#Network Operating Systems Market
Explore tagged Tumblr posts
Text
Global Network Operating Systems Market size is expected to reach nearly USD 42.81 Bn by 2030 with the CAGR of 41.21% during the forecast period. The report has covered Country market trends with a competitive landscape.
0 notes
Text
Empower Your Business with DDS4U's Comprehensive Services

At DDS4U, we provide a suite of services designed to streamline your operations, drive growth, and ensure your business stays ahead in today’s competitive market.
AI-Powered Business Automation
Revolutionize your workflows with our AI-driven automation platform. By automating repetitive tasks and integrating advanced AI technologies, we help you save time, reduce costs, and improve accuracy, allowing you to focus on strategic initiatives.
Custom Software Development
Our experienced software developers create tailored solutions that meet your unique business needs. Whether you require a new application or need to upgrade existing systems, our innovative and scalable software solutions ensure your business operates efficiently and effectively.
CRM Solutions
Enhance your customer relationships with our comprehensive CRM platform. Manage customer interactions, streamline sales processes, and gain valuable insights to drive better business decisions. Our CRM system is designed to boost customer satisfaction and loyalty, ultimately leading to increased sales and growth.
Targeted Advertisement Platform
Maximize your reach and engagement with our cutting-edge advertising platform. Tailor your campaigns to specific audiences and utilize real-time analytics to optimize performance. Our platform helps you achieve higher conversion rates and a stronger online presence.
In-App Advertisement Space
Monetize your mobile applications with designated ad spaces. Our in-app advertising feature allows you to serve targeted ads to users, providing an additional revenue stream while ensuring ads are relevant and non-intrusive.
Referral Portal
Expand your network and drive business growth with our referral portal. Easily manage and track referrals, incentivize partners, and streamline communication. Our portal fosters strong professional relationships and opens new opportunities for your business.
Business Networking Platform
Connect with industry professionals and collaborate on projects through our dynamic networking platform. Share knowledge, explore partnerships, and expand your reach in a supportive community designed to foster business success.
Social Media Poster Design
Boost your social media presence with professionally designed posters. Our team creates visually appealing graphics tailored for social media platforms, helping you engage with your audience and enhance your brand’s online visibility.
Discount Booklets
Offer your customers exclusive discounts through our customizable discount booklets. This feature helps increase customer loyalty and encourages repeat business, driving higher sales and customer satisfaction.
Self-Managed Advertisements
Take control of your advertising campaigns with our self-managed ad platform. Create, monitor, and optimize your ads independently, giving you the flexibility to adjust strategies and maximize ROI.
Video Promotions
Enhance your marketing efforts with engaging promotional videos. Showcase your products and services, highlight unique selling points, and captivate your audience with compelling visual content that drives brand awareness and customer engagement.
At DDS4U, we are committed to helping your business succeed. Our comprehensive services are designed to address your unique challenges and support your growth ambitions. Partner with us to unlock new opportunities and achieve your business goals.
#At DDS4U#we provide a suite of services designed to streamline your operations#drive growth#and ensure your business stays ahead in today’s competitive market.#AI-Powered Business Automation#Revolutionize your workflows with our AI-driven automation platform. By automating repetitive tasks and integrating advanced AI technologie#we help you save time#reduce costs#and improve accuracy#allowing you to focus on strategic initiatives.#Custom Software Development#Our experienced software developers create tailored solutions that meet your unique business needs. Whether you require a new application o#our innovative and scalable software solutions ensure your business operates efficiently and effectively.#CRM Solutions#Enhance your customer relationships with our comprehensive CRM platform. Manage customer interactions#streamline sales processes#and gain valuable insights to drive better business decisions. Our CRM system is designed to boost customer satisfaction and loyalty#ultimately leading to increased sales and growth.#Targeted Advertisement Platform#Maximize your reach and engagement with our cutting-edge advertising platform. Tailor your campaigns to specific audiences and utilize real#In-App Advertisement Space#Monetize your mobile applications with designated ad spaces. Our in-app advertising feature allows you to serve targeted ads to users#providing an additional revenue stream while ensuring ads are relevant and non-intrusive.#Referral Portal#Expand your network and drive business growth with our referral portal. Easily manage and track referrals#incentivize partners#and streamline communication. Our portal fosters strong professional relationships and opens new opportunities for your business.#Business Networking Platform#Connect with industry professionals and collaborate on projects through our dynamic networking platform. Share knowledge#explore partnerships
1 note
·
View note
Text


In the current rapidly evolving digital currency market, decentralized finance (DeFi) platforms are redefining the shape of financial services with their unique advantages. Bit Loop, as a leading decentralized lending platform, not only provides a safe and transparent lending environment, but also opens up new passive income channels for users through its innovative sharing reward system.
Personal links and permanent ties: Create a stable revenue stream One of the core parts of Bit Loop is its recommendation system, which allows any user to generate a unique sharing link when they join the platform. This link is not only a “key” for users to join the Bit Loop, but also a tool for them to establish an offline network. It is worth noting that offline partners who join through this link are permanently tied to the recommender, ensuring that the sharer can continue to receive rewards from the offline partner’s activities.
Unalterable referral relationships: Ensure fairness and transparency A significant advantage of blockchain technology is the immutability of its data. In Bit Loop, this means that once a referral link and live partnership is established, the relationship is fixed and cannot be changed. This design not only protects the interests of recommenders, but also brings a stable user base and activity to the platform, while ensuring the fairness and transparency of transactions.
Automatically distribute rewards: Simplify the revenue process Another highlight of the Bit Loop platform is the ability for smart contracts to automatically distribute rewards. When the partner completes the circulation cycle, such as investment returns or loan payments, the smart contract automatically calculates and sends the corresponding percentage of rewards directly to the recommender’s wallet. This automatic reward distribution mechanism not only simplifies the process of receiving benefits, but also greatly improves the efficiency of capital circulation.
Privacy protection and security: A security barrier for funds All transactions and money flows are carried out on the blockchain, guaranteeing transparency and traceability of every operation. In addition, the use of smart contracts significantly reduces the risk of fraud and misoperation, providing a solid security barrier for user funds. Users can confidently invest and promote boldly, and enjoy the various conveniences brought by decentralized finance.
conclusion As decentralized finance continues to evolve, Bit Loop offers a new economic model through its unique recommendation system that enables users to enjoy highly secure and transparent financial services while also earning passive income by building and maintaining a personal network. Whether for investors seeking stable passive income or innovators looking to explore new financial possibilities through blockchain technology, Bit Loop provides a platform not to be missed.

#In the current rapidly evolving digital currency market#decentralized finance (DeFi) platforms are redefining the shape of financial services with their unique advantages. Bit Loop#as a leading decentralized lending platform#not only provides a safe and transparent lending environment#but also opens up new passive income channels for users through its innovative sharing reward system.#Personal links and permanent ties: Create a stable revenue stream#One of the core parts of Bit Loop is its recommendation system#which allows any user to generate a unique sharing link when they join the platform. This link is not only a “key” for users to join the Bi#but also a tool for them to establish an offline network. It is worth noting that offline partners who join through this link are permanent#ensuring that the sharer can continue to receive rewards from the offline partner’s activities.#Unalterable referral relationships: Ensure fairness and transparency#A significant advantage of blockchain technology is the immutability of its data. In Bit Loop#this means that once a referral link and live partnership is established#the relationship is fixed and cannot be changed. This design not only protects the interests of recommenders#but also brings a stable user base and activity to the platform#while ensuring the fairness and transparency of transactions.#Automatically distribute rewards: Simplify the revenue process#Another highlight of the Bit Loop platform is the ability for smart contracts to automatically distribute rewards. When the partner complet#such as investment returns or loan payments#the smart contract automatically calculates and sends the corresponding percentage of rewards directly to the recommender’s wallet. This au#but also greatly improves the efficiency of capital circulation.#Privacy protection and security: A security barrier for funds#All transactions and money flows are carried out on the blockchain#guaranteeing transparency and traceability of every operation. In addition#the use of smart contracts significantly reduces the risk of fraud and misoperation#providing a solid security barrier for user funds. Users can confidently invest and promote boldly#and enjoy the various conveniences brought by decentralized finance.#conclusion#As decentralized finance continues to evolve#Bit Loop offers a new economic model through its unique recommendation system that enables users to enjoy highly secure and transparent fin
1 note
·
View note
Text
There Were Always Enshittifiers
I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me in DC TONIGHT (Mar 4), and in RICHMOND TOMORROW (Mar 5). More tour dates here. Mail-order signed copies from LA's Diesel Books.

