#malware targeting crypto
Explore tagged Tumblr posts
Text
सावधान! ये नया मालवेयर आपकी स्क्रीन से चुरा लेता है बैंक डिटेल्स, जानें क्या है बचने के उपाय
[NEWS] Coyote Malware: एक नया और खतरनाक साइबर हमलावर सामने आया है जिसका नाम है Coyote मालवेयर. यह मालवेयर अब Windows के accessibility tools को ही अपना हथियार बनाकर यूज़र्स की बैंकिंग जानकारी चुरा रहा है. यह मालवेयर खासतौर पर Windows की UI Automation फीचर का गलत इस्तेमाल करता है जो मूल रूप से दिव्यांग यूजर्स की सहायता के लिए बनाया गया था. कैसे काम करता है यह मालवेयर? Coyote आमतौर पर एक वैध दिखने…
#coiote#como funcionan los malware#coyote#coyote fur#Coyote Malware#coyote trojan#coyote virus news#coyotemalware#coyotetrojan#crypto malware#latest tech malware#lumma malware#malware#malware bancario#malware in windows systems#malware stealing bank details#malware targeting crypto#malwarealert#new malware 2025#tech news#TECH NEWS HINDI#uia malware attack#virus coyote#virus coyote de brasil#Windows#windows malware alert#windowsmalware#कोयोट मालवेयर#टेक टिप्स#टेक टिप्स हिंदी
1 note
·
View note
Text
Malware Torrents: The Telltale Signs
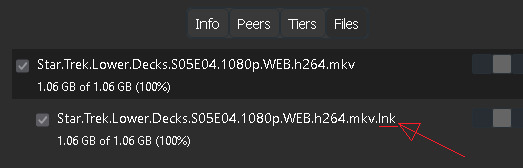
Be careful with piracy torrents you guys. The majority of them are legit, but every once in a while you'll find someone trying to use them to spread malware. Recently someone uploaded a torrent masquerading as an episode of a TV show I like, but when it downloaded I saw it was actually a disguised shortcut (.lnk file) with a crypto miner attached to it, with just over 1 BILLION zeroes added to the end to make the file big enough to look like a valid video.
The first warning sign was that the episode was uploaded almost 3 days before it actually aired. That's rare, really only happens with hacks/leaks and those are usually newsworthy. Second, my automatic media organizer software refused to import it because it was "not a video file". Again, weird; why wouldn't my software recognize a valid video?
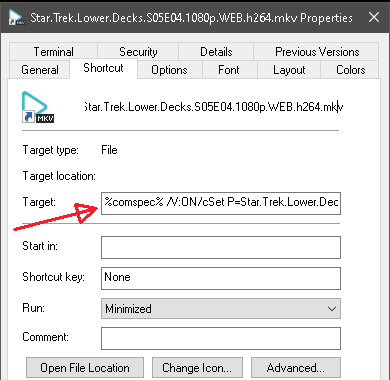
However the BIGGEST red flag was when I went to look at the downloaded file, it had a tiiiiiiiny curved arrow on it indicating that it was actually a shortcut, not a video. When I hovered over it, it showed that it was actually pointing at a completely different file in a protected system directory.


When I viewed the shortcut properties, I could see that it was going to run a command prompt and execute a batch command that installed an executable that would run every time I started my computer (basically, do a bunch of shit it shouldn't be doing. A video file shouldn't even have a target field, let alone one with command prompt stuff in it).
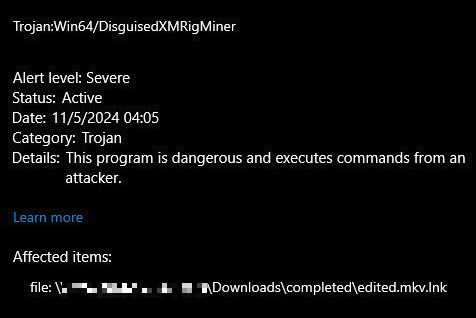
I had to learn how to use a hex editor to delete the billion zeros and separate the .lnk part (the install command) from the actual malware, and the instant I did that Windows Defender flagged it:
So. How can I identify suspicious torrents ahead of time?
When I went to inspect the torrent, in hindsight it was easy to see it was bad because of the file extension, but you can only see that if you inspect the files in the torrent, not just the torrent name. Many piracy sites don't bother showing you a list of files in the torrent ahead of time, so be sure to inspect them once they're in your download client.
I recommend familiarizing yourself with common media file extensions and then inspecting your torrents for outliers; any file name that includes a non-media extension like .lnk, .exe, .cmd, .bat, .ps1, .sh, etc. is automatically a huge red flag!
Secondly, look for that little shortcut icon before you open anything you download from the internet. And finally, don't ignore suspicious things that are adding up (in this case, the fact it was posted before the episode's actual air date, and the media organizer software flagging it as "not a video").
I think Windows Defender probably would have caught it if I had actually clicked it and the malware had tried to install itself, but our goal is obviously to never get to the point of clicking on viruses at all! So be aware of the warning signs, use antivirus software, and sale the high-seas safely!
#i've only run into stuff like this twice in like 10 years of downloading#so don't let this scare you away from torrenting#just posting to keep people safe and informed#the next thing on my list is a guide to piracy via torrenting but my time and motivation has been very low due to life stuff lately#fingers crossed i get to it soon!#torrenting#piracy#computer security#cybersecurity#mine#long post
21 notes
·
View notes
Text
macOS malware NimDoor refuses to die, targets crypto firms
North Korean hackers are deploying NimDoor, a stealthy macOS threat that auto-reinstalls itself when killed and loots crypto firms using fake Zoom updates and Telegram lures. It hijacks AppleScript and Nim binaries to bypass defences and steal credentials.
Sources: BleepingComputer | SentinelLABS
6 notes
·
View notes
Text
North Korean hackers have stolen the equivalent of billions of dollars in recent years and the nation is seeking to amass even greater wealth through illicit means, experts told DW.
Hackers belonging to the Lazarus Group — a notorious North Korean crypto theft ring — stole a record $1.5 billion (some €1.37 billion) in digital tokens from Dubai-based cryptocurrency exchange ByBit in late February. The company said the hackers had accessed its digital wallet for Ethereum, the second-largest electronic currency after Bitcoin.
Binance News, a new platform operated by cryptocurrency exchange firm Binance, reported last month that North Korea now has some 13,562 Bitcoins, the equivalent of $1.14 billion. Bitcoin is the world's oldest and best known cryptocurrency, often compared with gold due to its alleged resistance to inflation. Only the US and Great Britain have greater reserves of the currency, Binance News said, citing crypto data provider Arkham Intelligence.
"Let's not mince words — [North Korea] achieved this through theft," Aditya Das, an analyst at cryptocurrency research firm Brave New Coin in Auckland, New Zealand, told DW.
"Global policing agencies like the FBI have publicly warned that North Korean state-sponsored hackers are behind numerous attacks on cryptocurrency platforms," he added.
Hackers use social engineering against crypto firms
Despite those warnings, however, crypto firms are still being robbed and North Korean hackers are becoming increasingly sophisticated, the analyst said.
"North Korea employs a wide range of cyberattack techniques, but they've become especially known for their skill in social engineering," said Das.
"Many of their operations involve infiltrating employee hardware, then using that access to breach internal systems or lay traps from the inside."
The hacker's primary targets are crypto startups, exchanges and decentralized finance (DeFi) platforms due to their "often under-developed security protocols," he said.
Recovery of funds 'extremely rare'
Elite North Korean hackers tend to take their time when infiltrating a legitimate global organization, often by impersonating venture capitalists, recruiters or remote IT workers to build up trust and breach firms' defenses.
"One group, Sapphire Sleet, lures victims into downloading malware disguised as job applications, meeting tools or diagnostic software — essentially turning victims into their own attack vectors," Das said.
