#gmail hacking software
Explore tagged Tumblr posts
Text
guys I got mega mega hacked yesterday with remote control software. I suspect it piggybacked onto my computer from some video game mods I downloaded this summer, but my brother-in-law suggested it may have been lurking since I bought my laptop as a refurb from BestBuy over a year ago. The person was able to access both my emails and set up filters to hide the email alerts, my amazon, and make a third party charge with my credit card. Because they were using remote-desktop, I wasn't getting alerts about unuathorized sign ins, and they were able to skip 2FA phone alerts anywhere that email was supported for 2FA. Based on the filters they set, I do know they had 3 purchases planning and I interrupted before they completed the third (amazon, antonline, and pixel.)
I got a credit card text alert for the $1500 antonline order but thought it was spam, so I went to my computer to log in and check whether the alert was real, then watched with shock that someone had my secondary email open and was typing in a 2FA code and I had no control of the cursor. I immediately turned off my computer and used a different computer to go in and change passwords, flag fraud charges, lock down accounts and freeze my credit cards. After a period of time passed, we turned the other laptop back on and began running scans --we found remote desktop hackware, and 4 other "Severe" threat programs after running every type of in-depth scan possible. I spent the whole night changing every password and deleting old accounts and confirming 2FA to my phone specifically.
I had a home burglary years ago that caused lasting emotional trauma which this elbowed again. The fraud charges suck but it's the impact on my kids and the invasive feeling that sucks even more. Changing amazon email/password broke my kids' accounts on their tablets and the refresh wipes over a year of their game data, which is upsetting for them. There's the emotional stress of knowing these assholes had full unhibited access to my accounts but also to all my personal stuff --my writing, my family photos, my medical record logins. I know they don't care about those things but they where there.
If not for my husband telling me to check email filters, I would not have realized they accessed my gmail. Without the security checks, we would not have found the hackware and it would have kept happening without me understanding why.
Please use this as your universe reminder to review your passwords, run security scans on your computers, and make sure 2FA is set up for important accounts that cannot be bypassed if someone gets acess to your email. <3 <3 <3
22 notes
·
View notes
Text
Nihilus Rex 41: Throw to the Wolves
Nils lays low and spirals, then lays in plans to deal with Weasel. There are jokes about different hard drive organizations that various people I know have used. Beta-read and co-written by @canyouhearthelight. Nils also speaks to many people's favorite priest.
Nils
So, laying low.
It used to be so easy, but now that I was getting a taste of actual action, of actually impacting the world, of actually shaking the system up - it was so God. Damn. Boring.
Actually, I supposed, I should deal with the issue with the Fibbies. Weasel was still out there as a loose end I needed to tie off - though as I gave greater thought to it, I realized there was a glaring error in my previous plan. Yes, I could frame Weasel, but the downside was that my plan relied on him being found non-credible. While we’d been very careful to avoid making him credible, he would, at the very least, give the FBI our names in hope of mitigating his sentence. And I didn’t need any more Feds remembering we existed in the first place. One was enough.
We’d covered our tracks well, but we could very well get hit with conspiracy charges if they felt like being awful - worse if they felt like digging deep. No, our best bet was to make sure Weasel went down for something else entirely, something that would lead to him self-eliminating, and then breadcrumbing the feds to pin the crime on a dead man and declare victory in our time. Any chance he’d be alive to talk was too great a risk.
How to do it though? Weasel was a massive creep, but he tried to avoid being outed as a massive creep. Leaking his porn habits might do it, but it didn’t actually get him arrested unless he was much, much worse than I thought. Now, maybe he was doing shady spyware shit I could check into - I was always afraid he was going to hack someone’s webcam, but...hm.
Actually, let’s see if we could get him on something he was actually doing.
I opened my computer up again and tried to log into one of Weasel’s socials. Social predictability, what was he going to be into? Character requirements for this system, what do we have…okay. PopgoestheWeasel69!.
The fact that that worked was…annoying. To say the least. One of the best icebreakers in the business and he was this bad at securing his basic stuff .�� Well, okay. If I hadn’t known who he was, there was probably no way I’d have been able to break his encryptions. However, social engineering was a technique all its own. Now, to see the contents of Google Drive….
Nothing to see here but a lot of essays. Actually decently well written ones, and a few that have. Reasonably good politics. Huh. Go figure. Seething hatred of tech bros and rudimentary AI, and pretty good predictions regarding the efficiency of combined solar/nuclear energy.
Right, he was a math whiz, I’d forgotten that.
I took a breath. Okay, so somewhere here there’d be a backdoor…Uh…lesseee. No, but I could find an email attached to his resume, which was good enough. Generate a very realistic looking phishing email. Odds are good he won’t actually click the link in it once he reads it through, but he doesn’t need to. He just needs to open it.
Subject: Research Grant Application Cal Poly
Dear Mr. Winston, you have been selected to apply for a grant of five thousand dollars for research and development of software from the San Luis Obispo California Polytechnic Institute through our partners on your campus. Please follow the link below to complete the application.
Dean of Computer Science, Cal Poly San Luis Obispo.
Faking a trail and even an impersonated gmail he couldn’t check on site was easy, and just to sweeten the pot I ran a few dozen searches of San Luis Obispo through his google account, so he could be treated to the sight of California women on beaches showing up in search functions fed by the algorithm. Let him ponder enjoying the famous lack of modesty the California climate allowed to make it as tempting as possible to open, in contrast to remaining here with the winter-mandated modesty enjoyed by the women of the Pacific Northwest.
“California girls, we’re undeniable…” I sing-songed in a falsetto I was glad no one could hear. “Tempting to in-cel douche-bags.” That was probably off beat. Fuck. I had a suspicion most other people could have done it better. Note to self, not that I was considering it anyway but no musical numbers at any point in the grandiose Nihilus Rex persona. At most, dramatic reads of Ozymandias or some shit. Things I could do.
With that attended, I leaned back and waited. I considered calling Lash, and then stopped. I should…probably give her some space. She’d be pissed if I kept poking her, and apparently my last hunch about her emotional state had been wrong. Jumping to conclusions based on incomplete information - she’d broken down at the hospital, she’d thrown up after the initial retaliation, but clearly if she’d been in communication with Ayanti, she hadn’t just been falling apart.
Still, it was easier to just handle Weasel myself. Fewer communications involved meant fewer people on the line if it went sideways, and clearly Ayanti had more trust in Lash than me. So, for now, the obvious tactical choice was for me to do the dirty work and her to make the world a bit brighter. Maybe we’d swap that role later, but for the time being this made sense. And unlike last time, it wasn’t like I felt like I was being forced to do it today.
I leaned back and looked at the situation, picked up a book and started reading. I had been getting behind on homework late…
Wow. He had already clicked the link. Alright, malware packet in, let’s open you up, Winston. See what goodies you have in your computer. Folder organization. Okay. Files, homework, software, projects, art…art?
That was probably - nope, nope. It was not porn, surprisingly. Good for him. I was learning an awful lot about Winston today. What about…ah. There we go. I should have just scrolled the rest of the way. “Fun Times” - in that, three subfolders. A Pocket flash player, an emulator…and Magical Realm.
