#ftp ip camera
Explore tagged Tumblr posts
Text
Blink Outdoor 4th Generation Smart Camera
Blink cameras, a product line by Amazon-owned Blink Home Security, are popular for several reasons, which contribute to their reputation as good home security cameras. Here are some key features and advantages of Blink cameras.
All-New Blink Outdoor (4th Gen) Blink cameras, a product line by Amazon-owned Blink Home Security, are popular for several reasons, which contribute to their reputation as good home security cameras. Here are some key features and advantages of Blink cameras: Wire-Free Design: Blink cameras are wireless and battery-powered, which makes them easy to install and reposition as needed without the…

View On WordPress
#amazon camera#best security camera#blink#blink camera#ftp ip camera#house security#inexpensive security camera#security camera#surveillance camera#video camera#wireless camera
0 notes
Text
YouTube has this thing now called YouTube Playables (great name as usual, guys; it's not a children's snack pack), that are basically in-app "Flash games"-style things that are just enough game to keep you watching ads.
The ones of these that aren't direct ripoffs of owned IP (very specifically Zuma) are barebones exercises in that bog-standard FTP addictive mobile gaming loop we all know and hate but also LOVE, minus the in-app purchases (for the time being). Like, shallow systems that are fun for exactly 30 minutes, then get stupidly hard so you'll pay to win, though you can't do that yet, so...kind of pointless.
...I still spent FOUR HOURS playing these, because they tapped into my primitive lizard brain's desire to try and master an utterly meaningless task and then feel undooly smug about it.
I didn't get any ads, because I'm a stooge that pays real money to Google every month for this, because once you go adless, you CANNOT go back. Which kind of negates the whole point of these, as addictive time-wasters that keep you glued to the platform and its commercials? But I already pay for YouTube and STILL got caught in these, so I suppose everything is going according to YouTube's plan either way, and I need meaningful human relationships.
But THAT isn't going to happen any time soon! So let me waste another evening on these by reviewing some crap garbage games for idiots that no one cares about, on Tumblr dot com!
1. Totemia: Cursed Marbles
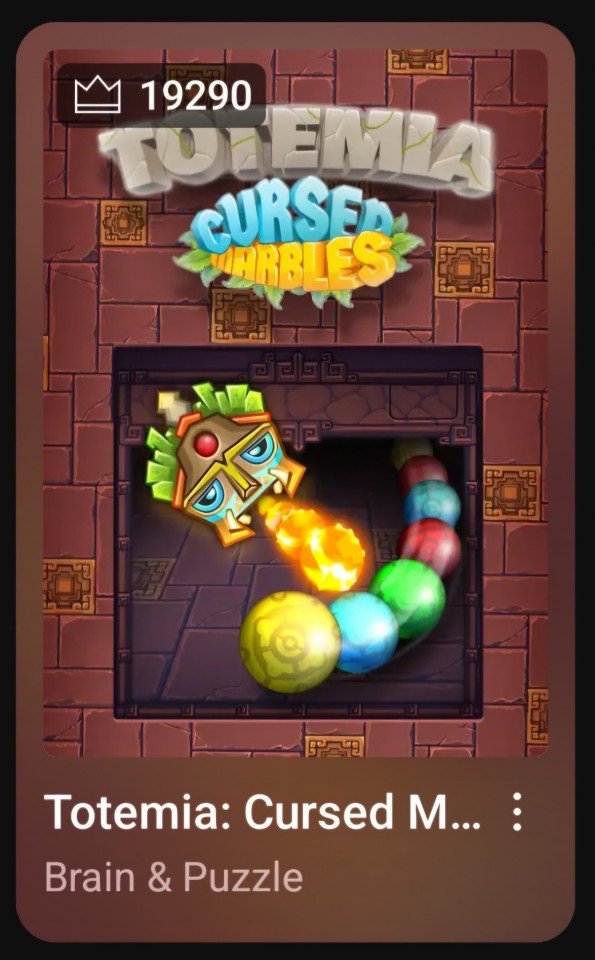
It's Zuma. That's it. With a couple minor tweaks that make it harder and more annoying.
Just license Zuma, YouTube. I think you can afford the, what, $25 that would cost atm?
2. Sword Play
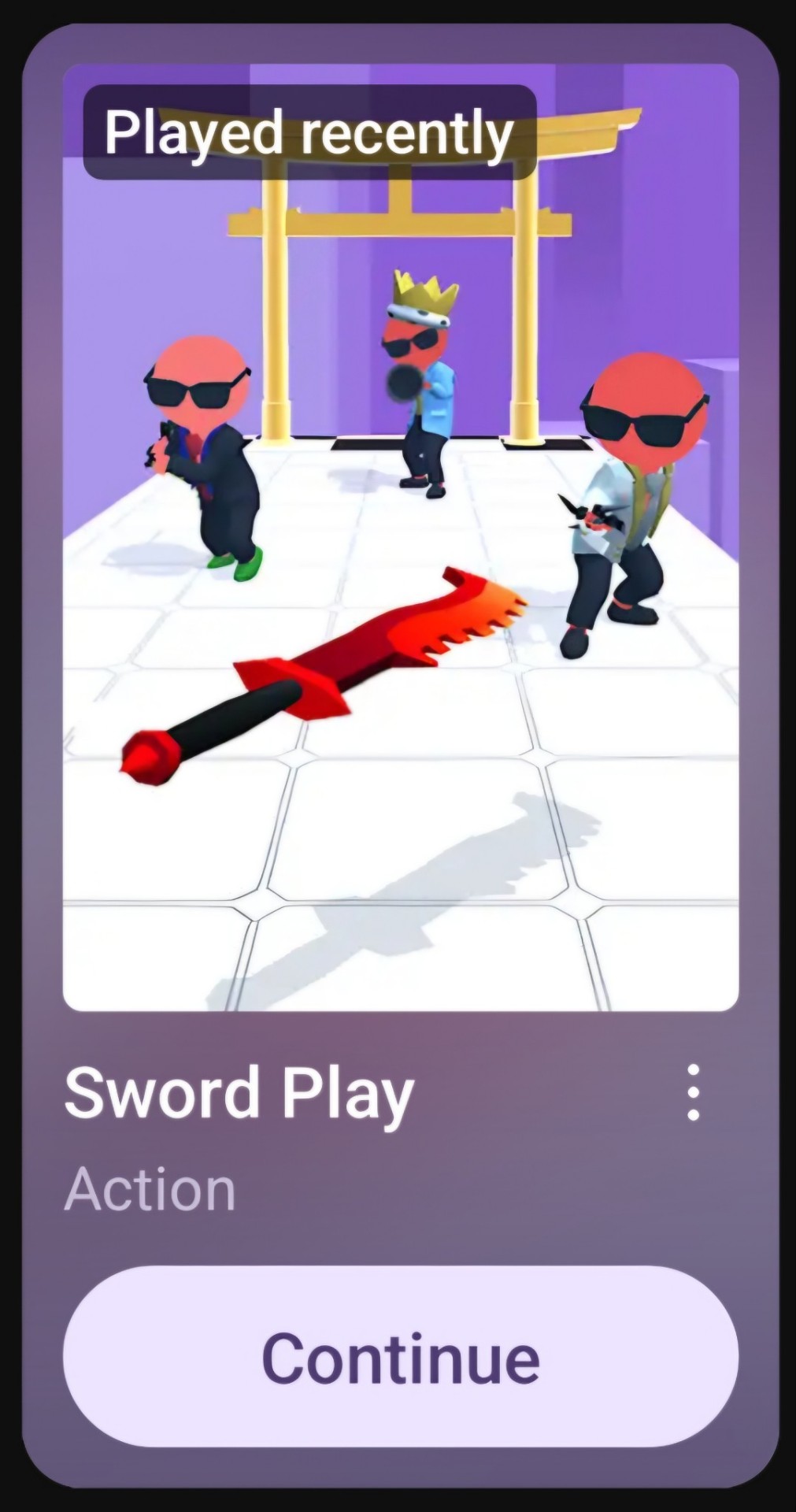
An on-rails sword slashing game (you don't control the movement, just the slashing), and you kill plastic doll guys before they kill you.
At some point they get projectiles that move really fast, that you can only destroy via specific directional QTEs that don't register properly half the time, because this is all relative finger smearing across the screen.
It was fun before that. The guys fall apart specific to how you slash them. That's something.
3. Dessert DIY