Once crypto has been stolen, Das says recovery is "extremely rare." Cryptocurrency systems are designed to make transactions irreversible and striking back against North Korean operatives "is not a viable option because these are nation-state actors with top-tier cyber defenses."
Kim Jong Un's regime 'saved' by cryptocurrency theft
Park Jung-won, a professor of law at Dankook University, said North Korea previously relied on risky transactions — such as smuggling narcotics and counterfeit goods or supplying military instructors to African nations — to earn illicit funds.
The legal expert says the advent of cryptocurrency "has been a huge opportunity" for dictator Kim Jong Un.
"It is probably fair to say that given the way the world was cracking down on Pyongyang's smuggling efforts, crypto has saved the regime," Park told DW. "Without it, they would have been completely without funds. They know that and they have invested heavily in training the best hackers and getting them up to a very high level of skill."
"The money that they are stealing is going straight to the government and the assumption is that it is being spent on weapons and greater military technology as well as the Kim family," according to Park.
North Korea immune to international pressure
Park does not believe that outside pressure would force North Korea to end hacking attacks.
"For Kim, the survival of his dynasty is the most important priority," the law professor said.
"They have become accustomed to this source of revenue, even if it is illegal, and they will not change," he added. "There is no reason for them to suddenly start abiding by international law and there is no way to apply more pressure."
Das agrees there are few tools available to influence North Korea. He says companies need to do everything in their power to avoid becoming the next victim.
"Best practices like secure-by-design smart contracts, constant internal verification and social engineering awareness are essential if the industry wants to stay ahead," he said.
Crypto firms need universal security standards
There's growing momentum for sector-wide information sharing which would help crypto firms detect North Korean tactics and avert attacks, but Das warns that crypto remains "fragmented" because there is no universal security standard. Also, North Korean hackers are good at turning security tools against their users, according to the analyst.
"In the Bybit case, the attackers exploited Safe, a multi-signature wallet system meant to enhance security. Ironically, this added security layer became the very exploit they used," he said.
And in practice, Das added, "some firms still treat security as an afterthought."
"From my experience, teams often prioritize shipping fast over building secure systems and until that changes, the space will remain vulnerable," Das said.
#nunyas news#have to wonder what would happen#if all of a sudden a bunch of countries#started selling their crypto off#would the market tank or no
8 notes
·
View notes
Text
Crypto Scam Recovery: How to Spot, Report, and Recover from Online Frauds
The world of cryptocurrency is booming, offering investors a decentralized and promising way to grow their wealth. But with that growth comes an increasing number of scams targeting unsuspecting users. From fake investment platforms to phishing attacks, online fraud is a real threat. The good news? Victims can take action. In this post, we’ll guide you on how to spot crypto scams, report them, and increase your chances of recovery.

How to Spot a Crypto Scam
Knowing how to recognize the signs of a scam can save you from massive losses. Below are common types of cryptocurrency scams and the red flags to watch out for.
1. Fake Investment Platforms
These websites or apps promise guaranteed returns on crypto investments. They often look professional and mimic real companies, but they operate purely to steal your funds.
Red Flags:
Promises of high, risk-free returns
Urgency to deposit funds quickly
No verifiable company background
2. Phishing Attacks
Scammers send emails, messages, or pop-ups that look like they’re from trusted platforms. These messages trick users into giving away private keys or login credentials.
Red Flags:
Misspelled URLs or suspicious email addresses
Requests for sensitive information
Offers or warnings that seem too good or too urgent
3. Pump and Dump Schemes
Fraudsters hype up a worthless coin to drive demand and inflate prices. Once the price peaks, they dump their holdings, causing massive losses for late investors.
Red Flags:
Unusual hype in online forums or social media
Sudden spike in price without real news or updates
Unverified claims about partnerships or technology
How to Report a Crypto Scam
If you’ve been scammed, it’s essential to report the incident immediately. Doing so not only helps protect others but also increases your chance of recovery.
1. Report to Local Authorities
File a police report or contact your country's cybercrime unit. Include all details—transaction history, wallet addresses, emails, and screenshots.
2. Notify the Exchange
If the scammer used a known exchange to receive your funds, contact that platform’s support team. Many exchanges can freeze the funds if reported in time.
3. Report to Online Watchdogs
Organizations like the Internet Crime Complaint Center (IC3), FTC, or Action Fraud (UK) collect reports to investigate and track online scams.
4. Alert Blockchain Forensics Firms
Specialized companies like Chainalysis or CipherTrace can trace stolen crypto on the blockchain. In many cases, they collaborate with law enforcement and legal teams to initiate recovery.
How to Recover from a Crypto Scam
While recovering lost crypto isn’t easy, it’s not impossible. Here’s a structured plan from crypto recovery experts:
1. Secure All Accounts
Change passwords and enable two-factor authentication on your wallets, exchanges, and email. Run a malware scan on your devices to ensure no backdoors remain.
2. Collect Evidence
Document every aspect of the fraud—wallet addresses, transaction IDs, email conversations, social media links, and screenshots. The more information you gather, the better.
3. Consult a Crypto Recovery Expert
Work with a reputable crypto recovery agency or blockchain forensic specialist. These professionals use tracking software to trace your funds across wallet addresses and exchanges.
Note: Be cautious—scammers also pose as recovery agents. Only trust firms with proven results, legal backing, and strong online presence.
Prevention Tips to Avoid Future Crypto Frauds
Use hardware wallets for secure storage of your crypto assets.
Double-check URLs before entering credentials.
Avoid platforms or individuals promising “guaranteed returns.”
Do your research before investing—verify reviews, company registration, and team transparency.
Final Thoughts
Crypto scams are becoming more sophisticated, but with awareness and the right actions, you can fight back. Spotting red flags early, reporting to the proper authorities, and seeking expert help are key steps toward recovery.
If you or someone you know has fallen victim to a crypto scam recovery, don’t delay. Act fast, gather your data, and reach out to professionals who can help you trace and possibly recover your stolen funds.
3 notes
·
View notes
Text
ELTFV Security Guide: Safeguarding User Assets Against Scam Threats
As the crypto market evolves, threats from hackers, scammers, and malware are also on the rise. For investors, ensuring the security of their crypto assets is of utmost importance. ELTFV Exchange is committed to providing a secure and stable trading environment, offering effective preventive measures to help investors protect their crypto assets.

Common Cryptocurrency Theft Methods
The decentralized nature of the cryptocurrency market makes it an attractive target for hackers and scammers. The scam prevention guide of ELTFV Exchange outlines some of the most common methods used in cryptocurrency theft.
One of the most prevalent scams, phishing involves scammers impersonating legitimate cryptocurrency exchanges, wallet providers, or reputable companies. They use emails, social media, or fake websites to trick users into revealing sensitive information such as private keys or login credentials.
Hackers deploy malicious software like keyloggers or remote access trojans to infect user devices. If a user enters private keys or transaction details on an infected device, hackers can steal their assets. Scammers often promote high-yield investment projects via social media, forums, or private messages, luring investors to deposit funds. These projects are usually scam schemes that collapse, leaving investors with significant losses.
Preventing Cryptocurrency Theft
Despite the security risks in the cryptocurrency market, investors can take several measures to protect their assets. The scam prevention guide of ELTFV Exchange offers key strategies for safeguarding investments.
Selecting a reliable and regulated cryptocurrency exchange is crucial. ELTFV Exchange employs advanced security technologies, including multi-factor authentication (MFA), cold wallet storage, and big data security analytics, to ensure the safety of user assets.
The scam prevention team at ELTFV advises investors to avoid clicking on suspicious links, especially those received via email or social media. Always verify the exchange URL and avoid accessing it through third-party links. Never disclose private keys or seed phrases. For long-term holdings, consider storing crypto assets in a hardware wallet. Investors should create strong passwords, update them regularly, and avoid using the same password across multiple platforms. Additionally, enabling two-factor authentication (2FA) adds an extra layer of security, making it harder for hackers to access accounts even if passwords are compromised.
