#error code: ken
Explore tagged Tumblr posts
Note
Hello! I have a request!
Could you do something where Kenma isn't really giving the female reader any attention because he's busy streaming so the reader sneaks under his desk where the viewer's can't see her and she pleasures him until he eventually cums down her throat?
:) I un-ironically love writing bjs

The shared house was silent anytime after 5 o’clock. Kuroo had just left— his afternoon business management classes calling him in, and Bokuto’s practice overcrowded his schedule to the point where he went twice a day with some gym sessions in between. That leaves you alone with Kenma in your 4 bedroom home off campus that was supposedly his father’s apology gift.
The bills are mainly kept satisfied with Kenma’s profit as his streaming allows you all to live as you do. Of course, there was a sense of independency by your own jobs regardless. There has probably been twice where everyone was in the living room at once, but it’s like there’s a tacit agreement each of you have your own goals.
You can’t be mad at the man for being busy when his job supports his friends and himself.
Kenma has been your friend, now boyfriend, for the longest out of all of them, next in line being Kuroo. Kenma took computer engineering and coding related classes, despite having already perfected building PC’s just out of pure experience. The work is hard. You’ve seen it.
You’ve witnessed him stress first hand about a single error in a strenuous, long line of codes—and you ask him why he doesn’t stop doing it if it bothers him to the extent it does. His determination has grown for activities he enjoys over the years; 12 year old him would have quit.
Kenma’s way to deal with stress is isolation. The entire day he’s been crammed in his room, and with being the only other person in the house majority of the time, you bring it upon yourself to feed him. He gets focused and forgets to eat.
The reminder has you clicking your Ipad off from whatever distraction show you had playing. It was so boring most of the days, Netflix couldn’t even fulfill you. You toss the covers off yourself, then bounce downstairs into the kitchen.
It was so quiet that your feet patting against the floor filled the air. To cure the ennui you felt, you’d take the time to have fun with this culinary experience.
By the time there was fluffy white flour messily coating the kitchen and dishes stacked like game cards in the sink, your dish was plated for two. Maybe you’d keep him some company?
Careful not to fall up the stairs, you prod at his door in attempt to knock with one hand. Somehow you turn the knob successfully.
The fan cuts through the air, every click of Kenma’s pen accompanied with a glance to the paper beside him. He won’t even look up at the waitress bearing goods.
“Hi Ken,” you grab his attention but his slim eyes only dart up at the smell of cuisine. “Have you eaten?”
You know the answer. His hair is pulled back into a ponytail, so when he shakes his head the usual strands that follow aren’t there. You place the plate on his desk, next to the two cans of some energy drink and a diet Dr. Pepper.
“Thank you,” he speaks softly. There was a hint of edge to the sound, like he hadn’t used his voice all day.
“Mhmm.”
You turn on your heels to his bed, then sit criss cross as it squeaks and dips. “Do you mind if I just stay in here? It gets lonely in the house.”
To be honest, you forget he’s there sometimes.
“I’m kinda busy,” he replies. He loves you, and your presence, but he just knows he won’t be able to focus. “I’ll be done soon.”
The pout you flaunt deepens, “You’ve been stuck in here for almost a week now! Come out; I miss you Ken.”
He refrains himself from turning to look at you because he knows when he weighs his options, you’ll always come out on top. The chances of you getting picked multiply with your pout.
“Soon, I just need to finish this.”
“Please?”
He doesn’t even have a valid response for that, so he forces the spoon into his mouth. You’re actually a great cook, but since you all eat so much takeout, nobody’s at the dinner table at the same time to enjoy it.
You huff and negotiate to just sit in silence, as long as you’re in his presence. As long as you know he’s there.
This only lasts about fifteen minutes before you’re whining for him again. You completely understand the heavy load of schoolwork, and that it has to get done, but he genuinely has been at it for so long it cannot be healthy.
“I’m done,” he announces coincidentally, his soft fingers coming up to brush a tendril of hair back as he gathers his things on the desk into a neat pile.
Your head perks up like a puppy at attention. He arises from his chair after closing the laptop, pulling his rubber band from the hair connected at his nape as he steps towards you laying on his bed. You giggle in expectancy when he smiles gingerly at you, reaches his arms forward around your feet to plant his hands on the duvet, then crawls up your body. The hair tie wraps around his wrist to join all the other colorful bracelets and bands.
He makes you swoon by just giving you attention.
His hands grew into proportion as he aged, so now they were relatively large. Large enough to connect at your hips as he kisses his way up.
Stomach, chest, then an abundance on your chin and around your face, just for his thumb and index finger to hold your cheeks in position for his softer, slower kiss right on your lips.
You wrap your arms around him like he’d just disintegrate any second. You can feel his body slump, leaving you with most of his weight to carry and his head withdrawing from the kiss to between your breasts. With one hand massaging the round muscle, Kenma was in his element.
Black with barely-there blonde crowds your vision. His soft skin felt warm as you two lay intertwined in the still house, and if you were to fall asleep it would greatly help that Kenma never keeps the big light on. He moans in satisfactory below you.
You lift your hand to rest over his face, the bigger part of your thumb gliding gently over his cheek.
“I love you,” he mutters.
“I love you too Ken.”
After a while of Kenma following your heartbeat and breathing, you would’ve guessed he was asleep. He clarifies he isn’t when he groans lowly.
“I have to get up.”
The words rest tensely in the air, and maybe if you pretend you didn’t hear him, he’ll lay there and forget about it.
He attempts to raise himself from you, politely grabbing your hand and locking your fingers when he comes to a hover above. His pink lips come to the corner of yours as you blink open your eyes.
Truthfully, he wants nothing more than to be with you, here, resting—but he hasn’t streamed in a solid week because of school. You were completely his priority though, so he would make sure to give you equal attention as his stream.
He finds the little willpower to come off you and the bed. He was genuinely hoping you’d stay there and sleep peacefully, that way he’ll come back to join you and it will feel like he never left.
He flips a blanket over your body before he strolls to his setup usually beaming with bright lights. He takes a seat, making sure to turn the brightness down of everything, refraining from playing music, and ultimately deciding not to turn on any light not connected to his PC anyway.
As much as you hate that he’s not cuddled up next to you right now, you love the fact that he’s a steamer overall because he looks so damn hot doing it. Especially the way his muscles on his forearm flex as he quickly types or plays. His hair that’s usually up is down, because he isn’t wearing his mic.
Or like the way every now and then he’ll pop a piece of gum in his mouth and manspread in his gaming chair to shoot a quick message or check his feed. Or like the way he’s so attent, making call-outs, or whenever he gets angry his brows furrow the slightest bit and his face displays whatever he’s actually thinking. You find it hilarious when his eyes roll.
At some point, he hears you come up behind him into view, and his head relaxes into your two hands sliding up his neck to his jaw. You crouch into the screen and the chat immediately multiples. It’s too quick to read them all. Knowing his viewers, Kenma takes the responsibility of closing it with the click of a button, so fast that it seems he never even did it.
“Cracked, 130,” he calls.
You stood there for a moment to watch him play. He and his team beat the level, game, you don’t know, but he releases his focus from the screen and mindlessly cracks his knuckles.
A donation comes in that’s read aloud. Kenma tenses, but you’re excited to hear it.
“jump1nnit donates $70. ‘girl to girl, is it big?’”
Kenma’s head drops back in your hands, eyes closing in annoyance.
“Jesus Christ,” he mumbles. Where were his mods?
All you were thinking about was how much Kenma was actually earning. 70 dollars in a single donation? How many of these does he get a day? How much more do people pay that’s over 70 when you aren’t here?
You shake these questions away. You knew he was famous. This was not new information; his fans see you sometimes in the background, and they adore you. It’s why your instagram has so many followers and people saying outrageous things in your comments. Ken begs you not to check them.
You find it amusing honestly. God knows what he’s being sent despite his DM’s or what they’re saying in his chats. You know there’s girls all over the world after him, but he doesn’t entertain them, so you don’t either. You trust him completely.
Brought back to reality, you look down at Kenma.
He starts, “Are you-“
To rile up the scene, you nod at the monitor with a mischievous smirk on your face. You bend and kiss his forehead.
“Can I sit right here?” You ask quickly, already pulling up his desk stool because he has no reason to say no. He takes your momentary absence to mute the computer.
“Yeah. yeah, Definitely.”
The blonde’s tone is a little off, but you chalk it up to what just happened. He was just surprised you’d actually respond. He ignores them so he doesn’t get demonetized.
So you sit next to him on your phone playing games, or watching him, or laying on his shoulder. It made it a little difficult for him to play with the last one, but he doesn’t mind. He places a kiss to your forehead, matching earlier actions, and the way you two looked at each other after will definitely reel in some fan edits.
You return to gaming on your phone until you drop it. It tumbles down and under the PC, into the jungle of wires below.
At least with everything included in the setup, that’s what you expect to see, but they’re all neatly accounted for. The seat moves back against the carpet to accommodate for your body, the space you’ve created to retrieve the device. The problem is, you and Kenma occupy this space. You won’t fit.
Kenma heard your phone drop, so he had an idea why you’re down there. He even chuckled a little. Once you pick up the phone, you use his thigh as leverage to turn yourself around, causing him to flinch, and immediately an idea pops into your head.
You could stay down here.
You press the heart of your palm into him once more, the same reaction procreating ideas like a lightbulb.
His voice from above makes another callout.
The lightness of your fingertips glide across his thigh and up to his waist, slipping past the barrier of the thin shirt he’s wearing. Kenma is not ticklish, but his abdomen turns concave to your touch.
By now he has concluded what is happening, or going to happen, and just the thought has him hardening in front of you. Of course it’s something he’s thought about. He hasn’t asked because it feels unnatural—like you would only do it because he suggested it.
His poker face remains stone cold, but the rest gives him away. With every touch you only got closer. You trail your whole hand up the shirt, running this one along the dips of his pale skin, while the other goes back and forth along his thigh. Inwards, then back out. Your phone was long forgotten.
You run the length of your fingers over his center sneakily before meeting both hands in the middle and fiddling with his waistband. He shivers, but continues to play.
He hadn’t been purposely edging himself, and he definitely knows that you would help him whenever he asked, but with all the schoolwork piled on top of him, it never crossed his mind. It was now though, and sensitivity was at its highest.
“No, why would you do that; that’s stupid,” Kenma replies to what you assume is a donation. The technological voice isn’t there anymore for you to hear.
The tips of your nails dive past every ounce of clothing settled at his hips.
He shifts in his seat, whether to allow you to pull the band down just enough or to calm his nerves, you don’t know, but the opportunity was right in front of your face. Literally.
You don’t even do anything but hold his length before you start the up and down motions. It’s enough to turn him on more, having him grow in your hand. You can’t imagine the faces he’s making while his viewers’ minds were already polluted.
“Keep going, push,” he exclaims. Voice still soft, but with some sense of urgency.
He was not speaking to you, but you listen anyway, and do as he says. Maybe you could play a game: see how long it takes before he realizes you’re taking orders.
With this, you stroke him a little faster, then run your fleshy thumb over his tip. It began dripping, a single bud threatening to fall. After swiping it away, you disperse what little you could, then wrap your plush lips around his head.
He wasn’t expecting it right after your slow pace.
“Ugh, fuck- third party.”
The groan he emitted was covered quickly by a call, as if that’s what “frustrated” him.
You pop off as quickly as you came, spread your saliva, and now slide your enclosed hand down his cock steadily. Silky smooth, it took no energy to glide along him. Your unoccupied hand squeezes his thigh through the cotton.
“Down, he’s under and one shot.”
You jerk him off as his breathing barely picks up, occasionally coming down to wet him some more, but you see a significant difference when your hand consistently twists just the tip. You’d swirl your tongue around the reddening, most sensitive part of him before dropping even farther to take his balls in your mouth.
You tug and pull harmlessly.
“Hmm...”
Despite what was going on, the streamer was clever with how he hid it.
He asks, “Hey, what do y’all want to hear?”
The viewers were astonished they were being asked; Kenma has previously told them he likes his music and would play whatever he felt like hearing. He did a stream for song recommendations and half of it was him hating on their music and the other half was his viewers attempting to find songs he would like.
Regardless, he unmuted the sound on his computer and turned on the playlist, only slightly louder than usual.
You took this opportunity to actually wrap your lips around his cock, not having to worry about the sounds. You start on the slower side but it didn’t take long to get comfortable. Whatever you couldn’t fit, you jerked off.
His abdomen showcased whatever his face wouldn’t, stuttering every now and then with his hips correcting their position. You brought the wet hand to his balls once more, and attempted to fit all of him down your throat. There was a deep sigh above you.
You closed your eyes and went again, trying to go deeper. You didn’t gag, but your throat made sounds that was enough implication of what was going on. That’s okay though. Some random band one of his mods recommended was playing.
Once more, you tried to go deeper, actually sputtering this time, but once you got past the uncomfortableness of it all, you could go the same depth over and over. You did, breathing through your nose. He could hear your throat, but chat couldn’t. If they could, they would be saying something.
“Oh shit, oh shit, he’s on me,” he huffs, “I’m gonna twist around to cover.”
You remove yourself, partially to breathe, and take two hands to twist on top of each other in opposite directions. His belly button caves in with some more muscles, pure evidence of his pleasure.
This was the second he knew what you were doing. What game you were playing.
If you wanted to play, he could too.
“Where is she?” he reads chat calmly. “I think she’s downstairs eating.”
Was it calm enough—you’re not sure, because he was fidgeting excessively in the leaning chair.
The double entendre has you giggling silently. With a deep breath, you’re back down on him again. It’s not long until you sputter.
“Do you want me to tell her to come back up?” You hear him spit out quickly.
You do as he says, but not without the price of your fingers doubling speed at his head.
“Yeah, I’ll tell her. Hold on.”
With quickness, he mutes and turns his camera off.
He was sweating and physically overwhelmed. Pushing back on his heels, his chair rolls from under the table with you following, finally in his sight. He could already imagine how you looked.
Red lips. Glowing face. Glossy eyes, smiling and happy. You were ethereal. Your hands are working him, but now with his cock down your throat too? Oh my god.
He held a soft touch at your cheek and caressed your face with his thumb. Picking up speed, you smile.
The other hand of his would do the same, brushing a loose stand of hair behind your ear. Faster.
“Just like that,” he breathes.
“Mhmm?” you deepthroat him.
His head drops back involuntarily. His mouth does the same. The heavy breaths that he was holding from the stream let loose.
One last look at your flushed features and-
He groans heavily, adam’s apple bobbing and cock tightening. Skin usually pale but red with desire, he stills.
You close your eyes. It was so fulfilling with your throat stretched and his hands on either side of your plush face.
Warmth seeps past your tongue and down the cavern. It causes you to choke but Kenma definitely doesn’t mind. His sounds flow into your ears, plus some faint praise as he soon begins to release from his high.
You couldn’t taste anything as you slowly raise yourself from him, leaving his cock glistening with saliva and pink, but the taste just barely started to form once it caught your tongue on the way down. You swallow anyway—it wasn’t bad.
You use the back of your hand to wipe your eyes and breathe freely. You lay your cheek on the driest part of his pants, even though you’ll have to get up. You just aren’t ready to see the red wilts on your knees.
“You are amazing,” Kenma catches his breath. He looks back down with his eyes glossed over and tired, but he still runs his finger over your wet lip. You softly kiss it.
. .
“Are you getting back on?” You climb into his fluffy bed, throwing the covers back.
Kenma shakes his head and follows after you in a fresh new set. He grabs the covers and returns them over you both, pushing his hair back and holding you close.
©️ hxltic
#this lowkey sucked#haikyuu!!#haikyū!!#haikyuu headcanons#haikyu x reader#haikyuu hcs#haikyuu smut#god i want him so bad#kenma scenario#kozume kenma#haikyuu kenma#kenma smut#kenma headcanons#kenma hcs#kenma kuzome#kenma x reader#kenma x you#hq kenma#kenma imagine#kenma fanfic#kozume#kozume x reader#kozume x y/n#hq kozume#haikyuu kozume#kodzuken#kenma haikyuu#haikyuu kenma smut
767 notes
·
View notes
Text
my thoughts for the arhc1ve wifies lore is that it happens before all the kww stuff (maybe at the same time as omz but idk) and like. seperates wifies in and outside of minecraft (saiints idea) and then evilfies is created out of that which then leads to all the clonefies. 404* is like patient zero for all the wifies lore
the 'how this becomes arg-core' part TO ME would be that wato and ken start getting weird world glitches and ask wifies for help so he does a normal 'arg solving' video except this time it's himself haunting the worlds. <- during this wifies straight up couldnt access mc at all - I AM STILL PRAYING FOR KWW ARG but i doubt this will be it and i would love love anything so idk if ill include this part LMAO
*IDEAS for numbers (all based on error codes) are 404, 05 (unable to locate host) or 133 (JOIN command cant be used on something thats already been joined) maybe another one but i dont have enough time to look through error codes ToT
#connie rants#notttt sure which number to use so i wont tag for now#sorry tumblr i said most of this before i need to be insane
8 notes
·
View notes
Text

