#PortSwigger Research
Explore tagged Tumblr posts
Text
Application Security Testing (AST) Software Market is Set To Fly High in Years to Come
Latest released the research study on Global Application Security Testing (AST) Software Market, offers a detailed overview of the factors influencing the global business scope. Application Security Testing (AST) Software Market research report shows the latest market insights, current situation analysis with upcoming trends and breakdown of the products and services. The report provides key statistics on the market status, size, share, growth factors of the Application Security Testing (AST) Software The study covers emerging player’s data, including: competitive landscape, sales, revenue and global market share of top manufacturers are Checkmarx (Israel), WhiteHat Security (United States), PortSwigger (United Kingdom), Acunetix (United States), Veracode (United States), Qualys (United States), Micro Focus (United Kingdom), Rapid7 (United States), IBM (United States), Contrast Security (United States), ImmuniWeb (Switzerland), Netsparker (United States), Synopsys (United States), Edgescan (Ireland), Onapsis (United States), NetSPI (United States), ERPScan (United States),
Free Sample Report + All Related Graphs & Charts @: https://www.advancemarketanalytics.com/sample-report/124705-global-application-security-testing-ast-software-market?utm_source=Organic&utm_medium=Vinay
Application Security Testing (AST) Software Market Definition:
Application security testing (AST) is the process of identifying security vulnerabilities in source code in order to make applications more resistant to security attacks. AST must be automated because of the increasing modularity of business software, the vast number of open-source components, and the high number of known vulnerabilities and possible attacks. The majority of businesses employ a hybrid of application security solutions.
Market Trend:
Development of High-Speed Software Processes such as Agile and Dev0ps
Market Drivers:
Need to Prevent Security Vulnerabilities against Threats
The demand for Data Security and to Build Customer Confidence
Market Opportunities:
Protect Code against Exploits and Known Buds will grow the Application Security Testing (AST) Software Market
The Global Application Security Testing (AST) Software Market segments and Market Data Break Down are illuminated below:
by Type (Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Interactive Application Security Testing (IAST), Mobile Application Security Testing (MAST), Software Composition Analysis (SCA), Runtime Application Self-Protection (RASP)), Application (Web Application Firewall, Runtime Protection, Advanced Bot Protection, Client-Side Protection, Serverless Protection, API Security, Attack Analytics, Others), Deployment Mode (Cloud, On-premises), Organization Size (SMEs, Large Enterprises), Component (Software, Service, Solution), End User (IT, Healthcare, Financial Service, Telecom & ISPs, Retail, Others)
Region Included are: North America, Europe, Asia Pacific, Oceania, South America, Middle East & Africa
Country Level Break-Up: United States, Canada, Mexico, Brazil, Argentina, Colombia, Chile, South Africa, Nigeria, Tunisia, Morocco, Germany, United Kingdom (UK), the Netherlands, Spain, Italy, Belgium, Austria, Turkey, Russia, France, Poland, Israel, United Arab Emirates, Qatar, Saudi Arabia, China, Japan, Taiwan, South Korea, Singapore, India, Australia and New Zealand etc.
Enquire for customization in Report @: https://www.advancemarketanalytics.com/enquiry-before-buy/124705-global-application-security-testing-ast-software-market?utm_source=Organic&utm_medium=Vinay
Strategic Points Covered in Table of Content of Global Application Security Testing (AST) Software Market:
Chapter 1: Introduction, market driving force product Objective of Study and Research Scope the Application Security Testing (AST) Software market
Chapter 2: Exclusive Summary – the basic information of the Application Security Testing (AST) Software Market.
Chapter 3: Displayingthe Market Dynamics- Drivers, Trends and Challenges of the Application Security Testing (AST) Software
Chapter 4: Presenting the Application Security Testing (AST) Software Market Factor Analysis Porters Five Forces, Supply/Value Chain, PESTEL analysis, Market Entropy, Patent/Trademark Analysis.
Chapter 5: Displaying market size by Type, End User and Region 2015-2020
Chapter 6: Evaluating the leading manufacturers of the Application Security Testing (AST) Software market which consists of its Competitive Landscape, Peer Group Analysis, BCG Matrix & Company Profile
Chapter 7: To evaluate the market by segments, by countries and by manufacturers with revenue share and sales by key countries (2021-2026).
Chapter 8 & 9: Displaying the Appendix, Methodology and Data Source
Finally, Application Security Testing (AST) Software Market is a valuable source of guidance for individuals and companies in decision framework.
Data Sources & Methodology The primary sources involves the industry experts from the Global Application Security Testing (AST) Software Market including the management organizations, processing organizations, analytics service providers of the industry’s value chain. All primary sources were interviewed to gather and authenticate qualitative & quantitative information and determine the future prospects.
In the extensive primary research process undertaken for this study, the primary sources – Postal Surveys, telephone, Online & Face-to-Face Survey were considered to obtain and verify both qualitative and quantitative aspects of this research study. When it comes to secondary sources Company's Annual reports, press Releases, Websites, Investor Presentation, Conference Call transcripts, Webinar, Journals, Regulators, National Customs and Industry Associations were given primary weight-age.
For Early Buyers | Get Up to 20% Discount on This Premium Report: https://www.advancemarketanalytics.com/request-discount/124705-global-application-security-testing-ast-software-market?utm_source=Organic&utm_medium=Vinay
What benefits does AMA research study is going to provide?
Latest industry influencing trends and development scenario
Open up New Markets
To Seize powerful market opportunities
Key decision in planning and to further expand market share
Identify Key Business Segments, Market proposition & Gap Analysis
Assisting in allocating marketing investments
Definitively, this report will give you an unmistakable perspective on every single reality of the market without a need to allude to some other research report or an information source. Our report will give all of you the realities about the past, present, and eventual fate of the concerned Market.
Thanks for reading this article; you can also get individual chapter wise section or region wise report version like North America, Europe or Southeast Asia.
Contact Us:
Craig Francis (PR & Marketing Manager) AMA Research & Media LLP Unit No. 429, Parsonage Road Edison, NJ New Jersey USA – 08837
0 notes
Link
0 notes
Link
