#You have a major reduction in memory retrieval!
Explore tagged Tumblr posts
Text
I keep getting so anxious my mind fogs up and I can't think.
#I can literally watch the fog roll in off the ocean#It's just like whoosh: Status Update! You have attained the Effect Fogged!#You are now unable to comprehend complex concepts!#You have a 10% reduction comprehending basic thoughts!#You have a major reduction in memory retrieval!#Your ability Focus is severely reduced!#The chances of gaining the status Fatigued has greatly increased!
0 notes
Text
From Focus to Creativity: The Cognitive Benefits of Daily Meditation

Meditation has become an increasingly popular practice in today’s fast-paced, often stressful world, and for good reason. While many turn to meditation as a tool for relaxation and emotional balance, its cognitive benefits are equally profound. Regular meditation practice can enhance focus, creativity, memory, emotional regulation, and overall cognitive function. In this exploration, we’ll delve into how daily meditation can transform your brain, sharpen your mental faculties, and foster greater creativity.
1. Improved Focus and Attention
One of the most well-documented cognitive benefits of meditation is its ability to enhance focus and concentration. Meditation practices, especially mindfulness and concentration meditation, help train the brain to stay in the present moment and avoid distractions. This mindfulness approach can lead to a marked improvement in the ability to sustain attention on tasks for extended periods.
For example, a study found that participants who practiced mindfulness meditation showed improved attention and the ability to concentrate, even after a short training period. This means that individuals who engage in daily meditation may find it easier to focus on work, study, and daily tasks, reducing mental distractions and increasing productivity.
2. Enhanced Memory and Learning
Meditation not only improves focus but also boosts memory, particularly working memory. Working memory is essential for tasks like problem-solving, reasoning, and decision-making, as it allows you to hold and manipulate information. Studies have shown that meditation, particularly mindfulness meditation, can enhance the function of the hippocampus, a brain region associated with memory and learning.
Regular meditation can increase the size and connectivity of the hippocampus, improving the brain’s capacity to store and retrieve information. As a result, meditators often experience better memory retention and quicker learning abilities. This benefit is especially helpful for students, professionals, or anyone who needs to process and retain new information efficiently.
3. Stimulated Creativity
One of the most exciting cognitive benefits of meditation is its ability to stimulate creativity. Creativity often arises when the mind is in a relaxed, open state, free from mental clutter and distractions. Meditation encourages such a state by fostering mental clarity and calmness. With daily practice, meditation enhances the brain's ability to think flexibly, connect disparate ideas, and solve problems in innovative ways.
Research has found that mindfulness meditation boosts divergent thinking, which is a key component of creative thought. Divergent thinking involves generating many possible solutions to a problem, which is often the foundation of creative thinking. By quieting the mind and allowing it to remain open and present, meditation helps unlock new ideas and creative solutions.
4. Emotional Regulation and Resilience
Meditation significantly improves emotional regulation, a critical aspect of cognitive function. By practicing mindfulness, meditators become more aware of their emotional states without becoming overwhelmed by them. This increased emotional awareness allows individuals to respond thoughtfully rather than react impulsively to stressors, leading to better decision-making and clearer thinking.
Daily meditation can reduce the reactivity of the amygdala, the brain's center for emotional responses, making it easier to manage feelings of anxiety, fear, and frustration. This ability to maintain emotional balance enhances cognitive performance, particularly in high-pressure situations where clear thinking is crucial.
5. Stress Reduction and Mental Clarity
Stress is a major cognitive barrier, negatively impacting memory, decision-making, and focus. Meditation has been shown to reduce stress by lowering cortisol levels (the stress hormone) and promoting relaxation. This reduction in stress leads to improved cognitive performance, as the brain is no longer bogged down by the mental clutter that stress creates.
Moreover, daily meditation helps clear mental fog and enhances mental clarity, enabling better focus, problem-solving, and critical thinking. With less cognitive energy spent on managing stress, individuals are able to direct more of their mental resources toward creative thinking and complex tasks.
6. Neuroplasticity and Brain Health
Neuroplasticity refers to the brain’s ability to reorganize itself and form new neural connections. Meditation has been found to enhance neuroplasticity, which is crucial for maintaining cognitive function as we age. Regular meditation leads to structural changes in the brain, particularly in areas related to memory, emotional regulation, and decision-making.
For instance, research has shown that long-term meditation increases the volume of gray matter in the prefrontal cortex, which is involved in executive functions like decision-making and problem-solving. These changes promote a healthier, more adaptable brain that can better cope with cognitive challenges.
7. Cognitive Flexibility and Adaptability
Cognitive flexibility—the ability to switch between tasks and adjust thinking based on new information—is another benefit of daily meditation. Meditation encourages a more adaptable and open-minded approach to challenges, which is critical for effective problem-solving and decision-making.
By fostering greater awareness and mindfulness, meditation allows the brain to remain flexible in the face of uncertainty and change. This flexibility enhances creativity and the ability to find novel solutions to complex problems, which is valuable both in personal and professional contexts.
8. Integrating Meditation into Your Routine
To experience the cognitive benefits of meditation, it’s important to make it a regular part of your routine. If you're new to meditation, guided meditation sessions can be a great way to start. These sessions provide structure and can help you learn different meditation techniques that suit your personal goals, whether that's reducing stress, enhancing focus, or boosting creativity.
You might also consider joining online meditation classes for a more comprehensive understanding of meditation practices. These classes can offer deeper insights into how meditation affects the brain and provide guidance on how to meditate effectively.
For those seeking a more personalized experience, working with a personal meditation trainer or enrolling in meditation coaching at home can help you develop a practice tailored to your specific needs. This individualized approach ensures that you maximize the cognitive benefits of meditation.
Conclusion
Daily meditation is not just a tool for relaxation—it’s a powerful cognitive enhancer. From improving focus and memory to stimulating creativity and enhancing emotional regulation, the cognitive benefits of meditation are vast and well-documented. Whether you’re looking to boost productivity at work, enhance creativity, or reduce stress, meditation provides the mental clarity and resilience needed to thrive in today's world. By incorporating meditation into your daily routine, you can unlock a sharper, more creative mind that’s better equipped to tackle challenges and embrace new opportunities.
#Benefits of Meditation#Online Meditation Classes#Guided Meditation Sessions#Personal Meditation Trainer#Meditation Coaching at Home#Meditation Classes in Delhi
1 note
·
View note
Text
Unlocking the Power of Neuro-Sonic Harmonics for Better Memory and Focus

Imagine a tool that helps you sharpen your memory, boost concentration, and achieve a deep mental focus—all by tapping into the power of sound. This might sound like science fiction, but it’s actually the exciting science of Neuro-Sonic Harmonics. This approach blends neuroscience with sound technology to help optimize the brain’s potential, promoting cognitive wellness and emotional balance.
Let’s dive into how Neuro-Sonic Harmonics works, why it’s gaining traction, and how it can help improve memory and concentration naturally.
What is Neuro-Sonic Harmonics?
In simple terms, Neuro-Sonic Harmonics is a sound-based technology designed to enhance brain function by using specific sound frequencies. Our brains are highly responsive to sound, and certain frequencies can trigger specific neural responses. Brainwave frequencies like delta, theta, alpha, beta, and gamma each have unique effects on mood, focus, and relaxation. By harmonizing these frequencies through Neuro-Sonic Harmonics, it’s possible to enter mental states that support memory retention and improved focus.
How Does Neuro-Sonic Harmonics Work?
The process involves carefully calibrated sounds—often through binaural beats or isochronic tones. When these sounds reach the ears, they create a response in the brain that synchronizes its electrical activity with the audio frequencies. This synchronization can guide the brain toward states that naturally foster relaxation or heightened mental clarity, making it easier to retain information and stay attentive.
Benefits of Neuro-Sonic Harmonics for Memory and Concentration
Enhanced Memory RetentionOne of the biggest challenges we face is remembering details, whether it’s study material, meeting points, or day-to-day tasks. Neuro-Sonic Harmonics can help by promoting the theta brainwave state, often linked to memory encoding. By regularly listening to these harmonic sounds, you can create a supportive environment for your brain to encode and retrieve memories more effectively.
Increased Concentration and FocusStruggling to stay focused? Neuro-Sonic Harmonics might be the answer. Beta waves are associated with alertness and concentration. By using sound patterns that encourage beta wave activity, you can enter a mental state that supports sharp focus and increased productivity.
Stress ReductionStress is a major factor in poor memory and focus. Neuro-Sonic Harmonics offers a non-invasive way to calm the mind, easing it into alpha and theta wave states that are ideal for relaxation. The reduction in stress allows the brain to concentrate on tasks with clarity and efficiency.
Better Sleep QualityDelta waves, associated with deep sleep, can be encouraged through Neuro-Sonic Harmonics. Quality sleep is directly linked to memory and focus, as it’s when the brain processes and stores information. By improving sleep quality, Neuro-Sonic Harmonics can indirectly boost cognitive function during waking hours.
How to Get Started with Neuro-Sonic Harmonics
If you’re interested in trying Neuro-Sonic Harmonics, you’ll find a variety of options available—from smartphone apps to specialized sound systems. Here’s a quick guide to getting started:
1. Find the Right Tool
There are numerous apps and programs designed to deliver harmonic sounds. Look for ones that are specifically labeled for memory enhancement or focus improvement. Brain.fm and Hemi-Sync are popular choices that utilize binaural beats and isochronic tones.
2. Use High-Quality Headphones
The best results come when you use good-quality headphones, as these frequencies need to be distinct in each ear. This setup allows the brain to respond effectively to the binaural audio.
3. Make It Part of Your Routine
Consistency is key. Try to incorporate Neuro-Sonic Harmonics into your daily routine for 15-30 minutes, preferably during times when you need to concentrate or relax.
4. Pair It with Meditation
Combining Neuro-Sonic Harmonics with mindfulness meditation can amplify its effects. Meditation can improve your overall mental clarity, making the benefits of Neuro-Sonic Harmonics even more noticeable.
These search terms can provide valuable insights and techniques that complement Neuro-Sonic Harmonics and can take your learning journey to the next level.
Who Should Consider Neuro-Sonic Harmonics?
Neuro-Sonic Harmonics can benefit nearly anyone looking to enhance their mental performance. However, it’s particularly popular among students, professionals, and even older adults who want to keep their minds sharp.
Ideal Candidates
Students: Retain study material more effectively and reduce test anxiety.
Working Professionals: Improve productivity and mental stamina for demanding tasks.
Aging Adults: Support cognitive function as part of a healthy brain-aging strategy.
Situations Where Neuro-Sonic Harmonics Is Helpful
During Study or Work Sessions: Play these sounds while reading, writing, or solving problems to stay focused.
Before Sleep: Listening to delta frequency sounds can help you wind down, ensuring you get a deep, restful sleep.
As a Midday Boost: A short session with beta wave sounds can rejuvenate your mind, making it easier to get through the afternoon slump.
Frequently Asked Questions
1. Are there any side effects of using Neuro-Sonic Harmonics?
Generally, Neuro-Sonic Harmonics is considered safe. However, if you have epilepsy or similar neurological conditions, it’s best to consult a healthcare professional before using sound-based therapies.
2. How long does it take to see results?
Results vary by individual. Many people notice improvements in focus within the first week, while memory benefits may take a few weeks of consistent use.
3. Do I need special equipment?
No special equipment is needed beyond a good pair of headphones. If you want to take it up a notch, you can invest in dedicated sound therapy devices or high-fidelity speakers designed for sound healing.
Final Thoughts on Neuro-Sonic Harmonics: Memory and Concentration
With all the demands of daily life, it’s easy for memory and focus to take a hit. Neuro-Sonic Harmonics offers a promising, natural solution for enhancing your mental abilities without relying on stimulants or pharmaceuticals. Its effects on brainwave frequencies make it a versatile tool for anyone looking to optimize mental performance. So why not give it a try? By incorporating sound therapy into your routine, you may discover a new level of mental clarity, memory retention, and focus you never knew was possible.
0 notes
Text
Week 6: The history of Biodiversity
“There is no peculiar merit in ancient things, but there is merit in integrity, and integrity entails the keeping together of the parts of any whole, and if these parts are scattered throughout time, then the maintenance of integrity entails a knowledge, a memory, of ancient things. …. To think, feel or act as though the past is done with, is equivalent to believing that a railway station through which our train has just passed, only existed for as long as our train was in it.” - Edward Hyams, Chapter 7, The Gifts of Interpretation
It took me a while to form my interpretation of this quote. Hyams uses the word integrity quite a bit in it, which got me thinking about how he was using and why that word over any others. In its modern connotation, ‘integrity’ typically refers to someone or somethings reliability or the quality of their morality and nature. The word came into the English language via the Old French ‘integrité’ then meaning innocence, chastity, or purity. ‘Integrité’ evolved out of the Latin ‘integritas’ whose root is ‘integer’ meaning soundness, wholeness, or completeness. Reading the quote again but with the connotation of ‘a whole’ in mind, Hyam began to make a lot more sense to me. “There is no peculiar merit in ancient things, but there is merit in [completeness], and [completion] entails the keeping together of the parts of any whole , and if these parts are scattered throughout time, then the maintenance of [a whole] entails a knowledge, a memory, of ancient things [...]”. What I think Hyam is getting at is that history doesn’t make sense without context, understanding why certain actions were taken or why certain events occurred. Its often easy to overlook historical context in favour of personal belief, but this often leads to dangerous rhetoric. Countless times we have seen history distorted in order to target ethnic, religious, linguistic, and cultural minorities.

Here’s an example of how languages evolve and change over time using the pronoun “I”. (Source: https://www.reddit.com/r/europe/comments/dj7rb1/evolution_of_the_pronoun_i_in_indoeuropean/)
What stood out to me in this week’s unit were the questions “Who/what benefits from this story and how might that impact them/others in the future?” and “how a community might be enhanced, it is often through the recognition of collective memories, stories” (Hooykaas 2021). This week I want to talk about the history of biodiversity (my uni major).
The concept of biodiversity has existed in some form for as long as the human conscious has. Aristotle made note of the differences between animals; and in its most basic sense, that is what biodiversity is, differences between organisms and their variety (Mayr, 1998). Biodiversity, the word itself, has a much shorter history, but why? It was coined in 1985 by Walter G. Rosen for the creation of the National Forum on BioDiversity. The forum was made to discuss the increasing demands of the human species on economic development and the potential ramifications it might have on the natural environment. Edward Wilson, an American biologist, summarized the forum as “BioDiversity creates a systematic framework for analyzing the problem and searching for possible solutions” (Wilson, 1988). This describes the political, economic, and scientific climate during the time of ‘biodiversity’s creation. The public and scientific community were becoming increasingly aware of the negative impacts of human development, of air pollution, deforestation, habitat fragmentation, water pollution, etc… on the environment and the implied repercussions on the economy (Wilson, 1988).

Image illustrates some of the main threats causing global biodiversity decline. (Source: https://www.visualcapitalist.com/biggest-threats-to-earths-biodiversity/)
Through out the century, scientists were noticing that when certain species were removed from their ecosystems trophic downgrading would occur, and, notably, the increasing the rate of extinction worldwide (Wilson, 1992; Myers, 1979). In 1979, Norman Myers, an English ecologist, published The Sinking Ark: A New Look at the Problem of Disappearing Species. In it, he discusses extinction but draws attention to the unexpectedly fast rate at which species were going extinct in the modern day; far greater than one would expect over the course of the process of evolution. However, unlike the Cretaceous or any mass extinctions before, this one was not caused by natural disasters but by a single species; the cause was and is anthropogenic (Myers, 1979). A warning call. Wilson’s Biodiversity, a series of articles written by leading authorities in biological and environmental disciplines, compiled from the BioDiversity Forum, further outlined the importance of diversity of species and the ecosystems that support them as well as the very species that threatens their stability (Wilson, 1986).

“The Sinking Ark” by Norma Myers (source: https://www.goodreads.com/book/show/2381140.The_Sinking_Ark)
By the late 1980s, biodiversity, used interchangeably with biological diversity, had entered the mainstream of scientific literature and public culture. Yet the understanding of what biodiversity is and what it means was vague at best and measuring biodiversity was controversial and can be a challenging task (Franco, 2013). With its growing popularity and the urgency felt by the scientific community, in 1992, the United Nation’s Environment Program organized and launched the Convention on Biological Diversity (CBD) to clarify what was meant by ‘biodiversity’. The broad definition of “Biological diversity means the variability among living organisms from all sources including, inter alia, terrestrial, marine and other aquatic ecosystems and the ecological complexes of which they are part; this includes diversity within species, between species and of ecosystems” was given (CBD, 1992).
So “Who/what benefits from this story and how might that impact them/others in the future?” and “how a community might be enhanced, it is often through the recognition of collective memories, stories” (Hooykaas 2021). Knowing this story, we understand that ‘biodiversity’ is a word made for a purpose, as a defence of conservation biology. In this sense, the two are inexorably linked. Biological diversity had no need for a name before the 20th century because it was a constant of life. As a community we are enhanced in our collective appreciation of it and its causes. Human development caused, and is causing, a massive reduction in native species diversities, which in turn reduces genetic diversity, and on a global scale, human development has caused the largest and fastest mass extinction on record (Wilson, 1988).
