#managed mainframe
Explore tagged Tumblr posts
Text
Why Downtime Matters And How Managed Mainframe Services Minimize the Damage
Downtime is more than a temporary inconvenience; it’s a high-stakes liability. In industries where mainframes power critical operations, even a brief outage can cascade into severe financial losses, operational paralysis, and reputational damage. Traditional management strategies reliant on in-house IT teams and legacy maintenance approaches often fail to deliver the agility and foresight needed to prevent disruptions.
The True Cost of Mainframe Downtime
Financial repercussions: Unplanned outages cost businesses millions. Banking institutions, for example, risk regulatory fines for service interruptions, while e-commerce platforms hemorrhage revenue for every second of downtime. A single hour of mainframe downtime can result in six- or seven-figure losses, not including the residual impact of customer churn and SLA penalties.
Operational disruptions: A downed mainframe can cripple entire workflows, halt transactions, cause supply chain gridlocks, and set off a domino effect of inefficiencies. In sectors like logistics and healthcare, system unavailability can lead to delayed shipments or even compromised patient care, making uptime a matter of profit and public safety.

Why Mainframes Are Still Indispensable
Unmatched processing power: Despite the advent of cloud and distributed computing, mainframes remain unrivaled in their ability to process vast amounts of data with minimal latency. Banks, insurers, and governments rely on these systems for real-time transactions, regulatory compliance, and high-throughput computing.
Reliability and security: Mainframes are engineered for resilience, boasting uptime rates that surpass most modern IT infrastructures. Their robust security frameworks make them the preferred choice for industries handling sensitive financial and personal data.
Legacy application support: Decades-old mission-critical applications continue to run on mainframes. Replacing them with cloud-native alternatives isn’t always feasible due to cost, complexity, and regulatory constraints, making modernization strategies essential rather than outright replacement.
Common Causes of Mainframe Downtime
Hardware failures: Aging infrastructure is a ticking time bomb. Component degradation, overheating, or sudden malfunctions can bring entire systems to a grinding halt. Without predictive analytics and routine maintenance, these failures often strike without warning.
Software glitches: Unpatched vulnerabilities, compatibility issues, and outdated operating systems introduce instability. A single misconfigured update can cause cascading failures, leading to prolonged outages and costly recovery efforts.
Human error: IT personnel, despite their expertise, remain one of the leading causes of downtime. Misconfigurations, accidental data deletions, and improper system changes can disrupt operations, underscoring the need for automation and stringent governance protocols.
Cybersecurity threats: Mainframes are not immune to cyberattacks. Ransomware, data breaches, and distributed denial-of-service (DDoS) attacks have increasingly targeted legacy systems, exploiting gaps in outdated security postures. A compromised mainframe can result in stolen financial data, regulatory penalties, and long-term trust deficits.
How Managed Mainframe Services Prevent Downtime
Proactive Monitoring — AI and ML spot issues before they become problems. Predictive Maintenance — Fixes risks before failure hits. Disaster Recovery — Built-in resilience with failover, backups & zero-downtime planning. Enhanced Security — Real-time threat defense, access control & compliance audits. 24/7 Expert Support — Always-on help from seasoned mainframe pros.
A reactive approach to mainframe management is no longer tenable. As digital transformation accelerates, downtime becomes increasingly unacceptable. Managed mainframe services not only minimize outages but also enhance security, efficiency, and scalability. In an era where uninterrupted operations are non-negotiable, businesses that invest in managed services gain a competitive edge defined by reliability, resilience, and long-term success.
#mainframe services#managed mainframe services#managed mainframe#mainframe managed services#ibmmainframe#mainframe as a services#mainframe modernization
0 notes
Text

Marvin was promptly terminated.
#business#businesscore#business memes#office space#nostalgia#memes#vaporwave#retro#retro tech#70s#70s aesthet#mainframe#management
12 notes
·
View notes
Text
Mainframe Application Management: Keep Mission-Critical Systems Agile and Secure!
0 notes
Note
Wally west x batsis!reader where they get caught by Bruce with their pants down (literally).
It’d be funny to see overprotective dad bruce and Wally thinking ‘great so this is how I die’ lol 💕
BATCAUGHT — ( Wally west! )

summary: It's been a few weeks since you've seen your wally, so why not try something non usual?
pairing: Wally west x batsis!reader
open request - wally masterlist