The results are in! After 51 nominations whittled down to 15 finalists by a community vote, an expert panel consisting of Nicolas Grégoire, Soroush Dalili, Filedescriptor, and myself have conferred, voted, and selected the Top 10 new web hacking techniques of 2019. Every year, professional researchers, seasoned pentesters, bug bounty hunters and academics release a flood of blog posts, presentations, videos and whitepapers. Whether they're suggesting new attack techniques, remixing old ones, or documenting findings, many of these contain novel ideas that can be applied elsewhere. However, in these days of vulnerabilities arriving equipped with logos and marketing teams it's all too easy for innovative techniques and ideas to get missed in the noise, simply because they weren't broadcast loudly enough. That's why every year, we work with the community to seek out and enshrine ten techniques that we think will withstand the test of time. We regard these ten as the creme of the most innovative web security research published in the last year. Every entry contains insights for aspiring researchers, pentesters, bug bounty hunters, and anyone else interested in recent developments in web security. Community Favourite - HTTP Desync AttacksThe entry with the most community votes by a substantial margin was HTTP Desync Attacks, in which I revived the long forgotten technique of HTTP Request Smuggling to earn over $90k in bug bounties, compromise PayPal's login page twice, and kick off a wave of findings for the wider community. I regard this as my best research to date, but I made the tactical decision to exclude it from the official top 10 because there's no way I'm going to write a post that declares my own research the best. Moving swiftly on... 10. Exploiting Null Byte Buffer Overflow for a $40,000 bountyAt number 10 we have a fantastic heartbleed-style memory-safety exploit from Sam Curry and friends. This critical but easily-overlooked vulnerability almost certainly affects other websites, and serves us a reminder that even if you're an expert, there's still a place for simply fuzzing and keeping an eye out for anything unexpected. 9. Microsoft Edge (Chromium) - EoP to Potential RCE In this writeup, Abdulrhman Alqabandi uses a mixture of web and binary attacks to pwn anyone who makes the mistake of visiting his site using Microsoft's new Chromium-Powered Edge (aka Edgium). $40,000 in bounties later this is now patched, but it's still a sterling example of an exploit chain combining multiple low-severity vulnerabilities to achieve a critical impact, and also beautifully demonstrates how web vulnerabilities can bleed onto your desktop through privileged origins. It inspired us to update Hackability to detect when it's on a privileged origin by scanning the chrome object. For another look at web vulnerability chaos in the browser-chrome battleground, check out Remote Code Execution in Firefox beyond memory corruptions. 8. Infiltrating Corporate Intranet Like NSA: Pre-Auth RCE On Leading SSL VPNsThe incumbent winner Orange Tsai makes his first appearance alongside Meh Chang with multiple unauthenticated RCE vulnerabilities in SSL VPNs. The privileged, internet-exposed position VPNs typically sit in means that in terms of sheer impact, this is about as good as it gets. Although the techniques applied are largely classics, they use some creative twists that I won't spoil for you here. This research helped spawn a wave of audits targeting SSL VPNs, leading to numerous findings including a clutch of SonicWall vulnerabilities published last week. 7. Exploring CI Services as a Bug Bounty Hunter Modern websites are stitched together from numerous services reliant on secrets to identify each-other. When these get leaked, the web of trust can fall apart. Secrets leaking in Continuous Integration repositories/logs is a common occurrence, and finding them via automation is even more common. Yet this research by EdOverflow et al systematically sheds new light on overlooked cases and potential future research areas. It's also quite possibly the inspiration for the hilarious site/tool SSHGit. 6. All is XSS that comes to the .NETMonitoring novel research is a core part of my job, but I still managed to completely miss this post when it was first released. Fortunately, someone in the community had sharper eyes and nominated it. Paweł Hałdrzyński takes a little-known legacy feature of the .NET framework and shows how it can be used to add arbitrary content to URL paths on arbitrary endpoints, causing us some mild panic when we realised even our own website supported it. Reminiscent of Relative Path Overwrite attacks, this is a piece of arcana that can sometimes kick off an exploit chain. In the post it's used for XSS, but we strongly suspect alternative abuses will emerge in future. 5. Google Search XSSThe Google Search box is probably the most-tested input on the planet, so how Masato Kinugawa managed to XSS it was beyond comprehension, up until he revealed all via a collaboration with his colleague LiveOverflow. These two videos provide a solid introduction on how to find DOM parsing bugs by reading the docs and fuzzing, and also give a rare look into the creativity behind this magnificent exploit. 4. Abusing Meta Programming for Unauthenticated RCEOrange Tsai returns with a pre-auth RCE in Jenkins, described over two posts. The authentication bypass is nice, but our favourite innovation is the use of meta-programming to create a backdoor that executes at compile-time, in the face of numerous environmental constraints. We expect to see meta-programming again in future. It's also an excellent example of research continuation, as the exploit was subsequently improved by multiple researchers. 3. Owning The Clout Through Server Side Request ForgeryThis presentation from Ben Sadeghipour and Cody Brocious starts out with an overview of existing SSRF techniques, shows how they can be adapted and applied to server-side PDF generators, then brings DNS rebinding into the mix for good measure. The work targeting PDF generators is an insightful look into a feature-class that's all too easily ignored. We first saw DNS rebinding on server-side browsers appear on the 2018 nomination list, and the release of HTTPRebind should help make this attack more accessible than ever. Finally, I might be wrong about this but I suspect this presentation may deserve some credit for finally persuading Amazon to think about securing their EC2 metadata endpoint. 2. Cross-Site Leaks Cross-site leaks have been a long time coming. First documented over a decade ago, and creeping into our top 10 last year, it's in 2019 that awareness of this attack class and its sheer number of crazy variations exploded. It's hard to apportion credit at such a scale but we clearly owe thanks to Eduardo Vela's succinct introduction to the concept with a novel technique, the collaborative effort to build a public list of known XS-Leak vectors, and researchers applying the XS-Leaks technique to great effect. XS-Leaks have already had a lasting impact on the web security landscape, as they played a major role in the death of browser XSS filters. Block-mode XSS filtering was a major source of XS-Leak vectors, and this combined with even worse issues with filter-mode to persuade Edge and later Chrome to both discard their filters in a victory for web security and a disaster for web security researchers alike. 1. Cached and Confused: Web Cache Deception in the WildIn this academic whitepaper, Sajjad Arshad et al take Omer Gil's Web Cache Deception technique (which premiered at #2 in our top 10 back in 2017), and share a systematic exploration of Web Cache Deception vulnerabilities across the Alexa Top 5000 websites. For legal reasons, most offensive security research is conducted during professional audits or on websites with bug bounty programs, but through careful ethical footwork this research offers a glimpse into the state of security on the wider web. With the help of a well-crafted methodology that could easily be adapted for other techniques, they prove that Web Cache Deception is still a prevalent threat. Aside from the methodology, the other key innovation is the introduction of five novel path confusion techniques which expand the number of vulnerable websites. They also do a better job of documenting web-caching provider's caching behaviour than many providers themselves. Overall, this is a superb example of the community taking existing research in a new direction, and a well deserved number one! ConclusionWe saw a particularly strong set of nominations this year, so many excellent pieces of research didn't make it into the top 10. As such, I recommend checking out the full nomination list. For those interested in getting access to 2020 research as soon as it's released, we recently created the r/websecurityresearch subreddit and @PortSwiggerRes Twitter accounts to promote notable research. You can also find past year's top 10 lists here: 2018, 2017, 2015, 2014, 2013, 2012, 2011, 2010, 2009, 2008, 2007, 2006. Year after year we see great research comes from building on other people's ideas, so we'd like to thank everyone who takes the time to publish their findings, whether nominated or not. Finally, we'd like to thank the wider community for your enthusiastic participation. Without your nominations and votes, this wouldn't be possible. Till next year!
0 notes
Photo