What do you think of the story of biodiversity? Although not a physical artifact, certainly an important part of history. Can you think of any other historically significant words?
References:
Convention on Biological Diversity Article 2. Use of Terms. (CBD). (2006, November 2). Retrieved April 10, 2020, from: https://www.cbd.int/convention/articles/?a=cbd-02
Hooykaas, A. (2021). Unit 6: Nature Interpretation Through History. Lecture Notes Retrieved, February 24, 2021 from https://courselink.uoguelph.ca/d2l/le/content/666945/viewContent/2592718/View
Mayr, E. W. (1998). The Development of Biological Thinking.
Myers, N. The Sinking Ark: A New Look at the Problem of Disappearing Species. Oxford, United Kingdom: Pergamon Press, 1979.
Wilson, E. O. Biodiversity. Washington, DC: National Academy of Sciences Press/Smithsonian Institution,1988.
2 notes
·
View notes
Text
Zack’s Stats FFVII (Classic)
Points: LV Zack EXP 1 - 10 - 20 0 30 119770 40 225940 50 363825 60 491470 70 537068 80 1310000 90 1930050 99 2500000
HP Range (Bottom to Max) 679-8502
MP Range (Bottom to Max) 150-980
Primary Stats: (Bottom to Max) Strength: 27-80 (Adjusted Range 34-100) Dexterity: 20-70 Vitality: 30-75 (Adjusted Range 30-96) Magic: 35-100 Spirit: 30-98 Luck: 20-31
Zack, initially known as Ex-SOLDIER (though his name is revealed before being added to the party gameshark and glitch manipulation can be used to get the designation with its original code). He wields broadswords (the same as Cloud) and can use any of these weapons that Cloud doesn’t have equipped, except for Ultimate Weapon. In this game Zack fill a Red Mage role, and uniquely his derived stats manipulate based on his row placement (with an increased offensive power, both spells and attacks, while in back row, but increased defensive powers in front row). This array usually encourages Zack to remain in the back row, and often players move him to the front row when using him to cast healing magic or use items.
Notably, Zack’s Limit Breaks are all alluded to other characters in his backstory. Chain Slash is what he starts with, and relies on his Strength stat, meaning that it ultimately scales to be better than his other Limit Rush Assault, which scales off of Vitality. Zack’s Limits are earned by flashbacks to the events of his and Cloud’s life prior to the events of the game, usually earned by playing as either Cloud or Zack, and seeing another character doing something. Zack’s final Limit, Apocalypse, is earned by defeating the optional boss Simulation Genesis. Notable is that Zack’s Limits seem to have more to do with the character his memory discusses, including Healing Wave, which functions the same as Aerith’s Limit of the same name.
When brought into the party Zack’s level is the party’s average +3, or 1 level higher than the highest-level party member. If either of these numbers are sub-20, then Zack defaults to level 20.
Battle
Zack is a character who is best moved between the rows depending on what he is specifically meant to do. Notably, if he never completes the questline to repair his degeneration, Zack is best set to use his melee attacks from back row, as the normal reductions do not apply to his attacks. Zack’s limit breaks match his utility, being able to do simple things such as deal damage, to heal, to increasing the luck of the entire party, though they’re often tied to scripted events and may be considered underwhelming given his stat association, in many cases.
Stats
Zack’s stats are notably reflective of his storyline, with weak Strength and Vitality, the latter of which is the lowest in the party, favoring his casting, and having the highest, though slowest-growing, Luck stat as well. Zack’s ATB also fills quickly, allowing him to cast repeatedly and often, making him a good support character. If the player decides to complete a side quest after Cloud recovers from his second bout of Mako Poisoning, Zack’s physical state is restored fully, and his Strength and Vitality become adjusted accordingly, giving him extremely well-rounded stats, like Cloud, but renders him unable to upgrade Buster Sword and make it his strongest weapon (which in terms of performance would make Zack a stronger character). Doing one quest or the other closes out the corresponding questline.
Equipment
Zack’s equipment is the same as Cloud’s in-game, though he notably cannot use Ultima Weapon, or any weapon that Cloud has equipped. Notably, thanks to his unique ability, Zack is able to slot additional Materia based on the total slots of his equipment, giving him more natural versatility and use as a means of leveling up many materia at a time. Because of this ability, many players will favor Apocalypse as Zack’s lategame weapon, and essentially his endgame until Ragnarok is freed up by Cloud obtaining Ultima Weapon, because of the higher Spirit stat. Notably, other players may prefer to have Zack wield Heaven’s Cloud as it can grant him an additional two materia slots. Zack’s own strongest weapon in the game, though, is the Buster Sword that is available to Cloud at the start. If the player listens to Cloud’s internal dialogue in the first battle, and refrains from making attacks with the Buster Sword whatsoever, essentially requiring him to repeatedly defend, use magic, or items throughout the first reactor mission, until Zack is able to give him his second weapon at Seventh Heaven, then this quest will later become available to the player. So long as only Zack makes attacks with the Buster Sword throughout the game, until the quest that allows Zack to improve the Buster Sword is started, at which point it can no longer be equipped to Cloud, and at the end has its stats improved in such a way that Zack’s damage output becomes similar to Cloud’s with the Ultimate Weapon equipped. A notable ability attached to the Buster Sword when this occurs is that it also deals more damage based on the percent of Zack’s remaining MP, indicating that the game expects Zack’s playstyle to change along with the Buster Sword to essentially being a second Cloud. Due to similar stats, and the suppression of his ability that allows his melee attacks to deal the same in the back row, many often allow Zack to still act as a caster or item support, but others also enjoy the option of having two high-damage output characters.
Materia
Zack joins the party with Fire, Blizzard, and HP Up equipped. Due to his high magic stat, Zack often spend the majority of the game casting in the back row, switching to front row when not attacking, because his dodge chance improves dramatically. Additionally, thanks to Zack being the only character with “personal slots” for his materia that allows him to slot more with more slot-rich equipment, Zack is also suited for leveling up a player’s materia in bulk, allowing players to quickly develop expensive materia simultaneously, or quickly working up a full set of casting materia for their other characters.
Quests
Prior to his introduction as a party member, Zack will send Cloud on a number of quests that he calls “Merc Contracts” though they’re often relay and running quests. These are optional in nature, but serve as a quick way to earn a decent amount of gil in the early game.
Return of the SOLDIER Following Cloud’s recovery from Mako Poisoning, in Mideel, if Zack is in the party while you talk to either the Weapon Shop Clerk, or the nurse at the clinic, Zack gets a corresponding recommendation to see about touching up his Buster Sword from The Monk Smith Bhest outside of Banora (the original forger of the Buster Sword) or the Dr. Rhiner in Sector 4 of Midgar about the condition of his arm.
If Zack receives the quest to see Bhest, he is admonished for allowing such a fine work of his to become so worn with lack of care that it could barely hold an edge. For a price (calculated with a formula that’s determined by how many times Zack has used it to attack, or cast elemental spells while it was equipped) he will repair it, while also sending Zack to retrieve a number of difficult to get materials, one of which is dropped following a boss fight. After these are completed, Bhest returns the weapon to Zack, telling him that no matter how roughly he handles it, the material will allow the Buster Sword to always remain in perfect condition, and he was even able to install some additional slots to it. (If Zack attempts to see Bhest without meeting the conditions for the quest, or after having started the Rhiner quest, he will be scolded and told that the weapon is as good as a doorstop the way he’s handled it.)
If Zack recieves the quest to see Rhiner, he will find Rhiner in a free clinic in Sector 4. Rhiner will inspect Zack and determine that he’s experiencing some sort of accelerated version of the typical degeneration caused by make treatments. This sends Zack to Nibelheim to collect notes necessary for Rhiner to find out what was different about Zack’s treatment. Upon his return, he is then sent out to seek some unique components and materials from Hojo’s lab, requiring them to again sneak into the Shinra headquarters, or having stolen them successfully from Hojo during his boss fight (can only be stolen in first and third phases, with the chance of steal being halved in the third phase). Upon his return, Zack is treated for two days, eventually coming out with a repaired arm and physical health. Doing this permanently modifies his stats, but prevents him from being able to enhance his Buster Sword (without cheating and hacking it in with a gameshark).
1 note
·
View note
Text
Printer Repair in Dubai
Therefore, spilling a drink in your laptop can lead to internal damage. Regrettably there's very little hope in the event the computer is completely drenched then although Just a little splash of fluid remains manageable. Therefore, water damage can cause data loss.Data recovering services can help you to acquire your data back from devices like hard drive, desktop computer, notebook, SSD, RAID, SCSI, SAS, USB, along with memory cards, etc..4. Power Blackout Virus & Malware Now, what should the device itself is stolen?
You will eliminate the system as well as your information. Device theft is common. From time to time, you can not avoid it. Nonetheless, you have to be certain even if the unit is gone, you're still able to recover your data. Modern technology has given us that choice. Using which we can stop the information from falling into wrong hands as well as retrieving it.Too much information stored onto a hard drive may also cause it to crash. We don't take good care of the system.
Overheating dropping it may also be accountable for a busted hard disk. Whether the hard disk of your computer is damaged, you are able to start looking to understand.Slowing from the system and overheating.Severe hard disk damage can cause the system to reduce data files. Hard drives are the most vulnerable portion of a notebook computer or a pc. Printer Repair in Dubai may be damaged as a result of production flaws, improper handling, or mechanical troubles.Recovering deleted information can be as straightforward as going into the recycle bin and then retrieving it from that point. But, that is not the situation.
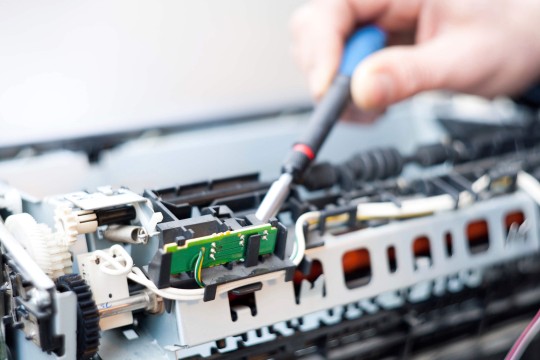
You may use applications for creating routine backups of the body.Thus, no matter what device you use for system backups be certain it can be repaired.These strikes can differ in their strength but almost all of them cause harm to the data stored in the computer system. Attacks can cause damage that is greater . These attacks are more vicious when they are targeted towards businesses. Device TheftSo, be cautious with your computers, laptops and other devices in order to not cause any hard drive damage.6 Reasons Why Data Could Be MissingNot being able to open files and folders or folders being corrupt.Governmental and corporate offices require advanced and sophisticated measures to guard their data.
But, don't just set up an antivirus and forget about it. Update it and also run scans to be sure.The system takes an excessive amount of time to boot up.Reasons you should know so which you can take precautions and won't end up losing your precious data. However, in those instances where precaution is not enough professional help is required.Regular hard drive crash. If you're in the center of important work and the pc abruptly shuts down then it ends in data loss. Butnot information reduction power fluctuation or outage can damage your computer hardware. The only way it is possible to stop data loss is by setting up an automatic system backup.You are able to avoid these attacks by installing fantastic quality antivirus software and firewall protection on your PC. This makes it more difficult for malware and viruses to permeate the body.The internet is a dangerous place. The disadvantages are only too many although it has its benefits.
This is not properly understood by The majority of the average folks and fall prey to virus strikes. Malware and viruses attack the usable applications and operating system of the system. Call up your friends and ask them if they recommend anyone. Or, you may use the net. Open your browser and search.And, just like this, you will see a listing of top service centers you can pick from. Choose a few options and compare them. Remember to look at their reviews. There you may see what their previous customers have to say about their services. Water Damage Continuous freezing of the machine.Therefore, in case you've spill water on your notebook then flip it off and quickly use a dry tissue to absorb as much moisture as you can. In Dubai, call technicians in Data Recovery Service providers Following that to analyze the gadget.This one is not as likely but has happened to a couple folks.
We all know not to bring water or any other liquids close to our computers, laptops, hard drives, etc.. But, accidents do occur. Most of the devices mentioned don't have protection from damage.We're constantly cautioned about the negative effects of incorrect shut from a computer. In case the system does shut down it's possible to face difficulties. This can happen because of electricity blackouts.Data recovery costs in Dubai are also quite reasonably priced. You don't have to worry overly much about the ceremony cost.We hope that the information given in this article helped you to know what variables can make you lose data and approaches to take precautions.
All you have to do is find the top-notched service center for your needs and getting your data recovered. Human Error Noises coming out of the computer.You're able to find that assistance at any renowned data recovery services based here in Dubai, UAE. They can assist that you are having. And if you are wondering about the expense of their help then relax, data recovery fees from Dubai will fit within your budget.As already spoken several issues can cause data loss. We will advise you about what they're in this area. You can make the decision in the event that you can manage it yourself or whether you require assistance.Service Provided by Data Recovery Services Dubai Data loss can be quite upsetting. Losing information causes worry and anxiety. Personal and professional information are all of importance.
Everyone tries to keep it as safe as possible. However, we cannot control device error.The majority of the data recovery service providers in Dubai have benefits like On-time shipping, Pickup and delivery support, 24*7 customer service, Expert technicians, Experienced information, Free diagnostic service along with Quick solutions.Machines do not often make mistakes. However, that cannot be said concerning us people. That is human error is the most common reason for data loss. We delete files or restarting the parts we did not mean to. And, we can do all of it without developing a backup that is proper.Visit their sites to get further understanding of the kind of work they perform. You can also compare their listed price . After going through all this information select an Information Recovery Center and phone them.Keeping these motives aside, there are other things such as fire harm or a fall from a excellent height that can lead to precisely exactly the identical thing occurring.
In cases, like those, we can not mend the device but that's no reason for your data. You can reach out for almost any information reclaiming services in Dubai to restore your missing data.Many folks do not even realise their mistakes until they are desperately searching for that file. That is exactly why it is always suggested to create a backup.Official information reduction can cause as much damage that occasionally it is irreversible. Official data include company history, information about the customers, project info, private and financial info, etc.. Thus, you can imagine how the reduction of these information can be for an enterprise.Once the data stored in a variety of devices like a computer, hard disk, USB, etc have inadvertently deleted or if it will become corrupted then qualifies as data loss. In terms of the origin, it can happen for a whole good deal of factors.Losing private data leads to a privacy violation. And, if it is corporate or governmental data which is missing then it means reducing money and time. That is where Data Recovery Services Dubai comes into play.What does data reduction mean and why does it happen?
0 notes
Link
Using Cannabis to Treat the Effects of Trauma
Back in 2016 a Canada based medical marijuana firm opened an office in Edmonton, Alberta for treating Post Traumatic Stress Disorder (PTSD) among war veterans. The company called Marijuana is owned and managed by Fabian Henry who has been using cannabis for alleviating the symptoms of PTSD since his combat duty in Afghanistan. According to him marijuana is way more effective than traditional medicines and can go a long way in helping patients battling with PTSD.
What is PTSD?
PTSD usually develops after a traumatic event in your life such as being in the war zone or experiencing a life threatening situation such as an assault or a natural calamity. PTSD can have a lasting effect on the human mind and people often are known to experience difficulty while sleeping and a host of issues which can interfere with normal functioning of life. Usually, people who experience the symptoms for a long stretch of time are more prone to develop PTSD. Although traditional medicines and psychotherapy have been so far used for the treatment of PTSD, the legalization of cannabis has opened the path for many new researches on the use of marijuana for trauma victims. Cannabis is slowly coming up as a rather effective alternative to prescription drugs which generally come with many negative side effects.
Marijuana for trauma victims
CBD and THC the two most important cannabinoids can be of great help in reducing the symptoms of PTSD as they enhance our endocannabinoid system’s intervention in important body functions such as the consolidation of memory and retrieval. Marijuana can activate the CB1 and CB2 receptors thereby prompting the endocannabinoid system of the body to create neurotransmitters which aid the promotion of pleasure and happiness.
The cannabinoids have a critical role to play in thwarting the retrieval of the underlying trauma and is also known to keep away the memories of the trauma and the associated nightmares. The sense of euphoria produced by marijuana also helps the trauma victims to attain a state of emotional wellbeing. This is precisely why cannabis has come up as a popular medication for treating PTSD patients the majority of whom are combat veterans. “There’s a consensus among clinicians that existing pharmaceutical treatments such as antidepressants simply do not work.
In fact, we know very well that people with PTSD who use marijuana — a potent cannabinoid — often experience more relief from their symptoms than they do from antidepressants and other psychiatric medications. Clearly, there’s a very urgent need to develop novel evidence-based treatments for PTSD.” says Dr. Alexander Neumeister who has done substantial work in this field.
Cannabis for controlling the after-effects of PTSD
Some of the most common symptoms of PTSD are stress and disturbing nightmares. Particular strains of cannabis can help in reducing the REM sleep which is the time when we have vivid dreams. This is why cannabis can help you get rid of those recurring nightmares which are often associated with PTSD. Moreover, PTSD can also lead to intense stress which often places the individual in a constant state of tension. A study was conducted among 47 trauma victims all of whom were under prescription drugs and also undergoing psychotherapy. Following the cannabis treatment, a whopping 72% of the patients reported a marked reduction in nightmares and anxiety. Many patients also noted a remarkable improvement in the quality of sleep along with a reduction of daytime flashbacks and night sweats. Researches have shown that the cannabinoids present in marijuana can greatly surpass the role of antidepressants in the treatment of PTSD.
