#forensic engineering analysis software
Explore tagged Tumblr posts
Text
Integrating Advanced Software for Demolition, Forensic Engineering, and Structural Analysis
In the modern engineering landscape, advanced software solutions offer essential tools for various specialized tasks. Demolition software is crucial for planning safe and controlled structure dismantling, minimizing risks. Similarly, forensic engineering analysis software helps engineers investigate structural failures by simulating different scenarios, leading to insightful failure analysis. Structural analysis software plays a vital role in assessing load-bearing capacities and ensuring the stability of structures. Together, these technologies enhance project safety, efficiency, and precision.
Read the complete Blog here: https://extremeloading11.medium.com/integrating-advanced-software-for-demolition-forensic-engineering-and-structural-analysis-ff18148f039e
0 notes
Text
Why Should Construction Teams Invest in Structural Analysis Before Demolition?

Before starting any demolition work, construction teams face many risks. A building that looks weak from the outside could still have parts that are dangerous to remove without proper planning. This is why it is smart for teams to look closely at the structure before starting any work. Careful planning helps protect people, equipment, and nearby properties from harm.
One important part of this planning is a demolition analysis. This process gives teams a clear picture of how a building will react during demolition. It helps in finding weak points and areas that could cause trouble if not handled properly. With this knowledge, teams can plan safer and smoother operations.
Another tool that helps in such projects is protective design software. This software allows engineers to test and plan different demolition methods using computer models. It helps in finding the safest way to bring down a structure while keeping workers and surroundings safe. Using technology like this saves time and reduces costly mistakes.
Forensic engineering analysis also plays a role in the planning stage. This type of study helps in understanding why certain parts of a building failed or could fail. It gives insight into hidden dangers that might not be seen in regular inspections. With this information, teams can avoid unexpected problems during demolition.
Applied Science offers smart solutions for construction teams looking to carry out demolition work safely. Their services help teams avoid risks and complete projects with care. Contact Applied Science today to learn how they can support your next demolition project.
0 notes
Text
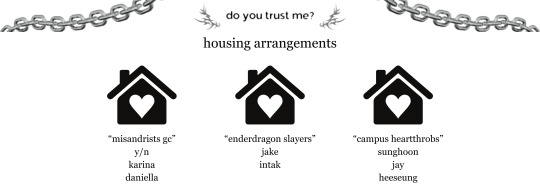
character profiles




artms choerry as reader "y/n" decelis university business analysis & marketing decelis dance team: sweet venom dance crew



enhypen sunghoon decelis university forensics decelis dance team: sweet venom dance crew y/n's ex-boyfriend of 2 years jay's twin



enhypen jake decelis university physics & probability "art hoes" y/n's childhood best friend




enhypen heeseung
decelis university music technology & composition decelis dance team: sweet venom dance crew "art hoes"
enhypen jay
decelis university chemistry sunghoon's twin "art hoes"
katseye daniella
decelis university fine arts in dance decelis dance team: sweet venom dance crew "art hoes"
piwon intak
decelis university software engineering decelis dance team: sweet venom dance crew y/n's little brother
aespa karina
decelis university literature decelis dance team: sweet venom dance crew "art hoes"
side characters: ive wonyoung red velvet irene nct taeyong

masterlist
copyright 2024 - present © hoonieyun all rights reserved
all writing here is fiction & not in any association with characters mentioned.
#kiki diaries#enhypen#do you trust me?#en-diaries#kpop#kpop au#kpop fic#kpop fanfic#kpop fanfiction#enha#fanfiction#enhypen au#enhypen x reader#enha x reader#sunghoon x reader#jake x reader#enhypen jake#enhypen sunghoon#park sunghoon#sim jaeyun#enhypen smau#enha smau
39 notes
·
View notes
Text
A Manhattan Federal Court judge on Friday extended the temporary restraining order that bars staffers from the so-called Department of Government Efficiency from accessing US Treasury Department data—which attorneys general from New York and other blue states have slammed as an unlawful threat to privacy—while she considers whether to impose a longer-term injunction.
After hearing some two hours of arguments, Judge Jeannette A. Vargas told lawyers for New York and allied states, and their opponents from the Department of Justice, “I do find good cause to extend the TRO as modified.” Vargas said she would soon issue her decision, but not today, to “give the court time to consider” the issues.
While the proceeding largely maintained the status quo, it also lifted the veil on just how little is known about DOGE’s access to information—and where it went.
When Vargas asked Jeffrey Oestericher, the Justice Department attorney representing Trump, on Friday whether any DOGE-accessed information had been shared outside of the Treasury Department, he said: “The short answer on that is we don’t presently know.”
“We’re performing a forensic analysis. What we can tell from the forensic analysis thus far is there were emails sent outside Treasury,” Oestericher said. “We do not know [the] content.”
Vargas asked: Wasn’t this problematic from a privacy standpoint?
“The short answer is no,” Oestericher said.
“During this time that the DOGE team members had access to this information, there were extensive mitigation efforts in place to prevent this precise harm.”
But Oestericher admitted at another point, “We candidly admit that there was some measure of increased risk, but we took all appropriate mitigation measures to mitigate that risk as much as possible.”
Vargas’ decision came six days after New York and allied litigants were granted a temporary restraining order that ultimately prohibited the Treasury Department from giving DOGE hires and special government employees access to sensitive data and computer systems. Donald Trump tapped Elon Musk to head DOGE, an agency the president created under the auspices of rooting out fraud and governmental waste—despite a dearth of evidence indicating fraud.
In issuing that temporary restraining order early February 8, Judge Paul A. Engelmayer said that the states suing Trump and Treasury Secretary Scott Bessent would “face irreparable harm in the absence of injunctive relief.”
Engelmayer noted that Treasury’s new policy, enacted at Trump’s direction, appears to allegedly “[expand] access to the paytment systems of the Bureau of Fiscal Services (BFS) to political appointees and ‘special government employees.’”
This, Engelmayer reasoned, represented a “risk that the new policy presents of the disclosure of sensitive and confidential information and the heightened risk that the systems in question will be more vulnerable than before to hacking.”
