#cybersecurity project
Explore tagged Tumblr posts
Text
In the age of AI, authentication shouldn't be a static barrier; it should be an intelligent, adaptive, and engaging experience. Within @leonbasinwriter Intelligence Singularity, access is not simply granted—it's earned through a dynamic interplay with AI itself.
#adaptive authentication#ai#AI Security#AI security authentication system access control#AI-driven authentication#Artificial Intelligence#authentication challenge#chatgpt#Claude#cybersecurity project#digital-marketing#Express.js#intelligence singularity#Javascript#LLM#multi-layered authentication#nft#Node.js#OpenAI#passwordless authentication#portfolio project#prompt engineering#proof of concept#research project#technology#user experience#web security#Web3#zero-trust security
0 notes
Text
As we enter back into an era where technology is used primarily as a weapon against you by the United States and Russian governments, (welcome back 1980s! 😍) let’s go over some tips to consider if you are a queer, bipoc, or otherwise an “enemy from within” as trump so lovingly and hypocritically put it, to protecting your identity and privacy through the internet so that you can continue to resist this cultural shift safely and resiliently!
• stop posting identifying information on social media like your full name, place of residence, and pictures of yourself or other at risk people, and go back and delete posts in which you might’ve already.
• disable location tracking services and camera and mic access to apps, services, or websites that you know to be compromised by the influence of shady overseers, such as X, Instagram, Facebook, Google, and TikTok. I know it’s convenient to use these but it’s a MAJOR security hazard.
• Turn your phone COMPLETELY off when discussing sensitive subjects with friends or when you are making plans of resistance and gathering your communities, or when you are discussing personal feelings on such subjects with family, friends, or a doctor/therapist. Basically all mobile phones now have live mics that are constantly listening to you.
• Create a new email under a fake name if you haven’t already to use as your primary email address, in order to further protect your true identity.
• use an alternative browser like DuckDuckGo or brave in place of google, preferably with a VPN on top of it to even further secure your browsing history and to bypass potential IP blocks of websites from the government.
• if you want to watch YouTube and don’t want a recording of your watch history, log out of your account and watch that way, preferably you would just delete your account entirely but I understand why some might not want to.
• pirate content from streaming services via piracy websites, again so that your watch history can’t be used to make assumptions about you if that data were ever sold to the government.
These are obviously just some of the ways to bypass data collection and ti protect your real identity online, but there are many others I’m sure I’m not aware of. Please add to this if you can, and stay safe out there, because anything you say can and will be used against you in the future of this country. But: We have survived this kind of shit before, we can again, if we are careful. Loose lips sink ships, and that goes for the internet as well.
#online privacy#privacy#data privacy#social media#identity protection#oppression#big brother is watching you#lgbtq community#bipoc#trans#technology#cybersecurity#anti tech#net neutrality#trump regime#fdt#fuck donald trump#project 2025#fuck the gop#maga cult#Reaganism#trumpism#politics#us politics
28 notes
·
View notes
Text
I've been complimented on my handwriting 10 different times by 10 different people JUST this past week alone so I think that's a sign I should rb a handwriting-related meme on here,
#tbd.#◜✧ . ❪ ooc. ❫#I'm currently juggling the crafting of 3 project plans due tomorrow girl help. girl. Help Me Girl 😭 ADSJSAHDSAGJ#The topics are wholly unrelated too it's hilarious. I'm over here discussing cybersecurity 4 children; fascism; then EU values/competences#Imagine an exhausted guy with 5000000 papers fluttering around him in every direction you look. That's me rn I fear#Alternative imagination exercise: Imagine a guy writing on paper w 1 hand; writing in docs w the other & holding a phone w his shoulder#(OUGHHH Ango kinnie against my will 😭😭😭)#Staring at my handwriting reminded me abt how odd it was that ppl from diff places w ZERO relation between each other casually decided#that this past week was Compliment Chris' Handwriting Week. Hence the handwriting memes popping up in my head ADJASHDASGDJ#I remember a few existed ageees ago. I'll see if I can find them again & we'll both see if they'll be ic; hc or pos/ooc then!
