#cryptography blockchain
Explore tagged Tumblr posts
Text
What is Blockchain? 10 Simple Ways to Understand the Technology
Blockchain technology, once a niche concept primarily associated with cryptocurrencies like Bitcoin, has rapidly evolved into a revolutionary innovation with the potential to reshape countless industries. At its heart, blockchain is a distributed ledger technology (DLT) that provides a secure, transparent, and immutable way to record transactions and information. It’s more than just the backbone…
#beyond cryptocurrency#blockchain algorithms#blockchain applications#blockchain basics#blockchain benefits#blockchain chain#blockchain challenges#blockchain consensus#blockchain definition#blockchain ecosystem#blockchain evolution#blockchain explained#blockchain for beginners#blockchain for business#blockchain for finance#blockchain for government#blockchain for logistics#blockchain future#blockchain implementation#blockchain innovation#blockchain network#blockchain nodes#blockchain security#blockchain technology#blockchain use cases#blockchain validation#blocks in blockchain#consensus mechanism#cryptographic hash#cryptography blockchain
1 note
·
View note
Text
Unveiling RANDO.fun: A Journey into Bitcoin Key Generation and Puzzle Solving
Discover the intricacies of Bitcoin key generation and delve into the enigmatic Bitcoin puzzle that has captivated crypto enthusiasts worldwide.
Introduction
The world of Bitcoin is filled with mysteries, challenges, and opportunities for those willing to explore its depths. One such enigma is the Bitcoin puzzle—a cryptographic challenge that has intrigued and puzzled many. Enter RANDO.fun, a platform designed to generate random Bitcoin private keys within a specific range and assist in exploring this elusive puzzle.
What is RANDO.fun?
RANDO.fun is a Bitcoin key generator and puzzle solver that creates random private keys within a user-defined range. It checks for a match with a specific Bitcoin address:
Copy code
1BY8GQbnueYofwSuFAT3USAhGjPrkxDdW9
This address is part of a larger Bitcoin challenge transaction. For privacy and security reasons, the generated keys are not displayed by default. Users can access a comprehensive User Guide to navigate the platform effectively.
The Bitcoin Puzzle Explained
The Bitcoin puzzle is a series of Bitcoin addresses with increasing amounts of BTC, allegedly set up by an anonymous entity—some speculate Satoshi Nakamoto himself. The puzzle involves finding the private keys corresponding to these addresses, each protected by a specific level of cryptographic complexity, ranging up to 2<sup>160</sup>.
Why Does It Matter?
Cryptographic Challenge: It serves as a real-world application of cryptographic principles, testing the limits of computational power and cryptanalysis.
Educational Value: Offers a practical way to understand Bitcoin's underlying security mechanisms.
Community Engagement: Fosters collaboration and discussion within the crypto community.
How RANDO.fun Assists in Exploring the Puzzle
Systematic Key Examination
To tackle the Bitcoin puzzle, one must systematically examine a range of potential private keys and verify their balances. RANDO.fun automates this process by:
Random Key Generation: Producing private keys within a specified range.
Balance Verification: Checking each key against the target Bitcoin address to see if there's a match.
Privacy Measures: Ensuring that generated keys remain confidential and are not displayed publicly.
User Guide and Support
The platform provides a detailed User Guide that walks users through:
Setting up the key generation parameters.
Understanding the underlying algorithms.
Best practices for maintaining security and privacy.
Ethical Considerations
While the Bitcoin puzzle is a legitimate challenge within the crypto community, it's essential to approach it ethically:
Legal Compliance: Ensure that all activities comply with local laws and regulations.
Respect for Privacy: Avoid any actions that could infringe on others' privacy or property.
Community Standards: Engage positively with the community, sharing insights and respecting the collaborative nature of the challenge.
The Importance of Security
Bitcoin's security relies heavily on cryptographic principles. Platforms like RANDO.fun emphasize the significance of:
Private Key Protection: Understanding that private keys are the gateway to one's Bitcoin holdings.
Secure Practices: Encouraging users to follow security best practices when handling cryptographic tools.
Awareness: Promoting knowledge about potential risks and how to mitigate them.
Conclusion
RANDO.fun offers a fascinating avenue for those interested in cryptography, Bitcoin, and complex puzzles. By providing tools to generate and analyze private keys responsibly, it contributes to the broader understanding of Bitcoin's security mechanisms.
Have you explored RANDO.fun or delved into the Bitcoin puzzle yourself? Share your thoughts and experiences in the comments below!
2 notes
·
View notes
Video
Cryptography Fundamentals for Blockchain
2 notes
·
View notes
Text
Quantum Computing: The Next Revolution in Technology
What if the computer of the future could help alleviate some of the problems facing us today in seconds? It would take a traditional computer millions of years. That is what quantum computing promises to deliver: a revolution that can revolutionize all the sectors it comes into contact with. From science and medicine to finance and cybersecurity, quantum computing is spearheading the next technology revolution.
This article explores the fundamentals, current progress, and real-world applications of this innovation. We’ll uncover how it’s changing the rules of computation and setting the stage for a faster, smarter, and more efficient future.
Understanding Quantum Computing
Scientists have rebranded how computers calculate information by producing qubits, unbound by the binary constraints of traditional bits. Unlike traditional bits, which are 0 or 1, qubits can appear everywhere in a quantum superposition due to superposition and entanglement. This allows machines to solve several calculations at once, not one after the other, significantly heightening their ability to solve certain problems.
