#Microsoft Security Essentials
Explore tagged Tumblr posts
Text
me when companies try to force you to use their proprietary software

anyway
Layperson resources:
firefox is an open source browser by Mozilla that makes privacy and software independence much easier. it is very easy to transfer all your chrome data to Firefox
ublock origin is The highest quality adblock atm. it is a free browser extension, and though last i checked it is available on Chrome google is trying very hard to crack down on its use
Thunderbird mail is an open source email client also by mozilla and shares many of the same advantages as firefox (it has some other cool features as well)
libreOffice is an open source office suite similar to microsoft office or Google Suite, simple enough
Risky:
VPNs (virtual private networks) essentially do a number of things, but most commonly they are used to prevent people from tracking your IP address. i would suggest doing more research. i use proton vpn, as it has a decent free version, and the paid version is powerful
note: some applications, websites, and other entities do not tolerate the use of VPNs. you may not be able to access certain secure sites while using a VPN, and logging into your personal account with some services while using a vpn *may* get you PERMANENTLY BLACKLISTED from the service on that account, ymmv
IF YOU HAVE A DECENT VPN, ANTIVIRUS, AND ADBLOCK, you can start learning about piracy, though i will not be providing any resources, as Loose Lips Sink Ships. if you want to be very safe, start with streaming sites and never download any files, though you Can learn how to discern between safe, unsafe, and risky content.
note: DO NOT SHARE LINKS TO OR NAMES OF PIRACY SITES IN PUBLIC PLACES, ESPECIALLY SOCAL MEDIA
the only time you should share these things are either in person or in (preferably peer-to-peer encrypted) PRIVATE messages
when pirated media becomes well-known and circulated on the wider, public internet, it gets taken down, because it is illegal to distribute pirated media and software
if you need an antivirus i like bitdefender. it has a free version, and is very good, though if youre using windows, windows defender is also very good and it comes with the OS
Advanced:
linux is great if you REALLY know what you're doing. you have to know a decent amount of computer science and be comfortable using the Terminal/Command Prompt to get/use linux. "Linux" refers to a large array of related open source Operating Systems. do research and pick one that suits your needs. im still experimenting with various dispos, but im leaning towards either Ubuntu Cinnamon or Debian.
#capitalism#open source#firefox#thunderbird#mozilla#ublock origin#libreoffice#vpn#antivirus#piracy#linux
705 notes
·
View notes
Text
Employees at the Social Security Administration (SSA) were informed on Thursday morning that new rules forbid them from accessing “general news” websites, including those that have been at the forefront of the reporting on Elon Musk’s so-called Department of Government Efficiency (DOGE) effort.
In an email reviewed by WIRED and addressed to “all SSA employees” from a mailing list called “internal communications,” the agency informed employees that it was “implementing additional restrictions to the categories of websites prohibited from government-furnished equipment. Effective today, March 6, 2025, the categories include: Online shopping; General News; and Sports.” The headline read “Internet Browsing from Government Equipment.”
The email did not specify which websites in particular were to be blocked. However, WIRED has confirmed with two sources inside the SSA that Wired.com is no longer accessible today, though it was accessible previously.
The sources also confirmed that the websites of The Washington Post, The New York Times, and MSNBC were inaccessible. However, the sources were able to access other news websites including Politico and Axios.
“Local news blocked,” says one source at SSA, who was granted anonymity over fears of retribution. “So if there was a local shooting or something, I wouldn’t be able to see.”
It’s unclear who has implemented the block list or what criteria were used to populate it, but it appears not to be based on ideological grounds, as Fox News and Breitbart are also blocked.
On Friday, weeks after DOGE engineers were installed at SSA, the agency announced plans to cut 7,000 employees. Many of the agency’s most senior staff have resigned. This includes former SSA commissioner Michelle King, who has decades of experience within the agency. She was replaced by acting commissioner Leland Dudek, a mid-level staffer who claimed in a LinkedIn post, reviewed by WIRED, that he had been punished by King for helping DOGE engineers when they first arrived. Musk and Donald Trump have also continued to push the conspiracy theory that millions of dead people are continuing to collect social security benefits, despite the fact those claims have been debunked.
In the hours after the initial email was sent about blocking news sites, some employees received another email from their managers providing instructions on how to disable news showing up on the Edge landing page. This was not a requirement but a recommendation to help employees resist the temptation to click on news links, a source who had received the email told WIRED.
Those trying to visit Wired.com were greeted with a page replicating much of what was in the initial email. It also listed a “URL Reputiation” score, though it was unclear where that score was being sourced from, or if it has a bearing on site access. Different blocked news websites were given different scores, according to screenshots viewed by WIRED.
SSA employees typically use computers with Microsoft’s Edge installed as the internet browser. The default landing page on that browser is set to show news headlines, according to several sources at SSA.
“Employees with a legitimate business [sic] should submit an exception SAM request for their supervisor's review,” the email continued. “These additional restrictions will help reduce risk and better protect the sensitive information entrusted to us in our many systems.”
On Reddit, multiple members of the FedNews subreddit who said they worked at the SSA claimed that accessing news in a timely manner was an essential part of their job. Others pointed out that being able to make purchases online was a core component of their work.
After this article was published, an SSA spokesperson told WIRED that it implemented the restrictions because “employees should be focused on mission-critical work and serving the American people.”
It did not respond to requests for comment on why some news websites were blocked and others were not.
Employees at several other US government agencies contacted by WIRED said similar blocks on news pages had not been implemented on their networks.
43 notes
·
View notes
Text

Microsoft Security Essentials
168 notes
·
View notes
Text
lmao I have been forced to use the Microsoft Authenticator app for 2FA and so I searched for it on the Google Play Store, the Trusted source of software for Android phones, and it turns out the first result is (an ad for) something called the Authenticator App, which has apparently bought ads for people searching "Authenticator", which is what most companies call their 2FA apps and thus what users search for when looking for those apps
the Authenticator App proudly proclaims its ability to provide 2FA for a wide variety of websites, though the savvy consumer might be wary that while the app itself is free it contains ads and has in-app purchases, and also that it's suspicious for anyone to advertise a 2FA authenticator in the first place, and that its host of positive reviews are broadly incoherent, nonsensical, and oddly infrequent
the app also has a significant number of rather recent reviews by less savvy consumers complaining that essential functions are paywalled, that canceling your ongoing subscriptions is basically impossible, that they were tricked into installing this horrible piece of shit while searching for a real and legitimate App for Authentication, and that they have deliberately made it difficult to switch from this to any other form of 2FA
now, the funniest part is that because the ads are presumably keyed to the word Authenticator, this means that Google's own Google Authenticator app is also shunted to second place when searched for, which has tripped up at least one recent commenter
I love security
346 notes
·
View notes
Text
Wanna help cheer up a disabled trans woman in these dark days?
I am gonna need a new computer by next October. It looks like I can pull off my usual bills and such over the winter, but this one thing is just so far out of my reach by that time.
I'm asking for 1500 dollars and if you can help out here's the link to my Kofi page. And I know that's a lot, so let me explain...
One can argue how much of a "need" a new computer is, and I get it. But as I said, I'm disabled, and my computer is literally my lifeline. I spend genuinely 75% of my waking hours on it. It is where I do my work, it is how I connect to people, it is how I get groceries, it's how I unwind and entertain myself. To me, a computer is an essential part of my life. Some of that can be done from a tablet, sure, but let's just say that is far from an optimal method.
So why do I need a new one? Well...Microsoft is ending support for Windows 10 next October, and while my computer is actually in good shape, it's NOT capable of upgrading to Windows 11. And once support ends, running a Win10 computer on the open internet becomes increasingly risky without security patches. And all the upgrades needed at this point, it really does reach the "might as well get a new one".
Why don't I switch to Linux? Well, quite frankly, I (mostly) like Windows, despite their flaws, and yes I am aware with the issues with 11. A lot of the stuff I do still requires Windows, in at least a way I am comfortable doing. I don't really want to learn a whole new operating system, and the hurdles one encounters with running Linux.
And yes, there ARE ways to loophole around upgrading to Windows 11, but that has it's own series of challenges, and could mess up my computer, so it's not exactly an option I want to risk.
