#adversarial interop
Explore tagged Tumblr posts
Text
An adversarial iMessage client for Android
Adversarial interoperability is one of the most reliable ways to protect tech users from predatory corporations: that's when a technologist reverse-engineers an existing product to reconfigure or mod it (interoperability) in ways its users like, but which its manufacturer objects to (adversarial):
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
"Adversarial interop" is a mouthful, so at EFF, we coined the term "competitive compatibility," or comcom, which is a lot easier to say and to spell.
Scratch any tech success and you'll find a comcom story. After all, when a company turns its screws on its users, it's good business to offer an aftermarket mod that loosens them again. HP's $10,000/gallon inkjet ink is like a bat-signal for third-party ink companies. When Mercedes announces that it's going to sell you access to your car's accelerator pedal as a subscription service, that's like an engraved invitation to clever independent mechanics who'll charge you a single fee to permanently unlock that "feature":
https://www.techdirt.com/2023/12/05/carmakers-push-forward-with-plans-to-make-basic-features-subscription-services-despite-widespread-backlash/
Comcom saved giant tech companies like Apple. Microsoft tried to kill the Mac by rolling out a truly cursèd version of MS Office for MacOS. Mac users (5% of the market) who tried to send Word, Excel or Powerpoint files to Windows users (95% of the market) were stymied: their files wouldn't open, or they'd go corrupt. Tech managers like me started throwing the graphic designer's Mac and replacing it with a Windows box with a big graphics card and Windows versions of Adobe's tools.
Comcom saved Apple's bacon. Apple reverse-engineered MS's flagship software suite and made a comcom version, iWork, whose Pages, Numbers and Keynote could flawlessly read and write MS's Word, Excel and Powerpoint files:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
It's tempting to think of iWork as benefiting Apple users, and certainly the people who installed and used it benefited from it. But Windows users also benefited from iWork. The existence of iWork meant that Windows users could seamlessly collaborate on and share files with their Mac colleagues. IWork didn't just add a new feature to the Mac ("read and write files that originated with Windows users") – it also added a feature to Windows: "collaborate with Mac users."
Every pirate wants to be an admiral. Though comcom rescued Apple from a monopolist's sneaky attempt to drive it out of business, Apple – now a three trillion dollar company – has repeatedly attacked comcom when it was applied to Apple's products. When Apple did comcom, that was progress. When someone does comcom to Apple, that's piracy.
Apple has many tools at its disposal that Microsoft lacked in the early 2000s. Radical new interpretations of existing copyright, contract, patent and trademark law allows Apple – and other tech giants – to threaten rivals who engage in comcom with both criminal and civil penalties. That's right, you can go to prison for comcom these days. No wonder Jay Freeman calls this "felony contempt of business model":
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Take iMessage, Apple's end-to-end encrypted (E2EE) instant messaging tool. Apple customers can use iMessage to send each other private messages that can't be read or altered by third parties – not cops, not crooks, not even Apple. That's important, because when private messaging systems get hacked, bad things happen:
https://en.wikipedia.org/wiki/2014_celebrity_nude_photo_leak
But Apple has steadfastly refused to offer an iMessage app for non-Apple systems. If you're an Apple customer holding a sensitive discussion with an Android user, Apple refuses to offer you a tool to maintain your privacy. Those messages are sent "in the clear," over the 38-year-old SMS protocol, which is trivial to spy on and disrupt.
Apple sacrifices its users' security and integrity in the hopes that they will put pressure on their friends to move into Apple's walled garden. As CEO Tim Cook told a reporter: if you want to have secure communications with your mother, buy her an iPhone:
https://finance.yahoo.com/news/tim-cook-says-buy-mom-210347694.html
Last September, a 16-year old high school student calling himself JJTech published a technical teardown of iMessage, showing how any device could send and receive encrypted messages with iMessage users, even without an Apple ID:
https://jjtech.dev/reverse-engineering/imessage-explained/
JJTech even published code to do this, in an open source library called Pypush:
https://github.com/JJTech0130/pypush
In the weeks since, Beeper has been working to productize JJTech's code, and this week, they announced Beeper Mini, an Android-based iMessage client that is end-to-end encrypted:
https://beeper.notion.site/How-Beeper-Mini-Works-966cb11019f8444f90baa314d2f43a54
Beeper is known for a multiprotocol chat client built on Matrix, allowing you to manage several kinds of chat from a single app. These multiprotocol chats have been around forever. Indeed, iMessage started out as one – when it was called "iChat," it supported Google Talk and Jabber, another multiprotocol tool. Other tools like Pidgin have kept the flame alive for decades, and have millions of devoted users:
https://www.eff.org/deeplinks/2021/07/tower-babel-how-public-interest-internet-trying-save-messaging-and-banish-big
But iMessage support has remained elusive. Last month, Nothing launched Sunchoice, a disastrous attempt to bring iMessage to Android, which used Macs in a data-center to intercept and forward messages to Android users, breaking E2EE and introducing massive surveillance risks:
https://www.theverge.com/2023/11/21/23970740/sunbird-imessage-app-shut-down-privacy-nothing-chats-phone-2
Beeper Mini does not have these defects. The system encrypts and decrypts messages on the Android device itself, and directly communicates with Apple's servers. It gathers some telemetry for debugging, and this can be turned off in preferences. It sends a single SMS to Apple's servers during setup, which changes your device's bubble from green to blue, so that Apple users now correctly see your device as a secure endpoint for iMessage communications.
Beeper Mini is now available in Google Play:
https://play.google.com/store/apps/details?id=com.beeper.ima&hl=en_US
Now, this is a high-stakes business. Apple has a long history of threatening companies like Beeper over conduct like this. And Google has a long history deferring to those threats – as it did with OG App, a superior third-party Instagram app that it summarily yanked after Meta complained:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
But while iMessage for Android is good for Android users, it's also very good for Apple customers, who can now get the privacy and security guarantees of iMessage for all their contacts, not just the ones who bought the same kind of phone as they did. The stakes for communications breaches have never been higher, and antitrust scrutiny on Big Tech companies has never been so intense.
Apple recently announced that it would add RCS support to iOS devices (RCS is a secure successor to SMS):
https://9to5mac.com/2023/11/16/apple-rcs-coming-to-iphone/
Early word from developers suggests that this support will have all kinds of boobytraps. That's par for the course with Apple, who love to announce splashy reversals of their worst policies – like their opposition to right to repair – while finding sneaky ways to go on abusing its customers:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
The ball is in Apple's court, and, to a lesser extent, in Google's. As part of the mobile duopoly, Google has joined with Apple in facilitating the removal of comcom tools from its app store. But Google has also spent millions on an ad campaign shaming Apple for exposing its users to privacy risks when talking to Android users:
https://www.theverge.com/2023/9/21/23883609/google-rcs-message-apple-iphone-ipager-ad
While we all wait for the other shoe to drop, Android users can get set up on Beeper Mini, and technologists can kick the tires on its code libraries and privacy guarantees.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/12/07/blue-bubbles-for-all/#never-underestimate-the-determination-of-a-kid-who-is-time-rich-and-cash-poor
#pluralistic#multiprotocol#interoperability#adversarial interop#beeper#reverse engineering#blue bubbles#green bubbles#e2ee#end to end encrypted#messaging#jjtech#pypushbeeper mini#matrix#competitive compatibility#comcom
1K notes
·
View notes
Text
I will say, as funny as the schadenfreude of Facebook going down is, you really need to contact your Congresspeople and tell them, “Please for the love of god don't kill Section 230 due to this, just expand antitrust and adversarial interoperability”
Cause, like, a lot of politicians are really going horny for “Kill Section 230″ as a solution to the problem of Facebook and the other tech monopolists, and they’re giving all indications they’re going to go even harder on it now, when in fact it would simply make the social media monopolies more powerful (By creating regulations basically nobody but them could abide by) and basically fuck over all our abilities to post.
Like, remember the time we did do a carve-out of Section 230 with FOSTA/SESTA, it basically fucked over everyone while fixing absolutely nothing?
All who survived the Tumblr Horny Purge are probably painfully aware, of course. And it’d probably end up even worse considering how the legislation they’re proposing is basically tailor-made to fuck over, amongst others; any and all artists who relys on commissions to make a living.
We don’t need a “better” Facebook/Twitter/Google at everyone else’s expense, we need them broken up into tiny pieces, and that’s what antitrust and adversarial-interop would be best to do.
But, I’m scared if we don’t do something, pre-emptively and continually, that the way the wind’s gonna blow is gonna be the worst-case scenario...
551 notes
·
View notes
Text
The Year in Security: Adversarial AI and the Rush to the Cloud
The Year in Security: Adversarial AI and the Rush to the Cloud
Interop keynoter Gunter Ollmann, Microsoft’s cloud and AI security leader, shares insights on 2020’s instant pivot to the cloud, the state of adversarial AI, and how top organizations can stop attackers.

Image: jirsak – stock.adobe.com
A global pandemic and its impact on the way we work and live served as a catalyst for enterprise digital transformation in 2020. The enterprise did two years’…
View On WordPress
0 notes
Text
Get New Ip Address

Buy premium private proxies with New IP Now. Choose among 20+ locations, get started in minutes, and refresh IPs at any time. The public IP address is dynamically assigned by Verizon. The only way to change it is to call support and ask them to release your address. But there is no chance you will get a new address. Other folks on here have indicated you can release the address and then request a new address. Then again no chance you will get a new address, just a.
Change Ip Address For Free Online
How To Find Ip Address On Computer
Get New Ip Address Cox
Get New Ip Address Free
Tailscale needed a better IP address type
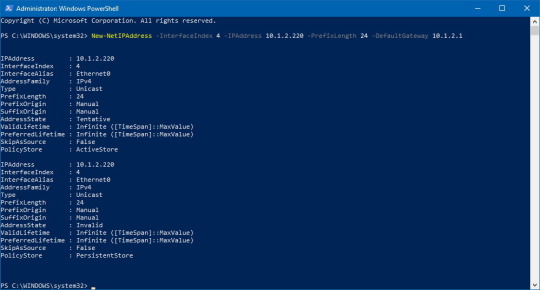
Tailscale is a networking application so naturally we need to work withand manipulate IP addresses and sets of IP addresses often.
Being written almost entirely in Go, the obvious choice would be forTailscale to use the Go standard library’snet.IP address type for individualIPs and net.IPNet type fornetworks. Unfortunately, the standard library’s types have a number ofproblems, so we wrote a new package,inet.af/netaddr (github) containinga new IP type and more.
What’s wrong with Go’s net.IP type?
When I was working on Go full time, I filed Go issue#18804 to track somethings that aren’t great about Go’s IP address:
It’s mutable. The underlyingtype of a net.IP is just a()byte, which means anything you pass it to might mutateit. Immutable data structures are safer, easier to reason about, anddon’t require defensive copies.
It’s notcomparablebecause a slice in Go is not comparable, which means it doesn’tsupport Go’s operator and can’t be used as a map key.
There are two IP address types in the standard library: net.IP for justa basic IPv4 or IPv6 address, and then alsonet.IPAddr if you need to supportIPv6 zone scopes.Having two types in the standard library means youneed to decide which type to accept or return from your code, orhave two+ variants, which gets annoying (e.g. Go’s Resolver.LookupIPvs Resolver.LookupIPAddr)
It’s large. A Go slice is 3 words (so 24 bytes total on 64-bitmachines) just for the slice header, without counting the underlyingarray that the slice points to (background).So an IP address with Go’s net.IP istwo parts: the 24 byte slice header, and then also the 4 or 16 bytesof IP address. If you want an IPv6 zone, you have to use net.IPAddr witha 16 byte string header also.
It allocates, #43451. Go’s net package is full of allocations everywhere,putting more work on the GC and thus the CPU. If you callnet.ParseIP or receive a UDP packet, it needs to allocate theunderlying array where it records the IP address, to put thatpointer in the returned slice header of the net.IP.
When parsing an IP from its string form, Go’s IP type can’tdistinguish betweenIPv4-mapped IPv6addressesand IPv4 addresses. The Go IP type doesn’t record the original address family.This is tracked in Go issue #37921.
It’s a transparent type. The definition of net.IP is: type IP ()byte,which means its underlying type is a byte slice,which is part of its public API and unchangeable. By contrast, Go’stime.Time type is defined like type Time struct ( /* unexported */ )so it’s free to change without breaking API promises. In fact, Go’s Time did changeits representation recently in Go 1.9 when it gainedtransparent monotonic time support.That would not have been possible if the type weren’t opaque.As some trivia: the Go Timeused to be transparent prior to Go 1.Unfortunately we weren’t wise enough at the time to do the samefor the IP address type.
Some of this was by design at the time, before Go 1 locked in thecompatibility promise in 2012, butmuch of it was just never considered well or predated enoughexperience with Go to learn what patterns worked well and whichdidn’t. In any case, the Go standard library can’t change much now.
What do we want?
In summary, this is what we want, and how Go’s net.IP fares:
FeatureGo's net.IPImmutable❌, sliceComparable❌, sliceSmall❌, 28-56 bytesAllocation free❌, slice's underlying arraySupports IPv4 & IPv6✅Can distinguish IPv4/IPv6❌, #37921Supports IPv6 zones❌, has separate net.IPAddr typeOpaque type❌, defined as ()byteInterops with standard library✅
So, let’s do better.
This story has several parts:
Take 1: wgcfg.IP
The story begins in April 2019 with89476f8cb5 in which David Crawshaw, aware of all these problems,created an IP type like:
That’s a bit better:
Featurenet.IPwgcfg.IPImmutable❌, slice✅Comparable❌, slice✅Small❌, 28-56B✅, 16BAllocation free❌✅Supports IPv4 & IPv6✅✅Can distinguish IPv4/IPv6❌❌Supports IPv6 zones❌❌Opaque type❌❌Interops with standard library✅❌, with adapters
We used that for quite a bit in some places but it wasn’t quite good enough tostart using more widely.
Making it opaque would be easy enough (unexporting the Addr field, renaming it to addr), butthat still would leave us with the lost address family bit and lackof IPv6 zones.
Take 2: netaddr.IP, opaque comparable interfaces
One bit about the Go language specification that many people don’t know isis that interfaces are comparable (support & being map keys),but they panic at runtime if theunderlying value in the interface is not comparable.
Taking advantage of that to be comparable, the firstversionof netaddr.IP was represented like this:
Notably, the IP type there is an opaque struct embedding aninterface. An interface, being 2 wordswide, is 16 bytes on 64-bitmachines, so the IP type here is 16 bytes. That’s better than thestandard library’s 24 byte (3 word) slice header used for net.IP.But both still need to a pointer to the actual bytes of the IPaddress. At least with this representation, the interface’s type wordencodes whether the address is IPv4, IPv6, or IPv6 with a zone scope.
It was good in some ways, but not perfect:
Featurenet.IPwgcfg.IP'Take 2'Immutable❌, slice✅✅Comparable❌, slice✅✅Small❌, 28-56B✅, 16B🤷, 20-32BAllocation free❌✅❌Supports IPv4 & IPv6✅✅✅Can distinguish IPv4/IPv6❌❌✅Supports IPv6 zones❌❌✅Opaque type❌❌✅Interops with standard library✅❌, with adapters❌, with adapters
I got the impression that Crawshaw in particular was very “meh” onthis representation needing to allocate compared to our existingwgcfg.IP type.
Let’s do better.
Take 3: allocation-free 24 byte representation
At some point I realized that the maximum tolerable size of our IPaddress type was 24 bytes: that’s the same size as Go’s net.IP sliceheader, and Go slices are very common. A time.Time is also a 24byte value type, so surely the compiler deals with 24 byte value typesjust fine. But mostly I didn’t want our new IP type to be worse inany dimension compared to the standard library’s net.IP, which is(in part) 24 bytes. So I somewhat arbitrarily decreed that 24 byteswas our limit.
Since an IPv6 address is already 16 bytes, that leaves us 8 bytesremaining in which to encode the following things:
Change Ip Address For Free Online
the address family (v4, v6, or neither, such as the IP zero value). There’sat least two bits.
the IPv6 zone
Also, we need to be comparable.
Using an interface is out: that’s two words (16 bytes), so that’s toobig. Likewise, a string is also two words (a pointer and length), sothat’s out.
We could play bit-packing games like:
… and try to encode the address family and zone into the 64 zoneAndFamily bits, but how?
If we have 1 or 2 bits for the address family, we have 62 or 63 bitsleft. Various options included:
shove the 7-bit ASCII string into the remaining 62 bits. But thatlimits us to 8 characters. Even our default 'tailscale0' interfacename wouldn’t fit.
encode a zone index into the 62 or 63 bits instead. But then we can’t parseand represent an interface that the local machine doesn’t have.
use a zone mapping table, mapping between zone index integers and zone name strings.That’s what the Go standard library does internally. But then we’re left susceptible to an attack where an adversary forcesus to parse a bunch of IP addresses with scopes and we forever bloat a mappingtable that we don’t have a good opportunity to ever shrink. The Go standardlibrary doesn’t need to deal with this, as it only ever maps interfaces thatexist on the machine and doesn’t expose the integers to users in representations;its net.IPAddr.Zone field is a string.
So, I didn’t like any of those options.
But then I thought of something gross. Or awesome.
We could use a pointer!
Ignoring the zone and actual definition of T for now, the addressfamily is easy: we make three sentinel pointer values to represent thefamily, and whether the IP address is the zero value (as opposed to,say, actually '0.0.0.0').
But how do we represent the zone string such that it’s comparable soGo’s works and IP values can be map keys?
Remember, our goal is that this prints true:
But comparisons on Go pointers compare the pointer values, not whatthey point to. That is, new(string) != new(string).
So we need to make sure that two separate ParseIP calls with same'eth0' zone at any point and any time in the program always returnthe same pointer value for that process.
That implies we need a mapping between these pointer values and theirprocess-wide-unique names ('eth0', etc). If this sounds a lot likethe earlier problem with the zone indexes, it is, but there’s onething that’s different: when shoving a zone index into an integerabove, we didn’t have a way to do any cleanup of the mappingtable. But with a pointer, we can useruntime.SetFinalizer.Using SetFinalizer is gross and scary and you should think twicebefore using it. We sure did. But sometimes gross and scary things arethe right tool for the job.
What we ended up writing was thego4.org/intern package tohide the bodies so ourinet.af/netaddr package couldhave plausible deniability as to its innocence.
The go4.org/intern package is tiny and worth reading infull (and perhapsworthy of a future blog post on its own), but thecore of it is this ungodliness:
Basically, it’s playing unsafe games behind the Go garbage collector’sback, hiding pointers in untyped uintptr integers so Go will beforced to eventually garbage collect things which then causes thefinalizer to be invoked to step in and either clean up its lies orclean up the map.
But the end result is that this is now true:
So our IP representation can be:
The accessors to get/set the zone are then:
How we’d do?
Featurenet.IPnetaddr.IPImmutable❌, slice✅Comparable❌, slice✅Small❌, 28-56B✅, 24B, alwaysAllocation free❌✅Supports IPv4 & IPv6✅✅Can distinguish IPv4/IPv6❌✅Supports IPv6 zones❌✅Opaque type❌✅Interops with standard library✅🤷, adaptor methods
Nailed it.
Take 4: uint64s for speed
We were pretty happy, but Dave Anderson took advantage of the type’sopaque representation and changed the representation to make it faster in4eb479db13,replacing the addr (16)byte with a pair of uint64 values:

