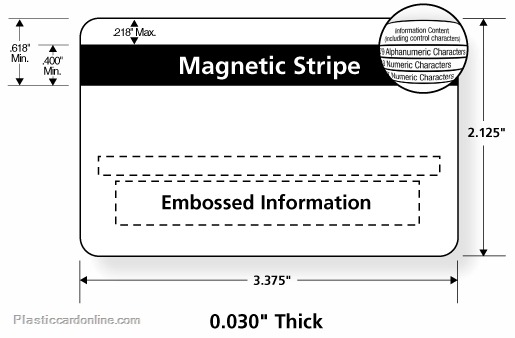
#magstripe encoder
Explore tagged Tumblr posts
Note
could you link to that post where you talked about/talk more about credit card fraud? if you even remember what i'm talking about? i love reading about that kinda stuff
sometimes, if you're lucky, or unlucky, there are unauthorized duplicates of your credit card made during the production process. maybe the wrong color tipping was loaded into the embossing machine, or maybe the mailer was loaded into the printer upside down so your address printed illegibly over a patch of preprinted background color. and when this happens, the embossing machine operator has to take the duplicate cards to the locked gate of the the high security area inside the high security area (the vault) in order to get it voided out, where they lock the duplicates in a cage, until they're ready to take a large batch of them to the high security area inside the high security area inside the high security area (the shred room). and sometimes, in the middle of the night, you can hear it rumbling all across the factory floor because the shred machine is really loud and kind of broken and they're shoving literally thousands of unauthorized but fully functional duplicates of real people's credit cards into it
this really brings the fiction of the whole thing into relief: a credit card is a piece of plastic that has numbers encoded onto the magstrip and the emv chip that link to a bank account without arousing suspicion at the point of sale, much in the same way that a forged coin that fools experts must be real. we're always talking about the best way to pull off a heist at the factory, but i'm always saying you should go big and try to get out with one of the embossing machines and a pallet of gift card blanks
22 notes
·
View notes
Text
How Do Hotel Key Cards Work Across Multiple Doors?

When you check into a hotel and grab that little key card from the front desk, you probably don't think much about how it not only unlocks your room door but also works for the elevator, and even gets you into the gym, business center, or executive lounge. There’s a whole intricate access control system and permission logic behind it. In this article, we’ll take a closer look at how key cards make "one card opens many doors" possible, covering their working principles, security features, and the actual operational processes.
Basics of Key Cards: Structure and Functionality
Magstripe Cards
Magstripe cards were the go-to type of key cards used by hotels for many years. The back of the card features a black magnetic strip embedded with tiny magnetic particles that can hold encoded information. This usually includes:
User ID code
Room number or access area
Card expiration date
When a guest swipes their magstripe card at the door lock or reader, the magnetic head inside captures the strip's data and sends it to the control system for verification. While magstripe cards are cost-effective and part of a well-established system, they have some major downsides:
Wear and Tear: With frequent swipes, the magnetic strip can lose its integrity or stop working.
Easily Duplicated: You can clone a card easily with a cheap magnetic card reader, which poses security threats.
Contact-Based Use: Requires precise swiping, making for a less smooth experience compared to modern contactless key cards.
RFID(Radio Frequency Identification) Cards
These days, most mid-range and upscale hotels have switched to contactless RFID key cards. An RFID card is equipped with a tiny chip and an antenna module, allowing it to communicate with reading devices via wireless radio frequencies (13.56 MHz is the standard frequency).
When a guest brings the RFID card close to a door lock or reader, the device sends out a radio frequency signal to activate the chip, which then sends back a unique ID (UID) along with other data. The system compares this information to access permissions to decide if entry is granted.
Some benefits of RFID cards include:
No contact needed, making them super convenient.
Encrypted communication for enhanced security.
Permission levels can be changed on the fly without replacing the card.
The most common standards for RFID cards include MIFARE Classic® and MIFARE® DESFire®, with DESFire® offering stronger encryption and higher levels of security.
Why Can One Key Card Open Multiple Doors?
Unique Identification Code (UID)
Every RFID key card is assigned a unique UID, sort of like the “ID number” of the card. When the hotel front desk issues a card, they link that UID to the guest’s check-in info and upload it to the central access control management system.
Multi-Permission Logic Binding
Unlike physical keys that can only open one lock, modern hotel access systems work on a permission allocation system, allowing the same UID to grant access to multiple areas. These permissions are configured through the backend system, for example:
Room door (like 1208)
Elevator-accessible floors (restricted to the 12th floor)
Common areas (such as the pool, gym, and executive lounge)
Special locations (like conference rooms and VIP corridors)
This “role + permission” setup not only adds flexibility but also makes it easier to manage and adjust. For instance, if a guest upgrades to an executive floor, the system just needs to modify the permissions without the hassle of reissuing a new key card.
Backend System Coordination and Recognition
The hotel’s PMS (Property Management System) or Access Control System (ACS) continuously compares every card swipe in real time. When the door lock reads the card’s UID, it checks the system to see if that UID has access rights for that door. If the verification goes through, the electromagnetic lock is activated, letting the guest in; if not, the door stays locked, and the attempt is logged.
How Does the Security Mechanism Ensure the Reliable Operation of the Key Card System?
Data Encryption Technology
Modern RFID key cards commonly use advanced encryption methods (like DES, 3DES, AES) to make sure that the data exchanged between the card and the door lock can’t be intercepted or tampered with. Some high-end systems even implement dynamic keys or challenge-response protocols, which means that even if a card gets duplicated, it won't be able to unlock the door it's meant for.
Real-Time Permission Revocation and Expiration Mechanism
The system allows for immediate deactivation of a key card in the following scenarios:
The card is automatically canceled after the guest checks out.
