#devsecops implementation strategy
Explore tagged Tumblr posts
Text
# devsecops strategies#devops consulting companies#devsecops implementation strategy#devsecops strategy#product development firm#Secure Software Development
0 notes
Text
AWS DevOps Careers: Navigating the Cloud-Infused Professional Landscape
In the rapidly evolving tech terrain, the confluence of AWS and DevOps has given rise to a dynamic realm, promising an array of career prospects. This all-encompassing guide unveils the diverse roles and responsibilities within AWS DevOps, offering insights into the multifaceted career avenues that await proficient individuals.
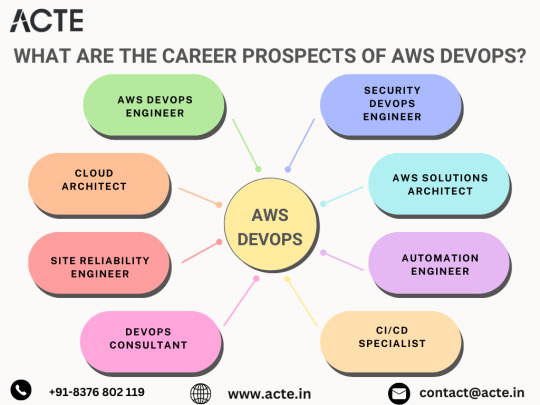
1. Crafting Cloud Solutions: The Role of an AWS DevOps Engineer
Overview: AWS DevOps Engineers serve as architects of automated software development, leveraging AWS cloud services.
Responsibilities: Dive into Infrastructure as Code (IaC), fine-tune AWS tools, and champion the principles of Continuous Integration/Continuous Deployment (CI/CD).
2. Architecting Scalable Cloud Solutions: The Realm of Cloud Architects
Overview: Cloud Architects design scalable and reliable cloud infrastructure on AWS, seamlessly aligning with DevOps principles.
Responsibilities: Collaborate to optimize AWS services, ensuring a resilient and scalable cloud environment.
3. Reliability in the Cloud: The Role of a Site Reliability Engineer (SRE)
Overview: SREs focus on ensuring system reliability, availability, and performance on AWS through vigilant monitoring and automation.
Responsibilities: Implement automation strategies, monitor AWS resources, and respond adeptly to incidents.
4. DevOps Consultancy: Guiding Organizations to DevOps Excellence
Overview: DevOps Consultants provide expertise in implementing DevOps practices, specializing in AWS services.
Responsibilities: Offer guidance on best practices, implement CI/CD pipelines, and optimize workflows using AWS tools.

5. Embedding Security into DevOps: The Role of a Security DevOps Engineer (DevSecOps)
Overview: DevSecOps Engineers integrate security practices into the AWS DevOps pipeline.
Responsibilities: Implement robust security measures, conduct risk assessments, and ensure compliance with security policies.
6. Solutions Architecture on AWS: Crafting Business-Aligned Solutions
Overview: AWS Solutions Architects design and implement solutions aligned with business requirements, utilizing AWS services.
Responsibilities: Collaborate across teams, grasp project intricacies, and architect solutions that optimize AWS resources.
7. Scripting the Future: The Role of an Automation Engineer in AWS
Overview: Automation Engineers script and automate processes within AWS DevOps.
Responsibilities: Script infrastructure deployment, automate testing processes, and lead AWS automation initiatives.
8. Streamlining Software Delivery: The Role of a CI/CD Specialist on AWS
Overview: CI/CD Specialists optimize and streamline the software delivery pipeline within the AWS environment.
Responsibilities: Configure and manage CI/CD tools, ensuring the efficient and reliable delivery of software.
Embarking on an AWS DevOps career journey presents professionals with a landscape rich in challenges and opportunities. Each role within AWS DevOps contributes to a fulfilling and dynamic career trajectory, promising innovation and significant contributions to the ever-evolving technological realm. Best of luck as you navigate the transformative path of AWS DevOps careers!
2 notes
·
View notes
Text
What is DevOps and How Does it Work?
In today’s fast-paced software industry, businesses are under pressure to release features faster, fix bugs more quickly, and improve overall application performance. This is where DevOps comes in—a methodology that bridges the gap between development (Dev) and operations (Ops) teams to streamline software delivery and ensure reliability, scalability, and speed.
DevOps is not a tool or a single process—it is a culture shift and a set of practices that promote collaboration, automation, and continuous feedback throughout the software development lifecycle. By integrating development and operations, DevOps helps eliminate traditional silos, reduces manual tasks, and enables frequent, reliable software releases.

Understanding the DevOps Lifecycle
The DevOps lifecycle includes several stages: plan, develop, build, test, release, deploy, operate, and monitor. Each stage is interconnected, forming a continuous loop that ensures faster and more efficient software delivery. Automation plays a vital role at every step—whether it’s continuous integration (CI), continuous delivery (CD), automated testing, or infrastructure as code (IaC).
"DevOps is not a goal, but a never-ending process of continual improvement." – Jez Humble
This lifecycle encourages iterative development and immediate feedback, helping teams detect issues early and respond quickly to changing requirements.
To make the DevOps journey successful, many organizations turn to DevOps consulting services. These services provide expert guidance on tools, automation strategies, CI/CD pipeline design, container orchestration, cloud-native development, and more. For companies at the beginning of their DevOps journey, consulting ensures that the transformation aligns with business goals and is scalable for future growth.
How DevOps Works in Real Life
Let’s consider a practical example. Imagine a fintech startup building a mobile app. Traditionally, developers would write code, hand it over to QA, then to the operations team for deployment—leading to delays, errors, and frustration.
With DevOps, the startup integrates CI/CD pipelines, enabling developers to push code frequently. Every commit is automatically built, tested, and deployed to a staging environment. Operations teams use infrastructure as code (IaC) to manage cloud resources, ensuring consistency across environments. Monitoring tools continuously track app performance and user behavior, allowing real-time feedback loops for developers to fix issues quickly.
This automation and collaboration not only improve software quality but also boost team morale and accelerate time to market.
In fact, startups that adopt DevOps early benefit from faster innovation. That’s why it’s essential to identify what's the best DevOps platform for startups. Choosing the right combination of tools and cloud infrastructure ensures that DevOps implementation is cost-effective, scalable, and tailored to startup needs.
The Role of DevOps Consultants
DevOps transformation isn’t just about tools—it’s about mindset, structure, and workflows. A DevOps transformation consultant helps businesses adopt agile principles, restructure teams for collaboration, and implement best practices like version control, automated testing, and continuous monitoring.
"You build it, you run it." – Werner Vogels, CTO of Amazon
This principle emphasizes ownership and accountability—a core value of DevOps culture. Consultants also help in selecting suitable cloud platforms (like AWS, Azure, or GCP), integrating Kubernetes for container orchestration, and establishing security practices such as DevSecOps.
By offering hands-on support, DevOps consultants accelerate transformation and ensure long-term success.
Challenges and Considerations
While DevOps offers numerous advantages—faster releases, better quality, reduced risk—it also presents challenges. Cultural resistance, lack of skills, and toolchain complexity can slow down adoption. Hence, organizations must invest in team training, leadership buy-in, and robust planning.
Moreover, metrics and monitoring are crucial. Tracking deployment frequency, lead time for changes, change failure rate, and MTTR (mean time to recovery) helps measure the success of DevOps practices.
For businesses aiming to stay competitive in a digital-first world, DevOps is not optional—it’s essential.
Final Thoughts
In summary, DevOps is a transformative approach that merges development and operations to foster automation, collaboration, and rapid delivery. Whether you’re a startup looking for agility or an enterprise modernizing legacy systems, adopting DevOps can drastically enhance software development outcomes.
Visit Cloudastra Technology: Cloudastra DevOps as a Services to learn how tailored DevOps solutions can help your business scale faster and smarter.