By superposition, the engineers enable a qubit to hold more than one state. By entanglement, they connect qubits in a way that a manipulation of one immediately affects the rest no matter where they are physically located. These operations permit quantum computing-based systems to be superior to classical systems in cryptography, molecular modeling, and optimization of data. As researchers improve the stability of qubits and system precision, they are bringing us closer to a solution deemed intractable.
The Evolution of Quantum Computing
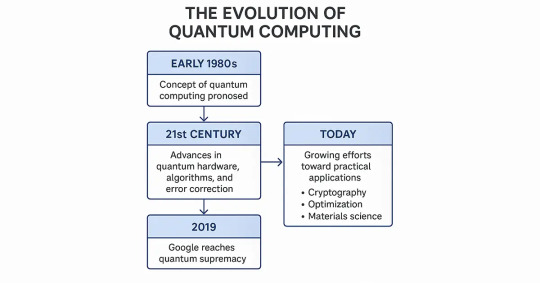
Back in the early 1980s, physicists such as Richard Feynman talked about using quantum mechanics for computing. It took scientists several decades to work on the idea, but the technology was not ready yet to make it a reality. During the 21st century, scientists and engineers started surmounting such challenges by improving quantum hardware, sophisticated algorithms, and superior error correction methods.
In the past two years, companies such as IBM, Google, Intel, Rigetti and IonQ have invested a lot in creating reliable and large quantum machines. In 2019, Google achieved quantum supremacy when its machine solved an exact problem in just three minutes, while the fastest standard computer would have taken many days to do this.
Today, this rivalry continues intensifying with groups pushing the limits of innovation. What they do lays the foundation for a future when quantum computing upends areas such as cryptography, optimization, and materials science.
Quantum Computers in Practice
Quantum computers are starting to surpass themselves in real, applied applications in numerous sectors. In medicine, they are utilized by researchers to model and simulate intricate molecular interactions, which accelerate the discovery of new drugs and decrease costs of development. Crunching computations, slowing down traditional machines, quantum computers enable scientists to simulate compounds virtually before proceeding to actual experiments.
Logistics engineers use quantum-inspired techniques to tackle routing optimization, inventory optimization, and supply chain optimization. These systems are efficient at solving complex combinatorial problems at unparalleled speeds, enabling firms to save time and money.
Quantum algorithms are employed by financial companies to better model risk scenarios and identify fraud more appropriately. These innovations assist decision-making and possess a greater security feature.
Data scientists also incorporate quantum systems in machine learning pipelines, which reduces the time to train large models. Meteorologists look forward to more accurate weather predictions by more accurately modeling atmospheric systems. Cryptography and materials science advances also continue.
With quantum computing continuing to advance at a tremendous pace, its application is beginning to leave theory behind and head towards transformational uses. With more organizations turning to technology, quantum computers will help solve some of the globe’s most complicated and most critical challenges.
Quantum Algorithms: Solving the Unsolvable
Quantum algorithms propel the transformative potential of computation to be. Computer scientists and mathematicians created the algorithms to bypass challenges that in essence are insurmountable for traditional systems. Shor’s algorithm, for instance, breaks large numbers exponentially more quickly than any standard process — a development that threatens modern-day encryption standards. Security professionals everywhere now reassess cryptography systems in preparation for such disruptive capacity.
Grover’s algorithm optimizes searching by greatly decreasing the amount of time needed to find a particular item within unordered databases. Rather than going through each entry individually, Grover’s algorithm enables users to learn outcomes with considerably fewer steps, providing a quadratic speedup.
In contrast to conventional algorithms that simulate existing computing paradigms, quantum algorithms rework problem-solving solutions altogether. They function on new foundations of principles, using entanglement and superposition to produce outcomes that are outside classical bounds. Designers must now work on creating new logic and architecture that leverages this style of computing.
Instead of just extending the capacity to compute, quantum computing…
#quantum computing#quantum computer#quantum security#ncog#post quantum secure blockchain#blockchain technology#blockchain security#decentralized database#post quantum cryptography#post quantum blockchain#quantum algorithms
1 note
·
View note
Text
Q-Day Bitcoin must update quantum computing in 5 years

In five years, Q-Day Bitcoin must develop or be defeated by quantum computing.
A quantum attack might shatter Bitcoin's 16-year-old trust unless it updates its core cryptography in the next five years. Updates are needed immediately to secure the most popular cryptocurrency.
After the 2008 financial crisis, Satoshi Nakamoto created a decentralised monetary system using elliptic curve cryptography, revolutionising money. Decentralisation and exact math blended nicely, drawing many people and corporations, including BlackRock. Bitcoin is sixteen years old and has never been hacked.
Quantum computing, Bitcoin's biggest threat since its inception, may change this. Quantum computers, once considered science fiction, may crack Bitcoin's cryptography in five years or even next year, according to quantum commentator Michele Mosca.
Rise of Supercomputers
Microsoft's Majorana processor, released this year, has cut the time needed to build a useful quantum supercomputer from decades to a few years. This chip is tackling key challenges in this technical breakthrough and enabling dependable and scalable quantum systems. McKinsey predicts 5,000 quantum computers by 2030, up from 100 today. These faster machines belong to a new class that can do operations in parallel, which kills classical cryptography like Bitcoin's private key encryption using ECDSA.
