#powershell date
Explore tagged Tumblr posts
Text
I don't want to reply to this on the post it's on, because it'd be getting pretty far away from the original point (that being that chromebooks have actively eroded the technological literacy of large proportions of young people, especially in the US), but I felt enough of a need to respond to these points to make my own post.
Point 1 is... pretty much correct in the context that it's replying to; the Google Problem in this case being the societal impact of Google as a company and how their corporate decisions have shaped the current technological landscape (again, especially in the US). I'd argue it's less like saying Firefox is a good alternative for your dishwasher and more like saying Firefox is a solution for climate change, but whatever, the point's the same. You can't personal choices your way out of systemic issues.
Point 2 is only correct in the most pedantic way; we both know that 'running on a Linux kernel' isn't what we mean when we talk about Linux systems. It's one true definition, but not a functional or useful one. Android and ChromeOS (and to a lesser extent, MacOS, and to an even greater extent, the fucking NES Mini) all share a particular set of characteristics that run counter to the vast majority of FOSS and even Enterprise Linux distributions. Particularly, they're a.) bundled with their hardware, b.) range from mildly annoying to damn near impossible (as well as TOS-breaking) to modify or remove from said hardware, and c.) contain built-in access restrictions that prevent the user from running arbitrary Linux programs. I would consider these systems to all be Linux-derived, but their design philosophies and end goals are fundamentally different from what we usually mean when we talk about 'a Linux system'. Conflating the two is rhetorically counterproductive when you fucking know what we mean.
Point 3 is a significant pet peeve of mine, and the primary reason why I feel the need to actually respond to this even if only on my own blog. "Linux is not a consumer operating system" is such a common refrain, it's practically a meme; yet, I've never seen someone explain why they think that in a way that wasn't based on a 30-year-old conception of what Linux is and does. If you pick up Linux Mint or Ubuntu or, I don't know, KDE Plasma or something, the learning curve for the vast majority of things the average user needs to do is nearly identical to what it would be on Windows. Office software is the same. Media players is the same. Files and folders is the same. Web browsers is the same. GIMP's a little finicky compared to Photoshop but it also didn't cost you anything and there are further alternatives if you look for them. There are a few differences in terms of interface, but if you're choosing between either one to learn for the first time you're using a computer, the difference isn't that large. Granted, you can also do a bunch of stuff with the command line - you could say the same of Powershell, though, and you don't have to use either for most things. Hell, in some respects Windows has been playing catch-up - the Windows Store post-dates graphical software browsers on Linux by at least a decade, maybe more. Finding and installing programs has, quite literally, never been harder on Linux than on Windows - and only recently has Windows caught up. I used Linux as my daily driver for five years before I ever regularly had to open up the terminal (and even then it was only because I started learning Python). I was also seven when I started. If the average teenager these days has worse computer literacy than little seven year old Cam Cade (who had, let me think, just about none to start with), I think we have bigger issues to worry about.
In my opinion, Linux users saying Linux 'isn't for consumers' is an elitist, condescending attitude that's not reflective of the actual experience of using a Linux system. To say so also devalues and trivializes the work put in to projects like Mint and Ubuntu, which are explicitly intended to be seamlessly usable for the vast majority of day-to-day computer tasks.
3 notes
·
View notes
Text
TS4 CC not working despite installing correctly? Make sure Windows unblocked the file!
I've seen this a lot on some CC creators Patreons, where the person can't seem to get the CC working despite installing it correctly. If you're using Windows 10 or 11, it could be that Windows is blocking your downloads.
This is a security feature by Windows and AFAIK, you can't disable it but you can fix your downloads (including things you've already installed!). Though this is tedious, you only have to do this once per folder.
If you have CC that's in a zip/rar/compressed file, you can just do the first few steps on the zip/rar/compressed file and it was unblock everything within the zip file but ONLY if that file has the "unblock" notification seen in my screenshots.
You can't make things faster by tossing all of your CC into a zip/rar/compressed file and then unblocking it - you would have to use the Powershell command that's in part two of this.
A quick note: I'm using Windows 10 and a custom theme with custom-made cursors as well as custom-made taskbar and desktop icons, so my UI might look different than yours.
Read on, I have you covered in this super short tutorial.
PART ONE: UNBLOCKING SINGLE FILES.
When I download CC, I put my .package files into a folder on my desktop and name it Creator Name - Date, so that if I'm having trouble with my game being weird, I can do back and see what I last installed by looking for the date in the folder name. After I know this CC won't cause trouble, I'll just remove the date sometimes but usually I just leave it.
