Therefore, implementing advanced security measures has become essential.
Modernizing your IAM solutions with the latest technologies can ensure that you're secure, compliant, and able to respond quickly to changing business requirements.
What is IAM?
In simple words, Identity and access management (IAM) is the framework that enables the right user to access the right resources at the right times for the right reasons. IAM helps businesses control the access to their business-critical assets, making them more secure and accessible, all the time.
IAM is a powerful solution for managing users and assigning permissions. You can use it to give users access to specified resources on your network, revoke their privileges, and assign a single digital identity to each user.
IAM is no longer just for employees and clients. Digital transformation is bringing a new type of identity management to businesses. Organizations are moving to assign identities to the Internet of Things (IoT) devices.
Reasons to Consider Modernizing Your IAM
Automation
The outdated IAM system necessitates more manual work, which slows down business operations—not ideal in this fast-paced world. Automating these manual tasks is, therefore, necessary to maintain better efficiency.
Modern IAM systems automate and streamline processes to make it simpler to manage the majority of tasks automatically, saving much more time.
For instance, modern IAM uses data analysis to make intelligent decisions, recommending roles and permissions to new users based on the organization’s groups to which they belong.
Cloud
The majority of businesses are migrating to the cloud because it is more dependable and secure than on-premises infrastructure. It has become essential to move toward Cloud IAM solutions.
The benefits of cloud IAM include real-time information accessibility, dynamic and intelligent information updating, and the flexibility for your users to operate from any place and on any device.
Security
One of the most important reasons for wanting to upgrade from an outdated IAM solution is security concerns. Legacy IAM solutions are vulnerable to attacks and aren’t ready for the digital future.
A cloud IAM solution offers a better security approach than your old, outdated solution.
Real-time availability is one of the most effective advantage which can help identify the full scope of the security attack. It can help to identify which resources have been accessed and can take further actions to enhance security.
Best practices for migrating legacy IAM to a cloud-based solution
MFA Methods
A solid identity and access management (IAM) policy must include MFA (Multi-factor authentication) as a fundamental element. 99.9% of account hacking attempts can be stopped by MFA. MFA reduces the likelihood of a successful intrusion by requiring one or more additional verification criteria in addition to a username and password.
Cloud-based SSO
Cloud SSO eliminates password fatigue and lowers IT management overheads. Users only need to set up a single username and password. Therefore, providing a frictionless login experience without sacrificing security.
Zero Trust Security
Zero trust involves constantly checking who is authorized to access confidential papers, resources, and tools while giving each user the fewest rights possible.
Conclusion
You need to stay secure in today’s digital world, where cyber-attacks are common and threats can come from anywhere. Cloud-based access management is the way to go in this era, protecting your organization’s data and applications from loss, unauthorized use, and misuse.
#IdentityAccessManagement#IAM#CyberSecurity#CloudSecurity#DigitalTransformation#MultiFactorAuthentication#ZeroTrust#DataProtection#CloudComputing#Automation#SSO#SecurityBestPractices
1 note
·
View note
Text
From Novice to Pro: Master the Cloud with AWS Training!
In today's rapidly evolving technology landscape, cloud computing has emerged as a game-changer, providing businesses with unparalleled flexibility, scalability, and cost-efficiency. Among the various cloud platforms available, Amazon Web Services (AWS) stands out as a leader, offering a comprehensive suite of services and solutions. Whether you are a fresh graduate eager to kickstart your career or a seasoned professional looking to upskill, AWS training can be the gateway to success in the cloud. This article explores the key components of AWS training, the reasons why it is a compelling choice, the promising placement opportunities it brings, and the numerous benefits it offers.

Key Components of AWS Training
1. Foundational Knowledge: Building a Strong Base
AWS training starts by laying a solid foundation of cloud computing concepts and AWS-specific terminology. It covers essential topics such as virtualization, storage types, networking, and security fundamentals. This groundwork ensures that even individuals with little to no prior knowledge of cloud computing can grasp the intricacies of AWS technology easily.
2. Core Services: Exploring the AWS Portfolio
Once the fundamentals are in place, AWS training delves into the vast array of core services offered by the platform. Participants learn about compute services like Amazon Elastic Compute Cloud (EC2), storage options such as Amazon Simple Storage Service (S3), and database solutions like Amazon Relational Database Service (RDS). Additionally, they gain insights into services that enhance performance, scalability, and security, such as Amazon Virtual Private Cloud (VPC), AWS Identity and Access Management (IAM), and AWS CloudTrail.
3. Specialized Domains: Nurturing Expertise
As participants progress through the training, they have the opportunity to explore advanced and specialized areas within AWS. These can include topics like machine learning, big data analytics, Internet of Things (IoT), serverless computing, and DevOps practices. By delving into these niches, individuals can gain expertise in specific domains and position themselves as sought-after professionals in the industry.

Reasons to Choose AWS Training
1. Industry Dominance: Aligning with the Market Leader
One of the significant reasons to choose AWS training is the platform's unrivaled market dominance. With a staggering market share, AWS is trusted and adopted by businesses across industries worldwide. By acquiring AWS skills, individuals become part of the ecosystem that powers the digital transformation of numerous organizations, enhancing their career prospects significantly.
2. Comprehensive Learning Resources: Abundance of Educational Tools
AWS training offers a wealth of comprehensive learning resources, ranging from extensive documentation, tutorials, and whitepapers to hands-on labs and interactive courses. These resources cater to different learning preferences, enabling individuals to choose their preferred mode of learning and acquire a deep understanding of AWS services and concepts.
3. Recognized Certifications: Validating Expertise
AWS certifications are globally recognized credentials that validate an individual's competence in using AWS services and solutions effectively. By completing AWS training and obtaining certifications like AWS Certified Solutions Architect or AWS Certified Developer, individuals can boost their professional credibility, open doors to new job opportunities, and command higher salaries in the job market.
Placement Opportunities
Upon completing AWS training, individuals can explore a multitude of placement opportunities. The demand for professionals skilled in AWS is soaring, as organizations increasingly migrate their infrastructure to the cloud or adopt hybrid cloud strategies. From startups to multinational corporations, industries spanning finance, healthcare, retail, and more seek talented individuals who can architect, develop, and manage cloud-based solutions using AWS. This robust demand translates into a plethora of rewarding career options and a higher likelihood of finding positions that align with one's interests and aspirations.

In conclusion, mastering the cloud with AWS training at ACTE institute provides individuals with a solid foundation, comprehensive knowledge, and specialized expertise in one of the most dominant cloud platforms available. The reasons to choose AWS training are compelling, ranging from the industry's unparalleled market position to the top ranking state.
