#SCADASecurity
Explore tagged Tumblr posts
Text
SCADA (supervisory control and Data Acquisition)
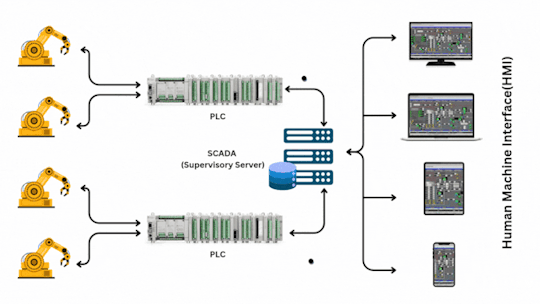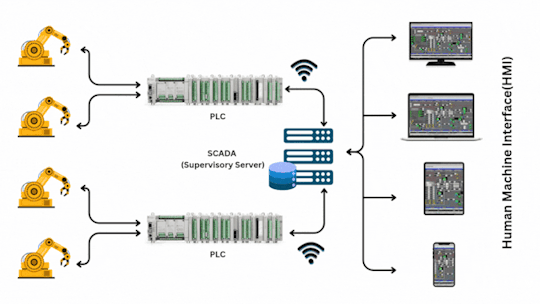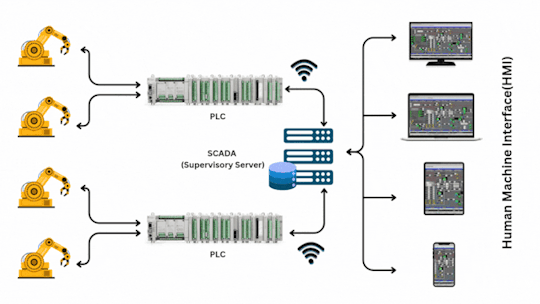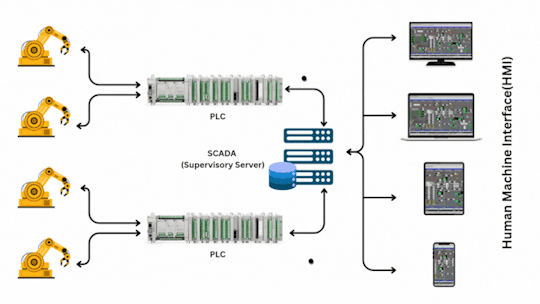
PLC (programmable logic controller) and SCADA (supervisory control and Data Acquisition) systems are essential components of modern industrial automation. They play a crucial role in controlling, monitoring and optimizing various processes in industries such as manufacturing, energy and water management.
PLCs (Programmable Logic Controllers):
The signals from field devices are sent to the PLCs.
PLCs are responsible for real-time control of machinery based on pre-programmed logic.
Each PLC interfaces with one or more pieces of equipment.
SCADA (Supervisory Server):
The SCADA system connects to the PLCs and collects data from them.
It also sends control instructions back to the PLCs.
SCADA provides centralized monitoring and control, data logging, and alarm management.
Database and Network
The SCADA server stores process data in a database.
A network switch or communication system ensures connectivity between SCADA, PLCs, and HMIs.
Human Machine Interface
Monitor live data from the system.
Send manual commands.
View alarms and historical data.
#automation#viral#viralpost#PLC#HMI#technology techpage#technology#automotive#plc automation#techtrends#SCADA#allen bradley#scada systems#scadasecurity#tumblr trends#rockwell automation
0 notes
Text
Key Security Measures for Protecting OT/ Industrial Control System (ICS) Security

The security of our essential infrastructure has never been more important. At the heart of this worry is a critical question: what is ICS security? Industrial Control System (ICS) security is the first line of defense for the systems that control our electricity grids, water treatment facilities, manufacturing units, and other critical industrial operations. As cyber threats emerge and attack these essential systems with increasing complexity, understanding ICS security has become significant for corporations, governments, and security professionals.
All industrial sectors use technology and automation technologies to increase productivity and ROI on processes. Industrial Control Systems (ICS) are critical for automating and controlling manufacturing, production, and data-collecting processes. However, as digital complexity increases, industrial control systems present a variety of security issues. In this blog, we will discuss what OT/industrial control systems are, the security measures for ICS, and market insights into growing cyber threats.
What is OT/Industrial Control Systems (ICS) Security?
