#directory structure in OS
Explore tagged Tumblr posts
Text
Directory Structure in OS: Implementation, Types and Examples

Hello Learners! Today, we are going to show you all possible things about what is directory structure in OS; involving with their examples and types of directory structure in operating system with ease. This is ultimate article over the Internet. So, after reading this post, you will definitely educate about Directory Structure in Operating System without getting any hassle.
Article Hot Headlines:
In this section, we will show you all headlines about this entire article; you can check them as your choice; below shown all:
What is Directory in OS?
Directory Implementation in OS
Operations in Directory Structure
Types of Directory Structure in Operating System
Directory Structure in Windows OS
Directory Structure in Unix-Based OS
FAQs (Frequently Asked Questions)
What is the purpose of directory structure in OS?
What is the maximum number of files that can be stored in directory in OS?
Where is directory structure stored?
What is the root directory?
How are directories and files represented in a graphical user interface (GUI)?
What are some common directory names found in a directory structure?
How does the directory structure contribute to system security?
Let’s Get Started!!
0 notes
Text
how to build a digital music collection and stuff
spotify sucks aaaass. so start downloading shit!!
file format glossary
.wav is highest quality and biggest
.mp3 is very small, but uses lossy compression which means it's lower quality
.flac is smaller than .wav, but uses lossless compression so it's high quality
.m4a is an audio file format that apple uses. that's all i really know
downloading the music
doubledouble.top is a life saver. you can download from a variety of services including but not limited to apple music, spotify, soundcloud, tidal, deezer, etc.
i'd recommend ripping your music from tidal or apple music since they're the best quality (i think apple music gives you lossless audio anyway. .m4a can be both lossy and lossless, but from the text on doubledouble i assume they're ripping HQ files off apple music)
i also love love love cobalt.tools for ripping audio/video from youtube (they support a lot of other platforms too!)
of course, many artists have their music on bandcamp — purchase or download directly from them if you can. bandcamp offers a variety of file formats for download
file conversion
if you're downloading from apple music with doubledouble, it spits out an .m4a file.
.m4a is ok for some people but if you prefer .flac, you may wanna convert it. ffmpeg is a CLI (terminal) tool to help with media conversion
if you're on linux or macOS, you can use parameter expansion to batch convert all files in a folder. put the files in one place first, then with your terminal, cd into the directory and run:
for i in *.m4a; do ffmpeg -i "$i" "${i%.*}.flac"; done
this converts from .m4a to .flac — change the file extensions if needed.
soulseek
another way to get music is through soulseek. soulseek is a peer-to-peer file sharing network which is mainly used for music. nicotine+ is a pretty intuitive (and open-source) client if you don't like the official one.
you can probably find a better tutorial on soulseek somewhere else. just wanted to make this option known
it's bad etiquette to download from people without sharing files of your own, so make sure you've got something shared. also try to avoid queuing up more than 1-2 albums from one person in a row
tagging & organizing your music
tagging: adding metadata to a music file (eg. song name, artist name, album) that music players can recognize and display
if you've ripped music from a streaming platform, chances are it's already tagged. i've gotten files with slightly incorrect tags from doubledouble though, so if you care about that then you might wanna look into it
i use musicbrainz picard for my tagging. they've got pretty extensive documentation, which will probably be more useful than me
basically, you can look up album data from an online database into the program, and then match each track with its file. the program will tag each file correctly for you (there's also options for renaming the file according to a certain structure if you're into that!)
there's also beets, which is a CLI tool for... a lot of music collection management stuff. i haven't really used it myself, but if you feel up to it then they've got extensive documentation too. for most people, though, it's not really a necessity
how you wanna organize your music is completely up to you. my preferred filestructure is:
artist > album > track # track

using a music player
the options for this are pretty expansive. commonly used players i see include VLC, foobar2000, clementine (or a fork of it called strawberry), and cmus (for the terminal)
you can also totally use iTunes or something. i don't know what audio players other systems come with
i personally use dopamine. it's a little bit slow, but it's got a nice UI and is themeable plus has last.fm support (!!!)
don't let the github page fool you, you don't have to build from source. you can find the releases here
click the "assets" dropdown on the most recent release, and download whichever one is compatible with your OS
syncing
if you're fine with your files just being on one device (perhaps your computer, but perhaps also an USB drive or an mp3 player), you don't have to do this
you can sync with something like google drive, but i hate google more than i hate spotify
you can get a free nextcloud account from one of their providers with 2GB of free storage. you can use webDAV to access your files from an app on your phone or other device (documents by readdle has webDAV support, which is what i use)
disroot and blahaj.land are a couple providers i know that offer other services as well as nextcloud (so you get more with your account), but accounts are manually approved. do give them a look though!!
if you're tech-savvy and have an unused machine lying around, look into self-hosting your own nextcloud, or better yet, your own media server. i've heard that navidrome is a pretty good audio server. i unfortunately don't have experience with self-hosting at the moment so i have like zero advice to give here. yunohost seems to be a really easy way to manage a server
afterword
i don't know if any of this is helpful, but i just wanted to consolidate my personal advice in one place. fuck big tech. own your media, they could take it away from you at any moment
2K notes
·
View notes
Text
OS commands injection testing & defense
OS command injection is a technique used via a web interface in order to execute OS commands on a web server.
How to test for the issue
During code review
Check if any command execute methods are called and in unvalidated user input are taken as data for that command.
Besides, appending a semicolon to the end of a URL query parameter followed by an operating system command, will execute the command. %3B is URL encoded and decodes to semicolon. This is because the ; is interpreted as a command separator.
Example:
http://sensitive/something.php?dir=%3Bcat%20/etc/passwd
If the application responds with the output of the /etc/passwd file then you know the attack has been successful. Many web application scanners can be used to test for this attack as they inject variations of command injections and test the response.
Equally Static Code Analysis tools check the data flow of untrusted user input into a web application and check if the data is then entered into a dangerous method which executes the user input as a command.
Remediation
If it is considered unavoidable the call to a system command incorporated with user-supplied, the following two layers of defense should be used within software in order to prevent attacks
Parameterization - If available, use structured mechanisms that automatically enforce the separation between data and command. These mechanisms can help to provide the relevant quoting, encoding.
Input validation - the values for commands and the relevant arguments should be both validated. There are different degrees of validation for the actual command and its arguments:
When it comes to the commands used, these must be validated against a list of allowed commands.
