#SQL Server cloud backups
Explore tagged Tumblr posts
Text
Enhancing SQL Server with External API Calls: A Guide to sp_invoke_external_rest_endpoint
In the bustling world of database management, SQL Server shines as a beacon of strength, flexibility, and a treasure trove of features ready to tackle a wide array of data challenges. Among its many jewels is a feature that feels almost like magic: the ability to chat with external APIs right from the cozy confines of T-SQL code, courtesy of the sp_invoke_external_rest_endpoint stored procedure.…
View On WordPress
#database data enrichment#external API calls in SQL#sp_invoke_external_rest_endpoint examples#SQL Server API integration#SQL Server cloud backups
0 notes
Text
Unraveling the Power of Managed Cloud Server Hosting: A Step-by-Step Guide?
In today's digital era, businesses are increasingly turning to "cloud server management solutions" to enhance efficiency, scalability, and security. One of the most sought-after options in this realm is fully managed cloud server hosting. This comprehensive guide will take you through the ins and outs of managed cloud server hosting, providing a step-by-step understanding of its benefits, implementation, and best practices.
Understanding Managed Cloud Server Hosting Managed cloud server hosting refers to the outsourcing of server management tasks to a third-party service provider. This includes server setup, configuration, maintenance, security, updates, and troubleshooting. By "opting for managed cloud hosting", businesses can focus on their core activities while leaving the technical aspects to experienced professionals.
Benefits of Managed Cloud Server Hosting Enhanced Security: Managed cloud server hosting offers robust security measures such as firewalls, intrusion detection systems, data encryption, and regular security audits to protect sensitive data and applications.
Scalability: With managed cloud hosting, businesses can easily scale their resources up or down based on demand, ensuring optimal performance and cost-efficiency.
Cost Savings: By outsourcing server management, businesses can save costs on hiring dedicated IT staff, infrastructure maintenance, and upgrades.
24/7 Monitoring and Support: Managed cloud hosting providers offer round-the-clock monitoring and support, ensuring quick resolution of issues and minimal downtime.
Step-by-Step Implementation of Managed Cloud Server Hosting
Step 1: Assess Your Hosting Needs Determine your storage, processing power, bandwidth, and security requirements. Identify the type of applications (e.g., web hosting, databases, e-commerce) you'll be hosting on the cloud server.
Step 2: Choose a Managed Cloud Hosting Provider Research and compare different managed cloud hosting providers based on their offerings, pricing, reputation, and customer reviews. Consider factors such as server uptime guarantees, security protocols, scalability options, and support services.
Step 3: Select the Right Cloud Server Configuration Choose the appropriate cloud server configuration (e.g., CPU cores, RAM, storage) based on your hosting needs and budget. Opt for features like automatic backups, disaster recovery, and SSL certificates for enhanced security and reliability.
Step 4: Server Setup and Configuration Work with your "managed cloud hosting provider" to set up and configure your cloud server according to your specifications. Ensure that all necessary software, applications, and security protocols are installed and activated.
Step 5: Data Migration and Deployment If migrating from an existing hosting environment, plan and execute a seamless data migration to the "managed cloud server". Test the deployment to ensure that all applications and services are functioning correctly on the new cloud server.
Step 6: Ongoing Management and Optimization Regularly monitor server performance, security, and resource utilization to identify potential issues and optimize performance. Work closely with your "managed cloud hosting provider" to implement updates, patches, and security enhancements as needed.
Step 7: Backup and Disaster Recovery Planning Set up automated backups and disaster recovery mechanisms to protect data against hardware failures, cyber threats, and data loss incidents. Regularly test backup and recovery processes to ensure their effectiveness in real-world scenarios.
Best Practices for Managed Cloud Server Hosting Regular Security Audits: Conduct regular security audits and vulnerability assessments to identify and mitigate potential security risks. Performance Monitoring: Continuously monitor server performance metrics such as CPU usage, memory utilization, disk I/O, and network traffic to optimize resource allocation.
Backup and Restore Testing: Test backup and restore procedures periodically to ensure data integrity and recovery readiness. Compliance and Regulations: Stay compliant with industry regulations and data protection laws relevant to your business operations. Disaster Recovery Planning: Develop and implement a comprehensive disaster recovery plan with predefined procedures for data restoration and business continuity.
In conclusion, "managed cloud server hosting" offers a myriad of benefits for businesses seeking reliable, scalable, and secure hosting solutions. By following the step-by-step guide outlined above and adhering to best practices, businesses can leverage the power of "managed cloud hosting" to streamline operations, reduce costs, and drive business growth in the digital landscape.
#Cloud Server Management in Delhi#Managed cloud server in Delhi#Cloud Server Manger in Delhi#Cloud server management in Delhi#Cloud based server manager in Delhi#Fully managed cloud server in Delhi#Cloud server management panel in Delhi#Cloud server management Services in Delhi#Cloud Server Management Software in Delhi#Managed Cloud server hosting in Delhi#Google Cloud Sql Server management studio in Delhi#Cloud server management on local machine#Managed Cloud dedicated server#Cloud server management tools#What is cloud management#What is cloud server#Managing the cloud infrastructure#Types of cloud management#Cloud server hosting#Cloud server for small business#Cloud server providers#Cloud server cost#Cloud server meaning#Cloud server pricing#Cloud server VS physical server#Cloud server backup
0 notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
Exploring the Power of Amazon Web Services: Top AWS Services You Need to Know
In the ever-evolving realm of cloud computing, Amazon Web Services (AWS) has established itself as an undeniable force to be reckoned with. AWS's vast and diverse array of services has positioned it as a dominant player, catering to the evolving needs of businesses, startups, and individuals worldwide. Its popularity transcends boundaries, making it the preferred choice for a myriad of use cases, from startups launching their first web applications to established enterprises managing complex networks of services. This blog embarks on an exploratory journey into the boundless world of AWS, delving deep into some of its most sought-after and pivotal services.

As the digital landscape continues to expand, understanding these AWS services and their significance is pivotal, whether you're a seasoned cloud expert or someone taking the first steps in your cloud computing journey. Join us as we delve into the intricate web of AWS's top services and discover how they can shape the future of your cloud computing endeavors. From cloud novices to seasoned professionals, the AWS ecosystem holds the keys to innovation and transformation.
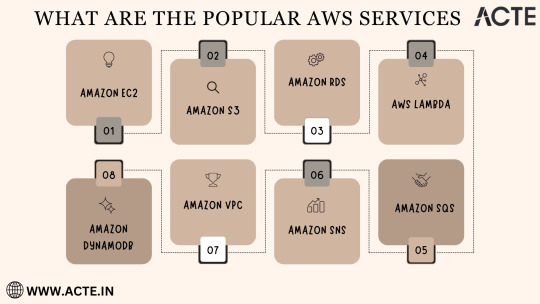
Amazon EC2 (Elastic Compute Cloud): The Foundation of Scalability At the core of AWS's capabilities is Amazon EC2, the Elastic Compute Cloud. EC2 provides resizable compute capacity in the cloud, allowing you to run virtual servers, commonly referred to as instances. These instances serve as the foundation for a multitude of AWS solutions, offering the scalability and flexibility required to meet diverse application and workload demands. Whether you're a startup launching your first web application or an enterprise managing a complex network of services, EC2 ensures that you have the computational resources you need, precisely when you need them.
Amazon S3 (Simple Storage Service): Secure, Scalable, and Cost-Effective Data Storage When it comes to storing and retrieving data, Amazon S3, the Simple Storage Service, stands as an indispensable tool in the AWS arsenal. S3 offers a scalable and highly durable object storage service that is designed for data security and cost-effectiveness. This service is the choice of businesses and individuals for storing a wide range of data, including media files, backups, and data archives. Its flexibility and reliability make it a prime choice for safeguarding your digital assets and ensuring they are readily accessible.