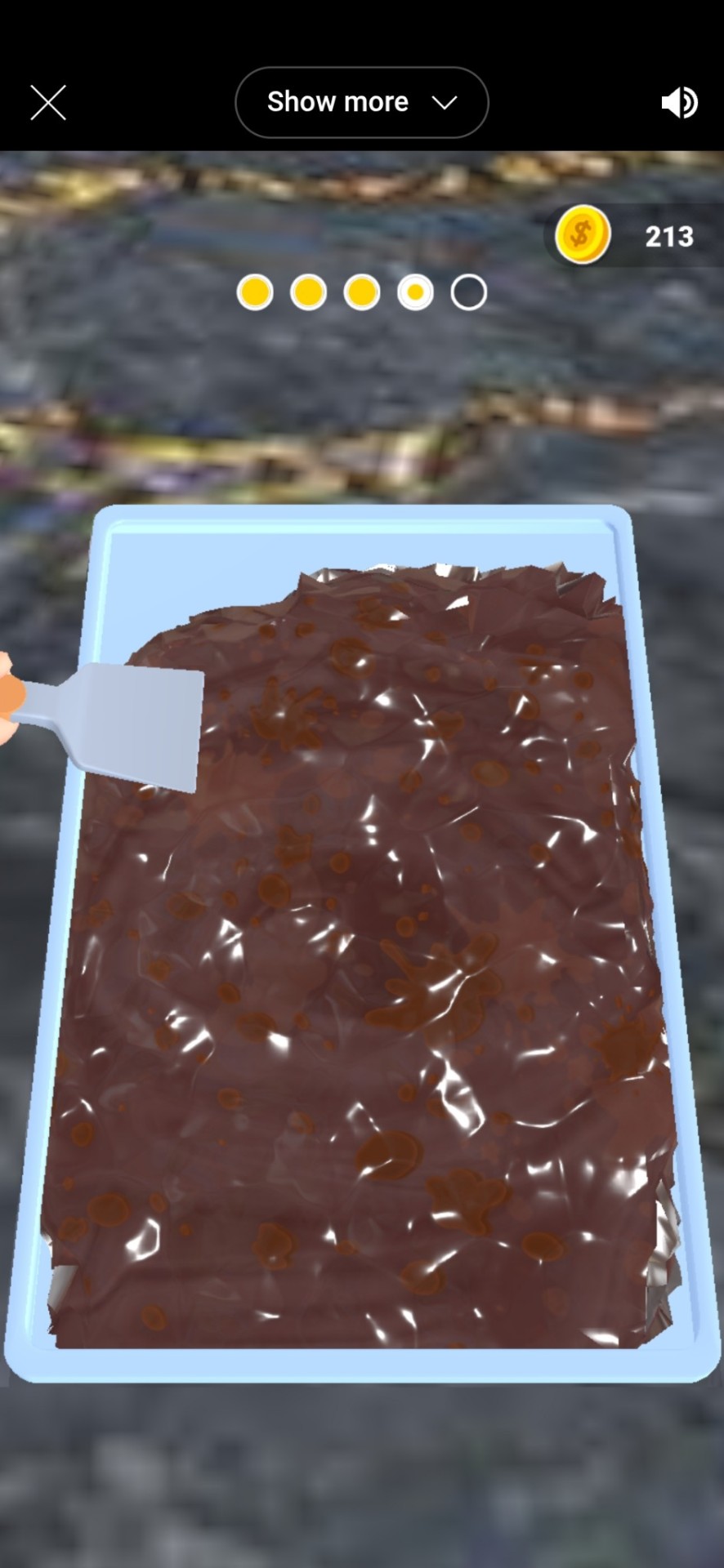
This one sucks. You're just picking from very limited options, then doing specific motions to trigger animations that create desserts that don't even look much like the promo art. People request different things, but early game all they ask for is "whatever you want to make" and "do one out of poop with bugs on it to make someone I hate throw up."
And then there's an animation of someone accepting what is obviously poop with bugs on it from their sworn enemy, they eat it anyway, then vomit.
The only fun part about this is the shameless inclusion of NPCs that look like celebrities, specifically Billie Eilish, Kanye West, and Donald Trump.
If you want to make a poop ice cream cone with bugs on it and feed it to Trump until he vomits all over his desk, this is the game for you. Otherwise, this is meh even for one of these meh games.
4. Bowmasters
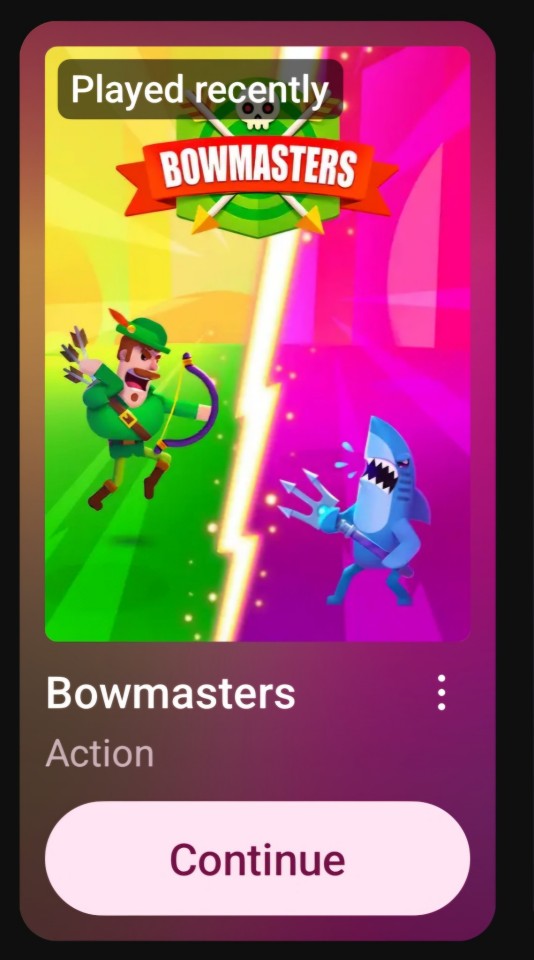