In regards to the arguments used for these commands, they should be validated using the following options:
Positive or allowlist input validation - where are the arguments allowed explicitly defined
Allow-list Regular Expression - where is explicitly defined a list of good characters allowed and the maximum length of the string. Ensure that metacharacters like & | ; $ > < \ \ !` and whitespaces are not part of the Regular Expression. For example, the following regular expression only allows lowercase letters and numbers, and does not contain metacharacters. The length is also being limited to 3-10 characters:
^[a-z0-9]{3,10}$
Example code - Java
Incorrect Usage
ProcessBuilder b = new ProcessBuilder("C:\DoStuff.exe -arg1 -arg2");
the command together with the arguments are passed as a one string, making easy to manipulate that expression and inject malicious strings.
Correct Usage
ProcessBuilder pb = new ProcessBuilder("TrustedCmd", "TrustedArg1", "TrustedArg2"); Map<String, String> env = pb.environment(); pb.directory(new File("TrustedDir")); Process p = pb.start();
starts a process with a modified working directory
The command and each of the arguments are passed separately which makes it easy to validate each term and reduces the risk to insert malicious strings
3 notes
·
View notes
Text
1. Introduction: Understanding the Importance of Automating File Operations with Python Scripts Python scripts can be incredibly useful tools for automating repetitive file operations and tasks. Whether you need to rename hundreds of files, transfer data between folders, or analyze large datasets, Python offers a powerful and flexible solution. By writing simple scripts, you can save time and ensure accuracy in your file management processes. 2. Overview of Python and Its Capabilities for File Operations Python, a versatile programming language known for its simplicity and readability, is a powerful tool for automating file operations. With its rich library of modules like os, shutil, and glob, Python provides efficient ways to manipulate files, directories, and paths. 3. Benefits of Automating File Operations: Efficiency and Accuracy Automating file operations with Python offers significant benefits in terms of efficiency and accuracy. By utilizing Python scripts to handle repetitive file tasks, you can save time and reduce the chances of human errors. The automation process ensures consistency in file operations, eliminating the risk of overlooking important steps. 4. Common Use Cases for Python Script Automation in File Management Python script automation can be applied to various aspects of file management. Some common use cases include bulk renaming files, sorting and organizing files based on specific criteria, extracting data from files for analysis, and generating reports from multiple files. 5. Step-by-Step Guide to Creating Your First File Automation Script Now that we've discussed the various ways Python scripts can streamline file operations, it's time to dive into practical implementation. In this section, we will walk you through a step-by-step guide to creating your first file automation script. We will cover essential concepts such as reading, writing, and manipulating files using Python's built-in functions and modules. 6. Best Practices for Writing Robust and Scalable Python Scripts To ensure the efficiency and maintainability of your Python scripts for automating file operations, it's crucial to follow best practices. Make your code more readable and maintainable by using meaningful variable names and comments. Implement error handling to anticipate and manage potential issues during script execution. 7. Conclusion: Embracing Automation for Enhanced File Management Efficiency In conclusion, adopting automation through is pivotal for optimizing file management efficiency. By adhering to best practices such as utilizing clear variable names, thorough comments, error-handling mechanisms, modular code structure, and scalability considerations, you set yourself up for success in automating file operations. Portfolio : https://hazratali.dev/ Blog : https://hazrataliblog.com/ Problem Solving : https://hazratalips.com/

0 notes
Text
Linux Directory Structure & File Editing Basics with vi Editor | CertBlaster
youtube
Linux for CompTIA A+ Exam 220--902 Main Domain 2.0, sub-objective 2.1 " Identify common features and functionality of the Mac OS and Linux operating systems." This video shows some folder structure and navigation. You will also be exposed to the ls and ls -l commands as well as vi, cls and q commands. This is meant to assist you in preparing for the A+ exam.
#linuxbasics #vieditor #linuxnavigation #linuxcommands #terminaltutorial #linuxforbeginners #fileediting #learnlinux #linuxfilesystem #commandlinetutorial
0 notes
Text
10 Skills You Need to Become an Ethical Hacker in 2025

Ethical hacking has moved from the margins to the mainstream. In today’s digitally driven world, cybersecurity is no longer optional; it is a necessity. As businesses grow increasingly dependent on digital infrastructure, the threats they face have also become more sophisticated and relentless. This rising demand makes it crucial to understand the skills to become an ethical hacker and contribute meaningfully to the field.
To protect sensitive data, intellectual property, and critical operations, organizations are investing heavily in cybersecurity talent. As a result, ethical hackers are now seen as essential contributors to risk management and digital trust.
Many professionals begin their journey through industry-recognized programs such as Certified Ethical Hacking, which lay a strong foundation in real-world attack and defense scenarios.
However, to stand out in this competitive and high-stakes environment, you need more than just basic technical knowledge. You need a sharp, strategic mindset and a well-rounded skill set that keeps you adaptable across changing threats, evolving tools, and complex systems.
Whether you aim to work in a corporate security team, consult independently, or pursue bug bounty programs, it all starts with mastering the right skills. Let’s break down the ten core capabilities you’ll need to become a confident and capable ethical hacker in 2025.
Deep Understanding of Networking Fundamentals
Ethical hacking starts with understanding how data flows through networks. Knowing how devices communicate and how information travels between them is the backbone of penetration testing.
Start by learning the OSI and TCP/IP models in detail. These models explain how different layers of a network function and interact with one another.
Study concepts like IP addressing, MAC addressing, ports, NAT, and subnetting. These are crucial for mapping out networks, identifying entry points, and configuring scanning tools.
Explore routing and switching principles to understand how data moves between internal systems and external destinations.
Learn how protocols like HTTP, HTTPS, FTP, DNS, SMTP, and DHCP operate. Being able to analyze their behavior helps you spot misconfigurations and exploit weaknesses during tests.
Practice using network analyzers like Wireshark to observe real traffic and understand communication patterns. Hands-on exploration sharpens your analytical skills.
Without this foundation, it becomes difficult to simulate real-world attacks accurately or identify vulnerabilities that attackers might exploit.
A solid grasp of networking is not just an asset; it is a requirement for ethical hackers who aim to work in complex environments and defend real systems.
Proficiency in Operating Systems (Linux and Windows)
As an ethical hacker, working across different operating systems is a necessity. Linux and Windows are the two most commonly used platforms in both personal and enterprise environments.