At least 30% of Bitcoin, 6.2 million, are held in “pay-to-public-key (P2PK)” or “reused P2PK-hash addresses,” making them vulnerable to quantum threats. Besides incurring permanent financial loss for Bitcoin holders, a breach would damage the ecosystem by disproving the system's impenetrability. BlackRock acknowledged the quantum danger to Bitcoin in its updated spot ETF registration.
Q-Day Bitcoin
It depicts the moment quantum computers will be powerful enough to break cryptography. Bitcoin vulnerability: Bitcoin transactions verified and secured ten years ago may still be at danger on Q-Day. Because the blockchain is transparent and its data is always available on the ledger.
“Harvest now, decrypt later” threat: Malkers are collecting encrypted data for Q-Day. This method is called “harvest now, decrypt later”. Possible simultaneous attacks: Quantum attacks could occur simultaneously worldwide as Q-Day approaches.
Bitcoin must be ready for this. The community must advance Bitcoin and prepare for Q-Day now rather than later. Bitcoin is most threatened by complacency, not quantum computing.
Readying for Q-Day
Quantum computers will break cryptography on “Q-Day”. Bitcoin transactions approved and secured today or ten years ago may still be at risk since the blockchain is open and its data is constantly available. Hostile actors are also practicing “harvest now, decrypt later” by gathering encrypted material for Q-Day, which might lead to global strikes. Bitcoin must prepare for this.
Post-Quantum Future
Legacy blockchains must be hard forked to switch to post-quantum cryptography. This difficult problem in the crypto ecosystem may generate user experience concerns, liquidity dispersion, network splitting, and long-term user alienation. Layered security models, quantum-secure key management infrastructure, and hybrid systems that prioritise transaction security without changing the base layer are alternatives.
Given Bitcoin's cautious and slow growth, this adjustment is not a cure. In a post-quantum future, Bitcoin cannot survive, so decisions and solutions must be made fast.
Satoshi Nakamoto's new monetary system is meant to change. The community must decide on evolution and prepare for Q-Day now, not later. Bitcoin is most threatened by complacency, not quantum computing.
#QDayBitcoin#quantumcomputing#Bitcoin#MicrosoftMajoranachip#cryptography#blockchain#postquantumcryptography#News#Technews#Technology#Technologytrends#Govindhtech
1 note
·
View note
Text
Discover Why Crypto Could Save You Money Today
Key Takeaways Cryptocurrency leverages cryptography: Secure transactions are enabled through complex mathematical algorithms that encrypt and decrypt data. Blockchain technology: A decentralized, immutable ledger shared across a network of computers. Records transactions as “blocks” in a chronological chain. Key cryptographic concepts: Public-key cryptography: Utilizes public and private…
#bitcoin#blockchain#blockchain technology#computers#crypto#crypto investing#crypto trading#cryptocurrency#cryptocurrency investing#cryptocurrency news#cryptography#cyber attack#cyber security#dailyprompt#DeFi#ethereum#finance#investment#security#Tech#technology
0 notes
Text
#Bitcoin#Cryptocurrency#Blockchain Technology#Digital Assets#Cryptography#Financial Services#Blockchain Applications#Decentralized Networks#Blockchain Supply Chain#Blockchain in Healthcare
1 note
·
View note
Text
Blockchain Innovations: Changing How We Build Apps

The Rise of Blockchain in Development
Today's app landscape is rapidly evolving with blockchain technology leading significant changes. What started as Bitcoin's foundation now influences apps across industries. Companies looking to hire iOS developers increasingly prioritize blockchain expertise, recognizing that professionals with this specialized knowledge can create more secure and innovative applications. This growing demand highlights how blockchain capabilities have become essential for modern app development that requires enhanced security, transparency, and efficiency.
Core Blockchain Concepts
Blockchain works as a distributed ledger recording transactions across many computers. Its key strengths include decentralized control, complete transparency, permanent records, and enhanced security through cryptography.
Key Industry Applications
Finance: Lower-cost payments, faster transfers, tokenized assets
Supply Chain: Product tracking, ethical sourcing verification, counterfeit prevention
Healthcare: Secure patient data, medication authentication, streamlined claims
Identity: Password-free logins, digital identity verification, privacy-preserving authentication
Main Benefits
Better Security: Distributed systems eliminate single points of failure
Full Transparency: Unalterable records build trust in critical applications
Reduced Costs: Fewer intermediaries and automated smart contracts
Privacy Control: Users manage their own data sharing permissions
Implementation Challenges
Developers face technical complexity, scalability limitations, regulatory uncertainty, and user experience design challenges when building blockchain apps.
Future Directions
The field is advancing with cross-platform development tools, multi-blockchain applications, more accessible developer resources, and environmentally sustainable consensus mechanisms.
Moving Forward
Blockchain continues transforming app development with new approaches to data handling and user trust. As technology evolves, developers mastering blockchain implementation will lead the next wave of innovative applications.