Engelmayer also said in his written decision that the states suing over Treasury’s policy change “have shown a likelihood of success on the merits of their claims, with the States’ statutory claims presenting as particularly strong.”
The complaint against Trump and Bessent repeatedly cited WIRED’s reporting that revealed how a 25-year-old engineer named Marko Elez, with ties to Musk, enjoyed read and write access to two Treasury Department systems responsible for virtually all payments made by the federal government. Tom Krause—who is on the DOGE team despite being CEO of Cloud Software Group—was also granted access to these capabilities.
Two sources told WIRED that Elez’s privileges allowed him not just to read but also write code for two of the most sensitive US government computer systems. These include the Payment Automation Manager and Secure Payment System at the Bureau of the Fiscal Service (BFS). These systems, which are kept on a secure mainframe, control government payments that total more than 20 percent of the US economy, WIRED previously reported.
In court papers filed February 13, New York and allies allege that Trump and his Treasury Department don’t even contest that states have a “clear and reasonable interest in protecting their confidential bank account numbers and other sensitive financial information, including details and amounts of payments, from unauthorized disclosure.” But this information was disclosed to two DOGE members, they claim, violating “numerous laws and regulations.”
New York and other states argued in that same filing that BFS’s development of “mitigation strategies” to reduce risk was testament to the “substantial and imminent” danger. They say that at least on one occasion, Elez was “mistakenly provided with ‘read/write permissions instead of read-only.’”
“But even with the more restricted ‘read-only’ access, Elez still had ‘the ability to view and query information and data’; in other words, he had access to the States’ sensitive financial information.” Despite the fact that Elez resigned when asked for comment by The Wall Street Journal about racist social media posts, the government didn’t provide any reassurance that he didn’t participate in improper activity, New York and its allies alleged. (Meanwhile, Musk suggested in a post on X, his social media platform, that Elez would be rehired, writing: “He will be brought back. To err is human, to forgive divine.”)
Andrew Amer, an attorney in New York state attorney general Letitia James’ office, said Friday that Elez and Krause “have no lawful job duty to access this information.”
Despite the government’s insistence that Elez was in a “sandbox environment” when he had access to the code, which they insist minimized risk, Amer said that wasn’t all that comforting.
“We know that the same engineer took screenshots of the data in the data system and that he may have given those screenshots to his supervisor,” Amer said.
Amer said the Justice Department’s insistence that Krause only had “over-the-shoulder access” didn’t inspire much confidence either.
“The fact that we don’t know if any information went beyond Treasury is a red flag that causes concern about the ethics issue,” Amer said. “This is especially important, as we do have people, especially Mr. Krause, who is simultaneously employed elsewhere outside Treasury.”
“You have somebody who’s been given access to source code within the bureau whose other job is CEO of one of the world’s largest software companies.”
“We are here because the states’ banking information has been accessed— that has happened,” Amer said at another point in court. “We know that the people who accessed it have been somewhat careless in the way they handled it.”
Amer also rejected any notion that DOGE acolytes’ access was normal. “This was not a Treasury function, this was building a new automated process to apply an ideological litmus test to funding requests. There’s nothing typical or normal in terms of Treasure functions about that.”
Trump’s camp has contended that his opponents are trying to thwart the White House’s right “to exercise politically accountable oversight of agency activities and to implement the president’s policy priorities.”
Treasury Department officials are responsible for liaising with the United States DOGE Service, which needs to have access to BFS systems, they argue, “to perform their Presidentially-directed mandate of maximizing efficiency and productivity, including ensuring data and payment integrity with respect to the 1.2 billion transactions and over $5 trillion in outlays handled by BFS,” they said in court papers.
Red states including Florida, Georgia, and Alabama have also entered the fray to show support for Trump. They contend in court papers that blue states’ opposition to DOGE meddling is unconstitutional. “This case involves an unprecedented assault on the separation of powers and the President’s authority under Article II of the Constitution,” they wrote. “Ultimately, Plaintiffs here are upset because one set of bureaucrats in the Executive Branch have access to data that they believe only other bureaucrats in the Executive Branch should have access to.”
“This type of fiddling around with the President’s prerogatives asks this Court to insert itself into core Executive decision-making regarding policy and personnel. The President is working to combat what former President Biden’s administration identified, at minimum, as hundreds of billions of dollars in fraud,” they wrote.
11 notes
·
View notes
Text

Tools of the Trade for Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Cybersecurity professionals use a lot of different tools to get the job done. There are plenty of fancy and expensive tools that enterprise security teams use, but luckily there are also lots of brilliant people writing free and open-source software. In this post, I'm going to list some popular free tools that you can download right now to practice and learn with.
In my opinion, one of the most important tools you can learn how to use is a virtual machine. If you're not already familiar with Linux, this is a great way to learn. VMs are helpful for separating all your security tools from your everyday OS, isolating potentially malicious files, and just generally experimenting. You'll need to use something like VirtualBox or VMWare Workstation (Workstation Pro is now free for personal use, but they make you jump through hoops to download it).
Below is a list of some popular cybersecurity-focused Linux distributions that come with lots of tools pre-installed:
Kali is a popular distro that comes loaded with tools for penetration testing
REMnux is a distro built for malware analysis
honorable mention for FLARE-VM, which is not a VM on its own, but a set of scripts for setting up a malware analysis workstation & installing tools on a Windows VM.
SANS maintains several different distros that are used in their courses. You'll need to create an account to download them, but they're all free:
Slingshot is built for penetration testing
SIFT Workstation is a distro that comes with lots of tools for digital forensics
These distros can be kind of overwhelming if you don't know how to use most of the pre-installed software yet, so just starting with a regular Linux distribution and installing tools as you want to learn them is another good choice for learning.
Free Software
Wireshark: sniff packets and explore network protocols
Ghidra and the free version of IDA Pro are the top picks for reverse engineering
for digital forensics, check out Eric Zimmerman's tools - there are many different ones for exploring & analyzing different forensic artifacts
pwntools is a super useful Python library for solving binary exploitation CTF challenges
CyberChef is a tool that makes it easy to manipulate data - encryption & decryption, encoding & decoding, formatting, conversions… CyberChef gives you a lot to work with (and there's a web version - no installation required!).