Linux is the go-to choice for many cybersecurity professionals. It offers extensive control through the command line, access to powerful tools like Nmap, Wireshark, and Metasploit, and a modular design that makes customization easy.
You should become familiar with Linux distributions like Kali Linux, Parrot OS, and Ubuntu. Learn basic shell commands, scripting, user and file permissions, cron jobs, and service management.
At the same time, knowledge of Windows systems is critical, especially when assessing environments commonly used by large organizations. Many legacy applications still run on Windows, and it remains a popular OS for corporate networks.
Understand Windows architecture, registry structures, Active Directory, PowerShell, and Group Policy settings. These elements often become the focal points in privilege escalation or lateral movement during penetration testing.
Knowing how to pivot between these two systems allows you to test and secure a wider range of targets. It also makes your skills more adaptable in multi-platform environments.
A solid command over both Linux and Windows boosts your effectiveness and credibility as a versatile ethical hacker.
Programming and Scripting Skills
In ethical hacking, the ability to write and understand code is not just helpful; it is often essential. Programming allows you to interact directly with applications, craft custom exploits, and automate repetitive tasks.
Python is a favorite among ethical hackers due to its simplicity, readability, and wide range of security libraries. It is ideal for writing scripts that scan for vulnerabilities, test system defenses, or analyze network traffic.
Bash scripting is another key skill, especially in Linux-based environments. Automating tasks like log parsing, user account monitoring, or system configuration saves time and enhances consistency.
JavaScript plays a critical role in web-based testing. It helps you understand how web applications function and identify client-side vulnerabilities like cross-site scripting (XSS).
It’s also useful to have basic familiarity with other languages such as C, C++, PHP, and SQL. These allow you to dive deeper into source code, understand buffer overflows, and simulate database attacks. More than just writing code, you’ll learn to read and dissect scripts written by others, often the first step in understanding how a threat works.
Ultimately, programming sharpens your ability to think like an attacker and respond like a defender, making it a vital skill in your ethical hacking toolkit.
Mastery of Tools Used in Penetration Testing
To work efficiently as an ethical hacker, you need more than theory; you need mastery of the tools that simulate attacks and expose weaknesses.
Metasploit is one of the most powerful tools for developing and executing exploit code. It’s widely used for penetration testing and understanding how vulnerabilities are exploited in real systems. Nmap, or Network Mapper, is essential for scanning networks, identifying live hosts, open ports, and services running on those ports.
It provides the groundwork for any vulnerability assessment. Burp Suite is a go-to tool for testing web application security. It helps intercept, analyze, and modify traffic between your browser and a web server, making it easier to detect flaws in input validation, authentication, and session handling.
Wireshark is used to capture and analyze network packets in real time. It helps you understand what’s happening on your network at a very detailed level and is especially helpful in spotting unusual behavior.
Nikto is a lightweight web server scanner used to identify outdated software, dangerous files, and common misconfigurations. Each tool serves a unique purpose, but their real value lies in knowing when and how to use them together. The more fluent you are with these tools, the more precise and efficient your penetration tests will be.
Strong Grasp of Web Application Security
Most real-world attacks today target web applications, making this area one of the most critical for ethical hackers to master.
Start by understanding the OWASP Top 10, which highlights the most common and dangerous web vulnerabilities. These include SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and broken authentication.
Each of these vulnerabilities can be exploited to access sensitive data, manipulate transactions, or take over user accounts. Knowing how they work allows you to test applications effectively and help development teams fix them.
It is also important to understand how web technologies work together. Learn how HTML, JavaScript, backend databases, and server logic interact within common web architectures.
Dive into how authentication and session management should be implemented to prevent hijacking or brute-force attacks.
Misconfigurations in these areas are among the most exploited in modern applications.
Input validation is another key concept. Applications that fail to properly validate or sanitize user input can become easy targets for injection and scripting attacks.
A strong grasp of web security allows you to think like an attacker and defend like an architect. With web apps at the center of digital experiences, your skills in this domain will always be in demand.
Familiarity with Cybersecurity Frameworks and Standards
In professional cybersecurity environments, knowledge of industry frameworks is essential. They provide a structured approach to securing systems, managing risks, and maintaining compliance.
Begin by understanding the NIST Cybersecurity Framework. It outlines five core functions: Identify, Protect, Detect, Respond, and Recover, that help organizations manage cybersecurity risks effectively.
ISO 27001 is another widely adopted standard. It focuses on information security management systems (ISMS) and offers guidelines for establishing, implementing, and continually improving security protocols.
PCI-DSS is critical for anyone working in environments that handle credit card data. It sets requirements for secure payment processing, including encryption, access control, and regular testing.
These frameworks not only guide your actions as a security professional but also help standardize your reporting and testing methodologies.
Learning how to apply these standards in real-world scenarios improves your credibility and employability in structured, enterprise-grade environments.
Moreover, understanding these frameworks prepares you for roles that involve audit preparation, compliance reporting, and risk assessment.
As businesses become more regulated and security-conscious, your familiarity with these guidelines will give you a practical advantage.
Practical Knowledge of Cloud Security
As more businesses migrate to platforms like AWS, Azure, and Google Cloud Platform (GCP), ethical hackers need to understand how these cloud environments function.
Begin by learning how cloud architectures differ from traditional on-premise setups. Each provider offers different services, interfaces, and security protocols that you must be able to evaluate.
Assessing cloud configurations involves reviewing storage settings, virtual machine access, security groups, and permission roles. Misconfigurations in any of these areas can lead to serious vulnerabilities.
Securing APIs is a major priority in cloud-based systems. Understand how tokens, encryption, and rate limiting protect cloud APIs and what happens when these controls are missing.
Identity and Access Management (IAM) is central to cloud security. Learn how to assign roles, use multi-factor authentication, and limit privileges based on user responsibilities.
Also, study the shared responsibility model. In cloud computing, security responsibilities are divided between the provider and the client. Knowing where your role begins is critical to identifying and mitigating risk.
Cloud security is not static. Providers update their services frequently, so staying current with documentation and certifications is part of the job.
Mastering cloud security gives you the versatility to support businesses of all sizes as they scale in digital environments.
Social Engineering Awareness
Not all cybersecurity threats originate from code. In fact, many successful attacks are the result of manipulating human behavior. This is where social engineering becomes a critical area of focus for ethical hackers.
