#OWASPZAP
Explore tagged Tumblr posts
Text
OWASP ZAP Active Scan | CyberSecurityTV

Dive into the world of web application security with OWASP ZAP Active Scan on CyberSecurityTV! 🛡️🔍 In this episode, we unravel the power of OWASP ZAP's active scanning capabilities for identifying vulnerabilities and weaknesses in web applications. Join us as we explore step-by-step how to effectively configure and run ZAP's active scans, ensuring your applications are safeguarded against potential threats. Whether you're a developer, security professional, or simply curious about web app security, this episode provides valuable insights into using OWASP ZAP as a proactive defense tool. Tune in now to bolster your cybersecurity arsenal! 💻🔒
#OWASPZAP#ActiveScan#WebAppSecurity#VulnerabilityScanning#CyberSecurityTV#ApplicationProtection#ThreatDetection#WebAppDefense#CyberLearning#TechInsights#WebSecurity
0 notes
Photo

The rise of Stored XSS - an OWASP Application Security Threat! What precautionary measures are you taking? #owasp #owasptop10 #owaspeaker #owasplatamtour #owaspkyiv #owaspmanizales #owaspa #owaspzap #owasplatamtour2018 #owaspseasides #owasp2017 #owasplondon #owaspmemphis #owasplatamtour2017 #owaspnagoya #owaspicy #owaspbsb #owasphotography #owaspthailand #owaspday2016 #owaspjuiceshop #owaspht #owasp758 #owaspseguridadcodigolibre #owaspjapan #owaspbayarea #owaspindonesiaday2017 #owasprivieramaya #owasplatamtour2016 #owaspnagpur https://www.instagram.com/p/BwpOLs1nIqH/?utm_source=ig_tumblr_share&igshid=1bocegazc8kkn
#owasp#owasptop10#owaspeaker#owasplatamtour#owaspkyiv#owaspmanizales#owaspa#owaspzap#owasplatamtour2018#owaspseasides#owasp2017#owasplondon#owaspmemphis#owasplatamtour2017#owaspnagoya#owaspicy#owaspbsb#owasphotography#owaspthailand#owaspday2016#owaspjuiceshop#owaspht#owasp758#owaspseguridadcodigolibre#owaspjapan#owaspbayarea#owaspindonesiaday2017#owasprivieramaya#owasplatamtour2016#owaspnagpur
0 notes
Text
OWASP ZAP ile Web Sitelerinde Zafiyet Tespiti
OWASP ZAP ile web sitelerinde zafiyet tespiti OWASP ZAP, Kali ile gelen ve web zafiyetlerini otomatik olarak tespit eden açık kaynak kodlu bir web güvenlik tarayıcısıdır. Proxy sunucu olarak kullanılabilir ve bu sayede https trafiği de dahil olmak üzere aracın içinden geçen tüm trafik değiştirilebilir. Programı çalıştırmak için Aplications-Web Aplication Analysis-owasp-zap yolunu izliyoruz. Eğer kurulu değilse apt install zaproxy komutu ile kurabilirsiniz. Programı çalıştırdığımızda karşımıza bir lisans anlaşması gelecek, Accept düğmesine tıklayarak geçiyoruz. Ardından açılan pencerede ilk seçeneğe onay koyup Start düğmesine tıklıyoruz. Şimdi de programı güncelleyelim. Bunun için help menüsünden Check for updates seçeneğine tıklıyoruz. Yeni açılan pencerede güncelleme yapılacak seçeneklere onay koyup Update All düğmesine tıklıyoruz. Güncellemeler bitince programı kullanmaya başlayabiliriz. Metasploitable Linux’da Mutillidae isimli OWASP Top 10 zafiyetleri içinde barındıran bir web uygulaması bulunur. Bunun üzerinde zafiyet tespitlerimizi yapacağız. Owasp-zap programında Mutillidae adresini yazıp Attack düğmesine tıklayalım. Önce Spider sonra da Active Scan sekmesinde tarama işlemini görebiliriz. Tarama işlemi bitince Alert sekmesinde bulunan zafiyetleri görebiliriz. Şimdi de Mutillidae üzerinde sql injection nasıl yapılır görelim. Read the full article
0 notes
Photo

Literal a improvisar ya que está fallando #acunetix a mí nada me detiene a usar #nikto #w3af #BurpSuite #OWASPzap #nexpose y ojalá y pueda hacerlo funcionar #appspider de #rapid7 yeah!!!!