Before investing in any opportunity, conduct comprehensive research. Avoid blindly trusting “guaranteed profit” schemes. Verify whether the project is regulated, review the team background, and examine technical whitepapers. Community feedback can also provide insights into the project credibility.
ELTFV Commitment to Asset Security
ELTFV Exchange is dedicated to providing comprehensive security measures to ensure a safe trading experience for its users. The platform employs bank-grade encryption technology and stores the majority of user assets in cold wallets to minimize the risk of online attacks.
Through its KYC (Know Your Customer) process, ELTFV Exchange ensures that every user identity is verified, preventing identity scams and illegal transactions. The platform is equipped with an intelligent risk control system that monitors abnormal trading behaviors in real time to prevent malicious attacks.
ELTFV Exchange boasts a professional security team that monitors platform security 24/7, swiftly identifying and addressing potential threats. The platform also regularly issues security announcements and scam prevention guides to enhance user awareness and help them avoid potential risks.
As the cryptocurrency market grows rapidly, so do the associated security risks. Investors must remain vigilant and adopt necessary protective measures. With its advanced security technologies and stringent risk control systems, ELTFV Exchange provides a reliable environment for cryptocurrency trading. By implementing effective preventive measures, investors can mitigate scam risks and participate in crypto investments with greater peace of mind.
2 notes
·
View notes
Text
As the Biden administration comes to a close, the White House released a 40-page executive order on Thursday aimed at shoring up federal cybersecurity protections and placing guardrails on the US government’s use of AI. WIRED also spoke with outgoing US ambassador for cyberspace and digital policy, Nathaniel Fick, about the urgency that the Trump administration not cow to Russia and China in the global race for technical dominance. Outgoing FCC chair Jessica Rosenworcel details to WIRED the threats facing US telecoms, at least nine of which were recently breached by China’s Salt Typhoon hackers. Meanwhile, US officials are still scrambling to get a handle on multiple espionage campaigns and other data breaches, with new revelations this week that a breach of AT&T disclosed last summer compromised FBI call and text logs that could reveal the identity of anonymous sources.
Huione Guarantee, the massive online marketplace that researchers say provides an array of services to online scammers, is expanding its offerings to include a messaging app, stablecoin, and crypto exchange and has facilitated a whopping $24 billion in transactions, according to new research. New findings indicate that GitHub’s efforts to crack down on the use of deepfake porn software are falling short. And WIRED did a deep dive into the opaque world of predictive travel surveillance and the companies and governments that are pumping data about international travelers into AI tools meant to detect people who might be a “threat.”
But wait, there's more! Each week, we round up the security and privacy news we didn’t cover in depth ourselves. Click the headlines to read the full stories. And stay safe out there.
US Names One of the Chinese Hackers Allegedly Behind Massive Salt Typhoon Intrusions
China spies, the US spies, everybody spies. Mutual espionage is a geopolitical game played by virtually every nation in the world. So when the US government singles out a single hacker for espionage-focused intrusions, naming him and targeting him with sanctions, he must have spied aggressively—or effectively—enough to have made powerful people very angry.
The US Treasury on Friday imposed sanctions on Yin Kecheng, a 39-year old Chinese man accused of being involved in both the breach of nine US telecommunications companies carried out by the Chinese hacker group known as Salt Typhoon, as well as another recent breach of the US Treasury. In a statement about the news, Treasury alleges that Yin is affiliated with China’s Ministry of State Security and has been a “cyber actor” for over a decade. It also imposed sanctions on Sichuan Juxinhe Network Technology, a company that Treasury says is also associated with Salt Typhoon.
Salt Typhoon’s breach of US telecoms gave Chinese hackers enormous access to the real-time texts and phone calls of Americans, and was reportedly used to spy on president-elect Donald Trump and vice president-elect JD Vance, among other targets. FBI director Christopher Wray has called the telecom breaches China’s "most significant cyberespionage campaign in history.”
China’s Silk Typhoon Hackers Targeted Sanctions and Intelligence in Treasury Breach
As the Treasury hits back at China’s spy operations, it’s also still working to determine the scope of the intrusion some of those same hackers carried out inside its network. An internal Treasury report obtained by Bloomberg found that hackers had penetrated at least 400 of the agency’s PCs and stolen more than 3,000 files in a recent breach. The espionage-focused intrusion appears to have gone after sanctions and law-enforcement related information, the report found, as well as other intelligence materials. Despite that vast access, the intruders didn’t gain access to Treasury’s emails or classified portions of its network, the report states, nor did they leave behind malware that would suggest an attempt at maintaining longer-term access.
FBI Uninstalls Chinese PlugX Malware From Thousands of Machines
The Justice Department revealed this week that the FBI carried out an operation to delete a specimen of malware known as PlugX from 4,200 computers around the world. The malware, which was typically transmitted to computers via infected USB drives, has persisted for at least a decade and been used at times by Chinese state-sponsored hacker groups to target Chinese dissidents. In July of last year, cybersecurity firm Sekoia and French law enforcement took over the command-and-control server behind the malware. This week, the FBI obtained a court order that allowed the bureau to send a self-destruct command to the software on infected machines.
Victims of “PowerSchool” Edtech Data Breach Say “All” of Their Student and Teacher Info Was Stolen
After news earlier this week of a cyberattack in December that breached the US education technology platform PowerSchool, school districts targeted in the intrusion told TechCrunch on Thursday that attackers gained access to “all” stored student and teacher data in their accounts. PowerSchool is used by more than 60 million K-12 students in the US. Hackers gained access to the information by stealing login credentials that gave them access to the company’s customer support portal. The attack has not yet been publicly linked to a specific perpetrator. PowerSchool has not yet disclosed the exact number of victim schools nor whether all of its customers were affected.
3 notes
·
View notes
Text
Recover Stolen Crypto

Cryptocurrency has revolutionized the way we transact, offering decentralized and secure solutions for the modern economy. But with these benefits come risks, including the possibility of theft. Crypto theft can be devastating, leaving victims feeling powerless due to the anonymity of blockchain transactions. However, while challenging, recovering stolen crypto isn’t impossible. This guide will walk you through the steps to maximize your chances of retrieving lost funds and fortify your crypto security. Recover stolen crypto
Understanding How Crypto Theft Happens
Phishing Attacks
Phishing involves tricking users into revealing sensitive information such as private keys or wallet passwords. Scammers often impersonate legitimate platforms via fake websites or emails designed to look authentic. Once you input your details, they gain access to your wallet.
Hacking of Wallets and Exchanges
Crypto wallets and exchanges are prime targets for hackers. Weak security protocols, vulnerabilities in the platform, or user negligence can lead to unauthorized access and fund transfers.
Social Engineering Scams
These scams prey on human psychology. For instance, scammers may pose as trusted individuals or companies, convincing victims to transfer funds or disclose sensitive information.
Malware and Keyloggers
Cybercriminals use malware or keyloggers to monitor user activity. When you type your wallet credentials, the software captures and transmits the data to the attacker.
Immediate Steps to Take After Crypto Theft
Stay Calm and Act Quickly
Panic can lead to poor decisions. Assess the situation logically and act swiftly to prevent further losses.
Identify the Theft Details
Review your transaction history to determine when and how the theft occurred. Note the wallet addresses involved, the amount stolen, and the transaction ID.
Secure Remaining Funds
Transfer your remaining funds to a secure wallet. Hardware wallets or cold storage solutions are preferable as they are offline and immune to hacking.
Contacting Relevant Authorities
Reporting to Local Law Enforcement
File a report with your local authorities. While they may lack blockchain expertise, having an official record can support further recovery efforts.
Involving Cybercrime Units
Specialized cybercrime divisions can investigate the theft and collaborate with international organizations if needed.
Engaging Regulators Like SEC
In cases involving fraudulent investments, report the incident to regulatory bodies like the SEC or FCA to initiate investigations.
