#Security with SAP ETD
Explore tagged Tumblr posts
Text
SAP Enterprise Threat Detection | SAP ETD | Threat Management | ToggleNow
SAP Enterprise Threat Detection (SAP ETD) plays a pivotal role in safeguarding complex SAP environments supporting critical business processes. ToggleNow implemented SAP ETD to heighten visibility and monitoring across organizational SAP landscapes. By centralizing logs and normalizing data sources within the solution’s security knowledge base, SAP ETD effectively identified internal threats from both internal and third-party users involved in non-core activities.

This tool empowered security teams with crucial insights, enabling swift detection of fraud attempts and information leaks within SAP systems. In the vast and intricate realm of SAP landscapes, SAP ETD emerged as a vital asset, offering a proactive approach to tackle cybersecurity challenges, particularly in identifying and addressing security risks that would otherwise be challenging to detect.
Read more: https://togglenow.com/services/sap-entripise-threat-detection/
#SAP Threat Management#SAP ETD#Security with SAP ETD#SAP Enterprise threat detection cloud#SAP Enterprise Threat Detection#SAP Enterprise threat detection implementation#Security Service for SAP Enterprise Threat Detection#GRC Access Control#sap user management automation#sap sod analysis
0 notes
Text
AP HANA services offer a robust set of security features to protect data, manage user access, and ensure compliance in cloud and on-premises environments. These features cover key aspects like authentication, authorization, encryption, auditing, and compliance.
Security Features of SAP HANA Services
1. Authentication
User Authentication: Validates user identities using various methods:Username and password.X.509 certificates for secure communications.SAML 2.0 for Single Sign-On (SSO).SAP Identity Authentication Service (IAS).
Integration with Identity Providers (IdP): Supports integration with enterprise IdPs for federated authentication.
2. Authorization
Role-Based Access Control (RBAC):Permissions are assigned based on roles.Supports fine-grained privileges for database objects, such as tables, views, or schemas.
Attribute-Based Access Control (ABAC):Controls access based on dynamic user attributes, such as location, job title, or department.
Dynamic Data Masking:Hides sensitive data from unauthorized users by dynamically masking content.
3. Data Encryption
Data-at-Rest Encryption:Encrypts stored data using AES-256 encryption.Ensures compliance with GDPR and other regulations.
Data-in-Transit Encryption:Encrypts communication between SAP HANA components using TLS/SSL.
Application Layer Encryption:Supports column-level encryption for sensitive data fields.
4. Auditing and Logging
Audit Logging:Tracks critical activities such as logins, schema modifications, and data changes.Provides detailed logs for compliance and forensic investigations.
Change Logs:Monitors data changes in tables for better traceability.
Secure Log Management:Logs are encrypted and protected against tampering.
5. Network Security
Secure Network Zones:Segregates networks to isolate critical components.
Firewall Rules:Controls incoming and outgoing traffic to SAP HANA instances.
IP Whitelisting:Allows access only from approved IP addresses.
Virtual Private Network (VPN) Integration:Ensures secure remote connections.
6. User and Role Management
Centralized tools for managing users and roles across multiple SAP HANA instances.
Integration with LDAP/Active Directory for streamlined user management.
Temporary roles and privileges for time-limited access.
7. Compliance and Standards
Certified for international standards such as:ISO 27001 (Information Security).GDPR (Data Protection and Privacy).SOC 1/2/3 (Service Organization Controls).
Regular updates to meet global security standards.
8. Backup and Recovery Security
Encrypted backups for data protection.
Role-based access to backup and restore functionalities.
Secure storage integration for backups in cloud environments.
9. Advanced Threat Detection
Integration with SAP Enterprise Threat Detection (ETD) for monitoring anomalies.
Built-in alerts for unauthorized activities or potential breaches.
Security advisories and patches provided by SAP to mitigate vulnerabilities.
10. Multi-Tenancy and Isolation
For SAP HANA Cloud:Logical data isolation between tenants.Separate encryption keys for each tenant.
Ensures secure coexistence of multiple workloads on the same infrastructure.
Key Benefits
Protects sensitive business data.
Ensures regulatory compliance.
Reduces the risk of unauthorized access or breaches.
Provides tools for secure cloud and hybrid deployments.
Would you like detailed examples of any specific feature, such as configuring encryption or setting up RBAC in SAP HANA?
Anubhav Trainings is an SAP training provider that offers various SAP courses, including SAP UI5 training. Their SAP Ui5 training program covers various topics, including warehouse structure and organization, goods receipt and issue, internal warehouse movements, inventory management, physical inventory, and much more.
Call us on +91-84484 54549
Mail us on [email protected]
Website: Anubhav Online Trainings | UI5, Fiori, S/4HANA Trainings