For this tutorial, we're going to assume your CC is in a folder like mine:

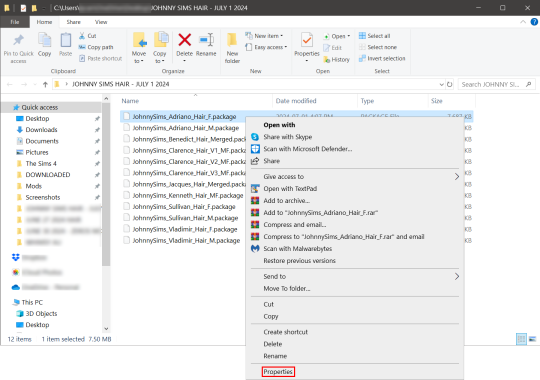
So, you can see I have a few Johnny Sims hair I've downloaded today. It's ready to go into my CC folder but first I need to 'unblock' it. Let's right-click the first file, "JohnnySims_Adriano_Hair_F.package" and left-click "properties".
Now you're going to have a new window come up with a message:
This file came from another computer and might be blocked to help protect this computer.
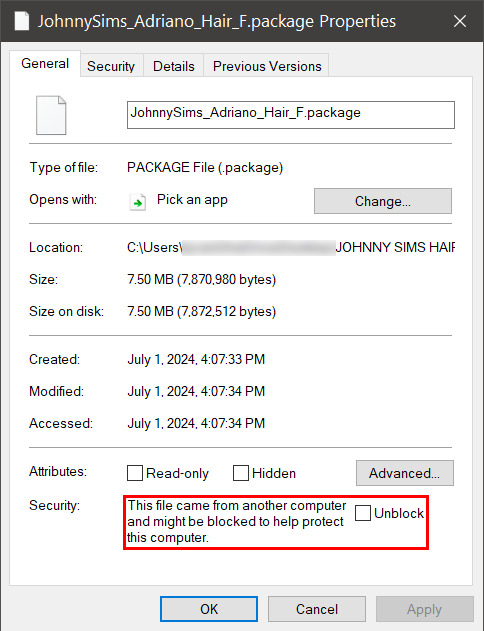
Click the checkbox (the square) next to the word Unblock that is to the right of the message, and then click "apply" and "okay". This window will now close. Do this for each of your .package files.
That's it! You're done and can now move your CC into your mods folder. You will have to do this each time you download new CC as Windows has this security feature on by default and it's not a good idea to disable it unless you really know what you are doing. It protects your computer from allowing harmful malware to run.
There is a command to use to unblock an entire folder in one go if you're wanting a quick means to do this, so read on for that.
PART TWO: UNBLOCKING AN ENTIRE FOLDER WITH WINDOWS POWERSHELL
If you want to unblock an entire CC folder, the easiest way is with a Windows PowerShell command. This requires you to be on an administrator account on your Windows machine, otherwise you will have to enter the administrator password or have some other means to bypass UAC.
I would recommend making a backup/copy of your mods folder and making a backup before doing this, as well, moving your mods folder to your desktop and executing this command there, rather than doing so within the Sims 4 folder.
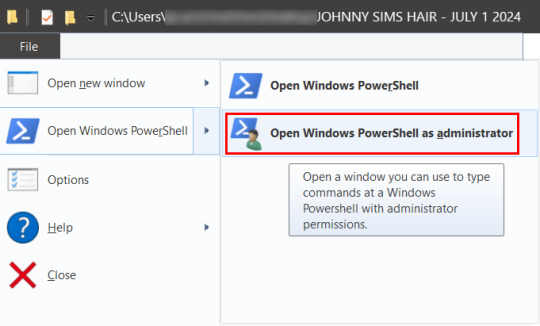
You'll want to click "file" up on the top left of your CC folder, then hover over "Open Windows PowerShell":
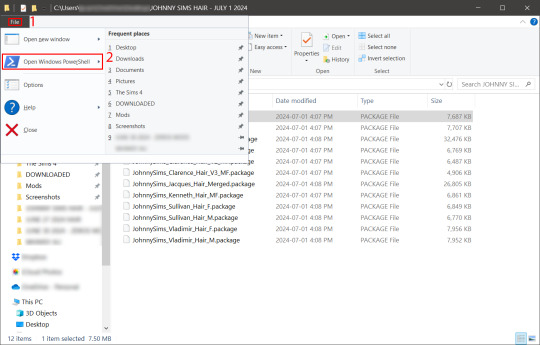
From there, a second menu should come out that gives two options: "Open Windows PowerShell" and "Open Windows PowerShell as administrator".
We want to click "Open Windows PowerShell as administrator":
You'll have a command prompt-looking window pop up then. Mine is blue, yours may be a different color depending on if you have a different Windows theme or dark mode enabled (I do not have dark mode).