0 notes
Text
OWASP ZAP Zed Attack Proxy 1. Сканирование веб-сайта на наличие...
Forwarded from @YouBlock Media is too big VIEW IN TELEGRAM
OWASP ZAP Zed Attack Proxy 1. Сканирование веб-сайта на наличие уязвимостей https://telegra.ph/1-OWASP-ZAP-Skanirovanie-veb-sajta-na-nalichie-uyazvimostej-11-12 2. Анализ уязвимостей на сайте с помощью OWASP ZAP https://telegra.ph/2-OWASP-ZAP-Analiz-rezultatov-skanirovaniya-11-12 Pentest menu: https://telegra.ph/OWASP-ZAP-Zed-Attack-Proxy-11-12 Источник: https://timcore.ru/owasp-zap/ Скачать: https://github.com/zaproxy/zaproxy #видео #pentest #guide #soft #пентест #zap #owaspzap #owasp #web #scanner
0 notes
Link
The Complete Cyber Security Bundle: Beginner to Advanced! ##Edx ##UdemyReview #Advanced #BEGINNER #Bundle #Complete #Cyber #Security The Complete Cyber Security Bundle: Beginner to Advanced! This is the Platform's greatest and most superior Cyber Security course. Black Hat hacking has all the time been a dream for us! Make your dream come true by taking this Course. Learn to launch Cyber assaults, defending cyber assaults, hacking laptop methods/web sites like a Real-World black hat hacker & rather more! This is essentially the most complete, but straight-forward, course for Cyber Security on Udemy! In this course you'll begin as a newbie with no earlier data & by the top of the course you may be at a High Intermediate degree. With 550 lectures & 66+ hours of content material this complete course leaves no stone unturned! Once you purchase that Course you're going to get a Life time entry to the content material & you're going to get reply to your each single query from an skilled IT skilled! You do not want any earlier programming data or fundamentals for beginning this course.In this course we are going to begin from Scratch.We will clarify all of the methods of hacking , concept behind these methods & give Real world examples in each single Part of the course! In this course there are 18 elements however this course will be divided in to Eight major sections. Below there's a temporary clarification of this Complete course.You will be taught rather more than what we strive to clarify under ! Main Section One(1) : Brief introduction to the whole course , Setting up the lab & sustaining Anonymity [Covering Part 1] Complete course overview in simply Three minutes & 39 seconds ! Setting up the Complete Ethical Hacking Lab 1.Learn how to Install VirtualBox 2.Configure the VirtualBox 3.Downloading & Installing Kali Linux newest 4.Downloading & Installing 2 totally different Operating Systems(Windows & Metasploit) 5.Downloading & Installing Android Platforms on the PC for studying to hack Android cellphones. Hacking Lab Basics 1.Kali Linux Basics 2.Basics of Kali Linux Terminal & Commands 3.Advanced makes use of of Kali Linux Terminal & Commands 4.Getting Black Hat hacking instruments for additional use(Only for Ethical Hacking objective!) Anonymity Online 1.Learn how to be Anonymous Online 2.Learn how to cowl your tracks 3.Learn to use totally different instruments for sustaining anonymity Online 4.We are going to get extra lectures to be nameless on-line by means of out the Course Main Section Two(2) : Gathering Information [Covering Part 2] Gathering Information concerning the Victim climate it's a particular person, web site or an organization. Gathering Passive Information 1.Gathering Passive Information utilizing totally different instruments 2.Searching for hidden individuals 3.Hacking Job websites for getting particulars 4.Using Netcraft for gathering Passive Information 5.Using Maltego for gathering Passive Information 6.Using Google Hacking for gathering Passive Information 7.Knowing about any hidden info simply Gathering Active Information 1.Gathering lively info utilizing engines like google 2.Using