Social engineering exploits trust, distraction, or lack of awareness to gain access to sensitive systems or information. Phishing emails, baiting with malicious USB drives, and pretexting are some of the most common tactics used by attackers.
Ethical hackers must be able to recognize these techniques and replicate them in controlled environments to test an organization’s resilience. Knowing how users typically respond to these threats allows you to create more effective simulations.
Beyond tactics, understanding human psychology is vital. Learn how attackers build rapport, use urgency, or mimic authority to influence behavior. These psychological levers are often more powerful than technical exploits.
Communication skills also play a big role. As an ethical hacker, you may need to educate clients or team members about the social risks they face and how to minimize them.
By mastering both the technical and human aspects of security, you develop a more comprehensive approach to threat detection and defense.
Problem Solving and Lateral Thinking
Ethical hacking involves navigating through complex systems where vulnerabilities are not always easy to spot. Success often depends on how well you can think beyond conventional boundaries.
Traditional approaches may not always yield results, especially in hardened environments. That’s where lateral thinking comes into play. It involves approaching a problem from multiple perspectives and making creative connections others might miss.
For example, if a network scan shows no open ports, you might consider indirect paths such as phishing or supply chain weaknesses. Thinking like an attacker requires mental flexibility and a deep understanding of both systems and human behavior.
Patience and persistence are equally important. You may spend hours on dead ends before discovering a small misconfiguration that opens the door to an exploit.
Build structured thinking habits using tools like mind maps, flowcharts, or threat modeling techniques. These can help you visualize the problem space and test assumptions.
In addition, learn from past engagements or case studies. Studying how others have uncovered unexpected flaws can expand your problem-solving toolkit.
Ultimately, adaptability is key. Every test presents unique challenges, and your ability to adjust strategies on the fly will set you apart as a skilled ethical hacker.
Continuous Learning and Ethical Responsibility
Cybersecurity is one of the fastest-changing fields in technology. New vulnerabilities, exploits, and defensive measures emerge regularly, which means standing still is not an option.
As an ethical hacker, you must stay updated with the latest trends, tools, and techniques. Subscribe to reputable blogs, follow thought leaders, attend cybersecurity conferences, and participate in online communities where current threats are analyzed and discussed.
Pursue continuous certification to validate your expertise. Courses such as CEH, OSCP, and CompTIA Security+ not only build your skill set but also strengthen your credibility in the eyes of employers and clients.
Equally important is staying informed about security patches and vendor updates. Regular practice in lab environments ensures you retain what you learn and can apply it in real scenarios.
But beyond knowledge and skill lies something even more critical: ethical responsibility. With the power to test, probe, and exploit comes the duty to act with integrity. Your work must always prioritize safety, transparency, and legal boundaries.
Ethical hacking is not just about thinking like a hacker. It’s about protecting systems and people while holding yourself to the highest standards of accountability and professionalism.
How Appin Can Help You Build These Skills
At Appin, we don’t just teach theory; we help you build a career-ready skill set.
You get hands-on experience with real tools, real vulnerabilities, and structured guidance on ethical hacking frameworks. Our programs are shaped around the demands of the industry, helping you stay prepared for what’s ahead.
Whether you’re starting from scratch or leveling up your current knowledge, Appin will guide you through every phase of your learning journey.
Ready to master the skills of ethical hacking in 2025? Your future in cybersecurity starts here, with Appin. Inquire Now to take your first step toward becoming a certified and confident ethical hacker.
0 notes
Text
Computer Science 352 Programming Assignment 1
This first PA for CS 352 has three parts. The first will require you to research, experiment with, and write several bash commands. The second will be a very simple C program. The Third will require you to write python code to test an executable (compiled from C) using the os and subprocess python modules. For the project, you should end up with the following directory structure: pa1 ├──…
0 notes
Text
A file browser or file manager can be defined as the computer program which offers a user interface for managing folders and files. The main functions of any file manager can be defined as creation, opening, viewing, editing, playing or printing. It also includes the moving, copying, searching, deleting and modifications. The file managers can display the files and folders in various formats which include the hierarchical tree which is based upon directory structure. Some file managers also have forward and back navigational buttons which are based upon web browsers. Some files managers also offers network connectivity and are known as web-based file managers. The scripts of these web managers are written in various languages such as Perl, PHP, and AJAX etc. They also allow editing and managing the files and folders located in directories by using internet browsers. They also allow sharing files with other authorized devices as well as persons and serve as digital repository for various required documents, publishing layouts, digital media, and presentations. Web based file sharing can be defined as the practice of providing access to various types of digital media, documents, multimedia such as video, images and audio or eBooks to the authorized persons or to the targeted audience. It can be achieved with various methods such as utilization of removable media, use of file management tools, peer to peer networking. The best solution for this is to use file management software for the storage, transmission and dispersion which also includes the manual sharing of files with sharing links. There are many file sharing web file management software in the market which are popular with the people around the world. Some of them are as follows: Http Commander This software is a comprehensive application which is used for accessing files. The system requirements are Windows OS, ASP.NET (.NET Framework) 4.0 or 4.5 and Internet Information Services (IIS) 6/7/7.5/8. The advantages include a beautiful and convenient interface, multiview modes for file viewing, editing of text files, cloud services integration and document editing, WEBDAV support and zip file support. It also includes a user-friendly mobile interface, multilingual support, and easy admin panel. The additional features of the software include a mobile interface, high general functionality and a web admin. You can upload various types of files using different ways such as Java, Silverlight, HTML5, Flash and HTML4 with drag and drop support. CKFinder The interface of this web content manager is intuitive, easy to access and fast which requires a website configured for IIS or Internet Information Server. You would also require enabled Net Framework 2.0+ for installation. Some advantages include multi-language facility, preview of the image, and 2 files view modes. You also get search facility in the list as well drag and drop file function inside the software. The software has been programmed in Java Script API. Some disadvantages include difficulty in customizing the access of folders, inability to share files and finally, non integration of the software with any online service. You cannot edit the files with external editors or software. Also, there is no tool for configuration and you cannot drag and drop files during upload. Some helpful features include ease in downloading files using HTML4 and HTML5, also the documentation is available for installation and setup. File Uploads And Files Manager It provides a simple control and offers access to the files stored in servers. For installation, the user requires Microsoft Visual Studio 2010 and higher as well as Microsoft .NET Framework 4.0. Some advantages include a good interface where all icons are simple and in one style, 2 files view modes including detailed and thumbnails. It also supports basic file operations, supports themes, filters the file list as well as being integrated with cloud file storage services.
