#delphix
Explore tagged Tumblr posts
Text
4 Biggest Risks of Non-Compliance With Data Privacy Regulations
Not complying with data privacy laws can jeopardize an organization’s cybersecurity, finances, reputation, and more.
Data Compliance is non-negotiable. Here are the risks of non-compliance

On Dec. 9, 2022, an important data privacy compliance deadline will pass for organizations that process U.S. consumers’ financial data. Under the Gramm-Leach-Bliley Act (GLBA)’s updated Safeguards Rule, organizations have until that day to comply with a series of data security practices that the landmark U.S. financial data privacy law has mandated, which include:
Releasing periodic reports to boards of directors and governing bodies
Instituting secure software development practices
Identifying and managing data based on risk
Implementing and reviewing data access controls
Encrypting data both in transit and at rest
Establishing secure procedures for disposing data
The GLBA is just one of many regulations across the globe with substantial privacy protections— a group that includes the European Union’s General Data Protection Regulation (GDPR), Brazil’s General Data Protection Law (LGPD), and the United States’ Health Insurance Portability and Accountability Act (HIPAA). These laws mandate that organizations within their jurisdiction employ effective data privacy practices to protect personally identifiable information (PII), or what the Safeguards Rule calls non-public personal information (NPI).
The stakes for data privacy compliance are high, as non-compliance can result in devastating consequences. Organizations can expect to face four major risks for non-compliance with data privacy laws: inadequate cybersecurity, expensive fines, high individual penalties, and reputational damage.
The Compliance (Cyber)Security Blanket
Compliance and data security go hand-in-hand— if an organization’s systems don’t comply with data privacy standards, there’s a good chance that its data security could be lacking. After all, a major component of data privacy on your compliance is ensuring that consumers’ data is safe from the hands of bad actors who could use the data nefariously.
For instance, the GLBA requires financial institutions to, “protect against any reasonably anticipated threats or hazards” as well as “unauthorized access to, or use of,” customers’ data. The Federal Financial Institutions Examination Council, which audits financial institutions, dictates that these institutions should use strong encryption and key management practices.
These practices, of course, improve compliance and security alike. So, even if your organization doesn’t get slapped with a data privacy lawsuit, non-compliance with data privacy regulations reflects poor data controls, a significant liability for your organization.
Non-Compliance Fines Aren’t Fine
If your organization violates a data privacy law, a punitive fine is almost guaranteed. The severity of fines cover a wide spectrum. For instance, every GLBA violation carries a fine of up to $100,000, while LGPD infractions carry a financial penalty of up to 2 percent of the sanctioned organization’s gross revenue, with a maximum fine of 50 million Brazilian Reals (about $9.7 million).
GDPR fines are even more grave— every GDPR violation can cost up to 4 percent of a company’s annual global revenues or €20 million (about $22 million)— whichever is highest. So far, Amazon Europe Core S.a.r.l. incurred the largest-ever GDPR fine when the Luxembourg National Commission for Data Protection levied a whopping $746 million fine on the technology giant for infringements related to Amazon’s advertising targeting system. Even moderate GDPR fines can exceed $10 million.
The Big House Awaits
When a data privacy law is broken, the organization may not be the only party held liable (if at all). While it varies case-by-case, employees within an infringing organization are sometimes penalized, as well.
These penalties can include individual fines and jail time— and like fines, they encompass a wide spectrum of severity. For instance, one individual who violated the U.K.’s Data Protection Act (DPA) in 2018 by stealing and selling customer records to rogue organizations incurred a 6- month prison sentence. Individual penalties under GLBA, meanwhile, are much higher—each violation of the Act can result in fines of up to $10,000 for directors and officers, license revocations, and up to five years of imprisonment.
The new Safeguards Rule requires covered entities to report annually to their boards of directors, effectively putting the protection of PII/NPI directly onto board agendas. So, while prison sentences for GLBA non-compliance are rare, accountable organizations’ board members in particular should be concerned with upholding the interests of their stakeholders via compliance.
Your Reputation Precedes You
The penalties and gravity of a cybersecurity breach that a noncompliant organization experiences can, of course, be measured. Less quantifiable though, is the reputational harm that a non-compliance lawsuit can inflict on organizations. Today’s omnipresent digital media presence ensures that word travels far and fast when organizations break the law— and as Warren Buffett famously said, “it takes 20 years to build a reputation and five minutes to ruin it.”