9 notes
·
View notes
Text
The Future of Cloud Consulting Services: Trends to Watch in 2025 and Beyond

As cloud technology transforms how businesses function, cloud consulting services are adapting to address emerging demands. With digital transformation now a strategic imperative, organizations are increasingly turning to expert cloud consultants to navigate a rapidly evolving landscape. The future of cloud consulting is not just about infrastructure—it's about enabling innovation, security, agility, and sustainability.
Let’s examine the major trends set to reshape cloud consulting services in 2025 and beyond.
1.Rapid Growth in Multi-Cloud and Hybrid Cloud Approaches
Businesses are shifting away from depending on just one cloud provider. Instead, they are embracing multi-cloud and hybrid cloud strategies that offer greater flexibility, cost-efficiency, and risk management.
Cloud consultants are now expected to guide businesses through:
Optimal cloud vendor selection
Integration between public, private, and on-premise environments
Efficient workload distribution and orchestration
With this trend, the complexity of managing diverse environments has increased, making expert consulting services more critical than ever.
2. Cloud-Native and Serverless Architectures Taking Center Stage
The future belongs to cloud-native applications—those built specifically for cloud environments using containers, microservices, and DevOps methodologies. Furthermore, serverless computing is gaining momentum, enabling developers to concentrate purely on coding without managing the underlying infrastructure.
Cloud consultants play a key role in enabling companies to:
Designing cloud-native solutions from the ground up
Implementing CI/CD pipelines and automation frameworks
Migrating legacy systems to agile, scalable environments
This evolution requires deep technical expertise paired with strategic insight.
3. AI and Machine Learning Integration in Cloud Platforms
As cloud platforms integrate AI and machine learning features, processes become more intelligent and data-driven. From automated security monitoring to intelligent resource allocation, AI is becoming a core enabler of digital transformation.
Cloud consultants are helping businesses:
Deploy AI-powered analytics and automation tools
Build and train ML models in cloud environments
Integrate intelligent workflows into existing operations
As AI becomes central to cloud strategies, consultants will play a vital role in unlocking its full potential.
4. Edge Computing and Decentralized Cloud
With the growing use of IoT, smart devices, and real-time applications, edge computing is gaining greater significance. Rather than relying on centralized cloud servers, data is now processed nearer to its origin.
Cloud consultants need to adapt through:
Designing architectures that balance cloud and edge computing
Implementing edge nodes and managing distributed data
Ensuring low-latency, high-performance systems
This shift demands a deep understanding of decentralized models and emerging edge platforms.
5. Cybersecurity and Compliance-Driven Cloud Consulting
Security remains a major priority for companies utilizing cloud services. In 2025, the emphasis on compliance, data privacy, and zero-trust security models will be stronger than ever.
Consultants are increasingly relied upon for:
Risk assessments and cloud security audits
Implementing identity and access management (IAM)
Navigating regulations like GDPR, HIPAA, and local data laws
With cyber threats on the rise, cloud consultants must combine technical defenses with strategic governance frameworks.
6. Sustainable Cloud Solutions and Green IT
As organizations become more conscious of their environmental footprint, sustainable cloud computing is emerging as a top priority. Businesses are seeking greener data center options and energy-efficient solutions.
Cloud consultants will support sustainability goals by:
Choosing environmentally responsible cloud providers
Designing low-energy architectures and carbon-efficient operations
Reporting and monitoring environmental KPIs in cloud usage
This shift not only helps the planet but also strengthens brand reputation and compliance.
7. Rise of Industry-Specific Cloud Services
Cloud platforms are no longer one-size-fits-all. In 2025 and beyond, we’ll see an increase in industry-specific cloud solutions tailored to sectors like healthcare, finance, manufacturing, and logistics.
Cloud consultants with vertical expertise will:
Align solutions with sector regulations and workflows
Customize integrations and industry data models
Enhance performance and compliance for specific use cases
This trend opens up new opportunities for niche consulting services.
8. Skills Shift: From Infrastructure to Strategic Advisory
The role of the cloud consultant is evolving from a technical executor to a strategic advisor. While technical knowledge remains essential, clients are now looking for partners who can align cloud initiatives with broader business goals.
Modern consultants must focus on:
Business transformation planning
Cost-benefit analysis and ROI evaluation
Change management and training strategies
As a result, future consulting engagements will require a blend of tech expertise and business acumen.
Conclusion
In 2025, the cloud consulting landscape is evolving rapidly, guided by data and closely aligned with overall business strategy. From embracing AI and sustainability to navigating complex compliance frameworks and decentralized environments, the future demands more than just cloud migration—it calls for cloud innovation.
Organizations that invest in forward-thinking cloud consulting services will be best positioned to thrive in an increasingly digital and competitive world. The future is in the cloud—and expert consultants are the key to unlocking its full potential.
0 notes
Text
Cloud App Development: Transforming Businesses with Wagner Engineering USA

In the era of digital transformation, Cloud app development has become the backbone for innovative, scalable, and efficient business solutions. Organizations across industries are migrating to the cloud to harness the power of flexibility, real-time collaboration, and robust data processing. However, building a cloud application requires specialized expertise—not just in coding but in architecture, security, and systems integration.
This is where Wagner Engineering USA excels. With decades of experience in embedded systems, software engineering, and cloud technologies, Wagner Engineering delivers cloud app development services tailored to meet complex, real-world challenges. Their holistic approach ensures every cloud application is robust, secure, and future-proof.
What is Cloud App Development?
Cloud app development refers to creating software applications that run on cloud infrastructure rather than on local servers or user devices. These apps leverage cloud computing platforms such as Amazon Web Services (AWS), Microsoft Azure, or Google Cloud Platform to provide on-demand scalability, high availability, and accessibility from anywhere.
Unlike traditional software, cloud applications support distributed teams, integrate easily with other services, and enable businesses to innovate rapidly while controlling costs. From consumer-facing apps to industrial control platforms, cloud applications are essential for modern digital ecosystems.
Why Choose Cloud App Development?
Cloud applications offer several distinct advantages:
Scalability: Automatically adjust computing resources to handle changes in user demand without service interruption.
Cost-Efficiency: Reduce the need for expensive on-premises hardware; pay only for what you use.
Accessibility: Users can access apps securely from any device or location.
Reliability: Cloud providers offer built-in redundancy and backup systems to minimize downtime.
Security: Advanced encryption, identity management, and monitoring tools protect sensitive data.
Rapid Deployment: Agile development and DevOps practices accelerate time to market.
Wagner Engineering USA understands these benefits and helps clients capitalize on them through expert cloud app development.
Wagner Engineering USA’s Approach to Cloud App Development
Wagner Engineering USA approaches cloud app development as a comprehensive engineering process, combining software development, system architecture, and security best practices. Their multidisciplinary team includes software engineers, embedded systems experts, and cloud architects who collaborate to build applications that are deeply integrated with clients’ hardware and business workflows.