QKS Group defines an OT/Industrial Control Systems (ICS) Security as the protection of operational technology (OT) systems that monitor critical infrastructure and industrial processes. That includes protecting systems that provide energy, water, manufacturing, and more. These systems process sensor data from across industrial enterprises, enabling alerting and management of processes. ICS usually refers to systems that manage and operate infrastructure-supporting functions like water, power, transportation, manufacturing, and other critical services. With the increased digitization of nearly all aspects of commercial and public business, these systems often depend on software, computers, endpoints, and networks—all of which must be secured for the safety of the system, the people operating it, and those it serves.
Security Measures for OT/Industrial Control System (ICS) Security
Each industrial sector is unique and must leverage specialized ICS security requirements. In this technology-driven era where automation is the key to seamless progress, industries must implement ICS security measures to protect the entire system. According to QKS Group's "Market Share: OT/Industrial Control Systems (ICS) Security, 2023, Worldwide" and "Market Forecast: OT/Industrial Control Systems (ICS) Security, 2024-2028, Worldwide" reports Let's explore the security measures industries need for enhanced security.
Establish an incident response plan: Most companies consider how to respond once an incident occurs. That leaves the architecture, systems configuration, and activity logs misaligned. Thus, organizations should create incident response plans to identify how to manage and recover from any incident.
Enable network visibility and continuous monitoring: Formerly effective industrial technology and control automation systems may eventually fail. As a result, enterprises should constantly test their network and Industry Control Systems design by employing security visibility techniques.
Implement a vulnerability management program: Vulnerabilities in industrial systems and IoT devices can pose serious risks to the enterprise. Organizations should develop risk management strategies by repairing patches and filling holes in the various elements of the ICS.
Enforce ICS security policies: If companies properly implement industry security measures, that will work great for all industries. Security professionals should lay out a plan to evaluate, obey, and execute multiple best practices. Operations, security professionals, and management should work together to implement the policies.
Implement the principle of least privilege: The least privileged access limits user access rights. It provides the bare minimum privileges and ownership required to perform any task.
Secure all remote access: Many staff and operational team members want remote access to operate ICS assets across geographical locations. ICS systems should have strong authentication procedures, such as a robust encryption protocol that avoids unwanted remote access.
Market Insights: Rising Demand for OT/ICS Security Amid Growing Cyber Threats
The OT/ICS security market is forecast to expand rapidly by 2028, compelled by the growing need to protect key infrastructure and industrial processes from sophisticated cyber-attacks. This growth has been fuelled by heightened awareness among multinational corporations, utility companies, and manufacturing sectors about cybersecurity resilience and compliance with stringent regulations.
Using sophisticated technologies like machine learning (ML), artificial intelligence (AI), and advanced encryption methods in OT/ICS security systems improves threat identification, incident response, and secure remote access. Regions with above-average adoption rates include the United States, Canada, and Japan, while Western Europe and the Asia-Pacific region are also investing heavily in cybersecurity measures.
Industries in these areas emphasize deploying advanced security solutions to protect against cyberattacks, assure operational continuity, and comply with regulatory requirements such as NIST, NERC CIP, and ISA/IEC 62443. This holistic approach to OT/ICS security emphasizes its vital role in ensuring industrial stability and resilience in an increasingly linked and digital environment.
The OT/Industrial Control Systems (ICS) Security market is growing rapidly, driven by the growing need to secure key infrastructure and industrial processes from increasingly sophisticated cyber-attacks. Companies plan to invest extensively in OT/ICS security solutions to maintain operational continuity, protect against cyber-attacks, and meet severe regulatory requirements.
Conclusion
As industrial processes become increasingly digitized, the need for robust OT/ICS security measures has never been greater. Protecting essential infrastructure from increasing cyber threats requires a combination of proactive security strategies, cutting-edge technologies, and compliance with industry regulations. With growing investments in cybersecurity and the adoption of AI, ML, and advanced encryption, businesses can strengthen their resilience against cyberattacks.
#ICSsecurity#OTsecurity#CriticalInfrastructure#SCADAsecurity#IndustrialCybersecurity#CyberRisk#ThreatDetection
0 notes
Text
Infrastructure Security Market
🏗️ 𝐈𝐧𝐟𝐫𝐚𝐬𝐭𝐫𝐮𝐜𝐭𝐮𝐫𝐞 𝐌𝐚𝐭𝐭𝐞𝐫𝐬. 🔒 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐢𝐬 𝐍𝐨𝐧-𝐍𝐞𝐠𝐨𝐭𝐢𝐚𝐛𝐥𝐞.