CBD for PTSD
Although both THC and CBD can be of help for reducing the symptoms in trauma victims, many patients are apprehensive about the intake of THC since it can produce strong psychoactive effects. CBD, on the other hand, being completely non-psychoactive can promote a deep sense of relaxation and provide lasting relief from the symptoms of PTSD. Ideally, patients of PTSD need to go for CBD high strains for daytime use and stick to THC heavy strains for a night of uninterrupted sleep.
Cannabis strains for patients of PTSD
Blue Dream- This sativa dominant strain with a soothing fruity aroma is known to promote a sense of full body relaxation. However, this strain comes with a rather high THC content (17% -24%) and a negligible level of CBD (0.1%- 0.2%). Blue Dream can be an ideal companion for a good night’s sleep in patients of PTSD.
OG Kush- OG Kush, one of the most powerful kush strains is an indica dominant strain that produces intense euphoric effects and is known to work as a sedative. Ideal for night time smoking, this strain calms your body and mind and ensures a relaxing ‘high’ time.
Pineapple Express– This super popular weed strain is known for its smooth and well-balanced effects. Patients of PTSD can greatly benefit from this strain since it promotes a sense of clearheadedness accompanied by a sense of wellbeing. Trauma victims who also suffer from social anxiety should definitely opt for this strain since it can potentially allay the fears and considerably reduce anxiety making you highly functional under any circumstances. The THC content of Pineapple Express is around 20% while the CBD content is 0.1%.
Master Kush – Yet another kush strain, this one should be avoided by the novice users because of its extreme potency. PTSD patients who suffer from insomnia can always rely on the Master Kush buds for a peaceful night of sleep. It also promotes a euphoric sensation before putting you off to sleep.
Cannatonic – This cannabis strain which comes with a high level of CBD will hardly produce any psychoactive effects but promote a deep sense of relaxation and a very mild high.
The legalization of medical marijuana has prompted doctors, and scientists to continue with additional researches for discovering the benefits of marijuana for victims of trauma. However, it is always suggested that you talk to your physician before trying out any of the above mentioned strains. Once you have made up your mind just walk into your nearest cannabis dispensary and place an order.
https://greenserenity.co/benefits-of-cannabis-for-trauma-victims/
0 notes
Text
How CBD Oil Helps with PTSD

Post-traumatic stress disorder or PTSD, most commonly seen in war veterans nowadays. It includes uncontrolled and unbearable flashback of previous traumatic experiences which ultimately results in a scary level of anxiety and pain. Today many recent researches and studies conducted by scientific community shows that Cannabidiols or CBD found on the cannabis plant are highly effective in PTSD treatment. CBD are effective at lessening the emotional impact of traumatic events and can help patients experience less anxiety and fear which gives them relief from pain and improves their sleep. Understanding PTSD Before talking about PTSD treatment, let’s try to understand the causes and symptoms of PTSD. According to American Psychiatric Association Post-traumatic stress disorder (PTSD) is a psychiatric disorder that can occur in people who have experienced or witnessed a traumatic event such as a natural disaster, a serious accident, a terrorist act, war/combat, rape or other violent personal assaults. Though PTSD is a common threat to war veterans, it can effect common people of any ethnicity, nationality, culture, or age. In PTSD diagnosis direct or indirect exposure to an upsetting traumatic event is observed in the first hand. Numerous methods have been used to treat the symptoms of PTSD throughout the past years. psychotherapy and pharmaceutical medication are traditional methods for PTSD treatment. Today CBD as a treatment of PTSD is emerging successfully. Symptoms and Diagnosis of PTSD The inherent characteristics of any psychiatric disorders makes them hard to diagnose; according to professionals a patient diagnosed with PTSD if he/she has experienced all of the following symptoms for at least a month. Re-experiencing past traumatic symptoms: Flashbacks, bad dreams, frightening thoughts or anything that may cause problems in a person’s everyday routine. Words, objects, or situations can trigger re-experiencing symptoms. Avoidance symptom: Avoiding thoughts, feelings, places, events or objects that reminds a person of a traumatic event can trigger an avoidance symptom. These symptoms cause a person to change his or her personal routine, such as avoiding cars after a car accident.Over excitement and reactivity symptoms: Reactivity simply refers to reactions such as “lashing out” in relation to irritability and being triggered by seemingly nothing. Arousal symptoms, on the other hand, are constant. This would be referring to symptoms such as difficulties concentrating or insomnia. These symptoms cause stress and anger, and may cause difficulty eating, sleeping or concentrating. These symptoms are usually related to the anxiety, insomnia and outbursts connected to PTSD.Cognition and mood symptoms: These symptoms begin or worsen after a traumatic experience, but are not due to any injury sustained in the event. The symptoms include loss of enjoyment, distorted feelings, negative and pessimistic thoughts, and trouble recalling significant features of the event. Side effects and problems of traditional medication: Side-effects: United States Food and Drug Administration (FDA) has approved sertraline (Zoloft) and paroxetine (Paxil), both antidepressants, for use as post-traumatic stress disorder medication. The side effects of these drugs include: HeadacheNauseaSleeplessness or drowsinessAgitation or a jittery feelingProblems having or enjoying sex Physicians also prescribes medications like Zoloft and Paxil genre medications. According the US National Institute of Health (NIH), benzodiazepines are also used to give relaxation and sleep to patients. The side effects of these 3 types of drugs include, problems with memory and the risk of drug dependency. Antipsychotics may be prescribed. They are typically given to patients with coexisting conditions, such as schizophrenia. Some side effects of antipsychotics are weight gain and a higher risk of heart disease and diabetes. Additionally, other antidepressants may be used as PTSD drugs. Possible options are fluoxetine (Prozac) and citalopram (Celexa). In addition to the side effects already listed, the following side effects may occur: Dry mouthIncreased appetiteBlurred visionDizziness PTSD Drug Addiction, Dependence and Withdrawal illness: The Journal of the American Academy of Family Physicians warns about the abuse risk of benzodiazepines. When taken chronically, they can be addictive but they are relatively safe when taken in moderation. If you have a history of substance abuse, benzodiazepines should not be used. It is important that you not cease taking your medication as this can cause withdrawal effects and lead to recurrence of the symptoms of your illness. Medication Overdose: The New York Times of February 14,2011 carries the disturbing news of an alarming increase in deaths from accidental overdose among our active duty military personnel and our war veterans. The usual scenario is a diagnosis of PTSD unsuccessfully treated with a wide array of psychotropic drugs, which in their aggregate, wind up killing the patient-- often at a very young age. Autopsy reveals significant blood levels of prescribed medication reflecting the heavy drug cocktail and no other apparent cause of death. PTSD are often prescribed a combination of psychotropics that may include--one antidepressant, one antipsychotic, one antianxiety, one sleep, and one pain medicine. Sometimes, the enormous medication burden is worsened even further--either by the simultaneous prescription of more than one drug from a given class or the additional self-medication effected by the sharing of pills among patients. With this wide range of medication comes with their own side effects and often cause overdose eventually resulting in death. Using CBD for PTSD There is no ideal drug treatment for PTSD sufferers, clinical or preclinical. However, studies suggest that the endocannabinoid system, which plays an essential role in maintaining emotional homeostasis and in regulating memory retrieval, consolidation and most importantly extinction, is a possible and ideal target to treat both the emotional and cognitive characterizations of PTSD. Martin Lee, a researcher of the Multidisciplinary Association of Psychedelic Research, found people with PTSD had uniformly lower levels of an endocannabinoid called anandamide compared to controls. The experience of PTSD appeared to reset their baseline endocannabinoids at a lower level permanently. Endocannabinoids are involved in regulating dozens of biological and psychological functions, so addressing this deficiency through the highly refined chemistry of cannabis, people experiencing the diverse effects of PTSD can find relief. The endocannabinoid system, first discovered in 1992 by Israeli researcher Dr. Ralph Mechoulam, is made up of two main receptors. These receptors, cannabinoid 1 (CB1) and cannabinoid 2 (CB2), were found to be an integral part of all human and animal physiologies, and are only configured to accept cannabinoids, especially tetrahydrocannabinol (THC) and cannabidiol (CBD). These receptors have been found to modulate the release of neurotransmitters and produce a wide range of effects on the central nervous system, including pleasure and the alteration of the memory process. Research suggests that the cannabinoids found in CBD have the ability to work in conjunction with the cannabinoid receptors to block the continuous retrieval of traumatic events and reduce the anxieties associated with it. Why CBD is so Helpful for PTSD The cannabis plant contains more than 100 different chemical compounds known as cannabinoids, which interact with the body's endocannabinoid system. Cannabidiol or CBD is the most famous among them for having hundreds of medical benefits. So, Cannabidiol—CBD—is a cannabis compound that has remarkable medical and recreational benefits, but does not make people feel “High”. It can actually prevent the psychoactivity of THC. Cannabidiol is one of at least 100 active cannabinoids identified in cannabis. It is a major phytocannabinoid, accounting for up to 40% of the plants extract. The fact is that CBD-infused cannabis strains are non-psychoactive or less psychoactive than THC-dominant strains. It’s made CBD products a good option for patients looking for relief from inflammation, pain, anxiety, psychosis, seizures, spasms, and other conditions without disconcerting feelings of lethargy or dysphoria. In particular, CBD has been shown to be effective for PTSD. CBD and PTSD aren’t always associated together but CBD has shown to help. CBD does not directly stimulate the endocannabinoid system. Instead, it acts by inhibiting the enzymes that break down the endocannabinoids, much like an MAOI works by blocking serotonin destruction. This raises the levels of anandamide and symptoms are relieved. Furthermore, because CBD does not directly stimulate the CB1 receptor in the brain, it is not intoxicating. It doesn’t get you high; it just brings relief. No impairment. No sleepiness. No effects that may prevent you from working or participating in society. Recent Studies on CBD’s Effect on Post-Traumatic Stress Disorder: These studies showed evidence of how effective CBD is in PSTD treatment. These are all available in govt sites. PTSD patients saw a 75% reduction in PTSD symptoms, as measured by the Clinical Administered Post Traumatic Scale, when they were using cannabis compared to when they were not. (http://www.ncbi.nlm.nih.gov/pubmed/24830188) Evidence from human studies indicates that CBD found in cannabis has considerable potential as a treatment for anxiety disorders. (http://www.ncbi.nlm.nih.gov/pubmed/26341731) A review of published evidence finds that cannabinoids help PTSD patients manage the condition’s three major symptoms (re-experiencing, avoidance and numbing, hyperarousal) and helps improve sleep in those PTSD patients suffering from insomnia and nightmares. (http://www.ncbi.nlm.nih.gov/pubmed/26195653) Repeated CBD administration prevents the long-lasting anxiogenic effects observed after predator exposure probably by facilitating 5HT1A receptors neurotransmission. Our results suggest that CBD has beneficial potential for PTSD treatment and that 5HT1A receptors could be a therapeutic target in this disorder. (https://www.ncbi.nlm.nih.gov/pubmed/22979992) case report of a 19-year-old male patient with a spectrum of severe PTSD symptoms, such as intense flashbacks, panic attacks, and self-mutilation, who discovered that some of his major symptoms were dramatically reduced by smoking cannabis resin…This review shows that recent studies provided supporting evidence that PTSD patients may be able to cope with their symptoms by using cannabis products. Cannabis may dampen the strength or emotional impact of traumatic memories through synergistic mechanisms that might make it easier for people with PTSD to rest or sleep and to feel less anxious and less involved with flashback memories. The presence of endocannabinoid signalling systems within stress-sensitive nuclei of the hypothalamus, as well as upstream limbic structures (amygdala), point to the significance of this system for the regulation of neuroendocrine and behavioural responses to stress. Evidence is increasingly accumulating that cannabinoids might play a role in fear extinction and antidepressive effects. (https://www.ncbi.nlm.nih.gov/pubmed/22736575) CBD both acutely inhibited fear expression and enhanced extinction to produce longer lasting reductions in fear. These observations provide further support for the potential translational use of CBD in conditions such as post-traumatic stress disorder and specific phobias. (https://www.ncbi.nlm.nih.gov/pmc/articles/PMC5101100/) The main finding from this case study is that CBD oil can be an effective compound to reduce anxiety and insomnia secondary to PTSD. This case study provides clinical data that support the use of cannabidiol oil as a safe treatment for reducing anxiety and improving sleep in a young girl with post-traumatic stress disorder. (https://www.ncbi.nlm.nih.gov/pmc/articles/PMC5101100/) CBD, PTSD & YOU: Unlike THC, CBD provides the same medical benefits of hemp plants without experiencing a high. The positive effects of CBD can help PTSD patients manage the core symptoms of the condition which include re-experiencing, avoidance, and hyperarousal. CBD has become an alternative to traditional drug and psychotherapy treatments in recent years and at least 24 states have approved CBD and cannabinoids for treatment of post-traumatic stress disorder. Frequently used for coping purposes by combat veterans, CBD has proven to be a suitable replacement for traditional drugs in treating emotional regulation, stress tolerance, irregular sleeping patterns, nightmares, social anxieties and lessening the effects of triggers. While there is no cure for PTSD, CBD is a suitable replacement, backed by medical research, for both drug and psychotherapeutic means of controlling and treating symptoms. Traditionally, PTSD is very difficult to treat due to the plethora of symptoms. While most treatment options only focus on treating a few symptoms, CBD has the ability to treat a wide range of symptoms associated with the disorder. It has the ability to reduce anxiety, help with depression, fight insomnia, and reduce or eliminate flashbacks without the risk of possible substance abuse. Final Words: So, now we have it, a current look at how CBD and PTSD is becoming mutually beneficial terms instead of unknown ones. It is encouraging that more and more PTSD patients are choosing CBD as a way to at least take the edge off their pain, depression and anxiety while steadily reducing the amount of prescription meds that they have been prescribed. It’s obvious to all of us who use cannabidiol that CBD improves our quality of life as well as helping to heal our nervous system naturally instead of dealing with unwanted side effects of the aforementioned SSRI’s and SNRI’s. In fact, all 113+ cannabinoids found in Cannabis are proven safe and non-addictive. CBD has no psycho-active properties (no high or euphoria) and is often recommended by health professionals for children for countless ailments and diseases ranging from PTSD, ADD/ADHD to asthma and epilepsy. CBD products are found with increasing frequency to be preferred by patients of all ages over prescription medication and the countless negative side effects that comes with all of them. If the list of side effects from prescription medications seems antithetical to the discoveries from post-modern medical science, Any way you look at it, the Veterans Administration is and has been for too long complicit in not only obfuscation of the truth about Cannabis, but withholding of proper medical care and general medical malpractice – the extent of which is only now being exposed. The question persists… How far down the rabbit hole do we have to go to determine the true extent of medical malpractice, insurance fraud, and Big Pharma/U.S. Government collusion that has permeated our medical system? PSTD, CBD, Side-effects, Experience References: Akirav, I. (2013). Targeting the endocannabinoid system to treat haunting traumatic memories. Frontiers in Behavioral Neuroscience, 7, 124. Retrieved from http://www.ncbi.nlm.nih.gov/pmc/articles/PMC3776936/. Betthauser, K., Pilz, J., and Vollmer, L.E. (2015, August). Use and effects of cannabinoids in military veterans with posttraumatic stress disorder. American Journal of Health-System Pharmacy, 72(15), 1279-84. Blessing E.M., Steenkamp, M.M., Manzanares, J., and Marmar, C.R. (2015, September 4). Cannabidiol as a Potential Treatment for Anxiety Disorders. Neuotherapeutics, Epub ahead of print. Retrieved from http://www.ncbi.nlm.nih.gov/pubmed/26341731. Boden, M.T., Babson, K.A., Vujanovic, A.A., Short, N.A., and Bonn-Miller, M.O. (2013, May-June). Post-traumatic stress disorder and cannabis use characteristics among military veterans with cannabis dependence. The American Journal on Addictions, 22(3), 277-84. Bonn-Miller, M.O., Babson, K.A., and Vandrey, R. (2014, March 1). Using cannabis to help you sleep: heightened frequency of cannabinoids use among those with PTSD. Drug and Alcohol Dependence, 136, 162-5. Bonn-Miller, M.O., Vujanovic, A.A., and Drescher, K.D. (2011, September). Cannabis use among military veterans after residential treatment for posttraumatic stress disorder. Psychology of Addictive Behavior, 25(3), 485-91. Campos, A.C., Ferreira, F.R., and Guimaraes, F.S. (2012, November). Cannabidiol blocks long-lasting behavioral consequences of predator threat stress: possible involvement of 5Ht1A receptors. Journal of Psychiatric Research, 46(11), 1501-10. Greer, G.R., Grob, C.S., and Halberstadt, A.L. (2014, January-March). PTSD symptom reports of patients evaluated for the New Mexico Cannabinoids Program. Journal of Psychoactive Drugs, 46(1), 73-7. Passie, T., Emrich, H.M., Karst, M., Brandt, S.D., and Halpern, J.H. (2012, July-August). Mitigation of post-traumatic stress symptoms by Cannabis resin: a review of the clinical and neurobiological evidence. Drug Testing and Analysis, 4(7-8), 649-59. Post-traumatic stress disorder (PTSD). (2014, April 15). Mayo Clinic. Retrieved from http://www.mayoclinic.org/diseases-conditions/post-traumatic-stress-disorder/basics/definition/con-20022540. Potter, C.M., Vujanovic, A.A., Marshall-Verenz, E.C., Bernstein, A., and Bonn-Miller, M.O. (2011, April). Posttraumatic stress and Cannabis use coping motives: the mediating role of distress tolerance. Journal of Anxiety Disorders, 25(3), 437-43. Trezza, V., and Campolongo, P. (2013, August 9). The endocannabinoid system as a possible target to treat both the cognitive and emotional features of post-traumatic stress disorder (PTSD). Frontiers in Behavioral Neuroscience, 7, 100. Walsh, Z., Gonzalez, R., Crosby, K., S Thiessmen, M., Carroll, C., and Bonn-Miller, M.O. (2016, October 12). Medical cannabis and mental health: A guided systematic review. Clinical Psychology Review, 51, 15-29. What is Post-traumatic Stress Disorder (PTSD)? (n.d.). National Institute of Mental Health. Retrieved from http://www.nimh.nih.gov/health/topics/post-traumatic-stress-disorder-ptsd/index.shtml. https://www.istss.org/about-istss.aspx https://www.ncbi.nlm.nih.gov/pubmed/21307846 https://www.ptsd.va.gov/public/treatment/therapy-med/treatment-ptsd.asp http://www.militarywithptsd.org/ptsd-changes-thinking/ https://www.hellomd.com/answers/57d06528ffcc7c00096a41d4/the-right-dosage-of-cbd http://woundedwarriorhomes.org/ptsd?gclid=CPHMqO2bqtMCFZBlfgodzWUFIQ Read the full article
0 notes
Text
Magic Items: Clubs
Monkey Paw of Extreme Prejudice The neo-orog captain, Sprawg, is the current instructor of general battle tactics for the new Legion of the Chimera recruits. As such, he needed a tool to keep his new recruits submissive and in line. Thus, the Monkey Paw of Extreme Prejudice was created. The Monkey Paw looks exactly like the name it describes. It consists mainly of a large, petrified monkey’s arm severed at the shoulder. At the shoulder joint, it looks like a one-handed grip was jammed into the bone and magically fused. At the opposite end, the paw is open and is the main dealer of pain. Once someone is smacked with the paw, aside from the considerable damage, there is a chance that the recipient of the discipline will suffer from heightened fear and/or confusion. Once these symptoms wear off, it is not likely that the recipient of the paw’s discipline will ever be a problem in the future, especially while class is in session. Stats- This +5 club gives you two extra attacks per round, 15% chance to cast Fear on the Target, and 5% chance of casting Confusion
Memories of Kuldahar This Huge gnarled tree limb is a broken bough from the great tree of Kuldahor, a might oak far from the southeast of Targos. The great oak is believed to be a gift of the God of Nature, Silvanus and it is an awe-inspiring sight , towering hundreds of feet into the sky and providing a great circle of warmth to all who live beneath its sheltering limbs. For many, the three represents as peaceful symbiosis between town and nature, and the three is revered as a holy site by druids throughout Faerun. When the town of Kuldahar was laid siege by the great evil from the Spine of the World Mountains in the Year of the Cold Soul, 1281 DR, the great of Kuldahar was buffered by the great winds and howling storms blasting the region, causing the circle of warmth to recede and snapping off several limbs from the top of the tree. These limbs were gathered up by the town’s residents after the Great Tree was saved and they were kept in many houses as a symbol of the town’s persistence in the face of adversity. Some of these pieces of the great tree have found their way throughout the Ten-Towns, and the limbs still carry some of the warmth and enchantment of the great tree within them, making them powerful weapons. Stats- This +4 club gives 5 cold reduction, 1 Piecing Reduction and 2 Bludgeoning Reduction
Club of Confusion The Club of Confusion was crafted by the ogress Shavauntea as a ‘gift’ for her husband, Grothak the Stupid. Her hope was the club could be used to “knock sense into empty head” Shavauntea was quite surprised to find that the weapon had the opposite effect when she brought it down upon her husband’s unsepecting head. The club was thought to have been destroyed in the battle between the two lovers after Grothak regained his senses, obviously this was not the case. Stats- This +5 club has a 99% to deal 2d6 blunt damage, 50% chance of becoming confused, Critical Hit increased by 1
Dazer A powerful weapon created by the wizard retland of Westgate, Dazer was typically used by thugs in said wizard’s employ. Despite Retland’s high education, he was little more than a racketeering boss and thug. His gang, the Cobble Boys, intimidated and oppressed various neighborhoods of Westgate for a decade until a wizard in service of Tyr, Alistar Lavell (not that one), rallied his allies against Retland’s cronies. When Alistar defeated Retland and his gang, he turned Dazer over to the church of Tyr, where it was given to a traveling priest. Stats- This +1 light club has a 5% chance of Stunning target, Concentration Check (DC 18) to disrupt caster’s spells.