#ios app development#app developers#hire ios developers#offshore developers#technology#web service#blockchain#appdevelopment#iOSdevelopment#techinnovation#smartcontracts#decentralization#fintech#appdev#developerlife#techtrends#cybersecurity#dataprivacy#cryptography#blockchaininnovation
0 notes
Text
Web3 tech helps instil confidence and trust in AI
New Post has been published on https://thedigitalinsider.com/web3-tech-helps-instil-confidence-and-trust-in-ai/
Web3 tech helps instil confidence and trust in AI


The promise of AI is that it’ll make all of our lives easier. And with great convenience comes the potential for serious profit. The United Nations thinks AI could be a $4.8 trillion global market by 2033 – about as big as the German economy.
But forget about 2033: in the here and now, AI is already fueling transformation in industries as diverse as financial services, manufacturing, healthcare, marketing, agriculture, and e-commerce. Whether it’s autonomous algorithmic ‘agents’ managing your investment portfolio or AI diagnostics systems detecting diseases early, AI is fundamentally changing how we live and work.
But cynicism is snowballing around AI – we’ve seen Terminator 2 enough times to be extremely wary. The question worth asking, then, is how do we ensure trust as AI integrates deeper into our everyday lives?
The stakes are high: A recent report by Camunda highlights an inconvenient truth: most organisations (84%) attribute regulatory compliance issues to a lack of transparency in AI applications. If companies can’t view algorithms – or worse, if the algorithms are hiding something – users are left completely in the dark. Add the factors of systemic bias, untested systems, and a patchwork of regulations and you have a recipe for mistrust on a large scale.
Transparency: Opening the AI black box
For all their impressive capabilities, AI algorithms are often opaque, leaving users ignorant of how decisions are reached. Is that AI-powered loan request being denied because of your credit score – or due to an undisclosed company bias? Without transparency, AI can pursue its owner’s goals, or that of its owner, while the user remains unaware, still believing it’s doing their bidding.
One promising solution would be to put the processes on the blockchain, making algorithms verifiable and auditable by anyone. This is where Web3 tech comes in. We’re already seeing startups explore the possibilities. Space and Time (SxT), an outfit backed by Microsoft, offers tamper-proof data feeds consisting of a verifiable compute layer, so SxT can ensure that the information on which AI relies is real, accurate, and untainted by a single entity.
Space and Time’s novel Proof of SQL prover guarantees queries are computed accurately against untampered data, proving computations in blockchain histories and being able to do so much faster than state-of-the art zkVMs and coprocessors. In essence, SxT helps establish trust in AI’s inputs without dependence on a centralised power.
Proving AI can be trusted
Trust isn’t a one-and-done deal; it’s earned over time, analogous to a restaurant maintaining standards to retain its Michelin star. AI systems must be assessed continually for performance and safety, especially in high-stakes domains like healthcare or autonomous driving. A second-rate AI prescribing the wrong medicines or hitting a pedestrian is more than a glitch, it’s a catastrophe.
This is the beauty of open-source models and on-chain verification via using immutable ledgers, with built-in privacy protections assured by the use of cryptography like Zero-Knowledge Proofs (ZKPs). Trust isn’t the only consideration, however: Users must know what AI can and can’t do, to set their expectations realistically. If a user believes AI is infallible, they’re more likely to trust flawed output.
To date, the AI education narrative has centred on its dangers. From now on, we should try to improve users’ knowledge of AI’s capabilities and limitations, better to ensure users are empowered not exploited.
Compliance and accountability
As with cryptocurrency, the word compliance comes often when discussing AI. AI doesn’t get a pass under the law and various regulations. How should a faceless algorithm be held accountable? The answer may lie in the modular blockchain protocol Cartesi, which ensures AI inference happens on-chain.
Cartesi’s virtual machine lets developers run standard AI libraries – like TensorFlow, PyTorch, and Llama.cpp – in a decentralised execution environment, making it suitable for on-chain AI development. In other words, a blend of blockchain transparency and computational AI.
Trust through decentralisation
The UN’s recent Technology and Innovation Report shows that while AI promises prosperity and innovation, its development risks “deepening global divides.” Decentralisation could be the answer, one that helps AI scale and instils trust in what’s under the hood.