PortSwigger Software Products Resellers
Burp Suite by PortSwigger Web Security is an integrated platform for performing security testing of web applications
Thousands of organizations use Burp Suite to find security exposures before it’s too late. By using cutting-edge scanning technology, you can identify the very latest vulnerabilities. Our researchers frequently uncover brand new vulnerability classes that Burp is the first to report.
1 note
·
View note
Text
[Media] param-miner
param-miner This extension identifies hidden, unlinked parameters. It's particularly useful for finding web cache poisoning vulnerabilities. https://github.com/PortSwigger/param-miner
YouTubeHow to use Param Miner to detect fat GET cache poisoningJames Kettle (PortSwigger's Director of Research) explains how to use Param Miner to detect fat GET cache poisoning vulnerabilities within Burp Suite. This has been documented in James's recent Web Cache Entanglement research, presented at Black Hat USA 2020. Get Param Miner on GitHub: https://github.com/PortSwigger/param-miner Read the full research: https://portswigger.net/research/web-cache-entanglement

0 notes
Text
Security experts are laying Mastodon's flaws bare
Security experts are laying Mastodon’s flaws bare
The rising recognition of Mastodon, partly as a side-effect of Elon Musk shopping for Twitter, has triggered a wave of vulnerability discoveries within the app. Cybersecurity researchers utilizing the platform not too long ago found three separate vulnerabilities that would permit menace actors to tamper with the information, and even obtain it. For instance, a researcher at PortSwigger, Gareth…
View On WordPress
0 notes
Text
Dynamic Application Security Testing Market:2027 Size, Opportunities, Company Profile, Developments
Dynamic Application Security Testing
Dynamic Application Security Testing Market
The qualitative and quantitative parts of an in-depth primary and secondary study on the Dynamic Application Security Testing market are both important. The research offers a trustworthy market share analysis that reveals subtle business patterns and sophisticated operational models, as well as an evaluation of business development strategies, advanced supply chain systems, innovative sales and marketing approaches, and product/project development. The research also calculates the actual industry valuation, as well as market share and size parameters at the global and country levels. The Dynamic Application Security Testing market forecast included in the study illustrates possible market sizes and projected market share, as well as expected growth forecasts.
Key players:
• Accenture • IBM • Micro Focus • Veracode • Synopsys • Pradeo • Rapid7 • Tieto • Trustwave • WhiteHat Security • Hewlett Packard Enterprise • Acunetix • Cigital • Checkmarx Inc. • Qualys, Inc. • PortSwigger
Request for free sample:
https://www.maximizemarketresearch.com/request-sample/13020/
Dynamic Application Security Testing market Segmentation:
Global Dynamic Application Security Testing Market, by Type
• Solution • Service
Global Dynamic Application Security Testing Market, by Application
• Web Application Security • Mobile Application Security
Global Dynamic Application Security Testing Market, by Deployment Mode
• On-Premises • Cloud
Global Dynamic Application Security Testing Market, by organization size
• SMEs • Large Enterprises
Global Dynamic Application Security Testing Market, by Vertical
• Government & Defense • BFSI • IT & Telecom • Healthcare • Retail
***
The qualitative components of the Dynamic Application Security Testing market research piece include market drivers, restraints, major trends, opportunities, and challenges. The most crucial variables increasing the opportunistic landscape of the Dynamic Application Security Testing market are correctly enlisted in a complete analysis of the market drivers. The ability to accurately categorize market drivers and restraints allows for a clear demarcation of growth stimulators and inhibitors, giving clients simply digestible and important information. The study examines the important trends that are driving the Dynamic Application Security Testing market's growth and development throughout the projected period, both current and emerging.
The COVID-19 impact analysis is a section of the global Dynamic Application Security Testing market research report that is mostly summarised. The research article explains the disruptions caused when an unprepared industrial environment was exposed to a brutal crisis that effectively swept away business dynamics all over the world, obstructing distribution networks and supply chains with the consistently implemented lockdown regulations imposed to stop the pandemic from spreading. With limited production capacity and the remaining population already fighting an unknown biological entity, the global Dynamic Application Security Testing market was negatively damaged, with a precipitous reduction in demand for products and financial capabilities exposed to the unstable infrastructure.
Get Report Details:
https://www.maximizemarketresearch.com/market-report/dynamic-application-security-testing-market/13020/
The purpose of the global Dynamic Application Security Testing market study is to provide vital information on industry deliverables including market size, valuation projections, and sales volume. The Dynamic Application Security Testing research provides product information as well as benefits for readers looking to expand their business opportunities and increase their annual growth rate over time. Similarly, the study identifies different potential possibilities for the Dynamic Application Security Testing market in the next years. It's calculated how much money the market's sales bring in. This report also includes information on all of the regions and nations, as well as regional growth statistics such as volume, market size, and value, as well as pricing information.
Contact us:
MAXIMIZE MARKET RESEARCH PVT. LTD.
3rd Floor, Navale IT park Phase 2,
Pune Banglore Highway,
Narhe,Pune, Maharashtra 411041, India.
Email: [email protected]
Phone No.: +91 20 6630 3320
0 notes
Text
Application Security Testing (AST) EUROPE Market Research Report 2021-2026
The Application Security Testing (AST) Tools market report provides a detailed analysis of global market size, regional and country-level market size, segmentation market growth, market share, competitive Landscape, sales analysis, impact of domestic and global market players, value chain optimization, trade regulations, recent developments, opportunities analysis, strategic market growth analysis, product launches, area marketplace expanding, and technological innovations.
ALSO READ: http://www.marketwatch.com/story/application-security-testing-ast-market-research-report-with-size-share-value-cagr-outlook-analysis-latest-updates-data-and-news-2021-2021-07-19
According to our latest research, the global Application Security Testing (AST) Tools size is estimated to be USD xx million in 2026 from USD xx million in 2020, with a change XX% between 2020 and 2021. The global Application Security Testing (AST) Tools market size is expected to grow at a CAGR of xx% for the next five years.
Market segmentation Application Security Testing (AST) Tools market is split by Type and by Application. For the period 2016-2026, the growth among segments provide accurate calculations and forecasts for revenue by Type and by Application. This analysis can help you expand your business by targeting qualified niche markets.
Market segment by Type, covers Cloud Based On-premises
Market segment by Application, can be divided into SMEs Large Enterprises
ALSO READ: http://www.marketwatch.com/story/carbon-black-market-research-report-with-size-share-value-cagr-outlook-analysis-latest-updates-data-and-news-2020-2026-2021-06-22