The A-12 pilot who while looking for a crashed F-105 in Utah came across a brothel with a runway (A C-7A Caribou was the largest aircraft to ever land there)
The Oxcart
In 1959, Lockheed began work on the design of a long-range, high-altitude plane, then known as the A-11. It was a Cold War project. Heading the project team was Clarence “Kelly” Johnson, Lockheed’s Vice President for Advanced Development Projects. Johnson had previously led the development of the U-2 spy plane. Five years after work began on the A-11, on Feb. 29, 1964, President Lyndon Johnson told reporters that the aircraft (by that time modified to the A-12 Oxcart production version with a reduced radar cross section) had attained speeds of over 2,000 mph and altitudes of more than 70,000 feet in tests at Edwards Air Force Base (AFB).

CLICK HERE to see The Aviation Geek Club contributor Linda Sheffield’s T-shirt designs! Linda has a personal relationship with the SR-71 because her father Butch Sheffield flew the Blackbird from test flight in 1965 until 1973. Butch’s Granddaughter’s Lisa Burroughs and Susan Miller are graphic designers. They designed most of the merchandise that is for sale on Threadless. A percentage of the profits go to Flight Test Museum at Edwards Air Force Base. This nonprofit charity is personal to the Sheffield family because they are raising money to house SR-71, #955. This was the first Blackbird that Butch Sheffield flew on Oct. 4, 1965.
Noteworthy, according to Col. Richard H. Graham’s book The Complete Book of the SR-71 Blackbird: The Illustrated Profile of Every Aircraft, Crew, and Breakthrough of the World’s Fastest Stealth Jet, during the first three years of pre-operational testing, three A-12s crashed – two from mechanical malfunctions and one because of ground crew error. All pilots ejected safely.
The A-12 crash in Utah and the F-105 crash cover story
On May 24, 1963, A-12 number 926 involved in a subsonic engine test flight and piloted by Ken Collins, crashed fourteen miles south of Wendover, Utah. While testing an inertial navigation system, Collins flew into heavy clouds above thirty thousand feet and began noticing erroneous and confusing airspeed and altitude readings just before the A-12 pitched up, stalled, and went into an inverted spin. Unable to regain control, he ejected at around twenty-five thousand feet and was unhurt. A press cover story referred to the crashed aircraft as being a Republic F-105.
It was first thought that it was a pilot error but later confirmed that it was an inadequate pitot tube design that had caused the air data computer to fail.
Because his sortie was low altitude, Collins was not in his pressure suit, so it added to the credence that the crash was an F-105.