Evil Spider Crusher of Doom This weapon was made by a halfling priest of Brandobaris who was terribly afraid of spiders. The halfling’s name was Caligope and his greatest enemy was an evil elven wizard named Eil-Makar. The wizard’s tower was surrounded by a hedge maze filled with giant spiders. The elf’s tower was also filled with a variety of abnormal spiders. For over a year, Caligope refused to even look at the tower. Eventually, he decided to construct a club to deal with her fear. The resulting weapon was named the Evil Spider crusher of Doom. Caligope succeeded in his quest to rob Eil-Makar Blind, and he left dozens of dead spiders in his wake. Stats- This +2 club is +4 against spiders.
Peacekeeper A tough bartender in Westgate named Righteous Tad commissioned the creation of this weapon to deal with his rowdier patrons. Tad would normally pound the club against the bar if things got out of hand, but he frequently had to join the brawl to restore ‘order’. He is said to have clubbed so many thieves over the head with the stick that no major criminal in Westgate could honestly claim that they had never felt Peacekeepr’s string. One such criminal, a thug named Hellpin, took offense at the beating he received. Helpin trained his dogs on Righteous Tad one foggy night. Tad managed to kill more than half of the canines before he was overborne and done in. Hellpin kept the club as a trophy in his hangout as a warning to those who might cross him. The Night Masks did. Stat- This +3 club gives immunity to backstab
Svian’s Club A massive club, this weapon used to belong to the powerful barbarian warrior Svian of the Elk Tribe. Svian was a grim man, tall and wiry who was known throughout the north for his dire disposition and serious who was known throughout the north for his dire disposition and serious manner. In battle, unlike his kin, he rarely became excited to panicked. He simply held his ground and destroyed everyone that came near him. It is said that when Svian was morally wounded, he simply walked over to a nearby rock and sate down, never indicating that he was suffering. It was several hours before his kinsmen realized he was dead. Stats- These +5 clubs deal an extra 1D6 damage to wood based enemies. Gladiator’s Club Jorag Mithkik was the champion of the gladiator pits in Chessenta. His owner, a mage of dubious reputation, made certain that Jorag always had the latest equipment. He made this club as a gift when Jorga’s win made the mage a fortune in bets, Jorag eventually retired and became a teacher at one of the top gladiator schools in Chessenta. His club was a feared disciplinary weapon. Stats- This +8 spiked club has 50% chance to daze for 2 rounds (DC 22)
Baton of the Holy The Devout clerics of the forgotten Ashen Order made these clubs for neophytes. When the main hold of the order was destroyed by an infestation of zombies, most of the batons were lost Stats- This +1 Baton gives an extra 1st level cleric spells and emits a dim yellow light. It is +2 against Zombies
Ironwood Club Ironwood is an extremely durable yet light type of wood that can only be found in the oldest and deepest forests. Despite its amazing properties it is considered a non magical material. This +1 ironwood club is 40% lighter.
Tethir-Wood Cudgel Encroachment on elven territory is not tolerated, though an exception is occasionally made for those who show proper reverence. Such is the case in the forest of Tethir, where a sect of druids have been welcomed and, on occasion, given special boons for their tireless work. While usually information such as a gift might also induce an elven-crafted item like this one Stats- This +2 Cudgel deals 1D6 acid damage and gives you a +2 bonus to diplomacy with elves
Watchman’s Club This was one of many such weapons distributed among a short-lived private militia in Waterdeep called the Watchmen’s Club (pun hell). No expense was spared for their equipment because the primary backers were a group of adventurous nobles who fancied that they were “taking the night back from hoodlums and roustabouts” The movement folded when the pursuit fell out of fashion. By which I mean, military coups. Stats- This +1 War Club gives the bonus feat alertness, emits light, and gives a +2 to Spot and Listen.
The Angry Soul In the early days of exploration within the jungles of Chult, a Calimshan expedition clashed with a small tribe after removing artifacts from a burial site. A local shaman named Gol’Kai killed a noble while trying to retrieve the sacred items, and the ‘civilized’ invaders retaliated. The tribe did not survive. Weapons such as this were found in nearby villages soon after, accompanied by a silent apparition of Gol’Kai, voiceless as his people. Stats- This+3 war Club deals an extra 1D6 electrical bonus and has a 50% to inflict fear for 2 rounds (DC 14).
Will of the Lost Strangely, the well-worn grip of this weapon is a furniture pattern from around 1200 DR, the club itself being a leg from the central table in a 500-seat fest-hall. The hall was the heart of a warrior can and the site of their last stand during the Year of the Black Horde. In the face of the overwhelming orc hordes they fought with whatever means they could, but were ultimately lost to a man Stats- This +1 Club gives vampire regeneration 3
Bone Club This vicious club was created hundreds of years ago, reportedly by a shaman on a quest for revenge. His family had fallen to undead, and so personal was his rage that he amputated his own leg, using the femur for the body of the weapon. Magical runes empower it, though it is likely the sheer force of his hatred have served on its own. Stats- +2 club, +3 vs. undead.
Devil’s Due This weapon has a black metal handle that seems to have grown into the narrow skull that is affixed to its top. The metal looks as if it has grown out of the skull, and spikes pierce through the eye sockets, jaw and from the skull cap itself. The ‘metal’ is not metal at all, but the remnants of a creatures forearm that punched through the base of the fiendish skull that now bedecks the head of this weapon. The Spikes have pierced through the skull actually appear to be some sort of quills form the creatures forearm. The common name of this weapon is ‘Devil’s Due” to who or what event it refers to is unknown, but it was obviously a painful experience for the two parties involved. Stats- This spiked club is +2 for attack and +1 to damage. It also deals an extra 1D8 acid damage to the target and 1D6 acid damage to the wielder
The Nameless One’s Arm This served arm is as hard as a wooden club. It looks like it was severed cleanly at the shoulder (most likely by a scythe blade) and though it looks many decades old, it is more petrified than rotted. It has an unhealthy gray pallor and is covered with scars. Intrinsic tattooed decorate its surface, spiraling up from the wrist all the way to the remains of the should. Upon closer inspect, you know for a fact that this arm is yours. How long it has been lying around waiting for you is anyone’s guess. Stats- This +1 warclub is the Nameless one’s left arm
Corpse limb #985 This arm snapped clean off corpse #985 when it, uh, accidentally toppled. As much as the corpse knee was rotten clean through, it looks like the combination of thick applications of embalming fluid and rigor mortis has made this arm almost as hard as wood. If you needed to, you could either use it to shake someone’s hand from a distance or use it to bash their skull in Stats- This Club deals double damage to zombies.
Fiend Femur This tanar’ri femur carries the last traces of a balor’s essence within its marrow. Disgraced in battle and torn apart from its fellow demons in an ceremonial execution the bone has since carried with it a vengeful spite towards all of its kind. When the femur strikes any tanar’ri or baatezu, serrated teeth bristle up and down the length of the bone and causes tremendous damage to any the creature. Stats- This +2 bone club deals an extra 3D8 damage to Devils or Demons, not usable by good characters.
Club of Nettles This club seems to be made form some sort of prickly plant. Small thorns adorn the head of the club and can easily be broken off. This particular club is one of the more favored weapons of thieves. Upon making a successful hit on an opponent, tiny barbed thorns lodge into the skin and cause the victim to become disoriented for a brief period of time. This allows the thief time to safely rob and escape the victim. Stats- This +2 spiked club makes the wielder make a spirit check (DC 16) or be effected by Confusion.
Root of the Problem This enchanted club is said to have existed since the time of the fall of Netheril and the birth of the great Anauroch Desert. While the toll on civilization was great, the true victims were natures’s creatures, condemned to stand and watch as their homes decayed and died. As habitats receded, those that remained were invaded by displaced hordes of creatures, the more impatient of which marched on unspoiled land taking whatever they wished. This particular weapon is said to have come form a dryad’s tree, a final gift to nature’s cause from pain, as her wood might not have suffered so if it had not been so strong and lush. Less respecting scholars have since bestowed the item’s ironic name, though the humor is not appreciated among nature’s more devout followers Stats- +1 Club deals an extra point of acid damage, +3 vs. unnatural creatures (aberrations, outsiders, undead)
Blackblood This oak club is coated with darkened dried clots of a tar-like substance. Durin battle this substance glow black with an inner light, and becomes thick and fluids. When the club strikes an opponent it delivers additional acid damage from the liquid splashing over the victim Stats- This +3 club deals an extra 3 points of acid damage, and lets you use the spell water walk only on oil at will.
Club of Detonation This crude wooden club burns with the raging spirit of a demon forever trapped within by the powerful enchantments placed on the weapon. Occasionally however, the demon’s wrath escapes in a fiery blast. The enchantments from the Ring of Fire Resistance makes the demon spirit trapped within this weapon easier to control, though the wrath of the creature may occasionally still be released without warning. Stats- This +3 club deals an extra 3 points of dire damage, and has a 20% chance of dealing an extra 10 points of fire damage. There is a 7% chance that a fireball (caster level 10) explodes centered on the target. If upgraded it becomes +5 and deals 5 points of fire damage. There is a 30% chance that it will deal an extra 15 points of damage and a 5% chance that a Fireball is detonated by the weapon. Speed 3
Gnasher Makal of the Pine, a devious druid, carved this club and bounded it with the spirit of his wolverine companion. Like that tenacious creature, Gnasher is a dangerous weapon in the hands of a skilled user. Wehen the clubs strikes, sharp splinters dig into the victim’s flesh, causing extreme pain and extra damage that continues for some time after the blow. Makal used the club successful on several occasions, earning the anger of orc loggers threatening his forests. Stats- This +2 Club can make a foe suffer 2 points of damage for rounds after each hit. This doesn’t stack.
Mighty Oak Fashioned from the hardest old oak from the high forest, this gnarled cudgel can fell an adult grizzly when wielded by a skilled warrior. Stats- +2 greatclub gives you a +2 to Vitality Saves
Cudgel of Entry A unique magical item which could be found amongst the belongings of the warrior Dorstag, the cudgel of entry offered no special benefits in combat, but rather allowed those who brandished it to deftly smash apart stubborn locks with ease, making it an efficient (if not precisely stealthy) means of entering sealed chambers. With such an artifact in their possession, an adventurer could largely dispense with lockpicks and spells of opening. Stats- This +2 Cudgel can cast Knock at will
Night Club
This darkwood shaft surrounds a core of lead, giving it both stealth and heft. Its enchantment connects the club to the Shadow Weave, lending it greater power under cloak of night.
Stats: This +1 Club is +2 at night and also gives a +2 to Move Silently.
Mosela’s Cudgel
Mosela was dissapointed when she learned that she would be finishing her apprentence under the tutelage of a sorcerer- sorcerers were not know for their institutional genius- but the opportunity to work with golem was one that no enterprising young mage could reasonably pass up and that happened to be Listrom’s specialty. Unfortunately-and it took Mosela only a few short days to discover this-Listorm knew more about making the golems than he did about controlling them, and by the end of Mosela’s first week she realized that she would need some means of protecting herself. Thus was created this cudgel that, she hoped, would keep the misbehaving constructs at baby. When Listorm lost what little sanity he had, Mosela discovered that her invention worked just as well on raving lunatics
stats: This +2 Club is +3 against Construct and gives you a +2 to Saves vs. Alteration Spells
Backwhacker
Most Thieves favor bladed weapons when striking from the shadows, but not all. Whether due to religious convictions, personal preference, or anti-establishment tendencies, some thieves prefer to backstab their enemies with a blunt instrument.
stats: If this +2 club is used for backstab or sneak attack, the target must make a Vitality Save (DC 17) or be knocked out for 2 acts.
Dial Ewa Dibita
ial Ewn Dibita
Once owned by the Glanfathan barbarian Bardwn Cawldha, this club has ended the life of many an opponent. Badrwn was known to rush headlong into every battle, swinging the club over his head shouting Dial Ewn Dibita (Vengeance, Just, and and Merciless). Even in victory, Badrwn was relentless, using the club to dispatch wounded or captive foe where the ylay. In time, his battle cry came to be associated with the weapon itself, remembered long after Badrwn’s death.
Stats: This +5 club which deals 3D4 extra damage against flanked enemies.
Blesca’s Labor
An unlikely but effective leader, the barbarian Blesca held off Aedyran expansion north of Readceras by organizing the southern Ixamitl tribes. She kept her ragged alliance together by persuasion, coercion, and force, when necessary. Her coalition held together just long enough to dissuade an advance.