Market segment by players, this report covers Veracode Checkmarx PortSwigger Micro Focus WhiteHat Security Qualys Acunetix Contrast Security Netsparker Rapid7 HCL Technologies GitLab Synopsys ImmuniWeb GitHub WhiteSource Edgescan CAST GrammaTech
ALSO READ: http://www.marketwatch.com/story/diet-shake-market-research-report-with-size-share-value-cagr-outlook-analysis-latest-updates-data-and-news-2021-2028-2021-06-21
Market segment by regions, regional analysis covers North America (United States, Canada, and Mexico) Europe (Germany, France, UK, Russia, Italy, and Rest of Europe) Asia-Pacific (China, Japan, South Korea, India, Southeast Asia, Australia, and Rest of Asia-Pacific) South America (Brazil, Argentina, Rest of South America) Middle East & Africa (Turkey, Saudi Arabia, UAE, Rest of Middle East & Africa)
The content of the study subjects, includes a total of 12 chapters: Chapter 1, to describe Application Security Testing (AST) Tools product scope, market overview, market opportunities, market driving force and market risks. Chapter 2, to profile the top players of Application Security Testing (AST) Tools, with revenue, gross margin and global market share of Application Security Testing (AST) Tools from 2019 to 2021. Chapter 3, the Application Security Testing (AST) Tools competitive situation, revenue and global market share of top players are analyzed emphatically by landscape contrast. Chapter 4 and 5, to segment the market size by type and application, with revenue and growth rate by type, application, from 2016 to 2026. Chapter 6, 7, 8, 9, and 10, to break the market size data at the country level, with revenue and market share for key countries in the world, from 2016 to 2021.and Application Security Testing (AST) Tools market forecast, by regions, type and application, with revenue, from 2021 to 2026. Chapter 11 and 12, to describe Application Security Testing (AST) Tools research findings and conclusion, appendix and data source.
ALSO READ: http://www.marketwatch.com/story/retrievable-bridge-plug-market-research-report-with-size-share-value-cagr-outlook-analysis-latest-updates-data-and-news-forecast-year-2021-06-23
Table of Contents
1 Market Overview 1.1 Product Overview and Scope of Application Security Testing (AST) Tools 1.2 Classification of Application Security Testing (AST) Tools by Type 1.2.1 Overview: Global Application Security Testing (AST) Tools Market Size by Type: 2020 Versus 2021 Versus 2026 1.2.2 Global Application Security Testing (AST) Tools Revenue Market Share by Type in 2020 1.2.3 Cloud Based 1.2.4 On-premises 1.3 Global Application Security Testing (AST) Tools Market by Application 1.3.1 Overview: Global Application Security Testing (AST) Tools Market Size by Application: 2020 Versus 2021 Versus 2026 1.3.2 SMEs 1.3.3 Large Enterprises 1.4 Global Application Security Testing (AST) Tools Market Size & Forecast 1.5 Global Application Security Testing (AST) Tools Market Size and Forecast by Region 1.5.1 Global Application Security Testing (AST) Tools Market Size by Region: 2016 VS 2021 VS 2026 1.5.2 Global Application Security Testing (AST) Tools Market Size by Region, (2016-2021) 1.5.3 North America Application Security Testing (AST) Tools Market Size and Prospect (2016-2026) 1.5.4 Europe Application Security Testing (AST) Tools Market Size and Prospect (2016-2026) 1.5.5 Asia-Pacific Application Security Testing (AST) Tools Market Size and Prospect (2016-2026) 1.5.6 South America Application Security Testing (AST) Tools Market Size and Prospect (2016-2026) 1.5.7 Middle East and Africa Application Security Testing (AST) Tools Market Size and Prospect (2016-2026) 1.6 Market Drivers, Restraints and Trends 1.6.1 Application Security Testing (AST) Tools Market Drivers 1.6.2 Application Security Testing (AST) Tools Market Restraints 1.6.3 Application Security Testing (AST) Tools Trends Analysis
ALSO READ: http://www.marketwatch.com/story/electromagnetic-surgical-navigation-system-market-research-report-with-size-share-value-cagr-outlook-analysis-latest-updates-data-and-news-2021-2028-2021-06-24
2 Company Profiles 2.1 Veracode 2.1.1 Veracode Details 2.1.2 Veracode Major Business 2.1.3 Veracode Application Security Testing (AST) Tools Product and Solutions 2.1.4 Veracode Application Security Testing (AST) Tools Revenue, Gross Margin and Market Share (2019-2021) 2.1.5 Veracode Recent Developments and Future Plans 2.2 Checkmarx 2.2.1 Checkmarx Details 2.2.2 Checkmarx Major Business 2.2.3 Checkmarx Application Security Testing (AST) Tools Product and Solutions 2.2.4 Checkmarx Application Security Testing (AST) Tools Revenue, Gross Margin and Market Share (2019-2021) 2.2.5 Checkmarx Recent Developments and Future Plans 2.3 PortSwigger 2.3.1 PortSwigger Details 2.3.2 PortSwigger Major Business 2.3.3 PortSwigger Application Security Testing (AST) Tools Product and Solutions 2.3.4 PortSwigger Application Security Testing (AST) Tools Revenue, Gross Margin and Market Share (2019-2021) 2.3.5 PortSwigger Recent Developments and Future Plans 2.4 Micro Focus 2.4.1 Micro Focus Details 2.4.2 Micro Focus Major Business 2.4.3 Micro Focus Application Security Testing (AST) Tools Product and Solutions 2.4.4 Micro Focus Application Security Testing (AST) Tools Revenue, Gross Margin and Market Share (2019-2021) 2.4.5 Micro Focus Recent Developments and Future Plans 2.5 WhiteHat Security 2.5.1 WhiteHat Security Details 2.5.2 WhiteHat Security Major Business 2.5.3 WhiteHat Security Application Security Testing (AST) Tools Product and Solutions 2.5.4 WhiteHat Security Application Security Testing (AST) Tools Revenue, Gross Margin and Market Share (2019-2021) 2.5.5 WhiteHat Security Recent Developments and Future Plans 2.6 Qualys 2.6.1 Qualys Details 2.6.2 Qualys Major Business 2.6.3 Qualys Application Security Testing (AST) Tools Product and Solutions 2.6.4 Qualys Application Security Testing (AST) Tools Revenue, Gross Margin and Market Share (2019-2021) 2.6.5 Qualys Recent Developments and Future Plans 2.7 Acunetix 2.7.1 Acunetix Details 2.7.2 Acunetix Major Business 2.7.3 Acunetix Application Security Testing (AST) Tools Product and Solutions 2.7.4 Acunetix Application Security Testing (AST) Tools Revenue, Gross Margin and Market Share (2019-2021) 2.7.5 Acunetix Recent Developments and Future Plans 2.8 Contrast Security 2.8.1 Contrast Security Details 2.8.2 Contrast Security Major Business 2.8.3 Contrast Security Application Security Testing (AST) Tools Product and Solutions 2.8.4 Contrast Security Application Security Testing (AST) Tools Revenue, Gross Margin and Market Share (2019-2021) 2.8.5 Contrast Security Recent Developments and Future Plans 2.9 Netsparker 2.9.1 Netsparker Details 2.9.2 Netsparker Major Business 2.9.3 Netsparker Application Security Testing (AST) Tools Product and Solutions 2.9.4 Netsparker Application Security Testing (AST) Tools Revenue, Gross Margin and Market Share (2019-2021) 2.9.5 Netsparker Recent Developments and Future Plans 2.10 Rapid7 2.10.1 Rapid7 Details 2.10.2 Rapid7 Major Business 2.10.3 Rapid7 Application Security Testing (AST) Tools Product and Solutions 2.10.4 Rapid7 Application Security Testing (AST) Tools Revenue, Gross Margin and Market Share (2019-2021) 2.10.5 Rapid7 Recent Developments and Future Plans 2.11 HCL Technologies 2.11.1 HCL Technologies Details 2.11.2 HCL Technologies Major Business 2.11.3 HCL Technologies Application Security Testing (AST) Tools Product and Solutions 2.11.4 HCL Technologies Application Security Testing (AST) Tools Revenue, Gross Margin and Market Share (2019-2021) 2.11.5 HCL Technologies Recent Developments and Future Plans
….CONTINUED
CONTACT DETAILS :
+44 203 500 2763
+1 62 825 80070
971 0503084105
0 notes
Link
[Updated Report] Press Release, August 01, 2023 (Orbis Research) - The Global Cybersecurity, Red Tea
0 notes
Text
Top 10 vulnerability scanners