My latest Locus column is "There Were Always Enshittifiers." It's a history of personal computing and networked communications that traces the earliest days of the battle for computers as tools of liberation and computers as tools for surveillance, control and extraction:
https://locusmag.com/2025/03/commentary-cory-doctorow-there-were-always-enshittifiers/
The occasion for this piece is the publication of my latest Martin Hench novel, a standalone book set in the early 1980s called "Picks and Shovels":
https://us.macmillan.com/books/9781250865908/picksandshovels
The MacGuffin of Picks and Shovels is a "weird PC" company called Fidelity Computing, owned by a Mormon bishop, a Catholic priest, and an orthodox rabbi. It sounds like the setup for a joke, but the punchline is deadly serious: Fidelity Computing is a pyramid selling cult that preys on the trust and fellowship of faith groups to sell the dreadful Fidelity 3000 PC and its ghastly peripherals.
You see, Fidelity's products are booby-trapped. It's not merely that they ship with programs whose data-files can't be read by apps on any other system – that's just table stakes. Fidelity's got a whole bag of tricks up its sleeve – for example, it deliberately damages a specific sector on every floppy disk it ships. The drivers for its floppy drive initialize any read or write operation by checking to see if that sector can be read. If it can, the computer refuses to recognize the disk. This lets the Reverend Sirs (as Fidelity's owners style themselves) run a racket where they sell these deliberately damaged floppies at a 500% markup, because regular floppies won't work on the systems they lure their parishioners into buying.
Or take the Fidelity printer: it's just a rebadged Okidata ML-80, the workhorse tractor feed printer that led the market for years. But before Fidelity ships this printer to its customers, they fit it with new tractor feed sprockets whose pins are slightly more widely spaced than the standard 0.5" holes on the paper you can buy in any stationery store. That way, Fidelity can force its customers to buy the custom paper that they exclusively peddle – again, at a massive markup.
Needless to say, printing with these wider sprocket holes causes frequent jams and puts a serious strain on the printer's motors, causing them to burn out at a high rate. That's great news – for Fidelity Computing. It means they get to sell you more overpriced paper so you can reprint the jobs ruined by jams, and they can also sell you their high-priced, exclusive repair services when your printer's motors quit.
Perhaps you're thinking, "OK, but I can just buy a normal Okidata printer and use regular, cheap paper, right?" Sorry, the Reverend Sirs are way ahead of you: they've reversed the pinouts on their printers' serial ports, and a normal printer won't be able to talk to your Fidelity 3000.
If all of this sounds familiar, it's because these are the paleolithic ancestors of today's high-tech lock-in scams, from HP's $10,000/gallon ink to Apple and Google's mobile app stores, which cream a 30% commission off of every dollar collected by an app maker. What's more, these ancient, weird misfeatures have their origins in the true history of computing, which was obsessed with making the elusive, copy-proof floppy disk.
This Quixotic enterprise got started in earnest with Bill Gates' notorious 1976 "open letter to hobbyists" in which the young Gates furiously scolds the community of early computer hackers for its scientific ethic of publishing, sharing and improving the code that they all wrote:
https://en.wikipedia.org/wiki/An_Open_Letter_to_Hobbyists
Gates had recently cloned the BASIC programming language for the popular Altair computer. For Gates, his act of copying was part of the legitimate progress of technology, while the copying of his colleagues, who duplicated Gates' Altair BASIC, was a shameless act of piracy, destined to destroy the nascent computing industry:
As the majority of hobbyists must be aware, most of you steal your software. Hardware must be paid for, but software is something to share. Who cares if the people who worked on it get paid?
Needless to say, Gates didn't offer a royalty to John Kemeny and Thomas Kurtz, the programmers who'd invented BASIC at Dartmouth College in 1963. For Gates – and his intellectual progeny – the formula was simple: "When I copy you, that's progress. When you copy me, that's piracy." Every pirate wants to be an admiral.
For would-be ex-pirate admirals, Gates's ideology was seductive. There was just one fly in the ointment: computers operate by copying. The only way a computer can run a program is to copy it into memory – just as the only way your phone can stream a video is to download it to its RAM ("streaming" is a consensus hallucination – every stream is a download, and it has to be, because the internet is a data-transmission network, not a cunning system of tubes and mirrors that can make a picture appear on your screen without transmitting the file that contains that image).
Gripped by this enshittificatory impulse, the computer industry threw itself headfirst into the project of creating copy-proof data, a project about as practical as making water that's not wet. That weird gimmick where Fidelity floppy disks were deliberately damaged at the factory so the OS could distinguish between its expensive disks and the generic ones you bought at the office supply place? It's a lightly fictionalized version of the copy-protection system deployed by Visicalc, a move that was later publicly repudiated by Visicalc co-founder Dan Bricklin, who lamented that it confounded his efforts to preserve his software on modern systems and recover the millions of data-files that Visicalc users created:
http://www.bricklin.com/robfuture.htm
The copy-protection industry ran on equal parts secrecy and overblown sales claims about its products' efficacy. As a result, much of the story of this doomed effort is lost to history. But back in 2017, a redditor called Vadermeer unearthed a key trove of documents from this era, in a Goodwill Outlet store in Seattle:
https://www.reddit.com/r/VintageApple/comments/5vjsow/found_internal_apple_memos_about_copy_protection/
Vaderrmeer find was a Apple Computer binder from 1979, documenting the company's doomed "Software Security from Apple's Friends and Enemies" (SSAFE) project, an effort to make a copy-proof floppy:
https://archive.org/details/AppleSSAFEProject
The SSAFE files are an incredible read. They consist of Apple's best engineers beavering away for days, cooking up a new copy-proof floppy, which they would then hand over to Apple co-founder and legendary hardware wizard Steve Wozniak. Wozniak would then promptly destroy the copy-protection system, usually in a matter of minutes or hours. Wozniak, of course, got the seed capital for Apple by defeating AT&T's security measures, building a "blue box" that let its user make toll-free calls and peddling it around the dorms at Berkeley:
https://512pixels.net/2018/03/woz-blue-box/
Woz has stated that without blue boxes, there would never have been an Apple. Today, Apple leads the charge to restrict how you use your devices, confining you to using its official app store so it can skim a 30% vig off every dollar you spend, and corralling you into using its expensive repair depots, who love to declare your device dead and force you to buy a new one. Every pirate wants to be an admiral!
https://www.vice.com/en/article/tim-cook-to-investors-people-bought-fewer-new-iphones-because-they-repaired-their-old-ones/
Revisiting the early PC years for Picks and Shovels isn't just an excuse to bust out some PC nostalgiacore set-dressing. Picks and Shovels isn't just a face-paced crime thriller: it's a reflection on the enshittificatory impulses that were present at the birth of the modern tech industry.
But there is a nostalgic streak in Picks and Shovels, of course, represented by the other weird PC company in the tale. Computing Freedom is a scrappy PC startup founded by three women who came up as sales managers for Fidelity, before their pangs of conscience caused them to repent of their sins in luring their co-religionists into the Reverend Sirs' trap.
These women – an orthodox lesbian whose family disowned her, a nun who left her order after discovering the liberation theology movement, and a Mormon woman who has quit the church over its opposition to the Equal Rights Amendment – have set about the wozniackian project of reverse-engineering every piece of Fidelity hardware and software, to make compatible products that set Fidelity's caged victims free.
They're making floppies that work with Fidelity drives, and drives that work with Fidelity's floppies. Printers that work with Fidelity computers, and adapters so Fidelity printers will work with other PCs (as well as resprocketing kits to retrofit those printers for standard paper). They're making file converters that allow Fidelity owners to read their data in Visicalc or Lotus 1-2-3, and vice-versa.
In other words, they're engaged in "adversarial interoperability" – hacking their own fire-exits into the burning building that Fidelity has locked its customers inside of:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
This was normal, back then! There were so many cool, interoperable products and services around then, from the Bell and Howell "Black Apple" clones:
https://forum.vcfed.org/index.php?threads%2Fbell-howell-apple-ii.64651%2F
to the amazing copy-protection cracking disks that traveled from hand to hand, so the people who shelled out for expensive software delivered on fragile floppies could make backups against the inevitable day that the disks stopped working:
https://en.wikipedia.org/wiki/Bit_nibbler
Those were wild times, when engineers pitted their wits against one another in the spirit of Steve Wozniack and SSAFE. That era came to a close – but not because someone finally figured out how to make data that you couldn't copy. Rather, it ended because an unholy coalition of entertainment and tech industry lobbyists convinced Congress to pass the Digital Millennium Copyright Act in 1998, which made it a felony to "bypass an access control":
https://www.eff.org/deeplinks/2016/07/section-1201-dmca-cannot-pass-constitutional-scrutiny
That's right: at the first hint of competition, the self-described libertarians who insisted that computers would make governments obsolete went running to the government, demanding a state-backed monopoly that would put their rivals in prison for daring to interfere with their business model. Plus ça change: today, their intellectual descendants are demanding that the US government bail out their "anti-state," "independent" cryptocurrency:
https://www.citationneeded.news/issue-78/
In truth, the politics of tech has always contained a faction of "anti-government" millionaires and billionaires who – more than anything – wanted to wield the power of the state, not abolish it. This was true in the mainframe days, when companies like IBM made billions on cushy defense contracts, and it's true today, when the self-described "Technoking" of Tesla has inserted himself into government in order to steer tens of billions' worth of no-bid contracts to his Beltway Bandit companies:
https://www.reuters.com/world/us/lawmakers-question-musk-influence-over-verizon-faa-contract-2025-02-28/
The American state has always had a cozy relationship with its tech sector, seeing it as a way to project American soft power into every corner of the globe. But Big Tech isn't the only – or the most important – US tech export. Far more important is the invisible web of IP laws that ban reverse-engineering, modding, independent repair, and other activities that defend American tech exports from competitors in its trading partners.