0 notes
Text
Strengthening defenses with SAP ETD | Toggle Now

SAP Enterprise Threat Detection (SAP ETD) plays a pivotal role in safeguarding complex SAP environments supporting critical business processes. ToggleNow implemented SAP ETD to heighten visibility and monitoring across organizational SAP landscapes. By centralizing logs and normalizing data sources within the solution’s security knowledge base, SAP ETD effectively identified internal threats from both internal and third-party users involved in non-core activities.
This tool empowered security teams with crucial insights, enabling swift detection of fraud attempts and information leaks within SAP systems. In the vast and intricate realm of SAP landscapes, SAP ETD emerged as a vital asset, offering a proactive approach to tackle cybersecurity challenges, particularly in identifying and addressing security risks that would otherwise be challenging to detect.
Read More: https://togglenow.com/services/sap-entripise-threat-detection/
1 note
·
View note
Text
Something I've been recommending a lot to my fellow MCAS + POTS-sufferers at the moment, has been investing in a soup blender.
Apart from beta blockers, the primary treatment for POTS is increasing salt and water. A really good way of combining both and upping your nutritional value is by drinking things like bone broth or veggie stock.
But if you're like me with a ton of allergies (so you can't buy anything premade🙃) and bone broth raises your histamine, then you're left with the energy sapping task of making your own.
And I don't know about any of you, but when my nervous system is throwing a wobbler, the last thing I am capable of doing is standing up for long periods at a time over a hot stove.
Some people get around this by using a slow cooker, which is great if you can. I personally can't because slow cooking raises the histamine content of food (especially meat) and also, the clue is in the name, it's a slow cooker and sometimes my POTSie, ADHD butt needs food now-ish or as soon as possible and not 8 hours later. Instapots can be good, but they take up a lot of counter space and also I don't know if you've ever tried to release a pressure cooker valve when you can barely stand, but I genuinely think that's the closest I've come to dying and I've experienced both megaloblastic and hemalytic anemia.
Which is why we got a soup blender. They take up less space, are generally easier to clean, and also easier for me, at least, to use. All you need to do is roughly chop your ingredients up, dump them in the jug, add seasoning, fill the jug with water, hit the soup function and then sit your ass down for the next 20 minutes while this magical fucking thing both cooks and blends you some liquidy goodness.
I will say, don't invest in the instapot one. It's not worth the price point, and the motor burned out on mine after about six months. It was also a pain in the ass to clean. (The self clean was more of a "swish water around for 30 seconds" function and I can't tell you how many times I hurt myself trying to get gunk off the bottom.)
The one I currently have is a Ninja HB152 Foodi Heat-iQ Blender, which was a little more expensive, but in my opinion, far superior and better made. It's faster, makes either chunky or smooth soup, really good consistency dips, ice cream and smoothies. I've also used it to make alternative milks like oat milk and it didn't jam the blades.
It also has a great cleaning system that actually takes a full 6 minutes to run and really gets any residue off the base, and it also alerts you to things like the jug or lid not being secure, which is great when I'm brain-fogged and try to blend things without the lid on.
Anyway, this post brought to you not by Ninja but by @mothman-etd making me some leek and potato soup laden with enough salt to make this POTS episode manageable.

