#Subfinder
Explore tagged Tumblr posts
Text
Lobo Guará - Cyber Threat Intelligence Platform
Lobo Guará is a platform aimed at cybersecurity professionals, with various features focused on Cyber Threat Intelligence (CTI). It offers tools that make it easier to identify threats, monitor data leaks, analyze suspicious domains and URLs, and much more. Features 1. SSL Certificate Search Allows identifying domains and subdomains that may pose a threat to organizations. SSL certificates…
0 notes
Text
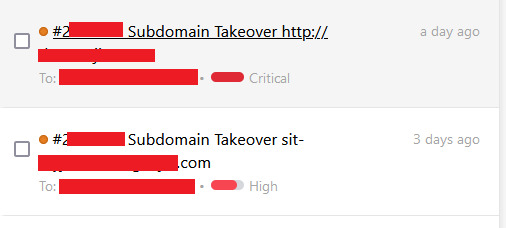
How I Discovered and Reported Two Subdomain Takeovers
I am constantly searching for potential vulnerabilities because I am an avid security enthusiast and bug bounty hunter. I recently discovered two subdomain takeovers thanks to a private invitation I received on HackerOne. This is a detailed explanation of how I found and reported these vulnerabilities. I got a private invitation to take part in a security program on HackerOne. The invitation…
View On WordPress
1 note
·
View note
Text
👩🏻💻 𝙰𝚛𝚌𝚑𝚒𝚟𝚒𝚘 𝚍𝚒 𝚜𝚝𝚛𝚞𝚖𝚎𝚗𝚝𝚒 𝚙𝚎𝚛 𝚌𝚢𝚋𝚎𝚛𝚜𝚎𝚌𝚞𝚛𝚒𝚝𝚢 𝚌𝚑𝚎 𝚖𝚒 𝚟𝚎𝚗𝚐𝚘𝚗𝚘 𝚌𝚘𝚗𝚜𝚒𝚐𝚕𝚒𝚊𝚝𝚒 𝚘 𝚌𝚒𝚝𝚊𝚝𝚒 𝚗𝚎𝚕 𝚝𝚎𝚖𝚙𝚘
AnyRun: cloud-based malware analysis service (sandbox).
Burp Suite: a proprietary software tool for security assessment and penetration testing of web applications. La community edition, gratis, contiene Burp Proxy and Interceptor (intercetta le richieste effettuate dal browser, consente modifiche on-the-fly e di modificare le risposte; utile per testare applicazioni basate su javascript), Burp Site Map, Burp Logger and HTTP History, Burp Repeater (consente di replicare e modificare le richieste effettuate, aggiungere parametri, rimuoverli, ecc), Burp Decoder, Burp Sequencer, Burp Comparer, Burp Extender (estensioni delle funzionalità di burpsuite, plugin specializzati per individuare bug specifici, automatizzare parte delle attività, ecc) e Burp Intruder (consente di iterare richieste con payload differenti e automatizzare attività di injection).
CyberChef: is a simple, intuitive web app for carrying out all manner of "cyber" operations within a web browser. These operations include simple encoding like XOR and Base64, more complex encryption like AES, DES and Blowfish, creating binary and hexdumps, compression and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character encodings, and much more.
DorkSearch: an AI-powered Google Dorking tool that helps create effective search queries to uncover sensitive information on the internet.
FFUF: fast web fuzzer written in Go.
GrayHatWarfare: is a search engine that indexes publicly accessible Amazon S3 buckets. It helps users identify exposed cloud storage and potential security risks.
JoeSandbox: detects and analyzes potential malicious files and URLs on Windows, Mac OS, and Linux for suspicious activities. It performs deep malware analysis and generates comprehensive and detailed analysis reports.
Nikto: is a free software command-line vulnerability scanner that scans web servers for dangerous files or CGIs, outdated server software and other problems.
Nuclei: is a fast, customizable vulnerability scanner powered by the global security community and built on a simple YAML-based DSL, enabling collaboration to tackle trending vulnerabilities on the internet. It helps you find vulnerabilities in your applications, APIs, networks, DNS, and cloud configurations.