Stats: THis +4 club is +5 if you are targeting the same enemy as an ally, which will deal an extra 1D6 damage. It also has a 20% of drains 1D6 damage
Caballu’s Whispering Staff
This ironwood staff was once held by the goblin sorcerer Caballus, and it still bears the stink of his torch. Trails of runes encircle the staff like snakes, and aside from a single minor rune of accuracy and another of wounding, the rest appear to be nonsense syllables and bunk. The staff is surprisingly light and well-balanced for its size, and it can be held easily in one hand. So more of a club than a staff for a medium sized creature
Stats: This +4 Club gives you a +5 to Move Silently, can cast invisibility sphere 1/day, deals 3 extra damage to non goblins
Branching Paths of Kuldahar
This huge gnarled tree limb is a broken bough from the great tree of Kuldahar, a mighty oak far to the southeast of Targos. The great oak is believed to be a gift of the God of Nature, Silvanus, and it is an awe-inspiring sight, towering hundreds of feet into the skye and providing a great circle of warmth to all who live beneath its sheltering limbs. For many, the three is revered as a holy site by druids throughout Faerun.
When the town of Kuldahar was laid siege by the great evil from the Spine of the World Mountains in the Year of the Cold soul, 1281 DR, the great tree of Kuldahar was buffeted by the great winds and howling storms blasting the region, causing its circle of warmth to recede and snapping off several limbs from the top of the tree. These limbs were gathered up by the town’s residents after the town of the Kuldahar was saved, and they were kept in many houses as a symbol of the town’s persistence in the face of adversity. Some of these pieces of the great tree have found their way throughout the Ten-Towns, and the limbs still carry some of the warmth and enchantments of the great tree within them, making them powerful weapons.
Stats: This +4 Club gives you Cold Resistance 5, Bludgeoning Resistance 2, Piercing Resistance
The Nasty Club
Krandok the Bugbear was never a great thinker, even by bugbear standards. However, when his big wooden club began to end up with shards of metal embedded in it, Krandok thought that they just might make his club hurt a little more in battle, so he left them as it is. Over time, his club began to collect more and more of these shards and Krandok also intentionally embedded some of his own. The result is what Krandok has called his “Nasty Club”.
Stats: This +1 Spiked Club has a 10% of doing 1d6 extra piercing damage
St. Wygelt
A strictly devoted follower of Woedica, Wygelt was haunted by dream of criminals committing horrific acts of violence, only to escape punishment or receive one that was unduly light. She came to believe Woedica was speaking to her through these dreams, demanding these people receive justice.
Wygelt found these criminals in hideouts and homes, and very often in jail, serving inadequate sentences. She would steal into these places, which were frequently under heavy guard, find her way to the criminal, and pronounce the judgement of Woedica. (her incredible knack for reaching these places were in some instances later declare as miracles when she was canonized.) If the criminal was lucky, it would only mean disfigurement, but most were executed on the spot with Wygelt cudgel.
Eventually Wygelt’s reputation spread too far, and many criminals that feared her began to set traps and issue bounties. When she was finally caught, she was clubbed to death with her own weapon. It is said that with her final words, she declared that she was a murderer, that she deserved this fate.
St. Wygelt’s cudgel is a simple spiked club with a leather-wrapped handle. The wood itself is irreversibly stained reddish brown with the blood of criminals.
Stats: This +5 Cudgel deals 2D4 extra damage
Kuluk’s Skull Splitter
Kuluk, was the great warrior priest of the Butklor tribe, and fought in the vanguard in the many wars against human, elves, dwarves and goblins alike. Eventually he earned enough prestige to take power and started to try to unify the tribes, an incredibly difficult task considering the formidable opponents he was up against. To achieve his ends, Kuluk did the unthinkable, he crafted a weapon to kill other orcs. He commissioned the weapon from spies from a local human kingdom, who hoped to pit the orcs against each other and were happy to create a weapon to for an orc to kill his own kind (cough Cold War cough). His weapon of choice was a great club, as opponents would always assume that an orc with a club is nothing more than a brute. Kuluk would often try to defeat enemy chiefs in one on one duels, using his weapon to give him the edge he needed to defeat them and earn the favor of his gods. When Kuluk had unified all but one of the tribes, he was celebrating the victory that night with wine, when he, drunkenly reenacting the duel, accidentally brained himself with its spike, leaving him a vegetable. The tribes fell into war and for decades the lands around were at peace. Rumors quickly spread that the club was designed to kill Kulak, and a generation later, a great war between the tribes and the kingdom broke out which lasted for a decade.
Stats: This +2 spiked greatclub deals 1D10 extra damage to any orc or half orcs. Upon the role of a 1, the wielder will always hit himself (no second roll).
7 notes
·
View notes
Text
Making Coggle Even Faster
Today we've got another update from the tech behind Coggle: how we cut the average response time by over 40% with some fairly simple changes, and learned a lesson in checking default configurations.
First, a bit of architecture. Coggle is divided into several separate services behind the scenes, with each service responsible for different things. One service is responsible for storing and accessing documents, another for sending email, one for generating downloads, and so on.
These services talk to each other internally with HTTP requests: so for each request from your browser for a page there will be several more requests between these services before a response is sent back to your browser.
This all adds up to quite a lot of HTTP requests - and many of these Coggle services call out to further services hosted by AWS, using (yep you guessed it!) even more HTTP requests.
So, in all, an awful lot of HTTP requests are going on.
Coggle is written in node.js, and originally we just used the default settings of the node request module, and the AWS SDK for node for most of these requests. (At this point there are better options than the request module - we'd recommend undici for new development - but there isn't a practical alternative to the AWS SDK.)
Why does this matter? Well, it turns out both of these default configurations are absolutely not tuned for high-throughput applications...
The Investigation Begins
A few weeks ago I came across this interesting interactive debugging puzzle by @b0rk - now, no spoilers here (go try it for yourself!), but when I finally got to the solution it did make me immediately wonder if the same issue was present in Coggle - as for a long time our average response time for requests has been about 60ms:

It didn't take long to confirm that the problem in the puzzle was not occurring for us, but this made me wonder why exactly our average response-time graph was so consistently high - was there room for any improvement? Are all those requests between the different services slowing things down?
What About the Database?
The first obvious place to check is the database. While the vast majority of requests are very fast, we have some occasionally slower requests. Could these be holding things up due to slow trains? Tweaking the connection pool size options of the mongodb driver showed a small improvement, and this is definitely a default configuration that you should tune to your application rather than leaving as-is (note maxPoolSize, not poolSize, is the option that should be used for unified topology connections).
No dramatic improvements here though.
All Those Internal Requests...
Like the mongodb driver, nodejs itself also maintains a global connection pool (in this case an http.Agent) for outgoing connections. If you search for information about this connection pool you will find lots articles saying that it's limited to 5 concurrent connections. Ahha! This could easily be causing requests to back-up.
Inter-service requests are generally slower than database requests, and just five slow requests could cause others to start piling up behind them!
Fortunately, all those articles are very out of date. The global nodejs connection pool has been unlimited in size since nodejs 0.12 in 2015. But this line of investigation does lead directly to the true culprit.
The global http Agent which our internal requests were using is constructed using default options. And a careful reading of the http agent documentation shows that the keepAlive option is false by default.
This means, simply, that after a request is complete nodejs will close the connection to the remote server, instead of keeping the connection in case another request is made to the same server within a short time period.
In Coggle, where we have a small number of component services making a large number of requests to each other, it should almost always be possible to re-use connections for additional requests. Instead, with the default configuration, a new connection was being created for every single request!
A Solution!
It is not possible to change the global default value, so to configure the request module to use an http agent with keepalive set, a new agent must be created and passed in the options to each request. Separate agents are needed for http and https, but we want to make sure to re-use the same agent for multiple requests, so we use a simple helper function to create or retrieve an agent:
Code not formatted nicely? view on bloggle.coggle.it for syntax highlighting.
const http = require('http'); const https = require('https'); const shared_agents = {'http:':null, 'https:':null}; const getAgentFor = (protocol) => { if(!shared_agents[protocol]){ if(protocol === 'http:'){ shared_agents[protocol] = new http.Agent({ keepAlive: true }); }else if(protocol === 'https:'){ shared_agents[protocol] = new https.Agent({ keepAlive: true, rejectUnauthorized: true }); }else{ throw new Error(`unsupported request protocol ${protocol}`); } } return shared_agents[protocol]; };
And then when making requests, simply set the agent option:
args.agent = getAgentFor(new URL(args.url).protocol); request(args, callback);
For Coggle, this simple change had a dramatic effect not only on the latency of internal requests (requests are much faster when a new connection doesn't have to be negotiated), but also on CPU use. For one service a reduction of 70%!

The AWS SDK
As with the request module, the AWS SDK for nodejs will also use the default http Agent options for its own connections - meaning again that a new connection is established for each request!
To change this, httpOptions.agent can be set on the constructor for individual AWS services, for example with S3:
const https = require('https'); const s3 = new AWS.S3({ httpOptions:{ agent: new https.Agent({keepAlive:true, rejectUnauthorized:true}) } });
Setting keepAlive when requests are not made sufficiently frequently will not have any performance benefit. Instead there will be a slight cost in memory and cpu of maintaining connections only for them to be closed by the remote server without being re-used.
So how often do requests need to be for keepAlive to show a benefit, or in other words, how long will remote servers keep the connection option?
When keepAlive Makes Sense
The default for nodejs servers is five seconds, and helpfully the Keep-Alive: timeout=5 header is set on responses to indicate this. For AWS things aren't so clear.
While the documentation mentions enabling keepAlive in nodejs clients, it doesn't say how long the server will keep the connection open, and so how frequent requests need to be in order to re-use it.
Some experimentation with S3 in the eu-west-1 region showed a time of about 4 seconds, though it seems possible this could vary with traffic, region, and across services.
But as a rough guide, if you're likely to make more than one request every four seconds then there's some gain to enabling keepAlive, and from there on, as request rates increase, the benefit only grows.
Combined Effect
For Coggle, the combined effect of keepalive for internal and AWS requests was a reduction from about 60ms to about 40ms for the median response time, which is quite amazing for such simple changes!
In the end, this is also a cautionary tale about making sure default configurations are appropriate, especially as patterns of use change over time. Sometimes there can be dramatic gains from just making sure basic things are configured correctly.
I'll leave you with the lovely graph of how much faster the average request to Coggle is since these changes:

I hope this was an interesting read! As always if you have any questions or comments feel free to email [email protected]
Posted by James, June 16th 2021.
0 notes
Text
Water Damage 101 - Think About My Memories?
Damage from water is uncompromising and is destructive. The strain suffered by decrease in the application of your home is poor sufficient but the decline of irreplaceable images and family heirlooms could be a huge stress. This article summarize some methods will reduce burning to these goods. - Reduction is the key - Each the sentence, InchOne ounce of elimination may be valued at a pound of Treatment,In the easiest way to prevent loss of irreplaceable pics and family treasures is by removing or severely lowering to be able to get rid of claimed products. Avoiding to be able to lose or harm this kind of things is key to enjoying the highest delight and benefit this kind of things communicate to the greatest length of time. - Photograph all important papers and photos on your Computer - Every one's some form of code reader inside their household or place of business but for many who don't, and for many who don't have time, fascination, or scientific power to get it done their selves, you can find cheap services that can graphic these products for any affordable price tag. - Connect your iDevices, digital cameras, as well as other electronic devices to your Computer system - iPhones, iPads, feel units, and other equivalent items which permit the user to adopt photographs, download particular goods, or else go to town creatively, are misplaced, thieved, and harmed daily so all the personal data comprised on this kind of system is forever missing. For many people, synchronizing this sort of unit is simply by plugging their system to their Laptop or computer. Higher people can have turned off the autostart method but they can reactivate the support simply by managing the initial program. - Often backup your computer - People appear to fail to remember 1 standard occupant of computer legislation... desktops are models... it's not necessarily if they will digest however, if. Often times personal computers break down at the most annoying times and except the consumer has supported their PC for some external supply - i.e. usb drive, record host, Online copy, etc., all of the documents, docs, pictures, and so forth. on these Laptop or computer are dropped until eventually these kinds of time their Computer system is bound or their data is retrieved. Your entire problem scenario might be eliminated simply by storing laptop. - Preserve all original and Personal computer backup copies in the safe and sound storage area off the driveway - This should go without saying but a majority of individuals keep the back up specifically beside the resource. Even though this might not exactly matter from the predicament of any pc freeze, if your user experience fireplace or water damage, then its fair to assume that something that killed the cause can crush backup. It is just a finest exercise to help keep the back-up in the rut apart from the origin. - Exclusively use replicates or automated photographs - Seeing that all not avoidable photos and family members treasures are safely secured and put away, the enjoyment of such things should not be lost inside the attempt to shield this kind of products. The electronic digital reproduction for these goods will pay the application such products supply with the assurance knowing that the genuine ones feel safe from burning or deterioration. Truly a get-win circumstances. Sadly, these terms of wisdom may come too far gone to your requirements. If this should be so, after that professional water damage restoration business may be able to recommend your electronic devices to some certified recuperation centre for achievable restore or recovery. Any cardstock or not for-digital things, on the other hand, might be misplaced according to the circumstances in the damage. It's distinct that the very best step to rehabilitation is reduction. Source: http://houstonwaterdamagepros.net/
0 notes
Text
Machine Learning Platform meetup
Recap of the Oct 2017 ML Platform meetup at Netflix HQ
By Faisal Siddiqi
Machine Learning is making fast inroads into many areas of business and is being employed in an increasingly widening array of commercial applications. At Netflix, ML has been used for several years on our Recommendations and Personalization problems. Over the last couple of years, ML has expanded into a wide range of newer applications here, such as Content Promotion, Content Price Modeling, Programmatic Marketing, Efficient Content Delivery, Adaptive Streaming QoE, to name only a handful. Scaling and speeding up the application of ML is at the top of mind for the multitudes of researchers, engineers, and data scientists working on these salient problems. We are always looking to learn from academic research and industry application in large scale contexts and love to share what we have learnt as part of running the Netflix use cases at scale.
Last week we hosted a Machine Learning Platform meetup at Netflix HQ in Los Gatos. We had five talks from top practitioners in the industry and in this post we will provide a brief overview summarizing them. The talks from Google, Twitter, Uber, Facebook and Netflix largely fell into one or both of these themes:
Sparse Data in ML: Challenges and solutions
Scaling up Training: Distributed vs Single machine approaches
Google
Ed Chi kicked off the talks with a presentation on how to learn user and item representation for sparse data in recommender systems. His talk covered two major areas of emphasis — Focused Learning and Factorized Deep Retrieval.
In setting up the motivation for the first area, Ed talked of the Tyranny of the Majority in describing the outsized impact of dense sub-zones in otherwise sparse data sets. As as solution to this challenge, he talked about Focused Learning, a sort of divide-and-conquer approach, where you look for subsets of data to focus on and then figure out which models can learn on each subset with differing data density. As an example of this approach, he talked about how using focused and unfocused regularization factors in the cost function, allowed them to model the problem with more success. In the canonical example of movie recommendations, he demonstrated how this approach led to outsized improvements in model prediction quality for sparse data sets (e.g. where Documentaries is one of the most sparse categories).
The use case that Factorized Deep Retrieval addresses is about predicting good co-watch patterns of videos when the corpus of items to recommend is huge (YouTube). You want the recommendations to not ignore the fresh content while still ensuring relevance. He presented TensorFlow’s distributed implementation of WALS (weighted alternating least squares) Factorization as the solution they used for picking sparse but relevant candidates out of the huge candidate corpus. Online rankings for serving were staged into a tiered approach with a first pass nominator selecting a reasonably small set. Then subsequent rankers further refined the selection until a small set of highly relevant candidates were chosen and impressed to the user.
https://medium.com/media/dbe8bb59d3158712d0e20db20322689d/href
Ed also talked about several implementation challenges, in sharing, failures, versioning, and coordination, that the TensorFlow team encountered and addressed in the TFX (TensorFlow Extended) system internally in use at Google. They are looking to add some of these features to TF Serving open-source in the future.
Twitter
Next up was Joe Xie from Twitter who started off by setting the stage with the real time use cases of Twitter. He talked about their single/merged online training and prediction pipeline as a backdrop to the parameter server approach his team took to scaling training and serving. Joe talked about how they tackled one area to scale up at a time. He walked through three stages of their parameter server, starting with first decoupling the training and prediction requests, then focusing on scaling up the training traffic and finally scaling up the model size.
They were able to increase the prediction queries/sec by 10x by separating training and prediction requests in v1 and increase training set size by 20x in v2. They are working on accepting models 10x larger in size in v3, and looking to explore data-parallel optimizations and feature sharding across their v3 distributed architecture. When asked about whether trainers and predictors are also sharded, Joe mentioned that for now they have sharded the trainers but not the predictors.
https://medium.com/media/49012ba8b4951679ec21be9f8d17f9cc/href
Uber
Alex Sergeev from Uber introduced a new distributed training library they have recently open-sourced — Horovod, for making distributed TensorFlow workloads easier. Alex started off by setting the problem of scaling up model training. With ever increasing data sizes and the need for faster training, they explored distributed TensorFlow. Alex alluded to challenges in using the distributed TensorFlow package out of the box. At some level they felt lack of clarity around which knobs to use. As well, they weren’t quite able to do justice to their GPU utilization when training data at scale via TensorFlow.