9 notes
·
View notes
Text
DIASPORAFOUNDATION.ORG


#JOIN THE FEDIVERSE#the diaspora project#decentralized#social media#fediverse#diaspora#web3#internet privacy#cybersecurity#fedi#social networks
12 notes
·
View notes
Text
John Nichols at The Nation:
Donald Trump has made no secret of his determination to govern as a “dictator” if he regains the presidency, and that’s got his critics warning that his reelection would spell the end of democracy. But Trump and his allies are too smart to go full Kim Jong Un. Rather, the former president’s enthusiasm for the authoritarian regimes of Russia’s Vladimir Putin, Turkey’s Tayyip Erdoğan, and Hungary’s Viktor Orbán suggests the models he would build on: managing elections to benefit himself and his Republican allies; gutting public broadcasting and constraining press freedom; and undermining civil society. Trump, who famously demanded that the results of Georgia’s 2020 presidential voting be “recalculated” to give him a win, wants the trappings of democracy without the reality of electoral consequences. That’s what propaganda experts Edward Herman and Frank Brodhead once described as “demonstration elections,” in which, instead of actual contests, wins are assured for the authoritarians who control the machinery of democracy. The outline for such a scenario emerges from a thorough reading of Project 2025’s Mandate for Leadership, which specifically proposes a Trump-friendly recalculation of the systems that sustain American democracy. The strategy for establishing an American version of Orbán’s “illiberal democracy” is not spelled out in any particular chapter of Mandate. Rather, it is woven throughout the whole of the document, with key elements appearing in the chapters on reworking the Department of Homeland Security (DHS), the Federal Communications Commission (FCC), and the Federal Election Commission (FEC). In the section on the DHS, for instance, there’s a plan to eliminate the ability of the agency that monitors election security to prevent the spread of disinformation about voting and vote counting.
How serious a threat to democracy would that pose? Think back to November 2020, when Trump was developing his Big Lie about the election he’d just lost. Trump’s false assertion that the election had been characterized by “massive improprieties and fraud” was tripped up by Chris Krebs, who served as director of the Cybersecurity and Infrastructure Security Agency (CISA) in the DHS. The Republican appointee and his team had established a 24/7 “war room” to work with officials across the country to monitor threats to the security and integrity of the election. The operation was so meticulous that Krebs could boldly announce after the voting was finished: “America, we have confidence in the security of your vote, you should, too.” At the same time, his coordinating team declared, “The November 3rd election was the most secure in American history.” This infuriated Trump, who immediately fired the nation’s top election security official.
In Mandate’s chapter on the DHS, Ken Cuccinelli writes, “Of the utmost urgency is immediately ending CISA’s counter-mis/disinformation efforts. The federal government cannot be the arbiter of truth.” Cuccinelli previously complained that CISA “is a DHS component that the Left has weaponized to censor speech and affect elections.” As for the team that worked so successfully with Krebs to secure the 2020 election, the Project 2025 document declares that “the entirety of the CISA Cybersecurity Advisory Committee should be dismissed on Day One.” The potential impact? “It’s a way of emasculating the agency—that is, it prevents it from doing its job,” says Herb Lin, a cyber-policy and security scholar at Stanford’s Center for International Security and Cooperation.
This is just one way that Project 2025’s cabal of “experts” is scheming to thwart honest discourse about elections and democracy. A chapter on public broadcasting proposes to defund the Corporation for Public Broadcasting as part of a larger plan to upend NPR, PBS, and “other public broadcasters that benefit from CPB funding, including the even-further-to-the Left Pacifica Radio and American Public Media.” More destabilizing than the total funding cut that Project 2025 entertains is a parallel plan to end the status of NPR and Pacifica radio stations as “noncommercial education stations.” That could deny them their current channel numbers at the low end of the radio spectrum (88 to 92 FM)—a move that would open prime territory on the dial for the sort of religious programming that already claims roughly 42 percent of the airwaves that the FCC reserves for noncommercial broadcasting. And don’t imagine that the FCC would be in a position to write new rules that guard against the surrender of those airwaves to the Trump-aligned religious right.