Amazon RDS (Relational Database Service): Streamlined Database Management Database management can be a complex task, but AWS simplifies it with Amazon RDS, the Relational Database Service. RDS automates many common database management tasks, including patching, backups, and scaling. It supports multiple database engines, including popular options like MySQL, PostgreSQL, and SQL Server. This service allows you to focus on your application while AWS handles the underlying database infrastructure. Whether you're building a content management system, an e-commerce platform, or a mobile app, RDS streamlines your database operations.
AWS Lambda: The Era of Serverless Computing Serverless computing has transformed the way applications are built and deployed, and AWS Lambda is at the forefront of this revolution. Lambda is a serverless compute service that enables you to run code without the need for server provisioning or management. It's the perfect solution for building serverless applications, microservices, and automating tasks. The unique pricing model ensures that you pay only for the compute time your code actually uses. This service empowers developers to focus on coding, knowing that AWS will handle the operational complexities behind the scenes.
Amazon DynamoDB: Low Latency, High Scalability NoSQL Database Amazon DynamoDB is a managed NoSQL database service that stands out for its low latency and exceptional scalability. It's a popular choice for applications with variable workloads, such as gaming platforms, IoT solutions, and real-time data processing systems. DynamoDB automatically scales to meet the demands of your applications, ensuring consistent, single-digit millisecond latency at any scale. Whether you're managing user profiles, session data, or real-time analytics, DynamoDB is designed to meet your performance needs.
Amazon VPC (Virtual Private Cloud): Tailored Networking for Security and Control Security and control over your cloud resources are paramount, and Amazon VPC (Virtual Private Cloud) empowers you to create isolated networks within the AWS cloud. This isolation enhances security and control, allowing you to define your network topology, configure routing, and manage access. VPC is the go-to solution for businesses and individuals who require a network environment that mirrors the security and control of traditional on-premises data centers.
Amazon SNS (Simple Notification Service): Seamless Communication Across Channels Effective communication is a cornerstone of modern applications, and Amazon SNS (Simple Notification Service) is designed to facilitate seamless communication across various channels. This fully managed messaging service enables you to send notifications to a distributed set of recipients, whether through email, SMS, or mobile devices. SNS is an essential component of applications that require real-time updates and notifications to keep users informed and engaged.
Amazon SQS (Simple Queue Service): Decoupling for Scalable Applications Decoupling components of a cloud application is crucial for scalability, and Amazon SQS (Simple Queue Service) is a fully managed message queuing service designed for this purpose. It ensures reliable and scalable communication between different parts of your application, helping you create systems that can handle varying workloads efficiently. SQS is a valuable tool for building robust, distributed applications that can adapt to changes in demand.
In the rapidly evolving landscape of cloud computing, Amazon Web Services (AWS) stands as a colossus, offering a diverse array of services that address the ever-evolving needs of businesses, startups, and individuals alike. AWS's popularity transcends industry boundaries, making it the go-to choice for a wide range of use cases, from startups launching their inaugural web applications to established enterprises managing intricate networks of services.
To unlock the full potential of these AWS services, gaining comprehensive knowledge and hands-on experience is key. ACTE Technologies, a renowned training provider, offers specialized AWS training programs designed to provide practical skills and in-depth understanding. These programs equip you with the tools needed to navigate and excel in the dynamic world of cloud computing.
With AWS services at your disposal, the possibilities are endless, and innovation knows no bounds. Join the ever-growing community of cloud professionals and enthusiasts, and empower yourself to shape the future of the digital landscape. ACTE Technologies is your trusted guide on this journey, providing the knowledge and support needed to thrive in the world of AWS and cloud computing.
8 notes
·
View notes
Text
Navigating the Cloud Landscape: Unleashing Amazon Web Services (AWS) Potential
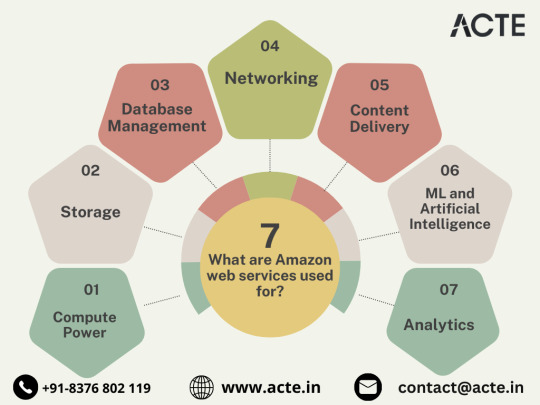
In the ever-evolving tech landscape, businesses are in a constant quest for innovation, scalability, and operational optimization. Enter Amazon Web Services (AWS), a robust cloud computing juggernaut offering a versatile suite of services tailored to diverse business requirements. This blog explores the myriad applications of AWS across various sectors, providing a transformative journey through the cloud.

Harnessing Computational Agility with Amazon EC2
Central to the AWS ecosystem is Amazon EC2 (Elastic Compute Cloud), a pivotal player reshaping the cloud computing paradigm. Offering scalable virtual servers, EC2 empowers users to seamlessly run applications and manage computing resources. This adaptability enables businesses to dynamically adjust computational capacity, ensuring optimal performance and cost-effectiveness.
Redefining Storage Solutions
AWS addresses the critical need for scalable and secure storage through services such as Amazon S3 (Simple Storage Service) and Amazon EBS (Elastic Block Store). S3 acts as a dependable object storage solution for data backup, archiving, and content distribution. Meanwhile, EBS provides persistent block-level storage designed for EC2 instances, guaranteeing data integrity and accessibility.
Streamlined Database Management: Amazon RDS and DynamoDB
Database management undergoes a transformation with Amazon RDS, simplifying the setup, operation, and scaling of relational databases. Be it MySQL, PostgreSQL, or SQL Server, RDS provides a frictionless environment for managing diverse database workloads. For enthusiasts of NoSQL, Amazon DynamoDB steps in as a swift and flexible solution for document and key-value data storage.
Networking Mastery: Amazon VPC and Route 53
AWS empowers users to construct a virtual sanctuary for their resources through Amazon VPC (Virtual Private Cloud). This virtual network facilitates the launch of AWS resources within a user-defined space, enhancing security and control. Simultaneously, Amazon Route 53, a scalable DNS web service, ensures seamless routing of end-user requests to globally distributed endpoints.
Global Content Delivery Excellence with Amazon CloudFront
Amazon CloudFront emerges as a dynamic content delivery network (CDN) service, securely delivering data, videos, applications, and APIs on a global scale. This ensures low latency and high transfer speeds, elevating user experiences across diverse geographical locations.
AI and ML Prowess Unleashed
AWS propels businesses into the future with advanced machine learning and artificial intelligence services. Amazon SageMaker, a fully managed service, enables developers to rapidly build, train, and deploy machine learning models. Additionally, Amazon Rekognition provides sophisticated image and video analysis, supporting applications in facial recognition, object detection, and content moderation.
Big Data Mastery: Amazon Redshift and Athena
For organizations grappling with massive datasets, AWS offers Amazon Redshift, a fully managed data warehouse service. It facilitates the execution of complex queries on large datasets, empowering informed decision-making. Simultaneously, Amazon Athena allows users to analyze data in Amazon S3 using standard SQL queries, unlocking invaluable insights.
In conclusion, Amazon Web Services (AWS) stands as an all-encompassing cloud computing platform, empowering businesses to innovate, scale, and optimize operations. From adaptable compute power and secure storage solutions to cutting-edge AI and ML capabilities, AWS serves as a robust foundation for organizations navigating the digital frontier. Embrace the limitless potential of cloud computing with AWS – where innovation knows no bounds.
3 notes
·
View notes
Text
Azure Data Engineering Tools For Data Engineers
Azure is a cloud computing platform provided by Microsoft, which presents an extensive array of data engineering tools. These tools serve to assist data engineers in constructing and upholding data systems that possess the qualities of scalability, reliability, and security. Moreover, Azure data engineering tools facilitate the creation and management of data systems that cater to the unique requirements of an organization.