The compiler liked that much more.
Take 5: a uint128 type
But why stop there? Being able to change the representation without affecting the API is too muchfun, so in 318330f177I replaced the uint64 pair with a new uint128 type, as Go doesn’t have a native one.
We’re now at:
But the compiler didn’t like that,so bf0e22f9f3broke it back down into:
And that’s basically where we’re at today.
We’re talking about breaking out the uint128 type into its own packagebut haven’t done so yet.
Other inet.af/netaddr fun
In addition to just IP addresses, inet.af/netaddr contains:
IPPort: a value type for an IP address and a port
IPPrefix: a value type for an IP address and a CIDR prefix (e.g. 192.168.0.1/16)
IPRange: a value type for range of IPs (e.g. 10.0.0.200-10.0.0.255)
IPSet: an efficient, immutable set of IP addresses, built with anIPSetBuilder.
As one contrived example, this code:
Outputs:
FAQ
Should you use netaddr.IP?
How To Find Ip Address On Computer
If you work with a lot of IP addresses and sets, ranges, andprefixes thereof, you’d probably benefit from using netaddr.IP overthe standard library’s types.
Is the API stable?
Mostly. We haven’t done a 1.0.0 yet and we might yet change a fewminor things, but it’spretty much done at this point.
What’s with the package name’s inet.af?
AF_INET, of course.
Was IPv6 worth it?
It is what it is.
This was too many words.
If you’d like this blog post in video form, my FOSDEM2021 talk, “Go atTailscale”discusses this starting at time 18:45.
Get New Ip Address Cox
Thanks
Get New Ip Address Free
Writing the inet.af/netaddr package was a fun collaborationwith@crawshaw,@danderson,@josharian,@mdlayher, and@tklauser.

0 notes
Text
Are the means of computation even seizable?
I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me in PITTSBURGH in TOMORROW (May 15) at WHITE WHALE BOOKS, and in PDX on Jun 20 at BARNES AND NOBLE with BUNNIE HUANG. More tour dates (London, Manchester) here.

Something's very different in tech. Once upon a time, every bad choice by tech companies – taking away features, locking out mods or plugins, nerfing the API – was countered, nearly instantaneously, by someone writing a program that overrode that choice.
Bad clients would be muscled aside by third-party clients. Locked bootloaders would be hacked and replaced. Code that confirmed you were using OEM parts, consumables or adapters would be found and nuked from orbit. Weak APIs would be replaced with muscular, unofficial APIs built out of unstoppable scrapers running on headless machines in some data-center. Every time some tech company erected a 10-foot enshittifying fence, someone would show up with an 11-foot disenshittifying ladder.
Those 11-foot ladders represented the power of interoperability, the inescapable bounty of the Turing-complete, universal von Neumann machine, which, by definition, is capable of running every valid program. Specifically, they represented the power of adversarial interoperability – when someone modifies a technology against its manufacturer's wishes. Adversarial interoperability is the origin story of today's tech giants, from Microsoft to Apple to Google:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
But adversarial interop has been in steady decline for the past quarter-century. These big companies moved fast and broke things, but no one is returning the favor. If you ask the companies what changed, they'll just smirk and say that they're better at security than the incumbents they disrupted. The reason no one's hacked up a third-party iOS App Store is that Apple's security team is just so fucking 1337 that no one can break their shit.
I think this is nonsense. I think that what's really going on is that we've made it possible for companies to design their technologies in such a way that any attempt at adversarial interop is illegal.
"Anticircumvention" laws like Section 1201 of the 1998 Digital Millennium Copyright Act make bypassing any kind of digital lock (AKA "Digital Rights Management" or "DRM") very illegal. Under DMCA, just talking about how to remove a digital lock can land you in prison for 5 years. I tell the story of this law's passage in "Understood: Who Broke the Internet," my new podcast series for the CBC:
https://pluralistic.net/2025/05/08/who-broke-the-internet/#bruce-lehman
For a quarter century, tech companies have aggressively lobbied and litigated to expand the scope of anticircumvention laws. At the same time, companies have come up with a million ways to wrap their products in digital locks that are a crime to break.
Digital locks let Chamberlain, a garage-door opener monopolist block all third-party garage-door apps. Then, Chamberlain stuck ads in its app, so you have to watch an ad to open your garage-door:
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Digital locks let John Deere block third-party repair of its tractors:
https://pluralistic.net/2022/05/08/about-those-kill-switched-ukrainian-tractors/
And they let Apple block third-party repair of iPhones:
https://pluralistic.net/2022/05/22/apples-cement-overshoes/
These companies built 11-foot ladders to get over their competitors' 10-foot walls, and then they kicked the ladder away. Once they were secure atop their walls, they committed enshittifying sins their fallen adversaries could only dream of.
I've been campaigning to abolish anticircumvention laws for the past quarter-century, and I've noticed a curious pattern. Whenever these companies stand to lose their legal protections, they freak out and spend vast fortunes to keep those protections intact. That's weird, because it strongly implies that their locks don't work. A lock that works works, whether or not it's illegal to break that lock. The reason Signal encryption works is that it's working encryption. The legal status of breaking Signal's encryption has nothing to do with whether it works. If Signal's encryption was full of technical flaws but it was illegal to point those flaws out, you'd be crazy to trust Signal.
Signal does get involved in legal fights, of course, but the fights it gets into are ones that require Signal to introduce defects in its encryption – not fights over whether it is legal to disclose flaws in Signal or exploit them:
https://pluralistic.net/2023/03/05/theyre-still-trying-to-ban-cryptography/
But tech companies that rely on digital locks manifestly act like their locks don't work and they know it. When the tech and content giants bullied the W3C into building DRM into 2 billion users' browsers, they categorically rejected any proposal to limit their ability to destroy the lives of people who broke that DRM, even if it was only to add accessibility or privacy to video:
https://www.eff.org/deeplinks/2017/09/open-letter-w3c-director-ceo-team-and-membership
The thing is, if the lock works, you don't need the legal right to destroy the lives of people who find its flaws, because it works.
Do digital locks work? Can they work? I think the answer to both questions is a resounding no. The design theory of a digital lock is that I can provide you with an encrypted file that your computer has the keys to. Your computer will access those keys to decrypt or sign a file, but only under the circumstances that I have specified. Like, you can install an app when it comes from my app store, but not when it comes from a third party. Or you can play back a video in one kind of browser window, but not in another one. For this to work, your computer has to hide a cryptographic key from you, inside a device you own and control. As I pointed out more than a decade ago, this is a fool's errand:
https://memex.craphound.com/2012/01/10/lockdown-the-coming-war-on-general-purpose-computing/
After all, you or I might not have the knowledge and resources to uncover the keys' hiding place, but someone does. Maybe that someone is a person looking to go into business selling your customers the disenshittifying plugin that unfucks the thing you deliberately broke. Maybe it's a hacker-tinkerer, pursuing an intellectual challenge. Maybe it's a bored grad student with a free weekend, an electron-tunneling microscope, and a seminar full of undergrads looking for a project.
The point is that hiding secrets in devices that belong to your adversaries is very bad security practice. No matter how good a bank safe is, the bank keeps it in its vault – not in the bank-robber's basement workshop.
For a hiding-secrets-in-your-adversaries'-device plan to work, the manufacturer has to make zero mistakes. The adversary – a competitor, a tinkerer, a grad student – only has to find one mistake and exploit it. This is a bedrock of security theory: attackers have an inescapable advantage.
So I think that DRM doesn't work. I think DRM is a legal construct, not a technical one. I think DRM is a kind of magic Saran Wrap that manufacturers can wrap around their products, and, in so doing, make it a literal jailable offense to use those products in otherwise legal ways that their shareholders don't like. As Jay Freeman put it, using DRM creates a new law called "Felony Contempt of Business Model." It's a law that has never been passed by any legislature, but is nevertheless enforceable.
In the 25 years I've been fighting anticircumvention laws, I've spoken to many government officials from all over the world about the opportunity that repealing their anticircumvention laws represents. After all, Apple makes $100b/year by gouging app makers for 30 cents on ever dollar. Allow your domestic tech sector to sell the tools to jailbreak iPhones and install third party app stores, and you can convert Apple's $100b/year to a $100m/year business for one of your own companies, and the other $999,900,000,000 will be returned to the world's iPhone owners as a consumer surplus.
But every time I pitched this, I got the same answer: "The US Trade Representative forced us to pass this law, and threatened us with tariffs if we didn't pass it." Happy Liberation Day, people – every country in the world is now liberated from the only reason to keep this stupid-ass law on their books:
https://pluralistic.net/2025/01/15/beauty-eh/#its-the-only-war-the-yankees-lost-except-for-vietnam-and-also-the-alamo-and-the-bay-of-ham
In light of the Trump tariffs, I've been making the global rounds again, making the case for an anticircumvention repeal:
https://www.ft.com/content/b882f3a7-f8c9-4247-9662-3494eb37c30b
One of the questions I've been getting repeatedly from policy wonks, activists and officials is, "Is it even possible to jailbreak modern devices?" They want to know if companies like Apple, Tesla, Google, Microsoft, and John Deere have created unbreakable digital locks. Obviously, this is an important question, because if these locks are impregnable, then getting rid of the law won't deliver the promised benefits.
It's true that there aren't as many jailbreaks as we used to see. When a big project like Nextcloud – which is staffed up with extremely accomplished and skilled engineers – gets screwed over by Google's app store, they issue a press-release, not a patch:
https://arstechnica.com/gadgets/2025/05/nextcloud-accuses-google-of-big-tech-gatekeeping-over-android-app-permissions/
Perhaps that's because the tech staff at Nextcloud are no match for Google, not even with the attacker's advantage on their side.
But I don't think so. Here's why: we do still get jailbreaks and mods, but these almost exclusively come from anonymous tinkerers and hobbyists:
https://consumerrights.wiki/Mazda_DMCA_takedown_of_Open_Source_Home_Assistant_App
Or from pissed off teenagers:
https://www.theverge.com/2022/9/29/23378541/the-og-app-instagram-clone-pulled-from-app-store
These hacks are incredibly ambitious! How ambitious? How about a class break for every version of iOS as well as an unpatchable hardware attack on 8 years' worth of Apple bootloaders?
https://pluralistic.net/2020/05/25/mafia-logic/#sosumi
Now, maybe it's the case at all the world's best hackers are posting free code under pseudonyms. Maybe all the code wizards working for venture backed tech companies that stand to make millions through clever reverse engineering are just not as mad skilled as teenagers who want an ad-free Insta and that's why they've never replicated the feat.
Or maybe it's because teenagers and anonymous hackers are just about the only people willing to risk a $500,000 fine and 5-year prison sentence. In other words, maybe the thing that protects DRM is law, not code. After all, when Polish security researchers revealed the existence of secret digital locks that the train manufacturer Newag used to rip off train operators for millions of euros, Newag dragged them into court:
https://fsfe.org/news/2025/news-20250407-01.en.html
Tech companies are the most self-mythologizing industry on the planet, beating out even the pharma sector in boasting about their prowess and good corporate citizenship. They swear that they've made a functional digital lock…but they sure act like the only thing those locks do is let them sue people who reveal their workings.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/05/14/pregnable/#checkm8
#pluralistic#apple#drm#og app#instagram#meta#dmca 1201#comcom#competitive compatibility#interop#interoperability#adversarial interoperability#who broke the internet#self-mythologizing#infosec#schneiers law#red team advantage#attackers advantage#luddism#seize the means of computation
433 notes
·
View notes
Text
Antiusurpation and the road to disenshittification

THIS WEEKEND (November 8-10), I'll be in TUCSON, AZ: I'm the GUEST OF HONOR at the TUSCON SCIENCE FICTION CONVENTION.