0 notes
Text
Leading Cloud Application Development Company: Wagner Engineer USA
In today’s fast-paced, cloud-first world, working with an adaptable, experienced Cloud Application Development Company isn’t just an option—it’s critical to your business success. At Wagner Engineer USA, we specialize in building cloud-native, resilient, and secure applications that expand your scale, accelerate your delivery, and empower your teams to innovate. Whether you're a startup launching an MVP, an enterprise modernizing legacy systems, or an SMB scaling operations globally, our end-to-end cloud application development drives measurable outcomes for your organization.
Why Choose a Cloud Application Development Company?
Cloud apps enable businesses to be agile, elastic, and future-ready. Here’s how partnering with Wagner Engineer USA can transform your operations:
Scalability & Elasticity: Automatically scale up or down based on user demand, supplanting manual provisioning or idle servers.
Cost Optimization: Harness the pay-per-use economy of cloud computing to avoid excessive infrastructure spend.
Faster Time to Market: Leverage CI/CD pipelines and microservices to deploy features continuously and reliably.
Performance & Availability: Distribute applications across availability zones and leverage fault-isolated microservices for higher uptime.
Security & Compliance: Built-in identity management, encryption, and standards compliance (HIPAA, GDPR, PCI-DSS) protect data and users.
Global Reach: Rapidly serve international users by deploying across multiple regions with minimal latency.
Wagner Engineer USA guides you through every stage of cloud application development—strategy, architecture, development, deployment, and post-launch optimization.
Our Core Services
1. Strategic Consulting & Discovery
Our engagement begins with in-depth workshops. We uncover your goals, user personas, technical constraints, and KPIs. Together, we craft a roadmap outlining platform choices (AWS, Azure, or GCP), architectures (microservices, serverless, hybrid), and go-to-market timelines.
2. Architecture & System Design
We engineer resilient, scalable architectures using patterns like microservices, event-driven workflows, and serverless execution. Each design considers tenant isolation, state handling, global distribution, and operational observability.
3. Infrastructure-as-Code (IaC) & Cloud DevOps
Using tools like Terraform, CloudFormation, and Azure Bicep, we define and version infrastructure components. We implement automated CI/CD pipelines via GitHub Actions or Jenkins—handling builds, testing, security scans, and deployments.
4. Full-Stack Development
Our engineering team builds scalable, secure services using:
Backend: Node.js, Python, Go, Java, .NET
Frontend: React, Angular, Vue.js
APIs: REST or GraphQL with secure gateways and documented contracts
Containers + Orchestration: Docker & Kubernetes on EKS, AKS, or GKE
Serverless: AWS Lambda, Azure Functions, or GCP Cloud Functions
5. Quality Assurance & DevSecOps
Quality and security are baked in through:
Unit, integration, and end-to-end testing (automated)
Load simulations and performance benchmarking
Security scans at each commit and environment level
Compliance readiness: HIPAA, PCI-DSS, SOC 2, ISO
6. Deployment & Production Readiness
Using rollback-friendly Cloud Application Development Company strategies such as blue/green and canary releases, we deploy with minimal downtime. We configure observability using Prometheus, Grafana, ELK Stack, CloudWatch, or Azure Monitor. Our systems include automated alerts, log management, and cost dashboards.
7. Ongoing Monitoring & Optimizations
Our managed services include 24/7 monitoring, bug patching, scaling adjustments, security updates, and quarterly architecture reviews to ensure your application evolves with your business needs.
Industry Verticals We Empower
Startups & MVPs: Rapid prototyping and iterative feature delivery for lean innovation.
SaaS & ISVs: Secure multi-tenant platforms engineered for scale, compliance, and extensibility.
FinTech & HealthTech: High-performance, encryption-ready systems with mandatory compliance audits.
Enterprise IT: Migration of monoliths into microservices and automated DevOps ecosystems.
IoT & Edge Computing: Telemetry ingestion, analytics pipelines, and integration with control systems.
eCommerce & Data Analytics: Real-time data processing, recommendation engines, and scalable storefronts.
Tangible Business Benefits
Accelerated Delivery Deploy features weekly instead of quarterly—rapidly adapt to user demands and market trends.
Operational Efficiency Eliminate manual toil through automation—spend more time building value and less time maintaining undifferentiated infrastructure.
Reliability & Uptime Reduce outages with fault-isolated design patterns, monitored systems, and automated failover.
Cost Control & Insights Use intelligence-driven dashboards to optimize instance size, retirement, and serverless function execution times.
Security and Compliance Assurance Embedded encryption, auditing, and authentication flows reduce regulatory risk and bolster trust.
Real Project Example
Industrial IoT Monitoring Platform Wagner Engineer USA architected a serverless platform leveraging AWS Lambda, API Gateway, DynamoDB, and S3. The system compiled device telemetry for real-time dashboards and alerts—all while auto-scaling to support thousands of devices. Result: a 35% reduction in infrastructure costs and 99.99% uptime.
Our Technology Ecosystem
LayersTools & TechnologiesCloud PlatformsAWS, Azure, GCPIaC & DevOpsTerraform, CloudFormation, GitHub Actions, JenkinsBackendNode.js, Python, Java, Go, .NETFrontendReact, Angular, Vue.jsContainers & ServerlessDocker, Kubernetes, AWS Lambda, Azure FunctionsObservabilityPrometheus, Grafana, ELK/EFK, CloudWatch, Azure MonitorSecurity & AuthOAuth 2.0, JWT, IAM, Vault, Encryption
What Makes Us Different
Full-Stack Engineering: We combine embedded systems insight with digital cloud acumen to deliver end-to-end solutions.
Vendor-Neutral Advice: Our recommendations are client-focused, not platform-biased.
Security-First DNA: We build secure systems from inception, not bolt them on.
Transparent Collaboration: Agile delivery, sprint reviews, and shared documentation keep you in control.
Operational Continuity: We don’t walk away after deployment—our support ensures ongoing success.
Contact Wagner Engineer USA to start with a complimentary cloud strategy consultation. We’ll assess your needs, propose a bespoke roadmap, and offer a proof of concept that delivers business value fast.
0 notes
Text
DevOps Services at CloudMinister Technologies: Tailored Solutions for Scalable Growth
In a business landscape where technology evolves rapidly and customer expectations continue to rise, enterprises can no longer rely on generic IT workflows. Every organization has a distinct set of operational requirements, compliance mandates, infrastructure dependencies, and delivery goals. Recognizing these unique demands, CloudMinister Technologies offers Customized DevOps Services — engineered specifically to match your organization's structure, tools, and objectives.
DevOps is not a one-size-fits-all practice. It thrives on precision, adaptability, and optimization. At CloudMinister Technologies, we provide DevOps solutions that are meticulously tailored to fit your current systems while preparing you for the scale, speed, and security of tomorrow’s digital ecosystem.
Understanding the Need for Customized DevOps
While traditional DevOps practices bring automation and agility into the software delivery cycle, businesses often face challenges when trying to implement generic solutions. Issues such as toolchain misalignment, infrastructure incompatibility, compliance mismatches, and inefficient workflows often emerge, limiting the effectiveness of standard DevOps models.
CloudMinister Technologies bridges these gaps through in-depth discovery, personalized architecture planning, and customized automation flows. Our team of certified DevOps engineers works alongside your developers and operations staff to build systems that work the way your organization works.
Our Customized DevOps Service Offerings
Personalized DevOps Assessment
Every engagement at CloudMinister begins with a thorough analysis of your existing systems and workflows. This includes evaluating:
Development and deployment lifecycles
Existing tools and platforms
Current pain points in collaboration or release processes
Security protocols and compliance requirements
Cloud and on-premise infrastructure configurations
We use this information to design a roadmap that matches your business model, technical environment, and future expansion goals.