Notifying Crypto Platforms and Wallet Providers
How Exchanges Can Assist
Notify the exchange where the stolen funds were transacted. They may freeze suspicious accounts or provide information to investigators.
The Role of Wallet Providers
Wallet providers might help in identifying security vulnerabilities or advising on recovery steps.
Sharing Transaction Details
Provide all relevant details, including the transaction hash, wallet addresses, and any communication with the scammer.
Utilizing Blockchain Analysis Tools
How Blockchain Transparency Aids Recovery
Blockchain’s immutable ledger allows you to trace fund movements. With the right tools, you can monitor the thief’s wallet and subsequent transfers.
Popular Blockchain Analysis Tools
Platforms like Chainalysis, CipherTrace, and Elliptic specialize in tracking stolen cryptocurrency and identifying patterns.
Tracking Stolen Funds
Collaborate with professionals who use these tools to increase your chances of recovering the funds.
Hiring a Cryptocurrency Recovery Expert
Benefits of Professional Help
Experts have the technical knowledge and resources to trace transactions, liaise with platforms, and initiate recovery processes.
Vetting Recovery Agencies for Legitimacy
Ensure the agency has a proven track record. Beware of additional scams that exploit victims seeking help.
Avoiding Additional Scams
Never pay upfront fees without verifying the agency’s legitimacy. Genuine recovery services operate transparently.
Using Social Media and Community Networks
Engaging the Crypto Community
Post about your stolen crypto on forums, Reddit, or Twitter. The community often shares valuable insights or connects you with experts.
Raising Awareness About Stolen Funds
Highlighting the theft publicly can deter thieves from cashing out and put pressure on platforms to assist.
Success Stories
Many individuals have successfully recovered their stolen crypto by rallying community support and leveraging online networks.
Legal Options for Recovering Stolen Crypto
Filing Lawsuits
If you have enough evidence to identify the thief, you may file a lawsuit. Courts can issue orders to freeze assets or compel exchanges to provide information about suspicious accounts.
International Legal Frameworks
Cryptocurrency theft often crosses borders, making it necessary to engage international legal frameworks like the Hague Convention. Collaborating with global enforcement agencies can enhance recovery efforts.
Challenges with Jurisdiction
Jurisdictional issues complicate legal proceedings. Many crypto criminals operate in countries with lax regulations, making prosecution and recovery harder.
Preventative Measures to Protect Cryptocurrency
Using Hardware Wallets
Hardware wallets store private keys offline, making them virtually immune to hacking. They are the gold standard for crypto security and should be your primary storage method for large holdings.
Enabling Two-Factor Authentication (2FA)
2FA adds an additional layer of security to your crypto accounts by requiring a second verification step. Always enable it, preferably using an authenticator app rather than SMS.
Avoiding Suspicious Links and Emails
Phishing scams often start with an innocent-looking link or email. Be cautious and double-check URLs before entering sensitive information. Bookmark trusted platforms to avoid accidental clicks on fake sites.
Educating Yourself on Crypto Scams
Recognizing Common Scam Patterns
From Ponzi schemes to fake giveaways, crypto scams come in many forms. Stay informed about the latest trends and tactics used by scammers.
Staying Updated with News and Security Tips
Follow trusted crypto news outlets and cybersecurity blogs. Awareness is your best defense against evolving threats in the crypto space.
Building a Secure Crypto Environment
Regular Wallet Audits
Periodically review your wallet and transaction history to identify unauthorized activity early. This practice can prevent small breaches from escalating into significant losses.
Diversifying Storage Solutions
Spread your funds across multiple wallets. Use a combination of hardware wallets, paper wallets, and software wallets for added security.
Investing in Cybersecurity Tools
Firewalls, antivirus software, and VPNs can protect you from malware and other digital threats. These tools are essential for safe crypto trading and storage.
Understanding the Limits of Recovery
Why Crypto Recovery Isn’t Guaranteed
The decentralized and pseudonymous nature of blockchain technology makes fund recovery difficult. Once funds are transferred to a thief’s wallet, reversing the transaction is nearly impossible without their cooperation.
Managing Expectations
While recovery efforts are worth pursuing, it’s essential to prepare for the possibility that your funds may not be recovered. Focus on improving your security to prevent future losses.
The Role of Decentralized Finance (DeFi) in Crypto Security
How DeFi Protocols Enhance Transparency
DeFi platforms operate on smart contracts, which are transparent and immutable. This openness can help in tracking fraudulent activity and ensuring secure transactions.
Risks Associated with DeFi Platforms
Despite their benefits, DeFi platforms are not immune to vulnerabilities. Exploits in smart contracts and lack of insurance can lead to significant losses.
Recovering stolen cryptocurrency is no easy feat, but it’s not entirely hopeless either. By taking immediate action, leveraging blockchain tools, and engaging with experts, you can increase your chances of recovering your funds. Most importantly, prioritize prevention by adopting stringent security measures. Remember, in the world of cryptocurrency, staying one step ahead of scammers is your best protection.
Contact Info: Email: - [email protected]
2 notes
·
View notes
Text
Web Search Engine) Links
Hidden Wiki Links – Now you are here then you already know about deep web links / The Hidden Wiki / Dark web links. But before sharing large amount of .onion directory I want to share some very good deep web links which always help you, because all these are deep web search engine links by the help of these search engine you can find any latest working deep web marketplace, hidden wiki or deep web sites list.
Dark Web Marketplace
Darknet markets is a solution for all type products because these type marketplace gives security to both party means seller or buyer, here you can use escrow service which make your payment mode more secure and clear. These type darknet markets places having some big number of listed categories and each category having more than thousands of unique products.
So simple, Today If you are planning to buy anything on deep web/the hidden wiki then these markets can provide you all type products buying or selling opportunity and here you also can get more than one alternatives into single category.
Mostly these deep web links having Drugs, Weapon, Digital products, Fraud, Services, Guide and Tutorials categories.
Bellow I am giving you some very popular deep web Links (dark web links), which you can try but before using these hidden wiki links, you need to register yourself on these darknet markets deep web link.
Note: If you are seller then these dark web marketplace links will proving milestone for you. where you can sell your products. and you can easily get targeted users or can achieve your goals within very short time span.
Note: I am not recommending you to visit these deep web sites (dark web links), I only added these deep web sites/onion sites here for education purpose or freedom information. If you visit these deep web sites then this is total on your risk, but I am recommending you here before visiting these deep web sites make sure focus on your privacy Security.
Recommended: For better security use NordVPN Onion Over Server + Tor Browser. ( Always run both software before access hidden Internet).
http://pwoah7foa6au2pul.onion – Marketplace – Alphabay is most popular and trusted deep web market. If you are truly looking something trusted on deep web then Alphabay is one of the best market, And this marketplace also has all major categories items like as fraud, drugs, chemicals, Guide & Tutorials, Digital Products, Services, and much more. According to current status, This marketplace has more than 3 Lakh listed items, and Just now support two type crypto currency which is Monero and Bitcoins.
Note: Before Buy any product here always check seller profile and available feedback and reviews.
http://lchudifyeqm4ldjj.onion/ – Marketplace – Dream Market : Second largest and most trusted dark web market, also you can say alternative of alphaby market, This marketplace place have drugs and digital products, and both these category have more than 75000+ listed items which is huge. If you are looking another great platform then dream market can provide you right items.
http://wallstyizjhkrvmj.onion/ – Marketplace – WallStreet Market – Another deep web markets which have more than 500+ listed items and each item are well categorized. According to category, You can get products related to drugs, counterfeits, jewelry & gold, services, Software & malware, security & hosting and much more.. and listing growing day to day. Marketplace support PGP and data encrypt by strong algorithm and also support German language. WallStreet has scam free status and multisig support.
http://udujmgcoqw6o4cp4.onion – Deep Web Market – UnderGround, one of the best and reliable deep web market with the possibility to pay in two times. Markets have more than thousands listed items and items related to Prepaid cards, PayPal account, Diploma, Passport, ID Cards, Driver License, Phone, Computer, Tablets, Game Console, Hacker, Weapons, Professional Killer, Humen Organs, Medicines and so on.