Just throwing the info out there. Hope it helps someone.
2K notes
·
View notes
Text
New Course: SECETD SAP Enterprise Threat...
In this course you will learn how to use SAP Enterprise Threat Detection (ETD) to secure and monitor the security of your SAP landscape. The main objective of the course is to understand how the different features of the product can be used, like Alert Processing, Forensic Analysis and Threat Hunting, Security Monitoring, customizing of the SAP delivered Alert Detection Patterns, building of the customer/LOB specific Alert Detection Patterns. An important focus is given to the understanding of the different Log Data coming out of SAP ERP systems. A technical overview shows the different components of ETD on how it can be set up in different modes, and how to connect to the various log sources.
New Course: SECETD SAP Enterprise Threat...
In this course you will learn how to use SAP Enterprise Threat Detection (ETD) to secure and monitor the security of your SAP landscape. The main objective of the course is to understand how the different features of the product can be used, like Alert Processing, Forensic Analysis and Threat Hunting, Security Monitoring, customizing of the SAP delivered Alert Detection Patterns, building of the customer/LOB specific Alert Detection Patterns. An important focus is given to the understanding of the different Log Data coming out of SAP ERP systems. A technical overview shows the different components of ETD on how it can be set up in different modes (e.g. High Availability set up alternatives), and how to connect to the various log sources...Read More
SAP Get Social
0 notes
Text
New Course: SECETD SAP Enterprise Threat...
In this course you will learn how to use SAP Enterprise Threat Detection (ETD) to secure and monitor the security of your SAP landscape. The main objective of the course is to understand how the different features of the product can be used, like Alert Processing, Forensic Analysis and Threat Hunting, Security Monitoring, customizing of the SAP delivered Alert Detection Patterns, building of the customer/LOB specific Alert Detection Patterns. An important focus is given to the understanding of the different Log Data coming out of SAP ERP systems. A technical overview shows the different components of ETD on how it can be set up in different modes, and how to connect to the various log sources.
New Course: SECETD SAP Enterprise Threat...
In this course you will learn how to use SAP Enterprise Threat Detection (ETD) to secure and monitor the security of your SAP landscape. The main objective of the course is to understand how the different features of the product can be used, like Alert Processing, Forensic Analysis and Threat Hunting, Security Monitoring, customizing of the SAP delivered Alert Detection Patterns, building of the customer/LOB specific Alert Detection Patterns. An important focus is given to the understanding of the different Log Data coming out of SAP ERP systems. A technical overview shows the different components of ETD on how it can be set up in different modes (e.g. High Availability set up alternatives), and how to connect to the various log sources...Read More
SAP Get Social
0 notes
Text
SAP Business Integrity Screening. What should you know?
SAP Business Integrity Screening
SAP Business Integrity Screening is a tool that helps organizations detect potential risks and compliance issues within their business processes. It is a key component of SAP’s Governance, Risk, and Compliance (GRC) suite, which provides a range of solutions to help organizations manage risk and ensure compliance with various regulations and standards.
One of the main benefits of SAP Business Integrity Screening is its ability to automate the risk detection process. By integrating with various SAP systems and data sources, it can continuously monitor business transactions and flag any potential risks or issues for further investigation. This can help organizations identify problems before they become more serious and take proactive steps to mitigate any risks..
SAP Business Integrity Screening also provides a range of analytical tools and reporting capabilities, which allow organizations to analyse and understand the risks they face. This includes the ability to create custom risk scenarios, simulate different risk scenarios to understand the potential impacts and create reports to help communicate risk information to relevant stakeholders..
In addition to detecting potential risks, SAP Business Integrity Screening can also help organizations manage and mitigate those risks. It provides a range of tools to help organizations develop and implement risk management plans, as well as tools to monitor the effectiveness of those plans..
Overall, SAP Business Integrity Screening is a powerful tool that can help organizations detect and manage risks and ensure compliance with various regulations and standards. Automating the risk detection process, providing analytical tools, and reporting capabilities, it can help organizations proactively manage risk and ensure the integrity of their business processes..
There are several advantages to using SAP Business Integrity Screening:
Real-time monitoring: SAP Business Integrity Screening can scan millions of transactions and communications per day, helping organizations detect and address potential issues in real time.
Advanced analytics and machine learning: The tool uses advanced analytics and machine learning algorithms to analyse data sources and flag potential violations of legal and ethical standards.
Compliance management: SAP Business Integrity Screening provides detailed reports and dashboards that give organizations visibility into their compliance status and allow them to track progress over time.
Customization: The tool can be customized to meet the specific needs and requirements of different organizations and industries.
Scalability: SAP Business Integrity Screening can handle large volumes of data, making it suitable for organizations of all sizes.
Integration with other SAP solutions: SAP Business Integrity Screening can be easily integrated with other SAP solutions, such as SAP S/4HANA and SAP Ariba, providing a seamless and consistent experience for users.
Read more: https://togglenow.com/blog/sap-business-integrity-screening/
#sap security#sap security services#sap grc security#sap grc and security#sap audit management#sap sod analysis#sap hana solutions#sap hana server access#sap hana software#SAP Cloud IAG#sap audit services#SAP Risk management#sap user management automation#Protect Sap with MFA#SAP ETD#GRC Access Control#SAP 2FA
0 notes
Text
Insider attacks - How vulnerable are you to insider threat?
A recent study reveals that ERP systems, including SAP, are more vulnerable to insider attacks
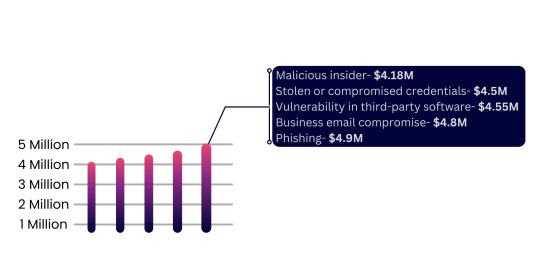
The recent Data breach report by IBM reveals that malicious insiders are equally liable for the data breaches. Many of us think that stolen or compromised credentials are the primary or the most common cause of a data breach.
It is also evident that Insider attacks by these malicious insiders are most common across the ERP systems and pose a potential threat to the organization’s key assets, i.e., data. Here are a few facts:
6 out of 10 data thefts in the past 3 years are by malicious insider attacks, while only 4 are by external threats.
Nearly half of all data breaches happen in the cloud. It cost $4.24M loss on average for organizations that are on private clouds and $5.02M for organizations in public clouds.
According to the “Insider Threat Report 2022”, insider attacks are a much more significant threat. As far as the security of SAP systems is concerned, insider attacks are by far the greatest problem.
Identifying a malicious insider attacks is a tougher task than an external event
The focus of this blog is on securing the SAP systems. However, ToggleNow has expertise in Oracle GRC and can build Ruleset for other ERP packages as per the customer’s requirement.
Did you ever think of the potential reasons for malicious insider attacks? If not, here is what you should know:
Unstructured Authorizations are the Primary Culprits
Many of the insider attacks are by employees who cause problems either intentionally, unintentionally, or by mistake. A recent study reveals that the main reason for unintended security incidents was that the authorizations were granted too generously (Wider authorizations).
This is a common issue in SAP systems where roles and authorizations are developed ad-hoc and from time to time they are piled up. With the complexity of an ERP system, it is easier for administrators – who do not necessarily have the expertise required to appropriately restrict authorizations – to assign authorizations by way of general role descriptions. This gives wider authorizations.
Secondly, not auditing the system for non-Dialog users such as communication, system, or service. Malicious insider attacks typically target these IDs, which usually have broader authorizations. It is therefore vital to audit them periodically and set up processes to utilize them correctly.
Third on the list of reasons for security problems is the complexity of the relevant systems. A new way of working has been introduced by Industry 4.0. This is the age of systems communicating with one another. Furthermore, SAP AG acquired many products, including S/4 HANA, C/4 HANA, the SAP Cloud Platform, SAP Ariba, SAP Success Factors, etc. It is crucial to secure not only the systems but also the interfaces since these systems are interconnected. There is a high level of vulnerability in cloud-based systems as well, as previously mentioned.
The latest IBM report indicates that cloud systems are equally vulnerable to attacks. It has been estimated that 45% of breaches have happened in the cloud.
Read more: https://togglenow.com/blog/insider-attacks-to-sap-system/
#sap security#sap security services#sap grc security#sap grc and security#sap audit management#sap sod analysis#sap hana solutions#sap hana server access#sap hana software#SAP Cloud IAG#sap audit services#SAP Risk management#sap user management automation#Protect Sap with MFA#SAP ETD#GRC Access Control#SAP 2FA
0 notes
Text
SAP HANA DB | 6 Best Tips To Secure HANA Database
How secure your SAP HANA DB is?
To secure SAP HANA DB modern businesses employ a variety of applications such as SAP, etc., to run their business with seamless integrations. These applications contain vast amounts of sensitive business data. Hackers often target databases instead of applications, as many of the enterprises give utmost importance to secure the applications, but not the databases. To prevent possible attacks, comprehensive security processes and configurations are crucial at the database level as well.
There are however differences between database systems when it comes to security. Not all the databases are the same. Some, such as SAP HANA, provide built-in security. Others require you to manage security manually. The purpose of this article is to give you an overview of SAP HANA and its security features. Additionally, you will learn some best practices for securing SAP HANA deployments.

