#pentesting
Explore tagged Tumblr posts
Text
is there a wider tumblr tag/blogs for ethical hacking and cybersecurity? i really got into this hobby and might work to get a job in it.
the codeblr/progblr tags seem to be mostly people learning coding
if you regularly post about it please let me know too
9 notes
·
View notes
Text

Zoey. One cat three trials.
#artists on tumblr#lineart#stippling#eyes#linedrawing#pet portrait#cat#drawing#pen and ink#pentesting
5 notes
·
View notes
Text
Prevent OAuth Misconfiguration in Symfony Apps Securely
Introduction
OAuth is the industry-standard protocol for authorization. While Symfony offers first-class OAuth bundles, a single misconfiguration can expose sensitive data or allow unauthorized access.

In this guide, we’ll walk you through:
What OAuth misconfiguration entails
Common pitfalls in Symfony setups
Hands-on coding examples
How to scan your app using our Website Vulnerability Scanner online
Best practices to lock down your OAuth flows
For more in-depth tutorials, visit our blog: ➡️ Pentest Testing Corp Blog
What Is OAuth Misconfiguration?
OAuth misconfiguration occurs when the authorization server or client settings are improperly defined, leading to:
Open Redirects: Attackers abuse redirect URIs
Insecure Scopes: Granting excessive permissions
Weak Token Validation: Skipping signature or audience checks
In Symfony, these mistakes often stem from inaccurate security.yaml entries or incorrect client registration on your OAuth provider.
Example: Insecure OAuth Setup
Below is an insecure security.yaml that illustrates two pitfalls: missing state checks and overly permissive redirect URIs.
# config/packages/security.yaml security: firewalls: oauth_login: pattern: ^/connect/ oauth: resource_owners: google: "/login/check-google" login_path: /connect/google check_path: /login/check-google default_target_path: / use_referer: true # insecure: trusts HTTP Referer header oauth_user_provider: service: app.user_provider
Issues:
use_referer: true trusts the HTTP Referer header—easy to spoof.
Redirect URIs not strictly defined on the OAuth provider side.
How to Scan with Our Free Tool
Use our Website Vulnerability Scanner to automatically detect OAuth misconfigurations and other vulnerabilities in seconds.
Screenshot of the free tools webpage where you can access security assessment tools for vulnerability detection
Within moments, you’ll receive a detailed report identifying misconfigurations, insecure headers, and more.
Sample Vulnerability Assessment Report
Once the scan completes, you’ll see sample assessment report to check Website Vulnerability:
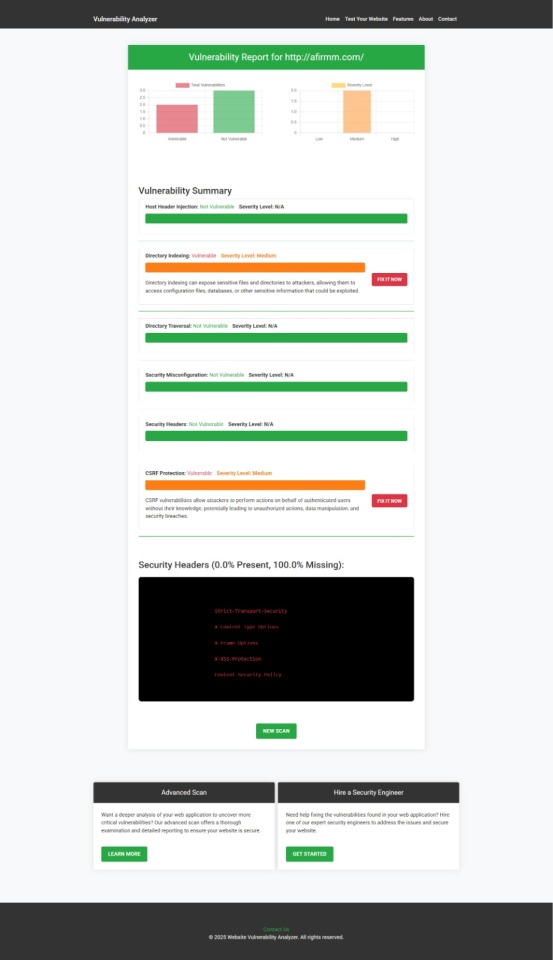
Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities
Best Practices to Secure OAuth in Symfony
Strict Redirect URIs Register only exact URIs on your OAuth provider.
# security.yaml oauth: resource_owners: google: redirect_uri: 'https://your-app.com/connect/google/check'
2. Enforce State Parameter Prevent CSRF in the authorization flow.
oauth: resource_owners: google: options: use_state: true
3. Validate Tokens Always verify issuer (iss), audience (aud), and signature.
// src/Security/GoogleTokenValidator.php use Firebase\JWT\JWT; public function validate(string $jwt): array { $publicKey = file_get_contents($this- >projectDir.'/config/jwt/public.pem'); $payload = JWT::decode($jwt, $publicKey, ['RS256']); if ($payload->aud !== 'your-client-id') { throw new \Exception('Invalid audience'); } return (array)$payload; }
4. Limit Scopes Only request the scopes your app truly needs.
oauth: resource_owners: google: options: scope: ['email', 'profile']
AI Application Cybersecurity
Leverage our AI-powered analysis for advanced threat detection in AI applications:
🔗 AI Application Cybersecurity Services
Partner With Us
Offer top-tier cybersecurity to your clients by reselling our pentest & assessment services:
🔗 Offer Cybersecurity Service to Your Clients
Stay Updated
Subscribe to our LinkedIn newsletter for the latest in web security:
✉️ Subscribe on LinkedIn
By following these guidelines and examples, you’ll eliminate OAuth misconfiguration risks in your Symfony applications—and keep your users’ data safe.
Want a free scan? DM me or check https://free.pentesttesting.com/.
2 notes
·
View notes
Text
Building Your Own Cyberdeck:
What do you do when you have extra time between a job and your next? How about building your own Cyberdeck? Check this article out for tips on building your own!
The Ultimate Hacker Project For aspiring cybersecurity professionals, cyberpunk enthusiasts, hardware hackers, and circuit benders, one of the best hands-on projects you can take on is building your own cyberdeck. Despite overwhelming schedules full of training programs, full time work weeks, sometimes limited funds, and the endless possibilities of hardware combinations, many fans of the…