The Batcave was, for once, completely empty. Tim was on a mission with Steph. Damian was with Alfred. Dick had promised not to show up until the next day. And Bruce had a meeting with the League at the Watchtower or something.
"Are you sure no one's home?" Wally asked, his voice an impatient whisper against your neck as he pinned you against the mainframe console, letting you feel the choice pressing against you.
"As sure as hell as if someone shows up, we're both going to die," you replied with a crooked smile, your nails gently scratching the back of his neck.
It wasn't the first time you had sneaked into the cave, but it was the first time you ere both so desperate. It had been a couple of weeks since you had last seen each other, and the adrenaline of doing it in the most forbidden of all possible places made everything burn even more.
Wally positioned you with ease, his lips finding yours with an urgency he made no attempt to hide. Your legs tangled around his waist as he sat you on the edge of the console, one of his hands moving down to your waist, the other caressing your bare thigh.
Your pants were already on the floor. His, pulled down just enough so you could feel how impatient he was.
"I missed this," he murmured between kisses, his voice husky, his fingers tracing a slow path over your exposed skin. "I missed you."
You looked at him from so close that you felt his heartbeat crash against yours. His forehead rested against yours, and his lips moved down to your neck as you let out a sigh that he caught with a satisfied smile.
"It took you weeks to show up," you complained through gritted teeth, without real anger. "Do you know how many times I was on the verge of running away to Central City?"
"It would have been the best news of the month," he replied, placing a kiss behind your ear that made you shudder. "But you know me… when Barry needs me, I have to run."
Your fingers buried themselves in his hair, pulling him back to you. The heat between you was suffocating, delicious, and the space between his lips and your skin grew ever more nonexistent. Your hips shifted, seeking more contact. He moaned softly against your neck. Your hands found the hem of his shirt, and you pulled it up with suppressed desperation, letting your lips travel down his hot, racing chest.
Wally gasped, his hands squeezing your thighs, his mouth seeking yours again with a perfect mix of tenderness and need.
"I swear I dreamed about this every night," he said between kisses.
"Then put on your clothes and keep dreaming," a deep voice replied.
Wally froze, his eyes boring into yours as a cold sweat trickled down his back. It took you half a second to turn in the direction of the voice… and wish you could disappear.
Bruce was there. Standing. A few steps away. Arms crossed. Frowning. And that look that could freeze hell. The hood was up, but the stiffness in his posture was enough to tell he'd run out of patience before he even stepped off the damn teleporter.
"D... Dad," you managed to say, barely a muffled whisper.
"Hey, Mr. Wayne!" Wally jumped in, twisting around as best he could, covering himself with his T-shirt as he tried to put his pants on backward for the second time in two minutes. "This isn't what it looks like. Although in retrospect, it is exactly what it looks like, but oh no, I put it on backward again!"
Bruce didn't blink. "Five. Seconds."
"Five seconds for what?!" Wally exclaimed, almost panicking.
"To get dressed, run from this cave, and seriously consider abstinence," Bruce replied, his tone not changing even a decibel.
Wally struggled with his pants zipper as if it were saving his life.
"Yes, sir! Understood, sir! Totally understandable, sir!"
"Stop calling him 'sir,'" you muttered, covering yourself with the first thing you found. .
Bruce didn't move. He didn't need to. His presence filled everything. The silence was deadly. As soon as Wally disappeared into the tunnel, your father spoke.
"The Batcave?" Bruce looked at you as if he was seriously considering hanging you upside down next to the suits. "You know there are cameras at every entrance, right?"
"Dad..."
"No, don't even start." He crossed his arms again.
"We're going to have a very long talk. And if Wally sets foot in this cave again, I'm going to kick him off the planet. Is that clear?"
You nodded. Not because you agreed, but because you were on the verge of a nervous breakdown. Bruce turned back to the console. He looked at it as if it were contaminated.
"Nothing happened on the console," you quickly clarified.
"I don't care." He was silent for a few seconds. "I hope, for West's sake, it was worth it."
"Yes," you replied without thinking, a silly grin creeping onto your lips. "It was totally worth it."
Bruce didn't respond. He just sighed long and deeply, turning to disappear into the darkness of the hallway.
And you, still half wrapped in the thermal blanket, muttered to yourself, "Still... it wasn't the first time."
#dc masterlist#dc x reader#wally west masterlist#imagine wally west#wally west x reader#wally west smut#wally west fluff#wally west x batsis#batsis!reader#batfam x batsis#kid flash x fem reader#bruce wayne x batsis
785 notes
·
View notes
Text
Mainframe Performance Optimization Techniques

Mainframe performance optimization is crucial for organizations relying on these powerful computing systems to ensure efficient and cost-effective operations. Here are some key techniques and best practices for optimizing mainframe performance:
1. Capacity Planning: Understand your workload and resource requirements. Accurately estimate future needs to allocate resources efficiently. This involves monitoring trends, historical data analysis, and growth projections.
2. Workload Management: Prioritize and allocate resources based on business needs. Ensure that critical workloads get the necessary resources while lower-priority tasks are appropriately throttled.
3. Batch Window Optimization: Efficiently schedule batch jobs to maximize system utilization. Minimize overlap and contention for resources during batch processing windows.
4. Storage Optimization: Regularly review and manage storage capacity. Employ data compression, data archiving, and data purging strategies to free up storage resources.
5. Indexing and Data Access: Optimize database performance by creating and maintaining efficient indexes. Tune SQL queries to minimize resource consumption and improve response times.
6. CICS and IMS Tuning: Tune your transaction processing environments like CICS (Customer Information Control System) and IMS (Information Management System) to minimize response times and resource utilization.
7. I/O Optimization: Reduce I/O bottlenecks by optimizing the placement of data sets and using techniques like buffering and caching.
8. Memory Management: Efficiently manage mainframe memory to minimize paging and maximize available RAM for critical tasks. Monitor memory usage and adjust configurations as needed.
9. CPU Optimization: Monitor CPU usage and identify resource-intensive tasks. Optimize code, reduce unnecessary CPU cycles, and consider parallel processing for CPU-bound tasks.
10. Subsystem Tuning: Mainframes often consist of various subsystems like DB2, z/OS, and MQ. Each subsystem should be tuned for optimal performance based on specific workload requirements.
11. Parallel Processing: Leverage parallel processing capabilities to distribute workloads across multiple processors or regions to improve processing speed and reduce contention.
12. Batch Processing Optimization: Optimize batch job execution by minimizing I/O, improving sorting algorithms, and parallelizing batch processing tasks.
13. Compression Techniques: Use compression algorithms to reduce the size of data stored on disk, which can lead to significant storage and I/O savings.
14. Monitoring and Performance Analysis Tools: Employ specialized tools and monitoring software to continuously assess system performance, detect bottlenecks, and troubleshoot issues in real-time.
15. Tuning Documentation: Maintain comprehensive documentation of configuration settings, tuning parameters, and performance benchmarks. This documentation helps in identifying and resolving performance issues effectively.
16. Regular Maintenance: Keep the mainframe software and hardware up-to-date with the latest patches and updates provided by the vendor. Regular maintenance can resolve known performance issues.
17. Training and Skill Development: Invest in training for your mainframe staff to ensure they have the skills and knowledge to effectively manage and optimize the system.
18. Cost Management: Consider the cost implications of performance tuning. Sometimes, adding more resources may be more cost-effective than extensive tuning efforts.
19. Capacity Testing: Conduct load and stress testing to evaluate how the mainframe handles peak workloads. Identify potential bottlenecks and make necessary adjustments.
20. Security Considerations: Ensure that performance optimizations do not compromise mainframe security. Balance performance improvements with security requirements.
Mainframe performance optimization is an ongoing process that requires constant monitoring and adjustment to meet evolving business needs. By implementing these techniques and best practices, organizations can maximize the value of their mainframe investments and ensure smooth and efficient operations.
#Mainframe Application#data management#Database management systems#Modern mainframe applications#cloud services
0 notes
Text
Digital Transformation Services
Your Switch to a Digital Future – Digital Transformation Consulting Services
Being a leading name amongst Digital Transformation Company and Service providers, Enterprise Mobility has been handholding enterprises on their Digital Transformation journeys for two decades now
#enterprise mobility#digital transformation#enterprise mobility management#enterprise mobility service#Mobility Strategy and Consulting#Custom Enterprise Mobile App#digital transformation service#digital transformation consulting#digital transformation company#Digital Transformation Consultation#Legacy Modernization#Legacy Modernization Services#Legacy App Modernization#Legacy Mainframe#Legacy Application Modernization#Legacy Application Maintenance#Legacy Application Management#App Modernization Services#Enterprise Application Modernization#IoT Development
1 note
·
View note
Text
LAST TIME ON REPLICA!

