#and rewrites data at the byte level
Explore tagged Tumblr posts
Text

On Incremental Improvement:
With VCF Southwest almost here, and having run into a dead end on getting NetBSD running on my 68030 homebrew computer, Wrap030, I decided to circle back to my multi-user BASIC kernel. There are some important features the system is needing to get it ready for running as an exhibit for all three days of the show.
Memory Protection
There's a fun couple fairly standard BASIC commands, PEEK and POKE. The former will read a byte of memory from a specified address, and the latter will write a byte. These were commonly used in the 8-bit era to manipulate hardware registers. For instance, POKE 53280,1 on the Commodore 64 would set the screen frame color to white by writing 1 to the address 53280.
While there were ways to cause problems by writing bad values to the wrong address, on a single-user home computer the impact was only to the one user. On a multi-user system however, PEEK could be used maliciously to look at private data from other users. An errant POKE command could overwrite user data, kernel data, even code being run by users.
A good multi-user system needs some way to prevent one user from accessing memory used by another user, and to prevent users from overwriting shared code. The Motorola 68030 has a couple tools to solve this problem: separate supervisor & user states, and a built-in Memory Management Unit (MMU).
The supervisor state has access to all instructions and registers in the CPU. The user state is blocked from running certain instructions that would change system state or CPU configuration. I was already using supervisor state for my kernel and user state for BASIC programs, but it doesn't prevent users from accessing memory that doesn't belong to them.
That's what the the MMU is for.
The MMU takes the memory address the CPU is outputting (the Logical Address) and uses a table to remap it to a new address (the Physical Address). That table can hold additional information about how a particular region of memory can be used, and can be configured by the kernel at any time.
So we can, for instance, set up the table to mark the program code for BASIC as read-only when the CPU is in the user state. Or remap the memory allocated to each user so that it always starts at logical address zero. In fact, there's also nothing that requires the entirety of physical memory to be mapped — so as far as one user program is concerned, the other users' memory doesn't even exist.
Adding MMU support to my Multibasic kernel has been a goal from the beginning. It's a challenge though. The 68k MMU is a very capable, very complex beast. It supports tables that are up to four levels deep, supports page sizes from 256B to 32kB, and can use separate data and code tables for both supervisor and user states. It's something I've struggled to understand, but my work with NetBSD helped show me how to use it.
I decided to use 32kB pages and only map the 16MB of actual RAM I have installed. This allowed me to use a single-level table with 512 entries. During startup, the kernel initializes the supervisor table and a table for each user. When switching users, only the Root Pointer register in the MMU needs to be updated point to that user's table.
I was able to get the table initialization running after a few rewrites. And then realized I had forgotten to update the user initialization routines to point to their new logical addresses. And I was using the wrong table entry marker for the user tables, so the MMU was expecting more table entries instead of reading page descriptors. This got me to the point of the kernel running with the MMU enabled and I could even run a user program or two in BASIC, but if I tried to run three user programs, things got ... weird.
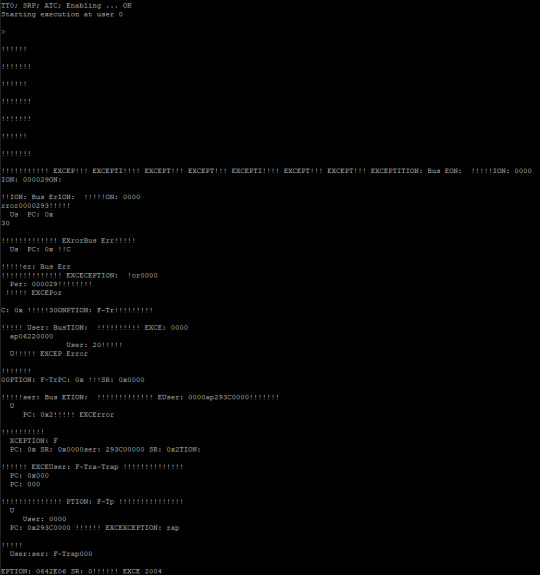
Overlapping exceptions is never a good sign. Or, it usually isn't. In this case I was trying to print out some debugging data for exceptions which takes a relatively long time. Longer than my timer interrupt, in fact … I had forgotten to disable the timer at the start of an exception handler. My timer was doing exactly what it was supposed to, I just needed to stop it when handling exceptions. That fixed the overlapping exceptions, but I still couldn't run more than two programs at a time.
This one had me stuck for a while, but I finally decided to review the NetBSD source to see what I was doing differently. All of my initialization and task switching code looked similar; there was just one thing that stood out to me as being different — NetBSD was clearing CPU cache on task switch and I wasn't. The 68030 doesn't have a large cache, surely that's not the probl…
It was the CPU cache.
Once I added the single instruction to clear cache when switching users, everything ran smoothly no matter how many programs I ran.
Loading from Disk
Having to enter programs by hand each time you want to run one is no fun. It's tedious and error-prone. Sure, it was common four decades ago for books and magazines to publish listings of BASIC programs. But after taking the time to carefully enter in hundreds of lines of code, most people are going to want to save the program to disk so it can be quickly reloaded later.
In my case, I would like to have a few demos, games, and interactive programs available for my exhibit. I do not want to have to type them in by hand every morning. It's time I finally sit down and figure out how to add file loading to EhBASIC.
The EASy68k applications page has a link to an archive of EhBASIC that supports the EASy68k simulator's I/O traps. This was the perfect starting point. All I needed was to add new system calls to my kernel for similar file open, read, and close operations, then update the EhBASIC file handling routines to use them.
I started by copying the Elm-Chan FAT filesystem library I had used for my bootloader into my kernel. It's a great minimal C library for FAT-formatted disks that doesn't take much to get up and running. I was able to write wrapper functions for its f_open(), f_read(), and f_close() functions that worked with my existing system call format.
This went surprisingly well. I found that EhBASIC was trying to re-open the file after each line, so I did have to update my code to keep track of whether it had reached the end of the file yet. That got me to the point where it would read the entire program and echo it to the terminal, but it couldn't run anything. It turns out EhBASIC was using address refused A0 for a line pointer; gcc C convention treats A0 as a scratch register that doesn't normally need to be saved. I just had to be sure to save the register contents to memory before calling the filesystem library functions.

Finally, I can load programs from disk instead of having to type them in manually every time!
Printing Disk Contents
It would be really helpful to be able to see what programs are on the disk. Loading a program requires entering the LOAD command followed by the filename. That's hard to do without knowing what programs are available.
Luckily, the Elm-Chan FatFs library also has functions for reading directory contents. I just needed to add three new system calls for the directory counterparts to the previous file operations.
EhBASIC didn't already have a command for printing directory contents though, I would have to add one. I wrote the function and was able to use the built-in CALL command to run it by the compiled address of the function, but CALL $100178 is not the easiest to remember.
I tried adding a new command, CAT (short for Catalog, a common directory listing command for early BASIC systems), to the command tables. All it would give me was a Syntax Error, however. I eventually stumbled onto the answer for this one — when parsing a line of code, EhBASIC will check if the token for a given keyword is greater or less than the token for the TAB keyword. Keywords less than TAB are treated as commands that can be executed at the beginning of a line; keywords greater than TAB must follow another statement such as PRINT. All I needed to do was move my new CAT command above TAB in the table.
On Incremental Improvement
These three new features go a long way towards making the system something robust enough and usable enough that I feel good about running it as an interactive exhibit for VCFSW this year.
But more than that, these new features bring my little Multibasic kernel just that much closer to a "proper" operating system — it is now a preemptive multiuser kernel with hardware memory protection and the ability to load programs from disk.
It currently does not support saving files to disk (intentionally omitted for now), doesn't support dynamic memory allocation, and can't run any processes other than the eight instances of BASIC. But it is starting to look the part. And I am definitely proud of the work that I have managed to do on this project.
If you would like to see Wrap030 running Multibasic in person, I will be exhibiting it June 20-22, 2025 at VCF Southwest in Richardson, Texas. This will be the third annual VCFSW since it was rebooted after a decade-long hiatus, and the third year in a row that I have had the opportunity to exhibit and volunteer for the show. This year is bigger than ever with over 90 exhibitors & vendors and a full schedule of workshops, talks, & presentations. If you're in the area, I highly recommend attending!
#wrap030#mc68030#motorola 68k#motorola 68030#debugging#vcfsw#vcf southwest#retrotech#homebrew computing#homebrew computer#retro computing#vintage computing#vintage computer festival#vintage computer festival southwest 2025#os development#operating systems#basic programming
15 notes
·
View notes
Text
This Week in Rust 541
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on Twitter or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Official
Announcing Rust 1.77.1
Changes to u128/i128 layout in 1.77 and 1.78
Newsletters
This Week In Bevy: 2d Lighting, Particle Systems, Meshlets, and more
Project/Tooling Updates
Dioxus 0.5: Signal Rewrite, Remove lifetimes, CSS Hotreloading, and more!
EtherCrab 0.4.0: Pure Rust EtherCAT, now with Distributed Clocks
nethsm 0.1.0 - first release for this high level library for the Nitrokey NetHSM
BugStalker v0.1.3 released - first release of rust debugger
git-cliff 2.2.0 is released! (highly customizable changelog generator)
Observations/Thoughts
On Reusing Arc and Rc in Rust
Who killed the network switch?
Xr0 Makes C Safer than Rust
Easy Mode Rust
Bashing Bevy To Bait Internet Strangers Into Improving My Code
Conway's Game of Life Through Time
Functions Everywhere, Only Once: Writing Functions for the Everywhere Computer
Rust Bytes: Is Rust the Future of JavaScript Tooling?
Explaining the internals of async-task from the ground up
Programming ESP32 with Rust: OTA firmware update
Fast Development In Rust, Part 2
Rust Walkthroughs
Modelling Universal Domain Types in Rust
[video] developerlife.com - Get started with unit testing in Rust
Research
Rust Digger: More than 14% of crates configure rustfmt. 35 Have both rustfmt.toml and .rustfmt.toml
Miscellaneous
Building a Managed Postgres Service in Rust: Part 1
Beware of the DashMap deadlock
Embedded Rust Bluetooth on ESP: BLE Client
Rust Unit and Integration Testing in RustRover
[podcast] cargo-semver-checks with Predrag Gruevski — Rustacean Station
[video] Data Types - Part 3 of Idiomatic Rust in Simple Steps
[video] Deconstructing WebAssembly Components by Ryan Levick @ Wasm I/O 2024
[video] Extreme Clippy for new Rust crates
[video] [playlist] Bevy GameDev Meetup #2 - March 2024
Building Stock Market Engine from scratch in Rust (I)
Crate of the Week
This week's crate is cargo-unfmt, a formatter that formats your code into block-justified text, which sacrifices some readability for esthetics.
Thanks to Felix Prasanna for the self-suggestion!
Please submit your suggestions and votes for next week!
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
No calls for testing were issued this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Call for Participation; projects and speakers
CFP - Projects
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
greptimedb - Support specifying time ranges in the COPY FROM statement to avoid importing unwanted data
greptimedb - Support converting UNIX epoch numbers to specified timezone in to_timezone function
mirrord - Capability to modify the local listen address
mirrord - Fix all check-rust-docs warnings
Hyperswitch - [REFACTOR]: Remove Default Case Handling - Braintree
Hyperswitch - [REFACTOR]: Remove Default Case Handling - Fiserv
Hyperswitch - [REFACTOR]: Remove Default Case Handling - Globepay
If you are a Rust project owner and are looking for contributors, please submit tasks here.
CFP - Speakers
Are you a new or experienced speaker looking for a place to share something cool? This section highlights events that are being planned and are accepting submissions to join their event as a speaker.
* RustConf 2024 | Closes 2024-04-25 | Montreal, Canada | Event date: 2024-09-10 * RustLab 2024 | Closes 2024-05-01 | Florence, Italy | Event date: 2024-11-09 - 2024-11-11 * EuroRust 2024| Closes 2024-06-03 | Vienna, Austria & online | Event date: 2024-10-10 * Scientific Computing in Rust 2024| Closes 2024-06-14 | online | Event date: 2024-07-17 - 2024-07-19 * Conf42 Rustlang 2024 | Closes 2024-07-22 | online | Event date: 2024-08-22
If you are an event organizer hoping to expand the reach of your event, please submit a link to the submission website through a PR to TWiR.
Updates from the Rust Project
431 pull requests were merged in the last week
CFI: (actually) check that methods are object-safe before projecting their receivers to dyn Trait in CFI
CFI: abstract Closures and Coroutines
CFI: fix drop and drop_in_place
CFI: fix methods as function pointer cast
CFI: support calling methods on supertraits
add a CurrentGcx type to let the deadlock handler access TyCtxt
add basic trait impls for f16 and f128
add detection of (Partial)Ord methods in the ambiguous_wide_pointer_comparisons lint
add rust-lldb pretty printing for Path and PathBuf
assert that ADTs have the right number of args
codegen const panic messages as function calls
coverage: re-enable UnreachablePropagation for coverage builds
delegation: fix ICE on wrong Self instantiation
delegation: fix ICE on wrong self resolution
do not attempt to write ty::Err on binding that isn't from current HIR Owner
don't check match scrutinee of postfix match for unused parens
don't inherit codegen attrs from parent static
eagerly instantiate closure/coroutine-like bounds with placeholders to deal with binders correctly
eliminate UbChecks for non-standard libraries
ensure std is prepared for cross-targets
fix diagnostics for async block cloning
fixup parsing of rustc_never_type_options attribute
function ABI is irrelevant for reachability
improve example on inserting to a sorted vector to avoid shifting equal elements
in ConstructCoroutineInClosureShim, pass receiver by mut ref, not mut pointer
load missing type of impl associated constant from trait definition
make TyCtxt::coroutine_layout take coroutine's kind parameter
match ergonomics 2024: implement mutable by-reference bindings
match lowering: build the Place instead of keeping a PlaceBuilder around
match lowering: consistently merge simple or-patterns
match lowering: handle or-patterns one layer at a time
match lowering: sort Eq candidates in the failure case too
pattern analysis: Require enum indices to be contiguous
replace regions in const canonical vars' types with 'static in next-solver canonicalizer
require Debug for Pointee::Metadata
require DerefMut and DerefPure on deref!() patterns when appropriate
rework opaque type region inference
simplify proc macro bridge state
simplify trim-paths feature by merging all debuginfo options together
store segment and module in UnresolvedImportError
suggest associated type bounds on problematic associated equality bounds
suggest correct path in include_bytes!
use the Align type when parsing alignment attributes
warn against implementing Freeze
enable cargo miri test doctests
miri: avoid mutating the global environment
miri: cotrol stacked borrows consistency check with its own feature flag
miri: experiment with macOS M1 runners
miri: extern-so: give the version script a better name; show errors from failing to build the C lib
miri: speed up Windows CI
miri: tree Borrows: Make tree root always be initialized
don't emit load metadata in debug mode
avoid some unnecessary query invocations
stop doing expensive work in opt_suggest_box_span eagerly
stabilize ptr.is_aligned, move ptr.is_aligned_to to a new feature gate
stabilize unchecked_{add,sub,mul}
make {integer}::from_str_radix constant
optimize core::char::CaseMappingIter
implement Vec::pop_if
remove len argument from RawVec::reserve_for_push
less generic code for Vec allocations
UnixStream: override read_buf
num::NonZero::get can be 1 transmute instead of 2
fix error message for env! when env var is not valid Unicode
futures: make access inner of futures::io::{BufReader,BufWriter} not require inner trait bound
regex-syntax: accept {,n} as an equivalent to {0,n}
cargo add: Preserve comments when updating simple deps
cargo generate-lockfile: hold lock before querying index
cargo toml: Warn on unused workspace.dependencies keys on virtual workspaces
cargo fix: bash completion fallback in nounset mode
clippy: large_stack_frames: print total size and largest component
clippy: type_id_on_box: lint on any Box<dyn _>
clippy: accept String in span_lint* functions directly to avoid unnecessary clones
clippy: allow filter_map_identity when the closure is typed
clippy: allow manual_unwrap_or_default in const function
clippy: don't emit duplicated_attribute lint on "complex" cfgs
clippy: elide unit variables linted by let_unit and use () directly instead
clippy: fix manual_unwrap_or_default suggestion ignoring side-effects
clippy: fix suggestion for len_zero with macros
clippy: make sure checked type implements Try trait when linting question_mark
clippy: move box_default to style, do not suggest turbofishes
clippy: move mixed_attributes_style to style
clippy: new lint legacy_numeric_constants
clippy: restrict manual_clamp to const case, bring it out of nursery
rust-analyzer: add rust-analyzer.cargo.allTargets to configure passing --all-targets to cargo invocations
rust-analyzer: implement resolving and lowering of Lifetimes (no inference yet)
rust-analyzer: fix crate IDs when multiple workspaces are loaded
rust-analyzer: ADT hover considering only type or const len not lifetimes
rust-analyzer: check for client support of relative glob patterns before using them
rust-analyzer: lifetime length are not added in count of params in highlight
rust-analyzer: revert debug extension priorities
rust-analyzer: silence mismatches involving unresolved projections
rust-analyzer: use lldb when debugging with C++ extension on MacOS
rust-analyzer: pattern analysis: Use contiguous indices for enum variants
rust-analyzer: prompt the user to reload the window when enabling test explorer
rust-analyzer: resolve tests per file instead of per crate in test explorer
Rust Compiler Performance Triage
A pretty quiet week, with most changes (dropped from the report below) being due to continuing bimodality in the performance data. No particularly notable changes landed.
Triage done by @simulacrum. Revision range: 73476d49..3d5528c
1 Regressions, 2 Improvements, 5 Mixed; 0 of them in rollups 61 artifact comparisons made in total
Full report here
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
Merge RFC 3543: patchable-function-entry
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
No RFCs entered Final Comment Period this week.
Tracking Issues & PRs
Rust
[disposition: merge] Pass list of defineable opaque types into canonical queries
[disposition: merge] Document overrides of clone_from() in core/std
[disposition: merge] Tracking Issue for Seek::seek_relative
[disposition: merge] Tracking Issue for generic NonZero
[disposition: merge] Tracking Issue for cstr_count_bytes
[disposition: merge] privacy: Stabilize lint unnameable_types
[disposition: merge] Stabilize Wasm target features that are in phase 4 and 5
Cargo
[disposition: merge] feat(add): Stabilize MSRV-aware version req selection
New and Updated RFCs
[new] RFC: Add freeze intrinsic and related library functions
[new] RFC: Add a special TryFrom and Into derive macro, specifically for C-Style enums
[new] re-organise the compiler team
Upcoming Events
Rusty Events between 2024-04-03 - 2024-05-01 🦀
Virtual
2024-04-03 | Virtual (Cardiff, UK) | Rust and C++ Cardiff
Rust for Rustaceans Book Club: Chapter 4 - Error Handling
2024-04-03 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2024-04-04 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-04-09 | Virtual (Dallas, TX, US) | Dallas Rust
BlueR: a Rust Based Tool for Robust and Safe Bluetooth Control
2024-04-11 | Virtual + In Person (Berlin, DE) | OpenTechSchool Berlin + Rust Berlin
Rust Hack and Learn | Mirror: Rust Hack n Learn Meetup
2024-04-11 | Virtual (Nürnberg, DE) | Rust Nüremberg
Rust Nürnberg online
2024-04-15 & 2024-04-16 | Virtual | Mainmatter
Remote Workshop: Testing for Rust projects – going beyond the basics
2024-04-16 | Virtual (Dublin, IE) | Rust Dublin
A reverse proxy with Tower and Hyperv1
2024-04-16 | Virtual (Washinigton, DC, US) | Rust DC
Mid-month Rustful
2024-04-17 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
2024-04-18 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-04-25 | Virtual + In Person (Berlin, DE) | OpenTechSchool Berlin + Rust Berlin
Rust Hack and Learn | Mirror: Rust Hack n Learn Meetup
2024-04-30 | Virtual (Dallas, TX, US) | Dallas Rust
Last Tuesday
2024-05-01 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
Africa
2024-04-05 | Kampala, UG | Rust Circle Kampala
Rust Circle Meetup
Europe
2024-04-10 | Cambridge, UK | Cambridge Rust Meetup
Rust Meetup Reboot 3
2024-04-10 | Cologne/Köln, DE | Rust Cologne
This Month in Rust, April
2024-04-10 | Manchester, UK | Rust Manchester
Rust Manchester April 2024
2024-04-10 | Oslo, NO | Rust Oslo
Rust Hack'n'Learn at Kampen Bistro
2024-04-11 | Bordeaux, FR | Rust Bordeaux
Rust Bordeaux #2 : Présentations
2024-04-11 | Reading, UK | Reading Rust Workshop
Reading Rust Meetup at Browns
2024-04-15 | Zagreb, HR | impl Zagreb for Rust
Rust Meetup 2024/04: Building cargo projects with NIX
2024-04-16 | Bratislava, SK | Bratislava Rust Meetup Group
Rust Meetup by Sonalake #5
2024-04-16 | Leipzig, DE | Rust - Modern Systems Programming in Leipzig
winnow/nom
2024-04-16 | Munich, DE + Virtual | Rust Munich
Rust Munich 2024 / 1 - hybrid
2024-04-17 | Bergen, NO | Hubbel kodeklubb
Lær Rust med Conways Game of Life
2024-04-20 | Augsburg, DE | Augsburger Linux-Infotag 2024
Augsburger Linux-Infotag 2024: Workshop Einstieg in Embedded Rust mit dem Raspberry Pico WH
2024-04-23 | Berlin, DE | Rust Berlin
Rust'n'Tell - Rust for the Web
2024-04-25 | Aarhus, DK | Rust Aarhus
Talk Night at MFT Energy
2024-04-25 | Berlin, DE | Rust Berlin
Rust and Tell
2024-04-27 | Basel, CH | Rust Basel
Fullstack Rust - Workshop #2
North America
2024-04-04 | Mountain View, CA, US | Mountain View Rust Meetup
Rust Meetup at Hacker Dojo
2024-04-04 | Portland, OR, US | PDXRust Meetup
Hack Night and First Post-Pandemic Meetup Restart
2024-04-09 | New York, NY, US | Rust NYC
Rust NYC Monthly Meetup
2024-04-10 | Boulder, CO, US | Boulder Rust Meetup
Rust Meetup: Better Builds w/ Flox + Hangs
2024-04-11 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group Meetup
2024-04-11 | Spokane, WA, US | Spokane Rust
Monthly Meetup: Topic TBD!
2024-04-15 | Somerville, MA, US | Boston Rust Meetup
Davis Square Rust Lunch, Apr 15
2024-04-16 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2024-04-16 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group: Meet Servo and Robius Open Source Projects
2024-04-18 | Mountain View, CA, US | Mountain View Rust Meetup
Rust Meetup at Hacker Dojo
2024-04-24 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
2024-04-25 | Nashville, TN, US | Music City Rust Developers
Music City Rust Developers - Async Rust on Embedded
2024-04-26 | Boston, MA, US | Boston Rust Meetup
North End Rust Lunch, Apr 26
Oceania
2024-04-30 | Canberra, ACT, AU | Canberra Rust User Group
April Meetup
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
Panstromek: I remember reading somewhere (probably here) that borrow checking has O(n^3) asymptotic complexity, relative to the size of the function.
