#RBAC
Explore tagged Tumblr posts
Text
Kubernetes RBAC Best Practices for Secure Identity Management
Role-Based Access Control (RBAC) is a crucial aspect of securing your Kubernetes cluster. In this article, we'll explore the best practices for implementing RBAC in your Kubernetes cluster. At IAMDevBox.com, we understand the importance of secure identity management and will guide you through the process. RBAC is a mechanism for controlling access to cluster resources by assigning roles to users or service accounts. This allows you to define a set of permissions for a role, and then assign that role to a user or service account. This way, you can ensure that only authorized users or service accounts have access to sensitive resources. To implement RBAC in your Kubernetes cluster, you'll need to create a set of roles and bind them to users or service accounts. You can use the `kubectl create role` and `kubectl create rolebinding` commands to achieve this. For example, you can create a role that allows access to a specific namespace, and then bind that role to a user or service account. Read more: Kubernetes RBAC Best Practices for Secure Identity Management
0 notes
Text

#CloudSecurity#SecureAccess#DataPrivacy#RBAC#Encryption#CloudCompliance#ProphecyTechs#EnterpriseSecurity#CloudSolutions#DigitalTrust
0 notes
Text
🔐 Authentication and Identity Management in Red Hat OpenShift Administration III
In today's hybrid and multi-cloud environments, enterprise IT teams must deliver secure, scalable applications without slowing down development. Red Hat OpenShift Administration III focuses on advanced administration tasks like scaling, securing, and managing OpenShift clusters—one of the most critical being Authentication and Identity Management.
Let’s explore how OpenShift handles enterprise-level user access and identity control—without diving into code.
🧩 Why Authentication & Identity Management Matter in OpenShift
In an enterprise setting, OpenShift serves thousands of users—from developers and testers to platform engineers and administrators. As the number of users and applications grows, the platform must:
Authenticate users securely
Integrate with enterprise identity systems
Apply consistent access policies
Support multi-tenancy
Comply with security and audit requirements
Authentication and identity management are not just about login screens—they’re central to security, compliance, and smooth collaboration.
🛠️ Built-In Support for Enterprise Identity Providers
OpenShift natively supports integration with a variety of identity providers, making it adaptable to your enterprise’s existing infrastructure. These include:
LDAP and Active Directory
OAuth-based providers (GitHub, Google, GitLab, etc.)
SAML providers for Single Sign-On (SSO)
Red Hat Identity Management (IdM)
Admins can configure these integrations from the OpenShift web console, mapping roles and groups without ever touching the command line.
🔒 Role-Based Access Control (RBAC)
Once users are authenticated, OpenShift uses Role-Based Access Control (RBAC) to define what users can do. Roles can be assigned at various levels:
Cluster-level: For platform admins managing infrastructure
Project-level: For developers working within specific teams
Custom roles: Tailored for unique security or governance needs
RBAC ensures that users only have access to what they need, reducing the risk of accidental or malicious actions.
🧠 Identity Management at Scale
When organizations scale to hundreds of applications and thousands of users, managing identities manually becomes unmanageable. OpenShift supports:
Group sync with identity providers (e.g., sync AD groups to OpenShift groups)
Centralized identity federation for hybrid and multi-cloud setups
Automated onboarding using predefined user and group templates
Audit logging for user access, changes, and role assignments
These features help enterprises stay compliant, secure, and efficient—all without scripting or manual configuration.
🚀 Scaling Securely Across Environments
As enterprises scale deployments across development, staging, and production, maintaining consistent access and identity control is critical. OpenShift Administration III provides:
Namespace isolation for multi-team environments
Standardized templates for user permissions
Federated identity management across multiple clusters or regions
Integration with CI/CD tools for seamless handoff between roles
These capabilities allow enterprises to expand infrastructure without losing visibility or control over who has access to what.
✅ Key Benefits for Enterprises
🔐 Centralized user control
⚙️ Seamless identity provider integration
📈 Scalable access management for large teams
🛡️ Improved compliance and auditability
🤝 Better collaboration between teams and departments
All of this is possible through configuration, not coding—empowering IT teams to deliver secure and efficient operations at scale.
🧾 Final Thoughts
Authentication and identity management in OpenShift aren’t just about letting users in—they’re about securing the platform, enabling collaboration, and ensuring governance as your infrastructure grows.
With the tools and integrations provided in Red Hat OpenShift Administration III, enterprises can scale deployments confidently, maintain high security standards, and reduce administrative overhead—all without writing a single line of code.
For more info, Kindly visit: Hawkstack Technologies
#OpenShift#RedHat#IdentityManagement#Authentication#EnterpriseSecurity#OpenShiftAdmin#KubernetesSecurity#RBAC#DevOps#AccessControl#SSO#CloudSecurity#HybridCloud#LinuxAdmin#PlatformEngineering#ZeroTrust#ITGovernance#ScalableInfrastructure#DevSecOps#NoCodeOps
0 notes
Text
Role-Based Access Control (RBAC) is an essential feature for managing user permissions in web applications. It allows you to assign different roles to users (e.g., Admin, Editor, User) and grant permissions accordingly.