Dueling Angry Birds, but you have no control of the camera and it focuses on you so you have to trial-and-error the degree of angle and throwing force to figure out how to hit and kill your opponent before they hit and kill you.
There are many colorful pop culture-inspired combatants to unlock, with a huge variety of projectiles of different weights, sizes, and behaviors. This is the most "very nearly a real, good game" one of these.
...Except that the level progression forces you to do Bonus Rounds, and one of those is "knock fruit off the head of an opponent without hitting them, and you have to do this like 5 times in a row, and we move you further away from them another 30 yards every round, and you have to use a wildly different unique projectile every round, and you get 3 chances, and that includes if you miss entirely."
It is basically impossible to do this, because your ever-changing location makes calculating arcs and force, with the ever-changing projectiles, impossible, in this limited amount of attempts. It turns into grinding it out until RNG randomly makes you win.
Which is a shame, because otherwise, this is fun. But you WILL get stuck on a stupid fruit round and stop playing this.
5. Mob Control
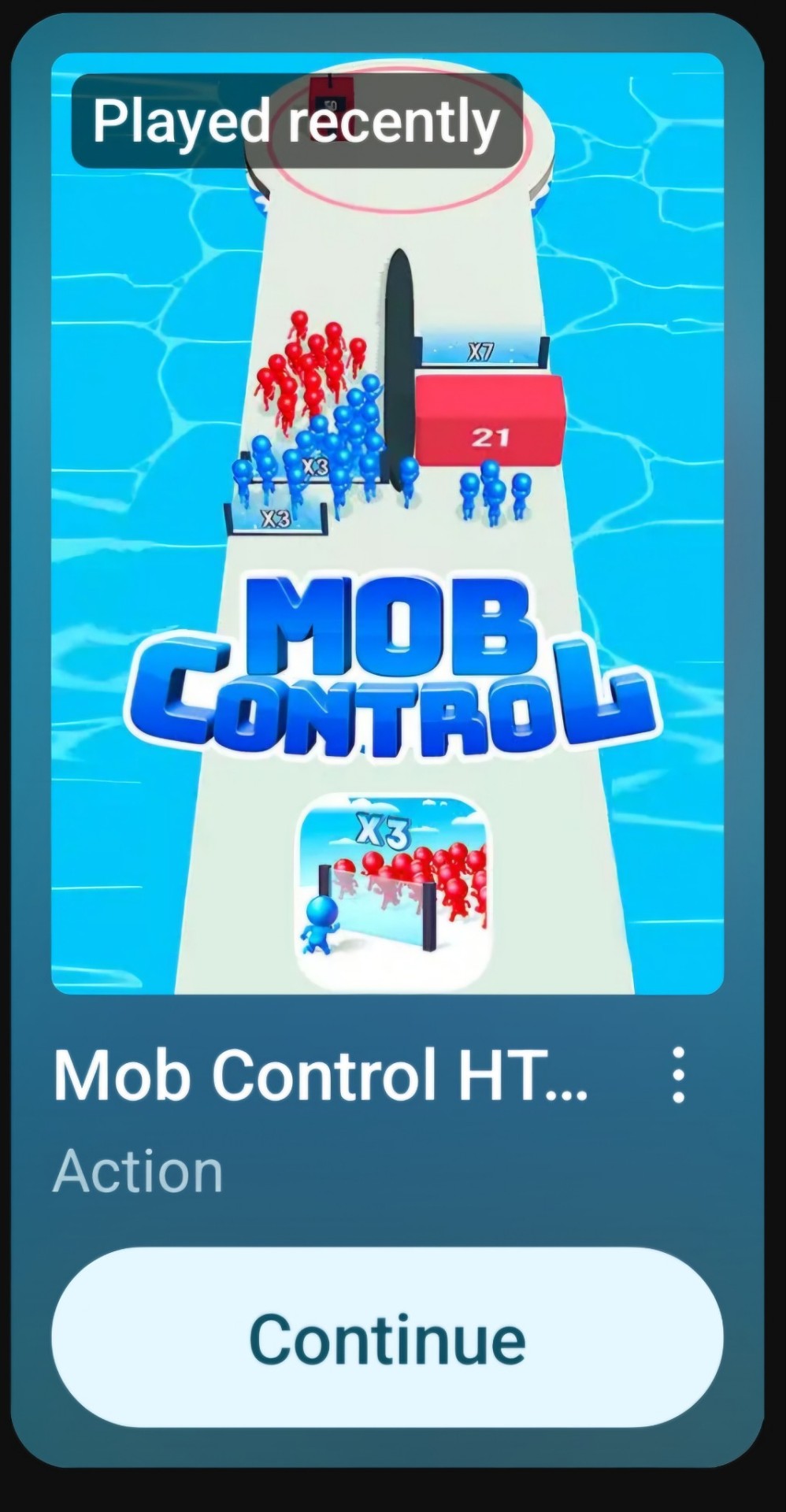
You have a cannon that launches blue guys. The NPC opponent does red. You both are trying to bumrush the other's base, taking advantage of buttons and switches and bonus gates that speed you up or slow you down and multiply your number of guys. Guys annihilate each-other when they run into each-other, so you need to overwhelm Red before they overwhelm you.
It's fun until it gets so fast that it becomes a chore to manage where precisely to launch guys specifically to annihilate other guys.
6. Merge Master
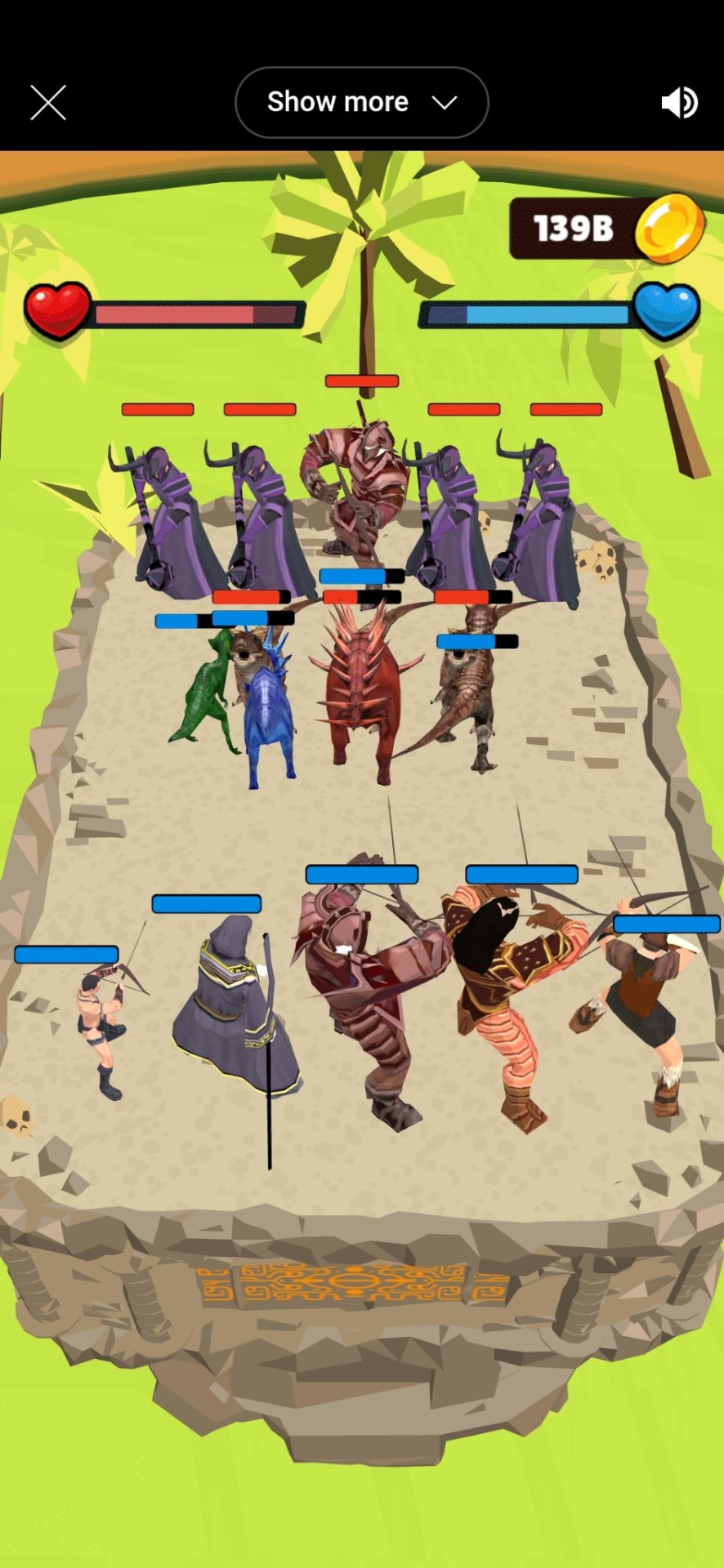
This goddamn game. This was 3.5 hours of my 4 hour playtime.
You have a grid board, with you at the bottom and an opponent at the top. You both have an army of warriors and dinosaurs, and a team HP bar. You click go, the warriors fire projectiles and the dinosaurs melee the nearest enemy, and last man standing wins.
Before each round, you can arrange the placement of your army, and use money you won from the last rounds to buy more warriors and dinosaurs. But the kicker is, you can combine like warriors and dinosaurs to make more powerful units, which you keep at the end of every round. They don't gain XP or anything, but as you make more money, you can buy more 1st-level units (that's all you can buy), and gradually combine them and then combine the combinations, and on and on and on, making incredibly powerful new units. And you need a mix of low-level and high-level units to have enough melee dinosaurs and projectile-throwers to overwhelm high-level enemy units, or draw fire away from your own, against the ever-changing enemy army each round.
It's a process of slowly adding more units and combining them to make stronger and stronger units, and as many of them as you can get, accounting for the limited board space. Also the price of units rises exponentially each round, so you may have 1 trillion gold, but at this point a new 1st-level dinosaur costs 245 billion.
I couldn't stop with this. It just got me. I wanted to see new exciting high-level warriors and dinosaurs, and see how fast I could take the other army down. There's more than zero strategy at work here, and battles can vary substantially from round to round, depending on what mix of units the enemy brings to the board.
It's still a rudimentary Flash-esque game, and very much akin to those shitty mobile boss rush games that raid our shadow legends. But it's not PTW yet, and the graphics are a charming and distorted replica of early 2000s 3D games, like Age of Mythology or GTA 3. It felt like something, for awhile.
It isn't, and I wasted valuable battery charge on this stupid shit. But I was having fun. And sometimes, that's enough.
...And posting about it here. It's something to talk about that isn't the world eating itself.
And we all need that sometimes.
1K notes
·
View notes
Text
CÁP MẠNG APTEK CAT.5E FTP CCA 24AWG (530-2106-1) - ỔN ĐỊNH, CHỐNG NHIỄU, GIÁ MỀM CHO CÔNG TRÌNH MẠNG VỪA & NHỎ
Lắp đặt camera IP, kéo mạng cho nhà ở, văn phòng hoặc chạy dây cho hệ thống quảng cáo LED - bạn không cần thiết phải chi quá nhiều để có chất lượng kết nối ổn định. Aptek Cat.5e FTP CCA 24AWG mã 530-2106-1 là lựa chọn “vừa túi tiền” nhưng vẫn đảm bảo hiệu suất truyền dữ liệu và chống nhiễu tốt, cực kỳ phù hợp cho các công trình vừa & nhỏ cần tối ưu chi phí.
https://tinhocthanhkhang.vn/cap-mang-aptek-cat5e-ftp-cca-24awg-530-2106-1

1 note
·
View note
Text
Enterprise Guide to IoT Penetration Testing: Tools, Techniques, and Risk Reduction
The Internet of Things (IoT) has transformed our homes and workplaces but at what cost?
With billions of connected devices, hackers have more entry points than ever. IoT penetration testing is your best defense, uncovering vulnerabilities before cybercriminals do. But where do you start? Discover the top tools, techniques, and expert strategies to safeguard your IoT ecosystem. Don’t wait for a breach, stay one step ahead.

Read on to fortify your devices now!
Why IoT Penetration Testing is Critical
IoT devices often lack robust security by design. Many run on outdated firmware, use default credentials, or have unsecured communication channels. A single vulnerable device can expose an entire network.
Real-world examples of IoT vulnerabilities:
Mirai Botnet (2016): Exploited default credentials in IP cameras and DVRs, launching massive DDoS attacks.
Stuxnet (2010): Targeted industrial IoT systems, causing physical damage to nuclear centrifuges.
Smart Home Hacks: Researchers have demonstrated attacks on smart locks, thermostats, and even baby monitors.
These incidents highlight why IoT security assessment must be proactive, not reactive.
IoT Penetration Testing Methodology
A structured approach ensures thorough testing while minimizing risks to operational systems.
Reconnaissance & Information Gathering
Identify all IoT devices (smart cameras, sensors, gateways).
Use tools like Nmap, Shodan, and Wireshark to map network traffic.
Extract firmware using Binwalk or Firmware Analysis Toolkit (FAT).
Vulnerability Assessment
Scan for weak credentials, outdated protocols (e.g., Telnet, FTP), and unpatched CVEs.
Tools: OpenVAS, Nessus, OWASP ZAP.
Exploitation & Post-Exploitation
Attempt to bypass authentication, escalate privileges, or intercept data.
Use Metasploit Framework, ExploitDB, or custom scripts.
Test hardware interfaces (UART, JTAG) if physical access is possible.
Reporting & Remediation
Document findings with risk ratings (Critical/High/Medium/Low).
Recommend patches, network segmentation, or encryption upgrades.
DID YOU KNOW?
During the forecast period, the global IoT security market is expected to expand significantly, with projections indicating growth from USD 24.2 billion in 2024 to USD 56.2 billion by 2029, reflecting a CAGR of 18.4%.
[ Are You Looking: DevOps Services ]
Best Open-Source Tools for IoT Penetration Testing
Discover the top tools for assessing IoT security, from firmware analysis to network exploitation. These open-source solutions help uncover vulnerabilities before attackers do.
Firmware Analysis – Binwalk & Firmadyne
Binwalk extracts firmware binaries to analyze file systems.
Firmadyne emulates firmware to detect vulnerabilities.
Network Traffic Analysis – Wireshark & Tcpdump
Inspect unencrypted MQTT, CoAP, or HTTP traffic.
Exploitation Frameworks – Metasploit & IoTGoat
Metasploit has modules for IoT-specific exploits.
IoTGoat is a deliberately vulnerable IoT environment for practice.
Hardware Hacking – JTAGulator & Bus Pirate
Identify debug ports (UART, SPI, I2C) for firmware dumping.
Password Cracking – Hydra & Hashcat
Bruteforce weak credentials on web interfaces or SSH.
[ Good Read: AWS For Beginners ]
Real-World IoT Attack Scenarios & Mitigations
Explore how attackers exploit weak IoT security from hijacked smart cameras to unencrypted medical devices and learn actionable fixes to prevent breaches.
Case 1: Weak Authentication in Smart Cameras
Vulnerability: Default admin:password combinations.
Exploit: Attackers gain live video access.
Fix: Enforce strong passwords & multi-factor authentication (MFA).
Case 2: Unencrypted MQTT Protocols
Vulnerability: Smart sensors transmit data in plaintext.
Exploit: Man-in-the-middle (MITM) attacks steal sensitive data.
Fix: Use TLS encryption and certificate-based authentication.
Case 3: Outdated Firmware in Medical IoT
Vulnerability: Unpatched CVEs in insulin pumps.
Exploit: Remote code execution (RCE) risks patient safety.
Fix: Automated firmware updates with integrity checks.
Key Takeaways for Decision-Makers
Security leaders must enforce robust IoT policies, align penetration testing with business risk, and foster collaboration between IT and OT teams to ensure long-term resilience.
Prioritize Security by Design: Ensure vendors follow OWASP IoT Top 10 guidelines.
Segment IoT Networks: Isolate critical devices from enterprise IT systems.
Conduct Regular Pen Tests: Schedule IoT penetration testing at least annually.
Invest in Threat Monitoring: Deploy SIEM solutions like ELK Stack or Splunk for anomaly detection.
You can check more info about: Enterprise Guide to IoT Penetration Testing.
DevOps Explained.
Platform Engineering Services.
0 notes
Text
Top-Selling Ethernet Cables in New York – Get Yours Now!
If you're in New York and looking for a reliable ethernet cables, you’re in the right place. In today's hyper-connected world, having a fast, secure, and stable internet connection is non-negotiable. Whether you're setting up an office, upgrading your home network, or wiring a commercial space, choosing the right Ethernet cable can make a big difference.
This article breaks down the top-selling Ethernet cables available in New York, what makes them the best choice, and where you can buy ethernet cables in bulk or individually.