Owasp Zap: Zed Attack Proxy (ZAP) by Checkmarx is a free, open-source penetration testing tool. ZAP is designed specifically for testing web applications and is both flexible and extensible. At its core, ZAP is what is known as a “manipulator-in-the-middle proxy.” It stands between the tester’s browser and the web application so that it can intercept and inspect messages sent between browser and web application, modify the contents if needed, and then forward those packets on to the destination. It can be used as a stand-alone application, and as a daemon process.
PIA: aims to help data controllers build and demonstrate compliance to the GDPR. It facilitates carrying out a data protection impact assessment.
SecLists: is the security tester's companion. It's a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more.
SQLMAP: is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Subfinder: fast passive subdomain enumeration tool.
Triage: cloud-based sandbox analysis service to help cybersecurity professionals to analyse malicious files and prioritise incident alerts and accelerate alert triage. It allows for dynamic analysis of files (Windows, Linux, Mac, Android) in a secure environment, offering detailed reports on malware behavior, including malicious scoring. This service integrates with various cybersecurity tools and platforms, making it a valuable tool for incident response and threat hunting.
VirusTotal: analyse suspicious files, domains, IPs and URLs to detect malware and other breaches, automatically share them with the security community.
Wayback Machine: is a digital archive of the World Wide Web founded by Internet Archive. The service allows users to go "back in time" to see how websites looked in the past.
Wapiti: allows you to audit the security of your websites or web applications. It performs "black-box" scans of the web application by crawling the webpages of the deployed webapp, looking for scripts and forms where it can inject data. Once it gets the list of URLs, forms and their inputs, Wapiti acts like a fuzzer, injecting payloads to see if a script is vulnerable.
WPScan: written for security professionals and blog maintainers to test the security of their WordPress websites.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝚂𝚒𝚝𝚒-𝚕𝚊𝚋𝚘𝚛𝚊𝚝𝚘𝚛𝚒
flAWS: through a series of levels you'll learn about common mistakes and gotchas when using Amazon Web Services (AWS).
flAWS2: this game/tutorial teaches you AWS (Amazon Web Services) security concepts. The challenges are focused on AWS specific issues. You can be an attacker or a defender.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝙱𝚛𝚎𝚟𝚎 𝚕𝚒𝚜𝚝𝚊 𝚍𝚒 𝚜𝚒𝚝𝚒 𝚊𝚙𝚙𝚘𝚜𝚒𝚝𝚊𝚖𝚎𝚗𝚝𝚎 𝚟𝚞𝚕𝚗𝚎𝚛𝚊𝚋𝚒𝚕𝚒 𝚜𝚞 𝚌𝚞𝚒 𝚏𝚊𝚛𝚎 𝚎𝚜𝚎𝚛𝚌𝚒𝚣𝚒𝚘
http://testphp.vulnweb.com
0 notes
Text
A Comprehensive Guide to Bug Hunting
This guide provides a structured, step-by-step approach to bug hunting, focusing on reconnaissance, subdomain enumeration, live domain filtering, vulnerability scanning, and JavaScript analysis.
It incorporates essential tools like SecretFinder, Katana, GetJS, Nuclei, Mantra, Subjs, Grep, and Anew to enhance efficiency and coverage.
1. Initial Reconnaissance
Gather information about the target to identify IP blocks, ASNs, DNS records, and associated domains.
Tools and Techniques:
ARIN WHOIS: Lookup IP blocks and ownership details.
BGP.HE: Retrieve IP blocks, ASNs, and routing information.
ViewDNS.info: Check DNS history and reverse IP lookups.
MXToolbox: Analyze MX records and DNS configurations.
Whoxy: Perform WHOIS lookups for domain ownership.
Who.is: Retrieve domain registration details.
Whois.domaintools: Advanced WHOIS and historical data.
IPAddressGuide: Convert CIDR to IP ranges.
NSLookup: Identify nameservers.
BuiltWith: Discover technologies used on the target website.
Amass: Perform comprehensive information gathering (subdomains, IPs, etc.).
Shodan: Search for exposed devices and services.
Censys.io: Identify hosts and certificates.
Hunter.how: Find email addresses and domain-related data.
ZoomEye: Search for open ports and services.