Nadrieril: Compared to match exhaustiveness which is NP-hard and trait solving which is undecidable, a polynomial complexity feels refreshingly sane.
– Panstromek and Nadrieril on zulip
Thanks to Kevin Reid for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
2 notes
·
View notes
Text
FLASH MEMORY PT1 - AO3 / FFN
(Metal Sonic, Mecha Sonic & Silver Sonic II)
"Sonic runs and rests; the sun rises and sets. Don't give up on the sun. Don't make the sun laugh at you." — Japanese tagline, Sonic & Knuckles.

A/N: welcome back my fellow robot enjoyers! this is the second installment of our totally normal and not fucked up robot bros just trying to live their freaking lives. for those of you who are new and haven't read the previous one, i'd highly recommend that you skim through it or you'll be confused. if that sounds like effort, lemme summarize a few things for you; neo = metal sonic. after his defeat as metal overlord, he returned to his normal form but now wears the same white arrows as he did before. he's also got this like split personality thing going on (it's okay i have DID lmao) so there's a divide between OG metal sonic programming and (ironically) new neo. mecha = mecha sonic, the oldest brother. he is very tired and very traumatized and trying to figure out wtf emotions are. can also solve a captcha. silver = silver sonic mk ii. the baby brother. gamer by day, crimefighter by night under the alias SUPERBOT. name not chosen by him. also not trademarked yet. died once. don't bring it up. anyway, long story short after a whole bunch of trauma and a rollercoaster of fucked up shit they're defected from eggman and live on their own, with some other robots who also left. dialogue in italics = robot beep boop code because neo's voice no work right. he's #on that bumblebee transformers shit
trigger warning as usual for trauma discussions, mentions of death & self harm. continuation of damage.

Emerald Coast.
A group of tropical islands outside Station Square. Under a light blue sky laid an expanse of golden sands. Behind them, green grass and blue stone made up the coastal grasslands, home to a huge array of wildlife. Palm trees, ripe with coconuts, dotted the coastline to add shades of green to the painting-worthy landscape. Gentle winds rustled their fronds, offering a soft song in harmony with the marram grasses. Far out across the sparkling waters, boats came to rest on the calmer waves, sitting as kings where they adored the seawater view. It was paradise, and apparently, the hottest vacation destination on the planet. It was an unlikely place for three ex-killer robots to hang out, but the three of them never had been too fond of conforming to societal expectations.
"Neo," Mecha Sonic said. Damp sand and fragments of shells sifted under his feet as he turned to look at his recumbent companion. "Neo, look."
Neo gave a noncommittal noise. He had been sitting back against the old brick wall for quite some time now, channeling his inner toaster to just sit and bask in the heat of the seaside sun whilst Mecha admired the view. But the sun was rising quite quickly now, and at the sound of his older brother's voice, Neo sat up, albeit with a show of reluctance at having to move.
"What?" Neo signed, moving to stand beside his brother.
Mecha pointed wordlessly out to the ocean and Neo followed his finger, out across the open waters. In the distance, just before the horizon, blue shapes leaped and twisted amongst the rolling waves. Mecha watched, entranced, as the wild animals moved in near-sync, leaping out of the water and into the air as if they had wings. The waves beneath them came like rain to a desert, the strong give, thriving life.
"Dolphins." Mecha said.
"Dolphins." Neo agreed.
The dolphins splashed down again, vanishing in a fountain of seafoam. Neo stood at Mecha's side, watching the sea thoughtfully as the aquatic dance continued, and the light grew brighter, but softer, and streaks of pink and purple made themselves at home in the sky.
"Where is Silver?" Neo signed calmly, knowing he would be nearby somewhere.
Mecha reached up to his ear and pinged Silver. "Silver, send your coordinates-"
Silver Sonic MK II appeared in the distance just on time. He was flung up into the air by a rambunctious dolphin with a scream before plunging back down with a loud splash.
Mecha and Neo didn't move from their position. Neo, if anything, got more comfortable with an elbow atop the rail in front of him.
"Do you think they are attempting to kill him?" Mecha asked nonchalantly.
Neo shrugged a shoulder. "Perhaps. He is waterproof, though. He will be fine."
Silver appeared again, flung high into the air, but this time he did a flip and laughed.
"My coordinates are: in the sky! WOOHOO!" Silver finally replied, before falling back down and disappearing once more.
A woosh of air could be heard from behind them, marking the approach of fast-moving footsteps. Mecha and Neo looked over their shoulders at the same time to see Sonic hopping to a stop behind them.
"Hey, guys! Where's Silv? I thought all three of you were gonna come." Sonic asked casually. He lifted one foot and dusted sand and pebbles from the sole of his shoe.
Mecha motioned with his head to where Silver was in the distance. "He is being murdered again."
"Figures. It's kind of his thing." Sonic said with a laugh.
"Why here." Mecha asked, looking out to the ocean. "It is an open space. We are at risk of being targeted here."
Sonic patted Mecha on the shoulder before slinging an arm around it. "Lighten up Mecha! It's neutral territory. You guys are meeting my pals for the first time and I want it to be peaceful. No fighting, no shooting, no causing trouble." He ended with a small side glance to Neo, who folded his arms and tilted his head to one side mockingly.
"Understood." Mecha replied.
"Thanks for coming, lil bro." Sonic finally said, throwing his arms around Neo and patting his back in a brotherly gesture. Neo returned the gesture after a moment with a sarcastic roll of his optics. Sonic pulled away and shoved Neo's shoulder playfully, and Neo jabbed a claw tip at Sonic's chest in a lighthearted threat.
"Well, it's good to see you again, boys," Sonic said, turning to watch as his friends appeared atop the slope that led down to the beach, "now, remember, play nice."
"I don't take orders from you..." Neo grumbled to his side, making a displeased display on his screen that read, " ¬_¬."
Sonic bounded up the hill to greet his friends: Knuckles, Amy, and Cream, three of his closest friends and allies.
"Hey, Knux! It's good to see you, buddy!" Sonic called out to Knuckles, greeting him with a fist bump.
"Sonic! It's good to-" Knuckles trailed off, looking over Sonic's shoulder, where he spotted two of his worst enemies just casually standing about as if waiting for something, or someone. "You're kidding me. Sonic, no. No no NO." Knuckles shoved past Sonic and marched down towards them, fists clenched and teeth bared.
"This Knucklehead... wait! Wait just a sec!" Sonic called after him. He ran down and grabbed Knuckles' arm, slowing him down just a little.
"You're protecting these two pieces of junk?" Knuckles hissed in disbelief. "What gives?"
"If you wait a second I'll expl-"
In that one second, Knuckles threw a fist at Neo, but Mecha side-stepped and caught it easily in one hand.
"Greetings, Knuckles the Echidna." Mecha said, unfazed by the display of aggression. It wasn't the first time he had a fist come at his face and he knew it wouldn't be the last.
"You..." Knuckles leaned in close, baring his fangs at the robot fiercely, "don't think I've forgotten about you!"
"I understand what situation you are referencing. I was carrying out my creator's orders in our initial encounter," Mecha said simply, holding steady, "and I regret my actions. I now know better. I act of my own free will, and I use it today to say that I am sorry. I apologize for the harm I have caused, to you, and to your sacred home."
"What's wrong with this guy?!" Knuckles murmured, looking over to Sonic in disbelief. He met Mecha's gaze again with fierce intensity. "Oh, sure! With you taking the Master Emerald and trashing my home, all of this worked out just perfect for you, huh? You're sorry?!"
Mecha regarded him with a cool look. He glanced away for a moment, watching the dolphins in the distance. "Dolphins frequently leap above the water surface for social displays, orientation, and entertainment." He looked back to Knuckles, tilting his head a little to one side. "Are you finding entertainment in this interaction? Does it make you happy to respond to my apology in this manner?"
Knuckles slowly drew his fist away. "Jeez..." He scratched his head and looked to Sonic. "Did I hit this guy on the head too hard or something? Alright, alright... but tread lightly, rustbucket."
Neo moved to stand beside his brother protectively. Knuckles caught the movement out of the corner of his eye and sharply looked at him.
"Oh, look who it is! Should I call you Metal Sonic or Metal Madness today?" Knuckles spat at him.
Neo shrugged a shoulder and signed, "neither of those are my name."
Knuckles stared at him for a long moment. "Uh... I don't..."
"If you're not going to hit him, I WILL!" Came a shriek from behind them. Knuckles side-stepped just in time as Amy came charging through with her hammer, swinging it wildly as she barrelled straight towards Neo. "Knuckles might have missed, but I won't!"
Once again, Mecha casually reached up and stopped the blow with a hand. "Miss Rose. Please refrain."
"Don't you Miss Rose me you hunk of junk! Who do you think you are?!" Amy snapped, drawing her hammer back away from him.
Neo cast a sidelong look over to Sonic. "Your friends are not very pleasant."
Sonic mouthed "sorry" back to him. Despite everyone's reservations, he had hope that they would all get along. It just might take a bit longer than first expected.
The runaway Silver finally darted over to join the little meeting. He landed beside Mecha and waved at everyone, excited to meet new people as always. He shook seaweed off of his head with a grin after that.
"Hi guys! It's so cool to finally meeEET-" Silver ducked as Amy's hammer came swinging at him. He hopped and danced backwards, avoiding her wild swings with growing laughter. "Woah, hey! I'm friendly! FRIENDLY!"
"Friendly?! Friendly?! Ohh, you are so dead! DEAD!" Amy continued her assault, growing more enraged the more Silver laughed and dramatically jumped to avoid her. "All you pretend Sonics are the same!"
"So, like, cool and fun and totally friendly? You got me!" Silver replied, giggling as he ducked under the hammer. "Do it faster, it's more fun if it's a challenge! I'll do a flip!"
Mecha swept his little brother under his arm and held him firmly. "There will be no challenge to speak of. We are not here to fight."
"Then why are you here?" Knuckles finally asked, folding his arms with a furrowed brow.
"To make friends, apparently." Silver mumbled from under Mecha's arm, where he dangled helplessly.
Sonic patted Neo's shoulder and grinned enthusiastically. "The kiddo's right. We're all here today to make peace."
Knuckles scoffed at the proposition. "Peace? Peace. You trashed my home and committed theft of a sacred object. You kidnapped Amy and held her hostage. And you..." Knuckles paused, squinting at Silver in thought, "I don't even know what you did, but it's probably evil. What's your game?"
Silver perked up instantly. He looked left and right excitedly. "Game?! Where?"
"Look, guys..." Sonic said, sighing as he stepped in front of the robots with his hands up. "Whether you like it or not, these guys are my lil' bros now. It's a long story. Now, we're going to go have fun, with no fighting, no yelling, and no Eggman ruining the day."
Begrudgingly, Sonic's band of friends moved on to the beach. The robots walked behind them, keeping a respectable distance.
"Have you lost your mind, Sonic?" Knuckles whispered to his best friend, staying close to his side. "They're our enemies."
"Nah... these guys saved my life. All of our lives." Sonic replied, just as quietly. "They're part of our weird little family just like you."
Mecha wandered off to survey the expanses of sand and washed-up creatures on the shoreline. He found the scenery intriguing - it was most unlike the cold metal base he had been created in. Knuckles and Amy stayed close to Sonic, still wary of the robots in the group, but begrudgingly let Neo stand with them. Neo and Sonic stayed far back from the open waters. Being mirrors of one another, they both feared those murky depths, the unknown that laid beneath, the... the jellyfish and tangles of seaweed and the inability to touch their feet against the bottom. They both shuddered in unison as they thought about it at the same time.
"Race ya to the end of the pier." Sonic challenged Neo, turning to him with a cocky smirk.
Neo's optics brightened at the proposed competition. Nothing more needed to be said, for their body language did all the talking. Neo pushed one foot back in the sand, Sonic crouched down just a fraction, and then they were off with a crack of the air. Amy was left covered in damp sand.
"My dress! You ruined it!" Amy yelled after Sonic, raising a fist in the air out of frustration. "How dare you, Sonic!"
"And there they go." Knuckles said, shielding his eyes from the sun as he watched them go. "They're fast."
"They're just as annoying as each other." Amy commented, crossing her arms with a small pout.
Cream carefully laid out a beach towel and sat down, inviting Silver to join her with a wave. Silver did so, smiling down at her as he moved to sit.
"It's nice to meet you, Mr. Silver!" Cream greeted him with a warm smile.
"Likewise! Oh, and you don't gotta call me Mr. Silver, it's okay. Just call me Silver." Silver reassured her.
"Oh, I'm sorry! Do you prefer Miss? Mrs?" Cream asked, worried that she had caused offense.
Silver's smile turned into a grin, then a laugh. "Any of those fly, if you really gotta use a title for me."
Shutting off his optics for a minute, Silver prepared to bask under the sun, leaving the extraneous activities to the organics. At least, that's what he wanted to do. Watching him with a sneaky glint to his visor, a plan formed in Mecha's mind as he wandered back over to his little brother. He snuck closer to Silver quietly, pressing a finger to his muzzle plate to signal to Knuckles and Amy nearby. Knuckles only snickered, crossing his arms to watch what Mecha was going to do. Silver felt Mecha's shadow loom over him, whisking away the sun's warmth. He onlined his optics a fraction, seeing Mecha for only a split second before he-
"Mecha?!"
Silver shrieked, his body no longer on the towel but instead thrown over Mecha's shoulder.
"Mecha, put me down or so help me!"
"Your temperature is rising beyond optimal levels. Why do you not cool off for a second?"
Mecha's hands grasped Silver's sides, lifting him off of his shoulder before tossing him into the crystal clear water. Although it was refreshing against his warmed armour, the sudden barrage of sensory information flooded Silver's CPU. He planted his feet onto the ocean ground and pushed his body up.
"Mecha Sonic, you motherfu-"
"There are children present. Mind your language." Mecha said, but not without a mocking hint to his tone.
"I AM the children, motherfucker!" Silver yelled back. He splashed water at Mecha, which sprayed all over his face - but he didn't outwardly react to it.
"Error 404, fucks not found." Mecha responded with a shrug of a shoulder.
"Get in here, asshole..." Silver stood up, marched over to Mecha, and flung an arm around his shoulders before gripping him in a headlock and falling back down into the water. Mecha came down with him, falling on top of him with a beep of surprise. Silver scrubbed Mecha's head with his knuckles whilst playfully growling up at him, and Mecha made sure to pin him so that he was under the water after that. It was then that Silver was actually glad to be a robot. It did take away the possibility of drowning, after all.
Sonic zipped back over to his best friend with a triumphant grin. "I won. As usual!"
Knuckles was used to Sonic coming and going so quickly, so he didn't jump when he returned. Instead, he watched the two robots out at sea and chuckled to himself. Their oddly organic behaviour was starting to grow on him. "They remind me of us, Sonic."
"Yeah. They're the spitting image of us." Sonic gave a quick laugh before nudging Knuckles in the side. "Told ya. They're not bad kids."
Knuckles grinned with fangs bared as he grabbed Sonic by the shoulder and scrubbed the top of his head, messing up his quills. "If they're anythin' like you, they're big trouble."
Silver and Mecha tussled for another minute before the younger robot broke away. He ran back onto the shore, armour dripping wet, and almost barrelled straight into Knuckles. He bumped into the red echidna with a squeak of surprise before backing up and looking up at him sheepishly.
Knuckles managed a smile despite himself. "Hello, Trouble."
"Hey! Is it Knuckles or Knux? I get confu-" Silver looked over his shoulder and was met by a splat of seaweed to the face. He slowly reached up and dragged it down and off of his face to find Mecha standing a few feet away.
"You bastard." Silver whispered, grinning dangerously at him. "You're so dead."
"You just got pranked." Mecha replied flatly.
"Oh, so that's how it's gonna be, M? Wanna see an epic prank? I call this prank, I run really fast at you, and you die." Silver said through his taunting grin, before charging back over to Mecha and tackling him down into the sand. Silver made quick work of tossing sand all over him, making sure to get it in every place imaginable. Once he was sufficiently buried, Silver stood up, dusted off his hands, and bounded back up to Sonic and Knuckles.
Mecha stayed flat on his back in the sand, his spines already sunken down into the damp. "I am dead."
The small rabbit in the group hopped over to him and leaned over him. "Mr. Mecha Sonic?"
Mecha turned his head slightly. Sand fell off the tip of his nose. "Yes?"
"Don't die." Cream said, holding her ears anxiously.
"I am merely executing an 'inside joke.' Do not be concerned." Mecha reassured her, sitting up to face her.
"Mr. Mecha Sonic, can we be friends?" Cream asked hopefully.
Mecha slowly stood up, so as not to scare the much smaller girl in front of him. "There is no reason for us not to be."
"Yay!" Cream took her bucket and showed it to the killer robot with a smile. "Do you want to collect seashells with me?"
Mecha gave a nod and a "smile" back. "Of course. Let us begin."
Hand in hand, the killer robot and the small rabbit walked down the shoreline, Cream skipping with her bucket in her other hand. Mecha knew his strong hands would break more than just a few shells, so he didn't try to pick any up himself. Instead, he pointed out the most interesting and unique ones, making note of how Cream picked and chose the ones of interest. There was probably some algorithm to it, and he was going to figure it out.
Cream suddenly gasped and crouched down in front of a shell. "Look, Mr. Mecha! It's a purple one!"
Mecha bent down to get a closer look, tilting his head with curiosity. "Argopecten purpuratus. A marine species of saltwater shellfish, a bivalve mollusk in the family Pectinidae."
Cream picked it up carefully, turning it around under the sunlight. She took a piece of string from her pocket, tied the shell to it, and presented the newly-made necklace to her robot friend.
Mecha tilted his head the other way. "What is it."
"It's jewellery! For you!" Cream explained enthusiastically, handing it to Mecha. He wasn't sure what to do with it, so she carefully put it into his hand with a giggle at his confusion.
Mecha slowly and carefully opened his hand, noting the fragility of the object in his palm. His fingers shook a little as he took the string between them and put it over his head. He inspected it with great interest, but dared not to touch it for fear of damaging it.
"Do you like it?" Cream asked, hope clear in her face. She laced her hands behind her back and smiled up at him.
"Affirmative." Mecha replied. He looked around for a moment, searching for a shell to give in return. Despite his worries about breaking it, he very carefully picked one up between his fingers, which shook nervously - a bright yellow seashell. He presented it to Cream, his hand now shaking more violently. "For you."
"I love it! It's so pretty!" Cream exclaimed, taking it into her hands with amazement. "Like you."
Mecha straightened. "What."
Cream reached out and ran a hand up Mecha's arm, admiring his armour. In the sunlight it was a radiant deep violet, freshly painted, complimenting the slip of silver of his upper arms and muzzle. She noticed the scratches, partly filled in by the new coats of paint, but still undeniably there like old battle scars. Mecha held very still. He had always been unsure of touch, especially after what had happened to him before, but he trusted her.
"You're pretty." Cream repeated herself, beaming up at him.
Mecha tilted his head. "That is not a word that has been used to describe me before. Thank you."
"Really?! Oh Mr. Mecha, that's so sad." Cream said, rubbing her thumb over a deep-seated scratch that ran horizontally across his arm. She would never know the story behind it, and that was probably for the best. She didn't need to know that Neo, or rather, Metal, had torn it to shreds months ago when he lost his memory.
Mecha shook his head. "It is not sad. I simply have not been in a situation that would call for-"
Not a second later, he swept Cream under his arm and spun around, staring out to the sea on high alert. Neo and Silver were by his side a moment later, sensing something too. A signal. A robotic one. That couldn't mean anything good.
"I am detecting an E-Series." Mecha told Neo, in code so that Cream couldn't understand.
Neo narrowed his optics at the water. "As am I."
"I hate when you two do that..." Silver grumbled, raising a fist and focusing on the waves.
"Looks like the boys have found something," Sonic commented. He stretched an arm out and rolled his shoulder, walking over to them. "What have your robo senses d-"
Before any of them said a word, said mystery machine came reaching out of the water. Seafoam and water sprayed onto the three robots, sending Neo reeling back in disgust, while Mecha and Silver stayed put. The machine before them was a bright purple and red with green cameras for "eyes" at every angle, loosely resembling an octopus-like creature.
"E-38 Octaron." Mecha said, watching as it rose to stand at its full height. A whopping 44 feet.
"E-38 Octaron." Neo agreed. He shook his head clear of the water with a squinted optic.
"E-38 Octaron." Silver added. His brothers looked at him. "What? I felt left out."
Mecha took Cream from under his arm and gently handed her to Sonic, keeping his gaze fixed on the robot in front of him. Sonic wordlessly nodded and took Cream further up the beach, back to his friends.
"Mr. Sonic, what's happening?" Cream asked nervously.
"Don't worry about it! These guys know what they're doing." Sonic said with a reassuring grin. If anyone was equipped to deal with a creation of Eggman's, it was his ex-minions.
"This unit's abilities include swimming, tentacle extension, elasticity, and enhanced strength. It is not a significant threat to us." Mecha mused out loud.
"It's not sentient, is it?" Silver asked quickly.
"Negative. It merely detects motion and attacks. Our creator is likely to be close by, instructing it." Mecha responded simply.
"So what you're sayin' is, if we hit it really hard..." Silver started, but was interrupted as a metallic tentacle came crashing down just an inch from his face. It curled around to take a jab at Mecha's leg, but Neo smacked a fist down into it and it retreated. Sonic came skidding back over to them, still wearing his trademark cocky smile, even as the next tentacle made way for him next. Silver met the challenge head-on, jumping on it with both feet before it could hit Sonic. Once again it retreated.
Silver looked at him and matched his smile. "Its name is dangerously close to a slur... all the more reason to hit it really hard."
Sonic nodded. "You said it. And, this is why I hate the water! All these creeps hiding in there... Mountains are far superior."
Neo nodded in agreement by his side.
"We can continue this discussion later," Mecha said, "now, remain focused. With one well-placed and well-timed blow we can put this unit out of order."
Sonic cupped his hands around his mouth and yelled, "yo, Octaron! I heard how ugly you were and just had to come see for myself."
"No, no Sonic! DIBS!" Silver called out, rushing up to meet E-38 Octaron with glee. He jumped as a tentacle swept under his feet, then ran up it whilst laughing almost maniacally. In his impulsive race, he didn't account for the other tentacles coming at him - and, unsurprisingly so, he found himself wrapped up in one of them. It held him up triumphantly.
"Okay! Okay. Maybe the youngest bro shouldn't always get dibs?" Silver offered sheepishly. He found himself getting squished a little tighter with every second, but didn't panic. He trusted his brothers more than anyone. If he was in serious danger, they would have already acted. So, he did nothing drastic yet.
"His hedgehog-series pride will have him see this fight to the end, even if it kills him." Neo remarked with pride.