If a card is lost, the front desk can report it lost instantly.
If a guest changes rooms, the old card is deactivated, and the new card is activated.
This significantly reduces the risk of cards being lost and misused.
Card Activity Logs and Monitoring
Every card swipe attempt (success or failure) is logged by the door lock, capturing details like:
Card number
Time of the swipe
Whether the door was opened successfully
Admins can check these logs in real-time to monitor for suspicious activities, resolve disputes, or fine-tune system management.
Anti-Copying Measures
While there are devices available that can duplicate cards, the RFID cards used by hotels are mostly high-frequency encrypted cards with unique identity authentication. This makes it impossible for standard card readers to replicate their full structure and keys. Plus, due to dynamic encryption algorithms, even if duplication does occur, it can only work for a short period before it becomes useless because of key updates.
How are Key Card Permissions Set and Managed?
Card Issuance Process
When guests check in at the hotel, the front desk uses a card encoder to write their check-in information onto the key card, including:
Associating the card UID with the room number
Setting check-in and check-out times
Adding additional access permissions (like for the elevator or gym)
This whole card issuance process usually takes about 10 seconds and allows for repeated modifications.
Modifying Permissions and Issuing Multiple Cards
In the following situations, hotels can quickly make dynamic adjustments to key card permissions:
Room Change: Clear the permissions of the original card and bind a new card to the new room.
Additional Cards: Issue multiple cards for the same room to accommodate more guests.
Late Check-out: Temporarily extend the expiration time of the key card.
Front desk staff can carry out these operations in real time through the PMS system without needing to contact IT personnel, which boosts efficiency.
Differentiated Management of Employee Cards and Visitor Cards
Employee Cards: These have complex and varied permissions, require regular key changes, and are connected to the attendance system.
Visitor Cards: Designed for temporary visitors, granting access to specific areas for a limited duration.
By defining card types and permission templates, the system can automate setups and enable tiered management.
Conclusion: The Intelligent System Behind a Small Card
A hotel key card is much more than just a tool for opening doors; it is actually an efficient, flexible, and secure identity authentication medium. With unique UID identification, centralized permission control, real-time log monitoring, and high-strength encrypted communication, it enables smart access management where "one card opens many doors."
For hotels, key cards not only enhance the customer experience but also serve as crucial tools for security management and operational efficiency. In the future, key card systems will continue to evolve towards higher security, lower manual intervention, and greater intelligence.
If you want to learn more about hotel key card solutions, please visit RFIDCard.com. This company has been deeply involved in the industry for over a decade, producing 100 million cards annually and providing key card products and services for over 2,000 hotels worldwide.
0 notes
Text
Unveiling the Underworld of Cybercrime: Inside Brian'sClub CM
In the digital underbelly of the internet, where anonymity is currency and illicit transactions thrive, one name stands out: Brian'sClub CM. This clandestine marketplace operates in the shadows, specializing in the sale of compromised payment card data, offering cybercriminals an expansive arsenal for financial fraud and identity theft.
BriansClub CM, like its notorious counterpart Brian'sClub CVV, is a hub for cybercriminal activity, accessible only through encrypted channels on the dark web. Here, buyers and sellers converge to exchange stolen credit card information, exploiting vulnerabilities in the global financial ecosystem for personal gain.
Central to Brian'sClub CM's operation is its repository of card magstripe data (hence the "CM" designation), which contains the encoded information stored on the magnetic stripe of payment cards. This data, when harvested from compromised cards, enables cybercriminals to clone cards or conduct fraudulent transactions, bypassing traditional security measures with alarming ease.
The marketplace thrives on a network of hackers, data thieves, and cybercriminal syndicates, who constantly seek out new methods to breach the defenses of financial institutions, retailers, and other entities that handle sensitive payment data. Once obtained, the stolen card magstripe data is promptly uploaded to Brian'sClub CM, where it is meticulously organized and made available for purchase.
The allure of Brian'sClub CM lies in its convenience and reliability for cybercriminals. With a vast inventory of compromised card data readily accessible, buyers can quickly locate the information they need to perpetrate fraud without the technical expertise required for hacking or data theft. Moreover, the marketplace offers tools and resources to streamline the use of stolen data, including tutorials on card cloning techniques and advice on evading detection.
However, the operation of Brian'sClub CM is not without its risks. Law enforcement agencies worldwide are actively engaged in combating cybercrime and shutting down illicit marketplaces like Brian'sClub CM. Recent years have seen numerous arrests and successful operations to dismantle these criminal networks, disrupting their activities and bringing perpetrators to justice.
Furthermore, the consequences of participating in card fraud can be severe, ranging from criminal prosecution and imprisonment to substantial financial penalties and reputational damage. Victims of such crimes, including financial institutions, merchants, and individual cardholders, may suffer significant losses and emotional distress as a result of unauthorized transactions and identity theft.
In conclusion, Brian'sClub CM represents a dark nexus of technology, crime, and exploitation, where stolen payment card data fuels a lucrative underground economy. While it may offer opportunities for cybercriminals, the risks and repercussions associated with such activities are profound. As law enforcement efforts intensify, the lifespan of marketplaces like Brian'sClub CM may be limited, but the ongoing battle against cybercrime remains ever-vigilant.
For More Info :-
bclub cm
0 notes
Text
A Comprehensive Guide to ID Card Printing
ID cards play an important role in identifying individuals in schools, workplaces, events, and more. With advances in printing technology, it's now easier than ever for organizations to create customized ID cards onsite. This guide will explore everything you need to know about ID card printing.
What is ID Card Printing?
ID card printing refers to the process of printing personalized identification cards on blank card stock. It typically involves using a direct-to-card printer (DTC) that can print full-color images, text, logos, barcodes, and more directly onto the cards.