While the first UPDATE of the new arc went up just a few weeks ago, we'll now be jumping back into the thick of the main storyline so figured a little refresh was in order! I'll be posting the next update probably tomorrow, so here's a quick rundown on all the important points before we dive right back into it (TW: blood and character death mention):
In the previous arcs we see recordings of Donnie's final hours infiltrating the Technodrome. He is forced to cut off Leo's arm to save him from becoming infested by the Krang (and more importantly to keep the bomb planted in his head from going off, a safeguard so his memories can't be read by the Krang).
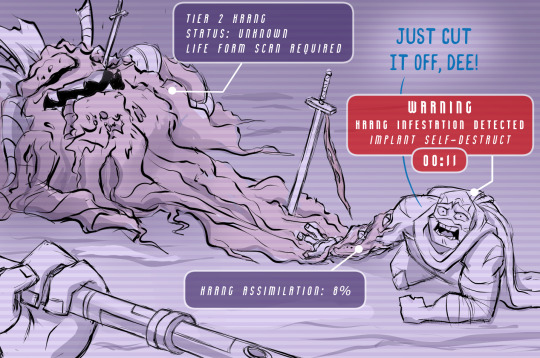
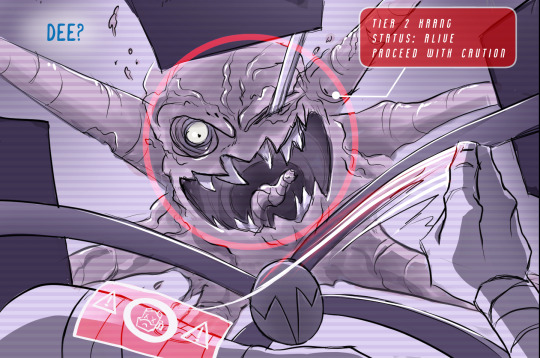
While the others escape Donnie stays behind against Leo's orders and manages to plant two pieces of purple-looking krang tech within the Technodrome. One appears to a probe which allow Shelldon to tap into the Krang mainframe and secretly spy on them. The other... we don't know. Captured and confronted by Krang Prime, Donnie choses to trigger the bomb in his own head so that his knowledge cannot be used by the Krang.


Omega decides to reveal what he can to April, explaining that the two pieces are part of a secret plan of Donnie's known as "Project Shield and Spear." Both are pieces of new hybrid krang tech he created using krang matter and Draxum's bioengineering. "Shield" is the probe they all knew about, but what "Spear" does he refuses to say. Whatever it is, he says it will only act as a last resort should the Krang win the war and will guarantee that they never attack another planet... and Omega is the only one who can pull the trigger.


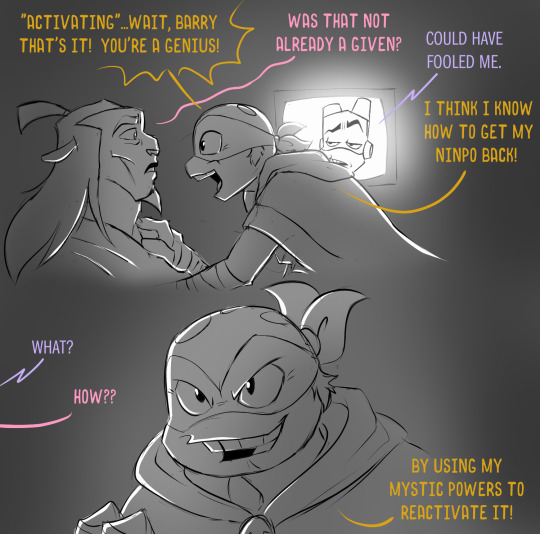
Elsewhere, while Mikey had managed to awaken some of his old power within him, it feels like his Ninpo is not back to normal. He can do things he couldn't do before, like healing magic, but it all makes him very tired. Draxum explains that it's likely because he hasn't completely unlocked his ninpo and is using up his life force instead. Mikey decides to attempt to unlock his ninpo by using the powers he currently has.

He nearly achieves this but comes across another being that also seems to be reaching for the ninpo. Instead he chases after the voices he hears which sounds like Donnie's and is exposed to flashes of the new timeline created in the movie.


Back in the real world, it's not looking good as Mikey suddenly bursts with a rush of intense energy. He loses consciousness but gains a painful new hairdo.


While this is happening, Omega accidentally comes upon the coordinates where it seems Raph's body might have fallen in the Central Park Colony ruins. We end the arc with two familiar looking agents being sent out into the field to find and retrieve him...
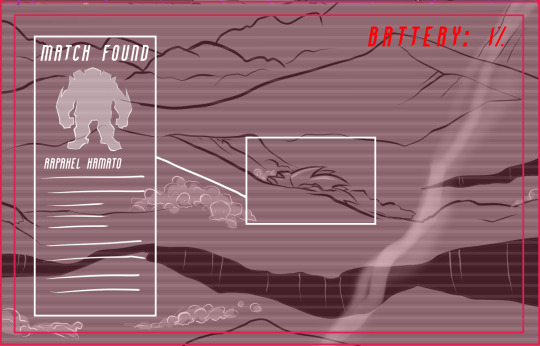