"Guys, a little help? I kinda give up, 'cause I can't move!" Silver called down to them.
"I'll kill him." Neo murmured.
"You must learn, Silver," Mecha started, stepping forward, "to not act so impulsively."
"You wouldn't get it, Aquarius. I'm a fire sign. It's what I do! Now are you gonna help or not? Not a fan of being crushed to death!" Silver shouted down to him. The grip around his body tightened and he laughed a little. "Stop, it tickles."
Neo watched and stifled a laugh, causing his vocalizer to give static for a second.
"Out of the way!" A voice behind them yelled. They all turned to find Amy charging over, hammer in hand. Without a shred of fear she charged right up to the towering machine and slammed her hammer into it repeatedly. "Take that! And that! And this! Aaaaaand THAT!"
"Damn! She's badass." Silver remarked, grinning madly at her show of wild courage. "Girlboss power!"
Knuckles came next, sending a clenched fist into it, then the other, until he was working a comfortable rhythm. "Get back into the hole you crawled out from, creep!"
Sonic and Neo exchanged looks.
"You ready to face our fear?" Sonic whispered.
"Aquaphobes, assemble." Neo affirmed his suggestion, albeit with some reluctance.
They took off at the same time, dropped into spin-dashes, and tore through E-38 Octaron like it was paper. Neo came to a stop and hopped up onto the robot's head. Sonic landed beside him. Then, Neo tilted his head back to see Eggman in his Eggmobile. Eggman watched with disdain as another prized creation of his was about to be written off.
"Boy, don't make me come down there and be a parent!" Eggman shouted down to Neo, pointing a finger at him.
"Oho, first time for everything!" Silver yelled up at him, interrupting him.
"Don't do it." Eggman snapped. "Do not!"
"I'm going to do it." Neo murmured to Sonic.
"Me too." Sonic whispered.
The two of them dropped into spin-dashes again and ripped one more hole through the robot. As Knuckles had asked it to, E-38 Octaron fell back into the ocean with a loud splash. Before the robot or the organic could hit the water, they landed squarely on the robot's middle and jumped back onto the shore.
"Damn you boys! You always ruin my fun!" Eggman protested, before disappearing back to where he had come from. Good riddance.
Silver was released from the robot's grip instantly, and Mecha was quick to jump up and catch him in his arms. He put Silver down on his feet and placed his hands on his shoulders.
"Are you injured, brother?" Mecha asked, concern for his little brother showing.
Silver smiled and leaned forward, bumping his forehead to Mecha's. "Nah. I'm all good, promise."
Sonic and Neo walked over to them, very thankful to have not gone for an impromptu swim after all.
"Well, your heart was in the right place, kiddo." Sonic told Silver, patting his head affectionately.
Neo moved over and promptly hit Silver on the head with a reprimanding look.
"You're a girlboss too, Princess. No need to get jealous." Silver said, poking his tongue out at his older brother.
"You know that's not what that was for." Neo grumbled, turning away from him.
"Sonic! Our hero..." Amy cried, falling into Sonic's side with a wistful smile.
Sonic gestured to Neo with his elbow and smiled. "Don't forget, he helped too."
Amy looked at Neo and, after a moment, gave a nod of approval. "Thank you. That Eggman, always ruining our perfect days out..."
Mecha gave a quiet laugh at that. "I concur."
Knuckles walked up to Neo and clapped a hand on his shoulder. "Thanks. I guess you're alright. You just proved yourself."
Neo met his eyes with sincerity. He gave a nod.
Cream came running over, ecstatic that her friends had saved the day once again. They always did! She ran straight for Mecha and threw herself into him, hugging him tightly.
"Thank you, Mr. and Miss Robots!"
Silver, Neo, and Mecha exchanged warm looks. Mecha reached down and gently patted her head, as he had seen Sonic do to Silver before.
The family just kept on growing, and they welcomed that with open arms.

With tensions resolved between the robots and the organics, it seemed like things were looking up for everyone. That night was like any other. Egg Pawns pattered about the warehouse they called home, putting up decorations, chatting between themselves, and doing what robots do. That meant that a lot of them were in recharge by now.
"Evening, Metal!"
Metal Sonic looked up from the broken mirror that he had been fixing. A tube of glue sat on the sink by the mirror. He looked over his shoulder and displayed a "HELLO" across his screen back at Silver, who peered around the door at him.
"Tell Neo I said he's a loser and that I beat his score on the racing game!" Silver taunted them before skipping by. He snickered to himself as he heard footsteps from the bathroom. He knew by those footsteps that Neo was coming for him now. So, he stopped halfway across the main floor and looked back. If there was an opportunity to harass and annoy his older brother, he was always going to take it.
"You did not." Neo signed, narrowing his optics accusingly.
Silver turned around and put his hands on his hips, grinning triumphantly. "I so did."
"Did not."
"Did too!"
"Did not."
"Does the scoreboard lie, bro?" Silver asked teasingly.
Neo looked over to the TV to see that Silver had indeed beaten him. He folded his arms defensively.
"Exactly. You lost the bet. Poor, poor Neo, the slowest thing alive." Silver told him with overdramatic sympathy.
Neo gave him the middle finger. A common treatment from the ex-overlord.
"Oh no, the Princess is all huffy! What are you gonna do, take over the world again? Because I have Sonic on speed dial."
"You must be as stupid as he is if you think he can work a phone." Neo retorted in code.
Silver recognized the inflection on the word "stupid" and pouted. "Don't call me stupid."
"Okay then, how about bitch?" Neo signed this time.
"Arrogant prick." Silver countered.
"Spoiled sow." Neo retaliated.
"Oh, how original! A hedgehog insult. Fuck you." Silver quipped back.
"Fuck you." Neo riposted.
"Fuck you!" Silver yelled, jabbing a finger at Neo's chest.
Neo huffed and held out a hand as if offering a handshake in defeat. Silver grinned proudly and shook his hand. Neo firmly shook it back, and it went on for just a little too long.
"Okay, okay, you can let go now," Silver said, laughing, "let go. Bro, let go."
Neo stared him in the face with a smirk about his optics.
Silver tried to pull his hand away only to find that it was stuck. He looked up to find Neo laughing at him.
Superglue.
"You monster..." Silver whispered. "You got me. You pranked me."
"You, me, outside." Neo signed, pointing to the back door.
Silver's face lit up. He grinned dangerously. "Race?"
Neo nodded. "Race."
Silver slung an arm around Neo's shoulder as they walked to the back door. "I need to go out on patrol anyways. Might as well race there." Silver told him with a shrug of one shoulder. He looked over it for a moment. "Hey, M! We're off out on patrol! Be back soon!"
Mecha peered out from around the corner of a doorway, paintbrush in hand. A freshly-painted Egg Pawn bounced out of the room, elated with their updated paint job.
"What time will you return?" Mecha asked, tilting his head to one side.
Silver turned his free wrist up as if looking at a watch. "Before like... three AM."
"I will keep them out of trouble." Neo assured Mecha with a wink.
Mecha tilted his head the other way. "That would be more reassuring to me if you were not currently glued to one another."
"We'll be back!" Silver called out as he and Neo walked to the back door, still very much stuck to one another. "Enjoy your time alone!"
Enjoy your time alone. Enjoy your time alone. Enjoy your time alone.
Mecha stopped. Neo heard the way Mecha's engine paused, then grew just that tiny bit louder. He knew his older brother like the back of his hand, and knew that something was wrong. He stopped and looked back, finding Mecha's gaze fixed on him and Silver. Silver went to drag Neo along with him, but when Neo resisted, he looked back too.
"Oh."
The two brothers knew that look well.
---
"Enjoy your alone-time, rustbucket, It won't last long."
The door closed and locked, leaving Mecha by himself in the dark room. Slowly, he slackened into his restraints and let his head hang forward, finally taking the time to process his situation. His firewall was in pieces, CPU working overtime to process his own thoughts as well as the commands of the virus, and his body was damaged in several places. He kept hearing the sound of the door closing over and over as his auditory processing units re-booted over and over, further making him dizzy and uncertain.
But one thing kept bugging him the most... the fact that he didn't know if Silver and Neo were safe.
His gaze shifted to the wall.
If his siblings were okay, then he would be, too.
---
"Woah, hey, M... you're okay." Silver offered gently, raising his free hand in surrender.
"Do not leave." Mecha said, quietly. "It is not safe."
He heard the door close and lock. A deadbolt. It echoed in his mind on repeat.
That door needed to close. Now.
"I said do not LEAVE." Mecha snapped. He slammed the door shut and turned on his heel to face them.
"We're right here, brother." Neo reassured him, and he too put his free hand up.
Mecha got in Neo's face, his engine now revving aggressively. "Do not leave. Do not leave. It is not safe."
At the same time, Silver and Neo took Mecha's hands in theirs and held them tightly. Neo moved forward and gently pressed his forehead to Mecha's.
The door stayed shut. His little brothers were safe. No men would come in with metal rods and chains and other instruments of torture to bring harm to them. He had done his job. I am a machine built for one task, that is all, Mecha had once said, and that task for the past year had become to be his brothers' keeper.
"A brother is made adversity. I am not leaving you behind." Neo told him softly, leaning into him with an air of protectiveness. "Never."
"Never again, M. We love you." Silver murmured into Mecha's shoulder, gently putting his free hand around his back.
Mecha slowly calmed down and came back to his senses. The two younger brothers sensed the change instinctively but stayed close to him. They had made promises to never leave each other behind, and this was just one of those times where that promise needed to be affirmed.
"It starts when you stop. When you're safe." Silver said quietly, rubbing Mecha's back. "Your mind finally gets a chance to process all the shit that's been put into it. We get it. Both of us, we get it. You stay busy with your books and repairs and video games, but it catches up to you once you sit down on your own."
Mecha leaned into Neo's form and closed his fingers around his hand. "Yes. That is true."
Silver looked up at him with empathy. "We shake hands with devils, and we walk past them. We live between death and life, we all do. We were never built to survive, not for this long. So the things we go through, there's no instruction manual for that. You just gotta take what happens in both hands, and-"
Mecha took Silver's hand from around his back and held it, too, closing his fingers around his little brother's palm. "In both hands." He used his free hand to prize his siblings' glued hands apart.
"I was gonna say, take what happens in both hands and throw it into the sun or something stupid like that, but I like your addition better." Silver replied with a small laugh. He offered Mecha a warm smile and gently swung his hand back and forth. "You wanna stay busy? Come with us to the city. You can bring one of your books, sit in the cafe for a while."
Mecha nodded in agreement. "Yes. I will do that." He pulled away from his siblings and disappeared into the office to find one of his favourites - a Windows XP instruction manual. Even though he could process each word in just milliseconds, he would get lost in the text for hours, taking in every little detail, the style of the writer, the all-important data. He liked to learn, so he would keep doing that.
Silver and Neo waited for him, watching as he went.
Silver gave a small sigh and looked to Neo. In a whisper, he said, "I hate what they did to him."
Neo nodded and signed, "me too."
Silver turned to the door and took his trusty rifle from the hook that he had placed beside it. He placed it in the sling over his shoulder and gave it a fond pat, running his hand over the bright orange "Silver Sonic" he had painted onto the side. Mecha soon returned to them, instruction manual in hand, and Silver threw an arm around his shoulder as they pushed the door open.
"Superbot, Murder Machine and Sparky are back in business!" Silver cheered with a grin. He bounded on ahead, excited to be out on the town for another night, doing what he did best - both causing and averting trouble.
Mecha watched him fondly. "It makes me happy to see them excited for something."
Neo nodded in agreement as he walked close by Mecha's side. "Me too. They deserve it."
Mecha turned his head to look at Neo. "I apologize for what happened."
"Do not apologize. A brother is made for adversity," Neo said, staying close to his brother's side, "so adversity it is. I am not leaving you in the dark."

After patrolling the streets together, Neo and Silver took their usual seats in the cafe downtown. It was always quiet at this time of day, only the most loyal of customers going about their business. And, as always, manning the till was their friend and comrade, Pisces, an ex-GUN soldier. Their real name still a mystery. Silver liked it better that way. Mecha, on the other hand, continued to wander, reading his instruction manual under the street lights as he passed under them.
"And then it went boom!" Silver explained, throwing his arms out to illustrate.
Pisces laughed as they put down the cup they had been cleaning. "I can imagine. You guys are very good at making things do that."
Neo nodded in agreement. He took a piece of paper and wrote, 'except it was not him who made it go "boom" this time."
Pisces peered over and read it. "That's surprising. You're usually all up in that, Silver."
Silver shrugged a shoulder. "My insides were starting to go BOOM, if that counts."
"Too much info, kid..." Pisces murmured, taking another cup into one hand to clean it.
"Meh, your loss if you don't want it." Silver murmured.
"It's good to see you two getting along." Pisces commented with a smile.
"Oh yeah, we get on soooo well... he's definitely not mean to me all the time!" Silver replied sarcastically.
"Only because of this idiot's constant backchat." Neo scribbled down.
Silver scoffed. "Hey, you stood there and watched me get squished! You were like, two hundred miles away in your own head!"
"My hand is about to be two hundred miles upside your head." Neo scribbled again.
"Shut up." Silver retorted.
Neo drew a smiley face and pushed the paper over to Silver.
Silver took his pen and wrote "fuck you" in reply.
Neo turned his seat around and put his back to Silver.
Silver prodded him in the back repeatedly. "Hey! Hey! Notice me!"
"NO!"
"Siblings, huh? They're the best." Pisces laughed, enjoying the two brothers' back and forth.
The front doors swung open all of a sudden. A waft of alcohol came through the doors before the next customer even walked in.
"These fucking robots..." They started, walking straight up to Silver and Neo.
Neo immediately stood up and moved to block his baby brother with his head lowered and optics glowing brightly.
"These FUCKING robots!" The man grabbed a glass and smashed it into the wall. It shattered and the shards scattered across the floor. "You just come in 'ere to our city, make like you're all good, well we all know you're not!"
Silver was taken aback by the tirade. He looked to Pisces, and Pisces shrugged, just as confused.
The drunken man pointed in Neo's face. "You tried to take over the whole fucking world! Huh? That was you, weren't it? Well? Say something!"
Neo remained silent, naturally. The human tried to shift around Neo to get to Silver, but Neo moved with him, blocking his path. The man pointed over the robot's shoulder instead.
"And you... I don' even know what you did. But you prance around like some kind of knockoff hero with your guns and stupid fucking know-it-all smile..."
"Hey! First off, heard that line earlier. Second, I've not done anything, actually!" Silver retorted, pointing a finger back at him. "Not all robots are criminals. That's really rude."
"You robots are all fakes. Fake people, fake heroes, you're not foolin' nobody!" The man continued his tirade, getting closer to them with every word. He jabbed a finger towards Silver accusingly.
At this point, other cafe-goers started to stand up. They murmured to each other, expressing disapproval for this stranger's insults towards the two robots. They were very well known for being protectors of the city.
Neo finally slapped the man's hand away and squared up into his face. His patience was running very, very thin. Nobody insulted his little brother. No. Body.
The man spat in Silver's face. Big mistake.
Neo punched him in the face faster than anyone could react. He hit the ground with a thud just as quickly.
Other customers in the cafe jumped out of their seats to crowd around the two robots. A few helped the downed man back up.
Silver slowly reached up to his ear to comm Mecha. "Hey, M. Might be a bit late leaving this place."
"Is there a problem?" Mecha asked. A turn of the page.
"Well... Princess just decked someone in the face. Someone, uh, started a fight with him."
Silver cringed at the sigh of disapproval over the comm. He heard Mecha shut his book just a little too loudly, and the soft clink of his fingers as they held his head in his hand.
"I shall arrive in two minutes. Order our Princess to compromise." Mecha murmured.
"I'll try. He's not one for compromises, though." Silver replied, grimacing.
"I am aware."
The link cut off.
Silver tried reaching out and putting a hand on Neo's shoulder. "You should apologize. Human faces are less, uh, durable than ours. You might break it."
Neo just stood there, seething with a deep-seated rage he thought he had buried months ago. His claws curled in and out, tense, wanting to draw blood. How dare he. How dare this insignificant fleshbag insult his little brother. How dare they! The idea of apologizing to this cretin was out of the question.
"Neo. C'mon." Silver grabbed Neo's shoulder harder and shook it to get his attention. "We should go. We've had enough fun for tonight."
"It punched me in the face! It fucking punched me!" The man screeched as he staggered to his feet. The few people who had helped quickly backed away.
Right on cue, Mecha pushed the doors open and walked in. "Outside. Now. That is an order."
"Roger that, Commander M." Silver said with a sigh of defeat. He let go of Neo's shoulder and walked by him. "Sorry, ladies, gents 'n others. We'll foot your bills for the inconvenience."
Neo slowly looked up to meet Mecha's gaze, narrowing his optics. "He was going to put his hands on Silver."
"We do not harm living creatures unless necessary." Mecha replied sternly. His gaze trailed over to the man, and for a moment, he swore he recognized him from somewhere. He chose to shake it off and focus on what was more important, pointedly avoiding looking at the person.
"Shut the fuck up with that beep-boop shit!" The man spat at both of them. "Nobody wants to hear it!"
Neo sharply glared at him, fire quickly returning to his optics.
"Come. They are not a threat to us." Mecha said. He took Neo's hand and practically had to drag him outside to break them up.
"Yeah, run away, freaks! Go talk your secret toaster language somewhere else!"
The drunken man was swiftly pushed outside by Pisces. "Out. Out, now. You're barred from entering."
Mecha kept hold of Neo's hand as they walked. "We shall discuss this incident in a more suitable location."
It was a long walk home.

Mecha paced back and forth, hands behind his back. Silver watched him with his hands laced together on his lap. His gaze trailed over to Neo, who stood with his arms crossed, leaning back against the wall.
Silver lifted his head to meet his brother's optics, sitting back. He threw an arm over the back of his chair. "So. You didn't listen to Mx. Apologize or Mx. Compromise. Now, we have Mr. I'm Going To Fucking Explode You in our back yard."
Bang. Bang. Bang. BANG. More rocks hit the window. The next one was rather large. It was becoming a problem.
Silver threw his head back, irritated by the repetitive noises. "Now, Neo, do you apologize in English, or sign language, or robot "beep-boop" code? Or do we ask them which language they prefer?"
Neo said nothing.
"Whatever. I'll deal with it." Silver huffed and stood up. He strode out through the back door, pulled it shut, and approached the man. He briefly noted the black eye and couldn't help but smirk a little. His big bro was strong, he had to give him that. The moron had gotten what he deserved, even if it was a little too hard of a punch. Or was it? He wasn't sure yet. This encounter would probably tell him.
"The freak finally shows itself!" The man shoved him by the shoulder but he didn't budge.
"Listen, friend. We're apologizing." Silver told him, looking him in the face. "I know it doesn't seem like it, but beneath it all, my brother's a rational guy."
"Beneath all what?! You mean beneath the attempted murders, the destruction of property, the-"
"Yup. All of that." Silver finished for him. "Now, look. You put your hands on me again..." He took a step forward. "He won't be so rational next time. You get me? We don't want any trouble. We're tryin' to live in peace here, and you throwing things at our home isn't exactly the most peaceful. It's kinda hard for Mecha to read with all the noise, and Princess Neo will want her beauty sleep. And I, for one, don't deal well with repetitive sounds. Gives me a CPU-ache."
"The news says that you lot saved the city. Well, I don't buy it, alright? It was all Sonic." The man spat.
Silver stifled a laugh with a fist to his mouth. Yeah, like the flesh-hog can fly.
"What's so funny?"
"Sonic? Which one? We've got a Silver Sonic, the second by the way, a Mecha Sonic, and a Metal Sonic. That's three Sonics." Silver said. He shifted around to the man's side and took a few steps back. He followed. Silver was drawing him away from the warehouse as they talked.
"Smartass punk. I know who you are."
Silver tilted his head, amused, and took a few more steps. "Oh? Then, do enlighten me."
"I know Mecha."
Silver's smile dropped for a moment. He folded his arms defensively. Another step back. "Most people do. We're heroes around here."
The man closed the gap between them, smirking in Silver's face. Silver stayed put now, unintimidated.
"No, you don't get it. I know him," The man said, smirk growing wider, "and you're the only one out of the three of ya who hasn't punched me in the face yet."
Silver's expression darkened. He didn't like where this was going or what this guy was implying. "That can be arranged."
"I'm sure it will, little one."
Silver let out a low growl. For once, he let his killer robot side show itself. "You dare lay a single finger on my brothers... I'm putting a bullet between your eyes."
"The mad Mecha Sonic, the nutjob Metal Sonic, and the psycho Silvy-"
"That's Silver Sonic to you." Silver corrected him, gritting his teeth.
"You're such a dick."
"Been so long since you last saw yours that you don't recognize one, huh?"
"Very mature of you."
"You're built like a fucking coffee cup."
"What?"
"Did you just fart or something? 'Cause it smells like meow meow woof out here, goddamn..."
"I- No. This is a message to you. The experiment isn't over."
Silver watched in a mixture of confusion and anger as the human turned and walked away. That was a direct threat towards his brothers, and most importantly, Mecha. Without thinking about it he found his rifle in his hands. By instinct, he cocked it and aimed. He fired a warning shot after the human, the shot cracking the air with a loud bang. The target took off running to catch the next train, disappearing out of sight and range.
"Get the fuck out of here." Silver hissed after him quietly.
Two Egg Pawns, the Casino Manager and Casino Clown who had once battled under his command, rushed outside to stand on either side of him. Silver lifted his head and looked out to the sky. He watched, idly, as the sun went down and the stars started to show their faces beyond the amber.
"Young boss."
Silver turned his head slightly. "Hmm?"
"You did well." The Casino Manager congratulated him.
"Yeah." Silver sighed and turned around to walk back. "I guess so."
"Did that loser threaten you?" The Casino Clown asked, intrigued. "You haven't shot at anyone so angrily in a long time."
"I wasn't gonna hit him." Silver murmured as he placed his rifle back in its sling. "It was a warning shot."
"I didn't say you would actually shoot him." The Clown replied.
"I wouldn't. That's not me." Silver asserted. "That's them. Those fuckers."
"Yeah! Fuck them!" The Clown called out from behind him.
"Is someone coming for you?" The Manager asked, clearly more concerned than their bright green comrade.
"Pssh, yeah. But I'm already dead." Silver said flatly. "What's the worst that could happen to me now? It's the other two I'm worried about." He reached up to the door handle and went to move it.
"Wait. Stay out here." The Manager asked of him.
Silver paused. He slowly lowered his hand from the door handle.
"Why do you talk about dying so much? You've not even seen your first birthday yet."
Silver stopped cold. Slowly, he let out a long sigh, lowering his hand back down to his side.
"I was made all wrong, that's why." Silver said, turning back around to face his comrade. "I'm like Neo. I was created with someone else's data. Someone alive. My mind just works differently than yours, that's all."
"That doesn't explain it though."