What Is SAP HANA?
It is SAP’s next-generation revolutionary database, built primarily with a column-oriented table structure. Additionally, it uses in-memory storage, storing data in Random Access Memory (RAM). This differs from traditional databases, which tend to use persistent storage like hard drives.
SAP HANA can store and retrieve application data from memory, which functions as a database server. As your data is stored in memory, you can retrieve it much faster than data that is stored on the disk.
With SAP HANA, you can perform a variety of advanced analytics, such as stream analysis, spatial data analysis, and predictive analytics. Additionally, you can use it to transfer data between databases using Extract, Transform, Load (ETL) processes.
SAP HANA runs in a variety of environments, including on-premises and in the cloud. You can run SAP HANA on Azure, AWS, or GCP.
There are however differences between database systems when it comes to security. Not all the databases are the same. Some, such as SAP HANA, provide built-in security. Others require you to manage security manually. The purpose of this article is to give you an overview of SAP HANA and its security features. Additionally, you will learn some best practices for securing SAP HANA deployments.
Risks with SAP HANA database
SAP HANA DB are vulnerable to a variety of risks, including:
Web applications – Internet access leaves systems more vulnerable due to the requirement for open traffic flow. Since SAP HANA supports integration to third party application, reporting tools, and IDE environments, it is vulnerable to code injection and cross-site scripting attacks. These attacks involve inserting malicious scripts or commands through user input.
RAM scraping – Viruses or malware run within SAP HANA’s memory are used to infect your systems. Since memory is ephemeral, it is difficult to track these risks. Also, in-memory processes cannot be encrypted since it would degrade performance, so attacks are difficult to stop.
Read more: https://togglenow.com/blog/tips-to-secure-sap-hana-db/
#sap security#sap security services#sap grc security#sap grc and security#sap audit management#sap sod analysis#sap hana solutions#sap hana server access#sap hana software#SAP Cloud IAG#sap audit services#SAP Risk management#sap user management automation#Protect Sap with MFA#SAP ETD#GRC Access Control#SAP 2FA
0 notes
Text
Why Security Optimization important? Secure Your SAP System
Security Optimization as a Service Portfolio is the right solution to prevent a full downtime and costly security incidents by analyzing high-risk violations and taking security measures proactively.
Read through this Portfolio article from SAP that details what it can do for you.
By using Security Optimization Service, you can avoid business interruptions and ensure that the security aspect of SAP solutions is managed properly, reducing risk. As a result of this service, you will be able to concentrate on your daily business requirements instead of spending time handling the complexities of security maintenance. The advantages are:
Decrease the risk of a system intrusion
Ensure the confidentiality of your business data
Ensure the authenticity of your users
Substantially reduce the risk of costly downtime due to wrong user interaction