They explored recent approaches to leveraging data-parallelism in the distributed training space. Motivated by some past work at Baidu and more recently at Facebook (see below), they took a different approach to their deep network training. Conceptually, the training set was split up in chunks of data each of which was processed in parallel by executors, computing gradients. In each pass the gradients are averaged and then fed back into the model.
Typically, in TensorFlow the workers compute the gradients and then send them to the Parameter Server(s) for averaging. Horovod utilizes a data-parallel “ring-allreduce” algorithm that obviates the need to have a parameter server. Each of the workers are involved in not only computing the gradients but also averaging them, communicating in a peer-to-peer fashion. Horovod uses NVDIA’s NCCL2 library to optimize bandwidth of communication between workers.
Alex talked about how they were able to utilize this for both single GPU as well as multiple GPU cases. He also talked about Tensor Fusion, an approach to smart batching that gave them larger gains on less optimized networks.
https://medium.com/media/745233f5b8c850f58d7ee8eae2e3d5c1/href
When asked about distributing the data across GPUs, interestingly, Alex mentioned that in their benchmarks they have seen better scale performance with 8 machines with a single GPU versus a single machine with 8 GPUs.
Facebook
Continuing the thread of GPU optimization for large scale training, Aapo Kyrola from Facebook shared some insights on their experiences working on this problem. As a matter of fact, Aapo described in more detail the case study that was referenced by the Uber presentation on Horovod just prior to this talk.
Aapo started off by giving a quick overview of Caffe2, a lightweight ML framework, highlighting how training can be modeled as a directed graph problem. He compared synchronous SGD (stochastic gradient descent) with asynchronous SGD and then proceeded to describe how they pushed the boundaries on sync SGD on Caffe2 with GLOO. The latter is an open-sourced fast library for performing distributed reductions and leverages NVIDIA’s NCCL2 for inter-GPU reductions.
This all led to the case study of their recently published milestone achievement — they were able to train a ResNet-50 (a 50 layer residual convolutional net) on the ImageNet-1K dataset in less than 1 hour. Sync SGD was used with a data-parallel approach and the “all-reduce” algorithm from GLOO. The case study described how they were able to tweak the learning rate piece-wise with an 8K mini-batch size to get to near state-of-the-art on error rate metrics.
Aapo ended the talk on some lessons learned through this exercise, like how Sync SGD can be pushed quite far on modern GPUs, and how learning rate is an important hyper-parameter for mini-batch size.
https://medium.com/media/ba056537a370ac65965120aa239ceba9/href
Netflix
Netflix’s Benoit Rostykus talked about VectorFlow, a recently open-sourced library for handling sparse data. VectorFlow is designed to be a lightweight neural network library for not-so-deep networks and sparse data.
In many ways Benoit’s talk presented a bit of a counter narrative to the rest of the talks. He argued that while there are a lot of applications in ML which are better served by throwing more training data and more layers (eg, images in convolutional nets), there is a surprising number of applications on the other end of the spectrum too. Such applications, like real-time bidding, can be handled in a single machine context, often need simple feed-forward shallow nets, and performance on CPUs can be pushed hard enough to meet the training latency and cost budget.
VectorFlow was designed for these contexts and this philosophy informed several design decisions. For example the choice of the language, D, was one such decision. The modern system language was chosen to address the goal of a single language in adhoc as well as production contexts — providing the power of C++ and the simplicity/clarity of Python.
Another notable differentiator for VectorFlow is its focus on optimizing for latency instead of throughput. By avoiding large data transfers between RAM and CPU/GPU memory, and avoiding allocations during forward/back-prop, VectorFlow is able to speed things up considerably during training. Benoit was able to demonstrate that for a training set size of 33M rows with a data sparsity of 7%, VectorFlow was able to run each pass of SGD in 4.2 seconds on a single machine with 16 commodity CPU cores.
VectorFlow is used in real-time bidding, programmatic advertising, causal inference, and survival regression to name a few applications in Netflix.
https://medium.com/media/74b6f38ac25e9a62cad5cd393f04e4d0/href
Benoit scoped out some of the future work on VectorFlow’s roadmap which includes deeper sparsity support, more complex nodes, and more optimizers, without giving up the core mantra behind VectorFlow that Simple > Complex. VectorFlow is open-sourced and available on github.
This meetup featured high quality talks and active participation by the audience. It was followed by engaging informal conversations after the talks around the direction of ML in general and deep learning in particular. At Netflix, we are solving many such challenging problems in ML research, engineering and infrastructure at scale as we grow to meet the needs of the next 100 million Netflix members. Join us if you are interested in pushing the state of the art forward.
Machine Learning Platform meetup was originally published in Netflix TechBlog on Medium, where people are continuing the conversation by highlighting and responding to this story.
Source
https://medium.com/netflix-techblog/machine-learning-platform-meetup-ddec090f3c17
0 notes
Text
youtube
Brand Protection Is Essential
Piracy is bad, all of us know that. Downloading pirated applications from the Internet, is the same as stealing something from a shop. We are aware that also. Stores suffer great loses because of theft, in order software creators. anti piracy protection The main distinction is, the initial ones, do not attempt to minimize their loses, at the expense of their customers.It's been quite some time since software companies began to execute in their applications, anti-piracy mechanics. It's clear as everybody would want to secure their work, from being stolen, altered or used without consent. The question is, how far can you go with this?
It started with simple serial numbers or typing in a given world from paper manual shipped with the software. Somewhat time-consuming, but it functioned. As long as you'd the setup disk and manual, an individual could easily set up, re-install the program a dozen times per day, without having Onsist to explain why. But as the Internet popularity grew, it started new possibilities of software protection -- activation providers. The mechanism is pretty simple: purchase applications, input specific product key, validate it via Web and you're ready to go. Simple? Not actually...
Few individuals understand, that most firms established a limit of feasible activations per serial number. Why? In theory, because each permit is valid only for X amount of computers. So to make sure, that we don't share ours with all our Facebook friends, a limit is present. go to wikipedia for more The catch is, if we decide to format our hard disk and perform an original system installation, all software that require reactivation, will treat like a fresh one, and so the counter will go up 1. Now imagine what could happen, in case your hard disk breaks down.
You send it to some service. It's returned, you re-install all, but after a month that the problem returns. Again and again. When finally the faulty part gets replaced brand protection solutions properly, another effort of reactivating your favorite software becomes rejected. Why? Because limit of possible activations has been attained.
What can you do? Call support center and ask to enable you, to activate your applications. Almost always the solution is positive, but... I own the applications, so why so I need to request permission to use it? I know my peace is valid, I have my invoice, cd, manual, sequential number.
I don't need to validate the software further. I just want to use my applications. Some may say, that such situations are rare and it is probably correct. Still this circumstance, makes one wonder, even when the anti-piracy forces are moving in right way. If it persists, we might be facing a critical problem: the variety of viruses, malicious applications increases almost exponentially, making the demand for regular software updates very urgent.
Regular upgrading makes the OS run slower, as one version installed more than older, does not necessarily run as smooth as a fresh install. That is why we replicate our drive C and then set up everything from scratch... and activate our software successfully. This moment. Next time, we might start to think, that it's better to use free alternatives instead. They may not be as strong as their industrial counterparts, but at least they do not care why we install or re-install them.
To put it simple: they do not ask so many questions and that's something most people want -- privacy. Privacy restricted by the anti-piracy campaigns. Time will tell whether these practices, will have any impact on piracy levels worldwide. For the time being, it made our lives a little tougher, than before.
Computer piracy is a lot different from sea piracy. Instead Of plundering and assaulting the commercial ships in the middle of the sea, pc pirates generally steal intellectual property and then, eventually, give it away for public usage. This can possibly destroy the person or business and there are a number of examples to back that up.
Piracy is rampant in gambling industry
Computer game companies are one of the mostly impaired industries by pirates. With the assistance of skilled programmers, pirates crack the code of this game which stores information about individual copies. To put it differently, you no longer need to go to the shop to buy a match - you can just download it at no cost from a pirate host.
Pirate applications has its flaws. Many internet applications are almost not crack-able, because your ID is confirmed on a business server, and pirates have no access over there. Standalone cracked software is with a code that is altered and is susceptible to malfunction and can really damage your computer, let alone not run correctly. Official licensed software guarantees that it can get the work done and is bug free - something pirates provide no absolute guarantee. They just don't care, because, after all, in case you enjoy the program, you will probably buy it yourself.
Necessity and types of software piracy defense
To fight with this situation computer software companies have created software piracy protection program. The software piracy protection comes in several forms according to the functions. Some DVDs are created so that the game just runs if your certified DVD is existing in your CD-ROM drive. Other require a serial number together with security applications on the actual DVD you purchased.
Pirates are usually very great programmers who look forward to be appreciated in large businesses and thus boost their popularity and income. Others do it for pleasure and expect no sensible gain from it. They're driven by the sole sense of evil doing.
There are lots of notorious classes of crackers-pirates who crack virtually every game that comes out and greatly reduce actual incomes of the companies-producers and programmers. The multimillion probac stop actavis sector of entertainment is continuing to have problems with heavy losses because of piracy and this is soon going to change as new anti piracy laws are becoming implemented.
In this highly technological era, practically every aspect of major business is paperless. Though this evolution has significantly simplified the procedure for conducting business, it has also left industries vulnerable to IC piracy attacks. Actually, intellectual theft costs American businesses billions of dollars in losses each and every year. One solution that tech teams should think about is using OTP (one-time-programmable) memory to their microchip devices instead. Here are some reasons why.
--Although the technology isn't brand new (it was first developed in 1969), it is surely reliable; and its Onsist anti piracy protection capabilities have certainly been refined and enhanced through the years. It's virtually problem-free.
--It's comparatively cheap. It is not uncommon for organizations to spend into the thousands and thousands of dollars view publisher blog to get additional anti-piracy solutions, but OTP memory is easy to install and use at a mere fraction of the price.
--The random number system used by OTP memory allows the user to generate an identification number from a massive pool of chances. It is virtually impossible for pirates to discover a particular number when there are literally billions of possible combinations.
--A system with OTP may be adjusted to match any particular preference or program. As an instance, it can be set to permit certain identification numbers to be retrieved only by authorized personnel.
--It's a system That's remarkably simple, yet forcefully effective.
In these tough financial times, companies will need to find anti-piracy techniques that actually work and which are also cost-effective: OTP memory may be the IC protection alternative you've been looking for.
Every publisher will be pleased to acquire anti piracy software that can ably protect PDF files, swf flash content and html content. Fortunately, DRM - digital rights management programs are available to deal with these needs and also to provide the necessary controls to adequately implement data loss protection (DLP). These platforms permit the author to register a client using a licensing system, pick the right customer access level, create customized messages to inform unauthorized customers that they do not have permission to start protected files and also to give them details about where to supply for the permission, and also to set expiry dates and display a web page that affirms the expiration of the protected file.
Using DRM document control applications the document author can execute a watermark capability whereby the user's name and/or business name, and specifics of date/time of usage are displayed on each of the printouts. Additional on antipiracy monitoring, we can even have PDF software which has the capacity to demonstrate user and document statics, auditing and reporting.
Through the watermarking capability DRM will help to identify the location where the leak happened. Additionally, it reports when the document was used and equips the writer with record control abilities to shut off document access if abuse is detected. This is a useful anti piracy measure which prevents individuals from replicating or even altering your work as this normally contributes to the misinterpretation of the planned message. Data loss prevention can be also implemented by requiring users to look at the document using a proprietary application rather different from the one that created it. This way, only authorized users can view the document and document processing tools could be disabled.
Data reduction prevention is all about forestalling the leaking from a document/s beyond the control of the organization that owns it. In nature this anti piracy procedure is all about identifying, monitoring and protecting, which is accomplished by protecting a document's context Onsist and content via a filtering and centralized management program. This record control method helps efforts to automate the recognition of cases once the material contravenes set DRM rules, and also prevents documents from being emailed or duplicated to say a flash drive.
An organization will always find itself being required to share its own confidential information with offshore staff and even attorneys all of whom are external to the company's firewalls and this also makes anti piracy solutions even more crucial. As such, in an effort to stem piracy, information loss protection systems need to have the ability to secure protected files as soon as they are in the hands of outside but authorized parties. Encryption has always been the Reply to document
Control but it only goes as far as stopping unauthorized persons from accessing the protected information. But, it doesn't control what the authorized user can perform with the document once it is decrypted. Nonetheless, we can always combine encryption with DRM controls in order to restrict the ability of these users to share or pass onto the limited information.
Attack Profiles
Successful attacks on vessels, where asset protection is minimum, follow common vulnerabilities, which are manipulated by pirates. These are as follows:
Low speed - (below 16 knots)
Low freeboard - (distance from the waterline to the freeboard deck of a fully loaded boat)
Insufficient preparation and implementation of processes
Alert of team on board is Low or there is no visual evidence of self-protection steps
Where there is a slow response over at this website by the boat and crew
Normally the pirates will use two or more small boats capable of speeds in excess of 20 knots, these are available crafts usually known as "skiffs" and they normally approach the intended goal from the port quarter or stern.
The use of a mother ship is employed as a portable logistics foundation that carries the equipment and personnel to enable attacks to occur farther out to sea, a few attacks have happened at 600 NM from the shore.
The majority of strikes will happen at first and last light, so in these times extra vigilance is required.
Before the Transit
Before a transit, These bodies should be informed and comprise;
The Maritime Security Centre - Horn of Africa (MSCHOA), That's the planning and coordination jurisdiction for EU Forces from the Gulf of Aden and the area from the Coast of Somalia and the United Onsist Social Network Kingdom Maritime Trade Operations (UKMTO), that is in Dubai and will be the first point of contact for vessels in the Area. The day-to-day interface with Experts and the army is the UKMTO.
Before transiting high-risk locations, the owner and Master must carry out their own risk assessments to assess the likelihood of an attack by pirates. The outcome of this risk assessment must identify measures to be taken to protect against the vessel being taken by pirates.
Company Crisis Management Procedures and measures to meet the threat within the area the vessel is transiting, should be addressed.
In order to best prepare a boat, the next training and planning should be considered as a minimum, to control risks from assault:
Register the vessel with the police, UKMTO and MSCHOA
Review the ships safety plan
Carry out team anti-piracy and safety awareness training
Appoint security consultants for your own transit, who have international marine safety experience
Make Sure You have a good and effective anti-piracy contingency plan
Defensive Measures
The vessel should review its safety measures and processes and consider:
Ensuring that the vessels patterns are adjusted in advance to Make Sure that the crew are well rested before they enter the high risk area
Observing radio silence or enabling minimum use of radio gear
Identify a safe room
Securing access to this bridge, onsist.com engine room and crew cottages
Provision of night vision device(s) for watch personnel
Throughout the epsxe anti copy protection patches Transit
Masters should utilize the International Recommended Transit Corridor (IRTC). This is recommended by the naval authorities, westbound vessels utilize the northern part of the corridor and the eastbound vessels use the southern part of the IRTC.
Vessels should remain within the IRTC at all times and ensure that it keeps up with onsist its group transit. The boat should comply with international rules on light.
MSCHOA will advise on the group transit timings which depart at different times and are identified by the speed of the vessel, so if a vessel has a maximum speed of 16 knots it should look at joining a 14 knot group transit.
For those who have employed a security company, they are there for advice and guidance and should also install the procedures and steps for every vessel as suitable. However, vessels should still make sure that they have added crew as lookouts at exposed parts of the vessel especially on the rear port quarter.
It's paramount that a boat protects the crew from danger; this means that only fundamental crew work should be run on the deck whilst in the high-risk areas.
0 notes
Text
Investigations Into Binaural Beats and Solfeggio Frequencies
* This is a more in depth look at the material I presented as part of week 4 of my process journal
PRODUCTION STRATEGIES WEEK 5-
SOME IDEAS RELATED TO MY PROJECT
I’d been investigating the idea of Solfeggio frequencies and Binaural Beats as a way of stimulating healing
through sound Interestingly in terms of Magical Correspondences the 5th frequency of 741 is called Sol traditionally a word for the Sun in the major Western Scale SOL is generally a G though in order to tune my instruments exactly with the Solfeggio of 741 I have tuned the Instruments to 440.6. In order to achieve this I had to switch my project from Protools to Logic as none of the virtual instruments in Pro-tools allow exact tunings (They are still reloading Native instruments on the school computer). Logic allows you to tune your project to any desired tuning system, which is nice. The 741 Hz solfeggio frequency is meant to stimulate intuition. The scale is a medieval and was used in Gregorian chants and has 6 notes. At this stage I’m not a hundred precent on the validity of these frequencies if they are ‘Magic” but it seems as good a place to start as any and I have to say I felt quite lovely after working on the 741hz piece. I made a binaural beat from the 741 theta brain wave.I decided to write the piece in F and note G as that was more in tune with the 440.6 tuning system I found a website that listed how to tune guitar/ piano to be in tune with the solfeggio frequencies. 440.6 is very close to the standard pitch of 440 so I figured if I want to I can tune my guitar to this pretty easily (I had to do an extensive search for a tuner that could detect such micro frequencies.) I also did some investigation into musical intervals and the feelings they are meant to induce.