Key Elements of Their Cloud App Development Services:
1. Custom Architecture Design
Wagner designs cloud applications from the ground up, focusing on microservices architecture, containerization, and API-driven development. This enables the creation of modular, scalable systems that can evolve with your business needs.
They integrate cloud-native services such as serverless functions, managed databases, and content delivery networks to optimize performance and cost.
2. Security-First Mindset
Security is integral to every stage of development. Wagner employs identity and access management (IAM), encryption both at rest and in transit, secure coding practices, and compliance with industry standards to protect applications and data.
3. User-Centric Design
Recognizing that user experience drives adoption, Wagner’s teams build intuitive frontends using modern frameworks like React or Angular. Their designs prioritize usability, responsiveness, and accessibility to ensure seamless interactions across devices.
4. Integration with Embedded Systems
One of Wagner’s unique strengths is their expertise in embedded systems and firmware development. This allows them to build cloud applications that connect directly to IoT devices, industrial sensors, or specialized hardware—providing real-time monitoring, control, and analytics.
5. DevOps and Continuous Delivery
Wagner leverages DevOps tools and practices such as CI/CD pipelines, automated testing, and infrastructure as code to streamline development and deployment. This results in faster iteration cycles, higher software quality, and easier maintenance.
Industries Benefiting from Wagner’s Cloud App Development
Wagner Engineering USA serves a broad range of industries, applying cloud app development expertise to solve specific sector challenges:
Healthcare & Medical Devices: Building HIPAA-compliant cloud platforms for patient data management, diagnostics, and remote monitoring.
Industrial Automation: Cloud-based SCADA and control systems that provide real-time operational insights and predictive maintenance.
Energy & Utilities: Secure cloud applications for smart grid management, energy consumption analytics, and remote asset monitoring.
Defense & Aerospace: Resilient, secure cloud systems that support mission-critical operations and data integrity.
Consumer Technology: Scalable cloud apps for smart home devices, wearables, and mobile solutions.
Each project is tailored to meet regulatory requirements and performance expectations unique to the industry.
The Cloud App Development Process at Wagner Engineering
Wagner Engineering USA follows a structured development lifecycle designed to deliver robust cloud applications on time and within budget.
Step 1: Discovery & Requirements Gathering
Collaborating closely with clients, Wagner’s team identifies business goals, user needs, and technical constraints. This phase defines the project scope and technology stack.
Step 2: Architecture & Design
Engineers design the cloud infrastructure, microservices, data flows, and user interfaces. Security and compliance are integrated from the outset.
Step 3: Development & Integration
Using agile methodologies, Wagner builds the application in iterative sprints. Integration with embedded hardware and third-party systems is tested thoroughly.
Step 4: Testing & Validation
Automated and manual testing ensures performance, security, and usability meet high standards. Wagner conducts stress tests and compliance audits as needed.
Step 5: Deployment & Monitoring
Applications are deployed using CI/CD pipelines with monitoring tools in place to track performance and quickly address issues.
Step 6: Maintenance & Continuous Improvement
Wagner provides ongoing support, performance tuning, and feature updates to keep applications optimized and aligned with evolving business needs.
Why Partner with Wagner Engineering USA for Your Cloud App Development?
Expertise Across the Stack: From embedded hardware to cloud infrastructure and frontend interfaces, Wagner offers holistic engineering capabilities.
Custom Solutions: No cookie-cutter apps—each solution is tailored for your specific workflows, security needs, and scalability targets.
Industry Experience: Deep domain knowledge across regulated and complex sectors ensures reliable, compliant applications.
Agile & Transparent Process: Regular updates, collaborative planning, and flexible iterations keep you involved at every step.
Security-First: With embedded security practices, Wagner minimizes risks and safeguards your critical data.
Proven Track Record: Numerous successful projects for industrial, medical, and defense clients demonstrate Wagner’s commitment to quality.
Cloud app development is a strategic imperative for businesses aiming to innovate, scale, and secure their operations. With its engineering-driven approach, Wagner Engineering USA offers unparalleled expertise to transform your ideas into reliable, scalable cloud applications tailored to your unique challenges.
Whether you’re integrating complex hardware systems, ensuring compliance with stringent regulations, or building intuitive user experiences, Wagner Engineering is the trusted partner to help you realize your cloud ambitions.
0 notes
Text
Cloud Product Design: Scalable, User-Centric Digital Solutions
Cloud computing is transforming modern software development, making cloud product design essential for creating scalable, reliable, and user-friendly digital products. From SaaS platforms to enterprise applications, cloud product design ensures optimal performance, user satisfaction, and long-term growth.

What is Cloud Product Design?
Cloud product design involves creating software products specifically built to run and scale within cloud infrastructures like AWS, Microsoft Azure, or Google Cloud. Unlike traditional design, this approach emphasizes distributed architecture, real-time data processing, and global accessibility while combining UX, software architecture, and cloud-native practices.
Key Principles of Cloud Product Design
User-Centric Design: Focus on UX research, personas, and intuitive interfaces to enhance user satisfaction.
Scalability: Use auto-scaling, microservices, and containerization (e.g., Docker, Kubernetes) for flexible, dynamic growth.
Reliability: Build with load balancing, redundancy, and failover mechanisms to minimize downtime.
Security: Implement secure data handling, encryption, IAM, and compliance (e.g., GDPR, HIPAA).
Performance Optimization: Leverage techniques like CDNs, edge computing, and optimized databases for speed.
Seamless Integration: Design with APIs and interoperability for smooth cross-platform functionality.
Continuous Deployment: Employ CI/CD pipelines for regular updates and improvements based on user feedback.
Benefits of Cloud Product Design
Global Accessibility: Reach users worldwide with cloud-native applications.
Faster Time-to-Market: Speed up development and deployment with cloud tools.
Cost Efficiency: Reduce infrastructure expenses with a pay-as-you-go model.
Innovation: Leverage cloud services like AI, IoT, and analytics to create smarter products.
Why Embrace Cloud Product Design?
Cloud product design is critical for building future-ready digital solutions. By aligning user experience with scalable cloud architecture, businesses can stay competitive in a rapidly evolving digital landscape. Whether developing a SaaS platform or modernizing legacy systems, adopting cloud product design ensures your product is secure, efficient, and ready for the demands of a cloud-first world. Optimize your digital solutions with cloud product design. Build products that scale, perform, and thrive in today’s fast-paced cloud ecosystem.
0 notes
Text
Cybersecurity Solutions & Services in the Middle East: Why Paramount is Your Trusted Partner
In today's fast-paced digital landscape, cybersecurity has become a business imperative. Organizations across the Middle East are rapidly embracing digital transformation, cloud computing, IoT, and remote work technologies—but with these advancements comes increased vulnerability to cyber threats. As a leading cybersecurity provider in the region, Paramount delivers end-to-end cybersecurity solutions designed to safeguard businesses from emerging cyber risks.