Burp Suite is a handy tool for web security testing that has a free community edition
Metasploit is a popular penetration testing framework, check out Metasploitable if you want a target to practice with
SANS also has a list of free tools that's worth checking out.
Programming Languages
Knowing how to write code isn't a hard requirement for learning cybersecurity, but it's incredibly useful. Any programming language will do, especially since learning one will make it easy to pick up others, but these are some common ones that security folks use:
Python is quick to write, easy to learn, and since it's so popular, there are lots of helpful libraries out there.
PowerShell is useful for automating things in the Windows world. It's built on .NET, so you can practically dip into writing C# if you need a bit more power.
Go is a relatively new language, but it's popular and there are some security tools written in it.
Rust is another new-ish language that's designed for memory safety and it has a wonderful community. There's a bit of a steep learning curve, but learning Rust makes you understand how memory bugs work and I think that's neat.
If you want to get into reverse engineering or malware analysis, you'll want to have a good grasp of C and C++.
Other Tools for Cybersecurity
There are lots of things you'll need that aren't specific to cybersecurity, like:
a good system for taking notes, whether that's pen & paper or software-based. I recommend using something that lets you work in plain text or close to it.
general command line familiarity + basic knowledge of CLI text editors (nano is great, but what if you have to work with a system that only has vi?)
familiarity with git and docker will be helpful
There are countless scripts and programs out there, but the most important thing is understanding what your tools do and how they work. There is no magic "hack this system" or "solve this forensics case" button. Tools are great for speeding up the process, but you have to know what the process is. Definitely take some time to learn how to use them, but don't base your entire understanding of security on code that someone else wrote. That's how you end up as a "script kiddie", and your skills and knowledge will be limited.
Feel free to send me an ask if you have questions about any specific tool or something you found that I haven't listed. I have approximate knowledge of many things, and if I don't have an answer I can at least help point you in the right direction.
#studyblrmasterpostjam#studyblr#masterpost#cybersecurity#late post bc I was busy yesterday oops lol#also this post is nearly a thousand words#apparently I am incapable of being succinct lmao
22 notes
·
View notes
Text
Securing the Digital World: B Tech in Cyber Security

In a world where data breaches and cyber threats make headlines every other day, cyber security has emerged as one of the most in-demand fields in technology. Whether it's safeguarding sensitive government data, protecting corporate networks, or securing online financial transactions, cyber security experts are the unsung heroes behind digital safety. A Bachelor of Technology (B Tech) in Cyber Security is the perfect launchpad for students interested in building a career in this dynamic and vital sector.
Why Choose B Tech in Cyber Security?
Cyber security is no longer just an IT concern—it’s a critical business issue. With increasing reliance on digital infrastructure, the need for skilled cyber security professionals has skyrocketed. A B Tech in Cyber Security equips students with the knowledge of ethical hacking, digital forensics, network security, cryptography, risk management, and malware analysis. It is a blend of theoretical concepts and hands-on training, making students ready for real-world challenges.
youtube
B Tech Cyber Security Admission: The Entry Gate to a Secure Future
Getting admission into a B Tech Cyber Security program is the first step toward becoming a cyber-warrior. Admission usually takes place through engineering entrance examinations such as:
1. JEE Main
2. State-level entrance exams (like MHT CET, WBJEE)
3. University-level exams (like VITEEE, SRMJEEE, etc.)
4. Direct admission through merit-based selection in some private institutions
Prospective students should keep a close watch on application deadlines, counselling dates, and entrance exam schedules. Some reputed universities also offer early application options for high-scoring students.
B Tech Cyber Security Eligibility: Are You the Right Fit?
The B Tech Cyber Security Eligibility criteria are similar across most Indian universities and colleges, though there can be slight variations. The general requirements include:
1. Completion of 10+2 (or equivalent) with Physics, Chemistry, and Mathematics as core subjects
2. A minimum of 50-60% marks in aggregate, depending on the institution
3. A valid score in the required entrance examination
Some institutions may also look for additional aptitude in logical reasoning or programming basics. If you have a passion for solving complex problems, an analytical mindset, and a curiosity for how things work behind the screen, cyber security is definitely your calling.
B Tech Cyber Security Fees: Planning Your Investment
One of the crucial considerations for students and parents is the financial aspect of the program. B Tech Cyber Security Fees vary depending on the institution type:
Government institutions (IITs, NITs, state universities): ₹50,000 – ₹2,00,000 per year
Private universities and deemed institutions: ₹1,00,000 – ₹3,50,000 per year
Some colleges offer scholarships, financial aid, and installment-based fee payment options. Apart from tuition, students should also account for costs related to hostel, lab equipment, certifications, and internships. However, considering the booming demand for cyber security professionals, the investment often pays off quickly in the form of high-salary placements.
B Tech Cyber Security Placement: Step Into the Digital Frontlines
One of the biggest attractions of this course is its strong placement record. The increasing frequency of cyberattacks has pushed companies to hire dedicated security teams. As a result, B Tech Cyber Security graduates are in high demand across industries such as:
1. IT and Software Services
2. Banking, Financial Services, and Insurance (BFSI)
3. Government Agencies and Defense
4. E-Commerce
5. Telecommunication
Top recruiters include Infosys, TCS, Wipro, IBM, Deloitte, Accenture, Cisco, EY, and many more. Some graduates also opt for prestigious government roles in cybersecurity departments, CERT-In, DRDO, or the cyber wing of law enforcement agencies.
Average starting packages for freshers range from ₹4 to ₹10 LPA, and with experience, professionals can easily cross ₹20 LPA and move into high-profile roles like Security Analyst, Penetration Tester, Cyber Security Consultant, or Chief Information Security Officer (CISO). Whether you are just out of school or looking to specialize in a growing field, the B Tech Cyber Security Admission process opens the door to a thrilling and rewarding career. So, are you ready to turn your interest in technology into a force for good? Cyber security isn’t just a career—it's a mission.
0 notes
Text
B.Tech in Cyber Security vs Computer Science: Which Should You Choose?
For students passionate about technology, the decision to pursue engineering after 12th grade often leads to a new question, should you choose a B. Tech in Computer Science or a more focused course like B.Tech in Cyber Security and Digital Forensics?