Nineties kids had a good reason to be excited about the internet's promise of disintermediation: the gatekeepers who controlled our access to culture, politics, and opportunity were crooked as hell, and besides, they sucked.
For a second there, we really did get a lot of disintermediation, which created a big, weird, diverse pluralistic space for all kinds of voices, ideas, identities, hobbies, businesses and movements. Lots of these were either deeply objectionable or really stupid, or both, but there was also so much cool stuff on the old, good internet.
Then, after about ten seconds of sheer joy, we got all-new gatekeepers, who were at least as bad, and even more powerful, than the old ones. The net became Tom Eastman's "Five giant websites, each filled with screenshots of the other four." Culture, politics, finance, news, and especially power have been gathered into the hands of unaccountable, greedy, and often cruel intermediaries.
Oh, also, we had an election.
This isn't an election post. I have many thoughts about the election, but they're still these big, unformed blobs of anger, fear and sorrow. Experience teaches me that the only way to get past this is to just let all that bad stuff sit for a while and offgas its most noxious compounds, so that I can handle it safely and figure out what to do with it.
While I wait that out, I'm just getting the job done. Chop wood, carry water. I've got a book to write, Enshittification, for Farar, Straus, Giroux's MCD Books, and it's very nearly done:
https://twitter.com/search?q=from%3Adoctorow+%23dailywords&src=typed_query&f=live
Compartmentalizing my anxieties and plowing that energy into productive work isn't necessarily the healthiest coping strategy, but it's not the worst, either. It's how I wrote nine books during the covid lockdowns.
And sometimes, when you're not staring directly at something, you get past the tunnel vision that makes it impossible to see its edges, fracture lines, and weak points.
So I'm working on the book. It's a book about platforms, because enshittification is a phenomenon that is most visible and toxic on platforms. Platforms are intermediaries, who connect buyers and sellers, creators and audiences, workers and employers, politicians and voters, activists and crowds, as well as families, communities, and would-be romantic partners.
There's a reason we keep reinventing these intermediaries: they're useful. Like, it's technically possible for a writer to also be their own editor, printer, distributor, promoter and sales-force:
https://pluralistic.net/2024/02/19/crad-kilodney-was-an-outlier/#intermediation
But without middlemen, those are the only writers we'll get. The set of all writers who have something to say that I want to read is much larger than the set of all writers who are capable of running their own publishing operation.
The problem isn't middlemen: the problem is powerful middlemen. When an intermediary gets powerful enough to usurp the relationship between the parties on either side of the transaction, everything turns to shit:
https://pluralistic.net/2022/06/12/direct-the-problem-of-middlemen/
A dating service that faces pressure from competition, regulation, interoperability and a committed workforce will try as hard as it can to help you find Your Person. A dating service that buys up all its competitors, cows its workforce, captures its regulators and harnesses IP law to block interoperators will redesign its service so that you keep paying forever, and never find love:
https://www.npr.org/sections/money/2024/02/13/1228749143/the-dating-app-paradox-why-dating-apps-may-be-worse-than-ever
Multiply this a millionfold, in every sector of our complex, high-tech world where we necessarily rely on skilled intermediaries to handle technical aspects of our lives that we can't – or shouldn't – manage ourselves. That world is beholden to predators who screw us and screw us and screw us, jacking up our rents:
https://www.thebignewsletter.com/p/yes-there-are-antitrust-voters-in
Cranking up the price of food:
https://pluralistic.net/2023/10/04/dont-let-your-meat-loaf/#meaty-beaty-big-and-bouncy
And everything else:
https://pluralistic.net/2023/11/06/attention-rents/#consumer-welfare-queens
(Maybe this is a post about the election after all?)
The difference between a helpmeet and a parasite is power. If we want to enjoy the benefits of intermediaries without the risks, we need policies that keep middlemen weak. That's the opposite of the system we have now.
Take interoperability and IP law. Interoperability (basically, plugging new things into existing things) is a really powerful check against powerful middlemen. If you rely on an ad-exchange to fund your newsgathering and they start ripping you off, then an interoperable system that lets you use a different exchange will not only end the rip off – it'll make it less likely to happen in the first place because the ad-tech platform will be afraid of losing your business:
https://www.eff.org/deeplinks/2023/05/save-news-we-must-shatter-ad-tech
Interoperability means that when a printer company gouges you on ink, you can buy cheap third party ink cartridges and escape their grasp forever:
https://www.eff.org/deeplinks/2020/11/ink-stained-wretches-battle-soul-digital-freedom-taking-place-inside-your-printer
Interoperability means that when Amazon rips off audiobook authors to the tune of $100m, those authors can pull their books from Amazon and sell them elsewhere and know that their listeners can move their libraries over to a different app:
https://pluralistic.net/2022/09/07/audible-exclusive/#audiblegate
But interoperability has been in retreat for 40 years, as IP law has expanded to criminalize otherwise normal activities, so that middlemen can use IP rights to protect themselves from their end-users and business customers:
https://locusmag.com/2020/09/cory-doctorow-ip/
That's what I mean when I say that "IP" is "any law that lets a business reach beyond its own walls and control the actions of its customers, competitors and critics."
For example, there's a pernicious law 1998 US law that I write about all the time, Section 1201 of the Digital Millennium Copyright Act, the "anticircumvention law." This is a law that felonizes tampering with copyright locks, even if you are the creator of the undelying work.
So Amazon – the owner of the monopoly audiobook platform Audible – puts a mandatory copyright lock around every audiobook they sell. I, as an author who writes, finances and narrates the audiobook, can't provide you, my customer, with a tool to remove that lock. If I do so, I face criminal sanctions: a five year prison sentence and a $500,000 fine for a first offense:
https://pluralistic.net/2022/07/25/can-you-hear-me-now/#acx-ripoff
In other words: if I let you take my own copyrighted work out of Amazon's app, I commit a felony, with penalties that are far stiffer than the penalties you would face if you were to simply pirate that audiobook. The penalties for you shoplifting the audiobook on CD at a truck-stop are lower than the penalties the author and publisher of the book would face if they simply gave you a tool to de-Amazon the file. Indeed, even if you hijacked the truck that delivered the CDs, you'd probably be looking at a shorter sentence.
This is a law that is purpose-built to encourage intermediaries to usurp the relationship between buyers and sellers, creators and audiences. It's a charter for parasitism and predation.
But as bad as that is, there's another aspect of DMCA 1201 that's even worse: the exemptions process.
You might have read recently about the Copyright Office "freeing the McFlurry" by granting a DMCA 1201 exemption for companies that want to reverse-engineer the error-codes from McDonald's finicky, unreliable frozen custard machines:
https://pluralistic.net/2024/10/28/mcbroken/#my-milkshake-brings-all-the-lawyers-to-the-yard
Under DMCA 1201, the Copyright Office hears petitions for these exemptions every three years. If they judge that anticircumvention law is interfering with some legitimate activity, the statute empowers them to grant an exemption.
When the DMCA passed in 1998 (and when the US Trade Rep pressured other world governments into passing nearly identical laws in the decades that followed), this exemptions process was billed as a "pressure valve" that would prevent abuses of anticircumvention law.
But this was a cynical trick. The way the law is structured, the Copyright Office can only grant "use" exemptions, but not "tools" exemptions. So if you are granted the right to move Audible audiobooks into a third-party app, you are personally required to figure out how to do that. You have to dump the machine code of the Audible app, decompile it, scan it for vulnerabilities, and bootstrap your own jailbreaking program to take Audible wrapper off the file.
No one is allowed to help you with this. You aren't allowed to discuss any of this publicly, or share a tool that you make with anyone else. Doing any of this is a potential felony.
In other words, DMCA 1201 gives intermediaries power over you, but bans you from asking an intermediary to help you escape another abusive middleman.
This is the exact opposite of how intermediary law should work. We should have rules that ban intermediaries from exercising undue power over the parties they serve, and we should have rules empowering intermediaries to erode the advantage of powerful intermediaries.
The fact that the Copyright Office grants you an exemption to anticircumvention law means nothing unless you can delegate that right to an intermediary who can exercise it on your behalf.
A world without publishing intermediaries is one in which the only writers who thrive are the ones capable of being publishers, too, and that's a tiny fraction of all the writers with something to say.
A world without interoperability intermediaries is one in which the only platform users who thrive are also skilled reverse-engineering ninja hackers – and that's an infinitesimal fraction of the platform users who would benefit from interoperabilty.
Let this be your north star in evaluating platform regulation proposals. Platform regulation should weaken intermediaries' powers over their users, and strengthen their power over other middlemen.
Put in this light, it's easy to see why the ill-informed calls to abolish Section 230 of the Communications Decency Act (which makes platform users, not platforms, responsible for most unlawful speech) are so misguided:
https://www.techdirt.com/2020/06/23/hello-youve-been-referred-here-because-youre-wrong-about-section-230-communications-decency-act/
If we require platforms to surveil all user speech and block anything that might violate any law, we give the largest, most powerful platforms a permanent advantage over smaller, better platforms, run by co-ops, hobbyists, nonprofits local governments, and startups. The big platforms have the capital to rig up massive, automated surveillance and censorship systems, and the only alternatives that can spring up have to be just as big and powerful as the Big Tech platforms we're so desperate to escape:
https://pluralistic.net/2024/03/23/evacuate-the-platforms/#let-the-platforms-burn
This is especially grave given the current political current, where fascist politicians are threatening platforms with brutal punishments for failing to censor disfavored political views.
Anyone who tells you that "it's only censorship when the government does it" is badly confused. It's only a First Amendment violation when the government does it, sure – but censorship has always relied on intermediaries. From the Inquisition to the Comics Code, government censors were only able to do their jobs because powerful middlemen, fearing state punishments, blocked anything that might cross the line, censoring far beyond the material actually prohibited by the law:
https://pluralistic.net/2024/02/22/self-censorship/#hugos
We live in a world of powerful, corrupt middlemen. From payments to real-estate, from job-search to romance, there's a legion of parasites masquerading as helpmeets, burying their greedy mouthparts into our tender flesh:
https://www.capitalisnt.com/episodes/visas-hidden-tax-on-americans
But intermediaries aren't the problem. You shouldn't have to stand up your own payment processor, or learn the ins and outs of real-estate law, or start your own single's bar. The problem is power, not intermediation.
As we set out to build a new, good internet (with a lot less help from the US government than seemed likely as recently as last week), let's remember that lesson: the point isn't disintermediation, it's weak intermediation.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/11/07/usurpers-helpmeets/#disreintermediation

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en (Image: Cryteria, CC BY 3.0, modified)
#pluralistic#comcom#competitive compatibility#interoperability#interop#adversarial interoperability#intermediaries#enshittification#posting through it#compartmentalization#farrar straus giroux#intermediary liability#intermediary empowerment#delegation#delegatability#dmca 1201#1201#digital millennium copyright act#norway#article 6#eucd#european union copyright act#eucd article 6#eu#usurpers#crad kilodney#fiduciaries#disintermediation#dark corners#self-censorship
576 notes
·
View notes
Text
Big Tech and “captive audience venues”

I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me in CHICAGO with PETER SAGAL next WEDNESDAY (Apr 2), and in BLOOMINGTON next FRIDAY (Apr 4). More tour dates here.

Enshittification is what you get when tech companies, run by the common-or-garden mediocre sociopaths who end up at the top of most businesses, are unshackled from any consequence for indulging their worst, greediest impulses:
https://pluralistic.net/2025/01/20/capitalist-unrealism/#praxis
The reason Facebook was once a nice place to hang out and talk with your friends and isn't anymore is that Mark Zuckerberg is no longer disciplined by competitors like Instagram (which he bought) nor by regulators (whom he captured), nor by interoperable tech like ad-blockers and alternative clients (which he uses IP law to destroy) nor by his own workforce (who have become disposable thanks to workforce supply catching up with demand). It used to be that Mark Zuckerberg couldn't really move the enshittification lever in the Facebook C-suite because these disciplining forces gummed it up. He had to worry about losing users, or about users installing alternative technology, or about regulators hitting him hard enough to hurt, or about workplace revolts. Now, he doesn't have to worry about these things, so he's indulging the impulses that he's had since the earliest days in his Harvard dorm, when he was a mere larval incel cooking up an online service to help him rate the fuckability of his female classmates.
When we had defenses, Mark Zuckerberg had to respect them. Now that we're defenseless, he's shameless. He's insatiable. He will devour us to the marrow.
When I'm explaining enshittification to normies, I often make comparisons to other places where you can't escape like airports and sports stadiums: "Facebook can afford to abuse you once they have you locked for the same reason that water costs $7/bottle on the other side of the airport TSA checkpoint." It's an extremely apt comparison, as you can verify for yourself by reading "Shakedown at the Snack Counter: The Case for Street Pricing," a new report from the Groundwork Collective:
https://groundworkcollaborative.org/work/street-pricing/
"Shakedown" makes the point that – as is the case with tech giants – sports stadiums and airports are creatures of vast public subsidy. If this seems counterintuitive, try Mariana Mazzucato's Entrepreneurial State, which lists all the ways in which the tech revolution represents a privatization of publicly funded research, as with the iPhone, whose semiconductors, internet connection, voice assistant technology, touchscreen and other components all count the public as a key investor:
https://www.pbs.org/newshour/economy/the-entrepreneurial-state-appl
And, as with airports and sports stadiums, the proprietors of the iPhone business are able to reap this gigantic public subsidy without taking on any public duties. Regulators that could impose some kind of public service obligations as quid pro quo for using public funds are AWOL, or worse, captured and complicit in the ongoing, publicly financed ripoff:
https://pluralistic.net/2024/08/15/private-law/#thirty-percent-vig
Airport, stadiums and tech platforms are all walled gardens – roach motels that are hard to escape once they've been entered. Thus the scorching prices of stadium and airport food, and the 30% transaction fees imposed by Apple and Google on app revenues (this is 1,000% higher than the average fees charged by the rest of the payment processing industry!), the 51% fees extracted by Google/Meta from advertisers and publishers (compare with the historical average of 15%), and the 45-51% that Amazon takes out of every dollar earned by its platform sellers. Once you're locked in, they can turn the screws, either by gouging buyers directly, or by gouging sellers, who pass those additional costs onto buyers.
Groundwork has a proposal to address this in physical settings: regulation. Specifically, a "street pricing" regulation that keeps the charges for food and drinks within these walled gardens to prices comparable to those on the outside. They note that these regulations enjoy wide, bipartisan support. 76% of Republicans support a regulation that can only be described as "price controls," two words that normally trigger head-explosions in the right.
How is it that such a commanding majority of Republicans can get behind government price controls? Simple: it's obvious that when a company no longer faces market discipline – when they're the only game in town (or on the other side of the TSA checkpoint) – that government discipline has to fill the vacuum, and if it doesn't, you will get mercilessly screwed.
This is where enshittification – a form of monopolistic decay unique to the tech sector – departs from everyday monopoly abuse in other sectors, like aviation and league sports. Tech has an in-built flexibility, the inescapable property of "interoperability" that comes standard with every digital system thanks to the universal nature of computers themselves.
Interoperable technologies let you hack Instagram to restore it to the state of privacy- and attention-respecting glory that made it a success in the first place:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
They let you monitor Facebook's failures to uphold its own promises about not profiting from paid political disinformation:
https://pluralistic.net/2021/08/06/get-you-coming-and-going/#potemkin-research-program
They let you claw back control over how Facebook's feeds are constructed:
https://pluralistic.net/2021/10/08/unfollow-everything/#shut-the-zuck-up
They let Apple customers maintain their privacy, even if they have the temerity to be friends with Android users:
https://pluralistic.net/2023/12/07/blue-bubbles-for-all/#never-underestimate-the-determination-of-a-kid-who-is-time-rich-and-cash-poor
They let shoppers use Amazon to order from local mom-and-pop stores:
https://pluralistic.net/2022/07/10/view-a-sku/
They even let you destroy the net worth – and power – of Elon Musk:
https://pluralistic.net/2025/03/08/turnabout/#is-fair-play
Interoperability creates a unique, easily administered source of discipline over tech bosses that just isn't available as a means of countering the ripoffs we see elsewhere, including in sports stadiums and airports. That means that, far from being harder to fix than other disgusting scams in our society, tech is easier to fix. All that stands in the way is the IP laws that criminalize the kind of reverse-engineering work that allow the users of technology to have the final say over how the devices and services they rely on work:
https://locusmag.com/2020/09/cory-doctorow-ip/
Those IP laws were spread around the world by the US Trade Representative, who insisted that every country that wanted to export its products to the US without punitive tariffs must pass laws protecting the rent-extracting scams of US tech giants. With those tariff promises now in tatters, there's never been a better time for the rest of the world to jettison those Big Tech-protecting laws:
https://pluralistic.net/2025/01/15/beauty-eh/#its-the-only-war-the-yankees-lost-except-for-vietnam-and-also-the-alamo-and-the-bay-of-ham

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/03/28/street-pricing/#sportball-analogies

Image: Daniel Brody (modified) https://commons.wikimedia.org/wiki/File:South-Station-snack-bar-1970.jpg
CC BY-SA 4.0 https://creativecommons.org/licenses/by-sa/4.0/deed.en
#pluralistic#street pricing#captive audience venues#groundwork collective#enshittification#we dont have to care were the phone company#regulation#competition#privatized gains socialized losses#sportsball#aviation#travel#monopolism#interop#interoperability#comcom#competitive compatibility#felony contempt of business model#adversarial interoperability
149 notes
·
View notes
Text
Forcing your computer to rat you out