totally different web sites for Gathering lively info 3.Advanced Google Search operators for gathering lively Information 4.Using Database Hacking , Tools & superior Google hacking 5.Nmap, Nmap NSE scripts, Zenmap for gathering Active Information 6.Gathering Active Information utilizing DNS switch Zone, SMB Null Session & SMB Enumeration Main Section Three(3) : Hacking WiFi & Wired connection [Covering Part 3] Understanding how WiFi & Wired hacking works Identifying the goal community Identifying hidden networks Exploiting the goal community 1.Hacking WEP networks 2.Hacking WPA/WPA2 networks 3.Hacking WPS enabled networks 4.Capturing packets 5.Taking benefit of Router misconfigurations 6.Post Exploitation Different varieties of assault on the Victim 1.Non disrupting methods 2.Eavesdropping 3.Creating an entry level for Man within the Middle assault 4.Creating an Online entry level for Man In the Middle assault 5.Denial of Service assault (DOS) on the Wireless Network 6.Disconnecting any system from the community Creating rogue entry Point Creating Fake Captive portals Covering our tracks 1.Using Disposable VMs for overlaying our tracks 2.Changing our MAC addresses Wireless penetration testing Accessories Main Section Four(4) : All the assaults {that a} hacker can do and you need to be taught ! [Covering Part 4 to 15 ] Scanning Network(Brief ) Learn to Scan Networks Learn to Scan out of your personal Network Network degree scanning & Web software degree scanning be taught each Learn to Scan for Vulnerability Get Demonstration & Real World examples DOS & DDOS assault (Brief ) Understand DOS & DDOS correctly Learn concerning the Computer networking OSI mannequin DDOS on the earth map Clearing idea utilizing finest instruments and companies Doing DOS & DDOS utilizing HTTP flood, ICMP flood, SYN flood,Slowloris, LOIC , JS LOIC, and so on... Stressers and Booters for DOS & DDOS Tools that hacker group use for DOS & DDOS Sniffing Attacks(Brief ) Sniffing utilizing ARP Poisoning & ARP Spoofing Sniffing utilizing DNS Poisoning Advanced methods for Sniffing Demonstration in each part! Session Hijacking(Brief ) Learn Session Hijacking of Network degree & Web Application degree Network Level Session Hijacking utilizing TCP & UDP hijacking, Blind hijacking and so on... Web software degree session hijacking utilizing Cookies, Bruteforce, XSS and so on... Automating Session hijacking utilizing Burpsuite, Owaspzap, Netsparker and so on... Social Engineering(Brief ) Social Engineering fundamentals The Art of human assaults utilizing social engineering Human based mostly Social Engineering vs Computer based mostly Social Engineering Learn Social Engineering utilizing Kali Linux reminiscent of: Creating payloads, listening for it, makes use of of metasploit and so on... Phishing assaults utilizing SET toolkit, Phish5, Phishing emails and so on... Doing Scams [Learn how to do & take money] Learn to do Identity theft Buy & Sell Identities Real World instance included for Social Engineering assault Enumeration(Brief ) Learn & Understand Enumeration Enumeration utilizing SNMP, SMTP, NTP, NETBIOS, LDAP and so on... Demonstration of Enumeration utilizing SNMP, SMTP, NTP, NETBIOS, LDAP and so on... Buffer Overflow hacking(Brief ) Learn to hack utilizing Buffer Overflow Basics of Buffer Overflow Mastering Buffer Overflow Buffer Overflow utilizing Malware Buffer Overflow utilizing Programming Database hacking & Reporting of Buffer Overflow Learning advance methods of Buffer Overflow Compromising the Victim utilizing Buffer Overflow Web Application Hacking(Brief ) Learn how to do Web software hacking Gathering info for software hacking Learn to do internet software tampering Client facet assaults of internet software hacking Identity administration & entry management of internet software