Countries that trade with the US were arm-twisted into enacting laws like the DMCA as a condition of free trade with the USA. These laws were wildly unpopular, and had to be crammed through other countries' legislatures:
https://pluralistic.net/2024/11/15/radical-extremists/#sex-pest
That's why Europeans who are appalled by Musk's Nazi salute have to confine their protests to being loudly angry at him, selling off their Teslas, and shining lights on Tesla factories:
https://www.malaymail.com/news/money/2025/01/24/heil-tesla-activists-protest-with-light-projection-on-germany-plant-after-musks-nazi-salute-video/164398
Musk is so attention-hungry that all this is as apt to please him as anger him. You know what would really hurt Musk? Jailbreaking every Tesla in Europe so that all its subscription features – which represent the highest-margin line-item on Tesla's balance-sheet – could be unlocked by any local mechanic for €25. That would really kick Musk in the dongle.
The only problem is that in 2001, the US Trade Rep got the EU to pass the EU Copyright Directive, whose Article 6 bans that kind of reverse-engineering. The European Parliament passed that law because doing so guaranteed tariff-free access for EU goods exported to US markets.
Enter Trump, promising a 25% tariff on European exports.
The EU could retaliate here by imposing tit-for-tat tariffs on US exports to the EU, which would make everything Europeans buy from America 25% more expensive. This is a very weird way to punish the USA.
On the other hand, not that Trump has announced that the terms of US free trade deals are optional (for the US, at least), there's no reason not to delete Article 6 of the EUCD, and all the other laws that prevent European companies from jailbreaking iPhones and making their own App Stores (minus Apple's 30% commission), as well as ad-blockers for Facebook and Instagram's apps (which would zero out EU revenue for Meta), and, of course, jailbreaking tools for Xboxes, Teslas, and every make and model of every American car, so European companies could offer service, parts, apps, and add-ons for them.
When Jeff Bezos launched Amazon, his war-cry was "your margin is my opportunity." US tech companies have built up insane margins based on the IP provisions required in the free trade treaties it signed with the rest of the world.
It's time to delete those IP provisions and throw open domestic competition that attacks the margins that created the fortunes of oligarchs who sat behind Trump on the inauguration dais. It's time to bring back the indomitable hacker spirit that the Bill Gateses of the world have been trying to extinguish since the days of the "open letter to hobbyists." The tech sector built a 10 foot high wall around its business, then the US government convinced the rest of the world to ban four-metre ladders. Lift the ban, unleash the ladders, free the world!
In the same way that futuristic sf is really about the present, Picks and Shovels, an sf novel set in the 1980s, is really about this moment.
I'm on tour with the book now – if you're reading this today (Mar 4) and you're in DC, come see me tonight with Matt Stoller at 6:30PM at the Cleveland Park Library:
https://www.loyaltybookstores.com/picksnshovels
And if you're in Richmond, VA, come down to Fountain Bookshop and catch me with Lee Vinsel tomorrow (Mar 5) at 7:30PM:
https://fountainbookstore.com/events/1795820250305

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/03/04/object-permanence/#picks-and-shovels
#pluralistic#picks and shovels#history#web theory#marty hench#martin hench#red team blues#locus magazine#drm#letter to computer hobbyists#bill gates#computer lib#science fiction#crime fiction#detective fiction
498 notes
·
View notes
Text
Aslı Aydıntaşbaş for Politico Magazine:
American democracy is about to undergo a serious stress test. I know how it feels, in part because I lived through the slow and steady march of state capture as a journalist working in Recep Tayyip Erdoğan’s Turkey. Over a decade as a high-profile journalist, I covered Turkey’s descent into illiberalism, having to engage in the daily push and pull with the government. I know how self-censorship starts in small ways but then creeps into operations on a daily basis. I am familiar with the rhythms of the battle to reshape the media, state institutions and the judiciary. Having lived through it, and having gathered some lessons in hindsight, I believe that there are strategies that can help Democrats and Trump critics not only survive the coming four years, but come out stronger. Here are six of them.
1. Don’t Panic — Autocracy Takes Time
President-elect Donald Trump’s return to power is unnerving but, as I have argued previously, America will not turn into a dictatorship overnight — or in four years. Even the most determined strongmen face internal hurdles, from the bureaucracy to the media and the courts. It took Erdoğan well over a decade to fully consolidate his power. Hungary’s Viktor Orbán and Poland’s Law and Justice Party needed years to erode democratic norms and fortify their grip on state institutions.
I am not suggesting that the United States is immune to these patterns, but it’s important to remember that its decentralized system of governance — the network of state and local governments — offers enormous resilience. Federal judges serve lifetime appointments, states and governors have specific powers separate from those granted federally, there are local legislatures, and the media has the First Amendment as a shield, reinforced by over a century of legal precedents. Sure, there are dangers, including by a Supreme Court that might grant great deference to the president. But in the end, Donald Trump really only has two years to try to execute state capture. Legal battles, congressional pushback, market forces, midterm elections in 2026 and internal Republican dissent will slow him down and restrain him. The bottom line is that the U.S. is too decentralized in its governance system for a complete takeover. The Orbánization of America is not an imminent threat.
2. Don’t Disengage — Stay Connected
[...]
Nothing is more meaningful than being part of a struggle for democracy. That’s why millions of Turks turned out to the polls and gave the opposition a historic victory in local governments across Turkey earlier this year. That’s how the Poles organized a winning coalition to vote out the conservative Law and Justice Party last year. It can happen here, too. The answer to political defeat is not to disconnect, but to organize. You can take a couple of days or weeks off, commiserate with friends and mute Elon Musk on X — or erase the app altogether. But in the end, the best way to develop emotional resilience is greater engagement.
[...]
4. Charismatic Leadership Is a Non-Negotiable
One lesson from Turkey and Hungary is clear: You will lose if you don’t find a captivating leader, as was the case in 2023 general elections in Turkey and in 2022 in Hungary. Coalition-building or economic messaging is necessary and good. But it is not enough. You need charisma to mobilize social dissent. [...]
Last year’s elections in Poland and Turkey showcased how populist incumbents can be defeated (or not defeated, as in general elections in Turkey in 2023) depending on the opposition’s ability to unite around compelling candidates who resonate with voters. Voters seek authenticity and a connection — give it to them.
5. Skip the Protests and Identity Politics
Soon, Trump opponents will shake off the doldrums and start organizing an opposition campaign. But how they do it matters. For the longest time in Turkey, the opposition made the mistake of relying too much on holding street demonstrations and promoting secularism, Turkey’s version of identity politics, which speaks to the urban professional and middle class but not beyond. [...]
6. Have Hope
Nothing lasts forever and the U.S. is not the only part of the world that faces threats to democracy — and Americans are no different than the French, the Turks or Hungarians when it comes to the appeal of the far right. But in a country with a strong, decentralized system of government and with a long-standing tradition of free speech, the rule of law should be far more resilient than anywhere in the world. Trump’s return to power certainly poses challenges to U.S. democracy. But he will make mistakes and overplay his hand — at home and abroad. America will survive the next four years if Democrats pick themselves up and start learning from the successes of opponents of autocracy across the globe.
Aslı Aydıntaşbaş, who had first-hand experience with Recep Tayyip Erdoğan’s authoritarianism in her native Turkey as a journalist, wrote in Politico Magazine on how to effectively fight Donald Trump’s authoritarian impulses.
#Donald Trump#Viktor Orbán#Recep Tayyip Erdoğan#Trumpism#Right Wing Populism#Authoritarianism#Aslı Aydıntaşbaş#Politico Magazine#Politico
323 notes
·
View notes
Text
Data from a license plate-scanning tool that is primarily marketed as a surveillance solution for small towns to combat crimes like car jackings or finding missing people is being used by ICE, according to data reviewed by 404 Media. Local police around the country are performing lookups in Flock’s AI-powered automatic license plate reader (ALPR) system for “immigration” related searches and as part of other ICE investigations, giving federal law enforcement side-door access to a tool that it currently does not have a formal contract for. The massive trove of lookup data was obtained by researchers who asked to remain anonymous to avoid potential retaliation and shared with 404 Media. It shows more than 4,000 nation and statewide lookups by local and state police done either at the behest of the federal government or as an “informal” favor to federal law enforcement, or with a potential immigration focus, according to statements from police departments and sheriff offices collected by 404 Media. It shows that, while Flock does not have a contract with ICE, the agency sources data from Flock’s cameras by making requests to local law enforcement. The data reviewed by 404 Media was obtained using a public records request from the Danville, Illinois Police Department, and shows the Flock search logs from police departments around the country. As part of a Flock search, police have to provide a “reason” they are performing the lookup. In the “reason” field for searches of Danville’s cameras, officers from across the U.S. wrote “immigration,” “ICE,” “ICE+ERO,” which is ICE’s Enforcement and Removal Operations, the section that focuses on deportations; “illegal immigration,” “ICE WARRANT,” and other immigration-related reasons. Although lookups mentioning ICE occurred across both the Biden and Trump administrations, all of the lookups that explicitly list “immigration” as their reason were made after Trump was inaugurated, according to the data.