Some disadvantages include limited and basic operation with files, inability to work as a standalone application, settings are in code, and finally it cannot view files in a browser, weak general functionality, no mobile interface and no web admin. Some useful features include uploading multiple files at one go, multilingual support and availability of documentation. Easy File Management Web Server This file management software installs as a standalone application and there is no requirement for configuration. The software does not support AJAX. A drawback is that it looks like an outdated product and the interface is not convenient. The system requirement for this software is Windows OS. The advantages include having no requirement for IIS, uploading of HTML4 files one at a time, providing support notifications with email and can be easily installed and configured from the application. The disadvantages include the interface not being user-friendly, full page reload for any command, it cannot edit files and does not support Unicode characters. Moreover, it does not provide multilingual support for users and has a small quantity of functions when compared with others. ASP.NET File Manager This file manager at first glance, is not intuitive and is outdated. The system requirement for this manager is IIS5 or higher version and ASP.NET 2.0 or later version. Some advantages include editing ability of text files, users can do file management through browsers which is very simple, and it can provide support for old browsers. You can do basic operations with files stored and have easy functions. On the other hand, some disadvantages include the redundant interface, its need to reload full page for navigation. Additionally there is no integration with online services. The user cannot share files, cannot drag and drop files during uploading, gets only one folder for file storage and there's no tool for configuration. Moreover, there's no multilingual support, no mobile interface, low general functionality and no web admin. File Explorer Essential Objects This file manager offers limited functionality regarding files and is a component of Visual Studio. The system requirements include .Net Framework 2.0+ and a configured website in IIS. Some advantages include previewing of images, AJAX support with navigation, integration with Visual Studio and 2 file view modes. The disadvantages include no command for copy, move or rename file, no editing of files even with external editors and inability to share files with anyone. What's more, there's no support for drag and drop file for uploading, an outdated interface, no 'access rights' customization for various users, no web admin, no mobile interface and no multilingual support for users. FileVista This file management software offers a good impression at the outset but has limited functionalities. The system requirements include Microsoft .NET Framework 4 (Full Framework) or higher and enabled Windows Server with IIS. Some advantages include setting quotas for users, uploading files with drag n drop, Flash, HTML4, Silverlight and HTML5, multilingual support, presence of web admin, archives support, easy interface, fast loading and creation of public links. The disadvantages include disabled editing ability, no integration with document viewers or online services, no search function and no support of drag and drop for moving files. IZWebFileManager Even though the software is outdated and has not been updated,it's still functional. The interface of this software is similar to Windows XP. It has minimum functionality and no admin. It provides easy access to files but is suitable only for simple tasks. The advantages of this software include 3 file view modes, preview of images, facility to drag and drop files, various theme settings and a search feature. The disadvantages of this software include the old interface, no editing of files, no integration with online services, no sharing of files, and no drag and drop support for uploading files.
The user cannot set a permission command as well. Moxie Manager This file management software is modern and has a nice design. Also, it is integrated with cloud services which functions with images. The system requirements include IIS7 or higher and ASP.NET 4.5 or later versions. Some advantages include an attractive interface, ability to use all file operations, preview of text and image files. You can also edit text and image files, support Amazon S3 files and folders, support Google Drive and DropBox with download capability, support FTP and zip archives. On the other hand, some disadvantages include having no built-in user interface, no right settings for users, no support of drag and drop, no mobile interface and no web admin. Some features include multilingual format, available documentation, upload files with drag and drop support, average functionality.
0 notes
Text
This article is almost 10 years old.
A kid puts her hand up in my lesson. 'My computer won't switch on,' she says, with the air of desperation that implies she's tried every conceivable way of making the thing work. I reach forward and switch on the monitor, and the screen flickers to life, displaying the Windows login screen.
This one's newer, just over 2 years old.
More broadly, directory structure connotes physical placement — the idea that a file stored on a computer is located somewhere on that computer, in a specific and discrete location. That’s a concept that’s always felt obvious to Garland but seems completely alien to her students. “I tend to think an item lives in a particular folder. It lives in one place, and I have to go to that folder to find it,” Garland says. “They see it like one bucket, and everything’s in the bucket.”
Schools are demanding kids as young as 5 or 6 use computers - and nobody is teaching computer basics. Nobody is teaching the names of the computer components (monitor, hard drive, cpu, ram); nobody is teaching what the parts do; nobody is teaching what "apps" are (...we used to call them "programs") or how files work.
Of course Adobe is very happy that people will say "I'm using Adobe" because nobody remembers the name "Acrobat Reader." Adobe is thrilled that most people don't know that PDFs are a filetype that can be opened or edited by many different programs.
Typing, as far as I can tell, is taught less than it was when I was in high school - in a country where everyone is expected to spend many hours a week on a keyboard.
(When I applied for college at the for-profit scammy school where I got my paralegal degree, I tested out of their basic typing class. The class's goal was 40wpm; I type at more than double that speed. The counselor assigned to me said she'd never seen typing that fast. I have no idea if she was lying to try to boost my ego or was just really oblivious.) (If she was trying to boost my ego, she failed. I know what secretarial typing speeds are. Mine is mediocre.)
If I were more geekish and had formal education training, I'd try to put together a series of Basic Computer Literacy courses for schoolkids - a set for ages 5-8, another for 9-12 year olds, and a third set for teenagers.
Start with parts of the computer - and how they look different in desktops, laptops, tablets, phones.
Move on to OS: Windows, Mac, IOS, Android, Linux, and a hint of others. (Throw in a mention of game consoles and how their OS is and isn't like a standard computer OS.)
A bit of mention of OS types/versions - WinXP and Win10, and so on. A bit of what commonly changes from one version to the next, and what doesn't.
These are the starting points, not because they're the core of How Computers Work, but because they're the parts everyone interacts with. The 8-year-old doesn't specifically need to know Linux exists... but they need to know there's a DIFFERENCE between a Windows 11 new laptop and a desktop running something else. Needs to know that not all "Android" phones work the same way. Needs to know, when they open a new device, that it has an OS, and there are ways to figure out what that OS is.