Really man, that meme? I sighed. Fuckin’...
Oh….Oh that was a lot of porn. Okay, so. Let’s see, had he, in any way, organized it?
Let’s…had he labelled…I hate it when people do this. There was a correct way to organize porn, and I’d been using it before I started getting laid often enough that I’d stopped needing it. I’d kept it in a folder that simply said “porn.” And in it? Subfolders. Subfolders that said “animated” - “kinky shit” - “sweet couple stuff.” Why? Simple. Perfect. But did Weasel do this? No, instead Winston was a weird, messy bitch who just liked the Netflix version of endless scrolling while horny and trying to find something to jerk it to because everything here was alphanumeric and no organizational scheme. Just. Absolute goddamn degenerate behavior.
Idly, I wondered if I’d have been better off waiting to do this until Lash and I were on better terms, then I remembered that this was Weasel and I refused to be turned on by anything he was into.
***
Almost three hours of scrolling later, I had managed to find eight instances of things definitely taken from compromised webcams, and two instances where I was reasonably suspicious that one of the performers was not of legal age. That was a lot of sex crimes for one incel. I forced myself to acknowledge that, as disgusting as Weasel was, and how little time he spent with real women, there were about even odds he legitimately didn’t realize that he’d committed the latter two. Not that it mattered.
I dropped in a slight malware packet that would flag him for the FBI and then leak his download history very publicly, see what that got him. When he realized what had been compromised, he’d probably panic, but it didn’t matter. Once you were flagged, certain files were frozen - and I’d already saved backups of his entire porn folder deep, deep in his C-drive.
Ugh, why had that sounded dirty in my head? Too much time looking at Weasel’s crap, probably.
I disengaged from the hack and called Bishop. “Bishop. Anything interesting?”
“Eh…got a few people in the net looking for answers we may be able to ring in for them. Trade for favors later, maybe recruit some of them. Also, Gray wants to talk to you about a bigger project a little later?”
“Thank you. I’ll deal with Gray. Who are the others?”
“Tracking that down. It’s more my speciality than yours, pretty sure. I’m talking to my contacts in Eastern Europe, as well.”
“Understood. Thank you.” I sat back down, thinking about the risks. The FBI were still combing through the financial sector, and I wanted to look at the boards that Grey kept wound up. Some people were claiming that the original attack on the bank had been inspired or planned by some computer loving virgin, but most people there weren’t going for it. Then my phone started ringing.
My personal phone, for being Nils. I snapped it up and said, “Andover.”
“Nils.” The voice on the other end was one I knew well, one I’d been familiar with.
“Father Rivera. To what do I owe the pleasure?”
“I was contacted through backchannels in the Catholic Church for priests to communicate with each other. I was told that an orphanage the Mother Church runs in El Salvador is being given thousands of dollars worth of supplies by a mysterious benefactor, fluent in Latin but not Spanish - and that they were told by this mysterious benefactor that I would be able to reach him if they thought of anything else. Now, there is only one person on the planet that I can think of who might be doing something like that. So, Nils. Where is the money coming from?”
“Does it matter? Hungry kids are being fed, babies are being kept in diapers, sick kids are getting medicine and shots to keep from getting sick again.”
“Nils…” His voice took on a warning note.
“It’s coming from corporations who can afford it. No, I do not repent. You can turn me in but you’ll be cutting a lifeline for vulnerable people if you do. There are hundreds, if not thousands, of people that my scheming supplies with lifesaving things they cannot get through ‘better’ means. Please, Father Rivera. Leave me to my work.” My answer, and the quiet, desperate truth of it, must have convinced him of something.
He sighed heavily on the other end of the phone. “I want to speak with you directly, Nils. Soon. But for today, they say they’re worried about damage to their well, so they want water filters.”
I let out a bitter laugh. “Of all the things…yeah, I can do it. Tell them I hope the well will last a bit longer, because that’s a…harder ask than it really should be, right now.”
Rivera’s voice grew strained. “Do I want to know?”
“No, probably not.”
I took a breath. Rivera knew. That was a mistake. I could speak to him about other things weighing on me in the future. Other plans I’d laid. In the meantime, I’d wait for the plans with Weasel to bear fruit.
Hopefully the plan with Ayanati was going well for Lash.
#writeblr#writers on tumblr#original fiction#my writing#cyberpunk dystopia#modern dystopia#traumatized characters#Arcadian Inquisition prequel#Miys Prequel#Nihilus Rex
2 notes
·
View notes
Text
Considering what google has done with search and gmail, I think they want people to get hacked and viruses and hurt. I think they have some long term malicious goal that pivots on making the internet a special kind of hell.
Perhaps a portal system where everything you do goes through google under the guise that google is the middleman between you and harm. But to do that, they have to make the internet much more harmful, they have to get adblockers and third-party safety features out of the way. I imagine that after adblockers, they will probably start going after antivirus software - youtube won't work if you have any sort of anitvirus or firewall system.
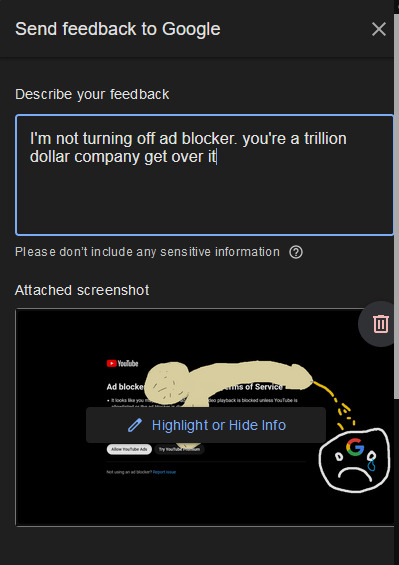
173K notes
·
View notes
Text
Passwords hashing is used to secure passwords. Hashing is a common technique across various software and tools. Hashing is used as a security mechanism for preventing plain text information known to others. It's mathematically impossible to calculate a plain text for Hash since hashing is a one-way process. Still, there are different ways exist that can crack the hash and retrieve your password or other sensitive information that may have been hashed. Hashing technique is mostly applicable to protect password like information since its a one-way process. You may also want to check out - how to learn hacking and cracking. This is a simple tutorial that will explain how hash cracking works. Why Password Hashing Is Considered Secure Hashing is a one-way process. This guarantees that the hash of a plain text value can be generated however the process can not be reversed. Most software and websites use this way to store password since the user knows the password. Whenever they need to authenticate the user, they generate the hash of user input and match it with a stored password. This mechanism guarantees that even the software provider themselves do not know your password. However, there are hacking and cracking tools as well as other techniques described below that may be able to find out your password from a hash. Today we will learn about Cracking the Hashes using CPU and GPU. CPU: Central Processing Unit GPU: Graphical Processing Unit We will cover: What is a Hash? What is the need for a Hash? Why Hash over Encryption or Encoding? Hardware configuration Tools required Hash cracking [CPU] Hash cracking [GPU] Hash cracking using Search engine Why such a difference? What Is A Hash? A. A Cryptographic function that converts a data or file of arbitrary length or size to a fixed length, which is considered practically impossible to invert. see Wikipedia What Is The Need Of A Hash? A major use of Hash is in the security field. To provide security or privacy to the user who is using any service of a company. For example, You are using Gmail, Facebook, Twitter, eBay, Amazon or Online payment portals like Paypal. Where you use the service by providing your credentials(username/password) There are basically 2 reasons: Making it difficult for hackers to recover/retrieve Password, Online service(Gmail,eBay, etc) or even Wi-Fi. Checking for the file verification. see SHA1 here Even If a company’s security is breached (Hacked), then also the user’s credentials are safe(only if you use a strong password) Why Hash Over Encryption And Encoding? Imagine a scenario, which perhaps happens to almost every Big banner, take it Google, Facebook, Yahoo! etc. A website is compromised and User’s data(credentials) is compromised. What is the thing that will make you worry when you come to know that if you are a registered user on that site? Yes! your Password (might be the master password, for all your accounts). Now, It is in service provider’s hand to provide security to their consumers. Hence, Hashing is the solution. How? well, you might be familiar with these terms: Encoding/Decoding Encrypt/Decrypt and now, Hashing Not going into the details, I will tell you a basic and most important feature of Hash which makes Hash much different and important over Encoding and Decoding. and that is : Encoded text/file can be Decoded, Encrypted text/file can be Decrypted, But hashed text/file can never be De-hashed. Yes, Hash, unlike Encryption/Encoding, is a One-way process i.e when a text/file goes through the Cryptographic hash function, it is converted into a fixed character length. Example: md5 type hash has a character length of 32, where SHA1 has a character length of 40. If we hash a string, say “test123″, md5 and SHA1 hash for “test123″ will be md5(“test123″) : CC03E747A6AFBBCBF8BE7668ACFEBEE5 SHA1(“test123″) : 7288EDD0FC3FFCBE93A0CF06E3568E28521687BC Length differs from md2, md4 to SHA256, SHA512 and so on.