Before discussing the top vulnerability scanners that organizations are using, we will first discuss why vulnerability scanners are required to any organization, which vulnerability scanner suits their requirements?
A vulnerability scanner is an automated tool that allows an organization to identify if its public-facing applications, network, systems pose any security risk that could expose them to attack. It is common practice that an organization should follow and often required by industry guidelines and government regulations to enhance the organization's security posture.
The vulnerability scanner uses a database of known vulnerabilities, coding bugs, flawed default configuration, potential paths to sensitive data and uses it to compare the target attack surface. After performing automated web application vulnerability scan, network scan, and identifying possible vulnerabilities in any devices within the scope of the engagement, the scan generates a report. The findings in the report can then be analyzed and interpreted to identify opportunities for an organization to improve security posture.
PortSwigger Burp Suite
Most trusted and highly used software by more than 13000 organizations worldwide and personal favorite tool of pen testers. Burp Suite is a centralized toolset for web application penetration testing. It acts as a middle entity between client and server to intercept traffic and allows to modify and automate changes to webpage requests. It has the great feature of scanning, identify vulnerabilities using extensions, decoding hashes, brute-forcing.

Probely
Probely is a developer-friendly vulnerability scanning tool, it allows to scan source code of web application in the early stage of development. It scans web applications to identify vulnerabilities, reports real vulnerabilities, and provides tailored instructions on how to fix vulnerabilities. It also provides solutions for microservices and standalone APIs, also achieves compliance by showing specific reports with requirements for PCI-DSS, ISO27001,HIPAA, and GDPR.

UpGuard
UpGuard provides security solutions using a combination of third-party security ratings, vendor questionnaires, and threat intelligence scanning to help organizations reduce their risk. Understand security posture of an organization, discover web application vulnerabilities, check for third party misconfiguration, identifies if there was any security breach or data exposure to unauthorized parties, provides remediation for risks, represent risks with severity graphically using a template, save time by proactively and securely sharing security information in one place.