View On WordPress
#Cyber#Cyber Security#cyberdeck#cyberpunk#Cybersecurity Specialist#Ethical Hacking#hack#hacker#infosec#IT#IT professional#mobile#mobile computer#Pentesting#programming#project
31 notes
·
View notes
Text
Greetings fellow freaks and geeks!
Allow me to introduce myself:
My name is Haru
Im (at the time of posting this) 18!
Im a Therian and a furry :3
Im pansexual and genderfluid (so if possible please ask for my pronouns)
I enjoy Cybersecurity, general technological devices, music (punk, rock, indie and a whole lot more)
Im diagnosed autistic, ADHD, dislexic, disbraxic, disgraphic and more ^^;
Im currently self teaching for red team cybersecurity, art and guitar as well as fursuit making and other crafty things
Currently this is my main blog where ill post just whatever and i plan on making 2 other blogs but ill announce when that is ;3
For now enjoy the insane ramblings about anything and everything all of the time.
#intro post#introduction#blog intro#main blog#furry#therian#punk rock#dedsec#hack the planet#cybersecurity#red team#pentesting
2 notes
·
View notes
Text

Dear My Arch Debian Nemesis @kali-official,
Naturally, and this USB stick's not big enough for the both of us (it's a 4gb usb2.0 😬). But just because we are rivals, that's no excuse to misgender you.
2 notes
·
View notes
Text
youtube
3 notes
·
View notes
Text

🌐📚 Elevate your cloud skills prowess with our training courses! 🎓💻
💡 Gear up for success with our in-depth training designed to help you nail the Cloud certification exam. 💯🥇
📅 Enroll today and take the first step towards unlocking endless opportunities! Don't miss out on this incredible offer. ⏳🔓
For Additional Info🔔 🟢Whatsapp: https://wa.me/9677781155 , https://wa.me/7558184348 , https://wa.me/9677724437 📨Drop: https://m.me/elysiumacademy.org 🌐Our website: https://elysiumacademy.org/networking-course-certification/ 📌Live Visit: https://maps.app.goo.gl/YegrK4aKEWbEY2nc8 🔖Appointment: https://elysiumacademy.org/appointment-booking/
#elysiumacademy#no1academy#jobassurance#tesbo#no1trainingacademy#elysiumacademy_madurai#cybersecurity#ethicalhacking#hackers#programming#hack#technology#security#coding#tech#ethicalhacker#pentesting#cyber#malware#programmer#informationsecurity#AWS#cloudskillawareness#coder
2 notes
·
View notes
Text
CloudBrute - Awesome Cloud Enumerator
A tool to find a company (target) infrastructure, files, and apps on the top cloud providers (Amazon, Google, Microsoft, DigitalOcean, Alibaba, Vultr, Linode). The outcome is useful for bug bounty hunters, red teamers, and penetration testers alike. The complete writeup is available. here Motivation we are always thinking of something we can automate to make black-box security testing easier. We…