Infrastructure Security Market size is estimated to reach $185 Billion by 2031, growing at a CAGR of 9.3% during the forecast period 2025-2031.
🔑 𝐊𝐞𝐲 𝐌𝐚𝐫𝐤𝐞𝐭 𝐃𝐫𝐢𝐯𝐞𝐫𝐬
1. Escalating Cyber Threats
The increasing frequency and sophistication of cyberattacks, including ransomware and state-sponsored threats, are compelling organizations to invest heavily in infrastructure security.
2. Regulatory Compliance
Governments worldwide are implementing stringent regulations, such as the EU's NIS Directive and the UK's Cyber Security and Resilience Bill, mandating enhanced security measures for critical infrastructure.
3. Integration of IoT Devices
The proliferation of Internet of Things (IoT) devices in critical infrastructure sectors increases the potential attack surface, necessitating robust security solutions.
🔗 𝐆𝐞𝐭 𝐑𝐎𝐈-𝐟𝐨𝐜𝐮𝐬𝐞𝐝 𝐢𝐧𝐬𝐢𝐠𝐡𝐭𝐬 𝐟𝐨𝐫 𝟐𝟎𝟐𝟓-𝟐𝟎𝟑𝟏 → 𝐃𝐨𝐰𝐧𝐥𝐨𝐚𝐝 𝐍𝐨𝐰
🔄 𝐄𝐦𝐞𝐫𝐠𝐢𝐧𝐠 𝐌𝐚𝐫𝐤𝐞𝐭 𝐓𝐫𝐞𝐧𝐝𝐬
1. Adoption of AI and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are being leveraged for predictive analytics, real-time threat detection, and automated response systems, enhancing the efficiency of security operations.
2. Cloud Security Solutions
With the shift towards cloud computing, organizations are increasingly adopting Secure Access Service Edge (SASE) and cloud-native security platforms to safeguard data and applications.
3. Focus on Endpoint Security
The rise in remote work and mobile devices has heightened the need for robust endpoint security solutions, including Extended Detection and Response (XDR) and Endpoint Detection and Response (EDR) systems.
𝐓𝐨𝐩 𝐊𝐞𝐲 𝐏𝐥𝐚𝐲𝐞𝐫𝐬:
Honeywell, Johnson Controls, Siemens, Cisco., IBM, Schneider Electric Hub, ABB., Thales, Fortinet., Motorola Solutions, Raytheon Technologies, BAE Systems, Cognimatics AB - since 2017 integrated into Axis Communications, Genetec., Leidos, Check Point Software, Huawei Technologies Lanka Co., (Pvt) Ltd., FLIR Systems, Securitas Sverige AB, Bosch Security and Safety Systems
#InfrastructureSecurity #CriticalInfrastructure #CyberSecurity #PhysicalSecurity #OTSecurity #ITSecurity #ICSsecurity #SCADASecurity #NetworkSecurity #ZeroTrust #AIinSecurity #ThreatDetection #RiskManagement #SecurityOperations #CyberResilience #SecurityByDesign #DigitalTransformation #SmartInfrastructure