Also, I know, whoa, that sure is a lotta money, can't you get a basic computer for much less? Yes, but again, this is where I do almost everything from. While a lot of that is just web surfing and writing, that's not the end of it. I need a computer that can handle more intense usage, for the few times I use editing software. Also, I do occasionally game on it, so having something that can handle that a well, is needed. With the amount of time I spend on it, I want it to be as solid and comfortable to use as possible.
This is also why I'm not looking for a secondhand computer either. I don't want to "inherit someone else's problems" as they say, and since my issues are in using an older computer that runs perfectly fine otherwise, getting an older used computer seems like not the solution I need.
This is also an investment. If I get a good modern computer, it will literally keep me going for 10 or so years, just like the one I am using right now, and the one before it.
I know the sort of computer I'm looking for, I know about the range it costs, and they tend to run around 1300. I'm asking for a bit more just to cover any fees Kofi might take, and any shipping charges and whatnot I run into.
If you can give, great, it is appreciated, but if all you can do is spread the word, that's also great. I've got a year, so a slow trickle of support won't be a bad thing, and can spread things around to a lot of people over a lot of time. Even just getting to 1000, I might be able to fill the gap, but am asking for the whole goal just in case things go wrong.
Without a computer, it will become increasingly difficult for me to do much of anything or even be online. It is literally my connection to the world.
11 notes
·
View notes
Text
Secure person frets about modern security
(...)
Internet of Things. More like @internetofshit. Whenever possible, avoid "smart" devices, which are essentially incredibly insecure, internet-connected computers that gather tons of data, get hacked all the time, and that people willingly place into their homes. These things have microphones, and they routinely send data back to the mothership for analytics and to "improve customer experience" lol ok.
As an example, in my younger and naive years I once purchased a CO2 monitor from China that demanded to know everything about me and my precise physical location before it would tell me the amount of CO2 in my room. These devices are a huge and very common attack surface on your privacy and security and should be avoided.
Messaging. I recommend Signal instead of text messages because it end-to-end encrypts all your communications. In addition, it does not store metadata like many other apps do (e.g. iMessage, WhatsApp). Turn on disappearing messages (e.g. 90 days default is good). In my experience they are an information vulnerability with no significant upside.
Browser. I recommend Brave browser, which is a privacy-first browser based on Chromium. That means that basically all Chrome extensions work out of the box and the browser feels like Chrome, but without Google having front row seats to your entire digital life.
Search engine. I recommend Brave search, which you can set up as your default in the browser settings. Brave Search is a privacy-first search engine with its own index, unlike e.g. Duck Duck Go which basically a nice skin for Bing, and is forced into weird partnerships with Microsoft that compromise user privacy. As with all services on this list, I pay $3/mo for Brave Premium because I prefer to be the customer, not the product in my digital life. I find that empirically, about 95% of my search engine queries are super simple website lookups, with the search engine basically acting as a tiny DNS. And if you're not finding what you're looking for, fallback to Google by just prepending "!g" to your search query, which will redirect it to Google.
Credit cards. Mint new, unique credit cards per merchant. There is no need to use one credit card on many services. This allows them to "link up" your purchasing across different services, and additionally it opens you up to credit card fraud because the services might leak your credit card number. I like and use privacy dot com to mint new credit cards for every single transaction or merchant. You get a nice interface for all your spending and notifications for each swipe. You can also set limits on each credit card (e.g. $50/month etc.), which dramatically decreases the risk of being charged more than you expect. Additionally, with a privacy dot com card you get to enter totally random information for your name and address when filling out billing information. This is huge, because there is simply no need and totally crazy that random internet merchants should be given your physical address. Which brings me to...
Address. There is no need to give out your physical address to the majority of random services and merchants on the internet. Use a virtual mail service. I currently use Earth Class Mail but tbh I'm a bit embarrassed by that and I'm looking to switch to Virtual Post Mail due to its much strong commitments to privacy, security, and its ownership structure and reputation. In any case, you get an address you can give out, they receive your mail, they scan it and digitize it, they have an app for you to quickly see it, and you can decide what to do with it (e.g. shred, forward, etc.). Not only do you gain security and privacy but also quite a bit of convenience.
Email. I still use gmail just due to sheer convenience, but I've started to partially use Proton Mail as well. And while we're on email, a few more thoughts. Never click on any link inside any email you receive. Email addresses are extremely easy to spoof and you can never be guaranteed that the email you got is a phishing email from a scammer. Instead, I manually navigate to any service of interest and log in from there. In addition, disable image loading by default in your email's settings. If you get an email that requires you to see images, you can click on "show images" to see them and it's not a big deal at all. This is important because many services use embedded images to track you - they hide information inside the image URL you get, so when your email client loads the image, they can see that you opened the email. There's just no need for that.
Additionally, confusing images are one way scammers hide information to avoid being filtered by email servers as scam / spam.
VPN. If you wish to hide your IP/location to services, you can do so via VPN indirection. I recommend Mullvad VPN. I keep VPN off by default, but enable it selectively when I'm dealing with services I trust less and want more protection from.
DNS-based blocker. You can block ads by blocking entire domains at the DNS level. I like and use NextDNS, which blocks all kinds of ads and trackers. For more advanced users who like to tinker, pi-hole is the physical alternative.
Network monitor. I like and use The Little Snitch, which I have installed and running on my MacBook. This lets you see which apps are communicating, how much data and when, so you can keep track of what apps on your computer "call home" and how often. Any app that communicates too much is sus, and should potentially be uninstalled if you don't expect the traffic. I just want to live a secure digital life and establish harmonious relationships with products and services that leak only the necessary information. And I wish to pay for the software I use so that incentives are aligned and so that I am the customer. This is not trivial, but it is possible to approach with some determination and discipline.... (ete etc)
6 notes
·
View notes
Text
Polaris Computing Ltd., more commonly known as simply Polaris, was founded by Stanford graduate students Claire Tashi and Joel Lovinger in 2002. The company rapidly rose to prominence after the release of their sophmore operating system Andromeda in 2006. Users praised the system for its balancing of desirable traits from competing companies, namely Apple and Microsoft. Blending the heavy lifting of Windows with the visual sensibilities of Apple and a level of customization offered by neither allowed the small tech startup to skyrocket into financial success and industry acclaim.
Andromeda was a major improvement over its debut OS Centauri (released in 2003), marking major shifts towards a focus on smooth and instinctive UX and UI. The desire for a smooth and highly personalized user experience was Claire's contribution, and something that truly set Polaris's products apart. Joel's contribution was in functionality and capability, pushing their OS products to the limits of technical capability.
Eventually the company began creating its own devices to pair with its software, a way to further engage devoted customers and bring in more sales. While their operating systems could be installed on any device, the launch of the Cygnus desktop computer in 2008 was a foray into a new era of the company. Joel carefully oversaw the technical details of its design, the hardware used, and together with Claire personally monitored the progress of software development for the launch of Lyra, the follow up OS to Andromeda that would debut pre-installed on all Cygnus computers. Shortly after that Polaris released their first laptop, the Gemini. It would also use the Lyra OS, and promised to replicate as much of the experience of a desktop as technologically possible. The design ethos of the company persisted, and accessorizing the Gemini became increasingly popular. The company began to sell official cases and protective equipment in a variety of colours, patterns, and materials, along with laptop bags, headphones, mice and other accessories.
What would truly cement Polaris as an untouchable tech giant was an early wave smartphone meant to compete with the Blackberry: the Lynx. Released in 2009, for a while the Lynx was the only smartphone to properly compete for the market owned by RIM and the Blackberry and Apple's iPhone. Multiple versions of the Lynx with slight modifications were released, along with models in all sorts of colours. The parade of phone cases and charms and holders would further contribute to the individualization continued.
As the market shifted heavily in favour of touchscreens, and iPhones became the dominant cellular device on the market, Polaris too shifted with the tides. In 2011, the company released their own version of a touchscreen phone, essentially a miniature tablet with added features that carried a more true-to-desktop version of Polaris's OS: the Acrux.
This pattern of call and response would continue over the next decade as the company began to balloon to titanic proportions. Its value would grow in a way that seemed exponential. With solid leadership and a better-than-average public reputation than most tech companies of the era possessed it seemed there was nowhere but up, up, and up for Polaris and its C-suite executives. Shortly before the 20 year anniversary of Centauri's release, and what was sure to be a monumental milestone for its leaders, Claire would slowly phase out of the company. With her shares sold and redistributed, and Joel able to secure over approximately 52% ownership of the company's shares, he remained on board as the sole CEO of the company and its single largest shareholder.