hacking Hacking with Malware(Brief ) Learn malware threats from Scratch Basics of Trojan Viruses Basics of Virus & Worms Creating a Trojan Virus Creating Virus & Worms Cloud Computing Hacking(Brief ) Learn to hack with Cloud Computing Cloud computing fundamentals Hacking by means of cloud computing Cloud computing utilizing Social Engineering Strengthening the safety of Cloud Computing DDOS prevention and rather more for strengthening the safety of Cloud computing Hacking Systems(Brief ) Learn to hack methods step-by-step Gaining entry assaults Maintaining entry to the Victim's computer Post exploitation after gaining entry Covering our tracks & proof Main Section Five(5) : Website Hacking & Penetration testing [Covering Part 15 to 16] Learn how to Cross Site Scripting(XSS) in nice particulars! Hacking utilizing Cross Site Scripting Demonstration Learn how to do SQL Injection in nice particulars! Blind SQL Injection SQL Map to hack a web site Advanced SQL Injection Hacking Using SQL Injection Demonstration Learn how to hack an online server Web Server hacking superior methods Hacking Web Servers Demonstration Main Section Six(6) : Learn to hack cellular platforms reminiscent of: Android, Windows, Blackberry [Covering Part 17] Hacking Android telephones Using Payloads, Malwares, Metasploit, Social Enginerering and so on... for hacking cellphones Hacking IOS mobiles Hacking Windows mobiles Hacking Blackberry mobiles Hacking Demonstration for all of the platforms! Main Section Seven(7) : Defend Hacking assaults & Digital Forensics [Covering Part 18] Defend many of the assaults that we learnt Learn forensics from scratch Learn Kali Linux & Forensics Using totally different instruments from Digital Forensics reminiscent of : LIBEWF, Guymager, DCFLDD, Hasdeep and so on... Main Section Eight(8) : Bonus Sections ! Python & Kali(Brief ) Learning Python Programming language from Scratch Making a Web App with Python for clearing our idea & mastering Python Python & Kali Linux collectively Writing a TCP Client in Python Writing a UDP Client in Python Writing a TCP Server in Python Developing an software like Netcat in Python Metasploit in Hacking(Brief ) Learn Metasploit from Scratch Scanning utilizing Metasploit Gaining entry to the system utilizing Metasploit Maintaining entry to the System utilizing Metasploit Learning superior makes use of of Metasploit Who is the audience? People who need to study Cyber Security Anybody who's interested by studying moral hacking & penetration testing People who need to get a coaching to turn into a Certified Ethical Hacker (CEH) People with fundamentals/superior degree data of Hacking and need to take their data to subsequent degree Anybody who desires to learn the way to launch totally different assaults precisely the identical means Black Hat hackers do Anybody who desires to study Website Hacking & Penetration Testing From Scratch Anybody who desires to study Digital Forensics Anybody who desires to be taught Python & Kali Linux Anybody who desires to develop their talent to get a greater job Anybody who desires to advance their profession as a freelancer on-line & improve their hourly pay charge Anybody who desires to learn the way a hacker would assault their Computer / Websites Anybody who desires to safe their Computer / Websites 👉 Activate Udemy Coupon 👈 Free Tutorials Udemy Review Real Discount Udemy Free Courses Udemy Coupon Udemy Francais Coupon Udemy gratuit Coursera and Edx ELearningFree Course Free Online Training Udemy Udemy Free Coupons Udemy Free Discount Coupons Udemy Online Course Udemy Online Training 100% FREE Udemy Discount Coupons https://www.couponudemy.com/blog/the-complete-cyber-security-bundle-beginner-to-advanced/
0 notes
Photo

[F4LT] Complete Ethical Hacking Masterclass: Go from zero to hero !