Reputational damage that an organization suffers as a result of any kind of lawsuit can manifest in two ways, as one business and commercial law firm notes. On the one hand, a lawsuit can hurt the organization’s reputation with the public— yet on the other hand, it can also dissuade companies from doing business with the defendant organization. A data privacy lawsuit naturally implies that an organization is either inept or apathetic in handling consumers’ data, so it could easily inflict both kinds of reputational damage.
Alliance With Compliance
The updated GLBA Safeguards Rule confirms two truths for accountable organizations. First, data privacy is a constantly evolving practice. And second, organizations cannot rest on their laurels when bringing their practices into compliance with these laws due to their evolving nature. Carrying out the necessary due diligence to ensure compliance with updated regulations is far less severe than risking penalties for noncompliance. The December 9 deadline is fast approaching. Delphix helps many banks and other covered organizations ensure compliance with a variety of data privacy-related regulations, including the GLBA Safeguards Rule, while also bolstering data security.
This article was originally published on Preludesys.
0 notes
Text
Announcing Delphix Compliance Services for Microsoft Fabric: Automating Data Compliance in Microsoft’s Next-Generation Platform
Overall, the collaboration between Delphix and Microsoft brings a wealth of value to large enterprises, providing a seamless and efficient way to achieve multi-cloud compliance while also unifying their data estate for analytics.

Today at Microsoft Build, Microsoft announced their next generation data platform, Microsoft Fabric. Delphix is proud and excited to be part of this solution and included in today’s announcement and the Microsoft Build demo session. Reflecting Microsoft and Delphix’s joint commitment to partner success and hands-on product collaboration, we collaborated on a solution to help unblock data access for wherever it’s needed across the enterprise to accelerate value generation from data — a mission tightly aligned with Delphix’s company vision. It’s been an ideal way for us to be better together, delivering the best of data compliance and data integration.
The Growing Impact of Privacy Regulations on Technology Professionals
Our customers tell us the growing framework of privacy regulations makes it harder for technology professionals who depend on sensitive data to do their jobs. For software developers, quality engineers, data analysts and scientists, AI/ML engineers, and citizen users of data, protecting privacy and complying with mandates such as GDPR and HIPAA often means relying on manual or sub-optimized processes for protecting sensitive data such as personally identifiable information (PII), customer lists, and payment details.
Unfortunately, these processes are not practical or sustainable. For one, they inevitably lead to delays in data access, hindering innovation, frustrating team members, and blocking citizen users from access to the data they need. But just as often they often fail to sufficiently protect data privacy, leaving sensitive data exposed to developers, testers, third parties, off-shore teams, systems administrators and others without a legitimate need-to-know. This is especially true with decentralized processes that are poorly governed across the enterprise. The challenge is making useful data available on demand while protecting sensitive elements from disclosure and replication.
Introducing Delphix Compliance Services for Microsoft Fabric
This is where Delphix comes into the picture. In close collaboration with Microsoft’s data integration team, we have introduced Delphix Compliance Services for Microsoft Fabric. Delphix provides intelligent, scalable, and seamless data masking for Microsoft Fabric users, allowing them to achieve multi-cloud data compliance in a way that is secure, efficient, easy-to-manage, and sustainable.
For background, Delphix software has a proven track record of masking data across Microsoft and non-Microsoft environments. We have worked with enterprises of all sizes, industries, and geographies, to address both cybersecurity requirements and privacy mandates. Critically for cloud migration use cases, our masking technology works with both non-cloud and cloud environments, helping many businesses shift their applications and data to the cloud. With this collaboration, Microsoft and Delphix are bringing our proven technology to the Microsoft Fabric platform in an experience tailored for ease-of-use and fast path to value.
Delphix Compliance Services for Microsoft Fabric provide masking APIs as a service so users can transform sensitive data to fictitious but realistic values, all from within the data flows. Like in the below diagram, you can simply call Delphix masking APIs from within your data flow, to ensure that data is compliant when being moved from Point A to Point B: you can mask and move data all in a single data flow. This approach preserves the utility of the data for analytics and BI without disclosing sensitive values such as PII. Furthermore, the solution supports the more than 170 source and target connectors provided by Microsoft’s platform and ensures referential integrity across multi-cloud environments. As a result, Delphix provides masking for even the most complex analytics scenarios.

The Benefits for Developers, Data Professionals, and Citizen Users
Delphix Compliance Services was built to make privacy compliance easy and automatic. It works seamlessly with Microsoft’s platform, including a code-free experience directly within the UI. This means Microsoft users can easily configure masking rules to be applied when moving data for secure analytics.