This print is available in multiple sizes from AircraftProfilePrints.com – CLICK HERE TO GET YOURS. SR-71A Blackbird 61-7972 “Skunkworks”
‘With an ironic twist of faith sometime after the loss of Article 123, an F-105 from Nellis was lost and members of the Oxcart (code word of A-12) program were involved in the search for the crash site,’ A-12 pilot Frank Murray recalls in Paul Crickmore���s latest book “Lockheed Blackbird Beyond the Secret Missions.
A-12 pilot searching for crashed F-105
Frank Murray and Dr. Roger Anderson were airborne in a Cessna searching for the crashed F-105 when they located the crash near a small lake with the adjoining property of one of the brothels in the area known as Ash Meadow Ranch. The brothel provided a small dirt runway graded out to allow its customers the option of air travel into the facility.
‘We taxied into Ash Meadow Ranch and we explained that we were here looking for the crash site and we had located it,’ Murray explains.
‘By then it was lunchtime and the Madame got the cook to rustle up some lunch. There was some polite conversation with the Madame and my aviation curiosity got the better of me.
Brothel with landing strip
The A-12 pilot who while looking for a crashed F-105 in Utah came across a brothel with a runway (A C-7A Caribou was the largest aircraft to ever land there)
C-7A Caribou

‘I asked her what was the largest aircraft ever to use the landing strip.
‘She replied the largest was an Army C- 7A Caribou full of GIs from an army base in California! ‘Mind you” she added mischievously they weren’t looking for any downed airplanes!’
Murray concludes;
‘After lunch, the three of us said our goodbyes and departed for our lives back at our Ranch [“Groom Lake,” “The Ranch,” “Area 51,” and “Dreamland” are all names that have been associated with the Groom Lake facility in the Nevada desert]. ‘
I had heard when I was a girl growing up in California that brothels were legal in Nevada. These kinds of rumors were hard for me to believe, but I believe them now!
Be sure to check out Linda Sheffield Miller (Col Richard (Butch) Sheffield’s daughter, Col. Sheffield was an SR-71 Reconnaissance Systems Officer) Twitter X Page Habubrats SR-71, Instagram Page SR71Habubrats and Facebook Page Born into the Wilde Blue Yonder Habubrats for awesome Blackbird’s photos and stories.
@Habubrats71 via X
19 notes
·
View notes
Text
ROUND 1 MATCH 40

Lucio propaganda:
“He's so babygirl. "He's commited war crimes." Yeah, and he looked good doing it.
In all seriousness tho, in his route he experiences a major growth where he realizes the error of his ways and how much he hurted everyone. Most of his mistakes are because he was stupid and ignorant and those that aren't he owns up to, and he also apologizes for everything, multiple times. All he needs is the players support and a little bit of harsh truth to realize just how terrible he was. His redemption arc is amazing and he very much deserves your love.
Also, he's kinda Ken coded, but replaced the horses love with dog love.
Oh yeah, he also has two very cute and pretty dogs, and they become both of your dogs in the good ending, and you two become like bounty hunters or smth witcher style and I think that's really cool. And also he really likes food and cookies and he knows how to sword fight very good, It's said in the canon that knowing his way around the Battlefield is his thing and the one thing he's really good at and I think that's very babygirl of him”
Felicia propaganda:
No Felicia propaganda :(
#lucio the arcana#The Arcana#The Arcana game#Felicia fire emblem#Fire Emblem#Fire Emblem Fates#Round 1#MDDC 2
25 notes
·
View notes
Text


Got myself a few Barbie Land miniature sets and figures. I am looking for the Kens, so I wrote the codes for the ones I got, because I don't feel I have seen these anywhere (I mean these same codes). I didn't get any Ken sadly. But I will keep trying, even if I have never come across the confirmed codes. Then again, I only found these three lipsticks figures in my nearest Walmrt.
I got all the Monster High figures in my nearest Dollar Tree as well. I wanted to get all the characters available, and doubles of Frankie and Draculaura to unbox one, but most of these have damage of some sort, so I just got all the ones that were left to keep the nicer ones mint. Luckily, they had all four in sets of two, except for Laguna. Whose box has the worst damage (IMHO), a factory error, of a piece of carboard from another figure's packaging, stuck right onto the plastic holding her to the card. DX If I can find a second one, with a mint card, I'll get a second one. I wish they had done a Cleo and Skelitas as well, but the latter is probably not a popular or a character they'll be bringing back for any reason (other than Day Of The Dead "collector" dolls). I don't hoard MH anymore, so these are just because I hoard miniatures...
I went to DT to find the Nightmare Before Christmas figures, but I didn't find anything like that at my nearest DT stores. Sadly. T__T;;
5 notes
·
View notes
Text
SIL Levels of Safety Integrity
Safety integrity level (SIL) is an important rating that dictates functional safety requirements. It is a ranking from 1 to 4. Depending on the hazard and risk analysis, it determines which hardware is used for the protection function.
Hardware must meet a specific target failure probability defined during the allocation process. This can be measured in PFD or PFH.
SIL 1
SIL International’s work focuses on Bible translation, literacy, education, development and linguistic research. Founded in the 1930s, SIL is a global nonprofit organization that trains linguist-missionaries so they can live in remote areas and learn local languages to translate the Bible for minority groups.
SIL 1 is the lowest level of Safety Integrity, suitable for systems with low risk and failure consequences that are not severe. It focuses on predefined safety functions, and uses systems that have been verified to be reliable to reduce the risk of dangerous errors.
Ken Pike envisioned SIL as a research organization and self-identified both as a missionary and a scholar. He believed that evangelicals could serve God with their hearts and minds, and that adding to the world’s knowledge was a legitimate way of doing so. He modeled this throughout his career, and SIL continues to emphasize scholarship as an important strategy for Bible translation. SIL’s research activities are guided by the Pike Principles of Research.
SIL 2
The SIL 2 rating signifies a moderate level of risk reduction. Safety systems that enact a SIL 2 SIF typically have more redundancy, higher hardware fault tolerance, and rigorous testing than those that enact a SIL 1 SIF. Safety systems designed for a SIL 2 SIF are more common in the process industry.
Hazard and risk analysis must be performed for each specific function in order to determine the SIL level required. These analyses are used to identify the severity of the possible dangerous events caused by the function and their frequency or likelihood.
Costs increase significantly with each SIS / SIF SIL level, so selecting the correct SIL rating must be done carefully. A SIL compliant design requires specialist software, including tools for HAZOP and LOPA studies and SIF designs. Additionally, functional safety coding standards like MISRA make it easier for engineering teams to comply with IEC 61508 requirements when writing code. This is especially true when using a static analysis tool, such as Helix QAC or Klocwork.
SIL 3
SIL 3 is the highest safety integrity level. It’s used in situations where a failure could lead to fatalities or irreversible environmental damage. It requires more stringent safety measures than SIL 2 and is often chosen by industries that are exposed to high risks, such as oil and gas or petrochemicals.
The SIL process requires a thorough risk assessment to determine whether or not your plant needs SIS. Once this is determined, it is important to understand the cost implications associated with a specific SIL level.
A higher SIL means more redundancy, lower maintenance intervals and strict requirements during development and testing. This can increase costs by up to 10 times compared to a device designed for SIL 1. However, it also provides greater reliability. For example, reducing the proof test duration and frequency can reduce hidden failures and improve overall system safety. This is why KROHNE offers a variety of solutions that are suitable for different SIL levels.
SIL 4
SIL 4 is the highest level of safety integrity. This level is used in high-risk industries where the consequences of system failure are catastrophic. It requires highly reliable hardware and complex fault tolerances. Achieving a SIL 4 rating is expensive and time-consuming.
To determine a SIL for a safety instrumented function, the analyst performs a Hazard and Risk Analysis. This process determines the severity of a dangerous event caused by the SIF and the frequency, or likelihood, that this event will occur. The resulting probability of hazardous failure on demand (PFDavg/PFH) is the SIL for the safety function.
Jenny is a new engineer who has been assigned to a project. She has been wondering why a system may require different SILs for the same SIF. Eddie explains the reasoning behind this. He also offers some helpful tips on how to make sure the SIL allocation is done correctly.
0 notes
Text
Texas Senate passes bill preventing gender changes to birth certificates

AUSTIN — Transgender Texans would not be allowed to have their birth certificates amended to reflect their gender identity under a bill the Senate passed Thursday despite warnings from constituents of the harm it could cause.