Hashing your Wi-Fi password is also secured using a hash function named PBKDF2(Password-Based Key Derivation Function) Hardware Configuration Hardware used in this tutorial: Laptop with 4 GB RAM Nvidia Graphic card 1 GB Tools Required Software used in this tutorial: Windows 8, 32-bit Cain & Abel (CPU based cracker). igHashGPU (GPU based cracker), download here Nvidia graphics driver, for igHashGPU, download here Hash Cracking [CPU] Cain & abel is a multi-purpose tool. It is used for various purpose like Sniffing Hash calculating Hash recovery(this tutorial) ARP spoofing WiFi hacking, using hardware called AirPcap and so on. We will take MD5(Message Digest 5) cracking as an example to keep it simple and easy to understand. Install Cain & abel, then follow the instruction along, step-by-step: Open Cain & abel Press Alt+C to open the Hash calculator Type in “test123” and hit [ENTER], here “test123″ is our test string You should see something similar, Here we got the MD5, and other Hash for string “test123″ i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5. select and copy the MD5 hash.
NOTE: Hashing is Case sensitive, Hash for “Test123” will be absolutely different. Click on Cracker tab, then select MD5 Hashes column in the left. then right click and select Add to list. Paste the copied MD5 hash and hit [ENTER] Now, Hash is added to list. Right click on hash and select Brute-Force attack Set max length to 7 and click Start, and you should see this
. Here I have set the Max length of the password to be 7 to just test the output of the tool, and cracking speed of the CPU.
See the Password/Second CPU is testing: 6.3M (approx) and the remaining time i.e total time which will take CPU to recover the original string is 3.5 hours. It is too lame to wait for 3.5 hours for a small string test123 of the length of 7 characters with no special characters. isn’t it? well, here comes the GPU cracking to put some speed in the process! Hash Cracking [GPU] igHashGPU is a password recovery tool specialized for ATI (RV) and nVidia (Cuda) based cards. It recovers password of hashes which are used over the internet(weak), example md4/md5/SHA1. Let's get started, We have the MD5 string for test123 i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5 Follow the instructions along, step-by-step: Download and extract igHashGPU. Go to folder Right click and edit the file “example.cmd“. It is the example file for testing GPU speed of recovering MD5 password. Paste the MD5 code in the file after h:
and it should look like this :
ighashgpu.exe /h:CC03E747A6AFBBCBF8BE7668ACFEBEE5 /t:md5 /c:sd /min:4 /max:7 Close file. Click save and yes. Select “Example.cmd” and hit [ENTER]. A command prompt window will open like this
. See the CURSPD(Current speed), ~50 Million. Nice! but not good, isn’t it? see the battery symbol in the lower right corner. The laptop is running on battery. See what happens when I plug in the charger, notice the clock and speed. WHOA! See the difference! from 50M to 195M passwords/second, isn’t it great ? from 6.3M pass/sec to 195M pass/sec. That’s a big Jump. What you think how long it would have taken to recover the Password ? Just 5 minutes and 53 seconds. See how much time we saved by using GPU. From 3+ hrs to just 5 minutes. isn’t it amazing? also see the average speed also, 62,847 Million passwords/second. CPU: ~3 hrs with 6M pass/sec
GPU: ~6 min with 195M pass/sec You might ask, Hey! can we crack this even faster? well, the answer is Yes you can(not always though). How? Hash Cracking Using Search Engine [Google] We had MD5 string copied, right? what you need to do is very simple. Just paste and search the MD5 string i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5 on Google. and you’re done! Notice the text string “test123” and the Hash. So simple to recover the string from MD5, no? Now see the time above, it took us to recover the original string. Just 0.31 seconds. not even a second. Wow! that’s great.
You might be thinking why such a difference? here’s the answer Why Such A Difference? The difference in the speed is due to the architecture of the 3. CPU: Uses 4 cores(Shared with system processes) at maximum, 8-cores in some cases. GPU: Used 96 cores (In this case). All the 96 cores(Parallel processing units) were 100% dedicated for the password recovery process unlike CPU, which was simultaneously handling the complete OS including background processes, GUI(mapping of pixels on screen), and many other processes. Even if the CPU stop handling those, then also it won’t match GPU’s performance. difference because of the #of cores i.e 96 vs. 4 or 8 Latest GPU’s that I have seen comes with more than 400 cores. It can take you more than a billion passwords/second to recover the MD5 hashed string. Google Don’t Crack The Hash. Yes!, Google doesn’t crack/recover the string. It sends a request for the specific Text input i.e the hash in our case, to all the servers, takes the response back and displays the result according to the page rank of the site. There are plenty of online crackers, which can be used to crack a variety of hashes. They search their Database for the hash you have entered. If the string of hash is already recovered by them, they will give it to you, else you have to pay to avail the service. An email is sent if the string has been recovered. So, what Google does is sending a request to all these servers and displaying you the result. Result of the hash already cracked. It certainly becomes the Top priority for hash cracking. Search google first, if you didn’t find the password, go for GPU cracking.