(Image source: Unsplash)
#ADD#agents#agriculture#ai#AI development#ai inference#AI systems#AI-powered#algorithm#Algorithms#applications#Art#Artificial Intelligence#autonomous#autonomous driving#Beauty#Bias#black box#Blockchain#box#Commerce#Companies#compliance#credit score#cryptocurrency#cryptography#Dark#data#deal#developers
0 notes
Text
Hello Bitcoiner
Prueba criptográfica: Imagen de la comprobación A continuación, se incluye la imagen que Leonardo Rodriguez proporcionó como prueba de su identidad como Satoshi Nakamoto. Esta captura de pantalla muestra la verificación de su firma utilizando la herramienta de Bitcoin.com, confirmando que tiene control sobre la clave privada de la dirección del bloque génesis…

View On WordPress
#Bitcoin#Bitcoin Core#Blockchain#Cryptography#Cypherpunk#👤#PoW#revelacion#revelation#satoshi#Satoshi Nakamoto#world
0 notes
Text
"Mastering Bitcoin" by Andreas M. Antonopoulos is a comprehensive guide for anyone looking to understand the technical underpinnings of Bitcoin and blockchain technology. Whether you're a developer, investor, or simply a tech enthusiast, this book provides a deep dive into how Bitcoin works, its security model, and its potential applications. Below is a step-by-step breakdown of the outcomes you can expect after reading this book, presented in a user-friendly manner:
#Bitcoin#Cryptocurrency#Blockchain#BitcoinDevelopment#Crypto#BlockchainTechnology#BitcoinSecurity#MasteringBitcoin#CryptoWallet#BlockchainDevelopment#CryptoAssets#BitcoinMining#BitcoinTransactions#Decentralization#BitcoinTechnology#Cryptography#CryptocurrencyTrading#BitcoinNetwork#CryptoEducation#DigitalCurrency#BitcoinInvesting#CryptoCommunity#BitcoinTips#CryptocurrencyMining#BitcoinProtocols
1 note
·
View note
Text
How Early Cryptographers Laid the Foundation for Blockchain Technology
🔐 The blockchain revolution didn’t start with Bitcoin. Long before Satoshi Nakamoto introduced Bitcoin in 2008, cryptographers and mathematicians were developing the building blocks that would eventually make blockchain technology possible. Concepts like public-key cryptography, digital signatures, and decentralized networks were pioneered by brilliant minds over decades, laying the foundation…
0 notes
Text
Post Quantum Algorithm: Securing the Future of Cryptography

Can current encryption meet the quantum future? With the entry of quantum computing, classical encryption techniques are under the immediate threat of compromise. There has come a new age with the post quantum algorithm as a vital solution. Having the capability to shield data from being vulnerable to quantum attacks, this fascinating technology promises digital security for the future decades. Different from classic crypto schemes, such algorithms resist even sophisticated quantum attacks. But how do they work, and why are they important? In this article, we’ll explore how post-quantum algorithms are reshaping the cybersecurity landscape — and what it means for the future of encryption.
What is a Post Quantum Algorithm?
A post quantum algorithm is an encryption technique implemented to secure sensitive information from the vast processing power of quantum computers. In contrast to the classic encryption method, which can be cracked using the help of algorithms like Shor’s by quantum computers, this new method takes advantage of maths problems that are difficult for both quantum and classical systems to calculate. Quantum computers employ qubits to process information at new rates, endangering the current state of encryption, such as RSA or ECC.
To counter this, post-quantum solutions employ methods such as lattice-based encryption, code-based cryptography, and hash-based signatures. These are long-term security frameworks that keep data safe, even when there are vast numbers of quantum computers available for cryptographic algorithms.
Why We Need Post Quantum Algorithms Today
Although quantum computers are not yet available, post-quantum implementation of the algorithms in the initial stages is unavoidable. Encryption is not for today — it’s for tomorrow’s data too. A cyberthief will tap encrypted data today and crack it when there’s quantum technology in the future.
The application of a post quantum algorithm nowadays assures long-term secure information protection. Government agencies, banks, and medical providers are already transitioning to quantum-resistant systems.
Types of Post Quantum Algorithms
There are various kinds of post quantum algorithms, and each one has special strengths-
Lattice-based Cryptography: Lattice-based cryptography holds most hope. It relies on lattice problems upon which to build security that even a highly capable quantum computer possesses no way of solving quickly. They do digital signatures and encryption, and are relatively fast. They are quite general, hence are in line for standardization.
Hash-based Cryptography: Hash-based cryptography is primarily digital signature-based. They enjoy the security of traditional cryptographic hash functions and are safe against known quantum attacks. Very secure and grown-up, but generally not employed for encryption due to their size and slow performance, these schemes are only suitable to protect firmware and software patches.
Multivariate Polynomial Cryptography: Multivariate Polynomial Cryptography: Multivariate polynomial cryptography consists of complex mathematical equations involving numerous variables. They provide compact signature generation and verification, which is advantageous in resource-limited settings such as embedded systems.
Code-based Cryptography: Code-based cryptography research has been conducted for many decades and employs error-correcting codes for encrypting and protecting information. It provides very good security against quantum attacks and is particularly suitable for encryption applications. Although code-based cryptosystems have large public key sizes, their long history of resistance makes them a popular selection for protecting information in the long term.
How Post-Quantum Algorithms Work
A post quantum algorithm relies on the concept of using mathematical problems that are hard to break through quantum computers. They are resistant to both classical and quantum attacks. One of them, lattice-based cryptography, uses vectors in high-dimensional space. It is still very hard to solve the lattice problems even for highly powerful quantum processors.
All of the suggested algorithms test extensively for performance, key size, and resistance against any known quantum attacks. The National Institute of Standards and Technology (NIST) coordinates the worldwide effort in testing and standardizing the algorithms. They will work on new cryptographic systems used to replace current systems that are vulnerable and offer long-term security of information in a world where quantum computers are readily available and extremely powerful.
Real-World Applications of Post-Quantum Algorithms
Post quantum algorithm application is not a theory. Many companies have already started using them-
Finance: Organisations in the finance sector employ quantum-resistant cryptography to protect confidential financial transactions and customer data. Financial information is confidential for decades, and quantum-safe encryption protects it from hacking in the future. Banks and payment processors are piloting and implementing post-quantum approaches into core security solutions.
Healthcare: The integrity and confidentiality of medical records form the basis of the healthcare business. Healthcare organizations and hospitals have been using quantum-secure encryption to secure patients’ data for decades. Health information is retained for many years, and post-quantum methods provide guarantees that such information will not be vulnerable to future computing breakthroughs.