Next there is:
Files, folders, internal structure - and how the tablet/phone OS tends to hide this from you
The difference between the app/program and the stuff it opens/edits
That the same file can look different in a different app
Welcome To The Internet: The difference between YOUR COMPUTER and THE CLOUD (aka, "someone else's computer") as a storage place; what a browser is; what a search engine is
Welcome To Metadata I Am So Sorry Kiddo Your Life Is Full Of Keywords Now And Forever
Computer Operations Skills: Typing. Hardware Assembly, aka, how to attach an ethernet cable, is the monitor turned on, what's the battery level and its capacity. Software-Hardware interfaces: how to find the speaker settings, dim or brighten the monitor, sleep vs power off, using keyboard shortcuts instead of the mouse.
After alllll that, we get to
Command line: This is what a terminal looks like; this is what you can do with it; no you don't have to program anything (ever) but you really should know how to make it show you your IP address. (See above: Welcome to the Internet should have covered "what is an IP address?")
Internet safety. What is a virus; what's malware. How to avoid (most of) them.
SOCIAL internet safety: DO NOT TELL ANYONE your age, real name, location. Do not tell strangers your sexual identity, medical history, family details, or anything about any crimes you may have committed.
...I'm probably missing some things. (I'm probably missing a lot of things.) Anyway. Something like that. The simple version is a half-day crash-course in overview concepts culminating in a swarm of safety warnings; the long version for teens is probably 30+ hours spread out over a few weeks so they can play with the concepts.
Telling young zoomers to "just switch to linux" is nuts some of these ipad kids have never even heard of a cmd.exe or BIOS you're throwing them to the wolves
61K notes
·
View notes
Text
Blog Post 2: File Structure
As graphic designers and other creatives in the industry, we always want to be top-notch and organized regarding our work. But in my experience, it has always been this way in the beginning whereas, towards the end of a project, we all are scrambling to meet our deadlines and looking for the exact finalized version to send to the client or for our final submission. I usually like to keep my files organized I am a huge advocate for it! Especially after joining this program, we were taught this vital skill. However, one thing I do want to make more use of is the file naming conventions. I usually do it by course name, the iterative version numbers, and a very detailed description, which makes it easier to find. But sometimes I may have abandoned this format which causes some distress in it. One thing I learnt from the course material for this week is to try nesting folders within each other. All in all, I feel that keeping a clean digital workspace makes me feel like I am more productive than chaotic when working.
(Windows doesn't have the column view like Mac os so this is the best I could do to show the file path directory)




0 notes
Text
The Ultimate Beginner's Guide to Learning Linux
Linux is an open-source operating system that powers everything from smartphones to supercomputers. Unlike proprietary operating systems like Windows and macOS, Linux is freely available to everyone. It’s known for its stability, security, and flexibility, making it an ideal choice for developers, system administrators, and tech enthusiasts.
Why Learn Linux?
1. High Demand for Linux Professionals Learning Linux opens up numerous job opportunities in fields like system administration, software development, cloud computing, and cybersecurity. Linux is the backbone of many cloud services, data centers, and tech companies.
2. Open-Source Nature Linux is open-source, meaning it is free to use, and its source code is available to modify. This is a key reason why it’s favored by tech communities worldwide.
3. Flexibility and Control Linux gives users full control over their system. It is highly customizable, allowing you to build an operating system tailored to your needs.
4. Learn Command-Line Skills The command line is a powerful tool in Linux, and mastering it will help you become more proficient in navigating and managing your system efficiently.
What You Will Learn in This Linux Course
Here’s a breakdown of the essential skills and concepts that would be covered in a comprehensive Linux course.
1. Basic Linux Commands You’ll start with basic commands like ls, cd, pwd, and mkdir. These are the building blocks that help you navigate the file system and manage files.
2. File Permissions and Ownership Learn how to manage file permissions and ownership to secure your system and ensure that users and groups have the correct access rights to files.
3. File System Structure Understand the Linux directory structure, including root directories (/, /home, /etc, etc.), and how to efficiently navigate through the filesystem.
4. User Management You’ll learn how to create, delete, and modify user accounts, as well as manage groups and user permissions.
5. Process Management Linux gives you full control over running processes. You’ll learn how to manage processes with commands like ps, top, kill, and how to use nice and renice to control process priorities.
6. Package Management Linux distributions use package managers to install, remove, and update software. Learn how to use package managers like apt (for Debian-based systems) or yum (for Red Hat-based systems).
7. Networking Basics Linux provides a variety of networking tools. You’ll learn how to configure network interfaces, troubleshoot connections, and use tools like ping, netstat, and ifconfig.
8. Shell Scripting One of the most valuable skills in Linux is shell scripting. You'll learn how to write scripts to automate tasks, save time, and enhance productivity.
9. System Logs and Monitoring Linux systems generate logs that are crucial for troubleshooting. Learn how to read and interpret system logs, and use tools like dmesg and journalctl to monitor system performance.
10. Security Practices Linux is known for its security features, and in this course, you’ll learn how to harden your system with firewalls, SELinux, and user authentication mechanisms.
How to Get Started
Step 1: Choose a Linux Distribution There are many flavors of Linux to choose from. For beginners, distributions like Ubuntu, Fedora, or Linux Mint are excellent choices. You can download and install them on a virtual machine (VM) or set up a dual boot alongside your main OS.
Step 2: Install VirtualBox or VMware If you prefer to learn without changing your current system, installing a Linux distribution on a virtual machine is a great option. VirtualBox and VMware are free tools that allow you to run Linux on top of your current OS.
Step 3: Use Linux Regularly The best way to learn Linux is by using it regularly. Install it on your computer or run it from a USB stick to get hands-on experience. The more you use it, the more comfortable you will become.
Step 4: Join Linux Communities There are active Linux communities where you can ask questions, share knowledge, and collaborate. Websites like Stack Overflow, Reddit's rlinux, and Linux forums are great resources.
0 notes
Text
Ok but phones have directory structures. You organize files and navigate directories the same way you would on a desktop OS. A phone app isn't inherently different from a desktop application, they're just marketed differently. Most users won't access their phone's shell, but it's still there (and most desktop users probably don't use a shell much, either). Your phone has a BIOS (or something analogous) and a bootloader. It's still a computer.
People not using PCs seems like a separate (and not a priori negative) phenomenon to this decrease in technological literacy people are describing.
My best guess is that it's an unintended consequence of "sensible defaults" prevailing in software.