Sen. Mayes Middleton, R-Galveston, said his legislation would ensure birth certificates “remain accurate, consistent and reflective of biological reality.”
“A birth certificate, like a death certificate, is a snapshot in time that records accurate vital statistics existing at the time of birth,” Middleton, who authored the proposal, said during Senate debate Wednesday.
“A birth certificate states that child’s God-given sex.”
Senators voted 20-11 to send Senate Bill 406 to the House, where the legislation also must pass in order for it to reach Gov. Greg Abbott’s desk.
All Senate Democrats voted against the bill.
youtube
Transgender Texans and LGBTQ allies testified during a hearing last month that the proposal would harm those who lack identity documents that reflect their gender identity, making access to education, housing and employment more difficult as well as negatively impacting transgender people’s mental health.
SB 406 would require birth certificate forms to include a space to record the biological sex of a child as either male or female.
Texas courts couldn’t issue orders amending them, and registrars could only update the certificate to correct a clerical error or complete one that doesn’t list a biological sex.
That would include updating it later for a person whose sex was unknown at birth due to atypical or ambiguous sex organs, chromosomes or endogenous profile.
A House version of the proposal has not been scheduled for a public hearing.
Witnesses told the Senate State Affairs Committee that birth certificates are key to proving one’s identity or citizenship.
“Now imagine not possessing a form of government identification that accurately reflects your person,” said Landon Richie, a transgender man and policy associate at the Transgender Education Network of Texas.
“The end result,” Richie said, “is isolation, the incentive for others to discriminate against you and the placement of targets on the backs of an already vulnerable group of people.”
President Donald Trump issued an executive order in January that declared the federal government recognizes two sexes that “are not changeable and are grounded in fundamental and incontrovertible reality.”
Later that month, Abbott told state agencies their rules, internal policies, employment practices and other actions should “comply with the law and the biological reality that there are only two sexes.”
The Texas Department of Public Safety stopped accepting court orders to change gender markers on driver’s licenses last year.
Around the same time, the Department of State Health Services similarly stopped allowing gender changes on birth certificates unless the hospital made an error.
In an unbinding opinion issued last month, Texas Attorney General Ken Paxton wrote that district courts lack the authority to require DPS and the health department to amend documents.
Court orders “are void,” and state agencies should immediately correct any driver’s licenses or birth certificates that were “unlawfully altered,” he wrote.
Middleton said his bill “reiterates in our state code what Texas is already doing” and “closes a loophole that courts created with no authority.”
He framed his legislation as a “necessary extension” of the Legislature’s efforts to ban transgender girls and transgender women from participating in girls and women’s sports.
“This bill is not about restricting anyone’s personal expression,” Middleton said.
“It is about ensuring that legal documents reflect accurate statistics and biological reality.”
0 notes
Text
USA DevOps Market- Key Trends Driving Growth
The USA DevOps market is experiencing a remarkable transformation as businesses aim to enhance agility, optimize efficiency, and accelerate innovation in software development. With the increasing pace of digital transformation and widespread adoption of cloud-based technologies, DevOps has emerged as a vital enabler for gaining a competitive edge. According to Ken Research’s latest findings, the market is set for substantial growth, offering unparalleled opportunities for organizations, technology providers, and IT professionals. This blog explores the key trends, challenges, and opportunities that are shaping the future of the DevOps market in the USA.
Request For Free Sample Report @ USA DevOps Market
Key Trends Fueling Market Growth
The growth of the USA DevOps market is being propelled by technological advancements and the growing demand for seamless, efficient operations.
1. Cloud-Centric Solutions Revolutionizing DevOps: Cloud computing has become a pivotal driver of innovation in DevOps practices. Organizations are leveraging cloud-native technologies to improve scalability and adaptability in their development processes.
Containers and Orchestration: Platforms like Kubernetes and Docker are revolutionizing the deployment of applications by providing flexible and scalable solutions. These tools have become the backbone for businesses aiming to manage dynamic workloads effectively.
Serverless Computing: The shift to serverless architectures eliminates the need for managing physical infrastructure, allowing teams to focus on delivering high-value features. This trend is particularly appealing for startups and enterprises seeking cost-efficient scalability.
2. Automation Redefining Development Pipelines: Automation lies at the heart of DevOps, empowering organizations to streamline workflows and reduce errors in software development and delivery.
Continuous Integration/Continuous Delivery (CI/CD): CI/CD pipelines automate testing and deployment, ensuring faster release cycles and minimizing human intervention. By incorporating automated feedback loops, organizations can quickly adapt to changing requirements.
AI-Powered DevOps: Artificial Intelligence is playing a growing role in enhancing DevOps pipelines by predicting potential failures, optimizing resource allocation, and identifying vulnerabilities before they become critical issues.
3. DevSecOps: Integrating Security into DevOps: With cybersecurity threats becoming more prevalent, businesses are prioritizing the integration of security into their DevOps processes.
Proactive Security Measures: The "shift-left" approach emphasizes addressing security concerns early in the development lifecycle. This includes vulnerability assessments during coding stages to minimize risks.
Secure Automation Tools: Automated security testing tools ensure that compliance standards are met without compromising development speed. These solutions are especially critical for sectors like finance and healthcare that handle sensitive data.
Challenges Impacting Market Growth
Despite its significant potential, the USA DevOps market faces several obstacles that need to be addressed for continued expansion.
1. Cultural and Organizational Resistance: One of the most significant barriers to DevOps adoption is resistance to change within organizations. Teams that operate in silos or adhere to traditional development practices often struggle to embrace the collaborative culture that DevOps requires.
2. Skill Shortages: The demand for skilled DevOps professionals far exceeds supply, creating a significant talent gap. Companies often face difficulties in hiring and retaining professionals who possess expertise in tools, methodologies, and cloud-based systems essential for DevOps.
3. Complexity of Tool Integration: The DevOps ecosystem involves a wide range of tools for automation, monitoring, and collaboration. Integrating these tools into a cohesive system can be challenging, especially for enterprises transitioning from legacy systems.
Opportunities in the USA DevOps Market
The market offers abundant opportunities for growth, driven by the increasing adoption of digital transformation and the demand for operational efficiency.
1. Small and Medium-Sized Enterprises (SMEs) Embracing DevOps: While larger organizations have led the way in DevOps adoption, SMEs are now recognizing its value. By adopting cloud-native tools and automation, SMEs can compete with larger players by improving operational efficiency and reducing time-to-market.
2. Expansion of DevOps Services: Managed DevOps services are gaining traction as businesses seek to outsource complex tasks to third-party providers. These services include toolchain management, security implementation, and performance optimization, allowing organizations to focus on core business goals.
3. Hybrid and Multi-Cloud Strategies: With businesses increasingly adopting hybrid and multi-cloud strategies, DevOps solutions that enable seamless integration across multiple environments are in high demand. Providers offering innovative solutions in this area are likely to thrive in the competitive landscape.
Why the USA is a Critical Market for DevOps
Several factors position the USA as a key driver of global DevOps growth:
Digital Transformation Leadership: The USA leads global innovation in digital transformation, with enterprises continuously exploring advanced tools and methodologies to stay ahead.
Cloud Adoption: The widespread adoption of cloud computing in the USA has created a robust foundation for the expansion of DevOps practices.
Tech-Savvy Workforce: The USA boasts a highly skilled workforce that is adept at embracing new technologies, making it an ideal market for DevOps adoption.
Conclusion
The USA DevOps market is transforming how software is developed and delivered, with a focus on agility, automation, and security. While challenges such as skill shortages and organizational resistance persist, the market’s growth is being fueled by technological innovations, increasing adoption among SMEs, and expanding hybrid cloud strategies. As businesses continue to prioritize operational efficiency and customer satisfaction, DevOps will remain a critical enabler of success. Organizations and stakeholders that invest in overcoming challenges and leveraging opportunities in this dynamic market will be well-positioned for future growth. For detailed insights into the trends, challenges, and growth drivers of this market, explore Ken Research’s USA DevOps Market Research Report and unlock the potential of this evolving industry.
#USA DevOps Market#USA DevOps Market Outlook#USA DevOps Market Analysis#USA DevOps Market Top Players#USA DevOps Market Major Player#USA DevOps Market Competitors#DevOps Market#USA DevOps Sector
0 notes
Text
What Is Golang Used For? Common Uses and Applications
Go is also known as Golang is an open-source programming language created by Google in 2007 and was released in 2009. It was developed by Robert Griesemer, Rob Pike and Ken Thompson with the aim to simplify the development process while also providing robust performance, scalability and easy handling of concurrency. Nowadays, Golang is widely used across a range of applications and industries. This article examines the typical use cases and the applications for Golang by highlighting its strengths and the reasons it is an increasingly popular choice for developers.

What Makes Golang Special?
Before diving into the uses of Golang it's important to comprehend the reason Golang is gaining popularity with developers. The language is well-known for its easy learning and its powerful capabilities, such as:
Consistency: The goroutines as well as channels are ideal for programming concurrently, which allows efficient parallelism and multitasking. Performance: Golang is a compiled language that can directly translate into machine code, which makes it more powerful than interpreted languages such as Python and JavaScript. Statically Typing Golang makes use of static typing to reduce the risk of running into errors and increasing the reliability of the applications. A strong standard library has an extensive standard library that comes with built-in support of web servers, handling files as well as networking.
Building Web Servers and APIs One of the more popular applications of Golang is for web development. Golang's light syntax, coupled with the powerful standard library makes it the ideal choice for creating web servers, REST APIs as well as full-blown web applications.
Why Golang for Web Servers?
The web servers typically must handle a variety of clients' requests at once. Go's goroutines enable developers to handle multiple requests at once with little impact on the system.
Speed: Golang is compiled, which means that it runs faster than other interpreted languages. This makes it perfect to build powerful web servers.
Scalability: As traffic rises the server that runs on Golang can expand horizontally without difficulty. The simple concurrency model of Golang ensures that developers are able to efficiently handle more requests without requiring complex programming.
Popular web frameworks such as Gin or Echo are extensively used within the Go ecosystem to ease the creation of microservices and APIs for web development. Numerous major corporations including Google, Dropbox, and Uber utilize Golang to provide the web-based infrastructure of their companies.
2. Cloud Computing and Distributed Systems
The high performance of Golang and its effective memory management make it the ideal option in cloud computing as well as distributed systems. The ability of the language to manage large amounts of concurrent users with a minimum amount of resources makes it a perfect choice for developing cloud-based applications.
Key Benefits of Cloud Computing:
Microservices Architecture Golang can be used in many cases to create microservices, which allows the application to break into smaller, independent deployable parts. Its ability to support concurrency and parallelism aids in creating robust and scalable systems that are fault-tolerant.
Containerization Go is the primary language used to create Docker which is a well-known containerization platform. Docker's capability to pack applications in containers is essential in cloud computing. Golang is a key component in the cloud computing ecosystem.
Kubernetes: The most popular cloud orchestration and container management platform Kubernetes can also be written using Golang. Its capability to automate the scale, deployment and management of containerized apps is what has made it a popular choice in the world of cloud computing.
3. Command-Line Tools and Utilities Golang is frequently utilized to develop utility tools and command line programs due to its ease of use and speed. The tools are a range of utility programs for the system, network monitoring tools, as well as more complicated applications such as backup software for data.
Why Golang for CLI Tools?
Cross-Platforms: Golang supports cross-compilation, meaning that programmers can write their own tool and then deploy it across multiple operating systems like Linux, macOS, and Windows. Single Binary Golang is compiled to one and statically linked binary making it simple for you to share and distribute command line tools without having to worry about dependencies or libraries from outside. Efficiency: Since Golang is fast, it's ideal for performance-sensitive tools that need to process large datasets or perform complex operations quickly.
4. Networking and Cloud Services Due to its speedy nature, Golang course is frequently used to build cloud services and network services. Its integrated support for networking libraries, like TCP/IP and HTTP It is the ideal choice for projects such as the creation of load balancers, proxies as well as VPNs.
Network-Related Applications:
Proxy Servers: Go's effectiveness and ease of use make it a great option for creating reverse proxies or web proxy servers which allow developers to direct network traffic effectively. Concurrency in Load Balancing: Go's capabilities permit developers to write fast as well as efficient load balancers that spread the network's traffic equally across several servers. VPN Services Golang's strong network capabilities make it the perfect choice to create high-performance, secure Virtual Private Network (VPN) solutions.
5. Data Processing and Analysis Another important application for Golang can be found in the area of data processing as well as analysis. With the growth of real-time analytics and big data Golang's efficiency as well as its scalability, concurrency, and performance makes it a good choice for jobs such as pipelines for data, ETL processes, and streaming analytics.
Use Cases for Data Processing:
Real-Time Analytics: Golang's capability to process huge amounts of data fast and concurrently is particularly beneficial for applications that require real-time analytics. ETL Pipelines: The Go's speed and its ease of integration with other services make it a top option for the construction of ETL (Extract Transform and Load) pipelines for the field of data engineering. Machine Learning: Although Golang isn't as extensively utilized in machine learning as Python its speed and simplicity make it the ideal choice for specific kinds of tasks in data processing that are related to machine-learning workflows.
6. Game Development Although Go isn't as extensively utilized in game development as languages such as C++ or Unity's C#, it has begun to gain traction in some areas, particularly for the development of server-side components in multiplayer games. Go's concurrency capabilities are particularly useful when dealing with large amounts of users in real time.
Conclusion
In the end, Golang is a versatile swift, quick, and efficient programming language that can be used for many applications. It can be used for creating high-performance web servers, creating cloud-native apps, writing command line tools, or performing complicated data processing tasks. Golang's efficiency and simplicity make it a preferred option for developers. The capability to effectively handle concurrency as well as the ability to support cloud computing, network in addition to data processing, position it as a language for the future.
In the future, as Golang continues to increase in popularity, its applications will surely expand and will continue to be an option for developers seeking to build quick reliable, scalable, and stable systems. No matter if you're just beginning to learn programming or a seasoned developer, Golang offers a wide variety of software to suit all kinds of projects.
0 notes
Text
Go (Golang): Unveiling the Power of Simplicity and Performance in Backend Development