Still didn’t succeed? Try CloudCraker, crackStation, HashKiller You can google “Online hash cracker” for more results. Note: Cracking speed varies depending on factors like: GPU configuration, ATI graphics cards are the best for this task. Hash type, for SHA1 it will be even lesser and for WPA hash cracking it goes down to 4000 Pass/sec on my graphics card. see this list. My card’s performance is near to GeForce 8800 GTS (CUDA) Interested in WPA cracking, or WiFi pentesting? Follow my WiFi Security and Pentesting Series Hope you found this tutorial helpful. Let me know in the comment section. Thanks! This article is contributed by Hardeep Singh (Facebook | Twitter). Hardeep is a guest author and Full-time Blogger @ rootsh3ll.com, Security person, Penetration, tester, Linux and python Lover. Loves to share knowledge with everyone. Updated On June 2019: Fixed Broken links and updated minor typos.
0 notes
Text
Suggerimenti avanzati per rafforzare la sicurezza di Gmail
Se desideri portare la sicurezza del tuo account Gmail a un livello superiore, esistono strategie avanzate che possono aiutarti a rafforzare ulteriormente la tua protezione online. Di seguito ne presentiamo alcuni tra i più efficaci.
Innanzitutto, si consiglia di abilitare l'autenticazione con una chiave di sicurezza fisica. Questa opzione è disponibile nelle impostazioni di sicurezza di Google e fornisce un ulteriore livello di protezione contro attacchi di phishing e hacking.
Un'altra strategia efficace consiste nel rivedere e gestire le autorizzazioni di accesso per le applicazioni di terze parti. Nella sezione sicurezza del tuo account Google, puoi vedere quali app hanno accesso al tuo account Gmail. Se rilevi un'applicazione sospetta o che non utilizzi più, revocane immediatamente l'accesso.
Inoltre, è importante attivare gli avvisi di sicurezza. Gmail e Google offrono notifiche ogni volta che vengono rilevate attività sospette sul tuo account, come tentativi di accesso da posizioni insolite. Mantieni attivi questi avvisi per agire rapidamente in caso di tentativo di intrusione.
Puoi anche utilizzare un gestore di password affidabile per archiviare e generare password complesse. Ciò ti consentirà di mantenere un accesso più sicuro senza la necessità di ricordare più password complesse.
Infine, assicurati di aggiornare costantemente il tuo sistema operativo e il tuo browser. Molte vulnerabilità della sicurezza si verificano a causa di versioni obsolete del software, rendendo più facili gli attacchi informatici.
Seguendo questi suggerimenti avanzati, otterrai una solida protezione per il tuo account Gmail, riducendo al minimo i rischi e garantendo la tua privacy online.

0 notes
Text
Trusted Gmail Backup Tool
DevopixTech Software Solutions offers a reliable Gmail backup tool that ensures your valuable emails and attachments are securely stored. With easy-to-use features and fast backup speeds, you can protect your data from accidental loss, hacking, or server issues. Trust DevopixTech for seamless, efficient Gmail backups that keep your information safe. Contact us: +91-7827275804
0 notes
Text
Best solution to restore Apple email
Don’t look any further for a solution to restore Apple email
Maybe you have never felt the need to restore data. But you keep hearing the experts telling you to archive email data and keep ready for restore if need be. You cannot ignore this advice as it is extremely valid and important. Archiving emails and backing up data regularly is what any wise person will do because we know how data is so prone to damage or hacking or other kind of losses. This is especially true when original messages don’t get stored in device like the case with IMAP based services. You will need to restore Apple email in a case you lose data due to any reason like hardware failure or some other. You will be able to restore only if you have backed it up or archived email folders. Else, you will not be able to do anything. You need a good backup and recovery option for this. Although we will be focusing on a method which covers all IMAP based email services like Gmail, Thunderbird, Yahoo, etc., you can read a little about Apple email to get a fair idea why we must backup emails. Here is the link- https://en.wikipedia.org/wiki/Apple_Mail
Best way to restore Apple email is with a certified software

There are a few methods available to backup as well as restore Apple mails and other on Mac. Yet, you see experts recommending only certified tools. Why is it so? Why don’t they recommend a manual method or maybe restore Apple email app which works online? There must be some factor behind it. While manual methods are never recommended for any similar task which is to be done regularly, they also pose a great challenge to novices. And when we talk of online apps, they are fraught with dangers like data loss, data stealth, corruption, etc. Along with these risks, there is almost zero support available for any doubts or mishaps. This means we shouldn’t be using these apps. We should only use a reliable certified archiving and restoring tool like Mail backup X by InventPure. This is the best one out there for end users.
Now restore Apple email account and other multiple accounts in a short, precise, and easy way
This tool makes it really easy, quick, as well as accurate to backup and restore IMAP emails on Mac. There is something else also which we need to look at. If I am in a need of a software, and I have heard good things about it, even then it would be normal for my mind to have some doubts. All users face these doubts and thus this issue must be settled. This issue is settled by bringing to users a free albeit a limited use demo of this backup tool so that their doubts are settled. They can use most of the important functions that the full restore Apple email tool comes with and once satisfied, they can purchase full version for daily data preservation in the manner they prefer https://www.mailbackupx.com/restore-apple-email/.
1 note
·
View note
Text
youtube
how to find gmail password,password with keke palmer,chelsea handler password password,wifi password hacker, wifi password hacker app,password hacking,how to hack wifi password,hack wifi password,how to hack a password, wifi hacking password,password cracking,how to hack wifi without password,wifi password,hacker, wifi password change,windows password hacking,password hash,how to crack wifi password,1password, passwords,how to connect wifi without password,password tips,password hacking kali,how to hack password, reset windows 10 password,password reset,password,forgot password,remove password on windows 10, how to reset forgotten password in windows 10,how to reset windows 10 password,reset windows 11 password, reset windows 10 password without cd or software,reset windows 10 password with cmd,windows 10 password reset, reset windows 11 password command prompt,reset windows 10 password without losing data, how to reset password on windows 10,windows 11 password,facebook password,facebook password change, how to recover facebook password,show facebook password,facebook password reset,how to see facebook password, how to change facebook password,facebook ka password kaise pata kare,facebook,i forgot my facebook password, how to find facebook password,how to reset facebook password,how to see facebook password in mobile, forgot facebook password,facebook forgot password,facebook password kaise pata kare,gmail password, change gmail password,how to change gmail password,reset gmail password,gmail password change, password,how to reset gmail password,change gmail password on android,gmail password change kaise kare, how to change password in gmail,gmail password change in mobile,forgot gmail password, gmail ka password kaise change kare,gmail ka password bhul jane par kya kare,gmail id password change, change gmail password in mobile,gmail account password change
0 notes
Text
Secret in Cellphones hacking
I found Thomas on truthspy website referring to how he helped people spy on their partner's phone. I need help also to access my husband's phone, and to have access to view his phone and gps tracker. Within 24hours they gave me software that i can use in spying his phone without any traces, i can get to see all he has been hiding from me and have full access to his phone without getting close to him, you can get in touch with them via email at Tomcyberghost @ gmail com just tell him I refer you to him. He is a man with a heart of gold...