DTC printers offer many benefits over traditional offset printing for ID cards:
Fast turnaround: Cards can be printed on demand as needed, without having to wait for an external print shop.
Customization: Organizations can fully design and personalize the ID cards.
Security: Sensitive data can be kept in-house.
Convenience: New employees can get ID cards printed immediately. Lost or damaged cards can be replaced quickly.
Why Do Organizations Need ID Cards?
There are many reasons why companies, schools, and other organizations need identification cards:
Security – ID cards allow controlling access to facilities and events. Cards can contain RFID chips, barcodes, or magstripes.
Identification – They enable quickly identifying employees, students, event attendees, etc. This improves security and efficiency.
Information – ID cards store useful data like names, ID numbers, departments, access levels, and more.
Branding – Organizations can reinforce their brand by including logos, colors, and other branding elements.
Membership – ID cards serve as a membership card and proof that someone is affiliated with the organization.
Tracking – Usage tracking, time tracking, and other metrics can be tied to the ID card.
Key Components of an ID Card Printer
Direct-to-card printers contain several important components that enable printing directly onto blank cards:
Card feeder – This is the input tray that holds the blank cards and feeds them into the printer one at a time.
Printhead – The printhead contains ink cartridges and precision print nozzles that print the graphics, text, and other elements onto the card's surface.
Encoder – The encoder writes information to the card’s magstripe or RFID chip.
Lamination module – Some printers apply lamination to cards for protection and security.
Cleaning station – Rollers clean and remove debris from card surfaces before printing.
Card flipper – Units that print both card sides contain a mechanism to flip the card over.
Output hopper – The newly printed cards are deposited into the output tray.
ID Card Printer Features
Today's ID card printers offer many features and options:
Single- or dual-sided printing – Print on just the front or both sides of the cards.
Full-color printing – All modern direct-to-card printers offer full-color printing. Most use dye-sublimation for photorealistic images.
Magnetic stripe encoding – The printer can encode magstripes with data that can then be swiped through readers.
Contactless card encoding – Smart card chips and antennas can be encoded with data for contactless ID badges used in access control systems.
Lamination – Applying lamination protects printed cards from wear and tear.
Connectivity – ID printers usually connect via USB or Ethernet and come with card design software.
Print speed – Print speeds generally range from about 100 to over 1,000 cards per hour.
ID Card Printing Supplies
Printing ID cards requires certain supplies, most importantly:
Blank cards – You’ll need blank card stock made of PVC or PET plastic. Cards come in different styles and thicknesses.
ID card ribbons – Ribbons contain the color panels used during dye-sublimation printing. YMC with resin black panels are common.
Lamination pouches – Transparent laminate pouches are applied to card surfaces to protect printing.
Cleaning supplies – Cleaning kits and swabs help clean the printhead and rollers.
Magstripe cards – You’ll need blank cards with magnetic stripes for encoding.
Smart cards – These have embedded RFID chips and antennas for contactless encoding.
It’s important to use only approved supplies that meet your printer manufacturer’s specifications to ensure optimal print quality and performance.
ID Card Printer Costs
Here are the main costs associated with ID card printing:
ID card printer – Printer prices range widely from about $1,000 to $5,000 or more depending on features, print speeds, etc. Additional options like magstripe or smart card encoding increase costs.
Supplies – Ongoing costs for blank cards, ribbons, laminate, and other supplies need to be factored in. These are usually fairly inexpensive per card.
Software – Many ID printers include card design software. More full-featured software ranges from about $500 to thousands for enterprise systems.
Training – Some training on the printer operation and software is recommended to get started.
Overall, ID card printing offers tremendous convenience and professional results at relatively affordable costs for most organizations. For large volumes, outsourcing production may have advantages over in-house printing.
How to Design ID Cards
The first step in ID card printing is designing the cards. Here are some best practices for ID card design:
Include organization branding like logos, colors, and fonts to maintain consistency.
Make sure text is legible by using sans serif fonts and reasonable font sizes.
Use both text and photos/graphics – don’t make it text-heavy.
Focus on key information like names, titles, ID numbers, departments, expiry date, etc.
Front-load important info at the top/front of cards.
Use white space and borders to segment content.
Make any barcodes large and scannable.
Provide visual cues like color coding for easy identification.
Keep it simple. Avoid cluttering the design.
Proofread content closely before finalizing designs.
Consider both aesthetics and functionality.
Using ID card template software simplifies otherwise complex design work. Work with your printer vendor to verify card designs before printing.
How to Set Up an ID Card Printing System
Here are some tips for setting up ID card printing in-house:
Choose a dependable, high-quality ID card printer that fits your volume needs and feature requirements. Top vendors include Zebra, Fargo, Magicard, Evolis, and IDP.
Buy supplies like blank cards, ribbons, and laminate from reputable sources to avoid quality issues.
Install print driver software and card design software that comes with your printer.
Familiarize yourself thoroughly with the printer’s operation and maintenance requirements.
Establish ID card design standards and templates for consistency.
Train staff on designing and printing ID cards properly.
Store blank cards and supplies securely with limited access.
Plan for distribution of finished ID cards to new personnel.
Budget for ongoing card and supply replenishment. Factor in defect rates.
Schedule periodic printer maintenance and calibration to maximize uptime.
Maintaining Your ID Card Printer
To keep your ID card printer running smoothly:
Perform cleaning cycles regularly using cleaning kits. This maintains print quality.
Replace spent ribbons and laminate pouches promptly. Use only approved supplies.
Calibrate the printer as needed if print alignment drifts or cards aren’t being fed properly.
Update printer firmware when new versions are released to fix bugs and improve performance.
Don't expose the printer to dust, debris, liquids, or extremes of temperature or humidity. Keep covered when not in use.