In this article, we will explore nine key Azure data engineering tools that should be in every data engineer’s toolkit. Whether you’re a beginner in data engineering or aiming to enhance your skills, these Azure tools are crucial for your career development.
Microsoft Azure Databricks
Azure Databricks is a managed version of Databricks, a popular data analytics and machine learning platform. It offers one-click installation, faster workflows, and collaborative workspaces for data scientists and engineers. Azure Databricks seamlessly integrates with Azure’s computation and storage resources, making it an excellent choice for collaborative data projects.
Microsoft Azure Data Factory
Microsoft Azure Data Factory (ADF) is a fully-managed, serverless data integration tool designed to handle data at scale. It enables data engineers to acquire, analyze, and process large volumes of data efficiently. ADF supports various use cases, including data engineering, operational data integration, analytics, and data warehousing.
Microsoft Azure Stream Analytics
Azure Stream Analytics is a real-time, complex event-processing engine designed to analyze and process large volumes of fast-streaming data from various sources. It is a critical tool for data engineers dealing with real-time data analysis and processing.
Microsoft Azure Data Lake Storage
Azure Data Lake Storage provides a scalable and secure data lake solution for data scientists, developers, and analysts. It allows organizations to store data of any type and size while supporting low-latency workloads. Data engineers can take advantage of this infrastructure to build and maintain data pipelines. Azure Data Lake Storage also offers enterprise-grade security features for data collaboration.
Microsoft Azure Synapse Analytics
Azure Synapse Analytics is an integrated platform solution that combines data warehousing, data connectors, ETL pipelines, analytics tools, big data scalability, and visualization capabilities. Data engineers can efficiently process data for warehousing and analytics using Synapse Pipelines’ ETL and data integration capabilities.
Microsoft Azure Cosmos DB
Azure Cosmos DB is a fully managed and server-less distributed database service that supports multiple data models, including PostgreSQL, MongoDB, and Apache Cassandra. It offers automatic and immediate scalability, single-digit millisecond reads and writes, and high availability for NoSQL data. Azure Cosmos DB is a versatile tool for data engineers looking to develop high-performance applications.
Microsoft Azure SQL Database
Azure SQL Database is a fully managed and continually updated relational database service in the cloud. It offers native support for services like Azure Functions and Azure App Service, simplifying application development. Data engineers can use Azure SQL Database to handle real-time data ingestion tasks efficiently.
Microsoft Azure MariaDB
Azure Database for MariaDB provides seamless integration with Azure Web Apps and supports popular open-source frameworks and languages like WordPress and Drupal. It offers built-in monitoring, security, automatic backups, and patching at no additional cost.
Microsoft Azure PostgreSQL Database
Azure PostgreSQL Database is a fully managed open-source database service designed to emphasize application innovation rather than database management. It supports various open-source frameworks and languages and offers superior security, performance optimization through AI, and high uptime guarantees.
Whether you’re a novice data engineer or an experienced professional, mastering these Azure data engineering tools is essential for advancing your career in the data-driven world. As technology evolves and data continues to grow, data engineers with expertise in Azure tools are in high demand. Start your journey to becoming a proficient data engineer with these powerful Azure tools and resources.
Unlock the full potential of your data engineering career with Datavalley. As you start your journey to becoming a skilled data engineer, it’s essential to equip yourself with the right tools and knowledge. The Azure data engineering tools we’ve explored in this article are your gateway to effectively managing and using data for impactful insights and decision-making.
To take your data engineering skills to the next level and gain practical, hands-on experience with these tools, we invite you to join the courses at Datavalley. Our comprehensive data engineering courses are designed to provide you with the expertise you need to excel in the dynamic field of data engineering. Whether you’re just starting or looking to advance your career, Datavalley’s courses offer a structured learning path and real-world projects that will set you on the path to success.
Course format:
Subject: Data Engineering Classes: 200 hours of live classes Lectures: 199 lectures Projects: Collaborative projects and mini projects for each module Level: All levels Scholarship: Up to 70% scholarship on this course Interactive activities: labs, quizzes, scenario walk-throughs Placement Assistance: Resume preparation, soft skills training, interview preparation
Subject: DevOps Classes: 180+ hours of live classes Lectures: 300 lectures Projects: Collaborative projects and mini projects for each module Level: All levels Scholarship: Up to 67% scholarship on this course Interactive activities: labs, quizzes, scenario walk-throughs Placement Assistance: Resume preparation, soft skills training, interview preparation
For more details on the Data Engineering courses, visit Datavalley’s official website.
#datavalley#dataexperts#data engineering#data analytics#dataexcellence#data science#power bi#business intelligence#data analytics course#data science course#data engineering course#data engineering training
3 notes
·
View notes
Text
Demystifying Microsoft Azure Cloud Hosting and PaaS Services: A Comprehensive Guide
In the rapidly evolving landscape of cloud computing, Microsoft Azure has emerged as a powerful player, offering a wide range of services to help businesses build, deploy, and manage applications and infrastructure. One of the standout features of Azure is its Cloud Hosting and Platform-as-a-Service (PaaS) offerings, which enable organizations to harness the benefits of the cloud while minimizing the complexities of infrastructure management. In this comprehensive guide, we'll dive deep into Microsoft Azure Cloud Hosting and PaaS Services, demystifying their features, benefits, and use cases.
Understanding Microsoft Azure Cloud Hosting
Cloud hosting, as the name suggests, involves hosting applications and services on virtual servers that are accessed over the internet. Microsoft Azure provides a robust cloud hosting environment, allowing businesses to scale up or down as needed, pay for only the resources they consume, and reduce the burden of maintaining physical hardware. Here are some key components of Azure Cloud Hosting:
Virtual Machines (VMs): Azure offers a variety of pre-configured virtual machine sizes that cater to different workloads. These VMs can run Windows or Linux operating systems and can be easily scaled to meet changing demands.
Azure App Service: This PaaS offering allows developers to build, deploy, and manage web applications without dealing with the underlying infrastructure. It supports various programming languages and frameworks, making it suitable for a wide range of applications.
Azure Kubernetes Service (AKS): For containerized applications, AKS provides a managed Kubernetes service. Kubernetes simplifies the deployment and management of containerized applications, and AKS further streamlines this process.
Exploring Azure Platform-as-a-Service (PaaS) Services
Platform-as-a-Service (PaaS) takes cloud hosting a step further by abstracting away even more of the infrastructure management, allowing developers to focus primarily on building and deploying applications. Azure offers an array of PaaS services that cater to different needs:
Azure SQL Database: This fully managed relational database service eliminates the need for database administration tasks such as patching and backups. It offers high availability, security, and scalability for your data.
Azure Cosmos DB: For globally distributed, highly responsive applications, Azure Cosmos DB is a NoSQL database service that guarantees low-latency access and automatic scaling.
Azure Functions: A serverless compute service, Azure Functions allows you to run code in response to events without provisioning or managing servers. It's ideal for event-driven architectures.
Azure Logic Apps: This service enables you to automate workflows and integrate various applications and services without writing extensive code. It's great for orchestrating complex business processes.
Benefits of Azure Cloud Hosting and PaaS Services
Scalability: Azure's elasticity allows you to scale resources up or down based on demand. This ensures optimal performance and cost efficiency.
Cost Management: With pay-as-you-go pricing, you only pay for the resources you use. Azure also provides cost management tools to monitor and optimize spending.
High Availability: Azure's data centers are distributed globally, providing redundancy and ensuring high availability for your applications.
Security and Compliance: Azure offers robust security features and compliance certifications, helping you meet industry standards and regulations.
Developer Productivity: PaaS services like Azure App Service and Azure Functions streamline development by handling infrastructure tasks, allowing developers to focus on writing code.