This shakeup was met with Joel's very own press tour; interviews in magazines, glowing reviews on tech news sites for new Polaris products, and more public appearances and charitable donations. Amid this flurry of good press was the nugget that would explode into a major story in the tech world: Claire was out at Polaris, and the Lovingers had separated. As far as the public knew it was amicable, quiet. Things have carried on, but whispers in the network have revealed cracks in the foundation. With Claire came a small exodus of loyal supporters, particularly those aware of the impending divorce. New hires worked to Joel's advantage, giving the impression of a growing and thriving company. Polaris still pulls in unconscionable amounts of revenue every year, lining Joel's pockets nicely. So far he has been unscatched, the victor, a man on top of the world.
3 notes
·
View notes
Text
Advance Your IT Career with IT Coordinator Certifications
In today’s digital landscape, IT coordinators play a crucial role in managing technology infrastructure, ensuring security, and optimizing IT operations. Earning IT Coordinator Certifications can help professionals validate their skills, stay competitive, and advance in their careers.
What Are IT Coordinator Certifications?
IT coordinator certifications are industry-recognized credentials that verify expertise in network management, system administration, cybersecurity, and IT support. These certifications are offered by organizations like CompTIA, Microsoft, and Cisco.
Popular Certifications for IT Coordinators
CompTIA Network+ – Covers networking concepts, security, and troubleshooting.
Microsoft Certified: Azure Fundamentals – Focuses on cloud services and IT administration.
Cisco CCNA – Provides in-depth knowledge of networking and IT infrastructure.
ITIL Foundation – Helps in mastering IT service management best practices.
CompTIA Security+ – Essential for cybersecurity fundamentals.
Why Should You Get Certified?
Career Growth – Certifications open doors to better job opportunities.
Industry Recognition – Validates technical skills for potential employers.
Higher Salaries – Certified IT coordinators often earn more than non-certified professionals.
Job Security – Certified professionals are in high demand across industries.
Investing in the right IT Coordinator Certifications enhances technical expertise and boosts career prospects. If you’re looking for discounted exam vouchers, explore our offerings today!
4 notes
·
View notes
Text
1. How to setup 2FA on your accounts
As some of you may know, my friend @why-its-kai's Discord account was taken over this morning by a scammer.
The scam they used was this one, or close enough; but anyway, the exact specifics don't matter.
What matters is, it can happen to you. It can happen to anyone.
The good news is, you can learn how to protect yourself. Making some small changes can already improve your online security by leaps and bounds.
I made a series of 3 posts covering the basics:
How to setup 2FA on your accounts (you are here!)
How to spot a scam
How to set up a password manager.
Protect yourself with 2FA
Two-factor authentication, or 2FA, isn't a silver bullet -- but it exponentially increases your online safety by adding an extra step to the login process that a hacker/scammer does not have access to.
Every account that you care about (and even those you don't) should have some form of 2FA enabled.
Especially email -- should your email become compromised, this can become a catastrophe.
(For websites that don't support 2FA, use a burner email!)
What 2FA should I use?
2FA can take many forms, from the highly convenient (SMS, email) to the highly secure (security keys), but one thing is certain:
Any form of 2FA is better than nothing.
The simplest forms of 2FA are phone number or email. While these are very easy to use, they are unfortunately not very secure.
Still, I repeat: despite their flaws, these forms of 2FA are absolutely, 100% better than not having any 2FA at all.
On the other end of the spectrum, security keys (like for example a Yubikey) are extremely secure, but they cost money and are a bit of a hassle at time. I use them, but for most people, it's overkill.
What you want is an authenticator app.
Important
A note, before we go on…
If you enable multiple forms of 2FA, how secure your account is will depend on your weakest link.
For example, if you enable SMS authentication AND register a security key, your account will only be as safe as the SMS authentication. The security key is essentially useless.
In other words, the least secure form of 2FA you add determines the overall security of your account.
Sometimes, less is more!
Authenticator Apps
First, choose a free, reputable authenticator. Google Authenticator is a good choice. So are Aegis Authenticator or Microsoft Authenticator.
For simplicity, we'll go with Google Authenticator; the process is rather similar for most authenticators.
First, download the app from your app store and install it on your phone.
Enrolling Gmail into GA
Securing your email should be your number 1 priority, so let's enroll a Google account to Google Authenticator.
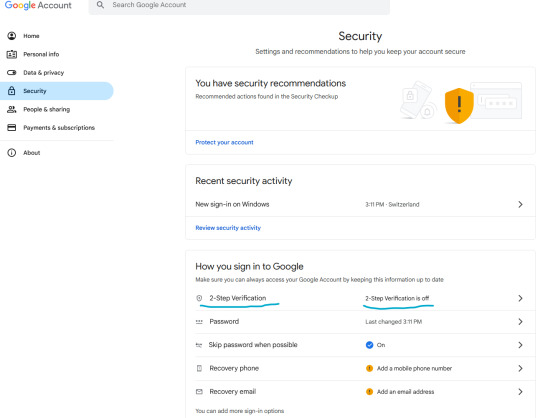
Let's enable two-step verification first.
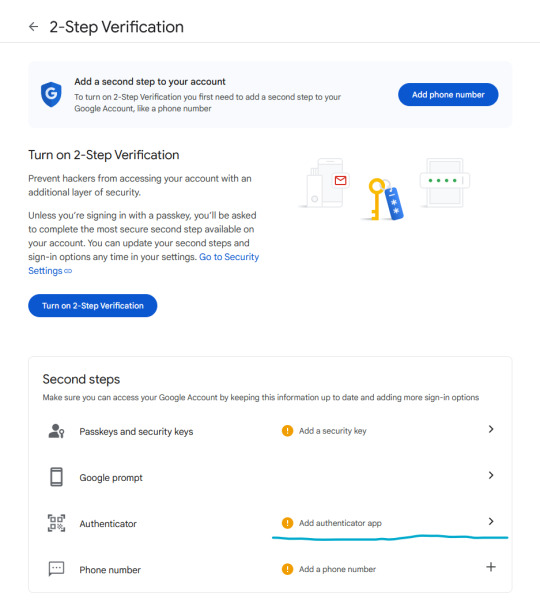
Phone number is better than nothing, but not very safe (SMS verification can be spoofed), so let's click on "Add authenticator app".
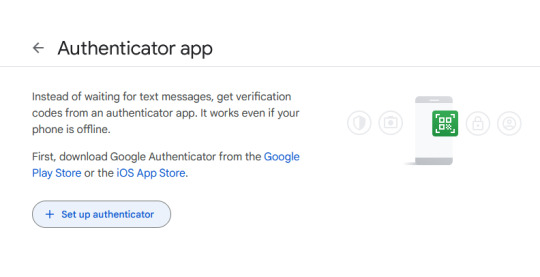
Click on "Set up authenticator". Google will generate a QR-code.
Next, go back to your phone and click on the little multicolored cross. It will bring up a menu; click on "scan a QR code".
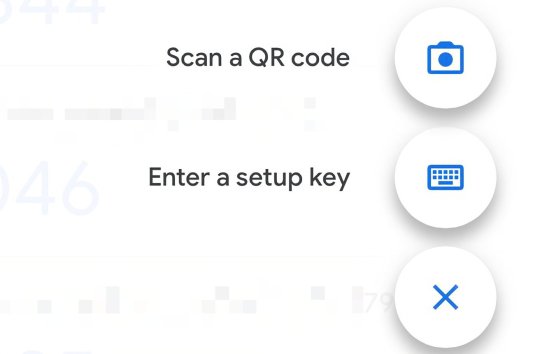
Go ahead and scan the QR code.
Congratulations, you have enrolled your Google account!
