#how to hack gmail account
Explore tagged Tumblr posts
Text
My Account on tiktok was hacked last night. Please don’t respond to it at all, even block.
Please let others know.
I will post publicly if I get my my Account back, bur right now, i don’t have access
If it asks you to send anything to a gmail or any codes, DO NOT DO IT. It’s how I was hacked.

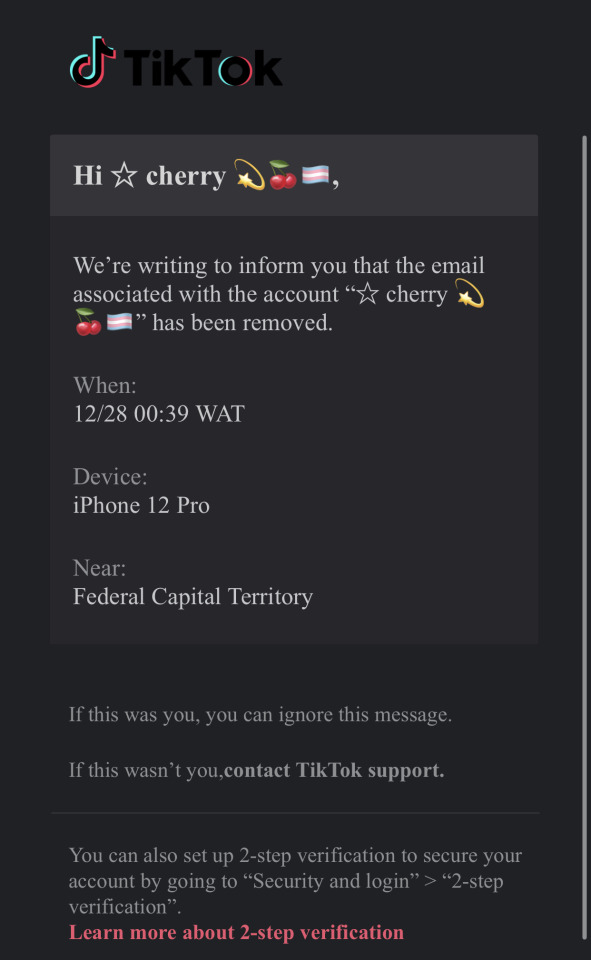

my tiktok account now is rainbowpiss34_
29 notes
·
View notes
Note
1. Tubbo confirm himself in the clip that he only kissed her, to which she later confirmed it too. As pre the video
Tubbo made the video and She would confirm it AFTER the hacker had allegedly made the post.
Let me help you, hacker did their job -> Tubbo made the video -> She confirmed it. Then how did the hacker make such a lucky guess about what happened that night in Tubbo's house?
I didn't have to go past the first point for it. Didn't even use my two degrees on Physics. Can't believe what they are feeding these IT students these days ....
"HoW dId The HaCkEr MaKe SuCh A LuCky GuEsS?"
THE VIDEO IN QUESTION WAS FILMED WAS FILMED A YEAR AGO OF HIM AT A PARTY WITH HER, AND ALL HER FRIENDS AS THEY DRANK
youtube
My goodness it would take a genius to be like "Hey I'm making allegations that they both got drunk (as shown in he video from a year ago) and Tubbo S/A her while drunk"
To which they allegations never specified WHERE THEY WERE it only specified part they were at
So Tubbo, confused as fuck Tubbo, said they came to there place, kissed and then talked about Jazz
Them going back to Tubbo's place wasn't even in the original allegations
Bitch if I went to a party, got drunk, PUBLICLY POSTED ABOUT IT ONLINE, and then someone was like "(me) was harassed by xyz", I'D BE SO FUCKING DUMB BECAUSE THEIR EVIDENCE WOULD BE THE VIDEO FROM A YEAR AGO. WHY THE FUCK WOULD SOMEONE INCRIMINATE THEMSELVES
Now dear clear idiot. I shall explain how 2-step verification works and how it didn't work in this case. AhEm
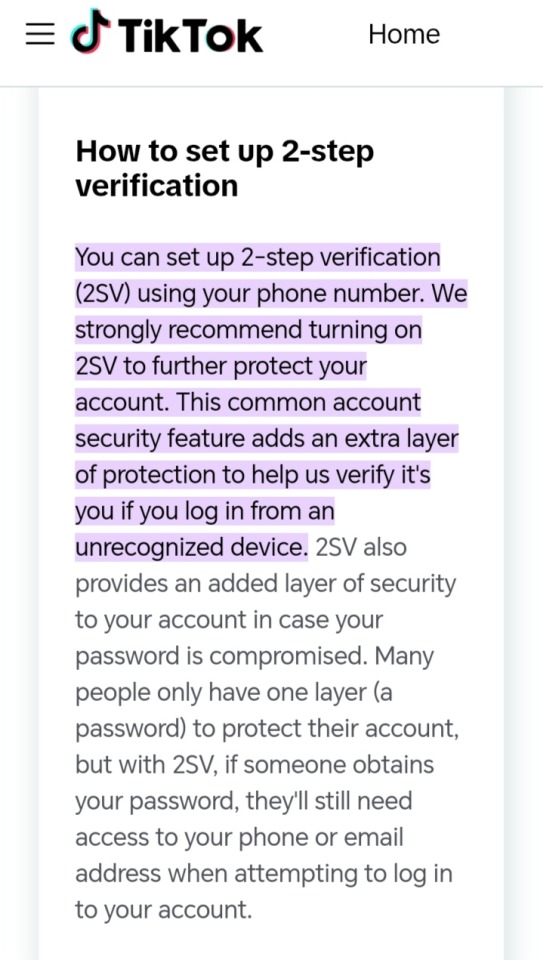
1. 2-Step Verification is as it sounds, in which after attempting to log on to a platform, the platform holders will either send a text message (through phone number) , email/gmail/AOL (if your old), notification or another form of communication to ensure the person login in is actually, ya know, you.
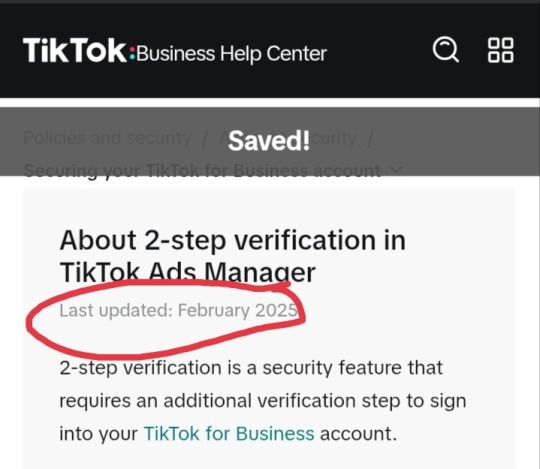
2. 2-Step Verification became a thing on TikTok, official and refined, on February 2025 (very late tbh)
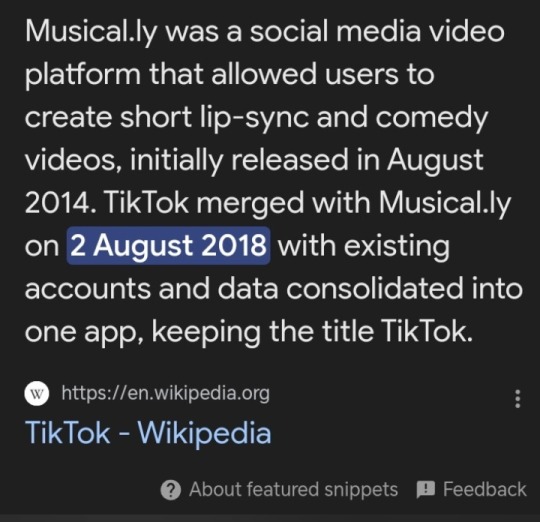
3. Your young people don't know that back in my day TikTok didn't exist. OMG HOW COULD THIS BEEE??? Because it was called Musicly before it rebranded to tiktok
And since Musicly was primarily a kids/teens/young adults app, who tf is hacking a child's account?? Ya know?