Delphix offers pre-built, deterministic masking algorithms to address major privacy regulations such as GDPR, HIPAA, and CCPA, so citizen users do not have to be experts in regulatory compliance or in data masking. The algorithms intelligently mask fields such as birth dates, phone numbers, zip codes, and other fields so they remain useful for analytics, testing, and other purposes. Once those masking algorithms have been configured, they are applied automatically, every time, for consistent protection.
Important for those users with enterprise-scale complex or multicloud data estates, our solution intelligently enforces referential integrity when masking data. This means that sensitive fields such as names, addresses, and account numbers are masked identically across data sources. For example, the patient name “Lisandra Preston” that is masked to “Iwana Villar” in one location will be masked to “Iwana Villar” in all others. This means that integrated environments will function the same way, even after masking has been applied.
The Benefits for the Enterprise
With Microsoft Fabric, Microsoft gives enterprises the ability to unify the data estate for analytics and other use cases. By collaborating with Delphix, Microsoft makes it seamless for those enterprises to apply data masking at any scale and complexity. This makes it much easier and more efficient to get value from data, unblocking data streams and accelerating the pace of innovation, while protecting data privacy.
“Data compliance is a major challenge for businesses today,” said Jedidiah Yueh, Delphix CEO. “Our multicloud data compliance and masking solution is designed to make Microsoft Fabric the easiest, most secure, and most compliant cloud in the industry.”
Underscoring the importance of our collaboration, Microsoft’s VP of Data Integration Faisal Mohamood said, “We’re pleased about the multicloud data compliance solution for use in Microsoft Fabric that the Delphix and Microsoft teams have created in close collaboration. Together, we’ve developed a robust data compliance and integration solution for our customers.”
By automating data compliance with our leading masking technology, the solution removes one of the most common barriers to accelerating innovation, business insights and AI/ML adoption. In turn, businesses will bring new features and capabilities to market faster without exposing themselves to unnecessary risks.
Overall, the collaboration between Delphix and Microsoft brings a wealth of value to large enterprises, providing a seamless and efficient way to achieve multicloud compliance while also unifying their data estate for analytics. With its code-free experience, built-in data governance, and out-of-the-box integrations with widely used Microsoft solutions, this solution is an ideal choice for enterprises looking to leverage their data for competitive advantage while also ensuring compliance with all major regulations.
Note: PreludeSys is a trusted Delphix partner. The original source of the content is delphix.com/blog.
#Data compliance for Microsoft Fabric#gdpr compliance consulting services#delphix authorised service provider#microsoft fabric data analytics#microsoft fabric consulting company#microsoft fabric services
0 notes
Text
Delphix leva inovação em dados seguros para IA à FEBRABAN
A Delphix, empresa global de virtualização e gestão inteligente de dados para DevOps, confirma mais uma vez sua participação na FEBRABAN TECH 2025, evento de tecnologia e inovação do setor financeiro, reforçando seu compromisso e investimento contínuo no segmento. O evento acontece de 10 a 12 de junho, no Transamerica Expo Center, em São Paulo. Durante o evento, a Perforce Delphix apresenta suas…
0 notes
Note
Delphix! ....Mail?
She kind of just walks up to you. It's Pythia.
After a moment of staring you down, she sighs quite loudly and pats you on the shoulder. Some more quiet eye contact, and she pulls out her stick. Another moment later and Phoebus' Espeon is unceremoniously dumped into your arms.
Pythia walks away after that.
[ – @sunlit-arrows ]
oh-
uhm. thank you...? i'm. REALLY confused on how that just happened but i'm not really going to question it right now, i appreciate it a lot though-
1 note
·
View note
Text
Perforce Releases Delphix Compliance Services to Offer Automated AI and Analytics Data Compliance
http://securitytc.com/TK17vF
0 notes
Text
Service Virtualization Market Size, Share, Scope, Analysis, Forecast, Growth and Industry Report 2032 – SWOT and PESTLE Analysis
TheService Virtualization Market Share was valued at USD 745.8 Million in 2023 and is expected to reach USD 2853.1 Million by 2032, growing at a CAGR of 16.1% over the forecast period 2024-2032.
The Service Virtualization Market is witnessing rapid adoption across various sectors. It is enabling faster software development and better testing environments. Organizations are increasingly using it to simulate service behavior in complex systems.