Powerful people imprisoned by the cluelessness of their own isolation, locked up with their own motivated reasoning: “It’s impossible to get a CEO to understand something when his quarterly earnings call depends on him not understanding it.”
Take Mark Zuckerberg. Zuckerberg insists that anyone who wanted to use a pseudonym online is “two-faced,” engaged in dishonest social behavior. The Zuckerberg Doctrine claims that forcing people to use their own names is a way to ensure civility. This is an idea so radioactively wrong, it can be spotted from orbit.
From the very beginning, social scientists (both inside and outside Facebook) told Zuckerberg that he was wrong. People have lots of reasons to hide their identities online, both good and bad, but a Real Names Policy affects different people differently:
https://memex.craphound.com/2018/01/22/social-scientists-have-warned-zuck-all-along-that-the-facebook-theory-of-interaction-would-make-people-angry-and-miserable/
For marginalized and at-risk people, there are plenty of reasons to want to have more than one online identity — say, because you are a #MeToo whistleblower hoping that Harvey Weinstein won’t sic his ex-Mossad mercenaries on you:
https://www.newyorker.com/news/news-desk/harvey-weinsteins-army-of-spies
Or maybe you’re a Rohingya Muslim hoping to avoid the genocidal attentions of the troll army that used Facebook to organize — under their real, legal names — to rape and murder you and everyone you love:
https://www.amnesty.org/en/latest/news/2022/09/myanmar-facebooks-systems-promoted-violence-against-rohingya-meta-owes-reparations-new-report/
But even if no one is looking to destroy your life or kill you and your family, there are plenty of good reasons to present different facets of your identity to different people. No one talks to their lover, their boss and their toddler in exactly the same way, or reveals the same facts about their lives to those people. Maintaining different facets to your identity is normal and healthy — and the opposite, presenting the same face to everyone in your life, is a wildly terrible way to live.
None of this is controversial among social scientists, nor is it hard to grasp. But Zuckerberg stubbornly stuck to this anonymity-breeds-incivility doctrine, even as dictators used the fact that Facebook forced dissidents to use their real names to retain power through the threat (and reality) of arrest and torture:
https://pluralistic.net/2023/01/25/nationalize-moderna/#hun-sen
Why did Zuck cling to this dangerous and obvious fallacy? Because the more he could collapse your identity into one unitary whole, the better he could target you with ads. Truly, it is impossible to get a billionaire to understand something when his mega-yacht depends on his not understanding it.
This motivated reasoning ripples through all of Silicon Valley’s top brass, producing what Anil Dash calls “VC QAnon,” the collection of conspiratorial, debunked and absurd beliefs embraced by powerful people who hold the digital lives of billions of us in their quivering grasp:
https://www.anildash.com/2023/07/07/vc-qanon/
These fallacy-ridden autocrats like to disguise their demands as observations, as though wanting something to be true was the same as making it true. Think of when Eric Schmidt — then the CEO of Google — dismissed online privacy concerns, stating “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place”:
https://www.eff.org/deeplinks/2009/12/google-ceo-eric-schmidt-dismisses-privacy
Schmidt was echoing the sentiments of his old co-conspirator, Sun Microsystems CEO Scott McNealy: “You have zero privacy anyway. Get over it”:
https://www.wired.com/1999/01/sun-on-privacy-get-over-it/
Both men knew better. Schmidt, in particular, is very jealous of his own privacy. When Cnet reporters used Google to uncover and publish public (but intimate and personal) facts about Schmidt, Schmidt ordered Google PR to ignore all future requests for comment from Cnet reporters:
https://www.cnet.com/tech/tech-industry/how-cnet-got-banned-by-google/
(Like everything else he does, Elon Musk’s policy of responding to media questions about Twitter with a poop emoji is just him copying things other people thought up, making them worse, and taking credit for them:)
https://www.theverge.com/23815634/tesla-elon-musk-origin-founder-twitter-land-of-the-giants
Schmidt’s actions do not reflect an attitude of “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.” Rather, they are the normal response that we all have to getting doxed.
When Schmidt and McNealy and Zuck tell us that we don’t have privacy, or we don’t want privacy, or that privacy is bad for us, they’re disguising a demand as an observation. “Privacy is dead” actually means, “When privacy is dead, I will be richer than you can imagine, so stop trying to save it, goddamnit.”
We are all prone to believing our own bullshit, but when a tech baron gets high on his own supply, his mental contortions have broad implications for all of us. A couple years after Schmidt’s anti-privacy manifesto, Google launched Google Plus, a social network where everyone was required to use their “real name.”
This decision — justified as a means of ensuring civility and a transparent ruse to improve ad targeting — kicked off the Nym Wars:
https://epeus.blogspot.com/2011/08/google-plus-must-stop-this-identity.html
One of the best documents to come out of that ugly conflict is “Falsehoods Programmers Believe About Names,” a profound and surprising enumeration of all the ways that the experiences of tech bros in Silicon Valley are the real edge-cases, unreflective of the reality of billions of their users:
https://www.kalzumeus.com/2010/06/17/falsehoods-programmers-believe-about-names/
This, in turn, spawned a whole genre of programmer-fallacy catalogs, falsehoods programmers believe about time, currency, birthdays, timezones, email addresses, national borders, nations, biometrics, gender, language, alphabets, phone numbers, addresses, systems of measurement, and, of course, families:
https://github.com/kdeldycke/awesome-falsehood
But humility is in short supply in tech. It’s impossible to get a programmer to understand something when their boss requires them not to understand it. A programmer will happily insist that ordering you to remove your “mask” is for your own good — and not even notice that they’re taking your skin off with it.
There are so many ways that tech executives could improve their profits if only we would abandon our stubborn attachment to being so goddamned complicated. Think of Netflix and its anti-passsword-sharing holy war, which is really a demand that we redefine “family” to be legible and profitable for Netflix:
https://pluralistic.net/2023/02/02/nonbinary-families/#red-envelopes
But despite the entreaties of tech companies to collapse our identities, our families, and our online lives into streamlined, computably hard-edged shapes that fit neatly into their database structures, we continue to live fuzzy, complicated lives that only glancingly resemble those of the executives seeking to shape them.
Now, the rich, powerful people making these demands don’t plan on being constrained by them. They are conservatives, in the tradition of #FrankWilhoit, believers in a system of “in-groups whom the law protects but does not bind, alongside out-groups whom the law binds but does not protect”:
https://crookedtimber.org/2018/03/21/liberals-against-progressives/#comment-729288
As with Schmidt’s desire to spy on you from asshole to appetite for his own personal gain, and his violent aversion to having his own personal life made public, the tech millionaires and billionaires who made their fortune from the flexibility of general purpose computers would like to end that flexibility. They insist that the time for general purpose computers has passed, and that today, “consumers” crave the simplicity of appliances:
https://memex.craphound.com/2012/01/10/lockdown-the-coming-war-on-general-purpose-computing/
It is in the War On General Purpose Computing that we find the cheapest and flimsiest rhetoric. Companies like Apple — and their apologists — insist that no one wants to use third-party app stores, or seek out independent repair depots — and then spend millions to make sure that it’s illegal to jailbreak your phone or get it fixed outside of their own official channel:
https://doctorow.medium.com/apples-cement-overshoes-329856288d13
The cognitive dissonance of “no one wants this,” and “we must make it illegal to get this” is powerful, but the motivated reasoning is more powerful still. It is impossible to get Tim Cook to understand something when his $49 million paycheck depends on him not understanding it.
The War on General Purpose Computing has been underway for decades. Computers, like the people who use them, stubbornly insist on being reality-based, and the reality of computers is that they are general purpose. Every computer is a Turing complete, universal Von Neumann machine, which means that it can run every valid program. There is no way to get a computer to be almost Turing Complete, only capable of running programs that don’t upset your shareholders’ fragile emotional state.
There is no such thing as a printer that will only run the “reject third-party ink” program. There is no such thing as a phone that will only run the “reject third-party apps” program. There are only laws, like the Section 1201 of the Digital Millennium Copyright Act, that make writing and distributing those programs a felony punishable by a five-year prison sentence and a $500,000 fine (for a first offense).
That is to say, the War On General Purpose Computing is only incidentally a technical fight: it is primarily a legal fight. When Apple says, “You can’t install a third party app store on your phone,” what they means is, “it’s illegal to install that third party app store.” It’s not a technical countermeasure that stands between you and technological self-determination, it’s a legal doctrine we can call “felony contempt of business model”:
https://locusmag.com/2020/09/cory-doctorow-ip/
But the mighty US government will not step in to protect a company’s business model unless it at least gestures towards the technical. To invoke DMCA 1201, a company must first add the thinnest skin of digital rights management to their product. Since 1201 makes removing DRM illegal, a company can use this molecule-thick scrim of DRM to felonize any activity that the DRM prevents.
More than 20 years ago, technologists started to tinker with ways to combine the legal and technical to tame the wild general purpose computer. Starting with Microsoft’s Palladium project, they theorized a new “Secure Computing” model for allowing companies to reach into your computer long after you had paid for it and brought it home, in order to discipline you for using it in ways that undermined its shareholders’ interest.
Secure Computing began with the idea of shipping every computer with two CPUs. The first one was the normal CPU, the one you interacted with when you booted it up, loaded your OS, and ran programs. The second CPU would be a Trusted Platform Module, a brute-simple system-on-a-chip designed to be off-limits to modification, even by its owner (that is, you).
The TPM would ship with a limited suite of simple programs it could run, each thoroughly audited for bugs, as well as secret cryptographic signing keys that you were not permitted to extract. The original plan called for some truly exotic physical security measures for that TPM, like an acid-filled cavity that would melt the chip if you tried to decap it or run it through an electron-tunneling microscope:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
This second computer represented a crack in the otherwise perfectly smooth wall of a computer’s general purposeness; and Trusted Computing proposed to hammer a piton into that crack and use it to anchor a whole superstructure that could observe — and limited — the activity of your computer.
This would start with observation: the TPM would observe every step of your computer’s boot sequence, creating cryptographic hashes of each block of code as it loaded and executed. Each stage of the boot-up could be compared to “known good” versions of those programs. If your computer did something unexpected, the TPM could halt it in its tracks, blocking the boot cycle.
What kind of unexpected things do computers do during their boot cycle? Well, if your computer is infected with malware, it might load poisoned versions of its operating system. Once your OS is poisoned, it’s very hard to detect its malicious conduct, since normal antivirus programs rely on the OS to faithfully report what your computer is doing. When the AV program asks the OS to tell it which programs are running, or which files are on the drive, it has no choice but to trust the OS’s response. When the OS is compromised, it can feed a stream of lies to users’ programs, assuring these apps that everything is fine.
That’s a very beneficial use for a TPM, but there’s a sinister flipside: the TPM can also watch your boot sequence to make sure that there aren’t beneficial modifications present in your operating system. If you modify your OS to let you do things the manufacturer wants to prevent — like loading apps from a third-party app-store — the TPM can spot this and block it.
Now, these beneficial and sinister uses can be teased apart. When the Palladium team first presented its research, my colleague Seth Schoen proposed an “owner override”: a modification of Trusted Computing that would let the computer’s owner override the TPM:
https://web.archive.org/web/20021004125515/http://vitanuova.loyalty.org/2002-07-05.html
This override would introduce its own risks, of course. A user who was tricked into overriding the TPM might expose themselves to malicious software, which could harm that user, as well as attacking other computers on the user’s network and the other users whose data were on the compromised computer’s drive.
But an override would also provide serious benefits: it would rule out the monopolistic abuse of a TPM to force users to run malicious code that the manufacturer insisted on — code that prevented the user from doing things that benefited the user, even if it harmed the manufacturer’s shareholders. For example, with owner override, Microsoft couldn’t force you to use its official MS Office programs rather than third-party compatible programs like Apple’s iWork or Google Docs or LibreOffice.
Owner override also completely changed the calculus for another, even more dangerous part of Trusted Computing: remote attestation.
Remote Attestation is a way for third parties to request a reliable, cryptographically secured assurances about which operating system and programs your computer is running. In Remote Attestation, the TPM in your computer observes every stage of your computer’s boot, gathers information about all the programs you’re running, and cryptographically signs them, using the signing keys the manufacturer installed during fabrication.
You can send this “attestation” to other people on the internet. If they trust that your computer’s TPM is truly secure, then they know that you have sent them a true picture of your computer’s working (the actual protocol is a little more complicated and involves the remote party sending you a random number to cryptographically hash with the attestation, to prevent out-of-date attestations).
Now, this is also potentially beneficial. If you want to make sure that your technologically unsophisticated friend is running an uncompromised computer before you transmit sensitive data to it, you can ask them for an attestation that will tell you whether they’ve been infected with malware.
But it’s also potentially very sinister. Your government can require all the computers in its borders to send a daily attestation to confirm that you’re still running the mandatory spyware. Your abusive spouse — or abusive boss — can do the same for their own disciplinary technologies. Such a tool could prevent you from connecting to a service using a VPN, and make it impossible to use Tor Browser to protect your privacy when interacting with someone who wishes you harm.
The thing is, it’s completely normal and good for computers to lie to other computers on behalf of their owners. Like, if your IoT ebike’s manufacturer goes out of business and all their bikes get bricked because they can no longer talk to their servers, you can run an app that tricks the bike into thinking that it’s still talking to the mothership:
https://nltimes.nl/2023/07/15/alternative-app-can-unlock-vanmoof-bikes-popular-amid-bankruptcy-fears
Or if you’re connecting to a webserver that tries to track you by fingerprinting you based on your computer’s RAM, screen size, fonts, etc, you can order your browser to send random data about this stuff:
https://jshelter.org/fingerprinting/
Or if you’re connecting to a site that wants to track you and nonconsensually cram ads into your eyeballs, you can run an adblocker that doesn’t show you the ads, but tells the site that it did:
https://www.eff.org/deeplinks/2019/07/adblocking-how-about-nah
Owner override leaves some of the beneficial uses of remote attestation intact. If you’re asking a friend to remotely confirm that your computer is secure, you’re not going to use an override to send them bad data about about your computer’s configuration.
And owner override also sweeps all of the malicious uses of remote attestation off the board. With owner override, you can tell any lie about your computer to a webserver, a site, your boss, your abusive spouse, or your government, and they can’t spot the lie.
But owner override also eliminates some beneficial uses of remote attestation. For example, owner override rules out remote attestation as a way for strangers to play multiplayer video games while confirming that none of them are using cheat programs (like aimhack). It also means that you can’t use remote attestation to verify the configuration of a cloud server you’re renting in order to assure yourself that it’s not stealing your data or serving malware to your users.
This is a tradeoff, and it’s a tradeoff that’s similar to lots of other tradeoffs we make online, between the freedom to do something good and the freedom to do something bad. Participating anonymously, contributing to free software, distributing penetration testing tools, or providing a speech platform that’s open to the public all represent the same tradeoff.
We have lots of experience with making the tradeoff in favor of restrictions rather than freedom: powerful bad actors are happy to attach their names to their cruel speech and incitement to violence. Their victims are silenced for fear of that retaliation.
When we tell security researchers they can’t disclose defects in software without the manufacturer’s permission, the manufacturers use this as a club to silence their critics, not as a way to ensure orderly updates.
When we let corporations decide who is allowed to speak, they act with a mixture of carelessness and self-interest, becoming off-the-books deputies of authoritarian regimes and corrupt, powerful elites.
Alas, we made the wrong tradeoff with Trusted Computing. For the past twenty years, Trusted Computing has been creeping into our devices, albeit in somewhat denatured form. The original vision of acid-filled secondary processors has been replaced with less exotic (and expensive) alternatives, like “secure enclaves.” With a secure enclave, the manufacturer saves on the expense of installing a whole second computer, and instead, they draw a notional rectangle around a region of your computer’s main chip and try really hard to make sure that it can only perform a very constrained set of tasks.
This gives us the worst of all worlds. When secure enclaves are compromised, we not only lose the benefit of cryptographic certainty, knowing for sure that our computers are only booting up trusted, unalterted versions of the OS, but those compromised enclaves run malicious software that is essentially impossible to detect or remove:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
But while Trusted Computing has wormed its way into boot-restrictions — preventing you from jailbreaking your computer so it will run the OS and apps of your choosing — there’s been very little work on remote attestation…until now.
Web Environment Integrity is Google’s proposal to integrate remote attestation into everyday web-browsing. The idea is to allow web-servers to verify what OS, extensions, browser, and add-ons your computer is using before the server will communicate with you:
https://github.com/RupertBenWiser/Web-Environment-Integrity/blob/main/explainer.md
Even by the thin standards of the remote attestation imaginaries, there are precious few beneficial uses for this. The googlers behind the proposal have a couple of laughable suggestions, like, maybe if ad-supported sites can comprehensively refuse to serve ad-blocking browsers, they will invest the extra profits in making things you like. Or: letting websites block scriptable browsers will make it harder for bad people to auto-post fake reviews and comments, giving users more assurances about the products they buy.
But foundationally, WEI is about compelling you to disclose true facts about yourself to people who you want to keep those facts from. It is a Real Names Policy for your browser. Google wants to add a new capability to the internet: the ability of people who have the power to force you to tell them things to know for sure that you’re not lying.
The fact that the authors assume this will be beneficial is just another “falsehood programmers believe”: there is no good reason to hide the truth from other people. Squint a little and we’re back to McNealy’s “Privacy is dead, get over it.” Or Schmidt’s “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.”
And like those men, the programmers behind this harebrained scheme don’t imagine that it will ever apply to them. As Chris Palmer — who worked on Chromium — points out, this is not compatible with normal developer tools or debuggers, which are “incalculably valuable and not really negotiable”:
https://groups.google.com/a/chromium.org/g/blink-dev/c/Ux5h_kGO22g/m/5Lt5cnkLCwAJ
This proposal is still obscure in the mainstream, but in tech circles, it has precipitated a flood of righteous fury:
https://arstechnica.com/gadgets/2023/07/googles-web-integrity-api-sounds-like-drm-for-the-web/
As I wrote last week, giving manufacturers the power to decide how your computer is configured, overriding your own choices, is a bad tradeoff — the worst tradeoff, a greased slide into terminal enshittification:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
This is how you get Unauthorized Bread:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
All of which leads to the question: what now? What should be done about WEI and remote attestation?
Let me start by saying: I don’t think it should be illegal for programmers to design and release these tools. Code is speech, and we can’t understand how this stuff works if we can’t study it.
But programmers shouldn’t deploy it in production code, in the same way that programmers should be allowed to make pen-testing tools, but shouldn’t use them to attack production systems and harm their users. Programmers who do this should be criticized and excluded from the society of their ethical, user-respecting peers.
Corporations that use remote attestation should face legal restrictions: privacy law should prevent the use of remote attestation to compel the production of true facts about users or the exclusion of users who refuse to produce those facts. Unfair competition law should prevent companies from using remote attestation to block interoperability or tie their products to related products and services.
Finally, we must withdraw the laws that prevent users and programmers from overriding TPMs, secure enclaves and remote attestations. You should have the right to study and modify your computer to produce false attestations, or run any code of your choosing. Felony contempt of business model is an outrage. We should alter or strike down DMCA 1201, the Computer Fraud and Abuse Act, and other laws (like contract law’s “tortious interference”) that stand between you and “sole and despotic dominion” over your own computer. All of that applies not just to users who want to reconfigure their own computers, but also toolsmiths who want to help them do so, by offering information, code, products or services to jailbreak and alter your devices.
Tech giants will squeal at this, insisting that they serve your interests when they prevent rivals from opening up their products. After all, those rivals might be bad guys who want to hurt you. That’s 100% true. What is likewise true is that no tech giant will defend you from its own bad impulses, and if you can’t alter your device, you are powerless to stop them:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Companies should be stopped from harming you, but the right place to decide whether a business is doing something nefarious isn’t in the boardroom of that company’s chief competitor: it’s in the halls of democratically accountable governments:
https://www.eff.org/wp/interoperability-and-privacy
So how do we get there? Well, that’s another matter. In my next book, The Internet Con: How to Seize the Means of Computation (Verso Books, Sept 5), I lay out a detailed program, describing which policies will disenshittify the internet, and how to get those policies:
https://www.versobooks.com/products/3035-the-internet-con
Predictably, there are challenges getting this kind of book out into the world via our concentrated tech sector. Amazon refuses to carry the audio edition on its monopoly audiobook platform, Audible, unless it is locked to Amazon forever with mandatory DRM. That’s left me self-financing my own DRM-free audio edition, which is currently available for pre-order via this Kickstarter:
http://seizethemeansofcomputation.org

I’m kickstarting the audiobook for “The Internet Con: How To Seize the Means of Computation,” a Big Tech disassembly manual to disenshittify the web and bring back the old, good internet. It’s a DRM-free book, which means Audible won’t carry it, so this crowdfunder is essential. Back now to get the audio, Verso hardcover and ebook:
https://www.kickstarter.com/projects/doctorow/the-internet-con-how-to-seize-the-means-of-computation

If you’d like an essay-formatted version of this post to read or share, here’s a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai

[Image ID: An anatomical drawing of a flayed human head; it has been altered to give it a wide-stretched mouth revealing a gadget nestled in the back of the figure's throat, connected by a probe whose two coiled wires stretch to an old fashioned electronic box. The head's eyes have been replaced by the red, menacing eye of HAL 9000 from Stanley Kubrick's '2001: A Space Odyssey.' Behind the head is a code waterfall effect as seen in the credits of the Wachowskis' 'The Matrix.']