Steps:
Identify the target domain and associated IP ranges.
Collect WHOIS data for ownership and registration details.
Map out nameservers and DNS records.
Use Amass to enumerate initial subdomains and IPs.
Leverage Shodan, Censys, and ZoomEye to find exposed services.
2. Subdomain Enumeration
Subdomains often expose vulnerabilities. The goal is to discover as many subdomains as possible, including sub-subdomains, and filter live ones.
Tools and Techniques:
Subfinder: Fast subdomain enumeration.
Amass: Advanced subdomain discovery.
Crt.sh: Extract subdomains from certificate transparency logs.
Sublist3r: Enumerate subdomains using multiple sources.
FFUF: Brute-force subdomains.
Chaos: Discover subdomains via ProjectDiscovery’s dataset.
OneForAll: Comprehensive subdomain enumeration.
ShuffleDNS: High-speed subdomain brute-forcing (VPS recommended).
Katana: Crawl websites to extract subdomains and endpoints.
VirusTotal: Find subdomains via passive DNS.
Netcraft: Search DNS records for subdomains.
Anew: Remove duplicate entries from subdomain lists.
Httpx: Filter live subdomains.
EyeWitness: Take screenshots of live subdomains for visual analysis.
Steps:
Run Subfinder, Amass, Sublist3r, and OneForAll to collect subdomains.
Query Crt.sh and Chaos for additional subdomains.
Use FFUF and ShuffleDNS for brute-forcing (on a VPS for speed).
Crawl the target with Katana to extract subdomains from dynamic content.
Combine results into a single file and use Anew to remove duplicates: cat subdomains.txt | anew > unique_subdomains.txt
Filter live subdomains with Httpx: cat unique_subdomains.txt | httpx -silent > live_subdomains.txt
Use EyeWitness to capture screenshots of live subdomains for manual review.
3. Subdomain Takeover Checks
Identify subdomains pointing to unclaimed services (e.g., AWS S3, Azure) that can be taken over.
Tools:
Subzy: Check for subdomain takeover vulnerabilities.
Subjack: Detect takeover opportunities (may be preinstalled in Kali).
Steps:
Run Subzy on the list of subdomains: subzy run --targets live_subdomains.txt
Use Subjack for additional checks: subjack -w live_subdomains.txt -a
Manually verify any flagged subdomains to confirm vulnerabilities.
4. Directory and File Bruteforcing
Search for sensitive files and directories that may expose vulnerabilities.
Tools:
FFUF: High-speed directory brute-forcing.
Dirsearch: Discover hidden directories and files.
Katana: Crawl for endpoints and files.
Steps:
Use FFUF to brute-force directories on live subdomains: ffuf -w wordlist.txt -u https://subdomain.target.com/FUZZ
Run Dirsearch for deeper enumeration: dirsearch -u https://subdomain.target.com -e *
Crawl with Katana to identify additional endpoints: katana -u https://subdomain.target.com -o endpoints.txt
5. JavaScript Analysis
Analyze JavaScript files for sensitive information like API keys, credentials, or hidden endpoints.
Tools:
GetJS: Extract JavaScript file URLs from a target.
Subjs: Identify JavaScript files across subdomains.
Katana: Crawl for JavaScript files and endpoints.
SecretFinder: Search JavaScript files for secrets (API keys, tokens, etc.).
Mantra: Analyze JavaScript for vulnerabilities and misconfigurations.
Grep: Filter specific patterns in JavaScript files.
Steps:
Use Subjs and GetJS to collect JavaScript file URLs: cat live_subdomains.txt | subjs > js_files.txt getjs --url https://subdomain.target.com >> js_files.txt
Crawl with Katana to find additional JavaScript files: katana -u https://subdomain.target.com -o js_endpoints.txt
Download JavaScript files for analysis: wget -i js_files.txt -P js_files/
Run SecretFinder to identify sensitive data: secretfinder -i js_files/ -o secrets.txt
Use Mantra to detect vulnerabilities in JavaScript code: mantra -f js_files/ -o mantra_report.txt
Search for specific patterns (e.g., API keys) with Grep: grep -r "api_key\|token" js_files/
6. Vulnerability Scanning
Perform automated scans to identify common vulnerabilities.