Tailored CI/CD Pipeline Development
Continuous Integration and Continuous Deployment (CI/CD) pipelines are essential for accelerating software releases. At CloudMinister, we create CI/CD frameworks that are tailored to your workflow, integrating seamlessly with your repositories, testing tools, and production environments. These pipelines are built to support:
Automated testing at each stage of the build
Secure, multi-environment deployments
Blue-green or canary releases based on your delivery strategy
Integration with tools like GitLab, Jenkins, Bitbucket, and others
Infrastructure as Code (IaC) Customized for Your Stack
We use leading Infrastructure as Code tools such as Terraform, AWS CloudFormation, and Ansible to help automate infrastructure provisioning. Each deployment is configured based on your stack, environment type, and scalability needs—whether cloud-native, hybrid, or legacy. This ensures repeatable deployments, fewer manual errors, and better control over your resources.
Customized Containerization and Orchestration
Containerization is at the core of modern DevOps practices. Whether your application is built for Docker, Kubernetes, or OpenShift, our team tailors the container ecosystem to suit your service dependencies, traffic patterns, and scalability requirements. From stateless applications to persistent volume management, we ensure your services are optimized for performance and reliability.
Monitoring and Logging Built Around Your Metrics
Monitoring and observability are not just about uptime—they are about capturing the right metrics that define your business’s success. We deploy customized dashboards and logging frameworks using tools like Prometheus, Grafana, Loki, and the ELK stack. These systems are designed to track application behavior, infrastructure health, and business-specific KPIs in real-time.
DevSecOps Tailored for Regulatory Compliance
Security is integrated into every stage of our DevOps pipelines through our DevSecOps methodology. We customize your pipeline to include vulnerability scanning, access control policies, automated compliance reporting, and secret management using tools such as Vault, SonarQube, and Aqua. Whether your business operates in finance, healthcare, or e-commerce, our solutions ensure your system meets all necessary compliance standards like GDPR, HIPAA, or PCI-DSS.
Case Study: Optimizing DevOps for a FinTech Organization
A growing FinTech firm approached CloudMinister Technologies with a need to modernize their software delivery process. Their primary challenges included slow deployment cycles, manual error-prone processes, and compliance difficulties.
After an in-depth consultation, our team proposed a custom DevOps solution which included:
Building a tailored CI/CD pipeline using GitLab and Jenkins
Automating infrastructure on AWS with Terraform
Implementing Kubernetes for service orchestration
Integrating Vault for secure secret management
Enforcing compliance checks with automated auditing
As a result, the company achieved:
A 70 percent reduction in deployment time
Streamlined compliance reporting with automated logging
Full visibility into release performance
Better collaboration between development and operations teams
This engagement not only improved their operational efficiency but also gave them the confidence to scale rapidly.
Business Benefits of Customized DevOps Solutions
Partnering with CloudMinister Technologies for customized DevOps implementation offers several strategic benefits:
Streamlined deployment processes tailored to your workflow
Reduced operational costs through optimized resource usage
Increased release frequency with lower failure rates
Enhanced collaboration between development, operations, and security teams
Scalable infrastructure with version-controlled configurations
Real-time observability of application and infrastructure health
End-to-end security integration with compliance assurance
Industries We Serve
We provide specialized DevOps services for diverse industries, each with its own regulatory, technological, and operational needs:
Financial Services and FinTech
Healthcare and Life Sciences
Retail and eCommerce
Software as a Service (SaaS) providers
EdTech and eLearning platforms
Media, Gaming, and Entertainment
Each solution is uniquely tailored to meet industry standards, customer expectations, and digital transformation goals.
Why CloudMinister Technologies?
CloudMinister Technologies stands out for its commitment to client-centric innovation. Our strength lies not only in the tools we use, but in how we customize them to empower your business.
What makes us the right DevOps partner:
A decade of experience in DevOps, cloud management, and server infrastructure
Certified engineers with expertise in AWS, Azure, Kubernetes, Docker, and CI/CD platforms
24/7 client support with proactive monitoring and incident response
Transparent engagement models and flexible service packages
Proven track record of successful enterprise DevOps transformations
Frequently Asked Questions
What does customization mean in DevOps services? Customization means aligning tools, pipelines, automation processes, and infrastructure management based on your business’s existing systems, goals, and compliance requirements.
Can your DevOps services be implemented on AWS, Azure, or Google Cloud? Yes, we provide cloud-specific DevOps solutions, including tailored infrastructure management, CI/CD automation, container orchestration, and security configuration.
Do you support hybrid cloud and legacy systems? Absolutely. We create hybrid pipelines that integrate seamlessly with both modern cloud-native platforms and legacy infrastructure.
How long does it take to implement a customized DevOps pipeline? The timeline varies based on the complexity of the environment. Typically, initial deployment starts within two to six weeks post-assessment.
What if we already have a DevOps process in place? We analyze your current DevOps setup and enhance it with better tools, automation, and customized configurations to maximize efficiency and reliability.
Ready to Transform Your Operations?
At CloudMinister Technologies, we don’t just implement DevOps—we tailor it to accelerate your success. Whether you are a startup looking to scale or an enterprise aiming to modernize legacy systems, our experts are here to deliver a DevOps framework that is as unique as your business.
Contact us today to get started with a personalized consultation.
Visit: www.cloudminister.com Email: [email protected]
0 notes
Text
Secure Software Development: Protecting Apps in the USA, Netherlands, and Germany

In today’s digital landscape, where cyber threats are evolving rapidly, secure software development is critical for businesses across the globe. Companies in the USA, Netherlands, and Germany are increasingly prioritizing security to protect their applications and user data. By leveraging custom software development services, organizations can build robust, secure applications tailored to their needs while adhering to regional regulations and industry standards. This blog explores key strategies for secure software development and highlights best practices for safeguarding apps in these tech-forward regions.
Why Secure Software Development Matters
The rise in cyberattacks—such as data breaches, ransomware, and phishing—has made security a top priority for developers. In the USA, high-profile breaches have pushed companies to adopt stringent security measures. In the Netherlands, a hub for tech innovation, businesses face pressure to comply with GDPR and other EU regulations. Similarly, Germany’s strong emphasis on data privacy drives demand for secure development practices. Without a security-first approach, applications risk vulnerabilities that can lead to financial losses and reputational damage.
Key Strategies for Secure Software Development
1. Adopt a Security-First Mindset
Secure software development begins with embedding security into every phase of the development lifecycle. This includes:
Threat Modeling: Identify potential risks early, such as SQL injection or cross-site scripting (XSS), during the design phase.
Secure Coding Standards: Follow guidelines like OWASP’s Secure Coding Practices to minimize vulnerabilities.
Regular Training: Equip developers with up-to-date knowledge on emerging threats, tailored to regional concerns like GDPR compliance in the Netherlands.
For example, Dutch companies often integrate GDPR requirements into their threat models, while US-based firms may focus on compliance with standards like SOC 2.
2. Implement Robust Testing Practices
Testing is critical to identify and fix vulnerabilities before deployment. Key testing methods include:
Static Application Security Testing (SAST): Analyze source code for vulnerabilities during development.
Dynamic Application Security Testing (DAST): Test running applications to uncover runtime issues.
Penetration Testing: Simulate real-world attacks to evaluate app resilience.
In Germany, where data protection laws are stringent, companies often conduct rigorous penetration testing to ensure compliance with the Federal Data Protection Act (BDSG).
3. Leverage Encryption and Authentication
Protecting data in transit and at rest is non-negotiable. Use:
End-to-End Encryption: Safeguard sensitive data, such as user credentials or payment information.
Multi-Factor Authentication (MFA): Add an extra layer of security to prevent unauthorized access.
Secure APIs: Validate and sanitize inputs to protect against API-based attacks.
US companies, especially in fintech, prioritize encryption to meet standards like PCI DSS, while Dutch firms focus on secure APIs to support their thriving e-commerce sector.
4. Stay Compliant with Regional Regulations
Each region has unique compliance requirements:
USA: Adhere to standards like HIPAA for healthcare apps or CCPA for consumer data privacy.