Silver held air in his intake for a moment. "Alright. Death... you've never experienced that. You can't act it. And as a robot, you can die a thousand casual deaths - but when your mind is completely alive, it's... an intensity that squeezes out your whole life. Every last drop of it. And even as you die you know you might come back with different paint. But nobody really gets up after death - there's no applause - only silence and second-hand parts, and that's - death. When my life was taken from me, it hurt. I felt pain, I felt all of those injuries all at once. It felt like someone holding me down, I couldn't move. And then it all felt... okay. You realize you can't stop it once you're in it. And that has to be okay."
"That sounds horrible." The Clown said.
"Kind of. But once it's happened once, you don't get scared of it again." Silver said a bit too casually.
This haunting was hereditary. If he shut down the background processes in his CPU, thoughts of the past hedgehog-series would come to mind. Sometimes, if he shut off his optics and stalled his engine, he could feel their hand searching for his in the repair bay. Perhaps if he had been there earlier, he could have taken it in his, lifted it from that pit. Some might call those thoughts bad dreams. The ex-killer robots once shook hands with devils, but now walked past them. They lived between life and death, never built to survive this long.
It seemed that all three of the brothers' demons were raising their heads tonight.
"Anyway. Yeah, he deserved that. Neo shoulda hit him harder." Silver said.
Silver opened the door and the pair of Pawns followed after him. They both took one last look back to make sure that the human intruder was gone before the door closed. Silver walked over to the makeshift sofa on the floor and collapsed onto it with a huff. He stared up at the ceiling, frowning a little with a hand across his chest.
Neo walked over and sat by him. He looked at the wall for a long moment before looking down at Silver, meeting his optics.
"Gamers never truly rest, do they?" Silver said, forcing a smile.
"What did he want?" Neo asked in sign.
Silver gave a quiet "hmph" as he turned over. "Just wanted to yell at me, or, one of us at least. I told him that we're all sorry, so he's gone now. Where's Mecha?" He peered over his shoulder to see what Neo would sign back to him.
"Emergency repair, he said. I told him that we would call if he was needed."
Silver nodded and turned back over. "We need to talk when he's asleep."
Neo nodded. I knew there was more to it, he thought to himself.
Silver took his rifle out of its sling and placed it over his chest. He placed a hand over it, tracing the name written across it with a finger.
"You and me against the world, bro. I think it's gonna be that way for a while longer."
Neo placed a hand on his brother's gun. "I wouldn't have it any other way."
"I dunno what you just said, but for once, I don't think it was mean or a joke at my expense." Silver replied with a snicker.
They were quiet for a long moment.
"Emergency repairs, you said?" Silver asked, looking up at Neo.
Neo nodded.
"Did she say what she was repairing?" Silver questioned him, a frown coming over his face.
Neo shook his head.
Silver paused.
"Shit."
"Shit shit shit."
"SHIT!"
Silver scrambled to his feet, tossing his gun aside, and ran to the repairs room. Neo leaped up to his feet and ran after Silver in a panic. Without hesitation Neo rammed a shoulder into the locked door, breaking it off its hinges.
Mecha slowly looked up. In one hand was a cut-off tool. His left wrist was scratched and broken - where the cuffs around him had once been.
"Mecha, it's okay..." Silver started, quietly, as he slowly walked over to his brother. "Put that thing down and we'll talk about it, okay?"
"Do not touch me." Mecha warned him, taking a shaky step back away from him.
"Easy, easy..." Silver said softly, taking a few more gentle steps towards him. He very carefully lifted a hand, aiming for the cut-off tool. "I won't touch you, I promise."
"You are not authorized to-" Mecha paused, moving his hand to aim the tool at Silver instead. "To touch me."
"I know, I know. Shhh." Silver whispered, lifting his hand just a fraction more. His fingers brushed the top of the rotor ever so slightly. "It's gonna be okay."
"You are too close. Move. Move. MOVE." Mecha snapped, thrusting the tool closer to him in a threat.
Silver's hand moved to the protector guard. His fingers closed around it slowly. "You're okay."
"Remove them from me. Please. Please." Mecha started to beg, lifting up his wrist with a jittery rev of his engine.
"Can I touch you?" Silver asked carefully. His hand fully closed around the cut-off and, with Mecha now distracted, he gently pulled it out of his hand.
Mecha nodded hesitantly. "Get them off of me. That is all I ask."
Silver gingerly brushed a hand up Mecha's arm, coming back down to his wrist. Of course, nothing was there, but he wasn't about to invalidate his older brother's pain by outright telling him that. "You're free. Look. It's gone."
Mecha looked down. He could see clearly, now. Seeing the change, Neo gently put an arm around his sibling and ushered him over to the chair. He sat Mecha down and placed a hand on his shoulder, using the other to pick up a lightly abrasive buffing pad. This would sand down the damaged paint and clean away the rougher edges before he filled in the scratches.
"Let me take care of you, brother." Neo murmured, gently running the pad over Mecha's wrist. It lifted away the scratched-up paint, revealing the bare silver underneath. Mecha didn't mind this. He was aware of what he was and was alright with it.
Silver set the cut-off down on the table and sighed. He planted both hands on the edge of the table and leaned back against it, looking down at the floor.
"That human," Mecha began, watching as Neo worked with care, "was one of those involved in my capture. I overheard your exchange with him, Silver."
"That bastard." Silver sighed through grit teeth. His fingers curled under the edge and squeezed the metal beneath them.
"I will arrange additional security measures." Neo assured him as he worked out the edges of Mecha's arm. "Fuck these people. What right do they have to trespass on our home?"
Silver lifted his head. "No idea what you just said, but I probably agree."
With his hands busy, Neo nodded to Mecha to ask him to translate.
"They said that they will arrange additional security for our home. They also said some unsavoury words that I shall not repeat." Mecha told him, looking up to meet Silver's optics.
"Pssh. If anything, those words were probably too sweet for the situation." Silver replied with a shrug of his shoulder.
"When I punched him, he folded like origami." Neo signed, putting his tools down for a moment to include Silver.
"Beta male, got it." Silver huffed.
"Was he alone?" Mecha asked.
"Beta males often travel al- I mean, yeah, he wasn't with a group. What do you call a group of humans? A gaggle? A pride? A colony? A pandemonium?"
"An infestation." Neo grumbled.
"They said an infestation." Mecha translated.
"Too true." Silver murmured. He pushed himself away from the table and walked out of the room, leaving Neo and Mecha to finish the repairs together. He wandered over to the sofa and stood there for a moment, thinking to himself.
Silver took his rifle in one hand and used the other to open the breech. He moved the bolt handle upwards, then pulled it back as far as it would go.
"Less impulsive my ass..."
He picked up a magazine from the side table and placed it below the breach, through the stock. It clicked into place.
"Since when has sitting around gotten us anywhere?"
He pushed the bolt forward as far as it would go, then closed it. The bolt head stripped a bullet from the magazine with a click.
"Nothing starts 'till you take action..."
He put on his rifle sling and put the gun over his shoulder into it.
"So when you wanna do something, do it right away. Do it when you can. It's the only way to live a life without regrets."
He opened the door and stepped out.
"I'm going for a run on the beach, guys. Be back soon!"
Silver walked out of that door and into the eventide without looking back.
#fanfiction#gamers never rest#flash memory also known as flash storage is a type of nonvolatile memory that erases data in units called blocks#and rewrites data at the byte level#flash memory is widely used for storage and data transfer#idk itjust sounded cool <3
7 notes
·
View notes
Text
MySQL: ALTER TABLE for UUID
A question to the internal #DBA channel at work: »Is it possible to change a column type from BIGINT to VARCHAR ? Will the numbers be converted into a string version of the number or will be it a byte-wise transition that will screw the values?« Further asking yielded more information: »The use-case is to have strings, to have UUIDs.« So we have two questions to answer: Is ALTER TABLE t CHANGE COLUMN c lossy? INTEGER AUTO_INCREMENT vs. UUID Is ALTER TABLE t CHANGE COLUMN c lossy? ALTER TABLE is not lossy. We can test. mysql> create table kris ( id integer not null primary key auto_increment); Query OK, 0 rows affected (0.16 sec) mysql> insert into kris values (NULL); Query OK, 1 row affected (0.01 sec) mysql> insert into kris select NULL from kris; Query OK, 1 row affected (0.01 sec) Records: 1 Duplicates: 0 Warnings: 0 ... mysql> select count(*) from kris; +----------+ | count(*) | +----------+ | 1024 | +----------+ 1 row in set (0.00 sec) mysql> select id from kris limit 3; +----+ | id | +----+ | 1 | | 2 | | 3 | +----+ 3 rows in set (0.00 sec)Having a test table, we can play. I am running an ALTER TABLE kris CHANGE COLUMN command. This requires that I specifiy the old name of the column, and then the full new column specifier including the new name, the new type and all details. Hence the “id id ...” mysql> alter table kris change column id id varchar(200) charset latin1 not null; Query OK, 1024 rows affected (0.22 sec) Records: 1024 Duplicates: 0 Warnings: 0 mysql> select count(*) from kris; +----------+ | count(*) | +----------+ | 1024 | +----------+ 1 row in set (0.00 sec) mysql> select id from kris limit 3; +------+ | id | +------+ | 1 | | 1015 | | 1016 | +------+ 3 rows in set (0.00 sec) mysql> show create table krisG Table: kris Create Table: CREATE TABLE `kris` ( `id` varchar(200) CHARACTER SET latin1 COLLATE latin1_swedish_ci NOT NULL, PRIMARY KEY (`id`) ) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_0900_ai_ci 1 row in set (0.00 sec)We can see a number of things here: The conversion is not lossy: We have the same number of records, and the records are still sequences of decimal digits. The order of the output is somehow different. The records which previous showed up in ascending integer order are now showing up in ascending alphabetical order. Given that they are now strings, this is partially logical (if there is an order, it should be alphabetical for strings), and partly mysterious (why is there an order and what happened?). Let’s go through that step by step. Expensive ALTER TABLE ALTER TABLE tries to do changes to the table in place, without rewriting the entire table, if possible. In some cases this is not possible, and then it tries to do it in the background. In some cases not even that is possible, and then the table is locked, rewritten in full, and unlocked. Our table change was of the third, most expensive kind. An ENUM change that extends the ENUM at the end is the least expensive possible change. We just add a new value at the end of the list of possible values for the ENUM. This is a change to the data dictionary, not even touching the table. An ENUM change in the middle of the list requires recoding the table. Turning an ENUM(“one”, “three”) into an ENUM(“one”, “two”, “three”) is expensive. Turning ENUM(“one”, “three”) into ENUM(“one”, “three”, “two”) is cheap. MySQL stores ENUMs internally as integer, so the expensive change re-encodes all old “three” values from 2 to 3. The cheap change stores “three” as 2, and adds 3 as an encoding for “two” in the data dictionary. Some ALTER TABLE t ADD index variants are examples for things happening in the background. They still cost time, but won’t lock. The index will become available only after its creation has finished. There cannot be multiple background operations ongoing. In our case, we internally and invisibly lock the original table. Create a temp table in the new format. Read all data from the original table, write it into the new table as an INSERT INTO temptable SELECT ... FROM oldtable would do. RENAME TABLE oldtable TO temptable2, temptable TO oldtable; DROP TABLE temptable2; unlock everything and are open for business again This process is safe against data loss: If at any point in time this fails, we drop the temptable and still have the original table, unchanged. This processes for some time doubles disk storage: The table converted will for some time exist in both variants. It requires an appropriate amount of disk space for the duration of the conversion. This process can be emulated. Locking a production table for conversion for an extended amount of time is not an option. Online Schema Change (OSC) does the same thing, in code, while allowing access to the table. Data changes are captured in the background and mirrored to both versions. Multiple competing implementations of this exist, and we have institutionalized and automated this in the DBA portal at work. This process does the INSERT ... SELECT ... thing internally (and so does OSC). That is why the conversion works, and how the conversion works. The rules are the MySQL data type conversion rules, as documented in the manual. There is an order, and it changed When looking at the test-SELECT we see there seems to be an order, and it changed. There is an order, because the column I changed was the PRIMARY KEY. The MySQL InnoDB storage engine stores data in a B+-Tree. A B-Tree is a balanced tree. That is a tree in with the path length of the longest path from the root of the tree to any leaf is at most one step longer than the shortest path. So assuming a database with a page size of 16384 bytes (16KB), as MySQL uses, and assuming index records of 10 byte (4 Byte integer plus some overhead), we can cram over 1500 index records into a single page. Assuming index records of 64 byte size - quite large - we still fit 256 records into one page. We get an index tree with a fan-out per level of 100 or more (in our example: 256 to over 1500). For a tree of depth 4, this is good for 100^4 = 100 million records, or in other words, with 4 index accesses we can point-access any record in a table of 100 million rows. Or, in other words, for any realistic table design, an index access finds you a record with at most 4 disk accesses. 4 (or less): The number of disk accesses to get any record in any table via an index. In the InnoDB storage engine, the PRIMARY KEY is a B+-Tree. That is a B-Tree in which the leaves contain the actual data. Since a tree is an ordered data structure, the actual data is stored in primary key order on disk. Data with adjacent primary key values is likely stored in the same physical page. Data with small differences in primary key values is likely stored closer together than data with large differences in primary key values. Changing a primary key value changes the physical position of a record. Never change a primary key value (Never UPDATE t SET id = ...). For an AUTO_INCREMENT key, new data is inserted at the end of the table, old data is closer to the beginning of the table. MySQL has special code to handle this efficiently. Deleting old data is not handled very efficiently. Look into Partitions and think about ALTER TABLE t DROP PARTITION ... for buffer like structures that need to scale. Also think about proper time series databases, if applicable, or about using Cassandra (they have TTL). We remember: In InnoDB the primary key value governs the physical layout of the table. Assuming that new data is accessed often and old data is accessed less often, using primary keys with an AUTO_INCREMENT value collects all new, hot records in a minimum number of data pages at the end of the table/the right hand side of the tree. The set of pages the database is accessing a lot is minimal, and most easily cached in memory. This design minimizes the amount of memory cache, and maximizes database speed automatically for many common access patterns and workloads. That is why it was chosen and optimized for. Random, Hash or UUID primary key Consider table designs that assign a primary key in a random way. This would be for any design that uses a primary key that is an actual random number, the output of a cryptographic hash function such as SHA256(), or many UUID generators. Using an integer auto_increment primary key, we are likely to get hot data at the right hand side, cold data at the left hand side of the tree. We load hot pages, minimising the cache footprint: AUTO_INCREMENT integer primary key controlling data order. Hot data in few pages to the “right” side of the tree, minimal cache footprint But with a random distribution of primary keys over the keyspace, there is no set of pages that is relatively cold. As soon as we hit a key on a page (and for hot keys, we hit them often), we have to load the entire page into memory and keep it there (because there is a hot key in it, and we are likely to hit it again, soon): Primary Key values are randomly chosen: Any page contains a primary key that is hot. As soon as it is being accessed, the entire 16KB page is loaded. So we need a comparatively larger (often: much larger) amount of memory to have a useful cache for this table. In MySQL, numeric integer primary key auto_increment optimizes memory footprint for many workloads. MySQL provides a way out: UUID_TO_BIN(data, 1) Unfortunately, MySQL itself produces UUID() values with the UUID function that sort very badly: mysql> select uuid(); +--------------------------------------+ | uuid() | +--------------------------------------+ | 553d5726-eeaa-11ea-b643-08606ee5ff82 | +--------------------------------------+ 1 row in set (0.00 sec) mysql> select uuid(); +--------------------------------------+ | uuid() | +--------------------------------------+ | 560b9cc4-eeaa-11ea-b643-08606ee5ff82 | +--------------------------------------+ 1 row in set (0.00 sec) mysql> select uuid(); +--------------------------------------+ | uuid() | +--------------------------------------+ | 568e4edd-eeaa-11ea-b643-08606ee5ff82 | +--------------------------------------+ 1 row in set (0.00 sec)MySQL provides the UUID() function as an implementation of RFC 4122 Version 1 UUIDs. The manual says: The first three numbers are generated from the low, middle, and high parts of a timestamp. The high part also includes the UUID version number. The fourth number preserves temporal uniqueness in case the timestamp value loses monotonicity (for example, due to daylight saving time). The fifth number is an IEEE 802 node number that provides spatial uniqueness. A random number is substituted if the latter is not available (for example, because the host device has no Ethernet card, or it is unknown how to find the hardware address of an interface on the host operating system). In this case, spatial uniqueness cannot be guaranteed. Nevertheless, a collision should have very low probability. Having the timestamp in front for printing is a requirement of the standard. But we need not store it that way: MySQL 8 provides a UUID_TO_BIN() function, and this function has an optional second argument, swap_flag. »If swap_flag is 1, the format of the return value differs: The time-low and time-high parts (the first and third groups of hexadecimal digits, respectively) are swapped. This moves the more rapidly varying part to the right and can improve indexing efficiency if the result is stored in an indexed column.« TL;DR So if you must use a UUID in a primary key Choose MySQL 8. Make it VARBINARY(16). Store it with UUID_TO_BIN(UUID(), 1). Access it with BIN_TO_UUID(col, 1). See also: MySQL Server Team Blog on UUID support for MySQL 8. MySQL Server Team on the pain of pre-MySQL 8 UUID (Article from 2015). https://isotopp.github.io/2020/09/22/alter-table-for-uuid.html
0 notes
Photo

A lot of questions for JavaScript developers
#492 — June 12, 2020
Unsubscribe | Read on the Web
JavaScript Weekly

153 JavaScript Questions (With Their Answers Explained) — Want to test your JavaScript knowledge? Whether for fun or a job interview, this is an interesting set of questions, complete with explanations of the answers. We first linked to this a year ago when it only had about 40 questions, so it’s grown a lot!
Lydia Hallie
An ECMAScript Proposal: Logical Assignment Operators — Dr. Axel covers another proposal in the pipeline for the language that would let us do things like a ||= b or a &&= b as you might in, say, Ruby or Perl.
Dr. Axel Rauschmayer
New Course: React Native — Leverage your JavaScript and React skills for mobile iOS and Android platforms using React Native – ship your very own native mobile applications.
Frontend Masters sponsor
Node Weekly: Our Sister Newsletter for Node Developers — Earlier this week I was speaking with a long time JavaScript Weekly subscriber who hadn’t heard of Node Weekly, our Node-focused weekly newsletter, so I thought I should invite you all to check out the latest issue as we cover a lot of Node things there that we don’t include in JSW :-) Be sure to check out the “7 Interesting Node Modules and Tools” section at the bottom!
Cooperpress
⚡️ Quick bytes:
JSGrids is a handy compilation of the best spreadsheet and data grid libraries so you can compare and pick the right one for you.
VS Code May 2020 has been released with a preview of editor setting syncing between multiple machines, CommonJS auto imports, preserved newlines during JS/TS refactorings, and more.
Excited for Vue 3? There's now an 'awesome' list for Vue 3 resources, links, videos, etc.
MDN has introduced a new front-end development learning pathway to add an opinionated and curated set of tutorials to guide you through learning things like CSS and JavaScript.
There's a JavaScript game you can play in your browser's title bar. Yes, it's open source.
💻 Jobs
JavaScript Developer at X-Team (Remote) — Join X-Team and work on projects for companies like Riot Games, FOX, Coinbase, and more. Work from anywhere.
X-Team
Find A Job Through Vettery — Vettery specializes in tech roles and is completely free for job seekers. Create a profile to get started.
Vettery
📚 Tutorials, Opinions and Stories
An Old School Doom Clone (in 13KB of JavaScript) — I have no idea how we missed this last year, but wow, what a neat piece of work. You can even grab it and play with the code yourself.
Nicholas Carlini
Type Assertions in TypeScript — A way to temporarily override a type, a little like lightweight casting.
Dr. Axel Rauschmayer
How to Deploy a Gridsome App on Azure Static Web Apps — Brings together the Gridsome Vue.js site generator with Azure’s new static app deployment service.
Gift Egwuenu
Bitmovin Magazine 5th Edition: Shaping the Future of Video — Get the latest overview of our products, recent feature releases, current video trends, and customer case studies.
Bitmovin Inc. sponsor
Using Higher-Order Components in React — Learn about higher-order components, the syntax of higher-order components, as well as use cases for them.
Shedrack Akintayo
How to Compare Objects in JavaScript — Compares a few different levels of what ‘equality’ actually is when it comes to JS objects.
Dmitri Pavlutin
Svelte, Why So Much Hype? — A closer look at the component-based library.
Anthony Le Goas
Improving the Rendering Performance of a Large List View in AngularJS 1.2.22 — You’re probably not doing this, but this is a pretty neat look at approaching performance issues in legacy apps.
Ben Nadel
🔧 Code & Tools
njt (npm jump to): A Quick Navigation Tool for npm Packages — njt is a tool you can either use locally (npm install njt first) or on the Web site and it acts as a way to quickly reach a package’s issues, homepage, pull request, and numerous other things. Clever idea.
Alexander Kachkaev
Math.js 7.0: An Extensive Math Library for Node.js and Browser — Work with complex numbers, fractions, units, matrices, symbolic computation, etc.
Jos de Jong
Stream Chat API & JavaScript SDK for Custom Chat Apps — Build real-time chat in less time. Rapidly ship in-app messaging with our highly reliable chat infrastructure.
Stream sponsor
Quotebacks: Embed Quotes Without Losing Context — This is a small library that can embed a quote in an attractive format within the source context. Can also be used as a Chrome extension that saves to local storage.
Tom Critchlow and Toby Shorin
Johnny Five 2.0: A JavaScript Robotics and IoT Programming Framework — If you’d wondered why you haven’t seen much about Johnny Five lately, don’t fear, because… Five is Alive! v2.0 is primarily an internal rewrite release rather than boasting lots of new features, though.
Rick Waldron
Karma 5: A Multiple Real Browser Test Runner for JavaScript — A popular way to test your code in multiple, real browsers at once. GitHub repo.
Karma
React Date Picker 3.0: A Simple and Reusable Date-Picker Component — A mature option that continues to get frequent updates. Demo here.
HackerOne
ModJS: A JavaScript Module for KeyDB and Redis — This isn’t for using Redis (or the KeyDB fork) from JavaScript but for taking JavaScript into the popular data structure server in case you prefer JavaScript to Lua for scripting it.
John Sully
Getting Started With OpenTelemetry In Node.js
Lightstep sponsor
Lightweight Charts 3.0: Canvas-Powered Financial Charts
TradingView, Inc.
tsParticles v1.15.0: A TypeScript Library for Particle Effects — Lots of neat demos in this announcement post. It’s basically Particles.js, but ported to TypeScript. GitHub repo.
Matteo Bruni
Josh.js: A Library to Animate Content on Page Scroll — This effect feels a little overdone nowadays, but this library is small, efficient, and it feels performant to me too.
Al Mamun
SVGuitar: Create SVG-Based Guitar Chord Charts — Very flexible and customizable and you can have a hand-drawn effect as well.
Raphael Voellmy
🗓 Upcoming Online Events
JS Nation (June 18-19) — This free two-day remote conference features over 25 speakers, including Jen Looper, Max Stoiber, John Papa and others.
OpenJS World (June 23-24) — Speakers at this 'virtual experience' include Nicole Sullivan, Prosper Otemuyiwa, Cassidy Williams and more.
CascadiaJS 2020 (September 1-2) — This upcoming online conference is set to take place in September.
by via JavaScript Weekly https://ift.tt/2Yu0uCP
0 notes
Text
Version 285
youtube
windows
zip
exe
os x
app
tar.gz
linux
tar.gz
source
tar.gz
I had a great week. There are several fixes and improvements, and the local booru is working again.
network menu and other highlights
I have created a new 'network' menu in the main gui window. It takes possession of several things that used to be under 'services' (including 'manage subscriptions') and will be the new home for the various gui related to the ongoing downloader overhaul.
The edit subscription panel now has a 'paste queries' button that lets you add queries en masse from a newline-separated list on the clipboard.
You can now set 'manage_file_urls' and 'get_similar_to_x' (for similar file search) shortcut actions under the 'media' shortcut set.
An issue where a December->January bandwidth calculation was giving errors should be fixed!
As some people are still getting hit by the old listctrl sort crash bug, I've turned off column sorting on all the old listctrls. Please feel free to now try to sort listctrls as much as you like--if the control is the new one, it will sort correctly, and if it isn't, nothing will happen. I will continue to update the last instances of the old control in the future. There are about 15 left to do now.
local booru
The local booru finally has its manage and review services panels back! These were replaced with placeholders in a big service rewrite a while ago, and it has taken a while to catch up on this cleanup job. They work essentially as they used to, but I updated a couple of things, like their buttons work a little better, and there's a little status text to tell you if the service isn't currently running. I apologise for the delay.
The local booru basically works as it used to before the change. This was always an experimental thing, but if you were ever into it, please give it another go and let me know your thoughts about possible features for future iterations. I expect a future version of this could be much more dynamic and permit searches and other high-CPU browsing and so on, perhaps in tandem with a broader client-API.
url class stuff
This is still only for advanced users.
As well as splitting the http header and url class panels apart into separate dialogs, I've added a new network->manage class links. It connects the defined url classes to other things. At the moment, it only allows you to show/hide different classes on the media viewer, but in future, it will connect them to known parsers on the new downloading engine.
Any url that is not matched to a url class by the domain manager will currently be shown in the media viewer by default, but I think I will add a bunch of url classes for the existing downloaders in the coming weeks and change this to be 'hide' by default.
full list
added 'network' main gui menu and moved network stuff from services to it
split the new domain manager stuff up into separate dialogs and menu entries on the new network menu
manage url classes dialog now lists url type in the listctrl
added url class links info (which will permit client-specific settings and downloader mappings for url classes) to the domain manager
wrote a 'url class links' dialog and added it to the new network menu (only the 'display on media viewer' part works atm)
the domain manager now filters urls on the media viewer depending on whether they have a url match and are set to display in the new links panel
updated the local booru service code to the new service system
the local booru's shares can be reviewed again under review services
the local booru's port and bandwidth settings can be set again under manage services
the different gui parts of the local booru are updated to new controls
fixed a local booru 404 reporting error
the edit subscription panel now has a 'paste queries' button that lets you add queries en masse
added 'manage_file_urls' to shortcuts system
added several 'get_similar_to_x' actions to the shortcuts system
the manage upnp dialog now initialises its mappings on another thread and fails better when UpnP mappings cannot be fetched
connection and readtimeout network exceptions are now recognised more specifically by the client. subscriptions will only delay for an hour on one of these exceptions
improved the resilience of the HF login code after wake from sleep (when networking is often not available for a couple of seconds)
like the recent subscription query randomisation update, subscriptions themselves are now synced in random order (this stops a subscription named 'aadvark' always getting first bite into available bandwidth)
fixed import for jpegs that have unparsable exif data
fixed a bug in 'next month' bandwidth estimate calculation when the month is December, wew
fixed some logic that was setting max page at 165 rather than the intended 200 and added a dialog that even lets you engage the debug override at 200 if you are insane
all audio mime detection and duration parsing is now done through ffmpeg. hsaudiotag is no longer needed to run the program
since the old listctrl sort crash bug is still hitting some people, I've disabled sort on the old listctrl class. feel free to try to sort any listctrls now, no matter your situation. I will continue replacing the old class with the new working class over time
updated another listctrl
a ton of misc controller options/manager access refactoring
cleared out some old code
moved Time controls to their own file and added velocity and checker options stuff as well
wrote a new edit panel for single controls and updated the time delta button to use it
misc refactoring
next week
I am not sure. I plan to reserve a big wx update in the last two weeks of the year, so I only have two weeks left before the year is done. I'd like to have something neat ready in that time, so I'll review what I have and push either towards a simple working login system or maybe some first custom parsers, perhaps for the thread watcher. I'll also continue to push on small issues and improvements as normal.
Also, we should hit 🎉200 million mappings🎉 on the public tag repository this week. Congratulations, everyone! The PTR has grown far larger than I ever expected (those 200m mappings are for 2.2m different tags and 11m files), and I'm really happy with and thankful for everyone's contributions to this milestone. Things have been running a lot better since the round of 'compactions' that cut the size of client.mappings.db (we now run about 32 bytes per mapping including hash and tag definitions, which I am very happy with), and now we are seeing different pressures, particularly at the CPU and workflow level. In the coming year, I expect to add some sort of 'clearing out crap' mechanism to the tag repository code so we can more solidly fix mis-parsed junk and filter things you do not care about and reduce CPU load in accessing this very large store of tags.
If you looked at one tag every second for eight solid hours a day, it would take nineteen years to see every tag on the PTR!
2 notes
·
View notes
Text
300+ TOP COMPUTER HARDWARE Objective Questions and Answers
Computer Hardware Multiple Choice Questions :-
1. How many pins does a SIMM have? A. 50 B. 64 C. 30 or 72 D. 168 Ans: C 2. The various cards in a PC requires _______ voltage to function. A. AC B. DC Ans: B 3. What type of hard disk formatting creates FAT (File Allocation Table) ? A. High Level B. Low Level Ans: A 4. What is the name of the printed circuit board? A. Ram B. Mother Board Ans: B 5. Which Component of pc maintains data and time A. CMOS RAM B. vRAM Ans: A 6. IRQ 1 is commonly assigned to: A. it's usually open B. system timer C. real time clock D. keyboard Ans: D 7. LCD monitor is also known as___________ A. TFT B. CRT Ans: A 8. How can you tell that a particular ribbon cable should only be used to connect a floppy drive? A. it B. it has a red line along one edge C. it D. it has a twist in it Ans: D 9. Data stored in a ROM cannot be changed by user of a computer? A. TRUE B. FALSE Ans: A 10. Is the data in a RAM stored on a permanent or temporary basis A. Temporary B. Permanent Ans: A

COMPUTER HARDWARE MCQs 11. Winchester drive is also called: A. Hard Disk Drive B. Floppy Disk Drive Ans: A 12. TO write, erase, rewrite data on a CD RAM what type of CD ROM you should use? A. CD-RW B. CD R Ans: A 13. A byte is equivalent to...? A. 8 bits B. 10 bits Ans: A 14. SMPS stands for: A. Switch Mode Power Supply B. Simple Mode Power Supply Ans: A 15. Which of the following is NOT a type of motherboard expansion slot? A. ISA B. PCI C. AGP D. ATX Ans: D 16. Which IRQ does LPT1 commonly use? A. 1 B. 4 C. 5 D. 7 Ans: D 17. How much data will a high density (HD) floppy disk hold? A. 124 KB B. 640 KB C. 1.44 MB D. 2.88MB Ans: C 18. What is the name of the spec for the holes in a monitor's aperture grill? A. dot pitch B. space holes Ans: A 19. Which is the best hard disk seek time? A. 3ms B. 5ms Ans: B 20. Fragmentation of data on computer hard disk causes it to work faster than before? A. FALSE B. TRUE Ans: A 21. What is the name of the card that controls read,write head and motor in the hard disk A. Network Card B. Disc Controller Card Ans: B 22. Which of the following retains the information it's storing when the power to the system is turned off? A. CPU B. ROM C. DRAM D. DIMM Ans: B 23. Acronym of HDD? A. Hard Disk Drive B. Hard Drive Disk Ans: A 24.A program written using binary codes is called: A. Software language B. Machine language Ans: B 25. How many bytes a sector of hard disk holds? A. 512 Bytes B. 1024 Bytes Ans: A 26. To be bootable a DOS partition must be: A. active B. copied Ans: A 27. What does FDISK do? A. performs low-level formatting of the hard drive B. fixes bad sectors on the hard drive C. recovers lost clusters on the hard drive D. creates partitions on the hard drive Ans: D 28. hat kind of connectors are used to connect a PC power supply to a hard drive? A. AT B. molex C. mini-molex D. P9 Ans: B 29. Acronym of FDD? A. Floppy Drive Disk B. Floppy Disk Drive Ans: B 30. Which of the following is NOT a type of computer hard drive? A. IDE B. FDD C. SCSI D. EIDE Ans: B COMPUTER HARDWARE Questions and Answers pdf Download Read the full article
0 notes
Text
Debugging 68030 PCB

I had dared to hope that since this board was created from the same schematic and board file I had made and referenced for my wire-wrap 68030 project, that I could just move the parts over and let it run. If I was really lucky, it might even be able to run faster than the original.
I should know by now it's never that easy.
The board does indeed run. It starts up, initializes its serial port, copies BASIC into RAM, verifies the copy, then starts running BASIC. It never gets to the BASIC ready prompt though.
Time to pull out the logic analyzer. This would certainly be easier if I had a proper logic analyzer with 64 or even over 100 channels, but there is a lot that can be learned 16 channels at a time. Watching important parts of the address bus I was able to watch it step through the BASIC initialization routines. However just before it got to the point where it would print its first carriage return, it jumped to an address I didn't expect, and I couldn't follow where it had gone. Shortly after, it would start accessing invalid addresses and generating bus errors.
The point where I lost it was right when it called a vector to its character print subroutine. This version of BASIC is written to be position-independent, so it has a short vector table for common I/O handlers in its global variable space. When it's time to call one of these routines, it performs a jump operation using the vector in that table ( jsr voutp(a3) ).
I could see it getting that far, recall the vector, and push its return address to stack. But where it ended up was a mystery.
This points to memory corruption somewhere, but where? I had a similar issue when I was building the prototype, before I had properly built out the RAM chip select signals, but that fix is already incorporated into this board.
I started writing some memory test routines. Unsurprisingly, long word write and read back tests all passed (after all it was loading and verifying BASIC the same way already). Byte-level tests also passed without issue. I needed something more thorough.
I put together a simple test that would write a single byte, followed by writing a long word, alternating for 16 total bytes. This would force it to write misaligned long words to confirm RAM addressing was working correctly.
It failed.
The bytes read back were all jumbled, and a couple values were missing altogether. This really was looking like that old problem with the missing chip select signals, but I had already verified those were firing.

This chart from the 68030 manual shows what data will be output for any given write cycle. I went through my memory test one write at a time, writing down what would be present on the data bus and where for each cycle.
The random, nonsensical data read back from RAM immediately made sense. Where a byte write cycle should have written data to the lowest-order bits, the highest-order bits were getting saved, and vice versa.
My chip RAM chip select signals are indeed working — they're just wired backwards.
Thankfully, that's an easy fix. I used a CPLD for all the glue logic on this project, so all I really need to do is update the pin assignments for those four signals. I don't even need a new board.
I might take this opportunity to further update the CPLD. I initially built out the logic for this project entirely in Quartus schematic view. I think I could do the same in System Verilog now. I suspect my old CPLD configuration may be partially responsible for my speed problems, so it may do some good to rewrite it.
16 notes
·
View notes
Text
This Week in Rust 487
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on Twitter or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub. If you find any errors in this week's issue, please submit a PR.
Foundation
Welcoming Software Engineer Adam Harvey to the Rust Foundation Team
New SLSA++ Survey Reveals Real-World Developer Approaches to Software Supply Chain Security
Newsletters
This Month in Rust OSDev: February 2023 | Rust OSDev
Project/Tooling Updates
autometrics 0.3: Defining Service-Level Objectives (SLOs) in Rust Source Code
Typst starts its public beta test and goes open source
Klint: Compile-time Detection of Atomic Context Violations for Kernel Rust Code
rust-analyzer changelog #173
Gitea 1.19.0 is released
Fornjot (code-first CAD in Rust) - Weekly Release - Finished!
activitypub-federation 0.4.0: Major rewrite with improvements to usability and documentation
Quickwit 0.5: Distributed tracing with Open Telemetry and Jaeger, VRL, Pulsar support, and more...!
pavex, a new Rust web framework - Progress report #2
Observations/Thoughts
Temporary lifetimes
Must move types
Defer blocks and async drop
A template proposal for adopting Rust at work
Patterns & Abstractions
Const as an auto trait
Item Patterns And Struct Else
Why use Rust on the backend?
The Importance of Logging
AsRef vs Borrow trait (ft. ChatGPT)
[audio] Cargo Limit with Alexander Lopatin :: Rustacean Station
[video] The Truth about Rust/WebAssembly Performance
Rust Walkthroughs
Using Cow in Rust for efficient memory utilization
STM32F4 Embedded Rust at the PAC: Creating Hardware Abstractions
STM32F4 Embedded Rust at the PAC: GPIO Interrupts
Build your own Counting Bloom Filter
[video] Setting up CI and property testing for a Rust crate
Research
Verus: Verifying Rust Programs using Linear Ghost Types
Ownership guided C to Rust translation
Optimizing a parser/compiler with data-oriented design: a case study
Miscellaneous
Bringing Rust to the Xen Project
The birth of a package manager [written in Rust ;)]
Crate of the Week
This week's crate is Speedy2D, a crate offering cross-platform Hardware-accelerated drawing of shapes, images, and text, with an easy to use API.
Thanks to Aleksey Kladov for the suggestion!
Please submit your suggestions and votes for next week!
Call for Participation
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
racoon - Open Source IAM call for contributors
Ockam - create clap command to show the details of a secure-channel listener on a node
Ockam - create clap command to delete an existing Forwarder on a node
Ockam - ockam run - a single command to run many ockam “create” commands
If you are a Rust project owner and are looking for contributors, please submit tasks here.
Updates from the Rust Project
321 pull requests were merged in the last week
inherit_overflow: adapt pattern to also work with v0 mangling
read_buf_exact: on error, all read bytes are appended to the buffer
add enable-warnings flag for llvm, and disable it by default
add useless_anonymous_reexport lint
add note for mismatched types because of circular dependencies
do not ICE for unexpected lifetime with ConstGeneric rib
don't ICE for late-bound consts across AnonConstBoundary
don't suggest similar method when unstable
fix ICE in custom-test-frameworks feature
fix ClashingExternDeclarations lint ICE
emit diagnostic when calling methods on the unit type in method chains
ensure ptr::read gets all the same LLVM load metadata that dereferencing does
erase escaping late-bound regions when probing for ambiguous associated types
error-msg: expand suggestion for unused_def lint
error-msg: impl better suggestion for E0532
fall back to old metadata computation when type references errors
fast path for process_obligations
fix generics_of for impl's RPITIT (Return Position Impl Trait In Trait) synthesized associated type
fix generics mismatch errors for RPITITs on -Zlower-impl-trait-in-trait-to-assoc-ty
install projection from RPITIT to default trait method opaque correctly
make fns from other crates with RPITIT work for -Zlower-impl-trait-in-trait-to-assoc-ty
fix object safety checks for new RPITITs
fix linker detection for clang with prefix
flatten/inline format_args!() and (string and int) literal arguments into format_args!()
implement FixedSizeEncoding for UnusedGenericParams
implement checked Shl/Shr at MIR building
only expect a GAT const param for type_of of GAT const arg
pass the right HIR back from get_fn_decl
remove identity_future indirection
remove box expressions from HIR
replace ZST operands and debuginfo by constants
simplify proc macro signature validity check
some cleanups in our normalization logic
suggest surrounding the macro with {} to interpret as a statement
use unused_generic_params from crate metadata
miri: move reject with isolation logic in fcntl
miri: tree borrows
properly allow macro expanded format_args invocations to use captures
optimize dep node backtrace and ignore fatal errors
fallback to lstat when stat fails on Windows
stabilise unix_socket_abstract
stabilize atomic_as_ptr
use index based drop loop for slices and arrays
allow using Range as an Iterator in const contexts
cargo: accurately show status when downgrading dependencies
cargo: add --ignore-rust-version flag to cargo install
cargo: add more information to wait-for-publish
cargo: align semantics of generated vcs ignore files
cargo: handle case mismatches when looking up env vars in the Config snapshot
rustdoc: correctly merge import's and its target's docs in one more case
rustdoc: docFS: replace rayon with threadpool and enable it for all targets
rustdoc: implement bag semantics for function parameter search
clippy: add allow_attribute lint
clippy: new lint to detect &std::path::MAIN_SEPARATOR.to_string()
clippy: enhance ifs_same_cond to warn same immutable method calls as well
clippy: fix almost_swapped false positive (let mut a = b; a = a)
clippy: fix almost_swapped: Ignore external macros
clippy: issue function modifiers in the right order in manual_async_fn lint
rust-analyzer: add an autofix for inserting an unsafe block to missing unsafe diagnostic
rust-analyzer: prioritize missing variants in match pattern completions
rust-analyzer: allow the status bar item to be clicked again
rust-analyzer: fix reference completions being emitted in places other than argument lists
rust-analyzer: fix rustc proc-macro handling being broken on the rustc workspace itself
rust-analyzer: fix visibility resolution not respecting parent blocks
rust-analyzer: only skip adjustment hints for block, if and match expressions for reborrows
rust-analyzer: lint incoherent inherent impls
Rust Compiler Performance Triage
A mixed week, with some nice wins, but also at least two PR's that were subsequently reverted, such as the upgrade to LLVM 16. We do want to note PR #108944, which cut down on crate metadata, binary sizes, and was an overall win on execution time for many benchmarks.
Triage done by @pnkfelix. Revision range: 00587489..ef03fda3
1 Regressions, 4 Improvements, 11 Mixed; 2 of them in rollups 37 artifact comparisons made in total
Full report here
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
No RFCs were approved this week.
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
[disposition: merge] RFC: result_ffi_guarantees
Tracking Issues & PRs
[disposition: merge] Initial support for return type notation (RTN)
[disposition: merge] rustdoc: add support for type filters in arguments and generics
[disposition: merge] rustdoc: run more HIR validation to mirror rustc
[disposition: merge] Add a builtin FnPtr trait that is implemented for all function pointers
[disposition: merge] Clarify stability guarantee for lifetimes in enum discriminants
New and Updated RFCs
No New or Updated RFCs were created this week.
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
No RFCs issued a call for testing this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Upcoming Events
Rusty Events between 2023-03-22 - 2023-04-19 🦀
Virtual
2023-03-22 | Virtual (Richmond, VA, US) | Rustaceans RVA
Rustaceans RVA - March Meetup
2023-03-27 | Virtual | Rust Formal Methods Interest Group
Flux: Ergonomic Verification of Rust Programs with Liquid Types
2023-03-28 | Virtual (Berlin, DE) | Berline.rs - OpenTechSchool Berlin
Rust Hack and Learn
2023-03-28 | Virtual (Dallas, TX, US) | Dallas Rust
Last Tuesday
2023-03-28 | Virtual (Redmond, WA, US) | Microsoft Reactor Redmond
Crack code interview problems in Rust: S2 Ep3
2023-03-29 | Virtual (Cardiff, UK) | Rust and C++ Cardiff
Writing your own rust 'book' with mdBook
2023-03-31 | Virtual (Tunis, TN) | Rust Tunisia
Rust Meetup Tunisia - Volume I, Number III
2023-04-04 | Virtual (Buffalo, NY, US) | Buffalo Rust Meetup
Buffalo Rust User Group, First Tuesdays
2023-04-05 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2023-04-05 | Virtual (Stuttgart, DE) | Rust Community Stuttgart
Rust-Meetup
2023-04-11 | Virtual (Berlin, DE) | Berline.rs - OpenTechSchool Berlin
Rust Hack and Learn
2023-04-11 | Virtual (Dallas, TX, US) | Dallas Rust
Second Tuesday
2023-04-11 | Virtual | Rust Live
Rust Live: Asynchronous Rust
2023-04-18 | Virtual (Washington, DC, US) | Rust DC
Mid-month Rustful—Introducing duplicate! and the peculiarities of proc macros
2023-04-19 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
Europe
2023-03-28 | Zurich, CH | Rust Zurich
High performance concurrent data structures in Rust - March Meetup
2023-03-29 | Paris, FR | Rust Paris
Rust Paris meetup #57
2023-04-04 | Berlin, DE | Berline.rs
Rust and Tell - Goodbye👋 Edition
2023-04-06 | Lyon, FR | Rust Lyon
Rust Lyon Meetup #3
2023-04-19 | Zurich, CH | Rust Zurich
sett: data encryption and transfer made easy(ier)
Asia
2023-04-08 | Kyoto, JP | Kansai Rust
Demystifying Closures
2023-04-12 | Kuala Lumpur, MY | Rust Malaysia; Telegram
Rust Meetup Malaysia April 2023: How far is Dioxus from React? by Ivan Tham | Map
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
The generated program is a random sequence of bytes that just happens to take the shape of a seemingly working program by accident. Such is the joy of code that causes UB. You cannot deduce anything from what happens when you execute a program with UB, since that act is by itself meaningless. You need to establish that your program has no UB before making any inference based on what you see the program do after it came out of the compiler.