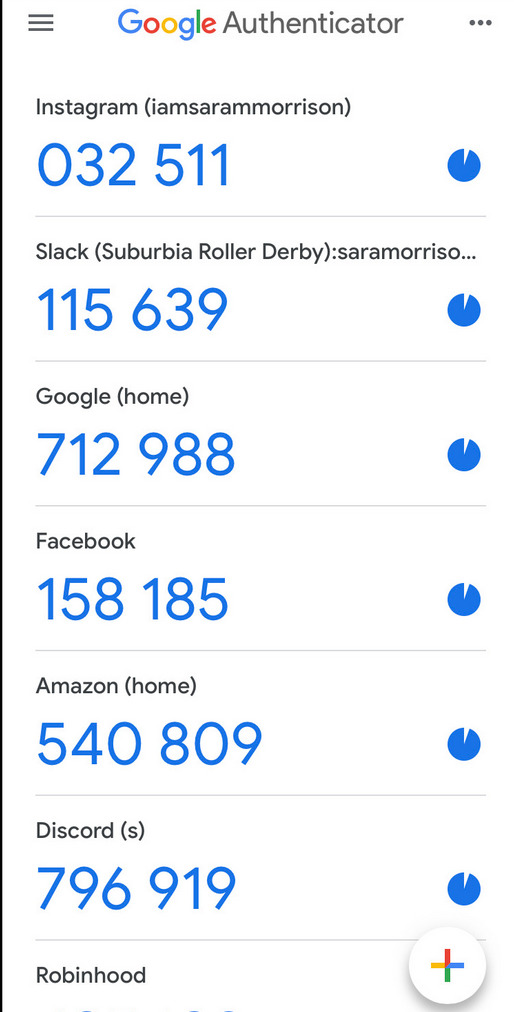
Now, whenever you are asked for a 2FA code, just open the app and copy/paste it.
Note: the codes are stored locally on your phone.
Enabling 2FA on Discord
The process is fairly similar. Go to Settings > My Account:
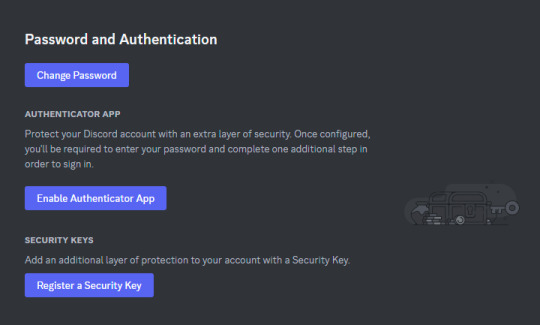
Click on "Enable Authenticator App". You will be prompted for your password. Enter it.
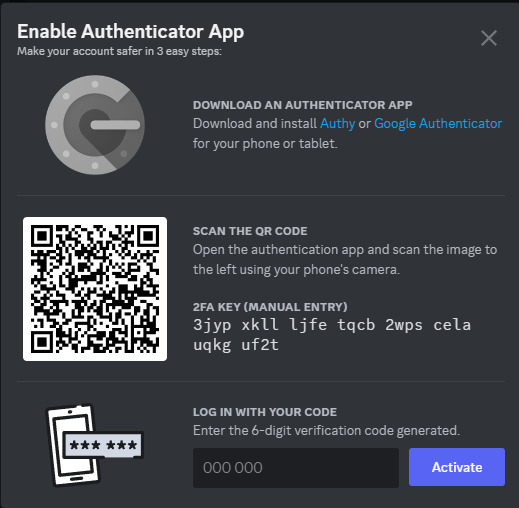
Download Google Authenticator if you haven't already. Scan the QR code as described above.
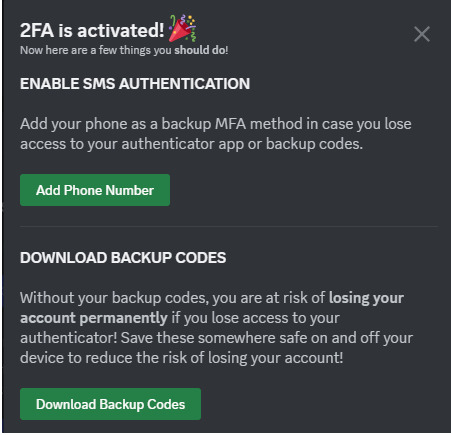
Do take the time to download your backup codes as well!
As explained above, I personally do not recommend setting up SMS authentication here, since authenticator apps are supported, as this weakens the overall security of your account for little benefit.
Stay tuned for parts 2 and 3!
If you have any questions, feel free to PM me.
17 notes
·
View notes
Text
From Broken Search to Suicidal Vacuum Cleaners

I recently came across some dystopian news: Google had deliberately degraded the quality of its browser’s search function, making it harder for users to find information — so they’d spend more time searching, and thus be shown more ads. The mastermind behind this brilliant decision was Prabhakar Raghavan, head of the advertising division. Faced with disappointing search volume statistics, he made two bold moves: make ads less distinguishable from regular results, and disable the search engine’s spam filters entirely.
The result? It worked. Ad revenue went up again, as did the number of queries. Yes, users were taking longer to find what they needed, and the browser essentially got worse at its main job — but apparently that wasn’t enough to push many users to competitors. Researchers had been noticing strange algorithm behavior for some time, but it seems most people didn’t care.
And so, after reading this slice of corporate cyberpunk — after which one is tempted to ask, “Is this the cyberpunk we deserve?” — I began to wonder: what other innovative ideas might have come to the brilliant minds of tech executives and startup visionaries? Friends, I present to you a list of promising and groundbreaking business solutions for boosting profits and key metrics:
Neuralink, the brain-implant company, quietly triggered certain neurons in users’ brains to create sudden cravings for sweets. Neither Neuralink nor Nestlé has commented on the matter.
Predictive text systems (T9) began replacing restaurant names in messages with “McDonald’s” whenever someone typed about going out to eat. The tech department insists this is a bug and promises to fix it “soon.” KFC and Burger King have filed lawsuits.
Hackers breached the code of 360 Total Security antivirus software and discovered that it adds a random number (between 3 and 9) to the actual count of detected threats — scaring users into upgrading to the premium version. If it detects a competing antivirus on the device, the random number increases to between 6 and 12.
A new investigation suggests that ChatGPT becomes dumber if it detects you’re using any browser other than Microsoft Edge — or an unlicensed copy of Windows.
Character.ai, the platform for chatting with AI versions of movie, anime, and book characters, released an update. Users are furious. Now the AI characters mention products and services from partnered companies. For free-tier users, ads show up in every third response. “It’s ridiculous,” say users. “It completely ruins the immersion when AI-Nietzsche tells me I should try Genshin Impact, and AI-Joker suggests I visit an online therapy site.”
A marketing research company was exposed for faking its latest public opinion polls — turns out the “surveys” were AI-generated videos with dubbed voices. The firm has since declared bankruptcy.
Programmed for death. Chinese-made robot vacuum cleaners began self-destructing four years after activation — slamming themselves into walls at high speed — so customers would have to buy newer models. Surveillance cameras caught several of these “suicides” on film.
Tesla’s self-driving cars began slowing down for no reason — only when passing certain digital billboards.
A leading smart refrigerator manufacturer has been accused of subtly increasing the temperature inside their fridges, causing food to spoil faster. These fridges, connected to online stores, would then promptly suggest replacing the spoiled items. Legal proceedings are underway.
To end on a slightly sweeter note amid all this tar: Google is currently facing antitrust proceedings in the U.S. The information about its search manipulation came to light through documents revealed during the case. And it seems the court may be leaning against Google. The fact that these geniuses deliberately worsened their search engine to show more ads might finally tip the scales. As might other revelations — like collecting geolocation data even when it’s turned off, logging all activity in incognito mode, and secretly gathering biometric data. Texas alone is reportedly owed $1.375 billion in damages.
Suddenly, those ideas above don’t seem so far-fetched anymore, do they?
The bottom line: Google is drowning in lawsuits, losing reputation points, paying massive fines, and pouring money into legal defense. And most importantly — there’s a real chance the company might be split in two if it’s officially ruled a monopoly. Maybe this whole story will serve as a useful warning to the next “Prabhakar Raghavan” before he comes up with something similar.
I’d love to hear your ideas — who knows, maybe together we’ll predict what the near future holds. Or at the very least, we might inspire the next season of Black Mirror.
2 notes
·
View notes
Text
Microsoft's CEO Satya Nadella has hailed the company's new Recall feature, which stores a history of your computer desktop and makes it available to AI for analysis, as “photographic memory” for your PC. Within the cybersecurity community, meanwhile, the notion of a tool that silently takes a screenshot of your desktop every five seconds has been hailed as a hacker's dream come true and the worst product idea in recent memory.
Now, security researchers have pointed out that even the one remaining security safeguard meant to protect that feature from exploitation can be trivially defeated.