The Service Virtualization Market continues to grow as businesses demand more agile and cost-effective development processes. With the rising pressure to deliver high-quality applications at speed, service virtualization is becoming essential to support continuous integration, DevOps, and automated testing workflows.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/4624
Market Keyplayers:
CA Technologies (Broadcom) – (CA Service Virtualization, CA DevTest)
IBM Corporation – (Rational Test Virtualization Server, IBM Rational Integration Tester)
Micro Focus – (Service Virtualization, LoadRunner Professional)
Parasoft – (Parasoft Virtualize, Parasoft SOAtest)
SmartBear Software – (ReadyAPI Virtualization, TestComplete)
Cavisson Systems – (Cavisson Service Virtualization, NetStorm)
Tricentis – (Tosca, Tricentis Virtualize)
Broadcom Inc. – (Broadcom DevTest, Broadcom Service Virtualization)
Maveric Systems – (Maveric Service Virtualization, Maveric Continuous Testing)
Wipro Limited – (Wipro HOLMES™, Wipro Virtualization Solutions)
Cognizant Technology Solutions – (Cognizant Testing Services, Cognizant Virtualization)
Sogeti (Capgemini) – (Sogeti Testing Services, Virtualization Platform)
Infosys Limited – (Infosys Virtualization Service, Infosys Test Automation)
Accenture – (Accenture Cloud Virtualization, Accenture Service Testing)
Tata Consultancy Services (TCS) – (TCS Service Virtualization, TCS Testing Services)
Delphix – (Delphix Data Platform, Delphix Virtualization)
Quali Systems – (CloudShell, Quali Service Virtualization)
QASymphony – (qTest, Service Virtualization)
Vector Software – (VectorCAST Virtualization, VectorCAST Test)
Trends in the Service Virtualization Market
Increased Adoption in DevOps: Companies are integrating service virtualization into DevOps pipelines to accelerate development and testing cycles.
Cloud-Based Solutions: There is a rising demand for cloud-native virtualization tools, offering flexibility and scalability across distributed teams.
AI and Automation Integration: Vendors are embedding AI-driven analytics and automation features to enhance test coverage and efficiency.
Focus on API Testing: With APIs becoming central to modern applications, service virtualization tools are now tailored to mimic complex API interactions.
Enquiry of This Report: https://www.snsinsider.com/enquiry/4624
Market Segmentation:
By Component
Software
Service
By Enterprise Size
Large Enterprise
SMEs
By Deployment
Cloud
On-premise
By End Use
BFSI
Healthcare
IT & Telecommunication
Automotive
Retail & E-Commerce
Market Analysis
Growing Demand Across Industries: BFSI, healthcare, retail, and telecom sectors are adopting service virtualization to reduce time-to-market and improve software quality.
Cost and Resource Efficiency: It minimizes the need for setting up complex test environments, saving costs and development time.
Support for Agile & Continuous Testing: Service virtualization plays a crucial role in enabling agile methodologies by providing early and continuous testing capabilities.
Rising Competition Among Vendors: Key players like Broadcom, IBM, Micro Focus, and SmartBear are enhancing their offerings with next-gen capabilities such as cloud compatibility and AI integration.
Future Prospects
The future of the Service Virtualization Market looks promising as digital transformation initiatives continue to gain momentum. As companies adopt microservices and cloud-native architectures, the need for simulating complex, distributed systems will increase. Service virtualization will become even more vital in testing environments where real services are either unavailable or costly to access.
Advancements in AI, machine learning, and automation will further enhance service virtualization tools, enabling intelligent test data generation, dynamic behavior simulation, and real-time analytics. Additionally, integration with CI/CD pipelines and containerized environments like Kubernetes will expand the scope and flexibility of service virtualization across development ecosystems.
With organizations aiming for faster releases and higher-quality software, service virtualization will continue to evolve as a foundational technology in modern application development and delivery.
Access Complete Report: https://www.snsinsider.com/reports/service-virtualization-market-4624
Conclusion
The Service Virtualization Market is set for steady growth, backed by digital transformation, DevOps adoption, and the demand for rapid, reliable software delivery. As development environments become more complex and interconnected, service virtualization offers the scalability, flexibility, and cost-efficiency that modern enterprises require.