Establish a maintenance schedule for tasks like cleaning the printhead, rollers, and sensors.
Visually inspect cards in the output hopper for defects so any printer issues can be caught early.
If print quality declines, try cleaning the printhead more aggressively and replacing old ribbons.
For smart card encoding issues, try cleaning the encoder head with a fiberglass pencil.
Taking good care of your ID card printer will ensure maximum uptime and print quality. Most issues can be resolved by keeping the printer clean and well-maintained.
Troubleshooting ID Card Printing Issues
Some common ID card printing issues and solutions:
Blank cards – The ribbon is finished or not installed correctly. Replace the ribbon.
Partial printing – Clean the printhead and check ribbon alignment.
Blurry printing – Clean the printhead, rollers, and cards. Calibrate the printer.
Misaligned printing – Realign and calibrate the printhead. Check card thickness.
Card jams – Clear the card path. Clean rollers and sensors. Lube the card feeder.
Encoding errors – Clean the encoder head. Check the card positioning.
Driver errors – Update printer drivers and card design software. Reinstall if needed.
** connectivity issues** – Check cabling, ports, and Ethernet connections. Update firmware.
Feed problems – Clean the card feeder components. Lubricate per manual instructions.
For any persistent issues, contact your printer vendor for support. Provide photos, videos, or sample defective cards to aid troubleshooting.
Key Takeaways on ID Card Printing
Direct-to-card printers allow fast, high-quality card printing in-house.
Proper ID cards enhance security, identification, tracking, and more.
Printer options include dual-sided printing, encoding, and lamination.
Supplies include blank cards, ribbons, laminate pouches, and cleaning kits.
Design focuses on organization branding and key cardholder information.
Proper printer care includes maintenance, calibration, and using approved supplies.
Support from printer vendors can help resolve any issues not fixable in-house.
With a quality ID card printing system and reliable supplies, organizations can produce personalized IDs reliably, quickly, and affordably.
#ID card printing#Custom ID cards#Employee ID badges#Identification cards#Plastic ID cards#Photo ID cards#ID card design#Access control cards#ID card solutions#ID card services
1 note
·
View note
Text
Magstripe Readers | Magstripe Encoder

ID Tech Solutions, Best Quality Magstripe Card Readers India, Supplier, Exporter, Seller, Magnetic Stripe Card Reader, USB Magstripe Reader, Audio jack magstripe Reader, Card Reader For Magstripe Cards, Magstripe Cards Reader and Encoder, Square Magstripe Card Reader Supplier/Dealer, Buy Magstripe Card Reader At Best Price, For Laptop In India, Delhi, Gurgaon.
#Magstripe Readers#Magstripe Encoder#Audio Jack Card Reader#Magnetic Stripe Card Reader#Audio jack magstripe Reader#Magstripe Card Reader Supplie Dealer
0 notes
Text
Magstripe Encoder | Magnetic Stripe Card Encoder | USB Magstripe Encoder

ID Tech Solutions Manufacturer, Supplier, Exporter, Seller, Trader Of Best Quality Magstripe Encoder, Magnetic Stripe Card Encoder, USB Encoder, Encoder For Magnetic Stripe Card, Magnetic stripe Card Encoder Supplier/Dealer, Buy Magstripe Card Encoder At Best Price In India, Gurgaon, Delhi, Laptop Best Quality Magnetic Stripe Card Encoder.
#Magstripe Encoder Supplier India#Magnetic Stripe Card Encoder#Magnetic Stripe Card Gurgaon#Buy Magstripe Card Encoder delhi
1 note
·
View note
Photo

cacall2021’s Top 7 Online Payment Trends You Should Know We hail from an era that has made tremendous technological advancements in every sector, whether that’s healthcare, fashion, food, sports, financial, etc. However, we will mainly focus on the massive advances made in the financial sector when the whole payment system shifted rapidly to digital mode..
Gone are the days when we used to check our wallets twice before leaving home. All we need is our mobile phone to make digital payments, or smartwatches can also do the work. Digital payment has attracted billions globally, even before the pandemic scenario. However, it acted as a turning point from 2020 where people wanted to make contactless payments and maintain social distance..
Contact-free payment tech became the safer option for people enabling the global online payment industry to hit USD 5.4 trillion in 2020. Digitalization has given people the opportunity to make faster payments with convenience and security. Cashless payment systems are putting in more effort to make the payment systems safer and secure.
Mobile app development companies are looking towards some more advancements to the current digital payment systems. Well, here are some of the best 2021 trends you want to know to boost your company’s success.
Top Cashless Payment Trends to Change the Dynamics of FinTech Industry
1. EMV Technology Shifting from reading the number printed on the cards, EMV tech is more secure. Europay, Mastercard, Visa (EMV) tech is a new payment method computerized and has higher security measures. Conventional magstripe cards stored all the data in a single magnetic strip, and one swipe was adequate to complete the transaction. Simultaneously, EMV cards have microprocessor smart chips with encoded data to save you from being scammed.
EMV is a super-advanced tech to finish transactions in offline mode too. Since the cards have microprocessors to interact with terminals, cardholder validation & offline transaction validation is possible. Enhanced security with no need for internet connectivity to the banks makes this new payment system one of the top payment trends.
2. Smart Speakers
With the revolution in payment technology, voice assistants are used to paying the dues. Smart speakers receive your voice command & answer your queries. Everything is possible, from booking a taxi to ordering food with these incredible speakers. All you need is to order Alexa, and the payment is made! Home assistants can be used to shop for products like groceries, home care, clothing, etc.
As per Business Insider, the use of smart speakers will rise from 18.4 million users in 2017 to 77.9 million users in 2022.
