#interceptor software
Explore tagged Tumblr posts
Text
👩🏻💻 𝙰𝚛𝚌𝚑𝚒𝚟𝚒𝚘 𝚍𝚒 𝚜𝚝𝚛𝚞𝚖𝚎𝚗𝚝𝚒 𝚙𝚎𝚛 𝚌𝚢𝚋𝚎𝚛𝚜𝚎𝚌𝚞𝚛𝚒𝚝𝚢 𝚌𝚑𝚎 𝚖𝚒 𝚟𝚎𝚗𝚐𝚘𝚗𝚘 𝚌𝚘𝚗𝚜𝚒𝚐𝚕𝚒𝚊𝚝𝚒 𝚘 𝚌𝚒𝚝𝚊𝚝𝚒 𝚗𝚎𝚕 𝚝𝚎𝚖𝚙𝚘
AnyRun: cloud-based malware analysis service (sandbox).
Burp Suite: a proprietary software tool for security assessment and penetration testing of web applications. La community edition, gratis, contiene Burp Proxy and Interceptor (intercetta le richieste effettuate dal browser, consente modifiche on-the-fly e di modificare le risposte; utile per testare applicazioni basate su javascript), Burp Site Map, Burp Logger and HTTP History, Burp Repeater (consente di replicare e modificare le richieste effettuate, aggiungere parametri, rimuoverli, ecc), Burp Decoder, Burp Sequencer, Burp Comparer, Burp Extender (estensioni delle funzionalità di burpsuite, plugin specializzati per individuare bug specifici, automatizzare parte delle attività, ecc) e Burp Intruder (consente di iterare richieste con payload differenti e automatizzare attività di injection).
CyberChef: is a simple, intuitive web app for carrying out all manner of "cyber" operations within a web browser. These operations include simple encoding like XOR and Base64, more complex encryption like AES, DES and Blowfish, creating binary and hexdumps, compression and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character encodings, and much more.
DorkSearch: an AI-powered Google Dorking tool that helps create effective search queries to uncover sensitive information on the internet.
FFUF: fast web fuzzer written in Go.
GrayHatWarfare: is a search engine that indexes publicly accessible Amazon S3 buckets. It helps users identify exposed cloud storage and potential security risks.
JoeSandbox: detects and analyzes potential malicious files and URLs on Windows, Mac OS, and Linux for suspicious activities. It performs deep malware analysis and generates comprehensive and detailed analysis reports.
Nikto: is a free software command-line vulnerability scanner that scans web servers for dangerous files or CGIs, outdated server software and other problems.
Nuclei: is a fast, customizable vulnerability scanner powered by the global security community and built on a simple YAML-based DSL, enabling collaboration to tackle trending vulnerabilities on the internet. It helps you find vulnerabilities in your applications, APIs, networks, DNS, and cloud configurations.
Owasp Zap: Zed Attack Proxy (ZAP) by Checkmarx is a free, open-source penetration testing tool. ZAP is designed specifically for testing web applications and is both flexible and extensible. At its core, ZAP is what is known as a “manipulator-in-the-middle proxy.” It stands between the tester’s browser and the web application so that it can intercept and inspect messages sent between browser and web application, modify the contents if needed, and then forward those packets on to the destination. It can be used as a stand-alone application, and as a daemon process.
PIA: aims to help data controllers build and demonstrate compliance to the GDPR. It facilitates carrying out a data protection impact assessment.
SecLists: is the security tester's companion. It's a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more.
SQLMAP: is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Subfinder: fast passive subdomain enumeration tool.
Triage: cloud-based sandbox analysis service to help cybersecurity professionals to analyse malicious files and prioritise incident alerts and accelerate alert triage. It allows for dynamic analysis of files (Windows, Linux, Mac, Android) in a secure environment, offering detailed reports on malware behavior, including malicious scoring. This service integrates with various cybersecurity tools and platforms, making it a valuable tool for incident response and threat hunting.
VirusTotal: analyse suspicious files, domains, IPs and URLs to detect malware and other breaches, automatically share them with the security community.
Wayback Machine: is a digital archive of the World Wide Web founded by Internet Archive. The service allows users to go "back in time" to see how websites looked in the past.
Wapiti: allows you to audit the security of your websites or web applications. It performs "black-box" scans of the web application by crawling the webpages of the deployed webapp, looking for scripts and forms where it can inject data. Once it gets the list of URLs, forms and their inputs, Wapiti acts like a fuzzer, injecting payloads to see if a script is vulnerable.
WPScan: written for security professionals and blog maintainers to test the security of their WordPress websites.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝚂𝚒𝚝𝚒-𝚕𝚊𝚋𝚘𝚛𝚊𝚝𝚘𝚛𝚒
flAWS: through a series of levels you'll learn about common mistakes and gotchas when using Amazon Web Services (AWS).
flAWS2: this game/tutorial teaches you AWS (Amazon Web Services) security concepts. The challenges are focused on AWS specific issues. You can be an attacker or a defender.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝙱𝚛𝚎𝚟𝚎 𝚕𝚒𝚜𝚝𝚊 𝚍𝚒 𝚜𝚒𝚝𝚒 𝚊𝚙𝚙𝚘𝚜𝚒𝚝𝚊𝚖𝚎𝚗𝚝𝚎 𝚟𝚞𝚕𝚗𝚎𝚛𝚊𝚋𝚒𝚕𝚒 𝚜𝚞 𝚌𝚞𝚒 𝚏𝚊𝚛𝚎 𝚎𝚜𝚎𝚛𝚌𝚒𝚣𝚒𝚘
http://testphp.vulnweb.com
0 notes
Text
A Comprehensive Guide to Flutter App Development
Flutter, Google's UI toolkit, has revolutionized cross-platform mobile app development. Its ability to create beautiful, natively compiled applications for mobile, web, and desktop from a single codebase has captured the hearts of developers worldwide. But where do you begin? This blog post aims to provide a comprehensive overview of Flutter app development, from the basics to advanced concepts.
Read: Top 10 Benefits of Using Flutter for Your Project
1. What is Flutter and Why Choose It?
Flutter is an open-source UI software development kit created by Google. It uses the Dart programming language and provides a rich set of pre-built widgets for creating visually appealing and high-performance applications.
Key Advantages:
Cross-Platform Development: Write code once and deploy it on iOS, Android, web, and desktop.
Hot Reload: See changes instantly without restarting the app, significantly speeding up development.
Rich Widget Library: Flutter's extensive library of customizable widgets allows for stunning UI designs.
Native Performance: Flutter apps are compiled to native code, ensuring optimal performance.
Growing Community: A large and active community provides ample support and resources.
2. Setting Up Your Flutter Environment:
Before diving into coding, you need to set up your development environment. This involves:
Installing the Flutter SDK.
Setting up an IDE (Integrated Development Environment) like VS Code or Android Studio with the Flutter and Dart plugins.
Configuring emulators or physical devices for testing.
3. Understanding the Flutter Architecture:
Flutter's architecture is built around widgets. Everything in Flutter is a widget, from buttons and text fields to entire screens.
Widgets: The basic building blocks of the UI.
Dart: Flutter's programming language, known for its speed and efficiency.
Rendering Engine: Flutter uses Skia, a 2D graphics library, to render UI elements.
Platform-Specific Layers: These layers handle platform-specific functionalities.
4. Building Your First Flutter App:
Let's break down the basic structure of a Flutter app:
main.dart: The entry point of your application.
MaterialApp: A widget that sets up the app's theme and navigation.
Scaffold: Provides a basic app structure with an app bar, body, and floating action button.
Widgets: Text, buttons, image, listviews etc.
Example of a simple "Hello World" app:
Dart
import 'package:flutter/material.dart';
void main() {
runApp(MyApp());
}
class MyApp extends StatelessWidget {
@override
Widget build(BuildContext context) {
return MaterialApp(
home: Scaffold(
appBar: AppBar(
title: Text('Hello World'),
),
body: Center(
child: Text('Hello, Flutter!'),
),
),
);
}
}
5. State Management:
State management is crucial for building complex apps. Flutter offers several state management solutions:
setState(): For simple state changes within a single widget.
Provider: A popular package for managing app-wide state.
Bloc (Business Logic Component): A pattern for managing complex state and business logic.
Riverpod: A reactive caching and data-binding solution.
6. Navigation and Routing:
Flutter provides robust navigation tools for managing screen transitions:
Navigator: Used to push and pop routes.
Named Routes: For defining and navigating to routes using strings.
Navigation 2.0: A declarative API for more complex navigation scenarios.
7. Working with APIs and Data:
Most apps require fetching data from external APIs. Flutter provides tools for handling network requests:
http package: For making HTTP requests.
dio package: A powerful HTTP client with interceptors and other advanced features.
FutureBuilder and StreamBuilder: Widgets for handling asynchronous data.
8. Advanced Flutter Concepts:
Animations: Flutter's animation framework allows for creating smooth and engaging UI animations.
Custom Widgets: Building reusable custom widgets to enhance your app's UI.
Plugins and Packages: Leveraging the vast ecosystem of Flutter packages to add functionality.
Testing: Writing unit, widget, and integration tests to ensure app quality.
Deployment: Building and deploying your Flutter app to various platforms.
9. Continuous Learning and Resources:
The Flutter ecosystem is constantly evolving. Stay updated with the latest trends and best practices by:
Following the official Flutter documentation.
Exploring Flutter community forums and blogs.
Taking online courses and tutorials.
Contributing to open-source Flutter projects.
Conclusion:
Flutter offers a powerful and efficient way to build cross-platform applications. By understanding the fundamentals and continuously learning, you can unlock the full potential of this incredible framework. Happy coding!
Need Expert Flutter Development?
If you're looking to build a high-quality, cross-platform Flutter application, but don't have the in-house expertise, we can help. Hire our experienced Flutter developers to bring your vision to life.
At Getwidget, we specialize in creating robust and scalable Flutter apps tailored to your specific needs.
Contact Us
Must check out: IoT-Driven Projects Using Flutter: A Comprehensive Guide
0 notes
Text
VPN Software: Comprehensive Guide to Virtual Private Networks
What is a VPN?
A Virtual Private Network (VPN) is a digital privacy tool that creates an encrypted connection between your device and the internet. It routes your internet traffic through a secure tunnel, masking your IP address and protecting your online activities from potential surveillance, tracking, and data interception.

How VPN Software Works
Encryption Process
Data Encryption: When you connect to a VPN, all your internet traffic is encrypted
Server Routing: Your connection is routed through a remote server
IP Masking: Your real IP address is replaced with the VPN server's IP
Secure Transmission: Data is protected from potential interceptors
Key Benefits of VPN Software
1. Online Privacy
Hide your real location and IP address
Prevent ISPs from tracking your browsing history
Protect personal information from potential hackers
2. Security Features
Encrypt data on public Wi-Fi networks
Protect against man-in-the-middle attacks
Shield sensitive information from potential cyber threats
3. Content Access
Bypass geographical restrictions
Access region-locked content
Circumvent internet censorship
4. Anonymous Browsing
Maintain anonymity online
Reduce targeted advertising
Prevent website tracking
Types of VPN Protocols
1. OpenVPN
Open-source protocol
Highly secure and configurable
Works on multiple platforms
Excellent balance of speed and security
2. WireGuard
Modern, lightweight protocol
Faster performance
Simplified codebase
Improved security features
3. IKEv2/IPsec
Stable mobile connection
Quick reconnection
Strong security
Excellent for mobile devices
4. L2TP/IPsec
Good encryption
Built-in on most platforms
Slightly slower than newer protocols
Reliable connection
Top VPN Software in 2024
1. NordVPN
Extensive server network
Strong security features
No-logs policy
Advanced encryption
2. ExpressVPN
High-speed connections
Global server coverage
User-friendly interface
Strong privacy protections
3. ProtonVPN
Swiss privacy laws
Free tier available
Strong encryption
Transparent privacy policy
4. Surfshark
Unlimited device connections
Affordable pricing
Growing server network
Advanced privacy features
5. Mullvad
Strong anonymity focus
Accepts cryptocurrency
Minimal personal information required
Transparent operations
Selecting the Right VPN Software
Key Considerations
Server Locations: Global coverage
Connection Speed: Minimal performance impact
Security Protocols: Multiple encryption options
Privacy Policy: No-logs commitment
Price: Competitive pricing
Device Compatibility: Multi-platform support
Potential Limitations
VPN Drawbacks
Potential speed reduction
Some services may log data
Not a complete anonymity solution
Can be blocked by some websites
Privacy and Legal Considerations
Legal Status
VPNs are legal in most countries
Some nations restrict VPN usage
Always check local regulations
Ethical Usage
Use VPNs responsibly
Respect content licensing
Avoid illegal activities
Setting Up VPN Software
Installation Steps
Choose a reputable VPN provider
Create an account
Download appropriate software
Install on your device
Select server location
Connect and browse securely
Future of VPN Technology
Emerging Trends
AI-powered security
Faster encryption protocols
Enhanced privacy features
Integration with other security tools
Conclusion
VPN software is an essential tool for maintaining online privacy, security, and freedom in the digital age. By understanding its features, benefits, and potential limitations, users can make informed decisions to protect their digital identity.
Frequently Asked Questions
Are VPNs completely anonymous?
VPNs enhance privacy but do not guarantee 100% anonymity. Choose providers with strict no-logs policies.
Can I use a free VPN?
Free VPNs often have limitations:
Slower speeds
Limited server locations
Potential data logging
Less robust security
How much do VPNs cost?
Budget options: $3-$5 per month
Premium services: $10-$15 per month
Annual plans offer significant discounts
Can VPNs be used on multiple devices?
Most modern VPN services support:
Smartphones
Tablets
Computers
Some support unlimited device connections
0 notes
Text
Do you think a partner is cheating on you? Do you think your voice is dressing up and going out more often than she used to? Would you like to have a confirmation if that is happening, or is it just in your head? Cocospy comes in the picture when you have such doubt in your mind. We know this feels like an awful dream, thinking if your partner is cheating on you or not. Well, Cocospy can help read someone's text messages without software installation. Cocospy for Your Rescue! Cocospy comes up with numerous ways for you to confirm if your partner is cheating when you’re not. Moreover, cocospy can help you catch your partner, red-handed. Cocospy can do a lot of other essential things, aside from tracking someone’s location. The app has thousands of different customers who are using it every day. Cocospy is recognized by Toms Guides, CNET, PCMag, TechRadar, Toms Guide, Digital examples, and that is just a hint of something more substantial. Keep this in mind that Cocospy permits you to read messages on iPhones similarly as android devices. You will not have to download or install any software, because Cocospy is an online app that works thoroughly fine on the web browser by picking up details to the target iPhone’s iCloud account or target Gmail account for an Android. Cocospy is among the best text interceptors you can invest in, and it allows you to read texts without presenting the target phone you are spying on. You can easily read the conversations without having to jailbreak the target iOS device or root the target android. You can take a look at Neatspy to find out more about cocospy. How to Read Someone's Text Messages without Any Software Through Cocospy? Here’s how you can use cocospy. All you have to do is follow the following steps, which will cause you no trouble, and we guarantee you that! You have to go to the cocospy website and sign up for a cocospy account. The site will require your Gmail account and ask you to set a password. Please note that this Gmail ID will be your username. After signing up, you will be asked to buy a premium membership. There are two types of memberships available for you to buy. We suggest you buy a family plan if you intend to spy on more than one person, and we recommend you to buy a premium version if you only want to spy on a single person. The next procedure is as easy as learning alphabets. All you have to do is tap a few clicks here and there, and you are good to go. After the setup wizard is set, you will see a start button. If you click it, you will be taken to the dashboard. The dashboard is where you will see all the features that are offered by cocospy. You can explore your options and see what you like. Cocospy makes the process of spying easy for you. Let’s explain with an example, for suppose you want to spy on text messages on the target phone. You will look for the “text message” option in the dashboard of the cocospy. Here you will be able to see all the latest text messages such as sent messages, received messages, draft messages, and deleted messages. Is Cocospy for You? If you have this question in mind, it is completely fine with us, and we will be obliged to answer you. Firstly, let’s see what cocospy offers you. Only then will we be able to tell if it is for you or not. Cocospy is a website based application that does not require you to download or install any app on your target phone. This only means that all you need is a web browser for Cocospy to work for you. Secondly, cocospy does not require you to jailbreak your target iPhone or root your android. This is a unique feature of cocospy. In many reviews, it is said that not many spying apps offer this feature. Let’s be very clear the apps that require a jailbreak or a root on the android phone only make it more prone to getting viruses and malware. Which is not very safe for a phone. One of the best features of cocospy is that it works in complete secrecy.
There will never be the day on which the person you are spying on will find out that you are spying on him if you trust cocospy for your spying needs. This is because you can access Cocospy on the web browser of your personal computer or laptop, and you do not need the target phone. We have heard it about 1000 times that once you buy an app subscription for a premium version, there is no customer service provided by that application. This is where cocospy draws the line. Once you buy our memberships, we will be there for your help and support 24 hours a day. You can ask any question you have in your mind, and we will answer it. We only work to make your life easier and better, especially after you become one of our loyal friends. If the features, as mentioned earlier, are what you’re looking for in your spying app, we are what you need. You answered yourself, Yes! Cocospy is for you. The Bottom Line We hope that with the assistance of this article, you are at long last able to understand How to Read Someone’s Text Messages Without Software. We believe the article, as mentioned above, clears every one of your inquiries. All you have to do is follow the mentioned steps. You will realize that Cocospy is the best thing that happened to you when you chose it out of all the other spying apps. You can use it without having a fear of getting caught. With the help of Cocospy, you can read someone’s text messages without software and also get the miscreant without getting exposed first. You can surely read your kid’s messages and find out what they are up to. Cocospy lets you lead things in your way.
0 notes
Text
How to Use Chrome Extensions with GenQE.ai: A Step-by-Step Guide

In today’s fast-paced software development environment, efficiency and automation are key to delivering high-quality applications. GenQE.ai, the world’s leading AI-powered software testing tool, is designed to streamline your testing process and make it faster, smarter, and more reliable. One of the most powerful ways to enhance your experience with GenQE.ai is by integrating it with Chrome Extensions. Chrome Extensions can extend the functionality of your browser, enabling you to automate tasks, improve productivity, and seamlessly integrate GenQE.ai into your workflow. In this article, we’ll explore how to use Chrome Extensions with GenQE.ai, the benefits of doing so, and step-by-step instructions to get started.
Why Use Chrome Extensions with GenQE.ai? Chrome Extensions are small software programs that customize and enhance the functionality of the Google Chrome browser. When used with GenQE.ai, they can:
Automate Repetitive Tasks: Extensions can automate tasks like test case generation, data entry, and report generation, saving you time and effort.
Enhance Collaboration: Extensions can integrate with communication tools like Slack or Microsoft Teams, enabling seamless collaboration between team members.
Improve Productivity: Extensions can provide quick access to GenQE.ai’s features, allowing you to perform tasks directly from your browser.
Simplify Integration: Extensions can help you integrate GenQE.ai with other tools and platforms, such as CI/CD pipelines, project management tools, and version control systems. By leveraging Chrome Extensions, you can unlock the full potential of GenQE.ai and take your software testing process to the next level.
Step-by-Step Guide to Using Chrome Extensions with GenQE.ai Here’s a detailed guide to help you get started with using Chrome Extensions alongside GenQE.ai: Step 1: Install GenQE.ai Chrome Extension
Open the Google Chrome browser on your computer.
Visit the Chrome Web Store by typing chrome.google.com/webstore in the address bar.
Search for GenQE - AI-Assisted Quality Engineering or use this direct link: GenQE Chrome Extension.
Click on the Add to Chrome button to install the extension.
Confirm the installation by clicking Add Extension in the pop-up window. Step 2: Set Up GenQE.ai
Once the extension is installed, click on the GenQE.ai icon in the Chrome toolbar (top-right corner of the browser).
Log in to your GenQE.ai account or create a new one if you don’t have an account yet.
Follow the on-screen instructions to configure your testing environment, including selecting your project, defining test cases, and setting up integrations with other tools. Step 3: Explore Chrome Extensions for Enhanced Functionality To maximize the benefits of GenQE.ai, consider installing additional Chrome Extensions that complement its features. Here are some popular extensions you can use:
Postman Interceptor: o Use this extension to capture and test API requests directly from your browser. o Integrate with GenQE.ai to automate API testing and validate endpoints.
JSON Formatter: o Format JSON responses for better readability. o Use with GenQE.ai to analyze API responses and identify issues.
Screen Recorder: o Record your browser sessions to document test cases or capture bugs. o Share recordings with your team for better collaboration.
Session Buddy: o Save and manage browser sessions for quick access to frequently used tabs. o Use with GenQE.ai to organize your testing workflows.
Grammarly: o Improve the quality of your test case documentation and reports. o Ensure clear and concise communication with your team. Step 4: Automate Testing with GenQE.ai
Use the GenQE.ai Chrome Extension to generate test cases automatically. Simply navigate to your application in the browser, and the extension will analyze the page to create relevant test scenarios.
Execute tests directly from the browser using the extension’s one-click testing feature.
Monitor test results in real-time and access detailed reports through the GenQE.ai dashboard. Step 5: Integrate with Other Tools
Use Chrome Extensions like Zapier or Integromat to connect GenQE.ai with other tools in your workflow, such as Jira, Trello, or GitHub.
Automate notifications and updates by integrating GenQE.ai with communication tools like Slack or Microsoft Teams. Step 6: Analyze and Optimize
Use GenQE.ai’s real-time analytics to identify trends, anomalies, and potential bottlenecks in your application’s performance.
Leverage Chrome Extensions like Google Analytics or Hotjar to gather additional insights into user behavior and application usage.
Apply the insights gained to optimize your application and retest using GenQE.ai.
Benefits of Using Chrome Extensions with GenQE.ai By combining GenQE.ai with Chrome Extensions, you can: • Save Time: Automate repetitive tasks and streamline your testing process. • Improve Accuracy: Use AI-driven tools to generate precise test cases and identify issues. • Enhance Collaboration: Integrate with communication and project management tools for better teamwork. • Boost Productivity: Access GenQE.ai’s features directly from your browser for quick and efficient testing.
Real-World Use Cases Here are some examples of how teams are using Chrome Extensions with GenQE.ai to improve their testing processes:
E-Commerce Platforms: o Use GenQE.ai to test the checkout process and ensure it works seamlessly across different browsers and devices. o Integrate with Chrome Extensions like Session Buddy to manage multiple test scenarios efficiently.
Financial Services: o Automate API testing with GenQE.ai and Postman Interceptor to validate transaction endpoints. o Use JSON Formatter to analyze API responses and identify potential issues.
Healthcare Applications: o Test telemedicine platforms for performance and reliability using GenQE.ai. o Use screen recording extensions to document test cases and share them with stakeholders.
Gaming Companies: o Simulate thousands of concurrent users with GenQE.ai to test multiplayer servers. o Integrate with communication tools like Slack to notify the team of test results in real-time.
Conclusion Using Chrome Extensions with GenQE.ai is a powerful way to enhance your software testing process. By automating tasks, improving collaboration, and integrating with other tools, you can unlock the full potential of GenQE.ai and deliver high-quality applications faster and more efficiently. Ready to Get Started? Install the GenQE.ai Chrome Extension today and explore the possibilities: GenQE - AI-Assisted Quality Engineering. Transform your testing process and experience the future of quality assurance with GenQE.ai!
0 notes
Text
Guardians of the Code: Ensuring Digital Safety in Software
In today's interconnected world, the dependence on software is more profound than ever. While software solutions revolutionize industries and personal lives, they also open doors to cyber threats. This intensifies the need to prioritize software security, emphasizing code and data protection. Let's journey into the realm of software vulnerabilities and the means to safeguard against them.
The High Stakes of Digital Safety Economic Ramifications:
A security breach can devastate businesses financially. From lost revenue to lawsuits, the economic implications are vast.
Preserving Trust and Reputation:
Trust is hard-earned but easily lost for brands. Data breaches can irreparably damage a company's reputation.
National and Global Threats:
Cyber-attacks can disrupt infrastructures, threaten national security, and potentially trigger global conflicts.
Unraveling the Web:
Understanding Software Vulnerabilities Frequent Culprits: Several vulnerabilities, like SQL injection, cross-site request forgery, and insecure deserialization, are notorious in the cyber world. Recognizing them is pivotal.
Proactive Detection:
Employing vulnerability scanners and regular security audits can detect flaws before they become catastrophic.
Ethical Hackers to the Rescue:
By simulating cyber-attacks, ethical hackers can identify weak spots in software, providing a realistic test of its security resilience.
Crafting Fortresses:
Best Practices in Software Development Inception of Security. Integrate security measures from the initial phases of software development. A proactive approach is always better than a reactive one.
Evolving with Updates:
As threats mutate, so should our defenses. Regular updates and patches keep software a step ahead of potential breaches.
Education is Power:
Equip developers with the knowledge and tools to write secure code. Regular workshops and training can fortify this knowledge base.
Access Control:
By restricting system access to only necessary personnel, the risk of internal breaches diminishes considerably.
The Armor of Encryption:
Encrypting data while it's stationary and during transmission ensures it remains a gibberish puzzle for unauthorized interceptors.
Being the Oracle:
Predicting and Countering Threats Mapping the Cyber Terrain: Stay updated with the ever-shifting threat landscape. Knowledge about current threats equips organizations to tackle them head-on.
Strength in Unity:
Engage in threat intelligence sharing. Collaborating with other organizations and experts can provide a more holistic view of the cyber environment.
Fueling Innovation:
To counteract evolving cyber threats, continually invest in research and development of newer, more robust security tools and protocols.
The Eternal Vigil of Software Security Guarding against software vulnerabilities is a ceaseless endeavor. As technology advances, so do the techniques of those wishing to exploit it. But with a vigilant approach, an emphasis on education, and the willingness to adapt and evolve, we can continue to enjoy the digital age's marvels with a sense of safety.
In the digital realm, the guardians of code and data stand on the front lines, ensuring that the digital world remains a secure space for all its inhabitants.
0 notes
Text
10 Must-Know Tools for Every React JS Developer
React JS developer, having the right set of tools can significantly enhance your productivity and help you build amazing web applications. We will explore ten must-know tools that every React JS developer should be familiar with. From code editors and debugging tools to state management libraries and UI component frameworks, we've got you covered with all the essentials.

1. Visual Studio Code (VS Code)
As a leading code editor, Visual Studio Code is a favorite among developers worldwide. Its lightweight, extensible, and powerful features make it an excellent choice for react js developer. With VS Code's extensive library of extensions, you can customize your environment and enhance your coding experience.
2. React Developer Tools
React Developer Tools is a browser extension that allows you to inspect and debug React component hierarchies. It provides valuable insights into your application's component structure, props, state, and performance. This tool is indispensable for identifying and resolving React-related issues efficiently.
3. Redux
Redux is a popular state management library for React applications. It helps you manage the state of your application in a predictable and organized manner. Redux is known for its single source of truth principle, making it easier to debug and maintain large-scale React projects.
4. Axios
Axios is a promise-based HTTP client that simplifies making AJAX requests in React applications. With its straightforward syntax and support for interceptors and transformations, Axios streamlines data fetching and handling in your projects.
5. React Router
When it comes to building dynamic and single-page applications with React, React Router is a must-have tool. It enables you to handle navigation and routing efficiently, making your application more interactive and user-friendly.
6. Storybook
Storybook is a fantastic tool for developing and testing UI components in isolation. It allows you to build, document, and visualize React components in different states, ensuring that your UI elements are robust and visually appealing.
7. ESLint
Maintaining code quality and consistency is crucial in any software development project. ESLint is a widely used tool for linting JavaScript code, providing real-time feedback and identifying potential errors and code style violations in your React projects.
8. Prettier
Prettier is an opinionated code formatter that helps you maintain a consistent code style across your React application. By automatically formatting your code, Prettier saves you time and reduces the chances of introducing syntax errors.
9. Jest
Jest is a powerful testing framework that simplifies writing unit and integration tests for your React components. With its built-in support for snapshot testing and parallel test execution, Jest boosts the reliability and performance of your test suites.
10. Material-UI
Material-UI is a widely used UI component library for React that follows Google's Material Design guidelines. It offers a wide range of customizable and aesthetically pleasing components, enabling you to create stunning and responsive user interfaces effortlessly.
Conclusion
Hire reactjs developer, having the right set of tools can make a significant difference in your development workflow. From code editors and debugging tools to state management libraries and UI component frameworks, each tool plays a crucial role in building exceptional React applications.
0 notes
Text
Improving API Efficiency With Dio In Flutter: A Comprehensive Guide

If you want to improve the efficiency of your API calls in Flutter to the next level, read this guide further. Here you can explore the benefits of using Dio and how it can enhance the performance of your app’s API integration. Proceed further and find how Dio can help you optimize your Flutter app.
What is an API?
API (Application Programming Interface) enables different software systems to exchange data with each other via communication. It plays a significant role in modern Flutter mobile app development and lets professional developers access data from external sources like web services or databases. Hence, optimizing the API calls can most effectively impact your Flutter app’s user experience and overall performance. Also you can read this on our official website Improving API Efficiency With Dio In Flutter: A Comprehensive Guide.
What is Dio?
In general, Dio is Flutter’s most potent HTTP client that can simplify the process of making API calls. It offers a better user interface, making it simple for Flutter development team to handle network requests & responses.
Benefits of using Dio
Take a look at the below and explore the benefits of using Dio:
1. Concise & Expressive Code
Dio lets you write concise and expressive code to handle API calls effectively. The expressive syntax of Dio makes it easy to define request parameters, query parameters, and headers. Its streamlined approach can make your codebase easier to read and more maintainable.
2. Effective Network Handling
Dio provides extraordinary features to improve network handling in Flutter. It effectively supports request cancellation and lets you terminate ongoing requests when they are not required. It helps prevent unnecessary data and optimize network resources to the next level. Dio offers various options to handle timeouts, intercept requests & responses, and configure HTTP proxies.
3. Powerful Error Handling
Generally, handling API call errors is the primary mobile app development process. Dio simplifies the error-handling process by offering an extraordinary set of features.
It effectively supports customizable error response parsing and lets you extract meaningful information from error responses and handle them effectively. Dio also offers the interceptor mechanism to process and intercept errors globally across your app.
4. Multi-Part Requests & File Uploads
Dio also simplifies the process of handling multipart requests & file uploads. You can easily send files, images, or any other data as part of the API requests with simple lines of code. Such a feature can be useful while working with APIs requiring file uploads like uploading images or documents.
5. Integration With Dio Interceptors
Dio interceptors are the most effective tool to modify, intercept or handle requests & responses at many stages of the API call lifecycle. Add the interceptors easily to Do for performing significant tasks such as adding authentication headers, caching responses, or logging requests. Such flexibility lets you customize Dio according to your app’s specific needs.
Conclusion
From the above scenario, you have explored the guide to improving API efficiency with Dio in Flutter. It helps you to implement Dio in your app effectively and benefit from improved API efficiency. The world is, however, paying close attention to Flutter with Dio. It implies that there will be a massive demand for Flutter engineers. However, you must first grasp the project or demand and your expectations of the Flutter development team before partnering with a reputable Flutter app development company.
Frequently Asked Questions (FAQs)
1. Why is HTTP Flutter better than Dio?
Dio offers additional functionality like interceptors, logs, caches, etc., and fundamental network functions, making it easy to develop clients as quickly as possible. Additional abstractions lessen the amount of code and quicken the development process.
2. What are the tasks that Dio interceptors do?
Dio instances may have one or more interceptors that let you capture errors before they are handled by catchError or the instance itself. Per request and answer, an interceptor is called upon once. It means that redirects aren’t setting off interceptors.
3. In Dio Flutter, how do you refresh a token?
We’ll add an interceptor to the DIO instance to implement automated token refresh. When it notices a 401 (Unauthorised) response from the server, this interceptor will take charge of the token refresh logic.
#flutter mobile app development#flutter development team#mobile app development process#flutter app#flutter app development
0 notes
Text
Logic module from an AN/FSQ-7, the largest computers ever built & heart of the Semi-Automatic Ground Environment air defense system! Designed and built in the 50s, at the height of the cold war, SAGE was a network of computers that processed data from radar stations around the United States and detected enemy nuclear bombers.
Externally, each site looked like this:

Via Wikipedia
Diagram view:
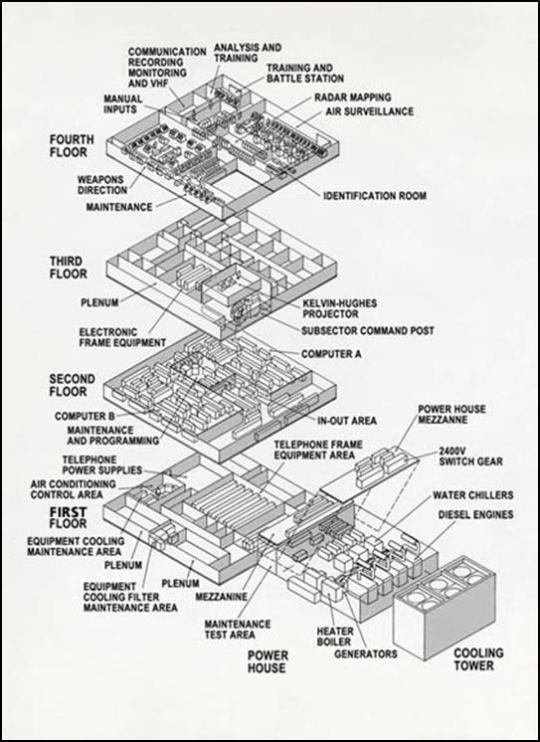
Via MIT Lincoln Laboratory
This is what the internals looked like - each of the "small" horizontal segments you see in the mainframe is what I'm holding in the original photo. These modules were designed to be easy to remove and repair on the fly, since it was vital that the computer not have any downtime. (So much in fact that each site had two separate computers running at all times.)

Via ArsTechnica: The Most Important Computer You've Never Heard Of (which I highly recommend reading if you want to learn more - I was lucky enough to see a talk on the subject by the author)
In the case that an enemy bomber was detected, SAGE would transmit the location to F-106 Delta Dart interceptor:

Via Wikipedia
The F-106 had an onboard computer connected to the SAGE network, and SAGE would autopilot it to the enemy's location. At which time it would be dispatched by Falcon air-to-air missiles, or the (much more interesting/insane) Genie rocket, a 1.5KT unguided (so that it couldn't be stopped/jammed, see) nuclear missile that would be detonated near enough to a bomber formation to hopefully knock them out. Everything in about a 1000 foot sphere would be obliterated, so odds were high.
While it was rendered (mostly, debatable) obsolete by ICBMs several years after it debuted, it was extremely influential in the fields of software design, project management and networking, prototyped computerized air traffic & reservation systems, and had some nifty asides like being the first recorded instance of computer art.
Its also just really cool and I'm beyond jazzed I was able to bring home a tiny piece of it. As an aside, we did a bit of research into my particular piece and suspect it's a part of the input/output system based on the serial number, though we couldn't find an exact match in the documentation.

I've gone and done it.
219 notes
·
View notes
Photo

UK 1985
33 notes
·
View notes
Text
Msi interceptor ds b1 gaming mouse software


Also, backlight could help to determine the active profile, of course if you set the different color for each profile. The backlit will make all “wow-effect" lovers happy. The only disadvantage which I found is that there is no function for auto-activating the profile based on launched software or game. I didn't find any glitch while working with software as well. The software is not complicated and you can learn how to use it without turning to any guide. The weight is not adjustable, which is pretty common for budget category of gaming mice.

Besides the tactile pleasure, such surface helps to seize the mouse even with sweat palm. I liked the coating surface of the mouse. I've tested this mouse for quite a long time in both games and routine tasks, and didn't face with any problem or glitch with it. It looks simple, but has all main features and functions which will fit to both gaming and regular users. Also, you can set number of loops for each command. The pauses between pressed buttons can be recorded in real-time and assigned with default fixed interval. You can test the different settings of this tab before saving in mouse's memory.ĭS100 supports the macro-commands. Also, pay attention to Test Area functionality. In the last tab System Settings, you can tune-up the speed of double-click, pointer and scroll. And again, each parameter can vary for each profile. In the same tab you can select preferred backlit color, brightness level or turn it off entirely. In Advanced tab you can adjust the polling rate. You can adjust X/Y-axis setting independently, if you wish to. In Sensitivity tab, which you can find on the right side of the software, you can adjust DPI resolution of Moreover, mouse support two modes with five profiles in each, so in sum you can keep up to 10 profiles in Certainly, for each profile you can use different assignments. Just click on required button and assign any other functionality, shortcut or macro-command. We can reassign all the buttons from the main windows of the software. The installation process is exactly the same as for any other app within Windows operating system. The cable is braided and connector is gold-plated.ĭespite having disc available, it's always better to download the software from the official website, for making sure that you're using the latest version. By this, after initial setup of profiles and modes, computer will not be necessary for switching either mode or profile. On the bottom-side of the mouse, besides the general information such as serial and model number, there is a hardware button for switching the modes.

There are no buttons on the right-side however, DPI indicator and backlit zones are available. Interesting to note, that side-buttons have a different surface for avoiding miss-clicks. On the left side, there are DPI indicator, two side-buttons and a backlight zone. Also, there is a logo of MSI company which has a backlight (in case of activation). Of course, you can reassign these buttons to any other function via software. On top of the mouse, besides the default mouse wheel, there are two buttons that operate as DPI-level switch by default. MSI DS100 has a symmetric shape, and because of this can be used by both left and right-handed users. Honestly, it's a first time in my experience when the mouse glides were included in the package. Inside the box you can find User's Guide, disc with software and even additional Teflon mouse feet. Actually, you can check design and shape of the The mouse itself is placed under the transparent plastic cover. More details can be found on the backside: specifications, system requirements and key features of the gaming mouse. On the front of the box manufacturer decided to highlight DPI resolution and laser sensor. The mouse is packed in a compact box with a brand-colored design. Due to fact that I have never reviewed MSI's products before, it doubled my interest to test it out. In addition, the company manufactures gaming devices such as mice, keyboards, mousepads. MSI company is well known for its desktops, laptops, motherboards, graphic cards and other “heavy artillery" of the computer world.