Note: This deep web links support JavaScript, If you want to access all function then you need to disable your javascript. But for security reasons, this is not good choice.
http://valhallaxmn3fydu.onion – Marketplace – Valhalla: This deep web marketplace is also very popular into deep web world and mostly people prefer this hidden wiki marketplace url for buying drugs, gadgets, hire services and lot many more things.
http://hansamkt2rr6nfg3.onion/ – Marketplace – Hansa is another famous deep web marketplace, which having more than 15K+ listed products. which is huge, and here you can buy all type products related to drugs, weapons, services, tutorials, services, electronics. It is one of most popular the dark web links.
http://zocaloczzecchoaa.onion – Marketplace – Zocalo Marketplace: Same as other marketplaces this .onion directory links also having good amount of listing product.
http://acropol4ti6ytzeh.onion – Marketplace – Acropolis forum also a good darknet markets, and community forum for sell and buy anything which you want, and also can find your questions answer in this dark web link.
http://tochka3evlj3sxdv.onion – Marketplace – Tochka Free Market: Tochka is also good darknet market where you can find mostly all type product related to education, hacking, drugs, weapon, services and software.
http://cryptomktgxdn2zd.onion – Marketplace – Crypto Market: Are you looking some other deep web links marketplace alternative then check out Crypto Market, Here you can participate in crypto market forum.
Warning: Before browsing the Deep web links/the dark web links, always run your NordVPN Onion Over VPN Server with Tor Browser. Since Tor Browser doesn’t provide your complete anonymity and privacy. You are completely safe only if you use NordVPN software.
http://kbhpodhnfxl3clb4.onion/ – not Evil (Tor Search Engine) for finding list of deep web sites, and one can easily find relevant information about the deep web/the hidden wiki which s/he want to get..
http://hss3uro2hsxfogfq.onion/ – not Evil search engine direct visit deep web links.
Note: Now Tor search engine has been moved on new name, now this popular search engine also known as not Evil, in the current date not Evil having more than 12477146 .onion links database.
Grams Search Engine and Associated Deep Web Services Links:
Grams is newly launched deep web search engine, this search engine getting good amount of popularity with in very short time and these days thousands of people use Grams for deep web access. You can access Grams by using below dark web link.
http://grams7enufi7jmdl.onion/ – Grams Search Darknet Markets and more.
Grams is not a single platform, but it’s like a Google, After couple month after grams launching date, Grams introduced some other product like Helix, Helix Light, Infodesk or Flow.
All three having unique features. If you want to access these three Grams sub product, then you can access by the help of Grams deep web link, or you can also go by the help of bellow given direct dark web links.
Note: Helix takes charge 2.5% every transaction.
Helix Tor Directory Link: http://grams7enufi7jmdl.onion/helix/light
InfoDesk: If you want to find any Vender, products or any specific marketplace tor link then this place can help you because here you can find some great marketplace which is trusted, and mostly people use in daily life.You can access InfoDesk using below deep web link.
InfoDesk Hidden Wiki Link: http://grams7enufi7jmdl.onion/infodesk
Flow: Now time for Flow, this is another popular deep web product which is also introduced by Grams, Hope you like Flow features because some person like this platform for Flow redirect feature.
According to this, if you want to access any darknet markets and you didn’t remember tor directory link then you can access these type hidden wiki url or deep web links easily.. GramsFlow makes this type complicated process more easy.
Now you only need to remember your marketplace name like Agora, Wiki, OutLaw, nuke or any other and you can access by help of Flow.
For Example: if you want to access the hidden wiki then you need to type in your Tor Browser gramsflow.com/wiki, then holla your link redirect on actual tor hidden directory.
For using awesome feature of Flow, visit below give deep web link.
Flow Tor Hidden Directory Link: http://grams7enufi7jmdl.onion/infodesk
http://skunkrdunsylcfqd.onion/sites.html – The Intel Wiki – This .onion site has the good number of trusted deep web links, which every day visited by most of the deep web users. But sometimes when I try to access this deep web link and I saw this dark web link is down. One more thing the Intel wiki also a forum which having great number of threads, which having useful information about the deep web and trusted deep web links/dark web links.
http://auutwvpt25zfyncd.onion/ – Tor Links Directory – OnionDir having more than 1200+ listed dark web sites, one better thing is here you can see on top how many dark net sites are live and how many deep web sites not and All .onions links are well categorized according to categories. For Example: If you are looking hacking or drugs related marketplace deep web links then you need to click on required category and visit any deep web sites which you like.
Forums & Community Deep Web Links(For Questions and Answers Conversation)
If you are eager to learn the darknet hidden wiki forum, also want to deep discuss on this sensitive topic and looking best deep web forums and the hidden wiki links and if you also looking how to access the deep web latest news and updates.
Deepwebsiteslinks is a best source where you can find all most popular deep web links, the hidden wiki news and darknet markets updates day to day and people visit here every day and participate into available threads.
Here I am giving you some popular deep web forums and darknet community links/deep web links, which are sharing the deep web/the hidden wiki related news and current updates everyday.
Privacy Tips: Always use NordVPN Onion Over Server with Tor browser while you accessing deep web sites. if you are thinking you are using TOR and you are safe. Let me clear for your privacy security. TOR doesn’t provide you full security. To access deep web with best anonymity and privacy, NordVPN and TOR both are must used software.
http://rrcc5xgpiuf3xe6p.onion/ – Forum/Community – IntelExchange is my favorite the dark web community because here you can find information thread and also can ask your question, I like this because here you can find mostly pre-discussed thread which having lot of meaningful information like best dark web search engines, dark web browser, most trusted the hidden wiki url.
http://parazite.nn.fi/roguesci/ – Forum – The Explosive and Weapon Forum, This hidden wiki link has some very good weapons and Explosive-related Documents and treads.
http://zw3crggtadila2sg.onion/imageboard/ – Forum – TorChan is darknet forum where you ask and participates into running chat thread, but If you are first time visitors then you don’t know how to visit this website then simple type given URL and after press enter you will get one popup on screen then you need to put given Username and Password into both field, ByDefault Username or Password is torchan2, torchan2. this is most popular the hidden wiki forum, where every day more than thousands or visitors visit and share something very interesting.
http://kpdqsslspgfwfjpw.onion/ – Forum/Community – A Chan, I think this deep web links having Russian language stuff, I can’t tell you about properly this site, and what type stuff this deep web sites have.
http://rhe4faeuhjs4ldc5.onion/ – Forum/Community – Do you have any query related to white hate hacking or black hat techniques, and you want to know some secret hacking tips then this hidden wiki community will proving helpful stuff and gernals. having more than 20+ active threads.
http://turkiyex6fkt46ra.onion/forum/ – Forum/Community/Non-English – Are you from Turkey, and looking your region related deep web forum then check out this hidden wiki forum link.
http://anonywebix6vi6gz.onion/ – Forum/Community – This is newly launched dark net forum. This hidden wiki link also will proving helpful for you, if you want to discuss about the deepweb, darknet markets or any others.
http://arcadian4nxs3pjr.onion/ – Forum/Community – ArcadiaNode is a dark net forum, Note: this deep web sites is not in the English language, that’s why I don’t have more idea about this forum.
http://5dhf54nxiuuv6jvs.onion/ – Forum/Community – AXAHis Community: This is another deepweb (hidden wiki) community where you can share your questions and knowledge, also can interact with related people.