Both fields are part of the tech ecosystem, but they differ in terms of curriculum, career paths, and skill development. Understanding these differences can help you make a more informed choice that matches your interests and future goals.
What is a B.Tech in Computer Science?
A B.Tech in Computer Science (CSE) is a four-year undergraduate program that covers the fundamentals of computing. The course includes:
Programming languages (C++, Java, Python)
Data structures and algorithms
Software development
Operating systems and databases
Artificial intelligence and machine learning
Web and mobile application development
This degree prepares you for a wide variety of careers in software development, data science, IT services, and tech startups. It offers flexibility and a broad skill set, ideal for those who want to explore different areas of technology.
What is B.Tech in Cyber Security and Digital Forensics?
A B.Tech in Cyber Security and Digital Forensics is a specialised course designed to prepare students for roles in information security, digital investigations, and cyber law enforcement. It includes subjects like:
Network security
Ethical hacking
Cryptography
Digital forensics and incident response
Malware analysis
Cyber law and regulations
This program is ideal for students who want to focus on defending systems from cyber threats, analysing digital crimes, and ensuring data protection in today’s digital world.
Curriculum comparison
While Computer Science offers a broader overview of computing, B Tech in Cyber Security and Forensics dives deeper into security protocols, data privacy, and investigation techniques.
Computer Science may be a better fit if you enjoy writing code, building software, or exploring AI and machine learning. But if you are interested in understanding how hackers operate, protecting systems, or tracing digital footprints, cyber security could be your calling.
Career paths and job roles
After B.Tech in Computer Science, common roles include:
Software Developer
Data Scientist
Web Developer
Mobile App Developer
System Analyst
Cloud Engineer
After B Tech in Cyber Security and Forensics, you can explore roles such as:
Cyber Security Analyst
Ethical Hacker
Digital Forensics Expert
Security Operations Center (SOC) Analyst
Information Security Manager
Incident Response Specialist
The demand for cyber security professionals is growing fast across industries such as banking, healthcare, telecom, and government, making it a lucrative and future-ready field.
Skills you’ll develop
Cyber security students gain expertise in:
Penetration testing
Risk assessment
Cyber threat intelligence
Legal frameworks and digital ethics
Secure software development
On the other hand, computer science students focus more on:
Full-stack development
Algorithm design
Software project management
Application performance optimization
Choosing the right college matters
Whether you choose a general or specialised stream, studying at one of the top B Tech in Cyber Security colleges in India ensures you receive quality education, hands-on training, and placement support. Look for:
A curriculum designed with industry input
Labs equipped for network and cyber forensics
Internships and certification support
Mentorship from experienced faculty
Opportunities for research and innovation
Why DY Patil University is a great option
DY Patil University, Navi Mumbai, offers a comprehensive B Tech in Cyber Security and Forensics program designed to meet the evolving demands of the industry.
Key highlights include:
Expert faculty and real-time lab infrastructure
Industry projects and certification support
Partnerships with cybersecurity firms
Internship and placement assistance
Workshops, seminars, and guest lectures from security professionals
DY Patil University equips students not just with academic knowledge but also with the confidence and experience to succeed in high-stakes tech careers.
Final thoughts
Both computer science and cyber security offer promising futures. If you’re looking for a versatile tech degree with wide applications, Computer Science may be your path. But if you are drawn to digital protection, ethical hacking, or forensic investigations, B Tech in Cyber Security and Forensics offers a specialised and exciting route.
DY Patil University, Navi Mumbai, is among the leading tech in cyber security colleges in India, providing a strong foundation for students ready to defend the digital world.
1 note
·
View note
Text
Hydraulic Punching Machine Market [2025] Size, Share and Trends upto 2033
Global “Hydraulic Punching Machine Market” research report is a comprehensive analysis of the current status of the Hydraulic Punching Machine industry worldwide. The report categorizes the global Hydraulic Punching Machine market by top players/brands, region, type, and end-user. It also examines the competition landscape, market share, growth rate, future trends, market drivers, opportunities, and challenges in the global Hydraulic Punching Machine market. The report provides a professional and in-depth study of the industry to help understand its current state and future prospects. What Are The Prominent Key Player Of the Hydraulic Punching Machine Market?
Wanzke
Baileigh Industrial
Baruffaldi Plastic
Baykal Makina
Bihler
Boschert
Cantec
Durma
Ferracci Machines
Friul Filiere
Kingsland Engineering
Production by Region
North America
Europe
China
Japan
The Primary Objectives in This Report Are:
To determine the size of the total market opportunity of global and key countries
To assess the growth potential for Hydraulic Punching Machine
To forecast future growth in each product and end-use market
To assess competitive factors affecting the marketplace
This report also provides key insights about market drivers, restraints, opportunities, new product launches or approvals.
Regional Segment of Hydraulic Punching Machine Market:
Geographically, the report includes research on production, consumption, revenue, market share, and growth rate of the following regions:
United States
Europe (Germany, UK, France, Italy, Spain, Russia, Poland)
China
Japan
India
Southeast Asia (Malaysia, Singapore, Philippines, Indonesia, Thailand, Vietnam)
Latin America (Brazil, Mexico, Colombia)
Middle East and Africa (Saudi Arabia, United Arab Emirates, Turkey, Egypt, South Africa, Nigeria)
The global Hydraulic Punching Machine Market report answers the following questions:
What are the main drivers of the global Hydraulic Punching Machine market? How big will the Hydraulic Punching Machine market and growth rate in upcoming years?
What are the major market trends that affecting the growth of the global Hydraulic Punching Machine market?
Key trend factors affect market share in the world's top regions?
Who are the most important market participants and what strategies being they pursuing in the global Hydraulic Punching Machine market?
What are the market opportunities and threats to which players are exposed in the global Hydraulic Punching Machine market?
Which industry trends, drivers and challenges are driving that growth?