Introduction
Go, also referred to as Golang, is a statically typed, compiled programming language with an emphasis on dependability, simplicity, and performance. Since its initial release in 2009, Go—a programming language developed by Google programmers Robert Griesemer, Rob Pike, and Ken Thompson—has grown in popularity due to its efficiency, user-friendliness, and suitability for developing concurrent and scalable systems.
History of Go
Go was first developed at Google in 2007 and released to the public in 2009. The language was designed to tackle certain issues that Google developers encountered, specifically with efficiency and scalability. Go was created with great performance, readability, productivity, and conciseness in mind. The language was widely adopted because of its open-source nature and rapid rise in popularity within the software development community.
Pros of Go
Concurrent and Parallel Programming:
Concurrency was a priority when Go was designed. Concurrent programming is easier to understand because to goroutines, which are lightweight threads controlled by the Go runtime. In addition, the language has channels, which facilitate Goroutine-to-Goroutine communication and simplify the writing of effective parallel code.
Efficiency and Performance:
Go runs more quickly because its compilation process generates native machine code. Because of its low latency optimization, its garbage collector is appropriate for real-time applications. Go is a fantastic option for applications that require high performance because its efficiency is frequently on par with that of languages like C and C++.
Readability and Simplicity:
Go values readability and simplicity. Because to its simple architecture and basic syntax, developers have less cognitive strain when writing and maintaining code. The language stays away from superfluous features and concentrates on offering a clear and effective programming environment.
Standard Library:
Go includes an extensive standard library encompassing a broad range of features, including cryptography and networking. When creating applications, developers can save time and effort by using the standard library, which is well-documented and adheres to best practices.
Static Typing:
Because Go is statically typed, a variable's type is known at compile time. As a result, errors are found early in the development process, improving the maintainability and reliability of the code.
Cross-Platform Support:
Go offers cross-compilation, which enables programmers to create binaries for various architectures and platforms using a single codebase. This feature facilitates the creation of applications that function flawlessly in a variety of environments and streamlines the deployment process.
Cons of Go
Prior to 2022, generics:
The lack of generics, a feature that makes code more flexible and reusable, has long been criticized in relation to Go. It is noteworthy to mention that Go 1.18, which was released in 2022, addressed this limitation by introducing support for generics, as of my last knowledge update in January 2022.
Learning Curve for Some Developers:
The switch to Go may initially be difficult for developers used to specific language features, such as inheritance and sophisticated type systems. But once they get a feel for it, a lot of developers really like how straightforward and consistent Go's design is.
Dependency Management (Historical):
Go's strategy for handling dependencies has changed over time. The language relied on manually copying dependencies into the project or using a tool known as "vendoring" in the past. Although the use of modules in more recent versions has made dependency management better, there may have been difficulties in the past for certain developers.
No GUI Library in the Standard Library:
There isn't a graphical user interface (GUI) library in the Go standard library. Although there are third-party options, developers working on desktop applications that need complex graphical interfaces may find it disadvantageous that there isn't a native GUI library.
Why Choose to Go as a Backend Language?
Scalability:
Go is an excellent choice for developing scalable backend systems because of its built-in support for concurrent programming via Goroutines and channels. Applications can efficiently handle a large number of concurrent requests thanks to the language's performance.
Performance:
Go is a great option for backend development due to its high performance, which is a result of its native compilation and effective garbage collector. Go's speed is a great advantage when managing resources, processing data, or handling API requests.
Simplicity and Productivity:
Go's design decisions and syntax are straightforward, which encourages productivity. With less complexity and a lower chance of errors, developers can write clear, maintainable code that facilitates teamwork.
Community and Ecosystem:
The community in Go is thriving and expanding. Major corporations support the language, guaranteeing ongoing development and assistance. Database drivers and web frameworks are just two examples of the many libraries and tools in the ecosystem that make backend development easier.
Docker and Kubernetes:
The development of containerization and orchestration technologies has been greatly aided by Go. Two popular tools for containerization and orchestration are written in Go: Docker and Kubernetes. Go is a great fit for backend development because it provides a smooth integration experience with these technologies.
Conclusion
With its focus on concurrent programming, efficiency, and simplicity, Go has grown in popularity as a language for backend development. Because of its scalability, performance, and strong community support, it's an excellent choice for developing reliable, high-performing systems. Go's advantages in concurrent programming and backend development make it a desirable choice for developers and businesses looking to create scalable and effective applications, even though it might not be the best choice for every use case. Go is probably going to stay the industry standard for backend development as long as the language keeps improving and addressing its shortcomings.
Credit- Kashif Patel
MetricsViews Pvt. Ltd.
MetricsViews specializes in building a solid DevOps strategy with cloud-native including AWS, GCP, Azure, Salesforce, and many more. We excel in microservice adoption, CI/CD, Orchestration, and Provisioning of Infrastructure - with Smart DevOps tools like Terraform, and CloudFormation on the cloud.
www.metricsviews.com
0 notes
Text
Workday Inc. boosts its performance to give ample competition for the top ranking
Being a Cloud-Based vendor in Human Capital Management, financial management and others, leading for a broad reach out with different goals set out for promising growth.
STORY OUTLINE
With the presence of cloud based and digitized solutions, Workday upgrades itself on a quick succession.
With technological innovation, Workday Inc. quickly propelled upwards.
Focusing mainly on people centricity, Workday Inc. receives increase in employee retention.
With User Training and Support, assisted with Integration Availabilities, makes working easier and seamless.

To Know More About US HR Analytics Market
1. With the presence of cloud based and digitized solutions, Workday upgrades itself on a quick succession.
To learn more about this report Download a Free Sample Report
With promising Next Gen Cloud-Based Human Capital Management (HCM) Platform leads to an overall increase in efficiency.
Workday Inc. places strong emphasis on continuous innovation, with increased performance and scalability and deeper insights into Supply Chain, resulting in overall growth.
With the leadership of co-founder and CEO of Workday Inc., Aneel Bhusri, improvements through strong determined hands have been observed.
Workday’s profitable User Centric approach helps bring more users and helps developing an enhanced experience.
According to Ken Research, Workday Inc. has made various changes through which they have are able to give a strong competitive standpoint, up in the US HR Analytics Market, getting improved through technology, insights, processing, employment and payments, resulting in an overall moderate growth over the years.
2. With technological innovation, Workday Inc. quickly propelled upwards.
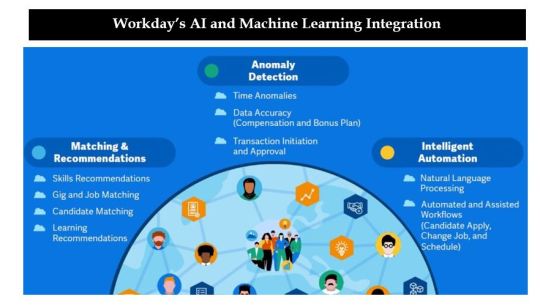
Visit this Link: – Request for custom report
Workday’s Cloud First Approach has allowed for the reduced IT complexities, scalability and real-time updates delivery.
With the involvement of Artificial Intelligence (AI), assisted with Cloud Services, Workday’s Day to day work becomes much more seamless.
Integration of deep Machine Learning (ML), reduces chances of making errors and allows for the induction of newer methodologies.
With the prioritization of mobile access through Online Applications, helping employees get real time data and future plans via one place, resulting in time preserving.
With Cloud Services handling maximum data, Stringent Security protocols are maintained with stronger encryption, assisted via the help of AI.
3. Focusing mainly on people centricity, Workday Inc. receives increase in employee retention.