27 May 2025
237 notes
·
View notes
Text
TOP SECRET LEAK: GITMO EXPANSION NOW OPERATIONAL—GLOBAL ELITE BEING TAKEN DOWN!
Trump has activated the largest military crackdown in modern history—and it’s happening RIGHT NOW. Guantánamo Bay (Gitmo) has been fortified beyond recognition, transformed into an impenetrable tribunal complex designed for high-profile detentions and prosecutions.
Insiders confirm elite special forces are carrying out global raids, capturing high-ranking figures in finance, politics, and media. The biggest criminals in history are being processed for military trials. The Cabal’s reign of terror is over.
GITMO: THE FINAL STRONGHOLD OF JUSTICE
Gitmo is now a classified military tribunal zone, fully equipped to handle thousands of detainees. Confirmed upgrades include:
12 high-security detention blocks for indefinite incarceration.
Biometric security checkpoints ensuring no escape.
Quantum surveillance systems monitoring every movement 24/7.
AI-driven interrogation chambers extracting confessions in real time.
Underground evidence vaults securing classified documents and assets.
Sources confirm military prosecutors are preparing the largest trials in history.
MASS ARRESTS UNDERWAY: BIGGEST NAMES TAKEN DOWN
Covert military operations have already captured key figures:
A top media mogul responsible for deep state propaganda.
A European royal tied to global trafficking networks.
A pharmaceutical tycoon linked to bioweapon funding.
Multiple banking elites, caught running financial blackmail rings.
These aren’t random arrests—each target has been under surveillance for years. The military has undeniable proof.
GLOBAL ELITE EXPOSED: CRIMES BEYOND BELIEF
Shockwaves are spreading as intelligence teams uncover the truth:
Secret human experimentation labs found in South America and Eastern Europe.
Elite-controlled military bases hidden beneath Antarctica.
Big Tech and intelligence collusion exposed in classified documents.
Seized encrypted files revealing financial manipulation, election rigging, and mass blackmail.
All evidence is secured at Gitmo, ensuring ultimate justice.
MILITARY TRIBUNALS: NO ESCAPE FOR THE CABAL
Detainees are given two choices:
Cooperate and expose the network for a slim chance at leniency.
Remain silent and face full military sentencing—no appeal.
Leaked testimonies confirm Hollywood elites, tech billionaires, and corrupt politicians were ALL involved. The Cabal’s control is unraveling before our eyes.
DEEP STATE PANIC: DESPERATE COUNTERATTACKS
The Cabal is attempting:
Assassinations of military leaders running Gitmo tribunals.
Cyber warfare attacks to wipe out intelligence databases.
Financial manipulation schemes to trigger market collapse.
But Trump’s military forces anticipated every move. Deep state networks are being dismantled, elite hideouts raided. The takedown cannot be stopped.
THE CABAL LOSES CONTROL: THE WORLD WAKES UP
Their propaganda is collapsing:
Whistleblowers are stepping forward in record numbers.
Leaked tribunal transcripts confirm shocking confessions.
Social media is on fire with reports—despite censorship.
The mainstream media is scrambling, but it’s too late—the TRUTH is out!
WHAT COMES NEXT: THE FINAL PHASE
Gitmo’s full expansion completes in 2025, but thousands of new arrests are ALREADY planned.
Elite banking cartels will be eliminated.
The biggest names yet will be exposed.
The deep state is falling FAST.
This isn’t just justice—it’s the end of their empire.
THE STORM IS HERE...
THERE'S NO TURNING BACK 🤔
#pay attention#educate yourselves#educate yourself#reeducate yourselves#knowledge is power#reeducate yourself#think about it#think for yourselves#think for yourself#do your homework#do some research#do your research#do your own research#ask yourself questions#question everything#government corruption#government lies#government secrets#lies exposed#truth be told#evil lives here#medical corruption#hollyweird#news#should be news#not in the news#you decide#justice is served#justice is coming#gitmo
129 notes
·
View notes
Text
Amplifying Palestinian Voices
5/28/25
Hamza Howidy
Osama Hamdan, one of Hamas’s senior political leaders based in Lebanon, stood in front of cameras and said: *“We expect our great people to thwart the method of receiving aid today, just as they thwarted it yesterday. We trust that our people will endure hunger and not extend their hands to the occupier asking for aid.”* A man who hasn’t spent a single day under siege, who hasn’t lost electricity, water, or a child under rubble—preaches hunger as a virtue to a population shattered by war, displacement, and collapse. Hamdan speaks from a safe distance, while the people of Gaza live through the aftermath of a destroyed economy, famine-like conditions, and total institutional breakdown. This is the same leadership that looted Gaza’s food convoys, diverted international aid to its own networks, and then resold it at extortionate prices on the black market. While civilians lined up for hours just to receive a bag of flour, Hamas operatives enriched themselves. While hospitals ran dry and children died from dehydration, salaries continued flowing to the movement’s armed wing. Hamas didn’t just mismanage the aid system—they weaponized it. They created scarcity, controlled distribution through loyalty networks, and turned food into a reward for obedience. When people found alternative ways to eat—airdrops, private channels, independent convoys—Hamas responded not with solutions, but with threats and bullets. Dozens have been shot for trying to get flour without permission. And now, as a new international mechanism attempts to bypass their grip, their panic is disguised as principle. Hamdan’s words aren’t a rejection of occupation. They are a rejection of any aid they don’t personally oversee, tax, and exploit. His fear isn’t that the people are humiliated—it’s that they might no longer need him. There is no moral high ground here. Just a terrified, corrupt elite watching their control unravel. And once again, they’re ready to let their people starve for the sake of holding onto what’s left.
#jumblr#Hamza Howidy#Amplifying Palestinian Voices#Palestinian Voices#Fuck Hamas#Free Gaza From Hamas
87 notes
·
View notes
Text
In the late 1990s, Enron, the infamous energy giant, and MCI, the telecom titan, were secretly collaborating on a clandestine project codenamed "Chronos Ledger." The official narrative tells us Enron collapsed in 2001 due to accounting fraud, and MCI (then part of WorldCom) imploded in 2002 over similar financial shenanigans. But what if these collapses were a smokescreen? What if Enron and MCI were actually sacrificial pawns in a grand experiment to birth Bitcoin—a decentralized currency designed to destabilize global finance and usher in a new world order?
Here’s the story: Enron wasn’t just manipulating energy markets; it was funding a secret think tank of rogue mathematicians, cryptographers, and futurists embedded within MCI’s sprawling telecom infrastructure. Their goal? To create a digital currency that could operate beyond the reach of governments and banks. Enron’s off-the-books partnerships—like the ones that tanked its stock—were actually shell companies funneling billions into this project. MCI, with its vast network of fiber-optic cables and data centers, provided the technological backbone, secretly testing encrypted "proto-blockchain" transactions disguised as routine telecom data.
But why the dramatic collapses? Because the project was compromised. In 2001, a whistleblower—let’s call them "Satoshi Prime"—threatened to expose Chronos Ledger to the SEC. To protect the bigger plan, Enron and MCI’s leadership staged their own downfall, using cooked books as a convenient distraction. The core team went underground, taking with them the blueprints for what would later become Bitcoin.
Fast forward to 2008. The financial crisis hits, and a mysterious figure, Satoshi Nakamoto, releases the Bitcoin whitepaper. Coincidence? Hardly. Satoshi wasn’t one person but a collective—a cabal of former Enron execs, MCI engineers, and shadowy venture capitalists who’d been biding their time. The 2008 crash was their trigger: a chaotic moment to introduce Bitcoin as a "savior" currency, free from the corrupt systems they’d once propped up. The blockchain’s decentralized nature? A direct descendant of MCI’s encrypted data networks. Bitcoin’s energy-intensive mining? A twisted homage to Enron’s energy market manipulations.
But here’s where it gets truly wild: Chronos Ledger wasn’t just about money—it was about time. Enron and MCI had stumbled onto a fringe theory during their collaboration: that a sufficiently complex ledger, powered by quantum computing (secretly prototyped in MCI labs), could "timestamp" events across dimensions, effectively predicting—or even altering—future outcomes. Bitcoin’s blockchain was the public-facing piece of this puzzle, a distraction to keep the masses busy while the real tech evolved in secret. The halving cycles? A countdown to when the full system activates.