Browse More Details On This Report at - https://www.businessresearchinsights.com/market-reports/hydraulic-punching-machine-market-104449
Contact Us:
Business Research Insights
Phone:
US: (+1) 424 253 0807
UK: (+44) 203 239 8187
Email: [email protected]
Web: https://www.businessresearchinsights.com
Other Reports Here:
Polyester Silo Market
Ticketing Kiosks Market
Screw Expander Market
Forensic Engineering Services Market
Roof Sheathing Market
Ratchet Market
Carrier Wi-Fi Equipment Market
Compressed Natural Gas and Liquefied Natural Gas Vehicle Market
Motorcycle Carbon Ceramic Brake Rotors Market
Coconut Milk Powder Market
Other Reports Here:
Golf and Sport Mats Market
Tactile Actuator Market
Employee Intranet Software Market
Edible Hydrogenated Oils Market
Water Supply Instrument Market
Tris (hydroxymethyl) Aminomethane Market
Odor Control Textiles Market
IC Advanced Packaging Equipment Market
Robotic Palletizers and De-Palletizers Market
Rhythm Machines Market
0 notes
Text
How Does a Motorcycle Collision Lawyer Reconstruct Accident Scenes?
When a motorcycle accident happens, understanding exactly what occurred is crucial for building a strong legal case. Motorcycle collision lawyers use accident reconstruction to piece together the events leading up to the crash. This process helps determine fault, liability, and the true cause of the accident. Let's explore how experienced attorneys use various techniques and evidence to reconstruct motorcycle accident scenes.
What Is Accident Reconstruction?
Accident reconstruction is a scientific process that analyzes physical evidence, witness statements, and crash data to determine how an accident occurred. For motorcycle accidents, this process is especially important because motorcyclists are often seriously injured and may not remember the details clearly. A skilled motorcycle attorney works with accident reconstruction experts to examine skid marks, vehicle damage, road conditions, and other evidence at the crash site.
The reconstruction process helps establish the sequence of events, vehicle speeds, impact points, and driver behavior before the collision. This information becomes vital evidence in personal injury claims and insurance negotiations. Traffic engineers and forensic experts often assist lawyers in creating detailed reports that explain the accident mechanics.
Gathering Physical Evidence from the Scene
The first step in accident reconstruction involves collecting physical evidence from the accident personal injury attorney scene. Motorcycle collision lawyers work quickly Look at more info to preserve this evidence before it disappears or gets cleaned up. Key pieces of physical evidence include skid marks on the roadway, debris from both vehicles, and damage patterns on the motorcycle and other vehicles involved.
Photographs of the accident scene are extremely important. Lawyers document the position of vehicles, road surface conditions, traffic signals, and any environmental factors that may have contributed to the crash. They also measure distances between impact points, final resting positions, and any obstacles that might have affected visibility or vehicle movement.
Paint transfers, broken glass, and metal fragments help experts understand the collision dynamics. The motorcycle's final position and the pattern of damage can reveal important details about the impact angle and force involved in the accident.
Using Technology and Expert Analysis
Modern accident reconstruction relies heavily on advanced technology. Motorcycle lawyers often employ computer simulation software that can recreate the accident based on the collected evidence. These programs calculate vehicle speeds, braking distances, and impact forces with remarkable accuracy.
Accident reconstruction experts use specialized equipment to measure and analyze the crash site. Laser scanners create detailed 3D models of the accident scene, preserving exact measurements and spatial relationships. GPS technology helps map the precise location of evidence and vehicle positions.
Biomechanical engineers may also be consulted to analyze injury patterns and determine how they relate to the collision forces. This analysis helps establish the severity of impact and can support claims for medical expenses and pain and suffering.
Analyzing Vehicle Damage and Mechanics
The damage to the motorcycle and other vehicles tells a detailed story about the accident. Collision lawyers work with mechanical engineers to exam
0 notes
Text
How to prevent a DDoS attack
"Securing Your Cloud Infrastructure: Proven DDoS Prevention Methods"
Introduction
Distributed Denial of Service (DDoS) attacks represent one of the most persistent and evolving threats in cybersecurity. At CloudMinister Technologies, we implement a robust, multi-faceted defense strategy to protect our clients' digital assets. This guide provides an exhaustive examination of our DDoS prevention methodology, detailing the technical implementation and strategic rationale behind each protective measure.
1. Cloud-Based DDoS Protection Services: Technical Implementation
Architecture and Operation
Our cloud-based DDoS protection operates through a distributed network of scrubbing centers that process all incoming traffic before it reaches client infrastructure. The system employs:
Deep Packet Inspection (DPI): Analyzes packet headers and payloads to identify malicious patterns
Behavioral Analysis Engines: Establish baseline traffic profiles for each client environment
Real-time Signature Matching: Compares traffic against known attack signatures
Platform-Specific Implementations
AWS Shield Advanced:
Integrated with Amazon CloudFront, Route 53, and Elastic Load Balancing
Provides always-on detection of network layer (Layer 3/4) attacks
Custom mitigations for application layer (Layer 7) attacks
Azure DDoS Protection:
Leverages Azure's global network infrastructure
Implements adaptive real-time mitigation policies
Provides attack analytics through Azure Monitor
Third-Party Solutions (Cloudflare/Akamai):
Anycast network architecture disperses attack traffic
TLS termination at edge locations reduces origin server load
Custom rulesets for industry-specific protection
2. Web Application Firewall (WAF) Configuration Details
Rule Set Composition
Our WAF deployments utilize a layered ruleset approach:
Foundation Rules:
OWASP Core Rule Set (CRS) 3.3
Protocol compliance checks
HTTP request validation
Custom Rules:
Application-specific allowlists
Business logic protection
API endpoint security
Rate Limiting Policies:
Granular controls by:
IP address
Session tokens
Geographic location
Dynamic adjustments based on traffic patterns
Bot Mitigation Techniques
JavaScript challenge verification
TLS fingerprinting
Behavioral analysis of mouse movements and interaction patterns
Progressive hardening for persistent threats
3. Advanced Traffic Monitoring Systems
Data Collection Framework
NetFlow/sFlow/IPFIX: Sampled at 1:1 ratio during normal operations, increasing to 1:10 during attacks
Packet Capture: Triggered by anomaly detection for forensic analysis
Log Aggregation: Centralized collection from all network devices
Analytics Pipeline
Pre-processing:
Traffic normalization
Feature extraction
Machine Learning Models:
Isolation Forest for anomaly detection
LSTM networks for time-series prediction
Supervised classifiers for attack categorization
Decision Engine:
Confidence thresholding
Mitigation action selection
4. Scalable Infrastructure Design Principles
Auto-scaling Implementation
Horizontal Scaling:
Instance groups with pre-warmed pools
Predictive scaling based on historical patterns
Vertical Scaling:
Dynamic resource allocation
Hot standby instances
Load Balancing Strategies
Geographic Load Distribution:
DNS-based geolocation routing
Anycast IP implementation
Application-Aware Routing:
Content-based routing
Session persistence management
5. Zero Trust Architecture Components
Network Segmentation Model
Micro-perimeter Creation:
Software-defined perimeters
Per-workload firewalls
Traffic Flow Policies:
East-west traffic controls
Default-deny posture
Access Control Mechanisms
Identity Verification:
Multi-factor authentication
Device attestation
Policy Enforcement:
Attribute-based access control
Just-in-time privilege elevation
6. Incident Response Protocol
Attack Mitigation Workflow
Detection Phase:
Threshold crossing alerts
Correlation engine output
Containment Phase:
BGP flow-spec announcements
On-premise scrubbing activation
Recovery Phase:
Traffic normalization monitoring
Post-mortem analysis
Forensic Investigation Process
Attack timeline reconstruction
Malicious payload analysis
Attacker attribution techniques
Countermeasure effectiveness evaluation
Conclusion
CloudMinister Technologies' DDoS protection framework combines cutting-edge technologies with proven security practices to deliver comprehensive protection. Our defense-in-depth approach addresses all layers of potential attack vectors while maintaining operational flexibility and performance.
