#Monitor Backup
Explore tagged Tumblr posts
Text
Install Splunk and Veeam App on Windows Server to monitor VBR
Splunk Enterprise is a powerful platform that automates the collection, indexing, monitoring, and alerting of data. This enables you to aggregate and analyze events efficiently. With Splunk, you can gain full control over your data flow and leverage it to drive business insights and decisions. Kindly read about data management and governance. n this acticle, we shall discuss how to install Splunk…
#Backup#Backup and Recovery#Backup Data#Backup Files and Folders#Linux#MacOS#Microsoft Windows#monitor#Monitor Backup#Monitor VBR with Splunk#Monitor Veeam Backup And Replication [VBR] with Splunk#Splunk#Splunk Enterprise#Veeam App for Splunk#Veeam App for Splunk Setup#Windows 10#Windows 11#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022
0 notes
Text
//I think about this off and on sometimes but the idea of Lambda referring to himself as a something sometimes and not a someone and not quite catching himself before it can slip out.
#backup log {ooc}#//is it a bit of the self hatred? yes#//but i do think it's partially him stepping back and being like 'huh. that it is?' and coming to a very not so great conclusion about-#//-his experiences#//i think i've got a mini story kicking around on my computer that goes into it a bit but the tl;dr of that story is him being like-#//-'if you're allowed to be people then you get to be a someone if you're not then you're a something. and somethings get to be monsters'#//or something like that it's kind of old so i don't really remember much of it right now#//it's that little bit that seeps out when he isn't monitoring/self policing himself#//idk it's something that's this bizarre mix of self hatred and being like kind of happy(?) that he doesn't have to deal with that in a-#//-sense? at least for him? idk a lot of mixed emotions there and this sounds silly as hell without much context but trust me it's sort of-#//-there? just roll with it
7 notes
·
View notes
Text
Today's show was so overhwelmingly chaotic that I had to use my inhaler TWICE (I've been trying to only use it once a day to see how my lungs are doing). But as chaotic and exhausting as it was... Goddamn I'm good at what I do.
While they were diagnosing a problem and working through Plan A, I set up Plan F by myself while 6 people stood around watching Plan A-C fail.
And when they yelled that the show would have to be canceled this week, I had Plan F up, set, running, and it was what I told them to do from the start.
Why is there only Plan A-C, then suddenly Plan F?
My Plan was always Plan F, for "Fuck it, we bail".
#i deserve this peanut butter cookie goddammit#the teleprompter system that's been failing for MONTHS finally kicked the bucket just before we were to film the show#and by the time they finally admitted it couldn't be saved i already had a backup system running#with the script fully loaded and formatted into a teleprompting software on my PC and had set up a monitor under the camera#it didn't have to be chaos but why tf did it take 6 people to watch 2 idiot engineers realize#they couldn't save THE COMPUTER THAT STILL RAN ON WINDOWS VISTA
11 notes
·
View notes
Text
okay, to be completely sure i post it here for Bubbs.
Gehog very quick reference in few minutes
for fun
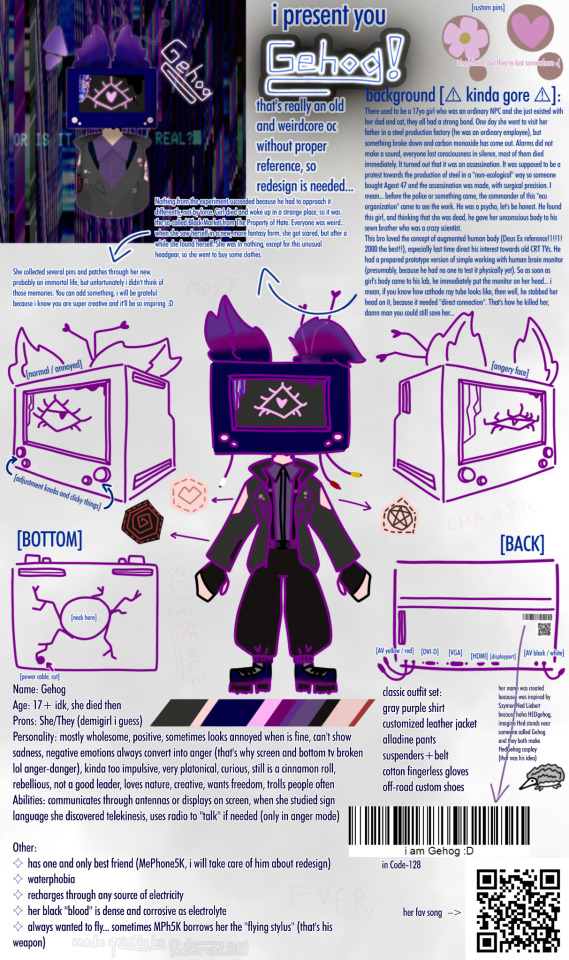
for fun....