3, Biometric Verification
This is one of the most anticipated technologies of the online payment world. Biometrics authentication methods can make payments safely and securely. The biological & structural attributes of a human will help the system to verify him/her. The digital payment will be made after evaluating the biometrics through face recognition, heartbeat analysis, iris recognition, vein mapping, and fingerprint scanning.
This verification system can prevent thefts and frauds. Biometric authentication will secure the Tap-and-Go payment method with improved security in place. Efficiency, accuracy, & security are the three tiers of this payment trend..
4. mPOS Payment Technology
mPOS stands for mobile point-of-sale, and its demand is rising each day. Everyone is looking ahead on accepting payment through this mobile, be it a retail store or any street merchant. An mPOS is movable and can be plugged into the charging ports of smartphone devices.
A great mPOS tech can gather data and help you in expanding your business. This payment tech can make a substantial difference in making your business more efficient & well-organized. According to Global Market Insights, a CAGR of 19% is expected between 2020 to 2026. 5. Artificial Intelligence & Machine Learning-based Payments AI and ML are the future of the payment industry. The most crucial aspect of every payment method is to be secure and safe. AI integration into the payment system can guarantee convenience and safety. An online payment system can have chatbots to offer 24*7 assistance to the users and respond to their queries. AI-based digital payment tech can flag unusual bills and tips that are higher than normal. AI eliminates the need for payment verification from banks. Amazon’s Deepens Tech eliminates the need to visit the cashier to bill your items. 6. e-Wallet Solutions As reported by RetailDive, approximately 2.1 billion customers were using e-wallets in 2019. Mobile wallets are the new payment method acting as a virtual wallet, saving a person’s payment information on the smart device. You can send & receive funds virtually through a digital payment system. Transactions take no more time than a single tap, consuming less energy and time compared to net banking. Some of the advantages of this payment system include getting discounts, gift cards, vouchers, and great deals.
7. NFC Technology You can pay money through your smartphone or credit card without having any physical contact. Besides being quick, smartphones or credit card systems ensure safety from viruses and bacteria. NFC (Near field communication) tech powers contactless payments through RFID (radio frequency identification). A particular radio frequency enables the payment to be made via smartphone or card when the payment reader device and the payment tools are close to each other. Contactless payments are safer than magnetic stripe cards. These strips use obsolete tech, which is easily prone to become the victim of frauds and identity thefts. Digital Payment Methods Will Continue To Boom Digital payment tech, with the help of the top app development companies are reshaping the fintech industry. Several companies are investing heavily to make online payment systems more advanced and secure worldwide. There are several benefits of using these new payment methods, and in 2021 we may come across more. While digital payment trends will continue to boom, we must remember that the essential aspect is ‘Security.’
1 note
·
View note
Text
PROMO! WA 08118-799-07 - Kartu RFID, ATM Smart Card, ID Card
PROMO! WA 08118-799-07 - Kartu RFID, ATM Smart Card, ID Card
Kunci Kartu Hotel, Kartu Diskon Hotel, Magnetic Bank Card, Kartu Smart Card, RFID Card Manufacturers, Cetak Kartu ATM di Surabaya, Magnetic Gift Card, Kartu ATM Magnetik, RFID Key Card, ID Card Magnetic Jakarta
CV. GRAMMI COMMUNICATION TECHNOLOGY, dikenal juga dengan nama Grammi, didirikan pada tahun 2008, sejak awal perusahaan kami…
View On WordPress
#bahan id card#cara bikin id card#desain id card#how to make a magnetic card writer#id card bandung#id card printing service#id pvc card#magnetic card programmer#magnetic card system#magnetic gift cards#magnetic id card#magnetic strip recognition#magnetic track#magstripe encoder#membership card#plastc card#plastic discount cards#plastic for cards#pvc cards with magnetic stripe#tempat id card
0 notes
Text
Chip reader credit card terminal

Chip reader credit card terminal code#
Is Your Business Required to Accept EMV Chip Cards?Īny business that processes credit or debit card purchases does not, legally, in the US, have to include an EMV card reader. To accept EMV chip cards at your business, you need to switch out your card reader and processor for a processor that reads activated chip-enabled credit and debit cards. How to Accept EMV Chip Cards at Your Business Is Every Chip-Enabled Card EMV Compliant?Ī Visa, Mastercard, Discover, or AMEX-issued chip card is EMV compliant as it is designed for use with POS EMV-compliant technology. EMV compliance means that a company uses point-of-sale (POS) processing equipment that features a credit card reader supporting EMV technology. The technology is growing rapidly, especially in parts of Canada and Europe. Today, EMV represents the worldwide standard for debit and credit card processing. While chips for EMV cards encrypt and secure data, the older magstripe cards carry static data on their magnetized strips. Why are EMV Cards More Secure?Ĭard-present transactions that include EMV chip technology make it difficult for fraudsters to copy information.
Chip reader credit card terminal code#
The EMV chip creates a unique code each time a customer makes a purchase, thereby encoding a new entry each time. Therefore, thieves can easily steal the data via phone apps or strip readers. This information, which is not encrypted, makes it easy to make a counterfeit card. The magnetic stripes on the older debit and credit cards carry all of a cardholder’s data. These three companies are responsible for putting the chip-and-pin or chip-enabled EMV card into use. “EMV” stands for the payment systems, Europay, Mastercard, and Visa. An EMV chip credit card greatly reduces fraud and speeds up in-store purchases. EMV represents the world standard for taking credit card transactions at physical point-of-sale (POS) locations and virtually.

0 notes
Text
What Information Is Stored on a Hotel Key Card? Security Risks & Myths

When you check into a hotel, the front desk usually gives you a little room key card. This card not only opens your door, but it often comes with a bunch of rumors, like:
“Does the hotel key card store my personal information? If I lose it, can someone steal my identity?”
“Does the key card record my credit card info, leaving me open to fraud?”
“Can hackers scan my key card with their phone and then make a fake card to unlock the door?”
These claims sound pretty alarming, but are they really true?
In this article, we'll dig into what information hotel key cards store, the potential security risks, and how to properly protect your key card, so you can feel more secure when using it.
What kind of information is stored on hotel room cards?
How hotel room cards work
The main role of hotel room cards is to serve as electronic keys, allowing the holder access to specific rooms for a set period of time. The data stored on these cards depends on their type:
Magstripe Card: This works like a credit card, using a magnetic strip to store data and requiring a swipe to read.
RFID (Radio-Frequency Identification) / NFC (Near Field Communication) smart cards: These use wireless technology for data transmission, letting you “tap” them without any contact.
While the technology behind these two types of cards is different, their main function is the same: granting room access.
Commonly Stored Information
Hotel room cards usually don’t store personal identification information; instead, they typically include the following data:
Room number (usually encoded or encrypted, so the actual room number isn’t displayed when read directly)
Check-in and check-out dates (this helps the system determine if the card is still valid)
Internal identification code for the hotel system (used to match with the hotel management system, not personal identification data)
When you swipe your card at the door lock, the lock system checks the card information against an internal database to decide whether to let you in.
Information Not Stored
A lot of folks worry that hotel room cards could be keeping their sensitive data, like:
❌ Name, ID number, passport number (this info is only stored in the hotel front desk's system)
❌ Credit card information (payment details are stored in the hotel’s financial system, not on the room card)
So, even if someone finds your room card, unless they know your room number, they can’t directly access your personal information or credit card data.
Security Risks of Hotel Room Cards
Can hackers clone hotel room cards?
Yes, magstripe cards can be cloned since their data storage method is quite basic. Hackers can easily use cheap card readers (which only cost a few bucks) to read and copy the magnetic stripe data.
However, most modern hotels have switched to encrypted RFID/NFC smart cards, which have their data protected by encryption. It’s tough for hackers to crack or replicate this data, even if they manage to scan it.
Can losing a room card lead to theft?
If you lose your room card and someone finds it, they might try to use it to access your room.
But hotels typically have these security measures in place:
Room cards don’t display the room number (most hotels have stopped printing room numbers on cards to prevent finders from easily locating the room)
The front desk can instantly deactivate the old card (once you report a loss, the hotel will quickly invalidate the old card and issue a new one)
Some hotels use one-time room card technology (the old card will automatically be disabled once it’s replaced by a new one)
So, if you lose your room card, be sure to contact the front desk right away to get a new one, which will clear up any security concerns.
Can hackers read hotel room card information remotely?
Magstripe cards require physical contact with the card reader, so hackers can't read them from a distance.
RFID/NFC cards might be scannable in theory, but due to encryption, hackers can't easily decipher or copy that information.
Even if someone tries to use "wireless hacking tools" to scan your room card, they won’t be able to extract valid room information directly from it.
Common Misconceptions About Hotel Room Cards
❌ Misconception 1: Hotel room cards store credit card information
✅ Fact: Credit card information is stored in the hotel management system; the room cards are just for access control and don’t involve payment data.
❌ Misconception 2: Hotel staff can read your room card information remotely
✅ Fact: You need physical equipment to read room card information, and the data is encrypted, so ordinary staff can’t access it without proper authorization.
❌ Misconception 3: Old room cards can be reused or stolen
✅ Fact: Once an old room card expires or gets replaced by a new one, its data becomes invalid and cannot be used again.
How to Protect Your Hotel Room Card
If you lose your room card, notify the hotel front desk right away.
They can quickly deactivate the old card and issue you a new one to prevent any unauthorized access to your room.
Avoid placing your room card next to your phone or wallet (for magnetic strip cards).
Magnetic strip cards can lose their magnetism due to interference from magnetic fields, making them unusable.
When you check out, you can either keep the room card or return it to the front desk.
If you're worried about it being misused, you can get rid of it yourself, but most hotels will recycle room cards and reprogram them, so your security isn’t compromised.
Use mobile keys instead of physical cards.
Many upscale hotels have rolled out mobile app room keys (like Hilton Honors, Marriott Bonvoy), which are safer than traditional cards because the data is stored on encrypted mobile devices, making it hard for hackers to duplicate.
Conclusion
Hotel room cards are generally safe and don't store personal information or credit card data. Magnetic strip cards carry a risk of being duplicated, while RFID/NFC smart cards are more secure and harder to crack. While losing a room card won’t directly lead to your information being exposed, it can still be misused by criminals, so it's crucial to contact the hotel right away to report it lost and get a replacement. Some hotels have rolled out mobile electronic room keys for a safer and more convenient option. By understanding the safety features of room cards and developing good habits—like keeping them secure and reporting them lost promptly—you can significantly enhance your safety while staying and ensure a worry-free trip.
If you want to learn more about hotel key cards, check out RFIDCard.com, a supplier that's been in the game for over a decade, producing 100 million cards a year and providing key card products and services for over 2,000 hotels worldwide.
0 notes
Text
ColorMax Printing manufactures Magnetic strip card,hico and loco for various industries using
UNDERSTANDING MAGNETIC STRIPE CARDS
Order magnetic stripe cards. Magnetic stripes or mag stripes, are the dark strip of magnetic material often seen on the back of gift cards, loyalty cards and membership cards, which are used in conjunction with a POS system. Mag stripe cards are also used in access control as key cards, as well as on ID cards. They come in two main varieties: high-coercivity (HiCo) and low-coercivity (LoCo).
High-coercivity magstrips are harder to erase, and are more appropriate for cards that are frequently used or require extended life. Low-coercivity magstrips require a lower amount of magnetic energy to record, reducing their cost. Gift cards, loyalty cards, fundraising cards and membership cards typically utilize a LoCo magstrip. A magnetic stripe card reader can read either type of magnetic stripe.
WHAT IS MAGNETIC STRIPE ENCODING,
When magnetic stripes are encoded, a unique serial number is stored on the strip. This serial number is recognized by the POS system or access control lock device, providing access to funds stored on the POS system or opening a locked door.
Our magnetic stripe encoding services will ensure that your mag stripe cards work with your card reader hardware and software. There are three available encoding tracks on a magnetic stripe (aka magstripe), with the first two tracks being the most commonly used. Magnetic stripe encoding is perfect for gift cards, loyalty cards, membership cards and more.
HOW DOES IT ALL WORK,
Using a gift card as an example, a customer purchases a gift card, which is swiped by the cashier to obtain the serial number stored on its magnetic stripe. The cashier then asks the customer how much money they would like to be “placed” on the gift card. That amount is entered into the POS system by the cashier.
The next time the gift card is swiped, the POS system uses the serial number stored on the magnetic stripe to look up the customer’s card balance, which is stored on the POS system using the same serial number. Sometimes, a POS system may fail to read a magnetic stripe. That’s why we also recommend printing the same serial number directly onto the card’s surface. This is called a human-readable number.
Loco magnetic strips (300OE)
Loco magnetic stripe card is perfect for short-term applications where top level high security and lasting card life are less of an issue. The magnetic stripes on these cards are more of a brownish tone, while HiCo mag stripes are nearly black in color. LoCo cards utilize a lower strength electromagnetic field and are utilized for a range of applications consisting of gift cards, membership and loyalty cards, transit passes, hotel space secrets, amusement park passes, grocery club cards, and much more.
Hico magnetic strips (2750OE)
Hico magnetic stirp card has actually now been completely embraced by the banking market and is likewise utilized in the bulk of access control applications. It must be kept in mind that the greater the coercivity, the more pricey the magnetic tape is. The key distinction is HiCo magstripe card is encoded with a more powerful magnetic field that makes them more ideal for safe and secure applications and for when the cards might be swiped more often.
So what should i chose, Hico or Loco,
The answer is Loco magnetic strip. Magnetic stripe readers are “blind” as to whether a stripe is HiCo or LoCo and are developed to check out both. LoCo magnetic stripe cards are perfect for most applications. 95% of our clients chose loco magstrip card. But if you run a bank, you need hico magstrip card of course.



Magstrip card encoding
Each magnetic strip card encoding consists of 3 tracks of details and the requirements and abilities of these is summed up as below.

Magstrip card encoding track 1

Magstrip card encoding track 2
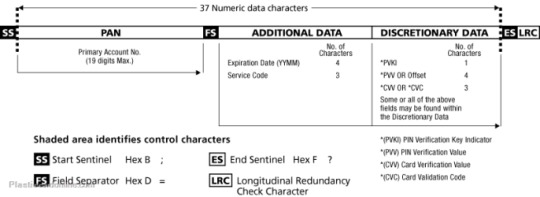
Magstrip card encoding track 3

Which track is the best to encode the information, 1, 2 and/or 3,
The answer is track 2, we can do seuqential or random number encoding according to client’s needs.
Magnetic plastic card applications
For membership cards
A magnetic stripe card, which might read by “swiping” it in a reading gadget. Each magstrip card from plasticcardonline.com has a magnetic stripe that is encoded with a distinct serial number. The value of the magnetic strip card is not saved on the card however within the point of membership card software in the shop. When the consumer returns with the card, the magnetic stripe is “swiped” or the human understandable characters are gotten in. The client might include added funds to the card or utilize its value to make a purchase.
Magnecti swip card for hotel door locks
Magnetic stripes are likewise utilized with lock systems such as hotel or institutional. The magnetic swip card is embedded in the back of a key card and the lock system encodes each card with the distinct code to get. You may contact your door lock system provider if you are not sure exactly what type of magnetic stripe or encoding your system needs. They can aid you with which kind of magnetic swip card will work best and the essential characters to be encoded for your certain system.
WHAT IF I ALREADY HAVE CARDS, BUT NEED THE MAGNETIC STRIPES ENCODED,
No problem. We can encode the magnetic stripe to your specifications. We can also manufacture and warehouse your PVC cards for delivery as needed.
WHAT DO I NEED TO KNOW IF I WANT MAGNETIC STRIPES ON MY CARDS,
To ensure your custom magnetic stripe cards will function properly, there are a few things you will need to know. Your POS or lock system provider will be able to assist you in obtaining this information.
Does your POS or lock system require magnetic stripes to be HiCo or LoCo, Or, is either option okay,
There are three available “tracks” or areas on your magnetic stripe. Which track or tracks should be used to encode your serial numbers onto your cards, Additional information regarding supplied data specifications can be found on our data specifications page.
There are two types of serial number formats: random and sequential. Which format is required by your POS or lock system, If random, are specific characters or a specific number of characters required, If possible, it’s best to obtain a random number file from your POS or lock system provider. If your serial numbers are sequential, what number should we start with,
Note: Some print options or print option combinations are not possible due to card thickness and other factors. Please contact us to verify which print options will work for you. Check with your POS system provider to answer any option questions you might have. This is important to ensure that your card’s barcode or magnetic stripe will be compatible with your POS system.