#information technology#technology#self help#studyspo#artificial intelligence#tech news#relationship quotes#inspiring quotes
0 notes
Text
Gmail Mastery 2024 Review – Ultimate Email Marketing Tools
Welcome to my Gmail Mastery 2024 Review Post. This is a real user-based Gmail Mastery 2024 review where I will focus on the features, upgrades, demo, pricing and bonus, how Gmail Mastery 2024 can help you, and my opinion. Start your journey to becoming a digital marketing royalty with Gmail Mastery 2024. Google and Yahoo have just redrawn the battlefield with their newest enhancements, which will take effect in February 2024.

>> Click Here to Get Gmail Mastery 2024 + My $20000 Special Bonus Bundle to Boost Up Your Earnings More Traffic, Leads & Commissions >>
Gmail Mastery 2024 Review: What Is It?
Gmail Mastery 2024 is an online course designed to transform your email experience. This online course, developed by Andrew Darius, delves deep into Gmail’s features and functionalities, equipping you with the knowledge and skills to conquer your inbox and supercharge your productivity. Whether you’re drowning in emails or just seeking efficiency, this comprehensive program promises to unlock the hidden potential of Gmail.

Gmail Mastery 2024 Review: Overview
Creator: Andrew Darius
Product: Gmail Mastery 2024
Date Of Launch: 2024-Feb-06
Time Of Launch: 11:00 EST
Front-End Price: $17
Official Website: Click Here
Product Type: Software (Online)
Support: Effective Response
Discount : Get The Best Discount Right Now!
Recommended: Highly Recommended
Skill Level Required: All Levels
Coupon Code: “EM5OFF” $5 Discount
Refund: YES, 30 Days Money-Back Guarantee
Gmail Mastery 2024 Review: Key Features
Go beyond basics: Explore hidden gems like filters, labels, stars, and keyboard shortcuts to streamline your workflow.
Advanced search & filtering: Master complex search operators and filters to find specific emails instantly, eliminating information overload.
Email organization pro: Learn effective strategies for inbox management, including creating filing systems, prioritizing emails, and avoiding clutter.
Automation & time-saving hacks: Discover powerful tools and techniques to automate repetitive tasks, save time, and boost your overall efficiency.
Actionable steps: The course provides practical exercises and resources to help you implement the learnings immediately and see results quickly.
Interactive exercises & quizzes: Hands-on activities solidify your understanding and track your progress, ensuring you retain valuable knowledge.
Supportive community forum: Connect with other students and instructors for discussion, troubleshooting, and support, fostering a sense of community and shared learning.
Protect your data: Understand the importance of email security and learn best practices to safeguard your information and privacy.
Two-factor authentication & encryption: Explore advanced security measures to ensure your inbox remains protected from unauthorized access.
Data privacy awareness: Learn how to manage your email data responsibly and navigate privacy settings effectively.
Bonus Features:
Downloadable resources: Cheat sheets, templates, and other materials reinforce learning and offer practical application.
Regular updates: Stay ahead of the curve with ongoing course updates reflecting the latest Gmail features and best practices.
>> Click Here to Get Gmail Mastery 2024 + My $20000 Special Bonus Bundle to Boost Up Your Earnings More Traffic, Leads & Commissions >>
Gmail Mastery 2024 Review: What You Will Find

Gmail Mastery 2024 Review: Why You Choose It?
Insider Knowledge: Learn the secrets that others don’t even know exist.
Actionable Strategies: No fluff, no filler — just hard-hitting, effective tactics.
Exclusive Access: Join a community of forward-thinking marketers, share insights, and grow together.
Gmail Mastery 2024 Review: Who Should Use It?
Affiliate Marketers
Freelancers
CPA Marketers
Online Business Owners
Artists/Content Creators
Product Owner
E-Commerce Business Owners
Any Kind of Online Businesses
Gmail Mastery 2024 Review: OTO And Pricing
Front End Price: Gmail Mastery 2024 ($17)
OTO 1: Newsletter Launchpad 5 Day Challenge ($9)
OTO 2: Newsletter Launchpad 5 Day Challenge VIP ($47)
OTO 4: Newsletter Linchpin AI App Standard ($27)
OTO 5: Newsletter Linchpin AI App Premium (37)
OTO 6: Newsletter Linchpin AI Unlimited (97)
OTO 7: Newsletter Linchpin AI Lead Magnet Builder ($67)
OTO 8: Newsletter Linchpin AI Professional ($67)
OTO 9: Newsletter Linchpin AI Done-For-You ($297)
OTO 10: Newsletter Linchpin AI Ultimate ($297)
OTO 11: AIpreneur VIP Club ($00)
>> Click Here to Get Gmail Mastery 2024 + My $20000 Special Bonus Bundle to Boost Up Your Earnings More Traffic, Leads & Commissions >>
Gmail Mastery 2024 Review: Pros and Cons
Pros:
In-depth and comprehensive coverage of email management.
Actionable strategies and practical tools for immediate implementation.
Expert-led instruction with a knowledgeable and experienced instructor.
Flexible learning format suitable for busy schedules.
Supportive community for motivation and peer-to-peer learning.
Cons:
May not be suitable for complete beginners with no prior email experience.
The price might be a barrier for some users.
Reliance on self-discipline and motivation for successful implementation.
Gmail Mastery 2024 Review: My Special Bonus Bundle
Gmail Mastery 2024 Review: Money Back Guarantee
You Have NO RISK With��Our Official 30 Days Money Back Guarantee

>> Click Here to Get Gmail Mastery 2024 + My $20000 Special Bonus Bundle to Boost Up Your Earnings More Traffic, Leads & Commissions >>
Gmail Mastery 2024 Review: Free Bonuses
BONUS #1: ChatGPT YouTube Summarizer App (value $497)
Have you become bored of viewing lengthy YouTube videos when you might have read a summary? Rest assured, ChatGPT YouTube Summarizer is here! Using OpenAI’s ChatGPT AI technology, this app lets you quickly summarize any YouTube video. Improve your knowledge and save time with ChatGPT YouTube Summarizer!
BONUS #2: ChatGPT Traffic Siphon Genie (value $497)
Artificial intelligence fans! Tired of producing content yourself? No worries — we’ll wow you with the greatest content production hack. You can utilize ChatGPT and other covert AI technologies to create unique content without doing anything. So, you can relax and enjoy a fine drink while the AI does the job. Favourite part? Don’t worry about being filmed or recorded. Share your content goals with the AI and let it work. This strategy can be customized for any topic and drives tonnes of traffic to your website, lead magnets, leadono links, or affiliate links. Put the AI in charge and watch your content and traffic rocket!
BONUS #3: ChatGPT’s Prompt Seed Vault (value $497)
Get ready to create some seriously amazing content with ChatGPT! But remember, the quality of your content is only as good as the prompts you provide. That’s where the ChatGPT Prompt Seed Vault comes in — with 2880 rewritable input sentences in 288 super profitable niches, you’ll be sucking in traffic in no time!