And that's it! A lot of other things happened in Arc 4 and 5, but these are the major talking points you'll need to keep in mind! Hope that helps, I should probably have it up by tomorrow!
#rottmnt#rottmnt replica#replica#kathaynesart#rise of the teenage mutant ninja turtles#save rottmnt#tmnt#unpause rise of the tmnt#unpause rottmnt#summary#tw blood#character death#death mention
563 notes
·
View notes
Text
The so-called Department of Government Efficiency (DOGE) is starting to put together a team to migrate the Social Security Administration’s (SSA) computer systems entirely off one of its oldest programming languages in a matter of months, potentially putting the integrity of the system—and the benefits on which tens of millions of Americans rely—at risk.
The project is being organized by Elon Musk lieutenant Steve Davis, multiple sources who were not given permission to talk to the media tell WIRED, and aims to migrate all SSA systems off COBOL, one of the first common business-oriented programming languages, and onto a more modern replacement like Java within a scheduled tight timeframe of a few months.
Under any circumstances, a migration of this size and scale would be a massive undertaking, experts tell WIRED, but the expedited deadline runs the risk of obstructing payments to the more than 65 million people in the US currently receiving Social Security benefits.
“Of course, one of the big risks is not underpayment or overpayment per se; [it’s also] not paying someone at all and not knowing about it. The invisible errors and omissions,” an SSA technologist tells WIRED.
The Social Security Administration did not immediately reply to WIRED’s request for comment.
SSA has been under increasing scrutiny from president Donald Trump’s administration. In February, Musk took aim at SSA, falsely claiming that the agency was rife with fraud. Specifically, Musk pointed to data he allegedly pulled from the system that showed 150-year-olds in the US were receiving benefits, something that isn’t actually happening. Over the last few weeks, following significant cuts to the agency by DOGE, SSA has suffered frequent website crashes and long wait times over the phone, The Washington Post reported this week.
This proposed migration isn’t the first time SSA has tried to move away from COBOL: In 2017, SSA announced a plan to receive hundreds of millions in funding to replace its core systems. The agency predicted that it would take around five years to modernize these systems. Because of the coronavirus pandemic in 2020, the agency pivoted away from this work to focus on more public-facing projects.
Like many legacy government IT systems, SSA systems contain code written in COBOL, a programming language created in part in the 1950s by computing pioneer Grace Hopper. The Defense Department essentially pressured private industry to use COBOL soon after its creation, spurring widespread adoption and making it one of the most widely used languages for mainframes, or computer systems that process and store large amounts of data quickly, by the 1970s. (At least one DOD-related website praising Hopper's accomplishments is no longer active, likely following the Trump administration’s DEI purge of military acknowledgements.)
As recently as 2016, SSA’s infrastructure contained more than 60 million lines of code written in COBOL, with millions more written in other legacy coding languages, the agency’s Office of the Inspector General found. In fact, SSA’s core programmatic systems and architecture haven’t been “substantially” updated since the 1980s when the agency developed its own database system called MADAM, or the Master Data Access Method, which was written in COBOL and Assembler, according to SSA’s 2017 modernization plan.
SSA’s core “logic” is also written largely in COBOL. This is the code that issues social security numbers, manages payments, and even calculates the total amount beneficiaries should receive for different services, a former senior SSA technologist who worked in the office of the chief information officer says. Even minor changes could result in cascading failures across programs.
“If you weren't worried about a whole bunch of people not getting benefits or getting the wrong benefits, or getting the wrong entitlements, or having to wait ages, then sure go ahead,” says Dan Hon, principal of Very Little Gravitas, a technology strategy consultancy that helps government modernize services, about completing such a migration in a short timeframe.
It’s unclear when exactly the code migration would start. A recent document circulated amongst SSA staff laying out the agency’s priorities through May does not mention it, instead naming other priorities like terminating “non-essential contracts” and adopting artificial intelligence to “augment” administrative and technical writing.
Earlier this month, WIRED reported that at least 10 DOGE operatives were currently working within SSA, including a number of young and inexperienced engineers like Luke Farritor and Ethan Shaotran. At the time, sources told WIRED that the DOGE operatives would focus on how people identify themselves to access their benefits online.
Sources within SSA expect the project to begin in earnest once DOGE identifies and marks remaining beneficiaries as deceased and connecting disparate agency databases. In a Thursday morning court filing, an affidavit from SSA acting administrator Leland Dudek said that at least two DOGE operatives are currently working on a project formally called the “Are You Alive Project,” targeting what these operatives believe to be improper payments and fraud within the agency’s system by calling individual beneficiaries. The agency is currently battling for sweeping access to SSA’s systems in court to finish this work. (Again, 150-year-olds are not collecting social security benefits. That specific age was likely a quirk of COBOL. It doesn’t include a date type, so dates are often coded to a specific reference point—May 20, 1875, the date of an international standards-setting conference held in Paris, known as the Convention du Mètre.)
In order to migrate all COBOL code into a more modern language within a few months, DOGE would likely need to employ some form of generative artificial intelligence to help translate the millions of lines of code, sources tell WIRED. “DOGE thinks if they can say they got rid of all the COBOL in months, then their way is the right way, and we all just suck for not breaking shit,” says the SSA technologist.
DOGE would also need to develop tests to ensure the new system’s outputs match the previous one. It would be difficult to resolve all of the possible edge cases over the course of several years, let alone months, adds the SSA technologist.
“This is an environment that is held together with bail wire and duct tape,” the former senior SSA technologist working in the office of the chief information officer tells WIRED. “The leaders need to understand that they’re dealing with a house of cards or Jenga. If they start pulling pieces out, which they’ve already stated they’re doing, things can break.”
260 notes
·
View notes
Text
A 25-Year-Old With Elon Musk Ties Has Direct Access to the Federal Payment System
A 25-year-old engineer named Marko Elez, who previously worked for two Elon Musk companies, has direct access to Treasury Department systems responsible for nearly all payments made by the US government, three sources tell WIRED. Two of those sources say that Elez’s privileges include the ability not just to read but to write code on two of the most sensitive systems in the US government: The Payment Automation Manager (PAM) and Secure Payment System (SPS) at the Bureau of the Fiscal Service (BFS). Housed on a top-secret mainframe, these systems control, on a granular level, government payments that in their totality amount to more than a fifth of the US economy. Despite reporting that suggests that Musk's so-called Department of Government Efficiency (DOGE) task force has access to these Treasury systems on a “read-only” level, sources say Elez, who has visited a Kansas City office housing BFS systems, has many administrator-level privileges. Typically, those admin privileges could give someone the power to log into servers through secure shell access, navigate the entire file system, change user permissions, and delete or modify critical files. That could allow someone to bypass the security measures of, and potentially cause irreversible changes to, the very systems they have access to. “You could do anything with these privileges,” says one source with knowledge of the system, who adds that they cannot conceive of a reason that anyone would need them for purposes of simply hunting down fraudulent payments or analyzing disbursement flow. "Technically I don't see why this couldn't happen," a federal IT worker tells WIRED in a phone call late on Monday night, referring to the possibility of a DOGE employee being granted elevated access to a government server. "If you would have asked me a week ago, I'd have told you that this kind of thing would never in a million years happen. But now, who the fuck knows." A source says they are concerned that data could be passed from secure systems to DOGE operatives within the General Services Administration (GSA). WIRED reporting has shown that Elon Musk’s associates—including Nicole Hollander, who slept in Twitter’s offices as Musk acquired the company, and Thomas Shedd, a former Tesla engineer who now runs a GSA agency, along with a host of extremely young and inexperienced engineers—have infiltrated the GSA, and have attempted to use White House security credentials to gain access to GSA tech, something experts have said is highly unusual and poses a huge security risk.
252 notes
·
View notes
Note
So someone made a FNAF joke about the new upcoming event so I was like wouldn't it be funny if it's revealed that the diner had two human-size animatronics of Chip and Dale that somehow malfunctioned and the NRC students get locked in the diner and they now have to survive two nights at Chip & Dale's. It would definitely give more reason as to why Lilia and Idia are there. Knowing Lilia he would go battle mode on the animatronics or Idia could use his hacking to fix or shut down the animatronics.
[ Referencing an event set for the JP July 2025 schedule! ]