Applications don't ask you where to save a collection, they just create a directory in ~/documents and put things there for you.
They almost never need to show you a file picker, because they have a large enough "recent files" section.
They don't need you to configure back-end settings, because they rely on standardized interfaces and just need you to tick a permission to access that API.
People don't need to worry about installation directories because modern systems use package managers (as they should!).
People don't need to worry about file types because for common use cases a handful of types have become the de-facto standard (when was the last time you had to deal with a .tiff, .eps, .ogg or .avi file?).
If everything "just works", you don't really have a reason to learn the underlying mechanics of it all.
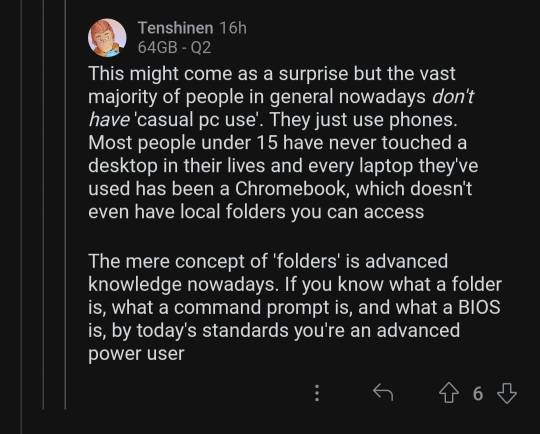
this can't be true can it
99K notes
·
View notes
Text
VeryUtils EML to PDF Converter is a highly powerful tool to Convert EML files to PDF with all attachments
VeryUtils EML to PDF Converter is a highly powerful tool to Convert EML files to PDF with all attachments.
VeryUtils EML to PDF Converter is Your Ultimate Solution for Seamless Email Data to PDF Conversion.
In the realm of digital communication, managing email data efficiently is paramount for both personal and professional endeavors. However, dealing with diverse file formats can pose challenges, especially when it comes to archiving and sharing information. Enter VeryUtils EML to PDF Converter – an innovative software designed to streamline the conversion process while ensuring the integrity and security of your email data.

✅ VeryUtils EML to PDF Converter Key Features:
Swift and Error-Free Conversion: VeryUtils EML to PDF Converter facilitates rapid and 100% accurate conversion of EML files to PDF format, both individually and in batch mode. With its intuitive interface and robust algorithms, users can seamlessly migrate their email data without the risk of data loss or corruption.
Batch Printing Capabilities: Say goodbye to the hassle of converting EML files one by one. With batch processing capabilities, users can effortlessly convert entire directories of EML data into PDF format, enhancing productivity and efficiency without requiring an internet connection.
Preservation of Email Components: Rest assured that your email components and EML file structure remain intact throughout the conversion process. VeryUtils ensures that key elements such as sender details, recipient information, subject lines, hyperlinks, and more are accurately preserved, maintaining the integrity of your email content.
Wide Compatibility: Whether you're using Thunderbird, Windows Live Mail, Outlook Express, or other email clients, VeryUtils supports the seamless transfer of EML files across various platforms. Additionally, the software is compatible with all versions of Windows OS, ensuring versatility and ease of use for all users.
Attachment Handling: VeryUtils EML to PDF Converter allows users to export attachments separately to a designated folder, ensuring comprehensive data migration without sacrificing file organization or integrity.
No Dependency on Adobe Reader or Additional Software: Bid farewell to dependencies on external applications. VeryUtils operates independently, eliminating the need for Adobe Acrobat or any other software installations. Users can seamlessly convert EML files to PDF format without any extra hassle or overhead.
✅ Why Choose EML to PDF Conversion?
Portability and Independence of PDF Files: PDF files offer unparalleled portability and independence, allowing users to access and view their content across multiple devices without the need for specific software installations. By converting EML files to PDF format, users can ensure seamless accessibility and convenience for their archived data.
Enhanced Security and Sharing Capabilities: With PDF files, users can apply strong passwords to protect their sensitive data from unauthorized access, ensuring enhanced security and privacy. Additionally, PDF files are easily shareable, allowing for seamless collaboration and communication across various platforms.
Effortless Printing: PDF files are renowned for their compatibility and ease of printing, making them the preferred choice for document output. By converting EML files to PDF format, users can simplify the printing process and ensure consistent, high-quality output across different devices and platforms.
Backup Multiple EML Files in One PDF: VeryUtils EML to PDF Converter enables users to efficiently backup multiple EML files into a single PDF document, ensuring comprehensive data management and organization. With its user-friendly interface and advanced features, the software simplifies the migration process while maintaining data safety and integrity.
✅ Conclusion: In conclusion, VeryUtils EML to PDF Converter stands as a reliable and efficient solution for seamlessly converting EML files to PDF format. With its robust features, wide compatibility, and user-friendly interface, the software empowers users to streamline their data migration processes while ensuring the security and integrity of their email content. Experience the convenience and efficiency of EML to PDF conversion with VeryUtils – your ultimate solution for hassle-free data management.
0 notes
Text
Linux Directory Structure & File Editing Basics with vi Editor | CertBlaster
youtube
Linux for CompTIA A+ Exam 220--902 Main Domain 2.0, sub-objective 2.1 " Identify common features and functionality of the Mac OS and Linux operating systems." This video shows some folder structure and navigation. You will also be exposed to the ls and ls -l commands as well as vi, cls and q commands. This is meant to assist you in preparing for the A+ exam.
#linuxbasics#vieditor#linuxnavigation#linuxcommands#terminaltutorial#linuxforbeginners#fileediting#learnlinux#linuxfilesystem#commandlinetutorial#Youtube
0 notes
Text
Python for Automation: Supercharge Your Productivity

In today's fast-paced world, automation is essential for productivity and efficiency. Python is a popular choice for automating jobs across fields because of its simplicity, versatility, and powerful libraries.
Programmers, data analysts, system administrators, and anybody wishing to automate monotonous operations can benefit from Python. So, let’s explore more about how python for automation can boost productivity.
Top 5 Processes You Can Automate with Python

Email automation
Email is standard in personal and business settings. Python libraries like smtplib and imaplib automate email sending, receiving, and processing. Python simplifies email administration, from mass sending to screening messages.
File operations
Many workflows include file and directory manipulation. Use Python's os modules to automate file renaming, copying, relocating, and deleting. Python is efficient for local file organization and server file operations.
