#SecureNetwork
Explore tagged Tumblr posts
Text

Discover the power of Lanmus managed switches—designed for superior network control and enhanced work security. Experience seamless connectivity, robust performance, and advanced features that keep your business network secure and efficient. Perfect for modern workplaces demanding reliability and protection. Upgrade your infrastructure with Lanmus for peace of mind and ultimate control.
For more information, Visit:https://newtrend.ae/product-category/dlink/ Live chat: +971 507542792
#LanmusSwitches#ManagedSwitches#NetworkControl#WorkSecurity#BusinessNetworking#SecureNetwork#ReliableConnectivity#NetworkPerformance#ITInfrastructure#TechSolutions#NewTrendAE#DLink#NetworkManagement#Cybersecurity#BusinessTech#TechUpgrade#NetworkSecurity#SeamlessConnectivity#ModernWorkplace#TechInnovation
0 notes
Text
#CyberSecurity#FirewallProtection#Cryptography#DataSecurity#NetworkSecurity#Encryption#CyberDefense#ITSecurity#InfoSec#DataProtection#SecuritySolutions#SecureNetwork#CyberThreats#RansomwareProtection#EndPointSecurity
1 note
·
View note
Text

QNodeOS: The Future of Quantum Networks
Researchers have introduced QNodeOS, the first-ever operating system designed specifically for quantum networks. This groundbreaking innovation brings quantum networking closer to reality, paving the way for ultra-secure communication, quantum cloud computing, and next-generation internet infrastructure. By enabling seamless interaction between quantum devices, QNodeOS marks a revolutionary advancement in network security and computational power. As quantum technology continues to evolve, QNodeOS sets the stage for a new era of data transmission, unlocking possibilities that were once only theoretical.
Visit Us : bookofaward.com
#QuantumComputing#QuantumNetworks#QNodeOS#NextGenInternet#CyberSecurity#QuantumEncryption#QuantumOS#NetworkingTech#QuantumInnovation#QuantumFuture#TechBreakthrough#QuantumCloud#QuantumInternet#AIandQuantum#SecureNetworking#QuantumTech#Superposition#Entanglement#QuantumData#QuantumCommunication#QuantumSecurity#ComputingRevolution#QuantumProcessing#QuantumInformation#FutureOfInternet#QuantumNodes#QuantumEngineering#QuantumDevelopment#QuantumProtocol#QuantumEvolution
1 note
·
View note
Text

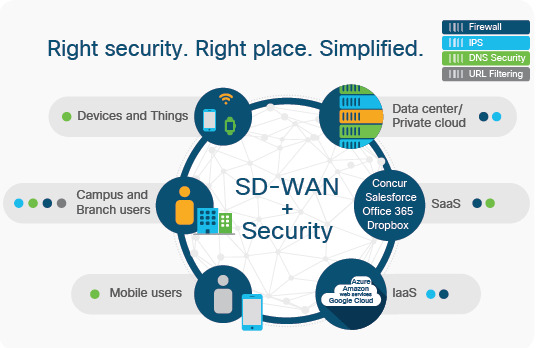
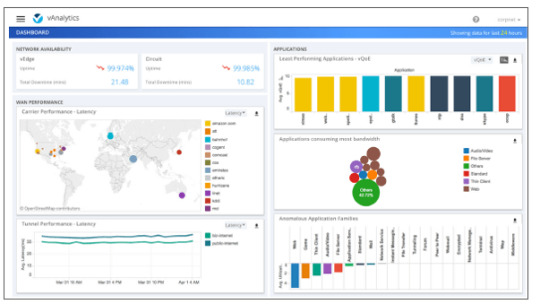
Learn to deploy and manage Viptela SD-WAN for secure and scalable enterprise connectivity. Start your networking journey with DCLessons. https://www.dclessons.com/category/courses/viptela
#CiscoViptela#SDWAN#Viptela#SecureNetworking#NetworkingJourney#EnterpriseConnectivity#CloudNetworking#DCLessons
0 notes
Link
#SDWAN#Netzwerke#NetworkSolutions#CloudNetworking#SecureNetworks#WANOptimization#DigitalTransformation#EnterpriseNetworking#Connectivity#ITInfrastructure#VirtualNetworks#BandwidthManagement#NetworkSecurity#BusinessNetworking#TechInnovation
0 notes
Text
Top Networking Solutions in Toronto
In the modern digital era, businesses depend on reliable, efficient, and secure networking solutions to succeed. Whether it's a small startup or a large enterprise, having the right networking infrastructure can make all the difference in maintaining seamless communication, data transfer, and overall business productivity. Toronto, being a global hub of innovation and technology, offers an array of networking solutions to meet the growing demands of businesses. Acelaservices brings forth top networking solutions in Toronto, catering to the specific needs of every enterprise.
Why Networking Solutions are Crucial for Businesses
Enhancing Connectivity and Communication
One of the primary reasons businesses seek top networking solutions in Toronto is to enhance their internal and external communication systems. Whether it's through cloud-based networks or local area networks (LANs), businesses require robust connectivity to keep their teams connected, no matter where they are. A reliable network can ensure uninterrupted data flow, improved collaboration, and faster access to information, all of which are vital for day-to-day operations.
Secure Data Transfer and Storage
Protecting data is a critical concern for businesses today. With rising cyber threats and data breaches, companies are more vulnerable than ever. Top networking solutions in Toronto focus on providing end-to-end encrypted services that secure sensitive business information. These solutions implement firewalls, VPNs (Virtual Private Networks), and intrusion detection systems to ensure that all data, whether being transferred or stored, remains protected from unauthorized access.
Scalability and Flexibility
As businesses grow, so do their networking needs. One of the hallmarks of top networking solutions in Toronto is their scalability. Whether your company is expanding its workforce or opening a new office in another location, these networking services provide flexible solutions that adapt to your needs. Acelaservices offers customized networking plans that can be scaled up or down depending on business requirements, ensuring cost-effectiveness and efficiency.