0 notes
Photo
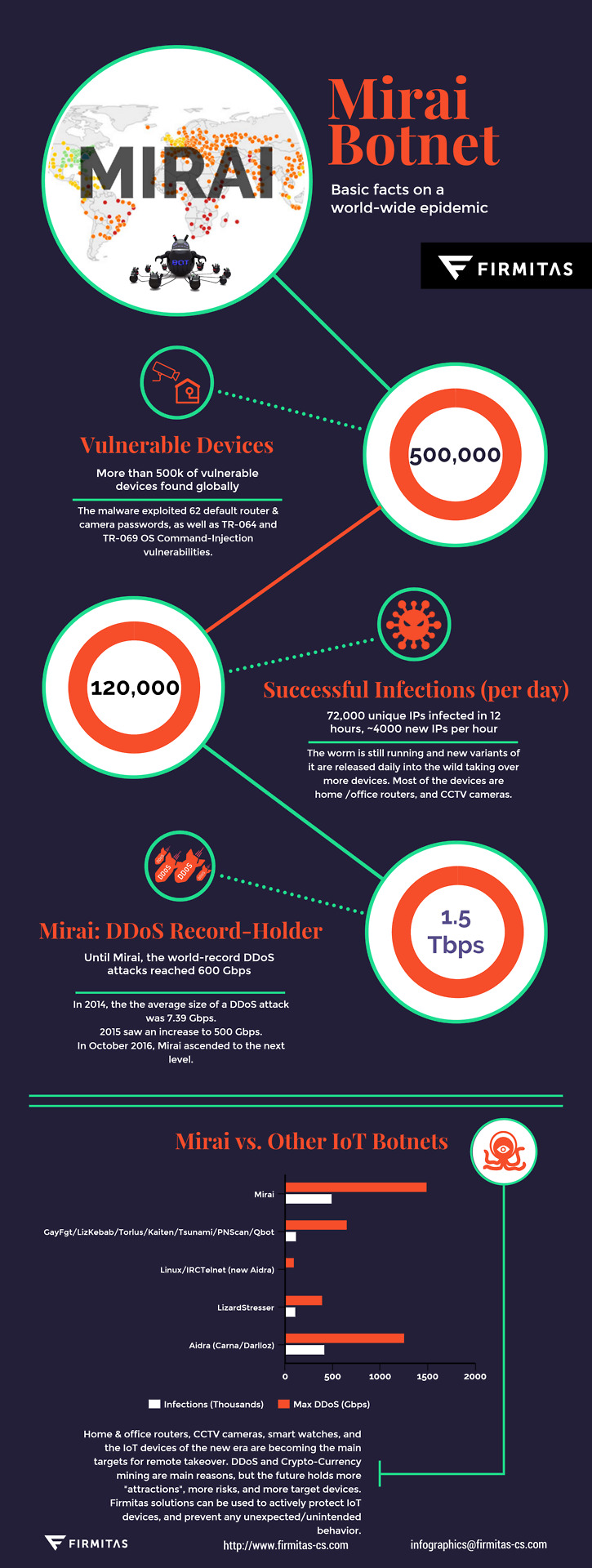
Firmitas Cyber Solutions - Inforgraphic - Mirai Botnet - A few basic facts on a world-wide epidemic
500,000 Vulnerable Devices More than 500k of vulnerable devices found globally. The malware exploited 62 default router & camera passwords, as well as TR-064 and TR-069 OS Command-Injection vulnerabilities. 120,000 Successful Infections (per day) 72,000 unique IPs infected in 12 hours, ~4000 new IPs per hour. The worm is still running and new variants of it are released daily into the wild taking over more devices. Most of the devices are home /office routers, and CCTV cameras. 1.5 Tbps - Mirai: DDoS Record-Holder Until Mirai, the world-record DDoS attacks reached 600 Gbps. In 2014, the the average size of a DDoS attack was 7.39 Gbps. 2015 saw an increase to 500 Gbps. In October 2016, Mirai ascended to the next level. Mirai vs. Other IoT Botnets Mirai - 500k infections, 1.5 Tbps DDoS GayFgt/LizKebab/Torlus/Kaiten/Tsunami/PNScan/Qbot - 120k infections, 655 Gbps DDoS Linux/IRCTelnet (new Aidra) - 3.5k infections, 100.5 Gbps DDoS LizardStresser - 118k infections, 400 Gbps DDoS Aidra (Carna/Darlloz) - 420k infections, 1.26 Tbps DDoS Home & office routers, CCTV cameras, smart watches, and the IoT devices of the new era are becoming the main targets for remote takeover. DDoS and Crypto-Currency mining are main reasons, but the future holds more "attractions", more risks, and more target devices. Firmitas solutions can be used to actively protect IoT devices, and prevent any unexpected/unintended behavior.
#Firmitas#FirmitasCyber#FirmitasCyberSolutions#FirmitasIndustrialSecurity#IoT Security#IoT#Firmitas Cyber#Firmitas Cyber Security#SCADA Security#SCADA Cyber Security#SCADACyber#SCADASecurity#SCADA/ICS#ICS Cyber Security#ICSCyberSecurity#ICSSecurity#IndustrialSecurity#RouterSecurity
0 notes
Photo

Poor Password Security Led to Recent Water Treatment Facility Hack #cyberattack #hackingnews #passwordsecurity #scadasecurity #teamviewer #windows7 #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes