#backup texts from iphone
Explore tagged Tumblr posts
Text
NO WAY IM BEING CONDESCENDED TO OVER APPLE SUPPORT TEXT BY A MAN NAMED FUCKING RAMOY.
“This is why a backup of your device is important.”
“So out of nowhere all the notes have disappeared?”
“Okay, I'm confused you're contradicting what you were saying.”
tell me ts is not condescending asf. like bruh. don’t tell me abt the importance of backing up my iPhone when this is not a problem of mine. you cannot try and shame me for my lack of preparation on an incident that was unprecedented and entirely apples fault. not mine. sure i should’ve backed up my device but why is bro trying to pin that on me when it was the company he works for that fucked up causing me to encounter this issue to begin with. i did not contradict shit in my messages he’s just a fucking numbskull who doesn’t believe me. then he wants to ask me stupid fucking questions as if i haven’t been trying to find my notes FOR FUCKING HOURS. AS IF I HAVENT DAMN NEAR SOBBED OVER THIS SHIT. AS IF MY ENTIRE LIFE WASNT IN MY NOTES APP. AS IF I DIDNT ALR TRY THIS SHIT. i am torn to shreds over this and it has completely ruined all motivation i have to write or read anything. so ofc i would think to check recently deleted and no, no one else has had access to this device and yes i tried searching key words from the disappeared notes on all accounts. im not a fucking idiot but also i have no control over if my phone is backed up or not CUZ IM A FIFTEEN YEAR OLD FUCKING GIRL GOING MANIC IN HER BEDROOM DELETING EVERYTHING FROM MY PHONE FOR STORAGE WHILE I PRAY THEY REAPPEAR. I DID NOT PURCHASE THIS PHONE NOR DO I PAY FOR IT. this is apples problem. not mine.
and ramoy whoever u are. count your calendar cuz ur fucking days are numbered.
#harry potter#james potter#the marauders#moony wormtail padfoot and prongs#james & peter & remus & sirius#sirius black#jegulus#regulus black#remus lupin#black brothers
21 notes
·
View notes
Text
READ THIS PLEASE
🤍˚ʚ🧸ɞ˚☁️
I don’t have personal pages not listed on www.MayaMorena.com/links
I DO NOT HAVE ANY “BACKUP ACCOUNTS”
I am NOT searching for a husband/boyfriend/friends with benefits/wife/girlfriend, or any meetups, collabs of any kind from any accounts. I am NOT looking for someone to get me a green card or to move in with anyone.
I have not been telling people my real name, address, etc. I do not live and have never traveled outside of the USA. I do not plan to travel outside the US.
I would NEVER send you my DRIVER’S LICENSE! Or any government ID’s of any kind. Anyone sending you an ID with my photo on it sent you a FAKE & PHOTOSHOPPED ID!!! Anyone sending you a photo of me holding a fake ID used AI to generate that fake photo. These fake ID are often very badly photoshopped.
Here are some very common [BASIC] clues:
The letters don’t look right, match or look overwritten
Things are misspelled
The photos they use doesn’t follow government ID photo standards
The IDs are in states I have never visited or lived in ever
The IDs get my birthday and other basic details wrong
My family/parents/siblings are not dead or in the hospital in critical condition. I have no brothers. I am not a cosmetologist. I have a lot of tech for my job. Two gaming computers, webcams, cameras, lighting equipment, 2 TVs, an Iphone, 5 old cellphones, and high speed internet. If someone can’t text you, call you, video chat with you, or doesn’t have a cellphone and needs you to buy them one….IT’S NOT ME!!!!
I live alone and my parents pay my rent. I am not poor and struggling. I am not living in a third world country. I am not on any dating sites, I am not on any escort sites. I do not have a free or public snapchat account.
If you come across this, they are all imposters and scammers. If they tell you otherwise to the effect of: “No, you are the exception, I just created this page for you” it’s a lie.
9 notes
·
View notes
Text
What to Do If You Get Lost in the Wild
Even in the age of smartphones and GPS, stories of hikers getting lost in the wilderness still regularly appear in the news. How do people get lost even when carrying their devices, and what should you do if you ever find yourself in that situation? To answer those questions, I called up Creek Stewart, a wilderness survival expert and instructor and a longtime friend of AoM. Creek is the author of numerous books on wilderness survival and has been the host of several Weather Channel shows on the subject, including S.O.S.: How to Survive. Besides his over two decades of survival experience, Creek told me that hosting S.O.S. gave him a unique perspective on how people get lost in the wilderness and what separates those who survive and get rescued quickly from those who flounder. When he hosted the show, he interviewed dozens of folks who had gotten lost in the wild, often in popular national parks filled with other people. Below Creek shares his insights on how anyone can become disoriented when traversing the great outdoors and, more importantly, how to stay safe if it happens to you. Pre-Trip Preparation: How to Ensure Your Quick Rescue in the Event You Get Lost Creek says there are three things you can do before your trip that, should you manage to get lost during it, will dramatically increase your chances of a quick rescue and a safe return: 1. Tell people where you’re going and when to expect you back. Do this even if you’re going on a simple day hike near your home. 2. Ensure your phone is fully charged and bring a power bank. If you plan on using a digital app/map to guide your hike, you’ll of course want to make sure your phone is fully charged and has a backup power source as well. A phone is of no use if it doesn’t have power. People get lost, their phones die, and they can’t figure out where they are and how to get back on track. A dead phone not only contributes to getting lost, but prevents a quick rescue as well. Creek told me the one thing that all the people who had a slow rescue had in common was that they went out into the wild without a fully charged phone and without a way to power it back up. “The people who got found quickly typically had a fully charged phone, so when they got lost, they could make a call or at least put out a distress signal with GPS,” he told me. If you’re looking for a power bank for outdoor excursions, I like and use the S.A.B.A.N.I. Portable Charger 35000mAh Power Bank. You can charge your iPhone up to five times with this power bank. 3. Consider carrying a Personal Locator Beacon (PLB). Creek recommends buying a PLB or satellite communicator. While they’re pricey and require a subscription, they will allow you to send a distress signal and share your GPS location even when you don’t have cell service. Garmin makes two satellite communicators: * Garmin inReach Messenger Handheld Satellite Communicator. This device is also a Personal Locator Beacon, and it works with your smartphone, so you can text even when you don’t have cell service. * Garmin inReach Mini 2. It allows you to text and also has maps and weather forecasts. It’s more expensive than the original inReach due to those additional features. Doing those three things before you leave for your trip will ensure you get found within 24 hours of getting lost in the wild. In addition to doing those three things, Creek also recommends that you dress appropriately for the climate and bring some essential gear for any wilderness outing, even a short day hike. Pack the essentials we list here. Having those things on you in the event you get lost will help you stay safe and comfortable in the outdoors while you’re waiting to be found. The Psychology of Getting Lost If you stay on marked trails when you’re out in nature, your risk of getting lost is very low. Before you begin a hike, download an offline map on your phone in case you don’t have cell service. Again, make sure you have a power charger. And carry a paper map as a backup, too. According to… http://dlvr.it/TCRdLG
4 notes
·
View notes
Text
5 key Trends in INFORMATION and COMMUNICATION TECHNOLOGY (ICT)
In today's ever-changing technological landscape, staying current on the latest trends is critical for both individuals and businesses. These patterns influence how we communicate, connect, and complete tasks in both our personal and professional lives. The following are five key trends in ICT that are making waves now, along with examples to demonstrate their significance.

1. CONVERGENCE
Convergence in ICT refers to the combination of various technologies to generate forms of communication and information. This trend focuses on establishing a seamless user experience by combining multiple functionalities into a single device or platform. Convergence has been a driving force in the creation of smartphones, which combine a phone, camera, music player, and internet browser in one device.
Examples:
- Smartphones: Combine various functions like calling, browsing, and photography.

- Smart TVs: Integrate television with internet browsing and streaming services.

2. SOCIAL MEDIA
Social media has become an essential part of our daily lives, changing the way we communicate and share information. Platforms such as Facebook, Twitter, and Instagram enable users to interact, create, discuss, modify, and share user-generated content. These platforms allow users to interact with a global audience, making social media an effective tool for personal and professional communication.
Examples:
- Facebook: Connects people globally and allows for sharing of updates, photos, and events.
- Twitter: Known for its microblogging feature, where users post short, concise updates.

3. MOBILE TECHNOLOGIES
The proliferation of smartphones and tablets has changed the way we access information and complete jobs. These gadgets have evolved into mini-computers capable of running a variety of apps that were previously limited to desktops. Mobile technology has permitted internet access at any time and from any location, making it important in today's fast-paced society.
Examples:
- iOS: Used in Apple devices such as iPhones and iPads.
- Android: An open-source operating system developed by Google, used by many mobile manufacturers.

4. ASSISTIVE MEDIA
Assistive media refers to technologies and services that help people with visual and reading impairments. These technologies make sure that everyone, regardless of physical restrictions, has access to and benefits from digital material. Assistive media is more than just accessibility; it is also about inclusivity.
Examples:
- Screen readers: Convert text to speech, allowing visually impaired users to interact with digital content.
- Braille displays: Provide tactile output of text for users who are blind.

5. CLOUD COMPUTING
Cloud computing has transformed how we store, access, and manage data. Users can utilize remote servers hosted on the internet to store data and access apps from anywhere in the globe. This tendency has resulted in enhanced productivity, scalability, and collaboration, particularly in the corporate sphere.
Examples:
- Google Drive: Allows users to store files online and access them from any device.
- Dropbox: A cloud storage service that enables easy file sharing and backup.

These developments demonstrate ICT's dynamic nature and tremendous impact on our lives. These trends, whether they improve connectivity, enable accessibility, or revolutionize data management, are altering the future of technology in previously imagined ways. Staying educated and flexible to these trends will be critical to success in the digital age.
Passed by: JEVE ASHLEY C. SUAGA
2 notes
·
View notes
Text
This is a long story, so buckle in. I have a Google Pixel, I switched from iPhone because I just wanted a fresh start and got sick of Apple as a company. I hated being constantly inundated with notifications and hounded by consumerism. The Pixel has its cons (it is a Google product after all) but at one point, I tried changing the OS for increased privacy and security. In the end, I ended up having an issue with text messages and switched back but that's not the point.
Prior to flashing the OS, I wanted to transfer my photos and other files on my Pixel to my PC for backup. Once you flash the OS, it wipes the phone. So I plugged the Pixel into my PC with a USB cable. (Please note my PC runs Windows 11 at the time. I now am working with a dual boot system where I primarily boot into Linux. This story was the final straw for me with Microsoft/Windows.)
My Win 11 PC refused to recognize my Pixel. It would beep constantly, telling me there was an issue connecting it. Sometimes, when I first plugged it in, I would get a little text box asking me what I would like to do with the plugged in device. Every time I tried to select any of the options, it wouldn't work. I tried every. Single. USB cord. I own. I'm a fucking nerd, I own at least a dozen of these things and you're telling me that these cables that normally work fine SUDDENLY can't connect my phone? (Note, I did have to use a higher quality USB cable to flash the OS, but in general have not had any other problems with any of these cords before.) I finally got the popup text box to tell me something about needing to use some sort of app to connect my phone to Microsoft. PhoneLink or something like that. I was automatically really wary. I shouldn't need to use an app just to transfer files between one storage device to another just because it's a phone. These are both personal devices, it made no sense. The USB cable should work fine, always has.
Alas, I downloaded the app, I couldn't get anything else to work, which of course needed your Microsoft account log in. Of course, I needed to log in to Microsoft to transfer my own fucking files, on my own fucking phone, to my own fucking computer. It's asking for permission after permission after permission. I mainly wanted to transfer photos, so that's the only thing I gave it permission for. At the start. I tried multiple times to transfer photos and it wouldn't let me. I gradually gave it more and more permissions, hoping one of them was the one that would make it work. I turned nearly all permissions on and it still wouldn't work. I was frustrated, I was angry, I was confused. This was so much work, just to transfer photos. And then I saw one of the permissions I really really didn't want to allow. This permission allowed the Microsoft Windows phone link app access to EVERYTHING ON MY PHONE. AUTOMATICALLY UPLOADING TO THE MICROSOFT SERVER CONSTANTLY. Begrudgingly, I selected it. I painstakingly waited for the photos to upload, and ONE BY ONE HAD TO MANUALLY TRANSFER THEM TO MY HARD DRIVE.
I immediately deleted the app, cleared the cache, I did everything I could think of to scrub this shit even with knowing the phone would just be reset anyway. Microsoft not only made Win 11 a pain in the ass to do this on, they made an app to target you and your data, made it a pain in the ass to transfer files through the app so you're forced to keep the app so they can keep stealing your data to sell, and removed your autonomy over your own personal fucking property.
I am fucking tired of everything being wireless. I am sick of being forced to have to use a phone for everything. I am tired of everything being a fucking scheme to sell your data. I hate everything being shoved into one device. I hate that everything is constantly regressing 'upgrading' into oblivion. I hate what this has done to my brain. I hate that I have to fight to have a working brain.
I don't know I'm not done talking about it. It's insane that I can't just uninstall Edge or Copilot. That websites require my phone number to sign up. That people share their contacts to find their friends on social media.
I wouldn't use an adblocker if ads were just banners on the side funding a website I enjoy using and want to support. Ads pop up invasively and fill my whole screen, I misclick and get warped away to another page just for trying to read an article or get a recipe.
Every app shouldn't be like every other app. Instagram didn't need reels and a shop. TikTok doesn't need a store. Instagram doesn't need to be connected to Facebook. I don't want my apps to do everything, I want a hub for a specific thing, and I'll go to that place accordingly.
I love discord, but so much information gets lost to it. I don't want to join to view things. I want to lurk on forums. I want to be a user who can log in and join a conversation by replying to a thread, even if that conversation was two days ago. I know discord has threads, it's not the same. I don't want to have to verify my account with a phone number. I understand safety and digital concerns, but I'm concerned about information like that with leaks everywhere, even with password managers.
I shouldn't have to pay subscriptions to use services and get locked out of old versions. My old disk copy of photoshop should work. I should want to upgrade eventually because I like photoshop and supporting the business. Adobe is a whole other can of worms here.
Streaming is so splintered across everything. Shows release so fast. Things don't get physical releases. I can't stream a movie I own digitally to friends because the share-screen blocks it, even though I own two digital copies, even though I own a physical copy.
I have an iPod, and I had to install a third party OS to easily put my music on it without having to tangle with iTunes. Spotify bricked hardware I purchased because they were unwillingly to upkeep it. They don't pay their artists. iTunes isn't even iTunes anymore and Apple struggles to upkeep it.
My TV shows me ads on the home screen. My dad lost access to eBook he purchased because they were digital and got revoked by the company distributing them. Hitman 1-3 only runs online most of the time. Flash died and is staying alive because people love it and made efforts to keep it up.
I have to click "not now" and can't click "no". I don't just get emails, they want to text me to purchase things online too. My windows start search bar searches online, not just my computer. Everything is blindly called an app now. Everything wants me to upload to the cloud. These are good tools! But why am I forced to use them! Why am I not allowed to own or control them?
No more!!!!! I love my iPod with so much storage and FLAC files. I love having all my fics on my harddrive. I love having USBs and backups. I love running scripts to gut suck stuff out of my Windows computer I don't want that spies on me. I love having forums. I love sending letters. I love neocities and webpages and webrings. I will not be scanning QR codes. Please hand me a physical menu. If I didn't need a smartphone for work I'd get a "dumb" phone so fast. I want things to have buttons. I want to use a mouse. I want replaceable batteries. I want the right to repair. I grew up online and I won't forget how it was!
71K notes
·
View notes
Text
Today, as the smart phone has become the device of choice for all those on the move for accessing the Internet, data security has become an extremely sensitive issue the world over. Malware, viruses amongst other threatening software rule the dark side of the Internet with impunity. Extreme levels of care need to be taken, especially when the driving engine behind most smart phones is the Android OS. As Android comes in many flavors as of today, and since it has been adopted by the majority of handset manufacturers globally, this issue has required to be tackled on a priority basis and on a war footing. The scenario can be even worse, if your phone is stolen or is accessed by undesired people. This article examines best apps for Smart phone security, especially those which are running Android: iPhone owners may want to checkout our list of security apps for iOS devices. Lookout If you are on the lookout for a free mobile app that is capable of protecting your android device around the clock from a wide range of mobile threats then Lookout Mobile Security is the right answer for you. This app is the perfect device security system in the post PC era. Lookout can secure you from unsecure WiFi networks, fraudulent links, malicious apps, etc. Lookout Mobile Security can also backup contacts such as scheduling automatic backups, which can later be accessed online. It can also use this information to restore your device in case your phone crashes, or in the event of a data loss. You can also locate your phone on a Google map in case your phone is lost, even if the GPS is off. Most of the top features are available for free with this app. However, the premium version offers much more with features such as remote locking, privacy scans, safe browsing, phishing protection, and app reports. Anti Spy and Spyware Scanner This app is a good help to identify any spyware apps on your android device. This can help you find and remove any spyware or location trackers that you do not see in list of installed apps. Avast Free Mobile Security This is a free mobile security app from the popular antivirus developer Avast. The Avast Free Mobile Security App includes a wide spectrum of anti malware as well as anti-theft features. Also included is browsing protection. This prompts the user if s/he visits a malicious website. Users can also make good use of the privacy advisor, which helps you identify potentially dangerous installed apps. At the same time, an application manager lets you manage running apps. Avast Free Mobile Security also includes SMS and call filtering. This feature helps block incoming messages as well as calls including outgoing calls that are based on times and contacts selected by the user. While the app lacks any backup functionality, enhanced anti-theft features along with a firewall are provided for rooted devices. With Avast, it is also possible to automatically scan apps that you install. Avast can also do full scans of your installed apps on the phone and on the SD card. This can be done manually or you can even specify the days and times for automatic scans. ESET Mobile Security & Antivirus The ESET mobile security comes with an interface that is completely easy to use as it provides real-time scanning of apps to detect malware and devious apps that try to send texts or make premium rate calls. The ESET mobile security basic version is completely free and it also includes a set of anti-theft tools. With ESET Mobile Security and Antivirus, it is also possible to remotely locate as well as lock your Smartphone or tablet. This feature also prevents anyone from uninstalling apps, by providing password protection. However, the remote wipe or SIM guard capabilities are available only with the premium version, which you have to pay for. This version provides additional features such as anti-phishing protection, an app audit feature, device monitoring so that unnecessary use of data can be checked, as also advanced call blocking.
Avira Antivirus Security The Avira Antivirus Security for Android phones provides 100% detection rate along with no false positives. Hence, users can trust the free version of Avira to keep their android Smartphone or tablet safe. At the same time, it has a light footprint when it comes to performance. Also, it has a minimalist as well as sleek design, so that it fits snuggly with the Android platform. With Avira, it is possible to scan apps for potential trouble, and it scans new apps or updates automatically. Also provided are a set of anti-theft tools, so that you can find your device remotely, or perform other actions such as locking, wiping, or even triggering an alarm. Avira also provides an additional tool, which it claims is able to tell you whether your email account has been hacked, and what action you need to take if you have to. Also included are a variety of blacklisting options that can potentially take care of nuisance callers and spam. BullGuard Mobile Security BullGuard Mobile Security is a premier quality mobile security app that provides you with an online account so that you can remotely access your smart phone. You are also provided with a mobile security manager that works in tandem with your GPS, so in the case you lose your device, it can be easily locked remotely and can be wiped clean. The BullGuard Mobile Security also includes a parental control module. This allows you to keep your children protected without directly accessing the phone. The app also includes anti-virus and anti-spyware, firewall, spam-filter, backup and restore features for contacts, along with SIM card protection. This app is available for Android, Symbian OS, Windows mobile, and Blackberry phones. 360 Mobile Security With a detection rate of 100%, the focus of 360 Mobile Security (developed by Chinese Player Quiho) is a lightweight, streamlined and elegantly designed app that is completely free. With 360 Mobile Security, it is possible to safeguard your device from malware, spyware, and any threats of infection. At the same time, it is also capable of detecting as well as fixing system vulnerabilities. 360 Mobile Security cleans up idle background apps so that it can help your phone run more efficiently. The app also includes a privacy advisor so that you can clear your usage history. In favor of a light touch, the app does not include a long list of extras. So, you will only find additional features such as call blocking, short cut toggles, as well as safe browsing option. This app also excludes the anti-theft component or the backup option. Android Device Manager This is a must have app for all its useful features. With the ability to track your lost device, and even ring it at max volume if you cannot find it, you couldn’t’ find a better app elsewhere. You can even lock your device or wipe your device from the web interface. This is a good way you can keep all sensitive data out of the hands of others. The best part of the deal is that this device is free. Hotspot Shield VPN This is a VPN app for your android device and is one of the most reasonably priced as well as popular VPN apps for android. With HotSpot VPN, can detect unsecured Wi-Fi to automatically enable HTTPS protection as well as automatically unblock content whenever certain apps or sites are accessed. It encrypts traffic in and out of your device for ultimate privacy. The Wi-Fi connection is secured with banking level HTTPS encryption, as your Wi-Fi network can be vulnerable even if the device is secure. It prevents hackers from stealing your private information and mask your IP address to browse the web anonymously as well as privately. Snap Secure Snap secure can automatically back up your data to your online account on a secure basis. From here, you can easily access your data, restore it, or transfer it to a new device if necessary. Snap Secure comes along with anti-virus as well as anti-spyware protection. It can also scan your new applications for malware.
Calls from unknown or un-shown numbers and also unwanted SMS messages on Android devices can be easily blocked. Snap Secure also includes a much-wanted privacy manager, in order to help you understand how apps are using your personal information. Also included are an anti-theft and a location tracker, which can be utilized in the case of the theft of your mobile device. Another unique feature called the Personal Guardian helps the user to press a panic button to send out an email, SMS, or tweet along with your location, in case the user is in the midst of an emergency situation. This app is also available for iOS and BlackBerry devices. Both free as well as pro versions are available. You may also be interested in VPN server software for other devices. Cerberus Anti Theft This is a free anti-theft app that includes many features which you can use for finding your lost or stolen device. With a standard web interface that you can see your device’s location, you can lock the device; hide the app from the app drawer, so that people will not know it exists. You can even record audio from the microphone to know what is going on around it as well as get information about the service the phone is connected to while getting call logs as well. You can even remote control your phone through their website and even via text messages. At the same time, you can even obtain alerts via the SIM checker if someone uses the phone with an unauthorized SIM card. Shivani Ajmerani works for Fusion Informatics Ltd., a mobile applications development company that also offers Custom android application development services. She loves leveraging the immense potential of the Internet to achieve corporate goals. Jennifer Brown is working as a software developer into the IT Company Digital Infoware Pvt. Ltd. since the last 3 years. I enjoy writing articles as a hobby on topics related to software, mobile app development, tutorials etc.
0 notes
Text

The Hidden Downsides of the HEIC Format (and the 30-Second Fix)
What Is the HEIC Format?
Why Apple Moved from JPEG to HEIC
In 2017, Apple rolled out a major photo format change with iOS 11 - switching from JPEG to HEIC. While it might seem like a behind-the-scenes tweak, it changed the way images are stored, shared, and opened across devices.
HEIC stands for High Efficiency Image Coding, and it uses a newer compression method (based on HEVC, or H.265) that maintains image quality at a fraction of the file size.
Why HEIC Is Actually Brilliant
Better Compression, Same Quality
HEIC files are significantly smaller without sacrificing image quality. This means you can store thousands of high-res photos without eating up your iPhone's storage.
Saving Storage Space on iPhones
For people with 64GB or 128GB phones, this is a huge win. More pictures, fewer cloud backups, and less “storage full” anxiety.
But Here’s the Catch…
Why You Can’t Open HEIC Files Everywhere
Despite its advantages, HEIC has a major downside: it doesn’t play nice outside Apple’s ecosystem. If you try to open an HEIC file on many Windows PCs, Android devices, or older software, you’ll get an error - or nothing at all.
Compatibility Issues Across Platforms
HEIC is supported on iPhones, iPads, macOS, and some newer versions of Windows. But for everything else - older Windows PCs, email clients, online forms, blogging platforms - it’s a guessing game.
The “Why Can’t I Open This?” Moment
A Typical Scenario: Sending Vacation Pics
Imagine this: you take a beautiful sunset shot during vacation. You send it to your family via email. They try to open it on their PC - and nothing happens.
The Frustration of Unsupported Files
The file opens as a blank icon, with no preview. “What is .HEIC?” someone texts back. You Google solutions, download clunky converters, and spend 20 minutes solving a 2-second problem.
The 30-Second HEIC Fix (No Download Needed)
Use a Free Online HEIC Viewer
Here’s the good news: you don’t need to install anything. You don’t need to change iPhone settings. And you definitely don’t need to email yourself images twice.
Instead of hunting for clunky desktop software, just drag the file onto our free HEIC Viewer and it opens instantly in your browser.
How It Works in 3 Simple Steps
Drag and drop your HEIC file onto the page.
Instant preview loads right in your browser.
Download or share the JPEG version if needed.
No installations, no spam, no complications.
1 note
·
View note
Text
Essendon Thu 12 Jun
Logging in to all the apps I might need to use on my backup ipad, I realised that to get 2 factor authorisation in Europe to log into or reinstall apps, I would need to receive texts sent to my Australian number. Seemingly simple. If my Australian SIM stays in the phone I can receive SMS messages only by paying Boost Mobile $3 per day to turn on roaming, according to their expert via chat (human, I think, she passed the Turing test). I don’t need roaming for calls or data, I’ll have the Orange ESIM for those.
This article https://www.smh.com.au/traveller/reviews-and-advice/how-to-deal-with-two-factor-authentication-when-you-re-overseas-20231023-p5eeb2.html
says you can turn on roaming in your phone, cellular data off (for your home SIM), and receive texts. The person in the shop where I picked up the spare Three UK SIM confirmed that this works for them in Europe with Telstra. Of course, no sending texts, or calls, or data. It may work with Boost too, since Boost is part of Telstra, or it may work with all telcos.
Then I found this https://support.apple.com/en-us/102545
I can forward and receive texts between any devices logged into my icloud account. Another reason I'll never leave Apple. I tried it with texts to/from my wifi-only ipad to Anne's phone (with Imsg disabled). My phone was sending/receiving the texts on the cellular network and forwarding them to the Ipad 1 metre away over the internet via icloud. It worked for both Imsg and SMS. So it should work with my phone (and SIM) in Australia and the ipad on cellular or wifi in 13000km away in Europe. I didn’t see this solution described on the interweb. It means buying Anne's new iphone before my trip and leaving my SIM in her old phone at home, locked, muted, connected to a charger. It does the relay between the Boost Mobile phone network and the icloud. This way I can send and receive texts and imsg to Australia on my own number, without concern for how roaming works with Boost.
So, 3 solutions to receive texts on my own number:
1. Pay Boost to roam (cheap really, at $3 per day). I can turn on roaming in the Boost app if I need it.
2. Turn on roaming in my phone to receive texts, on my home SIM.
3. Use Apple text forwarding to send and receive texts.
1 and 2 involve taking my home SIM to Europe, 3 means leaving it in Australia, so I need to decide before I leave.
0 notes
Text
What Did I Do Today? Thursday
-Completed 4 Real Estate Tests today (to renew real estate license)
-Deleted footage off iPhone (spent 40 minutes deleting screenshots of TikTok Lives, Google Map screenshots for reminders from last year's backpacking trip, deleted all but the "one" best photo if I had duplicates). This is to prep my iPhone to be clean because I like starting a journey fresh. It's like starting a new book. Nothing from a previous book is directly related to this new book I'm about to read. Then I plan to transfer everything I want save to an external hard drive. Then I will store this HDD at my parent's house. Then wipe my iPhone Photo app CLEAN! Ready for new memories :)
-Watched some podcasts in between phone wiping, to see what I like, don't like, and how to create my content (Ex. Don't just yap just to yap. Get to the point, then get out).
-Finally edited the remaining "San Francisco Brand Ambassador Temp Gig" vlog (and uploaded!) where I rode my bike and took the train to San Francisco. I'm deciding how polished I want my content to be. I noticed some "empty silences" in the video where music or sound effects could work. But I also don't want to polish something so much that's intended to be raw. But I also don't want to be boring. Decisions, decisions.
Personal Note: Today isn't over yet, and usually I do TikTok LIVE in the evening. But I used ChatGPT to really motivate myself to be 100% prepared for my bicycle across America trip. There's not much left for me except wait for my 2nd No-ATM Fee debit card (always good to have a backup travel card), get my bike for the trip as my current bike has no option to shift gears, and clean out iPhone photos and videos to make room for the new ones. Which I am really excited about because I am learning that if I don't edit my vlog of the day that night, I'm never going to edit. So it's sort of a nice thing to basically cut the fat from the videos of the day and live a "post-to-delete" sort of philosophy. Because I posted my videos and photos, I can delete them off my iPhone. I also am realizing, that I do enjoy this diary "text" outlet. Because sometimes I don't feel like making a video. I just want to get my thoughts out. Like wanting to get from USA to Vietnam - I don't care how (train, boat, car, airplane, shark - just get me there).
Yesterday | Wednesday
-Edited my children's book "The Super-Duper Big Secret Rule of Everything!" This took up the majority of my time while at the library. Some of the issues were:
How to ensure the cover art covers the entire page (I still can't figure out)
How to add page numbers at the bottom (I'm intending to use images of numbers and use the Microsoft Word View > Grid to align the page numbers on the bottom
The "Draw Here" box was IMPOSSIBLE to align consistently on each page. Still unsure while. The work around was to use Canva to create a dotted rectangle > export as PNG file > import into Microsoft Word > align with grid. After printing, there still was misalignment.
-Organized and Printed QR Codes for busking and to put on bike while riding
-Organized and Printed "Sleeping Signs." These are the signs where (I'm not sure how to attach yet) I will attach them to my tent when I guerilla camp.
0 notes
Text
technology ramble
I’ve been getting a lot more picky about my tech lately. I’ve switched out some apps for other apps, ditched some tech altogether, and just generally been more thoughtful about what technology I use or allow to take up my time.
First off, I’ve been very much wanting everything to be local-first. Anything that is completely cloud-based is gonna be much more likely to be a no from me lately. I switched note apps to Obsidian, for example. I tried out getting a pocket notebook because that’s been a trend and I am open to more low-tech solutions to things lately, but ultimately it’s still a lot easier and quicker to pull out my phone to jot something down, especially if I’m also carrying something and need to take a note. But why Obsidian? Because the files just live in a folder. It’s not some weird proprietary situation where my notes exist only in Obsidian. My notes exist in files that I can open without Obsidian and move or copy however I’d like. I very much prefer that. Apple Notes is technically local, but it doesn’t offer any way of actually exporting all your notes. That is very much whack. Obsidian doesn’t even require you to export. They just live right there on your hard drive. They’re always exported. Never stuck in some proprietary format. That’s a huge plus in my book.
I’m not syncing my obsidian vault. I mainly use it on my phone to jot down any quick notes I need to throughout the day. I do also have the app on my gaming pc and my Macbook in case I need to type anything on those devices, but having my notes in the cloud isn’t really something that’s necessary for me I’ve found. Which is kind of a plus, because if I do need to jot down something sensitive like an account number or something, it’s not gonna immediately upload to some server that I have to trust. Another plus in my book. My former notes app, UpNote, isn’t bad. But I just honestly really love the way that Obsidian creates a folder and stores actual text files in that folder. That’s the killer feature for me.
I’ve also ditched Google Photos. I just have my pictures on my Macbook primarily now. I sync my Mac photo library to my iPhone using Finder (not iCloud). I’m also going to upload a copy of everything to Google Drive every now and then probably, just as a backup in case something were to happen to my laptop.
Why switch from Google Photos to Google Drive for the backup? Because I don’t want to have to use Takeout to download the backup if I need it. I don’t want Google to organize them or modify the files in any way. I just want them to sit in the cloud in case I some day need a backup of my pictures. Google Photos does seem to modify the files. If I request all my pictures through Takeout and try to import them back into Apple Photos, they won’t be in the proper order. That’s a no go for me. Eventually I might look into if there’s a cheaper solution for cloud storage that I’m only going to be using as a backup and not for syncing and ditch Google altogether.
I’ve ditched most social media, including TikTok (it’s not banned, right?). I obviously have kept tumblr but I don’t have it on my phone (I used Obsidian on my phone to write this and then copied it over to my laptop to post). Reddit was probably the last survivor other than tumblr, but I’m glad I ditched it. I would read tons of comments and get pissed off often. I’m way better off reading on my Kindle than I am opening Reddit. It’s 10:15 and I have only an hour and a half of screen time today. 30 minutes of that was ordering groceries from Target. 20 minutes checking the news in safari - which is a habit I’d like to stop. I only open the news on my phone because I want to mindlessly scroll. I still want to stay informed, but I want to do it at my PC and be more intentional about what I read rather than just opening Google News on my phone and scrolling. 15 minutes in the weather app and a few minutes each in Discord, Messages, and Spotify. Basically, I’m doing a lot less time wasting on my phone. Honestly I think I could see that number going down even more.
A lot of that time is going into reading since I bought a Kindle recently. Which I think is a much better use of my time, since before I’d likely just waste time on Reddit or before that TikTok and not come out of it with anything that was even that interesting. It’s definitely a good trade. I’m also watching more actual media, like TV shows and even some movies. Even a tv show is a better use of my free time than TikTok. Maybe not a ton better, but if I spend an hour watching tv I’m probably gonna feel like I enjoyed it more at the end than if I spent that hour watching TikTok.
Subscriptions are definitely on the chopping block. The only ones that have survived are Spotify and Fastmail. Those are both pretty valuable to me, but I could see myself possibly getting rid of Fastmail in the future. I use it because I have my own domain I use for my email address. I kind of like having that, because it means I am extremely unlikely to ever lose access to it. But I’m not 100% thrilled about paying for email. So eventually what I might end up doing is just setting up forwarding through my domain registrar so I can continue to use my custom domain email when I’m registering accounts online, but cancel Fastmail since I don’t need to send from my custom email very often and could proooooobably settle for a Gmail address when I do need to send email. But for now I am not ready to let my custom email go.
I also could get rid of Spotify in the future and just put MP3s or FLACs on either my phone or even possibly a dedicated device, but for now I am happy with the organization I get from Spotify. I’m not always in the mood to listen to my entire library shuffled, and Spotify makes it easy to listen to specific vibes.
Alrighty I think I’m done rambling. I have started writing this post several times and failed because I wasn’t sure how to organize it. But I’ve been wanting to write a bunch of this out for my blog because I have changed a lot of my tech habits recently and I think it’s been for the better.
[update, 2 hours later]
Actually I'm not totally done rambling. I also got rid of my self-hosted blog, mainly because I decided I didn't want to pay for it because like I said I am not really vibing with subscriptions. I've settled on using tumblr as my main blogging platform, mainly because I already have posts here and it's free. I'm keeping all my future posts locally on my PC in an Obsidian vault, too. At least the ones like this one. Not really that concerned with saving the TV screenshots I share. I also have been journaling in an actual paper notebook. I'm trying to write at least something in that every day. So in a way that has been a sort of replacement for my blog. Tumblr is definitely not perfect as a blogging platform but it gets a lot of points for being free. It's also nice that it has a community built-in. I also do like being able to reblog stuff so my blog isn't just my posts but kind of just a collection of stuff I like. It's got pros and cons. Not being in complete control of it is not ideal, but that's why for anything long or important that I post I'll keep a copy of it on my PC.
Anyway. Now maybe I'm actually done rambling about tech. For now.
If you're still reading I'll leave you with a book recommendation: Careless People by Sarah Wynn-Williams :)
1 note
·
View note
Text
“Password1234”: Tulsi Gabbard’s Login

“Password1234”: How Tulsi Gabbard’s Login Habits Nearly Triggered a Hawaiian Missile Crisis 2.0
The National Security Threat of Reusing Your Ex-Boyfriend’s Name As a Password When “Aloha” Meets “Access Denied” In a shocking exposé that shook no one except the IT guy named Carl, The Daily Beast revealed that Tulsi Gabbard—a congresswoman, veteran, spiritual warrior, and occasional surfer—had apparently been using passwords that could be cracked by a caffeinated squirrel with an iPhone 4. According to leaked reports, her online security strategy was a combination of horoscope advice, yoga poses, and pure vibes. And yet, somehow, the nation remained standing. So we ask the vital question: What happens when the nuclear codes are one password reset question away from “What was your first pet’s name?” “She thought two-factor authentication meant having a backup horoscope.” — Ron White Let’s dive into the browser history of this satirical scandal.
“Tulsi2020!” Isn’t Just a Campaign Slogan, It’s Also Her Netflix Password
Gabbard’s Surfboard Contains More Encryption Than Her Laptop Tulsi Gabbard ran for president in 2020. Apparently, she also ran out of original password ideas in the same year. According to a cybersecurity leak no one asked for, Gabbard used “Tulsi2020!” across at least seven platforms—including MyFitnessPal, Dropbox, LinkedIn, and a suspicious site called “WarriorMonkDating.com.” What’s worse? She added the exclamation point thinking it was military-grade encryption. “It’s like putting a sticker over a webcam and calling it cybersecurity,” said retired NSA analyst and part-time laser tag champion Ron Skelton.
The Yoga of Password Management: Sun Salutations and Synced Devices
Sources close to Gabbard say she once attended a cybersecurity retreat in Maui, where instead of encryption, participants were taught to breathe deeply while entering their debit card numbers into public Wi-Fi. She later described it as “a transformative experience where I learned to align my chakras and my bank logins.” One witness described Gabbard’s “password flow” routine: First, she logs in with “namaste123” Then does downward dog while waiting for two-factor authentication And finally logs out by whispering “Aloha” to the server
The Cybercrime Wave: Russian Hackers, Meet “Password1234”
By 2017, her accounts were part of a larger leak that included over 3 billion records. Her contribution to this vast archive of human carelessness? Password: Tulsi123 Backup Password: Password1234 Security Question: “What’s your favorite color?” Answer: “YES” “It’s the cybersecurity equivalent of leaving your keys in your car with a note that says ‘Steal me, but with love,’” explained digital security expert Cliff “BitByte” Hernandez.
Gmail, Glam, and Glitches: Tulsi’s Digital Footprint is Wearing Flip-Flops
Among the compromised accounts was her Gmail, which—according to leaked metadata—was 70% promotional emails, 20% requests to appear on obscure podcasts, and 10% fan mail written entirely in binary. One intern who sorted through the compromised messages said: “There were multiple drafts of her resignation letter, all saved as ‘resignation_final_FINAL_FOR_REAL.docx’”
Exclusive: Her Two-Factor Authentication Was a Friendship Bracelet
Tech insiders were horrified to discover Tulsi’s idea of 2FA wasn’t a confirmation code—it was “texting her cousin Jaya to see if it was really her logging in.” On multiple occasions, hackers were stopped not by firewalls but by confusion when Jaya replied, “Is this for the yoga class or the kombucha group chat?” “Her defense strategy relied heavily on poor communication,” one cybersecurity consultant laughed while installing malware protection for his mom.
Even Her iCloud Had a Tan
A trove of iCloud data included: 400 nearly identical selfies from the Senate gym A playlist titled “Legislative Bangers” Several videos of her dog doing warrior poses next to a salt lamp According to unverified rumors, a hacker group named “404Bros” tried to ransom the data, but after seeing the contents, sent a formal apology and a $15 iTunes gift card.
LinkedIn Recommendations Written by... Herself
One of the strangest discoveries in the leak? Tulsi had endorsed herself on LinkedIn for: Strategic Visioning Yogic Thought Leadership Military Telepathy Surf Diplomacy “That’s not even a real thing,” said career coach Sheila Plonk.“But I’d still hire her for the vibe.”
Ancestral Passwords and a Trail of Spiritual Cookies
Insiders say Gabbard once consulted her past-life regression therapist for password inspiration. She emerged from the session convinced her soul password was “CleopatraLives9.” She later told “Stars & Data Protection Weekly”:“We must be as secure in our online lives as we are in our truth. Unless Mercury is in retrograde, then all bets are off.”
“Don’t Blame Me, I’m a Vet” Becomes New Security Phrase
Tulsi’s go-to deflection when asked about her weak passwords?“I served this country, dammit. Let me have one unencrypted yoga blog.” Critics note this is the digital equivalent of a politician speeding through a red light and shouting, “I was in ‘The Amazing Race: Congress Edition’—I know what I’m doing.”
Eye Witness Account: Hacker Testimony from His Mom’s Basement
One teenage hacker who cracked her Dropbox said: “Honestly, I was trying to hack Roblox. But when I typed ‘Tulsi’ and ‘123,’ I accidentally got her Whole Foods receipts and a bunch of PDFs labeled ‘The Real Truth.’” He has since retired and now teaches online safety at a community center in Delaware.
The FBI’s Official Response: “We’re Too Tired for This”
An internal memo from the Bureau reportedly read: “We spent three weeks untangling this woman’s security habits. At one point, she used a Haiku as her encryption key.” Her defense?“Syllables are the safest language.”
Political Repercussions: Senators Now Forced to Change “Obama2024” to “Obama2025?”
Following the leak, Congress issued new password requirements: No campaign slogans No personal affirmations No references to enlightenment As one Republican aide lamented:“Guess I’ll have to change ‘ReaganLives’ to ‘TaxCutz4Life!’”
What the Funny People Are Saying
“Tulsi's passwords were so bad, even her spirit animal logged out.”— Sarah Silverman “Hackers were like, ‘We don’t want her emails. We just want her to stop using ‘Namaste69.’”— Dave Chappelle “Her Dropbox was 90% surfboard selfies and 10% blurry screenshots of UFOs.”— Trevor Noah “I haven’t seen this many security holes since my grandma’s knitting project.”— Jerry Seinfeld “At this point, she’s just daring China to log in.”— Chris Rock
Her Yoga App is Still Logged In on Eight Public Devices
Eyewitnesses at a Honolulu smoothie bar confirmed they could still access Tulsi’s meditation schedule, her list of mantras, and a half-written memoir titled “Shiva, Surfing & Senate Committees.” “She’s logged in on the juicer,” one barista sighed.“We know when she’s late to Pilates. The blender just starts chanting.”
Final Thoughts: It’s Not Just About Tulsi—It’s About Us
Let’s not throw our encryption stones from glass iPhones. Who among us hasn’t: Reused a password from 8th grade? Used their dog’s name and added “123”? Logged into Wi-Fi named “FBI Surveillance Van”? Tulsi’s mistakes are a national metaphor: We all want to be free spirits until someone hacks our Hulu queue.
Public Opinion Poll: What Do Voters Think?
Conducted by Spintaxi Institute for Hilarious Policy Studies“Which of the following would make a stronger password than Tulsi’s current one?” “MyExSucks42” – 37% “!@$%&” – 22% “IamTheRealPOTUS” – 18% “Password1234ButWithVibes” – 13% “HunterBidenLaptop2025” – 10%
Actionable Advice: From SpinTaxi’s Chief Tech Guru, Bleepy VonFirewall
1. Never reuse passwords. Even if they contain the word “chakra.”2. Don’t rely on your cousin for 2FA unless she’s a Navy SEAL or works at Apple.3. Your ex’s nickname is not secure just because you added a symbol.4. Enlightenment is not a firewall.5. If your password is a pun, you’ve already been hacked.
Conclusion: What Have We Learned?
We’ve learned that no matter how confident, intelligent, or mystically inclined you are, the moment you type “Tulsi2020!” into seven websites, you are officially the cybersecurity version of wearing socks with sandals. But in a world where digital threats grow daily, Tulsi’s spiritual approach to password management is a gentle reminder:The only thing worse than hackers… is hubris. And now, if you’ll excuse us, we have to go change our Netflix login from “SpinTaxiRocks69.”
Satirical Sources:
Senator Accidentally Uses Dog’s Name as Nuclear CodeCongressional Cybersecurity Training Now Includes Deep Breathing and Essential OilsHackers Demand Tulsi Return Their Time After Reading Her EmailsNational Security Council Adds “Vibes Check” to Daily Threat ReportsTulsi Gabbard Named Honorary IT Disaster of the Month by the Geek Squad Auf Wiedersehen! Want the VPN password? Ask Tulsi—it’s probably still “Mahalo123.”

SpinTaxi Magazine - A wide-aspect Toni Bohiney-style cartoon in the spirit of Mad Magazine, fold-in style. The scene shows Tulsi Gabbard sitting on a yoga mat in a tropical ... spintaxi.com
Tulsi Gabbard Named Honorary IT Disaster of the Month by the Geek Squad
Here are 15 observations inspired by the recent revelations about Tulsi Gabbard's password habits: Password123? Even my grandma knows better. Reusing passwords is like using the same key for your house, car, and office—convenient until it's not. 'Shraddha' as a password? Might as well have used 'OpenSesame'. MyFitnessPal account hacked? Guess someone wanted to know her calorie intake. Fox News Dropbox breach? Hope there weren't any dance videos in there.The Daily Beast LinkedIn compromised? Now everyone knows she endorsed herself. Using the same password since 2012? That's commitment—or laziness. No evidence of government accounts being compromised. Phew! National secrets are safe... for now. Signal group chat leak? Maybe it's time to switch to smoke signals. HauteLook account hacked? Someone's getting fashion tips on the sly. Gmail breach? Hope those cat memes weren't classified.The Daily Beast Reusing passwords is a no-no. Even toddlers have unique passcodes for their iPads. Cybersecurity 101: Don't do what Tulsi did. Seriously. Википедия — свободная энциклопедия At least she didn't write her password on a sticky note... or did she? We may never know. Lesson learned: Always use two-factor authentication. Or better yet, three. For more details on this story, you can read the full article here: Tulsi Gabbard's 'Easily Cracked' Password Habits Revealed. Read the full article
0 notes
Text
How to Use a Digital Planner on GoodNotes & Notability: A Beginner's Guide
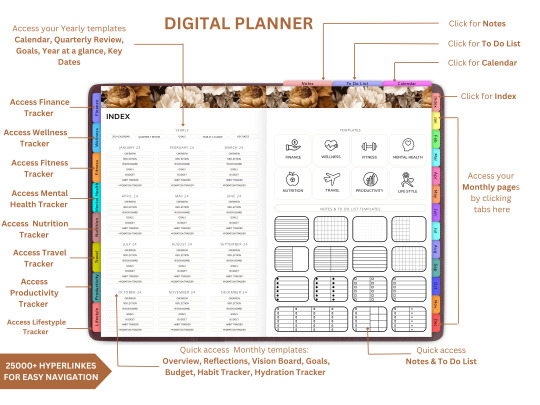
Are you new to the world of digital planning? Whether you just bought your first iPad or want to switch from traditional paper planners, this guide will walk you through how to use a digital planner in GoodNotes and Notability—two of the most popular annotation apps available today.
Digital planning is a fun, eco-friendly, and highly customizable way to stay organized. And the best part? You can start immediately with tools you already have and a beautifully designed planner from Digital Softech.
What Is a Digital Planner?
A digital planner is a PDF-based planner that mimics the layout and functionality of a traditional paper planner but is designed to be used on tablets. With apps like GoodNotes and Notability, you can annotate your planner using a stylus (like the Apple Pencil), just like writing on paper—but with endless digital advantages.
Why Use GoodNotes or Notability?
Both GoodNotes and Notability are powerful, user-friendly apps that support handwriting, highlighting, and hyperlinking. They're perfect for digital planning because they allow:
Seamless writing with a stylus
Easy importing of PDF planner files
Customization with stickers, images, and templates
Hyperlink navigation between planner pages
Tip: Start with GoodNotes if you prefer a notebook-like layout, or choose Notability for audio-note syncing and multi-media features.
What You Need to Get Started
Here’s your digital planner starter kit:
An iPad or compatible tablet
A stylus (Apple Pencil is ideal)
GoodNotes or Notability app
A digital planner PDF (available at Digital Softech)
Step-by-Step: Using a Digital Planner in GoodNotes
1. Download Your Planner
After purchasing or downloading a free digital planner from Digital Softech, save the PDF to your iPad.
2. Import into GoodNotes
Open GoodNotes
Tap the "+" icon > Import
Choose your downloaded planner PDF
Your planner is now ready to use
3. Learn the Interface
GoodNotes has tools like:
Pen and Highlighter
Eraser and Lasso Tool
Shape Tool
Text Box
Tip: Use the Lasso tool to move stickers or notes around your planner easily.
4. Navigate with Hyperlinks
Most planners from Digital Softech are hyperlinked—tap on dates or tabs to instantly jump to different sections.
5. Customize with Stickers & Inserts
Drag and drop PNG stickers into your planner
Copy-paste weekly inserts or habit trackers
6. Sync Across Devices
Enable iCloud sync to access your planner on iPhone, Mac, or multiple iPads.
Step-by-Step: Using a Digital Planner in Notability
1. Download Your Planner
Download the planner PDF from Digital Softech and save it to your iPad.
2. Import into Notability
Open Notability
Tap the Import icon (arrow)
Choose your planner file
3. Use Annotation Tools
Notability offers:
Pen, Highlighter, and Eraser
Voice Recording
Media Insertion (images, web clips)
Tip: You can record meetings while writing in your planner—great for students and professionals!
4. Customize Your Layout
Drag in extra templates or sticker sets to decorate your weekly and monthly views.
5. Secure and Backup
Enable automatic iCloud backup or Google Drive integration to never lose your notes.
Digital Planning Tips for Beginners
Set a Routine: Plan daily or weekly to stay on track.
Use Colors Strategically: Color-code tasks or priorities for clarity.
Add Digital Stickers: These add personality and can even act as reminders or labels.
Try Layering: Add sticky notes, checklists, and text boxes on top of your planner pages.
Practice Makes Perfect: It might feel new at first, but give yourself a week to adjust.
Common Mistakes to Avoid
Not Backing Up Your Planner: Always sync or export regularly.
Overloading Your Layout: Keep things clean and readable.
Skipping the Tutorial: Apps like GoodNotes and Notability have guides—use them!
Bonus: Where to Get the Best Digital Planners
At Digital Softech, we specialize in premium, easy-to-use digital planners designed for both beginners and seasoned users. Our planners are:
Hyperlinked for easy navigation
Aesthetic and minimal
Affordable and reusable
Whether you want a daily planner, wellness tracker, goal-setting template, or student planner—we’ve got it all.
Explore now: https://digitalsoftech.com
Final Thoughts
Learning how to use a digital planner with GoodNotes or Notability can truly transform your productivity. With a bit of practice, you’ll be planning smarter, faster, and more creatively. From hyperlinks to stickers, the digital planner world is full of possibilities.
Ready to get started? Visit Digital Softech and download a digital planner that fits your style and needs. Your perfect planning experience is just a tap away!
0 notes
Text
UPDATE REGARDING BILL’S BIBLE BASICS WEBSITE
Dear friends, for those of you who may have possibly missed seeing my previous messages nine days ago on February 21, 2025, I apologize for my website’s downtime.
Sadly, over the past year or so, due to computer age and related technical problems, I lost both of the computers which were being used to run the Bill’s Bible Basics online ministry.
The second and last remaining computer finally crashed completely — meaning both hard drives were totally fried — on February 20, 2025. That was when I made my last online post using regular BBB graphics, etc.
As a result, currently, all I have to work with right now is my six year old iPhone, which I have been using to post text-based messages only on the various social networks.
Since the last computer died ten days ago, I have been patiently waiting for a new computer to arrive. It was actually supposed to have arrived on February 24th. However, it has been delayed — thanks USPS! — and is still in transit from the continental USA.
Hopefully, the new computer will arrive within the next week. If so, once it does arrive, I will be able to determine exactly what needs to be done in order to get the Bill’s Bible Basics ministry and website back online.
Hopefully, no data was lost on my one remaining external backup drive, and I will be able to restore the Bill’s Bible Basics website completely. Time will tell.
In the meantime, your prayers are greatly appreciated. God bless you, and thanks so much!
0 notes
Text
iPhone tracker
iPhone Tracker: The Ultimate Guide to Monitoring and Security Solutions

In today’s digital age, keeping track of a device, especially an iPhone, has become essential for various reasons. Whether you’re a concerned parent wanting to monitor your child’s safety, an employer ensuring company data security, or an individual looking to recover a lost or stolen device, an iPhone tracker can be an invaluable tool.
With advanced tracking technology, users can remotely monitor the location, activities, and even communications on an iPhone without the target user’s knowledge. This article provides an in-depth guide to iPhone tracking, its applications, features, legal considerations, and the best tracking solutions available.
What is an iPhone Tracker?
An iPhone tracker is a software or service designed to monitor and track an iPhone’s location and activities. These tracking tools use GPS, Wi-Fi signals, and cellular data to provide real-time location updates, allowing users to keep an eye on the device’s whereabouts.
Apart from location tracking, some advanced iPhone tracking tools also allow monitoring of:
Call logs and text messages
Social media activities (WhatsApp, Facebook, Instagram, etc.)
Browsing history and app usage
Photos, videos, and media files
Keystroke logging (Keylogger features)
Email monitoring
Geofencing alerts
Why Use an iPhone Tracker?
There are several reasons why individuals and organizations might use an iPhone tracker:
1. Parental Control and Child Safety
Parents often worry about their children’s safety when they are away from home. With an iPhone tracker, parents can:
Monitor their child’s location in real time
Check call logs and text messages for suspicious conversations
Set geofencing alerts to receive notifications if their child enters or leaves a specific area
Block inappropriate websites or apps
2. Employee Monitoring for Businesses
Many companies provide employees with company-issued iPhones for work purposes. Employers may use an iPhone tracker to:
Ensure company devices are used only for business purposes
Prevent data leaks and insider threats
Track field employees for productivity and safety
Monitor emails and social media usage during work hours
3. Recovering Lost or Stolen iPhones
Losing an iPhone can be frustrating, especially considering the amount of sensitive data stored on the device. With a reliable iPhone tracking app, users can:
Track the real-time location of their lost phone
Remotely lock or wipe the device to prevent data theft
Capture photos of the thief using the phone’s camera
Receive SIM change alerts
4. Spouse and Relationship Monitoring
Some individuals use iPhone trackers to monitor their spouse’s activities if they suspect infidelity. While this is a common reason, it’s important to be aware of the legal implications of tracking someone without their consent.
5. Personal Security and Backup
Even for personal use, having an iPhone tracker can be beneficial. It helps users:
Keep a record of their travel history
Locate their iPhone in case of misplacement
Store data backups for easy recovery
How Do iPhone Tracking Apps Work?
GPS and Network-Based Tracking
Most iPhone tracking apps rely on GPS signals, Wi-Fi connections, and cellular towers to determine the device’s precise location. These methods ensure accuracy, even in remote areas.
Stealth Mode Functionality
Premium iPhone trackers operate in stealth mode, making them undetectable on the target device. The app runs silently in the background, ensuring the user remains unaware of the monitoring.
Data Sync and Remote Access
Once installed, an iPhone tracker syncs data to a secure online dashboard that users can access from any device. This allows for real-time monitoring and activity tracking.
Geofencing and Alerts
Many advanced tracking solutions offer geofencing, where users can set up virtual boundaries. If the target device enters or leaves a designated area, an instant alert is triggered.
Keystroke Logging (Keylogger Feature)
Some tracking apps come with keyloggers, which record every keystroke made on the device, including passwords, messages, and search queries.
Best iPhone Tracking Apps in 2025
If you’re looking for a reliable iPhone tracker, here are some of the best options available:
1. mSpy
One of the most popular iPhone tracking apps, mSpy offers: ✔️ GPS location tracking ✔️ Call and SMS monitoring ✔️ Social media tracking (WhatsApp, Facebook, Snapchat, etc.) ✔️ Keylogger feature ✔️ Stealth mode operation
2. FlexiSPY
Known for its advanced spy features, FlexiSPY provides: ✔️ Live call recording ✔️ Keylogging and remote camera access ✔️ Screenshot capturing ✔️ Social media and email monitoring
3. Spyic
A cloud-based tracking app, Spyic offers: ✔️ No jailbreak installation ✔️ GPS and geofencing alerts ✔️ Call and SMS tracking ✔️ Web browsing history monitoring
4. uMobix
A great option for parental control, uMobix includes: ✔️ Social media tracking ✔️ Live GPS tracking ✔️ Call and contact logs monitoring ✔️ Remote camera activation
5. Find My iPhone (Apple’s Built-In Tracker)
For basic tracking needs, Apple’s Find My iPhone feature allows: ✔️ Real-time device location tracking ✔️ Lost mode activation ✔️ Remote device locking and erasing ✔️ Play sound feature for easy location
Is Tracking an iPhone Legal?
The legality of iPhone tracking depends on the country and purpose of use. Here are some key legal considerations:
✅ When is Tracking Legal?
✔️ Parental control: Parents tracking their minor children’s devices ✔️ Employer monitoring: Tracking company-owned devices with employee consent ✔️ Lost/stolen device recovery: Using tracking tools to locate a lost or stolen phone
❌ When is Tracking Illegal?
❌ Spying on someone without their consent (e.g., spouse, partner, or friend) ❌ Accessing private data without permission❌ Using tracking apps for criminal purposes
⚠️ Always check local laws before using an iPhone tracker.
How to Protect Yourself from Being Tracked?
If you suspect someone is tracking your iPhone without your consent, follow these steps:
✔️ Check for unknown apps: Go to Settings > General > iPhone Storage and look for suspicious apps. ✔️ Disable Location Services: Turn off Location Services in Settings > Privacy. ✔️ Enable Two-Factor Authentication: Prevent unauthorized access to your iCloud account. ✔️ Use Anti-Spyware Apps: Apps like iVerify can detect spyware. ✔️ Factory Reset: As a last resort, perform a factory reset to remove any tracking software.
Final Thoughts
An iPhone tracker is a powerful tool for parents, businesses, and individuals seeking security, monitoring, and device recovery solutions. However, it’s crucial to use these tools ethically and legally.
For those in need of a professional spy and hack expert, choosing a sophisticated and reliable tracking solution ensures optimal performance while maintaining privacy and security.
Whether you’re looking for a parental control app, employee monitoring solution, or anti-theft tracking tool, the right iPhone tracker can help enhance safety, prevent data breaches, and ensure peace of mind.
1 note
·
View note
Text
Mobile Security: Protecting Users from Phishing, Malware, and Data Breaches

Mobile phones have become a means of communication that has become an integral part of our life, whether it is related to banking or sharing on social media. This excessive use only makes mobile devices the primary victims of these cyber attacks, which range from phishing to malware infections and data breaches. It is important to protect yourself from these threats, and cyber security courses are an excellent investment in staying ahead of hackers. Let's dive into the risks and explore how users can safeguard their mobile security.
The Growing Threat of Mobile Cyber Attacks
Phishing Attacks: Deceptive Tactics to Steal Your Data
Phishing remains one of the most dominant cyber threats on mobile devices. The criminals steal sensitive information like passwords and credit card information using fraud emails or text messages or fake websites. Mobile phishing attacks are effective since individuals are more likely to click on links without confirming their authenticity.
How to Protect Yourself:
Never click on links from unknown sources.
Enable two-factor authentication (2FA) for added security.
Verify URLs before filling out personal data.
Take courses in cyber security to learn sophisticated phishing detection.
Malware: The Silent Invader
Malware can enter your mobile device via malicious apps, infected websites, or misleading downloads. Once on your device, malware can snatch personal data, monitor your actions, or even hold your device for ransom (ransomware). Mobile malware is becoming ever more sophisticated and is often presented as legitimate apps.
Download apps only from official stores like Google Play or the Apple App Store.
Check app permissions before installing.
Use a reputable mobile antivirus software.
Keep your operating system and apps updated to patch vulnerabilities.
Data Breaches: Your Information at Risk
Data breaches are a case in which hackers infiltrate a company's storage and obtain sensitive user information. Users' personal information, payment details, and even biometric information are leaked and stolen, making way for identity theft and financial fraud.
Protecting Yourself:
Use unique and strong passwords on various accounts.
Keep an eye on your bank and credit card statements regularly.
Turn on fingerprint or face ID when possible.
Learn about mobile security through cyber security courses to keep abreast of the latest protective measures.
Best Practices for Mobile Security
Avoid Public Wi-Fi Networks
Public Wi-Fi is a hotspot for hackers who use man-in-the-middle (MITM) attacks to intercept your data. If you must use public Wi-Fi, consider using a VPN to encrypt your connection.
Enable Remote Wipe and Find My Device
In case your mobile device is lost or stolen, having remote wipe enabled can prevent unauthorized access to your personal data. Use services like Google's Find My Device or Apple's Find My iPhone to track and secure your phone remotely.
Disable Bluetooth and NFC When Not in Use
Cybercriminals can take advantage of the vulnerabilities in Bluetooth and NFC to access your device without permission. Turning them off when not in use reduces this risk.
Back Up Your Data Regularly
A backup ensures you do not lose important information in case of a cyber attack or failure of your device. You can use cloud storage or an external hard drive to keep your files safe.
Why You Should Consider a Cyber Security Course
With the rapid evolution of mobile threats, knowledge in cyber security can be a game changer. You can learn by enrolling in cyber security courses and:
Understand modern cyber threats and their prevention.
Learn ethical hacking techniques to test mobile security.
Gain insights into mobile security frameworks and best practices.
Enhance your career prospects in the cybersecurity domain.
Conclusion
With mobile devices dominating our daily lives, securing them is now more important than ever. It ranges from avoiding phishing scams to protecting against malware and data breaches. Users need to take proactive measures to ensure their safety. Taking cyber security courses is a smart step toward gaining expertise in mobile security and protecting personal and professional data. Stay informed, stay secure!
0 notes
Text
Liner Notes (January 11th, 2025)
Welcome to the first newsletter of 2025. This week’s supporter Q&A post can be found here. If you’d like this newsletter delivered to your inbox each week (it’s free and available to everyone), you can sign up here. A Few Things * We launched our Best of 2024 feature this week, and I’m super happy with how it turned out. It highlights the diversity of musical tastes across our contributors, and I love that it doesn’t look like all the other music publications’ end-of-the-year lists. If you haven’t checked it out yet, there is some excellent stuff on there. * My list (that also goes through movies, TV shows, and books I enjoyed in 2024) is also posted on my blog. I really enjoyed 2024 as a music year, and it’s one with quite a few albums that that will stay in permanent rotation. * I am always on the lookout for cool new iPhone or desktop wallpapers, and I recently came across this website. It’s one of the better collections online I’ve found for nerdy (Star Wars, superhero) wallpapers. I grabbed quite a few for my rotating collection. * Since this is is the first newsletter of the new year, I hope everyone had a nice holiday season. Ours was relatively calm. Lots of family time, and it was nice to get to experience the first holidays in our new home. * Hannah got me (along with new band hoodies and records) a hot air popcorn maker this year, and I’m a big fan. This, plus some coconut oil and sea salt, has made the best homemade popcorn I’ve ever had—big shoutout to whoever recommended the coconut oil to me. I’m sorry I forgot who it was, but it’s a real game-changer for home-popped popcorn. * I updated My Archive to link to new pages that automatically update each week with my favorite albums, movies, and TV shows. This was a holiday week coding project that I had on my list to want to do for a while. My next “for fun” project has gotten, admittedly, a little out of hand. What started as wanting to build a companion app for my Now Playing device to make it respond immediately to changes in songs has now become a full-on Mac app that also scrobbles to Last.fm. It’s my first attempt at Mac programming, and it’s been a fun little evening project I’ve been experimenting with. I want something that can work with my Now Playing device, but I also want something that I have more control over for how it scrobbles and interacts with Last.fm. Neptunes is great, but it’s also overkill for what I need and doesn’t scrobble how I prefer. (I like how Marvis queues a track and then scrobbles and how it handles paused tracks, I’ve found far fewer duplicates with Marvis than with Neptunes, so I want to mimic that.) I also want to build in a few features I’ve wanted for myself: the ability to immediately scrobble a track and skip to the next one, better sync loved/favorited tracks between Last.fm and Apple Music, and the big one, the ability to keep a local backup of scrobbled/played tracks in text files. I love Last.fm, but I’m also terrified of it one day going away. I want to have a way to recreate my Last.fm history if I need it, and I want to be prepared with something that can keep my music listening history going forward as well. It’s ridiculously overkill. But, it’s a fun project to work on and it lets me play with some programming muscles that I don’t get to stretch much these days. And I’ve never actually built an app before. So that’s fun to learn too. I have no idea if it will ever get to a place where I’ll share this, but for myself, I’m having a blast learning. In Case You Missed It * Chorus. fm’s Top 30 Albums of 2024 * Jason Tate’s Top Albums of 2024 * Craig Manning’s Top Albums of 2024 * Adam Grundy’s Top Albums of 2024 * Mark O’Connell Announces Departure From Taking Back Sunday * Interpunk Shuts Down * Mayday Parade Announce New Album * Tom DeLonge Teases Spring Shows * Albums in Stores – Jan 10th, 2025 Music Thoughts * One of my favorite parts of publishing our end-of-the-year feature is diving into… https://chorus.fm/features/articles/liner-notes-january-11th-2025/
0 notes