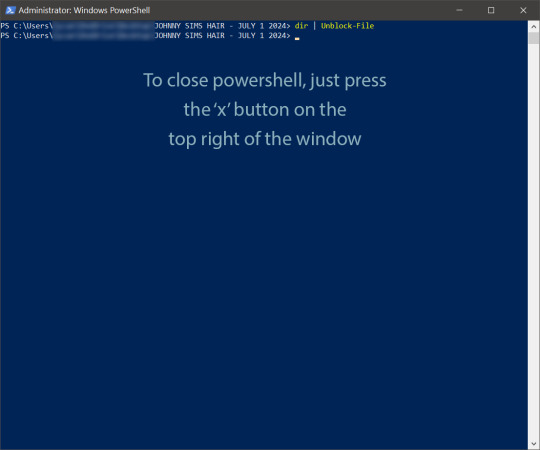
With this window open, you'll see that the directory listed is the one for your CC folder we were just in. Click at the end of the directory where the > is, and type: dir | Unblock-File (capitalization is important here, and for QWERTY keyboards, the | button is above the 'enter' key, you just have to use the 'shift' key while pressing it, otherwise you'll get a backslash):

Now hit 'enter'. You won't get any sort of message telling you the command has worked. If you get an error message, you typed something wrong. Just type correctly on the next line and hit 'enter' again.
If your user directory shows up like mine with a flashing cursor, that means Windows PowerShell is waiting for another command and you did it correctly. Close out of this window by clicking the 'x' on the top right of the window.
Check your CC by right-clicking any of the .package files as we did at the start, going to 'properties' and then making sure that message is gone:

See how it is blank under 'attributes'? The message is gone, meaning our CC is unblocked. Now we can move it into our mods folder and it should show up in the game.
If you have any questions, feel free to send me a message/ask and I'll do my best to help!
2 notes
·
View notes
Text
I'm actually making use of this now after nearly 5 years. Probably a good thing since I was in an awful headspace 5 years ago. I'm still not doing well, but I am doing *better* now that I'm like...employed and shit now. I work IT help desk. Not the greatest job but I make decent money. Not enough to own a house but...I'm not optimistic in my ability to own my own place in the future.
To introduce myself...I'm a 25 (soon to be 26) year old woman living in the US working IT help desk. I love to play video games (especially ARPGs such as Diablo) and have an obsession with vocal synthesizers such as VOCALOID. My sexuality is weird and doesn't really have a proper label to apply to it. All you need to know in that regard is that I am gay as hell. The "content" that I create are mods for video games, with my current project being a Diablo II LoD mod. I'm not much of a programmer though. I just know some scripting in Python and PowerShell. My mod is mostly changing database entries and modifying miscellaneous files like animation files and tilesets.
Today was a good day though. I got a big raise (holy shit I am beating inflation now) and I recently picked up the game Starsector. It seems like the type of game I'd be super into, but the egg is a bit hard to crack. It hasn't hooked me yet but I can feel its potential to become a big-ass obsession. I've been super into games with dynamic worlds and ever-changing systems like Doors of Trithius and Soldak games. Which, I highly recommend trying Soldak's games. They look and control really jankily but they're awesome and innovative.
It's late as I write this though so I will have to try Starsector a different night. Probably not tomorrow since I need to motivate myself to clean up my apartment and I can't stay up too late on Friday since I have a couple appointments on Saturday.
I started dating a dude despite saying I would never date a dude. He's super sweet and really supportive. I don't really feel like I am good enough for him in either the looks department or just...how much affection I show. I don't really show affection in the same way as other people and when I try to it feels fake as hell and makes me feel gross. Like I don't feel genuine when I do that but my genuine self feels cold to people I guess. He's quite a bit younger than me. 4 year age gap. He keeps comparing himself to me in terms of his career but like...my dude, I was *losing* money when I was his age. I was (is?) a lazy, privileged fuck who could go to college. He's doing better than I was but he doesn't seem to see that. He's working towards a career on his own and I practically had it handed to me on a silver platter. College is easy. Doing things on your own? Hard as hell.