Why Cybersecurity Is Critical in the Middle East
The Middle East is witnessing a surge in cyberattacks targeting government bodies, financial institutions, oil & gas companies, and enterprises of all sizes. High-profile breaches and ransomware incidents have underscored the need for proactive security strategies and resilient IT infrastructure.
The region’s unique geopolitical environment, growing digital economy, and increasing adoption of smart technologies make it a prime target for cyber adversaries. Without robust cybersecurity in place, organizations risk data loss, financial damage, reputational harm, and regulatory penalties.
Paramount: Leading the Way in Cybersecurity Services
With over two decades of experience, Paramount stands at the forefront of cybersecurity innovation in the Middle East. We partner with enterprises, governments, and institutions to provide holistic security solutions tailored to their specific needs.
Our Core Cybersecurity Services:
1. Risk Assessment & Compliance
We help organizations identify vulnerabilities, assess threats, and align with global security standards such as ISO 27001, NESA, SAMA, and GDPR.
2. Managed Security Services (MSSP)
Our 24/7 Security Operations Center (SOC) monitors, detects, and responds to cyber threats in real-time—ensuring maximum protection and peace of mind.
3. Cloud & Network Security
We secure your cloud environments, data centers, and enterprise networks with advanced firewall systems, zero-trust architecture, and secure access solutions.
4. Identity & Access Management (IAM)
Paramount’s IAM solutions protect sensitive data by ensuring that only the right individuals can access the right resources at the right time.
5. Digital Forensics & Incident Response
In the event of a breach, our expert team conducts swift investigations, containing threats and minimizing damage with industry-best forensics practices.
6. Cyber Awareness & Training
We empower your workforce with cybersecurity awareness training, helping them recognize and respond to potential threats effectively.
Why Choose Paramount?
Proven Track Record: Trusted by government entities, Fortune 500 companies, and critical infrastructure providers.
Regional Expertise: Deep understanding of the Middle East’s compliance landscape and threat landscape.
Advanced Technology Partners: We collaborate with top global cybersecurity vendors to deliver cutting-edge solutions.
Tailored Solutions: Every business is different—we build customized strategies to meet your unique requirements.
Serving Key Markets Across the Middle East
Paramount provides cybersecurity services across the GCC and wider Middle East region, including the UAE, Saudi Arabia, Qatar, Kuwait, Bahrain, and Oman. Whether you're a government agency or a private enterprise, our experts are here to support your digital journey securely.
Ready to Secure Your Business?
Cybersecurity is not just a technology issue—it's a business priority. With Paramount as your cybersecurity partner, you can confidently navigate the digital world and safeguard your critical assets.
Contact us today to schedule a consultation or learn more about our comprehensive cybersecurity solutions in the Middle East.
0 notes
Text
Introduction:
In today’s hyper-connected world, the Internet of Things (IoT) is driving innovation across industries, seamlessly linking devices to create smarter ecosystems. However, as IoT networks expand, so does the complexity of managing data and ensuring robust security. Enter Cloud Consulting, the transformative approach that addresses these challenges, offering tailored solutions to optimize IoT frameworks. This blog explores how Cloud Consulting empowers IoT systems with improved security and data management, highlighting the pivotal role of IoT development companies in this paradigm shift.
The Growing Importance of IoT in Business
IoT development has redefined industries, enabling real-time monitoring, predictive analytics, and automated workflows. Industries such as healthcare, manufacturing, and logistics have leveraged IoT to:
Optimize operations.
Enhance customer experiences.
Drive cost efficiency.
However, IoT systems rely on interconnected networks of devices, sensors, and applications. These generate enormous volumes of data while also exposing vulnerabilities to cyber threats.
The Intersection of IoT and Cloud Consulting
The integration of IoT devices creates massive volumes of data, demanding efficient storage, seamless accessibility, and advanced security mechanisms. This is where Cloud Consulting companies step in, offering expertise in designing cloud infrastructures that cater specifically to the nuances of IoT systems.
Through cloud-enabled IoT development, businesses can achieve scalable solutions that simplify data management and fortify security, ensuring their networks remain resilient against evolving cyber threats.
How Cloud Consulting Improves IoT Security
Security is a top concern in IoT development. With devices transmitting sensitive information, the risk of data breaches, malware attacks, and unauthorized access is ever-present. A cloud consulting company brings expertise in implementing robust security measures tailored to IoT environments. Here’s how:
End-to-End Encryption
Cloud consulting ensures that data transmitted between IoT devices, and the cloud is encrypted, safeguarding sensitive information from potential cyber threats.
Identity and Access Management
By deploying advanced IAM protocols, businesses can control who accesses their IoT networks, ensuring only authorized personnel have access to critical data and systems.
Real-Time Threat Detection
Cloud platforms integrated with IoT systems can leverage AI and machine learning to monitor network traffic and detect anomalies in real-time. Cloud consultants design these systems to proactively address vulnerabilities before they escalate.
Automated Security Updates
IoT devices often lack the capability for manual updates, leaving them vulnerable. Cloud consulting companies implement automated updates for both cloud infrastructure and IoT devices, keeping systems secure without manual intervention.
Improving IoT Data Management with Cloud Consulting
Scalability for Big Data
IoT devices generate an enormous volume of data. Cloud consulting ensures businesses have access to scalable storage solutions, accommodating data growth without performance issues. This scalability is critical for industries reliant on real-time data analysis.
Data Integration and Analytics
Effective IoT development requires seamless integration of data from various sources. Cloud consulting companies provide tools to unify data, enabling advanced analytics and actionable insights that drive decision-making.
Cost-Effective Storage Solutions
Cloud consulting helps businesses choose cost-effective storage options, such as tiered storage or on-demand solutions. By optimizing storage expenses, companies can allocate resources more effectively without compromising on performance.
Disaster Recovery and Backup
Data loss can cripple IoT operations. Cloud consulting ensures robust backup and disaster recovery solutions, enabling businesses to restore critical data quickly in the event of an outage or cyberattack.
Conclusion
Scalability for Big Data
IoT devices generate an enormous volume of data. Cloud consulting ensures businesses have access to scalable storage solutions, accommodating data growth without performance issues. This scalability is critical for industries reliant on real-time data analysis.
Data Integration and Analytics
Effective IoT development requires seamless integration of data from various sources. Cloud consulting companies provide tools to unify data, enabling advanced analytics and actionable insights that drive decision-making.
Cost-Effective Storage Solutions
Cloud consulting helps businesses choose cost-effective storage options, such as tiered storage or on-demand solutions. By optimizing storage expenses, companies can allocate resources more effectively without compromising on performance.