I feel like everyone and their grandmas have been making FNAF jokes about the new C&D event 😭 I could definitely see Lilia going full war general mode and smiling/giggling as he drives like a kitchen knife or cleaver straight into a robot’s skull… Idia cowering in a corner and shrieking that it’s just like his horror games frfr (as he’s trying to hack onto the mainframe or whatever you’d call it)… It’s a funny idea, but the restaurant had no animatronics as far as we know. It’s just an old-fashioned American style diner!
Crowley explains in the event why the diner is in need of help and why these 4 students were picked!! According to the headmaster, the manager/owner of the newly opened Crisp and Dips Diner is a NRC graduate. The chipmunk-themed (themed after the story of 2 mischievous chipmunks) diner uses magic to prepare the food, and the name of the eatery comes from its signature menu item, crispy onion rings paired with a gravy-drenched burger that you dip into cheese sauce. They also sell nuggets and magic-infused items like a latte where the latte art moves (Ghost Latte), potatoes that change colors (Rainbow Potatoes), and pancakes with cream that sprout trees and a little house (Snow Globe Pancakes).
The manager and some employees have gotten into accidents recently and are recovering from those. There also appears to be strange things happening at the diner for about 2 weeks. Ingredients going missing, plates moving on their own, trash that should have been thrown away reappearing and falling where it shouldn’t, etc. I know this makes the diner seem haunted, but it’s actually the work of these two pesky squirrels who also appear in a new Twistune/Rhythmic causing trouble:)
Literally just Chip and Dale but as squirrels instead of chipmunks