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#chaffing#spoofing#remote attestation#rene descartes#adversarial interoperability#war on general purpose computing#canvas attacks#vpns#compelled speech#onion routing#owner override#stalkerware#ngscb#palladium#trusted computing#secure enclaves#tor#interop#net neutrality#taking the fifth#right to remain silent#real names policy#the zuckerberg doctrine#none of your business#the right to lie#right to repair#bossware#spyware#wei web environment integrity
2K notes
·
View notes
Text
The enshittification of garage-door openers reveals a vast and deadly rot

I'll be at the Studio City branch of the LA Public Library on Monday, November 13 at 1830hPT to launch my new novel, The Lost Cause. There'll be a reading, a talk, a surprise guest (!!) and a signing, with books on sale. Tell your friends! Come on down!

How could this happen? Owners of Chamberlain MyQ automatic garage door openers just woke up to discover that the company had confiscated valuable features overnight, and that there was nothing they could do about it.
Oh, we know what happened, technically speaking. Chamberlain shut off the API for its garage-door openers, which breaks their integration with home automation systems like Home Assistant. The company even announced that it was doing this, calling the integration an "unauthorized usage" of its products, though the "unauthorized" parties in this case are the people who own Chamberlain products:
https://chamberlaingroup.com/press/a-message-about-our-decision-to-prevent-unauthorized-usage-of-myq
We even know why Chamberlain did this. As Ars Technica's Ron Amadeo points out, shutting off the API is a way for Chamberlain to force its customers to use its ad-beshitted, worst-of-breed app, so that it can make a few pennies by nonconsensually monetizing its customers' eyeballs:
https://arstechnica.com/gadgets/2023/11/chamberlain-blocks-smart-garage-door-opener-from-working-with-smart-homes/
But how did this happen? How did a giant company like Chamberlain come to this enshittening juncture, in which it felt empowered to sabotage the products it had already sold to its customers? How can this be legal? How can it be good for business? How can the people who made this decision even look themselves in the mirror?
To answer these questions, we must first consider the forces that discipline companies, acting against the impulse to enshittify their products and services. There are four constraints on corporate conduct:
I. Competition. The fear of losing your business to a rival can stay even the most sociopathic corporate executive's hand.
II. Regulation. The fear of being fined, criminally sanctioned, or banned from doing business can check the greediest of leaders.
III. Capability. Corporate executives can dream up all kinds of awful ways to shift value from your side of the ledger to their own, but they can only do the things that are technically feasible.
IV. Self-help. The possibility of customers modifying, reconfiguring or altering their products to restore lost functionality or neutralize antifeatures carries an implied threat to vendors. If a printer company's anti-generic-ink measures drives a customer to jailbreak their printers, the original manufacturer's connection to that customer is permanently severed, as the customer creates a durable digital connection to a rival.
When companies act in obnoxious, dishonest, shitty ways, they aren't merely yielding to temptation – they are evading these disciplining forces. Thus, the Great Enshittening we are living through doesn't reflect an increase in the wickedness of corporate leadership. Rather, it represents a moment in which each of these disciplining factors have been gutted by specific policies.
This is good news, actually. We used to put down rat poison and we didn't have a rat problem. Then we stopped putting down rat poison and rats are eating us alive. That's not a nice feeling, but at least we know at least one way of addressing it – we can start putting down poison again. That is, we can start enforcing the rules that we stopped enforcing, in living memory. Having a terrible problem is no fun, but the best kind of terrible problem to have is one that you know a solution to.
As it happens, Chamberlain is a neat microcosm for all the bad policy choices that created the Era of Enshittification. Let's go through them:
Competition: Chamberlain doesn't have to worry about competition, because it is owned by a private equity fund that "rolled up" all of Chamberlain's major competitors into a single, giant firm. Most garage-door opener brands are actually Chamberlain, including "LiftMaster, Chamberlain, Merlin, and Grifco":
https://www.lakewoodgaragedoor.biz/blog/the-history-of-garage-door-openers
This is a pretty typical PE rollup, and it exploits a bug in US competition law called "Antitrust's Twilight Zone":
https://pluralistic.net/2022/12/16/schumpeterian-terrorism/#deliberately-broken
When companies buy each other, they are subject to "merger scrutiny," a set of guidelines that the FTC and DoJ Antitrust Division use to determine whether the outcome is likely to be bad for competition. These rules have been pretty lax since the Reagan administration, but they've currently being revised to make them substantially more strict:
https://www.justice.gov/opa/pr/justice-department-and-ftc-seek-comment-draft-merger-guidelines
One of the blind spots in these merger guidelines is an exemption for mergers valued at less than $101m. Under the Hart-Scott-Rodino Act, these fly under the radar, evading merger scrutiny. That means that canny PE companies can roll up dozens and dozens of standalone businesses, like funeral homes, hospital beds, magic mushrooms, youth addiction treatment centers, mobile home parks, nursing homes, physicians’ practices, local newspapers, or e-commerce sellers:
http://www.economicliberties.us/wp-content/uploads/2022/12/Serial-Acquisitions-Working-Paper-R4-2.pdf
By titrating the purchase prices, PE companies – like Blackstone, owners of Chamberlain and all the other garage-door makers – can acquire a monopoly without ever raising a regulatory red flag.
But antitrust enforcers aren't helpless. Under (the long dormant) Section 7 of the Clayton Act, competition regulators can block mergers that lead to "incipient monopolization." The incipiency standard prevented monopolies from forming from 1914, when the Clayton Act passed, until the Reagan administration. We used to put down rat poison, and we didn't have rats. We stopped, and rats are gnawing our faces off. We still know where the rat poison is – maybe we should start putting it down again.
On to regulation. How is it possible for Chamberlain to sell you a garage-door opener that has an API and works with your chosen home automation system, and then unilaterally confiscate that valuable feature? Shouldn't regulation protect you from this kind of ripoff?
It should, but it doesn't. Instead, we have a bunch of regulations that protect Chamberlain from you. Think of binding arbitration, which allows Chamberlain to force you to click through an "agreement" that takes away your right to sue them or join a class-action suit:
https://pluralistic.net/2022/10/20/benevolent-dictators/#felony-contempt-of-business-model
But regulation could protect you from Chamberlain. Section 5 of the Federal Trade Commission Act allows the FTC to ban any "unfair and deceptive" conduct. This law has been on the books since 1914, but Section 5 has been dormant, forgotten and unused, for decades. The FTC's new dynamo chair, Lina Khan, has revived it, and is use it like a can-opener to free Americans who've been trapped by abusive conduct:
https://pluralistic.net/2023/01/10/the-courage-to-govern/#whos-in-charge
Khan's used Section 5 powers to challenge privacy invasions, noncompete clauses, and other corporate abuses – the bait-and-switch tactics of Chamberlain are ripe for a Section 5 case. If you buy a gadget because it has five features and then the vendor takes two of them away, they are clearly engaged in "unfair and deceptive" conduct.
On to capability. Since time immemorial, corporate leaders have fetishized "flexibility" in their business arrangements – like the ability to do "dynamic pricing" that changes how much you pay for something based on their guess about how much you are willing to pay. But this impulse to play shell games runs up against the hard limits of physical reality: grocers just can't send an army of rollerskated teenagers around the store to reprice everything as soon as a wealthy or desperate-looking customer comes through the door. They're stuck with crude tactics like doubling the price of a flight that doesn't include a Saturday stay as a way of gouging business travelers on an expense account.
With any shell-game, the quickness of the hand deceives the eye. Corporate crooks armed with computers aren't smarter or more wicked than their analog forebears, but they are faster. Digital tools allow companies to alter the "business logic" of their services from instant to instant, in highly automated ways:
https://pluralistic.net/2023/02/19/twiddler/
The monopoly coalition has successfully argued that this endless "twiddling" should not be constrained by privacy, labor or consumer protection law. Without these constraints, corporate twiddlers can engage in all kinds of ripoffs, like wage theft and algorithmic wage discrimination:
https://pluralistic.net/2023/04/12/algorithmic-wage-discrimination/#fishers-of-men
Twiddling is key to the Darth Vader MBA ("I am altering the deal. Pray I don't alter it further"), in which features are confiscated from moment to moment, without warning or recourse:
https://pluralistic.net/2023/10/26/hit-with-a-brick/#graceful-failure
There's no reason to accept the premise that violating your privacy, labor rights or consumer rights with a computer is so different from analog ripoffs that existing laws don't apply. The unconstrained twiddling of digital ripoff artists is a plague on billions of peoples' lives, and any enforcer who sticks up for our rights will have an army of supporters behind them.
Finally, there's the fear of self-help measures. All the digital flexibility that tech companies use to take value away can be used to take it back, too. The whole modern history of digital computers is the history of "adversarial interoperability," in which the sleazy antifeatures of established companies are banished through reverse-engineering, scraping, bots and other forms of technological guerrilla warfare:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
Adversarial interoperability represents a serious threat to established business. If you're a printer company gouging on toner, your customers might defect to a rival that jailbreaks your security measures. That's what happened to Lexmark, who lost a case against the toner-refilling company Static Controls, which went on to buy Lexmark:
https://www.eff.org/deeplinks/2019/06/felony-contempt-business-model-lexmarks-anti-competitive-legacy
Sure, your customers are busy and inattentive and you can degrade the quality of your product a lot before they start looking for ways out. But once they cross that threshold, you can lose them forever. That's what happened to Microsoft: the company made the tactical decision to produce a substandard version of Office for the Mac in a drive to get Mac users to switch to Windows. Instead, Apple made Iwork (Pages, Numbers and Keynote), which could read and write every Office file, and Mac users threw away Office, the only Microsoft product they owned, permanently severing their relationship to the company:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
Today, companies can operate without worrying about this kind of self-help measure. There' a whole slew of IP rights that Chamberlain can enforce against you if you try to fix your garage-door opener yourself, or look to a competitor to sell you a product that restores the feature they took away:
https://locusmag.com/2020/09/cory-doctorow-ip/
Jailbreaking your Chamberlain gadget in order to make it answer to a rival's app involves bypassing a digital lock. Trafficking in a tool to break a digital lock is a felony under Section 1201 of the Digital Millennium Copyright, carrying a five-year prison sentence and a $500,000 fine.
In other words, it's not just that tech isn't regulated, allowing for endless twiddling against your privacy, consumer rights and labor rights. It's that tech is badly regulated, to permit unlimited twiddling by tech companies to take away your rightsand to prohibit any twiddling by you to take them back. The US government thumbs the scales against you, creating a regime that Jay Freeman aptly dubbed "felony contempt of business model":
https://pluralistic.net/2022/10/23/how-to-fix-cars-by-breaking-felony-contempt-of-business-model/
All kinds of companies have availed themselves of this government-backed superpower. There's DRM – digital locks, covered by DMCA 1201 – in powered wheelchairs:
https://www.eff.org/deeplinks/2022/06/when-drm-comes-your-wheelchair
In dishwashers:
https://pluralistic.net/2021/05/03/cassette-rewinder/#disher-bob
In treadmills:
https://pluralistic.net/2021/06/22/vapescreen/#jane-get-me-off-this-crazy-thing
In tractors:
https://pluralistic.net/2022/05/08/about-those-kill-switched-ukrainian-tractors/
It should come as no surprise to learn that Chamberlain has used DMCA 1201 to block interoperable garage door opener components:
https://scholarship.law.marquette.edu/cgi/viewcontent.cgi?article=1233&context=iplr
That's how we arrived at this juncture, where a company like Chamberlain can break functionality its customers value highly, solely to eke out a minuscule new line of revenue by selling ads on their own app.
Chamberlain bought all its competitors.
Chamberlain operates in a regulatory environment that is extremely tolerant of unfair and deceptive practices. Worse: they can unilaterally take away your right to sue them, which means that if regulators don't bestir themselves to police Chamberlain, you are shit out of luck.
Chamberlain has endless flexibility to unilaterally alter its products' functionality, in fine-grained ways, even after you've purchased them.
Chamberlain can sue you if you try to exercise some of that same flexibility to protect yourself from their bad practices.
Combine all four of those factors, and of course Chamberlain is going to enshittify its products. Every company has had that one weaselly asshole at the product-planning table who suggests a petty grift like breaking every one of the company's customers' property to sell a few ads. But historically, the weasel lost the argument to others, who argued that making every existing customer furious would affect the company's bottom line, costing it sales and/or fines, and prompting customers to permanently sever their relationship with the company by seeking out and installing alternative software. Take away all the constraints on a corporation's worst impulses, and this kind of conduct is inevitable:
https://pluralistic.net/2023/07/28/microincentives-and-enshittification/
This isn't limited to Chamberlain. Without the discipline of competition, regulation, self-help measures or technological limitations, every industry in undergoing wholesale enshittification. It's not a coincidence that Chamberlain's grift involves a push to move users into its app. Because apps can't be reverse-engineered and modified without risking DMCA 1201 prosecution, forcing a user into an app is a tidy and reliable way to take away that user's rights.
Think about ad-blocking. One in four web users has installed an ad-blockers ("the biggest boycott in world history" -Doc Searls). Zero app users have installed app-blockers, because they don't exist, because making one is a felony. An app is just a web-page wrapped in enough IP to make it a crime to defend yourself against corporate predation:
https://pluralistic.net/2023/08/27/an-audacious-plan-to-halt-the-internets-enshittification-and-throw-it-into-reverse/
The temptation to enshitiffy isn't new, but the ability to do so without consequence is a modern phenomenon, the intersection of weak policy enforcement and powerful technology. Your car is autoenshittified, a rolling rent-seeking platform that spies on you and price-gouges you:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
Cars are in an uncontrolled skid over Enshittification Cliff. Honda, Toyota, VW and GM all sell cars with infotainment systems that harvest your connected phone's text-messages and send them to the corporation for data-mining. What's more, a judge in Washington state just ruled that this is legal:
https://therecord.media/class-action-lawsuit-cars-text-messages-privacy
While there's no excuse for this kind of sleazy conduct, we can reasonably anticipate that if our courts would punish companies for engaging in it, they might be able to resist the temptation. No wonder Mozilla's latest Privacy Not Included research report called cars "the worst product category we have ever reviewed":
https://foundation.mozilla.org/en/privacynotincluded/articles/its-official-cars-are-the-worst-product-category-we-have-ever-reviewed-for-privacy/
I mean, Nissan tries to infer facts about your sex life and sells those inferences to marketing companies:
https://foundation.mozilla.org/en/privacynotincluded/nissan/
But the OG digital companies are the masters of enshittification. Microsoft has been at this game for longer than anyone, and every day brings a fresh way that Microsoft has worsened its products without fear of consequence. The latest? You can't delete your OneDrive account until you provide an acceptable explanation for your disloyalty:
https://www.theverge.com/2023/11/8/23952878/microsoft-onedrive-windows-close-app-notification
It's tempting to think that the cruelty is the point, but it isn't. It's almost never the point. The point is power and money. Unscrupulous businesses have found ways to make money by making their products worse since the industrial revolution. Here's Jules Dupuis, writing about 19th century French railroads:
It is not because of the few thousand francs which would have to be spent to put a roof over the third-class carriages or to upholster the third-class seats that some company or other has open carriages with wooden benches. What the company is trying to do is to prevent the passengers who can pay the second class fare from traveling third class; it hits the poor, not because it wants to hurt them, but to frighten the rich. And it is again for the same reason that the companies, having proved almost cruel to the third-class passengers and mean to the second-class ones, become lavish in dealing with first-class passengers. Having refused the poor what is necessary, they give the rich what is superfluous.
https://www.tumblr.com/mostlysignssomeportents/731357317521719296/having-refused-the-poor-what-is-necessary-they
But as bad as all this is, let me remind you about the good part: we know how to stop companies from enshittifying their products. We know what disciplines their conduct: competition, regulation, capability and self-help measures. Yes, rats are gnawing our eyeballs, but we know which rat-poison to use, and where to put it to control those rats.
Competition, regulation, constraint and self-help measures all backstop one another, and while one or a few can make a difference, they are most powerful when they're all mobilized in concert. Think of the failure of the EU's landmark privacy law, the GDPR. While the GDPR proved very effective against bottom-feeding smaller ad-tech companies, the worse offenders, Meta and Google, have thumbed their noses at it.
This was enabled in part by the companies' flying an Irish flag of convenience, maintaining the pretense that they have to be regulated in a notorious corporate crime-haven:
https://pluralistic.net/2023/05/15/finnegans-snooze/#dirty-old-town
That let them get away with all kinds of shenanigans, like ignoring the GDPR's requirement that you should be able to easily opt out of data-collection without having to go through cumbersome "cookie consent" dialogs or losing access to the service as punishment for declining to be tracked.
As the noose has tightened around these surveillance giants, they're continuing to play games. Meta now says that the only way to opt out of data-collection in the EU is to pay for the service:
https://pluralistic.net/2023/10/30/markets-remaining-irrational/#steins-law
This is facially illegal under the GDPR. Not only are they prohibited from punishing you for opting out of collection, but the whole scheme ignores the nature of private data collection. If Facebook collects the fact that you and I are friends, but I never opted into data-collection, they have violated the GDPR, even if you were coerced into granting consent:
https://www.nakedcapitalism.com/2023/11/the-pay-or-consent-challenge-for-platform-regulators.html
The GDPR has been around since 2016 and Google and Meta are still invading 500 million Europeans' privacy. This latest delaying tactic could add years to their crime-spree before they are brought to justice.
But most of this surveillance is only possible because so much of how you interact with Google and Meta is via an app, and an app is just a web-page that's a felony to make an ad-blocker for. If the EU were to legalize breaking DRM – repealing Article 6 of the 2001 Copyright Directive – then we wouldn't have to wait for the European Commission to finally wrestle these two giant companies to the ground. Instead, EU companies could make alternative clients for all of Google and Meta's services that don't spy on you, without suffering the fate of OG App, which tried this last winter and was shut down by "felony contempt of business model":
https://pluralistic.net/2023/02/05/battery-vampire/#drained
Enshittification is demoralizing. To quote @wilwheaton, every update to the services we use inspires "dread of 'How will this complicate things as I try to maintain privacy and sanity in a world that demands I have this thing to operate?'"
https://wilwheaton.tumblr.com/post/698603648058556416/cory-doctorow-if-you-see-this-and-have-thoughts
But there are huge natural constituencies for the four disciplining forces that keep enshittification at bay.
Remember, Antitrust's Twilight Zone doesn't just allow rollups of garage-door opener companies – it's also poison for funeral homes, hospital beds, magic mushrooms, youth addiction treatment centers, mobile home parks, nursing homes, physicians’ practices, local newspapers, or e-commerce sellers.
The Binding Arbitration scam that stops Chamberlain customers from suing the company also stops Uber drivers from suing over stolen wages, Turbotax customers from suing over fraud, and many other victims of corporate crime from getting a day in court.
The failure to constrain twiddling to protect privacy, labor rights and consumer rights enables a host of abuses, from stalking, doxing and SWATting to wage theft and price gouging:
https://pluralistic.net/2023/11/06/attention-rents/#consumer-welfare-queens
And Felony Contempt of Business Model is used to screw you over every time you refill your printer, run your dishwasher, or get your Iphone's screen replaced.
The actions needed to halt and reverse this enshittification are well understood, and the partisans for taking those actions are too numerous to count. It's taken a long time for all those individuals suffering under corporate abuses to crystallize into a movement, but at long last, it's happening.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#monopolists#anticircumvention#myq#home assistant#pay or consent#enshittification#surveillance#autoenshittification#privacy#self-help measures#microsoft#onedrive#twiddling#comcom#competitive compatibility#interop#interoperability#adversarial interoperability#felony contempt of business model#darth vader mba
376 notes
·
View notes
Text
Kickstarting a book to end enshittification, because Amazon will not carry it