So up until before that point Musicly also didn't have 2-Step Verification. Which is important because that means this security measures didn't transfer over because they didn't exist
4. Listen Leandra is by no means old. But I will rest a hand on your shoulders when I say, Gmail was created in 2004

And if you were a kid/teen around that time, you were young enough to get a Gmail with your actual name, like full legal, government, on yo birth certificate name
Why this important? Because if your primary Gmail/email/AOL, if your full legal name or part legal name, then people have a higher chance of just guess your email or, putting down "forgot password", then linking it to their email address, getting the rights to change the password and then bam.
The only way this cannot happen is if you manual lock your Gmail to only known devices (but fr that takes to long ngl and plus you won't be able to work on something if you can't access the device that has the rights to your email and additionally if you lose that device then it's game over, try again, pack it tf up)
So if she made her Tiktok account via any of the emails, then it's done, sorted, etc...
4.1. Now let's say she made it with her phone number like Tubbo suggested.
You could gain access further:
Having the email/gmail/AOL be linked with your phone number as a contact/emergency contact (idk in what case Google would hit you up but they can ig)
Phising. Look it up. It's spelt with a PH but pronounced fishing. And it's much more common then you think
The most popular phone plan providers in the UK are EE and Vodafone, inwhich if you get a new SIM card in a new phone, you can call them to change the new SIM phone number back to your older on as I'd be more convenient. The thing is, literally anyone could call. Like anyone, all you really need is the either the email/gmail/AOL, or the make and model of the phone, to answer some relatively personal questions (which you can lowkey guess ngl), or live in the same area or they just say screw it and change the number. It's often very useful but THE MOST ANNOYING THING when someone tries to access your account, and depending on WHEN and WHERE you get the card they don't even send you a confirmation text because they assumed your the one calling.
But anyways, you'd only need to realistically find out the first few numbers of her phone number, if you went with this method, trial and error'd it till you got on that's active and you can at minimum text, then just straight up try to login in or call them.
This is a great time to mentioned that Snapchat is lowkey, unintentionally screwing people over with this, because you can check if someone has a Snapchat by their contact or trying to sign in with that phone number cause it'll say the numbers is already in use.
BUT ANYWAYS, it takes about 2-6 weeks to gain access to someone's phone number or Gmail/AOL/Email if they're born pre-2000s to early 2000s
My point being, you could just guesstimate her really name by putting it through bots, checking old posts, being in personal contact with them or like reallllyyyyy putting the effort into guessing
And this is why people are often told to regularly update or change both passwords, email/gmail /AOL password and even update their names to avoid this.
5. Leandra made her social media around 2023, for her official Lovejoy shenanigans, idk what they do tbh
And I'm in no way calling her old... But she's gotta be like minimum 2-6 years older then me putting her in the bracket of people who can get a G/E/AOL (I'm getting tired of writing I tbh) with their actual names
And since 2-Step Verification was a 2025 update on TikTok, it's likely that some people just don't have it because they're too lazy to update or set it up. But even then their are many ways to get around it.
I recommend looking at the BBC guide/explanation of multi-factor verification/ two step verification/ multi-factor verification: https://www.bbc.co.uk/programmes/articles/5VbNf6z14LS7bZ02L1NXcjG/how-to-set-up-two-factor-authentication
And to Look at this BBC bitesize link if you want to know more: https://www.bbc.co.uk/bitesize/guides/zf3bcj6/revision/6
And 6. To follow up on some misconception that I know you're probably gonna throw at me because let's be real here you just hate Tubbo and that's okay. You don't need to justify it, just dislike him and be done.
Misconception 1. For some reason people are saying that her Instagram and Snapchat were also hacked. I don't know if she has a Snapchat because I don't use it, but as for Instagram it has been confirm by many update accounts, people who know irl etc... That the insta is fine!
Misconception 2. Tubbo kissed her. Hahahahhahashhsshshslolklolol. Tubbo is gay, and it's been confirmed by both parties that she kissed him first, and apparently he freaked tf out. Because he's gay. And has been openly gay for like 1-3 years. Bit weird to call him not gay for getting a kiss from one women. Like girl do you not kiss your mom? Tf? No kissing the homies? Terrible friend you are.
Misconception 3. Tubbo cleared the allegations as well as her after the allegations were out... Because how tf are you meant to clear something that's didn't exist?
Misconception 4. The hacker got a lucky guess. Now. Stay with me here. Go find an AI prompter and type 'man and women get drunk at part, write something criminal' OR just use your imagination because you know they're at the same party from a video a year ago. And I literally peeped into my older siblings room and asked them "real talk, a man and women get drunk at a party and leave together, they get to his place and something criminal happens, what is that criminal thing?" LITERALLY the first thing they suggested. Murder was second and tax evasion strats were 3rd.
And finally 7. This is too you. Yeah anonymous asker. You.
Just like DM me because as funny as it is to post about this on twitter and laugh with moots, your cluttering up my page with unnecessary discourse. But your not gonna see this, are you?
Because you, yourself said you didn't read past my first previous point. Sooooooooooooooooooooo
But also also ALSO, if she's confirmed it didn't happen and he confirmed it didn't happen, and she confirmed she was hacked, as shown in screenshots above and previously, then why is this still a talking issue?
SHE LITERALLY SAID SHE WAS HACKED. IT WASN'T HER POSTING??
Like if you gonna be mad at Tubbo be mad that he's idk fight Sapnap or something
But you seem more upset that I'm suggesting the hacker could POTENTIALLY be a gnf fan or Wilbur fan by the way they're uproaring on Twitter. Need I remind you, humbly and respectfully, IT'S FUCKING TWITTER??!
I keep people on the loop, I ain't asking for your what ifs ngl. questions? Welcome. Petty insults and challenge stupidity? Nope.
As you can see with MUCH of my covering discourse and discussion content on both Twitter and Tumblr, I put allegedly on thing that are not 90% to 100% accurate, I stick it on rumours and provide both links and screenshot to back up point because I want to be as honest as possible.
Bro if my favourite mcyt was an asshole I'd hold them too it. If my favourite vtuber was a bitch I'd hold them too it.
But I've provided ample evidence both in my first post and this post with detailed explanation, links and breaking it down into sections, I EVEN LINKED EDUCATIONAL RESOURCES AND EXPLAINED EMAIL LORE AND WHY MILLENNIALS ARE ACTUALLY QUITE OLD
Like it's done. It's over. You ignorance, lack of real world perception, common sense, and critical thinking skills has lead you to a pre-made conclusion that please you and not the actual one. So congrats. Wish I could be that stupid.
And for the record, I got a 100% in both GCSE coursework units on Information Technology, covering a range of different topics including cyber security, and scored a 90% on the test (trust it hurts your hand writing that much)
Furthermore, I backed it up with links, educational links and screenshots reinforcing literally what I said/how it applies.