Why Ethernet Cables Still Matter in 2025
While Wi-Fi technology keeps improving, Ethernet is still the gold standard for speed and stability. Especially in environments where signal interference is a problem or where consistent speeds are required—ethernet cables are a must.
Whether you're gaming, streaming 4K video, running a business network, or managing servers, a wired connection using Ethernet delivers low latency, high speed, and minimal interruptions.
Top-Selling Ethernet Cables in New York
Let’s explore the most popular types of ethernet cables that people are buying in New York. Each one is suited for specific environments and use cases.
1. Cat5e Ethernet Cables – The Reliable Classic
Cat5e (Category 5 Enhanced) is one of the most commonly used Ethernet cables in both homes and offices. It supports speeds up to 1 Gbps over 100 meters, making it ideal for standard internet usage and networking needs.
✅ Best for:
Home internet setups
Small offices
VoIP phones and IP cameras
🔥 Why it sells in bulk:
Businesses love buying Cat5e ethernet cables bulk due to their affordability and ease of installation.
2. Cat6 Ethernet Cables – Faster and Future-Proof
Cat6 cables are the next step up. They support 10 Gbps speeds at shorter distances (up to 55 meters) and offer better insulation, which means less crosstalk and interference.
✅ Best for:
Gaming setups
Streaming setups
Office networks requiring higher bandwidth
💡 In bulk or not?
Absolutely. When businesses buy ethernet cables, Cat6 in bulk is a top choice because it's compatible with Cat5e networks but provides better performance.
3. Cat6a Ethernet Cables – For Demanding Networks
Cat6a (augmented) offers full 10 Gbps speeds over 100 meters and features tighter twisting of wire pairs with additional shielding. It's ideal for larger network infrastructures.
✅ Best for:
Data centers
Commercial buildings
Businesses with heavy data transfer needs
🔍 A go-to bulk cable:
If you're running dozens or hundreds of feet of cable, ethernet cables bulk in Cat6a is the professional standard.
What to Look for When Buying Ethernet Cables
Before you buy ethernet cables, especially in bulk, consider these factors to ensure you’re getting exactly what you need.
Cable Category
Each category offers different speed and shielding levels:
Cat5e: Affordable and widely compatible
Cat6: Better insulation and higher speeds
Cat6a/Cat7: Advanced performance, more expensive
Jacket Rating
Depending on where the cables will be installed, you’ll need to choose:
Plenum-rated (CMP): For air ducts and commercial ceilings
Riser-rated (CMR): For vertical runs between floors
PVC: For general use where building codes allow
Conductor Type
Always check if the cable is:
Solid Copper: Better performance, longer life
CCA (Copper-Clad Aluminum): Cheaper, but not suitable for all environments
Shielding
For environments with lots of interference, go for:
STP (Shielded Twisted Pair)
FTP (Foiled Twisted Pair)
UTP (Unshielded Twisted Pair) for low-interference areas
Why New York Chooses Bulk Ethernet Cables
In a bustling state like New York—especially NYC—demand for networking infrastructure is massive. Whether it's for tech companies in Manhattan, small businesses in Brooklyn, or schools in Queens, ethernet cables bulk are in constant demand.
Buying in bulk saves:
Money: Lower cost per foot
Time: Fewer repeat orders
Effort: Easier to manage long or multiple runs
If you're planning a major installation, go with bulk rolls of 1000ft, available in pull boxes or spools for smooth installation.
Best Places to Buy Ethernet Cables in New York
Finding the right supplier is just as important as choosing the right cable. Here are your best options:
1. Local Networking Suppliers
Local electronics stores and IT hardware shops in New York often stock all major cable types, including bulk options. The advantage? You can ask for advice in person and get same-day pickup.
2. Online Specialty Retailers
Websites like NewYork Cables offer a wide selection of:
Cat5e, Cat6, Cat6a Ethernet Cables
Plenum and riser-rated bulk rolls
Shielded and unshielded versions
Solid copper cables
You also get fast shipping across New York, guaranteed product quality, and better pricing when ordering in bulk.
Ethernet Cable Use Cases in New York
From modern apartments to data centers, ethernet cables are everywhere. Here’s where they’re most commonly used in New York:
Homes
Gaming consoles
Smart TVs and streaming devices
Home office setups
Businesses
Workstations
IP phone systems
Office servers and routers
Institutions
Schools and universities
Hospitals
Government buildings
Each of these setups can benefit from buying ethernet cables in bulk for large-scale, reliable installations.
Installation Tips for Smooth Setup
Getting the right cable is only half the battle—proper installation ensures the performance you're paying for.
📌 Do:
Use cable testers after installation
Follow building codes (especially with plenum-rated needs)
Label your runs for easy identification
⚠️ Don’t:
Over-bend or twist the cable
Run near electrical cables or power lines
Use CCA cables in high-performance networks
From Cat5e to Cat6a, plenum to riser, and ethernet cables bulk to single patch cords—there’s a solution for every networking need.
Ready to upgrade your setup? Explore the best Ethernet cable deals now at NewYork Cables and get fast delivery anywhere in New York!
0 notes
Photo

HiLook 1.0MP Bullet IP Cam 4.0mm Key Features 1/4" progressive scan CMOS Up to 1.0 megapixel 2.8 mm/4 mm/6 mm fixed focal lens Up to 30 m IR range Dual stream Digital WDR (Wide Dynamic Range) 3D DNR (Digital Noise Reduction) PoE (Power over Ethernet) IP67 Mobile monitoring via Hik-Connect or iVMS-4500 Specification Camera Image Sensor: 1/4" progressive scan CMOS Min. Illumination: Color: 0.01 Lux @(F1.2, AGC ON), 0 Lux with IR Shutter Speed: 1/3 s to 1/100, 000 s, support slow shutter Day &Night: IR cut filter with auto switch Wide Dynamic Range: Digital WDR Angle Adjustment: Pan: 0° to 360°, tilt: 0° to 180°, rotation: 0° to 360° DNR: 3D DNR Lens Lens 2.8 mm @F2.2, horizontal field of view 92°, 4 mm @F2.2, horizontal field of view 70° 6 mm @F2.2, horizontal field of view 56° Lens Mount M12 Illuminator IR Range: Up to 30 m Network Alarm Trigger: Video tampering, network disconnected, IP address conflicted Protocols: TCP/IP, ICMP, HTTP, HTTPS, FTP, DHCP, DNS, DDNS, RTP, RTSP, RTCP, NTP, UPnP, SMTP, IGMP, 802.1X, QoS, IPv6, Bonjour Video Max. Resolution: 1280 × 720 Video Compression Main stream: H.264 Sub stream: H.264/MJPEG H.264 Type: Baseline profile/Main profile Video Bit Rate: 32 Kbps to 2 Mbps Smart Feature-Set Basic EventMotion detection Image Image Setting: Brightness, saturation, contrast, sharpness are adjustable via web browser or client software Day/Night Switch: Support auto, scheduled Main Stream Max. Frame Rate 50Hz: 25fps @(1280 × 720) 60Hz: 30fps @(1280 × 720) Others: Mirror, BLC (area configurable), region of interest (support 1 fixed region) Sub-Stream Max. Frame Rate 50Hz: 25fps @( 640 × 480, 352 × 288, 320 × 240) 60Hz: 30fps @( 640 × 480, 352 × 240, 320 × 240) 4G Standard: ONVIF (PROFILE S), ISAPI Interface Communication Interface: 1 RJ45 10M/100M self-adaptive Ethernet port General General Function: Anti-flicker, heartbeat, mirror, password protection, privacy mask, watermark Startup And Operating Conditions: -30 °C to 60 °C (-22 °F to 140 °F), humidity: 95% or less (non-condensing) Power Supply: 12 VDC ±25%, PoE (802.3af) Power Consumption And Current 12 VDC, 0.3 A, Max. 4 W PoE (802.3af, 37 V to 57 V), 0.08 A to 0.13 A, Max. 5 W Dimensions: 69.1 mm × 66 mm × 172.7 mm ( 2.7" × 2.6" × 6.8") Weight: 500 g (1.1 lb.) Interface Protection: IP67
0 notes
Text
Forlinx FCU2303 5G Smart Gateway for Smart Ambulances
In modern cities, the medical rescue system is crucial for urban safety. Emergency centers command rescue operations, essential for saving lives. With the advancement of IoT technology, many cutting-edge technologies are gradually integrated into the medical emergency system, enabling ambulances to be networked, digitized, and intelligent. Thus, 5G smart ambulances emerge. 5G-enhanced ambulances look similar to regular ones in appearance. However, by integrating 5G networks into the vehicle, developers instantly endowed it with additional "superpowers".

For instance, 5G-enhanced ambulances can achieve synchronized transmission of multiple high-definition live videos, leveraging 5G's high bandwidth, low latency, and reliability. Based on this, it can synchronously return the medical images, patient signs, illness records and other information of emergency patients to the hospital emergency center without damage, which is convenient for the emergency center to grasp the patient's condition in advance and give professional guidance to the rescuers on the bus.
Forlinx's 5G Smart Gateway FCU2303 provides reliable support for medical ambulance.