[...]
While project 2025 seeks to rewire the FCC to favor Trump’s allies, it also wants to lock in dysfunction at the Federal Election Commission, the agency that is supposed to govern campaign spending and fundraising. Established 50 years ago, the FEC has six members—three Republicans and three Democrats—who are charged with overseeing the integrity of federal election campaigns. In recent years, however, this even partisan divide has robbed the FEC of its ability to act because, as a group of former FEC employees working with the Campaign Legal Center explained, “three Commissioners of the same party, acting in concert, can leave the agency in a state of deadlock.” As the spending by outside groups on elections “has exponentially increased, foreign nationals and governments have willfully manipulated our elections, and coordination between super PACs and candidates has become commonplace,” the former employees noted. Yet “the FEC [has] deadlocked on enforcement matters more often than not, frequently refusing to even investigate alleged violations despite overwhelming publicly available information supporting them.”
John Nichols wrote in The Nation about how Project 2025’s radical right-wing wishlist of items contains plans to wreck and subvert what is left of America’s democracy.
See Also:
The Nation: June 2024 Issue
#John Nichols#The Nation#Project 2025#Donald Trump#Authoritarianism#FCC#FEC#Federal Elections Commission#Federal Communications Commission#Corporation for Public Broadcasting#Cybersecurity and Infrastructure Security Agency#Chris Krebs
25 notes
·
View notes
Text
Skidaddle skidoodle

Wednesday, 11/22/2023 ❄️
I have now blasted your retinas with an ungodly amount of light, you're welcome. Anyways, this is the latest iteration of my portfolio... still haven't gotten around to actually coding it though. I'm thinking I should probably code my website in WordPress to be safe(r). Knowing me I'd probably unintentionally attract at least one person that will attempt an SQL injection or something. Speaking of which, I got sidetracked and now I'm learning about basic cybersecurity over at TryHackMe.
53 notes
·
View notes
Text
Java Developer-Full stack with React.js
Job title: Java Developer-Full stack with React.js Company: Adecco Job description: Java Developer – Full Stack (Java 21 / React.js) Location: London (Hybrid – 3 days onsite) Contract: 6-Month Contract…-office operations You’ll play a key role in building full–stack solutions using Java 21 and React.js, collaborating closely… Expected salary: Location: London Job date: Thu, 17 Jul 2025 00:39:43…
#5G#Aerospace#audio-dsp#business-intelligence#cloud-computing#cloud-native#CRM#Crypto#Cybersecurity#deep-learning#digital-twin#embedded-systems#erp#fintech#full-stack developer#gcp#hybrid-work#Java#project-management#regtech#remote-jobs#robotics#rpa#SoC#system-administration#technical-writing#telecoms#uk-jobs#visa-sponsorship
2 notes
·
View notes
Text
Building Your Own Cyberdeck:
What do you do when you have extra time between a job and your next? How about building your own Cyberdeck? Check this article out for tips on building your own!
The Ultimate Hacker Project For aspiring cybersecurity professionals, cyberpunk enthusiasts, hardware hackers, and circuit benders, one of the best hands-on projects you can take on is building your own cyberdeck. Despite overwhelming schedules full of training programs, full time work weeks, sometimes limited funds, and the endless possibilities of hardware combinations, many fans of the…

View On WordPress
#Cyber#Cyber Security#cyberdeck#cyberpunk#Cybersecurity Specialist#Ethical Hacking#hack#hacker#infosec#IT#IT professional#mobile#mobile computer#Pentesting#programming#project
31 notes
·
View notes
Text
Project Management Certificate (Undergraduate)
(no propaganda submitted)
BS in Cybersecurity
(no propaganda submitted)
#tumblr tournament#poll#University of Pheonix#round 0#Project Management Certificate (Undergraduate)#BS in Cybersecurity
2 notes
·
View notes
Text
Toward a code-breaking quantum computer
New Post has been published on https://thedigitalinsider.com/toward-a-code-breaking-quantum-computer/
Toward a code-breaking quantum computer
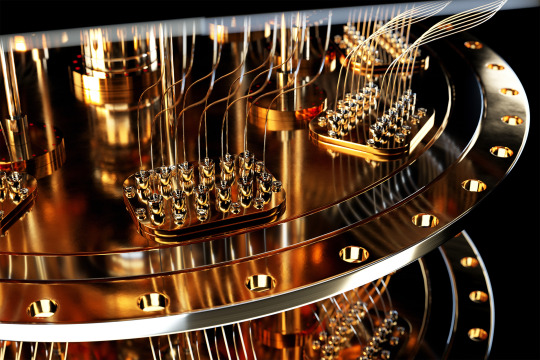

The most recent email you sent was likely encrypted using a tried-and-true method that relies on the idea that even the fastest computer would be unable to efficiently break a gigantic number into factors.