Don't doubt my intelligence. Doubt your own suckerrrr
2 notes
·
View notes
Text
TikTok Ban - Day 1
What I've done today:
1. Created new email on Proton Mail
I've been wanting to find a new service since they starting putting ads in Gmail that look like emails. This was the final straw.
They have a free version!
2. Moving accounts over to this new email
I know I won't finish this today, but my goal is to move a few logins each day.
3. Moved from Chrome to Firefox.
Also, switched what firefox searches from Chrome to DuckDuckGo (I havent used DDG before, but google doesn't get my data by default anymore either).
Wow, both proton and Firefox offer so many more user protections that I never knew was an option while on Google.
-tracker blockers (I already had ad blockers, realizing it wasn't good enough)
-alias emails. Absolutely everything wants your email, this gives you an in-between email that forwards to your actual email. The idea is if they sell your data/get hacked they aren't giving out your real email.
Thoughts today:
Before this ban i would not have gone out of way to make these changes, the effort wasn't there for me to learn it. But now, totally different situation. I am actively searching out alternatives to big tech and i refuse to use meta products. Happy to take the time to learn these new systems, even if it is a slow process.
I know i am not the only one doing this. I don't think they thought through how much this will radicalize people! The incoming administration started this problem and we will not forget. We have receipts.
-January 19, 2025
3 notes
·
View notes
Text
Nihilus Rex 41: Throw to the Wolves
Nils lays low and spirals, then lays in plans to deal with Weasel. There are jokes about different hard drive organizations that various people I know have used. Beta-read and co-written by @canyouhearthelight. Nils also speaks to many people's favorite priest.
Nils
So, laying low.
It used to be so easy, but now that I was getting a taste of actual action, of actually impacting the world, of actually shaking the system up - it was so God. Damn. Boring.
Actually, I supposed, I should deal with the issue with the Fibbies. Weasel was still out there as a loose end I needed to tie off - though as I gave greater thought to it, I realized there was a glaring error in my previous plan. Yes, I could frame Weasel, but the downside was that my plan relied on him being found non-credible. While we’d been very careful to avoid making him credible, he would, at the very least, give the FBI our names in hope of mitigating his sentence. And I didn’t need any more Feds remembering we existed in the first place. One was enough.
We’d covered our tracks well, but we could very well get hit with conspiracy charges if they felt like being awful - worse if they felt like digging deep. No, our best bet was to make sure Weasel went down for something else entirely, something that would lead to him self-eliminating, and then breadcrumbing the feds to pin the crime on a dead man and declare victory in our time. Any chance he’d be alive to talk was too great a risk.
How to do it though? Weasel was a massive creep, but he tried to avoid being outed as a massive creep. Leaking his porn habits might do it, but it didn’t actually get him arrested unless he was much, much worse than I thought. Now, maybe he was doing shady spyware shit I could check into - I was always afraid he was going to hack someone’s webcam, but...hm.
Actually, let’s see if we could get him on something he was actually doing.
I opened my computer up again and tried to log into one of Weasel’s socials. Social predictability, what was he going to be into? Character requirements for this system, what do we have…okay. PopgoestheWeasel69!.
The fact that that worked was…annoying. To say the least. One of the best icebreakers in the business and he was this bad at securing his basic stuff .… Well, okay. If I hadn’t known who he was, there was probably no way I’d have been able to break his encryptions. However, social engineering was a technique all its own. Now, to see the contents of Google Drive….
Nothing to see here but a lot of essays. Actually decently well written ones, and a few that have. Reasonably good politics. Huh. Go figure. Seething hatred of tech bros and rudimentary AI, and pretty good predictions regarding the efficiency of combined solar/nuclear energy.
Right, he was a math whiz, I’d forgotten that.
I took a breath. Okay, so somewhere here there’d be a backdoor…Uh…lesseee. No, but I could find an email attached to his resume, which was good enough. Generate a very realistic looking phishing email. Odds are good he won’t actually click the link in it once he reads it through, but he doesn’t need to. He just needs to open it.
Subject: Research Grant Application Cal Poly
Dear Mr. Winston, you have been selected to apply for a grant of five thousand dollars for research and development of software from the San Luis Obispo California Polytechnic Institute through our partners on your campus. Please follow the link below to complete the application.
Dean of Computer Science, Cal Poly San Luis Obispo.
Faking a trail and even an impersonated gmail he couldn’t check on site was easy, and just to sweeten the pot I ran a few dozen searches of San Luis Obispo through his google account, so he could be treated to the sight of California women on beaches showing up in search functions fed by the algorithm. Let him ponder enjoying the famous lack of modesty the California climate allowed to make it as tempting as possible to open, in contrast to remaining here with the winter-mandated modesty enjoyed by the women of the Pacific Northwest.
“California girls, we’re undeniable…” I sing-songed in a falsetto I was glad no one could hear. “Tempting to in-cel douche-bags.” That was probably off beat. Fuck. I had a suspicion most other people could have done it better. Note to self, not that I was considering it anyway but no musical numbers at any point in the grandiose Nihilus Rex persona. At most, dramatic reads of Ozymandias or some shit. Things I could do.
With that attended, I leaned back and waited. I considered calling Lash, and then stopped. I should…probably give her some space. She’d be pissed if I kept poking her, and apparently my last hunch about her emotional state had been wrong. Jumping to conclusions based on incomplete information - she’d broken down at the hospital, she’d thrown up after the initial retaliation, but clearly if she’d been in communication with Ayanti, she hadn’t just been falling apart.
Still, it was easier to just handle Weasel myself. Fewer communications involved meant fewer people on the line if it went sideways, and clearly Ayanti had more trust in Lash than me. So, for now, the obvious tactical choice was for me to do the dirty work and her to make the world a bit brighter. Maybe we’d swap that role later, but for the time being this made sense. And unlike last time, it wasn’t like I felt like I was being forced to do it today.
I leaned back and looked at the situation, picked up a book and started reading. I had been getting behind on homework late…
Wow. He had already clicked the link. Alright, malware packet in, let’s open you up, Winston. See what goodies you have in your computer. Folder organization. Okay. Files, homework, software, projects, art…art?
That was probably - nope, nope. It was not porn, surprisingly. Good for him. I was learning an awful lot about Winston today. What about…ah. There we go. I should have just scrolled the rest of the way. “Fun Times” - in that, three subfolders. A Pocket flash player, an emulator…and Magical Realm.
Really man, that meme? I sighed. Fuckin’...
Oh….Oh that was a lot of porn. Okay, so. Let’s see, had he, in any way, organized it?
Let’s…had he labelled…I hate it when people do this. There was a correct way to organize porn, and I’d been using it before I started getting laid often enough that I’d stopped needing it. I’d kept it in a folder that simply said “porn.” And in it? Subfolders. Subfolders that said “animated” - “kinky shit” - “sweet couple stuff.” Why? Simple. Perfect. But did Weasel do this? No, instead Winston was a weird, messy bitch who just liked the Netflix version of endless scrolling while horny and trying to find something to jerk it to because everything here was alphanumeric and no organizational scheme. Just. Absolute goddamn degenerate behavior.
Idly, I wondered if I’d have been better off waiting to do this until Lash and I were on better terms, then I remembered that this was Weasel and I refused to be turned on by anything he was into.
***
Almost three hours of scrolling later, I had managed to find eight instances of things definitely taken from compromised webcams, and two instances where I was reasonably suspicious that one of the performers was not of legal age. That was a lot of sex crimes for one incel. I forced myself to acknowledge that, as disgusting as Weasel was, and how little time he spent with real women, there were about even odds he legitimately didn’t realize that he’d committed the latter two. Not that it mattered.
I dropped in a slight malware packet that would flag him for the FBI and then leak his download history very publicly, see what that got him. When he realized what had been compromised, he’d probably panic, but it didn’t matter. Once you were flagged, certain files were frozen - and I’d already saved backups of his entire porn folder deep, deep in his C-drive.
Ugh, why had that sounded dirty in my head? Too much time looking at Weasel’s crap, probably.
I disengaged from the hack and called Bishop. “Bishop. Anything interesting?”
“Eh…got a few people in the net looking for answers we may be able to ring in for them. Trade for favors later, maybe recruit some of them. Also, Gray wants to talk to you about a bigger project a little later?”
“Thank you. I’ll deal with Gray. Who are the others?”
“Tracking that down. It’s more my speciality than yours, pretty sure. I’m talking to my contacts in Eastern Europe, as well.”
“Understood. Thank you.” I sat back down, thinking about the risks. The FBI were still combing through the financial sector, and I wanted to look at the boards that Grey kept wound up. Some people were claiming that the original attack on the bank had been inspired or planned by some computer loving virgin, but most people there weren’t going for it. Then my phone started ringing.
My personal phone, for being Nils. I snapped it up and said, “Andover.”
“Nils.” The voice on the other end was one I knew well, one I’d been familiar with.
“Father Rivera. To what do I owe the pleasure?”
“I was contacted through backchannels in the Catholic Church for priests to communicate with each other. I was told that an orphanage the Mother Church runs in El Salvador is being given thousands of dollars worth of supplies by a mysterious benefactor, fluent in Latin but not Spanish - and that they were told by this mysterious benefactor that I would be able to reach him if they thought of anything else. Now, there is only one person on the planet that I can think of who might be doing something like that. So, Nils. Where is the money coming from?”
“Does it matter? Hungry kids are being fed, babies are being kept in diapers, sick kids are getting medicine and shots to keep from getting sick again.”
“Nils…” His voice took on a warning note.
“It’s coming from corporations who can afford it. No, I do not repent. You can turn me in but you’ll be cutting a lifeline for vulnerable people if you do. There are hundreds, if not thousands, of people that my scheming supplies with lifesaving things they cannot get through ‘better’ means. Please, Father Rivera. Leave me to my work.” My answer, and the quiet, desperate truth of it, must have convinced him of something.
He sighed heavily on the other end of the phone. “I want to speak with you directly, Nils. Soon. But for today, they say they’re worried about damage to their well, so they want water filters.”
I let out a bitter laugh. “Of all the things…yeah, I can do it. Tell them I hope the well will last a bit longer, because that’s a…harder ask than it really should be, right now.”
Rivera’s voice grew strained. “Do I want to know?”
“No, probably not.”
I took a breath. Rivera knew. That was a mistake. I could speak to him about other things weighing on me in the future. Other plans I’d laid. In the meantime, I’d wait for the plans with Weasel to bear fruit.
Hopefully the plan with Ayanati was going well for Lash.
#writeblr#writers on tumblr#original fiction#my writing#cyberpunk dystopia#modern dystopia#traumatized characters#Arcadian Inquisition prequel#Miys Prequel#Nihilus Rex
2 notes
·
View notes
Text
I was in 3rd grade, playing with 2 1/4 circles (they were part of a magic trick set (basically, one looks bigger than the other, depending on the placement)) and I placed them to look like an X, then, I got thinking of words starting with X.
And I ended up with xoids [x-oids].
So, with this great name, I wanted to make a company with this name.
Eventually, I make a gmail account with the name, I started using it for general internet account stuff.
Now, why the 1?
Well, I got locked out of my old account BC I got hacked, why or how, I don't remember. But BC I kinda was already known as xoids, I chose to name myself as xoids1, so, when ever someone says xoids1, they say "xoids won".
This is also the reason I sometimes go as xoids_won when xoids1 is taken.
USERNAME LORE GIVE IT TO ME NOW YOU ALL
84K notes
·
View notes
Text
🎓 How to Claim Google VEO3 Premium Student Plan for Free (No University Required)

The demand for cloud services and productivity tools is growing rapidly in 2025. If you’re someone who needs access to advanced Google features but can’t afford a subscription, there’s a 100% working method to get Google VEO3 Premium Student Plan for free — no student ID or tuition needed.
With the help of a VPN, a temporary student email, and basic internet tools, you can get 15 months of premium access, 1 TB Google Drive space, and more — completely free. Let’s break it down step by step.
✅ Why Choose Google VEO3 Premium?
Google VEO3 Premium is a complete productivity package for students and professionals. Here's what you get:
1 TB of cloud storage
Pro-level access to Docs, Meet, Sheets, and more
Tools optimized for collaboration and online learning
Extra security and faster performance
Free use for 15 months if verified as a student
But what if you’re not enrolled in a university? That’s where this guide comes in.
🧩 The 3 Tools You Need
To activate this method, you’ll need:
A Gmail account
A VPN (to change your online location)
A temporary .edu email
A VCC (Virtual Credit Card) or PayPal for verification
Don’t worry — you won’t be charged. These steps are just for identity validation.
🛠️ Step 1: Create or Use a Gmail Account
If you already have a Gmail account, you can use it. Otherwise:
Visit: Gmail Signup
Register a new account with a secure password
Confirm with your mobile number
A fresh Gmail helps keep everything clean and reduces errors.
🌍 Step 2: Set Up a VPN
The student premium offer is geo-restricted. You need to appear as if you are in the U.S., Canada, or U.K. for it to work.
➡️ Click here to get your VPN
Download the VPN from the link
Install it on your PC or phone
Connect to a U.S. or U.K. server
Keep it active throughout the whole process
This is the key to unlocking the student portal.
📧 Step 3: Get a Free .EDU Email
Visit a free .edu email generator or temp service:
🔗 TempUMail – Free .EDU Email Provider
Choose a .edu email from the list
Copy it
Stay on the website — you’ll need to access your inbox for verification
This will serve as your student email during registration.
💳 Step 4: Add Payment for Verification
Although it’s a free plan, Google still requires a payment method to verify identity.
You can use:
A Virtual Credit Card (VCC)
Or your PayPal account
No actual charges will happen. Just follow the instructions and verify.
🚀 Step 5: Activate Google VEO3 Premium
Now that you’re verified:
Log in using your Gmail
Enter the .edu email on the student plan page
Confirm the link sent to the .edu email
Add your payment method
Enjoy 15 months of full access!
🎯 Benefits You’ll Enjoy
Once your account is activated, you’ll unlock:
✔️ Google VEO3 Premium plan
✔️ 1TB secure cloud storage
✔️ Pro tools for work, study, and meetings
✔️ Seamless sync with mobile and PC
All for zero cost.
🛡️ Important Notes
Don’t disconnect the VPN until the setup is complete
If an email doesn’t work, generate a new .edu address
Use this method on your personal device to avoid issues
Don’t forget to bookmark this page: 👉 HERE
🎉 Conclusion: Smart Hack for Smart Users
This method has helped thousands of users in 2025 get access to a world-class productivity suite for free. It's safe, fast, and 100% working if you follow the instructions exactly.
💡 Want to get started? 👉 Grab your free VPN here Start enjoying the full power of Google — without paying a dime.
0 notes
Text
Hi additional info I logged on to tweetdeck last night to schedule tweets for my second job and while the only x branding changes I can see on it is the loading screen now having the unicode symbol instead of the Twitter bird. Everything else is still Twitter branded, but the ui has been royally fucked up. New things about the tweetdeck ui that pisses me off royally:
The font and layout is no longer as dyslexia friendly, not that it was very friendly to begin with but it's now painfully illegible.
You can't adjust column widths anymore? Weird feature to remove honestly you would think no one would think about that.
I had to sign in as uwn because I could no longer tweet on its behalf as an affiliate account, which greatly decreases cyber security, mainly because the main account holder had to email me the sign in details over Gmail, and that's very much not secure, but also because we now have to very stringently monitor and confirm sign ins to avoid hacks which none of us have the time for.
Where scheduling a tweet used to involve clicking the date you want to post on a little calendar, typing in the time you want it to post and clicking am or pm, it now involves drop down menus. Yes plural. There is a drop down menu for the month, one for the day, one for the year, one for the hour, one for the minute, and one for am/pm. What's worse, there isn't a search function, meaning you have to scroll through as much as 60 minutes and 31 days to find the day and minute you want it to go out. This entire interface makes scheduling tweets 5 times slower and more annoying.
I'm not sure if it's happened yet and Liam just paid the fee, but supposedly tweetdeck is heading for or already behind a pay wall, allegedly linked to your Twitter blue subscription, which means you have to buy the now useless and ridiculously expensive blue checkmark to be able to, checks notes, schedule your posts.
Anyway based on what's currently happening, I suspect Elon actually wanted to completely rebuild and rebrand Twitter, essentially creating his own social media, but didn't want to struggle to get a strong userbase and wanted to piggyback off how popular Twitter already was. What's really stupid about this though is that he could have spent 40 million to create an entire social media platform from scratch, with the x branding and features and ui he's already introduced, market the fuck out of it to get a strong userbase, hire an entire team to manage the platform, create an app, create merch, and he'll only have spent less than 0.1% of what he spent on an existing company only to fuck it up in a bad rebrand attempt.
And his fan boys call him a genius? Besties the man can't even rebrand a social media platform correctlyor implement user friendly ui, and you think this man developed his own programs to get rich? Nah fam he literally bought his way to the top with daddy's blood money.
I slept in and just woke up, so here's what I've been able to figure out while sipping coffee:
Twitter has officially rebranded to X just a day or two after the move was announced.
The official branding is that a tweet is now called "an X", for which there are too many jokes to make.
The official account is still @twitter because someone else owns @X and they didn't reclaim the username first.
The logo is 𝕏 which is the Unicode character Unicode U+1D54F so the logo cannot be copyrighted and it is highly likely that it cannot be protected as a trademark.
Outside the visual logo, the trademark for the use of the name "X" in social media is held by Meta/Facebook, while the trademark for "X" in finance/commerce is owned by Microsoft.
The rebranding has been stopped in Japan as the term "X Japan" is trademarked by the band X JAPAN.
Elon had workers taking down the "Twitter" name from the side of the building. He did not have any permits to do this. The building owner called the cops who stopped the crew midway through so the sign just says "er".
He still plans to call his streaming and media hosting branch of the company as "Xvideo". Nobody tell him.
This man wants you to give him control over all of your financial information.
Edit to add further developments:
Yes, this is all real. Check the notes and people have pictures. I understand the skepticism because it feels like a joke, but to the best of my knowledge, everything in the above is accurate.
Microsoft also owns the trademark on X for chatting and gaming because, y'know, X-box.
The logo came from a random podcaster who tweeted it at Musk.
The act of sending a tweet is now known as "Xeet". They even added a guide for how to Xeet.
The branding change is inconsistent. Some icons have changed, some have not, and the words "tweet" and "Twitter" are still all over the place on the site.
TweetDeck is currently unaffected and I hope it's because they forgot that it exists again. The complete negligence toward that tool and just leaving it the hell alone is the only thing that makes the site usable (and some of us are stuck on there for work).
This is likely because Musk was forced out of PayPal due to a failed credit line project and because he wanted to rename the site to "X-Paypal" and eventually just to "X".
This became a big deal behind the scenes as Musk paid over $1 million for the domain X.com and wanted to rebrand the company that already had the brand awareness people were using it as a verb to "pay online" (as in "I'll paypal you the money")
X.com is not currently owned by Musk. It is held by a domain registrar (I believe GoDaddy but I'm not entirely sure). Meaning as long as he's hung onto this idea of making X Corp a thing, he couldn't be arsed to pay the $15/year domain renewal.
Bloomberg estimates the rebranding wiped between $4 to $20 billion from the valuation of Twitter due to the loss of brand awareness.
The company was already worth less than half of the $44 billion Musk paid for it in the first place, meaning this may end up a worse deal than when Yahoo bought Tumblr.
One estimation (though this is with a grain of salt) said that Twitter is three months from defaulting on its loans taken out to buy the site. Those loans were secured with Tesla stock. Meaning the bank will seize that stock and, since it won't be enough to pay the debt (since it's worth around 50-75% of what it was at the time of the loan), they can start seizing personal assets of Elon Musk including the Twitter company itself and his interest in SpaceX.
Sesame Street's official accounts mocked the rebranding.
158K notes
·
View notes
Text
Passwords hashing is used to secure passwords. Hashing is a common technique across various software and tools. Hashing is used as a security mechanism for preventing plain text information known to others. It's mathematically impossible to calculate a plain text for Hash since hashing is a one-way process. Still, there are different ways exist that can crack the hash and retrieve your password or other sensitive information that may have been hashed. Hashing technique is mostly applicable to protect password like information since its a one-way process. You may also want to check out - how to learn hacking and cracking. This is a simple tutorial that will explain how hash cracking works. Why Password Hashing Is Considered Secure Hashing is a one-way process. This guarantees that the hash of a plain text value can be generated however the process can not be reversed. Most software and websites use this way to store password since the user knows the password. Whenever they need to authenticate the user, they generate the hash of user input and match it with a stored password. This mechanism guarantees that even the software provider themselves do not know your password. However, there are hacking and cracking tools as well as other techniques described below that may be able to find out your password from a hash. Today we will learn about Cracking the Hashes using CPU and GPU. CPU: Central Processing Unit GPU: Graphical Processing Unit We will cover: What is a Hash? What is the need for a Hash? Why Hash over Encryption or Encoding? Hardware configuration Tools required Hash cracking [CPU] Hash cracking [GPU] Hash cracking using Search engine Why such a difference? What Is A Hash? A. A Cryptographic function that converts a data or file of arbitrary length or size to a fixed length, which is considered practically impossible to invert. see Wikipedia What Is The Need Of A Hash? A major use of Hash is in the security field. To provide security or privacy to the user who is using any service of a company. For example, You are using Gmail, Facebook, Twitter, eBay, Amazon or Online payment portals like Paypal. Where you use the service by providing your credentials(username/password) There are basically 2 reasons: Making it difficult for hackers to recover/retrieve Password, Online service(Gmail,eBay, etc) or even Wi-Fi. Checking for the file verification. see SHA1 here Even If a company’s security is breached (Hacked), then also the user’s credentials are safe(only if you use a strong password) Why Hash Over Encryption And Encoding? Imagine a scenario, which perhaps happens to almost every Big banner, take it Google, Facebook, Yahoo! etc. A website is compromised and User’s data(credentials) is compromised. What is the thing that will make you worry when you come to know that if you are a registered user on that site? Yes! your Password (might be the master password, for all your accounts). Now, It is in service provider’s hand to provide security to their consumers. Hence, Hashing is the solution. How? well, you might be familiar with these terms: Encoding/Decoding Encrypt/Decrypt and now, Hashing Not going into the details, I will tell you a basic and most important feature of Hash which makes Hash much different and important over Encoding and Decoding. and that is : Encoded text/file can be Decoded, Encrypted text/file can be Decrypted, But hashed text/file can never be De-hashed. Yes, Hash, unlike Encryption/Encoding, is a One-way process i.e when a text/file goes through the Cryptographic hash function, it is converted into a fixed character length. Example: md5 type hash has a character length of 32, where SHA1 has a character length of 40. If we hash a string, say “test123″, md5 and SHA1 hash for “test123″ will be md5(“test123″) : CC03E747A6AFBBCBF8BE7668ACFEBEE5 SHA1(“test123″) : 7288EDD0FC3FFCBE93A0CF06E3568E28521687BC Length differs from md2, md4 to SHA256, SHA512 and so on.
Hashing your Wi-Fi password is also secured using a hash function named PBKDF2(Password-Based Key Derivation Function) Hardware Configuration Hardware used in this tutorial: Laptop with 4 GB RAM Nvidia Graphic card 1 GB Tools Required Software used in this tutorial: Windows 8, 32-bit Cain & Abel (CPU based cracker). igHashGPU (GPU based cracker), download here Nvidia graphics driver, for igHashGPU, download here Hash Cracking [CPU] Cain & abel is a multi-purpose tool. It is used for various purpose like Sniffing Hash calculating Hash recovery(this tutorial) ARP spoofing WiFi hacking, using hardware called AirPcap and so on. We will take MD5(Message Digest 5) cracking as an example to keep it simple and easy to understand. Install Cain & abel, then follow the instruction along, step-by-step: Open Cain & abel Press Alt+C to open the Hash calculator Type in “test123” and hit [ENTER], here “test123″ is our test string You should see something similar, Here we got the MD5, and other Hash for string “test123″ i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5. select and copy the MD5 hash.
NOTE: Hashing is Case sensitive, Hash for “Test123” will be absolutely different. Click on Cracker tab, then select MD5 Hashes column in the left. then right click and select Add to list. Paste the copied MD5 hash and hit [ENTER] Now, Hash is added to list. Right click on hash and select Brute-Force attack Set max length to 7 and click Start, and you should see this
. Here I have set the Max length of the password to be 7 to just test the output of the tool, and cracking speed of the CPU.
See the Password/Second CPU is testing: 6.3M (approx) and the remaining time i.e total time which will take CPU to recover the original string is 3.5 hours. It is too lame to wait for 3.5 hours for a small string test123 of the length of 7 characters with no special characters. isn’t it? well, here comes the GPU cracking to put some speed in the process! Hash Cracking [GPU] igHashGPU is a password recovery tool specialized for ATI (RV) and nVidia (Cuda) based cards. It recovers password of hashes which are used over the internet(weak), example md4/md5/SHA1. Let's get started, We have the MD5 string for test123 i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5 Follow the instructions along, step-by-step: Download and extract igHashGPU. Go to folder Right click and edit the file “example.cmd“. It is the example file for testing GPU speed of recovering MD5 password. Paste the MD5 code in the file after h:
and it should look like this :
ighashgpu.exe /h:CC03E747A6AFBBCBF8BE7668ACFEBEE5 /t:md5 /c:sd /min:4 /max:7 Close file. Click save and yes. Select “Example.cmd” and hit [ENTER]. A command prompt window will open like this
. See the CURSPD(Current speed), ~50 Million. Nice! but not good, isn’t it? see the battery symbol in the lower right corner. The laptop is running on battery. See what happens when I plug in the charger, notice the clock and speed. WHOA! See the difference! from 50M to 195M passwords/second, isn’t it great ? from 6.3M pass/sec to 195M pass/sec. That’s a big Jump. What you think how long it would have taken to recover the Password ? Just 5 minutes and 53 seconds. See how much time we saved by using GPU. From 3+ hrs to just 5 minutes. isn’t it amazing? also see the average speed also, 62,847 Million passwords/second. CPU: ~3 hrs with 6M pass/sec
GPU: ~6 min with 195M pass/sec You might ask, Hey! can we crack this even faster? well, the answer is Yes you can(not always though). How? Hash Cracking Using Search Engine [Google] We had MD5 string copied, right? what you need to do is very simple. Just paste and search the MD5 string i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5 on Google. and you’re done! Notice the text string “test123” and the Hash. So simple to recover the string from MD5, no? Now see the time above, it took us to recover the original string. Just 0.31 seconds. not even a second. Wow! that’s great.
You might be thinking why such a difference? here’s the answer Why Such A Difference? The difference in the speed is due to the architecture of the 3. CPU: Uses 4 cores(Shared with system processes) at maximum, 8-cores in some cases. GPU: Used 96 cores (In this case). All the 96 cores(Parallel processing units) were 100% dedicated for the password recovery process unlike CPU, which was simultaneously handling the complete OS including background processes, GUI(mapping of pixels on screen), and many other processes. Even if the CPU stop handling those, then also it won’t match GPU’s performance. difference because of the #of cores i.e 96 vs. 4 or 8 Latest GPU’s that I have seen comes with more than 400 cores. It can take you more than a billion passwords/second to recover the MD5 hashed string. Google Don’t Crack The Hash. Yes!, Google doesn’t crack/recover the string. It sends a request for the specific Text input i.e the hash in our case, to all the servers, takes the response back and displays the result according to the page rank of the site. There are plenty of online crackers, which can be used to crack a variety of hashes. They search their Database for the hash you have entered. If the string of hash is already recovered by them, they will give it to you, else you have to pay to avail the service. An email is sent if the string has been recovered. So, what Google does is sending a request to all these servers and displaying you the result. Result of the hash already cracked. It certainly becomes the Top priority for hash cracking. Search google first, if you didn’t find the password, go for GPU cracking.
Still didn’t succeed? Try CloudCraker, crackStation, HashKiller You can google “Online hash cracker” for more results. Note: Cracking speed varies depending on factors like: GPU configuration, ATI graphics cards are the best for this task. Hash type, for SHA1 it will be even lesser and for WPA hash cracking it goes down to 4000 Pass/sec on my graphics card. see this list. My card’s performance is near to GeForce 8800 GTS (CUDA) Interested in WPA cracking, or WiFi pentesting? Follow my WiFi Security and Pentesting Series Hope you found this tutorial helpful. Let me know in the comment section. Thanks! This article is contributed by Hardeep Singh (Facebook | Twitter). Hardeep is a guest author and Full-time Blogger @ rootsh3ll.com, Security person, Penetration, tester, Linux and python Lover. Loves to share knowledge with everyone. Updated On June 2019: Fixed Broken links and updated minor typos.