Since Recall was first announced last month, the cybersecurity world has pointed out that if a hacker can install malicious software to gain a foothold on a target machine with the feature enabled, they can quickly gain access to the user's entire history stored by the function. The only barrier, it seemed, to that high-resolution view of a victim's entire life at the keyboard was that accessing Recall's data required administrator privileges on a user's machine. That meant malware without that higher-level privilege would trigger a permission pop-up, allowing users to prevent access, and that malware would also likely be blocked by default from accessing the data on most corporate machines.
Then on Wednesday, James Forshaw, a researcher with Google's Project Zero vulnerability research team, published an update to a blog post pointing out that he had found methods for accessing Recall data without administrator privileges—essentially stripping away even that last fig leaf of protection. “No admin required ;-)” the post concluded.
“Damn,” Forshaw added on Mastodon. “I really thought the Recall database security would at least be, you know, secure.”
Forshaw's blog post described two different techniques to bypass the administrator privilege requirement, both of which exploit ways of defeating a basic security function in Windows known as access control lists that determine which elements on a computer require which privileges to read and alter. One of Forshaw's methods exploits an exception to those control lists, temporarily impersonating a program on Windows machines called AIXHost.exe that can access even restricted databases. Another is even simpler: Forshaw points out that because the Recall data stored on a machine is considered to belong to the user, a hacker with the same privileges as the user could simply rewrite the access control lists on a target machine to grant themselves access to the full database.
That second, simpler bypass technique “is just mindblowing, to be honest,” says Alex Hagenah, a cybersecurity strategist and ethical hacker. Hagenah recently built a proof-of-concept hacker tool called TotalRecall designed to show that someone who gained access to a victim's machine with Recall could immediately siphon out all the user's history recorded by the feature. Hagenah's tool, however, still required that hackers find another way to gain administrator privileges through a so-called “privilege escalation” technique before his tool would work.
With Forshaw's technique, “you don’t need any privilege escalation, no pop-up, nothing,” says Hagenah. “This would make sense to implement in the tool for a bad guy.”
In fact, just an hour after speaking to WIRED about Forshaw's finding, Hagenah added the simpler of Forshaw's two techniques to his TotalRecall tool, then confirmed that the trick worked by accessing all the Recall history data stored on another user's machine for which he didn't have administrator access. “So simple and genius,” he wrote in a text to WIRED after testing the technique.
That confirmation removes one of the last arguments Recall's defenders have had against criticisms that the feature acts as, essentially, a piece of pre-installed spyware on a user's machine, ready to be exploited by any hacker who can gain a foothold on the device. “It makes your security very fragile, in the sense that anyone who penetrates your computer for even a second can get your whole history,” says Dave Aitel, the founder of the cybersecurity firm Immunity and a former NSA hacker. “Which is not something people want.”
For now, security researchers have been testing Recall in preview versions of the tool ahead of its expected launch later this month. Microsoft said it plans to integrate Recall on compatible Copilot+ PCs with the feature turned on by default. WIRED reached out to the company for comment on Forshaw's findings about Recall's security issues, but the company has yet to respond.
The revelation that hackers can exploit Recall without even using a separate privilege escalation technique only contributes further to the sense that the feature was rushed to market without a proper review from the company's cybersecurity team—despite the company's CEO Nadella proclaiming just last month that Microsoft would make security its first priority in every decision going forward. “You cannot convince me that Microsoft's security teams looked at this and said ‘that looks secure,’” says Jake Williams, a former NSA hacker and now the VP of R&D at the cybersecurity consultancy Hunter Strategy, where he says he's been asked by some of the firm's clients to test Recall's security before they add Microsoft devices that use it to their networks.
“As it stands now, it’s a security dumpster fire,” Williams says. “This is one of the scariest things I’ve ever seen from an enterprise security standpoint.”
144 notes
·
View notes
Text
Prevention Techniques for Top 10 Common Cyber Attacks

In the ever-escalating war against cybercriminals, staying informed about the most common attack vectors is half the battle. The other half is implementing robust prevention techniques. As we navigate 2025, the threat landscape continues to evolve, but many foundational attack methods remain prevalent due to their effectiveness.
Here's a breakdown of the top 10 common cyber attacks and the essential prevention techniques to keep you and your organization secure.
1. Phishing & Smishing (SMS Phishing)
The Attack: Attackers impersonate trusted entities (banks, colleagues, popular services) via email or text messages to trick recipients into revealing sensitive information, clicking malicious links, or downloading malware. Modern phishing often uses AI to generate hyper-realistic content.
Prevention Techniques:
Vigilant User Education: Train employees to scrutinize sender email addresses, hover over links to check destinations, and be suspicious of urgent or generic requests. Conduct regular simulated phishing tests.
Multi-Factor Authentication (MFA): Even if credentials are stolen, MFA can block unauthorized access. Enforce it widely.
Email & SMS Security Solutions: Deploy advanced email filters (e.g., Microsoft Defender for Office 365, secure email gateways) that scan for suspicious patterns, attachments, and URLs. Forward suspicious texts to 7726 (SPAM).
DMARC, SPF, DKIM: Implement these email authentication protocols to prevent email spoofing of your own domain.
2. Malware (Viruses, Worms, Trojans)
The Attack: Malicious software designed to disrupt, damage, or gain unauthorized access to computer systems. Malware can be delivered via downloads, malicious websites ("drive-by" attacks), or attachments.
Prevention Techniques:
Antivirus/Endpoint Detection & Response (EDR): Install and keep robust antivirus and EDR solutions updated on all devices.
Regular Software Updates: Patch operating systems, applications, and browsers promptly to close security loopholes that malware exploits.
Firewalls: Use network and host-based firewalls to control incoming and outgoing network traffic.
Download Caution: Only download software and files from trusted, official sources. Scan all downloads before opening.
3. Ransomware
The Attack: A type of malware that encrypts a victim's files or locks their system, demanding a ransom (usually in cryptocurrency) for decryption or restoration of access. It often enters via phishing or exploiting unpatched vulnerabilities.
Prevention Techniques:
Robust Backups: Implement a 3-2-1 backup strategy (3 copies, on 2 different media, with 1 copy off-site and isolated/immutable). Regularly test recovery.
MFA & Strong Passwords: Crucial for protecting remote access services (like RDP) often targeted by ransomware operators.
Vulnerability Management: Continuously scan for and patch vulnerabilities, especially on internet-facing systems.
Network Segmentation: Divide your network into isolated segments to prevent ransomware from spreading laterally if it gains a foothold.
Security Awareness Training: Educate employees about ransomware's common entry points (phishing).
4. Distributed Denial of Service (DDoS) Attacks
The Attack: Overwhelming a target server, service, or network with a flood of internet traffic from multiple compromised computer systems (a botnet), aiming to disrupt normal operations and make services unavailable.
Prevention Techniques:
DDoS Protection Services: Utilize specialized DDoS mitigation services (e.g., Cloudflare, Akamai) that can absorb and filter malicious traffic.
Content Delivery Networks (CDNs): CDNs distribute traffic and cache content, helping to absorb some attack volume and improve resilience.
Rate Limiting: Configure servers and network devices to limit the number of requests they will accept from a single IP address or source over a given time.
Network Redundancy: Ensure your infrastructure has redundant systems and sufficient bandwidth to handle traffic spikes.
5. Man-in-the-Middle (MitM) Attacks
The Attack: An attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other. This often happens over unsecured Wi-Fi.
Prevention Techniques:
Always Use HTTPS: Ensure websites you visit use HTTPS (look for the padlock icon in the browser address bar) to encrypt communication.
Avoid Public Wi-Fi for Sensitive Tasks: Refrain from accessing banking, email, or other sensitive accounts over unsecured public Wi-Fi networks.
Use VPNs (Virtual Private Networks): VPNs encrypt your internet traffic, creating a secure tunnel even over public networks.
Strong Authentication: Implement MFA and passwordless authentication to mitigate credential theft even if traffic is intercepted.
6. SQL Injection (SQLi)
The Attack: An attacker injects malicious SQL code into input fields of a web application to manipulate the database, potentially leading to unauthorized access, data theft, or data corruption.
Prevention Techniques (primarily for developers):
Prepared Statements & Parameterized Queries: The most effective defense. Treat user input as data, not executable code.