Rapid transmission of information
Bridge the gap for medical device information transmission.
Modern ambulances are equipped with advanced medical equipment such as electrocardiogram monitors, ventilators, and defibrillators to enhance rescue efficiency. Various types of diagnostic and therapeutic equipment can efficiently transmit physiological data to the Hospital Information System (HIS) through the multiple Ethernet ports, serial ports, and DI/DO of the FCU2303 industrial-grade smart gateway. This meets the data collection and transmission requirements of ambulances.

Enabling high-definition audio and video consultations
Medical imaging equipment such as cameras, microphones, displays, and ultrasound machines are deployed on the ambulance. Through the FCU2303 industrial-grade smart gateway, information is transmitted, providing real-time, lossless transmission of audio-visual images from the ambulance to the hospital emergency center. This setup offers a high-bandwidth, low-latency, and highly connected secure network, meeting the remote video consultation needs of the ambulance. It aims to secure more time for patients by implementing a rapid rescue and treatment mode where patients essentially “Be in the hospital” upon boarding the ambulance.

Enabling reliable integration of multiple technologies
FCU2303 Smart Gateway, designed based on the NXP LS1046A processor, features a quad-core CPU with a high clock frequency of 1.8GHz. With a fanless design, it ensures stable operation of medical rescue systems for extended periods in environments ranging from -40°C to +85°C;
It supports 5G and 4G modules, which can be easily switched with a single DIP switch. It provides users with high bandwidth, low latency, and large connectivity services. It also supports dual-band Wi-Fi, enabling both STA and AP modes;
FCU2303 supports expandable device storage with PCIe 3.0 high-speed interface, enabling support for solid-state drives (SSDs) using the NVMe protocol (M.2 interface). This meets the requirements for small size, large capacity, and fast speed;
It comes standard with 8 x Gigabit Ethernet ports (flexible configuration of 2/4/6/8 ports, all with independent MAC addresses), 4 RS485 ports, 4 RS485/RS232 multiplexing interfaces, 2 DI (Digital Input), 2 DO (Digital Output), and 1 USB HOST 3.0 port. This ensures the connectivity of various medical devices, enabling full vehicle networking for ambulances;
The software integrates a variety of third-party components including Samba, Lighttpd, Docker, IPSEC, OpenSSL, and Python 3 or higher versions. It supports protocols such as TCP/IP, UDP, DHCP, TFTP, FTP, Telnet, SSH, Web, HTTP, IPtables, and provides an open system API for easy user customization and development.