0 notes
Text

Rise of the Triad (2013) - Blast Review
Developer: Interceptor Entertainment (now Slipgate Ironworks) Rrp: £10.79 (Gog.com) £10.99 (Steam)
The original Rise of the Triad was created by Apogee Software (who now go by the name 3D Realms) back in 1995. This remake was created by Interceptor Entertainment (now Slipgate Ironworks) and published by Apogee Software, LLC (which is not the same one that created the original) in July of 2013. Three months later the developers Flying Wild Hog would release the reboot of Shadow Warrior (of which the original was created by 3D Realms in 1997) through Devolver Digital. Why mention any of this? Well it's because I kind of feel bad for this game, it really didn't stand a chance. It was relying on the nostalgia of those that played the original only to be overshadowed by a much larger, and to be perfectly honest, much better release.
I know how harsh I'm being in the opening paragraph but I feel its justified. This game is a very lazy remake of the original complete with stupid AI, frankly dull combat and puerile humour. Compare that to the Shadow Warrior remake where the AI, while not the smartest, did try to dodge your attacks, the combat was fast and frantic and the humour... well it was also puerile but in a different way. I can't help but make the comparison.
I remember playing the original version of this game way back in the 90's and even then it felt like yet another attempt to ape the original Doom.
Honestly give this game a miss.
#blast review#game review#games review#game reviews#games reviews#video games#video game#video gaming#interceptor entertainment#apogee software#rise of the triad#rise of the triad 2013#first person shooter#fps#slipgate ironworks#3d realms
0 notes
Photo






Both released in 1983
The Parker Brothers version was considered the best until a new version was released in 1993
#1
Edit * So my first for doubles has become a triple ;)
#frogger#c64#commodore 64#double release#sega#interceptor software#game cover#parker brothers#sierra vision
0 notes
Photo



intercep2.wad: Interception II MAP27: Cargo Cult (6784, -5024, 64) Author: The Interceptors Date: 2020-08-29 Description: Destroy demons in 31 action-packed levels; Interception II is here. Interception II is a Doom II community megawad spanning three episodes with a secret level included. The levels can get quite long, so check it out if you want a megawad you can spend some time with. After defeating Barbatos, you dive deep into the demons' domain, an eldritch world where the rules of our reality don't apply... Shoot, blast, and double-punch your way through otherworldly domains, abandoned space stations, and the blood-soaked fields of Earth. VERSION 1.1: -Fixed a lot of bugs (including a soft-lock on MAP27). -Added a DMAPINFO lump. -Updated the UMAPINFO lump. VERSION 1.2: -Changed the alternate COLORMAPs to be a little easier on the eyes. -I changed the timing of the voodoo doll conveyors in MAP10 to prevent the player from blowing up the doll. -Fixed a soft-lock in MAP13 where the player could get stuck between a lowering silo and the outer walls of the room. -Raised the height of some windows in the sealab in MAP13; this prevents some texture glitching in the software renderer. -Changed the door into the blue key area in MAP15 to stay open, preventing a soft-lock. -Added the proper line action to the secret lift in the northeastern section of MAP15. -Fixed a UMAPINFO bug that routed the secret exit in MAP15 to MAP16 instead of MAP31. -Fixed some missing textures in MAP19 in the computer room window. -Replaced some broken conveyor-belt-style monster teleports with more conventional sound based teleports. -Gave two secrets in MAP24 better hints. -Fixed a soft-lock in MAP27 where you could get stuck behind some crates by the yellow key. -Also in MAP27, made the edges of the ship impassable to prevent running off and getting stuck. Also fixed a few soft-locks on the deck of the ship. -MAP27: Added decorations to prevent the player from getting stuck behind one of the beds down in the ship's quarters. -Fixed a missing texture in the bridge of the ship in MAP27. -Incorporated galileo31dos01's MAP28 patch into the wad. -Moustachio, 20th of January, 2022
20 notes
·
View notes
Text

Saab Arexis selected for the electronic warfare variant of the German Eurofighters
Fernando Valduga By Fernando Valduga 06/16/2023 - 08:27 in Military, Saab
The German Defense Purchasing Office (BAAINBW) selected the Saab Arexis Sensor Suite as the preferred solution for the German Electronic Warfare variant of Eurofighter.
It is important to inform that Saab has not yet signed a contract or received an order related to this.
The process with Saab's Arexis follows the result of a market research recently conducted by BAAINBW, which evaluated the products of European and international Electronic Warfare suppliers, considering aspects such as performance, integration and route to certification.

Arexis system pod installed on a Saab Gripen.
“We welcome this decision and hope to continue with the next steps. The Arexis suite is the perfect match for Germany's electronic warfare requirements for the Eurofighter," said Anders Sjöberg, head of Saab Germany.
Saab's offer states that the company would carry out much of the work at its location in Bavaria, Germany, together with its artificial intelligence partner Helsing.
SAAB's modular Electronic Warfare solution uses advanced hardware and software, including cutting-edge artificial intelligence algorithms to stay superior in complex electromagnetic environments.
Tags: Military AviationEurofighter TyphoonEW - ELECTRONIC WARLuftwaffe - German Air Forcesaab
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, has participated in several events and air operations, such as Cruzex, AirVenture, Daytona Airshow and FIDAE. He has works published in specialized aviation magazines in Brazil and abroad. Uses Canon equipment during his photographic work around the world of aviation.
Related news
HIMARS missile launch system.
MILITARY
Russian Defense Ministry pays cash reward of up to $3,500 for the destruction of HIMARS
16/06/2023 - 16:00
ARMAMENTOS
Sky Sonic: Rafael's new hypersonic missile interceptor
16/06/2023 - 14:00
EMBRAER
Embraer delivers sixth C-390 Millennium aircraft to FAB
16/06/2023 - 13:46
MILITARY
Diamond DART-750 flies for the first time
16/06/2023 - 11:00
EMBRAER
Embraer inaugurates first C-390 Millennium multimission jet flight simulator
16/06/2023 - 09:42
MILITARY
Russian Aerospace Forces: just a shadow of what once was
15/06/2023 - 21:33
homeMain PageEditorialsINFORMATIONeventsCooperateSpecialitiesadvertiseabout
Cavok Brazil - Digital Tchê Web Creation
Commercial
Executive
Helicopters
HISTORY
Military
Brazilian Air Force
Space
Specialities
Cavok Brazil - Digital Tchê Web Creation
1 note
·
View note
Photo

Some familiar-looking space battle action from yesterday’s Death Star Interceptor article.
89 notes
·
View notes