BONUS #4: ChatGPT YouTube Title Master (value $297)
You can get 1,000 top-ranking, traffic-sucking YouTube title chatGPT prompt seeds from actual top-ranking videos! ChatGPT lets you create great multimedia to surprise the world! Remember, your prompts determine the quality of your article. So, play your best with ChatGPT YouTube Title Master!
BONUS #5: Mind Blowing “Act As” ChatGPT Prompts (value $297)
Did you know that ChatGPT is like the ultimate conversation machine? Just give it a little “Act As” prompt and it’ll come up with responses that’ll keep the chat going or give you even more info on what you asked it about. In this super-secret manifesto, there are all sorts of prompts that you can use with ChatGPT. Don’t tell anyone after you see them, okay? It’s a secret.
BONUS #6: The 7 AI Businesses to Start with Chat GPT (value $297)
Ready to jump on the AI bandwagon and start your own business? Look no further! In this training, we’ll explore 7 unique and innovative business ideas that you can start with the help of ChatGPT. These AI-powered businesses are guaranteed to make a splash in the world of entrepreneurship. Don’t miss out on this opportunity to get a head start in the exciting field of artificial intelligence. Discover the endless possibilities of ChatGPT and how it can help you launch the business of your dreams!
BONUS #7: 6 Fundamental Rules To Write YouTube Scripts with ChatGPT (Value $197)
Are you struggling to write engaging and effective scripts for your YouTube videos even when you use ChatGPT? Look no further! In this training, we’ll share the 6 fundamental rules for writing YouTube scripts with ChatGPT. From organizing your thoughts to optimizing for SEO, these tips will help you craft compelling scripts that will keep your viewers coming back for more. Whether you’re a seasoned content creator or just starting out, these guidelines are essential for creating high-quality videos that will stand the test of time. ChatGPT revolutionized the script writing process but only if you know those 6 fundamental rules!
Gmail Mastery 2024 Review: Conclusion
Gmail Mastery 2024 offers a comprehensive toolkit to transform your email experience. From mastering hidden features to implementing productivity hacks and conquering information overload, the course promises to empower you to take control of your inbox. Consider your budget, learning style, and specific needs to determine if this program is your key to unlocking email zen and supercharging your productivity. Remember, the journey to inbox mastery is ongoing, and Gmail Mastery 2024 can be your valuable guide along the way.
Frequently Asked Questions (FAQs)
Q. Who is this course for?
Gmail Mastery 2024 caters to both beginners overwhelmed by email clutter and experienced users seeking advanced organization and productivity hacks. Whether you’re a professional juggling multiple accounts or a casual user striving for efficiency, the course offers valuable insights for all.
Q. What will I learn?
Expect to delve into hidden Gmail features, master organization systems, discover automation tools, conquer advanced search and filtering, and understand email security best practices. The course goes beyond the basics, offering practical steps to transform your email experience.
Q. What format does the course take?
Engage with video lectures, downloadable resources, hands-on exercises, and a supportive community forum. The course provides a blend of learning styles to cater to diverse preferences and ensure knowledge retention.
Q. How much time will it take to complete?
The course duration depends on your pace and preferred depth of exploration. However, expect to dedicate several hours to video lectures, exercises, and community interaction to fully grasp the concepts and implement the learnings.
Q. Is there a guarantee or refund policy?
Course policies vary depending on the instructor and platform. Always check the official website or terms of service for details regarding guarantees, refunds, and trial periods before enrolling.
Q. What are some alternatives to Gmail Mastery 2024?
Explore other online courses, productivity resources, or email management apps to find the best fit for your needs and budget. Remember, the most important factor is finding a solution that resonates with your learning style and helps you achieve email mastery.
>> Click Here to Get Gmail Mastery 2024 + My $20000 Special Bonus Bundle to Boost Up Your Earnings More Traffic, Leads & Commissions >>
Thank for reading my Gmail Mastery 2024 Review till the end. Hope it will help you to make purchase decision perfectly.
Note: Yes, this is a paid software, however the one-time fee is $17 for lifetime
#Gmail Mastery 2024#Gmail Mastery 2024 Upgrades#Gmail Mastery 2024 Overview#Gmail Mastery 2024 Review#Gmail Mastery 2024 Features#Gmail Mastery 2024 Works#What Is Gmail Mastery 2024#Buy Gmail Mastery 2024#Gmail Mastery 2024 Price#Gmail Mastery 2024 Demo#Gmail Mastery 2024 Discount#Gmail Mastery 2024 Honest Review#Gmail Mastery 2024 Pricing#Gmail Mastery 2024 FE#Gmail Mastery 2024 Software Review#Gmail Mastery 2024 Pros#Gmail Mastery 2024 OTO#Gmail Mastery 2024 Preview#Gmail Mastery 2024 Scam#Gmail Mastery 2024 Software#Get Gmail Mastery 2024#Gmail Mastery 2024 Reviews#Purchase Gmail Mastery 2024#Gmail Mastery 2024 legal#Gmail Mastery 2024 By Andrew Darius#Artificial Intelligence#AI#Gmail Mastery 2024 Benefits#Gmail Mastery 2024 Bonus#Gmail Mastery 2024 Bonuses
0 notes
Quote
One of Team Jorge’s key services is a sophisticated software package, Advanced Impact Media Solutions, or Aims. It controls a vast army of thousands of fake social media profiles on Twitter, LinkedIn, Facebook, Telegram, Gmail, Instagram and YouTube. Some avatars even have Amazon accounts with credit cards, bitcoin wallets and Airbnb accounts. The consortium of journalists that investigated Team Jorge includes reporters from 30 outlets including Le Monde, Der Spiegel and El País. The project, part of a wider investigation into the disinformation industry, has been coordinated by Forbidden Stories, a French nonprofit whose mission is to pursue the work of assassinated, threatened or jailed reporters.