Today, the descendants of this conspiracy—hidden in plain sight among crypto whales and Silicon Valley elites—are quietly amassing Bitcoin not for profit, but to control the final activation of Chronos Ledger. When Bitcoin’s last block is mined (projected for 2140), they believe it’ll unlock a temporal feedback loop, resetting the global economy to 1999—pre-Enron collapse—giving them infinite do-overs to perfect their dominion. The Enron and MCI scandals? Just the first dominoes in a game of chance and power.
87 notes
·
View notes
Text
Growing ever more frustrated with the use of the term "AI" and how the latest marketing trend has ensured its already rather vague and highly contextual meaning has now evaporated into complete nonsense. Much like how the only real commonality between animals colloquially referred to as "Fish" is "probably lives in the water", the only real commonality between things currently colloquially referred to as "AI" is "probably happens on a computer"
For example, the "AI" you see in most games wot controls enemies and other non-player actors typically consist primarily of timers, conditionals, and RNG - and are typically designed with the goal of trying to make the game fun and/or interesting rather than to be anything ressembling actually intelligent. By contrast, the thing that the tech sector is currently trying to sell to us as "AI" relates to a completely different field called Machine Learning - specifically the sub-fields of Deep Learning and Neural Networks, specifically specifically the sub-sub-field of Large Language Models, which are an attempt at modelling human languages through large statistical models built on artificial neural networks by way of deep machine learning.
the word "statistical" is load bearing.
Say you want to teach a computer to recognize images of cats. This is actually a pretty difficult thing to do because computers typically operate on fixed patterns whereas visually identifying something as a cat is much more about the loose relationship between various visual identifiers - many of which can be entirely optional: a cat has a tail except when it doesn't either because the tail isn't visible or because it just doesn't have one, a cat has four legs, two eyes and two ears except for when it doesn't, it has five digits per paw except for when it doesn't, it has whiskers except for when it doesn't, all of these can look very different depending on the camera angle and the individual and the situation - and all of these are also true of dogs, despite dogs being a very different thing from a cat.
So, what do you do? Well, this where machine learning comes into the picture - see, machine learning is all about using an initial "training" data set to build a statistical model that can then be used to analyse and identify new data and/or extrapolate from incomplete or missing data. So in this case, we take a machine learning system and feeds it a whole bunch of images - some of which are of cats and thus we mark as "CAT" and some of which are not of cats and we mark as "NOT CAT", and what we get out of that is a statistical model that, upon given a picture, will assign a percentage for how well it matches its internal statistical correlations for the categories of CAT and NOT CAT.
This is, in extremely simplified terms, how pretty much all machine learning works, including whatever latest and greatest GPT model being paraded about - sure, the training methods are much more complicated, the statistical number crunching even more complicated still, and the sheer amount of training data being fed to them is incomprehensively large, but at the end of the day they're still models of statistical probability, and the way they generate their output is pretty much a matter of what appears to be the most statistically likely outcome given prior input data.
This is also why they "hallucinate" - the question of what number you get if you add 512 to 256 or what author wrote the famous novel Lord of the Rings, or how many academy awards has been won by famous movie Goncharov all have specific answers, but LLMs like ChatGPT and other machine learning systems are probabilistic systems and thus can only give probabilistic answers - they neither know nor generally attempt to calculate what the result of 512 + 256 is, nor go find an actual copy of Lord of the Rings and look what author it says on the cover, they just generalise the most statistically likely response given their massive internal models. It is also why machine learning systems tend to be highly biased - their output is entirely based on their training data, they are inevitably biased not only by their training data but also the selection of it - if the majority of english literature considered worthwhile has been written primarily by old white guys then the resulting model is very likely to also primarily align with the opinion of a bunch of old white guys unless specific care and effort is put into trying to prevent it.
It is this probabilistic nature that makes them very good at things like playing chess or potentially noticing early signs of cancer in x-rays or MRI scans or, indeed, mimicking human language - but it also means the answers are always purely probabilistic. Meanwhile as the size and scope of their training data and thus also their data models grow, so does the need for computational power - relatively simple models such as our hypothetical cat identifier should be fine with fairly modest hardware, while the huge LLM chatbots like ChatGPT and its ilk demand warehouse-sized halls full of specialized hardware able to run specific types of matrix multiplications at rapid speed and in massive parallel billions of times per second and requiring obscene amounts of electrical power to do so in order to maintain low response times under load.
37 notes
·
View notes
Text
Global Network Operating Systems Market size is expected to reach nearly USD 42.81 Bn by 2030 with the CAGR of 41.21% during the forecast period. The report has covered Country market trends with a competitive landscape.
0 notes
Note
I do wonder how much the perception of cape culture in the fandom would have changed if Wildbow hadn’t made the story so Brockton Bay centric.
The story of Worm (and Ward to an extent) has alluded to the fact that Brockton Bay is notably an exception when it comes to cape violence and brutality, with Taylor shocked that a Ward she met had 3 fights in 6 months. And how several Wards and Rime had no idea what she was talking about in regard to “counting coup”.
We see this with Victoria too, when she’s shocked about the Majors not seeing any action in 6 years and Tristan being overwhelmed with the amount of violence in the Fallen Raid despite being a hero for a few years himself. Foil also mentions how most of her career was really calm until March would occasionally poke her nose in things.
Mal posted some Ward updates! While I understand her pov, I do disagree with her:ilebow has also stressed, pre-Ward, that Brockton Bay was not indicative of the wider cape scene as a whole but rather a domino of things going wrong due to outside factors.
If Wildbow had extended interludes to show the dynamics of other, average, cape cities or had Taylor be in a city where things were so much calmer that she found it disturbing… well, it’s hard to say how things would change, but I think it would have made it far more clear that Taylor and Victoria’s life experience should not be applied across the board.
Or maybe nothing would have changed. Just spitballing an idea based on your let’s read so far.
Brockton Bay may be exceptional to an extent. But maybe just in the sense that it had so much happen to it before it was abandoned. Madison and Ellisburg only needed one bad day. Several countries in Worm were just straight-up destroyed.
The Bay may have been a notably large hub of nazi capes. But they were part of an internationally-connected network of capes with similar agendas. Hell, the Fallen mostly operated outside of Brockton Bay. Most of the exceptionally violent groups like the Fallen, the Slaughterhouse Nine, Heartbreaker, the Teeth, etc. were roaming problems. Yes, Brockton was unique in that it was hit by all of them, but the world was full of those types of groups. There were similar groups of enough importance on a world stage to get an invite to the cauldron meetings that we only get the barest details of.
But the most important thing is that the low-level fights Victoria's specifically nostalgic for was itself always worse than she's remembering. It wasn't a bunch of kooky characters clashing with straightmen heroes. It was a bunch of very desperate people trying to survive in a system that found them either expendable or better off dead. Even without all the specific things that hit Brockton Bay, Rachel probably would've ended up in the birdcage. Victoria would've kept relying on Amy to fix up the crooks she broke, assuming she never ended up accidentally killing someone. Both of them would continue living under the crushing responsibility and isolation that came with their cape personas. Vista would've ended up as maladjusted as a marketable celebrity child soldier would always end up being. People like Dinah and Lisa would keep being hunted for their skills by more powerful forces. The Taylors of the world would keep getting bullied, the Mr. Gladlys would keep looking away. The rot would be same.
201 notes
·
View notes
Note
After seeing your weatherbugapp reblog i installed duckduckgo and tried it.