What Are the Components of Top Networking Solutions?
Cloud Networking
Cloud networking allows businesses to access data and applications over the internet rather than relying on physical hardware. This solution is especially popular due to its cost-effectiveness, scalability, and ability to support remote workforces. Acelaservices provides top networking solutions in Toronto that include secure cloud networking, allowing businesses to access their data from anywhere while maintaining the highest security standards.
Virtual Private Networks (VPNs)
A VPN offers businesses secure access to their networks, especially when employees are working remotely. Top networking solutions in Toronto emphasize the importance of VPNs in protecting confidential business data by creating a secure tunnel for information to pass through. This ensures that even if your team is working from different parts of the globe, your business network remains safe from cyberattacks.
Network Monitoring and Management
Effective network management ensures that all systems are running optimally. Through real-time monitoring, businesses can detect and address potential issues before they escalate into significant problems. Acelaservices specializes in providing top networking solutions in Toronto, including proactive network monitoring, 24/7 support, and troubleshooting services. This results in minimal downtime, ensuring business operations continue without interruption.
Wireless Networking Solutions
In a world where mobility is key, wireless networking solutions have become an essential part of business operations. Wireless LANs (WLANs) enable employees to connect to the network from various devices, including laptops, tablets, and smartphones. Acelaservices delivers top networking solutions in Toronto that incorporate fast and secure wireless networks, designed to support high traffic and prevent connectivity issues.
How Acelaservices Stands Out
When it comes to offering top networking solutions in Toronto, Acelaservices goes beyond providing basic services. We understand the unique needs of different industries and customize solutions that fit each business model. Our team of networking experts ensures that your business remains connected, secure, and scalable. Here's why Acelaservices is a preferred choice:
Tailored Solutions: Every business has unique networking needs. Acelaservices works closely with clients to design, implement, and maintain networks that support their growth and security objectives.
Cutting-Edge Technology: Our networking solutions leverage the latest technologies in cybersecurity, cloud computing, and wireless networking to deliver the best results.
24/7 Support: Our dedicated team offers round-the-clock support to monitor, manage, and resolve any network issues that may arise, ensuring minimal disruptions to your business operations.
Conclusion
In the fast-paced business environment of Toronto, having the right networking infrastructure can determine the success or failure of an organization. Acelaservices is proud to provide top networking solutions in Toronto that cater to businesses of all sizes. From cloud networking to VPNs, wireless networking, and network management, we cover all aspects of networking to ensure businesses operate smoothly, securely, and efficiently.
Invest in the best networking solutions for your business with Acelaservices, and experience seamless connectivity, robust security, and scalability that grows with your enterprise.
FAQs
1. What are the benefits of cloud networking?
Cloud networking provides flexibility, scalability, and cost-effectiveness, allowing businesses to access data remotely while maintaining security.
2. How does Acelaservices ensure data security in networking solutions?
We implement advanced encryption, firewalls, and VPNs to ensure that all data transfers and storage are secure from cyber threats.
3. Why is network monitoring important?
Network monitoring allows for real-time detection and resolution of issues, ensuring minimal downtime and efficient operations.
By choosing Acelaservices, your business will receive the top networking solutions in Toronto, tailored to your specific needs, ensuring robust connectivity and security at all times.
FOR MORE INFORMATION
𝐄𝐦𝐚𝐢𝐥:[email protected]
𝐩𝐡𝐨𝐧𝐞 𝐧𝐮𝐦𝐛𝐞𝐫: +1 (647) 534-3589 | Canada
+91 9849494893 | India
𝐀𝐝𝐝𝐫𝐞𝐬𝐬: 3422 Fountain Park Ave Mississauga ON L5M7E3
𝐰𝐞𝐛𝐬𝐢𝐭𝐞: www.acela-services.com
#NetworkingSolutions#TorontoBusiness#SecureNetworking#BusinessConnectivity#Acelaservices#CloudNetworking#VPNServices#NetworkSecurity#WirelessNetworking#TorontoTech
0 notes
Text
#Cybersecurity#InfoSec#DataProtection#CyberAware#OnlineSafety#SecurityAwareness#PrivacyProtection#CyberDefense#ITSecurity#CyberThreats#SecureNetworks#DigitalSecurity#CyberResilience#InternetSafety#CyberEducation#ThreatIntelligence#CyberAttack#NetworkSecurity#CyberHygiene#InfoSecCommunity
0 notes
Text
The Ultimate Cyber Security Guide: Secure Your World