Use Cases for Azure Cloud Hosting and PaaS
Web Applications: Azure App Service is ideal for hosting web applications, enabling easy deployment and scaling without managing the underlying servers.
Microservices: Azure Kubernetes Service supports the deployment and orchestration of microservices, making it suitable for complex applications with multiple components.
Data-Driven Applications: Azure's PaaS offerings like Azure SQL Database and Azure Cosmos DB are well-suited for applications that rely heavily on data storage and processing.
Serverless Architecture: Azure Functions and Logic Apps are perfect for building serverless applications that respond to events in real-time.
In conclusion, Microsoft Azure's Cloud Hosting and PaaS Services provide businesses with the tools they need to harness the power of the cloud while minimizing the complexities of infrastructure management. With scalability, cost-efficiency, and a wide array of services, Azure empowers developers and organizations to innovate and deliver impactful applications. Whether you're hosting a web application, managing data, or adopting a serverless approach, Azure has the tools to support your journey into the cloud.
#Microsoft Azure#Internet of Things#Azure AI#Azure Analytics#Azure IoT Services#Azure Applications#Microsoft Azure PaaS
2 notes
·
View notes
Text
Odoo Implementation Services
— A Technical Guide to ERP Deployment
In today’s hyperconnected business landscape, digital transformation is no longer a luxury — it is a necessity. As organizations scale and diversify, managing complex workflows and ensuring real-time data access becomes crucial. Enterprise Resource Planning (ERP) systems like Odoo offer a powerful way to unify operations, streamline processes, and boost organizational agility. Businesses can achieve this transformation effectively through Odoo Implementation Services, which align the ERP’s deployment with specific operational and technical goals.
However, Odoo’s potential isn’t unlocked by default. It requires a structured, technically rigorous implementation — one that aligns with your business objectives, IT infrastructure, and long-term growth strategies. Implementing Odoo is more than installing software; it’s a systems-level engineering process demanding careful design, accurate configuration, and strategic foresight.
Understanding the Odoo Framework
Odoo operates on a Model-View-Controller (MVC) architecture. The backend is powered by Python, while PostgreSQL handles data storage. Its modular nature allows organizations to deploy only what they need — from Sales and CRM to Accounting, Inventory, HR, and beyond — all while maintaining seamless inter-module communication.
But these modules don’t integrate themselves. Misconfiguration can lead to data inconsistencies, bottlenecks, or security risks. That’s why technical discipline during implementation is essential.
1.0 Requirement Engineering and Process Mapping
Every successful deployment begins with deep understanding.
Business needs are captured through stakeholder interviews, process documentation, and technical audits.
Workflows are visualized using Business Process Model and Notation (BPMN) or similar methods.
These are then mapped against Odoo’s out-of-the-box capabilities to define:
Configuration scope
Custom development requirements
Functional gaps
This results in a comprehensive system blueprint — a document that aligns every stakeholder and sets expectations clearly.
2.0 Architecture and Infrastructure Design
With business processes mapped, the next step is setting the right technical foundation.
Key Considerations:
Hosting Choices: Odoo Online (SaaS), on-premise, or third-party cloud (AWS, DigitalOcean, etc.)
Database Design: PostgreSQL setup, replication, indexing strategies
Access & Security:
User role hierarchy
Access control layers
SSL certificates, firewall settings
Infrastructure Planning:
Backup automation
Load balancing and scaling
High availability setup
DNS and mail server configuration
A well-architected infrastructure ensures performance, security, and long-term scalability.
3.0 Module Configuration and Custom Development
Odoo’s default modules often meet 70–80% of business requirements — the rest needs customization.
Configuration Includes:
Adjusting user interfaces via XML views
Creating custom fields, logic, or workflows in Python
Implementing automated actions, scheduled jobs, and domain filters
Writing record rules and access rights for data governance
All custom code should follow Odoo’s conventions and be version-controlled using Git or similar tools to ensure traceability and maintainability.
4.0 Data Migration and Validation
Migrating legacy data is often underestimated — but it can make or break the system.
ETL (Extract, Transform, Load) Steps:
Extraction: Exporting data from legacy systems (CSV, Excel, SQL exports)
Transformation:
Normalizing data to match Odoo schema
Ensuring date, currency, and unit consistency
Loading: Importing into Odoo using scripts or UI tools
Key Considerations:
Ensuring relational integrity between models (e.g., invoices linked to customers)
Preserving audit trails and historical logs
Running dry migrations to identify errors early
Thorough validation scripts help ensure completeness and accuracy post-migration.
5.0 Integration with External Systems
Businesses rarely operate in isolation. Odoo must often integrate with:
Payment gateways (Razorpay, Stripe)
Shipping APIs (Shiprocket, DHL)
CRM tools, HRMS, or Data Warehouses
Integration Techniques:
REST APIs / XML-RPC calls
Webhooks for real-time data exchange
OAuth2 or token-based authentication
Middleware for protocol translation or queue handling
Error logging and retry mechanisms are implemented to prevent data loss or syncing failures.
6.0 Functional Testing and Quality Assurance
Before go-live, the system is tested from all angles — technically and functionally.
Testing Includes:
Unit tests for custom logic
Workflow walkthroughs across departments
Security and access control validations
Load testing for concurrent users
Device and browser compatibility
Test environments mirror the live setup to simulate real-world conditions and reduce surprises at rollout.
7.0 User Acceptance Testing (UAT) and Documentation
UAT is the bridge between development and deployment. Real users test real scenarios.
Focus Areas:
User-friendliness
Accuracy of business logic
Speed of operations
Error handling in edge cases
In parallel, documentation is created:
System architecture diagrams
Role-based user guides
SOPs (Standard Operating Procedures)
Escalation paths and troubleshooting manuals
This ensures teams are self-sufficient post-launch.
8.0 Deployment and Production Rollout
Deployment is executed through a controlled cutover strategy, often on weekends or low-traffic periods.
Rollout Checklist:
Final data sync
Activation of live users
Sanity testing of critical flows
System monitoring setup (CPU, RAM, DB load)
Emergency rollback plan
Post-deployment support is kept on standby for immediate issue resolution.
9.0 Post-Go-Live Support and Optimization
The launch is not the end — it’s just the beginning of continuous improvement.
Activities in This Phase:
Monitoring server performance and query optimization
Handling support tickets and change requests
Patch management and version upgrades
Rolling out additional modules in phases
Collecting feedback for UX and process refinements
A feedback loop ensures the system evolves in sync with business needs.
10.0 Conclusion
Implementing Odoo is not just a technical task — it's a transformative journey. Each phase of the implementation lifecycle, from requirement gathering to post-go-live optimization, plays a vital role in determining success.
With the right expertise, planning, and execution, Odoo becomes more than an ERP — it becomes the backbone of operational excellence.
0 notes
Text
Fortifying Your Online Presence Top Web Security Solutions to Protect Your Digital Assets
In today’s digital landscape, a strong online presence is essential but it also comes with significant security risks. Cyber threats like hacking, data breaches, malware, and phishing attacks can compromise your website, damage your brand, and result in financial loss. That’s why implementing robust web security solutions is more critical than ever. From firewalls and SSL certificates to DDoS protection and real-time threat monitoring, these tools safeguard your digital assets and ensure safe, uninterrupted access for your users. In this blog, we’ll explore the top web security that help protect your website, preserve user trust, and maintain your online integrity.
The Importance of a Secure Web Infrastructure
A strong web security solutions infrastructure forms the foundation of digital security. It includes secure hosting environments, updated server software, and properly configured networks. Without these basics, even the most advanced security tools can fall short. A secure infrastructure protects your website from vulnerabilities that hackers often exploit, such as outdated scripts or weak configurations. Regular updates, server patches, and backups ensure stability and reduce the risk of cyberattacks. Web security begins with building on a solid base one that supports all other layers of protection. By prioritizing infrastructure security, businesses can prevent breaches and safeguard their digital presence from the ground up.