#gehog#panterus2019#frau panteruz#frau panterus#gehog oc#hedgehog#szymon hed liebert#oc reference#chaotic oc#weirdcore#weirdcore oc#backup post#too lazy to remaster properly#tpoh inspired#tpoh oc#still working on it#tv head#tv girl#crt tv#crt monitor#fluffy ears#cinnamon roll#funny barcode#qr code#funny song#Agent 47 mentioned#gehog reference#quick character reference#man im tired#Bubbs
7 notes
·
View notes
Text
i swear to god if my computer doesn't start working properly again
i have two jobs dependent on that fucking thing and yet it once again doesn't connect with the monitor
#i have current commission backups on my laptop but that's not my only job#also that fucking monitor is the only well color calibrated thing in the house
8 notes
·
View notes
Text
Discover top-quality laptops, computers, gaming accessories, tech gadgets, and computer accessories at Matrix Warehouse. Shop online or in-store across South Africa for unbeatable prices and nationwide delivery. Visit now!
#Laptops & Accessories#Desktop Computers#Smart Devices#Computer Hardware#Monitors & Projectors#Computer Accessories#Backup Power Solutions#Printers and Printer Toners#Networking Equipment#Computer Software
2 notes
·
View notes
Text
UPS (Uninterruptible Power Supply): Protezione Affidabile per il Tuo PC in Caso di Blackout
SKE 850VA/480W UPS Gruppo di Continuità per PC Router Modem UPS Gruppo Continuità UPS HL850 In un mondo sempre più connesso e dipendente dall’elettricità, la protezione dei nostri dispositivi elettronici è fondamentale, soprattutto in caso di interruzioni di corrente o sbalzi di tensione. Un UPS (Uninterruptible Power Supply) è uno strumento essenziale per garantire la continuità…
#Review#Unboxing#850VA/480W#Backup alimentazione#Blackout protezione#Data Center UPS#Enterprise UPS#Gruppo di Continuità#ion#lithium#lithium ion#Lithium-ion UPS#Protezione dispositivi elettronici#recensione#SKE#SKE Smart-UPS Ultra#Smart-UPS#Smart-UPS Ultra#Uninterruptible Power Supply#UPS#UPS 850VA/480W#UPS Management#UPS Monitoring
4 notes
·
View notes
Text
this is NOT the time for my drawing tablet to act up!!!!!!!!!!!!
#. its not too bad but i need it to survive July for artfight#anyway thank god my ipad still works so i have a backup plan#but no yeah im gonna have to save money in july as a safety net#right now my anxiety is at its highest on it i dont know if it will survive the year#WHICH is shocking its barely 2 years old#its because im constantly using it everyday as my main monitor lmao#look a talking muffin
4 notes
·
View notes
Text
It's a Tech Kinda Weekend...
So, I have a PC and a laptop (and a Chromebook but whatever).
Both were Windows 10 when I got them, now upgraded to Windows 11. On Windows 10, you set a 4 digit pin. On Windows 11, you do 6-8 digit pins. But when it upgraded to Windows 11, all fine, it kept my pin.
An update came out the other day and I installed it on my laptop. Went to turn it on yesterday, and it asked for my pin instead of fingerprint (it's fine, it does that every month or so where it wants both in one login just to kind of re-verify).
And apparently it won't take my 4 digit pin anymore. It only wants a 6-8 digit pin. Which again, coming from windows 10 originally, I only ever had a 4 digit pin.
I ended up having to bitlocker my own laptop and completely reinstall the operating system, fully wiping my files and resetting to new, all because Windows 11 suddenly decided to force a 6-8 digit pin without letting me set one.
So, if you have a 4-digit login pin for your PC, go update it or you might face the same problem I did...
Today is less dramatic, I'm just upgrading my portable drive from 1TB to 2TB. So far I'm only moving the folder I keep shows in...
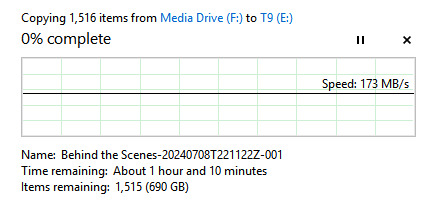
**I don't know why there are so many "Items" listed, I don't record THAT many shows...
Oh, it's because half of my watch-through posts were mistakenly put in that folder instead of the Screenshots one.