Where to start?
The EarlyWatch Alert (EWA) report is the most comprehensive snapshot of your SAP systems. The Security section gives you a detailed analysis, more accurate information to keep your SAP systems protected along with the root cause analysis of various findings.
Refer to the SAP note # 863362 to know more about the security checks in the EWA report. Incase if the EWA report generation is not yet configured, refer to SAP note # 2282944 (EarlyWatch Alert: Solution Manager 7.2 how to set up/configure EWA reports or add email recipients) that details the steps to configure.
Should you need help setting up the Solution Manager, our experts can create a SolMan system and set up the EWA configuration in just 10 to 15 days.
Is EarlyWatch (EWA) report itself is enough?
Certainly not. While EWA gives you a snapshot of your system, Solution Manager has lot many features that could help you to safeguard your SAP system. Experts recommend implementing additional tools like the Security Optimization Service, System Recommendations configuration in Solution Manager, or Change Diagnostics and Configuration Validation, also called as E2E Change Analysis and Change Reporting and Configuration Validation in Solution Manager.
These tools can be configured easily that adds an additional layer of security.
Great. Will this be sufficient for me to keep my system secure?
May be not. No solution can give you 100% gurantee. Monitoring the systems against the Security baseline is much important and is a contineous activity. In addition to utilizing the standard Security baselines by SAP, experts recommend to use additional applications such as SAP GRC Process Control, Risk Management etc.,
ToggleNow boasts an easy-to-use reporting application called GAMS360. It provides 100+ baseline reports for review, so it’s easy to spot problems as they arise. Further, the system trigger alerts for immediate review by the system owners/controllers.
Can these tools help me to protect my SAP systems completely?
Are these tools capable enough to detect and stop all sorts of risks associated with my SAP systems?
There are a variety of ways to protect your SAP systems. As mentioned, no single tool/product can make your SAP system free from risks. Incase if you have an authorization setup built a decade ago, uou may also need to consider an SAP Security Engagement which will provide you with an expert-guided analysis and approach for your SAP landscape.
ToggleNow enables its customers to leverage their business processes and streamline their security measures as part of the SAP Digital Transformation program.
One that will help you to discover the ASIS and derive a TOBE Roadmap. Second, that will identify the various processes where automation can be implemented quickly.
We take the EarlyWatch report as the baseline and also run various scripts to extract the current status of the system. This will be our starting point to offer detailed services mainly around Security Optimization.
Combining the results of the initial discovery, the security policy of the company, and the subject matter expertise, we define the SAP Security Baseline and make the necessary tweaks in the application, and the tools selected.
#sap security#sap security services#sap grc security#sap grc#sap risk and controls#sap grc risk management#sap risk management module#top sap consulting companies#SAP Enterprise Threat Detection#Enhanced Security with SAP ETD
0 notes
Text
A Right approach to build authorizations in SAP HANA
SAP HANA Privilege-based Roles – A deep dive
Designing, configuring, and implementing SAP Security is a complex and resource-intensive task. Hence, companies should identify the right approach before building authorizations. This is also important when it comes to SAP HANA privilege-based roles.
I have personally experienced and helped a few organizations with the design of the role definition approach. From this experience, I can say that identifying the proper security requirements during the system build helps in avoiding the need for redesigning at a later stage.