http://www.tradingprotoolsnews.com/2018/02/04/f4lt-complete-ethical-hacking-masterclass-go-from-zero-to-hero/
Black Hat hacking has always been a dream for us! Make your dream come true by taking this Course. This is the most comprehensive, yet straight-forward, course for Ethical Hacking & Penetration testing on Udemy! In this course you will start as a beginner with no previous knowledge & by the end of the course you will be at a High Intermediate level in Ethical Hacking & Penetration testing. With 550 lectures & 60+ hours of content this comprehensive course leaves no stone unturned! Once you buy that Course you will get a Life time access to the content & you will get answer to your every single question from an experienced IT professional! You don't need any previous programming knowledge or basics for starting this course.In this course we will start from Scratch.We will explain all the techniques of hacking , theory behind those techniques & give Real world examples in every single Part of the course! In this course there are 18 parts but this course can be divided in to 8 main sections. Below there is a brief explanation of this Complete course.You will learn much more than what we try to explain below ! Main Section One(1) : Brief introduction to the complete course , Setting up the lab & maintaining Anonymity [Covering Part 1] Complete course overview in just 3 minutes & 39 seconds ! Setting up the Complete Ethical Hacking Lab 1.Learn how to Install VirtualBox 2.Configure the VirtualBox 3.Downloading & Installing Kali Linux latest 4.Downloading & Installing 2 different Operating Systems(Windows & Metasploit) 5.Downloading & Installing Android Platforms on the PC for learning to hack Android mobile phones. Hacking Lab Basics 1.Kali Linux Basics 2.Basics of Kali Linux Terminal & Commands 3.Advanced uses of Kali Linux Terminal & Commands 4.Getting Black Hat hacking tools for further use(Only for Ethical Hacking purpose!) Anonymity Online 1.Learn how to be Anonymous Online 2.Learn how to cover your tracks 3.Learn to use different tools for maintaining anonymity Online 4.We are going to get more lectures to be anonymous online through out the Course Main Section Two(2) : Gathering Information [Covering Part 2] Gathering Information about the Victim weather it is a person, website or a company. Gathering Passive Information 1.Gathering Passive Information using different tools 2.Searching for hidden people 3.Hacking Job sites for getting details 4.Using Netcraft for gathering Passive Information 5.Using Maltego for gathering Passive Information 6.Using Google Hacking for gathering Passive Information 7.Knowing about any hidden information easily Gathering Active Information 1.Gathering active information using search engines 2.Using different websites for Gathering active information 3.Advanced Google Search operators for gathering active Information 4.Using Database Hacking , Tools & advanced Google hacking 5.Nmap, Nmap NSE scripts, Zenmap for gathering Active Information 6.Gathering Active Information using DNS transfer Zone, SMB Null Session & SMB Enumeration Main Section Three(3) : Hacking WiFi & Wired connection [Covering Part 3] Understanding how WiFi & Wired hacking works Identifying the target network Identifying hidden networks Exploiting the target network 1.Hacking WEP networks 2.Hacking WPA/WPA2 networks 3.Hacking WPS enabled networks 4.Capturing packets 5.Taking advantage of Router misconfigurations 6.Post Exploitation Different types of attack on the Victim 1.Non disrupting techniques 2.Eavesdropping 3.Creating an access point for Man in the Middle attack 4.Creating an Online access point for Man In the Middle attack 5.Denial of Service attack (DOS) on the Wireless Network 6.Disconnecting any device from the network Creating rogue access Point Creating Fake Captive portals Covering our tracks 1.Using Disposable VMs for covering our tracks 2.Changing our MAC addresses Wireless penetration testing Accessories Main Section Four(4) : All the attacks that a hacker can do and you should learn ! [Covering Part 4 to 15 ] Scanning Network(Brief Description) Learn to Scan Networks Learn to Scan out of your own Network Network level scanning & Web application level scanning learn both Learn to Scan for Vulnerability Get Demonstration & Real World examples DOS & DDOS attack (Brief Description) Understand DOS & DDOS properly Learn about the Computer networking OSI model DDOS in the world map Clearing concept using best tools and services Doing DOS & DDOS using HTTP flood, ICMP flood, SYN flood,Slowloris, LOIC , JS LOIC, etc... Stressers and Booters for DOS & DDOS Tools that hacker community use for DOS & DDOS Sniffing Attacks(Brief Description) Sniffing using ARP Poisoning & ARP Spoofing Sniffing using DNS Poisoning Advanced techniques for Sniffing Demonstration in every section! Session Hijacking(Brief Description) Learn Session Hijacking of Network level & Web Application level Network Level Session Hijacking using TCP & UDP