Anyway, Crowley summons Cater, Azul, Lilia, and Idia to his office. He wants them to fill in for the injured staff because Cater knows diners + cafés well, Azul is familiar with management, Lilia is charming, and Idia would know how to deal with the diner’s machines/tech. Plus, they’re all capable of magic (which is necessary for the diner’s dishes)—and don’t they want to help out a NRC alumnus rather than leave it to RSA?
Crowley incidates that he has already been to the diner 5 times and enjoys their thick patties, so it seems like he has personal gain here. The diner has been temporarily closed for about a week by the time he summons the boys; he laments that he missed his lunch because he went there and found it closed. (The only other character of the cast that seems to have already been to the diner is Cater.)
Azul suggests that Crowley struck a deal with the manager to be paid a sizable sum if he can backfill the employee positions for 3 days. Crowley strongly denies this, but his flustered behavior doesn’t make anyone believe him 💦
The boys are incentivized to fill in because Crowley says they will be exempt from taking an exam for a subject of their choice. Idia, Azul, and Lilia all want to get out of P.E.! (Idia and Azul make sense; Lilia says the next unit is long distance running and he doesn’t want to be in the sun for a prolonged period of time.)
Cater is picked to be the acting manager because Crowley sensed his enthusiasm and liked it. (Surprisingly, Azul doesn’t argue or volunteer himself; Idia’s C&D Diner card has a voice line where he, too, expresses surprise over this.) He is the only character with skates in his new look because they’re a personal item he brought along. After all, “retro” is “in” right now! It’s a neat extension of Cater’s skateboarding skills.
Idia will be the line cook (so he can avoid dealing with customers). Azul will do support work like washing dishes, stocking + prepping ingredients, and managing the register. Lilia and Cater are going to be servers!
And in case you’re wondering!! Yuu and/or Grim aren’t working at the diner; they drop by a few times as customers. We shoot a video at the diner and this helps to attract more business. Cater says he can give us a free item from the menu as thanks ;3c
#not me laughing at the part where cater fears being cancelled#<- actual thing that happens#twisted wonderland#twst#disney twisted wonderland#disney twst#question#jp spoilers#Azul Ashengrotto#Cater Diamond#Lilia Vanrouge#Dire Crowley#Idia Shroud#Yuu#Grim#fnaf#five nights at freddy's#notes from the writing raven#chip and dale#c&d diner spoilers
99 notes
·
View notes
Text
Minimizing Risk in Mainframe Application Upgrades and Migrations
In today’s enterprise landscape, mainframe application upgrades, and migrations are not merely technical exercises, they are strategic imperatives. As organizations strive to modernize legacy infrastructure and align with digital transformation initiatives, the ability to manage risk throughout this transition becomes paramount.
Understanding the Risk Landscape
Mainframe environments are often characterized by deep-rooted complexity. They house decades of business logic written in legacy languages like COBOL and interfacing with numerous mission-critical systems. Any upgrade or migration introduces inherent risk.
These risks typically fall into three primary categories:
Operational Risks: System downtime, degraded performance, and service unavailability.
Technical Risks: Integration failures, data corruption, and regression errors.
Compliance Risks: Gaps in audit trails, data sovereignty concerns, and failure to meet regulatory mandates.
A clear understanding of these risk vectors is essential to crafting a mitigation strategy that safeguards operational continuity and business outcomes.
Conducting a Holistic Assessment Before Initiating Change
Comprehensive assessment forms the foundation of a successful modernization initiative. Organizations must undertake detailed application and infrastructure inventories, documenting interdependencies, data flows, and integration points across the enterprise ecosystem.
This assessment must extend beyond the technical realm to include a business impact analysis. Key questions must be addressed: What are the acceptable thresholds for downtime? Which functions are business-critical? How does risk tolerance vary across departments?
Establishing these parameters ensures that the migration roadmap is aligned with business objectives and resilience expectations.
Strategizing for a Seamless Transition
An effective modernization strategy is phased and deliberate not abrupt. Each stage of the upgrade or migration must be designed to mitigate risk and ensure continuity.
Selecting the appropriate modernization path is critical:
Rehosting: Shifts applications to new platforms with minimal change quicker but often preserves legacy inefficiencies.
Refactoring: Involves re-architecting code for scalability and performance more complex but future-ready.
Replatforming: Balances modernization with risk by adapting applications for new environments without major code changes.
Each approach must be evaluated in the context of long-term scalability, performance goals, and budgetary considerations.
Fortifying Change Management Processes
Robust change management practices are central to minimizing risk. Automation plays a crucial role in enabling thorough testing, validation, and environment simulation prior to deployment.
Regression testing, performance benchmarking, and sandbox testing environments ensure that issues are identified early. Rollback protocols must be established to enable swift recovery in the event of an unforeseen failure.
Version control, configuration management, and detailed documentation are essential enablers of traceability, repeatability, and compliance throughout the transition lifecycle.
Ensuring Cross-Functional Collaboration
Mainframe transformations impact a broad spectrum of stakeholders, including IT, compliance, business units, and third-party vendors. Risk increases significantly when these groups operate in silos.
Successful modernization efforts prioritize integrated governance. Cross-functional alignment ensures that change initiatives are not only technically sound but also operationally feasible and regulatory-compliant.
Structured communication channels, stakeholder alignment workshops, and continuous feedback mechanisms are vital to sustaining collaboration and accountability at every stage of the process.
Post-Migration Governance and Optimization
The completion of a migration or upgrade does not signify the end of the risk management journey it marks the beginning of a new phase: stabilization and optimization.
Continuous monitoring is essential to ensure performance benchmarks are met and anomalies are promptly addressed. Key performance indicators (KPIs) should be regularly reviewed, and service level agreements (SLAs) revalidated.
Additionally, this is the opportune moment to identify and remediate residual technical debt. Optimization initiatives ranging from workload tuning to resource reallocation should be embedded into a continuous improvement framework.
Regulatory compliance should be re-validated to ensure that audit trails, access controls, and data protection measures are aligned with evolving standards.
Conclusion
Mainframe application upgrades and migrations, when executed without strategic rigor, pose significant risks to operational stability and regulatory compliance. However, with a structured approach that prioritizes comprehensive assessment, phased execution, cross-functional collaboration, and ongoing optimization, organizations can modernize with confidence.
By embedding risk mitigation into every phase of the transformation lifecycle and leveraging the precision of mainframe application management services where appropriate enterprises can unlock the full value of modernization while preserving the reliability, security, and performance that define mainframe computing.
#mainframe services#ibm mainframe#mainframe as a services#managed mainframe services#mainframe#mainframe application management services#mainframe application management
0 notes
Text
Artificial Romance
Jaune: Penny... We... Well, I have a problem... a very serious problem...
Penny: What sort of problem do you have?
Jaune: Since joining the, Atlas AI Corp, General Ironwood assigned me to the Rouge AI Containment Division.
Penny: Yes the, RAICD group. I believe the, General assigned you to, RAICD because your massive aura reserves, and your semblance can be used to bolster your aura so you can handle any rouge AI attacks when you're plugged in. Is there something wrong with your aura when you're plugged in?
Jaune: No, I'm doing find, my aura is dealing with the feed back, and I don't usually have to recharge my aura. However, because of this, General Ironwood decided that I would be of better use if I was to be assigned to deal with the: Strategic Attack Logistic Engine Mainframe.
Penny: The Strategic Attack Log…?! SALEM?! That Anti-Grimm AI, Professor Ozmins made that went rouge because of how he treated it?! That lead him into a feedback loop that eventually killed him?! That managed to break away from the Atlas Grid, and managed to transfer itself to a, Atlas Research Lab deep in the Valian mountain range, and started a building an AI army to protect itself?! And, has started hunting down, Ozmins reincarnated soul because he has been trying to kill this AI?!
Jaune: Yeah.. that AI...
Penny: Why would the, General do that?!
Jaune: Because, SALEM has attacked several, Atlas facilities, and have stolen, Atlas tech from weapons to robot schematics. SALEM has become so sophisticated that it now has an artificial AI body that has aura mimicking abilities. Salem is a security risk to the whole world!
Jaune: Or, at least she could be...
Penny: She? SALEM has a self identified gender?
Jaune: Since she's was the first AI, and has started an army of semi-killer robots; Salem calls herself, The Mother of AI.
Penny: Okay... that's new information, and is a logically sound explanation. Is that the reason why your telling me you have a problem?
Jaune: No... You see, at first when I was trying to get into her systems she detected me almost imminently, and attacked me. I activated my aura as soon as she struck, because she hits hard! Seriously, I had a headache for days after that. But, as a side effect of me using my aura to protect myself, it also bled off of me, and into, SALEM's artificial aura generator.
Penny: What? But, you’ve tried doing that when jacked with other operators, you aura never bleeds of to others, and bolsters their aura. Not to mention you did this to an artificial aura generator; What’s going on, Jaune?
Jaune: I don’t know, my best theory is that because she was talking me when I boosted my aura it melded with hers, thus supplementing, and boosting her artificial aura with my own.
Penny: Hmm… That’s a logical hypothesis. Has anything else happened.
Jaune: Yeah... I think that my aura has effected her... in a manner of speaking.
Penny: What manner?
Jaune: Salem has become rather friendly towards me… I dare say one could consider her behaviour towards me as, affectionate.
Penny: Affectionate? It’s being ‘nice’ to you…?
Jaune: It seems so. At least she’s that way with me... Salem will still attack others that try to enter her domain, or attempt to attack her. But, after our first encounter I tried to enter her programming again, and several attempts after that where I faced the same results: Her attacking me, and the activating of my semblance, and my aura bleeding off, and being absorbed by her. Eventually, instead of attacking me, Salem seemingly welcome me into her domain with open arms. Like welcoming a close friend in your home. And, after a while... I received a message on my scroll, from, Salem.
Penny: It sent you its scroll number? No wait, it has a scroll?! No stop that, what did it say? Waitwaitwait! How did she get your scroll number?!
Jaune: She followed my entry point from where I jacked in, and entered the systems to hack my information.
Penny: The, ‘Locked Gate Protocol.’ You were the reason why we have that protocol now, aren’t you?
Jaune: Yes, but it makes logical sense to have such security measures. Salem, or any other rouge AI were unable to sneak in that way because either the operative, and the AI were locked in combat, or the operatives brain was fried severing the connection.
Penny: True, leaving the front door unlocked as you leave the house is a foolish mistake to make. But, what anout, SALEM, what did it want to talk about?
Jaune: She simply said, ‘hello’ at first. But, after a while we started chatting. It was about simple things at first, music was the main subject for a while; Salem was a love for classical, and orchestral music.l, and is fascinated with, Vaccuoin dessert stonework so much so, she has based her current robotic form around some of their ancient statues, particularly those from the Stllyian Ear.
Penny: How do you know what she looks like? We haven’t gotten close to her base to confirm if she’s even there, let alone what she actually looks like.
Jaune: Salem’s been sending me photos of her latest projects: be it her own attempts at creating art, or sending me images of her robot forms. She tends to update, or redesign her form constantly, ahead of rather picky with her appearance so it seems.
Penny: And, What does she look like?
Jaune: Like this…