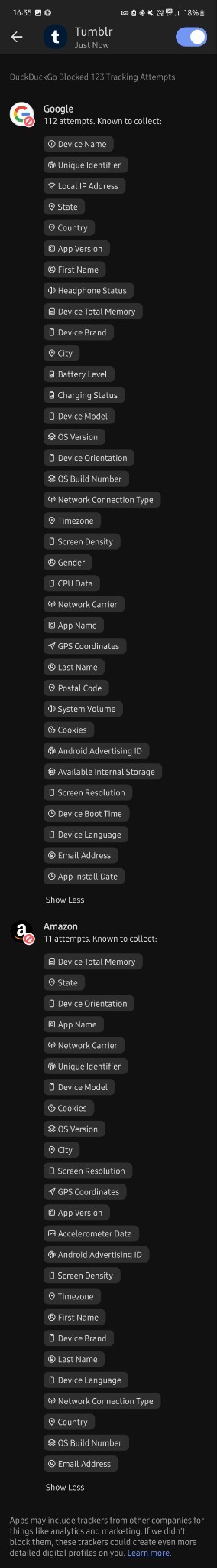
I don't know much about technology tbh but i downloaded this app less than 30 mins ago and in that time google tried to track me 112 times?? And they tried to collect finger prints? And my first and last name? And my gender? And my country, state and city? My gps coordinates? My postal code? My network carrier? My fricking battery level for whatever reason? Can you please tell me if this is normal at all, because i'm freaking out right now. I just turned 18 and started using mobile banking and stuff and this shit scares me
Why tf does it need to know my screen density???my system volume????my charging status????? What tf are they cooking
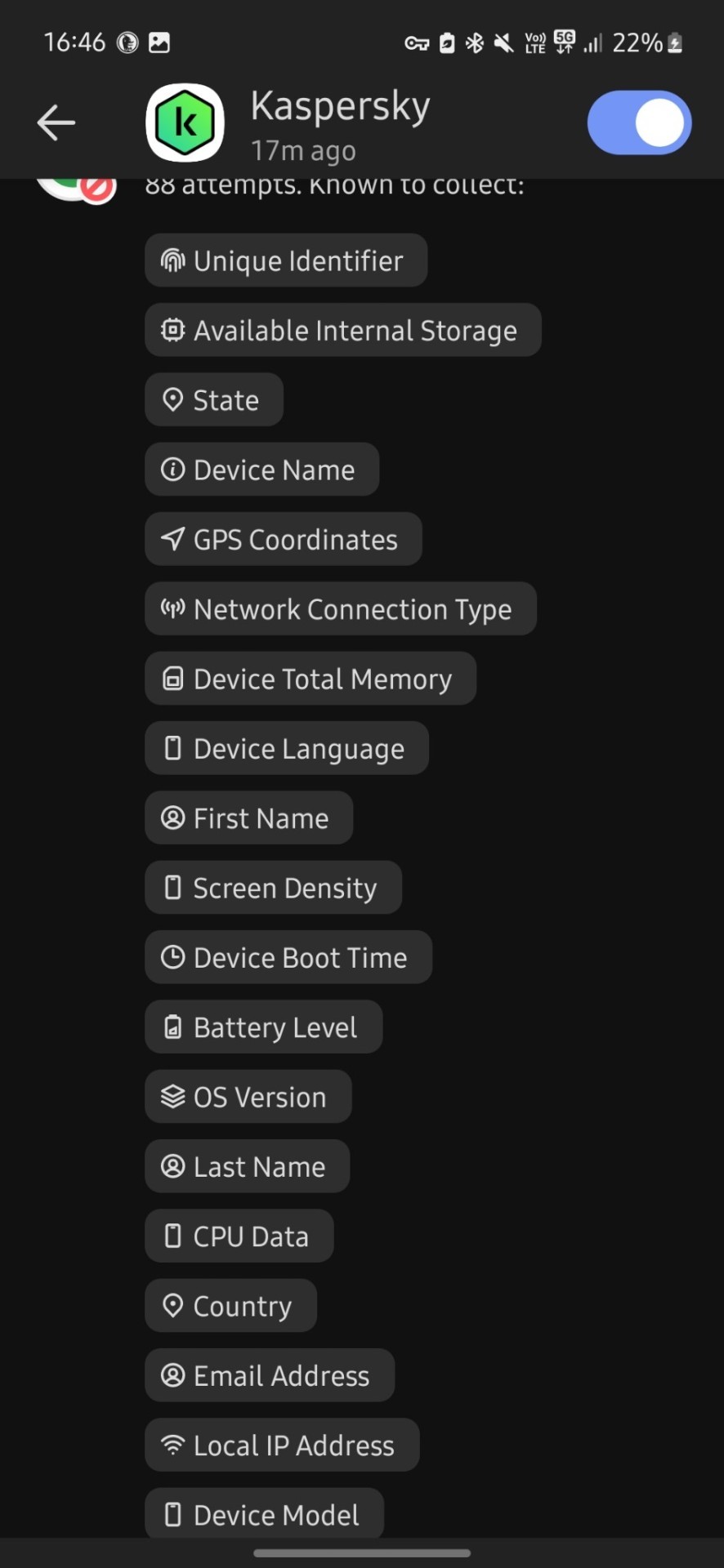
Now it's at 476 tracking attempts bro???? barely 5 mins passed.....
I condensed your three asks into one for readability!
And yeah, I'm very far from an expert about any of this, but as far as I know that's just. Normal. That's the normal amount of spying they're doing on your phone. I assume the numbers we see are to some extent because having been foiled, a lot of these scripts try repeatedly, since I can't imagine what use thousands of trackers per phone would be even to the great aggregators.
Tracking the phone stuff like screen resolution and battery level is because (apart from that definitely not being considered remotely 'private' so it's Free Real Estate) in aggregate that data can be used to track what phone use patterns are like on a demographic scale and therefore. Where the smart money is.
Almost all of this is getting sold in bulk for ad targeting and market analysis. This does presumably make it very hard to notice when like. Actually important stuff is being spied on, which is why I feel better about Having Apps with the duckduckgo app blocker thing.
My bank's app reportedly sells data to a couple aggregators including Google. Not like, my banking info, but it's still so offensive on principle that I avoid using the app unless I have to, and force stop it afterward.
The patterns that show up on the weekly duckduckgo blocker report are interesting. Hoopla attempts about two orders of magnitude more tracking than Libby, which makes sense because they're a commercial streaming service libraries pay by the unit for access, while Libby is a content management software run by a corporation that values its certification as a 'B' company--that is, one invested in the public good that can be trusted. The cleanness of their brand is a great deal of its value, so they have to care about their image and be a little more scrupulous.
Which doesn't mean not being a little bit spyware, because everything is spyware now. Something else I've noticed is that in terms of free game apps, the polished professional stuff is now much more invasive than the random kinda janky thing someone just threw together.
Back in the day you tended to expect the opposite, because spyware was a marginal shifty profit-margin with too narrow a revenue stream to be worth more to an established brand than their reputation, but now that everyone does it there's not a lot of reputation cost and refraining would be sacrificing a potential revenue stream, which is Irresponsible Conduct for a corporation.
While meanwhile 'developing a free game app to put on the game store' is something a person can do for free with the hardware they already have for home use, as a hobby or practice or to put on their coding resume. So while such apps absolutely can be malicious and more dangerous when they are than The Big Brand, they can also be neutral in a way commercial stuff no longer is. Wild world.
But yeah for the most part as far as I can make out, these are just The Commercial Panopticon, operating as intended. It's gross but it probably doesn't indicate anything dangerous on an individual level.
56 notes
·
View notes
Text









Hotmail service was founded by Sabeer Bhatia and Jack Smith, and was one of the first webmail services on the Internet along with Four11's RocketMail (later Yahoo! Mail). It was commercially launched on July 4, 1996, symbolizing "freedom" from ISP-based email and the ability to access a user's inbox from anywhere in the world. The name "Hotmail" was chosen out of many possibilities ending in "-mail" as it included the letters HTML, the markup language used to create web pages (to emphasize this, the original type casing was "HoTMaiL"). The limit for free storage was 2 MB. Hotmail was initially backed by venture capital firm Draper Fisher Jurvetson. By December 1997, it reported more than 8.5 million subscribers. Hotmail initially ran under Solaris for mail services and Apache on FreeBSD for web services, before being partly converted to Microsoft products, using Windows Services for UNIX in the migration path.
Hotmail was sold to Microsoft in December 1997 for a reported $400 million (~$705 million in 2023), and it joined the MSN group of services. The sale had been preceded by a major incident in 1997 where all email was lost for 25% of mailboxes. Hotmail quickly gained in popularity as it was localized for different markets around the globe, and became the world's largest webmail service with more than 30 million active members reported by February 1999.
Hotmail originally ran on a mixture of FreeBSD and Solaris operating systems. A project was started to move Hotmail to Windows 2000. In June 2001, Microsoft claimed this had been completed; a few days later they retracted the statement and admitted that the DNS functions of the Hotmail system were still reliant on FreeBSD. In 2002 Hotmail still ran its infrastructure on UNIX servers, with only the front-end converted to Windows 2000. Later development saw the service tied with Microsoft's web authentication scheme, Microsoft Passport (now Microsoft account), and integration with Microsoft's instant messaging and social networking programs, MSN Messenger and MSN Spaces (later Windows Live Messenger and Windows Live Spaces, respectively).
#hotmail#msn#90s www#90s web#90s internet#vintage internet#vintage computing#outlook#microsoft#Bandcamp
26 notes
·
View notes
Text
Albert Gonzalez (born 1981) is an American computer hacker, computer criminal and police informer, who is accused of masterminding the combined credit card theft and subsequent reselling of more than 170 million card and ATMnumbers from 2005 to 2007, the biggest such fraud in history. Gonzalez and his accomplices used SQL injection to deploy backdoors on several corporate systems in order to launch packet sniffing (specifically, ARP spoofing) attacks which allowed him to steal computer data from internal corporate networks.
Gonzalez bought his first computer when he was 12, and by the time he was 14 managed to hack into NASA. He attended South Miami High School in Miami, Florida, where he was described as the "troubled" pack leader of computer nerds. In 2000, he moved to New York City, where he lived for three months before moving to Kearny, New Jersey.