My next book is The Internet Con: How to Seize the Means of Computation: it’s a Big Tech disassembly manual that explains how to disenshittify the web and bring back the old good internet. The hardcover comes from Verso on Sept 5, but the audiobook comes from me — because Amazon refuses to sell my audio:
https://www.kickstarter.com/projects/doctorow/the-internet-con-how-to-seize-the-means-of-computation
Amazon owns Audible, the monopoly audiobook platform that controls >90% of the audio market. They require mandatory DRM for every book sold, locking those books forever to Amazon’s monopoly platform. If you break up with Amazon, you have to throw away your entire audiobook library.
That’s a hell of a lot of leverage to hand to any company, let alone a rapacious monopoly that ran a program targeting small publishers called “Project Gazelle,” where execs were ordered to attack indie publishers “the way a cheetah would pursue a sickly gazelle”:
https://www.businessinsider.com/sadistic-amazon-treated-book-sellers-the-way-a-cheetah-would-pursue-a-sickly-gazelle-2013-10

[Image ID: Journalist and novelist Doctorow (Red Team Blues) details a plan for how to break up Big Tech in this impassioned and perceptive manifesto….Doctorow’s sense of urgency is contagious -Publishers Weekly]
I won’t sell my work with DRM, because DRM is key to the enshittification of the internet. Enshittification is why the old, good internet died and became “five giant websites filled with screenshots of the other four” (h/t Tom Eastman). When a tech company can lock in its users and suppliers, it can drain value from both sides, using DRM and other lock-in gimmicks to keep their business even as they grow ever more miserable on the platform.
Here is how platforms die: first, they are good to their users; then they abuse their users to make things better for their business customers; finally, they abuse those business customers to claw back all the value for themselves. Then, they die:
https://pluralistic.net/2023/01/21/potemkin-ai/#hey-guys

[Image ID: A brilliant barn burner of a book. Cory is one of the sharpest tech critics, and he shows with fierce clarity how our computational future could be otherwise -Kate Crawford, author of The Atlas of AI”]
The Internet Con isn’t just an analysis of where enshittification comes from: it’s a detailed, shovel-ready policy prescription for halting enshittification, throwing it into reverse and bringing back the old, good internet.
How do we do that? With interoperability: the ability to plug new technology into those crapulent, decaying platform. Interop lets you choose which parts of the service you want and block the parts you don’t (think of how an adblocker lets you take the take-it-or-leave “offer” from a website and reply with “How about nah?”):
https://www.eff.org/deeplinks/2019/07/adblocking-how-about-nah
But interop isn’t just about making platforms less terrible — it’s an explosive charge that demolishes walled gardens. With interop, you can leave a social media service, but keep talking to the people who stay. With interop, you can leave your mobile platform, but bring your apps and media with you to a rival’s service. With interop, you can break up with Amazon, and still keep your audiobooks.
So, if interop is so great, why isn’t it everywhere?
Well, it used to be. Interop is how Microsoft became the dominant operating system:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay

[Image ID: Nobody gets the internet-both the nuts and bolts that make it hum and the laws that shaped it into the mess it is-quite like Cory, and no one’s better qualified to deliver us a user manual for fixing it. That’s The Internet Con: a rousing, imaginative, and accessible treatise for correcting our curdled online world. If you care about the internet, get ready to dedicate yourself to making interoperability a reality. -Brian Merchant, author of Blood in the Machine]
It’s how Apple saved itself from Microsoft’s vicious campaign to destroy it:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
Every tech giant used interop to grow, and then every tech giant promptly turned around and attacked interoperators. Every pirate wants to be an admiral. When Big Tech did it, that was progress; when you do it back to Big Tech, that’s piracy. The tech giants used their monopoly power to make interop without permission illegal, creating a kind of “felony contempt of business model” (h/t Jay Freeman).
The Internet Con describes how this came to pass, but, more importantly, it tells us how to fix it. It lays out how we can combine different kinds of interop requirements (like the EU’s Digital Markets Act and Massachusetts’s Right to Repair law) with protections for reverse-engineering and other guerrilla tactics to create a system that is strong without being brittle, hard to cheat on and easy to enforce.
What’s more, this book explains how to get these policies: what existing legislative, regulatory and judicial powers can be invoked to make them a reality. Because we are living through the Great Enshittification, and crises erupt every ten seconds, and when those crises occur, the “good ideas lying around” can move from the fringes to the center in an eyeblink:
https://pluralistic.net/2023/06/12/only-a-crisis/#lets-gooooo

[Image ID: Thoughtfully written and patiently presented, The Internet Con explains how the promise of a free and open internet was lost to predatory business practices and the rush to commodify every aspect of our lives. An essential read for anyone that wants to understand how we lost control of our digital spaces and infrastructure to Silicon Valley’s tech giants, and how we can start fighting to get it back. -Tim Maughan, author of INFINITE DETAIL]
After all, we’ve known Big Tech was rotten for years, but we had no idea what to do about it. Every time a Big Tech colossus did something ghastly to millions or billions of people, we tried to fix the tech company. There’s no fixing the tech companies. They need to burn. The way to make users safe from Big Tech predators isn’t to make those predators behave better — it’s to evacuate those users:
https://pluralistic.net/2023/07/18/urban-wildlife-interface/#combustible-walled-gardens
I’ve been campaigning for human rights in the digital world for more than 20 years; I’ve been EFF’s European Director, representing the public interest at the EU, the UN, Westminster, Ottawa and DC. This is the subject I’ve devoted my life to, and I live my principles. I won’t let my books be sold with DRM, which means that Audible won’t carry my audiobooks. My agent tells me that this decision has cost me enough money to pay off my mortgage and put my kid through college. That’s a price I’m willing to pay if it means that my books aren’t enshittification bait.
But not selling on Audible has another cost, one that’s more important to me: a lot of readers prefer audiobooks and 9 out of 10 of those readers start and end their searches on Audible. When they don’t find an author there, they assume no audiobook exists, period. It got so bad I put up an audiobook on Amazon — me, reading an essay, explaining how Audible rips off writers and readers. It’s called “Why None of My Audiobooks Are For Sale on Audible”:
https://pluralistic.net/2022/07/25/can-you-hear-me-now/#acx-ripoff

[Image ID: Doctorow has been thinking longer and smarter than anyone else I know about how we create and exchange value in a digital age. -Douglas Rushkoff, author of Present Shock]
To get my audiobooks into readers’ ears, I pre-sell them on Kickstarter. This has been wildly successful, both financially and as a means of getting other prominent authors to break up with Amazon and use crowdfunding to fill the gap. Writers like Brandon Sanderson are doing heroic work, smashing Amazon’s monopoly:
https://www.brandonsanderson.com/guest-editorial-cory-doctorow-is-a-bestselling-author-but-audible-wont-carry-his-audiobooks/
And to be frank, I love audiobooks, too. I swim every day as physio for a chronic pain condition, and I listen to 2–3 books/month on my underwater MP3 player, disappearing into an imaginary world as I scull back and forth in my public pool. I’m able to get those audiobooks on my MP3 player thanks to Libro.fm, a DRM-free store that supports indie booksellers all over the world:
https://blog.libro.fm/a-qa-with-mark-pearson-libro-fm-ceo-and-co-founder/
Producing my own audiobooks has been a dream. Working with Skyboat Media, I’ve gotten narrators like @wilwheaton, Amber Benson, @neil-gaiman and Stefan Rudnicki for my work:
https://craphound.com/shop/

[Image ID: “This book is the instruction manual Big Tech doesn’t want you to read. It deconstructs their crummy products, undemocratic business models, rigged legal regimes, and lies. Crack this book and help build something better. -Astra Taylor, author of Democracy May Not Exist, but We’ll Miss It When Its Gone”]
But for this title, I decided that I would read it myself. After all, I’ve been podcasting since 2006, reading my own work aloud every week or so, even as I traveled the world and gave thousands of speeches about the subject of this book. I was excited (and a little trepedatious) at the prospect, but how could I pass up a chance to work with director Gabrielle de Cuir, who has directed everyone from Anne Hathaway to LeVar Burton to Eric Idle?
Reader, I fucking nailed it. I went back to those daily recordings fully prepared to hate them, but they were good — even great (especially after my engineer John Taylor Williams mastered them). Listen for yourself!
https://archive.org/details/cory_doctorow_internet_con_chapter_01
I hope you’ll consider backing this Kickstarter. If you’ve ever read my free, open access, CC-licensed blog posts and novels, or listened to my podcasts, or come to one of my talks and wished there was a way to say thank you, this is it. These crowdfunders make my DRM-free publishing program viable, even as audiobooks grow more central to a writer’s income and even as a single company takes over nearly the entire audiobook market.
Backers can choose from the DRM-free audiobook, DRM-free ebook (EPUB and MOBI) and a hardcover — including a signed, personalized option, fulfilled through the great LA indie bookstore Book Soup:
https://www.kickstarter.com/projects/doctorow/the-internet-con-how-to-seize-the-means-of-computation
What’s more, these ebooks and audiobooks are unlike any you’ll get anywhere else because they are sold without any terms of service or license agreements. As has been the case since time immemorial, when you buy these books, they’re yours, and you are allowed to do anything with them that copyright law permits — give them away, lend them to friends, or simply read them with any technology you choose.
As with my previous Kickstarters, backers can get their audiobooks delivered with an app (from libro.fm) or as a folder of MP3s. That helps people who struggle with “sideloading,” a process that Apple and Google have made progressively harder, even as they force audiobook and ebook sellers to hand over a 30% app tax on every dollar they make:
https://www.kickstarter.com/projects/doctorow/red-team-blues-another-audiobook-that-amazon-wont-sell/posts/3788112
Enshittification is rotting every layer of the tech stack: mobile, payments, hosting, social, delivery, playback. Every tech company is pulling the rug out from under us, using the chokepoints they built between audiences and speakers, artists and fans, to pick all of our pockets.
The Internet Con isn’t just a lament for the internet we lost — it’s a plan to get it back. I hope you’ll get a copy and share it with the people you love, even as the tech platforms choke off your communities to pad their quarterly numbers.

Next weekend (Aug 4-6), I'll be in Austin for Armadillocon, a science fiction convention, where I'm the Guest of Honor:
https://armadillocon.org/d45/

If you'd like an essay-formatted version of this thread to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/07/31/seize-the-means-of-computation/#the-internet-con

[Image ID: My forthcoming book 'The Internet Con: How to Seize the Means of Computation' in various editions: Verso hardcover, audiobook displayed on a phone, and ebook displayed on an e-ink reader.]
#pluralistic#trustbusting#big tech#gift guide#kickstarter#the internet con#books#audiobooks#enshitiffication#disenshittification#crowdfunders#seize the means of computation#audible#amazon#verso
15K notes
·
View notes
Text
CDA 230 bans Facebook from blocking interoperable tools

I'm touring my new, nationally bestselling novel The Bezzle! Catch me TONIGHT (May 2) in WINNIPEG, then TOMORROW (May 3) in CALGARY, then SATURDAY (May 4) in VANCOUVER, then onto Tartu, Estonia, and beyond!

Section 230 of the Communications Decency Act is the most widely misunderstood technology law in the world, which is wild, given that it's only 26 words long!
https://www.techdirt.com/2020/06/23/hello-youve-been-referred-here-because-youre-wrong-about-section-230-communications-decency-act/
CDA 230 isn't a gift to big tech. It's literally the only reason that tech companies don't censor on anything we write that might offend some litigious creep. Without CDA 230, there'd be no #MeToo. Hell, without CDA 230, just hosting a private message board where two friends get into serious beef could expose to you an avalanche of legal liability.
CDA 230 is the only part of a much broader, wildly unconstitutional law that survived a 1996 Supreme Court challenge. We don't spend a lot of time talking about all those other parts of the CDA, but there's actually some really cool stuff left in the bill that no one's really paid attention to:
https://www.aclu.org/legal-document/supreme-court-decision-striking-down-cda
One of those little-regarded sections of CDA 230 is part (c)(2)(b), which broadly immunizes anyone who makes a tool that helps internet users block content they don't want to see.
Enter the Knight First Amendment Institute at Columbia University and their client, Ethan Zuckerman, an internet pioneer turned academic at U Mass Amherst. Knight has filed a lawsuit on Zuckerman's behalf, seeking assurance that Zuckerman (and others) can use browser automation tools to block, unfollow, and otherwise modify the feeds Facebook delivers to its users:
https://knightcolumbia.org/documents/gu63ujqj8o
If Zuckerman is successful, he will set a precedent that allows toolsmiths to provide internet users with a wide variety of automation tools that customize the information they see online. That's something that Facebook bitterly opposes.
Facebook has a long history of attacking startups and individual developers who release tools that let users customize their feed. They shut down Friendly Browser, a third-party Facebook client that blocked trackers and customized your feed:
https://www.eff.org/deeplinks/2020/11/once-again-facebook-using-privacy-sword-kill-independent-innovation
Then in in 2021, Facebook's lawyers terrorized a software developer named Louis Barclay in retaliation for a tool called "Unfollow Everything," that autopiloted your browser to click through all the laborious steps needed to unfollow all the accounts you were subscribed to, and permanently banned Unfollow Everywhere's developer, Louis Barclay:
https://slate.com/technology/2021/10/facebook-unfollow-everything-cease-desist.html
Now, Zuckerman is developing "Unfollow Everything 2.0," an even richer version of Barclay's tool.
This rich record of legal bullying gives Zuckerman and his lawyers at Knight something important: "standing" – the right to bring a case. They argue that a browser automation tool that helps you control your feeds is covered by CDA(c)(2)(b), and that Facebook can't legally threaten the developer of such a tool with liability for violating the Computer Fraud and Abuse Act, the Digital Millennium Copyright Act, or the other legal weapons it wields against this kind of "adversarial interoperability."
Writing for Wired, Knight First Amendment Institute at Columbia University speaks to a variety of experts – including my EFF colleague Sophia Cope – who broadly endorse the very clever legal tactic Zuckerman and Knight are bringing to the court.
I'm very excited about this myself. "Adversarial interop" – modding a product or service without permission from its maker – is hugely important to disenshittifying the internet and forestalling future attempts to reenshittify it. From third-party ink cartridges to compatible replacement parts for mobile devices to alternative clients and firmware to ad- and tracker-blockers, adversarial interop is how internet users defend themselves against unilateral changes to services and products they rely on:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
Now, all that said, a court victory here won't necessarily mean that Facebook can't block interoperability tools. Facebook still has the unilateral right to terminate its users' accounts. They could kick off Zuckerman. They could kick off his lawyers from the Knight Institute. They could permanently ban any user who uses Unfollow Everything 2.0.
Obviously, that kind of nuclear option could prove very unpopular for a company that is the very definition of "too big to care." But Unfollow Everything 2.0 and the lawsuit don't exist in a vacuum. The fight against Big Tech has a lot of tactical diversity: EU regulations, antitrust investigations, state laws, tinkerers and toolsmiths like Zuckerman, and impact litigation lawyers coming up with cool legal theories.
Together, they represent a multi-front war on the very idea that four billion people should have their digital lives controlled by an unaccountable billionaire man-child whose major technological achievement was making a website where he and his creepy friends could nonconsensually rate the fuckability of their fellow Harvard undergrads.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/05/02/kaiju-v-kaiju/#cda-230-c-2-b