What's more important today when it comes to your online Behavior, buying the must-have items, making some funny or emotional comments, sharing personal information like mail, age, hobby, likes, dislikes, or clicking on staying safe. Aippg's top cyber security tips help protect your Bank balance and your reputation in society.
The Ultimate Cyber Security Guide
1. Limit Personal Information for cyber security 2. Turn On Privacy Settings 3. Play It Smart While Browsing 4. Check Before Downloading Apps 5. Ensure Internet Connection Security 6. Select Strong Passwords 7. Shop on Secure Sites 8. Think Before Posting Online 9. Socialize Safely 10. Update Your Antivirus Protection 11. Always Back Up Your Data
1. Limit Personal Information for cyber security

Limit personal information. You don't give strangers your address and phone number in real life, so don't give it to millions of strangers online, and strangers don't need to know your relationship status either.
2. Turn On Privacy Settings
Turn on privacy settings. Today online hackers and every marketer try to use your social media presence and browsing habits for their good or bad. Turn on privacy safeguards whenever possible to limit their intrusion into your life. Speaking of privacy, always close your social media and retail account profiles and emails whenever you're not using them. This lessens the chance of hackers gaining access to your life.
3. Play It Smart While Browsing

When browsing, play it smart to stay safe. If a link ad or article looks explicit or shocking, avoid it. If a link asks for your personal information, no matter how legitimate it looks or appears to come from your bank or other trusted source, don't click on it. It may be a trap to Hack your infect your device or personal information with malware cause later on they will use it against you. So these tips should be at no one in your cyber security.
4. Check Before Downloading Apps

Check twice before downloading an app. Malware is often disguised as an app. Never download an app if it looks suspicious or comes from a site you don't trust.
5. Ensure Internet Connection Security

Make sure your internet connection is always secure. This is easy to do at home, but when you're in public, you have no control over your internet connection security. Never provide sensitive information over an unsecured network; this makes it easy for cybercriminals to steal from you and it's bad for cyber security. When you are using public Wi-Fi, always use a VPN.
6. Select Strong Passwords

Strong password Select strong passwords. In 2024 with so many data breaches and hacking occurring, you can't afford to use easy-to-remember passwords or use the same password over and over. These put your sensitive information at risk. Choose a complex password that's at least 16 characters long and includes numbers and special characters, then use a password manager to keep them handy and secure.
7. Shop on Secure Sites

Shop on Secure Sites Only shop on secure sites. You can see that most sites are encrypted and secure because its address starts with https. If it's not secure or starts with only http, you stand to lose a lot more than you will gain, it could be money or reputation.
8. Think Before Posting Online

Posting Online Think before posting anything on the Internet. What you post online may stay there permanently. That includes regrettable memories and embarrassing pictures or videos. Even if you delete those, copies may have already been shared that you can't remove. Remember, if you don't want your boss or mother or anyone else to see it, don't post it.
9. Socialize Safely

Socialize Safely Socialize safely. Did you know fake social profiles are one-way hackers gain access to your personal information and ultimately your wallet? The bottom line is: don't take anyone at face value before you befriend them.
10. Update Your Antivirus Protection

Update Your Antivirus Protection Update your antivirus protection. Cybercriminals are always upping their game, so protect your computer from malware by keeping your antivirus up to date.
11. Always Back Up Your Data

Always Back Up Your Data The last but most important tip for cyber security is always to Back up your data. Try to do this regularly in case you do fall victim to an online scam or ransomware. That way, you still have access to what's yours when it comes to internet safety for you. Always think before you click on any link, add, photos, and take time to secure your device. After all, it's your online safety. If you guys want to study Cyber security you can check top cyber security colleges in the USA. Read Our Latest Articles. Read the full article
#AntivirusUpdates#CyberAware#CyberAwareness#CyberDefense#CyberResilience#CyberSecurity#DataBackup#DataProtection#DigitalProtection#InfoSec#InternetSafety#MalwareProtection#OnlinePrivacy#OnlineSafety#PasswordSecurity#PrivacyMatters#SafeOnlineShopping#SecureBrowsing#SecureNetworking#SocialMediaSecurity
0 notes
Text
Unveiling the Secrets: What You'll Learn in Ethical Hacking
In ethical hacking training, various aspects are covered to equip individuals with the necessary skills and knowledge to identify and prevent cyber threats. Here are some key topics taught in ethical hacking:
Embark on a journey to become the digital world's guardian angel; an Ethical hacking course in Pune is your map to mastering the art of protecting with skilful precision.