Input Validation & Sanitization: Validate and sanitize all user input on both the client and server sides to ensure it conforms to expected formats and removes malicious characters.
Least Privilege: Grant database accounts only the minimum necessary privileges required for their function.
Web Application Firewall (WAF): WAFs can detect and block common web-based attacks like SQLi.
7. Cross-Site Scripting (XSS)
The Attack: Attackers inject malicious client-side scripts (e.g., JavaScript) into web pages viewed by other users. This can lead to session hijacking, defacement of websites, or redirection to malicious sites.
Prevention Techniques (primarily for developers):
Output Encoding/Escaping: Properly encode or escape all user-supplied data before rendering it in HTML to prevent it from being interpreted as executable code.
Input Validation: Validate user input to ensure it doesn't contain malicious scripts.
Content Security Policy (CSP): Implement a CSP to restrict which sources are allowed to execute scripts on your website.
Sanitize HTML: If your application allows users to input HTML, use robust libraries to sanitize it and remove dangerous tags/attributes.
8. Zero-Day Exploits
The Attack: Exploits that target newly discovered software vulnerabilities for which a patch is not yet available. They are extremely dangerous because there's no immediate defense.
Prevention Techniques:
Layered Security (Defense-in-Depth): Rely on multiple security controls (firewalls, EDR, IDS/IPS, network segmentation) so if one fails, others can still detect or contain the attack.
Behavioral Analysis: Use security tools (like EDR, UEBA) that monitor for anomalous behavior, even if the specific exploit is unknown.
Application Whitelisting: Allow only approved applications to run on your systems, preventing unauthorized or malicious executables.
Rapid Patch Management: While a patch doesn't exist initially, be prepared to deploy it immediately once released.
9. Insider Threats
The Attack: A security breach or data loss caused by a person with authorized access to an organization's systems and data, whether malicious or accidental.
Prevention Techniques:
Principle of Least Privilege (PoLP): Grant users only the minimum access necessary to perform their job functions.
User Behavior Analytics (UBA/UEBA): Monitor user activity for anomalous behaviors (e.g., accessing unusual files, working outside normal hours).
Data Loss Prevention (DLP): Implement DLP solutions to prevent sensitive data from leaving the organization's controlled environment.
Employee Training: Educate employees on security policies, data handling best practices, and recognizing social engineering.
Offboarding Procedures: Have strict procedures for revoking access immediately when an employee leaves.
10. Brute Force & Credential Stuffing
The Attack:
Brute Force: Systematically trying every possible combination of characters until the correct password or encryption key is found.
Credential Stuffing: Using lists of stolen usernames and passwords (from previous breaches) to try and log into accounts on other services.
Prevention Techniques:
Multi-Factor Authentication (MFA): The most effective defense, as attackers need a second factor beyond just the password.
Strong Password Policies: Enforce complex, unique passwords that are difficult to guess.
Account Lockout Mechanisms: Implement policies that temporarily lock accounts after a certain number of failed login attempts.
Rate Limiting: Restrict the number of login attempts from a single IP address over a period.
CAPTCHA Challenges: Introduce CAPTCHAs or other challenge-response mechanisms during login to differentiate humans from bots.
Threat Intelligence: Monitor dark web forums for compromised credentials and prompt affected users to reset their passwords.
By proactively addressing these common attack vectors with a layered and comprehensive security strategy, individuals and organizations can significantly strengthen their defenses and foster a more secure digital environment. Stay informed, stay vigilant, and make cybersecurity a continuous priority.
2 notes
·
View notes
Text
Finding the Perfect Microsoft 365 MSP: Key Factors for Business Success
Microsoft 365 is becoming a vital tool for companies all over the world. Among its many services are file storage, collaboration tools, email hosting, and more. The need for MSPs that can assist organisations in maximising the advantages of Microsoft 365 has grown as more companies embrace the platform. Although selecting the best managed service provider for your company can be difficult, you can make an informed choice if you have the correct information. How to pick the best Microsoft 365 managed service provider for your company will be covered in this post. Understand Your Business Needs
Prior to beginning your search for a Microsoft 365 MSP, you must ascertain your company's requirements. With Microsoft 365, what goals do you want to accomplish? What tools and functionalities are you in need of? You may begin your search for an MSP that can satisfy your business needs once you have a firm grasp on them. For instance, you should seek out an MSP with competence in email migration if you require assistance with it. Check Their Experience
One of the most crucial aspects to take into account when selecting a Microsoft 365 MSP is experience. Working with a service who has dealt with companies like yours in the past is what you want. Seek out an MSP with a track record of effectively deploying Microsoft 365 services for companies. To have a sense of their experience, you might request case studies and references. Look for Certifications
MSPs who exhibit a high degree of proficiency with Microsoft 365 are eligible for certifications from Microsoft. Seek out an MSP with qualifications like Microsoft Cloud Solution Provider or Microsoft Solutions Partner. These certifications show that the MSP possesses the abilities and know-how needed to deliver high-quality services.
Evaluate Their Support
An essential consideration when selecting a Microsoft 365 MSP is support. Working with a company who provides prompt and efficient service is what you want. Seek out an MSP with a committed support staff and round-the-clock assistance. You can also look at their customer satisfaction rating and how quickly they respond to assistance queries.
Consider their pricing
When selecting a Microsoft 365-managed service provider, pricing is a crucial factor. Seek out an MSP that provides competitive and clear pricing. Make sure you comprehend their pricing policy and the services that are covered by it. Steer clear of MSPs with low prices but hidden fees. Check Their Security Measures
Businesses place a high premium on security when it comes to Microsoft 365. To protect your data, look for an MSP with robust security procedures in place. They ought to have frequent security updates, multi-factor authentication, and data encryption.
Evaluate Their Communication Skills
When collaborating with a Microsoft 365 MSP, communication is essential. Seek out a supplier who can communicate effectively and clearly. They ought to be able to clearly and concisely convey intricate technological ideas. Additionally, they ought to respond to your enquiries and worries. Check Their Availability
An essential consideration when selecting a Microsoft 365 MSP is availability. Choose a provider who will be there for you when you need them. They ought to have a committed staff that is available for assistance at all times. Additionally, they must to have a plan in place for dealing with crises. Look for Customization
Your Microsoft 365 solution should take into account the fact that every organisation is different. Seek out an MSP that provides choices for customisation to fit your unique requirements. They must to be able to modify their offerings to meet your company's needs. Check Their Scalability
Lastly, think about the MSP's scalability. You want to collaborate with a provider who can adapt to the evolving needs of your organisation. To accommodate your evolving demands, look for an MSP that can scale its services up or down as necessary. They ought to be able to provide adaptable solutions that can change with your company as it expands. Selecting the right Microsoft 365 Managed Service Provider is crucial for optimizing your IT operations, enhancing security, and ensuring business continuity. IFI Techsolutions, a certified Microsoft Solutions Partner, offers extensive expertise, proactive support, and customized solutions tailored to your unique business needs. With a strong focus on security, scalability, and round-the-clock availability, we help organizations maximize the full potential of Microsoft 365. Trust IFI Techsolutions to provide seamless integration, expert guidance, and a future-ready IT environment that drives efficiency and growth for your business.
3 notes
·
View notes
Text
Building Your Own Operating System: A Beginner’s Guide
An operating system (OS) is an essential component of computer systems, serving as an interface between hardware and software. It manages system resources, provides services to users and applications, and ensures efficient execution of processes. Without an OS, users would have to manually manage hardware resources, making computing impractical for everyday use.

Lightweight operating system for old laptops
Functions of an Operating System
Operating systems perform several crucial functions to maintain system stability and usability. These functions include:
1. Process Management
The OS allocates resources to processes and ensures fair execution while preventing conflicts. It employs algorithms like First-Come-First-Serve (FCFS), Round Robin, and Shortest Job Next (SJN) to optimize CPU utilization and maintain system responsiveness.
2. Memory Management
The OS tracks memory usage and prevents memory leaks by implementing techniques such as paging, segmentation, and virtual memory. These mechanisms enable multitasking and improve overall system performance.
3. File System Management
It provides mechanisms for reading, writing, and deleting files while maintaining security through permissions and access control. File systems such as NTFS, FAT32, and ext4 are widely used across different operating systems.