Disaster Recovery and Backup
Data loss can cripple IoT operations. Cloud consulting ensures robust backup and disaster recovery solutions, enabling businesses to restore critical data quickly in the event of an outage or cyberattack.
0 notes
Text
IoT Identity and Access Management: Enhancing Security Through Innovation and Interoperability

View On WordPress
#AI in IAM#business#cybersecurity#IAM solutions#ict#Identity Access Management#identity and access management#Identity Management#informtion security#Internet of Things#iot#IoT IAM#IoT Identity and Access Management#iot identity management#IoT Security#Machine Learning#Security#technology#threat
0 notes
Text
Top Cybersecurity Challenges and Strategies for the Modern Enterprise

In mid-2025, the digital landscape is more interconnected and dynamic than ever before. While this brings unprecedented opportunities for innovation and growth, it also ushers in an era of increasingly sophisticated and relentless cyber threats. For the modern enterprise, cybersecurity is no longer just an IT concern; it's a fundamental business imperative, directly impacting reputation, financial stability, and operational continuity.
The adversaries are evolving, leveraging advanced techniques and even Artificial Intelligence to bypass traditional defenses. To thrive in this environment, organizations must move beyond reactive measures and adopt proactive, comprehensive strategies.
The Evolving Threat Landscape: Top Cybersecurity Challenges
Enterprises today grapple with a complex array of threats that exploit both technological vulnerabilities and human factors:
AI-Powered Attacks: This is a rapidly escalating threat. Attackers are now using AI for sophisticated phishing campaigns, generating highly convincing deepfakes for BEC (Business Email Compromise) scams, automating vulnerability scanning, and creating adaptive malware that evades traditional detection methods.
Ransomware and Extortion Attacks: Still a dominant and evolving threat. Attackers frequently employ "double extortion" (encrypting data and exfiltrating it for public release) or even "triple extortion" (adding DDoS attacks or direct victim shaming) to pressure payments. The focus is increasingly on critical infrastructure and large enterprises for maximum impact.
Supply Chain Attacks: Exploiting weaknesses in third-party vendors, software components, or managed service providers has become a favored tactic. A single vulnerability in a supplier can cascade down, affecting numerous downstream organizations, making these attacks highly impactful.
Advanced Phishing and Social Engineering: While old, these tactics are becoming incredibly sophisticated. AI enables personalized spear-phishing, voice cloning for vishing, and highly deceptive lures that are difficult for even trained employees to spot. Human error remains a leading cause of breaches.
Cloud Security Misconfigurations and Vulnerabilities: Rapid cloud adoption, multi-cloud strategies, and hybrid environments introduce new complexities. Misconfigured cloud storage buckets, overly permissive IAM roles, and insecure APIs are common entry points for attackers. Ensuring consistent visibility and control across diverse cloud platforms is a significant challenge.
Insider Threats (Malicious & Negligent): Whether intentional data theft by disgruntled employees or accidental data exposure due to carelessness, insider threats remain a persistent and often difficult-to-detect risk due to their privileged access.
IoT and OT (Operational Technology) Security: The proliferation of connected devices in industrial control systems (OT), smart buildings, and remote work environments significantly expands the attack surface. Many IoT devices lack robust built-in security, making them vulnerable entry points to critical networks.
The Cybersecurity Talent Shortage: There's a severe global deficit of skilled cybersecurity professionals. This makes it challenging for organizations to build robust in-house teams capable of keeping pace with evolving threats, implementing advanced defenses, and responding effectively to incidents.
Evolving Regulatory Pressures: Governments worldwide are enacting stricter data protection and breach notification laws. For instance, new regulations bring significant obligations around consent, data retention, breach notification, and cross-border data transfers, adding layers of compliance complexity for businesses.
Securing Remote and Hybrid Work Environments: The continued prevalence of remote work expands the traditional network perimeter, introducing challenges in securing distributed endpoints, home networks, and personal devices used for corporate access.
Strategic Defenses: Countering Modern Cyber Threats
Addressing these multifaceted challenges requires a multi-layered, adaptive, and proactive cybersecurity strategy.
Adopt a Zero Trust Architecture: Move away from perimeter-based security. Assume no user, device, or network is inherently trustworthy, even within the corporate network. Implement strict "never trust, always verify" principles with granular access controls and continuous authentication.
Strengthen Identity and Access Management (IAM) with MFA: Robust IAM is foundational. Implement Multi-Factor Authentication (MFA) everywhere possible. Explore passwordless technologies and adaptive authentication that adjust security based on context (location, device, time of day).
Invest in Advanced Threat Detection & Response (XDR/EDR): Deploy sophisticated Endpoint Detection and Response (EDR) or Extended Detection and Response (XDR) solutions. These use AI and behavioral analytics to detect, investigate, and respond to threats across endpoints, networks, cloud environments, and email, providing much deeper visibility than traditional antivirus.
Prioritize Cloud Security Posture Management (CSPM) & Cloud Workload Protection (CWPP): Implement tools to continuously monitor cloud environments for misconfigurations, compliance deviations, and vulnerabilities. CWPP solutions protect workloads (VMs, containers, serverless functions) regardless of where they run.
Develop a Robust Incident Response and Recovery Plan: A well-defined and regularly tested incident response plan is critical. This includes clear roles, communication protocols, forensic investigation procedures, containment strategies, and robust data backup and recovery mechanisms to minimize downtime and data loss.
Fortify Your Human Firewall with Continuous Training: Employees are often the weakest link. Conduct regular, engaging, and simulated phishing/social engineering training to raise awareness. Foster a strong cybersecurity culture where security is everyone's responsibility.
Enhance Supply Chain Risk Management: Conduct thorough security assessments and continuous monitoring of third-party vendors and service providers. Include strong security clauses in contracts and ensure they adhere to your security standards.
Implement Proactive Threat Hunting and Intelligence: Don't just wait for alerts. Actively search for threats within your network using threat intelligence feeds, anomaly detection, and specialized security teams. Leverage intelligence on emerging threats, tactics, and procedures (TTPs) of adversaries.
Integrate Security into the Software Development Lifecycle (DevSecOps): "Shift left" on security by embedding security practices from the design phase of applications, rather than bolting them on at the end. Automate security testing in CI/CD pipelines to identify and fix vulnerabilities early.
Leverage AI for Defense: While attackers use AI, defenders must too. Employ AI-powered security solutions for faster anomaly detection, predictive analytics, automated threat response, and to augment your security operations center (SOC) teams, compensating for the talent shortage.
Conclusion
The cybersecurity battle is an ongoing, adaptive arms race. For the modern enterprise, security is no longer a static defense but a dynamic, resilient capability woven into the very fabric of the organization. By understanding the evolving threat landscape and strategically implementing multi-layered, proactive, and people-centric defenses, businesses can not only mitigate risks but also build the trust and resilience necessary to thrive in an increasingly digital and interconnected world. The investment in robust cybersecurity is an investment in the future of the enterprise itself.