Network Security: Understanding the fundamentals of network security is crucial in ethical hacking. Participants learn about network protocols, vulnerabilities, and how to secure network infrastructure.
Web Application Security: This module focuses on identifying and mitigating vulnerabilities in web applications. Participants learn about common web application attacks, such as SQL injection and cross-site scripting, and how to secure web applications against these threats.
System Security: This segment covers securing operating systems (OS) and endpoints. Participants learn about different OS vulnerabilities, privilege escalation techniques, and how to secure systems against malware and unauthorized access.
Social Engineering: Ethical hacking training also delves into the psychology of human manipulation and social engineering techniques. Participants understand how attackers exploit human behaviour to gain unauthorized access to systems and learn how to prevent such attacks.
Wireless Security: This module focuses on securing wireless networks and understanding the vulnerabilities associated with wireless communication. Participants learn about encryption protocols, wireless attacks, and how to secure wireless networks against unauthorized access.
Penetration Testing: Participants are trained in conducting penetration tests to identify vulnerabilities in systems and networks. They learn about various tools and techniques used for penetration testing and how to effectively report and remediate identified vulnerabilities. Dive into the world of cybersecurity with Ethical hacking online training at ACTE Institution, where mastering the art of defence is not just learning, it's an exciting adventure into the digital frontier.
Legal and Ethical Considerations: Ethical hacking training emphasizes the importance of conducting tests within legal and ethical boundaries. Participants learn about the legal implications of hacking activities, ethical guidelines, and the importance of obtaining proper authorization before conducting any security assessments.

Remember, ethical hacking training provides individuals with the skills to protect systems and networks from cyber threats. It is essential to always use these skills responsibly and within legal boundaries.
#SocialEngineering#HumanManipulation#EthicalHackingTraining#CyberAwareness#NetworkSecurity#CyberDefense#SecureNetworks#WirelessSecurity#WiFiProtection#SecureWireless
0 notes
Text

Desktop Enterprise Gateway eKit AR303
Empower your business with the eKit AR303 Desktop Enterprise Gateway — a compact, high-performance networking solution designed for seamless connectivity, advanced security, and reliable performance. Ideal for small to medium enterprises, it ensures smooth operations, scalable management, and uninterrupted communication to keep your enterprise running at full speed.
For more information, Visit:https://newtrend.ae/product-category/huawei/huawei-authorized-partner-dubai-uae/ Live chat: +971 507542792
#eKitAR303#EnterpriseGateway#BusinessNetworking#SMBSolutions#NetworkSecurity#ReliableConnectivity#CompactPerformance#ScalableNetwork#ITInfrastructure#NewtrendUAE#DesktopGateway#HuaweiPartner#NetworkingSolutions#TechForBusiness#SecureNetwork#BusinessTech
0 notes
Text
𝐔𝐧𝐥𝐨𝐜𝐤𝐢𝐧𝐠 𝐏𝐨𝐬𝐬𝐢𝐛𝐢𝐥𝐢𝐭𝐢𝐞𝐬 𝐰𝐢𝐭𝐡 𝐑𝐞𝐬𝐢𝐝𝐞𝐧𝐭𝐢𝐚𝐥 𝐑𝐃𝐏 𝐟𝐫𝐨𝐦 𝐕𝐏𝐒 𝐏𝐫𝐨𝐱𝐢𝐞𝐬 𝐈𝐧𝐜