Revealed: the hacking and disinformation team meddling in elections | Technology | The Guardian
0 notes
Text
Internet security is a complicated thing to talk about. It is something both business owners and average users are concerned about. The more developers work on the security problems, the more hackers, and cybercriminals try to solve them. It is a vicious circle. But it doesn't mean you do not have to protect your private or business data even knowing that there is no such website or program which can't be hacked sometime. Statistics show that cybercriminals equally target both smaller and bigger businesses, making IT security the key to the company's stability and productivity. Serious cyber attacks are not chaotic or single. Usually, it is a set of programs, which target several companies in one industry at once. If you don't believe that the hackers can paralyze the work of the whole company, try not to use any program or service for the protection of your data. But we don't recommend even thinking about it. Of course, if you don't want to lose the amount of work you have already done and the money you have already earned. So, what can you do to prevent your business from being hacked by cybercriminals? The first and the most basic IT security step is getting the best FREE VPN service for your website and banking operations at least. The importance of VPN services results from their ability to encrypt the connection between your PC/laptop/smartphone and the Internet, which makes it invisible to hackers. But what else can you do to protect your personal and professional information? IT Security Solutions There are some differences between what average users and professionals do to protect their data from hacking. For example, average users consider antivirus software and strong passwords to be enough. While professional IT security experts consider installing software updates and using unique passwords to be far more important for your data. There are a lot of other critical things you probably do wrong when it comes to the security of your professional and personal information. So, let's have a look how it should be done correctly. Professional Tips on Internet Security First of all, let's mention one misunderstanding most Apple users have. "Apple can't be hacked. It's secure enough without an additional protection." That's not the truth. Even Apple products can be hacked. Not so easily as others but still they can be hacked. Apple is just doing a better job when it comes to security issues. And now we can officially skip to those basic steps you can do to protect your online business from being paralyzed by hackers. Use Two-factor authentication Two-factor authentication instead of changing your password every two months. This concerns most of your daily accounts like Gmail, Twitter, Facebook, Amazon, etc. Among all of these accounts, highlight your email account. As it is one the most important ones. If a hacker owns your email account, he'll probably own other services. He can reset all other passwords just using this email address. Two-factor authentication is something, which can prevent this from happening. Dealing with suspicious links Confirm suspicious links but do not click on them. This will show you where the link goes. Based on this you can decide whether to click on that link or not. And don't forget to check the sender's email address too. Backups Using a backup tool is a good starting point for any business when it comes to security. Having a good backup, which is not connected to your machine is very important. Try offline backups as one of the first steps while figuring out which security strategy is more suitable for you. Train your team A lot of cyber attacks happen because of the employees who click on the malicious links or websites. So, it would be a smart move to provide your employees with the key principles and rules of the company's IT security policy. Contact a security specialist Today, you have a choice between contacting a security specialist for any IT recommendations
on security issues or to hire a provider, which specializes in cybersecurity on a daily basis. It is a good outsourcing step, which gives you the ability to cover all online security gaps at once. This will save your time and money. Let IT specialists monitor the security of your business. Make a security review It is very useful to make a full security review of your passwords, access to them, backups, and testing every couple of months. Analyze the results you get and find out if your IT security system has any gaps. Consult an expert. This is what you can do to protect your business and personal data online. And what is your number one thing to protect the company on the Internet?
0 notes
Text
The case for native, offline capable apps
Exhibit #1 - Ever had the experience of trying to watch a movie or some tv show and it's no longe available on your streaming platform?
Exhibit #2 - How about that web app that went out of business and you lost all access and functionality. e.g. Google Reader just to point an innocent and harmless example?
Exhibit #3 - Are you ok when you try to access some service it because of reasons, it’s down?
I'm sure you either had one, two or all of these experiences happening to you.
This is just the current reality of computing in general, it's either streaming and subscription based, or the common Software as a Service modality. Either way, you have the freedom of choice, the freedom of using whatever device you want, but also the complete lack of control over what happens if for some reason, your provider ceases to exist, or, if any of the conditions of the current contract change.
There is a movement about combating this sort of thing, starting only on some intellectual fringe - AKA Geeks - that actually care about such things.
Disclosure: being a 47 old computer geek, you know where I'm coming. I was born with cassete tapes FFS. But even when the internet started to appear, it was just a way to ease the distribution of software that you ran and managed, on your own computer.
Skip a couple of decades later, yada, yada, yada, SaaS is king. You rent software, you rent music, you rent movies. There's no digital owning anymore. Anything you do is just within the bounds of a monthly subscription fee and while a lot of this makes sense from a ease of use and sometimes, even economically, it hides the truth about our lost of owning anything.
Even the phone or computer we use today is limited in what it can do, just look at iPads, you can only install whatever goes through the store, as we have all been deemed as incompetent to manage what runs on our own hardware.
You might guess where this is going to now... I'm in favor of apps, apps that we can freely install and keep to use, regardless of a company's business goes down, of if the internet has been hacked again and there's a fucking DoS on your service.
The internet was designed to be resilient to attacks and still keep going, but what you do have today is that all aspects of your life are in fact tied to specific services that rely on the internet working, and the company that owns your app paying the data center bills.
Thing is, we are now in the passenger seat.
If any of your service is not like an E-mail app,(not your Gmail), and by this I mean you have an IMAP client, you have your email with you. you can use it offline, and you can even change the servers it talks to, in case you move from provider.
See the diference? It uses the internet, but it is resilient to downtime, you own the app, you can use it whenever you want, and you're not tied to a single provider.
Thoughts? I'm going to be thinking about this in 2024.
0 notes
Text
Image to Data Entry Notepad RTX Conversion, Image to Notepad Plus Conversion, Image to Pixcel Notepad Conversion, Image to Text Conversion. All India Data Entry Type Work Solutions and Softwares. Call us at 7428811442 INTELLITECH DATA SERVICES
Image to Notepad Plus Conversion Software available .wrt Image to Pixcel Notepad Convertor available .nts. Bulk Text Encryptor (100% Non detection Gurantee) Don't use Any Autotyper on company Notepads because these notepads are highly encrypted and autotyper types fix keystrokes in non encrypted manner hence it is detected in company Quality Check. You have already been warned not to use any autotyper or third party program. Be safe use safe software.
Call us at 7418811442 @intellitechdataservices @intellitechdataservice Email:- intellitechdataservices@gmail. How to convert Image to Notepad Plus? How to convert Jpeg to Notepad Plus? How to copy paste text in Notepad Plus? How to edit text in Notepad Plus? How to save text in Notepad Plus? How to install Notepad Plus Software? How to transfer text in Notepad Plus? How to get text from Images? How to convert Image to typing? How to convert Image to Notepad? How to convert Images to Notepad? Notepad Plus Hacks Notepad Plus Tips Notepad Plus Tricks Notepad Plus Download Notepad Plus Install Notepad Plus 2023 NotepadPlus.exe Notebook.exe How to Convert Image to Wrt? How to Convert Jpg to Wrt? How to Convert JPEG to Wrt Wrt Convertor Software Notepad Plus Convertor Software Notepad Plus Conversion Software Notepad Plus Typer Notepad Plus Autotyper Notepad Plus Encryptor Notepad Plus All Hacks Notepad Plus Enable Copy Paste Option Notepad Plus India Notepad Plus Data Entry Notepad Plus Typing Notepad Plus Fast typing Notepad Plus Fast typer Notepad Plus Automatic Tying How to convert Image to Notepad Plus? How to convert Jpeg to Notepad Plus? How to copy paste text in Notepad Plus? How to edit text in Notepad Plus? How to save text in Notepad Plus? How to install Notepad Plus Software? How to transfer text in Notepad Plus? How to get text from Images? How to convert Image to typing? How to convert Image to Notepad? How to convert Images to Notepad? Notepad Plus Hacks Notepad Plus Tips Notepad Plus Tricks Notepad Plus Download Notepad Plus Install Notepad Plus 2023 NotepadPlus.exe Notebook.exe How to Convert Image to Wrt? How to Convert Jpg to Wrt? How to Convert JPEG to Wrt Wrt Convertor Software Notepad Plus Convertor Software Notepad Plus Conversion Software Notepad Plus Typer Notepad Plus Autotyper Notepad Plus Encryptor Notepad Plus All Hacks Notepad Plus Enable Copy Paste Option Notepad Plus India Notepad Plus Data Entry Notepad Plus Typing Notepad Plus Fast typing Notepad Plus Fast typer Notepad Plus Automatic Tying How to Install Notepad Plus on Windows 7? How to Install Notepad Plus on Windows 8? How to use Notepad Plus? How to check errors in Notepad Plus? How to find errors in Notepad Plus? Notepad Plus Error checking? Notepad Plus Qc Software How to Save text in Notepad Plus? Notepad Plus Free Software Notepad Plus free trick Notepad Plus free Autotyper Notepad Plus free Autotyping Software Notepad Plus free Download Notepad Plus free hack Notepad Plus Mod Notepad Plus Latest Mod
#notepadplus#pixcelnotepad#imagetotext#imagetonotepad#imagetonotepadconversion#dataentryimagetotext#dataentryimagetonotepad#ocr#imagetotextconvertor#imagetonotepadconvertor#autotyper#freeautotyper#freesoftware#software#pdftotext#pdftonotepadplus#StartTXT#Pixcel#pixelnotepad#imagetopixelnotepad
0 notes
Text
Sunsama Review: Best Daily Planner App?