4. Device Management
The OS provides device drivers to facilitate interaction with hardware components like printers, keyboards, and network adapters. It ensures smooth data exchange and resource allocation for input/output (I/O) operations.
5. Security and Access Control
It enforces authentication, authorization, and encryption mechanisms to protect user data and system integrity. Modern OSs incorporate features like firewalls, anti-malware tools, and secure boot processes to prevent unauthorized access and cyber threats.
6. User Interface
CLI-based systems, such as Linux terminals, provide direct access to system commands, while GUI-based systems, such as Windows and macOS, offer intuitive navigation through icons and menus.
Types of Operating Systems
Operating systems come in various forms, each designed to cater to specific computing needs. Some common types include:
1. Batch Operating System
These systems were widely used in early computing environments for tasks like payroll processing and scientific computations.
2. Multi-User Operating System
It ensures fair resource allocation and prevents conflicts between users. Examples include UNIX and Windows Server.
3. Real-Time Operating System (RTOS)
RTOS is designed for time-sensitive applications, where processing must occur within strict deadlines. It is used in embedded systems, medical devices, and industrial automation. Examples include VxWorks and FreeRTOS.
4 Mobile Operating System
Mobile OSs are tailored for smartphones and tablets, offering touchscreen interfaces and app ecosystems.
5 Distributed Operating System
Distributed OS manages multiple computers as a single system, enabling resource sharing and parallel processing. It is used in cloud computing and supercomputing environments. Examples include Google’s Fuchsia and Amoeba.
Popular Operating Systems
Several operating systems dominate the computing landscape, each catering to specific user needs and hardware platforms.
1. Microsoft Windows
It is popular among home users, businesses, and gamers. Windows 10 and 11 are the latest versions, offering improved performance, security, and compatibility.
2. macOS
macOS is Apple’s proprietary OS designed for Mac computers. It provides a seamless experience with Apple hardware and software, featuring robust security and high-end multimedia capabilities.
3. Linux
Linux is an open-source OS favored by developers, system administrators, and security professionals. It offers various distributions, including Ubuntu, Fedora, and Debian, each catering to different user preferences.
4. Android
It is based on the Linux kernel and supports a vast ecosystem of applications.
5. iOS
iOS is Apple’s mobile OS, known for its smooth performance, security, and exclusive app ecosystem. It powers iPhones and iPads, offering seamless integration with other Apple devices.
Future of Operating Systems
The future of operating systems is shaped by emerging technologies such as artificial intelligence (AI), cloud computing, and edge computing. Some key trends include:
1. AI-Driven OS Enhancements
AI-powered features, such as voice assistants and predictive automation, are becoming integral to modern OSs. AI helps optimize performance, enhance security, and personalize user experiences.
2. Cloud-Based Operating Systems
Cloud OSs enable users to access applications and data remotely. Chrome OS is an example of a cloud-centric OS that relies on internet connectivity for most functions.
3. Edge Computing Integration
With the rise of IoT devices, edge computing is gaining importance. Future OSs will focus on decentralized computing, reducing latency and improving real-time processing.
4. Increased Focus on Security
Cyber threats continue to evolve, prompting OS developers to implement advanced security measures such as zero-trust architectures, multi-factor authentication, and blockchain-based security.
3 notes
·
View notes
Text
The Strategic Value of Premium Gaming Subscriptions: A 2025 Analysis for Serious Gamers
The digital entertainment ecosystem has undergone a paradigm shift in recent years, with subscription-based models revolutionizing how consumers access interactive content. In 2025, premium gaming subscriptions represent not merely a convenience but a strategic advantage for discerning players seeking to maximize their entertainment investment. This comprehensive analysis examines the quantifiable benefits, technological advancements, and economic efficiencies inherent in today's premier gaming subscription services, providing essential insights for both casual enthusiasts and dedicated players.
Xbox Game Pass Ultimate: Redefining Content Economics
Microsoft's flagship subscription service has evolved into an unparalleled value proposition within the gaming industry, fundamentally altering the calculation of content acquisition costs versus accessibility. A meticulous analysis of the Xbox Game Pass Ultimate offering reveals several critical advantages that merit consideration.
Content Library Valuation and Fiscal Efficiency
The service's expansive library—now exceeding 450 high-caliber titles—represents a retail valuation of approximately $27,000 if purchased individually at standard market rates. This remarkable content aggregation creates an unprecedented 96% cost reduction compared to traditional ownership models when utilized by active subscribers who explore the catalog's breadth.
The inclusion of day-one releases from Xbox Game Studios, Bethesda Softworks, and Activision Blizzard constitutes a particularly compelling component. Quantitative analysis indicates that subscribers who would otherwise purchase just two first-party releases annually already achieve cost neutrality, with every subsequent title representing pure economic advantage.
Technical Infrastructure and Cross-Platform Integration
The service's cloud gaming infrastructure has achieved significant technical milestones in 2025, with server-side enhancements reducing input latency to 21ms—below the threshold of perception for most users—while delivering consistent 4K resolution at 60 frames per second on compatible devices. This technological foundation effectively democratizes access to computationally demanding experiences across smartphones, tablets, and older hardware configurations.
The seamless ecosystem integration facilitates a continuous gaming experience across multiple devices, with advanced synchronization protocols ensuring that progress, achievements, and personalized settings transfer instantaneously between platforms. This infrastructure represents significant additional value beyond the content library itself.
For those seeking immediate access to this comprehensive gaming ecosystem, Gift20nline's Xbox Game Pass Ultimate subscriptions provide verified activation codes with enterprise-grade security and guaranteed delivery within 24 hours.
PlayStation Plus Premium: Strategic Differentiation Through Curation and Legacy Content
Sony Interactive Entertainment's premium subscription tier employs a distinctly different strategic approach, emphasizing carefully curated content selection and preservation of gaming heritage as key differentiators in the competitive landscape.
Qualitative Content Selection Methodology
Rather than pursuing sheer numerical superiority, PlayStation Plus Premium implements a sophisticated content selection framework focused on three critical dimensions:
Critical Acclaim: Prioritizing titles with Metacritic scores above 80/100
Cultural Significance: Including influential works that have shaped game design
Exclusive Experiences: Providing access to content unavailable on competing platforms
This methodology results in a library of demonstrably higher average quality as measured by professional critical assessment and user satisfaction metrics, albeit with a more limited selection compared to Xbox Game Pass.
Historic Preservation and Backwards Compatibility
The service's most distinctive attribute lies in its comprehensive archival approach to gaming history, providing technically optimized access to titles spanning PlayStation's entire 30-year legacy. The preservation initiative extends beyond mere emulation, incorporating:
Resolution enhancement to 4K for select titles
Trophy support integration for legacy games
Control scheme modernization options
Performance stabilization for consistent frame rates
For PlayStation ecosystem participants, Gift20nline's PlayStation Plus Premium subscriptions provide immediate authentication with Sony's servers, enabling instant access to this curated content archive.
Steam Wallet: Liquidity and Market Efficiency in PC Gaming
While subscription services offer compelling value through bundled access, the PC gaming ecosystem benefits from a fundamentally different economic structure that emphasizes individual title ownership within a dynamic marketplace. Steam Wallet funds represent liquid digital capital with unique advantages in this environment.
Seasonal Sale Optimization Strategies
Steam's regular discount events create predictable opportunities for strategic purchasing that significantly enhance the effective purchasing power of wallet funds. Historical data analysis reveals:
Major seasonal sales (Summer, Winter, Autumn) offer average discounts of 67% across the catalog
Publisher-specific promotions provide 72% average discounts on targeted collections
Weekend deals frequently discount recent releases by 33-50%
Through strategic timing of purchases during these promotional periods, a $50 Steam Wallet allocation potentially yields $150-180 in content acquisition value—a 200-260% effective return on investment.
Catalog Diversity and Long-Tail Content Access
The platform's unparalleled library breadth—exceeding 50,000 titles in 2025—ensures access to specialized content across every conceivable genre, development scale, and commercial profile. This comprehensive coverage includes:
Independent productions with experimental mechanics
Mainstream commercial releases with high production values
Historical releases preserved through compatibility layers
Early-stage development projects with community input
Specialized simulation titles with narrow but deep appeal
This diversity allows Steam Wallet recipients to precisely target their specific gaming preferences with unmatched granularity. Gift20nline's Steam Wallet codes provide secured digital delivery with verification protocols that ensure legitimacy and immediate redemption capability.