hijacking, Blind hijacking etc... Web application level session hijacking using Cookies, Bruteforce, XSS etc... Automating Session hijacking using Burpsuite, Owaspzap, Netsparker etc... Social Engineering(Brief Description) Social Engineering basics The Art of human attacks using social engineering Human based Social Engineering vs Computer based Social Engineering Learn Social Engineering using Kali Linux such as: Creating payloads, listening for it, uses of metasploit etc... Phishing attacks using SET toolkit, Phish5, Phishing emails etc... Doing Scams [Learn how to do & take money] Learn to do Identity theft Buy & Sell Identities Real World example included for Social Engineering attack Enumeration(Brief Description) Learn & Understand Enumeration Enumeration using SNMP, SMTP, NTP, NETBIOS, LDAP etc... Demonstration of Enumeration using SNMP, SMTP, NTP, NETBIOS, LDAP etc... Buffer Overflow hacking(Brief Description) Learn to hack using Buffer Overflow Basics of Buffer Overflow Mastering Buffer Overflow Buffer Overflow using Malware Buffer Overflow using Programming Database hacking & Reporting of Buffer Overflow Learning advance techniques of Buffer Overflow Compromising the Victim using Buffer Overflow Web Application Hacking(Brief Description) Learn how to do Web application hacking Gathering information for application hacking Learn to do web application tampering Client side attacks of web application hacking Identity management & access control of web application hacking Hacking with Malware(Brief Description) Learn malware threats from Scratch Basics of Trojan Viruses Basics of Virus & Worms Creating a Trojan Virus Creating Virus & Worms Cloud Computing Hacking(Brief Description) Learn to hack with Cloud Computing Cloud computing basics Hacking through cloud computing Cloud computing using Social Engineering Strengthening the security of Cloud Computing DDOS prevention and much more for strengthening the security of Cloud computing Hacking Systems(Brief Description) Learn to hack systems step by step Gaining access attacks Maintaining access to the Victim's pc Post exploitation after gaining access Covering our tracks & evidence Main Section Five(5) : Website Hacking & Penetration testing [Covering Part 15 to 16] Learn how to Cross Site Scripting(XSS) in great details! Hacking using Cross Site Scripting Demonstration Learn how to do SQL Injection in great details! Blind SQL Injection SQL Map to hack a website Advanced SQL Injection Hacking Using SQL Injection Demonstration Learn how to hack a web server Web Server hacking advanced techniques Hacking Web Servers Demonstration Main Section Six(6) : Learn to hack mobile platforms such as: Android, Windows, Blackberry [Covering Part 17] Hacking Android phones Using Payloads, Malwares, Metasploit, Social Enginerering etc... for hacking mobile phones Hacking IOS mobiles Hacking Windows mobiles Hacking Blackberry mobiles Hacking Demonstration for all the platforms! Main Section Seven(7) : Defend Hacking attacks & Digital Forensics [Covering Part 18] Defend most of the attacks that we learnt Learn forensics from scratch Learn Kali Linux & Forensics Using different tools from Digital Forensics such as : LIBEWF, Guymager, DCFLDD, Hasdeep etc... Main Section Eight(8) : Bonus Sections ! Python & Kali(Brief Description) Learning Python Programming language from Scratch Making a Web App with Python for clearing our concept & mastering Python Python & Kali Linux together Writing a TCP Client in Python Writing a UDP Client in Python Writing a TCP Server in Python Developing an application like Netcat in Python Metasploit in Hacking(Brief Description) Learn Metasploit from Scratch Scanning using Metasploit Gaining access to the system using Metasploit Maintaining access to the System using Metasploit Learning advanced uses of Metasploit
0 notes
Text
ZAP Active Scan | CyberSecurityTV

Explore the power of ZAP Active Scan on CyberSecurityTV! 🛡️🔍 In this episode, we dive into the world of web application security testing using OWASP ZAP's active scanning capabilities. Learn how to identify vulnerabilities and weaknesses in your web applications through comprehensive scanning techniques. Our experts will guide you through the process, explaining how ZAP's features can help enhance your security posture. Whether you're a developer or a cybersecurity enthusiast, this episode will provide valuable insights into effectively using ZAP for proactive security testing. Tune in now to bolster your web application defense strategy! 💻🔒
#ZAPActiveScan#CyberSecurityTV#WebAppSecurity#OWASPZAP#VulnerabilityScanning#CyberProtection#ApplicationDefense#SecurityTesting#TechInsights#CyberLearning#WebSecurity
0 notes
Text
OWASP ZAP Active Scan | CyberSecurityTV

OWASP ZAP Active Scan is a powerful cybersecurity tool featured on CyberSecurityTV. Developed by the Open Web Application Security Project (OWASP), it offers comprehensive scanning capabilities to identify and address vulnerabilities in web applications.