Data compilation
Many businesses and projects need to collect and process data. Python excels at data compilation. Pandas lets you read data from many formats, clean and preprocess it, and easily merge datasets. Python automates data collecting and analysis.
Web scraping
Manually scraping webpage data is tedious. This method can be automated with Python's web scraping packages BeautifulSoup and Scrapy. Python simplifies web scraping for market study and content curation.
Generate reports
Monitoring and assessing a business or project requires reporting. Data manipulation and visualization make report generation easy in Python. You can automate PDF, Excel, and interactive online dashboard report generating to save time and ensure consistency.
Top Python Modules for Automation
Paramiko
Paramiko is a Python SSH implementation that lets you securely automate remote server functions. Paramiko streamlines remote admin tasks like command execution, file transfer, and SSH key management.
Pandas
The Panda framework is critical for any data analyst because structured data manipulation and analysis become easy. Pandas reduces any computational effort required from reading and writing to clever transformations, hence it is fundamental for data speed up.
Selenium
Selenium is an extensively adopted web automation tool for an interactive and behaviour-driven automated testing approach. By means of robotics, performing humanoid tasks becomes possible, like filling out form fields, clicking on buttons or harvesting dynamic content, for instance.
JSON
JSON, which is a straightforward data interchange format, is used for JSON configuration files and API response. The reason for Json support in Python, parsing and producing Json data becomes really easy, which makes simple JSON data interchanging automation chores.
Requests
Python portraying the Requests HTTP library is simple but powerful. Requests library also makes executing requests and calls in when automation is required for API clients or web services quite a simple task.
AutoMagica
AutoMagica, a Python library, facilitates RPA by offering a high-level API for desktop application automation. AutoMagica automates computer operations, including data entering, form filling, and application testing, without sophisticated programming.
PyBuilder
Python project build automation tool PyBuilder streamlines dependency management, testing, and packaging. PyBuilder helps python development serviceprovidersto automate Python development with consistent and reliable builds across environments.
Use Cases of Python Automation

Test automation
Software quality and dependability require automated testing. Python's testing frameworks like pytest and unit test make unit, integration, and end-to-end testing easy to automate, speeding up development process.
Web scraping
Web scraping can be performed for detecting market changes, competitive analysis and data extraction. Python's web scraping modules and the capabilities of HTTP PoS makes it suitable for automated cross-domain web scraping.
System administration
The work of a system administrator, such as server arrangement, log analysis, and user management, is always a job that is done repeatedly. A system admin is able to perform these operations seamlessly and efficiently due to powerful system administration tools and the scripting environment of Python, which allow them to automate the operations, thereby saving time for other essential tasks.
Data analysis and visualization
Data analysis and visualization are consequential for identifying insights and insightful decision-making. A broader category of data manipulation and visualization libraries, as well as its ability to automate tiresome data analysis processes and simply create visuals, composes the Python ecosystem and allows analysts to focus on more strategic tasks.
Robotics and IoT
The Python language is a great choice when automating software, robots, and IoT. Now, you can make robots and IoT work, for example, by monitoring sensors, activating actuators, and communication interfaces by using libraries like Raspberry Pi GPIO and PySerial that allow the computer to have almost indefinite automation capabilities.
Conclusion
The Python scripting, module, and library ecosystem makes Python a promising language for automating repetitive tasks. Web scraping, data visualization, data analysis, system administration, and robotics are just a few of the many niches that have praised Python for its exceptional task execution capabilities.
To top it all off, Python's simplicity and ease of understanding have become even more appealing to developers who want to use the language for automation purposes. Shiv Technolabs a professional python development company helps you leverage the full potential of Python for bringing automation benefits to your business.
0 notes
Text
Introduction to Computers: Everything You Need to Know

Introduction
Welcome to the world of computers! Whether you're a complete beginner or someone looking to brush up on the basics, understanding essential computing concepts and beginner computer skills is key to navigating the digital landscape with confidence. In this blog, we'll cover everything you need to know to kickstart your journey into the realm of computing.
Understanding Essential Computing Concepts
Before diving into the specifics of operating systems, hardware, and software, it's important to grasp some fundamental computing concepts. Let's break them down:
1. What is a Computer?
A computer is an electronic device that processes data to perform various tasks. It consists of hardware components such as the central processing unit (CPU), memory, storage, input devices (e.g., keyboard, mouse), and output devices (e.g., monitor, printer).
2. Operating System (OS)
An operating system is software that manages computer hardware and provides a user interface for interacting with the system. Common operating systems include Windows, Mac OS, and Linux.
3. Hardware vs. Software
Hardware refers to the physical components of a computer, while software comprises programs and data that instruct the hardware to perform specific tasks.
4. Data Storage
Data storage involves saving and retrieving information on a computer. This can be done using various storage devices such as hard disk drives (HDDs), solid-state drives (SSDs), and external storage devices.
5. Internet and Networking
The internet allows computers to communicate and share information globally. Networking involves connecting computers and other devices to share resources and access the internet.
Beginner Computer Skills
Now that we have a basic understanding of essential computing concepts, let's explore some beginner computer skills that will help you navigate your way around a computer:
1. Basic Navigation
Familiarize yourself with the desktop environment, including icons, taskbar, and Start menu (or equivalent). Learn how to open and close programs, switch between windows, and navigate file directories.
2. Typing Skills
Improving your typing speed and accuracy is essential for efficient computer use. Practice typing exercises and learn keyboard shortcuts to streamline your workflow.
3. Internet Browsing
Learn how to use a web browser to search the internet, navigate websites, bookmark pages, and manage browser tabs. Understand basic internet safety practices such as identifying secure websites and avoiding phishing scams.
4. File Management
Master the basics of file management, including creating, renaming, moving, and deleting files and folders. Organize your files into logical directory structures to keep your computer organized.
5. Basic Troubleshooting
Develop problem-solving skills for common computer issues such as software errors, frozen applications, and connectivity problems. Learn how to restart your computer, perform basic troubleshooting steps, and seek help when needed.
Conclusion
Congratulations! You've now been introduced to essential computing concepts and beginner computer skills. Remember, mastering these fundamentals is the first step towards becoming proficient in using computers effectively. Practice regularly, explore new features and applications, and don't hesitate to seek help or further guidance whenever you encounter challenges. With dedication and perseverance, you'll soon become a confident computer user ready to tackle any digital task that comes your way. Happy computing!
0 notes