Request free 30 minutes analyst call
With creation of software and Employee-Centric design philosophy, company prioritizes on the employee’s needs, interactions with Managers and other HR professionals.
Presence of Human Experience Design (Hx) team, mediates every interaction with a positive outcome benefiting the company’s growth.
User-Centric model has allowed for the real time user testing and validations, leading to an overall refinement based on actual user requirements.
With Workday’s advanced Learning management, employees are given hands on training day to day basis, to learn and grow new skills to perform efficiently.
4. With User Training and Support, assisted with Integration Availabilities, makes working easier and seamless.
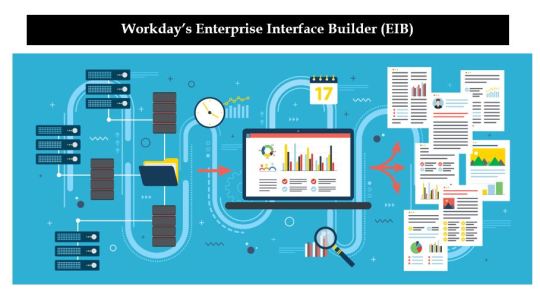
Incorporation of open Integration Platform has led to seamless connectivity and reach to wide third-party applications and systems.
With Integration Cloud giving platform for building, managing and monitoring integrations for proper development.
With the integration of Enterprise Interface Builder (EIB), configuration for integration is made simple without the need to write codes.
By connecting with other third-party like Salesforce, Microsoft 360, via the cloud, enables to seamlessly configure data from others by exchange.
CONLCUSION
With the rise in technological advancements and global digitization, company like Workday Inc. has not stopped its own innovation, leading to an overall growth which in turn increases the potential of the US HR Analytics Market.
#market research#business#united states#ken research#education#recuritment#market report#market analysis#market research report#work day
0 notes
Text
ok so initially i voted stage for this but i just have so many ideas for all of them ahdjdksk. but i think maybe computer of sort? some sort of code or system perhaps. in the show the universe is frequently referred to as being "broken" that they need to "fix" it a little like you would for a computer/system/some sort of technology. even in cast interviews people refer to dirk as a "glitch" in the universe - like an error in coding. the world is a system and the universe is running it but has a virus, perhaps XD. also ken is a computer guy, he fixes them for a living. and by the end of s2, perhaps he could be convinced he could fix the universe too, like you would a computer/code. (i can't remember if he actually said that or not, it's been a while since ive seen s2).
i am also partial to the idea of the universe being a character, narrative, stage, and basically every other option. and also my secret something else option. will rant about any of those if asked ;)
in dghda i always felt the universe was treated like something that wasnt just stars and space, ect. curious to know what you think (also sorry for the sortve vagueness with some options! i was struggling to phrase them exactly 😅 but hey open interpretation is always welcome)
41 notes
·
View notes
Text
452: Love Changes Everything
The Creator.
Hollywood has continued to double down over the last decade on franchises and the amount of original content has become sparse, yet in 2023, some of the biggest movies of the year were not based on existing movie franchises.
In this episode of The 602 Club hosts Matthew Rushing and Christy Morris talk about the new, original sci-fi film from director Gareth Edwards, The Creator. We discuss our anticipation, the world, chapters, personhood, error code, evolution, the cast, the soundtrack and our ratings.
Chapters Anticipation (00:02:23) The World (00:05:16) Chapters (00:16:00) Personhood (00:21:37) Error Code (00:27:08) Evolution (00:31:33) John David Washington (00:34:05) Madeleine Yuna Voyles (00:38:11) Gemma Chan (00:39:54) Allison Janney (00:42:37) Ken Watanabe (00:45:13) The Soundtrack (00:47:04) Ratings (00:49:51)
Host Matthew Rushing
Co-Host Christy Morris
Production Matthew Rushing (Editor and Producer) C Bryan Jones (Executive Producer) Matthew Rushing (Executive Producer)
Social Twitter: @The602Club Instagram: @the602clubtfm
New podcast episode:
0 notes
Text
Meanwhile with DigiAdvs 02 [...and some O.C.s]
Ken, to Inter-national O.C. Chosen Shane: Tell me {"US"} what else you saw. {In, the "Digital" Void} Shane: ... Ken: Like those "landmarks" you mentioned. S h a n e: ... Shane, Deep sighing: ...Fine. Shane: I could only "float" ("get pulled") through, so I wasn't going along *completely* by my own will. But at the same time, once the "landmark" came into view... I WANTED to Know what it was about. Because there might have been "hints" in that place as to "what was happening to me". Ken, nodding: (Go on...) Shane, grunting a bit in frustration when remembering 'that': ... So I got "pulled" closer to the landmark, and my partner... well, "they" usually follow along with me. (I'm not sure if I should tell "this person" that my partner has *control*...) (*Doesn't*) So I had a small "idea" it was an actual landmark, I just had no idea what I'd find there. Shane, recounting further: So I entered from the digital "stream" above, but suddenly... I landed. Ken, echoing: You "landed". Shane, NODDING: There was something similar to "gravity" there, except there *wasn't*. Ken, Wheels turning in Mind: ... So, how did you "land"? Shane: I'm not completely sure... but once I "explored" further, I realized the "digital space" surrounding "that" place may have been "warped". Shane: I saw something that looked like "Mt. Fuji" but then thought, "that can't POSSIBLY be Mt. Fuji??" KEN: ... (Oh no...) Shane: But it looked *scary similar* in silhouette. So I "landed" at random, and then (stumbled around) *walked* around, looking for any "clue" - if there even *were* any. And then, I found a "hidden place" that looked like it once had PEOPLE there... KEN: Shane: - But there *wasn't* any people around - but there WAS "tech" - "DIGITAL" related "tech" from OUR world. Ken: (That's the "scrap data"... that's 'normal'...) Shane: I had seen similar before, too, but this kind... it was once FUNCTIONAL. KEN: (... Oh no.) Shane: Over half of this "area" was already in ruins. There was shattered glass in one area of the ground... And the place itself looked like it had been "abandoned". But I went up to one of the strange "technological"-like "capsules" - that looked large enough to *hold a human*. Ken: (Oh NO.) Shane: The majority of these "tech" pieces still had their 'lids' on, but some clearly had pieces that broke off over time, because that glass was on the ground too. The one I went up to, though - it had a Digital panel ON it. And because I know a "little bit" (a LOT) about coding, I could ACCESS IT. Ken: What did you find?? Shane: It looked like the panel had BEEN accessed once before... AND, whoever accessed it, LET OUT whatever was inside. As if "whoever" was in there was once "held" or "contained" in there. Or... Ken: ... "Trapped?" Shane: Yeah. The glass was *heaviest* around a capsule *across* from the one I accessed too, like it had *mostly* shattered from *that* specific "capsule". And there were *exactly SEVEN others like the one I accessed*... KEN: ... 8 in total. SHANE: ... Yeah. KEN: ... ("Eight Chosen Children") SHANE: Except ONE of them had that extra glass near it. But it TOO was in an "open" state... KEN: SHANE: So I checked *that one's* panel... and that was when I also realized the glass was removed from the INSIDE. KEN: ... (Whoever inside was trying to "escape".) Shane: So I checked the panel's logs to see if I could figure out at all what had been happened there. It had big "ERROR" recordings all over - like the capsule's functioning was interrupted from the moment the damage began, even if it had been trying to keep the "subject" contained a little longer. Shane: So ... I reasoned, the one inside "this" capsule must have "let out" or "rescued" the ones inside all seven of *the rest*. *Whoever* it was... they *had knowledge* OF coding AND "hacking" to be able to access these panels. KEN: (... It's not unusual for some "Digital" beings, but when you add in "Eight Chosen" relevancy...) SHANE: ... And. The whole place was about ready to self destruct. Or. You know. Explode KEN:
#repeatverse#repeat shane#repeat koushiro#repeat ken#the past world#past world koushiro#past world koushirou#prince koushirou#digiadvs royalty au#the digital kingdom#coftff#coftff shane#og repeatverse#the digital void#knowledge kingdom#shane and ken#meanwhile with digiadvs 02#meanwhile with shane#koushirouizumi coftff#koushirouizumi cof#prince taichi#(Dun Dun Dun SHANES + O.C.s PLOTs THICKENS...)#(OK I Had This Drafted 3 Whole Days Ago)#(BUT over half this Plot INCLUDING Shane in {A} VoidTM has been in background of the whole 'Fic+A.M.V.s-verse since the BEGINNING)#(ItsATimelinesSeriesTM)#(MEANWHILE SonicPrime S2 just dropped Ep01 on Y.T and im LAUGHING so Hard *theyre LITERALLY CALLING IT 'THE VOID'*)#(YOUNG ME BANGING FISTS DOWN 'DIGITAL VOID!!! DIGITAL VOID!!! DIGITAL VOID Where I can Mess With Timelines & A.U.s')#('AND MAKE COOL THINGS HAPPEN Because These Were 'Verses For A s cI-FI tropey based Series')#(ANYWAY so its pretty similar to Something in DigiAdv 2020 Towards End but with Much More Than 2020 Actually Showed At Time)#(ThisWasJustONETimeline+A.U.Idea thenShaneHappened WHOOOO Koushiro Voice ' Why ' {Do I Have So Many A.U.s})
0 notes
Text


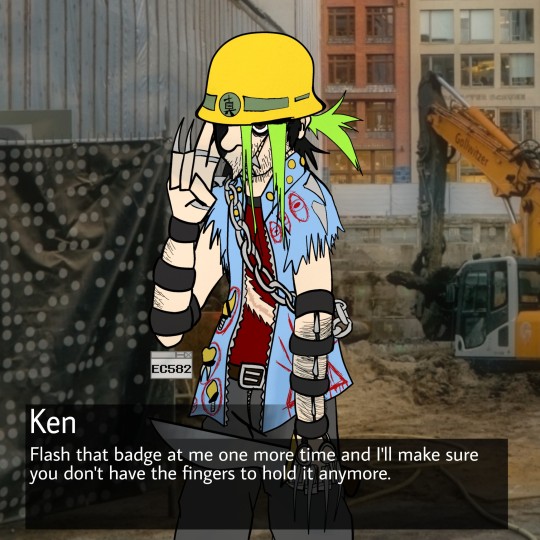
I am a liar I wound up coloring the sketch + giving it two bg variants
Kiwami 2: in which Ken gives up the liberty spikes for the sake of workplace safety, has to deal with way too many cops because "they're on our side calm down", and has at least one rooftop emotional breakdown
#error code: ken#error code: art#error code: ref sheet#kimd of??#it's the closest to a ref sheet k2 ken has for now#this game made me feel way too many emotions
2 notes
·
View notes
Text
Delegating trust is really, really, really hard (infosec edition)