– Ralf Jung on github
Thanks to bugaevc for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
1 note
·
View note
Text
docker 安装redis
1.下载redis 镜像
docker pull redis
2.启动镜像容器
docker run -d -p 6379:6379 --name redis -v /data/develop/docker/redis/conf/redis.conf:/etc/redis/redis.conf -v /data/develop/docker/redis/data:/data redis redis-server /etc/redis/redis.conf
3.查看是否已启动成功 1.查看docker 中redis的运行日志,如下:
docker logs -f redis

如果没有出现报错信息则使用redis连接工具进行验证,如下图:

注redis.conf默认配置如下:
# Redis configuration file example. # # Note that in order to read the configuration file, Redis must be # started with the file path as first argument: # # ./redis-server /path/to/redis.conf # Note on units: when memory size is needed, it is possible to specify # it in the usual form of 1k 5GB 4M and so forth: # # 1k => 1000 bytes # 1kb => 1024 bytes # 1m => 1000000 bytes # 1mb => 1024*1024 bytes # 1g => 1000000000 bytes # 1gb => 1024*1024*1024 bytes # # units are case insensitive so 1GB 1Gb 1gB are all the same. ################################## INCLUDES ################################### # Include one or more other config files here. This is useful if you # have a standard template that goes to all Redis servers but also need # to customize a few per-server settings. Include files can include # other files, so use this wisely. # # Notice option "include" won't be rewritten by command "CONFIG REWRITE" # from admin or Redis Sentinel. Since Redis always uses the last processed # line as value of a configuration directive, you'd better put includes # at the beginning of this file to avoid overwriting config change at runtime. # # If instead you are interested in using includes to override configuration # options, it is better to use include as the last line. # # include /path/to/local.conf # include /path/to/other.conf ################################## MODULES ##################################### # Load modules at startup. If the server is not able to load modules # it will abort. It is possible to use multiple loadmodule directives. # # loadmodule /path/to/my_module.so # loadmodule /path/to/other_module.so ################################## NETWORK ##################################### # By default, if no "bind" configuration directive is specified, Redis listens # for connections from all the network interfaces available on the server. # It is possible to listen to just one or multiple selected interfaces using # the "bind" configuration directive, followed by one or more IP addresses. # # Examples: # # bind 192.168.1.100 10.0.0.1 # bind 127.0.0.1 ::1 # # ~~~ WARNING ~~~ If the computer running Redis is directly exposed to the # internet, binding to all the interfaces is dangerous and will expose the # instance to everybody on the internet. So by default we uncomment the # following bind directive, that will force Redis to listen only into # the IPv4 loopback interface address (this means Redis will be able to # accept connections only from clients running into the same computer it # is running). # # IF YOU ARE SURE YOU WANT YOUR INSTANCE TO LISTEN TO ALL THE INTERFACES # JUST COMMENT THE FOLLOWING LINE. # ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ bind 127.0.0.1 # Protected mode is a layer of security protection, in order to avoid that # Redis instances left open on the internet are accessed and exploited. # # When protected mode is on and if: # # 1) The server is not binding explicitly to a set of addresses using the # "bind" directive. # 2) No password is configured. # # The server only accepts connections from clients connecting from the # IPv4 and IPv6 loopback addresses 127.0.0.1 and ::1, and from Unix domain # sockets. # # By default protected mode is enabled. You should disable it only if # you are sure you want clients from other hosts to connect to Redis # even if no authentication is configured, nor a specific set of interfaces # are explicitly listed using the "bind" directive. protected-mode yes # Accept connections on the specified port, default is 6379 (IANA #815344). # If port 0 is specified Redis will not listen on a TCP socket. port 6379 # TCP listen() backlog. # # In high requests-per-second environments you need an high backlog in order # to avoid slow clients connections issues. Note that the Linux kernel # will silently truncate it to the value of /proc/sys/net/core/somaxconn so # make sure to raise both the value of somaxconn and tcp_max_syn_backlog # in order to get the desired effect. tcp-backlog 511 # Unix socket. # # Specify the path for the Unix socket that will be used to listen for # incoming connections. There is no default, so Redis will not listen # on a unix socket when not specified. # # unixsocket /tmp/redis.sock # unixsocketperm 700 # Close the connection after a client is idle for N seconds (0 to disable) timeout 0 # TCP keepalive. # # If non-zero, use SO_KEEPALIVE to send TCP ACKs to clients in absence # of communication. This is useful for two reasons: # # 1) Detect dead peers. # 2) Take the connection alive from the point of view of network # equipment in the middle. # # On Linux, the specified value (in seconds) is the period used to send ACKs. # Note that to close the connection the double of the time is needed. # On other kernels the period depends on the kernel configuration. # # A reasonable value for this option is 300 seconds, which is the new # Redis default starting with Redis 3.2.1. tcp-keepalive 300 ################################# GENERAL ##################################### # By default Redis does not run as a daemon. Use 'yes' if you need it. # Note that Redis will write a pid file in /var/run/redis.pid when daemonized. daemonize no # If you run Redis from upstart or systemd, Redis can interact with your # supervision tree. Options: # supervised no - no supervision interaction # supervised upstart - signal upstart by putting Redis into SIGSTOP mode # supervised systemd - signal systemd by writing READY=1 to $NOTIFY_SOCKET # supervised auto - detect upstart or systemd method based on # UPSTART_JOB or NOTIFY_SOCKET environment variables # Note: these supervision methods only signal "process is ready." # They do not enable continuous liveness pings back to your supervisor. supervised no # If a pid file is specified, Redis writes it where specified at startup # and removes it at exit. # # When the server runs non daemonized, no pid file is created if none is # specified in the configuration. When the server is daemonized, the pid file # is used even if not specified, defaulting to "/var/run/redis.pid". # # Creating a pid file is best effort: if Redis is not able to create it # nothing bad happens, the server will start and run normally. pidfile /var/run/redis_6379.pid # Specify the server verbosity level. # This can be one of: # debug (a lot of information, useful for development/testing) # verbose (many rarely useful info, but not a mess like the debug level) # notice (moderately verbose, what you want in production probably) # warning (only very important / critical messages are logged) loglevel notice # Specify the log file name. Also the empty string can be used to force # Redis to log on the standard output. Note that if you use standard # output for logging but daemonize, logs will be sent to /dev/null logfile "" # To enable logging to the system logger, just set 'syslog-enabled' to yes, # and optionally update the other syslog parameters to suit your needs. # syslog-enabled no # Specify the syslog identity. # syslog-ident redis # Specify the syslog facility. Must be USER or between LOCAL0-LOCAL7. # syslog-facility local0 # Set the number of databases. The default database is DB 0, you can select # a different one on a per-connection basis using SELECT <dbid> where # dbid is a number between 0 and 'databases'-1 databases 16 # By default Redis shows an ASCII art logo only when started to log to the # standard output and if the standard output is a TTY. Basically this means # that normally a logo is displayed only in interactive sessions. # # However it is possible to force the pre-4.0 behavior and always show a # ASCII art logo in startup logs by setting the following option to yes. always-show-logo yes ################################ SNAPSHOTTING ################################ # # Save the DB on disk: # # save <seconds> <changes> # # Will save the DB if both the given number of seconds and the given # number of write operations against the DB occurred. # # In the example below the behaviour will be to save: # after 900 sec (15 min) if at least 1 key changed # after 300 sec (5 min) if at least 10 keys changed # after 60 sec if at least 10000 keys changed # # Note: you can disable saving completely by commenting out all "save" lines. # # It is also possible to remove all the previously configured save # points by adding a save directive with a single empty string argument # like in the following example: # # save "" save 900 1 save 300 10 save 60 10000 # By default Redis will stop accepting writes if RDB snapshots are enabled # (at least one save point) and the latest background save failed. # This will make the user aware (in a hard way) that data is not persisting # on disk properly, otherwise chances are that no one will notice and some # disaster will happen. # # If the background saving process will start working again Redis will # automatically allow writes again. # # However if you have setup your proper monitoring of the Redis server # and persistence, you may want to disable this feature so that Redis will # continue to work as usual even if there are problems with disk, # permissions, and so forth. stop-writes-on-bgsave-error yes # Compress string objects using LZF when dump .rdb databases? # For default that's set to 'yes' as it's almost always a win. # If you want to save some CPU in the saving child set it to 'no' but # the dataset will likely be bigger if you have compressible values or keys. rdbcompression yes # Since version 5 of RDB a CRC64 checksum is placed at the end of the file. # This makes the format more resistant to corruption but there is a performance # hit to pay (around 10%) when saving and loading RDB files, so you can disable it # for maximum performances. # # RDB files created with checksum disabled have a checksum of zero that will # tell the loading code to skip the check. rdbchecksum yes # The filename where to dump the DB dbfilename dump.rdb # The working directory. # # The DB will be written inside this directory, with the filename specified # above using the 'dbfilename' configuration directive. # # The Append Only File will also be created inside this directory. # # Note that you must specify a directory here, not a file name. dir ./ ################################# REPLICATION ################################# # Master-Replica replication. Use replicaof to make a Redis instance a copy of # another Redis server. A few things to understand ASAP about Redis replication. # # +------------------+ +---------------+ # | Master | ---> | Replica | # | (receive writes) | | (exact copy) | # +------------------+ +---------------+ # # 1) Redis replication is asynchronous, but you can configure a master to # stop accepting writes if it appears to be not connected with at least # a given number of replicas. # 2) Redis replicas are able to perform a partial resynchronization with the # master if the replication link is lost for a relatively small amount of # time. You may want to configure the replication backlog size (see the next # sections of this file) with a sensible value depending on your needs. # 3) Replication is automatic and does not need user intervention. After a # network partition replicas automatically try to reconnect to masters # and resynchronize with them. # # replicaof <masterip> <masterport> # If the master is password protected (using the "requirepass" configuration # directive below) it is possible to tell the replica to authenticate before # starting the replication synchronization process, otherwise the master will # refuse the replica request. # # masterauth <master-password> # When a replica loses its connection with the master, or when the replication # is still in progress, the replica can act in two different ways: # # 1) if replica-serve-stale-data is set to 'yes' (the default) the replica will # still reply to client requests, possibly with out of date data, or the # data set may just be empty if this is the first synchronization. # # 2) if replica-serve-stale-data is set to 'no' the replica will reply with # an error "SYNC with master in progress" to all the kind of commands # but to INFO, replicaOF, AUTH, PING, SHUTDOWN, REPLCONF, ROLE, CONFIG, # SUBSCRIBE, UNSUBSCRIBE, PSUBSCRIBE, PUNSUBSCRIBE, PUBLISH, PUBSUB, # COMMAND, POST, HOST: and LATENCY. # replica-serve-stale-data yes # You can configure a replica instance to accept writes or not. Writing against # a replica instance may be useful to store some ephemeral data (because data # written on a replica will be easily deleted after resync with the master) but # may also cause problems if clients are writing to it because of a # misconfiguration. # # Since Redis 2.6 by default replicas are read-only. # # Note: read only replicas are not designed to be exposed to untrusted clients # on the internet. It's just a protection layer against misuse of the instance. # Still a read only replica exports by default all the administrative commands # such as CONFIG, DEBUG, and so forth. To a limited extent you can improve # security of read only replicas using 'rename-command' to shadow all the # administrative / dangerous commands. replica-read-only yes # Replication SYNC strategy: disk or socket. # # ------------------------------------------------------- # WARNING: DISKLESS REPLICATION IS EXPERIMENTAL CURRENTLY # ------------------------------------------------------- # # New replicas and reconnecting replicas that are not able to continue the replication # process just receiving differences, need to do what is called a "full # synchronization". An RDB file is transmitted from the master to the replicas. # The transmission can happen in two different ways: # # 1) Disk-backed: The Redis master creates a new process that writes the RDB # file on disk. Later the file is transferred by the parent # process to the replicas incrementally. # 2) Diskless: The Redis master creates a new process that directly writes the # RDB file to replica sockets, without touching the disk at all. # # With disk-backed replication, while the RDB file is generated, more replicas # can be queued and served with the RDB file as soon as the current child producing # the RDB file finishes its work. With diskless replication instead once # the transfer starts, new replicas arriving will be queued and a new transfer # will start when the current one terminates. # # When diskless replication is used, the master waits a configurable amount of # time (in seconds) before starting the transfer in the hope that multiple replicas # will arrive and the transfer can be parallelized. # # With slow disks and fast (large bandwidth) networks, diskless replication # works better. repl-diskless-sync no # When diskless replication is enabled, it is possible to configure the delay # the server waits in order to spawn the child that transfers the RDB via socket # to the replicas. # # This is important since once the transfer starts, it is not possible to serve # new replicas arriving, that will be queued for the next RDB transfer, so the server # waits a delay in order to let more replicas arrive. # # The delay is specified in seconds, and by default is 5 seconds. To disable # it entirely just set it to 0 seconds and the transfer will start ASAP. repl-diskless-sync-delay 5 # Replicas send PINGs to server in a predefined interval. It's possible to change # this interval with the repl_ping_replica_period option. The default value is 10 # seconds. # # repl-ping-replica-period 10 # The following option sets the replication timeout for: # # 1) Bulk transfer I/O during SYNC, from the point of view of replica. # 2) Master timeout from the point of view of replicas (data, pings). # 3) Replica timeout from the point of view of masters (REPLCONF ACK pings). # # It is important to make sure that this value is greater than the value # specified for repl-ping-replica-period otherwise a timeout will be detected # every time there is low traffic between the master and the replica. # # repl-timeout 60 # Disable TCP_NODELAY on the replica socket after SYNC? # # If you select "yes" Redis will use a smaller number of TCP packets and # less bandwidth to send data to replicas. But this can add a delay for # the data to appear on the replica side, up to 40 milliseconds with # Linux kernels using a default configuration. # # If you select "no" the delay for data to appear on the replica side will # be reduced but more bandwidth will be used for replication. # # By default we optimize for low latency, but in very high traffic conditions # or when the master and replicas are many hops away, turning this to "yes" may # be a good idea. repl-disable-tcp-nodelay no # Set the replication backlog size. The backlog is a buffer that accumulates # replica data when replicas are disconnected for some time, so that when a replica # wants to reconnect again, often a full resync is not needed, but a partial # resync is enough, just passing the portion of data the replica missed while # disconnected. # # The bigger the replication backlog, the longer the time the replica can be # disconnected and later be able to perform a partial resynchronization. # # The backlog is only allocated once there is at least a replica connected. # # repl-backlog-size 1mb # After a master has no longer connected replicas for some time, the backlog # will be freed. The following option configures the amount of seconds that # need to elapse, starting from the time the last replica disconnected, for # the backlog buffer to be freed. # # Note that replicas never free the backlog for timeout, since they may be # promoted to masters later, and should be able to correctly "partially # resynchronize" with the replicas: hence they should always accumulate backlog. # # A value of 0 means to never release the backlog. # # repl-backlog-ttl 3600 # The replica priority is an integer number published by Redis in the INFO output. # It is used by Redis Sentinel in order to select a replica to promote into a # master if the master is no longer working correctly. # # A replica with a low priority number is considered better for promotion, so # for instance if there are three replicas with priority 10, 100, 25 Sentinel will # pick the one with priority 10, that is the lowest. # # However a special priority of 0 marks the replica as not able to perform the # role of master, so a replica with priority of 0 will never be selected by # Redis Sentinel for promotion. # # By default the priority is 100. replica-priority 100 # It is possible for a master to stop accepting writes if there are less than # N replicas connected, having a lag less or equal than M seconds. # # The N replicas need to be in "online" state. # # The lag in seconds, that must be <= the specified value, is calculated from # the last ping received from the replica, that is usually sent every second. # # This option does not GUARANTEE that N replicas will accept the write, but # will limit the window of exposure for lost writes in case not enough replicas # are available, to the specified number of seconds. # # For example to require at least 3 replicas with a lag <= 10 seconds use: # # min-replicas-to-write 3 # min-replicas-max-lag 10 # # Setting one or the other to 0 disables the feature. # # By default min-replicas-to-write is set to 0 (feature disabled) and # min-replicas-max-lag is set to 10. # A Redis master is able to list the address and port of the attached # replicas in different ways. For example the "INFO replication" section # offers this information, which is used, among other tools, by # Redis Sentinel in order to discover replica instances. # Another place where this info is available is in the output of the # "ROLE" command of a master. # # The listed IP and address normally reported by a replica is obtained # in the following way: # # IP: The address is auto detected by checking the peer address # of the socket used by the replica to connect with the master. # # Port: The port is communicated by the replica during the replication # handshake, and is normally the port that the replica is using to # listen for connections. # # However when port forwarding or Network Address Translation (NAT) is # used, the replica may be actually reachable via different IP and port # pairs. The following two options can be used by a replica in order to # report to its master a specific set of IP and port, so that both INFO # and ROLE will report those values. # # There is no need to use both the options if you need to override just # the port or the IP address. # # replica-announce-ip 5.5.5.5 # replica-announce-port 1234 ################################## SECURITY ################################### # Require clients to issue AUTH <PASSWORD> before processing any other # commands. This might be useful in environments in which you do not trust # others with access to the host running redis-server. # # This should stay commented out for backward compatibility and because most # people do not need auth (e.g. they run their own servers). # # Warning: since Redis is pretty fast an outside user can try up to # 150k passwords per second against a good box. This means that you should # use a very strong password otherwise it will be very easy to break. # # requirepass foobared # Command renaming. # # It is possible to change the name of dangerous commands in a shared # environment. For instance the CONFIG command may be renamed into something # hard to guess so that it will still be available for internal-use tools # but not available for general clients. # # Example: # # rename-command CONFIG b840fc02d524045429941cc15f59e41cb7be6c52 # # It is also possible to completely kill a command by renaming it into # an empty string: # # rename-command CONFIG "" # # Please note that changing the name of commands that are logged into the # AOF file or transmitted to replicas may cause problems. ################################### CLIENTS #################################### # Set the max number of connected clients at the same time. By default # this limit is set to 10000 clients, however if the Redis server is not # able to configure the process file limit to allow for the specified limit # the max number of allowed clients is set to the current file limit # minus 32 (as Redis reserves a few file descriptors for internal uses). # # Once the limit is reached Redis will close all the new connections sending # an error 'max number of clients reached'. # # maxclients 10000 ############################## MEMORY MANAGEMENT ################################ # Set a memory usage limit to the specified amount of bytes. # When the memory limit is reached Redis will try to remove keys # according to the eviction policy selected (see maxmemory-policy). # # If Redis can't remove keys according to the policy, or if the policy is # set to 'noeviction', Redis will start to reply with errors to commands # that would use more memory, like SET, LPUSH, and so on, and will continue # to reply to read-only commands like GET. # # This option is usually useful when using Redis as an LRU or LFU cache, or to # set a hard memory limit for an instance (using the 'noeviction' policy). # # WARNING: If you have replicas attached to an instance with maxmemory on, # the size of the output buffers needed to feed the replicas are subtracted # from the used memory count, so that network problems / resyncs will # not trigger a loop where keys are evicted, and in turn the output # buffer of replicas is full with DELs of keys evicted triggering the deletion # of more keys, and so forth until the database is completely emptied. # # In short... if you have replicas attached it is suggested that you set a lower # limit for maxmemory so that there is some free RAM on the system for replica # output buffers (but this is not needed if the policy is 'noeviction'). # # maxmemory <bytes> # MAXMEMORY POLICY: how Redis will select what to remove when maxmemory # is reached. You can select among five behaviors: # # volatile-lru -> Evict using approximated LRU among the keys with an expire set. # allkeys-lru -> Evict any key using approximated LRU. # volatile-lfu -> Evict using approximated LFU among the keys with an expire set. # allkeys-lfu -> Evict any key using approximated LFU. # volatile-random -> Remove a random key among the ones with an expire set. # allkeys-random -> Remove a random key, any key. # volatile-ttl -> Remove the key with the nearest expire time (minor TTL) # noeviction -> Don't evict anything, just return an error on write operations. # # LRU means Least Recently Used # LFU means Least Frequently Used # # Both LRU, LFU and volatile-ttl are implemented using approximated # randomized algorithms. # # Note: with any of the above policies, Redis will return an error on write # operations, when there are no suitable keys for eviction. # # At the date of writing these commands are: set setnx setex append # incr decr rpush lpush rpushx lpushx linsert lset rpoplpush sadd # sinter sinterstore sunion sunionstore sdiff sdiffstore zadd zincrby # zunionstore zinterstore hset hsetnx hmset hincrby incrby decrby # getset mset msetnx exec sort # # The default is: # # maxmemory-policy noeviction # LRU, LFU and minimal TTL algorithms are not precise algorithms but approximated # algorithms (in order to save memory), so you can tune it for speed or # accuracy. For default Redis will check five keys and pick the one that was # used less recently, you can change the sample size using the following # configuration directive. # # The default of 5 produces good enough results. 10 Approximates very closely # true LRU but costs more CPU. 3 is faster but not very accurate. # # maxmemory-samples 5 # Starting from Redis 5, by default a replica will ignore its maxmemory setting # (unless it is promoted to master after a failover or manually). It means # that the eviction of keys will be just handled by the master, sending the # DEL commands to the replica as keys evict in the master side. # # This behavior ensures that masters and replicas stay consistent, and is usually # what you want, however if your replica is writable, or you want the replica to have # a different memory setting, and you are sure all the writes performed to the # replica are idempotent, then you may change this default (but be sure to understand # what you are doing). # # Note that since the replica by default does not evict, it may end using more # memory than the one set via maxmemory (there are certain buffers that may # be larger on the replica, or data structures may sometimes take more memory and so # forth). So make sure you monitor your replicas and make sure they have enough # memory to never hit a real out-of-memory condition before the master hits # the configured maxmemory setting. # # replica-ignore-maxmemory yes ############################# LAZY FREEING #################################### # Redis has two primitives to delete keys. One is called DEL and is a blocking # deletion of the object. It means that the server stops processing new commands # in order to reclaim all the memory associated with an object in a synchronous # way. If the key deleted is associated with a small object, the time needed # in order to execute the DEL command is very small and comparable to most other # O(1) or O(log_N) commands in Redis. However if the key is associated with an # aggregated value containing millions of elements, the server can block for # a long time (even seconds) in order to complete the operation. # # For the above reasons Redis also offers non blocking deletion primitives # such as UNLINK (non blocking DEL) and the ASYNC option of FLUSHALL and # FLUSHDB commands, in order to reclaim memory in background. Those commands # are executed in constant time. Another thread will incrementally free the # object in the background as fast as possible. # # DEL, UNLINK and ASYNC option of FLUSHALL and FLUSHDB are user-controlled. # It's up to the design of the application to understand when it is a good # idea to use one or the other. However the Redis server sometimes has to # delete keys or flush the whole database as a side effect of other operations. # Specifically Redis deletes objects independently of a user call in the # following scenarios: # # 1) On eviction, because of the maxmemory and maxmemory policy configurations, # in order to make room for new data, without going over the specified # memory limit. # 2) Because of expire: when a key with an associated time to live (see the # EXPIRE command) must be deleted from memory. # 3) Because of a side effect of a command that stores data on a key that may # already exist. For example the RENAME command may delete the old key # content when it is replaced with another one. Similarly SUNIONSTORE # or SORT with STORE option may delete existing keys. The SET command # itself removes any old content of the specified key in order to replace # it with the specified string. # 4) During replication, when a replica performs a full resynchronization with # its master, the content of the whole database is removed in order to # load the RDB file just transferred. # # In all the above cases the default is to delete objects in a blocking way, # like if DEL was called. However you can configure each case specifically # in order to instead release memory in a non-blocking way like if UNLINK # was called, using the following configuration directives: lazyfree-lazy-eviction no lazyfree-lazy-expire no lazyfree-lazy-server-del no replica-lazy-flush no ############################## APPEND ONLY MODE ############################### # By default Redis asynchronously dumps the dataset on disk. This mode is # good enough in many applications, but an issue with the Redis process or # a power outage may result into a few minutes of writes lost (depending on # the configured save points). # # The Append Only File is an alternative persistence mode that provides # much better durability. For instance using the default data fsync policy # (see later in the config file) Redis can lose just one second of writes in a # dramatic event like a server power outage, or a single write if something # wrong with the Redis process itself happens, but the operating system is # still running correctly. # # AOF and RDB persistence can be enabled at the same time without problems. # If the AOF is enabled on startup Redis