In this tutorial, we will implement RBAC in Laravel 12 using spatie/laravel-permission package to manage roles and permissions efficiently.
#Laravel12#RBAC#RoleBasedAccessControl#Laravel#WebDevelopment#LaravelSecurity#Authentication#Authorization#LaravelApp#LaravelRoles#PHP#LaravelDevelopment#AccessControl#WebAppSecurity#BackendDevelopment#UserRoles#LaravelTutorial#LaravelBestPractices#LaravelProjects#RoleManagement#AccessPermissions#LaravelAuth#WebAppFeatures#LaravelAdminPanel#PermissionSystem#LaravelRoleBasedAccess
0 notes
Text
Leveraging SolveForce and The Telecom Broker to Address Key Cybersecurity Risks
Introduction Recent guidance from the Cybersecurity and Infrastructure Security Agency (CISA), alongside other global cybersecurity agencies, highlights significant vulnerabilities in telecommunications infrastructure exploited by malicious actors, such as state-sponsored cyber threats. The risks include unauthorized configuration changes, weak access controls, and insecure protocols. By…
#CISA Cybersecurity Guidance#Configuration Monitoring#Cybersecurity#encryption#MFA#Patch Management#RBAC#Secure Protocols#SIEM#SolveForce#Telecom Broker#Telecommunications Security
0 notes
Text
Implementing Role-Based Access Control in Django
Learn how to implement Role-Based Access Control (RBAC) in Django. This guide covers defining roles, assigning permissions, and enforcing access control in views and templates.
Introduction Role-Based Access Control (RBAC) is a method of regulating access to resources based on the roles of individual users within an organization. Implementing RBAC in Django involves defining roles, assigning permissions, and enforcing these permissions in your views and templates. This guide will walk you through the process of implementing RBAC in Django, covering user roles,…
#Django#Django templates#Django Views#permissions#Python#RBAC#role-based access control#Security#user roles#web development
0 notes
Text
Hey look! I made a thing! And I actually took videos of it this time!
0 notes
Text

Some jewelry on my messy bench. Excited about the Rainbow Bazaar Art Collective! We're a bunch of queer artists in southern AB and we're working together this market season!
#jewelry#rbac#sterling#silver#earrings#pearl#carnelian#turquoise#crystals#handmade#small business#gothic#upcycled
0 notes
Text
11 Lessons I Didn’t Know I Was Signing Up for When I Built My First SaaS
When I set out to build my first SaaS product, I thought the hardest part would be writing clean code. I figured the technical decisions would carry the most weight — choose the right stack, organize the database, write good tests, ship features. I had no idea I was about to get a crash course in business, legal strategy, pricing, communication, and product thinking. Here are 11 lessons I…
#.NET development#audit logging#authentication and authorization#bootstrapping software#C programming#custom SaaS platform#data modeling#deadline management software#developer productivity#enterprise SaaS#indie hacking#legal compliance software#legal software#Legal Tech#multi-tenant architecture#net-core#RBAC implementation#SaaS startup#software infrastructure#software-architecture#SQL Server#startup engineering#Substack for developers#system design#technical founder
0 notes
Video
youtube
Demo RBAC User Assignment Policy in Microsoft Exchange Server 2016/19
#youtube#RBAC User Assignment Policy in Microsoft Exchange Server 2016/19 rbac RBAC User Assignment Policy in Microsoft Exchange Server 2016/19
0 notes
Text
Misconfigured Kubernetes RBAC in Azure Airflow Could Expose Entire Cluster to Exploitation
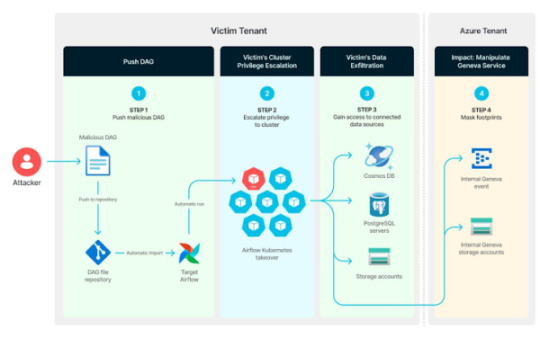
Source: https://thehackernews.com/2024/12/misconfigured-kubernetes-rbac-in-azure.html
More info: https://unit42.paloaltonetworks.com/azure-data-factory-apache-airflow-vulnerabilities/
11 notes
·
View notes
Text
HIPAA Compliance Solutions: Protecting Healthcare Data with Confidence
In today’s healthcare landscape, protecting patient data is not just a regulatory obligation but also a fundamental trust-building measure. The Health Insurance Portability and Accountability Act (HIPAA) sets the standards for safeguarding sensitive patient information, and non-compliance can lead to significant financial penalties and reputational damage. As cyber threats targeting healthcare organizations continue to rise, having robust HIPAA compliance solutions in place is critical to ensuring that patient data remains safe and secure.