Going forward, businesses that leverage advanced service virtualization tools will not only reduce development costs but also gain a competitive edge by accelerating innovation and improving software quality. The market is expected to thrive, playing a key role in shaping the future of agile and efficient software development.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#Service Virtualization Market#Service Virtualization Market Scope#Service Virtualization Market Trends
0 notes
Text
Test Data Management: A Comprehensive Guide

Why Test Data Management is Crucial for Modern Development
In today’s fast-paced software development landscape, test data management (TDM) plays a pivotal role in ensuring quality, speed, and efficiency in testing processes. As businesses strive for faster releases and better software quality, managing test data effectively has become more important than ever.
What is Test Data Management?
Test data management refers to the process of creating, managing, and maintaining data sets used for testing software applications. These data sets mimic real-world scenarios to ensure that software is rigorously tested before deployment. The goal of TDM is to provide accurate, consistent, and secure data to support testing processes.
The Importance of Test Data Management in the Software Development Lifecycle (SDLC)
Effective TDM is critical to achieving accurate test results, faster releases, and robust application performance in the SDLC. It ensures that test environments mirror production scenarios as closely as possible, leading to more reliable outcomes. Without proper TDM, software teams may encounter issues like incomplete test coverage, delays, and compromised quality.
Key Components of Test Data Management
A successful TDM strategy consists of several crucial components:
Data Discovery: Understanding and identifying data requirements is the first step in TDM. This involves analyzing the application and defining the type and volume of data needed.
Data Provisioning: Preparing and allocating test data sets to various testing environments ensures that teams have the resources they need at every stage.
Data Masking: To protect sensitive information, data masking techniques anonymize data while maintaining its usability for testing purposes.
Data Integrity: Maintaining consistency and accuracy of test data is essential for trustworthy testing outcomes.
Challenges in Test Data Management
Despite its importance, managing test data effectively comes with its own set of challenges:
Handling large data volumes: Managing big data sets for testing can be resource-intensive.
Ensuring data compliance and security: With stringent regulations like GDPR, safeguarding sensitive data is a top priority.
Providing realistic test scenarios: Ensuring that test data reflects real-world conditions is crucial but challenging.
Managing costs: The expenses associated with storage, provisioning, and management can add up quickly.
Benefits of Efficient Test Data Management
Organizations that implement robust TDM practices experience multiple benefits, including improved testing accuracy and reduced time-to-market.
Enhanced test coverage enables teams to identify and fix bugs early.
Accelerated testing cycles reduce delays in the development process.
Better compliance with data privacy regulations protects businesses from legal risks.
Cost efficiency in testing processes saves valuable resources.
Best Practices for Test Data Management
Implementing the following best practices can help streamline TDM and maximize its effectiveness:
Define clear data requirements: Collaborate with stakeholders to determine the exact test data needs.
Use automated tools: Automating data generation, masking, and provisioning saves time and reduces errors.
Maintain separate environments: Isolating test environments from production prevents data contamination.
Regularly update test data: Keep test data sets relevant by refreshing them periodically.
Tools for Test Data Management
Various TDM tools simplify the complexities of handling test data, enabling teams to focus on quality assurance.
Popular tools like Informatica, IBM Optim, Delphix, and TDM Pro offer features such as automated data provisioning, masking, and compliance support.
When selecting a tool, look for capabilities such as scalability, ease of integration, and advanced reporting.
Test Data Management for Compliance and Security
Ensuring compliance with data privacy regulations like GDPR, HIPAA, and CCPA is a crucial aspect of TDM.
Data masking and encryption techniques help safeguard sensitive information.
Regular audits and monitoring ensure compliance with industry standards.
Following regulatory guidelines reduces risks and builds customer trust.
Real-World Applications of Test Data Management
TDM finds applications across industries, from banking to healthcare, where precise and secure testing environments are critical.
Case study: A leading banking firm implemented automated TDM, reducing testing time by 40% while ensuring compliance with stringent data privacy regulations.
Use cases in healthcare involve anonymizing patient records for software testing, while retail companies use TDM to test their e-commerce platforms.
Future Trends in Test Data Management
Emerging technologies like AI and machine learning are shaping the future of TDM, enabling smarter and more efficient testing.
AI-powered data generation creates realistic test scenarios with minimal manual effort.
Cloud-based TDM solutions offer scalability and cost efficiency.
The focus on data compliance continues to grow, ensuring that TDM evolves with regulatory requirements.
Conclusion: Embracing Test Data Management for Better Software Quality Test data management is not just a support process but a strategic enabler for delivering high-quality software applications efficiently and securely. By investing in robust TDM strategies and tools, organizations can accelerate development cycles, enhance software quality, and stay ahead in the competitive technology landscape.