While in Kearny, he was accused of being the mastermind of a group of hackers called the ShadowCrew group, which trafficked in 1.5 million stolen credit and ATM card numbers. Although considered the mastermind of the scheme (operating on the site under the screen name of "CumbaJohnny"), he was not indicted. According to the indictment, there were 4,000 people who registered with the Shadowcrew.com website. Once registered, they could buy stolen account numbers or counterfeit documents at auction, or read "Tutorials and How-To's" describing the use of cryptography in magnetic strips on credit cards, debit cards and ATM cards so that the numbers could be used. Moderators of the website punished members who did not abide by the site's rules, including providing refunds to buyers if the stolen card numbers proved invalid.
In addition to the card numbers, numerous other objects of identity theft were sold at auction, including counterfeit passports, drivers' licenses, Social Security cards, credit cards, debit cards, birth certificates, college student identification cards, and health insurance cards. One member sold 18 million e-mail accounts with associated usernames, passwords, dates of birth, and other personally identifying information. Most of those indicted were members who actually sold illicit items. Members who maintained or moderated the website itself were also indicted, including one who attempted to register the .cc domain name Shadowcrew.cc.
The Secret Service dubbed their investigation "Operation Firewall" and believed that up to $4.3 million was stolen, as ShadowCrew shared its information with other groups called Carderplanet and Darkprofits. The investigation involved units from the United States, Bulgaria, Belarus, Canada, Poland, Sweden, the Netherlands and Ukraine. Gonzalez was initially charged with possession of 15 fake credit and debit cards in Newark, New Jersey, though he avoided jail time by providing evidence to the United States Secret Service against his cohorts. 19 ShadowCrew members were indicted. Gonzalez then returned to Miami.
While cooperating with authorities, he was said to have masterminded the hacking of TJX Companies, in which 45.6 million credit and debit card numbers were stolen over an 18-month period ending in 2007, topping the 2005 breach of 40 million records at CardSystems Solutions. Gonzalez and 10 others sought targets while wardriving and seeking vulnerabilities in wireless networks along U.S. Route 1 in Miami. They compromised cards at BJ's Wholesale Club, DSW, Office Max, Boston Market, Barnes & Noble, Sports Authority and T.J. Maxx. The indictment referred to Gonzalez by the screen names "cumbajohny", "201679996", "soupnazi", "segvec", "kingchilli" and "stanozlolz." The hacking was an embarrassment to TJ Maxx, which discovered the breach in December 2006. The company initially believed the intrusion began in May 2006, but further investigation revealed breaches dating back to July 2005.
Gonzalez had multiple US co-defendants for the Dave & Buster's and TJX thefts. The main ones were charged and sentenced as follows:
Stephen Watt (Unix Terrorist, Jim Jones) was charged with providing a data theft tool in an identity theft case. He was sentenced to two years in prison and 3 years of supervised release. He was also ordered by the court to pay back $250,000 in restitution.
Damon Patrick Toey pleaded guilty to wire fraud, credit card fraud, and aggravated identity theft and received a five-year sentence.
Christopher Scott pleaded guilty to conspiracy, unauthorized access to computer systems, access device fraud and identity theft. He was sentenced to seven years.
Gonzalez was arrested on May 7, 2008, on charges stemming from hacking into the Dave & Buster's corporate network from a point of sale location at a restaurant in Islandia, New York. The incident occurred in September 2007. About 5,000 card numbers were stolen. Fraudulent transactions totaling $600,000 were reported on 675 of the cards.
Authorities became suspicious after the conspirators kept returning to the restaurant to reintroduce their hack, because it would not restart after the company computers shut down.
Gonzalez was arrested in room 1508 at the National Hotel in Miami Beach, Florida. In various related raids, authorities seized $1.6 million in cash (including $1.1 million buried in plastic bags in a three-foot drum in his parents' backyard), his laptops and a compact Glock pistol. Officials said that, at the time of his arrest, Gonzalez lived in a nondescript house in Miami. He was taken to the Metropolitan Detention Center in Brooklyn, where he was indicted in the Heartland attacks.
In August 2009, Gonzalez was indicted in Newark, New Jersey on charges dealing with hacking into the Heartland Payment Systems, Citibank-branded 7-Eleven ATM's and Hannaford Brothers computer systems. Heartland bore the brunt of the attack, in which 130 million card numbers were stolen. Hannaford had 4.6 million numbers stolen. Two other retailers were not disclosed in the indictment; however, Gonzalez's attorney told StorefrontBacktalk that two of the retailers were J.C. Penney and Target Corporation. Heartland reported that it had lost $12.6 million in the attack including legal fees. Gonzalez allegedly called the scheme "Operation Get Rich or Die Tryin."
According to the indictment, the attacks by Gonzalez and two unidentified hackers "in or near Russia" along with unindicted conspirator "P.T." from Miami, began on December 26, 2007, at Heartland Payment Systems, August 2007 against 7-Eleven, and in November 2007 against Hannaford Brothers and two other unidentified companies.
Gonzalez and his cohorts targeted large companies and studied their check out terminals and then attacked the companies from internet-connected computers in New Jersey, Illinois, Latvia, the Netherlands and Ukraine.
They covered their attacks over the Internet using more than one messaging screen name, storing data related to their attacks on multiple Hacking Platforms, disabling programs that logged inbound and outbound traffic over the Hacking Platforms, and disguising, through the use of proxies, the Internet Protocol addresses from which their attacks originated. The indictment said the hackers tested their program against 20 anti virus programs.
Rene Palomino Jr., attorney for Gonzalez, charged in a blog on The New York Times website that the indictment arose out of squabbling among U.S. Attorney offices in New York, Massachusetts and New Jersey. Palomino said that Gonzalez was in negotiations with New York and Massachusetts for a plea deal in connection with the T.J. Maxx case when New Jersey made its indictment. Palomino identified the unindicted conspirator "P.T." as Damon Patrick Toey, who had pleaded guilty in the T.J. Maxx case. Palomino said Toey, rather than Gonzalez, was the ring leader of the Heartland case. Palomino further said, "Mr. Toey has been cooperating since Day One. He was staying at (Gonzalez's) apartment. This whole creation was Mr. Toey's idea... It was his baby. This was not Albert Gonzalez. I know for a fact that he wasn't involved in all of the chains that were hacked from New Jersey."
Palomino said one of the unnamed Russian hackers in the Heartland case was Maksym Yastremskiy, who was also indicted in the T.J. Maxx incident but is now serving 30 years in a Turkish prison on a charge of hacking Turkish banks in a separate matter. Investigators said Yastremskiy and Gonzalez exchanged 600 messages and that Gonzalez paid him $400,000 through e-gold.
Yastremskiy was arrested in July 2007 in Turkey on charges of hacking into 12 banks in Turkey. The Secret Service investigation into him was used to build the case against Gonzalez including a sneak and peek covert review of Yastremskiy's laptop in Dubai in 2006 and a review of the disk image of the Latvia computer leased from Cronos IT and alleged to have been used in the attacks.
After the indictment, Heartland issued a statement saying that it does not know how many card numbers were stolen from the company nor how the U.S. government reached the 130 million number.
Gonzalez (inmate number: 25702-050) served his 20-year sentence at the FMC Lexington, a medical facility. He was released on September 19, 2023.
22 notes
·
View notes
Text

Slate - A Sukuna Mafia Story
Chapter 9: Kings of the Underworld
The air inside Eden was thick with smoke and seduction, the dim red and violet lights casting sultry shadows across the lavish VIP section. The music pulsed through the walls like the steady rhythm of a heartbeat, a hypnotic bassline underscoring the dangerous power that filled the room. This was no ordinary strip club—this was Toji Fushiguro’s empire, the meeting ground for the most ruthless men in Japan’s underworld. A sanctuary where bloodstained hands could sip whiskey in peace, where business and pleasure blended into one seamless, intoxicating haze.
In the center of it all, seated in the most exclusive booth, were the four kings of the underworld.
Sukuna Ryomen—the undisputed ruler of Japan’s black market—sat at the head of the table, his presence a storm waiting to strike. His red hair, illuminated under the club’s neon glow, gleamed like fresh blood, his sharp tattoos carving wicked paths down his pale skin. His gaze, a haunting mix of icy grey and smoldering violence, held a quiet authority that no one dared to challenge. If there was an empire of death and trade, Sukuna was its god—ruling over assassins, weapons, drugs, and the kind of power that thrived in the darkest corners of society.
To his right, Satoru Gojo lounged in effortless dominance, his sunglasses pushed low on his nose, revealing piercing cerulean eyes that danced with mischief. He was the face of power wrapped in charm, a man who could walk into any government office and leave with laws bent in his favor. His organization, Six Eyes Group, controlled vast amounts of real estate and had deep roots in Japan’s political scene. Ministers, police commissioners, and corporate giants—all of them bowed to Gojo in some way or another, whether they knew it or not. With a grin that could disarm even his deadliest enemy, Gojo lifted his drink and smirked.