0 notes
Text
AWS Cloud Services: A Critical Enabler in the Healthcare Industry
The healthcare industry has undergone a digital transformation, driven by the need for agility, patient-centric services, and operational efficiency. Central to this evolution is the growing reliance on AWS cloud services. With its suite of AWS-managed services and scalable infrastructure, Amazon Web Services (AWS) is helping healthcare organizations overcome traditional IT limitations while ensuring compliance, data security, and innovation.

The Shift Toward Cloud in Healthcare
Healthcare providers, payers, and life sciences organizations are turning to cloud computing to modernize their systems, manage electronic health records (EHRs), and unlock the value of big data and artificial intelligence (AI). However, transitioning to the cloud involves complex challenges—from regulatory compliance to managing sensitive patient data. This is where AWS cloud managed services offer a significant advantage.
AWS provides a robust, secure, and compliant environment that is well-suited for hosting healthcare applications. Services like Amazon EC2, Amazon S3, and Amazon RDS offer scalable compute and storage solutions, while more specialized offerings like AWS HealthLake and Amazon Comprehend Medical provide tools tailored to the healthcare sector.
Data Security and Compliance
Security and regulatory compliance are top priorities in healthcare. AWS cloud services are designed with built-in security frameworks that support compliance with HIPAA, HITRUST, GDPR, and other healthcare-specific regulations. AWS provides encryption at rest and in transit, fine-grained access controls through IAM (Identity and Access Management), and detailed audit logs via AWS CloudTrail.
AWS managed services further simplify compliance by automating infrastructure management tasks such as patching, backups, and monitoring. This allows healthcare IT teams to focus on higher-value activities while ensuring that their infrastructure remains secure and compliant.
Enhancing Patient Care with AWS Cloud Services
AWS enables the use of AI and machine learning to analyze medical data, predict patient outcomes, and personalize treatment plans. For example, AWS SageMaker allows data scientists to build, train, and deploy machine learning models that can predict disease progression or assist in medical imaging analysis.
AWS HealthLake, a HIPAA-eligible service, allows organizations to store, transform, and analyze large volumes of health information in the Fast Healthcare Interoperability Resources (FHIR) format. By centralizing clinical data in a structured format, healthcare providers can better understand patient populations, improve clinical decision-making, and enhance operational efficiency.
Moreover, AWS managed services like Amazon RDS and AWS Lambda streamline backend operations, allowing developers to focus on building patient-facing apps rather than managing infrastructure.
Disaster Recovery and Business Continuity
Healthcare services must be available around the clock. AWS offers tools to ensure high availability and rapid disaster recovery. Services like Amazon S3 for data backup, AWS Backup for centralized backup management, and multi-region deployments ensure that critical healthcare systems are resilient and always accessible.
With AWS cloud-managed services, disaster recovery processes can be automated, tested, and optimized, ensuring minimal downtime in the event of a system failure or cyberattack. This reliability is essential in critical healthcare environments where data loss or system downtime can have life-threatening consequences.
Telehealth and Remote Monitoring
The COVID-19 pandemic accelerated the adoption of telehealth solutions. AWS supports this shift by providing low-latency, scalable cloud infrastructure capable of hosting real-time communication platforms. Amazon Chime SDK, for example, enables the development of secure video consultation apps, while AWS IoT Core can collect and process data from wearable health monitoring devices.
These services are essential for delivering care to remote or underserved communities and reducing the burden on physical healthcare infrastructure.
Cost Efficiency and Scalability
Traditional healthcare IT systems are often expensive to maintain and difficult to scale. AWS offers a pay-as-you-go pricing model that helps healthcare organizations control costs while scaling infrastructure based on demand. AWS managed services remove the burden of infrastructure maintenance, offering tools that automatically scale resources and manage performance.
By leveraging AWS’s elasticity, healthcare organizations can seamlessly expand storage, computing power, or database resources during peak demand—such as during a public health crisis—without overcommitting capital upfront.
Conclusion
From enhancing clinical insights to improving operational efficiency and ensuring robust security, AWS cloud services are playing a pivotal role in reshaping the healthcare landscape. By providing secure, scalable, and compliant infrastructure, AWS empowers healthcare organizations to focus on what matters most: delivering high-quality patient care.
As the healthcare industry continues to digitize and evolve, AWS managed services will remain a cornerstone for innovation, efficiency, and resilience. Organizations that strategically adopt AWS cloud-managed services will not only keep pace with regulatory and technological demands but also lead the way in transforming healthcare for the better.
#AWS cloud services#AWS cloud managed services#AWS managed services#healthcare cloud#digital transformation in healthcare#Cloud Modernization
0 notes
Text
Your Journey Through the AWS Universe: From Amateur to Expert
In the ever-evolving digital landscape, cloud computing has emerged as a transformative force, reshaping the way businesses and individuals harness technology. At the forefront of this revolution stands Amazon Web Services (AWS), a comprehensive cloud platform offered by Amazon. AWS is a dynamic ecosystem that provides an extensive range of services, designed to meet the diverse needs of today's fast-paced world.

This guide is your key to unlocking the boundless potential of AWS. We'll embark on a journey through the AWS universe, exploring its multifaceted applications and gaining insights into why it has become an indispensable tool for organizations worldwide. Whether you're a seasoned IT professional or a newcomer to cloud computing, this comprehensive resource will illuminate the path to mastering AWS and leveraging its capabilities for innovation and growth. Join us as we clarify AWS and discover how it is reshaping the way we work, innovate, and succeed in the digital age.
Navigating the AWS Universe:
Hosting Websites and Web Applications: AWS provides a secure and scalable place for hosting websites and web applications. Services like Amazon EC2 and Amazon S3 empower businesses to deploy and manage their online presence with unwavering reliability and high performance.
Scalability: At the core of AWS lies its remarkable scalability. Organizations can seamlessly adjust their infrastructure according to the ebb and flow of workloads, ensuring optimal resource utilization in today's ever-changing business environment.
Data Storage and Backup: AWS offers a suite of robust data storage solutions, including the highly acclaimed Amazon S3 and Amazon EBS. These services cater to the diverse spectrum of data types, guaranteeing data security and perpetual availability.
Databases: AWS presents a panoply of database services such as Amazon RDS, DynamoDB, and Redshift, each tailored to meet specific data management requirements. Whether it's a relational database, a NoSQL database, or data warehousing, AWS offers a solution.
Content Delivery and CDN: Amazon CloudFront, AWS's content delivery network (CDN) service, ushers in global content distribution with minimal latency and blazing data transfer speeds. This ensures an impeccable user experience, irrespective of geographical location.