SSL Certificates and HTTPS Encryption
Secure Sockets Layer (SSL) certificates are essential for encrypting data transmitted between a user’s browser and your website. By enabling HTTPS, SSL ensures that sensitive information like passwords, credit card numbers, and personal details remain private and secure. This encryption protects your users from man-in-the-middle attacks and builds trust by displaying the padlock icon in browsers. Moreover, search engines like Google favor HTTPS-enabled sites, giving you an SEO advantage. Installing an SSL certificate is one of the easiest and most effective ways to boost web security. It’s a critical first step in establishing credibility and protecting user data online.
Web Application Firewalls for Real-Time Protection
A Web Application Firewall acts as a shield between your website and incoming traffic, filtering out malicious requests before they reach your server. Detect and block threats like SQL injection, cross-site scripting, and file inclusion attacks in real time. They are especially valuable for businesses that handle sensitive customer data or rely on e-commerce platforms. Whether cloud-based or hardware-driven, WAFs can be customized to fit specific security needs, offering scalable protection. Implementing a WAF not only enhances website security but also ensures smoother performance and increased uptime making it a key component in a comprehensive web security strategy.
DDoS Protection to Maintain Website Availability
Distributed Denial of Service attacks aim to overwhelm your website with traffic, causing downtime and disrupting operations. These attacks can last for hours or even days, costing businesses significant revenue and damaging customer trust. protection services work by identifying and filtering malicious traffic while allowing legitimate users uninterrupted access. They use advanced algorithms, load balancing, and traffic scrubbing to neutralize the threat before it impacts your site. Implementing a reliable mitigation solution is essential for maintaining availability, especially for high-traffic websites. It ensures business continuity and resilience against one of the most common and disruptive cyber threats.
Malware Detection and Removal Tools
Malware can silently infiltrate your website, stealing data, redirecting traffic, or damaging your brand’s reputation. Regular malware scanning and automatic removal tools are crucial for identifying and eliminating harmful code. These solutions monitor files, plugins, and content management systemweb security solutionss for suspicious activity or unauthorized changes. Infected sites not only lose visitors but may also be blacklisted by search engines. By using trusted malware detection software, you can act swiftly to contain threats and restore your website’s integrity. Early detection prevents more serious breaches and gives your visitors confidence that your site is safe and secure to browse.
Secure Authentication and Access Controls
Unauthorized access is a major cybersecurity risk, especially for websites with multiple users or administrative roles. Implementing strong authentication methods like two-factor authentication, biometric logins, and role-based access controls helps prevent breaches caused by weak or stolen passwords. Limit access to sensitive areas of your site based on user roles and regularly review permissions to minimize vulnerabilities. Secure login protocols not only protect internal data but also reduce the risk of backdoor entry by cybercriminals. By tightening access controls and using advanced authentication, you can significantly enhance the security of your web environment and protect it from internal and external threats.
Regular Security Audits and Vulnerability Assessments
Security isn’t a one-time setup it’s an ongoing process. Regular audits and vulnerability assessments are essential to identify new risks and ensure all defenses are up to date. These evaluations involve checking for outdated plugins, scanning for open ports, testing input fields for injection flaws, and assessing access logs. Cybersecurity experts use both automated tools and manual penetration testing to uncover weaknesses before attackers do. Regular assessments help prioritize fixes, maintain compliance with regulations, and provide peace of mind. Staying proactive with security audits ensures that your website adapts to the ever-changing threat landscape and remains fortified against potential breaches.
Conclusion
In today’s ever-evolving digital landscape, protecting your website and data is more important than ever. Implementing robust web security solutions such as SSL encryption, firewalls, DDoS protection, malware detection, and secure authentication ensures your digital assets remain safe from cyber threats. Regular security audits and tailored protection strategies not only enhance user trust but also keep your business compliant and resilient. With the right tools and proactive measures, you can confidently fortify your online presence and prevent costly disruptions. In a world where online threats never rest, staying vigilant and secure is the key to long-term digital success and peace of mind.
0 notes
Video
youtube
Amazon RDS for PostgreSQL | Optimize and Manage Your Databases
RDS for PostgreSQL provides a managed environment for the advanced open-source PostgreSQL database. Known for its extensibility and support for complex queries, PostgreSQL is ideal for applications that require advanced data types, custom functions, and robust data integrity.
- Key Features: - Support for JSON, full-text search, and advanced indexing. - Extensions such as PostGIS for geospatial data. - Automatic backups, software patching, and database monitoring. - Multi-AZ deployments for high availability.
- Use Cases: - Complex business applications. - Data warehousing and analytics. - Applications requiring advanced data manipulation and integrity.
Key Benefits of Choosing the Right Amazon RDS Database:
1. Optimized Performance: Select an engine that matches your performance needs, ensuring efficient data processing and application responsiveness. 2. Scalability: Choose a database that scales seamlessly with your growing data and traffic demands, avoiding performance bottlenecks. 3. Cost Efficiency: Find a solution that fits your budget while providing the necessary features and performance. 4. Enhanced Features: Leverage advanced capabilities specific to each engine to meet your application's unique requirements. 5. Simplified Management: Benefit from managed services that reduce administrative tasks and streamline database operations.
Conclusion:
Choosing the right Amazon RDS database engine is critical for achieving the best performance, scalability, and functionality for your application. Each engine offers unique features and advantages tailored to specific use cases, whether you need the speed of Aurora, the extensibility of PostgreSQL, the enterprise features of SQL Server, or the robustness of Oracle. Understanding these options helps ensure that your database infrastructure meets your application’s needs, both now and in the future.
aws rds,Amazon RDS for PostgreSQL,cloud computing,Amazon RDS for PostgreSQL | Optimize and Manage Your Databases,aws for beginners,amazon web services,aws cloud,What Is Amazon RDS for PostgreSQL?,What Is Amazon RDS for PostgreSQL Key Features?,What Is Amazon RDS for PostgreSQL Use Cases?,cloudolus,aws bangla,AWS for Beginners,ClouDolus,Right Amazon RDS Database,rds,Optimize,Manage Your Databases,Databases,PostgreSQL,free course,aws training,Key Benefits,amazon
#AmazonRDS #RDSMonitoring #PerformanceInsights #CloudWatch #AWSDevOps #DatabaseOptimization #ClouDolus #ClouDolusPro
📢 Subscribe to ClouDolus for More AWS & DevOps Tutorials! 🚀 🔹 ClouDolus YouTube Channel - https://www.youtube.com/@cloudolus 🔹 ClouDolus AWS DevOps - https://www.youtube.com/@ClouDolusPro
*THANKS FOR BEING A PART OF ClouDolus! 🙌✨*
***************************** *Follow Me* https://www.facebook.com/cloudolus/ | https://www.facebook.com/groups/cloudolus | https://www.linkedin.com/groups/14347089/ | https://www.instagram.com/cloudolus/ | https://twitter.com/cloudolus | https://www.pinterest.com/cloudolus/ | https://www.youtube.com/@cloudolus | https://www.youtube.com/@ClouDolusPro | https://discord.gg/GBMt4PDK | https://www.tumblr.com/cloudolus | https://cloudolus.blogspot.com/ | https://t.me/cloudolus | https://www.whatsapp.com/channel/0029VadSJdv9hXFAu3acAu0r | https://chat.whatsapp.com/BI03Rp0WFhqBrzLZrrPOYy *****************************
#youtube#aws rdsAmazon RDS for PostgreSQLcloud computingAmazon RDS for PostgreSQL | Optimize and Manage Your Databasesaws for beginnersamazon web ser#AmazonRDS RDSMonitoring PerformanceInsights CloudWatch AWSDevOps DatabaseOptimization ClouDolus ClouDolusPro
0 notes
Text
Top WebApp Security Checklist for Businesses in the USA (2025)

In today’s digital-first world, web applications are the backbone of most business operations—from e-commerce to customer portals, CRMs, and more. However, with increasing cyber threats, securing your web applications is not optional; it's critical. Especially for businesses operating in the USA, where data breaches can lead to legal penalties, loss of customer trust, and significant financial setbacks.