Image: D-Kuru (modified): https://commons.wikimedia.org/wiki/File:MSI_Bravo_17_(0017FK-007)-USB-C_port_large_PNr%C2%B00761.jpg
Minette Lontsie (modified): https://commons.wikimedia.org/wiki/File:Facebook_Headquarters.jpg
CC BY-SA 4.0: https://creativecommons.org/licenses/by-sa/4.0/deed.en
#pluralistic#ethan zuckerman#cda 230#interoperability#content moderation#composable moderation#unfollow everything#meta#facebook#knight first amendment initiative#u mass amherst#cfaa
246 notes
·
View notes
Text
Netflix wants to chop down your family tree

Netflix has unveiled the details of its new anti-password-sharing policy, detailing a suite of complex gymnastics that customers will be expected to undergo if their living arrangements trigger Netflix’s automated enforcement mechanisms:
https://thestreamable.com/news/confirmed-netflix-unveils-first-details-of-new-anti-password-sharing-measures
If you’d like an essay-formatted version of this post to read or share, here’s a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/02/02/nonbinary-families/#red-envelopes
Netflix says that its new policy allows members of the same “household” to share an account. This policy comes with an assumption: that there is a commonly understood, universal meaning of “household,” and that software can determine who is and is not a member of your household.
This is a very old corporate delusion in the world of technology. In the early 2000s, I spent years trying to bring some balance to an effort at DVB, whose digital television standards are used in most of the world (but not the USA) when they rolled out CPCM, a DRM system that was supposed to limit video-sharing to a single household.
Their term of art for this was the “authorized domain”: a software-defined family unit whose borders were privately negotiated by corporate executives from media companies, broadcasters, tech and consumer electronics companies in closed-door sessions all around the world, with no public minutes or proceedings.
https://onezero.medium.com/the-internet-heist-part-iii-8561f6d5a4dc
These guys (they were nearly all guys) were proud of how much “flexibility” they’d built into their definition of “household.” For example, if you owned a houseboat, or a luxury car with seatback displays, or a summer villa in another country, the Authorized Domain would be able to figure out how to get the video onto all those screens.
But what about other kinds of families? I suggested that one of our test cases should be a family based in Manila: where the dad travels to remote provinces to do agricultural labor; the daughter is a nanny in California; and the son is doing construction work in the UAE. This suggestion was roundly rejected as an “edge case.”
Of course, this isn’t an edge case. There are orders of magnitude more people whose family looks like this than there are people whose family owns a villa in another country. Owning a houseboat or a luxury car makes you an outlier. Having an itinerant agricultural breadwinner in your family does not.
But everyone who is in the room when a cartel draws up a standard definition of what constitutes a household is almost certainly drawn from a pool that is more likely to have a summer villa than a child doing domestic work or construction labor half a world away. These weirdos, so dissimilar from the global majority, get to define the boxes that computers will shove the rest of the world into. If your family doesn’t look like their family, that’s tough: “Computer says no.”
One day at a CPCM meeting, we got to talking about the problem of “content laundering” and how the way to prevent it would be to put limits on how often someone could leave a household and join another one. No one, they argued, would ever have to change households every week.
I put my hand up and said, “What about a child whose divorced parents share custody of her? She’s absolutely going to change households every week.” They thought about it for a moment, then the rep from a giant IT company that had recently been convicted of criminal antitrust violations said, “Oh, we can solve that: we’ll give her a toll-free number to call when she gets locked out of her account.”
That was the solution they went with. If you are a child coping with the dissolution of your parents’ marriage, you will have the obligation to call up a media company every month — or more often — and explain that Mummy and Daddy don’t love each other any more, but can I please have my TV back?
I never forgot that day. I even wrote a science fiction story about it called (what else?) “Authorized Domain”:
https://craphound.com/news/2011/10/31/authorised-domain/
I think everyone understood that this was an absurd “solution,” but they had already decided that they were going to complete the seemingly straightforward business of defining a category like “household” using software, and once that train left the station, nothing was going to stop it.
This is a recurring form of techno-hubris: the idea that baseline concepts like “family” have crisp definitions and that any exceptions are outliers that would never swallow the rule. It’s such a common misstep that there’s a whole enre* called “Falsehoods Programmers Believe About ______”:
https://github.com/kdeldycke/awesome-falsehood
In that list: names, time, currency, birthdays, timezones, email addresses, national borders, nations, biometrics, gender, language, alphabets, phone numbers, addresses, systems of measurement, and, of course, families. These categories are touchstones in our everyday life, and we think we know what they mean — but then we try to define them, and the list of exceptions spirals out into a hairy, fractal infinity.
Historically, these fuzzy categorical edges didn’t matter so much, because they were usually interpreted by humans using common sense. My grandfather was born “Avrom Doctorovitch” (or at least, that’s one way to transliterate his name, which was spelled in a different alphabet, but which was also transliterating his first name from yet another alphabet). When he came to Canada as a refugee, his surname was anglicized to “Doctorow.” Other cousins are “Doctorov,” “Doctoroff,” and “Doktorovitch.”
Naturally, his first name could have been “Abraham” or “Abe,” but his first employer (a fellow Eastern European emigre) decided that was too ethnic and in sincere effort to help him fit in, he called my grandfather “Bill.” When my grandfather attained citizenship, his papers read “Abraham William Doctorow.” He went by “Abe,” “Billy,” “Bill,” “William,” “Abraham” and “Avrom.”
Practically, it didn’t matter that variations on all of these appeared on various forms of ID, contracts, and paperwork. His reparations check from the German government had a different variation from the name on the papers he used to open his bank account, but the bank still let him deposit it.
All of my relatives from his generation have more than one name. Another grandfather of mine was born “Aleksander,” and called “Sasha” by friends, but had his name changed to “Seymour” when he got to Canada. His ID was also a mismatched grab-bag of variations on that theme.
None of this mattered to him, either. Airlines would sell him tickets and border guards would stamp his passport and rental agencies would let him drive away in cars despite the minor variations on all his ID.
But after 9/11, all that changed, for everyone who had blithely trundled along with semi-matching names across their official papers and database entries. Suddenly, it was “computer says no” everywhere you turned, unless everything matched perfectly. There was a global rush for legal name-changes after 9/11 — not because people changed their names, but because people needed to perform the bureaucratic ritual necessary to have the name they’d used all along be recognized in these new, brittle, ambiguity-incinerating machines.
For important categories, ambiguity is a feature, not a bug. The fact that you can write anything on an envelope (including a direction to deliver the letter to the granny flat over the garage, not the front door) means that we don’t have to define “address” — we can leave it usefully hairy around the edges.
Once the database schema is formalized, then “address” gets defined too — the number of lines it can have, the number of characters each line can have, the kinds of characters and even words (woe betide anyone who lives in Scunthorpe).
If you have a “real” address, a “real” name, a “real” date of birth, all of this might seem distant to you. These “edge” cases — seasonal agricultural workers, refugees with randomly assigned “English” names — are very far from your experience.
That’s true — for now (but not forever). The “Shitty Technology Adoption Curve” describes the process by which abusive technologies work their way up the privilege gradient. Every bad technological idea is first rolled out on poor people, refugees, prisoners, kids, mental patients and other people who can’t push back.
Their bodies are used to sand the rough edges and sharp corners off the technology, to normalize it so that it can climb up through the social ranks, imposed on people with more and more power and influence. 20 years ago, if you ate your dinner under an always-on #CCTV, it was because you were in a supermax prison. Today, it’s because you bought a premium home surveillance system from Google, Amazon or Apple.
https://pluralistic.net/2021/07/29/impunity-corrodes/#arise-ye-prisoners
The Netflix anti-sharing tools are designed for rich people. If you travel for business and stay in the kind of hotel where the TV has its own Netflix client that you can plug your username and password into, Netflix will give you a seven-day temporary code to use.
But for the most hardcore road-warriors, Netflix has thin gruel. Unless you connect to your home wifi network every 31 days and stream a show, Netflix will lock out your devices. Once blocked, you have to “contact Netflix” (laughs in Big Tech customer service).
Why is Netflix putting the screws to its customers? It’s part of the enshittification cycle, where platform companies first allocate surpluses to their customers, luring them in and using them as bait for business customers. Once they turn up, the companies reallocate surpluses to businesses, lavishing them with low commissions and lots of revenue opportunities. And once they’re locked in, the company starts to claw back the surpluses for itself.
https://pluralistic.net/2023/01/21/potemkin-ai/#hey-guys
Remember when Netflix was in the business of mailing red envelopes full of DVDs around the country? That was allocating surpluses to users. The movie companies hated this, viewed it as theft — a proposition that was at least as valid as Netflix’s complaints about password sharing, but every pirate wants to be an admiral, and when Netflix did it to the studios, that was “progress,” but when you do it to Netflix, that’s theft.
Then, once Netflix had users locked in and migrated to the web (and later, apps), it shifted surpluses to studios, paying fat licensing fees to stream their movies and connect them to a huge audience.
Finally, once the studios were locked in, Netflix started to harvest the surplus for its shareholders: raising prices, lowering streaming rates, knocking off other studios’ best performing shows with in-house clones, etc. Users’ surpluses are also on the menu: the password “sharing” that let you define a household according to your family’s own idiosyncratic contours is unilaterally abolished in a quest to punish feckless Gen Z kids for buying avocado toast instead of their own Netflix subscriptions.
Netflix was able to ignore the studios’ outraged howls when it built a business by nonconsenually distributing their products in red envelopes. But now that Netflix has come for your family, don’t even think about giving Netfix some of what it gave to the MPAA.
As a technical matter, it’s not really that hard to modify Netflix’s app so that every stream you pull seems to come from your house, no matter where you are. But doing so would require reverse-engineering Netflix’s app, and that would violate Section 1201 of the DMCA, the CFAA, and eleventy-seven other horrible laws. Netflix’s lawyers would nuke you until the rubble bounced.
When Netflix was getting started, it could freely interoperate with the DVDs that the studios had put on the market. It could repurpose those DVDs in ways that the studios strenuously objected to. In other words, Netfix used adversarial interoperability (AKA Competitive Compatibility or ComCom) to launch its business:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
Today, Netflix is on the vanguard of the war to abolish adversarial interop. They helped lead the charge to pervert W3C web-standards, creating a DRM video standard called EME that made it a crime to build a full-featured browser without getting permission from media companies and restricting its functionality to their specifications:
https://blog.samuelmaddock.com/posts/the-end-of-indie-web-browsers/
When they used adversarial interoperability to build a multi-billion-dollar global company using the movie studios’ products in ways the studios hated, that was progress. When you define “family” in ways that makes Netflix less money, that’s felony contempt of business model.
[Image ID: A Victorian family tree template populated by tintypes of old-timey people. In the foreground stands a menacing, chainsaw-wielding figure, his face obscured by a hoodie. The blade of the chainsaw is poised to chop down the family tree. A Netflix 'N' logo has been superimposed over the man's face.]
#pluralistic#enshittification#shitty technology adoption curve#cpcm#interoperabiltiy#comcom#adversarial interoperability#interop#netflix#family#ambiguity#digitizatio#nym wars#authorized domain#dvb#dvds#password sharing
7K notes
·
View notes
Text
Podcasting "View A SKU"
This week on my podcast, I read my recent Medium column, “View a SKU: Let’s Make Amazon Into a Dumb Pipe,” about how interop can help us demonopolize Amazon and tame its market power:
https://doctorow.medium.com/view-a-sku-32721d623aee
To explain this proposal, I need to start with an axiom: there are lots of problems with Amazon (lots!) but the fact that Amazon is really convenient is not one of those problems. Your use of Amazon isn’t a mark of your “laziness” anymore than your consumption of plastics is a mark of your indifference to the planet.
As Zephyr Teachout writes in her stupendous book Break ’Em Up:
“I like supporting local retail for shopping whenever possible. But I will not shame people for buying from Amazon the magic markers they use to write ‘Break up Bezos’ power’ on a big poster they parade outside their state attorney general’s office.”
https://us.macmillan.com/books/9781250200907/breakemup
The drive to “shop local” is great, but it shouldn’t become a hairshirt. If you buy something from Amazon, it doesn’t necessarily mean that you support union-busting, monopolization and creepy surveillance doorbells. It might just mean that you are out of time and live in a place where Amazon killed most of the retail that survived Walmart.
[Image ID: A Mr Gotcha panel by Matt Bors from The Nib. A downtrodden peasant says, ‘We should improve society somewhat.’ Mr Gotcha replies, ‘Yet you participate in society, curious! I am very intelligent.’]
If you’ve enjoyed Matt Bors’s work, you understand this. It’s the essence of the Mr Gotcha gag. A downtrodden peasant says, “We should improve society somewhat” and Mr Gotcha replies, “Yet you participate in society, curious! I am very intelligent.”
https://pluralistic.net/2020/09/13/theory-of-change/#mr-gotcha
The fact that Amazon has given us a single database in which you can search for a large slice of all the objects of retail commerce, read reviews, and explore alternatives is good, actually. The problem is in how Amazon abuses its workforce, crams its suppliers, self-preferences its own goods, and shifts wealth from taxpaying local businesses to its tax-evading coffers.
The same politics and economics that have made it so hard not to use Amazon have also made working people much poorer, both in terms of money and time. It’s not reasonable to expect people who are piecing together a living from three or four casualized jobs and paying sky-high pump prices to spend hours driving around looking for a local merchant to buy a specific widget at.
But what if we could make shopping locally — where a local alternative existed — easier than shopping at Amazon? What if we could actually turn Amazon into a tool for finding goods at local merchants?
[Image ID: A screenshot from Library Extension, showing an Amazon listing for one of the Divergent books with the ‘Buy’ button replaced by buttons to reserve at a variety of local libraries.]
That’s where my proposal comes in. It was inspired by Library Extension, a browser plugin that notices if you’re looking at a book on Amazon and adds a “Reserve at your local library” button to the page, over the “Add to your cart” button.
https://www.libraryextension.com/
Library Extension is an example of adversarial interoperabitlity (or what we at EFF call “comcom,” short for “competitive compatibility”). That’s when someone adds features to an existing product or service without permission from the company that made it — like an ad-blocker that changes the websites you look at to make them better for you.
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
Library Extension works as well as it does because books all share a common set of unique identifiers: the ISBN, which is easy to detect on a webpage and also easy to look up in a database of library books. Shared identifiers make cross-referencing easy.
[Image ID: The product listing and URL for an Amazon product page, with the ASINs highlighted in pink.]
As it happens, Amazon has assigned unique identifiers to virtually anything you might want to buy: the ASIN (Amazon Standard Identification Number). What if a co-op created a database that cross-referenced ASINs with other inventory numbers (like UPCs and SKUs)? We could offer inventory control system plug-ins to merchants that automatically listed their inventory in a central, co-operatively managed database of what was for sale, where.
Then, users who wanted to shop locally could install a Library Extension-like browser plugin that did a quick lookup whenever they browsed an Amazon product page, and, if the product was for sale locally, replace the “Add to Cart” button with a “Buy from local merchant” one, which would automatically process a payment to the local merchant using a payment method stored in your browser (no need to set up a separate account for every merchant).
Likewise, we could expand Library Extension to add a “Buy from bookshop.org” button to every book page, and a “Buy from libro,fm” button to every audiobook page.
In other words, we could turn Amazon into a dumb pipe: a commodity supplier of catalog pages, reviews and recommendations. The conversion of centralized services into dumb pipes is a time-honored tradition, as David Isenberg wrote in his classic 1998 ACM paper:
https://www.isen.com/papers/Dawnstupid.html
Now, could we do this? As a technical matter, sure. A lot would depend on adapting small businesses’ inventory control systems, but the vendors behind those systems would benefit from participating in those adaptations, as would their customers.
What about as a legal matter? Well, IANAL, but…
Your browser is yours. Adapting the web-pages you get served to suit your tastes is unambiguously lawful, as is providing the tools to do so. Hence the rise of ad-blockers, “the biggest boycott in world history”:
https://blogs.harvard.edu/doc/2015/09/28/beyond-ad-blocking-the-biggest-boycott-in-human-history/
The ASIN database is a collection of factual identifiers; the USA has (wisely) not adopted the Database Right that the EU got suckered into, so databases of factual identifiers are not copyrightable:
https://en.wikipedia.org/wiki/Feist_Publications,_Inc.,_v._Rural_Telephone_Service_Co.
Amazon’s terms of service ban you from doing this kind of thing, but US federal judges are increasingly skeptical of attempts to block scraping public information through terms of service:
https://www.fenwick.com/insights/publications/hiq-labs-scrapes-by-again-the-ninth-circuit-reaffirms-that-data-scraping-does-not-violate-the-cfaa
Note that executing this plan won’t solve the Amazon problem, but it will solve an Amazon problem. It’s no substitute for other forms of antitrust enforcement (bans on self-preferencing, forced selloffs of anticompetitive acquisitions, merger scrutiny) but it is faster than those things, and will deliver immediate relief to shoppers and small businesses.
That’s the kind of “tech exceptionalism” I’m completely here for. The breakup of the Bell System took 69 years, all told. We don’t want to wait 69 years before we blunt Amazon’s monopoly power:
https://onezero.medium.com/jam-to-day-46b74d5b1da4
This is why Big Tech is the natural starting place for antitrust: because Big Tech is built atop general purpose computers that can be rendered interoperable, regulators seeking to limit Big Tech power have unique, powerful additions to their to toolkits.
I know that some of my comrades-in-arms are skeptical of Big Tech antitrust, correctly asserting that other monopolies (like telecoms and entertainment companies) are also corrupt monopolies in sore need of antitrust attention. I want to break those companies’ corporate power, too! In fact, my next book is all about limiting the power of tech and entertainment judges to screw creative workers:
http://www.beacon.org/Chokepoint-Capitalism-P1856.aspx
But the availability of cool, fast-acting interoperability remedies make Big Tech the natural place to start — the natural vanguard for the anti-monopoly fights we’ll have to bring to every sector, from cheerleading uniforms to beer, from finance to international shipping:
https://www.openmarketsinstitute.org/learn/monopoly-by-the-numbers
Taming Big Tech is where we start, not where we end. It’s the orchard with the most low-hanging fruit. Racking up victories against Big Tech will create the political will and the movement power to go after all those other monopolies:
https://www.eff.org/deeplinks/2019/07/interoperability-fix-internet-not-tech-companies
Here’s the podcast episode: https://craphound.com/news/2022/07/31/view-a-sku-lets-make-amazon-into-a-dumb-pipe/
Here’s a direct link to the MP3 (hosting courtesy of the Internet Archive; they’ll host your stuff for free, forever):
https://archive.org/download/Cory_Doctorow_Podcast_432/Cory_Doctorow_Podcast_432_-_View_a_SKU.mp3
And here’s a link to my podcast feed: https://feeds.feedburner.com/doctorow_podcast
[Image ID: A modified Amazon product listing page; the buy with Amazon button and Prime logo have been replaced with a "Buy from DIY Center" button a 'Buy local' logo with an upside-down Amazon smile logo, and the 'In Stock' wordmark has been replaced with 'In stock at a local merchant: DIY Center.]
73 notes
·
View notes
Text
Indonesia's gig work tech resistance
Gojek is a $10B Indonesian “super app” that combines “Postmates, Apple Pay, Venmo, and Uber” serviced by an army of ojol — drivers — who are subjected to all the high-handed algorithmic horrors that gig workers everywhere suffer through.
https://www.vice.com/en/article/7kvpng/delivery-drivers-are-using-grey-market-apps-to-make-their-jobs-suck-less
But Indonesian ojol aren’t helpless before their apps; a legion of toolsmiths produce, share, sell and support “tuyul apps” named for “a child-like spirit in Indonesian folklore that helps his human master earn money by stealing,” which modify the Gojek app.
As part of her MIT PhD, Rida Qadri studied Gojek, ojol and tuyul apps, and her account of the grey-market Gojek ecosystem for Motherboard is riveting.
https://www.vice.com/en/article/7kvpng/delivery-drivers-are-using-grey-market-apps-to-make-their-jobs-suck-less
Tuyul apps are wildly innovative and diverse, from tools to magnify text so older ojol drivers who can read the tiny default app’s text, to filters that allow drivers and riders to preview jobs, avoiding the algorithmic penalty for turning down a job after accepting it.
Indeed, many tuyul apps are tools that permit workers to resist their algorithmic employer’s “optimizations,” which inevitably “optimize” the work so as much value as possible is transferred from the workers to their bosses.
Take GPS-spoofing. Gojek’s corporate overlords have decreed that drivers have to be close to a pickup to be eligible to get the job. On its face, this sounds reasonable, but in practice, it creates massive jams around train stations where unsheltered riders wait in the rain.
Gojek created a situation that has clogged the roads around stations, creating traffic hazards and introducing delays into deliveries. Riders are on site and better equipped to decide how to do their job than a distant, unaccountable product manager.
Riders use GPS spoofers to trick the app into thinking they’re onsite when really they’re waiting at a sensible distance.
Tuyul app creators are drivers with tech knowhow, who fell into the work as part of mutual aid networks.
Over time, this has matured into IT Jalanan -”IT of the Road” — a full-service, somewhat ad-hoc tech support network of IT specialists who build, service and use apps that make gig workers’ lives better.
They have extensive documentation for users on how to root their phones and side-load the third party apps. Apps are sold and supported through Whatsapp and other platforms, along with service and support packages.
Crucially, the support for tuyul apps is much better than the support Gojek offers to gig workers when they struggle with the bugs in its app — making downloading a third-party mod a faster and better experience than trying to get Gojek to fix its shit.
Not all tuyul apps are benign. Some are scams that rip off drivers, other are scams that help drivers rip off Gojek. Gojek On Twitter, a driver community organized against being made “a slave of the algorithm,” has a mixed position on tuyul apps.
One of GOT’s founders has proposed that the GPS spoofing be integrated into Gojek’s official app, allowing users to place their pin within 1km of their actual location.
All of this is a powerful lesson in the importance of Adversarial Interoperability (AKA Competitive Compatibility/comcom), the practice of modifying an existing technology against the wishes (or without permission) of its maker.
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
Comcom allows the users of technology to override its designers’ choices based on their local, up-to-the-minute knowledge of their circumstances, like overriding your car’s mandatory software update when you’re trying to escape a wildfire.
https://locusmag.com/2021/07/cory-doctorow-tech-monopolies-and-the-insufficient-necessity-of-interoperability/
The point of interop isn’t “competition” or even “efficiency” — it’s technological self-determination, the right to decide how you live your life. This does lead to competitiveness and autonomous workers are more efficient than drones, but that’s not the point.
Companies like Gojek lump all mods into the same basket — mods that let drivers do their job better and mods that enable fraud. From Gojek’s perspective, anything that frustrates their shareholders is bad news —it’s all “felony contempt of business model.”
That’s why laws, not corporate decree, should determine what kind of interoperability we permit and which ones we don’t. Our current laws (in the US, Sec 1201 of DMCA, CFAA, etc) simply say, “If the manufacturer says no, it’s not allowed.”
https://gizmodo.com/in-2030-you-wont-own-any-gadgets-1847176540
We can — and should — draft laws that prevent fraud and require practices that don’t endanger others, while legalizing modifying our technology in ways that are socially beneficial and help workers and other users exercise technological self-determination.
Letting users modify their own technology makes life better for everyone. John Deere — archnemesis of users’ right to mod — “invented” modern tractors through engineers observing farmers’ mods to their Deeres and putting the ideas into production.
https://securityledger.com/2019/03/opinion-my-grandfathers-john-deere-would-support-our-right-to-repair/
Meanwhile, Gbwhatsapp and its constellation of primarily African Whatsapp mods are more popular on the continent than Facebook Messenger. There are many Whatsapp mods, used for different kinds of users Africa’s varied regions, nations and cities.
https://www.eff.org/deeplinks/2020/03/african-whatsapp-modders-are-masters-worldwide-adversarial-interoperability
Facebook rails against Gbwhatsapp the same way that Gojek rails against tuyul apps, pointing to the scams and harms from the mods that are created by crooks. But just like Gojek, FB lumps the mods that empower users in with the mods that harm them.
There are ways that interoperability can go wrong, but dominant corporations can’t be trusted with the decision about which mods are okay and which ones aren’t — they are terminally compromised by their own self-interest.
The rules for modding — privacy protections, anti-fraud protection and more — should come from democratically accountable legislatures, not the secret machinations of corporate boardrooms.
https://www.eff.org/wp/interoperability-and-privacy
159 notes
·
View notes
Text
Podcasting "When Automation Becomes Enforcement"