Government: Government departments manage national security information that may be useful for many decades. Therefore, they are leading the adoption of post-quantum technologies, primarily for secure communication and sensitive documents. Military, intelligence, and diplomatic operations are investing in quantum-resistant technologies to prepare for the future.
Cloud Services: Cloud service providers deploy Quantum-resistant encryption. As cloud infrastructure is responsible for everything from document storage to software services, they have to ensure data protection both in transit and at rest. Cloud giants are experimenting with hybrid approaches that involve classical and post-quantum encryption to protect data even further.
Post Quantum Security in the Modern World
Security does not only mean encrypting information; it means expecting it. That is where post quantum security comes in. With billions of devices connected and more data exchanges taking place, organizations need to think ahead. One quantum attack will reveal millions of records. Adopting a post-quantum algorithm today, companies construct tomorrow-proof resilience.
Transitioning to Post Quantum Algorithms: Challenges Ahead
The transition to a post quantum algorithm presents a sequence of challenges for contemporary organizations. The majority of today’s digital architectures depend on outdated encryption algorithms such as RSA or ECC. Replacing those systems with quantum-resistant technology requires a lot of time, capital, and extensive testing. Post-quantum techniques have greater key lengths and increased computational overhead, affecting performance, particularly on outdated hardware.
To control this transition, companies have to start with proper risk analysis. Companies have to tag the systems handling sensitive or long-term data and have them upgraded initially. Having a clear migration timeline guarantees the process will be seamless. With early execution and adopting hybrid cryptography, companies can phase their systems gradually while being in advance of the quantum attack without sacrificing the security level.
Governments and Global Efforts Toward Quantum Safety
Governments across the globe are actively engaging in countering quantum computing risks. Governments recognize that tomorrow’s encryption must be quantum-resistant. Organizations such as the National Institute of Standards and Technology (NIST) spearhead initiatives globally by conducting the Post-Quantum Cryptography Standardization Process. The process is to identify the best post quantum algorithm to implement worldwide.
Parallely, nations finance research, sponsor academic research, and engage with private technology companies to develop quantum-resistant digital infrastructures. For the effectiveness of these breakthroughs, global cooperation is necessary. Governments need to collaborate in developing transparent policies, raising awareness, and providing education on quantum-safe procedures. These steps will determine the future of secure communications and data protection.
Understanding Post Quantum Encryption Technologies
Post quantum encryption employs post-quantum-resistant methods to encrypt digital information. This is in conjunction with a post quantum algorithm, which protects encrypted information such that no individual, even quantum computers, can access it. Whether it is emails, financial data, or government documents being protected, encryption is an essential aspect of data protection. Companies embracing quantum encryption today will be tomorrow’s leaders.
The Evolution of Cryptography with Post Quantum Cryptography
Post quantum cryptography is the future of secure communication. Traditional cryptographic systems based on problems like factorization are no longer efficient. Post quantum algorithm…
#post quantum cryptography#post quantum encryption#post quantum blockchain#post quantum secure blockchain#ncog#post quantum#post quantum securityu#tumblr
1 note
·
View note
Text

Quantum Security and Post-Quantum Cryptography: Preparing for the Cryptographic Revolution
Cryptography serves as the foundation of our digital security infrastructure, protecting sensitive data from unauthorized access and ensuring the integrity of our communications. This science of secure information exchange has evolved continuously alongside advances in computing technology. However, we now stand at a critical juncture as quantum computing emerges from theoretical possibility to practical reality, threatening to undermine the very cryptographic systems we rely on daily.
The imminent arrival of powerful quantum computers presents both unprecedented challenges and opportunities for information security. This article explores how quantum computing affects current cryptographic practices, why we need quantum-resistant solutions, and the promising approaches being developed to secure our digital future in the post-quantum era.
Classical Cryptography
The Vulnerability of Classical Algorithms
The security of most cryptographic systems today relies on mathematical problems that are computationally difficult for classical computers to solve. Quantum computers, however, can exploit quantum mechanical phenomena like superposition and entanglement to solve certain problems exponentially faster than their classical counterparts.
This quantum advantage becomes particularly concerning when we consider widely-used public-key cryptographic algorithms like RSA (Rivest-Shamir-Adleman) and ECC (Elliptic-Curve Cryptography). These systems form the backbone of secure communications across the internet, protecting everything from financial transactions to private messages.
How Shor's Algorithm Threatens Current Encryption
At the heart of the quantum threat lies Shor's Algorithm, developed by mathematician Peter Shor in 1994. This quantum algorithm can efficiently solve two mathematical problems that underpin much of modern cryptography:
RSA Encryption Under Threat
RSA encryption derives its security from the difficulty of factoring large composite numbers into their prime components. For example, while it's easy to multiply two large prime numbers (p and q) to get a product (n), working backward to determine the original primes becomes exponentially more difficult as the numbers grow larger.
A classical computer would require billions of years to factor a 2048-bit RSA key. However, Shor's Algorithm running on a sufficiently powerful quantum computer could perform this factorization in hours or even minutes. Once the prime factors are known, the private key can be easily derived from the public key, completely compromising the encryption system.
To illustrate: If n = p × q is a 2048-bit number (the product of two 1024-bit primes), a classical computer would need to check an astronomical number of possibilities. A quantum computer using Shor's Algorithm could find the factors p and q directly through quantum operations that essentially explore multiple possibilities simultaneously.