#I upgrade it every 5 years or so just to make sure I don't have a drive go bad and lose data#the laptop reset wasn't more than an aggravation issue- i keep everything on it cloud backup anyways#but i had to spend 5 hours between the reset and recovering old stuff#i have a bit of a neurotic stupidity where at WORK i have to constantly monitor drives and worry about space#2 TB left on a drive at work is like 'you have 1 month to get new drives approved or it's a disaster'#I have 8tb at home now and i'm barely using 10% of the space I have#and most of that 10% is everything saved on two different drives in case one crashes#i have a lot of space free and frankly i'm always wanting more#i'm like a dragon who hoards unused space
2 notes
·
View notes
Text
Automated Disaster Recovery Solutions by Esconet Technologies
Esconet Technologies, based in New Delhi, offers comprehensive Automated Disaster Recovery (ADR) solutions designed to ensure business continuity and data integrity. Their services encompass Cold DR for cost-effective data backup, Hot DR for real-time data synchronization, and Application-Supported DR to safeguard critical applications like Active Directory and databases. With continuous DR monitoring, management operations, and partnerships with leading OEMs such as Dell Technologies, HPE, VMware, Veeam, and Microsoft, Esconet delivers robust and scalable disaster recovery solutions tailored to diverse organizational needs.
for more details, Visit- Esconet Technologies Automated Disaster Recovery Solutions page
#Automated Disaster Recovery#Business Continuity Solutions#Cold DR Services#Hot DR Solutions#Application-Supported DR#Data Backup and Recovery#DR Monitoring and Management#Esconet Technologies#Disaster Recovery New Delhi#IT Infrastructure Resilience
0 notes
Text
Backup Monitoring: The Silent Guardian of Cyber Resilience
In the race to prevent cyberattacks, many businesses focus heavily on firewalls, antivirus software, and access controls. But when it comes to recovering from an attack, Backup Monitoring becomes the silent hero. This article uncovers how real-time monitoring ensures your backups are intact, current, and free of corruption, ready for action when ransomware or data breaches occur. With data integrity and system continuity at stake, it's time to recognize Backup Monitoring as a key pillar of your cyber resilience strategy. Don't let a failed backup go unnoticed—because your survival may depend on it.
0 notes
Text

Happy Birthday AUTONNOMOUS
https://www.autonnomous.com/
0 notes
Text
Backups and Disaster Recovery | Innovative Computing Systems!

Our team of highly skilled and certified engineers will work with you to design a backup solution, build a Backups and Disaster Recovery plan, and validate that plan to ensure you are prepared for the worst. Our award-winning cloud-hosted backup platforms ensure that your backups are always available, safe, and secure.
Visit Now! https://www.innovativecomp.com/backups-and-disaster-recovery/
0 notes
Text
Cybersecurity Considerations in Cloud-Based Estimating Service Platforms
Introduction The rapid adoption of cloud-based tools in industries like construction, manufacturing, and engineering has revolutionized how businesses handle estimating services. Cloud-based estimating service platforms provide immense benefits, such as accessibility, collaboration, and real-time updates, which help companies improve efficiency and reduce costs. However, the increased use of these platforms also raises significant cybersecurity concerns. Protecting sensitive data, ensuring platform reliability, and maintaining secure access are all critical components of ensuring the success of cloud-based estimating services.
This article will explore the cybersecurity considerations that organizations must take into account when utilizing cloud-based estimating services. We will highlight the importance of robust security measures, best practices for mitigating risks, and the role of the cloud service provider in safeguarding data.
Understanding the Cybersecurity Risks in Cloud-Based Estimating Services Cloud-based estimating services store vast amounts of sensitive information, including cost estimates, project budgets, pricing data, and contract details. This data is crucial for project planning, and its loss or theft could result in financial, legal, or reputational damage. The cybersecurity risks in cloud platforms include data breaches, unauthorized access, data manipulation, and service outages that can disrupt operations.
Hackers and cybercriminals may target cloud-based estimating services to access proprietary cost data, sensitive client information, or intellectual property. This makes cloud security a critical concern for businesses that rely on these services. Additionally, the remote nature of cloud access increases the potential for data exposure, especially if users access the platform from unsecured devices or networks.
Choosing a Secure Cloud Service Provider One of the first steps in ensuring cybersecurity for cloud-based estimating services is selecting a reliable cloud service provider (CSP) that prioritizes security. Reputable CSPs offer advanced security features, including end-to-end encryption, multi-factor authentication (MFA), and continuous monitoring of their networks. They should also comply with industry standards and regulations, such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA), depending on the industry.
Before selecting a CSP, organizations should thoroughly evaluate the provider’s security protocols, certifications, and track record. It’s also important to assess the provider’s ability to scale security measures as your business grows. A strong partnership with a reputable provider ensures that security is embedded into the platform from the ground up.
Data Encryption and Secure Storage Data encryption is one of the most effective measures for securing sensitive information in cloud-based estimating platforms. By encrypting data both during transmission and at rest, companies can ensure that even if hackers intercept the data, they cannot access or misuse it.