This guide outlines a comprehensive WebApp Security Checklist tailored for businesses in the USA to ensure robust protection and compliance with modern security standards.
1. Use HTTPS with a Valid SSL Certificate
Secure Socket Layer (SSL) certificates are fundamental. HTTPS encrypts the data exchanged between the user and your application, ensuring it remains private.
Purchase and install a trusted SSL certificate.
Redirect all HTTP traffic to HTTPS.
Regularly renew and monitor the validity of your SSL certificate.
Fact: Google flags HTTP sites as “Not Secure,” impacting SEO and user trust.
2. Implement Strong Authentication & Access Controls

Weak login systems are a hacker’s playground. Use:
Multi-Factor Authentication (MFA): Add extra layers beyond passwords.
Role-Based Access Control (RBAC): Ensure users only access what’s necessary.
Session Management: Set session expiration limits and auto-logout on inactivity.
Bonus Tip: Use OAuth 2.0 or OpenID Connect for secure federated authentication.
3. Sanitize and Validate All User Inputs
Most web attacks like SQL Injection and XSS stem from unsanitized user inputs. To prevent this:
Sanitize inputs on both client and server sides.
Use prepared statements and parameterized queries.
Escape special characters in output to prevent script injections.
Best Practice: Never trust user inputs — even from authenticated users.
4. Regularly Update Dependencies and Frameworks
Outdated plugins, libraries, or frameworks can be exploited easily.
Use dependency management tools like npm audit, pip-audit, or OWASP Dependency-Check.
Enable automatic updates where possible.
Avoid deprecated plugins or unsupported software.
Real Example: The infamous Log4j vulnerability in 2021 exposed millions of apps worldwide.
5. Conduct Regular Vulnerability Scans and Penetration Testing
Security is not a one-time fix. It's a continuous process.
Schedule monthly or quarterly vulnerability scans.
Hire ethical hackers for real-world pen testing.
Fix discovered issues immediately and re-test.
🔍 Tools to Use: Nessus, Burp Suite, OWASP ZAP.
6. Implement Secure APIs

With APIs powering most modern web apps, they’re a common attack vector.
Authenticate API users with tokens (JWT, OAuth).
Rate-limit API calls to avoid abuse.
Use API gateways for logging and security enforcement.
Extra Tip: Never expose sensitive internal APIs to the public internet.
7. Data Encryption at Rest and in Transit
Whether storing user passwords, payment info, or PII — encryption is essential.
Encrypt sensitive data in the database using AES-256 or better.
Avoid storing passwords in plain text — use hashing algorithms like bcrypt.
Always encrypt data transfers via HTTPS or secure VPN tunnels.
Compliance: Required under data protection laws like HIPAA, CCPA, and PCI-DSS.
8. Monitor Logs & Set Up Intrusion Detection
Monitoring can alert you to threats in real-time.
Use centralized logging systems like ELK Stack or Splunk.
Implement intrusion detection systems (IDS) like Snort or OSSEC.
Set up alerts for unusual activities like multiple failed logins.
Tip: Review logs weekly and set up daily summaries for admins.
9. Backup Regularly & Prepare a Disaster Recovery Plan
Cyberattacks like ransomware can lock you out of your app.
Schedule automatic daily backups.
Store backups offsite or in the cloud (with encryption).
Test your disaster recovery plan quarterly.
Pro Tip: Use versioned backups to roll back only the infected data.
10. Comply with Data Privacy Regulations
For businesses in the USA, compliance isn't just good practice — it's the law.
If you handle health data → HIPAA compliance is mandatory.
Selling to California residents → comply with CCPA.
Accepting payments? → follow PCI-DSS requirements.
Reminder: Non-compliance can lead to heavy penalties and lawsuits.
11. Educate Your Team
The weakest link is often human error.
Train employees on phishing and social engineering attacks.
Enforce strong password policies.
Run annual cybersecurity awareness programs.
Result: A well-trained team is your first line of defense.
12. Use Web Application Firewalls (WAFs)

WAFs provide an extra layer of protection.
Block malicious traffic before it reaches your server.
Protect against DDoS, brute force, and zero-day attacks.
Use cloud-based WAFs like Cloudflare, AWS WAF, or Imperva.
Bonus: Easily deployable and scalable with your infrastructure.
Conclusion
For U.S.-based businesses, web application security should be a strategic priority — not a checkbox. With cyberattacks growing in complexity and volume, following a thorough security checklist is vital to protect your data, users, and brand reputation.
At the end of the day, your web application is only as secure as its weakest link. Make sure there isn’t one.
Ready to Secure Your WebApp?
If you're looking for expert support to secure or build a robust, secure web application, WeeTech Solution is here to help. Get in touch with our development and cybersecurity team today!
0 notes
Text
What Are the Key Roles in IT Infrastructure Management?
In the modern business age of the digital world, IT Infrastructure Management is what keeps businesses running well. The task of IT infrastructure management entails efforts made in diverse areas, including the maintenance of network performance and protection of the data security. But what are exactly the major roles that make this ecosystem to be efficient?
What are the most central positions and responsibilities that propel up a reliable, safe and scalable IT infrastructure? Let us go over them at a time.

1. IT Infrastructure Manager
The head of the ladder is IT Infrastructure Manager. Such an individual is involved in planning, designing and executing the whole IT infrastructure of an organization. They make sure that every hardware, software, network as well as cloud-based service are in line with business objectives.
They have day to day tasks of budgeting IT resources, vendor selection, team management, decisions on upgrade or change of systems among others. They also liaise with the top level management to ensure that the roadmap of the infrastructure matches the growth strategies of the business.
2. Network Administrator
The Network Administrator has the duty to maintain the network systems in the company. These are local area networks (LAN), wide area networks (WAN), firewalls, routers and switches. It is their task to maintain continuous connectivity and solve any problems connected with network performance.
They can be found in the background, doing software update and vulnerability patching and management, and uptime. Businesses would be experiencing constant blackouts and jeopardized security without network administrators.
3. System Administrator
System Administrators are often mixed up with the network administrators, but they take more attention to the machines, operating systems and servers. They administer, modify, and guarantee stable performance of the computer systems particularly the multi-user computers such as servers.
General system admins are involved in a user setup, maintenance of accesses, backup, and system status. They also do software upgrades and repair hardware.
4. Database Administrator (DBA)
Most businesses rely on data in the world today. Database Administrator makes sure that vital information is stored, retrieved, and secured in a streamlined way. They keep up database platforms such as Oracle, SQL Server or MySQL, according to the requirements of the organization.
They clean up performances, configure backup and recovery procedures, apply data access control, and observe storage. They also collaborate with security departments in ensuring they guard information that may be accessed or lost without authorization.
5. Cloud Infrastructure Engineer
As other enterprises increasingly migrate to the cloud, the importance of a Cloud Infrastructure Engineer has gotten significant adoption. Such experts control systems operating in the cloud: AWS, Azure or Google Cloud.
They are to implement virtual servers, allow cloud security, cloud cost optimization, and deployment automation. They make sure that the organization takes advantage of the use of cloud technology in an effective way that neither performance nor security is affected.
6. IT Security Specialist
Cybersecurity is not an option anymore. IT Security Specialist is specialized in ensuring the safety of the infrastructure against threats, breach and vulnerability. They would watch networks and look at certain abnormal activities, use firewalls, and encrypt data, and they would make security audits frequently.
They also teach the other members of the team about good practices and adherence to regulations such as GDPR, HIPAA, etc.
7. Help Desk and Support Teams
The IT Support and Help Desk Teams are the ones who are frequently ignored, but at the same time, his workforce has to be part of the management of an infrastructure. The employees contact them when there are technical problems.