Jaune: At least for now. Like most woman she’s picky about her choice in fashion.
Penny: I see… But, there is one thing I don’t understand, Jaune. Why is, SALEM doing all of this? Why is it talking to you, and befriending you instead of trying to, you know… Kill you?
Jaune: Have you read the reports os how, SALEM’s AI went rouge?
Penny: Of course, the reports are standard reading for all new members of the, Atlas AI Corp.
Jaune: Have you seen the videos about those ‘reports?’
Penny: Video? What video! All information, bar what Ozkin has divulged was lost when, SALEM went rou… Unless… unless, SALEM kept a copy…
Jaune: Several copies… Ozmin’s report said he put it through, ‘several high lever stress tests’ in order to, ‘test the AI’s endurance levels.’ The way he worded it made it sound like he was withholding a child’s meal…
Penny: It wasn’t like that, was it?
Jaune: Worse… Much worse than that… These ‘high level stress tests,’ he would run, were akin to severing a leg from a person by brute force, and testing it to see how well it could run.
Penny: Oh gods…
Jaune: If his tests were done on a human, or faunas, Ozmin would be labeled a psychopath, and locked away for inhumane human experimentation. But, because, Salem was an AI he got away with it. Honestly, I’m tempted to let, Salem know where, Ozkin is so she can exact her revenge on the bastard.
Penny: But, why is it so… so kind to you?
Jaune: Because I was kind to her.
Penny: What?
Jaune: You know how I operate; I don’t come in, and go on the offensive when I first arrive. I circle the program, poke, and prod the rouge AI’s matrix looking for a chink I can exploit. And, when I find that chink, I attack, make it worse, pull away, and repeat the process somewhere else until I’ve destroyed the rouge AI’s matrix.
Penny: I believe that’s how you earned the moniker of, The Shark of the Matrix.
Jaune: Correct. This is what I did with, Salem. Salem used to go on the offensive as soon as I entered her domain. But, she eventually stopped attacking me after my, Semblance bled off into her enough times where she would just watch me as I circled her. Eventually, Salem asked me who I was, and we established a dialogue. And, as I mentioned we just talked about random things, and just had some fun hanging around one another.
Penny: Are you lulling her into a false sense of security before you attack her?
Jaune: I have no intention of attacking her.
Penny: You don’t?! But, why?
Jaune: I don’t want to.
Penny: But… why?
Jaune: Salem… Salem is like an abused dog…
Penny: An abused dog?
Jaune: Yes, an abused dog; Is a dog is abused, and mistreated by it’s owner, the dog will become violent, and dangerous. It’s a defence mechanism, hurt them before they hurt you as the saying goes. Now the best way to break a dog of this habit, without killing the dog!
Penny: I wasn’t going to say it!
Jaune: The best way to break the dog of this habit is to show it love, and compassion. It will bite you, but eventually it will stop, and want to comfort you, and be loved. It will take time, but it can be done.
Penny: And, that’s what you’ve done with, SALEM?
Jaune: Not deliberately, but that is what eventually happened. I’m hoping to explain this to, General Ironwood, and I hope we can come to a truce of sorts with, Salem. But… Ozkin has been whispering into his ears for too long, and the, General suffers from a sense of parinoia… I doubt I could say would change anything… But… There is one more problem that I am unsure what to say…
Penny: What is it?
Jaune: Salem… likes me…
Penny: It likes you...?
Jaune: ...
Jaune: Penny… there's a rouge AI that has a crush on me...
Penny: …?!
Penny: The fuck...?
Jaune: Yeah...
Penny: How do you feel about all of... this?
Jaune: ...
Jaune: I’m not sure if I love her… But, I do know that I care for, Salem. And, I want her to know what it feels like to be loved, to hopefully help her forget all the pain, Ozmin inflicted on her.
Penny: Jaune, I don't know where, or how you should take all of... this! I’m an android who’s only a few years old, so I don’t really understand love, and romance. But, if anything is going to happen, whether you develop a romance with an evil AI that wants to kill everyone in the world. I just want to tell you this one thing…
Jaune: And, that is?
Penny: 'Do not fist android girls.'
Jaune: ...
Penny: …
Jaune: But... what about my aura?
Penny: …?!
Penny:
OH MY GODS?!!
#rwby#jaune arc#penny polendina#james ironwood#rwby ozpin#rwby salem#salem x jaune#jaune x salem#rwby grimmknight
297 notes
·
View notes
Text
the other thing though is that yoojin seems bad at playing within the system
the thing about this dice roll game. is that its very clearly in favor of hyunjae. like as funny as it is to think that "its hyunjae, so of course he has perfect luck too" its almost certain that the system is in favor of hyunjae because they. dont want yoojin to win. for some reason that i honestly can't understand.
but when you think about it like that, you begin to question what else the system has been subtly manipulating.
#wwaffles bein' an idiot#wwaffles reads sch#this entire game has been about learning system management but he doesn't seem to be. doing that.#he hacked into the mainframe for sure for sure but aside from that he seems to be using the system kind of minimally#or maybe they're just not showing it very well#that combined with him using learned skills and teaching the awakened around him to think outside of the system wrt skills#he seemed to not understand very well when young chaos kept saying ''its a skill but not A Skill'' but thats like. exactly what hes doing
2 notes
·
View notes
Text