Tenable Nessus
Tenable Nessus is trusted by more than 30,000 organizations worldwide and ranks first in vulnerability assessment for accuracy and coverage. Works in a real-time environment, plugins are automatically updated, new CVEs are added to the database. Provides comprehensive solutions for malware detection, network scan, compliance and audit, rich reporting feature i.e., customize by the host or by the plugin. Focuses on more comprehensive assessments and less time required to research, validate, and prioritize issues.

Detectify
Detectify deeply scans web applications and monitors assets in infrastructure. Not only focuses on well-known vulnerabilities, third-party misconfigurations, DNS flaws but also focuses on undocumented flaws. Organizations integrate this tool at the very first phase of SDLC. Monitors the application throughout the SDLC, give an alert when vulnerabilities are detected.

Acunetix Web Vulnerability Scanner
Acunetix offers vulnerability assessment and management for a web application, integration of third-party issue trackers such as Jira, GitLab, GitHub, TFS, Bugzilla, and Mantis. In addition to web application vulnerability scan, Acunetix provides network security solutions, protection to key assets, discover malware, misconfigurations in the webserver.

Netsparker
Netsparker comprehensively craws and scans the application to identify vulnerabilities in web applications and services such as API, dedicated JavaScript engines for a single page, and also capable of performing database servers that may pose threat to the security of an organization. Vulnerabilities are reported in a testing environment to reduce the count of false positives and identify only real threats. Organizations can schedule future scans, integrate with the current system such as GitHub, Jenkins, okta, slack, GitLab, circleci.

Qualys Web Application Scanner
Qualys is a cloud-based, on-premises solution, easy to deploy and manage.Capable of performing web application penetration testing and API security testing, provide a fix for them. Performs deep scan to identify OWASP TOP 10 risks, test IoT services, and mobile apps, detect malware. Hardens web application security with integrated web application firewall.

Rapid7 insightAppSec
InsightAppSec is a comprehensive vulnerability assessment tool by Rapid7. Understands application’s component, formats, protocols, and development technologies, test for more than 95 attacks including OWASP TOP 10 and an attack replay that developers can use to reproduce a scan to confirm vulnerabilities are real. Export findings in interactive HTML formats, compliance-specific report templates provide immediate understanding of the compliance risk. Schedule scans, cloud and on-premises scans are the key features.

HCL AppScan
HCL AppScan, previously known as IBM AppScan. AppScan offers DAST solutions to effectively identify, remediate web application vulnerability, and achieve regulatory compliance. Provide collaboration to developer and security team, powerful analytics prioritize scan results to minimize false positives. Effective Reporting with CVSS score, providing remediation to high severity vulnerabilities are the key features.

0 notes
Text
Penetration Testing Market Research Report
Penetration Testing Market:
Growth opportunities in the penetration testing market look promising over the next six years. This is mainly due to the growing adoption of cloud computing solutions and services, rising usage of cloud-based solutions and services, increase in implementation of security measures, and rise in mobile-based business-critical applications.
Request for a FREE Sample Report on Penetration Testing Market.
Penetration Testing Market Dynamics (including market size, share, trends, forecast, growth, forecast, and industry analysis)
Key Drivers
The factors supporting the growth of the global penetration market include the remarkable increase in mobile-based business applications, surge in the execution of security measures, and the augmenting adoption of cloud-computing business and services. Businesses throughout the world are switching to cloud computing solutions owing to the cost-effectiveness offered by them. The rising use of cloud-based solutions, including the e-mail services, CRM, data backups, and collaboration services for penetration of workload, boosts the demand for penetration testing.
Cloud deployment uplifts the vulnerabilities in software, making it easily available for unauthorized users. Furthermore, the hacking groups target leading corporations which contribute to the expanding awareness of cyber threats, as data breach results revenue loss. Owing to this, many organizations are arranging cybersecurity solutions such as intrusion detection, firewalls, and penetration testing to help secure workload on the cloud without the risk of cyber threats. However, the high cost associated with penetration testing and lack of skilled security analysts will restrain the market's growth.
Deployment mode Segment Drivers
Based on deployment mode, the market is segmented into on-premises and cloud. The Cloud segment is expected to grow at a higher CAGR over the forecast period as it helps the organization to reduce costs concerned with the hiring of technical staff and infrastructural maintenance. Also, SMEs are more prompt to adopt cloud-based deployment mode as it aids them in reducing the overall cost of security infrastructure.
Regional Drivers
On the basis of region, North America is anticipated to grow at a faster CAGR over the forecast period attributed to the rising focus of leading players towards technical advancements and development. Moreover, the accelerating adoption of smartphones and digital transformation in industries is fuelling the growth of the penetration testing market in the region. On the other hand, Asia-Pacific is predicted to expand at a high CAGR during the forecast period owing to the augmenting number of cyber frauds faced by citizens and businesses. Developing countries such as India and Japan have begun with penetration testing across BFSI, defense, healthcare, and government verticals.
Penetration Testing Market’s leading Manufacturers:
· PortSwigger Web Security
· Qualys Inc.
· Netsparker
· Cigital Inc
· Micro Focus International Plc
· FireEye
· Context Information Security
· Core Security Technologies
· Secureworks Inc
· IBM Corporation
Penetration Testing Market Segmentation:
Segmentation by Component:
· Solutions
· Services
Segmentation by Application Area:
· Web application
· Mobile application
· Network infrastructure
· Social Engineering
· Cloud
· Others (Embedded and IoT)
Segmentation by Deployment Mode:
· Cloud
· On-premises
Segmentation by Organisation Size:
· Large enterprises
· Small and Medium-sized Enterprises (SMEs)
Segmentation by Industry:
· Banking, Financial Services and Insurance (BFSI)
· Healthcare
· Information Technology (IT)
· Telecom
· Retail and eCommerce
· Education
· Others (transportation, energy, and social media)
Segmentation by Region:
· North America
o United States of America
o Canada
· Asia Pacific
o China
o Japan
o India
o Rest of APAC
· Europe
o United Kingdom
o Germany
o France
o Spain
o Rest of Europe
· RoW
o Brazil
o South Africa
o Saudi Arabia
o UAE
o Rest of the world (remaining countries of the LAMEA region)
About GMI Research
GMI Research is a market research and consulting company that offers business insights and market research reports for large and small & medium enterprises. Our detailed reports help the clients to make strategic business policies and achieve sustainable growth in the particular market domain. The company's large team of seasoned analysts and industry experts with experience from different regions such as Asia-Pacific, Europe, North America, among others, provides a one-stop solution for the client. Our market research report has in-depth analysis, which includes refined forecasts, a bird's eye view of the competitive landscape, key factors influencing the market growth, and various other market insights to aid companies in making strategic decisions. Featured in the 'Top 20 Most Promising Market Research Consultants' list of Silicon India Magazine in 2018, we at GMI Research are always looking forward to helping our clients to stay ahead of the curve.
Media Contact Company Name: GMI RESEARCH Contact Person: Sarah Nash Email: [email protected] Phone: Europe – +353 1 442 8820; US – +1 860 881 2270 Address: Dublin, Ireland Website: www.gmiresearch.com
0 notes
Text
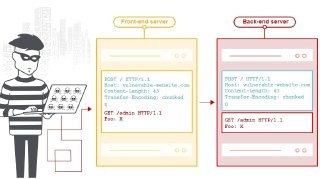
[Media] HTTP Request Smuggler
HTTP Request Smuggler This is an extension for Burp Suite designed to help you launch HTTP Request Smuggling attacks, originally created during HTTP Desync Attacks research. It supports scanning for Request Smuggling vulnerabilities, and also aids exploitation by handling cumbersome offset-tweaking for you. This extension should not be confused with Burp Suite HTTP Smuggler, which uses similar techniques but is focused exclusively bypassing WAFs. https://github.com/portswigger/http-request-smuggler
0 notes
Text
Brave Privacy Bug Exposed Tor Onion URLs To Your DNS Provider
Brave Browser had a privacy issue that leaked the Tor onion URL addresses you visited to your locally configured DNS server, "exposing the dark web websites you visit...", writes Bleeping Computer. Long-time Slashdot reader AmiMoJo quotes their report: To access Tor onion URLs, Brave added a "Private Window with Tor" mode that acts as a proxy to the Tor network. When you attempt to connect to an onion URL, your request is proxied through volunteer-run Tor nodes who make the request for you and send back the returned HTML. Due to this proxy implementation, Brave's Tor mode does not directly provide the same level of privacy as using the Tor Browser. When using Brave's Tor mode, it should forward all requests to the Tor proxies and not send any information to any non-Tor Internet devices to increase privacy. However, a bug in Brave's "Private window with Tor" mode is causing the onion URL for any Tor address you visit to also be sent as a standard DNS query to your machine's configured DNS server. This bug was first reported in a Reddit post and later confirmed by James Kettle, the Director of Research at PortSwigger. BleepingComputer has also verified the claims by using Wireshark to view DNS traffic while using Brave's Tor mode. Brave has since released an update which fixes the bug.