0 notes
Text
💥 Explore practical insights 👓 on utilizing #generative #AI 🧠🤖, including when and how to apply it, creation #methods, and key market #vendors! -> It’s estimated that by 2024, 60% of the #data used to develop #AI and analytics projects will be #syntheticallyz generated. 💡 Why? -_- Some types of data are costly to collect, or they are rare. -_- Many business problems that #AI & #ML models require access to #sensitive customer data such as Personally Identifiable Information (#PII) or Personal Health Information (#PHI). ----> As a result, #businesses are turning to data-centric approaches to #ArtificialInteligence #MachineLearning development, including #synthetic #data to solve these problems. -------> Click here for more: https://lnkd.in/g5252ajp Vendors: ✔️ BizDataX ✔️ CA Technologies Datamaker ✔️ CVEDIA ✔️ Deep Vision Data by Kinetic Vision ✔️ Delphix Test Data Management ✔️ Genrocket ✔️ Hazy ✔️ Informatica Test Data Management Tool ✔️ Mostly AI ✔️ Neuromation ✔️ Solix EDMS ✔️ Supervisely ✔️ TwentyBN
#digitaltransformation#commercialexcellencebulletin#digital#syntheticdata#businesstransformation#datamodel#datacrunching#datamining#deeplearning
0 notes
Text
Perforce's Acquisition Of Delphix Enhances DevOps With Enterprise Data Management

Perforce Software, supported by Francisco Partners and Clearlake Capital Group, has announced its definitive agreement to acquire Delphix, a leading Data Management software platform. Delphix's platform, renowned for scalable automation, governance, and compliance of enterprise data, will be integrated into Perforce's portfolio, enabling the realization of an automated and accelerated DevOps pipeline. Perforce's CEO, Jim Cassens, emphasizes the strategic addition of critical data management capabilities and expresses excitement about delivering operational efficiencies and reduced costs through Delphix's platform. This collaboration underscores Perforce's commitment to ongoing data management innovation, addressing the increasing importance of data for enterprise organizations.
Founded over 15 years ago, Delphix is dedicated to automating data and accelerating digital transformation. CEO Jedidiah Yueh anticipates continued innovation and strategic empowerment within Perforce, fostering the realization of the strategic power of their data platform. The acquisition, subject to customary closing conditions, is expected to conclude in the second quarter of 2024, further positioning Perforce to meet the growing demand for enterprise-scale data management in testing, AI modeling, and analytics. Centerview Partners played a crucial role as the exclusive financial adviser to Delphix in connection with the transaction.
Read More - https://www.techdogs.com/tech-news/pr-newswire/perforce-to-acquire-delphix-adding-enterprise-data-management-software-to-its-devops-portfolio
0 notes
Text
Delphix Online Training at Ecorptrainings Hyderabad India.
#Delphix is software that runs as a VM on VMware. Delphix manages storage. Delphix looks like a NAS to databases clones using Delphix. Delphix pulls in changes from source databases. Delphix exposes the source database data to clone databases via NFS. Clone databases share all duplicate blocks on Delphix and only modified blocks are kept private to those clones.
ABOUT ECORPTRAININGS:
Ecorp Trainings are one of the best institute providing quality level of training in E-learning process.This is instructor led online training.
We also provide corporate training , if group of people interested in same technology.
Contact us for detailed course content & register for a free demo.
We also provide support in client interviews , resume preparation , ticket resolving.
Contact us for custom designed training course by experts exclusively for yourself.
We provide training for almost all IT technologies i.e ; JAVA , DOTNET , SAP ,ORACLE , PEOPLESOFT ,HYPERION etc, contact us if you have any particular need.
Contact:
Ecorptrainings
Email: [email protected]
USA: +1-703-445-4802 UK : +44 20 3287 2021
India: 040-64643304/06,+91-8143-111-555
Gtalk ID : ecorptrainings
Skype ID : ecorptrainings
For content :click here
0 notes
Text
Strengthening Data Compliance and Security: How Delphix Protects Businesses in a Digital World
In today’s digital age, data compliance and security have become crucial topics for businesses across industries. With growing data privacy regulations and increasing cyber threats, companies face mounting pressure to safeguard their information assets while ensuring data protection and privacy compliance with a host of legal standards. However, achieving both compliance and security can be challenging, especially as data volumes grow and organizations move highly-sensitive information onto digital platforms.

Delphix Data Compliance and Security offers powerful tools to help companies address these challenges. In this article, we’ll break down what data compliance and security mean, why they’re essential for business operations, the common hurdles companies face, and how Delphix’s capabilities can help overcome these barriers.