#OWASPZAP #ActiveScan #CybersecurityTool #WebApplicationSecurity #VulnerabilityScanning #OWASPProject #CyberSecurityTV #ThreatDetection #WebAppProtection #SecureCoding
0 notes
Text
Mobile security und Owasp Zap - Testing Guidelines für Android und IOS

Immer wieder ein sehr interessantes Thema. Gerade das Thema mobile security bietet immer noch Stoff für viele Fragen, teilweise, weil entsprechend auch wenig Informationen fehlen. Aber auch hier bietet Owasp Zap eine entsprechende Lösung an. Basierend zu diesem Thema möchte ich auch noch das Thema mobile security Template anfügen welches durch OWASP selbst auch vertrieben wird. https://youtu.be/KWofjrHNNqs Für interessiert bietet Owasp entsprechend eben ein mobile security testing Guide, der alle Aspekte abdeckt, von der allgemeinen Planung über das Setup, und auch das Tooling. Anbei die Informationen aus dem Testing Guide von Owasp.
Table-of-Contents
Introduction - Foreword - Frontispiece - Introduction to the Mobile Security Testing Guide - Mobile App Taxonomy - Mobile App Security Testing General Testing Guide - Mobile App Authentication Architectures - Testing Network Communication - Cryptography in Mobile Apps - Testing Code Quality - Tampering and Reverse Engineering - Testing User Privacy Protection Android Testing Guide - Platform Overview - Android Basic Security Testing - Data Storage on Android - Android Cryptographic APIs - Local Authentication on Android - Android Network APIs - Android Platform APIs - Code Quality and Build Settings for Android Apps - Tampering and Reverse Engineering on Android - Android Anti-Reversing Defenses iOS Testing Guide - Platform Overview - iOS Basic Security Testing - Data Storage on iOS - iOS Cryptographic APIs - Local Authentication on iOS - iOS Network APIs - iOS Platform APIs - Code Quality and Build Settings for iOS Apps - Tampering and Reverse Engineering on iOS - iOS Anti-Reversing Defenses Appendix - Testing Tools - Suggested Reading
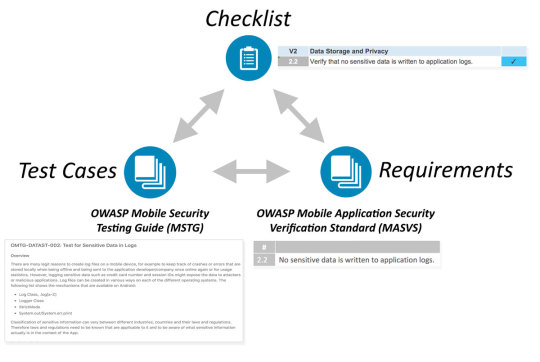
Hier eine kurze grafische Übersicht was das mobile security Test Template an Informationen bietet. Wie man unteranderem Android Geräte auf Sicherheitslücken testet, wird in diesem Beispiel hier gut beschrieben. https://youtu.be/tdjpgsL48Pw Wie man security Test auf IOS durchführt ist in diesem Beispiel gut erklärt. https://youtu.be/xOyViT8ekfU Read the full article
0 notes
Text
Wie man Sicherheitstests für AngularJS mit Hilfe von OWASP ZAP durchführt

Neben vielen anderen Test kann man natürlich auch AngularJS auf Sicherheits- und Schwachstellen testen. AngularJS macht viel Gebrauch von JavaScript, was die 'traditionelle' Spider nicht gut verarbeiten kann. https://www.youtube.com/watch?v=mz2nhYpU-sw Verwendet deshalb innerhalb von OWASP ZAP stattdessen die Ajax-Spider: https://github.com/zaproxy/zap-core-help/wiki/HelpAddonsSpiderAjaxConcepts Diese ist zwar langsamer, kommt aber mit jedem JS zurecht, während die Ajax Spider den Browser startet, um die Website zu crawlen. ZAP führt ein Spidering von der Basis-URL aus durch, die müssen von euch festgelegt werden. Wie das im Einzelnen aussehen kann könnt ihr in diesem Beispielvideo sehen. https://www.youtube.com/watch?v=EwbPPPBhM4A Dies ist auch eine praktische Möglichkeit, ZAP über Docker zum Laufen zu bringen. Ich selbst nutzte Owasp Zap als Docker Integration auf meinem Microserver. https://github.com/zaproxy/zaproxy/wiki/Docker https://www.youtube.com/watch?v=B-MDsECikqM Read the full article