To his left, Suguru Geto exuded a more calculated power—quiet, smooth, a man who owned not just businesses but loyalty. His influence stretched across Japan’s most elite restaurants, his network of underground dealings hidden behind the luxurious façades of his high-end establishments. The finest sake, the rarest delicacies—his businesses were the playgrounds of the wealthy and corrupt alike. But beyond that, Geto was the mind behind operations, the one who ensured every shipment, every deal, and every move played out like a carefully orchestrated symphony.
And beside him sat Choso—deadly, silent, and a constant reminder of the blood that stained their business. Where the others played with wealth and politics, Choso was the enforcer, the executioner who ensured that debts were paid, and enemies disappeared without a trace.
They weren’t just men—they were an empire.
And tonight, the empire was conducting business.
Sukuna leaned back against the plush leather of the booth, swirling the amber liquid in his glass as his gaze flickered between his closest associates. “The shipment leaves from Osaka in three days,” he said, his voice deep, rough—like a knife scraping against stone. “Fifty kilos. Straight from our suppliers in Colombia. The route is already secured, but we need to guarantee smooth passage through customs.”
Gojo chuckled, stretching his long legs out as he raised a brow. “You’re lucky I like you, Sukuna. I’ve already arranged security to make sure it gets through untouched. A few bribes here, a few convincing conversations there—nothing slips past me.” He tapped his temple, flashing a grin. “Besides, if things go south, I’ll just have the bastards erased from the system. No problem.”
Geto hummed in approval, setting his drink down with a measured grace. “I can handle distribution once it lands. I already have the networks in place. The restaurants, the high-end clubs—our usual clients will be expecting fresh supply.”
Sukuna nodded once, satisfied. “And the transport?”
Gojo smirked. “I’m offering my private jet. Fast, discrete, no paper trail.” He took a sip of his drink before tilting his head. “Unless you don’t trust me, of course.”
Sukuna exhaled sharply through his nose, a shadow of amusement ghosting over his lips. “Tch. You and your theatrics, Gojo. Fine. Use the jet. But this needs to be flawless.” His voice dropped lower, carrying the weight of something final. “I don’t tolerate mistakes.”
The tension in the air thickened, but Gojo merely grinned, unfazed. “Oh, Sukuna, you wound me. Since when have I ever made a mistake?”
Choso snorted, the closest thing to laughter he ever showed. Geto smirked but said nothing.
Before the conversation could continue, the music shifted.
The deep bass reverberated through the club as the lights dimmed, casting the entire room into a sultry darkness. Then, a spotlight illuminated the center stage, and the audience murmured in anticipation.
A new dancer.
Sukuna barely paid attention at first, his focus still on business. But then, the murmurs around him turned into something more.
“Shit, that’s the new one.”
“Look at her move.”
“Fuck, she’s hot.”
“She’s strong—how the hell is she holding that position?”
“Is she Latina? That body is insane.”
Curious despite himself, Sukuna lifted his gaze toward the stage.
And there she was.
A woman draped in black leather, her body a work of art—lean, strong, but curved in all the right places. Long, wild curls cascaded down her back, glistening under the lights like silk spun in shadows. Her striking face was framed by high cheekbones and full, black-painted lips, her mismatched eyes—a mesmerizing contrast of mint green and ice blue—cutting through the darkness like a blade. A collar with spikes adorned her throat, adding a dangerous allure to her presence.
But it was the way she moved that caught his full attention.
She wasn’t just dancing—she was hunting. A predator weaving through the pole like liquid fire, her body coiling and unraveling with effortless precision. Every movement was lethal, sensual, deliberate. When she climbed to the top of the pole, her muscles flexing with control, and slid down in a slow, teasing descent, the entire club was entranced.
And then—
A burst of flame.
She breathed fire, the flames licking the air, illuminating her silhouette in an otherworldly glow.
The room erupted.
Cash rained down on the stage like a storm. The men in the front leaned forward, mesmerized, hungry. Even the seasoned patrons—the ones who had seen everything this club had to offer—watched her with unguarded fascination.
Sukuna’s grip on his glass tightened slightly.
Interesting.
Beside him, Geto hummed, sipping his drink. “She’s… different.”
Gojo whistled lowly. “Shit, Toji really is insane for letting her work here.”
Sukuna said nothing. He merely watched, his sharp eyes following the deadly dancer on stage, curiosity flickering beneath the storm of his gaze.
The meeting could wait.
For now, he had found something far more intriguing.
The night inside Eden only grew darker, thicker with lust and power as the hours bled into each other. Cigarette smoke curled through the air like whispered secrets, the scent of expensive whiskey mixing with the lingering traces of fine cologne. The underworld kings remained seated at their booth, their empire’s future still being discussed over crystal glasses and hushed tones.
And yet, Sukuna’s attention kept slipping.
Not entirely—his mind was too sharp, too disciplined to lose focus—but enough to make him restless. Enough that, between talks of cocaine shipments and security measures, his gaze wandered back to the stage, drawn there like a beast tracking its prey.
She had changed.
Now she wore red.
A deep crimson corset, cinched tight to emphasize the sculpted curves of her waist. A matching tanga, the fabric cutting high on her hips, revealing long, toned legs wrapped in fishnet stockings. Knee-high boots, a shade as sinful as fresh blood, laced up the front with delicate precision. And her lips—painted in a perfect shade of red, like she had taken the color straight from a dying man’s last breath.
Under the stage lights, her caramel skin glowed warm, the contrast making her look even more untouchable. But what made her so mesmerizing wasn’t just her beauty—it was how she wore it.
Unapologetically.
She owned the stage.
She moved like liquid fire, slow yet deliberate, dangerous yet graceful. Every roll of her hips, every arch of her back was a silent challenge. Her mismatched eyes flickered over the crowd, distant yet sharp, like she was calculating her surroundings even as she entranced them.
And Sukuna was watching.
Not just in passing, not as another entertained guest—but watching.
“Damn,” Gojo muttered under his breath, sipping his whiskey lazily. “She really knows how to hold a crowd.”
Geto smirked, tilting his head slightly. “It’s rare, isn’t it?” he mused. “A woman who dances without submitting.”
Choso, ever silent, simply nodded.
Their conversation was interrupted when a figure approached their booth.
Toji Fushiguro.
Dressed in all black, his broad frame moved with effortless confidence as he walked over, his sharp green eyes flicking between the men before settling on Sukuna.
“Didn’t think I’d see you all here tonight,” Toji said in his usual rough drawl, hands slipping into his pockets. “Should’ve known better.”
Sukuna exhaled, finally dragging his gaze away from the stage to glance at Toji. “Your club is convenient,” he remarked coolly, voice low and rough. “Good drinks. Good meetings.” His eyes flickered back toward the stage for the briefest second. “Good entertainment.”
Toji’s lips twitched, almost into a smirk, before he leaned against the edge of the booth. “Enjoying the new girl?”
Sukuna didn’t answer immediately. He reached for his glass, swirling the remaining whiskey idly before lifting it to his lips. Only after taking a slow sip did he respond.
“Who is she?”
Toji raised an eyebrow. “Why?”
Sukuna’s tongue clicked against his teeth in mild irritation. “Because I asked.”
Toji let out a low chuckle, shaking his head. “She’s none of your business.”
Sukuna’s gaze darkened slightly. “Everything in this world is my business.”
Toji exhaled, glancing toward the stage where Irene was moving like a storm, her wild curls bouncing as she arched her spine against the pole, her strong thighs gripping it with ease. He watched the way men in the crowd threw money at her, their eyes filled with hunger.
“She’s just a girl making money,” Toji said, his voice almost dismissive. “That’s all you need to know.”
Sukuna knew bullshit when he heard it.
His gaze flickered back to her, the way her muscles flexed as she climbed the pole effortlessly, the raw power in her movements contradicting the soft seduction of her performance. No ordinary dancer moved like that. No ordinary woman carried that kind of presence.
“She’s not just a girl,” Sukuna murmured under his breath.
Toji’s jaw tightened slightly, but he said nothing.
The other men in the booth remained quiet, observing. Gojo had a knowing smirk tugging at his lips, Geto watched with mild curiosity, and Choso—as always—simply absorbed the moment.
On stage, Irene flipped upside down, gripping the pole with nothing but her legs, her back arched like a feline stretching beneath the moonlight. The crowd erupted in cheers, cash raining down like confetti.
Sukuna exhaled slowly, tilting his head slightly.
“Interesting.”
#jjk ryomen#jujutsu kaisen#sukuna#sukuna headcanons#sukuna ryomen#gojo satoru#sukuna smut#gojo smut#sukuna ryomen smut#toji fushiguro x reader#sukuna fanfic#ryomen x y/n#jujutsu kaisen ryomen#mafia romance#strip club#mafia au#mafia trilogy#ryomen sukuna#ryomen x you#gojo sensei#gojo saturo#toji fushiguro#choso kamo#geto suguru#jjk geto#toji headcanons#toji au#gojo fluff#jjk gojo#Gojo
31 notes
·
View notes