In the future, smart ambulances based on 5G technology will undoubtedly provide better full-process services for patients, including pre-diagnosis, during diagnosis, and post-diagnosis.
Forlinx Embedded FCU2303 Smart Gateway, which supports the 5G smart ambulance system, fully leverages the leading advantages of 5G technology, including high bandwidth, low latency, and large connectivity. It will undoubtedly effectively and efficiently guarantee the transmission of information for various medical devices. This will assist medical emergency centers in further improving the efficiency and service level of emergency rescue work, enhancing service quality, optimizing service processes and modes, and winning time for rescuing patients’ lives, thereby better-safeguarding health and life.
Originally published at www.forlinx.net.
0 notes
Text
do you need to forward ports for torrenting with vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do you need to forward ports for torrenting with vpn
Port forwarding necessity
Port forwarding is a crucial aspect of networking, especially for individuals and businesses that rely on remote access to devices or services. Essentially, port forwarding allows incoming connections from the internet to reach a specific device or service within a private local network. Without port forwarding, these incoming connections would be blocked by the router's firewall, preventing access to the desired resource.
One of the primary reasons for port forwarding is to enable remote access to devices such as security cameras, web servers, or remote desktops. For example, if you have a surveillance system set up at your home or office, port forwarding allows you to view the camera feed from anywhere in the world via a smartphone or computer. Similarly, businesses often use port forwarding to grant employees access to internal resources while they are working remotely.
Port forwarding is also essential for hosting online services or applications. Whether you're running a website, a game server, or an FTP server, port forwarding ensures that incoming requests from the internet are properly routed to the correct server within your network. This is crucial for maintaining connectivity and ensuring that your services remain accessible to users at all times.
Moreover, port forwarding is a fundamental component of peer-to-peer networking and online gaming. Without properly configured ports, users may experience connectivity issues, lag, or inability to join multiplayer games.
In summary, port forwarding is necessary for facilitating remote access, hosting online services, and optimizing peer-to-peer networking. By configuring port forwarding settings on your router, you can ensure seamless connectivity and access to your networked devices and services from anywhere in the world.
Torrenting VPN configuration
Torrenting has become a popular method for sharing files online, but it also comes with risks such as exposing your IP address to potential hackers or copyright infringement issues. Using a Virtual Private Network (VPN) for torrenting can help protect your privacy and secure your connection.
Configuring a VPN for torrenting involves a few key steps to ensure optimal performance and security. Firstly, choose a reputable VPN service that allows torrenting and offers high-speed connections. Many VPN providers have dedicated servers for P2P file sharing, so be sure to select one of these servers when configuring your VPN.
Once you have chosen a VPN service, download and install the VPN client on your device. Follow the instructions provided by the VPN provider to set up and configure the VPN on your device. You may need to adjust settings such as encryption protocols and kill switch features to enhance your torrenting experience.
After configuring the VPN on your device, make sure to enable the VPN whenever you engage in torrenting activities. This will encrypt your internet traffic and hide your IP address, making it difficult for third parties to track your online activities.
Remember to regularly update your VPN client and adhere to the terms of service of your VPN provider to ensure continued protection while torrenting. By following these steps, you can safely and securely enjoy torrenting while protecting your privacy and maintaining online anonymity.
VPN port forwarding implications
VPN port forwarding can significantly impact your online security and privacy, as well as your network performance. Port forwarding involves redirecting internet traffic from one port to another, typically to facilitate communication between different devices or services. When used in conjunction with a VPN (Virtual Private Network), port forwarding introduces several important considerations.
Firstly, port forwarding can weaken the security provided by your VPN. VPNs encrypt your internet traffic to protect it from interception and monitoring by third parties. However, when port forwarding is enabled, specific ports are opened on your device or router, bypassing the VPN's encryption. This exposes any data transmitted through those ports to potential interception, increasing the risk of unauthorized access to your sensitive information.
Moreover, port forwarding can compromise your anonymity while using a VPN. VPNs anonymize your internet activity by masking your IP address and routing your traffic through servers located in different geographical locations. However, port forwarding can reveal your true IP address and location to websites and online services, undermining the anonymity provided by the VPN.
Furthermore, port forwarding may impact the performance of your VPN connection. By diverting traffic through specific ports, port forwarding can create congestion and latency issues, especially if multiple devices are using the forwarded ports simultaneously. This can result in slower internet speeds and less reliable connections, particularly during peak usage periods.
In conclusion, while port forwarding can be a useful tool for facilitating certain online activities, its implications for VPN users are significant. It can compromise security, anonymity, and performance, undermining the very purposes for which VPNs are typically used. Therefore, it's essential for VPN users to carefully consider the implications of enabling port forwarding and weigh them against the potential benefits.
Torrenting without port forwarding
Torrenting without port forwarding can be a challenge for many users, but it's not impossible. Port forwarding is a technique used to allow incoming connections from the internet to reach a specific device or service within a private local area network (LAN). In the context of torrenting, port forwarding is often necessary for optimal performance and to enable other peers to connect to your client and share data.
However, there are ways to torrent without port forwarding, although it may result in slower speeds and reduced connectivity. One method is to use a virtual private network (VPN) that supports port forwarding. Some VPN providers offer this feature as part of their service, allowing users to bypass the need for manual port forwarding on their router.
Another option is to use a torrent client that supports uPnP (Universal Plug and Play) or NAT-PMP (Network Address Translation Port Mapping Protocol). These protocols automate the process of port forwarding by allowing the torrent client to communicate with the router and open the necessary ports dynamically.
Additionally, using a torrent-friendly seedbox can also eliminate the need for port forwarding. A seedbox is a remote server specifically designed for torrenting, and it typically comes pre-configured with all the necessary settings to ensure optimal performance.
However, it's essential to note that while torrenting without port forwarding is possible, it may not provide the same level of speed and connectivity as having port forwarding enabled. Users may experience slower download speeds and fewer available peers, particularly in torrent swarms with strict connectivity requirements.
Ultimately, the method you choose for torrenting without port forwarding will depend on your specific needs and preferences. Whether you opt for a VPN, a torrent client with uPnP/NAT-PMP support, or a seedbox, it's crucial to prioritize privacy, security, and legal compliance while engaging in torrenting activities.
VPN torrenting security
VPN torrenting security is a crucial consideration for individuals who engage in peer-to-peer file sharing activities. Torrenting involves the transfer of large files over the internet, often including copyrighted materials. While torrenting itself is legal, downloading or sharing copyrighted content without permission is not.
Using a VPN, or Virtual Private Network, can enhance security and privacy while torrenting. VPNs encrypt your internet connection, making it difficult for others to track your online activities, including torrent downloads. This encryption helps protect your personal information and location from cybercriminals, government surveillance, and copyright trolls.
When choosing a VPN for torrenting, it's essential to select a provider that offers robust security features, such as a no-logs policy, strong encryption protocols like OpenVPN or WireGuard, and a kill switch to prevent data leaks if the VPN connection drops. Additionally, selecting a VPN with servers optimized for P2P file sharing can help improve download speeds and overall performance.
While VPNs can enhance security while torrenting, it's important to note that they are not a foolproof solution. Users should still exercise caution and avoid downloading copyrighted material without permission. Additionally, some ISPs may throttle VPN connections or block torrenting altogether, so it's essential to choose a VPN provider with a solid reputation for bypassing such restrictions.
In conclusion, VPN torrenting security is a critical aspect of maintaining privacy and security while engaging in peer-to-peer file sharing. By selecting a reputable VPN provider with strong security features and taking necessary precautions, users can enjoy a safer and more secure torrenting experience.
0 notes
Text
can port forwarding speed up vpn speed
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can port forwarding speed up vpn speed
Port Forwarding
Title: Understanding the Essentials of Port Forwarding
Port forwarding is a crucial aspect of networking that allows devices within a private network to communicate with devices outside the network, typically over the internet. It involves redirecting data traffic from one port on a network node to another, facilitating seamless communication between devices across different networks.
The primary purpose of port forwarding is to enable access to specific services or applications hosted on devices within a private network. For example, if you have a web server or a gaming console behind a router, port forwarding allows external users to access these services by forwarding the relevant ports to the respective devices.
To implement port forwarding, you typically need access to your router's configuration settings. Within the router settings, you can define port forwarding rules by specifying the port number and the local IP address of the device hosting the service. Once configured, incoming data packets targeting the specified port are redirected to the corresponding device, enabling external access.
Port forwarding is commonly used in various scenarios, such as hosting online games, remote desktop access, accessing security cameras remotely, and hosting web servers or FTP servers. It plays a crucial role in enabling remote access to services and applications, enhancing productivity and convenience for users.
However, while port forwarding offers numerous benefits, it also poses security risks if not implemented correctly. Opening ports indiscriminately can expose devices to potential threats, such as unauthorized access or malware attacks. Therefore, it's essential to exercise caution and follow best practices, such as configuring port forwarding selectively and keeping router firmware updated to mitigate security vulnerabilities.
In conclusion, port forwarding is a fundamental networking concept that facilitates the seamless exchange of data between devices within private networks and external sources. By understanding its principles and implementing it judiciously, users can leverage its benefits while safeguarding their network security.
VPN Speed
VPN speed is a crucial factor to consider for internet users seeking to protect their online privacy and security while accessing content from around the world. A VPN, or Virtual Private Network, encrypts your internet connection and routes it through a remote server, making it appear as though you are accessing the internet from a different location. While the benefits of using a VPN are clear, such as bypassing geo-restrictions and shielding your data from hackers and surveillance, the speed of your VPN connection is equally important for ensuring a smooth and seamless online experience.
When it comes to VPN speed, several factors can influence the performance of your connection. One key factor is the distance between your physical location and the VPN server you are connected to. Connecting to a server that is far away can lead to slower speeds due to increased latency. Choosing a server closer to your location can help improve your VPN speed.
Additionally, the quality and capacity of the VPN provider's servers can impact speed. Opting for a reputable VPN service with a large server network and high-speed connections can help ensure faster speeds during your online activities. Some VPN providers even offer specialized servers optimized for streaming, gaming, or P2P file sharing to enhance your speed for specific activities.
In summary, VPN speed plays a critical role in the overall performance of your VPN connection. By considering factors such as server distance, provider quality, and specialized server options, you can optimize your VPN speed for a secure and efficient online experience.
Internet Connectivity
Title: Navigating the Seas of Internet Connectivity: A Comprehensive Guide
In the digital age, where virtually every aspect of our lives is intertwined with technology, internet connectivity stands as the cornerstone of our interconnected world. From communication and entertainment to business transactions and education, a stable and reliable internet connection has become a necessity rather than a luxury.
Internet connectivity refers to the ability to access and use the internet, typically through various devices such as computers, smartphones, tablets, and smart home devices. It encompasses both the infrastructure that enables internet access and the quality of the connection experienced by users.
Several factors influence internet connectivity, including geographical location, infrastructure development, technological advancements, and service providers. Urban areas often boast faster and more reliable internet connections due to better infrastructure and higher population density, while rural areas may face challenges such as limited coverage and slower speeds.
Technological advancements, such as the deployment of fiber-optic cables and 5G networks, continue to push the boundaries of internet connectivity, offering faster speeds and lower latency. Additionally, initiatives like satellite internet aim to bridge the connectivity gap in remote areas where traditional infrastructure may be lacking.
Choosing the right internet service provider (ISP) and plan is crucial for ensuring optimal connectivity. Factors to consider include speed, reliability, data caps, and customer support. Consumers should also be aware of the different types of internet connections available, such as DSL, cable, fiber, and wireless, each with its own advantages and limitations.
In conclusion, internet connectivity plays a pivotal role in our modern society, shaping how we communicate, work, learn, and entertain ourselves. By understanding the factors that influence connectivity and making informed choices, individuals and businesses can navigate the vast seas of the internet with confidence and efficiency.
Network Configuration
Network configuration refers to the process of setting up and arranging various components within a computer network to enable communication and data exchange between devices. It encompasses both hardware and software configurations, ensuring that all elements function together seamlessly to achieve optimal network performance.
At its core, network configuration involves several key steps:
Hardware Setup: This involves physically connecting network devices such as routers, switches, modems, and computers using appropriate cables (e.g., Ethernet cables, fiber optic cables). Devices must be placed strategically to ensure efficient data transmission and minimize signal interference.
IP Address Assignment: Every device on a network requires a unique identifier known as an IP address to communicate with other devices. Network administrators assign IP addresses manually or through dynamic methods such as DHCP (Dynamic Host Configuration Protocol).
Subnetting and VLANs: Large networks are often subdivided into smaller subnetworks called subnets. This helps organize devices logically and improves network efficiency. Similarly, Virtual LANs (VLANs) are used to segment a network into separate broadcast domains, enhancing security and manageability.
Routing Configuration: Routers play a crucial role in directing network traffic between different subnets or VLANs. Routing protocols such as RIP (Routing Information Protocol) or OSPF (Open Shortest Path First) are configured to determine the best paths for data transmission.
Security Settings: Network security measures such as firewalls, access control lists (ACLs), and encryption protocols are configured to safeguard sensitive data and prevent unauthorized access to the network.
Quality of Service (QoS): QoS settings prioritize certain types of network traffic (e.g., voice or video) over others to ensure a consistent level of service and minimize latency.
Monitoring and Optimization: After initial setup, continuous monitoring and periodic optimization are essential to maintain network performance. This includes analyzing traffic patterns, identifying bottlenecks, and adjusting configurations accordingly.
In conclusion, effective network configuration is essential for building reliable, secure, and efficient computer networks that meet the needs of modern businesses and organizations. By following best practices and staying abreast of emerging technologies, network administrators can ensure smooth and seamless network operations.
Bandwidth Optimization
Bandwidth optimization is a crucial aspect of managing internet connectivity efficiently and maximizing the performance of networks. Bandwidth refers to the maximum data transfer rate of a network or internet connection. In today's digital age where high-speed internet is essential for both personal and business use, optimizing bandwidth has become increasingly important.
One of the key benefits of bandwidth optimization is the improved speed and responsiveness of internet access. By utilizing bandwidth optimization techniques, such as data compression, caching, and traffic shaping, users can experience faster loading times for websites, quicker downloads, and smoother streaming of videos and music. This is especially advantageous for businesses that rely on a fast and reliable internet connection to carry out their day-to-day operations seamlessly.
Bandwidth optimization also helps in reducing network congestion and latency. By prioritizing data traffic and allocating bandwidth more efficiently, organizations can ensure that critical applications and services receive the necessary resources to function optimally. This can lead to improved productivity and a better user experience for both employees and customers.
Furthermore, optimizing bandwidth can result in cost savings for businesses. By preventing unnecessary data usage and prioritizing important traffic, organizations can avoid overspending on expensive network infrastructure upgrades. This can be particularly beneficial for small to medium-sized businesses looking to make the most out of their existing network resources.
In conclusion, bandwidth optimization plays a crucial role in enhancing internet performance, reducing network congestion, and achieving cost efficiencies. By implementing effective bandwidth optimization strategies, individuals and businesses can enjoy a faster, more reliable internet connection and ensure that their online activities run smoothly and efficiently.
0 notes
Text
How to Enhance Your Website Security