0 notes
Text
New Gmail Threats Targeting Users in 2025 (and How to Stay Safe)
Cybercriminals target Gmail a lot because it’s very popular. It also integrates with many other Google services. As AI-powered hacking attacks become more common, it gets harder for people to distinguish between real and fake emails. As 2025 approaches, it’s crucial for Gmail users to be aware of these new threats and take steps to keep their accounts safe. We’ll discuss the new threats that…
0 notes
Video
youtube
How to Recover Hacked Gmail Account | Personal Experience & Recovery Tips
0 notes
Text
How to Monitor Gmail Messages Efficiently Monitoring Gmail messages is a useful strategy for staying on top of all your information, especially if you use this account for personal or professional purposes. Proper email management allows you to respond in a timely manner, detect potential fraud, and prevent important messages from getting lost in the spam folder.
One way to monitor messages is by enabling notifications on both your mobile phone and your computer. Hacking Gmail allows you to receive a notification every time a new email arrives. You just need to go to your settings and enable desktop or mobile notifications.
Another key tool is filters. You can create custom filters so that every email from a specific sender is automatically archived, labeled, or forwarded. This is very useful for organizing your inbox and saving time searching for relevant emails.
You can also use the advanced search feature. With commands like “from:,” “subject:,” or “has:attachment,” you can quickly monitor messages of a certain type. This feature is ideal if you need to keep track of specific information.
Additionally, if you share your account with other users or want to keep track of usage, you can review the activity history and see which devices your account has been accessed from. This protects your security and privacy.
Properly monitoring your Gmail messages will help you not only stay informed, but also prevent problems and maintain good communication. Take advantage of these features and stay on top of your email.

0 notes
Text
it took me a year to understand that when I got the valentine with the phrases I had got 5 years prior word for word it's bc I uploaded them to twitter. Which is connected to my phone number. Which I gave to my supervisor phd student. Means that he exported his contacts on twitter sometime between after he got my number and last year's feb14th. And looked through my account. Which I cannot access now bc I deleted twitter from my phones and even though I found the password for it to try and log in on web. I cannot log in. Bc it sent the authentification code to the gmail I lost this autumn. It had no backup email adresses nor my phone number bc when I was 15 I didn't consider the possibility our PC would die someday, so I didn't put anything (or maybe in 2019 it wasn't required and I forgot to do the extra bit to be safe after creating the account). So the only hope to log in is to remember the password I came up with like 5.5 years ago. I have tried a lot. I cannot for the love of anything remember what I could have put there. I know my password creating logic hasn't shifted much (but it's because I've mostly been reusing them for quite some time now), and it is most likely either a fandom from back then or personal (mostly applies to fav numbers) related. Is it mafu or eve? Or is it bnha or kny or drstone? Or is it smth referencing my other accs on other social media (tried some but not all of these)? Did it only use lowercase letters, or were there uppercase ones as well? What about numbers? I know I don't actually always use those, but often enough. I doubt I used any special symbols, but _ and . seem a bit likely for some reason. How many symbols were there? I don't remember if I was invested in caring for sou or soraru or balloon or even amatsuki back then. I remember what I called the account (eh, might as well share, it's the name seen when commenting on yt): an ambivalent diamond. The g account is senkuxscience (if someone is in the mood to hack it for me <3 I don't think I used it for anything important, just a couple of other social media accs again sooo yeah would appreciate if it at least doesn't get deleted). Still, since I thought of diamond for the name, could I have been in the mood to reference su at the moment for the password as well?
Can someone murder me. I got so hung up on this and spent a lot of time trying but I still haven't done my assignment due in less than 40 hours. And I'm getting sleep deprivation again.
1 note
·
View note
Text
Santiago de Cali January 29 2025. Oscar Fredy Posso Vitali. Today More Problems. I am Writting a New Email Yahoo Since Computer of a Friend. Really My Concern Growing When I Can Not Open Freely My Accounts Emails Gmail and Hotmail. I Expecting a Code to My Mobile Phone Hacked. Really There Many Fraud and Lacking Honesty in Gestions of Google, Facebook and Hotmail, Outlook. Now All is Addressed in a Number Phone. My Phone is Hacked Since Yesterday. Facebook, Google and Outlook Hotmail Really These are Not Acting Rightly to My Person in This Moment of Crisis. I Have Not Economy at Moment. I Received a Brutal Hacking to My Phone. How Would Be If I Purchase a New Mobile Phone' Securely Also They Could Deny My Information Since 2010, 2011 Years When I Opened Accounts Facebook and Twitter. I Needs Personal Computer and Many Other Things. And for to Fill More the Cup, The Colombian Police in Persecution of a Man True, Honest. Noble With Need to Rebuild My Life, Really an Infamy More of The System Against My Person. Is Possible That a Neighbor Can Remove The Hacking to My Phone by 10.000.
Oscar Fredy Posso Vitali.
0 notes
Text
How to Setup Gmail Account Without Phone Number [Hindi]
youtube
Hello friends! In this video, we’ll show you an easy trick to create a Gmail account without a phone number. Learn how to fill in details, choose an email ID, skip recovery options, and enhance your privacy. This method helps protect your account from SMS spam and keeps your information secure. Don’t forget to subscribe to AI Expert Reviews for more tech hacks like this!
#GmailAccount#NoPhoneNumber#GmailSetup#PrivacyTips#SecureGmail#TechHacks#AIEexpertReviews#EmailWithoutPhone#GmailPrivacy#EasyGmailTrick#Youtube
0 notes
Text
Internet security is a complicated thing to talk about. It is something both business owners and average users are concerned about. The more developers work on the security problems, the more hackers, and cybercriminals try to solve them. It is a vicious circle. But it doesn't mean you do not have to protect your private or business data even knowing that there is no such website or program which can't be hacked sometime. Statistics show that cybercriminals equally target both smaller and bigger businesses, making IT security the key to the company's stability and productivity. Serious cyber attacks are not chaotic or single. Usually, it is a set of programs, which target several companies in one industry at once. If you don't believe that the hackers can paralyze the work of the whole company, try not to use any program or service for the protection of your data. But we don't recommend even thinking about it. Of course, if you don't want to lose the amount of work you have already done and the money you have already earned. So, what can you do to prevent your business from being hacked by cybercriminals? The first and the most basic IT security step is getting the best FREE VPN service for your website and banking operations at least. The importance of VPN services results from their ability to encrypt the connection between your PC/laptop/smartphone and the Internet, which makes it invisible to hackers. But what else can you do to protect your personal and professional information? IT Security Solutions There are some differences between what average users and professionals do to protect their data from hacking. For example, average users consider antivirus software and strong passwords to be enough. While professional IT security experts consider installing software updates and using unique passwords to be far more important for your data. There are a lot of other critical things you probably do wrong when it comes to the security of your professional and personal information. So, let's have a look how it should be done correctly. Professional Tips on Internet Security First of all, let's mention one misunderstanding most Apple users have. "Apple can't be hacked. It's secure enough without an additional protection." That's not the truth. Even Apple products can be hacked. Not so easily as others but still they can be hacked. Apple is just doing a better job when it comes to security issues. And now we can officially skip to those basic steps you can do to protect your online business from being paralyzed by hackers. Use Two-factor authentication Two-factor authentication instead of changing your password every two months. This concerns most of your daily accounts like Gmail, Twitter, Facebook, Amazon, etc. Among all of these accounts, highlight your email account. As it is one the most important ones. If a hacker owns your email account, he'll probably own other services. He can reset all other passwords just using this email address. Two-factor authentication is something, which can prevent this from happening. Dealing with suspicious links Confirm suspicious links but do not click on them. This will show you where the link goes. Based on this you can decide whether to click on that link or not. And don't forget to check the sender's email address too. Backups Using a backup tool is a good starting point for any business when it comes to security. Having a good backup, which is not connected to your machine is very important. Try offline backups as one of the first steps while figuring out which security strategy is more suitable for you. Train your team A lot of cyber attacks happen because of the employees who click on the malicious links or websites. So, it would be a smart move to provide your employees with the key principles and rules of the company's IT security policy. Contact a security specialist Today, you have a choice between contacting a security specialist for any IT recommendations
on security issues or to hire a provider, which specializes in cybersecurity on a daily basis. It is a good outsourcing step, which gives you the ability to cover all online security gaps at once. This will save your time and money. Let IT specialists monitor the security of your business. Make a security review It is very useful to make a full security review of your passwords, access to them, backups, and testing every couple of months. Analyze the results you get and find out if your IT security system has any gaps. Consult an expert. This is what you can do to protect your business and personal data online. And what is your number one thing to protect the company on the Internet?