will load the AOF, that is the file # with the better durability guarantees. # # Please check http://redis.io/topics/persistence for more information. appendonly no # The name of the append only file (default: "appendonly.aof") appendfilename "appendonly.aof" # The fsync() call tells the Operating System to actually write data on disk # instead of waiting for more data in the output buffer. Some OS will really flush # data on disk, some other OS will just try to do it ASAP. # # Redis supports three different modes: # # no: don't fsync, just let the OS flush the data when it wants. Faster. # always: fsync after every write to the append only log. Slow, Safest. # everysec: fsync only one time every second. Compromise. # # The default is "everysec", as that's usually the right compromise between # speed and data safety. It's up to you to understand if you can relax this to # "no" that will let the operating system flush the output buffer when # it wants, for better performances (but if you can live with the idea of # some data loss consider the default persistence mode that's snapshotting), # or on the contrary, use "always" that's very slow but a bit safer than # everysec. # # More details please check the following article: # http://antirez.com/post/redis-persistence-demystified.html # # If unsure, use "everysec". # appendfsync always appendfsync everysec # appendfsync no # When the AOF fsync policy is set to always or everysec, and a background # saving process (a background save or AOF log background rewriting) is # performing a lot of I/O against the disk, in some Linux configurations # Redis may block too long on the fsync() call. Note that there is no fix for # this currently, as even performing fsync in a different thread will block # our synchronous write(2) call. # # In order to mitigate this problem it's possible to use the following option # that will prevent fsync() from being called in the main process while a # BGSAVE or BGREWRITEAOF is in progress. # # This means that while another child is saving, the durability of Redis is # the same as "appendfsync none". In practical terms, this means that it is # possible to lose up to 30 seconds of log in the worst scenario (with the # default Linux settings). # # If you have latency problems turn this to "yes". Otherwise leave it as # "no" that is the safest pick from the point of view of durability. no-appendfsync-on-rewrite no # Automatic rewrite of the append only file. # Redis is able to automatically rewrite the log file implicitly calling # BGREWRITEAOF when the AOF log size grows by the specified percentage. # # This is how it works: Redis remembers the size of the AOF file after the # latest rewrite (if no rewrite has happened since the restart, the size of # the AOF at startup is used). # # This base size is compared to the current size. If the current size is # bigger than the specified percentage, the rewrite is triggered. Also # you need to specify a minimal size for the AOF file to be rewritten, this # is useful to avoid rewriting the AOF file even if the percentage increase # is reached but it is still pretty small. # # Specify a percentage of zero in order to disable the automatic AOF # rewrite feature. auto-aof-rewrite-percentage 100 auto-aof-rewrite-min-size 64mb # An AOF file may be found to be truncated at the end during the Redis # startup process, when the AOF data gets loaded back into memory. # This may happen when the system where Redis is running # crashes, especially when an ext4 filesystem is mounted without the # data=ordered option (however this can't happen when Redis itself # crashes or aborts but the operating system still works correctly). # # Redis can either exit with an error when this happens, or load as much # data as possible (the default now) and start if the AOF file is found # to be truncated at the end. The following option controls this behavior. # # If aof-load-truncated is set to yes, a truncated AOF file is loaded and # the Redis server starts emitting a log to inform the user of the event. # Otherwise if the option is set to no, the server aborts with an error # and refuses to start. When the option is set to no, the user requires # to fix the AOF file using the "redis-check-aof" utility before to restart # the server. # # Note that if the AOF file will be found to be corrupted in the middle # the server will still exit with an error. This option only applies when # Redis will try to read more data from the AOF file but not enough bytes # will be found. aof-load-truncated yes # When rewriting the AOF file, Redis is able to use an RDB preamble in the # AOF file for faster rewrites and recoveries. When this option is turned # on the rewritten AOF file is composed of two different stanzas: # # [RDB file][AOF tail] # # When loading Redis recognizes that the AOF file starts with the "REDIS" # string and loads the prefixed RDB file, and continues loading the AOF # tail. aof-use-rdb-preamble yes ################################ LUA SCRIPTING ############################### # Max execution time of a Lua script in milliseconds. # # If the maximum execution time is reached Redis will log that a script is # still in execution after the maximum allowed time and will start to # reply to queries with an error. # # When a long running script exceeds the maximum execution time only the # SCRIPT KILL and SHUTDOWN NOSAVE commands are available. The first can be # used to stop a script that did not yet called write commands. The second # is the only way to shut down the server in the case a write command was # already issued by the script but the user doesn't want to wait for the natural # termination of the script. # # Set it to 0 or a negative value for unlimited execution without warnings. lua-time-limit 5000 ################################ REDIS CLUSTER ############################### # Normal Redis instances can't be part of a Redis Cluster; only nodes that are # started as cluster nodes can. In order to start a Redis instance as a # cluster node enable the cluster support uncommenting the following: # # cluster-enabled yes # Every cluster node has a cluster configuration file. This file is not # intended to be edited by hand. It is created and updated by Redis nodes. # Every Redis Cluster node requires a different cluster configuration file. # Make sure that instances running in the same system do not have # overlapping cluster configuration file names. # # cluster-config-file nodes-6379.conf # Cluster node timeout is the amount of milliseconds a node must be unreachable # for it to be considered in failure state. # Most other internal time limits are multiple of the node timeout. # # cluster-node-timeout 15000 # A replica of a failing master will avoid to start a failover if its data # looks too old. # # There is no simple way for a replica to actually have an exact measure of # its "data age", so the following two checks are performed: # # 1) If there are multiple replicas able to failover, they exchange messages # in order to try to give an advantage to the replica with the best # replication offset (more data from the master processed). # Replicas will try to get their rank by offset, and apply to the start # of the failover a delay proportional to their rank. # # 2) Every single replica computes the time of the last interaction with # its master. This can be the last ping or command received (if the master # is still in the "connected" state), or the time that elapsed since the # disconnection with the master (if the replication link is currently down). # If the last interaction is too old, the replica will not try to failover # at all. # # The point "2" can be tuned by user. Specifically a replica will not perform # the failover if, since the last interaction with the master, the time # elapsed is greater than: # # (node-timeout * replica-validity-factor) + repl-ping-replica-period # # So for example if node-timeout is 30 seconds, and the replica-validity-factor # is 10, and assuming a default repl-ping-replica-period of 10 seconds, the # replica will not try to failover if it was not able to talk with the master # for longer than 310 seconds. # # A large replica-validity-factor may allow replicas with too old data to failover # a master, while a too small value may prevent the cluster from being able to # elect a replica at all. # # For maximum availability, it is possible to set the replica-validity-factor # to a value of 0, which means, that replicas will always try to failover the # master regardless of the last time they interacted with the master. # (However they'll always try to apply a delay proportional to their # offset rank). # # Zero is the only value able to guarantee that when all the partitions heal # the cluster will always be able to continue. # # cluster-replica-validity-factor 10 # Cluster replicas are able to migrate to orphaned masters, that are masters # that are left without working replicas. This improves the cluster ability # to resist to failures as otherwise an orphaned master can't be failed over # in case of failure if it has no working replicas. # # Replicas migrate to orphaned masters only if there are still at least a # given number of other working replicas for their old master. This number # is the "migration barrier". A migration barrier of 1 means that a replica # will migrate only if there is at least 1 other working replica for its master # and so forth. It usually reflects the number of replicas you want for every # master in your cluster. # # Default is 1 (replicas migrate only if their masters remain with at least # one replica). To disable migration just set it to a very large value. # A value of 0 can be set but is useful only for debugging and dangerous # in production. # # cluster-migration-barrier 1 # By default Redis Cluster nodes stop accepting queries if they detect there # is at least an hash slot uncovered (no available node is serving it). # This way if the cluster is partially down (for example a range of hash slots # are no longer covered) all the cluster becomes, eventually, unavailable. # It automatically returns available as soon as all the slots are covered again. # # However sometimes you want the subset of the cluster which is working, # to continue to accept queries for the part of the key space that is still # covered. In order to do so, just set the cluster-require-full-coverage # option to no. # # cluster-require-full-coverage yes # This option, when set to yes, prevents replicas from trying to failover its # master during master failures. However the master can still perform a # manual failover, if forced to do so. # # This is useful in different scenarios, especially in the case of multiple # data center operations, where we want one side to never be promoted if not # in the case of a total DC failure. # # cluster-replica-no-failover no # In order to setup your cluster make sure to read the documentation # available at http://redis.io web site. ########################## CLUSTER DOCKER/NAT support ######################## # In certain deployments, Redis Cluster nodes address discovery fails, because # addresses are NAT-ted or because ports are forwarded (the typical case is # Docker and other containers). # # In order to make Redis Cluster working in such environments, a static # configuration where each node knows its public address is needed. The # following two options are used for this scope, and are: # # * cluster-announce-ip # * cluster-announce-port # * cluster-announce-bus-port # # Each instruct the node about its address, client port, and cluster message # bus port. The information is then published in the header of the bus packets # so that other nodes will be able to correctly map the address of the node # publishing the information. # # If the above options are not used, the normal Redis Cluster auto-detection # will be used instead. # # Note that when remapped, the bus port may not be at the fixed offset of # clients port + 10000, so you can specify any port and bus-port depending # on how they get remapped. If the bus-port is not set, a fixed offset of # 10000 will be used as usually. # # Example: # # cluster-announce-ip 10.1.1.5 # cluster-announce-port 6379 # cluster-announce-bus-port 6380 ################################## SLOW LOG ################################### # The Redis Slow Log is a system to log queries that exceeded a specified # execution time. The execution time does not include the I/O operations # like talking with the client, sending the reply and so forth, # but just the time needed to actually execute the command (this is the only # stage of command execution where the thread is blocked and can not serve # other requests in the meantime). # # You can configure the slow log with two parameters: one tells Redis # what is the execution time, in microseconds, to exceed in order for the # command to get logged, and the other parameter is the length of the # slow log. When a new command is logged the oldest one is removed from the # queue of logged commands. # The following time is expressed in microseconds, so 1000000 is equivalent # to one second. Note that a negative number disables the slow log, while # a value of zero forces the logging of every command. slowlog-log-slower-than 10000 # There is no limit to this length. Just be aware that it will consume memory. # You can reclaim memory used by the slow log with SLOWLOG RESET. slowlog-max-len 128 ################################ LATENCY MONITOR ############################## # The Redis latency monitoring subsystem samples different operations # at runtime in order to collect data related to possible sources of # latency of a Redis instance. # # Via the LATENCY command this information is available to the user that can # print graphs and obtain reports. # # The system only logs operations that were performed in a time equal or # greater than the amount of milliseconds specified via the # latency-monitor-threshold configuration directive. When its value is set # to zero, the latency monitor is turned off. # # By default latency monitoring is disabled since it is mostly not needed # if you don't have latency issues, and collecting data has a performance # impact, that while very small, can be measured under big load. Latency # monitoring can easily be enabled at runtime using the command # "CONFIG SET latency-monitor-threshold <milliseconds>" if needed. latency-monitor-threshold 0 ############################# EVENT NOTIFICATION ############################## # Redis can notify Pub/Sub clients about events happening in the key space. # This feature is documented at http://redis.io/topics/notifications # # For instance if keyspace events notification is enabled, and a client # performs a DEL operation on key "foo" stored in the Database 0, two # messages will be published via Pub/Sub: # # PUBLISH __keyspace@0__:foo del # PUBLISH __keyevent@0__:del foo # # It is possible to select the events that Redis will notify among a set # of classes. Every class is identified by a single character: # # K Keyspace events, published with __keyspace@<db>__ prefix. # E Keyevent events, published with __keyevent@<db>__ prefix. # g Generic commands (non-type specific) like DEL, EXPIRE, RENAME, ... # $ String commands # l List commands # s Set commands # h Hash commands # z Sorted set commands # x Expired events (events generated every time a key expires) # e Evicted events (events generated when a key is evicted for maxmemory) # A Alias for g$lshzxe, so that the "AKE" string means all the events. # # The "notify-keyspace-events" takes as argument a string that is composed # of zero or multiple characters. The empty string means that notifications # are disabled. # # Example: to enable list and generic events, from the point of view of the # event name, use: # # notify-keyspace-events Elg # # Example 2: to get the stream of the expired keys subscribing to channel # name __keyevent@0__:expired use: # # notify-keyspace-events Ex # # By default all notifications are disabled because most users don't need # this feature and the feature has some overhead. Note that if you don't # specify at least one of K or E, no events will be delivered. notify-keyspace-events "" ############################### ADVANCED CONFIG ############################### # Hashes are encoded using a memory efficient data structure when they have a # small number of entries, and the biggest entry does not exceed a given # threshold. These thresholds can be configured using the following directives. hash-max-ziplist-entries 512 hash-max-ziplist-value 64 # Lists are also encoded in a special way to save a lot of space. # The number of entries allowed per internal list node can be specified # as a fixed maximum size or a maximum number of elements. # For a fixed maximum size, use -5 through -1, meaning: # -5: max size: 64 Kb <-- not recommended for normal workloads # -4: max size: 32 Kb <-- not recommended # -3: max size: 16 Kb <-- probably not recommended # -2: max size: 8 Kb <-- good # -1: max size: 4 Kb <-- good # Positive numbers mean store up to _exactly_ that number of elements # per list node. # The highest performing option is usually -2 (8 Kb size) or -1 (4 Kb size), # but if your use case is unique, adjust the settings as necessary. list-max-ziplist-size -2 # Lists may also be compressed. # Compress depth is the number of quicklist ziplist nodes from *each* side of # the list to *exclude* from compression. The head and tail of the list # are always uncompressed for fast push/pop operations. Settings are: # 0: disable all list compression # 1: depth 1 means "don't start compressing until after 1 node into the list, # going from either the head or tail" # So: [head]->node->node->...->node->[tail] # [head], [tail] will always be uncompressed; inner nodes will compress. # 2: [head]->[next]->node->node->...->node->[prev]->[tail] # 2 here means: don't compress head or head->next or tail->prev or tail, # but compress all nodes between them. # 3: [head]->[next]->[next]->node->node->...->node->[prev]->[prev]->[tail] # etc. list-compress-depth 0 # Sets have a special encoding in just one case: when a set is composed # of just strings that happen to be integers in radix 10 in the range # of 64 bit signed integers. # The following configuration setting sets the limit in the size of the # set in order to use this special memory saving encoding. set-max-intset-entries 512 # Similarly to hashes and lists, sorted sets are also specially encoded in # order to save a lot of space. This encoding is only used when the length and # elements of a sorted set are below the following limits: zset-max-ziplist-entries 128 zset-max-ziplist-value 64 # HyperLogLog sparse representation bytes limit. The limit includes the # 16 bytes header. When an HyperLogLog using the sparse representation crosses # this limit, it is converted into the dense representation. # # A value greater than 16000 is totally useless, since at that point the # dense representation is more memory efficient. # # The suggested value is ~ 3000 in order to have the benefits of # the space efficient encoding without slowing down too much PFADD, # which is O(N) with the sparse encoding. The value can be raised to # ~ 10000 when CPU is not a concern, but space is, and the data set is # composed of many HyperLogLogs with cardinality in the 0 - 15000 range. hll-sparse-max-bytes 3000 # Streams macro node max size / items. The stream data structure is a radix # tree of big nodes that encode multiple items inside. Using this configuration # it is possible to configure how big a single node can be in bytes, and the # maximum number of items it may contain before switching to a new node when # appending new stream entries. If any of the following settings are set to # zero, the limit is ignored, so for instance it is possible to set just a # max entires limit by setting max-bytes to 0 and max-entries to the desired # value. stream-node-max-bytes 4096 stream-node-max-entries 100 # Active rehashing uses 1 millisecond every 100 milliseconds of CPU time in # order to help rehashing the main Redis hash table (the one mapping top-level # keys to values). The hash table implementation Redis uses (see dict.c) # performs a lazy rehashing: the more operation you run into a hash table # that is rehashing, the more rehashing "steps" are performed, so if the # server is idle the rehashing is never complete and some more memory is used # by the hash table. # # The default is to use this millisecond 10 times every second in order to # actively rehash the main dictionaries, freeing memory when possible. # # If unsure: # use "activerehashing no" if you have hard latency requirements and it is # not a good thing in your environment that Redis can reply from time to time # to queries with 2 milliseconds delay. # # use "activerehashing yes" if you don't have such hard requirements but # want to free memory asap when possible. activerehashing yes # The client output buffer limits can be used to force disconnection of clients # that are not reading data from the server fast enough for some reason (a # common reason is that a Pub/Sub client can't consume messages as fast as the # publisher can produce them). # # The limit can be set differently for the three different classes of clients: # # normal -> normal clients including MONITOR clients # replica -> replica clients # pubsub -> clients subscribed to at least one pubsub channel or pattern # # The syntax of every client-output-buffer-limit directive is the following: # # client-output-buffer-limit <class> <hard limit> <soft limit> <soft seconds> # # A client is immediately disconnected once the hard limit is reached, or if # the soft limit is reached and remains reached for the specified number of # seconds (continuously). # So for instance if the hard limit is 32 megabytes and the soft limit is # 16 megabytes / 10 seconds, the client will get disconnected immediately # if the size of the output buffers reach 32 megabytes, but will also get # disconnected if the client reaches 16 megabytes and continuously overcomes # the limit for 10 seconds. # # By default normal clients are not limited because they don't receive data # without asking (in a push way), but just after a request, so only # asynchronous clients may create a scenario where data is requested faster # than it can read. # # Instead there is a default limit for pubsub and replica clients, since # subscribers and replicas receive data in a push fashion. # # Both the hard or the soft limit can be disabled by setting them to zero. client-output-buffer-limit normal 0 0 0 client-output-buffer-limit replica 256mb 64mb 60 client-output-buffer-limit pubsub 32mb 8mb 60 # Client query buffers accumulate new commands. They are limited to a fixed # amount by default in order to avoid that a protocol desynchronization (for # instance due to a bug in the client) will lead to unbound memory usage in # the query buffer. However you can configure it here if you have very special # needs, such us huge multi/exec requests or alike. # # client-query-buffer-limit 1gb # In the Redis protocol, bulk requests, that are, elements representing single # strings, are normally limited ot 512 mb. However you can change this limit # here. # # proto-max-bulk-len 512mb # Redis calls an internal function to perform many background tasks, like # closing connections of clients in timeout, purging expired keys that are # never requested, and so forth. # # Not all tasks are performed with the same frequency, but Redis checks for # tasks to perform according to the specified "hz" value. # # By default "hz" is set to 10. Raising the value will use more CPU when # Redis is idle, but at the same time will make Redis more responsive when # there are many keys expiring at the same time, and timeouts may be # handled with more precision. # # The range is between 1 and 500, however a value over 100 is usually not # a good idea. Most users should use the default of 10 and raise this up to # 100 only in environments where very low latency is required. hz 10 # Normally it is useful to have an HZ value which is proportional to the # number of clients connected. This is useful in order, for instance, to # avoid too many clients are processed for each background task invocation # in order to avoid latency spikes. # # Since the default HZ value by default is conservatively set to 10, Redis # offers, and enables by default, the ability to use an adaptive HZ value # which will temporary raise when there are many connected clients. # # When dynamic HZ is enabled, the actual configured HZ will be used as # as a baseline, but multiples of the configured HZ value will be actually # used as needed once more clients are connected. In this way an idle # instance will use very little CPU time while a busy instance will be # more responsive. dynamic-hz yes # When a child rewrites the AOF file, if the following option is enabled # the file will be fsync-ed every 32 MB of data generated. This is useful # in order to commit the file to the disk more incrementally and avoid # big latency spikes. aof-rewrite-incremental-fsync yes # When redis saves RDB file, if the following option is enabled # the file will be fsync-ed every 32 MB of data generated. This is useful # in order to commit the file to the disk more incrementally and avoid # big latency spikes. rdb-save-incremental-fsync yes # Redis LFU eviction (see maxmemory setting) can be tuned. However it is a good # idea to start with the default settings and only change them after investigating # how to improve the performances and how the keys LFU change over time, which # is possible to inspect via the OBJECT FREQ command. # # There are two tunable parameters in the Redis LFU implementation: the # counter logarithm factor and the counter decay time. It is important to # understand what the two parameters mean before changing them. # # The LFU counter is just 8 bits per key, it's maximum value is 255, so Redis # uses a probabilistic increment with logarithmic behavior. Given the value # of the old counter, when a key is accessed, the counter is incremented in # this way: # # 1. A random number R between 0 and 1 is extracted. # 2. A probability P is calculated as 1/(old_value*lfu_log_factor+1). # 3. The counter is incremented only if R < P. # # The default lfu-log-factor is 10. This is a table of how the frequency # counter changes with a different number of accesses with different # logarithmic factors: # # +--------+------------+------------+------------+------------+------------+ # | factor | 100 hits | 1000 hits | 100K hits | 1M hits | 10M hits | # +--------+------------+------------+------------+------------+------------+ # | 0 | 104 | 255 | 255 | 255 | 255 | # +--------+------------+------------+------------+------------+------------+ # | 1 | 18 | 49 | 255 | 255 | 255 | # +--------+------------+------------+------------+------------+------------+ # | 10 | 10 | 18 | 142 | 255 | 255 | # +--------+------------+------------+------------+------------+------------+ # | 100 | 8 | 11 | 49 | 143 | 255 | # +--------+------------+------------+------------+------------+------------+ # # NOTE: The above table was obtained by running the following commands: # # redis-benchmark -n 1000000 incr foo # redis-cli object freq foo # # NOTE 2: The counter initial value is 5 in order to give new objects a chance # to accumulate hits. # # The counter decay time is the time, in minutes, that must elapse in order # for the key counter to be divided by two (or decremented if it has a value # less <= 10). # # The default value for the lfu-decay-time is 1. A Special value of 0 means to # decay the counter every time it happens to be scanned. # # lfu-log-factor 10 # lfu-decay-time 1 ########################### ACTIVE DEFRAGMENTATION ####################### # # WARNING THIS FEATURE IS EXPERIMENTAL. However it was stress tested # even in production and manually tested by multiple engineers for some # time. # # What is active defragmentation? # ------------------------------- # # Active (online) defragmentation allows a Redis server to compact the # spaces left between small allocations and deallocations of data in memory, # thus allowing to reclaim back memory. # # Fragmentation is a natural process that happens with every allocator (but # less so with Jemalloc, fortunately) and certain workloads. Normally a server # restart is needed in order to lower the fragmentation, or at least to flush # away all the data and create it again. However thanks to this feature # implemented by Oran Agra for Redis 4.0 this process can happen at runtime # in an "hot" way, while the server is running. # # Basically when the fragmentation is over a certain level (see the # configuration options below) Redis will start to create new copies of the # values in contiguous memory regions by exploiting certain specific Jemalloc # features (in order to understand if an allocation is causing fragmentation # and to allocate it in a better place), and at the same time, will release the # old copies of the data. This process, repeated incrementally for all the keys # will cause the fragmentation to drop back to normal values. # # Important things to understand: # # 1. This feature is disabled by default, and only works if you compiled Redis # to use the copy of Jemalloc we ship with the source code of Redis. # This is the default with Linux builds. # # 2. You never need to enable this feature if you don't have fragmentation # issues. # # 3. Once you experience fragmentation, you can enable this feature when # needed with the command "CONFIG SET activedefrag yes". # # The configuration parameters are able to fine tune the behavior of the # defragmentation process. If you are not sure about what they mean it is # a good idea to leave the defaults untouched. # Enabled active defragmentation # activedefrag yes # Minimum amount of fragmentation waste to start active defrag # active-defrag-ignore-bytes 100mb # Minimum percentage of fragmentation to start active defrag # active-defrag-threshold-lower 10 # Maximum percentage of fragmentation at which we use maximum effort # active-defrag-threshold-upper 100 # Minimal effort for defrag in CPU percentage # active-defrag-cycle-min 5 # Maximal effort for defrag in CPU percentage # active-defrag-cycle-max 75 # Maximum number of set/hash/zset/list fields that will be processed from # the main dictionary scan # active-defrag-max-scan-fields 1000
0 notes
Text
November 04, 2019 at 10:03PM - BurnAware Premium (100% discount) Ashraf
BurnAware Premium (100% discount) Hurry Offer Only Last For HoursSometime. Don't ever forget to share this post on Your Social media to be the first to tell your firends. This is not a fake stuff its real.