Machine Learning and AI: AWS boasts a rich repertoire of machine learning and AI services. Amazon SageMaker simplifies the development and deployment of machine learning models, while pre-built AI services cater to natural language processing, image analysis, and more.
Analytics: In the heart of AWS's offerings lies a robust analytics and business intelligence framework. Services like Amazon EMR enable the processing of vast datasets using popular frameworks like Hadoop and Spark, paving the way for data-driven decision-making.
IoT (Internet of Things): AWS IoT services provide the infrastructure for the seamless management and data processing of IoT devices, unlocking possibilities across industries.
Security and Identity: With an unwavering commitment to data security, AWS offers robust security features and identity management through AWS Identity and Access Management (IAM). Users wield precise control over access rights, ensuring data integrity.
DevOps and CI/CD: AWS simplifies DevOps practices with services like AWS CodePipeline and AWS CodeDeploy, automating software deployment pipelines and enhancing collaboration among development and operations teams.
Content Creation and Streaming: AWS Elemental Media Services facilitate the creation, packaging, and efficient global delivery of video content, empowering content creators to reach a global audience seamlessly.
Migration and Hybrid Cloud: For organizations seeking to migrate to the cloud or establish hybrid cloud environments, AWS provides a suite of tools and services to streamline the process, ensuring a smooth transition.
Cost Optimization: AWS's commitment to cost management and optimization is evident through tools like AWS Cost Explorer and AWS Trusted Advisor, which empower users to monitor and control their cloud spending effectively.
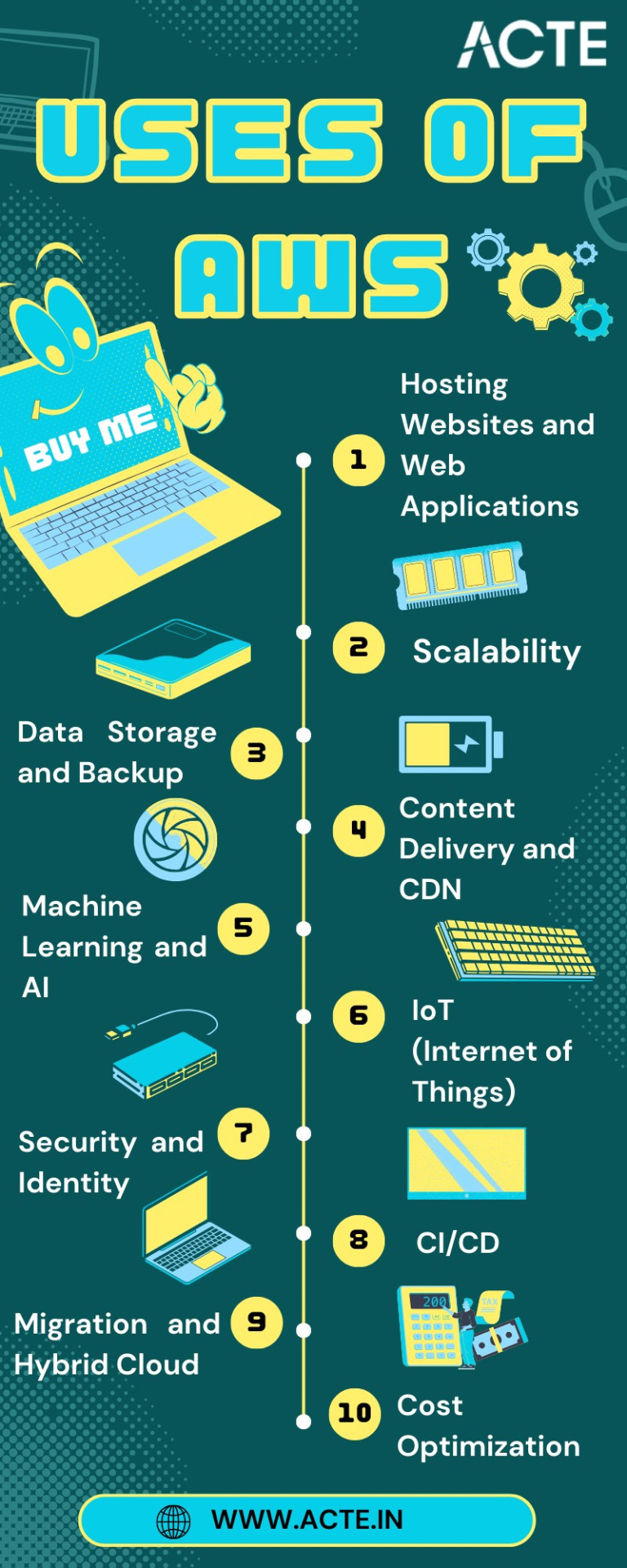
In this comprehensive journey through the expansive landscape of Amazon Web Services (AWS), we've embarked on a quest to unlock the power and potential of cloud computing. AWS, standing as a colossus in the realm of cloud platforms, has emerged as a transformative force that transcends traditional boundaries.
As we bring this odyssey to a close, one thing is abundantly clear: AWS is not merely a collection of services and technologies; it's a catalyst for innovation, a cornerstone of scalability, and a conduit for efficiency. It has revolutionized the way businesses operate, empowering them to scale dynamically, innovate relentlessly, and navigate the complexities of the digital era.
In a world where data reigns supreme and agility is a competitive advantage, AWS has become the bedrock upon which countless industries build their success stories. Its versatility, reliability, and ever-expanding suite of services continue to shape the future of technology and business.
Yet, AWS is not a solitary journey; it's a collaborative endeavor. Institutions like ACTE Technologies play an instrumental role in empowering individuals to master the AWS course. Through comprehensive training and education, learners are not merely equipped with knowledge; they are forged into skilled professionals ready to navigate the AWS universe with confidence.
As we contemplate the future, one thing is certain: AWS is not just a destination; it's an ongoing journey. It's a journey toward greater innovation, deeper insights, and boundless possibilities. AWS has not only transformed the way we work; it's redefining the very essence of what's possible in the digital age. So, whether you're a seasoned cloud expert or a newcomer to the cloud, remember that AWS is not just a tool; it's a gateway to a future where technology knows no bounds, and success knows no limits.
6 notes
·
View notes
Text
IoT Security Market to Witness Notable Growth Analysis, Opportunities, and Future Scope Forecast 2029
Microsoft (US), Fortinet (US), AWS (US), IBM (US), Intel (US), Cisco (US), Thales Group (France), Infineon (Germany) , Allot (Israel), Atos (France), Checkpoint (US), Palo Alto Networks (US), Mobileum (US), Entrust (US), NXP Semiconductors (Netherlands), and Kaspersky (Switzerland), MagicCube (US). IoT Security Market By Solutions (IAM, Data Encryption and Tokenization, IDS/IPS, Device…
0 notes
Text
Malaysia Cybersecurity Market to Witness 11.4% CAGR Growth Between 2024 and 2030
According to a recent comprehensive by MarkNtel Advisors Malaysia Cybersecurity Market research report, the Malaysia Cybersecurity market is set for significant growth, driven by factors such as market size, share, and evolving trends.