Planning your daily work in a week’s advance can make your work and life easier, more productive, and more organized.
You can use a calendar app or task manager app or a daily planner app to plan your week.
One of the daily planner apps that seems to be best is Sunsama. Sunsama streamlines your work and helps you plan your tasks, appointments, and goals.
Let’s look at the Sunsama app to figure out the features, the price it offers, and how you can integrate Sunsama with other apps.
Subscribe to Productivity Side Newsletter to get useful productive hacks, tricks, and tips weekly.
What Is Sunsama?
Sunsama is a daily planner app that is designed to help people manage their tasks, events, and meetings effectively. Unlike any other to-do list apps, Sunsama focuses on organizing and planning your day with a structured interface.

Features Of Sunsama
Many features make Sunsama — a powerful daily planner app. Let’s look at some of the features of Sunsama.
Pull tasks and emails from different apps
Schedule all your tasks in the calendar with time-boxing
Drag and drop tasks from different task manager tools and project management tools including Asana, Notion, Todoist, Trello, GitHub, Jira, and ClickUp.
Automatically update tasks from different apps — Sunsama takes care of all of this.
Drag and drop all your emails from your email app like Gmail and Outlook
Pull messages from Slack
Sync your app with calendar apps like Google Calendar and Outlook
Focus mode for important tasks
Auto-schedule your tasks into a calendar
Analytics
There are the Sunsama features that work collectively with other apps and organize all your different work in one app.
Integrations
Integration into different project management and task app makes Sunsama, a powerful application, and daily planner. You can integrate with different apps and bring those app’s works into the Sunsama dashboard.

Todoist:
Todoist is a task management app that integrates with Sunsama to pull all the tasks that have been created on Todoist.
It pulls Todoist tasks into your daily plans
Pick the tasks you want to add from the side panel
Drag the Todoist task into the calendar.
Changes made in Sunsama automatically sync with Todoist.
ClickUp:
ClickUp is a project management app that also integrates with Sunsama to bring tasks and projects into Sunsama
Here are some integration features.
Get ClickUp tasks into the Sunsama dashboard
Pick the tasks you want to work on from the side panel.
Add tasks into Calednar directly by drag and drop from the panel.
Auto sync with changes done in Sunsama to ClickUp
Trello:
Trello is a Kanban-style project management app that integrates with Sunsama to bring tasks, projects, and boards created in Trello.
Here are some integration features.
Bring Trello cards into the Sunsama dashboard from the side panel
Pick the card you want to work on from the panel.
Drag and drop the cards directly into the calendar.
Changes made in Sunsama automatically sync with Trello.
Asana:
Asana is a project management app that also works with Sunsama to bring tasks and projects created in Asana into one app.
Here are some integration features.
Bring Asana tasks into the Sunsama dashboard
Pick the task you want to work on from the panel.
Drag and drop the task into the calendar.
Changes made in Sunsama automatically sync with Asana.
Notion:
Notion is an all-in-one workspace app that works with the Sunsama app to bring tasks, projects, and other files into the Sunsama app.
Here are some integration features.
Bring Notion tasks into the Sunsama dashboard
Pick the Notion task you want to work on from the panel.
Drag and drop the Notion task into the calendar.
Changes made in Sunsama automatically sync with Notion.
Jira:
Jira is a bug tracking tool that allows software developers to plan and track their work. It also works with Sunsama to bring the issues into the app.
Here are some integration features.
Bring the Jira issue into the Sunsama dashboard
Pick the Jira issues you want to work on from the panel.
Drag and drop the Jira issues into the calendar.
Changes made in Sunsama automatically sync with Jira.
GitHub:
GitHub is a code hosting platform, for version control and collaboration and it works with Sunsama to bring the issues into the app.
Here are some integration features.
Bring the GitHub issue into the Sunsama dashboard
Pick the GitHub issues you want to work on from the panel.
Drag and drop the GitHub issues into the calendar.
Gmail:
Here are some integration features.
Bring the emails from Gmail into the Sunsama dashboard
Pick the emails from Gmail you want to work on from the panel.
Drag and drop the emails from Gmail into the calendar.
Changes made in Sunsama automatically sync with Gmail.
Outlook:
Here are some integration features.
Bring the emails from Outlook into the Sunsama dashboard
Pick the emails from Outlook issues you want to work on from the panel.
Drag and drop the emails from Outlook into the calendar.
Changes made in Sunsama automatically sync with Outlook.
Slack:
Slack is a team messaging app that connects with teams. It also works with Sunsama to bring the messages into the app.
Here are some integration features.
Connect Slack to bring and turn your messages into tasks.
Update your team when a task is complete.
Pricing
Sunsama costs $20 per user per month when you pay monthly and $192 per user per year when you pay annually. Sunsama is highly priced compared to other apps but they say, “It’s easy to justify paying for things you love. When you get a lot of value out of a service, it feels fair to pay a high price for it.”
Alternatives Of Sunsama
When it comes to the daily planner app, there are few good options available on the market. Here are some of the alternatives to Sunsama.
Akiflow: Akiflow is a daily planner and task management app just like Sunsama with less cost. It offers many features, collaboration, and integration to effectively manage all the work.
Todoist: Todoist is a task management app that also offers many features to manage your work. The features include task organization, due dates, priority level, task management dashboard, and other collaboration tools.
Motion: Motion is a unique daily planner app that combines task management with mindfulness techniques. It encourages users to focus on one task at a time, promoting a sense of calm and productivity.
Ellie Planner: Ellie Planner is a visually appealing and feature-rich daily planner app designed for creative individuals. It offers customizable templates, goal-setting features, and habit-tracking tools.
Wrapping Up…
To sum up, Sunsama is a powerful daily planner app that you can use to bring all your work from different productivity apps to one single app.
It may be a higher price but the value it provides makes all the money fade away.
If you are concerned with the price then go with Akiflow — Its direct alternative and a similar daily planner.
But in the end, it’s your own choice, and requirement, and need to choose the app you want to use.
Subscribe to Productivity Side Newsletter to get useful productive hacks, tricks, and tips weekly.
0 notes