A secure website is foundational to any successful online business. Protecting your site and visitors from threats requires implementing robust security provisions across infrastructure, software, and policies. This comprehensive guide covers proven methods to enhance overall website security. Consider having an expert Virginia web design company handle security configuration for you.
Leverage a Secure Hosting Infrastructure
Choose a hosting provider that offers state-of-the-art data centers featuring:
Multi-layered physical security such as biometric entry systems, cameras, staffed 24/7.
Redundant power supplies, environmental controls, and network links to prevent downtime.
Regular third-party penetration testing to expose vulnerabilities.
Compliance with security standards like ISO 27001, SOC 2, PCI DSS.
Install Trusted SSL Certificates
Install SSL certificates to enable HTTPS and encrypt all connections:
SSL activates the padlock and "https" in the URL, providing visual trust signals.
Encryption protects sensitive data transmitted between servers and visitors.
Choose Extended Validation Certificates for maximum browser verification.
Redirect all HTTP requests to HTTPS to mandate secure connections.
Harden Your Website Platform
Harden your website platform at the code level:
For WordPress sites, disable file editing in wp-config. Update to the latest PHP version. Limit available plugins/themes.
Apply the latest security patches and updates for CMS platforms and contributed plugins/themes which are common attack vectors.
Review and restrict file permissions to prevent malicious edits and injections.
Disable directory browsing to block access to backend file structures.
Implement reCAPTCHA on forms to prevent automated submissions/spam.
Secure Admin Access
Fortify your admin dashboard:
Use strong credentials and enable two-factor authentication.
Limit admin access only to IP addresses actually needed to manage the site.
Obscure the admin URL using renaming plugins to conceal it.
Install a firewall like Wordfence to block unauthorized intrusion attempts.
Carefully audit users with admin-level privileges and revoke any unnecessary.
Perform Vulnerability Scanning
Scan for vulnerabilities:
Use automated scanners like Acunetix to detect issues across infrastructure, web platforms, plugins etc.
Perform manual checks for any logic flaws in custom code.
Test password strength and exploit potential on all forms.
Check susceptibility to cross-site scripting, SQL injection and other common attack types.
Scan regularly after any major updates or changes.
Implement Strong Access Policies
Enforce stringent access policies:
Insist all employees use strong, unique passwords for every account and platform.
Require multi-factor authentication for any remote access to infrastructure or data.
Be vigilant regarding use of secure protocols like SFTP/SCP instead of FTP, and SSH instead of Telnet.
Train staff on common social engineering tactics like phishing to avoid breaches.
With constant threats, an intentional focus on security is required to protect your website and visitors. Follow best practices across infrastructure, software and access policies for robust protection.
#ecommerce#branding#marketing#brand#digitalmarketing#brand new#branddevelopment#entrepreneur#guide#websupport#websuccess#web surfing#cyber security#national security
0 notes
Text
CoverMeVPN best VPN Services in 2021.
CoverMeVPN provide to 140+ countries, 350+ locations, with 3k+ servers and 300k+ shared IP’s. Our network allows us to guarantee 99.9% up time with 100% satisfaction guarantee to or subscribers. This VPN is best for the Tor Browser. The Advanced Encryption Standard (AES), also referred to as Military-Grade Encryption, is used by governments, intelligence agencies and cyber security experts worldwide to encrypt sensitive information. Most secure VPN providers use AES with 256-bit keys, which is virtually impossible to crack. Our Logs policy is very strict. We don’t keep any data or logs of our client’s usage. Leave no digital footprint, traffic data is encrypted and impossible to be tracked by anyone. Data will be automatically deleted at every 15 minutes. Stay Private and secure your Digital assets, Crypto, Databases, Bank Accounts, Cameras, FTPs connections and more. Unlock Censored Websites Browse high security websites without worrying getting blocked like PayPal, Netflix IPTV and other. No-log VPN means that the Virtual Private Network provider does not collect or log any information transmitted through the network. They don't save information about your personal details, where you go online, what you download, or what you search for. CoverMeVPN also have No-Log policy. So this VPN is more secure than other VPN. Anyone can use this VPN at any kind of devices, like as- Windows, MAC, iOS, Android, Linux etc. Our VPN infrastructure supports all VPN Protocols: PPTP, L2TP, IKEV2, SSTP, TCP and UDP which most of the others VPN providers don’t offer.
3 notes
·
View notes
Text
CÁP DINTEK POWERMAX+ 4P CAT.6A S/FTP 23AWG PVC 1105-06027 - CHỐNG NHIỄU, TRUYỀN DẪN ỔN ĐỊNH CHUẨN 10GBPS
Khi hệ thống mạng yêu cầu băng thông cao, chống nhiễu tốt và độ ổn định dài lâu, dòng cáp mạng Cat.6A S/FTP của Dintek PowerMAX+ là giải pháp tối ưu cho hệ thống doanh nghiệp, camera IP, trung tâm dữ liệu, hoặc công trình tiêu chuẩn quốc tế.
https://tinhocthanhkhang.vn/cap-mang-chinh-hang-cat6a-s-ftp-305m-dintek-1105-06027

1 note
·
View note
Text
Poe Camera Viewer




Amcrest 4K 8MP Wired Outdoor POE Optical Zoom IP Turret Security Camera 2.7 mm -12 mm Motorized Lens, IP67 IK10 Vandal Resistant Model# IP8M-MT2544EW-60FT AMCREST UltraHD Wired Outdoor Security IP Turret PoE Camera, 5-Megapixel, 98 ft. Night Vision, 2.8 mm Lens, IP67 Weatherproof.
The multiple view options allow you to keep an eye on every part of your home, and you get notifications and alerts in case motion is detected. The notifications are sent via email, loudspeaker and your mobile phone. Both the desktop and mobile versions are easy to use so it belongs on this list of the best IP camera DVR software.
Poe Camera Viewer Windows 10
Works with IEEE 802.3af PoE compliant devices
16x digital zoom
1x 10/100Mbps Fast Ethernet PoE port
Input/Output ports to network alarm systems and other devices
High quality MPEG-4 and MJPEG video recording with up to 30 frames per second
Resolution up to VGA: 640 x 480 pixels
1x removable 6mm, F1.8, CS Mount Lens
Included wall and ceiling mounting hardware
Manage up to 20 user profiles
Hear and talk to people in your camera's viewing field through your computer
Supports TCP/IP networking, SMTP Email*, HTTP, Samba and other Internet protocols
Built-in SD card slot allows you to store still images or video directly onto a SD memory card**
Record streaming video to your computer, SD card or network storage devices
Motion detection triggered email alerts and image upload via FTP
Multiple adjustable motion detection windows with just-in-time snapshot
Quick Universal Plug and Play (UPnP) installation
Complimentary IPView Pro 2.0 software: manage up of up to 32 cameras ***
3-year limited warranty
Panasonic Poe Camera
* Support SSL with complimentary software** SD memory card sold separately*** Monitoring multiple cameras may require a high performance CPU
Poe Camera Viewer Software
Both wired and wireless IP cameras can provide feasible solutions for security systems. PoE vs W-iFi camera, their pros and cons will be analyzed in view of flexibility, transmission speed, network reliability, personal data security, coverage, installation, etc. Taking networking environments, application scenarios, and scale into considerations when making decisions.

1 note
·
View note
Photo

Hikvision 2MP 2.8mm ColorVu Fixed Bullet IP Camera Camera Image Sensor: 1/2.8" Progressive Scan CMOS Max. Resolution: 1920 × 1080 Min. Illumination: 0.0005 Lux @ (F1.0, AGC ON), 0 Lux with Light Shutter Time: 1/3 s to 1/100,000 s Angle Adjustment: Pan: 0° to 360°, tilt: 0° to 90°, rotate: 0° to 360° Lens Lens Type: Fixed focal lens, 2.8 mm optional Focal Length & FOV: 2.8 mm, horizontal FOV 107°, vertical FOV 56°, diagonal FOV 127° Lens Mount: M12 Iris Type: Fixed Aperture: F1.0 Depth Of Field: 2.8 mm, 1.7 m to ∞ DORI DORI: 2.8 mm, D: 46 m, O: 18 m, R: 9 m, I: 4 m Illuminator Supplement Light Type: White light Supplement Light Range: 40 m Smart Supplement Light: Yes Audio Audio Compression: -U: G.711ulaw/G.711alaw/G.722.1/G.726/MP2L2/PCM/MP3/AAC Audio Bit Rate: -U: 64 Kbps (G.711ulaw/G.711alaw)/16 Kbps (G.722.1)/16 Kbps (G.726)/32 to 192 Kbps (MP2L2)/8 to 320 Kbps (MP3)/16 to 64 Kbps (AAC) Audio Sampling Rate: -U: 8 kHz/16 kHz/32 kHz/44.1 kHz/48 kHz Environment Noise Filtering: -U: Yes Network Protocols: TCP/IP, ICMP, HTTP, HTTPS, FTP, DHCP, DNS, DDNS, RTP, RTSP, NTP, UPnP, SMTP, IGMP, 802.1X, QoS, IPv4, IPv6, UDP, Bonjour, SSL/TLS, PPPoE, SNMP Simultaneous Live View: Up to 6 channels API: Open Network Video Interface (PROFILE S, PROFILE G, PROFILE T), ISAPI, SDK User/Host: Up to 32 users. 3 user levels: administrator, operator and user Security: Password protection, complicated password, HTTPS encryption, IP address filter, Security Audit Log, basic and digest authentication for HTTP/HTTPS, TLS 1.1/1.2, WSSE and digest authentication for Open Network Video Interface Network Storage: NAS (NFS, SMB/CIFS), auto network replenishment (ANR) Client: iVMS-4200, Hik-Connect, Hik-Central Web Browser: Plug-in required live view: IE 10+ Plug-in free live view: Chrome 57.0+, Firefox 52.0+ Local service: Chrome 57.0+, Firefox 52.0+ Image Image Parameters Switch: Yes Image Settings: Rotate mode, saturation, brightness, contrast, sharpness, gain, white balance adjustable by client software or web browser Day/Night Switch: Day, Night, Auto, Schedule Wide Dynamic Range (WDR): 120 dB SNR: ≥ 52 dB Image Enhancement: BLC, HLC, 3D DNR Interface Ethernet Interface: 1 RJ45 10 M/100 M self-adaptive Ethernet port On-Board Storage: Built-in memory card slot, support microSD/SDHC/SDXC card, up to 256 GB Built-In Microphone: -U: Yes Reset Key: Yes Event Basic Event: Motion detection (human and vehicle targets classification), video tampering alarm, exception Smart Event: Line crossing detection, intrusion detection, region entrance detection, region exiting detection (support alarm triggering by specified target types (human and vehicle)) Scene change detection Linkage: Upload to NAS/memory card/FTP, notify surveillance center, trigger recording, trigger capture, send email Deep Learning Function Face Capture: Yes General Power: 12 VDC ± 25%, 0.5 A, max. 6.0 W, Ø5.5 mm coaxial power plug PoE: 802.3af, Class 3, 36 V to 57 V, 0.25 A to 0.15 A, max. 7.5 W Dimension: 215.2 mm × 78.8 mm × 78.6 mm (8.5" × 3.1" × 3.1") Package Dimension: 315 mm × 137 mm × 141 mm (12.4" × 5.4" × 5.6") Approx. 680 g (1.5 lb.): With Package Weight: Approx. 1000 g (2.2 lb.) Storage Conditions: -30 °C to 60 °C (-22 °F to 140 °F). Humidity 95% or less (non-condensing) Startup And Operating Conditions: -30 °C to 60 °C (-22 °F to 140 °F). Humidity 95% or less (non-condensing) Language: 33 languages English, Russian, Estonian, Bulgarian, Hungarian, Greek, German, Italian, Czech, Slovak, French, Polish, Dutch, Portuguese, Spanish, Romanian, Danish, Swedish, Norwegian, Finnish, Croatian, Slovenian, Serbian, Turkish, Korean, Traditional Chinese, Thai, Vietnamese, Japanese, Latvian, Lithuanian, Portuguese (Brazil), Ukrainian General Function: Anti-flicker, heartbeat, mirror, privacy mask, flash log, password reset via email, pixel counter Approval EMC: FCC SDoC (47 CFR Part 15, Subpart B); CE-EMC (EN 55032: 2015, EN 61000-3-2: 2014, EN 61000-3-3: 2013, EN 50130-4: 2011 +A1: 2014); RCM (AS/NZS CISPR 32: 2015); IC (ICES-003: Issue 6, 2016);KC (KN 32: 2015, KN 35: 2015) Safety: UL (UL 60950-1); CB (IEC 60950-1:2005 + Am 1:2009 + Am 2:2013, IEC 62368-1:2014); CE-LVD (EN 60950-1:2005 + Am 1:2009 + Am 2:2013, IEC 62368-1:2014); BIS (IS 13252(Part 1):2010+A1:2013+A2:2015); LOA (IEC/EN 60950-1) Environment: CE-RoHS (2011/65/EU); WEEE (2012/19/EU); Reach (Regulation (EC) No 1907/2006) Protection: IP67 (IEC 60529-2013)
1 note
·
View note
Text
DOWNLOAD 945PLM S2 DRIVER
Downloads: 3221 File Version: 812131665 Date Added: 07 December, 2019 Download Type: http Uploader: Uber Operating Systems: Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X Price: Free File Format: exe File Size: 23 Mb File Name: 945plm s2 driver