BurnAware is a full-fledged, easy-to-use burning software which allows users to write all types of files such as digital photos, pictures, archives, documents, music and videos to CDs, DVDs and Blu-ray Discs. With BurnAware, you also be able to create bootable or multisession discs, high-quality Audio CDs and Video DVDs, make and burn ISO images, copy and backup discs, extract audio tracks, erase and verify data, recover data from multisession or unreadable discs.
Key Benefits
One of the most noticeable feature is an user interface – clean, effective, easy-to-use and multilingual. Another great benefits are low CPU usage while burning and very stable burning process. Plus support of latest OS – Windows 8.1, as well as any version starting from Windows XP, both 32 and 64 bits.
Advanced Options
Besides standard options, BurnAware offers many advanced options such as BOOT settings, UDF partition and versions, ISO levels and restrictions, session selection, CD-Text for track and disc, byte by byte verification, direct copying and many more.
Main Features
Creates and burns standard / bootable Data CDs, DVDs, Blu-ray
Creates and burns Audio CDs, MP3 Discs and DVD-Videos
Creates standard / bootable ISO Images, burns various Disc Images
Copies standard / multimedia CDs, DVDs, Blu-ray to Disc Images
Erases rewritable Discs, verifies Discs, displays Disc / Drive details
Copies from Disc to Disc, direct CD, DVD, Blu-ray copying
Extracts audio tracks in wav format from Audio CDs
Recovers files from unreadable Discs and separate sessions
from Active Sales – SharewareOnSale https://ift.tt/2hWWtVs https:https://ift.tt/2NMGshI via Blogger https://ift.tt/2WG4DCq #blogger #bloggingtips #bloggerlife #bloggersgetsocial #ontheblog #writersofinstagram #writingprompt #instapoetry #writerscommunity #writersofig #writersblock #writerlife #writtenword #instawriters #spilledink #wordgasm #creativewriting #poetsofinstagram #blackoutpoetry #poetsofig
0 notes
Text
DBA Interview Questions with Answer Part14
Why drop table is not going into Recycle bin? If you are using SYS user to drop any table then user’s object will not go to the recyclebin as there is no recyclebin for SYSTEM tablespace, even we have already SET recycle bin parameter TRUE.Select * from v$parameter where name = 'recyclebin';Show parameter recyclebin; How to recover password in oracle 10g?You can query with the table user_history$. The password history is store in this table.How to detect inactive session to kill automatically?You can use the SQLNET.EXPIRE_TIME for the dead connections (for abnormal disconnections) by specifying a time interval in minute to send a problem message that verify client/server connections are active. Setting the value greater than 0 to this parameter ensures that connection is not left open indefinitely, due to abnormal client termination. If probe finds a terminated connection, or connection that is no longer in use, it returns an error, causing the server process to exit. SQLNET.EXPIRE_TIME=10Why we need CASCADE option with DROP USER command whenever dropping a user and why "DROP USER" commands fails when we don't use it?If a user having any object then ‘YES’ in that case you are not able to drop that user without using CASCADE option. The DROP USER with CASCADE option command drops user along with its all associated objects. Remember it is a DDL command after the execution of this command rollback cannot be performed.Can you suggest the best steps to refresh a Database?Refreshing the database is nothing but applying the change on one database (PROD) to another (Test). You can use import/export and RMAN method for this purpose.Import/Export Method:If you database is small and if you need to refresh particular schema only then it is always better to use this method.Export the dump file from source DBDrop and recreate Test environment User.Import the dump to destination DB.RMAN Method: Now days RMAN is most likely to be used for backup and recovery. It is relatively easier and better method for full database refresh to be refreshed. It is taking less time as compare to import/export method. Here also you can use particular SCN based refreshing.#!/usr/bin/kshexport ORAENV_ASK='NO'export ORACLE_SID=PRD/usr/local/bin/oraenvexport NLS_LANG=American_america.us7ascii;export NLS_DATE_FORMAT="Mon DD YYYY HH24:MI:SS";$ORACLE_HOME/bin/rman target / nocatalog log=/tmp/duplicate_tape_TEST.log connect auxiliary sys/PASSWORD@TEST;run{allocate auxiliary channel aux1 device type disk;set until SCN 42612597059;duplicate target database to "TEST" pfile='/u01/app/xxxx/product/10.2.0/db_1/dbs/initTEST.ora' NOFILENAMECHECK;}EOFHow will we know the IP address of our system in Linux environment?Either use ipconfig command or ip addr showIt will give you all IP address and if you have oracle 9i you can query from SQL prompt.SELECT UTL_INADDR.GET_HOST_ADDRESS "Host Address", UTL_INADDR.GET_HOST_NAME "Host Name" FROM DUAL;Can we create Bigfile Tablespace for all databases?Infact your question do we create bigfile tablespace for every database is not clear for me. If you are asking can we create bigfile for every database?Yes you can but it is not ideal for every datafile if your work is suitable for small file then why you create bigfile but if your mean is impact of bigfile that depends on your requirements and storage.A bigfile tablespace is having single very big datafile which can store 4GB to 128 TB.Creating single large datafile reducing the requirement of SGA and also it will allow you modification at tablespace level. In fact it is ideal for ASM, logical device supporting stripping. Avoid using bigfile tablespace where there is limited space availability. For more details impact, advantage, disadvantage of bigfile on my blog.Can you gice more explanation on logfile states?“CURRENT” state means that redo records are currently being written to that group. It will be until a log switch occurs. At a time there can be only one redo group current.If a redo group containing redo’s of a dirty buffer that redo group is said to be ‘ACTIVE’ state. As we know log file keep changes made to the data blocks then data blocks are modified in buffer cache (dirty blocks). These dirty blocks must be written to the disk (RAM to permanent media).And when a redolog group contains no redo records belonging to a dirty buffer it is in an "INACTIVE" state. These inactive redolog can be overwritten.One more state ‘UNUSED’ initially when you create new redo log group its log file is empty on that time it is unused. Later it can be any of the above mentioned state.What is difference between oracle SID and Oracle service name?Oracle SID is the unique name that uniquely identifies your instance/database where as the service name is the TNS alias can be same or different as SID. How to find session for Remote users?-- To return session id on remote session:SELECT distinct sid FROM v$mystat;-- Return session id of you in remote Environment:Select sid from v$mystat@remot_db where rownum=1;We have a complete cold Backup taken on Sunday. The database crashed on Wednesday. None of the database files are available. The only files we have are the taped backup archive files till Wednesday. Is there a possibility of recovering the database until the recent archive which we have in the tape using the cold backup.Yes, if you have all the archive logs since the cold backup then you can recover to your last logSteps:1) Restore all backup datafiles, and controlfile. Also restore the password file and init.ora if you lost those too. Don't restore your redo logs if you backed them up. 2) Make sure that ORACLE_SID is set to the database you want to recover 3) startup mount;4) Recover database using backup controlfile; At this point Oracle should start applying all your archive logs, assuming that they're in log_archive_dest5) alter database open resetlogs;How to check RMAN version in oracle?If you want to check RMAN catalog version then use the below query from SQL*plusSQL> Select * from rcver;If you want to check simply database version.SQL> Select * from v$version;What is the minimum size of Temporary Tablespace?1041 KBDifference b/w image copies and backup sets?An image copy is identical, byte by byte, to the original datafile, control file, or archived redo log file. RMAN can write blocks from many files into the same backup set but can’t do so in the case of an image copy.An RMAN image copy and a copy you make with an operating system copy command such as dd (which makes image copies) are identical. Since RMAN image copies are identical to copies made with operating system copy commands, you may use user-made image copies for an RMAN restore and recovery operation after first making the copies “known” to RMAN by using the catalog command.You can make image copies only on disk but not on a tape device. "backup as copy database;" Therefore, you can use the backup as copy option only for disk backups, and the backup as backupset option is the only option you have for making tape backups.How can we see the C: drive free space capacity from SQL?create an external table to read data from a file that will be as below create BAT file free.bat as @setlocal enableextensions enable delayedexpansion @echo off for /f "tokens=3" %%a in ('dir c:') do ( set bytesfree=%%a ) set bytesfree=%bytesfree:,=% echo %bytesfree% endlocal && set bytesfree=%bytesfree% You can create a schedular to run the above free.bat, free_space.txt inside the oracle directory.Differentiate between Tuning Advisor and Access Advisor?The tuning Advisor:– It suggests indexes that might be very useful.– It suggests query rewrites.– It suggests SQL profileThe Access Advisor:– It suggest indexes that may be useful– Suggestion about materialized view.– Suggestion about table partitions also in latest version of oracle.How to give Access of particular table for particular user?GRANT SELECT (EMPLOYEE_NUMBER), UPDATE (AMOUNT) ON HRMS.PAY_PAYMENT_MASTER TO SHAHID;The Below command checks the SELECT privilege on the table PAY_PAYMENT_MASTER on the HRMS schema (if connected user is different than the schema)SELECT PRIVILEGEFROM ALL_TAB_PRIVS_RECDWHERE PRIVILEGE = 'SELECT'AND TABLE_NAME = 'PAY_PAYMENT_MASTER'AND OWNER = 'HRMS'UNION ALLSELECT PRIVILEGEFROM SESSION_PRIVSWHERE PRIVILEGE = 'SELECT ANY TABLE';What are the problem and complexities if we use SQL Tuning Advisor and Access Advisor together?I think both the tools are useful for resolving SQL tuning issues. SQL Tuning Advisor seems to be doing logical optimization mainly by checking your SQL structure and statistics and the SQL Access Advisor does suggest good data access paths, that is mainly work which can be done better on disk.Both SQL Tuning Advisor and SQL Access Advisor tools are quite powerful as they can source the SQL they will tune automatically from multiple different sources, including SQL cache, AWR, SQL tuning Sets and user defined workloads. Related with the argument complexity and problem of using these tools or how you can use these tools together better to check oracle documentation.
0 notes
Text
DBA Interview Questions with Answer Part14
Why drop table is not going into Recycle bin? If you are using SYS user to drop any table then user’s object will not go to the recyclebin as there is no recyclebin for SYSTEM tablespace, even we have already SET recycle bin parameter TRUE.Select * from v$parameter where name = 'recyclebin';Show parameter recyclebin; How to recover password in oracle 10g?You can query with the table user_history$. The password history is store in this table.How to detect inactive session to kill automatically?You can use the SQLNET.EXPIRE_TIME for the dead connections (for abnormal disconnections) by specifying a time interval in minute to send a problem message that verify client/server connections are active. Setting the value greater than 0 to this parameter ensures that connection is not left open indefinitely, due to abnormal client termination. If probe finds a terminated connection, or connection that is no longer in use, it returns an error, causing the server process to exit. SQLNET.EXPIRE_TIME=10Why we need CASCADE option with DROP USER command whenever dropping a user and why "DROP USER" commands fails when we don't use it?If a user having any object then ‘YES’ in that case you are not able to drop that user without using CASCADE option. The DROP USER with CASCADE option command drops user along with its all associated objects. Remember it is a DDL command after the execution of this command rollback cannot be performed.Can you suggest the best steps to refresh a Database?Refreshing the database is nothing but applying the change on one database (PROD) to another (Test). You can use import/export and RMAN method for this purpose.Import/Export Method:If you database is small and if you need to refresh particular schema only then it is always better to use this method.Export the dump file from source DBDrop and recreate Test environment User.Import the dump to destination DB.RMAN Method: Now days RMAN is most likely to be used for backup and recovery. It is relatively easier and better method for full database refresh to be refreshed. It is taking less time as compare to import/export method. Here also you can use particular SCN based refreshing.#!/usr/bin/kshexport ORAENV_ASK='NO'export ORACLE_SID=PRD/usr/local/bin/oraenvexport NLS_LANG=American_america.us7ascii;export NLS_DATE_FORMAT="Mon DD YYYY HH24:MI:SS";$ORACLE_HOME/bin/rman target / nocatalog log=/tmp/duplicate_tape_TEST.log connect auxiliary sys/PASSWORD@TEST;run{allocate auxiliary channel aux1 device type disk;set until SCN 42612597059;duplicate target database to "TEST" pfile='/u01/app/xxxx/product/10.2.0/db_1/dbs/initTEST.ora' NOFILENAMECHECK;}EOFHow will we know the IP address of our system in Linux environment?Either use ipconfig command or ip addr showIt will give you all IP address and if you have oracle 9i you can query from SQL prompt.SELECT UTL_INADDR.GET_HOST_ADDRESS "Host Address", UTL_INADDR.GET_HOST_NAME "Host Name" FROM DUAL;Can we create Bigfile Tablespace for all databases?Infact your question do we create bigfile tablespace for every database is not clear for me. If you are asking can we create bigfile for every database?Yes you can but it is not ideal for every datafile if your work is suitable for small file then why you create bigfile but if your mean is impact of bigfile that depends on your requirements and storage.A bigfile tablespace is having single very big datafile which can store 4GB to 128 TB.Creating single large datafile reducing the requirement of SGA and also it will allow you modification at tablespace level. In fact it is ideal for ASM, logical device supporting stripping. Avoid using bigfile tablespace where there is limited space availability. For more details impact, advantage, disadvantage of bigfile on my blog.Can you gice more explanation on logfile states?“CURRENT” state means that redo records are currently being written to that group. It will be until a log switch occurs. At a time there can be only one redo group current.If a redo group containing redo’s of a dirty buffer that redo group is said to be ‘ACTIVE’ state. As we know log file keep changes made to the data blocks then data blocks are modified in buffer cache (dirty blocks). These dirty blocks must be written to the disk (RAM to permanent media).And when a redolog group contains no redo records belonging to a dirty buffer it is in an "INACTIVE" state. These inactive redolog can be overwritten.One more state ‘UNUSED’ initially when you create new redo log group its log file is empty on that time it is unused. Later it can be any of the above mentioned state.What is difference between oracle SID and Oracle service name?Oracle SID is the unique name that uniquely identifies your instance/database where as the service name is the TNS alias can be same or different as SID. How to find session for Remote users?-- To return session id on remote session:SELECT distinct sid FROM v$mystat;-- Return session id of you in remote Environment:Select sid from v$mystat@remot_db where rownum=1;We have a complete cold Backup taken on Sunday. The database crashed on Wednesday. None of the database files are available. The only files we have are the taped backup archive files till Wednesday. Is there a possibility of recovering the database until the recent archive which we have in the tape using the cold backup.Yes, if you have all the archive logs since the cold backup then you can recover to your last logSteps:1) Restore all backup datafiles, and controlfile. Also restore the password file and init.ora if you lost those too. Don't restore your redo logs if you backed them up. 2) Make sure that ORACLE_SID is set to the database you want to recover 3) startup mount;4) Recover database using backup controlfile; At this point Oracle should start applying all your archive logs, assuming that they're in log_archive_dest5) alter database open resetlogs;How to check RMAN version in oracle?If you want to check RMAN catalog version then use the below query from SQL*plusSQL> Select * from rcver;If you want to check simply database version.SQL> Select * from v$version;What is the minimum size of Temporary Tablespace?1041 KBDifference b/w image copies and backup sets?An image copy is identical, byte by byte, to the original datafile, control file, or archived redo log file. RMAN can write blocks from many files into the same backup set but can’t do so in the case of an image copy.An RMAN image copy and a copy you make with an operating system copy command such as dd (which makes image copies) are identical. Since RMAN image copies are identical to copies made with operating system copy commands, you may use user-made image copies for an RMAN restore and recovery operation after first making the copies “known” to RMAN by using the catalog command.You can make image copies only on disk but not on a tape device. "backup as copy database;" Therefore, you can use the backup as copy option only for disk backups, and the backup as backupset option is the only option you have for making tape backups.How can we see the C: drive free space capacity from SQL?create an external table to read data from a file that will be as below create BAT file free.bat as @setlocal enableextensions enable delayedexpansion @echo off for /f "tokens=3" %%a in ('dir c:') do ( set bytesfree=%%a ) set bytesfree=%bytesfree:,=% echo %bytesfree% endlocal && set bytesfree=%bytesfree% You can create a schedular to run the above free.bat, free_space.txt inside the oracle directory.Differentiate between Tuning Advisor and Access Advisor?The tuning Advisor:– It suggests indexes that might be very useful.– It suggests query rewrites.– It suggests SQL profileThe Access Advisor:– It suggest indexes that may be useful– Suggestion about materialized view.– Suggestion about table partitions also in latest version of oracle.How to give Access of particular table for particular user?GRANT SELECT (EMPLOYEE_NUMBER), UPDATE (AMOUNT) ON HRMS.PAY_PAYMENT_MASTER TO SHAHID;The Below command checks the SELECT privilege on the table PAY_PAYMENT_MASTER on the HRMS schema (if connected user is different than the schema)SELECT PRIVILEGEFROM ALL_TAB_PRIVS_RECDWHERE PRIVILEGE = 'SELECT'AND TABLE_NAME = 'PAY_PAYMENT_MASTER'AND OWNER = 'HRMS'UNION ALLSELECT PRIVILEGEFROM SESSION_PRIVSWHERE PRIVILEGE = 'SELECT ANY TABLE';What are the problem and complexities if we use SQL Tuning Advisor and Access Advisor together?I think both the tools are useful for resolving SQL tuning issues. SQL Tuning Advisor seems to be doing logical optimization mainly by checking your SQL structure and statistics and the SQL Access Advisor does suggest good data access paths, that is mainly work which can be done better on disk.Both SQL Tuning Advisor and SQL Access Advisor tools are quite powerful as they can source the SQL they will tune automatically from multiple different sources, including SQL cache, AWR, SQL tuning Sets and user defined workloads. Related with the argument complexity and problem of using these tools or how you can use these tools together better to check oracle documentation.
0 notes
Text
The impressive MP3 blog
When undertaking lossy audio encoding, including creating an MP3 info stream, there is a trade-off among the level of info produced and the seem high quality of the final results. The individual making an MP3 selects a bit rate, which specifies the quantity of kilobits for every second of audio is wanted. The upper the bit price, the greater the MP3 facts stream will probably be, and, generally, the closer it will eventually audio to the initial recording. With too small a bit amount, compression artifacts (i.e., Appears that were not current in the initial recording) may be audible in the copy. http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292 http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292http://manuellbpft.blogkoo.com/the-best-side-of-mp3-9059292 [93] There are also open compression formats like Opus and Vorbis that are available totally free and with none identified patent constraints. A lot of the more recent audio compression formats, for instance AAC, WMA Pro and Vorbis, are free of some limits inherent towards the MP3 structure that can not be prevail over by any MP3 encoder.[seventy one] Just enter the movie title in the second type and press "research". convert2mp3.net on Facebook: suggest convert2mp3.Internet: Tweet Participating in & editing software usually is made up of tag editing performance, but In addition there are tag editor applications committed to the intent. Aside from metadata pertaining to your audio articles, tags can also be used for DRM.[sixty eight] ReplayGain is a standard for measuring and storing the loudness of the MP3 file (audio normalization) in its metadata tag, enabling a ReplayGain-compliant participant to immediately alter the general playback volume for every file. Although Considerably of MUSICAM engineering and concepts were integrated into the definition of MPEG Audio Layer I and Layer II, the filter financial institution alone and the data structure based upon 1152 samples framing (file format and byte oriented stream) of MUSICAM remained from the Layer III (MP3) format, as A part of the computationally inefficient hybrid filter lender. This part is created like a private reflection or opinion essay that states a Wikipedia editor's individual emotions about a matter. Be sure to help strengthen it by rewriting it within an encyclopedic model. (January 2014) (Learn how and when to get rid of this template concept) What's Trending Now More Trending Words socialism 'a technique for Arranging a Culture in which significant industries are owned and controlled by The federal government' uphold 'to let stand' due procedure 'a study course of formal proceedings (as judicial proceedings)' asylum 'safety from arrest and extradition given Specially to political refugees' insubordinate 'disobedient to authority' SEE ALL Examples: MP3 Continue to focusing on Win10 with all program up to date. Evaluations give good instruction - if in hassle Continue reading. Sorry, we just need to be sure you're not a robot. For finest outcomes, be sure to be sure your browser is accepting cookies. That is followed by a tiny bit indicating that Here is the MPEG conventional and two bits that indicate that layer three is utilized; as a result MPEG-one Audio Layer 3 or MP3. Soon after this, the values will differ, based on the MP3 file. ISO/IEC 11172-three defines the range of values for every section with the header together with the specification with the header. Most MP3 data files currently have ID3 metadata, which precedes or follows the MP3 frames, as noted within the diagram. The data stream can have an optional checksum. Compression performance of encoders is typically defined by the bit level, due to the fact compression ratio depends upon the bit depth and sampling level of the input sign. Nevertheless, compression ratios are frequently posted. They might utilize the Compact Disc (CD) parameters as references (44. MP3 compression functions by reducing (or approximating) the accuracy of specified parts of sound which are regarded as being further than the hearing abilities of most human beings. This technique is commonly known as perceptual coding, or psychoacoustic modeling. Vivendi experienced challenges growing the provider and sooner or later dismantled the first internet site, promoting off all of its property including the URL and symbol to CNET in 2003. You can make mp3 files by using the mp3 audio codec. .mp3 data files would not have a container, so you must utilize the dummy container. It's also advisable to specify the --no-video clip choice if you are taking audio from a video. The letter claimed that unlicensed products and solutions "infringe the patent legal rights of Fraunhofer and Thomson. To generate, market or distribute solutions using the [MPEG Layer-three] common and therefore our patents, you should attain a license less than these patents from us."[eighty one] This resulted in the specific situation exactly where the LAME MP3 encoder project could not present its end users official binaries that would operate on their own Laptop. The challenge's position was that as supply code, LAME was only an outline of how an MP3 encoder can be carried out. Unofficially, compiled binaries had been offered from other resources.
0 notes