In addition to encryption, secure storage practices are crucial for protecting estimating data. Cloud service providers should store data in secure data centers equipped with physical security measures, such as biometric access controls, surveillance, and disaster recovery plans. These physical and digital safeguards help protect against both cyber threats and natural disasters.
User Access Control and Authentication Controlling user access is another essential aspect of cybersecurity in cloud-based estimating services. Businesses must establish strict user access protocols to ensure that only authorized personnel can access sensitive project data and cost estimates. This includes defining user roles, limiting permissions, and requiring strong authentication methods.
Multi-factor authentication (MFA) is a powerful tool for enhancing access security. By requiring users to provide additional verification, such as a code sent to their mobile device, alongside their username and password, MFA ensures that only legitimate users can access the platform.
Organizations should also regularly review and update user access permissions to ensure that former employees or contractors do not retain access to sensitive information after their engagement ends.
Data Backup and Disaster Recovery Plans Data loss is a major risk for businesses relying on cloud-based estimating services. Whether due to a cyber attack, natural disaster, or technical failure, losing critical estimating data can severely disrupt project timelines and budget management. Therefore, having a solid data backup and disaster recovery plan is crucial.
Cloud-based platforms should offer automated data backups to prevent loss of estimates and other project information. It is important for businesses to regularly test their backup systems and ensure that data can be quickly recovered in the event of an incident. The disaster recovery plan should also outline clear steps for restoring access to the platform, rebuilding project estimates, and ensuring continuity of operations.
Monitoring and Incident Response Continuous monitoring of the cloud environment is essential for detecting potential security threats. Cloud service providers should implement real-time threat detection systems to identify unusual activities, such as unauthorized access attempts or unusual data transfers. Monitoring tools can also track user behaviors, alert administrators about security anomalies, and provide insights into potential vulnerabilities.
In addition to monitoring, businesses should have a clear incident response plan in place. This plan outlines the steps to take in the event of a cyberattack, such as isolating affected systems, notifying affected parties, and coordinating with cybersecurity experts. A well-defined response plan helps minimize the impact of a security breach and ensures that the organization can recover quickly.
Employee Training and Security Awareness Even with the best technology in place, human error remains one of the largest cybersecurity risks. Employees who are unaware of security best practices may inadvertently compromise data by clicking on phishing emails, using weak passwords, or accessing the platform from unsecured devices.
To mitigate this risk, organizations should provide regular cybersecurity training to all employees who use cloud-based estimating services. Training should cover topics such as identifying phishing attempts, using strong and unique passwords, and securing devices. A culture of cybersecurity awareness helps reduce the chances of a successful attack and empowers employees to play an active role in protecting company data.
Compliance and Regulatory Requirements Depending on the industry, businesses using cloud-based estimating services must comply with various regulations related to data security and privacy. For instance, the construction industry may need to adhere to data protection laws, while healthcare-related estimating services might be subject to HIPAA regulations.
Cloud service providers should be transparent about their compliance with these regulations, and businesses should ensure that they understand their obligations when using cloud-based platforms. By partnering with a provider that meets the required compliance standards, companies can avoid legal and financial penalties while safeguarding their data.
Conclusion As cloud-based estimating services become increasingly integral to project planning and execution, securing sensitive data and protecting against cybersecurity threats are paramount concerns. Organizations must take proactive measures, such as selecting reputable service providers, implementing data encryption, controlling user access, and creating robust backup and disaster recovery plans. With a focus on cybersecurity, companies can confidently leverage cloud-based estimating services while minimizing the risk of data breaches and service disruptions.
By investing in the right security tools, maintaining ongoing monitoring, and ensuring employee awareness, businesses can strengthen the cybersecurity of their cloud-based estimating platforms and protect the valuable data that drives their projects forward.
#Estimating Service#cybersecurity#cloud-based platforms#data encryption#user access control#multi-factor authentication#cloud security#disaster recovery#data backup#incident response#project estimating#estimating tools#secure storage#data protection#compliance#security measures#cybersecurity best practices#project budgeting#risk management#phishing prevention#employee training#cloud service provider#threat detection#construction estimating#privacy regulations#disaster recovery planning#data breaches#system monitoring#project security#secure access
0 notes
Text
Simplify NoSQL Database Management with Simple Logic 🗂️
Database Optimization⚡ Enhance the performance of MongoDB, Cassandra, and more
Data Scalability📈 Seamlessly scale to meet evolving demands
Backup & Recovery🔄 Secure your data with robust recovery options
24/7 Monitoring👀 Proactively identify and resolve database issues
Partner with Simple Logic for NoSQL Success 📧 Email: [email protected] 📞 Phone: +91 86556 16540
#Database#DatabaseOptimization#DatabaseManagement#MongoDB#Cassandra#Data#DataScalability#Backup#Recovery#Monitoring#DatabaseIssues#SimpleLogicIT#MakingITSimple#SimpleLogic#MakeITSimple
0 notes