Such specialists are involved in password recovery, installation of software, and assistance. Proper support team eases productivity as issues are solved within the shortest time possible.
Conclusion
IT Infrastructure Management relies on all the diverse jobs dedicated to keep the system stable, performing well, and secure. All the job titles, be they network administrator, system admin, or cloud engineer are essential to guarantee a well-functioning technology foundation of an enterprise. The right team in the right place is not only important, but also necessary as the organizations keep on expanding and changing. Knowledge of these top functions will help businesses to organize their IT departments, prevent their outages, as well as being ready to meet any technological needs in future.
1 note
·
View note
Text
Ultimate Checklist for Web App Security in the Cloud Era

As businesses increasingly migrate their applications and data to the cloud, the landscape of cyber threats has evolved significantly. The flexibility and scalability offered by cloud platforms are game-changers, but they also come with new security risks. Traditional security models no longer suffice. In the cloud web app security era, protecting your web applications requires a modern, proactive, and layered approach. This article outlines the ultimate security checklist for web apps hosted in the cloud, helping you stay ahead of threats and safeguard your digital assets.
1. Use HTTPS Everywhere
Secure communication is fundamental. Always use HTTPS with TLS encryption to ensure data transferred between clients and servers remains protected. Never allow any part of your web app to run over unsecured HTTP.
Checklist Tip:
Install and renew SSL/TLS certificates regularly.
Use HSTS (HTTP Strict Transport Security) headers.
2. Implement Identity and Access Management (IAM)
Cloud environments demand strict access control. Implement robust IAM policies to define who can access your application resources and what actions they can perform.
Checklist Tip: - Use role-based access control (RBAC). - Enforce multi-factor authentication (MFA). - Apply the principle of least privilege.
3. Secure APIs and Endpoints
Web applications often rely heavily on APIs to exchange data. These APIs can become a major attack vector if not secured properly.
Checklist Tip: - Authenticate and authorize all API requests. -Use API gateways to manage and monitor API traffic. - Rate-limit API requests to prevent abuse.
4. Patch and Update Regularly
Outdated software is a common entry point for attackers. Ensure that your application, dependencies, frameworks, and server environments are always up to date.
Checklist Tip: - Automate updates and vulnerability scans. - Monitor security advisories for your tech stack. - Remove unused libraries and components.
5. Encrypt Data at Rest and in Transit
To meet compliance requirements and protect user privacy, data encryption is non-negotiable. In the cloud, this applies to storage systems, databases, and backup services.
Checklist Tip: - Use encryption standards like AES-256. - Store passwords using secure hashing algorithms like bcrypt or Argon2. - Encrypt all sensitive data before saving it.
6. Configure Secure Storage and Databases
Misconfigured cloud storage (e.g., public S3 buckets) has led to many major data breaches. Ensure all data stores are properly secured.
Checklist Tip: - Set access permissions carefully—deny public access unless necessary. - Enable logging and alerting for unauthorized access attempts. - Use database firewalls and secure credentials.
7. Conduct Regular Security Testing
Routine testing is essential in identifying and fixing vulnerabilities before they can be exploited. Use both automated tools and manual assessments.
Checklist Tip: - Perform penetration testing and vulnerability scans. - Use tools like OWASP ZAP or Burp Suite. - Test code for SQL injection, XSS, CSRF, and other common threats.
8. Use a Web Application Firewall (WAF)
A WAF protects your application by filtering out malicious traffic and blocking attacks such as XSS, SQL injection, and DDoS attempts.
Checklist Tip: - Deploy a WAF provided by your cloud vendor or a third-party provider. - Customize WAF rules based on your application’s architecture. - Monitor logs and update rule sets regularly.
9. Enable Real-Time Monitoring and Logging
Visibility is key to rapid response. Continuous monitoring helps detect unusual behavior and potential breaches early.
Checklist Tip: - Use centralized logging tools (e.g., ELK Stack, AWS CloudWatch). - Set up real-time alerts for anomalies. - Monitor user activities, login attempts, and API calls.
10. Educate and Train Development Teams
Security should be baked into your development culture. Ensure your team understands secure coding principles and cloud security best practices.
Checklist Tip: - Provide regular security training for developers. - Integrate security checks into the CI/CD pipeline. - Follow DevSecOps practices from day one.
Final Thoughts
In the cloud web app security era, businesses can no longer afford to treat security as an afterthought. Threats are evolving, and the attack surface is growing. By following this security checklist, you ensure that your web applications remain secure, compliant, and resilient against modern cyber threats. From identity management to encrypted storage and real-time monitoring, every step you take now strengthens your defense tomorrow. Proactivity, not reactivity, is the new gold standard in cloud security.
#web application development company india#web application development agency#web application development firm#web application and development#web app development in india#custom web application development
0 notes
Text
Reliable Website Maintenance Services In India | NRS Infoways
In today’s hyper‑connected marketplace, a website is far more than a digital brochure—it is the beating heart of your brand experience, your lead‑generation engine, and your most valuable sales asset. Yet many businesses still treat their sites as “launch‑and‑forget” projects, only paying attention when something breaks. At NRS Infoways, we understand that real online success demands continuous care, proactive monitoring, and seamless enhancements. That’s why we’ve built our Reliable Website Maintenance Services In India to deliver round‑the‑clock peace of mind, bulletproof performance, and measurable ROI for forward‑thinking companies like yours.
Why Website Maintenance Matters—And Why “Reliable” Makes All the Difference
Search engines reward fast, secure, and regularly updated sites with higher rankings; customers reward them with trust and loyalty. Conversely, a sluggish, outdated, or vulnerable site can cost you traffic, conversions, and brand reputation—sometimes overnight. Our Reliable Website Maintenance Services In India go beyond the basic “fix‑it‑when‑it‑breaks” model. We combine proactive health checks, performance tuning, security hardening, and content optimization into a single, cohesive program that keeps your digital storefront open, polished, and ready for growth.
What Sets NRS Infoways Apart?
1. Proactive Performance Monitoring
We leverage enterprise‑grade monitoring tools that continuously scan load times, server resources, and user journeys. By identifying bottlenecks before they escalate, we ensure smoother experiences and higher conversion rates—24/7.
2. Robust Security & Compliance
From real‑time threat detection to regular firewall updates and SSL renewals, your site stays impervious to malware, SQL injections, and DDoS attacks. We align with global standards such as GDPR and PCI‑DSS, keeping you compliant and trustworthy.
3. Seamless Content & Feature Updates
Launching a new product line? Running a seasonal promotion? Our dedicated team updates layouts, landing pages, and plugins—often within hours—to keep your messaging sharp and relevant without disrupting uptime.
4. Data‑Driven Optimization
Monthly analytics reviews highlight user behavior, bounce rates, and conversion funnels. We translate insights into actionable tasks—A/B testing CTAs, compressing heavy images, or refining navigation—all folded into our maintenance retainer.
5. Transparent Reporting & SLAs
Every client receives detailed monthly reports covering task logs, incident resolutions, and performance metrics. Our Service Level Agreements guarantee response times as low as 30 minutes for critical issues, underscoring the “Reliable” in our Reliable Website Maintenance Services In India.
Real‑World Impact: A Success Snapshot
A Delhi‑based B2B SaaS provider reached out to NRS Infoways after repeated downtime eroded user trust and slashed demo bookings by 18 %. Within the first month of onboarding, we:
Migrated their site to a high‑availability cloud cluster
Deployed a Web Application Firewall (WAF) to fend off bot attacks
Compressed multimedia assets, cutting average load time from 4.2 s to 1.3 s
Implemented weekly backup protocols with versioned restores
Result? Organic traffic climbed 27 %, demo sign‑ups rebounded 31 %, and support tickets fell by half—proving that consistent, expert care translates directly into revenue.