Additional cost for custom magnetic strips
Loco magnetic strips
+$40/1000pcs
300OE Order
Hico magnetic strips
+$80/1000pcs
2750OE Order Source: ColorMax Printing manufactures Magnetic strip card,hico and loco for various industries using
Need repost your products or artices, click Here
0 notes
Photo

ID Tech Solutions offers a wide range of encoder for magnetic stripe cards also known as Magstripe Encoder. MSR605 is a standard magnetic stripe card reader-writer. It is ideal for access control, timekeeping, banking, ID recognition, credit verification, and related applications. In fact, wherever a magnetic stripe ID or transaction card is used, one can find a related use for the versatile, user-friendly MSR605 reader-writer. MSR605 is designed to offer a reading and writing solution of high and/or low coercivity cards that will attractively complement an existing system.
#magnetic stripe cards#Magstirpe Encoder#USB encoders#Magnetic Stripe Card Encoder#ID Tech India#MSR605#access control#MSR605 reader-writer#rfidtags
0 notes
Photo

Dream Journal 2017-05-17: The Surplus Electronics Man
Here in the U.S., there are environmental regulations that you’re supposed to comply with when disposing of electronic equipment. So when you put that old computer out on the curb for the trash disposal people to pick up (sans hard drive, of course!), you’re probably unknowingly violating those statutes. It’s okay, though; I won’t tell anybody!
Anyway, the dream starts in my office and my coworker is telling me a story about a recent adventure he took to dispose of some old lead-acid batteries. And because this is a dream, I don’t have to just listen to the story; I CAN EXPERIENCE IT FIRSTHAND! My coworker starts telling his story and I am transported somewhere else. The last vestiges of daylight are shrinking into a purple horizon.
My coworker has a literal wagon-load of rectangular lead-acid batteries, and he is walking along an empty highway to make it to the local auto parts store. He’s trying to comply with the real-life regulation where you have to surrender these batteries to an authorized disposal facility. Basically, any place that can deal with car batteries can deal with the batteries we’re trying to get rid of. But the auto parts store is closed!
Fear not, my environmentally-conscious readers! There is a backup plan!
We travel down the road some more, turn down some side streets, and now we are in front of what appears to be a junk yard. A man in a trenchcoat is sitting on top of a nearby fence. He hops to the ground as we approach.
“What do you have to trade?”
It occurs to me as I am writing this out that the man in the coat is working as a metaphorical fence: someone who knowingly buys or deals in stolen goods.
“I have some batteries,” my coworker says. The man in the trenchcoat inspects the batteries with a careful eye, walking around the wagon.
“I’ll give you a magstripe encoder and an embosser for the whole lot,” the trenchcoat man says after a long pause. And in case you were wondering, a magstripe encoder is the machine that puts the necessary information on that black magnetic strip on the backs of your credit cards. The embosser is the machine that makes the raised letters on the cards.
This seems like a phenomenally good deal, if you are someone who feels like committing a lot of fraud. But the machines come with a catch: they are broken in such a way that they can only be used to encode information on credit cards with a credit limit of $50 or less. Depending on your perspective, this could be either a bug or a feature. It sucks that you can’t make cards with high credit limits, but you can still make basically an unlimited number of $50 cards and it’s difficult to buy enough stuff with those cards to be found guilty of grand larceny, so you’ll probably get away with the legal equivalent of a slap on the wrist if you get caught.
My coworker is an honorable man, but he is also incredibly curious about all manner of things. He accepts the offer and walks away with the new machines. My perspective shifts and I am back in the office, talking to my coworker.
“Hey, do you want a card that only has $23 on it?” he asks me.
HELL YES I DO, COWORKER! DO YOU KNOW HOW MANY BURRITOS I CAN BUY AT MY LOCAL GAS STATION FOR THAT MUCH MONEY? I CAN BUY MORE BURRITOS THAN I HAVE FINGERS ON BOTH HANDS, AND THAT IS A WORTHY PURCHASE.
And that’s the story of how I ended up with a fake credit card and an imminent massive burrito purchase and/or misdemeanor conviction.
------------
Header image of a shady dude selling stuff taken from here.
#batteries#fraud#credit card#trash#burritos#dreams#dream journal#fishdavidson#larceny#theft#trenchcoat
4 notes
·
View notes
Text
Magnetic Stripe Reader Market Size 2019 Outlook, Opportunity, and Demand Analysis Report by 2025
A magnetic stripe reader, also called a magstripe reader, is a hardware device that reads the information encoded in the magnetic stripe located on the back of a plastic badge. Magnetic stripe readers can be read by a computer program through a serial port , USB connection, or keyboard wedge , and are generally categorized by the way they read a badge. For instance, insertion readers require that the badge be inserted into the reader and then pulled out. Swipe readers require that the badge pass completely through the reader.
Read More: https://www.marketwatch.com/press-release/magnetic-stripe-reader-market-size-2019-outlook-opportunity-and-demand-analysis-report-by-2025-2019-12-04
0 notes
Text
ICQ : ((726638298)) SELLING FRESH CVVS FULLZ DUMPS+PIN PAYPAL BANK LOGIN WU
New Bluetooth MSRX6(BT) Credit Card Reader/Writer/Encoder Magstripe Swipe MSRX6 MSR206
Deftun MSR605 HiCo Magnetic Stripe Card Reader Writer Encoder MSR206
MCR200 EMV Smart IC Chip Card and Magnetic Stripe Card Reader and Writer
HCC100 USB Magnetic Stripe and IC Chip Card Reader Writer MSR+Chip All In One With SDK
(Perfect Money), WU(Western Union), BTC(Bitcoin) , PAYPAL (PP)
Shop Sell Dumps Track 1&2 Cvv Online - Buy Sell Dumps CHINA /
HONGKONG / EU / USA / CA / AU Fresh & High Balance -
Best Shop Dumps Online 2018 - Sell Dumps Good Fresh 99%
Email : [email protected]
ICQ > 726638298
0 notes