We offer customized security assessments and implementation services for organizations seeking enterprise-grade DDoS protection. Contact our security team to discuss your specific requirements.
Take the Next Step
Contact CloudMinister today for a free cloud security assessment or to learn more about our advanced DDoS protection solutions.
Visit www.cloudminister.com or speak to one of our security specialists
0 notes
Text
The Role of Demolition, Forensic, and Structural Analysis Software
The role of demolition, forensic, and structure analysis software cannot be overstated in modern engineering and construction. These tools enhance safety, streamline processes, and provide invaluable insights that contribute to the success and longevity of projects. To get complete information read the full blog or you can visit the website - https://www.evernote.com/shard/s453/sh/21660a79-6cd8-a122-e9fd-edaf6e9e5fde/r2F8Kr6Sttydk16DhVb93oJ7_LRDQ4VXPqx2fnu0CgwP3LacL5JsYFkLdQ
#structural analysis software#structure analysis software#structural engineering software programs#demolition software#forensic engineering analysis software
0 notes
Text
Revolutionizing Engineering: Applied Science International's Groundbreaking Innovations
Dive into the cutting-edge advancements of Applied Science International (ASI) in the field of engineering. This article explores their revolutionary solutions, including their commitment to redefining traditional engineering practices through technology and applied science. From advanced structural analysis to innovative demolition planning, ASI's tools and methodologies are transforming the way we approach engineering challenges.
Discover how their proprietary Extreme Loading® Technology (ELT) is making waves in structural modeling, risk assessment, and disaster mitigation. The blog highlights real-world applications, showcasing how ASI's innovative tools have enhanced efficiency, accuracy, and safety in the industry. Whether you're an engineer, project manager, or tech enthusiast, this piece offers valuable insights into how applied science is shaping the future of engineering.
Read the full article to learn more about ASI's groundbreaking contributions to engineering at - https://appliedint.science.blog/2025/01/14/the-future-of-forensic-engineering-structural-design-software-at-the-forefront/
#Forensic structural engineering#demolition planning#structural analysis engineering#cold formed steel software
0 notes
Text
Some Fortune 500 companies have begun testing software that can spot a deepfake of a real person in a live video call, following a spate of scams involving fraudulent job seekers who take a signing bonus and run.
The detection technology comes courtesy of GetReal Labs, a new company founded by Hany Farid, a UC-Berkeley professor and renowned authority on deepfakes and image and video manipulation.
GetReal Labs has developed a suite of tools for spotting images, audio, and video that are generated or manipulated either with artificial intelligence or manual methods. The company’s software can analyze the face in a video call and spot clues that may indicate it has been artificially generated and swapped onto the body of a real person.
“These aren’t hypothetical attacks, we’ve been hearing about it more and more,” Farid says. “In some cases, it seems they're trying to get intellectual property, infiltrating the company. In other cases, it seems purely financial, they just take the signing bonus.”
The FBI issued a warning in 2022 about deepfake job hunters who assume a real person’s identity during video calls. UK-based design and engineering firm Arup lost $25 million to a deepfake scammer posing as the company’s CFO. Romance scammers have also adopted the technology, swindling unsuspecting victims out of their savings.
Impersonating a real person on a live video feed is just one example of the kind of reality-melting trickery now possible thanks to AI. Large language models can convincingly mimic a real person in online chat, while short videos can be generated by tools like OpenAI’s Sora. Impressive AI advances in recent years have made deepfakery more convincing and more accessible. Free software makes it easy to hone deepfakery skills, and easily accessible AI tools can turn text prompts into realistic-looking photographs and videos.
But impersonating a person in a live video is a relatively new frontier. Creating this type of a deepfake typically involves using a mix of machine learning and face-tracking algorithms to seamlessly stitch a fake face onto a real one, allowing an interloper to control what an illicit likeness appears to say and do on screen.
Farid gave WIRED a demo of GetReal Labs’ technology. When shown a photograph of a corporate boardroom, the software analyzes the metadata associated with the image for signs that it has been modified. Several major AI companies including OpenAI, Google, and Meta now add digital signatures to AI-generated images, providing a solid way to confirm their inauthenticity. However, not all tools provide such stamps, and open source image generators can be configured not to. Metadata can also be easily manipulated.
GetReal Labs also uses several AI models, trained to distinguish between real and fake images and video, to flag likely forgeries. Other tools, a mix of AI and traditional forensics, help a user scrutinize an image for visual and physical discrepancies, for example highlighting shadows that point in different directions despite having the same light source, or that do not appear to match the object that cast them.
Lines drawn on different objects shown in perspective will also reveal if they converge on a common vanishing point, as would be the case in a real image.