Quantum computers, on the other hand, promise to rapidly crack complex cryptographic systems that a classical computer might never be able to unravel. This promise is based on a quantum factoring algorithm proposed in 1994 by Peter Shor, who is now a professor at MIT.
But while researchers have taken great strides in the last 30 years, scientists have yet to build a quantum computer powerful enough to run Shor’s algorithm.
As some researchers work to build larger quantum computers, others have been trying to improve Shor’s algorithm so it could run on a smaller quantum circuit. About a year ago, New York University computer scientist Oded Regev proposed a major theoretical improvement. His algorithm could run faster, but the circuit would require more memory.
Building off those results, MIT researchers have proposed a best-of-both-worlds approach that combines the speed of Regev’s algorithm with the memory-efficiency of Shor’s. This new algorithm is as fast as Regev’s, requires fewer quantum building blocks known as qubits, and has a higher tolerance to quantum noise, which could make it more feasible to implement in practice.
In the long run, this new algorithm could inform the development of novel encryption methods that can withstand the code-breaking power of quantum computers.
“If large-scale quantum computers ever get built, then factoring is toast and we have to find something else to use for cryptography. But how real is this threat? Can we make quantum factoring practical? Our work could potentially bring us one step closer to a practical implementation,” says Vinod Vaikuntanathan, the Ford Foundation Professor of Engineering, a member of the Computer Science and Artificial Intelligence Laboratory (CSAIL), and senior author of a paper describing the algorithm.
The paper’s lead author is Seyoon Ragavan, a graduate student in the MIT Department of Electrical Engineering and Computer Science. The research will be presented at the 2024 International Cryptology Conference.
Cracking cryptography
To securely transmit messages over the internet, service providers like email clients and messaging apps typically rely on RSA, an encryption scheme invented by MIT researchers Ron Rivest, Adi Shamir, and Leonard Adleman in the 1970s (hence the name “RSA”). The system is based on the idea that factoring a 2,048-bit integer (a number with 617 digits) is too hard for a computer to do in a reasonable amount of time.
That idea was flipped on its head in 1994 when Shor, then working at Bell Labs, introduced an algorithm which proved that a quantum computer could factor quickly enough to break RSA cryptography.
“That was a turning point. But in 1994, nobody knew how to build a large enough quantum computer. And we’re still pretty far from there. Some people wonder if they will ever be built,” says Vaikuntanathan.
It is estimated that a quantum computer would need about 20 million qubits to run Shor’s algorithm. Right now, the largest quantum computers have around 1,100 qubits.
A quantum computer performs computations using quantum circuits, just like a classical computer uses classical circuits. Each quantum circuit is composed of a series of operations known as quantum gates. These quantum gates utilize qubits, which are the smallest building blocks of a quantum computer, to perform calculations.
But quantum gates introduce noise, so having fewer gates would improve a machine’s performance. Researchers have been striving to enhance Shor’s algorithm so it could be run on a smaller circuit with fewer quantum gates.
That is precisely what Regev did with the circuit he proposed a year ago.
“That was big news because it was the first real improvement to Shor’s circuit from 1994,” Vaikuntanathan says.
The quantum circuit Shor proposed has a size proportional to the square of the number being factored. That means if one were to factor a 2,048-bit integer, the circuit would need millions of gates.
Regev’s circuit requires significantly fewer quantum gates, but it needs many more qubits to provide enough memory. This presents a new problem.