0 notes
Text
Buy Aged Old Gmail Accounts
Benefits of Buying Aged Old Gmail Accounts
Increased Credibility and Trust: An aged Gmail account shows longevity and consistent usage over time. When you communicate with others through such an account, recipients are more likely to view your emails as trustworthy and reliable, avoiding spam filters.
Better Email Deliverability: Older Gmail accounts are less likely to get caught in email filtering systems or be blocked, leading to higher chances that your important messages will be seen by recipients.
Enhanced Security: Aged Gmail accounts typically have more security layers like phone verification, recovery email, and other protective measures already in place. This reduces the risk of hacking and unwanted account breaches.
Access to Google Services: Gmail accounts are the key to accessing other essential Google services such as Google Drive, Google Docs, Google Analytics, and more. An older account with verified usage can provide seamless access without the delays and restrictions sometimes encountered with newer accounts.
Improved Marketing Opportunities: For email marketers, using aged Gmail accounts can be especially beneficial for avoiding spam traps and increasing open rates for campaigns. Aged accounts have more reputation and credibility in email servers, boosting your chances of successful delivery.
SEO and Social Media Growth: Older Gmail accounts can be connected to other Google services that affect SEO rankings and social media visibility. Their established nature helps you grow digital assets with greater ease and authority.
Types of Aged Old Gmail Accounts You Can Buy
At our marketplace, you can choose from a wide variety of aged old Gmail accounts, tailored to meet your specific needs:
Basic Aged Gmail Accounts: These accounts have been created and aged for at least one year. They are perfect for smaller business activities, email marketing, and personal communications.
Premium Aged Gmail Accounts: Premium accounts have been around for over 3 to 5 years, with a history of regular usage. These are ideal for businesses looking to establish long-term trust and engage in high-level email campaigns.
Aged Gmail Accounts with Google Services: These accounts come pre-linked with additional Google services like Google Drive, Google Analytics, and Google My Business. They are best suited for businesses and individuals who require full access to Google’s ecosystem for productivity and digital marketing.
How Aged Gmail Accounts Benefit Digital Marketers
Email marketing has become one of the most effective ways of reaching potential customers. However, ensuring your emails actually land in the inbox is key. This is where aged Gmail accounts shine for digital marketers.
When using newly created email accounts, you often encounter issues such as emails landing in the spam folder, getting blacklisted, or being blocked entirely by email service providers. Aged old Gmail accounts, on the other hand, have a much better reputation in email networks, improving deliverability and trust scores.
Additionally, since these accounts have been used and active for years, they are more likely to be accepted by email servers, allowing digital marketers to run campaigns with more confidence.
How to Use Aged Old Gmail Accounts for Social Media Success
Aged old Gmail accounts aren’t just beneficial for email; they can also enhance your social media presence. Many platforms require email verification, and an older Gmail account can increase the chances of your social media profiles appearing more legitimate and trustworthy to both the platforms themselves and potential followers.
This is especially useful when creating accounts on platforms like YouTube, Twitter, and LinkedIn, where older email accounts help in avoiding suspicion and ensuring smooth account creation. These Gmail accounts can also serve as recovery emails for multiple social media accounts, adding an extra layer of security to your online presence.
Aged Old Gmail Accounts for Affiliate Marketing and Business Growth
Affiliate marketers benefit greatly from using aged Gmail accounts because of their established standing in the email ecosystem. With these accounts, affiliate marketers can create numerous profiles across different networks, maintain constant contact with clients, and send promotional emails with a higher chance of success.
For businesses, aged Gmail accounts allow them to expand their email communication network without worrying about losing credibility. Many companies use aged Gmail accounts to create separate email lists, manage customer support, and stay connected to clients without risking their primary business emails.
Bulk Purchases of Aged Old Gmail Accounts for Agencies
If you manage a digital marketing agency, public relations firm, or a customer support team, buying aged Gmail accounts in bulk can be a game-changer. Agencies often require numerous accounts to manage different clients and campaigns, and having aged accounts ensures more successful communication efforts.

With bulk purchases, you can:
Create multiple user profiles for clients.
Manage distinct email campaigns with improved deliverability.
Expand outreach across social media and other platforms without triggering email spam filters.
By purchasing aged Gmail accounts in bulk, agencies can streamline their marketing efforts while ensuring their accounts remain reputable and secure.
Why You Should Buy Aged Gmail Accounts from Us
We are committed to providing high-quality aged Gmail accounts that offer reliability, security, and efficiency. All our accounts come with a guarantee of authenticity, and we provide personalized options based on your needs:
Verified Accounts: All Gmail accounts we offer are phone-verified, with a history of real usage to ensure credibility.
Custom Orders: Need a specific number of accounts or features? We offer custom solutions to meet your business or personal needs.
Safe Transactions: We provide secure transactions, ensuring you receive your Gmail accounts safely and confidentially.
24/7 Support: Our customer support team is available around the clock to assist you with any inquiries, from account setup to maintenance.
Frequently Asked Questions About Aged Old Gmail Accounts
What exactly are aged Gmail accounts? A: Aged Gmail accounts are email accounts that were created years ago and have been maintained over time. These accounts have built-in trust and stability, making them ideal for marketing, business operations, and secure communications.
How can I use aged Gmail accounts for my business? A: You can use aged Gmail accounts for various business purposes, including email marketing, client communications, setting up additional Google services, and managing social media profiles.
Are these accounts safe to use? Yes, we ensure that all the accounts we provide are secure, verified, and maintained properly to minimize any risk of breaches or security issues.
What is the difference between aged Gmail accounts and regular ones? Aged Gmail accounts offer more credibility and stability than newly created ones. They are less likely to trigger spam filters and are more trusted by email servers, making them more effective for marketing and business communications.
Can I buy these accounts in bulk? Absolutely! We offer bulk packages for businesses and agencies that require multiple aged Gmail accounts for their operations.
Start Building Your Digital Presence Today with Aged Old Gmail Accounts
Whether you're a business owner, digital marketer, or simply someone looking to enhance your online presence, aged old Gmail accounts offer a significant advantage. These established accounts provide the credibility, reliability, and trustworthiness that new accounts simply can't match.
By investing in aged Gmail accounts, you'll be able to expand your digital activities with ease, improve your email marketing performance, and grow your business with confidence. Get started today and unlock the full potential of aged Gmail accounts for your professional or personal needs!
This product description emphasizes the benefits and versatility of aged Gmail accounts for various uses such as digital marketing, business growth, and online presence expansion. It's detailed to engage potential buyers by showcasing the advantages of these accounts for multiple industries.
1 note
·
View note