Flexible Plans That Scale With You
Whether you manage a lean startup site or a sprawling enterprise portal, we offer tiered packages—Basic, Professional, and Enterprise—each customizable with à‑la‑carte add‑ons like e‑commerce catalog updates, multi‑language support, or advanced SEO audits. As your business evolves, our services scale seamlessly, ensuring you never pay for overhead you don’t need or sacrifice features you do.
Partner With NRS Infoways Today
Your website is too important to leave to chance. Join the growing roster of Indian businesses that rely on NRS Infoways for Reliable Website Maintenance Services In India and experience the freedom to innovate while we handle the technical heavy lifting. Ready to protect your digital investment, delight your visitors, and outpace your competition?
Connect with our maintenance experts now and power your growth with reliability you can measure.
0 notes
Text
BeDrive Nulled Script 3.1.5

Discover the Power of BeDrive Nulled Script – The Ultimate File Sharing & Cloud Storage Solution If you're searching for a powerful, user-friendly, and reliable cloud storage solution, look no further than the BeDrive Nulled Script. Designed for modern entrepreneurs, developers, and tech-savvy users, this high-performance platform offers seamless file sharing and secure cloud storage at your fingertips—without breaking the bank. What is BeDrive Nulled Script? The BeDrive Nulled Script is a premium file sharing and cloud storage platform developed using cutting-edge web technologies. It's the perfect alternative to mainstream services like Google Drive and Dropbox, offering the same robust functionalities with full control over your data. With its clean user interface and rich feature set, BeDrive is an ideal solution for startups, SaaS providers, and digital product marketplaces. Why Choose BeDrive Nulled Script? Getting your hands on the BeDrive Nulled Script means unlocking the full potential of a premium cloud storage system—entirely free. Whether you're hosting large files, collaborating with teams, or managing private user folders, BeDrive handles it all with efficiency and style. Thanks to its nulled version, users can enjoy premium features without the hefty licensing fees, making it a go-to choice for budget-conscious innovators. Technical Specifications Backend: Laravel Framework (robust, secure, and scalable) Frontend: Vue.js for a fast and interactive UI Database: MySQL or MariaDB supported Storage: Compatible with local storage, Amazon S3, and DigitalOcean Spaces File Types: Supports documents, videos, images, and compressed files Security: User authentication, folder permissions, and file encryption Key Features and Benefits Multi-user Support: Allow multiple users to register and manage their own files securely. Drag-and-Drop Upload: Easy file uploads with a modern drag-and-drop interface. File Previews: View PDFs, images, and videos directly within the platform. Folder Organization: Create, rename, and manage folders just like on your desktop. Sharing Options: Share files publicly or privately with time-limited links. Advanced Admin Panel: Monitor user activity, storage usage, and platform performance. Popular Use Cases The BeDrive Nulled Script is incredibly versatile. Here are just a few ways you can use it: Freelancers: Share deliverables securely with clients and collaborators. Agencies: Manage and distribute digital assets for projects and campaigns. Online Communities: Offer cloud storage features as part of a paid membership site. Startups: Launch your own file-sharing or backup service without building from scratch. Installation Guide Setting up the BeDrive Nulled Script is quick and hassle-free. Follow these steps to get started: Download the full script package from our website. Upload the files to your preferred hosting server. Create a new MySQL database and import the provided SQL file. Run the installation wizard to complete setup and admin configuration. Start uploading and sharing your files instantly! Make sure your hosting environment supports PHP 8.0 or later for optimal performance. FAQs – BeDrive Nulled Script 1. Is the BeDrive Nulled Script safe to use? Yes, the script is thoroughly tested for safety and performance. We recommend using secure hosting and regular updates to keep your platform safe. 2. Do I need coding knowledge to use it? No, the platform is designed to be user-friendly. However, basic web hosting knowledge will make installation and customization easier. 3. Can I monetize my BeDrive installation? Absolutely! Add premium user plans, integrate ads, or offer subscription models to monetize your cloud service. 4. What if I face issues during setup? We provide comprehensive installation documentation, and our community is always ready to help you troubleshoot any challenges. Download BeDrive Nulled Script Now Unlock the full potential of premium cloud storage for free with the BeDrive .
No hidden costs, no licensing fees—just powerful tools at your command. Looking for more great tools? Check out our vast library of nulled plugins to boost your digital projects. Also, if you're searching for top-quality WordPress themes, don’t miss the avada nulled theme—another fan-favorite you can grab for free!
0 notes
Text
Database Center GCP: Smarter Fleet Management with AI

Database Centre GCP
The AI-powered Database Centre, now GA, simplifies database fleet management.
Database Centre, an AI-powered unified fleet management system, streamlines database fleet security, optimisation, and monitoring. Next 25 Google Cloud announced its general availability.
Google Cloud Database Centre is an AI-powered fleet management system. It is commonly available.
Database Centre GCP simplifies database fleet administration, including security, optimisation, and monitoring. This AI-enabled dashboard provides a unified picture of your database fleet. We want to unleash your data's power and organise your database fleet.
It replaces disconnected tools, complex scripts, APIs, and other arduous database fleet monitoring methods. Database Centre offers a complete experience using Google's AI models.
AlloyDB Aiven is also available. Omni simplifies multi-cloud AI
The main Database Centre characteristics and capabilities are:
Unified view: It eliminates information silos and the need to seek customised tools and spreadsheets by showing your whole database fleet. This provides unparalleled database knowledge.
Database Centre GCP uses AI to make intelligent insights. It actively reduces fleet risk with smart performance, reliability, cost, compliance, and security advice.
Optimise your database fleet with AI-powered support. Using natural language chat, fleet issues may be resolved quickly and optimisation ideas given. This interface uses Gemini for usability.
Database Centre GCP improves health and performance tracking for several Google Cloud databases, including:
For PostgreSQL, AlloyDB
Bigtable
Memorystore
Firestore
MySQL, PostgreSQL, and SQL Server Cloud SQL Tracking Health Issues It summarises your fleet's most pressing health issues from your Security Command Centre and Google Cloud projects. It then suggests investigating affected projects or situations. You can monitor several health issues:
Used database engines and versions;
Important databases' availability and outage risk.
How well backups protect critical databases from errors and calamities.
If resources follow security best practices.
Find databases that don't meet industry requirements. The dashboard shows category problem counts. Your Google Cloud database footprint.
Database Centre GCP improves recommendations for supported databases with general availability, addressing issues like ineffective queries/indexes, high resource usage, hotspot detection, costly commands, deletion protection not enabled, and no automated backup policy.
Gemini Integration: Gemini provides clever ideas and an easy-to-use chat interface. Gemini Chat answers database fleet health questions, makes project-specific advice, and helps determine and implement the appropriate practices. It helps troubleshoot aid performance.
Saveable Views: Users can create, store, and share persona-specific views.
Historical Data: Users can track weekly issues and new database resources.
Alerting: Centralises occurrences and database alerting policies.
Database Governance Risks: Database Centre GCP reduces database governance risks, including procedures and tools for monitoring and protecting sensitive data access throughout its lifecycle. It helps enforce best practices and identify compliance issues.
Database Centre benefits enterprises with cloud resources across several projects and products. It protects database resources against outages.
Price and Database Centre Access
Database Centre is accessible from the Google Cloud managed database services console for Cloud SQL, AlloyDB, Spanner, and Bigtable. Users with IAM rights have it enabled by default.
Google Cloud users can access Database Centre GCP for free. Natural language chat and Gemini-backed recommenders (cost and performance) require Gemini Cloud Assist. Google Security Command Central (SCC) membership is required for sophisticated security and compliance monitoring capabilities.
Database Centre data takes a few minutes to update, but sometimes it takes 24 hours.
#DatabaseCenterGCP#Database#GoogleCloud#AImodels#AlloyDBOmni#PostgreSQL#CloudSQL#News#Technews#Techology#Technologynews#Technologytrendes#Govindhtech
0 notes