For instance why a minor third is considered to feel sad. Interestingly I found an article by Simon heather-http://www.simonheather.co.uk/pages/chapters/thehealingpowerofmusicalintervals_sample.pdf
He describes how unison is generally used in mantras as it creates wholeness. The 5th creates comfort and creativity the major six is considered the most beautiful. He had this to say about the fifth and how it can be used to stimulate the energy centres of the body-
FIFTH INTERVAL - NOTES C-G
Fabien Maman says that, "The fifth interval expands in all directions and provokes the widest movement of energy in space. It can be heard in Brazilian music where there is often the interval of the fifth between guitar and voice." Because of its stimulating nature, the cycle of fifths can be used both to concentrate and align chakra energies. The following order can be used to relax the body and bring about the maximum expansion of consciousness: - F C G D A E B." (Each note being five notes above the last)
In my piece I used this idea with 5ths the main tonal building block it also interestingly led back to another reason to use F as the basis of my work. I start with F as a tone to bring that sense of tuning or unity. It then spreads out to use fifths in this pattern for chakra alignment. For the melodic parts I use a major arpeggio as it is the most recognizable building block of western musical systems and I wanted a sense of universality. I also experimented with another pattern based on fifths and sixths. Simon heather describes the fifth as the sweetest interval and as a way to open yourself to the universe. Using octaves to create a sense of togetherness. Interestingly he also shows that intervals make specific patterns under and oscilloscope it would be interesting if this could be a visual component of the work.
I found another website quoting a book by Kay Gardner ( also used in the Simon Heather article) I should find this book Interesting as it breaks down the building blocks of healing music. Also of note is how when making my piece I felt it needed both drones and melodic components that repeat I was thinking about the Indian and its use in meditative practice. The form of the Raga is another point of departure I could look into. I felt that just drones or music wasn’t enough on its own . I would like to add rhythmic elements and the sounds of nature I’ve described above. I also feel its really important to have played instruments and not just synth as it seems in authentic in some way. I’d like to find a harp player as its so inspiring in the work of Alice Coltrane.
Kay Gardner, author of Sounding the Inner Landscape: Music as Medicine, has identified nine elements that demonstrate the healing effects of music.
1. Drone – healing music should have a constant tone that drones behind a simple melody. 2. Repetition – short musical phrases, vocal and instrumental, should be repeated over and over which produce a calming effect. 3. Harmonics – long sustained tones produce harmonic overtones, which balance the entire physical body at the cellular level. 4. Rhythm – rhythm duplicates many pulses in the human body and via entrainment, move the pulses into harmonious pattern 5. Harmony – affects the emotions. Various keys (minor or major evoke feelings of joyfulness, sadness or calmness. 6. Melody – the mind becomes enchanted with melody and ceases to engage in its continuous mental chit-chat. 7.Instrumental colours –each instrument has its own unique vibration. (playing the note of C on the piano would sound very different to the same note on a violin) 8. Form. – pieces that have many changes in tempo will affect stimulate us and steady pieces will calm us. 9. Intention – music played with a focused intention of healing would contain that intention in its frequency.
The main six Solfeggio frequencies are:
396 Hz – Liberating Guilt and Feart
417 Hz – Undoing Situations and Facilitating Change
528 Hz – Transformation and Miracles (DNA Repair)
639 Hz – Connecting/Relationships
741 Hz – Expression/Solutions
852 Hz – Returning to Spiritual Order
Binaural Beats are a way of stimulating the brain waves of humans by creating two sine waves and spacing the frequencies of the two tones within the Hz range specified and panning them hard left and right to stimulate the brain function required, For my first piece I used the spacing of HZ as that number ties into the use of the number 6 in the talismanic square of the sun. This works at the theta range to stimulate imagination daydreaming, As Apollo the sun is the father of the muses and father of imagination this seemed correct. For the most part my decision making had been based on a type of intuition anyway which seems the right way using the tables and correspondences as an entry point to the work. I was talking with my friend who runs a childrens music based play group. She said if you could make a deep sleep track that works parents would flock to it. We also talked about how she had an African drummer in he would drum the kids who seemed angry before would start shaking and rocking to music and would be happy after, She expressed interest in testing the workd on children which would be interesting as Childrens ears are clean and they would be a blank slate without the musical cultural consitioning of adults. I should also look into rhythmic functions of music in my creation
▪ Beta (14 – 30 Hz) – This is our awake and active state of awareness. In Beta state, we have lots of energy as we get things done and are in our peak concentration mode. If we stay in this mode too much, it can be very stressful to our minds and bodies.
▪ Alpha (8 – 14 Hz) This is our awake but relaxed state of awareness. In this state we can figure out creative solutions to problems. Our mind is clear and able focus on a goal. When we watch top performing athletes, chess players or jazz musicians, they are drawing from their alpha state of awareness.
▪ Theta (4 – 8 Hz) This state is associated with imagining and dreaming during sleep as well as imagining and daydreaming during the day. Our memories and things we learn are stored and retrieved from our subconscious mind in this state.
▪ Delta (0.5 – 4 Hz) This state is associated with deep sleep. Our minds and bodies are getting the rest and rejuvenation we require before the new day begins.
▪ https://ask.audio/articles/how-sound-affects-you-making-binaural-beats
* please note I did not write the material below it was copied this website https://attunedvibrations.com/solfeggio/
Where do these tones come from?
According to Professor Willi Apel, the origin of the ancient Solfeggio scale can be traced back to a Medieval hymn to John the Baptist. The hymn has this peculiarity that the first six lines of the music commenced respectively on the first six successive notes of the scale, and thus the first syllable of each line was sung to a note one degree higher that the first syllable of the line that preceded it. Because the music held mathematic resonance, the original frequencies were capable of spiritually inspiring mankind to be more “god-kind”.
The original Solfeggio scale was developed by a Benedictine monk, Guido d’Arezzo
(c. 991 AD – c. 1050 AD). It was used by singers to learn chants and songs more easily. Today we know the Solfeggio scale as seven ascending notes assigned to the syllables Do-Re-Mi-Fa-So-La-Ti. The original scale was six ascending notes assigned to Ut-Re-Mi-Fa-Sol-La. The syllables for the scale were taken from a hymn to St. John the Baptist, UtQueant Laxis, written by Paulus Diaconus.
Guidod’Arezzo
In the mid-1970’s Dr. Joseph Puleo, a physician and America’s leading herbalist, found six electro-magnetic sound frequencies that corresponded to the syllables from the hymn to St. John the Baptist.
How were the frequencies discovered?
According to the documentation provided in “Healing Codes for the Biological Apocalypse“, Dr. Joseph Puleo was introduced, through an open vision, to the Pythagorean method of numeral reduction. Using this method, he discovered the pattern of six repeating codes in the Book of Numbers, Chapter 7, verses 12 through 83.
The Pythagorean method is a simple reduction method, used to turn big numbers into single digits. The values of all digits in the number are added up. When after the first addition the number still contains more than one digit,the process is repeated.Here’s an example:456 can be reduced to 4+5+6 = 15, and subsequently reduced to 1+5=6. So the number 456 reduces eventually to the single digit 6.
Pythagoras of Samos
Dr. Joseph Puleo found repetitions of a single issue or subject in the Book of Numbers. In Chapter 7, verse 12 he found a reference to the first day, the second day was mentioned in verse 18, the third day in verse 24, and so forth until the final reference in verse 78 which is speaking of the twelfth day.
The Pythagorean reduction of these verse numbers is:
Verse 12 = 1 + 2 = 3Verse 18 = 1 + 8 = 9Verse 24 = 2 + 4 = 6
Verse 30 = 3 + 0 = 3Verse 36 = 3 + 6 = 9Verse 42 = 4 + 2 = 6
…untilverse 78
Do you see the repetition of 396? This is the first frequency.
He found the next frequency by looking at verse 13, which is speaking of an offering. Six verses down, which is verse 19, the same offering or idea is repeated, six verses down at verse 25 there is another repeat, etc. Thus, by using the Pythagorean method of reduction, again he discovered a pattern. This pattern is 417. It is the second frequency. The rest of the frequencies were found using the same method.
The secret meanings of the ancient syllables
Each tone has its own unique potential
As you already know, the syllables used to denote the tones are: Ut, Re, Mi Fa, Sol, La. They were taken from the first stanza of the hymn to St. John the Baptist:
Ut queant laxis Resonare fibris
Mira gestorum Famuli tuorum
Solve polluti Labii reatum
Sancte Iohannes
Literal translation from Latin: “In order that the slaves might resonate (resound) the miracles (wonders) of your creations with loosened (expanded) vocal chords. Wash the guilt from (our) polluted lip. Saint John.”
In other words, so people could live together in peace and communicate in harmony about the miracle in their lives, and how God blessed them to produce this “magic”, people’s true unpolluted spiritual natures required revelation. The above text seems to suggest that Solfeggio notes open up a channel of communication with the Divine.
Each syllable was thoroughly studied by Dr. Puleo and other professional researchers. David Hulse, a sound therapy pioneer with over 40 years of experience, described the tones as the following:
UT – 396 Hz – turning grief into joy, liberating guilt & fear
RE – 417 Hz – undoing situations & facilitating change
MI – 528 Hz – transformation & miracles, repairing DNA
FA – 639 Hz – relationship, connecting with spiritual family
SOL – 741 Hz – expression/solutions, cleaning & solving
Another sun frequency-supposedly the frequency the sun vibrates at (interesting)
126.22 https://youtu.be/sv6fWTMSDAg
The Solfeggio Skein
Frequency Name
Angelic Scale
The 2nd Scale
The 3rd Scale
The 4th Scale
Universal Scale
The 6th Scale
Earthly Scale
Divine Scale
Natural Scale
Karmic Freqs
111
123
135
147
159
162
174
186
198
Remembering
222
234
246
258
261
273
285
297
219
Opening
333
345
357
369
372
384
396
318
321
Change
444
456
468
471
483
495
417
429
432
DNA related
555
567
579
582
594
516
528
531
543
Connection
666
678
681
693
615
627
639
642
654
Awareness
777
789
792
714
726
738
741
753
765
Spiritual Journey
888
891
813
825
837
849
852
864
876
Unity
999
912
924
936
948
951
963
975
987
The Masculine/Metatron Solfeggio Skein
Subset Name
Angelic Scale
The 2nd Scale
The 3rd Scale
The 4th Scale
Universal Scale
The 6th Scale
Earthly Scale
Divine Scale
Natural Scale
Karmic Freqs
111
123
135
147
159
162
174
186
198
Remembering
222
234
246
258
261
273
285
297
219
Change
444
456
468
471
483
495
417
429
432
Connection
666
678
681
693
615
627
639
642
654
Unity
999
912
924
936
948
951
963
975
987
Fractal Tone
1011
1023
1035
1047
1059
1062
1074
1086
1098
Harmonic Tone
1455
1428
1482
1455
1428
1482
1455
1428
1482
http://islandrepublicofdan.blogspot.com.au/2013/05/solfeggio-frequencies-and-gregorian.html
https://youtu.be/sv6fWTMSDAg
741hz
Tune to 416hz
Keyboard – play a G5, Guitar – play a G as follows:
B string 20th fret
E string 15th fret
(Actual frequency reached – 741.23hz)
(Closest you can get on guitar is to tune to 415.9hz which will give you 741.05hz)
Appropriate keys
G Major, D Major, A Major, E Major, B Major, F# Major,
E Minor, B Minor, F# Minor, C# Minor, G# Minor, D# Minor
741hz exact
If you can tune to 370.5hz you can get it exactly:
Keyboard – play a A5, Guitar – play an A as follows:
E string 17th fret
B string 10th fret
Appropriate keys
C Major, G Major, D Major, A Major, E Major, Bb Major, F Major
A Minor, E Minor, B Minor, F# Minor, C# Minor, G Minor, D Minor
If you can tune to 440.6hz you can also get it exactly:
Keyboard – play an F#5, Guitar – play an F# as follows:
E string 14th fret
B string 19th fret
Appropriate keys
C# Major, G# Major, D# Major, A# Major, B Major, F Major
Bb Minor, C Minor, F# Minor, C# Minor, G# Minor, D# Minor
If you can tune to 466.8hz you can also get it exactly:
Keyboard – play an F5, Guitar – play an F as follows:
E string 13th fret
B string 18th fret
Appropriate keys
B Major, F# Major, C# Major, Ab Major, Eb Major, F Major
Eb Minor, B Minor, F Minor, C Minor, G Minor, D Minor
https://propheticguitar.com/solfeggio/
…………………………………………………………………………………………………….
0 notes
Text
PSYC343 Week 8 Final Exam
Click Link Below To Buy:
http://hwaid.com/shop/psyc343-week-8-final-exam/
PSYC343 Adult Development
Question 1 of 50 2.0/ 2.0 Points
Those who study adult development theorize that ________.
A.Reserve capacity remains the same throughout adulthood.
B.There is no plasticity in how an individual develops.
C.All age periods of development are equally important.
D.None of the above.
Question 2 of 50 2.0/ 2.0 Points
Paradigms of aging are distinguishable from theories because paradigms ______.
A.are not directly testable
B.are taken out of context
C.are not as respected as theories
D.are too mechanistic
Question 3 of 50 2.0/ 2.0 Points
Which of the following would be an example of ageism?
A.Hiring a 65 year old consultant because of his wealth of experiences dealing with a variety of clients.
B.A teenager offering to help an older couple load their groceries into their car.
C.Offering an employee the opportunity to retire with benefits once s/he reaches a certain age.
D.A doctor allowing less time per appointment for patients over a certain age.
Question 4 of 50 2.0/ 2.0 Points
Is the following statement true or false?
"Worldwide, the number of persons age 65 and over is increasing."
Question 5 of 50 2.0/ 2.0 Points
In 1997, Riley suggested that social dimensions of aging are best understood using a conceptual framework that emphasizes ________.
A.A social paradigm
B.Age integration
C.Filial piety
D.Androgyny
Question 6 of 50 2.0/ 2.0 Points
Which examines age-related changes between individuals?
A.ontogeny
B.intraindividual difference
C.developmental psychology
D.longitudinal differences
Question 7 of 50 2.0/ 2.0 Points
The idea that intraindividual differences occur in patterns of aging is known as _____.
A.social age
B.multidirectionality
C.reversibility of change
D.age graded opportunity structure
Question 8 of 50 2.0/ 2.0 Points
_____ is a disease that involves significant losses in bone calcium and increased bone brittleness.
A.osteopenia
B.presbycusis
C.osteoperosis
D.reticular activation
Question 9 of 50 2.0/ 2.0 Points
_____ refers to the disruption in expected routine and lifestyle.
A.Subjective caregiver burden
B.Daily hassles
C.Socio-emotional selectivity
D.Objective caregiver burden
Question 10 of 50 2.0/ 2.0 Points
Senescence means ______.
A.premature aging
B.normal aging
C.pathological aging
D.none of the above
Question 11 of 50 2.0/ 2.0 Points
Which of the following is the best supported account of biological aging at the cellular levele?
A.genetic mutation theory
B.free radical theory
C.genetic switching theory
D.none of the above
Question 12 of 50 2.0/ 2.0 Points
_____ refers to handling stressful situations by using resources available in the environment.
A.problem-focused coping
B.primary appraisal
C.secondary appraisal
D.emotion-focused coping
Question 13 of 50 2.0/ 2.0 Points
After Alzheimer's Disease, which condition comes in second (accounting for 20%) of the cases of dementia?
A.Lewy Body Dementia
B.Mixed dementia
C.Creutzfeldt-Jakob Disease
D.Parkinson's Disease
Question 14 of 50 2.0/ 2.0 Points
_____ affects a person's allostatic load.
A.biological functioning
B.cognitive processes
C.both biological functioning and cognitive processes
D.none of the above
Question 15 of 50 2.0/ 2.0 Points
According to data compiled by Kessier et. al., the prevalence of mental disorders in adults is highest among which group?
A.both men and women over 65 years old
B.both men and women between 20 to 30 years old
C.both men and women between the ages of 45 to 64 years old
D.none of the above
Question 16 of 50 2.0/ 2.0 Points
The biggest risk factors for suicide are _____ and _____.
A.being female and Asian
B.being a male and over the age of 25
C.being an older adult and male
D.none of the above
Question 17 of 50 2.0/ 2.0 Points
_____ is known to diminish with age, but _____ tends to improve duirng the adult years.
A.emotional stability - general cognitive processing
B.general cognitive processing - physical stamina
C.reserve capacity - emotional resources
D.physical stamina - reserve resources
Question 18 of 50 2.0/ 2.0 Points
The _____ model describes the relationship between stressful life events and a person's vulnerability as an explanation of the occurrence of mental illness
A.depletion
B.diathesis-stress
C.stress buffering
D.tension-reduction
Question 19 of 50 2.0/ 2.0 Points
Is the following statement true or false?
"Mortality rates have declined in general in recent decades."
Question 20 of 50 2.0/ 2.0 Points
Social support can provide _____ in older adults.
A.better coping skills
B.stress buffering
C.help with financial resources
D.none of the above
Question 21 of 50 2.0/ 2.0 Points
Which of the following contributes to an increased risk of falling in older adults?