Tools:
Nuclei: Fast vulnerability scanner with customizable templates.
Mantra: Detect misconfigurations and vulnerabilities in web assets.
Steps:
Run Nuclei with a comprehensive template set: nuclei -l live_subdomains.txt -t cves/ -t exposures/ -o nuclei_results.txt
Use Mantra to scan for misconfigurations: mantra -u https://subdomain.target.com -o mantra_scan.txt
7. GitHub Reconnaissance
Search for leaked sensitive information in public repositories.
Tools:
GitHub Search: Manually search for target-related repositories.
Grep: Filter repository content for sensitive data.
Steps:
Search GitHub for the target domain or subdomains (e.g., from:target.com).
Clone relevant repositories and use Grep to find secrets: grep -r "api_key\|password\|secret" repo_folder/
Analyze code for hardcoded credentials or misconfigurations.
8. Next Steps and Analysis
Review EyeWitness screenshots for login pages, outdated software, or misconfigurations.
Analyze Nuclei and Mantra reports for actionable vulnerabilities.
Perform manual testing on promising subdomains (e.g., XSS, SQLi, SSRF).
Document findings and prioritize vulnerabilities based on severity.
Additional Notes
Learning Resources: Complete TryHackMe’s pre-security learning path for foundational knowledge.
Tool Installation:
Install Anew: go install github.com/tomnomnom/anew@latest
Install Subzy: go install github.com/PentestPad/subzy@latest
Install Nuclei: go install github.com/projectdiscovery/nuclei/v2/cmd/nuclei@latest
Install Katana: go install github.com/projectdiscovery/katana/cmd/katana@latest
Optimization: Use a VPS for resource-intensive tools like ShuffleDNS and FFUF.
File Management: Organize outputs into separate files (e.g., subdomains.txt, js_files.txt) for clarity.
1 note
·
View note
Text
WebCopilot: Enumerates Subdomains and Scans for Vulnerabilities | #Enumeration #Subdomains #WebCopilot #Security
0 notes
Text
AesopOnline
AesopOnline is a new online portal that has taken the place of the current SubFinder absence system. AesopOnline was established on June 25, 2016. With the establishment of the AesopOnline portal, the SubFinder system can no longer be used now. Therefore, all the NPS employees have shifted to the AesopOnline portal now.
Features Of AesopOnline portal
AesopOnline system gives its employees more flexible ways while marking absences and also provides their classes with substitutes that don’t affect their classes too.
There are many modifications to the AesopOnline portal, but one of the majors is that users can now use their mobile phones to operate the system. Anyone can start using the AesopOnline portal just by visiting their website.
How To Sign In To the AesopOnline portal
AesopOnline system can be used anywhere and anytime if you have a good and stable internet connection.
However, for signing in, you need to have separate details for sign-in. These details are mandatory to get access while you are using the portal on your mobile device.
To know more about your AesopOnline credentials, you can e-mail NPS directly.
Also, you will get detailed information and instructions to use the online portal, and also with this, you can get in touch with us for any help.
Use of AesopOnline portal
The student learning must be uninterrupted whether the team is present there or not.
However, this indicates that you will have to regulate the vacation requests, also keep a check on the vacation credits, and also be responsive to district–wide emotions by putting up questions like, “How many days do I have in my hand?” and also get a replacement if required.
You can utilize your own time with the audience and substitute management (formerly Aesop) and ensure that the student learning doesn’t get harmed in any way.
You need to gather the information you need and make correct decisions working in favor of student learning.
To get access to the AesopOnline portal, you need to visit the official website and follow the steps below.
Get started by visiting the official portal of AesopOnline.
After opening the portal, open the register section. In this section, you will see a form that will ask you about your details, such as your name, address, contact details, etc.
Be sure while entering your mobile number, as it will work as your user ID in the future while you operate the portal.
Next, you will have to submit your password. Make sure it is a little tricky and difficult to guess.
Take a glance at the details you have entered again, and tap on “Submit” to proceed forwards.
With this, you have completed your registration process on the AesopOnline portal.