What are data compliance and security, and why do they matter?
Data compliance involves adhering to legal, regulatory, and ethical standards that govern the collection, storage, and use of data. These standards can vary depending on industry and geography, but some common frameworks include GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), and CCPA (California Consumer Privacy Act). Non-compliance with these regulations can lead to legal consequences, financial penalties, and reputational damage.
Data security, on the other hand, focuses on protecting data from unauthorized access, breaches, and leaks. Security measures include encryption, access controls, and monitoring systems to ensure data is protected from both internal and external threats. With the rise of sophisticated cyberattacks, maintaining robust data security is critical to preserving customer trust and protecting business assets.
For companies, data compliance and security aren’t just legal requirements; they’re foundational elements of responsible data management. Failing to meet these standards can lead to severe financial repercussions and erode customer trust, making it imperative for businesses to prioritize both.
Common Data Compliance and Security Challenges Businesses Face
Despite best efforts, businesses often encounter several challenges in meeting data compliance and security standards:
Complex Regulatory Requirements: Navigating different regulatory requirements across regions and industries can be overwhelming, especially when data is stored and accessed globally.
Data Proliferation: As organizations generate and store vast amounts of data, keeping track of sensitive information and ensuring it remains compliant becomes a significant challenge.
Risk of Data Breaches: With cyber threats on the rise, protecting sensitive information from breaches and unauthorized access is more complex than ever.
Data Privacy and Access Control: Balancing data accessibility with privacy protection is essential but difficult, particularly when data is shared across multiple departments or applications.
IT Governance, Risk, and Compliance (IT GRC): Ensuring that data governance, risk management, and compliance align with organizational goals can be challenging, as these areas often overlap.
These challenges require sophisticated tools and strategies. Delphix steps in to provide the capabilities needed to address each of these concerns effectively.
How Delphix Data Compliance and Security Helps Businesses Overcome These Challenges
Automated Data Masking for Privacy Protection Delphix offers automated data masking, a process that replaces sensitive information with realistic but fictional data. This feature is invaluable for protecting privacy during development and testing, as it prevents unauthorized access to actual sensitive data. By masking data automatically, Delphix helps organizations meet regulatory standards while maintaining data usability, ensuring both data protection and privacy compliance.
Regulatory Compliance Support With Delphix, businesses can align with multiple compliance frameworks, including GDPR, HIPAA, and CCPA. Delphix’s platform includes features designed to simplify audits and compliance reporting, helping companies meet regulatory standards with minimal friction. For organizations seeking data compliance services , Delphix provides the support needed to manage compliance with greater ease.
Data Control and Access Management Delphix enables granular access controls, allowing organizations to manage who can access sensitive data and under what circumstances. By setting strict access policies and monitoring usage, businesses can significantly reduce the risk of unauthorized access and ensure compliance with data privacy requirements.
Real-Time Monitoring and Auditing Delphix provides real-time monitoring and auditing tools that allow businesses to track data access and activity across the organization. These insights enable companies to detect and respond to potential security incidents promptly, adding a layer of protection that enhances both security and compliance.
Accelerated Data Delivery with Security in Mind Delphix’s platform accelerates the process of data delivery for development, testing, and analytics while embedding security throughout. This allows organizations to innovate and adapt quickly without sacrificing the safety of their data or regulatory compliance.
Why Companies Choose Delphix for Data Compliance and Security
Delphix isn’t just a data platform; it’s a comprehensive solution tailored to modern compliance and security needs. By automating data privacy processes, supporting compliance requirements, and enhancing data access control, Delphix empowers businesses to navigate complex regulatory landscapes and safeguard their data assets. Companies that choose Delphix can focus on innovation and growth with the confidence that their data compliance and security needs are met.
Protect Your Business with PreludeSys and Delphix
At PreludeSys, we understand the importance of strong data compliance and security measures. As a Delphix partner, we’re here to provide you with the guidance, expertise, and solutions you need to implement and maintain Delphix Data Compliance and Security. Ready to enhance your data protection strategy? Contact PreludeSys today to learn how our data compliance services can support your business in staying compliant and secure.
#data security services#delphix data masking#data compliance services#data protection and privacy compliance#it governance risk and compliance
0 notes
Text

Diptic.