In the rapidly evolving landscape of remote work, having the right tools is essential. VPS Proxies Inc takes the lead with Residential Remote Desktop Protocol (RDP), providing unparalleled features and benefits to enhance your virtual experience.
🌐 𝐔𝐧𝐝𝐞𝐫𝐬𝐭𝐚𝐧𝐝𝐢𝐧𝐠 𝐭𝐡𝐞 𝐖𝐨𝐫𝐥𝐝 𝐨𝐟 𝐑𝐃𝐏: 𝐓𝐲𝐩𝐞𝐬 𝐚𝐧𝐝 𝐏𝐫𝐨𝐭𝐨𝐜𝐨𝐥𝐬
Remote Desktop Protocol encompasses various types and protocols, each designed to meet specific needs. Whether it’s ISDN, POTS, or LAN protocols like IPX, NetBIOS, and TCP/IP, Microsoft’s RDP standardizes features in operating systems. Third-party providers like VPS Proxies Inc take it a step further, offering customizable plans with enhanced features like processor speed, bandwidth, storage options, and advanced security measures.
🛠️🔧 𝐇𝐨𝐰 𝐢𝐬 𝐑𝐃𝐏 𝐰𝐨𝐫𝐤𝐢𝐧𝐠 ❓
Remote Desktop Protocol (RDP) allows a user to connect to and control a remote computer over a network, enabling the transmission of graphical user interface (GUI) input and output. It operates by encoding and transmitting the user’s actions, such as mouse movements and keystrokes, to the remote computer while sending back the graphical updates to the local machine.
🏡🖥️ 𝐑𝐞𝐬𝐢𝐝𝐞𝐧𝐭𝐢𝐚𝐥 𝐑𝐃𝐏: 𝐁𝐫𝐢𝐝𝐠𝐢𝐧𝐠 𝐭𝐡𝐞 𝐆𝐚𝐩 𝐛𝐞𝐭𝐰𝐞𝐞𝐧 𝐇𝐨𝐦𝐞 𝐚𝐧𝐝 𝐎𝐟𝐟𝐢𝐜𝐞
Residential RDP from VPS Proxies Inc provides a unique IP address, distinct from data center counterparts, making it ideal for home users. This form of RDP caters to both management and remote administration needs. Let’s delve into the myriad benefits it offers:
🛡️ 𝐄𝐧𝐡𝐚𝐧𝐜𝐞𝐝 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐒𝐡𝐢𝐞𝐥𝐝
𝐂𝐞𝐧𝐭𝐫𝐚𝐥𝐢𝐳𝐞𝐝 𝐒𝐚𝐟𝐞𝐭𝐲 𝐍𝐞𝐭: Residential RDP eliminates the need for individual safety measures on each employee’s computer. It acts as a centralized shield, safeguarding your data and systems.
🔒 𝐏𝐫𝐢𝐯𝐚𝐜𝐲 𝐢𝐧 𝐅𝐨𝐜𝐮𝐬
𝐑𝐞𝐬𝐢𝐝𝐞𝐧𝐭𝐢𝐚𝐥 𝐈𝐏 𝐈𝐧𝐭𝐞𝐠𝐫𝐚𝐭𝐢𝐨𝐧: The integration of residential IP addresses ensures that user devices are linked to server-side IP addresses, offering an extra layer of privacy and security.
🌐 𝐆𝐥𝐨𝐛𝐚𝐥 𝐂𝐨𝐧𝐭𝐞𝐧𝐭 𝐀𝐜𝐜𝐞𝐬𝐬 𝐆𝐞𝐨-𝐁𝐥𝐨𝐜𝐤𝐞𝐝 𝐂𝐨𝐧𝐭𝐞𝐧𝐭 𝐔𝐧𝐥𝐨𝐜𝐤𝐞𝐝: Access restricted content from anywhere using your home IP address. VPS Proxies Inc ensures that geographical limitations are no longer a barrier to information.
🚀 𝐒𝐞𝐚𝐦𝐥𝐞𝐬𝐬 𝐎𝐩𝐞𝐫𝐚𝐭𝐢𝐨𝐧𝐬 𝐰𝐢𝐭𝐡 𝐔𝐧𝐥𝐢𝐦𝐢𝐭𝐞𝐝 𝐁𝐚𝐧𝐝𝐰𝐢𝐝𝐭𝐡
𝐕𝐢𝐫𝐭𝐮𝐚𝐥𝐥𝐲 𝐔𝐧𝐥𝐢𝐦𝐢𝐭𝐞𝐝 𝐁𝐚𝐧𝐝𝐰𝐢𝐝𝐭𝐡: Enjoy uninterrupted operations even during peak traffic times. Residential RDP hosted by VPS Proxies Inc ensures your websites run smoothly, regardless of the user load.
🔄 𝟐𝟒/𝟕 𝐒𝐮𝐩𝐩𝐨𝐫𝐭 𝐟𝐨𝐫 𝐔𝐧𝐢𝐧𝐭𝐞𝐫𝐫𝐮𝐩𝐭𝐞𝐝 𝐖𝐨𝐫𝐤𝐟𝐥𝐨𝐰
𝐑𝐨𝐮𝐧𝐝-𝐭𝐡𝐞-𝐂𝐥𝐨𝐜𝐤 𝐀𝐬𝐬𝐢𝐬𝐭𝐚𝐧𝐜𝐞: VPS Proxies Inc takes pride in offering 24/7 customer support. Any issues are promptly addressed, ensuring your workflow remains uninterrupted.
🤔🔍 𝐀𝐝𝐝𝐢𝐭𝐢𝐨𝐧𝐚𝐥 𝐅𝐞𝐚𝐭𝐮𝐫𝐞𝐬 𝐚𝐧𝐝 𝐂𝐨𝐧𝐬𝐢𝐝𝐞𝐫𝐚𝐭𝐢𝐨𝐧𝐬
🌐🔒 𝐓𝐫𝐮𝐬𝐭𝐰𝐨𝐫𝐭𝐡𝐲 𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐏𝐫𝐨𝐭𝐨𝐜𝐨𝐥 Ensure your chosen Residential RDP provider has a robust and reliable delivery network protocol. VPS Proxies Inc boasts a proven track record in providing secure and efficient network protocols.
🔐🛑 𝐀𝐝𝐯𝐚𝐧𝐜𝐞𝐝 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐌𝐞𝐚𝐬𝐮𝐫𝐞𝐬 VPS Proxies Inc goes beyond the basics, offering advanced security measures to protect your data. From encryption to multi-factor authentication, your Residential RDP is fortified against potential threats.
🛠️🔧 𝐂𝐮𝐬𝐭𝐨𝐦𝐢𝐳𝐚𝐭𝐢𝐨𝐧 𝐟𝐨𝐫 𝐎𝐩𝐭𝐢𝐦𝐚𝐥 𝐏𝐞𝐫𝐟𝐨𝐫𝐦𝐚𝐧𝐜𝐞 Tailor your Residential RDP plan to meet your specific needs. VPS Proxies Inc allows you to customize your RDP with features like adjustable processor speeds, scalable bandwidth, and a choice between SSDs and HDDs for storage.
🌍🌐 𝐆𝐥𝐨𝐛𝐚𝐥 𝐂𝐨𝐧𝐧𝐞𝐜𝐭𝐢𝐯𝐢𝐭𝐲 𝐰𝐢𝐭𝐡 𝐃𝐢𝐯𝐞𝐫𝐬𝐞 𝐈𝐏 𝐀𝐝𝐝𝐫𝐞𝐬𝐬𝐞𝐬 Expand your reach with VPS Proxies Inc’s diverse IP addresses. Whether you need a US IP address for accessing specific content or a global IP pool for extensive connectivity, the choice is yours.
🖥️🤝 𝐔𝐬𝐞𝐫-𝐅𝐫𝐢𝐞𝐧𝐝𝐥𝐲 𝐈𝐧𝐭𝐞𝐫𝐟𝐚𝐜𝐞 𝐚𝐧𝐝 𝐈𝐧𝐭𝐞𝐠𝐫𝐚𝐭𝐢𝐨𝐧 VPS Proxies Inc prides itself on providing a user-friendly interface, ensuring seamless integration into your existing workflow. Experience the convenience of managing your Residential RDP effortlessly.
𝑪𝒐𝒏𝒄𝒍𝒖𝒔𝒊𝒐𝒏:
Elevate Your Remote Desktop Experience with VPS Proxies Inc 🚀 In the vast realm of remote desktop protocols, VPS Proxies Inc emerges as a reliable partner. With an extensive array of features, enhanced security measures, and a commitment to customer satisfaction, VPS Proxies Inc takes your virtual experience to new heights. Connect effortlessly, unlock possibilities, and manage your operations seamlessly with Residential RDP from VPS Proxies Inc.
ℂ𝕠𝕟𝕥𝕒𝕔𝕥 𝕦𝕤:-: 👉🏻 Web: www.vpsproxies.com 👉🏻 Telegram: https://t.me/vpsproxiesinc 👉 Gmail: [email protected] 👉🏻 Skype: live:.cid.79b1850cbc237b2a
#PrivateRDP#SecureConnections#BusinessGrowth#RemoteDesktopSolution#ResidentialRDP#SecureNetworking#BusinessProductivity#PrivateAccess#RemoteWorkSolutions#HomeOfficeTech#BusinessSecurity#RDPforSuccess#GrowthThroughTechnology#PrivateNetworking#ProductiveWorkspace#SecureBusinessConnections#RDPAdvantage#HomeBaseBusiness#BusinessExpansion#PrivateProductivity
0 notes
Text
youtube
#QuantumComputing#QuantumNetworks#QNodeOS#NextGenInternet#CyberSecurity#QuantumEncryption#QuantumOS#NetworkingTech#QuantumInnovation#QuantumFuture#TechBreakthrough#QuantumCloud#QuantumInternet#AIandQuantum#SecureNetworking#QuantumTech#Superposition#Entanglement#QuantumData#QuantumCommunication#QuantumSecurity#ComputingRevolution#QuantumProcessing#QuantumInformation#FutureOfInternet#QuantumNodes#QuantumEngineering#QuantumDevelopment#QuantumProtocol#QuantumEvolution
0 notes
Text
Navigating Network Costs: The Top SD-WAN Providers in 2023
youtube
Businesses of all sizes are feeling the financial pinch of an expensive MPLS network. But what is an MPLS network and why is it so costly? MPLS (Multi-Protocol Label Switching) is a type of data communications network used to transport data packets over the internet. It is a Layer 3 (IP) network protocol designed to provide secure, reliable, and high-performance data transfer. MPLS networks are often used in large enterprises and service providers to connect multiple locations and provide a secure and high-speed connection between them.
#sdwan2023#networkcosts#mplsalternatives#businessconnectivity#cloudnetworking#costsavingtech#securenetworks#techsolutions#futureofnetworking#digitaltransformation#Youtube
0 notes
Text
Secure Access Service Edge (SASE) Market Strategic Analysis: Enabling Secure Transformation
The global secure access service edge market size is expected to reach USD 11.29 billion by 2028, registering a CAGR of 36.4% from 2021 to 2028, according to a new study conducted by Grand View Research, Inc. The existing networking technologies are complex and difficult to manage but easy for cybercriminals to intrude. The growing preference for remote working practices, increase in traffic across public clouds, and the rising dependence on data centers are further adding to the data security risks. At this juncture, the growing demand for ensuring secure access to data and networks is driving the need for advanced network approaches and technologies. The subsequent need for a unified and simplified approach to strengthen network security has resulted in the emergence of SASE.
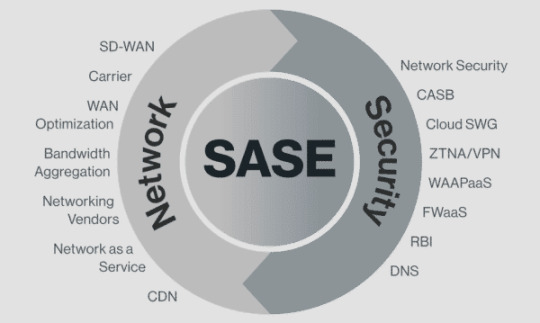
Secure Access Service Edge Market Report Highlights
The platform segment accounted for over 70% of the overall revenue share in 2020 as the growing preference for remote working continued to drive the demand for a unified security solution that can offer the capabilities of several network security services
The demand for SASE was higher among IT & telecom enterprises in 2020 as the need to filter contents across edges and ensure efficient security framework management continued to drive the adoption of SASE among IT & telecom organizations
North America dominated the global market in 2020 and is expected to remain dominant over the forecast period
Aggressive IT spending, effective implementation of security standards, and the continued rollout of the digital workforce by organizations across the U.S. and Canada are some of the factors that are expected to drive the regional market
For More Details or Sample Copy please visit link @: Secure Access Service Edge Market Report