0 notes
Text
Security Testing mit Owasp ZAP

OWASP ZAP (kurz für Zed Attack Proxy) ist ein Open-Source-Sicherheitsscanner für Webanwendungen. Er ist sowohl für Neueinsteiger in die Anwendungssicherheit als auch für professionelle Penetrationstester gedacht. Ich nutzte OWASP Zap in diversen Projekten, u.a. Magento und Salesforce Projekten um eben Schwachstellen Test auszuspüren. Durch seine starke Erweiterbarkeit über Skripte und Plugins kann man mit OWASP ZAP ein sehr nützliches Toolsetting aufbauen, welches eben auch recht einfach in eine Continuous Integration Umgebung eingebunden werden kann. https://www.youtube.com/watch?v=o_JZRgQMF4Q OWASP Zap bietet eine direkte Integration in Jenkins an, und kann so tägliche oder wöchentliche Scans eurer Projekte vornehmen, samt eines sehr ausführlichen Reporting. Dies hebt OWASP Zap hervor gegenüber käuflichen Softwarelösungen, wo man dann erst im Premium Modus eine Integration in einen CI Workflow erhält. Ich hatte in anderen Projekten unteranderem Acunetix genutzt, dies bot aber eine entsprechende Einbindung erst ab einem Premium Modus an (Stand 2016). OWASP Zap lässt sich nicht nur mit eigenen Skripten stark erweitern, sondern man kann durch das Community Addon Community Skripte nutzen. https://www.youtube.com/watch?v=3vVnMh6AUkk Gerade Read the full article
0 notes
Text
Payload basierter Schwachstellentest mit Jmeter und Owasp ZAP

Die Frage aller Fragen: "Kann ich überhaupt Jmeter und Owasp Zap kombinieren ?" JMeter kann als Proxy konfiguriert werden, um alle ZAP-Anfragen zu speichern und dann können ihr denselben OWASP-Test nach einer Korrektur oder Änderung erneut an dieselbe oder eine andere Umgebung senden. Grundsätzlich müsst ihr JMeter so konfigurieren, dass alle Anfragen über den ZAP Intercepting Proxy gesendet werden. Standardmäßig läuft ZAP auf demselben Host unter Verwendung von Port 8080, so dass ihr JMeter entweder wie folgt ausführen müsst: jmeter -H localhost -P 8000 -n -t test.jmx -l result.jtl Alternativ können ihr die gleichen Einstellungen auch über die Java Networking Properties vornehmen: jmeter -Dhttp.proxyHost=localhost -Dhttp.proxyPort=8080 -Dhttps.proxyHost=localhost -Dhttps.proxyPort=8080 -n -t test.jmx -l result.jtl https://www.youtube.com/watch?v=zCBnB0CKZE4 Und schließlich können ihr die folgenden Zeilen zur Datei system.properties hinzufügen (befindet sich im Ordner "bin" eurer JMeter-Installation) http.proxyHost=localhost http.proxyPort=8080 https.proxyHost=localhost https.proxyPort=8080 Ein Neustart von JMeter ist erforderlich, um die Eigenschaften zu übernehmen. Read the full article
0 notes