This week on my podcast, I read my recent Medium column, “When Automation Becomes Enforcement,” about the debate of interoperability and end-to-end encryption in the EU’s Digital Markets Act, and how that relates to the long-running battle over who’s in charge: you, or your computer?
https://onezero.medium.com/when-automation-becomes-enforcement-677461a78e62
When I first encountered the idea of disappearing messages, I thought they were stupid, but I was wrong. I thought that the point of disappearing messages was to let you send secrets to someone you didn’t trust, because the message would disappear and thus be safe.
Obviously, this is stupid. If you send a secret to someone you don’t trust, that untrustworthy person can take a screenshot, or use another device to photograph their screen. Or, you know, they can just remember the secret and blab it. Technology can’t make untrustworthy people trustworthy.
But then I had the other use-case for disappearing messages explained to me: not enforcing agreements about data-handling, but rather, automating them. You and I might trust each other not to blab our mutual secrets, but we might also agree that the best way to keep those secrets from leaking is to delete the record of our conversation.
We understand that we’re both fallible. We know that even with the best of intentions, we might forget to delete our chat logs, and that exposes them to being leaked, or coerced from us. A disappearing messages tool hands “remembering to delete files on a regular basis” — something humans are bad at doing — to a computer, which is very good at this.
The reason I assumed that disappearing messages were designed for the stupid fantasy of trusting untrustworthy people is that there’s a long history of this. Microsoft tried (unsuccessfully) to snuff out rivals to Microsoft Office in the mid-2000s with a product called “Information Rights Management” (IRM).
IRM was DRM for Office files, whose pitch was that you could send a Word doc or an Excel sheet to someone you didn’t trust, and IRM would stop them from leaking or printing or forwarding those docs.
IRM could be defeated by all the same measures as disappearing messages, but Microsoft claimed it could mitigate these with Trusted Computing — which would prevent you from installing non-Microsoft operating systems and software on your computer.
Microsoft used the unreliability of IRM to insist that all our computers be designed to disobey us, and take orders from Microsoft instead. If Microsoft said you couldn’t install an OS, or an app, or take a screenshot, your computer would listen to Microsoft — not you. In the process, Microsoft would become tech’s gatekeeper, with the power to approve or deny all new services and products.
Since then, this idea has spread to other companies, especially (and ironically), Apple — the company whose interoperable Office programs (Pages, Numbers, Keynote) Microsoft wanted to extinguish with IRM and Trusted Computing.
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
Today, Apple is one of the Big Tech companies targeted by the EU’s Digital Markets Act (DMA), which will require the largest tech companies to connect their messenging platforms to small companies systems on request.
This has the potential to do great good — and also great harm. On the positive side, forcing interop on tech giants will allow users who stick with them to leave for better rivals, without having to abandon their connections to customers, community and family. That will create space for co-ops, nonprofits and startups with better privacy policies and firmer commitments to user rights (for example, companies that, unlike Apple, would exit the Chinese market rather than allowing the Chinese state to backdoor its encryption).
On the negative side, the additional complexity of interop could lead to errors in the end-to-end encryption (E2EE) of instant message systems, which could expose users to terrible risks that the digital rights community has warned us about for 30+ years.
The DMA does include language requiring that interop embrace and uphold E2EE, but it also sets deadlines for the integration of interop with E2EE, and it’s entirely conceivable that these deadlines will arrive before a satisfactory, secure technical solution is in place. That has digital rights activists (including me) worried.
But within the debate over DMA and E2EE is a latent, unarticulated disagreement about measures like disappearing messages — ambiguous security measures that some users treat as agreement automation tools and others as enforcement tools. If disappearing messages are enforcement tools, then interop is in big trouble — because that enforcement requires that every chat client treat its owner as an attacker, and override their judgment when senders demand it.
That’s antithetical to the mission of DMA: to allow users to decide how their devices operate. I want there to be disappearing messages with “override” buttons — that would let you decide to retain your boss’s harassing messages, say, so you could show them to your lawyer.
For many years, disappearing message vendors were able to avoid speaking clearly about their products’ use-case, benefiting from the enforcement/automation ambiguity. Some users naively assumed they were getting enforcement, while others understood that automation was all they could hope for.
Now, though, interop is forcing the question — and that’s a good thing. The users who thought they were getting enforcement from disappearing messages were living in a fool’s paradise, after all!
We definitely need to ensure that the DMA doesn’t weaken E2EE — but that doesn’t have anything to do with ensuring that the DMA turns disappearing messages into an enforcement tool. Not only is that impossible — merely attempting it will give more market-structuring power to monopolists.
Here’s a link to the podcast episode:
https://craphound.com/news/2022/04/10/when-automation-becomes-enforcement/
And here’s a direct link to the MP3 (hosting courtesy of the Internet Archive; they’ll host your stuff for free, forever):
https://archive.org/download/Cory_Doctorow_Podcast_422/Cory_Doctorow_Podcast_422_-_When_Automation_Becomes_Enforcement.mp3
And here’s the RSS for my podcast:
https://feeds.feedburner.com/doctorow_podcast
12 notes
·
View notes
Text
Facebook's war on switching costs

If you took a drink every time an economist used “network effects” to explain why Big Tech is so big, you’d get very, very drunk.
To be fair to economists, network effects are important to the Big Tech story.
A system is said to have network effects if it gets better when more people use it. That certainly describes Facebook — you join FB because of the friends that are already there, and then someone else joins because you’re there.
https://en.wikipedia.org/wiki/Network_effect
But network effects are how FB gets big, not how it stays big. Because even though you might join FB to talk to your friends, the reason you stay there — despite surveillance and FB’s many abusive tactics — is that leaving FB will cut you off from those friends.
There’s no technical reason you couldn’t stay in touch with FB friends without being an FB user. You can switch phone companies or email providers without walking away from the family, community and customers you’re connected to.
FB deliberately engineers its system to block “interoperability” — the ability to plug rival services into its network.
Interop would let non-FB users connect with FB users, and make it so FB users don’t have to choose between their community and Facebook’s abuses.
The economist’s term for this is “switching costs.” A “switching cost” is whatever you have to give up to switch between products or services — switching from Audible to a rival platform would cost you all your audiobooks, for example, thanks to Audible’s DRM.
Facebook deliberately engineers its products to have high switching costs so that it can impose more pain on its users without losing them. So long as the pain of staying is less than the pain of leaving, Facebook calculates it can maintain its dominance.
Network effects are how Facebook attracts users, but switching costs are how it holds them hostage.
The higher the switching costs, the bigger the shit sandwich Facebook can force you to eat before you leave.
That’s why interoperability is such a big deal — because it lowers the switching costs. If you can take your apps or friends or files or media with you when you leave a service, then the service has to treat you better, lest you depart.
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
Now, I’ve been accusing Facebook of deliberately raising its switching costs for years, based on the obvious external evidence of this conduct. But to be honest, I didn’t have any proof that this was going on…
…Until now.
In its amended antitrust complaint against Facebook, the FTC draws on the internal communications it compelled Facebook to give up in order to build up a factual record of FB’s abuse of switching costs, which go all the way to CEO Mark Zuckerberg.
https://www.ftc.gov/system/files/documents/cases/ecf_75-1_ftc_v_facebook_public_redacted_fac.pdf
I published a collection of these for EFF’s Deeplinks blog, under the title, “Facebook’s Secret War on Switching Costs.”
https://www.eff.org/deeplinks/2021/08/facebooks-secret-war-switching-costs
Here’s some highlights:
Para 87: Zuckerberg’s M&A chief writes to him to say, “imo, photos (along with comprehensive/smart contacts and unified messaging) is perhaps one of the most important ways we can make switching costs very high for users…
“…if we are where all users’ photos reside because the upoading [sic] (mobile and web), editing, organizing, and sharing features are best in class, will be very tough for a user to switch if they can’t take those photos and associated data/comments with them.”
Translation: “I figured out a way to get our users to eat a very large shit sandwich indeed. Just take all their family photos hostage!”
Para 187: An exec explains how FB is preventing G+ from succeeding: “[P]eople who are big fans of G+ are having a hard time convincing their friends to participate because…switching costs would be high due to friend density on Facebook.”
Translation: Our users would rather be on G+ but we’ve stopped them because leaving means leaving behind their friends, because we won’t interconnect with Google’s service.
Para 212: One of Zuck’s execs sends him a memo reading, “ if we are where all users’ photos reside . . . will be very tough for a user to switch if they can’t take those photos and associated data/comments with them.”
There’s that shit sandwich again.
I’m so excited to see this stuff in the FTC complaint — not because it vindicates me (it was obvious that this was going on, though having the receipts is nice), but because it suggests that US antitrust enforcers are homing in on switching costs as an anticompetitive force.
The problem with the network effects story is that it’s a counsel of despair: “Well, this company has attained scale and now there’s no way they can lose.”
That’s bullshit. You don’t search Altavista with your Cray.
Network effects inflate services, but low switching costs let the air out again. Interop is the escape valve that keeps big tech firms from sucking up all the oxygen and asphyxiating their rivals.
46 notes
·
View notes