Before we move on, please note that the SAP HANA platform has its own role model, which is more complex than the SAP NetWeaver ABAP authorization model. SAP HANA has:
Analytic Privileges that will restrict user authorization on data
System Privileges that will control the authorization on administrative tasks
Object Privileges that allows various authorizations such as SELECT, DELETE, EXECUTE, etc., on database objects
Package Privileges are used for providing read/write authorization on repositories
Application Privileges are used for managing HANA applications, mostly XS Engine based
These privileges can be assigned to the users directly from the HANA Studio, or Web IDE if the administrator has a USER ADMIN privilege assigned to him. However, before designing the authorization approach, I would also like to highlight a few points that should be considered:
– Assigning privileges directly is not a recommended approach as:
It increases the maintenance activity
Makes the authorization management weird, and you will have no clue of who has what
Unnecessary access has to be provided to the administrators due to the GRANT authorization limitation.
Issues with ownership as objects are owned by the creator and not by the repository owner.
#sap audit management#sap sod analysis#sap hana solutions#sap hana server access#sap hana software#SAP Cloud IAG#sap audit services#SAP Risk management#sap user management automation#Protect Sap with MFA#SAP ETD#GRC Access Control#SAP 2FA#SAp Security
0 notes
Text
SAP Enterprise Threat Detection | SAP ETD | Threat Management | ToggleNow
SAP Enterprise Threat Detection (SAP ETD) plays a pivotal role in safeguarding complex SAP environments supporting critical business processes. ToggleNow implemented SAP ETD to heighten visibility and monitoring across organizational SAP landscapes. By centralizing logs and normalizing data sources within the solution’s security knowledge base, SAP ETD effectively identified internal threats from both internal and third-party users involved in non-core activities.

This tool empowered security teams with crucial insights, enabling swift detection of fraud attempts and information leaks within SAP systems. In the vast and intricate realm of SAP landscapes, SAP ETD emerged as a vital asset, offering a proactive approach to tackle cybersecurity challenges, particularly in identifying and addressing security risks that would otherwise be challenging to detect.
Read more: https://togglenow.com/services/sap-entripise-threat-detection/
0 notes
Text
SAP IAG for Enhanced Access Governance - ToggleNow
Toggle Now providing SAP IAG service. Know about key features & benefits of SAP access control Cloud, & provide best practices for implementation & customization
Understanding SAP Identity Access Governance (IAG)
SAP IAG serves as a comprehensive framework within the SAP ecosystem, designed to manage user access, control risks, and ensure compliance with regulatory standards. Its primary focus lies in governing user access across various SAP applications that are hosted on-premise and cloud along with other non-sap systems such as Azure ID, and platforms.