Read more of this story at Slashdot.
from Slashdot https://ift.tt/3kGGuaZ
0 notes
Text
0 notes
Link
Burp or Burp Suite is a set of tools used for penetration testing of web applications. It is developed by the company named Portswigger, which is also the alias of its founder Dafydd Stuttard. BurpSuite aims to be an all in one set of tools and its capabilities can be enhanced by installing add-ons that are called BApps.
It is the most popular tool among professional web app security researchers and bug bounty hunters. Its ease of use makes it a more suitable choice over free alternatives like OWASP ZAP. Burp Suite is available as a community edition which is free, professional edition that costs $399/year and an enterprise edition that costs $3999/Year. This article gives a brief introduction to the tools offered by BurpSuite. If you are a complete beginner in Web Application Pentest/Web App Hacking/Bug Bounty, we would recommend you to just read through without thinking too much about a term.
The tools offered by BurpSuite are:
1. Spider:

It is a web spider/crawler that is used to map the target web application. The objective of the mapping is to get a list of endpoints so that their functionality can be observed and potential vulnerabilities can be found. Spidering is done for a simple reason that the more endpoints you gather during your recon process, the more attack surfaces you possess during your actual testing.
2. Proxy:

BurpSuite contains an intercepting proxy that lets the user see and modify the contents of requests and responses while they are in transit. It also lets the user send the request/response under monitoring to another relevant tool in BurpSuite, removing the burden of copy-paste. The proxy server can be adjusted to run on a specific loop-back ip and a port. The proxy can also be configured to filter out specific types of request-response pairs.
3. Intruder:

It is a fuzzer. This is used to run a set of values through an input point. The values are run and the output is observed for success/failure and content length. Usually, an anomaly results in a change in response code or content length of the response. BurpSuite allows brute-force, dictionary file and single values for its payload position. The intruder is used for:
Brute-force attacks on password forms, pin forms, and other such forms.
The dictionary attack on password forms, fields that are suspected of being vulnerable to XSS or SQL injection.
Testing and attacking rate limiting on the web-app.
(adsbygoogle = window.adsbygoogle || []).push({});
4. Repeater:

Repeater lets a user send requests repeatedly with manual modifications. It is used for:
Verifying whether the user-supplied values are being verified.
If user-supplied values are being verified, how well is it being done?
What values is the server expecting in an input parameter/request header?
How does the server handle unexpected values?
Is input sanitation being applied by the server?
How well the server sanitizes the user-supplied inputs?
What is the sanitation style being used by the server?
Among all the cookies present, which one is the actual session cookie.
How is CSRF protection being implemented and if there is a way to bypass it?
(adsbygoogle = window.adsbygoogle || []).push({});
5. Sequencer:

The sequencer is an entropy checker that checks for the randomness of tokens generated by the webserver. These tokens are generally used for authentication in sensitive operations: cookies and anti-CSRF tokens are examples of such tokens. Ideally, these tokens must be generated in a fully random manner so that the probability of appearance of each possible character at a position is distributed uniformly. This should be achieved both bit-wise and character-wise. An entropy analyzer tests this hypothesis for being true. It works like this: initially, it is assumed that the tokens are random. Then the tokens are tested on certain parameters for certain characteristics. A term significance level is defined as a minimum value of probability that the token will exhibit for a characteristic, such that if the token has a characteristics probability below significance level, the hypothesis that the token is random will be rejected. This tool can be used to find out the weak tokens and enumerate their construction.
6. Decoder:

Decoder lists the common encoding methods like URL, HTML, Base64, Hex, etc. This tool comes handy when looking for chunks of data in values of parameters or headers. It is also used for payload construction for various vulnerability classes. It is used to uncover primary cases of IDOR and session hijacking.
(adsbygoogle = window.adsbygoogle || []).push({});
7. Extender:


BurpSuite supports external components to be integrated into the tools suite to enhance its capabilities. These external components are called BApps. These work just like browser extensions. These can be viewed, modified, installed, uninstalled in the Extender window. Some of them are supported on the community version, but some require the paid professional version.
8. Scanner:
The scanner is not available in the community edition. It scans the website automatically for many common vulnerabilities and lists them with information on confidence over each finding and their complexity of exploitation. It is updated regularly to include new and less known vulnerabilities.
0 notes
Text
Global Dynamic Application Security Testing Market
Global Dynamic Application Security Testing Market is expected to reach US$ XX Mn by 2026 at a CAGR of XX% during the forecast period. A dynamic application security testing provides a security solution that helps in identifying susceptibilities in web and mobile applications. In some cases, dynamic testing is referred to as black-box testing which finds defects in the applications without considering the internal structure of the program which is an added advantage. Dynamic application security testing solutions analyze application recital when subjected to web attacks for finding the susceptibility.
Dynamic application security characteristics are incorporating security testing into the developed strategy, enhancing security with cognitive capabilities, managing, and reducing risks in the application portfolio among many others. The report study has analyzed revenue impact of covid-19 pandemic on the sales revenue of market leaders, market followers and disrupters in the report and same is reflected in our analysis. The dynamic application security testing market includes application security in the early phase of adoption requiring more awareness and enterprises facing budget constraints are the restraining factors that could affect the growth of the market.
The increasing extent of business risks due to application vulnerabilities, stringent government regulations, increasing sophistication level of cyber-attacks, and growing adoption of third-party applications are expected to drive the growth of the market around the world. According to the verticals, Banking, Financial Services, and Insurance (BFSI) verticals are expected to have the largest market size during the forecast period, as it is quickly implementing digital technologies in its ecosystem for enhancing the customer experience. The technological advancements in the vertical attract cybercriminals and cyber-attacks. By the type segment, the market is divided into a solution and service segment. From these, the solutions segment is expected to have a larger market size during the forecast period, thanks to increased sophistication levels of threats.
Cyber-attackers do various attacks, such as spear phishing, ransomware, and zero-day attacks, to gain access to critical information. In terms of the applications, Web application security is likely to hold the largest dynamic application security testing market share during the forecast period. Web application security ensures the security of web-based applications by an extenuating insider as well as outsider threats using testing techniques. This security testing technique covers areas, such as configuration errors, checking for vulnerabilities, identifying the loopholes in server codes or scripts, and minimizing risks and enticements for cyber-attacks.
While using the deployment model, the On-premises deployment mode is expected to have a larger market size during the forecast period, as it provides organizations with full control over their platforms, applications, systems, and data. Based on the organization segment is divided into SMEs and large enterprises. The large enterprise's segment is expected to have a large market size during the forecast period, as it increases focus on reducing Capital Expenditure (CAPEX) and Operating Expenditure (OPEX). Large enterprises have enthusiastic in-house IT resources and larger IT budgets to consider the embracing of the as-a-service model for their business processes. Region-wise, North America is expected to have the largest market size, as it contains top dynamic application security testing service providers and the high adoption rate of security solutions.
The objective of the report is to present a comprehensive analysis of the Global Dynamic Application Security Testing Market including all the stakeholders of the industry. The past and current status of the industry with forecasted market size and trends are presented in the report with the analysis of complicated data in simple language. The report covers all the aspects of the industry with a dedicated study of key players that includes market leaders, followers and new entrants by Region. PORTER, SVOR, PESTEL analysis with the potential impact of micro-economic factors by Region on the market have been presented in the report.
External as well as internal factors that are supposed to affect the business positively or negatively have been analyzed, which will give a clear futuristic view of the industry to the decision-makers. The report also helps in understanding Global Dynamic Application Security Testing Market dynamics, structure by analyzing the market segments and project the Global Dynamic Application Security Testing Market size. Clear representation of competitive analysis of key players by Type, price, financial position, Product portfolio, growth strategies, and regional presence in the Global Dynamic Application Security Testing Market make the report investor’s guide.
For more information visit@ https://www.maximizemarketresearch.com/market-report/dynamic-application-security-testing-market/13020/
Scope of the Global Dynamic Application Security Testing Market
Global Dynamic application security testing market, by Type
• Solution • Service
Global Dynamic application security testing market, by Application
• Web Application Security • Mobile Application Security
Global Dynamic application security testing market, by Deployment Mode
• On-Premises • Cloud
Global Dynamic application security testing market, by organization size
• SMEs • Large Enterprises
Global Dynamic application security testing market, by Vertical
• Government & Defense • BFSI • IT & Telecom • Healthcare • Retail • Manufacturing • Others
Global Dynamic application security testing market,by Region
• North America • Europe • APAC • MEA • Latin America
Key Players of Global Dynamic Application Security Testing Market
• Accenture • IBM • Micro Focus • Veracode • Synopsys • Pradeo • Rapid7 • Tieto • Trustwave • WhiteHat Security • Hewlett Packard Enterprise • Acunetix • Cigital • Checkmarx Inc. • Qualys, Inc. • PortSwigger • CA Technologies
This report submitted by Maximize market Research Company
Customization of the report:
Maximize Market Research provides free personalized of reports as per your demand. This report can be personalized to meet your requirements. Get in touch with us and our sales team will guarantee provide you to get a report that suits your necessities.
About Maximize Market Research:
Maximize Market Research provides B2B and B2C research on 20,000 high growth emerging opportunities & technologies as well as threats to the companies across the Healthcare, Pharmaceuticals, Electronics & Communications, Internet of Things, Food and Beverages, Aerospace and Defense and other manufacturing sectors.
Contact info:
Name: Lumawant Godage
Organization Address: MAXIMIZE MARKET RESEARCH PVT. LTD.
Email: [email protected]
Address: Omkar Heights, Sinhagad Road, Manik Baug, Vadgaon Bk,Pune, Maharashtra 411051, India.
Contact: +919607195908
0 notes