SASE architecture comprises the capabilities of network security services, such as Zero Trust, FWaaS, and CASB, and software-defined WAN capabilities, combined in a unified platform to help organizations in ensuring easy and secure access to data and networks. SASE architecture simplifies the IT infrastructure and frees organizations from the burden of managing and periodically updating multiple security systems. SASE architecture also allows organizations to save on the costs incurred on procuring multiple security solutions and helps them in the quick implementation of data protection policies. All such benefits are driving the popularity of SASE frameworks among enterprises.
The COVID-19 pandemic and the subsequent restrictions on the movement of people imposed by various governments across the world have prompted organizations to switch to a remote working model. However, the remote working model has also triggered challenges related to managing the productivity of a flexible workforce and security governance. Organizations are also exposed to higher levels of cybersecurity risks than ever. As a result, organizations are looking forward to implementing robust security frameworks. The growing need to establish effective security frameworks while ensuring convenient access to information for employees using an integrated approach is expected to drive the adoption of SASE frameworks.
#SASE#NetworkSecurity#EdgeSecurity#Cybersecurity#CloudSecurity#SecureConnectivity#EnterpriseSecurity#CyberDefense#EdgeComputing#InfoSec#ITInfrastructure#NetworkArchitecture#SASESolutions#DataProtection#CyberThreats#SecureNetworking
0 notes
Text
Blockchain in MLM: Revolutionizing Transparency and Security
In an age where trust and security are paramount, industries are constantly seeking innovative solutions to enhance transparency and protect sensitive information. Multi-Level Marketing (MLM), a dynamic business model built on relationships and networks, is no exception. The integration of blockchain technology into MLM operations is heralding a new era of unparalleled security, transparency, and trust. In this article, we delve into the profound impact of blockchain in MLM, exploring how it is reshaping the landscape and empowering both distributors and consumers.
Blockchain Unveiled
Blockchain technology, originally devised for cryptocurrencies like Bitcoin, is a distributed and decentralized digital ledger that records transactions across multiple computers in a secure, transparent, and tamper-proof manner. Each block in the chain contains encrypted data linked to the previous block, creating an unbroken, immutable sequence of information. This inherent design makes blockchain a powerful tool for enhancing security and transparency across various industries.
Enhancing Transparency in MLM
One of the most significant advantages of integrating blockchain technology into MLM is the unprecedented transparency it offers. Traditional MLM models sometimes face challenges related to information asymmetry, where participants are left unaware of vital data. Blockchain changes the game by providing a shared, real-time ledger accessible to all network participants. Distributors can now track transactions, commissions, and even downline growth with unparalleled clarity. This transparency fosters trust among distributors, minimizing misunderstandings and enhancing overall satisfaction.
Unrivaled Security
Blockchain's hallmark feature is its security. The decentralized nature of the technology ensures that data cannot be altered without consensus from the entire network. This prevents malicious actors from tampering with transaction records or altering commission structures. In an industry that has faced its share of skepticism, blockchain's cryptographic encryption and consensus mechanism build a fortified barrier against fraud, protecting both the MLM company and its distributors.
Smart Contracts: Revolutionizing Payouts
Smart contracts are self-executing contracts with predefined conditions directly written into code. These contracts automate processes, ensuring that commissions, bonuses, and incentives are distributed automatically when predefined conditions are met. The introduction of smart contracts within MLM, enabled by blockchain, eradicates manual intervention, reduces errors, and guarantees accurate and timely payouts, fostering distributor trust and satisfaction.