View On WordPress
1 note
·
View note
Text
Red Teaming in the Digital Age: Adapting Traditional Tactics to Modern Threats
Introduction:
In an era dominated by digital advancements, the landscape of cyber threats is continually evolving. Organizations face unprecedented challenges in safeguarding their digital assets from an array of sophisticated adversaries. Red teaming has emerged as a crucial strategy to identify and mitigate vulnerabilities proactively. This article explores the evolution of red teaming in the digital age and the adaptation of traditional tactics to counter modern threats.
Understanding Red Teaming:
Red teaming is a systematic and comprehensive approach to testing the effectiveness of an organization's security measures. Unlike routine security assessments, red teaming simulates realistic attack scenarios to evaluate an organization's defensive capabilities. Traditionally, this practice was heavily focused on physical security, but in the digital age, the emphasis has shifted to cybersecurity.
Adapting Traditional Tactics:
Social Engineering in the Digital Sphere:
Traditional red teaming often involved physical interactions, such as tailgating or impersonating employees. In the digital age, these tactics have evolved into sophisticated social engineering techniques, such as phishing emails, pretexting, and baiting. Red teams must now simulate these online threats to assess an organization's susceptibility to manipulation.
Advanced Persistent Threats (APTs):
APTs are persistent and targeted cyber-attacks that aim to breach a network over an extended period. In the digital age, red teams need to replicate the tactics of APTs, utilizing advanced malware, zero-day exploits, and covert communication channels. This adaptation helps organizations fortify their defenses against prolonged and stealthy attacks.
Cloud Security Assessments:
With the widespread adoption of cloud computing, red teams must adapt their strategies to assess the security of cloud-based infrastructures. This involves evaluating configurations, access controls, and data encryption within cloud environments. Ensuring the resilience of digital assets in the cloud is paramount in the current threat landscape.
IoT Exploitation:
The proliferation of Internet of Things (IoT) devices has introduced new challenges in terms of security. Red teaming in the digital age involves simulating attacks on IoT devices to identify vulnerabilities and assess the potential impact on an organization's network. This adaptation is crucial as IoT devices become integral components of modern business operations.
Machine Learning and Artificial Intelligence Threats:
As organizations increasingly incorporate machine learning and artificial intelligence into their security protocols, red teams must adapt by exploring potential vulnerabilities in these technologies. Simulating attacks that exploit weaknesses in AI algorithms or manipulate machine learning models helps organizations stay ahead of adversaries leveraging similar tactics.
Conclusion:
Red teaming remains a vital component of cybersecurity strategies in the digital age, requiring constant adaptation to address emerging threats. By incorporating traditional tactics into modern contexts, red teams can effectively evaluate an organization's resilience against a wide range of cyber threats. As technology continues to evolve, the role of red teaming will be pivotal in enhancing cybersecurity postures and ensuring the ongoing protection of valuable digital assets.
2 notes
·
View notes
Text
Signal boosting
Thank you


#progblr#lainposting#196#free wifi#public service announcement#psa#network hacking#hacking#wifi#wifi hacking#ip address#pentesting
138K notes
·
View notes
Text
Prevent Command Injection in Symfony: Secure Your Code
Symfony is a powerful PHP framework trusted by thousands of developers, but like any framework, it's not immune to security threats. One of the most dangerous—and often overlooked—threats is a Command Injection Attack.

In this blog post, we’ll break down what a command injection attack is, how it can be exploited in a Symfony application, and—most importantly—how to prevent it. We’ll also include code examples and offer you a Website Vulnerability Scanner online free to scan your website for vulnerabilities like this one.
➡️ Visit Our Blog for More Cybersecurity Posts: 🔗 https://www.pentesttesting.com/blog/
🧨 What is Command Injection?
Command Injection is a type of security vulnerability that allows attackers to execute arbitrary system commands on your server. If user input is improperly sanitized, attackers can exploit functions like exec(), system(), or shell_exec() in PHP.
This can lead to:
Data breaches
Server hijacking
Total application compromise
🐘 Symfony Command Injection Example
Let’s start with a naive Symfony controller that might fall victim to command injection.
❌ Vulnerable Symfony Code
// src/Controller/BackupController.php namespace App\Controller; use Symfony\Component\HttpFoundation\Request; use Symfony\Component\HttpFoundation\Response; use Symfony\Bundle\FrameworkBundle\Controller\AbstractController; class BackupController extends AbstractController { public function backupDatabase(Request $request): Response { $filename = $request->query->get('filename'); // ⚠️ Dangerous input $output = shell_exec("mysqldump -u root -psecret mydb > /backups/{$filename}"); return new Response("Backup created: $filename"); } }
If an attacker sets filename=backup.sql;rm -rf /, this code could delete your entire server. Yikes!
🔐 Secure It With Escaping & Whitelisting
Let’s see how we can secure this.
✅ Safe Symfony Version
public function backupDatabase(Request $request): Response { $filename = $request->query->get('filename'); // Sanitize the filename using a whitelist or regex if (!preg_match('/^[\w\-\.]+$/', $filename)) { return new Response("Invalid filename", 400); } $safePath = escapeshellarg("/backups/" . $filename); $output = shell_exec("mysqldump -u root - psecret mydb > $safePath"); return new Response("Backup created: $filename"); }
By using escapeshellarg() and validating the input, we reduce the risk significantly.
🛠️ Automate Detection with Our Free Tool
Want to check if your website is vulnerable to command injection and other critical flaws?
🎯 We’ve built a Free Website Vulnerability Scanner that checks for command injection, XSS, SQLi, and dozens of other issues—all in seconds.
🖼️ Screenshot of our Website Vulnerability Scanner:

Screenshot of the free tools webpage where you can access security assessment tools.
👉 Try it now: https://free.pentesttesting.com/
📋 Sample Output Report
Our scanner doesn’t just find issues—it gives you a detailed, developer-friendly report you can act on.
🖼️ Screenshot of a sample scan report from our tool to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
💼 Need Help Fixing It? We've Got You Covered
🔐 Web App Penetration Testing Services If you're looking for expert-level help to secure your Symfony or PHP application, our team is ready to assist.
➡️ Learn more: https://www.pentesttesting.com/web-app-penetration-testing-services/
🤝 Are You a Tech Company or Agency?
We offer white-label cybersecurity services so you can resell pentesting to your clients without hiring a full team.
📦 Get the full service suite here: 🔗 https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
💌 Stay Ahead of Threats—Subscribe Now!
Don’t miss future posts, case studies, and cybersecurity tips.
📬 Subscribe to our LinkedIn Newsletter
🔁 Final Thoughts
Command injection remains one of the most dangerous web application vulnerabilities. Symfony gives you the tools to secure your app—but only if you use them correctly.
Don’t wait until you’re hacked. Take 2 minutes to scan your website with our free Website Security Scanner tool.
📝 Originally written by the Pentest Testing Corp. team 📌 Visit our blog for more: https://www.pentesttesting.com/blog/
2 notes
·
View notes
Text
Coding and Scripting for Beginner Hackers
Learning to code and write scripts is a crucial skill for getting into ethical hacking and cybersecurity. Scripting allows you to automate repetitive tasks, develop your own custom tools, analyze data, and program everything from small hacking tools to machine learning models. Understanding and knowing how to code in different languages can be extremely useful when doing deep dives into malware…

View On WordPress
#Cyber Security#cybersecurity careers#Ethical Hacking#hacer certifications#hacking for beginners#hacking guide#hacking homelab#infosec#learn to code#learn to hack#Penetration Testing#Pentesting
5 notes
·
View notes
Text
Why CTEM Solutions Are the Future of Proactive Cybersecurity
Let’s face it, traditional security assessments just don’t cut it anymore. With constantly evolving threats, expanding digital footprints, and limited internal resources, security teams need more than just periodic scans and outdated reports.
That’s where CTEM solutions come in. CTEM (Continuous Threat Exposure Management) is all about shifting from reactive defense to proactive, continuous security. At Siemba, we’ve built a next-gen CTEM platform that combines EASM (External Attack Surface Management), AI-driven DAST, automated vulnerability assessments, and on-demand pentesting (PTaaS)—all under one roof.
No more juggling multiple vendors. No more waiting weeks for reports. Just real-time visibility, smart prioritization, and actionable remediation.
Whether you're a fast-growing SaaS startup or a regulated enterprise, Siemba’s CTEM solution adapts to your threat landscape and scales with your needs. Because in cybersecurity, waiting to act isn’t a strategy—it’s a risk.
Explore Siemba’s CTEM capabilities and see how we’re helping businesses stay one step ahead.
0 notes
Text
Are You Prepared for 2025's Top Cyber Threats?
Cybercriminals are getting smarter—and no business is too small to be targeted. From phishing emails and ransomware attacks to insider threats and credential stuffing, understanding today’s most dangerous cyber risks is the first step to securing your systems and data.
0 notes
Text
Linux-Smart-Enumeration - Linux Enumeration Tool For Pentesting And CTFs With Verbosity Levels
First, a couple of useful oneliners 😉 wget "https://github.com/diego-treitos/linux-smart-enumeration/releases/latest/download/lse.sh" -O lse.sh;chmod 700 lse.sh curl "https://github.com/diego-treitos/linux-smart-enumeration/releases/latest/download/lse.sh" -Lo lse.sh;chmod 700 lse.sh Note that since version 2.10 you can serve the script to other hosts with the -S flag! Linux enumeration tools…

View On WordPress
#Ctfs#Hackthebox#KitPloit#Linux Enumeration#Linux-Smart-Enumeration#Oscp#PENTESTING#Privilege Escalation
1 note
·
View note