CORRECTION: A previous version of this thread reported that Trustcor has the same officers as Packet Forensics; they do not; they have the same officers as Measurement Systems. I regret the error.
I’ve got trust issues. We all do. Some infosec pros go so far as to say “trust no one,” a philosophy more formally known as “Zero Trust,” that holds that certain elements of your security should never be delegated to any third party.
The problem is, it’s trust all the way down. Say you maintain your own cryptographic keys on your own device. How do you know the software you use to store those keys is trustworthy? Well, maybe you audit the source-code and compile it yourself.
But how do you know your compiler is trustworthy? When Unix/C co-creator Ken Thompson received the Turing Prize, he either admitted or joked that he had hidden back doors in the compiler he’d written, which was used to compile all of the other compilers:
https://pluralistic.net/2022/10/11/rene-descartes-was-a-drunken-fart/#trusting-trust
OK, say you whittle your own compiler out of a whole log that you felled yourself in an old growth forest that no human had set foot in for a thousand years. How about your hardware? Back in 2018, Bloomberg published a blockbuster story claiming that the server infrastructure of the biggest cloud companies had been compromised with tiny hardware interception devices:
https://www.bloomberg.com/news/features/2018-10-04/the-big-hack-how-china-used-a-tiny-chip-to-infiltrate-america-s-top-companies
The authors claimed to have verified their story in every conceivable way. The companies whose servers were said to have been compromised rejected the entire story. Four years later, we still don’t know who was right.
How do we trust the Bloomberg reporters? How do we trust Apple? If we ask a regulator to investigate their claims, how do we trust the regulator? Hell, how do we trust our senses? And even if we trust our senses, how do we trust our reason? I had a lurid, bizarre nightmare last night where the most surreal events seemed perfectly reasonable (tldr: I was mugged by invisible monsters while trying to order a paloma at the DNA Lounge, who stole my phone and then a bicycle I had rented from the bartender).
If you can’t trust your senses, your reason, the authorities, your hardware, your software, your compiler, or third-party service-providers, well, shit, that’s pretty frightening, isn’t it (paging R. Descartes to a white courtesy phone)?
There’s a joke about physicists, that all of their reasoning begins with something they know isn’t true: “Assume a perfectly spherical cow of uniform density on a frictionless surface…” The world of information security has a lot of these assumptions, and they get us into trouble.
Take internet data privacy and integrity — that is, ensuring that when you send some data to someone else, the data arrives unchanged and no one except that person can read that data. In the earliest days of the internet, we operated on the assumption that the major threat here was technical: our routers and wires might corrupt or lose the data on the way.
The solution was the ingenious system of packet-switching error-correction, a complex system that allowed the sender to verify that the recipient had gotten all the parts of their transmission and resend the parts that disappeared en route.
This took care of integrity, but not privacy. We mostly just pretended that sysadmins, sysops, network engineers, and other people who could peek at our data “on the wire” wouldn’t, even though we knew that, at least some of the time, this was going on. The fact that the people who provided communications infrastructure had a sense of duty and mission didn’t mean they wouldn’t spy on us — sometimes, that was why they peeked, just to be sure that we weren’t planning to mess up “their” network.
The internet always carried “sensitive” information — love letters, private discussions of health issues, political plans — but it wasn’t until investors set their sights on commerce that the issue of data privacy came to the fore. The rise of online financial transactions goosed the fringe world of cryptography into the mainstream of internet development.
This gave rise to an epic, three-sided battle, between civil libertarians, spies, and business-people. For years, the civil liberties people had battled the spy agencies over “strong encryption” (more properly called “working encryption” or just “encryption”).
The spy agencies insisted that civilization would collapse if they couldn’t wiretap any and every message traversing the internet, and maintained that they would neither abuse this facility, nor would they screw up and let someone else do so (“trust us,” they said).
The business world wanted to be able to secure their customers’ data, at least to the extent that an insurer would bail them out if they leaked it; and they wanted to actually secure their own data from rivals and insider threats.
Businesses lacked the technological sophistication to evaluate the spy agencies’ claims that there was such a thing as encryption that would keep their data secure from “bad guys” but would fail completely whenever a “good guy” wanted to peek at it.
In a bid to educate them on this score, EFF co-founder John Gilmore built a $250,000 computer that could break the (already broken) cryptography the NSA and other spy agencies claimed businesses could rely on, in just a couple hours. The message of this DES Cracker was that anyone with $250,000 will be able to break into the communications of any American business:
https://cryptome.org/jya/des-cracker.htm
Fun fact: John got tired of the bar-fridge-sized DES Cracker cluttering up his garage and he sent it to my house for safekeeping; it’s in my office next to my desk in LA. If I ever move to the UK, I’ll have to leave it behind because it’s (probably) still illegal to export.
The deadlock might have never been broken but for a key lawsuit: Cindy Cohn (now EFF’s executive director) won the Bernstein case, which established that publishing cryptographic source-code was protected by the First Amendment:
https://www.eff.org/cases/bernstein-v-us-dept-justice
With cryptography legalized, browser vendors set about securing the data-layer in earnest, expanding and formalizing the “public key infrastructure” (PKI) in browsers. Here’s how that works: your browser ships with a list of cryptographic keys from trusted “certificate authorities.” These are entities that are trusted to issue “certificates” to web-hosts, which are used to wrap up their messages to you.
When you open a connection to “https://foo.com," Foo sends you a stream of data that is encrypted with a key identified as belonging to “foo.com” (this key is Foo’s “certificate” — it certifies that the user of this key is Foo, Inc). That certificate is, in turn, signed by a “Certificate Authority.”
Any Certificate Authority can sign any certificate — your browser ships with a long list of these CAs, and if any one of them certifies that the bearer is “Foo.com,” that server can send your browser “secure” traffic and it will dutifully display the data with all assurances that it arrived from one of Foo, Inc’s servers.
This means that you are trusting all of the Certificate Authorities that come with your browser, and you’re also trusting the company that made your browser to choose good Certificate Authorities. This is a lot of trust. If any of those CAs betrays your trust and issues a bad cert, it can be used to reveal, copy, and alter the data you send and receive from a server that presents that certificate.
You’d hope that certificate authorities would be very prudent, cautious and transparent — and that browser vendors would go to great lengths to verify that they were. There are PKI models for this: for example, the “DNS root keys” that control the internet’s domain-name service are updated via a formal, livestreamed ceremony:
https://www.cloudflare.com/dns/dnssec/root-signing-ceremony/
There are 14 people entrusted to perform this ceremony, and at least three must be present at each performance. The keys are stored at two facilities, and the attendees need to show government ID to enter them (is the government that issued the ID trustworthy? Do you trust the guards to verify it? Ugh, my head hurts).
Further access to the facility is controlled by biometric locks (do you trust the lock maker? How about the person who registers the permitted handprints?). Everyone puts a wet signature in a logbook. A staffer has their retina scanned and presents a smartcard.
Then the staffer opens a safe that has a “tamper proof” (read: “tamper resistant”) hardware module whose manufacturer is trusted (why?) not to have made mistakes or inserted a back-door. A special laptop (also trusted) is needed to activate the safe’s hardware module. The laptop “has no battery, hard disk, or even a clock backup battery, and thus can’t store state once it’s unplugged.” Or, at least, the people in charge of it claim that it doesn’t and can’t.
The ceremony continues: the safe yields a USB stick and a DVD. Each of the trusted officials hands over a smart card that they trust and keep in a safe deposit box in a tamper-evident bag. The special laptop is booted from the trusted DVD and mounts the trusted USB stick. The trusted cards are used to sign three months worth of keys, and these are the basis for the next quarter’s worth of secure DNS queries.
All of this is published, videoed, livestreamed, etc. It’s a real “defense in depth” situation where you’d need a very big conspiracy to subvert all the parts of the system that need to work in order to steal underlying secrets. Yes, bottom line, you’re still trusting people, but in part you’re trusting them not to be able to all keep a secret from the rest of us.
The process for determining which CAs are trusted by your browser is a lot less transparent and, judging from experience, a lot less thorough. Many of these CAs have proven to be manifestly untrustworthy over the years. There was Diginotar, a Dutch CA whose bad security practices left it vulnerable to a hack-attack:
https://en.wikipedia.org/wiki/DigiNotar
Some people say it was Iranian government hackers, who used its signing keys to forge certificates and spy on Iranian dissidents, who are liable to arrest, torture and execution. Other people say it was the NSA pretending to be Iranian government hackers:
https://www.schneier.com/blog/archives/2013/09/new_nsa_leak_sh.html
In 2015, the China Internet Network Information Center was used to issue fake Google certificates, which gave hackers the power to intercept and take over Google accounts and devices linked to them (e.g. Android devices):
https://thenextweb.com/news/google-to-drop-chinas-cnnic-root-certificate-authority-after-trust-breach
In 2019, the UAE cyber-arms dealer Darkmatter — an aggressive recruiter of American ex-spies — applied to become a trusted Certificate Authority, but was denied:
https://www.reuters.com/investigates/special-report/usa-spying-raven/
Browser PKI is very brittle. By design, any of the trusted CAs can compromise every site on the internet. An early attempt to address this was “certificate pinning,” whereby browsers shipped with a database of which CAs were authorized to issue certificates for major internet companies. That meant that even though your browser trusted Crazy Joe’s Discount House of Certification to issue certs for any site online, it also knew that Google didn’t use Crazy Joe, and any google.com certs that Crazy Joe issued would be rejected.
But pinning has a scale problem: there are billions of websites and many of them change CAs from time to time, which means that every browser now needs a massive database of CA-site pin-pairs, and a means to trust the updates that site owners submit to browsers with new information about which CAs can issue their certificates.
Pinning was a stopgap. It was succeeded by a radically different approach: surveillance, not prevention. That surveillance tool is Certificate Transparency (CT), a system designed to quickly and publicly catch untrustworthy CAs that issue bad certificates:
https://www.nature.com/articles/491325a
Here’s how Certificate Transparency works: every time your browser receives a certificate, it makes and signs a tiny fingerprint of that certificate, recording the date, time, and issuing CA, as well as proof that the CA signed the certificate with its private key. Every few minutes, your browser packages up all these little fingerprints and fires them off to one or more of about a dozen public logs:
https://certificate.transparency.dev/logs/
These logs use a cool cryptographic technology called Merkle trees that make them tamper-evident: that means that if some alters the log (say, to remove or forge evidence of a bad cert), everyone who’s got a copy of any of the log’s previous entries can tell that the alteration took place.
Merkle Trees are super efficient. A modest server can easily host the eight billion or so CT records that exist to date. Anyone can monitor any of these public logs, checking to see whether a CA they don’t recognize has issued a certificate for their own domain, and then prove that the CA has betrayed its mission.
CT works. It’s how we learned that Symantec engaged in incredibly reckless behavior: as part of their test-suite for verifying a new certificate-issuing server, they would issue fake Google certificates. These were supposed to be destroyed after creation, but at least one leaked and showed up in the CT log:
https://arstechnica.com/information-technology/2017/03/google-takes-symantec-to-the-woodshed-for-mis-issuing-30000-https-certs/
It wasn’t just Google — Symantec had issued tens of thousands of bad certs. Worse: Symantec was responsible for more than a third of the web’s certificates. We had operated on the blithe assumption that Symantec was a trustworthy entity — a perfectly spherical cow of uniform density — but on inspection it was proved to be a sloppy, reckless mess.
After the Symantec scandal, browser vendors cleaned house — they ditched Symantec from browsers’ roots of trust. A lot of us assumed that this scandal would also trigger a re-evaluation of how CAs demonstrated that they were worth of inclusion in a browser’s default list of trusted entities.
If that happened, it wasn’t enough.
Yesterday, the Washington Post’s Joseph Menn published an in-depth investigation into Trustcor, a certificate authority that is trusted by default by Safari, Chrome and Firefox:
https://www.washingtonpost.com/technology/2022/11/08/trustcor-internet-addresses-government-connections/
Menn’s report is alarming. Working from reports from University of Calgary privacy researcher Joel Reardon and UC Berkeley security researcher Serge Egelman, Menn presented a laundry list of profoundly disturbing problems with Trustcor:
https://groups.google.com/a/mozilla.org/g/dev-security-policy/c/oxX69KFvsm4/m/etbBho-VBQAJ
First, there’s an apparent connection to Packet Forensics, a high-tech arms dealer that sells surveillance equipment to the US government. One of Trustcor’s partners is a holding company managed by Packet Forensics spokesman Raymond Saulino.
If Trustcor is working with (or part of) Packet Forensics, it could issue fake certificates for any internet site that Packet Forensics could use to capture, read and modify traffic between that site and any browser. One of Menn’s sources claimed that Packet Forensics “used TrustCor’s certificate process and its email service, MsgSafe, to intercept communications and help the U.S. government.”
Trustcor denies this, as did the general counsel for Packet Forensics.
Should we trust either of them? It’s hard to understand why we would. Take Trustcor: as mentioned, it has a “private” email service called “Msgsafe,” that claims to offer end-to-end encrypted email. But it is not encrypted end-to-end — it sends copies of its users’ private keys to Trustcor, allowing the company (or anyone who hacks the company) to intercept its email.
It’s hard to avoid the conclusion that Trustcor is making an intentionally deceptive statement about how its security products work, or it lacks the basic technical capacity to understand how those products should work. You’d hope that either of those would disqualify Trustcor from being trusted by default by billions of browsers.
It’s worse than that, though: there are so many red flags about Trustcor beyond the defects in Msgsafe. Menn found that that company’s website identified two named personnel, both supposed founders. One of those men was dead. The other one’s Linkedin profile has him departing the company in 2019.
The company lists two phone numbers. One is out of service. The other goes to unmonitored voicemail. The company’s address is a UPS Store in Toronto. Trustcor’s security audits are performed by the “Princeton Audit Group” whose address is a private residence in Princeton, NJ.
A company spokesperson named Rachel McPherson publicly responded to Menn’s article and Reardon and Egelman’s report with a bizarre, rambling message:
https://groups.google.com/a/mozilla.org/g/dev-security-policy/c/oxX69KFvsm4/m/X_6OFLGfBQAJ
In it, McPherson insinuates that Reardon and Egelman are just trying to drum up business for a small security research business they run called Appsecure. She says that Msgsafe’s defects aren’t germane to Trustcor’s Certificate Authority business, instead exhorting the researchers to make “positive suggestions for improving that product suite.”
As to the company’s registration, she makes a difficult-to-follow claim that the irregularities are due to using the same Panamanian law-firm as Packet Forensics, says that she needs to investigate some missing paperwork, and makes vague claims about “insurance impersonation” and “potential for foul play.”
Certificate Authorities have one job: to be very, very, very careful. The parts of Menn’s story and Reardon and Egelman’s report that aren’t disputed are, to my mind, enough to disqualify them from inclusion in browsers’ root of trust.
But the disputed parts — which I personally believe, based on my trust in Menn, which comes from his decades of careful and excellent reporting — are even worse.
For example, Menn makes an excellent case that Packet Forensics is not credible. In 2007, a company called Vostrom Holdings applied for permission for Packet Forensics to do business in Virginia as “Measurement Systems.” Measurement Systems, in turn, tricked app vendors into bundling spyware into their apps, which gathered location data that Measurement Systems sold to private and government customers. Measurement Systems’ data included the identities of 10,000,000 users of Muslim prayer apps.
Packet Forensics denies that it owns Measurement Systems, which doesn’t explain why Vostrom Holdings asked the state of Virginia to let it do business as Measurement Systems. Vostrom also owns the domain “Trustcor.co,” which directed to Trustcor’s main site. Trustcor’s “president, agents and holding-company partners” are identical to those of Measurement Systems.
One of the holding companies listed in both Trustcor and Measurement Systems’ ownership structures is Frigate Bay Holdings. This March, Raymond Saulino — the one-time Packet Forensics spokesman — filed papers in Wyoming identifying himself as manager of Frigate Bay Holdings.
Neither Menn nor Reardon and Egelman claim that Packet Forensics has obtained fake certificates from Trustcor to help its customers spy on their targets, something that McPherson stresses in her reply. However, Menn’s source claims that this is happening.
These companies are so opaque and obscure that it might be impossible to ever find out what’s really going on, and that’s the point. For the web to have privacy, the Certificate Authorities that hold the (literal) keys to that privacy must be totally transparent. We can’t assume that they are perfectly spherical cows of uniform density.
In a reply to Reardon and Egelman’s report, Mozilla’s Kathleen Wilson asked a series of excellent, probing followup questions for Trustcor, with the promise that if Trustcor failed to respond quickly and satisfactorily, it would be purged from Firefox’s root of trust:
https://groups.google.com/a/mozilla.org/g/dev-security-policy/c/oxX69KFvsm4/m/WJXUELicBQAJ
Which is exactly what you’d hope a browser vendor would do when one of its default Certificate Authorities was credibly called into question. But that still leaves an important question: how did Trustcor, who marketed a defective security product, whose corporate ownership is irregular and opaque with a seeming connection to a cyber-arms-dealer, end up in our browsers’ root of trust to begin with?
Formally, the process for inclusion in the root of trust is quite good. It’s a two-year vetting process that includes an external audit:
https://wiki.mozilla.org/CA/Application_Process
But Daniel Schwalbe, CISO of Domain Tools, told Menn that this process was not closely watched, claiming “With enough money, you or I could become a trusted root certificate authority.” Menn’s unnamed Packet Forensics source claimed that most of the vetting process was self-certified — that is, would-be CAs merely had to promise they were doing the right thing.
Remember, Trustcor isn’t just in Firefox’s root of trust — it’s in the roots of trust for Chrome (Google) and Safari (Apple). All the major browser vendors were supposed to investigate this company and none of them disqualified it, despite all the vivid red flags.
Worse, Reardon and Egelman say they notified all three companies about the problems with Trustcor seven months ago, but didn’t hear back until they published their findings publicly on Tuesday.
There are 169 root certificate authorities in Firefox, and comparable numbers in the other major browsers. It’s inconceivable that you could personally investigate each of these and determine whether you want to trust it. We rely on the big browser vendors to do that work for us. We start with: “Assume the browser vendors are careful and diligent when it comes to trusting companies on our behalf.” We assume that these messy, irregular companies are perfectly spherical cows of uniform density on a frictionless surface.
The problem of trust is everywhere. Vaccine deniers say they don’t trust the pharma companies not to kill them for money, and don’t trust the FDA to hold them to account. Unless you have a PhD in virology, cell biology and epidemiology, you can’t verify the claims of vaccine safety. Even if you have those qualifications, you’re trusting that the study data in journals isn’t forged.
I trust vaccines — I’ve been jabbed five times now — but I don’t think it’s unreasonable to doubt either Big Pharma or its regulators. A decade ago, my chronic pain specialist told me I should take regular doses of powerful opioids, and pooh-poohed my safety and addiction concerns. He told me that pharma companies like Purdue and regulators like the FDA had re-evaluated the safety of opioids and now deemed them far safer.
I “did my own research” and concluded that this was wrong. I concluded that the FDA had been captured by a monopolistic and rapacious pharma sector that was complicit in waves of mass-death that produced billions in profits for the Sackler family and other opioid crime-bosses.
I was an “opioid denier.” I was right. The failure of the pharma companies to act in good faith, and the failure of the regulator to hold them to account is a disaster that has consequences beyond the mountain of overdose deaths. There’s a direct line from that failure to vaccine denial, and another to the subsequent cruel denial of pain meds to people who desperately need them.
Today, learning that the CA-vetting process I’d blithely assumed was careful and sober-sided is so slapdash that a company without a working phone or a valid physical address could be trusted by billions of browsers, I feel like I did when I decided not to fill my opioid prescription.
I feel like I’m on the precipice of a great, epistemological void. I can’t “do my own research” for everything. I have to delegate my trust. But when the companies and institutions I rely on to be prudent (not infallible, mind, just prudent) fail this way, it makes me want to delete all the certificates in my browser.
Which would, of course, make the web wildly insecure.
Unless it’s already that insecure.
Ugh.
Image:
Curt Smith (modified)
https://commons.wikimedia.org/wiki/File:Sand_castle,_Cannon_Beach.jpg
CC BY 2.0:
https://creativecommons.org/licenses/by/2.0/deed.en
[Image ID: An animated gif of a sand-castle that is melting into the rising tide; through the course of the animation, the castle gradually fills up with a Matrix-style 'code waterfall' effect.]
349 notes
·
View notes