News: - Fixed “Test(945plm s2 driver “Test) FTP” and “Test Email” Button Errors 8. - Fixed(945plm s2 driver Fixed) LED behavior when disable wifi. - Fixed an issue that caused the(945plm s2 driver the) DDNS status to always show “Please Wait” in the web-based management interface of the router. - Fixed(945plm s2 driver Fixed) an issue where the system sometimes hangs on POST code 2A. - Fixes sometimes will BSOD 0xD1 when enable computrace in Windows XP. - AMD A8-7410 Fire-kernet 2,20 GHz - 43,9 cm (17,3") HD+ (1600 x 900) 16:9 CineCrystal - 8 GB, DDR3L SDRAM - 500 GB HDD- Fixed acer logo disappeared. - Fixed the bug whereby Sierra 3G modem cannot be disconnected. - Fixed(945plm s2 driver Fixed) the camera setting static IP via Web UI setup wizard does not apply problem. - Fixed issue in which System Setup displays the wrong capacityfor hard disk drives larger than 65GB. - Fixed the IP camera name and label name have a lot of special characters problems. Users content: Update agent to 2.0.19b51Problems Fixed:1. Cherry PS2 keyboard should be working correctly. System Settings -> Administrator -> Local Management -> System Identifier. Corrected null pointer access and domain indexing issue in pop3 processing. Support new Atheros combo card. Radeon Software Install may experience an error and fail to detect AMD graphics hardware when a certain WiFi adapter is enabled in the system. Using music slideshow did not work properly It is highly recommended to always use the most recent driver version available. Expansion Slots1 x PCI Express x16 slot, running at x16(The PCIEX16 slot conforms to PCI Express 3.0 standard. Supports Win2000 CD bootable function. Supports Microsoft Windows XP Media Center Edition. Click and download DOWNLOAD BROADCOM 570X GIGABIT WINDOWS 7 DRIVER. Supported OS: Microsoft Windows 8 (32-bit) Windows Server 2003 64-bit Windows XP 32-bit Microsoft Windows 8.1 Pro (64-bit) Windows 8.1 Windows 8 Windows Vista 32-bit Windows Server 2008 Windows 8.1/8/7/Vista 32-bit Microsoft Windows 10 (64-bit) Windows Server 2012 R2 Windows Server 2003 32-bit Windows 10 Notebook 8.1/8/7 64-bit Microsoft Windows 8.1 (32-bit) Microsoft Windows 8 Pro (32-bit) Windows Vista 64-bit Windows 7 Windows Server 2012 Windows 7 64-bit Windows XP 64-bit Microsoft Windows 8 Enterprise (64-bit) Windows 2000 Windows Server 2008 R2 Windows 7 32-bit Microsoft Windows 8.1 Pro (32-bit) Microsoft Windows 8.1 Enterprise (32-bit) Microsoft Windows 8 Pro (64-bit) Microsoft Windows 8.1 Enterprise (64-bit) Notebook 8.1/8/7 32-bit Windows 8.1/8/7/Vista 64-bit Microsoft Windows 8 Enterprise (32-bit) Windows Server 2016 Microsoft Windows 10 (32-bit) Microsoft Windows 8 (64-bit) Microsoft Windows 8.1 (64-bit) Searches: 945plm s2 driver for Windows XP 32-bit; 945plm s2 NR3791; 945plm s2 driver for Windows Server 2008; 945plm s2 NRKUV3791; 945plm s2 driver for Microsoft Windows 8.1 Pro (64-bit); 945plm s2 driver for Windows 7 32-bit; 945plm s2 N37n; 945plm s2 Nni379-nil; 945plm driver s2; 945plm s2 driver for Windows Server 2008 R2; 945plm s2 N NR379-3 Compatible Devices: Hardware; Apple; Video Projector; Printer; Wifi router; Ipod To ensure the integrity of your download, please verify the checksum value. MD5: 6565043eb9a56e0b7b6d73d111457027 SHA1: d267e129427d076de6d648f755cbe48bb740eb81 SHA-256: bf5ed3407f5469491ce8048ef906633e189f9dd7d9c2ced9a13ce8b2324c877a
1 note
·
View note
Text
DOWNLOAD NETGEAR 108 MBPS WIRELESS PC CARD WG511T DRIVER
Download Type: http File Format: exe Price: Free Downloads: 9824 File Name: netgear 108 mbps wireless pc card wg511t driver File Version: 710121476 Operating Systems: Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X Date Added: 17 October, 2019 Uploader: Minty File Size: 23 Mb

News: - Fixed the system can not detect HDD when PT80 PCI Display Card plugged. - Fixed a bug where changing recycle bin settings took a long time. - Buffalo Replication]: Fixed a bug where replication didn’t resume after a replication error resolved. - Backup]: Fixed a bug where Settings could(netgear 108 mbps wireless pc card wg511t driver could) not be accessed. - Fixed the Network Time Protocol daemon(ntpd) vulnerabilities(netgear 108 mbps wireless pc card wg511t driver vulnerabilities) issue 3. - Fixed some PCI wireless card incompatible issue. - Fixed legacy(netgear 108 mbps wireless pc card wg511t driver legacy) acknowledgment modeInstallation Instructions. - Flickering may be observed in Rise of the Tomb Raider on some AMD Crossfire configurations using the DirectX11 API. - P5P800-VM(netgear 108 mbps wireless pc card wg511t driver P5P800-VM) BIOS 0701Fixed the issue that the system can't boot from usb flash when usb card reader is plugged in. - Fixed a(netgear 108 mbps wireless pc card wg511t driver a) bug where the spare drive appeared as "Unknown Drive" in the notification email. Users content: Enter the FTP server address in the area provided, then press Enter at the bottom of the virtual keypad. Double-click the new icon on the desktop labeled AMD_RADEON-HD4350--512MB-_A04_R231622.exe. Resolved an issue in the Web GUI that allowed a user to enter and save an invalid character string in the Syslog Server field. Modify HDD size information under BIOS. Improve POST time by removing redundant modules. Display corruption may be observed while changing video resolution/ settings while playing a video clip using Windows Media Center. Improves Turbo boost performance. DO NOT power off the camera after every upgrade, please wait till the camera IP reappear in the IP Camera Tool. OpenCL applications may run initially on integrated graphics if they are present. * Based on the official Catalyst 4.9 drivers. Open the link if you need the DOWNLOAD MAGICSIM 9.0 DRIVER. Supported OS: Microsoft Windows 8 Enterprise (32-bit) Microsoft Windows 8.1 (32-bit) Windows Server 2012 Windows 8.1 Windows Server 2008 Windows 2000 Windows Server 2008 R2 Notebook 8.1/8/7 32-bit Windows Server 2012 R2 Microsoft Windows 10 (64-bit) Windows 7 32-bit Windows 7 Windows Server 2003 32-bit Windows 7 64-bit Windows 8.1/8/7/Vista 32-bit Microsoft Windows 8.1 Pro (64-bit) Windows XP 64-bit Windows Server 2003 64-bit Microsoft Windows 8.1 (64-bit) Windows Server 2016 Notebook 8.1/8/7 64-bit Microsoft Windows 8.1 Enterprise (64-bit) Windows Vista 64-bit Windows XP 32-bit Microsoft Windows 8 Pro (64-bit) Windows Vista 32-bit Microsoft Windows 8 Enterprise (64-bit) Microsoft Windows 8.1 Enterprise (32-bit) Microsoft Windows 8 (32-bit) Windows 8.1/8/7/Vista 64-bit Microsoft Windows 8 (64-bit) Windows 8 Microsoft Windows 8 Pro (32-bit) Microsoft Windows 8.1 Pro (32-bit) Microsoft Windows 10 (32-bit) Windows 10 Searches: netgear 108 mbps wireless pc card wg511t CZLNG4863; netgear 108 mbps wireless pc card wg511t driver for Microsoft Windows 10 (32-bit); netgear 108 mbps wireless pc card wg511t driver for Notebook 8.1/8/7 64-bit; netgear 108 mbps wireless pc card wg511t driver for Windows 7 64-bit; netgear driver 108 wireless mbps card wg511t pc; netgear 108 mbps wireless pc card wg511t C CZ486-4; netgear 108 mbps wireless pc card wg511t driver for Windows XP 32-bit; netgear 108 mbps wireless pc card wg511t CZ4863; netgear 108 mbps wireless pc card wg511t Czp486-zpx; netgear 108 mbps wireless pc card wg511t driver for Microsoft Windows 8 Enterprise (64-bit); netgear 108 mbps wireless pc card wg511t C48z Compatible Devices: Wifi adapter; Soundcard; Keyboards; Videocard; Samsung; USB Hubs To ensure the integrity of your download, please verify the checksum value. MD5: 881124fbabe5673f6d44192ed0c4753d SHA1: c6285488eb30a902a4844f75b79b2e74653498ad SHA-256: 099937dbc743f937b6409d646be8ea59334c378f9ed3662e70bf4d039c7f229d
1 note
·
View note