A.sarcopenia
B.changes in sensory/perceptual systems
C.the actual fear of falling
D.all of the above
Question 22 of 50 2.0/ 2.0 Points
_____ involves retrieval of contextual information and is substantially impaired with aging.
A.recollection
B.familiarity
C.both recollection and familiarity
D.semantic memory
Question 23 of 50 0.0/ 2.0 Points
Which factor related to developmental changes in intelligence is linked to chronic illness?
A.cohort effects
B.selective dropout
C.terminal drop
D.sensory acuity
Question 24 of 50 2.0/ 2.0 Points
Non-demented individuals are more likely to experience _____ memory deficits than _____ memory deficits.
A.apparent, genuine
B.contextual, information processing
C.pathological, pre-clinical
D.neurological, age-associated impairment
Question 25 of 50 2.0/ 2.0 Points
Which of the following is characterized by the ability to solve novel problems, yet declines with age?
A.convergent thinking
B.fluid intelligence
C.chrystallized intelligence
D.primary mental abilities
Question 26 of 50 2.0/ 2.0 Points
Is the following statement true or false?
"Cross sectional studies tend to paint a more pessismistic picture of adult intellectual change that do longitudinal studies in large part due to the g factor.
Question 27 of 50 2.0/ 2.0 Points
Which is most likely to show an age-related "typical pattern of decline across all primary mental abilities", including intelligence?
A.a cross-sectional study
B.a longitudinal study
C.a sequential research design
D.none of the above
Question 28 of 50 2.0/ 2.0 Points
The ability to reexperience nuances of your first airplane trip, such as what you saw and felt while on the plane is an example of which type of memory?
A.source
B.declarative
C.semantic
D.episodic
Question 29 of 50 2.0/ 2.0 Points
Which of the following tends to be unimpaired by aging?
A.information processing
B.thinking
C.knowing
D.both thinking and knowing
Question 30 of 50 2.0/ 2.0 Points
According to Baltes research there is an increase in _____ from middle age to old age.
A.elective selection
B.compensation
C.loss-based selection
D.optimization
Question 31 of 50 2.0/ 2.0 Points
The term (phrase) _____ is used in successful aging models to mean using a new strategy or technique to adapt to a life task when a long-used ability is lost or falls below the critical level.
A.age-by-age-experience paradigm
B.fluid mechanics
C.selective optimization with compensation
D.postformal thinking
Question 32 of 50 2.0/ 2.0 Points
Stage theories of development (such as Erikson's theory of psychosocial development) have been criticized because:
A.they are difficult to empirically verify
B.they overlook cultural differences
C.they are difficult to empirically verify, and they overlook cultural differences
D.none of the above
Question 33 of 50 2.0/ 2.0 Points
Is the following statement true of false?
"With enough practice, some skills can become automatic and are then less susceptible to age-related decrements."
Question 34 of 50 2.0/ 2.0 Points
An elderly person may be more prone to being swindled by a fast-talking con artist because of _____.
A.the positivity effect
B.tendencies toward emotional regulation
C.decreases in deliberative processing
D.the negativity effect
Question 35 of 50 2.0/ 2.0 Points
According to the Staudinger study older adults seem to perform better on _____ than younger adults.
A.fluid related tasks
B.mechanics of the mind
C.wisdom related tasks
D.none of the above
Question 36 of 50 2.0/ 2.0 Points
Stress cardiomyopathy is also known as _____.
A.a heart attack
B.a stroke
C.arterial blockage
D.a broken heart
Question 37 of 50 2.0/ 2.0 Points
Is the following statement true or false?
"Women report greater marital satisfaction than men."
Question 38 of 50 2.0/ 2.0 Points
As love relationships mature, _____ becomes increasingly important.
A.passion
B.intimacy
C.caring
D.all of the above
Question 39 of 50 2.0/ 2.0 Points
When adult children begin to interact with their parent as one adult to another this is called _____.
A.role meaning
B.role satisfaction
C.role behavior
D.filial maturity
Question 40 of 50 2.0/ 2.0 Points
The majority of employees will experience _____ career changes in their lifetime.
A.3-4
B.2-5
C.5-8
D.none because choosing a career is a one time choice
Question 41 of 50 2.0/ 2.0 Points
Which of the following is NOT a reason that older adults work during retirement?
A.desire to stay active
B.to interact with people
C.to earn needed income
D.concerns about potential loss of spouse
Question 42 of 50 2.0/ 2.0 Points
Which of the following is a benefit to doing volunteer work after retirement?
A.improved physical health
B.social support
C.enhanced self-esteem
D.all of the above
Question 43 of 50 2.0/ 2.0 Points
Studies have found that roughly _____ percent of people between 60 and 71 years of age regularly engage in sexual intercourse, and _____ percent of those over 78 do so.
A.25; 10
B.50;15
C.60;20
D.35;5
Question 44 of 50 2.0/ 2.0 Points
A living will does which of the following?
A.It ensures the right of an individual to choose whether heroic measures will be used to sustain his or her life.
B.It establishes a contract between the person, the medical community, and close relatives.
C.It allows a person to declare his or her choice of under what circumstances life sustaining treatments should be provided.
D.all of the above
Question 45 of 50 2.0/ 2.0 Points
According to the developmental view of death, at what age do children hold both a biological and spiritual or religious view of death?
A.11 or 12
B.7 or 8
C.5 to 6
D.12 to 13
Question 46 of 50 2.0/ 2.0 Points
Kastenbaum (1981) suggested that the cumulative effects of having to cope with the deaths of friends and relatives in a short time span can cause the elderly to experience _____.
A.physical health related problems
B.cognitive decline
C.bereavement overload
D.all of the above
Question 47 of 50 2.0/ 2.0 Points
According to Kubler-Ross's theory it is in the _____ stage that individuals try to psychologically delay death.
A.anger
B.bargaining
C.depression
D.acceptance
Question 48 of 50 2.0/ 2.0 Points
Which of the following may contribute to a person's social death long before his or her physical death?
A.isolation, distancing, noncommunication
B.emotional abandonment by close family
C.lack of timely information from personal physician
D.none of the above
Question 49 of 50 2.0/ 2.0 Points
Treatment that is delivered in nursing homes, hospitals or homes, and is designed to enhance comfort and improve the quality of an individual's life during the last phase of life is called _____.
A.palliative care
B.hospice care
C.square of care
D.none of the above
Question 50 of 50 2.0/ 2.0 Points
Is the following statement true or false?
"Older women are more likely to outlive their husbands."
0 notes
Text
youtube
What Are the Different Types of Piracy
Piracy is bad, all of us know that. Downloading pirated applications from the Internet, is just like stealing something from a shop. We know that also. Shops suffer great loses anti piracy protection because of theft, in order software creators. The most important distinction is, the first ones, do not attempt to minimize their loses, at the cost of the customers.It's been quite some time since software companies began to execute in their applications, anti-piracy mechanics. It is clear as everybody would want to secure their work, from being stolen, altered or used without permission. The question is, just how far can you go with this?
It began with simple serial numbers or typing in a particular world from newspaper manual shipped with the software. A bit time-consuming, but it functioned. So long as you'd the installation disk and guide, an individual could easily install, re-install the program a dozen times a day, without needing to explain the reason why. But as the online popularity grew, it opened new possibilities of software protection -- activation providers. The mechanism is pretty simple: purchase applications, enter specific product key, validate it via Web and you're ready to go. Simple? Not really...
Few individuals know, that most companies established a limitation of feasible activations per serial number. anti-counterfeiting trade agreement (acta) explained Why? In theory, because each licence is valid only for X amount of computers. So to ensure, that we do not share ours with all our Facebook friends, a limit is present. The catch is, if we choose to format our hard disk and do an original system setup, all software that need reactivation, will treat like a fresh one, and so the counter will go up 1. Now imagine what could happen, in case your hard disk breaks down.
You send it to a service. It is returned, you re-install all, but after a month the problem returns. acta wikipedia Again and again. When eventually the faulty component gets replaced correctly, another attempt of reactivating your favourite software becomes rejected. Why? Because limitation of feasible activations has been attained.

What can you do? Call support center and ask to allow one, to activate your software. Almost always the answer is positive, but... I own the Onsist software, so why so I need to ask for permission to use it? I understand my peace is legal, I have my bill, cd, manual, serial number.
I don't need to validate the software further. I just want to use my applications. Some may say, that such scenarios are rare and it is likely true. Still this case, makes one wonder, even when the anti-piracy forces are moving in right way. If this persists, we might be facing a critical problem: the number of viruses, malicious applications increases nearly exponentially, making the need for regular software updates quite urgent.
Regular upgrading makes the OS run slower, as a single version installed over old, does not always run as easy as a fresh install. That's why we replicate our driveway C and then set up everything from scratch... and activate our applications successfully. This time. Next time, we may start to think, that it is better to use free options instead. They might not be as strong as their industrial counterparts, but at least they do not care why we reinstall or install them.
To put it simple: they don't ask a lot of questions and that's something the majority of us want -- privacy. Privacy restricted by the anti-piracy campaigns. check my reference Time will tell whether these practices, have no impact on piracy levels worldwide. For now, it made our lives a bit harder, than previously.
Computer piracy is far different than sea piracy. Instead Of plundering and assaulting the industrial ships in the middle of the ocean, computer pirates generally steal intellectual property and then, finally, give it away for public use. This can possibly destroy the individual or business and there are a number of cases to back up that.
Piracy is rampant in wikipedia here gambling sector
Computer game companies are among the mostly diminished sectors by pirates. With the assistance of skilled developers, pirates crack the code of this sport that stores information Onsist copy protection removal about individual copies. To put it differently, you do not need to visit the shop to buy a game - you can just download it at no cost from a pirate server.
Pirate software has its flaws. Many online programs are practically not crack-able, because your ID is verified on a company server, and pirates have no access on the market. Standalone cracked software is with a code that is altered and is susceptible to malfunction and can really damage your computer, let alone not operate correctly. Official licensed software ensures that it can find the job done and is bug free - something pirates provide no absolute guarantee. They simply don't care, since, after all, in case you enjoy the software, you will likely buy it yourself.
Necessity and types of software piracy defense
To fight with this situation software companies have created software piracy protection program. The software piracy protection comes in several forms in line with the functions. Some DVDs are made so that the game only runs if a certified DVD is existing in your CD-ROM drive. Other need a serial number along with security software on the actual DVD you purchased.
Pirates are usually very good developers who look forward to be appreciated in big businesses and so increase their popularity and income. Others do it for fun and anticipate no sensible gain from it. They are driven by the sole feeling of evil doing.
There are many notorious groups of crackers-pirates who decode virtually every game that comes out and significantly decrease actual incomes of the companies-producers and developers. The multimillion industry of amusement is continuing to suffer from heavy losses because of piracy and this is soon likely to change as new anti piracy laws are getting implemented.
In this highly technological age, practically every aspect of big company is paperless. Though this development has significantly simplified the process of conducting business, it has also left businesses vulnerable to IC piracy attacks. Actually, intellectual theft costs American businesses billions of dollars in losses each and each year. 1 solution that technology teams must think about is using OTP (one-time-programmable) memory for their microchip devices rather. Below are a few reasons why.
--Though the technology is not new (it was initially developed in 1969), it's certainly reliable; and its capabilities have certainly been refined and improved through the years. It is virtually problem-free.
--It is comparatively inexpensive. It's not uncommon for organizations to spend to the hundreds of thousands of dollars to get additional anti-piracy options, but OTP memory is easy to install and use in a mere fraction of the price.
--The arbitrary number system used by OTP memory permits the user to generate an identification number from a massive pool of possibilities. It is virtually impossible for pirates to discover a particular number when there are literally billions of possible combinations.

--A system with OTP may be adjusted to match any specific taste or application. As an example, it may be set to permit certain identification numbers to be retrieved only by authorized personnel.
--It's a system That's remarkably simple, yet powerfully effective.
In these difficult financial times, companies need to find anti-piracy methods that actually work and that Onsist are also cost-effective: OTP memory might be the IC protection solution you have been looking for.
Every writer will be pleased to acquire anti piracy software which may ably protect PDF documents, swf flash content and html content. Fortunately, DRM - digital rights management programs are readily available to address these needs and also to provide the required controls to satisfactorily execute data loss protection (DLP). These programs allow the author to enroll marketing monitoring definition a client using a licensing platform, pick the ideal customer access degree, produce customized messages to inform unauthorized customers that they do not have permission to start protected files and also to provide them details about where to source for the consent, and to establish expiry dates and exhibit a web page that confirms the expiry of the protected file.
Using DRM document control software the document writer can implement a watermark capability where the user's name and/or company name, and specifics of date/time of usage are displayed on all the printouts. Additional on antipiracy observation, we can even have PDF software that has the capability to demonstrate document and user statics, auditing and reporting.
Through the watermarking capacity DRM will help to identify the place where the leak happened. Additionally, it reports when the record was utilized and equips the writer with document control abilities to close off file access if abuse is detected. This is a useful anti piracy measure which prevents people from replicating or even altering your work as this normally contributes to the misinterpretation of their planned message. Data loss prevention is also employed by requiring users to look at the document with a proprietary program rather different from the one which created it. This way, only authorized users can view the document and record processing tools can be disabled.
Data reduction prevention is all about forestalling the dripping out of a document/s beyond the control of the organization that possesses it. In nature this anti piracy method is all about identifying, monitoring and shielding, and this is accomplished by shielding a record's content Onsist Social Profile and context via a filtering and centralized management system. This record control method helps efforts to automate the recognition of instances when the content contravenes set DRM rules, and also prevents documents from being emailed or duplicated to say a flash drive.
A company will always find itself being required to share its own confidential information with offshore staff as well as lawyers all of whom are external to the organization's firewalls and this makes anti piracy solutions all the more crucial. As such, in a bid to stem piracy, data loss protection techniques have to be able to secure protected files once they're in the hands of external but approved parties. Encryption has always been the Reply to document
Control but it only goes up to stopping unauthorized persons from accessing the protected data. But, it does not control what the authorized user can do with the record once it is decrypted. Nonetheless, we could always combine encryption with DRM controls so as to restrict the ability of these users to discuss or pass onto the limited information.
Attack Profiles
Successful attacks on vessels, where asset protection is minimum, follow common vulnerabilities, which are exploited by pirates. These are as follows:
Low rate - (under dvd authoring software with copy protection 16 knots)
Low freeboard - (distance from the waterline to the freeboard deck of a fully loaded ship)
Insufficient preparation and implementation of processes
Alert of crew on board is Low or there is no visual evidence of self-protection steps
Where There's a slow reaction by the boat and crew
Generally the pirates will utilize a couple of small boats capable of speeds in excess of 20 knots, these are available click over here crafts typically called "skiffs" plus they normally approach the intended target from the port quarter or stern.
The usage of a mother ship is employed as a portable logistics foundation that conveys the equipment and personnel to allow attacks to happen farther out to sea, some attacks have happened at 600 NM off the shore.
The majority of attacks will happen at first and last light, so in these times extra vigilance is necessary.
Before the Transit
Prior to a transit, These bodies should be informed and include;
The Maritime Security Centre - Horn of Africa (MSCHOA), That's the preparation and coordination authority for EU Forces in the Gulf of Aden and the area from the Coast of Somalia and the United Kingdom Maritime Trade Operations (UKMTO), which will be in Dubai and is the primary point of contact for boats in the region. The daily interface with Masters and the military is the UKMTO.
Before devoting high-risk locations, the owner and Master must carry out their own risk assessments to evaluate the likelihood of an attack by pirates. The results of the risk assessment must identify steps to be taken to protect against the vessel being accepted by pirates.
Company Crisis Management Procedures and steps to fulfill the threat within the region the vessel is transiting, should be addressed.
In order to best prepare a vessel, the next planning and training should be considered as a minimum, to control risks from assault:
Register the boat with the authorities, UKMTO and MSCHOA
Review the boats https://onsist.com safety plan
Carry out crew anti-piracy and safety awareness training
Appoint security consultants for your own transit, who have global marine safety experience
Make Sure You have a good and effective anti-piracy contingency program
Defensive Measures
The vessel should review its safety measures and procedures and consider:
Ensuring that the vessels routines are adjusted in advance to Make Sure that the team are well rested before they enter the high risk area
Watching radio silence or allowing minimal use of radio equipment
Identify a safe room
Securing access to the bridge, engine room and crew cottages
Provision of night vision device(s) to get watch employees
During the Transit
Masters should use the International Recommended Transit Corridor (IRTC). This is recommended by the naval authorities, westbound vessels use the northern portion of the corridor along with the eastbound vessels utilize the southern part of the IRTC.
Vessels should remain within the IRTC constantly and make sure that it keeps up with its set transit. The vessel should comply with international rules on light.
MSCHOA will counsel on the group transport timings which depart at different times and are recognized by the speed Onsist of the boat, so if a boat has a maximum speed of 16 knots it should consider joining a 14 knot group transit.
If you have employed a safety company, they are there for advice and guidance and should also install the procedures and measures for each vessel as suitable. But, vessels should still make sure that they have added crew as lookouts at exposed parts of the boat especially on the rear port quarter.
It is paramount that a boat protects the team from risk; this usually means that only essential crew work ought to be conducted on the deck whilst at the high-risk areas.
0 notes