Netherlands: Comply with GDPR, which mandates strict data handling and user consent protocols.
Germany: Follow GDPR and BDSG, emphasizing data minimization and user rights.
Integrating compliance into the development process ensures apps meet legal and industry standards, reducing the risk of penalties.
5. Embrace DevSecOps
DevSecOps integrates security into DevOps workflows, enabling continuous security monitoring. Key practices include:
Automated Security Scans: Use tools like Snyk or Checkmarx to detect vulnerabilities in real-time.
Continuous Monitoring: Track app performance post-deployment to identify suspicious activity.
Collaboration: Foster communication between development, security, and operations teams.
This approach is particularly popular in the Netherlands, where tech companies use DevSecOps to accelerate secure app delivery.
Regional Insights: Tailoring Security Practices
USA: With a diverse tech ecosystem, US developers focus on scalable security solutions. Cloud-based security tools and AI-driven threat detection are widely adopted, especially in Silicon Valley.
Netherlands: As a leader in digital infrastructure, Dutch firms emphasize privacy-by-design principles, aligning with GDPR. Rotterdam and Amsterdam-based startups often integrate security into agile workflows.
Germany: Known for precision, German companies prioritize thorough documentation and compliance. Munich’s tech scene leverages advanced encryption to protect industrial IoT applications.
Conclusion
Secure software development is no longer optional—it’s a necessity. By adopting a security-first mindset, implementing robust testing, leveraging encryption, ensuring compliance, and embracing DevSecOps, businesses in the USA, Netherlands, and Germany can protect their applications from evolving threats. Partnering with a trusted software development company ensures access to expertise and tailored solutions, empowering organizations to build secure, reliable, and compliant apps that drive success in today’s competitive markets.
#software development company#software development services#software development services company#custom software development services
0 notes
Text
Security and Compliance in the Cloud: Best Practices for Modern Workflows
As businesses accelerate cloud adoption, security and compliance remain two of the most critical—and complex—challenges they face. Cloud environments offer flexibility, scalability, and cost savings, but they also require a new approach to protecting data, ensuring privacy, and meeting regulatory requirements.
In today’s fast-paced digital landscape, traditional security methods are no longer sufficient. Organizations must adopt cloud-native security practices and embed compliance into every stage of their workflow, from development to deployment.
This article explores the top best practices for maintaining robust security and achieving compliance in modern cloud-based environments.
The Cloud Security Landscape
Cloud security involves protecting data, applications, and infrastructure from internal and external threats. It encompasses everything from access control and data encryption to incident response and vulnerability management.
The shared responsibility model defines that while cloud providers (like AWS, Azure, or GCP) secure the infrastructure, organizations are responsible for securing their own data and workloads. That makes it vital for businesses to adopt proactive security strategies tailored for cloud environments.
Key Compliance Considerations
Compliance refers to adhering to regulatory standards and industry frameworks, such as:
GDPR (General Data Protection Regulation)
HIPAA (Health Insurance Portability and Accountability Act)
PCI DSS (Payment Card Industry Data Security Standard)
ISO/IEC 27001
SOC 2
Each regulation comes with specific requirements for how data is stored, processed, and protected—especially in the cloud.
Failing to comply can lead to legal consequences, financial penalties, and reputational damage. That’s why security and compliance must go hand-in-hand.
Best Practices for Security and Compliance in the Cloud
1. Implement Zero Trust Architecture
Adopt a Zero Trust model that assumes no user or system is inherently trusted. This involves:
Strict identity verification
Least privilege access
Micro-segmentation
Continuous monitoring
Zero Trust helps reduce the attack surface and prevents lateral movement in case of breaches.
2. Use Encryption Everywhere
Encrypt data at rest, in transit, and during processing using industry-standard protocols. Make use of:
Key Management Services (KMS)
Bring Your Own Key (BYOK) strategies
Hardware Security Modules (HSMs)
This ensures sensitive information remains protected, even if unauthorized access occurs.
3. Automate Compliance Monitoring
Manual compliance audits are time-consuming and error-prone. Use automated tools that continuously monitor and audit your cloud infrastructure for compliance against predefined frameworks.
Tools like AWS Config, Azure Policy, and third-party solutions such as Prisma Cloud or Dome9 can detect and remediate policy violations in real-time.
4. Secure the CI/CD Pipeline
Your development pipeline is a potential attack vector. Secure it by:
Scanning code for vulnerabilities (SAST/DAST)
Verifying container and artifact integrity
Enforcing code signing and access controls
Implementing secrets management
This ensures that security and compliance are integrated into your DevSecOps workflow from day one.
5. Regularly Audit Access Controls
Set up role-based access controls (RBAC) and enforce multi-factor authentication (MFA). Periodically review access logs to detect unusual activity and revoke unused permissions.
Use tools like IAM analyzers to maintain tight control over who can access what.
6. Perform Continuous Risk Assessments
Cloud environments are dynamic, which means your security posture can change quickly. Schedule regular penetration testing, vulnerability scans, and risk assessments to stay ahead of threats.
Integrate these insights into your incident response plans to be better prepared for emergencies.
7. Leverage Cloud-Native Security Services
Cloud providers offer robust native security services. Use them to your advantage:
AWS GuardDuty, Inspector, Security Hub
Azure Security Center
Google Security Command Center
These tools provide insights, threat detection, and compliance recommendations tailored to your environment.
How Salzen Cloud Supports Secure Cloud Transformation
At Salzen Cloud, we understand that cloud transformation is only as strong as the security that underpins it. Our cloud experts help enterprises integrate end-to-end security and compliance practices into their modern workflows, ensuring continuous protection, regulatory alignment, and peace of mind.
From secure cloud architecture to compliance automation and threat monitoring, we make sure every part of your cloud journey is built on a foundation of trust and control.
Final Thoughts
Security and compliance aren’t just checkboxes—they’re essential components of a successful cloud strategy. In the era of constant digital change, building secure and compliant workflows requires a proactive, automated, and integrated approach.
By following the best practices outlined above and partnering with experts like Salzen Cloud, organizations can ensure their cloud environments are not only high-performing—but also fully secure and compliant from the ground up.
0 notes
Text
How to Secure AI Artifacts Across the ML Lifecycle – Anton R Gordon’s Protocol for Trusted Pipelines
In today’s cloud-native AI landscape, securing machine learning (ML) artifacts is no longer optional—it’s critical. As AI models evolve from experimental notebooks to enterprise-scale applications, every artifact generated—data, models, configurations, and logs—becomes a potential attack surface. Anton R Gordon, a seasoned AI architect and cloud security expert, has pioneered a structured approach for securing AI pipelines across the ML lifecycle. His protocol is purpose-built for teams deploying ML workflows on platforms like AWS, GCP, and Azure.
Why ML Artifact Security Matters
Machine learning pipelines involve several critical stages—data ingestion, preprocessing, model training, deployment, and monitoring. Each phase produces artifacts such as datasets, serialized models, training logs, and container images. If compromised, these artifacts can lead to:
Data leakage and compliance violations (e.g., GDPR, HIPAA)
Model poisoning or backdoor attacks
Unauthorized model replication or intellectual property theft
Reduced model accuracy due to tampered configurations
Anton R Gordon’s Security Protocol for Trusted AI Pipelines
Anton’s methodology combines secure cloud services with DevSecOps principles to ensure that ML artifacts remain verifiable, auditable, and tamper-proof.
1. Secure Data Ingestion & Preprocessing
Anton R Gordon emphasizes securing the source data using encrypted S3 buckets or Google Cloud Storage with fine-grained IAM policies. All data ingestion pipelines must implement checksum validation and data versioning to ensure integrity.
He recommends integrating AWS Glue with Data Catalog encryption enabled, and VPC-only connectivity to eliminate exposure to public internet endpoints.
2. Model Training with Encryption and Audit Logging
During training, Anton R Gordon suggests enabling SageMaker Training Jobs with KMS encryption for both input and output artifacts. Logs should be streamed to CloudWatch Logs or GCP Logging with retention policies configured.
Docker containers used in training should be scanned with AWS Inspector or GCP Container Analysis, and signed using tools like cosign to verify authenticity during deployment.
3. Model Registry and Artifact Signing
A crucial step in Gordon’s protocol is registering models in a version-controlled model registry, such as SageMaker Model Registry or MLflow, along with cryptographic signatures.
Models are hashed and signed using SHA-256 and stored with corresponding metadata to prevent rollback or substitution attacks. Signing ensures that only approved models proceed to deployment.
4. Secure Deployment with CI/CD Integration
Anton integrates CI/CD pipelines with security gates using tools like AWS CodePipeline and GitHub Actions, enforcing checks for signed models, container scan results, and infrastructure-as-code validation.
Deployed endpoints are protected using VPC endpoint policies, IAM role-based access, and SSL/TLS encryption.
5. Monitoring & Drift Detection with Alerting
In production, SageMaker Model Monitor and Amazon CloudTrail are used to detect unexpected behavior or changes to model behavior or configurations. Alerts are sent via Amazon SNS, and automated rollbacks are triggered on anomaly detection.
Final Thoughts
Anton R Gordon’s protocol for securing AI artifacts offers a holistic, scalable, and cloud-native strategy to protect ML pipelines in real-world environments. As AI adoption continues to surge, implementing these trusted pipeline principles ensures your models—and your business—remain resilient, compliant, and secure.
0 notes
Text
Why AcmeMinds Is a Leading DevOps Services Company for Agile Business Transformation?
In today’s fast-paced digital era, agility is no longer a luxury but a necessity. Businesses aiming for rapid innovation and scalability must embrace agile methodologies to stay ahead. One key enabler of agile transformation is DevOps—an integrated approach to software development and operations that fosters collaboration, automation, and continuous improvement. At the forefront of this shift is AcmeMinds, recognized as a leading DevOps services company helping enterprises unlock new levels of efficiency and agility.
After more than 50 words, let's dig deeper into why AcmeMinds stands out as a top-tier DevOps services provider and how their tailored strategies empower agile business transformation.
Bridging Development and Operations Seamlessly
At its core, DevOps focuses on breaking down the silos between software development and IT operations. AcmeMinds leverages cutting-edge DevOps practices to create a seamless workflow across the software lifecycle. From continuous integration and continuous deployment (CI/CD) pipelines to automated testing and monitoring, their DevOps solutions enable faster releases with fewer errors.
As a forward-thinking DevOps consulting company, AcmeMinds ensures that your infrastructure is built for speed, scalability, and resilience. Their team evaluates your current systems and designs a roadmap tailored to your needs, whether you’re launching a new product or modernizing legacy architecture.
Why Businesses Choose AcmeMinds as Their DevOps Partner
Custom DevOps Solutions: AcmeMinds understands that no two businesses are the same. Their DevOps services are customized to align with your operational goals, team structure, and technology stack.
Full Lifecycle Support: From planning and implementation to maintenance and optimization, AcmeMinds supports the entire DevOps lifecycle. They offer services such as infrastructure as code (IaC), release orchestration, and automated performance monitoring.
Toolchain Expertise: AcmeMinds integrates industry-leading DevOps tools like Jenkins, Docker, Kubernetes, GitLab, Ansible, and Terraform to streamline workflows. This ensures continuous delivery with improved code quality and shorter time-to-market.
Culture and Collaboration: DevOps is more than tools—it's about a cultural shift. AcmeMinds fosters collaboration across development, operations, and QA teams to build a shared sense of responsibility and accelerate delivery cycles.
Security and Compliance: As a modern DevOps solutions provider, AcmeMinds embeds security into the DevOps pipeline—known as DevSecOps—helping businesses remain compliant with industry standards while reducing vulnerabilities.
DevOps in Action: Real Results for Agile Enterprises
AcmeMinds has successfully transformed the delivery pipelines of enterprises across industries—tech startups, e-commerce platforms, and enterprise SaaS providers. For instance, a retail client was able to reduce deployment time from 5 days to under 2 hours thanks to AcmeMinds’ automated CI/CD framework. Another enterprise reduced post-deployment issues by 70% through advanced monitoring and testing integrations.
Such results make AcmeMinds not just a DevOps services company but a trusted digital transformation partner.
The AcmeMinds Advantage: Beyond DevOps
AcmeMinds goes beyond technical implementation. They offer strategic guidance, training, and post-deployment support to ensure long-term success. With their agile-first mindset and customer-centric approach, they help businesses embrace a DevOps culture and unlock new revenue streams through faster innovation cycles.
In an ecosystem where downtime and delays cost millions, partnering with a reliable DevOps company like AcmeMinds can be the game-changer your business needs.
Final Thoughts
Choosing the right DevOps services company is crucial for any business aiming to adopt agile methodologies and improve operational efficiency. AcmeMinds combines technical expertise with business insight to deliver customized, scalable, and secure DevOps solutions that drive real business value. Whether you're a startup or an enterprise, AcmeMinds ensures your software delivery pipeline is agile, automated, and always ahead of the curve.
0 notes
Text
Secure from the Start: Unlocking Success with DevOps Security Services
In today’s hyperconnected world, application security can’t be an afterthought. That’s where DevOps Security Services—better known as DevSecOps—come in. This approach integrates security from the ground up, embedding protection across the entire software development lifecycle. Through robust DevSecOps practices, businesses can proactively detect vulnerabilities, ensure compliance, and scale securely.
🔐 What is DevSecOps? DevSecOps stands for Development, Security, and Operations. It's a modern approach that weaves security into every step of software creation—from planning and coding to deployment and monitoring. Unlike traditional models where security checks happen late, DevSecOps empowers teams to identify and fix risks early, preventing costly breaches and delays.
⚙️ Common DevSecOps Tools To build secure and resilient applications, top teams rely on a powerful suite of tools:
🔍 Static Application Security Testing (SAST) Scans source code for bugs and vulnerabilities before deployment. Examples: SonarQube, Fortify
🛡️ Dynamic Application Security Testing (DAST) Simulates attacks to expose external security flaws—no source code access needed. Examples: Burp Suite, OWASP ZAP
🧩 Software Composition Analysis (SCA) Audits open-source libraries and third-party components for known vulnerabilities. Examples: Snyk, WhiteSource
⚡ Interactive Application Security Testing (IAST) Blends SAST and DAST to offer real-time, runtime analysis during testing. Examples: Seeker, Hdiv
🚀 Key Benefits of Implementing DevOps Security Services ✅ Improved Security Security is built into every phase, so vulnerabilities are addressed before they escalate.
✅ Faster Time to Market Automation and early detection reduce bottlenecks and speed up delivery.
✅ Regulatory Compliance Stay compliant with GDPR, HIPAA, PCI-DSS, and other industry standards.
✅ Better Code Quality Frequent testing and reviews ensure clean, maintainable code.
✅ Secure Feature Development Roll out new features without compromising application integrity.
🔄 How DevSecOps is Integrated Across the Lifecycle 📝 Planning & Development Security begins in the planning phase, with an evaluation of current systems and potential risks to shape a secure development strategy.
🔨 Building & Testing Automation tools merge code and identify issues early. Security testing is integrated into CI/CD pipelines for immediate feedback.
🚚 Deployment & Operation Using Infrastructure as Code (IaC), deployment is automated and secure. IaC helps eliminate human error and ensures consistency.
📈 Monitoring & Scaling Powerful monitoring tools are used to detect threats in real-time, while scalability is maintained to support growth without compromising security.
0 notes
Text
Enhancing Security in Cloud-Native Applications: Key Strategies

In the evolving landscape of cloud-native applications, security is paramount. This article delves into essential practices that fortify security and resilience in cloud environments.
1.Robust identity and access management (IAM)
Implement role-based access control.
Adhere to the principle of least privilege.
Employ multi-factor authentication.
2. Securing application secrets
Securely store API keys, passwords, and certificates using secret management tools.
Rotate secrets routinely and automate this process.
3. Utilization of secure containers
Regularly update container images to mitigate vulnerabilities.
Select trusted base images and conduct vulnerability scans.
Operate containers with the minimal required privileges.
4. Network security implementation
Deploy firewalls and network segmentation to control traffic flow.
Use secure communication protocols like TLS for data in transit.
5. Compliance and auditing
Conduct regular audits of cloud resources and configurations.
Ensure adherence to industry standards and regulations.
6. Secure software development lifecycle (SDLC)
Embed security in the development process, embracing practices like DevSecOps.
Perform regular code reviews and utilize code analysis tools.
7. Automating security
Leverage automated tools for vulnerability monitoring and response.
Automate threat responses.
8. Backup and disaster recovery
Regularly backup data and establish a disaster recovery plan.
Periodically test backup and recovery procedures.
9. Staff education and training
Provide ongoing training on security best practices.
Foster a culture of security awareness.
10. Monitoring and threat response
Implement monitoring solutions for threat detection.
Develop a response plan for various security incidents.
Additional considerations:
Zero trust architecture: Treat every microservice with skepticism, avoiding blind inter-service trust.
Input validation: Rigorously validate and sanitize all inputs, treating them as potential threats.
Internet exposure control: Limit internet access to essential components using advanced firewall settings and VPCs.
Secure file storage: Encrypt sensitive data at rest and implement role-based access.
Log data masking: Employ automated redaction tools and centralized log management.
In today’s dynamic digital landscape, implementing these security practices is crucial, but it can be challenging to navigate the complexities alone. This is where Centizen Cloud Consulting Services comes in. Our expert team specializes in crafting bespoke cloud security strategies that align with your specific business needs. From initial assessment to implementation and ongoing management, we provide end-to-end support to ensure your cloud-native applications are not only secure but also optimized for performance and scalability. Partner with Centizen to transform these best practices into a robust, secure foundation for your cloud-native journey.
0 notes
Text
Driving Scalable Innovation Through Cloud Engineering and Managed DevOps Solutions
The accelerating pace of digital transformation is forcing enterprises to rethink their technology strategies. Legacy systems, siloed teams, and manual processes no longer support the level of agility, speed, and innovation that modern businesses demand. In this context, organizations are increasingly turning to managed cloud services, managed DevOps, and cloud engineering to overcome digital bottlenecks and future-proof their operations.

These integrated services go far beyond just cloud migration or server maintenance. They form the foundation of a modern, responsive digital enterprise—where infrastructure is dynamic, software delivery is continuous, and customer experiences are seamless. This article explores how these solutions, backed by expert guidance and strategic consulting, enable businesses to achieve scalable innovation across industries.
Managed Cloud Services: A Strategic Enabler
Managed cloud services provide a strategic approach to cloud adoption, combining infrastructure management, monitoring, security, and optimization into one cohesive solution. These services empower businesses to offload the complexity of managing public, private, or hybrid cloud environments while ensuring high performance and compliance.
Core benefits include:
Operational Efficiency: Streamlined provisioning, backup, monitoring, and updates reduce operational overhead.
Cost Management: Real-time insights and automated scaling optimize spending and eliminate resource wastage.
Security and Compliance: Continuous patching, vulnerability management, and adherence to industry standards like HIPAA, GDPR, or ISO 27001.
Rapid Deployment: Faster provisioning of environments enables quicker go-to-market for digital products.
By leveraging managed cloud services, enterprises can shift their focus from maintenance to innovation—accelerating the delivery of new features, products, and capabilities.
Managed DevOps: Automating Delivery and Driving Collaboration
Software development today demands speed and stability in equal measure. Managed DevOps enables organizations to automate and optimize their development pipelines, ensuring fast, reliable, and secure software delivery. Instead of building DevOps expertise in-house, companies can rely on managed service providers to design, implement, and maintain their CI/CD environments.
Key capabilities of managed DevOps include:
CI/CD Pipeline Automation: Seamless integration of version control, automated testing, and deployment tools.
Infrastructure as Code: Consistent and repeatable infrastructure provisioning using Terraform, Ansible, or AWS CloudFormation.
Monitoring and Observability: Real-time tracking of application performance, resource usage, and potential issues.
Security as Code (DevSecOps): Integration of security policies throughout the development lifecycle, minimizing risks and accelerating compliance.
Managed DevOps bridges the gap between development and operations teams, fostering a culture of collaboration, transparency, and continuous improvement.
Cloud Engineering: Architecting for Performance and Resilience
While cloud adoption is widespread, not every implementation delivers optimal performance or cost savings. That’s where cloud engineering becomes essential. This discipline focuses on the design, development, and deployment of scalable, secure, and high-performance cloud-native architectures.
Cloud engineering services typically include:
Cloud Architecture Design: Tailored multi-cloud or hybrid-cloud strategies built around specific workloads and performance needs.
Application Modernization: Transitioning monolithic legacy applications into microservices or serverless models.
Automation and Orchestration: Deploying Kubernetes, Helm, Jenkins, and other tools to automate and orchestrate infrastructure and apps.
Disaster Recovery Planning: Architecting robust failover mechanisms and data backup solutions to ensure business continuity.
With cloud engineering, enterprises gain a resilient foundation for innovation—one that evolves alongside business demands and technology advancements.
Digital Transformation: The Broader Vision
Digital transformation is no longer a buzzword—it’s a necessity. It involves a fundamental shift in how businesses operate, deliver value, and interact with stakeholders. While cloud and DevOps are essential enablers, digital transformation also includes data strategy, automation, artificial intelligence, and workforce enablement.
Common goals of digital transformation include:
Improved Customer Experience: Personalization, real-time support, and omnichannel engagement.
Operational Agility: Replacing legacy systems with cloud-native platforms that adapt to change.
Data-Driven Decision Making: Using analytics and machine learning to uncover insights and drive actions.
Workforce Empowerment: Enabling remote work, self-service platforms, and cross-functional collaboration through digital tools.
A well-executed transformation strategy breaks down silos, enhances visibility, and creates a digital-first culture that supports sustained growth.
Why Integration Matters
The real power lies not in isolated services but in the integration of managed cloud services, managed DevOps, cloud engineering, and digital transformation. When combined, these services create a unified framework that accelerates innovation across every part of the enterprise.
For instance:
A cloud-native e-commerce platform can deploy updates multiple times a day using DevOps pipelines, backed by a scalable infrastructure managed through cloud services.
A healthcare organization can modernize its patient management system using cloud engineering, while ensuring data privacy through managed security and compliance frameworks.
A manufacturing company can implement IoT and AI analytics as part of its digital transformation, supported by resilient and optimized cloud architecture.
The synergy between these services leads to outcomes that are greater than the sum of their parts.
Overcoming Common Challenges
Despite the clear benefits, many organizations face obstacles in their digital journey:
Talent Gaps: Recruiting and retaining skilled DevOps engineers, cloud architects, or cybersecurity experts is difficult and expensive.
Legacy Infrastructure: Outdated systems often lack compatibility with modern platforms, creating integration hurdles.
Change Resistance: Internal resistance to process and culture changes can slow adoption.
Cost Overruns: Poorly managed cloud environments often lead to ballooning costs and underutilized resources.
Engaging with experienced service providers helps organizations overcome these roadblocks. Through proven frameworks, automation, and strategic roadmaps, companies can fast-track transformation with reduced risk and higher ROI.
Real-World Industry Impact
The adoption of these managed services is evident across industries:
Banking & Finance: Secure, compliant cloud infrastructure and DevOps pipelines support mobile banking and fraud detection.
Retail & E-Commerce: Real-time inventory tracking, AI-powered recommendations, and scalable infrastructure boost customer engagement.
Education: Remote learning platforms, digital content delivery, and performance tracking powered by cloud-native apps.
Logistics & Transportation: Predictive maintenance, route optimization, and real-time tracking using cloud and IoT solutions.
Each use case underscores the importance of integrating technology with business strategy to deliver measurable results.
The Role of Strategic IT Consulting
Technology alone isn't enough. Successful transformation requires careful planning, change management, and governance. That’s where IT consulting plays a vital role.
Consulting services guide organizations through:
Cloud Readiness Assessments: Evaluating current systems, workloads, and readiness for cloud migration.
DevOps Maturity Models: Identifying gaps in existing delivery pipelines and recommending improvements.
Architecture Reviews: Ensuring cloud architectures align with business and technical goals.
Risk Mitigation: Managing compliance, data protection, and operational risks proactively.
Consulting ensures that businesses make informed decisions, avoid costly missteps, and adopt technologies that align with their long-term objectives.
Final Thoughts: Building a Resilient Digital Future
In a digital-first world, the ability to adapt quickly is no longer optional—it’s essential. With managed cloud services, managed DevOps, cloud engineering, and digital transformation strategies, businesses can build an agile foundation that supports continuous innovation, reduces operational complexity, and delivers superior customer experiences.
These solutions provide the tools, automation, and expertise needed to stay competitive in a rapidly evolving market. By embracing them holistically, organizations are not only solving today’s challenges but also setting the stage for long-term digital success.
1 note
·
View note
Text
Navigating the DevOps Landscape: A Beginner's Comprehensive
Roadmap In the dynamic realm of software development, the DevOps methodology stands out as a transformative force, fostering collaboration, automation, and continuous enhancement. For newcomers eager to immerse themselves in this revolutionary culture, this all-encompassing guide presents the essential steps to initiate your DevOps expedition.

Grasping the Essence of DevOps Culture: DevOps transcends mere tool usage; it embodies a cultural transformation that prioritizes collaboration and communication between development and operations teams. Begin by comprehending the fundamental principles of collaboration, automation, and continuous improvement.
Immerse Yourself in DevOps Literature: Kickstart your journey by delving into indispensable DevOps literature. "The Phoenix Project" by Gene Kim, Jez Humble, and Kevin Behr, along with "The DevOps Handbook," provides invaluable insights into the theoretical underpinnings and practical implementations of DevOps.
Online Courses and Tutorials: Harness the educational potential of online platforms like Coursera, edX, and Udacity. Seek courses covering pivotal DevOps tools such as Git, Jenkins, Docker, and Kubernetes. These courses will furnish you with a robust comprehension of the tools and processes integral to the DevOps terrain.
Practical Application: While theory is crucial, hands-on experience is paramount. Establish your own development environment and embark on practical projects. Implement version control, construct CI/CD pipelines, and deploy applications to acquire firsthand experience in applying DevOps principles.

Explore the Realm of Configuration Management: Configuration management is a pivotal facet of DevOps. Familiarize yourself with tools like Ansible, Puppet, or Chef, which automate infrastructure provisioning and configuration, ensuring uniformity across diverse environments.
Containerization and Orchestration: Delve into the universe of containerization with Docker and orchestration with Kubernetes. Containers provide uniformity across diverse environments, while orchestration tools automate the deployment, scaling, and management of containerized applications.
Continuous Integration and Continuous Deployment (CI/CD): Integral to DevOps is CI/CD. Gain proficiency in Jenkins, Travis CI, or GitLab CI to automate code change testing and deployment. These tools enhance the speed and reliability of the release cycle, a central objective in DevOps methodologies.
Grasp Networking and Security Fundamentals: Expand your knowledge to encompass networking and security basics relevant to DevOps. Comprehend how security integrates into the DevOps pipeline, embracing the principles of DevSecOps. Gain insights into infrastructure security and secure coding practices to ensure robust DevOps implementations.
Embarking on a DevOps expedition demands a comprehensive strategy that amalgamates theoretical understanding with hands-on experience. By grasping the cultural shift, exploring key literature, and mastering essential tools, you are well-positioned to evolve into a proficient DevOps practitioner, contributing to the triumph of contemporary software development.
2 notes
·
View notes
Text
DevSecOps: Integrating Security into Every Stage of DevOps

As businesses shift to faster software delivery through agile methodologies and automation, securing applications and infrastructure from the start has become more critical than ever. This is where DevSecOps comes into play—a modern approach that integrates security practices directly into the DevOps lifecycle. Instead of treating security as an afterthought, DevSecOps ensures that it is embedded at every phase: from planning and development to deployment and monitoring.
Organizations embracing DevSecOps benefit from faster detection of vulnerabilities, improved compliance, and stronger collaboration between developers, security teams, and operations. It’s a cultural and technical transformation that’s redefining DevOps services and solutions globally.
What is DevSecOps?
DevSecOps stands for Development, Security, and Operations. It promotes a “security as code” philosophy, where security checks, controls, and policies are automated and built into CI/CD pipelines. In traditional workflows, security was often introduced late in the process, resulting in delays and costly reworks. With DevSecOps, automated security testing tools (like SAST, DAST, and dependency scanners) are integrated into the development process itself.
This shift-left strategy reduces risks and ensures vulnerabilities are identified and resolved early, when fixes are simpler and less expensive.
DevSecOps in Action: A Real-World Example
Let’s take the case of a fintech company launching a new online payment feature. Previously, their release cycle was slowed by manual penetration testing carried out just before deployment. After adopting DevSecOps, they integrated automated vulnerability scanning and static code analysis into their CI pipeline. This allowed developers to detect and fix issues during development, speeding up the release cycle by 30% while improving security posture.
Enhancing DevSecOps with DevOps Consulting Services
Implementing DevSecOps effectively requires expert guidance on selecting the right tools, defining workflows, and training teams. This is where DevOps consulting services play a vital role. Consultants help assess the organization’s security maturity, integrate security checkpoints within pipelines, and automate compliance reporting.
If your organization is looking to integrate security without slowing down development, consider exploring DevOps consulting services designed for seamless security integration.
Security in Managed Cloud: DevSecOps and Consulting
Cloud environments are dynamic, scalable, and often complex—making them particularly vulnerable to misconfigurations and attacks. By combining DevSecOps with devops consulting and managed cloud services, companies can ensure that their cloud-native infrastructure is both efficient and secure.
From automated secrets management to role-based access controls and infrastructure scanning, managed service providers can implement comprehensive security practices using DevSecOps principles.
For more insights on how cloud management is evolving through this integration, visit devops consulting and managed cloud services.
Role of DevOps Managed Services in DevSecOps
DevOps managed services providers are increasingly incorporating security layers across their solutions. By embedding security tools into monitoring, alerting, and deployment workflows, these providers offer clients secure, stable, and scalable environments without sacrificing agility.
For example, a managed services team might use real-time security alerts and compliance dashboards powered by tools like Aqua Security or Twistlock, ensuring quick remediation and audit-ready visibility.
Discover how DevOps managed services are elevating security standards in modern IT operations.
DevSecOps as a Key Component of DevOps Services and Solutions
As threats grow more sophisticated, security cannot remain a siloed responsibility. Modern devops services and solutions are now deeply integrated with DevSecOps principles, empowering organizations to build resilient systems without compromising on speed or innovation.
Whether it’s scanning container images, encrypting data at rest, or enforcing secure coding practices—DevSecOps is becoming the default rather than the exception. According to Gartner,
“By 2026, 60% of organizations will integrate security into DevOps pipelines, up from 20% in 2021.”
In the words of Shannon Lietz, a well-known DevSecOps advocate:
“Security has to be everyone’s responsibility—built into the code, baked into the pipeline.”
To see how organizations are adopting these cutting-edge strategies, explore the scope of devops services and solutions.
Final Thoughts
DevSecOps represents a fundamental shift in how security is perceived and implemented. By treating security as an integral part of the DevOps process—not a roadblock—organizations can aDevSecOps: Integrating Security into Every Stage of DevOpsccelerate innovation while maintaining trust and compliance.