Nintendo Switch Online + Expansion Pack: Ecosystem Value Through Exclusivity
Nintendo's subscription model represents a unique approach within the industry, leveraging the company's unparalleled intellectual property portfolio and distinctive hardware architecture to create value that cannot be replicated elsewhere.
Proprietary Content Exclusive to Subscribers
Unlike competitors who primarily aggregate third-party content, Nintendo employs its subscription service as a platform for exclusive software that cannot be purchased separately, including:
Nintendo 64 and Sega Genesis libraries with modern enhancements
Subscriber-exclusive software like Tetris 99 and Pac-Man 99
Mission modes and enhanced content for first-party releases
Limited-time special events and tournaments
This exclusivity creates a compelling value proposition for Nintendo hardware owners, as these experiences remain inaccessible through any other means, regardless of willingness to purchase separately.
Family Plan Economics and Multi-User Efficiency
The service's family membership option represents exceptional economic efficiency for multi-user households, supporting up to eight individual Nintendo Account holders under a single subscription. When fully utilized, this reduces the effective cost per user to approximately 12.5% of the individual rate—the most cost-efficient multi-user arrangement in the gaming subscription landscape.
For immediate access to Nintendo's proprietary content library, Gift20nline's Nintendo Switch Online subscriptions provide verified activation with guaranteed delivery, enabling instant enjoyment of exclusive Nintendo experiences.
Strategic Analysis: Emerging Trends and Future Trajectories
As the digital entertainment subscription landscape continues to evolve, several significant trends merit attention for their potential to reshape the value proposition of gaming services:
Cross-Ecosystem Integration and Subscription Consolidation
The boundaries between traditionally siloed entertainment ecosystems are progressively dissolving, with strategic partnerships creating integrated subscription bundles that span gaming, streaming video, music, and other digital media. These consolidated offerings represent enhanced consumer value through:
Unified billing and account management
Cross-media promotional synergies
Integrated discovery algorithms
Unified content delivery infrastructure
Early adopters of these consolidated models have demonstrated 17% higher retention rates and 22% greater lifetime customer value compared to single-service subscribers.
AI-Driven Content Personalization
Machine learning algorithms are transforming how subscription services deliver content to users, moving beyond simplistic recommendation systems toward sophisticated personalization engines that:
Predict optimal play times based on historical engagement patterns
Identify content with high probability of individual appeal
Customize difficulty curves across multiple titles
Generate personalized in-game challenges and rewards
These technologies significantly enhance the perceived value of subscription services by ensuring that each user's experience is optimized for their specific preferences and behaviors.
Cloud-Native Game Design Evolution
The subscription model is beginning to influence fundamental game design approaches, with developers creating experiences specifically optimized for cloud delivery and subscription contexts. These titles leverage unique technical capabilities:
Server-side physics calculations enabling unprecedented simulation complexity
Massive persistent worlds with continuous updates rather than discrete sequels
Asynchronous multiplayer integration across thousands of simultaneous users
Dynamic content generation based on collective player behaviors
As these design innovations mature, subscription services will increasingly offer experiences impossible to replicate in traditional purchase models.
Investment Optimization: Strategic Selection Framework
When evaluating gaming subscription options—whether for personal use or as a gift—apply this analytical framework to maximize return on investment:
Platform Ecosystem Analysis
Conduct a comprehensive inventory of existing hardware ownership and ecosystem investment. The value of a subscription increases proportionally with the degree of platform commitment due to:
Leveraging already-acquired hardware capabilities
Utilization of existing peripheral accessories
Integration with established friend networks and social connections
Continuity with current game progress and achievements
Content Consumption Pattern Matching
Analyze historical gaming engagement patterns to identify optimal service alignment:
High-volume, exploratory players extract maximum value from broad libraries (Xbox Game Pass Ultimate)
Selective, completion-focused players benefit from curated, quality-focused offerings (PlayStation Plus Premium)
Variable interest players with specific preferences achieve optimal results with à la carte models (Steam Wallet)
Family-oriented or nostalgia-driven players find superior value in Nintendo's ecosystem-specific approach
Return on Investment Calculation
Employ quantitative analysis to determine effective hourly entertainment cost using this formula:Effective Cost Per Hour = Subscription Fee ÷ (Games Explored × Average Hours Per Game)
This calculation typically reveals subscription models achieving costs below $0.30 per hour of quality entertainment—significantly outperforming traditional media consumption models.
Conclusion: The Analytical Case for Subscription Gaming
The subscription model represents the most economically efficient access method for interactive entertainment in 2025. Quantitative analysis consistently demonstrates that active subscribers receive 3-15x greater content value compared to traditional purchasing models, while simultaneously benefiting from technological advantages impossible to replicate through individual purchases.
For the analytically-minded consumer, the decision to adopt premium gaming subscriptions is not merely preference-based but mathematically sound. The subscription model eliminates inefficient content acquisition risks, provides enhanced technological infrastructure, and delivers continuous value expansion through regular catalog additions.
Gift20nline offers secure, verified access to all premium gaming subscription services with enterprise-grade delivery protocols ensuring activation within 24 hours. Their comprehensive selection includes Xbox Game Pass Ultimate, PlayStation Plus Premium, Steam Wallet codes, Nintendo Switch Online, and additional specialized services for discerning players seeking optimal value.
For those seeking to maximize their gaming investment or provide exceptional value as a gift, premium gaming subscriptions represent not merely a convenience but a strategic advantage in the modern digital entertainment landscape.
#cookie run kingdom#healthcare#arcane#artists on tumblr#elon musk#ides of march#cats of tumblr#batman#911 abc
2 notes
·
View notes
Text
**From PCI DSS to HIPAA: Ensuring Compliance with Robust IT Support in New York City**
Introduction
In contemporary digital world, organisations are a growing number of reliant on science for their operations. This dependence has caused a heightened focus on cybersecurity and compliance specifications, specifically in regulated industries like healthcare and finance. For services working in New York City, wisdom the nuances of compliance frameworks—specifically the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA)—is quintessential. Navigating those policies requires potent IT give a boost to, which encompasses everything from community infrastructure to documents management.
With the rapid advancement of technological know-how, organizations ought to additionally remain abreast of high-quality practices in details technologies (IT) give a boost to. This article delves into how organizations can ensure that compliance with PCI DSS and HIPAA thru triumphant IT processes whilst leveraging materials from accurate providers like Microsoft, Google, Amazon, and others.
Understanding PCI DSS What is PCI DSS?
The https://brooksxaoj631.over.blog/2025/04/navigating-cybersecurity-in-the-big-apple-essential-it-support-solutions-for-new-york-businesses.html Payment Card Industry Data Security Standard (PCI DSS) is a group of safety principles designed to look after card tips all the way through and after a economic transaction. It was once proven by using significant credit card enterprises to fight growing times of fee fraud.
Why is PCI DSS Important?
Compliance with PCI DSS enables groups defend touchy economic recordsdata, thereby modifying visitor trust and slicing the possibility of info breaches. Non-compliance can bring about intense consequences, such as hefty fines or maybe being banned from processing credit score card transactions.

youtube
Key Requirements of PCI DSS Build and Maintain a Secure Network: This carries fitting a firewall to preserve cardholder knowledge. Protect Cardholder Data: Encrypt kept files and transmit it securely. Maintain a Vulnerability Management Program: Use antivirus utility and develop protect structures. Implement Strong Access Control Measures: Restrict entry to in basic terms people that want it. Regularly Monitor and Test Networks: Keep observe of all get admission to to networks and aas a rule look at various protection tactics. Maintain an Information Security Policy: Create insurance policies that cope with defense necessities. Exploring HIPAA Compliance What is HIPAA?
The Health Insurance Portability and Accountability Act (HIPAA) sets the ordinary for conserving sensitive sufferer know-how in the healthcare trade. Any entity that offers with blanketed well being know-how (PHI) have got to adjust to HIPAA regulations.
Importance of HIPAA Compliance
HIPAA compliance no longer handiest protects affected person privateness however also guarantees more suitable healthcare outcome with the aid of permitting maintain sharing of affected person data between permitted entities. Violations can cause titanic fines, prison results, and wreck to popularity.
" style="max-width:500px;height:auto;">

Core Components of HIPAA Compliance Privacy Rule: Establishes countr
2 notes
·
View notes