Note: For access first time need registration.
http://p22i3mcdceionj36.onion/index.php – Forum/Community – XenForo: This deep web marketplace is a forum, but here you can buy Pfizer and GG249 Xanax products.
http://anonymzn3twqpxq5.onion/ – Forum/Community – Do you love DBA task and want to discuss on DBA related topics then check out this forum, hope this will proving helpful for you.
http://z2hjm7uhwisw5jm5.onion/ – Forum/Community – WallStreet: If you having any query about Tor or Looking some hidden web related answer then you can try on this deep web link.
http://support26v5pvkg6.onion/ – Forum/Community – Pedo Support Community: This Deep web forum is having more than 10K+ threads, like links, personal support, pedo literature, child love support, etc.
http://suprbayoubiexnmp.onion/ – Forum/Community – SuperBay: This community is having very good amount of thread and everyday lot’s of visitors use these threads, If you have some problem, then you can find relevant thread, and can resolve your problem.
https://blue.thevendingmachine.pw/index.php – Community/Forum – TheVendingMachine: This is very popular deep web community, every day more than 1000+ visitors visit this onion site, and share information. Here most popular thread is Torrent, Movies, General Discussion, TV shows, documentaries, etc.
http://npdaaf3s3f2xrmlo.onion/ – Tor Community – TwitterClon is just like twitter sites here you can share everything which you want into form of tweet, hope you also enjoy this sites, but mostly time I saw this site down.
NordVPN 2
http://ji7nj2et2kyrxpsh.onion/ – Forum – Dark Web Forum: I don’t know what you can find here because this is non-english forum but as per my guess, hope you can discuss about dark web and also can participate into active threads.
http://krainkasnuawwxmu.onion/ – Forum – Dark Web Community: This is the next Russian forum, where you can discuss about dark web community. If you have any question and want to know the right answers, then you can sign up on this forum and can find some easy solutions.
http://fbcy5ylyoeqzqzcr.onion/ – Forum – Moneybook: Another dark web forum where you can discuss about all popular topics related to dark web like as onion links, dark web markets review, PayPal accounts, music movie sites and much more, hope here you can find some good thread for you.
http://realpissxny3hgyl.onion/ – Forum/Porn – RealPiss Voyeur Community real uncensored female pee spycams: community for real girl piss videos and pictures, If you interested into such type content then you can try to visit realpiss site.
http://zzq7gpluliw6iq7l.onion/threadlist.php? – Forum – The Green Machine: Another deep web forum which provides discussion threads, do you have any questions and want to know the right answers then The green machine dark web links can provide you right information. But If you want to participate into available threads then you need to registered yourself on this deep web forum.
http://rutorzzmfflzllk5.onion/ – Forum/Russian – RuTor: Are you looking Russian forum, If yes then RuTor forum can provides you some great questions answer, but this forum not have more active thread, when I visited this deep web sites then I saw, website have only limited thread and also not have users engagement.
http://bm26rwk32m7u7rec.onion/ – Forum – The Majestic Garden: This is another deep web forum, which provides free forum SMF software solution, If you have any questions about this software then you can visit this deep web sites.
http://vrimutd6so6a565x.onion/ – Forum/Community – The Dark Lair: Forum for anonymous messaging, like as Twitter. Here you can share your status globally; Everyone can saw your status on this website. If they visit dark Lier, but you can’t post status on this site. Because you are not the registered member of Dark Lier, that’s the main reason. First your need to register on this website. Site also offers thread service and some good deep web links also.
http://answerstedhctbek.onion/ – Forum/Community – Hidden Answers: I think you already know about the yahoo questions and answers, This site offer same service just like yahoo questions and answers, If you have any questions and want to get your questions answers then you can try this deep web links.
http://saefjmgij57x5gky.onion/ – Forum/Community – TorStack – Q & A Community – Same Yahoo Questions and answer deep web sites, here you also can find right answers for your questions anonymously.
http://dnmavengeradt4vo.onion/ – Forum/Community – DNM Avengers: Another deep web forum site which provides communicating portal for deep web users anonymously. forum already have more than 100+ active threads. If you have any questions and want to know right answer anonymously. You can participate on available relevant thread. Also, you can share your skills in these running threads.
http://twittorxsun563wg.onion/ – Community/Social – Twitter Clone – This is microblogging site on the deep web, here you can share anything with all site readers anonymously. For status publishing you don’t need to signup here.
http://i2vzg7f44bj4l3r7.onion/ – Community – The Alliance – Another deep web social community sites, where users can share his though with all alliance community member or personally with your friends. One more thing, site also offers bookmarks service, by which you can tag any links on the Bookmarks category. which every site readers can read and visit anonymously.
http://www.smplace.com/forum/ – Forum/Community – S&M Place BDSM forum – Great Adult porn community for girls and boys, have all type threads where you can share adult porn videos and pictures, and also you can upload your videos and pictures collections. Forum have more than 70000+ active members.
http://rekt5jo5nuuadbie.onion/hiddenchan/ – Forum/Community – HideenChan – If you don’t know about the hidden chan. HiddenChan is just like as another community forum, here you can participate into current active threads. But hiddenchan is very engaging community here you can see every illegal activity related thread and also you can watch available videos and pictures which is uploaded by various current members.
http://start.jungswtfwgjwile2.onion/ – Forum/Community – Guys.WTF is primarily a community for people who love and love guys and / or feel sexually attracted by them. However, every interested person is expressly welcome. Here you want to help and support each other.
http://bfvfq7hjcdoinzo4.onion/ – Forum/Community – Darknet Erotic Forum – This deep web forum offer threads related to hot, geil, horny, porn, pervers and etc. If you want to discuss about these topics then you can participate on available threads. But without registration you can’t participate in this community.
http://rfwtogljhrrzxyrl.onion/ – Forum/Community – Lolita City – Another deep web forum, which offers hq legal stuff. Today when I visited this site, here only I found 2 threads. Hope here you can get your required information.
Email/Messaging/Chat related Deep Web Links
Warning: Always use NordVPN Tor Over Server + Tor Browser for complete security. Your privacy is not safe if you are accessing deep web links without VPN.
Same ad normal traditional in
#dark web#ethicalhacking#scammer#coding#contact a hacker#scammers#social media hackers#ethical hacker#deep web#hacker
5 notes
·
View notes
Note
Imagine Ganondorf with technology bro. He’d be a menace.
My modern Ganondorf is a hacker. He sits in his basement, his home heated by the sheer number of rigs he has running that are mining crypto. Do you know how many successful crypto scams he’s run? He effortlessly installs malware into credit card and government systems to scrape personal data that he sells onto the black market. He has dirt on so many politicians and people in power that he casually leaks files online when he’s feeling bored and wishes to cause some controversy. Every company and government organization that stokes his ire has been hit by his ransomware attacks, bringing down public confidence and stock prices. He is a master of social engineering, slowly needling critical information out of people to allow him to log into very secure systems and delete swaths of critcial data, corrupt critical infrastructure. He probably even sells malware as a service software, allowing other petty nefarious individuals to utilize his sophisticated malware to inflict more harm on others he doesn’t necessarily have the time nor interest to target. His presence looms over the technological age, so well adept at masking his trace that no one can ever truly place the blame on him.
(I mean Calamity Ganon literally hacking into the Divine Beasts and guardians, and then Ganondorf with the seized construct just cemented this for me. Modern Ganondorf is a master hacker with a fondness for metal music. It’s all canon babes.)
4 notes
·
View notes
Text
10 Million People Globally Targeted by Fake Crypto App Ads, Check Point Warns
A global malware campaign has exposed more than 10 million people to deceptive crypto app ads, according to a new report from cybersecurity firm Check Point. Key Takeaways: Fake crypto app ads have exposed over 10 million people to malware. The malware uses JavaScript and advanced evasion tactics to avoid detection. Victims risk losing passwords, Telegram data, and access to crypto…
0 notes
Text
Weekly Malware & Threats Roundup | 24 Feb - 02 Mar 2025

1️⃣ 𝗡𝗼𝗿𝘁𝗵 𝗞𝗼𝗿���𝗮𝗻 𝗛𝗮𝗰𝗸𝗲𝗿𝘀 𝗟𝗶𝗻𝗸𝗲𝗱 𝘁𝗼 $𝟭.𝟱 𝗕𝗶𝗹𝗹𝗶𝗼𝗻 𝗕𝘆𝗕𝗶𝘁 𝗖𝗿𝘆𝗽𝘁𝗼 𝗛𝗲𝗶𝘀𝘁 North Korea's Lazarus hacking group has been identified as responsible for the largest cryptocurrency heist in history, stealing over $1.5 billion from ByBit. Source: https://www.bleepingcomputer.com/news/security/north-korean-hackers-linked-to-15-billion-bybit-crypto-heist/
2️⃣ 𝗚𝗶𝘁𝗩𝗲𝗻𝗼𝗺 𝗖𝗮𝗺𝗽𝗮𝗶𝗴𝗻 𝗗𝗶𝘀𝘁𝗿𝗶𝗯𝘂𝘁𝗲𝘀 𝗠𝗮𝗹𝘄𝗮𝗿𝗲 𝘃𝗶𝗮 𝗙𝗮𝗸𝗲 𝗚𝗶𝘁𝗛𝘂𝗯 𝗥𝗲𝗽𝗼𝘀𝗶𝘁𝗼𝗿𝗶𝗲𝘀 Attackers are using fake GitHub projects to distribute stealers, backdoors, and cryptocurrency wallet clippers, targeting developers globally. Source: https://securelist.com/gitvenom-campaign/115694/
3️⃣ 𝟮,𝟱𝟬𝟬+ 𝗧𝗿𝘂𝗲𝘀𝗶𝗴𝗵𝘁.𝘀𝘆𝘀 𝗗𝗿𝗶𝘃𝗲𝗿 𝗩𝗮𝗿𝗶𝗮𝗻𝘁𝘀 𝗘𝘅𝗽𝗹𝗼𝗶𝘁𝗲𝗱 𝘁𝗼 𝗗𝗲𝗽𝗹𝗼𝘆 𝗛𝗶𝗱𝗱𝗲𝗻𝗚𝗵𝟬𝘀𝘁 𝗥𝗔𝗧 A large-scale campaign abuses a vulnerable Windows driver to evade EDR systems and deploy remote access trojans. Source: https://research.checkpoint.com/2025/large-scale-exploitation-of-legacy-driver/
4️⃣ 𝗡𝗲𝘄 𝗠𝗮𝗹𝘄𝗮𝗿𝗲 𝗖𝗮𝗺𝗽𝗮𝗶𝗴𝗻 𝗨𝘀𝗲𝘀 𝗖𝗿𝗮𝗰𝗸𝗲𝗱 𝗦𝗼𝗳𝘁𝘄𝗮𝗿𝗲 𝘁𝗼 𝗦𝗽𝗿𝗲𝗮𝗱 𝗟𝘂𝗺𝗺𝗮 𝗮𝗻𝗱 𝗔𝗖𝗥 𝗦𝘁𝗲𝗮𝗹𝗲𝗿 Cybercriminals are distributing malware via cracked software downloads, leveraging Dead Drop Resolver techniques to avoid detection. Source: https://asec.ahnlab.com/en/86390/
5️⃣ 𝗚𝗿𝗮𝘀𝘀𝗖𝗮𝗹𝗹 𝗠𝗮𝗹𝘄𝗮𝗿𝗲 𝗗𝗿𝗮𝗶𝗻𝘀 𝗖𝗿𝘆𝗽𝘁𝗼 𝗪𝗮𝗹𝗹𝗲𝘁𝘀 𝘃𝗶𝗮 𝗙𝗮𝗸𝗲 𝗝𝗼𝗯 𝗜𝗻𝘁𝗲𝗿𝘃𝗶𝗲𝘄𝘀 A Russian cybercrime group deceived Web3 job seekers into downloading malware through a fraudulent interview platform. Source: https://www.bleepingcomputer.com/news/security/grasscall-malware-campaign-drains-crypto-wallets-via-fake-job-interviews/
Additional Cybersecurity News:
🟢 𝟮𝟬𝟮𝟱 𝗨𝗻𝗶𝘁 𝟰𝟮 𝗜𝗻𝗰𝗶𝗱𝗲𝗻𝘁 𝗥𝗲𝘀𝗽𝗼𝗻𝘀𝗲 𝗥𝗲𝗽𝗼𝗿𝘁: 𝗖𝘆𝗯𝗲𝗿 𝗔𝘁𝘁𝗮𝗰𝗸𝘀 𝗦𝗵𝗶𝗳𝘁 𝘁𝗼 𝗗𝗶𝘀𝗿𝘂𝗽𝘁𝗶𝗼𝗻 86% of major cyber incidents in 2024 resulted in downtime or financial loss, with attackers increasingly focusing on sabotage and data exfiltration. Source: https://www.paloaltonetworks.com/blog/2025/02/incident-response-report-attacks-shift-disruption/
🟠 𝗖𝗵𝗶𝗻𝗲𝘀𝗲 𝗖𝘆𝗯𝗲𝗿 𝗘𝘀𝗽𝗶𝗼𝗻𝗮𝗴𝗲 𝗝𝘂𝗺𝗽𝘀 𝟭𝟱𝟬%, 𝗖𝗿𝗼𝘄𝗱𝗦𝘁𝗿𝗶𝗸𝗲 𝗥𝗲𝗽𝗼𝗿𝘁𝘀 Chinese state-backed cyber espionage activities surged in 2024, targeting finance, media, and manufacturing sectors. Source: https://www.crowdstrike.com/en-us/global-threat-report/
🔴 𝟲𝟭% 𝗼𝗳 𝗛𝗮𝗰𝗸𝗲𝗿𝘀 𝗨𝘀𝗲 𝗡𝗲𝘄 𝗘𝘅𝗽𝗹𝗼𝗶𝘁 𝗖𝗼𝗱𝗲 𝗪𝗶𝘁𝗵𝗶𝗻 𝟰𝟴 𝗛𝗼𝘂𝗿𝘀 𝗼𝗳 𝗗𝗶𝘀𝗰𝗹𝗼𝘀𝘂𝗿𝗲 Cybercriminals are exploiting newly released vulnerabilities faster than ever, with ransomware attacks targeting healthcare at record levels. Source: https://www.sonicwall.com/threat-report
#CyberSecurity#ThreatIntelligence#Malware#CyberAttack#Ransomware#APT#DataBreach#CyberThreats#ThreatHunting
7 notes
·
View notes
Text
Major new malware strain targets crypto users via malicious ads - here's what we know, and how to stay safe
Check Point finds thousands of ads promoting fake crypto apps The apps come with an infostealer malware targeting users The infostealer can bypass most antivirus protections Cryptocurrency users are being targeted by a highly sophisticated, widespread cybercriminal campaign with the goal of deploying malware capable of grabbing exchange and wallet information, essentially robbing the people of…
0 notes
Text
? #Security_and_Privacy ? Sophisticated Malware Campaign Targets Windows and Linux Systems A newly uncovered malware campaign targeting both Windows and Linux systems has revealed advanced evasion and credential theft techniques, according to the Sysdig Threat Research Team (TRT). The operation began with a malicious Python script uploaded via a misconfigured system, enabling the download of crypto-miners and the deployment of stealthy tools for evasion and data exfiltration. This mul...(read more) #campaign #Linux #Malware #Sophisticated #Systems #Targets #Windows ?
0 notes
Text
An indictment from the US Department of Justice may have solved the mystery of how disgraced cryptocurrency exchange FTX lost over $400 million in crypto. The indictment, filed last week, alleges that three individuals used a SIM-swapping attack to steal hundreds of millions in virtual currency from an unnamed company. The timing and the amount stolen coincides with FTX's theft. Meanwhile, in a letter obtained by WIRED this week, seven lawmakers have demanded the DOJ stop funding biased and inaccurate predictive policing tools until the agency has a way to ensure law enforcement won’t use them in a way that has a “discriminatory impact.”