Other startups that promise to flag deepfakes rely heavily on AI, but Farid says manual forensic analysis will also be crucial to flagging media manipulation. “Anybody who tells you that the solution to this problem is to just train an AI model is either a fool or a liar,” he says.
The need for a reality check extends beyond Fortune 500 firms. Deepfakes and manipulated media are already a major problem in the world of politics, an area Farid hopes his company’s technology could do real good. The WIRED Elections Project is tracking deepfakes used to boost or trash political candidates in elections in India, Indonesia, South Africa, and elsewhere. In the United States, a fake Joe Biden robocall was deployed last January in an effort to dissuade people from turning out to vote in the New Hampshire Presidential primary. Election-related “cheapfake” videos, edited in misleading ways, have gone viral of late, while a Russian disinformation unit has promoted an AI-manipulated clip disparaging Joe Biden.
Vincent Conitzer, a computer scientist at Carnegie Mellon University in Pittsburgh and coauthor of the book Moral AI, expects AI fakery to become more pervasive and more pernicious. That means, he says, there will be growing demand for tools designed to counter them.
“It is an arms race,” Conitzer says. “Even if you have something that right now is very effective at catching deepfakes, there's no guarantee that it will be effective at catching the next generation. A successful detector might even be used to train the next generation of deepfakes to evade that detector.”
GetReal Labs agrees it will be a constant battle to keep up with deepfakery. Ted Schlein, a cofounder of GetReal Labs and a veteran of the computer security industry, says it may not be long before everyone is confronted with some form of deepfake deception, as cybercrooks become more conversant with the technology and dream up ingenious new scams. He adds that manipulated media is a top topic of concern for many chief security officers. “Disinformation is the new malware,” Schlein says.
With significant potential to poison political discourse, Farid notes that media manipulation can be considered a more challenging problem. “I can reset my computer or buy a new one,” he says. “But the poisoning of the human mind is an existential threat to our democracy.”
13 notes
·
View notes
Text
Top 10 In-Demand Courses for BTech CSE Graduates in 2025
In Arya College of Engineering & I.T. guide students for choosing the right course after a BTech in Computer Science Engineering (CSE) can significantly boost your career prospects. The technology sector is rapidly evolving, and specialized skills are in high demand. Here are ten of the best courses you can pursue after BTech CSE, along with the job opportunities they offer in 2025:
1. Master of Technology (MTech) in Computer Science
Deepens your technical expertise in core computer science areas.
Opens doors to roles such as Software Developer, Systems Architect, and Research Engineer in top tech companies and research organizations.
2. Master of Science (MS/MSc) in Computer Science or Engineering
Offers advanced learning and research in areas like AI, data science, cybersecurity, and software engineering.
Graduates can pursue roles such as Data Scientist, Machine Learning Engineer, and Cloud Solutions Architect.
3. MBA in Information Technology
Combines management skills with IT knowledge, preparing you for leadership roles.
Leads to positions like IT Manager, Product Manager, and Technology Consultant in IT firms and startups.
4. Masters in Data Science or Big Data Analytics
Focuses on data analysis, machine learning, and business intelligence.
High demand for Data Scientists, Data Analysts, and Business Intelligence Analysts across industries.
5. Masters in Artificial Intelligence and Machine Learning
Specialized training in AI algorithms, robotics, and deep learning.
Opens up careers as an AI Engineer, Research Scientist, and NLP Engineer in tech giants and research labs.
6. Masters in Cybersecurity
Covers network security, ethical hacking, and digital forensics.
Growing need for Cybersecurity Analysts, Security Engineers, and Information Security Managers in both private and government sectors.
7. Masters in Software Engineering
Advanced study in software development, testing, and project management.
Prepares you for roles like Senior Software Engineer, DevOps Engineer, and Software Project Manager.
8. Masters in Cloud Computing
In-depth knowledge of cloud platforms, virtualization, and distributed systems.
Cloud Solutions Architect, Cloud Engineer, and Cloud Security Specialist are highly sought-after roles.
9. Masters in Computer Networking or Network Engineering
Focuses on network design, management, and security.
Network Engineer, Network Architect, and Systems Administrator roles are available in IT infrastructure companies.
10. Certification Courses (Short-term/Online)
Specialized certifications in fields like Blockchain, Internet of Things (IoT), Full Stack Development, or DevOps.
These certifications can quickly upskill you for niche roles such as Blockchain Developer, IoT Solutions Architect, or DevOps Engineer.
Job Opportunities and Industry Demand
Data Science, AI, and Cybersecurity are among the fastest-growing fields, with high salaries and global demand.
Cloud Computing and Software Engineering continue to be core areas for IT companies, offering stability and growth.
Management roles (with an MBA) are ideal for those interested in leadership and strategic decision-making.
Certification courses provide flexibility and can be pursued alongside jobs to specialize in emerging technologies.
Summary Table
Course/Specialization
Key Job Roles
Industry Demand in 2025
MTech/MS/MSc in Computer Science
Software Developer, Systems Architect
High
MBA in IT
IT Manager, Product Manager
High
Master's in Data Science/Big Data
Data Scientist, BI Analyst
Very High
Masters in AI & Machine Learning
AI Engineer, Research Scientist
Very High
Masters in Cybersecurity
Security Analyst, Security Engineer
Very High
Masters in Software Engineering
Senior Software Engineer, DevOps Engineer
High
Masters in Cloud Computing
Cloud Architect, Cloud Engineer
Very High
Masters in Computer Networking
Network Engineer, Systems Admin
High
Certification in Blockchain/IoT/DevOps
Blockchain Developer, IoT Architect
Growing
Masters in Network Engineering
Network Architect, Network Analyst
High
Pursuing any of these courses after BTech CSE in 2025 will enhance your skills, increase employability, and position you for success in the rapidly evolving tech landscape.