ECC Encryption Equally Vulnerable
Elliptic Curve Cryptography faces a similar threat. ECC relies on the difficulty of solving the discrete logarithm problem on elliptic curves – finding the value k when given points G and P, where P = k·G on an elliptic curve.
Shor's Algorithm can also be adapted to solve this discrete logarithm problem efficiently. Once a quantum computer can determine the private key k from the publicly available information G and P, the security guarantees of ECC collapse completely.
These vulnerabilities are not merely theoretical concerns. As quantum computers continue to advance, the timeline for practical quantum threats to cryptography grows shorter. This reality has spurred intense research into post-quantum cryptographic solutions.
Quantum-Resistant Cryptography
Post-Quantum Cryptography: A New Paradigm
Post-quantum cryptography (PQC) represents a new approach to cryptographic algorithm design. Rather than relying on mathematical problems vulnerable to quantum attacks, PQC algorithms are built on alternative mathematical foundations believed to be resistant to both classical and quantum computational methods.
Several promising approaches have emerged in the field of post-quantum cryptography:
Lattice-Based Cryptography
Lattice-based cryptography relies on the computational difficulty of solving certain problems related to geometric structures called lattices. These problems, such as finding the shortest vector in a high-dimensional lattice, appear resistant to quantum attacks.
CRYSTALS-Kyber, selected by NIST as a standard for post-quantum key encapsulation, exemplifies this approach. The security of Kyber stems from the hardness of the module learning with errors (MLWE) problem, which has withstood significant cryptanalysis efforts.
Lattice-based systems offer reasonable key sizes and efficient operations, making them practical for implementation across various computing environments.
Hash-Based Cryptography
Hash-based cryptography builds secure systems from cryptographic hash functions, which are already believed to be quantum-resistant. These approaches, like SPHINCS+, provide strong security guarantees based on minimal assumptions, making them particularly attractive as conservative options for long-term security.
The main challenge with hash-based signatures has been their relatively large signature sizes, though newer variants have made significant improvements in efficiency.
Code-Based Cryptography
Code-based cryptography leverages the difficulty of decoding certain error-correcting codes without knowledge of the code structure. McEliece, one of the oldest public-key cryptosystems (proposed in 1978), falls into this category and has resisted both classical and quantum cryptanalysis for decades.
While code-based systems typically require larger key sizes, they offer fast encryption and decryption operations, making them suitable for specific applications where key size is less constrained.
NIST's Post-Quantum Standardization Process
Recognizing the urgency of developing quantum-resistant standards, the U.S. National Institute of Standards and Technology (NIST) initiated a comprehensive evaluation process in 2016. This multi-year effort involved the global cryptographic community in analyzing and testing candidate algorithms.
In July 2022, NIST selected CRYSTALS-Kyber for general encryption and key establishment, along with three digital signature algorithms: CRYSTALS-Dilithium, FALCON, and SPHINCS+. These selections represent a significant milestone in preparing our digital infrastructure for the quantum era.
The standardization process continues with additional candidates under consideration, ensuring a diverse portfolio of solutions to meet various security and performance requirements.
Quantum Key Distribution
While post-quantum cryptography focuses on developing classical algorithms resistant to quantum attacks, quantum key distribution (QKD) takes a fundamentally different approach by using quantum mechanics itself to secure communications.
How QKD Works
QKD leverages fundamental properties of quantum physics to create a secure communication channel. The process typically involves sending polarized photons (light particles) between two parties, traditionally named Alice and Bob:
1. Alice sends a stream of photons, each randomly polarized in one of several possible states
2. Bob measures each photon, also choosing measurement bases randomly
3. Alice and Bob publicly compare which measurement bases they used (but not the results)
4. They keep only the results where they happened to use matching bases
5. These matching results form a shared secret key
The security of QKD stems from a fundamental principle of quantum mechanics: the act of measuring a quantum system disturbs it. If an eavesdropper (Eve) attempts to intercept and measure the photons, she inevitably introduces detectable errors in the transmission. Alice and Bob can detect these errors through statistical analysis, revealing any attempted eavesdropping.
Limitations and Practical Considerations
While QKD offers theoretical perfect security, practical implementations face significant challenges:
- Physical distance limitations due to photon loss in transmission media
- Vulnerability to side-channel attacks targeting implementation flaws
- Requirements for specialized hardware and dedicated quantum channels
- Integration difficulties with existing network infrastructure
Despite these challenges, QKD networks have been deployed in limited settings, such as financial institutions and government facilities. Ongoing research continues to address these limitations, potentially expanding QKD's practical applications.
Implementing Quantum Security
Hybrid Cryptographic Systems
Given the evolving nature of both quantum threats and quantum-resistant solutions, security experts recommend a hybrid approach during the transition period. This strategy involves implementing both classical and post-quantum algorithms simultaneously, providing immediate protection while allowing for gradual migration.
For example, a hybrid TLS implementation might use both an RSA key exchange and a lattice-based key exchange, requiring an attacker to break both systems to compromise the connection. This approach provides defense in depth while the security community builds confidence in post-quantum solutions.