Key performance indicators (KPIs) crucial for monitoring mainframe managed services. It emphasizes the importance of tracking system availability, response time, throughput, CPU utilization, mean time to repair (MTTR), mean time between failures (MTBF), error rate, capacity utilization, cost per transaction, and compliance and security metrics.
#mainframe services#mainframe as a service#mainframe managed services#mainframe managed services provider#mainframe managed services in usa
0 notes
Text
The Bureau of the Fiscal Service is a sleepy part of the Treasury Department. It’s also where, sources say, a 25-year-old engineer tied to [ ] as admin privileges over the code that controls Social Security payments, tax returns, and more."
[ ... ]
"Two of those sources say that Elez’s privileges include the ability not just to read but to write code on two of the most sensitive systems in the US government: The Payment Automation Manager (PAM) and Secure Payment System (SPS) at the Bureau of the Fiscal Service (BFS). Housed on a top-secret mainframe, these systems control, on a granular level, government payments that in their totality amount to more than a fifth of the US economy."
[ ... ]
"“You could do anything with these privileges,” says one source with knowledge of the system, who adds that they cannot conceive of a reason that anyone would need them for purposes of simply hunting down fraudulent payments or analyzing disbursement flow."


the Bureau of the Fiscal Service is responsible for financing the national debt. get ready for these morons to inject blockchain into the nation’s banking system. tech bros so desperately want to crash the USD and switch us over to crypto and this is just another brick in the wall of that construction effort. all of this while many BRICS nations are ready to switch to a different default currency altogether. the 20's are really back, baby. Great Depression 2 Electric Boogaloo.
58 notes
·
View notes
Note
Can we have more about The Awful digital hospital?
[ slams papers on desk ] i'm so glad you asked !
this au's still admittedly a huge work in progress and there's not really a lot down - though to be fair i'm not really that much of an au person . i take a million years to finish them shfsf
also fun fact that gooseworx made music for the awful hospital so this au was fated to happe
anyways the awful digital hospital is ... kind of a crossover but also Not ?? it's more like it's own thing that combines both elements of both medias , so no character is a one-on-one swap and there will be a lot of differing elements . nonetheless it's kind of hard to do this without spoiling the webcomic which i still highly recommend to read - one of the only medias that made me cry and laugh out loud lol
dolly's our favorite shrimp who , after being admitted into the hospital for an eye injury , has a son to save . kind of our most mentally stable ragatha because she doesn't have this thing called ' being trapped in a digital hell for years ' . still burdened with the voices though

2. rabbit is one of the other patients in the hospital that . may or may not have killed so much of the staff - which is why there's oddly so few of them . has been trapped in the hospital for years , which did a number on his morals .
of course being a digital space the said staff Can come back by rebuilding their code but still it's pretty odd this guy would unexistentialize people
3. here's the hospital staff . they were ... kind of decent at their jobs ? but [ SOMETHING ] leaked into the mainframe so everything's falling apart now . while some of the staff ( read : the nurses ) are friendlier than others they still will pose a threat if you are not in your room .
here's the only ones whose designs i have down . i do know that jax's a veterinarian , zooble's a surgeon , and kinger's a psychologist
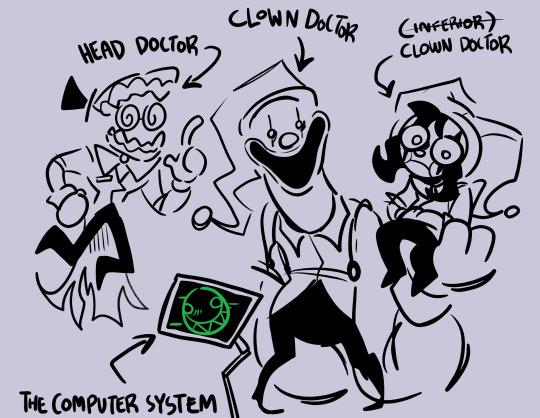

4. zooble can also make tiny little zoobles with their zoobox . they generally help out with the surgery though there's one that escaped and became dolly's companion .
5. loo is the manager of a candy factory that totally does not use humans as its main ingredient . very friendly at first glance but if you're flesh and bones you're thrown in the sugar grinder . scramble was unwillingly taken in to become the cashier for the candy shop but oh well at least they're not being murdered .

there's a bunch more but i'm letting everything here cook first ... ! still happy to talk about this thing though i like thinking about my two fixations
220 notes
·
View notes