This detailed report offers crucial insights into the Malaysia Cybersecurity market, covering key aspects such as market segmentation and definitions. It outlines the main drivers of growth and provides a clear forecast of the industry’s future direction. Additionally, the study provides a thorough overview of the competitive landscape, detailing recent developments and regional distribution across major areas. An expert competitor analysis delivers an in-depth understanding of market dynamics, offering strategic recommendations for businesses and investors.
With its robust analysis and forward-looking projections, this report is an essential resource for stakeholders aiming to leverage emerging opportunities and address potential challenges in the Malaysia Cybersecurity market.
✅In case you missed it, we are currently revising our reports. Click on the below to get the latest research data with forecast for years 2025 to 2030, including market size, industry trends, and competitive analysis. It wouldn’t take long for the team to deliver the most recent version of the report.
Get a Sample PDF of Report - https://www.marknteladvisors.com/query/request-sample/malaysia-cybersecurity-market.html
Malaysia Cybersecurity Market (2024-30): Analysis and Growth
Malaysia Cybersecurity Market was valued at around USD 1.05 billion in 2023 and is projected to reach around USD 2.17 billion by 2030. Along with this, the market is estimated to grow at a CAGR of around 11.4% during the forecast period, i.e., 2024-30.
What are the key drivers fueling growth in the Malaysia Cybersecurity Malaysia Cybersecurity market from 2024 to 2030?
Expansion of E-Commerce Industry Driving Market Growth – The Malaysian population has consistently been gaining internet access across the country. According to the World Bank, internet penetration has reached around 97% in 2022, up from about 84% in 2019. Thus, with the growing adoption of the internet, smartphones, tablets, computers, etc., the residents of the country are steadily integrating e-commerce services into their routine lives due to convenience, and the variety of options available. Additionally, the Malaysian government has been supportive of the development of digitalization in the country and is implementing various initiatives to boost the e-commerce sector. Such as programs to enhance the digital infrastructure and policies to smooth the online transaction process.
Malaysia Cybersecurity Malaysia Cybersecurity Market : Segmentation Analysis
-By Security Type
-Network Security- Market Size & Forecast 2019-2030, (USD Million)
-Cloud Security- Market Size & Forecast 2019-2030, (USD Million)
-Endpoint & IoT Security- Market Size & Forecast 2019-2030, (USD Million)
-Application Security- Market Size & Forecast 2019-2030, (USD Million)
-Data Security- Market Size & Forecast 2019-2030, (USD Million)
-Others (Identification & Access Management, etc.)- Market Size & Forecast 2019-2030, (USD Million)
- By Solution
-Identity & Access Management (IAM)- Market Size & Forecast 2019-2030, (USD Million)
-Antivirus/Antimalware- Market Size & Forecast 2019-2030, (USD Million)
-Log Management & SIEM- Market Size & Forecast 2019-2030, (USD Million)
-Firewall- Market Size & Forecast 2019-2030, (USD Million)
-Encryption & Tokenization- Market Size & Forecast 2019-2030, (USD Million)
-Compliance & Policy Management- Market Size & Forecast 2019-2030, (USD Million)
-Patch Management- Market Size & Forecast 2019-2030, (USD Million)
-Others- Market Size & Forecast 2019-2030, (USD Million)
- By Deployment mode
-On-premises- Market Size & Forecast 2019-2030, (USD Million)
-Cloud- Market Size & Forecast 2019-2030, (USD Million)
-Hybrid Cloud- Market Size & Forecast 2019-2030, (USD Million)
-By Organization size
-Large Enterprises- Market Size & Forecast 2019-2030, (USD Million)
-SMEs (Small & Medium Enterprises)- Market Size & Forecast 2019-2030, (USD Million)
-By End User
-Banking, Financial Services and Insurance (BFSI)- Market Size & Forecast 2019-2030, (USD Million)
-Government & Defense- Market Size & Forecast 2019-2030, (USD Million)
-Corporate- Market Size & Forecast 2019-2030, (USD Million)
-Healthcare & Life Sciences- Market Size & Forecast 2019-2030, (USD Million)
-Manufacturing- Market Size & Forecast 2019-2030, (USD Million)
-IT & Telecommunication- Market Size & Forecast 2019-2030, (USD Million)
-Others (Education, Media & Entertainment, etc.)- Market Size & Forecast 2019-2030, (USD Million)
-By Region
-North
-South
-East
-Central
-Sarawak
-Sabah
Explore the Complete Analysis Report – https://www.marknteladvisors.com/research-library/malaysia-cybersecurity-market.html
What role do key competitors play in shaping the market, and how are they adapting to emerging trends and challenges?
IBM, CISCO, Microsoft, Palo Alto Networks, Wizlynx group, AKATI Sekurity, AVG, Amazon Web Services, Inc., Qinetics MSP Sdn Bhd, Oracle, 3i Infotech Sdn Bhd, and others
“Market research studies from MarkNtel Advisors are offered in PDF, Excel and PowerPoint formats. Within 24 hours of the payment being successfully received, the report will be sent to your email address.”
Key Questions Answered in the Research Report:
What are the industry’s overall statistics or estimates (Overview, Size- By Value, Forecast Numbers, Segmentation, Shares)?
What are the trends influencing the current scenario of the market?
What key factors would propel and impede the industry across the country?
How has the industry been evolving in terms of geography & solution adoption?
How has the competition been shaping up across the country?
How have buying behavior, customer inclination, and expectations from product manufacturers been evolving during 2024-30?
Who are the key competitors, and what strategic partnerships or ventures are they coming up with to stay afloat during the projected time frame?
Why MarkNtel Advisors?
MarkNtel Advisors is a leading research, consulting, & data analytics firm that provides an extensive range of strategic reports on diverse industry verticals. We deliver data to a substantial & varied client base, including multinational corporations, financial institutions, governments, & individuals, among others.
Our specialization in niche industries & emerging geographies allows our clients to formulate their strategies in a much more informed way and entail parameters like Go-to-Market (GTM), product development, feasibility analysis, project scoping, market segmentation, competitive benchmarking, market sizing & forecasting, & trend analysis, among others, for 15 diverse industrial verticals.
For Media Inquiries, Please Contact:
Email: [email protected]
Sales Office: 564 Prospect St, B9, New Haven, Connecticut, USA-06511.4
Corporate Office: Office No.109, H-159, Sector 63, Noida, Uttar Pradesh-201301, India
0 notes