Key Components of SAP IAG
SAP IAG offers 5 key services as outlined in the below figure:

1. Access Analysis Service
Similar to SAP GRC, SAP IAG also has powerful capabilities to assess and mitigate access risks associated with user permissions. It conducts thorough analysis, identifying potential risks and vulnerabilities within the access structure. A clear definition of risks are displayed for each of the users enabling the Business Owners to take better decisions on managing the risks for each of the user.
2. Privileged Access Management (PAM) Service
PAM Service is similar to GRC Access Control Emergency Access Management aka Firefighter, a specialized solution designed to manage critical access by controlling, monitoring, and securing the SAP systems from unauthorized changes using privileged accounts. It focuses on a more controlled assignment and management of accesses which has business impact. PAM ensure compliance with regulatory standards, thereby fortifying the overall security posture of an enterprise.
Read more: https://togglenow.com/blog/sap-iag-for-enhanced-access-governance/
0 notes
Text
SAP Enterprise Threat Detection | SAP ETD | Threat Management | ToggleNow
Deploy SAP Enterprise Threat Detection with Expert Guidance from ToggleNow. Our Services Encompass Implementation, Detection Pattern Setup, and Ongoing Support for SAP ETD, Demonstrating Proficiency Across the Spectrum of Threat Detection.

SAP Enterprise Threat Detection (SAP ETD) plays a pivotal role in safeguarding complex SAP environments supporting critical business processes. ToggleNow implemented SAP ETD to heighten visibility and monitoring across organizational SAP landscapes. By centralizing logs and normalizing data sources within the solution’s security knowledge base, SAP ETD effectively identified internal threats from both internal and third-party users involved in non-core activities.
This tool empowered security teams with crucial insights, enabling swift detection of fraud attempts and information leaks within SAP systems. In the vast and intricate realm of SAP landscapes, SAP ETD emerged as a vital asset, offering a proactive approach to tackle cybersecurity challenges, particularly in identifying and addressing security risks that would otherwise be challenging to detect.
Read more: https://togglenow.com/services/sap-entripise-threat-detection/
0 notes
Text
SAP Enterprise Threat Detection | SAP ETD | Threat Management | ToggleNow
SAP Enterprise Threat Detection (SAP ETD) plays a pivotal role in safeguarding complex SAP environments supporting critical business processes. ToggleNow implemented SAP ETD to heighten visibility and monitoring across organizational SAP landscapes. By centralizing logs and normalizing data sources within the solution’s security knowledge base, SAP ETD effectively identified internal threats from both internal and third-party users involved in non-core activities.

This tool empowered security teams with crucial insights, enabling swift detection of fraud attempts and information leaks within SAP systems. In the vast and intricate realm of SAP landscapes, SAP ETD emerged as a vital asset, offering a proactive approach to tackle cybersecurity challenges, particularly in identifying and addressing security risks that would otherwise be challenging to detect.
Read more: https://togglenow.com/services/sap-entripise-threat-detection/
#SAP Enterprise Threat Detection#SAP Enterprise Threat#Threat Detection#Threat Management#SAP ETD#sap audit services#SAP Cloud IAG#SAP Authorization Review#SAP Role Review#SAP AC Implementation#SAP GRC RM#SAP GRC AM
0 notes
Text
SAP Enterprise Threat Detection | SAP ETD | Threat Management | ToggleNow
SAP Enterprise Threat Detection (SAP ETD) plays a pivotal role in safeguarding complex SAP environments supporting critical business processes. ToggleNow implemented SAP ETD to heighten visibility and monitoring across organizational SAP landscapes. By centralizing logs and normalizing data sources within the solution’s security knowledge base, SAP ETD effectively identified internal threats from both internal and third-party users involved in non-core activities.

This tool empowered security teams with crucial insights, enabling swift detection of fraud attempts and information leaks within SAP systems. In the vast and intricate realm of SAP landscapes, SAP ETD emerged as a vital asset, offering a proactive approach to tackle cybersecurity challenges, particularly in identifying and addressing security risks that would otherwise be challenging to detect.
Read more: https://togglenow.com/services/sap-entripise-threat-detection/
#sap sod analyzer#sap audit services#sap grc implementation#sap grc audit management#sap grc integration#SAP ETD#SAP Enterprise Threat Detection#SAP Threat#SAP Cloud IAG
0 notes