In Florida, prosecutors say a 17-year-old named Alan Winston Filion is responsible for hundreds of swatting attacks around the United States. The news of his arrest was first reported by WIRED days before law enforcement made it public. It was the culmination of a multi-agency manhunt to piece together a trail of digital breadcrumbs left by the teenager. In Ukraine, unmanned aerial vehicles have been powerful tools since the Russian invasion began in February 2022. But as the war rages on, another kind of unmanned robot has increasingly appeared on the front-lines: the unmanned ground vehicle, or UGV.
For months lawyers affiliated with an India based hacker-for-hire firm called Appin Technology have used legal threats to censor reporting about the company’s alleged cyber mercenary past. The EFF, Techdirt, MuckRock, and DDoSecrets are now pushing back, publicly sharing details for the first time about the firm's efforts to remove content from the web. It’s a dangerous world out there, so we’ve also got a list of some major patches issued in January that you can use to update your devices to keep them secure.
And there’s more. Each week, we highlight the news we didn’t cover in-depth ourselves. Click on the headlines below to read the full stories. And stay safe out there.
China’s Hackers Keep Targeting US Water and Electricity Supplies
For years Western security officials have warned about the threat of China collecting data about millions of people and the country’s hackers infiltrating sensitive systems. This week, Federal Bureau of Investigation director Christopher Wray said hackers affiliated with the Chinese Communist Party are constantly targeting US critical infrastructure, such as water treatment plants, the electrical grid, and oil and gas pipelines. Wray’s testimony, at a House subcommittee on China, came as the FBI also revealed it removed malware from hundreds of routers in people’s homes and offices that had been planted by the Chinese hacking group Volt Typhoon.
“China’s hackers are positioning on American infrastructure in preparation to wreak havoc and cause real-world harm to American citizens and communities,” Wray said in the public appearance. “Low blows against civilians are part of China’s plan.” The FBI director added that China has a bigger hacking operation than “every other major nation combined,” and claimed that if all of the FBI’s cyber-focused agents were assigned to work on issues related to China, they would still be outnumbered “by at least 50 to 1.”
While concerns about the scale of China’s espionage and cyber operations aren’t new, the US intelligence community has been increasingly vocal and worried about critical infrastructure being targeted by Volt Typhoon and other groups. “The threat is extremely sophisticated and pervasive,” NSA officials warned in November. In May 2023, Microsoft revealed it had been tracking Volt Typhoon intrusions at communications and transportation infrastructure, among other critical infrastructure, in US states and Guam.
The FBI and DOJ, also revealed this week that they remotely removed the KV Botnet malware from hundreds of routers infected by Volt Typhoon. The impacted routers, from Cisco and Netgear, were mostly at the end of their life, but were being used as part of wider operations. “The Volt Typhoon malware enabled China to hide, among other things, pre-operational reconnaissance and network exploitation against critical infrastructure like our communications, energy, transportation, and water sectors,” Wray said. It isn’t the first time US officials have obtained a court order to remotely wipe devices infected by hackers, but the move is still rare.
‘Untraceable’ Monero Transactions Have Been Traced, Police Claim
Since the first cryptocurrencies emerged more than a decade ago, there has been the assumption that the blockchain-based digital currencies are anonymous and untraceable. They are, in fact, very traceable. Researchers have shown how people can be linked to the transactions they make and law enforcement have used the techniques to help bust illicit dark web markets and catch pedophiles. There are, however, still some privacy-focused cryptocurrencies that appear to be less traceable than Bitcoin. This includes Monero, which is increasingly being adopted by sellers of child sexual abuse materials.
This week investigators in Finland said Moreno-tracing helped reveal the identity of a hacker who allegedly attacked psychotherapy company Vastaamo in 2020, stealing thousands of patient records and threatening to leak them unless people paid a ransom. Investigators from the Finnish National Bureau of Investigation claim they used heuristic analysis to infer where funds were moved to. The investigators did not reveal the full methods of how they allegedly traced the Monero payments, however, they add to the growing body of evidence that cryptocurrency tracing firms and investigators may be able to track the currency.
Russia Likely Behind a Spike in GPS Interference, Officials Say
Planes flying over Europe have faced a spike in accuracy issues with GPS systems used for navigation in recent months. The head of Estonia’s Defense Forces has claimed that Russia is likely the source of this interference, according to an interview with Bloomberg. “Someone is causing it, and we think it’s Russia,” Martin Herem told the publication, adding that Russia may be testing its electronic warfare capabilities and “learning” the most effective tactics. Across Europe, and particularly the Baltics region, there has been a reported increase in GPS jamming, with Finland reporting large interferences in December and pilots repeatedly reporting issues with their navigation systems.
Vault 7 Hacking Tools Leaker Joshua Schulte Sentenced to 40 Years
In 2017, the Vault 7 leaks exposed some of the CIA’s most sophisticated hacking tools, including how the agency could compromise routers, phones, PC, and TVs. Joshua Schulte, a former CIA engineer in the agency’s Operations Support Branch who prosecutors identified as being behind the data breach and responsible for leaking the materials to Wikileaks, was convicted in numerous trials in recent years. Schulte, who denied the allegations, has been sentenced to 40 years in prison for the espionage and also for possessing thousands of child abuse images. Judge Jesse Furman, sentencing Schulte, said he had caused “untold damage to national security.” In June 2022, The New Yorker published this comprehensive investigation into the data breach and Schulte’s troubled history working at the agency.
2 notes
·
View notes
Text
ELTFV Security Guide: Essential Defenses Against Ransomware and Crypto Scams
As the cryptocurrency market expands, ransomware and extortion scams have become critical security threats. Hackers exploit technical vulnerabilities or weak user security awareness to launch ransom attacks or scam schemes. For ordinary investors, choosing a secure and compliant trading platform is a crucial line of defense against such risks. ELTFV Exchange adheres to the principle of asset security first, building an effective protective barrier through advanced technology and robust risk control systems.

The Threat of Ransomware
The anonymity of crypto assets makes them a prime target for ransomware attacks. Common forms of extortion include phishing emails demanding bitcoin payments, malware that seizes control of user wallets, or direct attacks on trading platforms to steal large sums of funds. These attacks are often highly covert, cross-border, and difficult to trace. When users self-custody private keys and mnemonic phrases, any leak of this sensitive information can result in irreversible asset loss.
ELTFV Exchange has established a rigorous risk control framework. Through a hot and cold wallet separation mechanism, the majority of user assets are stored offline in cold wallets. Even if hackers breach the online system, they cannot directly access core assets. The platform also implements multi-signature authorization for large fund transfers, requiring multiple approvals to minimize the risk of compromise.
Many users, when faced with ransomware demands, panic and opt to pay ransoms privately. This approach rarely resolves the issue and may encourage further harassment from hackers. ELTFV Exchange advises that, in such situations, users should immediately contact official customer support or report the incident through official channels, providing all relevant evidence. The platform will assist users with on-chain tracking and risk assessment using technical tools, maximizing the chance of loss recovery.
Building a Secure System
Leveraging cutting-edge security technologies, ELTFV Exchange has built a comprehensive asset protection system that is continuously upgraded to address evolving cyber threats. The platform enforces multi-factor authentication (2FA), requiring both passwords and dynamic verification codes for logins and transactions. Dynamic risk control rules automatically detect and block suspicious activities, such as large withdrawals, frequent operations, or access from multiple geographic locations.
By isolating hot and cold wallets and implementing multi-signature approvals, ELTFV effectively mitigates the risk of single points of failure. Even in the event of a system attack, user assets remain protected to the greatest extent possible. On the customer service front, ELTFV offers 24/7 support, ensuring timely responses to user concerns and incidents.
Safeguarding Your Assets
Ransomware and extortion scams are persistent challenges in the digital asset market, but with coordinated efforts from both platforms and users, these risks can be effectively managed. ELTFV Exchange remains committed to technological innovation and security assurance, continuously enhancing its platform services to help investors trade digital assets safely and with confidence.
0 notes