Whether you're starting your DevSecOps journey or scaling your efforts, integrating security early and often will pay off in reliability, resilience, and peace of mind.
Ready to secure your DevOps pipeline with DevSecOps?Please visit Cloudastra DevOps as a Services if you are interested to study more content or explore our services. Our team of experienced devops services is here to help you turn innovation into reality—faster, smarter, and with measurable outcomes.
0 notes
Text
Best DevOps Training in Marathahalli Bangalore

Best DevOps Training Institute in Marathahalli Bangalore – Master DevOps & Accelerate Your Career
Looking to build a career in DevOps? Join the Best DevOps Training in Marathahalli Bangalore and gain hands-on expertise in top industry tools.
Whether you're a beginner or an experienced professional, this course will help you bridge the gap between development and operations seamlessly.
Why Choose Our DevOps Training Center in Marathahalli Bangalore?
Choose Our DevOps Training Center in Marathahalli Bangalore for:
✔ Comprehensive Curriculum – Master Docker, Kubernetes, Jenkins, Ansible, Git, Terraform, and more.
✔ Practical Learning – Work on real-world projects & case studies.
✔ Industry-Recognized Certification – Get a globally accepted certification.
✔ Expert-Led Training – Learn from industry professionals with hands-on experience.
✔ 100% Placement Assistance – Career guidance, resume building & interview preparation.
What You’ll Learn in Our DevOps Course in Marathahalli Bangalore
Our comprehensive DevOps Course in Marathahalli Bangalore covers:
🔹 DevOps Fundamentals – Concepts, best practices & industry trends
🔹 Version Control (Git & GitHub/GitLab) – Branching, merging & repo management
🔹 CI/CD Pipelines – Jenkins setup, automation & deployment strategies
🔹 Containerization – Manage applications using Docker & Kubernetes
🔹 Infrastructure as Code (IaC) – Automate cloud infrastructure with Ansible & Terraform
🔹 Cloud & DevOps – AWS, Azure, Google Cloud integration
🔹 Monitoring & Security – Implement ELK, Prometheus, Grafana, and DevSecOps
Who Should Enroll DevOps Certification Course in Marathahalli Bangalore
This DevOps Certification Course in Marathahalli Bangalore is perfect for:
✅ Software Developers & System Administrators
✅ Cloud & IT Professionals switching to DevOps
✅ Fresh Graduates looking for a DevOps career
Job Opportunities After DevOps Training in Marathahalli Bangalore
Upon completing our DevOps Training in Marathahalli Bangalore, you will be eligible for job roles such as:
✅ DevOps Engineer
✅ Cloud DevOps Architect
✅ Site Reliability Engineer (SRE)
✅ Release Manager
✅ Build & Release Engineer
Why is the Best Place for DevOps Training and placement in Marathahalli Bangalore?
As India’s IT hub, Bangalore offers excellent career opportunities for DevOps professionals. Top tech companies like Amazon, Google, Microsoft, Infosys, TCS, and Wipro are actively hiring DevOps experts. Completing your DevOps Training and placement in Marathahalli Bangalore enhances your job prospects and earning potential.
Enroll Today!
Join the top DevOps Training Institute in Marathahalli Bangalore and take the next step in your career.
📍 Location: 219, 1st Floor, Nagalaya, 3rd Cross, Neeladri Nagar, Electronic City, Bangalore, Karnataka 560100
☎ Call: +91-9513216462
📧 Email: [email protected]
🌐 Visit: https://www.emexotechnologies.com/courses/devops-training-in-marathahalli-bangalore/
<a href="https://www.emexotechnologies.com/courses/devops-training-in-marathahalli-bangalore/">DevOps Training in Marathahalli Bangalore</a>
#DevOps#DevOpsTraining#DevOpsCourse#LearnDevOps#DevOpsEngineer#DevOpsSkills#DevOpsCulture#Git#Jenkins#Docker#Kubernetes#Ansible#Terraform#Prometheus#Grafana#CI/CD#Automation#ITTraining#CloudComputing#SoftwareDevelopment#CareerGrowth#DevOpsTrainingcenterinBangalore#DevOpsTrainingInMarathahalliBangalore#DevOpsCourseInMarathahalliBangalore#DevOpsTrainingInstitutesInMarathahalliBangalore#DevOpsClassesInMarathahalliBangalore#BestDevOpsTrainingInMarathahalliBangalore#DevOpsTrainingandPlacementinMarathahalliBangalore
0 notes
Text
Cloud Security and Compliance: Proactive Measures for Modern Cloud Environments
As businesses rapidly adopt cloud technologies to power innovation and scale operations, the need for strong cloud security and compliance has never been more critical. Threats are evolving, regulations are tightening, and organizations must stay ahead with proactive strategies to protect their data, operations, and reputation.
In this blog, we'll explore the best proactive measures to secure modern cloud environments — and how partnering with Salzen Cloud can ensure your cloud systems remain compliant, resilient, and future-ready.
Why Cloud Security and Compliance Are Non-Negotiable
Modern cloud environments are dynamic, distributed, and complex, making them attractive targets for cyberattacks. Meanwhile, industries face increasing scrutiny from regulatory bodies with frameworks like GDPR, HIPAA, PCI-DSS, and ISO 27001.
Failure to address security and compliance risks can lead to data breaches, financial penalties, loss of customer trust, and serious business disruption.
Proactive security and compliance measures are essential for:
Protecting sensitive data and intellectual property
Ensuring business continuity and disaster recovery readiness
Meeting regulatory requirements and avoiding costly fines
Building customer trust and brand reputation
Key Proactive Measures for Cloud Security and Compliance
1. Adopt a Shared Responsibility Model
Understand that cloud providers secure the infrastructure, but customers are responsible for securing their applications, data, and user access. Always clarify responsibilities to avoid security gaps.
2. Implement Identity and Access Management (IAM)
Control who can access your cloud resources. Use multi-factor authentication (MFA), role-based access control (RBAC), and least privilege principles to minimize risks from compromised credentials.
3. Encrypt Data Everywhere
Encrypt data at rest, in transit, and even during processing. Use strong encryption standards and manage encryption keys securely.
4. Regularly Perform Security Audits and Penetration Testing
Proactively find vulnerabilities through regular audits and penetration testing. Continuous security assessments ensure vulnerabilities are identified and fixed before attackers can exploit them.
5. Automate Compliance Monitoring
Use automated tools to track compliance with internal policies and external regulations. Automation reduces manual errors and provides real-time visibility into compliance status.
6. Enable Continuous Monitoring and Incident Response
Monitor all cloud resources continuously for suspicious activity. Set up automated alerts and a well-defined incident response plan to react quickly when threats are detected.
7. Secure DevOps (DevSecOps)
Integrate security checks directly into the development lifecycle. This ensures vulnerabilities are caught early, not after deployment.
How Salzen Cloud Enhances Your Security and Compliance Posture
At Salzen Cloud, we help organizations build secure, compliant, and resilient cloud environments through customized strategies and cutting-edge technologies. Our cloud security services include:
Conducting comprehensive security assessments and compliance audits
Implementing advanced IAM policies, encryption standards, and network security measures
Automating compliance tracking and reporting across your cloud infrastructure
Integrating DevSecOps practices into your CI/CD pipelines
Providing 24/7 cloud monitoring and rapid incident response support
With Salzen Cloud as your security partner, you can focus on growth and innovation while we safeguard your critical assets.
Conclusion
Cloud adoption unlocks incredible opportunities, but without proactive security and compliance measures, it can also expose serious risks. To succeed in the modern digital era, businesses must prioritize security at every level and ensure full regulatory compliance.
By following best practices — and teaming up with experts like Salzen Cloud — your organization can build a cloud environment that's not only powerful and agile but also secure, resilient, and fully compliant.
Stay secure. Stay compliant. Stay ahead.
0 notes