Empowering Consumer Confidence
Beyond empowering distributors, blockchain technology also benefits consumers. With blockchain, the journey of a product from creation to purchase is traceable and transparent. Consumers can verify the authenticity of products, ensuring they receive genuine goods and fostering trust in the MLM brand. Blockchain's ability to store extensive product information ensures consumers have access to accurate details, empowering them to make informed purchasing decisions.
Conclusion
Blockchain technology is poised to revolutionize the MLM industry by infusing it with enhanced security, transparency, and trust. As the convergence of blockchain and MLM accelerates, the landscape will shift towards a model where trust is built on provable data, empowering distributors, consumers, and stakeholders alike. The integration of blockchain is not merely a technological upgrade; it's a transformational leap towards a more ethical, secure, and transparent MLM ecosystem that thrives on trust and shared success.
#BlockchainInMLM#TransparentMLM#SecureNetworks#TrustThroughBlockchain#BlockchainTechnology#MLMTransparency#DecentralizedTrust#SmartContracts#BlockchainSecurity#MLMInnovation#DistributedLedger#BlockchainRevolution#SecureDistributions#CryptoMLM#EmpoweringNetworks#BlockchainBenefits#MLMTrust#TransparentTransactions#EnhancedSecurity#BlockchainImpact
0 notes
Text
Data Diode Market Expansion: $4.1B to $10.5B by 2034 🔐
Data Diode Market is set for exponential growth, expanding from $4.1 billion in 2024 to $10.5 billion by 2034, at a CAGR of 9.9%. With the surge in cybersecurity threats, data diodes have become essential for secure, one-way data transmission, safeguarding critical infrastructure, defense systems, and financial institutions.
To Request Sample Report: https://www.globalinsightservices.com/request-sample/?id=GIS10572 &utm_source=SnehaPatil&utm_medium=Article
Key Market Drivers & Trends
🔹 Industrial control systems & government networks lead market adoption, ensuring secure communication & compliance. 🔹 Military & defense applications rank second, reflecting heightened national security priorities. 🔹 Financial services & energy sectors are rapidly adopting data diodes to prevent cyber attacks & ensure data integrity. 🔹 North America dominates, driven by robust cybersecurity policies & advanced infrastructure. 🔹 Europe follows closely, with stringent data protection regulations & increasing security investments. 🔹 Asia-Pacific is a high-growth region, fueled by rapid digital transformation & rising cyber threats.
Market Segmentation Overview
🛡 Types: Unidirectional, Bidirectional 💻 Products: Hardware Data Diodes, Software Data Diodes 🛠 Services: Installation, Maintenance, Consulting 📡 Applications: Industrial Control, Government, Military, Telecommunications, Healthcare 🏢 End Users: BFSI, Defense, Aerospace, Oil & Gas, Healthcare 🌐 Deployment: On-Premise, Cloud-Based, Hybrid
In 2024, the market witnessed 1.2 million units, projected to reach 2.5 million by 2028. The industrial sector leads with a 45% share, followed by government (30%) and defense (25%). Owl Cyber Defense, BAE Systems, and Advenica dominate with cutting-edge innovations in cross-domain security solutions.
With the rising cyber threat landscape, stringent regulations, and expanding digital infrastructures, the Data Diode Market is set to redefine network security for the future. 🔐💡
#DataDiode #CyberSecurity #DataProtection #CriticalInfrastructure #IndustrialSecurity #NetworkSecurity #SecureDataTransfer #CyberDefense #MilitaryTech #ITSecurity #FinancialCyberSecurity #IoTSecurity #GovernmentCyberSecurity #CloudSecurity #ThreatDetection #Encryption #DigitalTransformation #SecureNetworks #CyberResilience #SmartDefense #TechnologyTrends #InformationSecurity #AIinCyberSecurity #SecuritySolutions #ZeroTrust #NextGenSecurity
0 notes