The online portal of AesopOnline is designed so everyone can use it. Also, there are many other advantages too that you can take by using AesopOnline:
No need for access
To get started with the AesopOnline portal, you don’t need any access to any hardware, software, or phone line.
Easily Accessible
You can use the frontline AesopOnline easily, even on your phone or any other kind of electronic device which has an internet connection (which includes a mobile phone too).
User-friendly interface
The portal of AesopOnline is designed in a way that all users can operate it without any difficulty.
Safe and secure platform
The users of the AesopOnline platform also don’t have to worry about their safety, and the platform is completely safe and secure.
Time-saving solution
AesopOnline is a time-saving platform that saves precious time for the backup calls that you have to make manually. In addition, it tracks absences and reports with full efficiency.
Keeps Student Learning its priority
AesopOnline system ensures that the student learning system doesn’t get harmed even if there’s the absence of anyone on board.
1 note
·
View note
Text
找子網域的 subfinder
在「subfinder – 找子網域的工具」這邊看到的,專案是用 Golang 寫的,需要 Golang 1.10+ 才能裝… 這類工具在 PT 找入口時還蠻好用的。
裝完後馬上跑個熱門的 ./subfinder -d teamkp.tw 可以看到不多:
Total 4 Unique subdomains found for teamkp.tw .teamkp.tw donate.teamkp.tw www.donate.teamkp.tw www.teamkp.tw
加上 -v 則可以看到來源。
View On WordPress
2 notes
·
View notes
Text
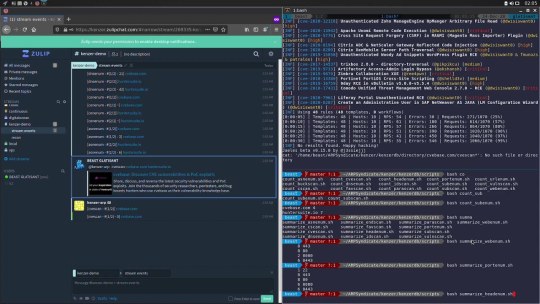
Kenzer - Automated Web Assets Enumeration And Scanning
Kenzer - Automated Web Assets Enumeration And Scanning #AQUATONE #Assets #Automated #Axiom #Domlock #Enumeration
Automated Web Assets Enumeration & Scanning Instructions for running Create an account on Zulip Navigate to Settings > Your Bots > Add a new bot Create a new generic bot named kenzer Add all the configurations in configs/kenzer.conf Install/Run using – ./install.sh -b [if you need kenzer-compatible binaries to be installed] ./install.sh [if you do not need kenzer-compatible binaries to be…

View On WordPress
#AQUATONE#Assets#Automated#Axiom#Domlock#Enumeration#Favinizer#Ffuf#Jaeles#Kenzer#Kenzer Bin#Kenzer Templates#Nuclei#S3Hunter#scan#Scanner#Scanning#shuffleDNS#subdomain#SUBFINDER#web
0 notes
Text
[Media] KENZER
KENZER Automated web assets enumeration & scanning. ▫️ Subdomain Enumeration using Subfinder, Amass, CerteX, TLSX, DNSX, NXScan, & ShuffleDNS ▫️ Port Enumeration using NXScan (Shodan, Netlas, Naabu & Nmap) ▫️ Web Enumeration using HttpX, Favinizer, Domlock, Gau, GoSpider, URLhunter & Waymore ▫️ Web Vulnerability Scanning using Jaeles, Wapiti, ZAP, Nuclei, Rescro & DalFox ▫️ Backup Files Scanning using Fuzzuli ▫️ Git Repository Enumeration & Scanning using RepoHunt & Trufflehog ▫️ Web Screenshot Identification using Shottie & Perceptic ▫️ WAF Detection & Avoidance using WafW00f & Nuclei ▫️ Reputation Scoring using DomREP (GreyNoise, URLHaus, PhishTank) ▫️ Every task can be distributed over multiple machines https://github.com/ARPSyndicate/kenzer
YouTubeARPSyndicate | Kenzer | Automated web assets enumeration & scanningKenzer (https://github.com/ARPSyndicate/kenzer) is a tool that aims to automate the workflow of web assets enumeration & scanning. This video demonstrates its basic usage & there are dozen of other things that could be done with it.