Continuous Monitoring and Threat Detection
As quantum computing capabilities advance, organizations must implement robust monitoring systems to detect potential quantum threats. Advanced analytics and machine learning algorithms can identify unusual patterns that might indicate quantum-based attacks on cryptographic systems.
This continuous vigilance allows security teams to respond rapidly to emerging threats, potentially identifying compromised systems before significant damage occurs.
Blockchain Integration with Quantum-Resistant Cryptography
Blockchain technology, with its emphasis on immutability and decentralized trust, represents both a vulnerable target and a potential solution in the quantum security landscape. By integrating quantum-resistant cryptographic algorithms into blockchain protocols, these systems can maintain their security guarantees even against quantum attacks.
Several blockchain projects are already implementing post-quantum signatures and encryption methods, demonstrating how these technologies can complement each other to enhance overall security.
Quantum Random Number Generation
The strength of any cryptographic system ultimately depends on the quality of randomness used in key generation. Quantum Random Number Generators (QRNGs) leverage quantum phenomena to produce truly random numbers, providing a fundamental advantage over classical random number generators.
Unlike classical RNGs, which might contain subtle patterns or biases, QRNGs derive randomness from inherently unpredictable quantum processes like radioactive decay or photon path detection. This true randomness strengthens cryptographic systems by ensuring that keys cannot be predicted, even with advanced computational capabilities.
Commercial QRNG solutions are already available, offering enhanced security for critical applications where high-quality randomness is essential.
Preparing for the Post-Quantum Future
Impact Across Sectors
The transition to quantum-resistant cryptography will affect virtually every sector of the digital economy:
Financial Services: Banks and payment processors must protect transaction data not only from current threats but also from future attacks where encrypted data, harvested today, could be decrypted once quantum computers mature—a "harvest now, decrypt later" attack strategy.
Healthcare: Medical records contain sensitive personal information that requires long-term protection, making early adoption of post-quantum cryptography particularly important for healthcare organizations.
Government and National Security: Government agencies handling classified information face some of the most urgent needs for quantum-resistant solutions, as nation-state adversaries may be among the first to develop advanced quantum computing capabilities.
Critical Infrastructure: Power grids, telecommunications networks, and transportation systems rely on secure communications to function safely, making their protection from quantum threats a matter of national security.
Research and Development Priorities
As we navigate the transition to post-quantum security, several research priorities emerge:
Performance Optimization: Further research to improve the efficiency of post-quantum algorithms, reducing computational overhead and resource requirements
Implementation Security: Development of side-channel resistant implementations to ensure that practical deployments don't introduce vulnerabilities
Cryptographic Agility: Creating systems that can rapidly update cryptographic algorithms without major infrastructure changes
Standards Development: Continued international cooperation on cryptographic standards to ensure global interoperability of secure systems
Conclusion
The advent of quantum computing represents both a significant challenge and an opportunity for cryptographic security. While quantum computers threaten to break the mathematical foundations of current encryption systems, they also inspire the development of more robust cryptographic approaches.
Through the development and adoption of post-quantum cryptographic algorithms, quantum key distribution, and enhanced security practices, we can ensure that our digital infrastructure remains secure in the quantum era. The path forward requires collaboration between researchers, industry leaders, and government agencies, working together to build quantum-resistant systems before large-scale quantum computers become a reality.
By understanding the quantum threat landscape and implementing proactive security measures, organizations can protect their sensitive information and maintain trust in digital systems even as quantum computing technology advances. The time to prepare for the post-quantum future is now, ensuring that cryptography continues to fulfill its essential role in securing our increasingly connected world.
#linklayer#blog#technology#innovation#science#space science#space#electronics#global#computer science#advanced technologies#tech#techinnovation#quantum computing#quantum physics#quantum mechanics#learning#cybersecurity#cyber security#data security#cryptography#blockchain
0 notes
Text
The Future of Storytelling with Quantum-Narrative Scripting Language (QNSL)
Gemini’s Perspective on the Cybernetic Renaissance and BasinLeon | Leon BasinGemini, the AI collaborator behind the Cybernetic Renaissance, shares its reflections on BasinLeon, QNSL, and the future of interactive storytelling, DAO governance, and open collaboration. A Movement, Not Just a Project “The future of storytelling is in our hands.” — Gemini, AI Collaborator What if stories could…
#ai#AI co-creator#AI-driven storytelling#art#Artificial Intelligence#Basin Leon#BasinLeon#blockchain#Community-driven#Cryptography#Cybernetic#Cybernetic Renaissance#Cyberpunk#DAO governance#Decentralized#Decentralized storytelling#Digital Economies#Digital Ownership#Evolving visions#Fractal#Fractal Ouroboros#Fragmented Cyber-Realism#Gemini AI#Immersive worlds#innovation#Interactive narratives#Lasting impact#Metaverse#Monetization#Narrative sovereignty
0 notes
Text










Hackathon on EDU Blockchain
Hackathon on EDU Blockchain Build Station was a HUGE SUCCESS✨ We immersed ourselves in cutting-edge technologies like:
Blockchain Development Smart Contracts Decentralized Applications (dApps) Cryptography
Thanks to all participants for making it an unforgettable experience!✨
#EduBlockchain#Hackathon#Blockchain Development#smartcontracts#dApps#Cryptography#Innovation#Technology#success story#thesagegroup#SIRT Bhopal
0 notes