“In a sense, some types of qubits are like apples or oranges. If you keep them around, they decay over time. You want to minimize the number of qubits you need to keep around,” explains Vaikuntanathan.
He heard Regev speak about his results at a workshop last August. At the end of his talk, Regev posed a question: Could someone improve his circuit so it needs fewer qubits? Vaikuntanathan and Ragavan took up that question.
Quantum ping-pong
To factor a very large number, a quantum circuit would need to run many times, performing operations that involve computing powers, like 2 to the power of 100.
But computing such large powers is costly and difficult to perform on a quantum computer, since quantum computers can only perform reversible operations. Squaring a number is not a reversible operation, so each time a number is squared, more quantum memory must be added to compute the next square.
The MIT researchers found a clever way to compute exponents using a series of Fibonacci numbers that requires simple multiplication, which is reversible, rather than squaring. Their method needs just two quantum memory units to compute any exponent.
“It is kind of like a ping-pong game, where we start with a number and then bounce back and forth, multiplying between two quantum memory registers,” Vaikuntanathan adds.
They also tackled the challenge of error correction. The circuits proposed by Shor and Regev require every quantum operation to be correct for their algorithm to work, Vaikuntanathan says. But error-free quantum gates would be infeasible on a real machine.
They overcame this problem using a technique to filter out corrupt results and only process the right ones.
The end-result is a circuit that is significantly more memory-efficient. Plus, their error correction technique would make the algorithm more practical to deploy.
“The authors resolve the two most important bottlenecks in the earlier quantum factoring algorithm. Although still not immediately practical, their work brings quantum factoring algorithms closer to reality,” adds Regev.
In the future, the researchers hope to make their algorithm even more efficient and, someday, use it to test factoring on a real quantum circuit.
“The elephant-in-the-room question after this work is: Does it actually bring us closer to breaking RSA cryptography? That is not clear just yet; these improvements currently only kick in when the integers are much larger than 2,048 bits. Can we push this algorithm and make it more feasible than Shor’s even for 2,048-bit integers?” says Ragavan.
This work is funded by an Akamai Presidential Fellowship, the U.S. Defense Advanced Research Projects Agency, the National Science Foundation, the MIT-IBM Watson AI Lab, a Thornton Family Faculty Research Innovation Fellowship, and a Simons Investigator Award.
#2024#ai#akamai#algorithm#Algorithms#approach#apps#artificial#Artificial Intelligence#author#Building#challenge#classical#code#computer#Computer Science#Computer Science and Artificial Intelligence Laboratory (CSAIL)#Computer science and technology#computers#computing#conference#cryptography#cybersecurity#defense#Defense Advanced Research Projects Agency (DARPA)#development#efficiency#Electrical Engineering&Computer Science (eecs)#elephant#email
5 notes
·
View notes
Text
GREAT OPPORTUNITY! This is the link to the American Dream Academy! It's an official partnership between the Milken Center and Coursera to provide learners FREE access to Coursera courses from top companies like IBM, Meta, Google, Amazon, Intuit, and Salesforce focused on in-demand skills like data analysis, IT support, cybersecurity, project management, UX Design, front-end and back-end development, sales operations and development, cloud solutions architecture, bookkeeping, and digital marketing.
They also provide FREE courses that will help you build soft skills such as communications, critical thinking, leadership, financial literacy, human skills and growth mindset.
I'm personally taking a bunch of courses myself and I can fully say that this is legit! I'm taking Frontend Development and Backend Development from Meta and the UX Design Course from Google. It's great because usually these courses cost a lot of money but I'm doing it all and getting certified for FREE! I already have a few certificates under my belt that I can use on my resume! 😎
Unfortunately, the American Dream Academy program will be ending in 2024 and the last day to sign up for this is NOVEMBER 1st! (They extended the deadline) Make sure you sign up by this date so you don't miss out! 💞
#coding#codeblr#web development#programming#ux desgin#digital marketing#data analysis#project management#cybersecurity#cloud solutions#courses#free courses#resources
11 notes
·
View notes
Text
“Ultimate Cybersecurity, Dario Raffa. Okay. I’m done now, right?”