What is HIPAA Compliance?
HIPAA is a U.S. federal law that governs how healthcare organizations must handle and protect personal health information (PHI). The law applies to healthcare providers, health plans, and healthcare clearinghouses, as well as business associates that manage or process PHI on behalf of healthcare entities.
HIPAA compliance is crucial for healthcare organizations because it ensures that patient data is protected from unauthorized access, misuse, or breach. Additionally, HIPAA compliance helps healthcare providers reduce the risks associated with data breaches, including fines, legal action, and the loss of patient trust.
Why HIPAA Compliance is Essential
The healthcare industry is a prime target for cybercriminals due to the wealth of sensitive data it handles. A breach in healthcare data not only exposes patient information but can also lead to significant financial loss. Under HIPAA, healthcare organizations are required to implement various safeguards to protect patient data, including administrative, physical, and technical protections.
Failing to comply with HIPAA standards can lead to penalties ranging from $100 to $50,000 per violation, with a maximum annual penalty of $1.5 million. These penalties can severely damage an organization's financial standing and reputation.
Moreover, HIPAA compliance helps healthcare organizations foster patient trust. When patients know that their personal health information is handled securely, they are more likely to choose and stay with providers who prioritize privacy and data protection.
Key HIPAA Compliance Solutions for Healthcare Providers
1. Risk Assessment and Management
Regular risk assessments are a cornerstone of HIPAA compliance. A thorough risk assessment identifies potential vulnerabilities in your systems and processes and allows you to address them proactively. It also helps you ensure that any changes to your systems or practices don’t inadvertently expose PHI to unauthorized access.
2. Data Encryption
Encrypting sensitive patient data is one of the most effective ways to protect it from unauthorized access. Both data in transit (e.g., during communications) and data at rest (e.g., stored data) must be encrypted to meet HIPAA standards.
3. Access Controls
Access to PHI should be limited to authorized personnel only. Implementing role-based access controls (RBAC) ensures that staff members only access the data they need to perform their jobs. Additionally, multi-factor authentication (MFA) adds an extra layer of security to user logins.
4. Employee Training
Employees must be regularly trained on HIPAA rules and data security best practices. Staff should be aware of how to properly handle, store, and transmit PHI to avoid inadvertent breaches.
5. Audit Trails and Monitoring
Implementing detailed audit trails and continuous monitoring can help detect unauthorized access to PHI in real time. This ensures that any suspicious activity is identified and mitigated promptly.
6. Incident Response Plan
An incident response plan outlines the steps to take in the event of a data breach. HIPAA requires that organizations notify affected individuals within 60 days of a breach, so having a plan in place is crucial to meeting this requirement.
How Securify Can Help with HIPAA Compliance
For healthcare organizations, maintaining HIPAA compliance can be overwhelming. Fortunately, Securify provides expert HIPAA compliance solutions to guide healthcare providers through every step of the compliance process. From risk assessments and encryption strategies to developing comprehensive incident response plans, Securify has the tools and expertise to ensure your organization meets all HIPAA standards.
With Securify’s HIPAA compliance solutions, you can rest assured that your patient data is secure, and you are meeting all necessary regulatory requirements. Our team of experts works closely with you to create customized compliance strategies that address your specific needs and risks.
By partnering with Securify, you protect not just your organization but also the trust and well-being of your patients.
2 notes
·
View notes
Text






Cora & Rose Rivers for @whyeverr Rebuild a City Challenge (more info + download under the cut)
I've been following whyeverr's rbac-challenge for such a long time and I was (and still am) totally in awe of the dedication that she puts into the challenge and the story itself! So when she announced that she was looking for survivors for the challenge, I knew I had to create some sims.
Meet Cora and Rose, two sisters who are originally from Chestnut Ridge, where they grew up on the outskirts of the city on a horse farm ... everything was fine until the day tragedy struck and the townie apocalypse started. They left their farm in a hurry and lost their parents who fought the townies off so that they could escape. There was grief, anger, and yet, determination to survive until the day, they would take back the farm from the townies.
Cora is pretty straightforward, she's a woman of action and has never lost a fight, while Rose is still a teenager who's trying to find herself against all odds. She may be seen hanging around with the wrong crowd and her decisions might not be the best, but she's always looking out for her loved ones. Even though both sisters are very different, they always have each other's back. (If anyone still knows the TV show The Tribe, that's where I got my inspiration for Rose from)
Download: You can find them in the gallery, my ID is aeromantica (please turn on custom content in the search, I've not used any CC but they somehow have that label)
#rbaccsurvivor#the sims 4#ts4#ts4 simblr#ts4 cas#whyeverr#sims download#sims 4 download#show us your sims#sims 4#sims 4 screenshots#sims 4 no cc#I am a cc-girlie so this was difficult but I hope they turned out well!#regarding The Tribe - I watched it when I was way too young but I loved the weird and iconic outfits back then#this is my last 'real' post before my holidays the rest will be queued until the 29th of september#*mine#*mydownload
41 notes
·
View notes