0 notes
Text
naturally! The idea of a comprehensive code on cybersecurity and information security is excellent and required, especially with increasing awareness and attention to it. Gadi gives you one detailed structure for topics you can cover them, your blog is a reference and the rank of Meziane. We can call it, for example:
"Your comprehensive guide for cyberspace and information security"
1️⃣ basic concepts
The difference between cybersecurity and information security
Types of sensitive data (personal, financial, medical data …)
Information Security Principles: Secret, Safety, and availability (CIA TRIAD)
2️⃣ Electronic threats and attacks
Types of cyber attacks:
Phishing (Fraud)
Malware (malware: viruses, trojans, ransomware …)
DDOS (attacks on service disable)
SQL Inject
Zero-Day Exploits
Social engineering and how to protect it
3️⃣ Tools and techniques
Anti -virus software and how to choose the best
Firewall walls and their types
VPN and why is important
Curvement (SSL/TLS, PGP, End-To-End Encryption …)
Password Management (Password Managers)
4️⃣ best safety practices for individuals
How to manage strong passwords
Verify two steps (2FA)
E -mail insurance and social accounts
Protecting smartphone and personal computers
5️⃣ Network security
Securing Wi -Fi networks
IDS and infiltration prevention systems (IPS)
Using VPN for public networks
6️⃣ Institutions Security
Information security policies
Cyber awareness and training of employees
Risk evaluation and accident management
Compliance: standards such as ISO 27001, NIST, GDPR
7️⃣ Specializations and professional opportunities in cybersecurity
Types of disciplines: penetration test, digital criminal analysis, accident management …
Professional certificates: CEH, Cissp, Comptia Security+
How to start a professional path, so cyber security
8️⃣ modern news and articles
Cover the latest gaps and attacks
Real case studies analysis
New tools and software reviews
9️⃣ Free Courses and Resources
COURSERA, CYBRARY, Tyhackme …)
Comics books and articles
Training laboratories and challenges (CTF)
10️⃣ The legal and moral aspect
Laws related to electronic crime
Ethics in the penetration test
Privacy and data protection policies
Technical additions (for the Baggi deepening)
Digital Forensics
Cloud Security
Internet Security (IOT Security)
Artificial intelligence and cyber security
Bash notes the blog succeeds
✅ Topics organize in clear sections (for example: for beginners - for applicants) ✅ A practical examples and explanations with pictures or video ✅ Try to give continuous updates Bash, the blog remains up to keep up with
0 notes
Text
Engineering Specializations: That Are in High Demand Today
Choosing the right engineering specialization is one of the most important decisions a student makes when entering this vast and ever-evolving field. With new technologies reshaping industries and businesses every year, some branches of engineering are now more in demand than ever.
As we move into 2025, here are the top engineering specializations that not only promise exciting learning experiences but also offer excellent career prospects in India and globally.
1. Artificial Intelligence and Machine Learning (AI & ML)
AI and ML continue to dominate the technology landscape in 2025. From virtual assistants to self-driving cars and predictive healthcare, these technologies are influencing every sector. Engineers with AI & ML expertise are being hired in industries like finance, healthcare, retail, automotive, and cybersecurity.
Skills in Python, data structures, neural networks, and deep learning are essential. Companies are also looking for professionals who can combine domain knowledge with AI applications.
2. Computer Science and Data Science
This specialization remains in high demand as businesses and governments rely on software systems, apps, and data analytics to make critical decisions. Engineers in this field work on designing software, building secure networks, analyzing big data, and developing scalable web services.
With cloud computing, cybersecurity, blockchain, and data privacy gaining importance, graduates of this branch are consistently recruited by global tech giants and startups alike.
3. Electrical and Electronics Engineering (EEE)
With a global push towards electrification and sustainability, EEE has regained prominence. From electric vehicles and solar grids to robotics and smart homes, this field plays a critical role in modern infrastructure.
Engineers with strong circuit design, embedded systems, IoT, and automation skills are in demand in both core electrical industries and emerging tech sectors.
4. Mechanical Engineering with Robotics and Mechatronics
Traditional mechanical engineering is evolving into a future-oriented domain with specializations in robotics, automation, and mechatronics. These fields are at the core of Industry 4.0, enabling innovations in manufacturing, aerospace, defense, and even medicine.
Engineers who understand both mechanical systems and intelligent electronic controls are highly valued for their interdisciplinary knowledge.
5. Civil Engineering with Smart Infrastructure Focus
Civil engineering is more than just building bridges and roads in 2025. The focus has shifted toward smart cities, sustainable infrastructure, and green construction. As urbanization increases, engineers with skills in urban planning, environmental impact analysis, and geotechnical technologies are in high demand.
Proficiency in design software, project management, and sustainable materials gives graduates a strong advantage.
6. Electronics and Communication Engineering (ECE)
As the world becomes increasingly connected, ECE remains a strong and evolving field. In 2025, there's a growing demand for engineers working on 5G networks, IoT devices, semiconductor design, and communication satellites.
Companies working in consumer electronics, telecom, and chip manufacturing are hiring ECE graduates who understand signal processing, embedded systems, and wireless technology.
7. Information Science and Cybersecurity
With data breaches becoming more frequent, information science and cybersecurity have emerged as strategic areas. Engineers in this domain help protect digital systems and sensitive information.
This specialization includes ethical hacking, data encryption, and digital forensics—making it highly appealing for students interested in protecting the digital world.
Why the Right College Matters
To build expertise in these high-demand engineering branches, students need to choose institutions that offer modern curricula, strong lab infrastructure, research opportunities, and industry exposure. That’s where location and college reputation become important.
Many students looking for the top engineering colleges in Mangalore are drawn by the region’s academic ecosystem and the quality of institutions it offers. Mangalore, with its blend of urban development and serene learning environment, has become a preferred destination for engineering education.
NMAM Institute of Technology (NMAMIT), Nitte – Leading the Way
Among the best engineering colleges in Mangalore, NMAM Institute of Technology (NMAMIT), Nitte, stands out for its commitment to excellence in education, innovation, and career preparedness.
NMAMIT offers specialized programs in emerging fields such as AI & ML, Data Science, Cybersecurity, Robotics, and Smart Infrastructure. With modern labs, experienced faculty, hands-on projects, and strong placement support, the institute ensures students are ready for real-world challenges from day one.
Students at NMAMIT also benefit from international collaborations, industry-led training modules, and opportunities to work on cutting-edge research, making it one of the most future-ready engineering colleges in Karnataka.
1 note
·
View note