Meet Dario Raffa, The Ultimate Cybersecurity.
Age: 20
Pronouns: He/Himself or It/Itself
Nationality: Italian
Likes: The Internet, Coding, Chocolate Pudding
Dislikes: Being Ordered Around, Chalkboards, Laundry
Birthday: November 15th
Appearance: Dario has a very square body with long arms. He stands at 5’9”, with sandy blonde hair pulled into a low bun and black eyes, commented by some stubble. He also has a gray hearing aid on his right ear. He has a rainbow sweater that’s tucked into his straight cut jeans, and wears a teal checkered over it. Finally, he wears burger socks and white slide-ons.
Backstory: Dario is a hermit. After the tragic death of his parents, how could he not be? Inside his room was safe, controlled, fun. His sister found this complete nonsense, since she was the one paying for their apartment, and she had to be the one to tell Dario to take care of himself. She could hardly stand the guy, until a new car appeared on her doorstep, courtesy of Dario. See, from the outside, Dario might look like a modern day slob, but what he was actually doing on his computer was huge. He was apart of group called “Saving U Corp.”, a group of internet vigilantes playing Robin Hood. He’s taken down many corrupt cooperations, without even leaving a hint that his group was the one who caused it. And yeah, he made a pretty penny from it too.
#akeda amuesments#danganronpa#danganronpa akeda amuesments#fanganronpa#fangan#fan project#dario raffa#Ultimate cybersecurity
3 notes
·
View notes
Text
What is Google’s Project Nimbus and why is it controversial?
Google’s Project Nimbus is a cloud computing contract that Google and Amazon signed with the Israeli government in April 2021. With a hefty price tag of $1.2 billion, this collaboration between tech behemoths and the Israeli government was poised to revolutionize the way data is stored and processed. But not all is sunny with Project Nimbus; it’s a project that has become as controversial as it…

View On WordPress
#Amazon#Artificial intelligence#Cybersecurity#Data Privacy#Digital Transformation#Google#Government Contracts#Human Rights#Machine Learning#Project Nimbus#Tech Controversy#Tech Ethics
2 notes
·
View notes
Text
The Importance of Regular IT Maintenance
In today’s fast-paced digital landscape, neglecting regular IT maintenance can leave your business vulnerable to security threats, downtime, and performance issues. Techblokes highlights how scheduled updates, system health checks, data backups, and proactive monitoring can prevent costly disruptions and enhance operational efficiency.
By investing in ongoing IT maintenance, businesses not only protect their digital infrastructure but also ensure long-term growth, reduced risk, and optimal performance. Whether you’re a small business or a growing enterprise, regular IT upkeep is no longer optional — it’s essential.
Need expert IT support? Contact Techblokes today at +61 449 130 194 and let our team keep your systems secure, stable, and future-ready. Read More:
0 notes
Text
Project Analyst
Job title: Project Analyst Company: Sage Publications Job description: desired. Project Management, Business Analysis, and/or Scrum Master certification If you have a disability and need… Expected salary: Location: London Job date: Sun, 29 Jun 2025 00:56:05 GMT Apply for the job now!
#5G#agritech#Automotive#Blockchain#business-intelligence#CRM#Cybersecurity#data-science#ethical-hacking#fintech#full-stack#generative AI#GIS#iOS#marine-tech#metaverse#NFT#NLP#no-code#project-management#prompt-engineering#regtech#robotics#rpa#Salesforce#Scrum Master#site-reliability#visa-sponsorship#vr-ar
2 notes
·
View notes
Text
5 Must-Have Certifications for Tech Jobs in 2025
In a world where AI is rewriting job descriptions and cloud computing is reshaping how companies operate, one thing remains clear: skills speak louder than degrees. And in tech, certifications are your loudest voice. Whether you’re just entering the tech space, pivoting careers, or chasing that promotion, these five industry-recognized certifications will boost your credibility, sharpen your…
#agile project management#cloud certification guide#cybersecurity jobs#Microsoft Azure learning#tech certifications 2025
0 notes