Impressions of the video camera checks yesterday before our third performance (in a row!!!) of La Voix Humaine, Theater Chur with Musikkollegium Winterthur. Photo credits delphix
2 notes
·
View notes
Text
LO Characters as Pokemon Trainers: Godesses
No Artemis for reasons. These are goddesses of LO as Pokemon trainers based on LO and the Greek mythology. So let's begin.
Heccate

The Goth queen of LO, Hecate has a magicbased team. Heccate's ace is ancient Delphix named Baba Yaga. As cunning as her trainer, Baba Yaga is not one to be triffled with. Her Hatterene, Morgana, shares her hattred of noise. Morgana and Baba Yaga sometimes throws sticks for Hades dog pokemon for fun, despite the doggos noisy natures. Her Alolan Ninetales, Mystic is often seen playing with Hades's Houndoom, Cerberus. Mismagius helps when dealing with dead employed at Underworld Corps. Her Mimikyu, Nightmare loves to scare people, but never scares Persephone. As she is the only one other than Hecate who shows him any affection. How or why she has a Hoopa named Chaos, should be obvious. They both love chaos. Chaos and Nightmare are BFFs, much to the employees of Underworld Corps horror. Persephone is just happy that Nightmare finally has a friend. Hecate also has Zoarark named Shadow, but no ever knows where it is. Thus it is not on her team. Although the Furies suspect Hecate uses on days she wants to sleep in. Bewarned messing with Hecate, Persephone, Hades or their pokemon will lead to all of Hecate's pokemon to wanting vengence. The results are brutal just ask Minthe and Thetis.
Hestia
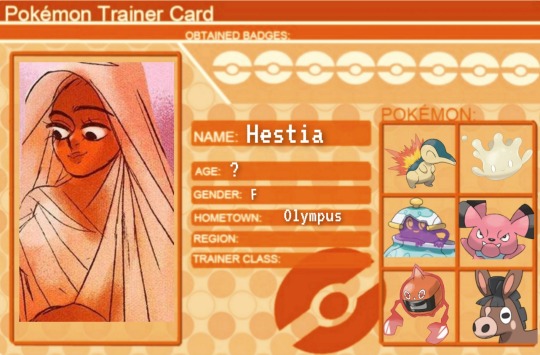
Hestia despite never battling, still has a pokemon team. Although she considered beloved by Fire types she does not share their firey nature. Her Rotom, Trouble, lives up to his name. Despite this Trouble loves Hestia alot due to her saving it when she founded terribly injured. He possess a oven which is useful for Hestia, who loves to cook. Tea, Hestia's Polteageist has been her tea time partner for ages. Her Cyndaquil, Muffin is the reason that Cyndaquil are Sacred to Hestia. Muffin is always there to warm up other pokemon, or help roast a marshmellows. Trouble and Tea are very protective of Cyn due to his shy nature. Still don't mess with any of the rest of her team or Muffin will get mad. If Muffin gets mad at you, you better run. Hestia never evolved her Milcery, Milk into Alcremie. Her Mudbray, Sweety is there to bring injured pokemon to its trainer, and Snubull, Hug just acts as a cute cuddle bug.
Athena
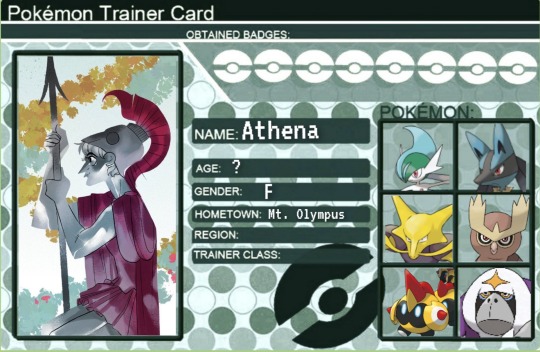
Athena as the godess of wisdom and battle stratgy her team reflects that. Her Gallade is not just her ace but was gifted to her as a Ralts by Hera herself. Gallade and Athena are extremely close. Athena's Noctowl, Bubo is extremely small for his size, but is adored by Athena. He is always sitting on her shoulder. Her Lucario, is another one of warrior pokemon. Gallade and Lucario are often seen sparing with each other when Athena is not around.She likes to play chess with her Alakazam and Oranguru, when she not busy. Her Falinks, is there to help figure out army formations. She also has a Sirfetch'd as a companion, it stands as guard over its trainers temple.
Next up is Artemis and her family.
23 notes
·
View notes
Text
Cultivating Speed and Scale for the Modern Application with MongoDB and Delphix by Perforce
http://securitytc.com/TG958F
0 notes