1 note
·
View note
Text
Ars0N-Framework - A Modern Framework For Bug Bounty Hunting
Howdy! My name is Harrison Richardson, or rs0n (arson) when I want to feel cooler than I really am. The code in this repository started as a small collection of scripts to help automate many of the common Bug Bounty hunting processes I found myself repeating. Over time, I built a simple web application with a MongoDB connection to manage my findings and identify valuable data points. After 5…
youtube
View On WordPress
#Ars0N-Framework#KitPloit#Shuffledns#Subdomain#Subdomains#Subfinder#Sublist3R#Transparency#Troubleshooting#VAST#Youtube
0 notes
Text
Rapidclick github

#RAPIDCLICK GITHUB FULL#
#RAPIDCLICK GITHUB SOFTWARE#
Set tags (I/O points), equipment (modules, devices, PLCs. Tool and language for data acquisition, process supervision, industrial automation, storing, reports generation and applications development. Naven is a port of the Apache Maven tool and concept to. Designed by real estate agents for real estate agents.
#RAPIDCLICK GITHUB SOFTWARE#
When a new job is available, SubAssistant automatically sends a text message or email with the job details.īPO Automation Software from the BPO Automation Group.Īutomate the broker price opinion (BPO) process. SubAssistant is an online service substitute teachers use to automatically and continuously check the online SubFinder®, SmartFindExpress® or Aesop® systems. Use RapidClick to save your hand from getting tired whenever you have to do a lot of clicking. RapidClick automatically clicks your mouse up to 20 times per second. It includes integrated compilers, fieldbus configuration, an integrated visualization editor, an optional motion control extension. Hundreds of devices of more than 250 automation manufacturers can be programmed with that tool. The pioneering engineering framework optimizes all planning, machine and process procedures and offers a standardized and integrated operating concept.It seamlessly integrates controllers, distributed I/O, HMI, drives, motion control and motor management into a single engineering.ĬoDeSys - the IEC 61131-3 programming system.CoDeSys is the market leading hardware independent programming system for PLCs and industrial controllers.
#RAPIDCLICK GITHUB FULL#
TIA Portal is the key to unlocking the full potential of Totally Integrated Automation (TIA). This greatly reduces the complexity of the configuration and allows automation systems to be programmed or configured. Programming is done in one of two graphical programming languages - FBD (Function Block Diagram) or LAD (Ladder Diagram).Simulation and online monitoring is available.Suitable for use in small automation applications such as lighting, heating, ventilation, gate control etc.ĬX-One software allows users to build, configure and program a host of devices such as PLCs, HMIs and motion-control systems and networks using just one software package with one installation and license number. LOGO! Soft Comfort is software for programming simple Siemens LOGO! PLCs.

1 note
·
View note
Text
Subfinder – A Subdomain Discovery Tool
Subfinder – A Subdomain Discovery Tool
Source: Hacking News Subfinder – A Subdomain Discovery Tool So what is this subfinder tool all about? Subfinder is a subdomain discovery tool that… Subfinder – A Subdomain Discovery Tool on Latest Hacking News.
View On WordPress
0 notes
Photo

Zin – A Payload Injector For Bugbounties Written In Go #bugbounties #injector #patternmatching #payload #subfinder #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Text
[Media] subtron
subtron Let the subtron do the subdomain enumeration for you with subfinder, assetfinder and with amass at once. https://github.com/d4rkwarrior/subtron #cybersecurity #infosec #bugbounty #pentesting
0 notes
Link
0 notes
Text
SqliSniper - Advanced Time-based Blind SQL Injection Fuzzer For HTTP Headers
SqliSniper is a robust Python tool designed to detect time-based blind SQL injections in HTTP request headers. It enhances the security assessment process by rapidly scanning and identifying potential vulnerabilities using multi-threaded, ensuring speed and efficiency. Unlike other scanners, SqliSniper is designed to eliminates false positives through and send alerts upon detection, with the…

View On WordPress
#KitPloit#Scanning#sql-injection#SqliSniper#Subfinder#Time-Based Blind SQL Injection#Vulnerabilities#Webhook
0 notes