Well, that's all I'm going to write for tonight. I'll probably play a couple of bot matches in Unreal Tournament then go to sleep. Still one more day of work this week. Aaaaaaaa
5 notes
·
View notes
Note
hi! your lighting mod script is a godsend!!! however it doesn't seem to work for me, when i run with powershell the window opens and immediately closes again. and i haven't checked in game yet but the .world files don't seem to have been replaced in my game folder (judging by the modification date of the files in my game folder) so i'm assuming it didn't work. do you have any idea why this is happening? i'm on windows 11, could that have anything to do with it? thanks!!
are you seeing the "Lighting mod or game files not found!" message at all before it closes? the powershell window does immediately close after, so i know it's quick. maybe you need to change the paths, you can send me dms with pictures for more help if necessary
2 notes
·
View notes
Text
Metadata Management After Moving from Tableau to Power BI
Migrating from Tableau to Power BI is a strategic decision for organizations looking to centralize analytics, streamline licensing, and harness Microsoft's broader ecosystem. However, while dashboard and visual migration often take center stage, one crucial component often overlooked is metadata management. Poor metadata handling can lead to inconsistent reporting, broken lineage, and compliance issues. This blog explores how businesses can realign their metadata strategies post-migration to ensure smooth and reliable reporting in Power BI.
Understanding Metadata in BI Tools
Metadata is essentially "data about data." It includes information about datasets, such as source systems, field types, data definitions, relationships, and transformation logic. In Tableau, metadata is often embedded in workbooks or managed externally via Data Catalog integrations. In contrast, Power BI integrates metadata tightly within Power BI Desktop, Power BI Service, and the Power BI Data Model using features like the Data Model schema, lineage views, and dataflows.
Key Metadata Challenges During Migration
When migrating from Tableau to Power BI, metadata inconsistencies often arise due to differences in how each platform handles:
Calculated fields (Tableau) vs. Measures and Columns (Power BI)
Data lineage tracking
Connection methods and source queries
Terminology and object references
Without careful planning, you may encounter broken dependencies, duplicate definitions, or unclear data ownership post-migration. This makes establishing a robust metadata management framework in Power BI essential.
Best Practices for Metadata Management in Power BI
1. Centralize with Dataflows and Shared Datasets Post-migration, use Power BI Dataflows to centralize ETL processes and preserve metadata integrity. Dataflows allow teams to reuse cleaned data models and ensure consistent definitions across reports and dashboards.
2. Adopt a Business Glossary Rebuild or migrate your business glossary from Tableau into Power BI documentation layers using tools like Power BI data dictionary exports, documentation templates, or integrations with Microsoft Purview. This ensures end users interpret KPIs and metrics consistently.
3. Use Lineage View and Impact Analysis Leverage lineage view in Power BI Service to trace data from source to dashboard. This feature is essential for auditing changes, understanding data dependencies, and reducing risks during updates.
4. Implement Role-Based Access Controls (RBAC) Metadata often contains sensitive definitions and transformation logic. Assign role-based permissions to ensure only authorized users can access or edit core dataset metadata.
5. Automate Metadata Documentation Tools like Tabular Editor, DAX Studio, or PowerShell scripts can help export and document Power BI metadata programmatically. Automating this process ensures your metadata stays up to date even as models evolve.
The OfficeSolution Advantage
At OfficeSolution, we support enterprises throughout the entire migration journey—from visual rebuilds to metadata realignment. With our deep expertise in both Tableau and Power BI ecosystems, we ensure that your metadata remains a strong foundation for reporting accuracy and governance.
Explore more migration best practices and tools at 🔗 https://tableautopowerbimigration.com/
Conclusion Metadata management is not just an IT concern—it’s central to trust, performance, and decision-making in Power BI. Post-migration success depends on aligning metadata strategies with Power BI’s architecture and features. By investing in metadata governance now, businesses can avoid reporting pitfalls and unlock more scalable insights in the future.
0 notes
Text
Sort your holiday photos!
Just made a powershell script to help those like me, who sort their photos only at the end of their trip.
I would be happy to answer your questions if any Lightroom may do it, but my script is free and open source :]
#software development#powershell#software#coding#sorting algorithms#holiday#pictures#travel#microsoft windows#dev#programming
0 notes
Text
Associate
Job title: Associate Company: HCLTech Job description: plus ServiceNow certification (e.g., Certified Implementation Specialist, Certified Application Developer) a plus Proficiency… in scripting languages such as JavaScript, PowerShell, or Python Familiarity with IRM principles and practices Excellent analytical… Expected salary: Location: Hyderabad, Telangana Job date: Thu, 22 May 2025 01:39:15…
0 notes
Text
I hate TikTok!
Not the people - some of them seem absolutely lovely, and they've been very welcoming 🥰 ...
🤬No, I'm talking about the interface for uploading on Android. As far as I can tell it was designed in hell!🤬
I'm creating slideshows with between 25 & 35 slides in each, all of which have to be in the right order, the only thing on each that changes being the text on the slide.
The low res previews are so bad I had to use Phone Link on my PC so I can make everything bigger so I can see it (some of us do not have young eyes) - and I still have to pattern match most of the text rather than really reading it.
It has taken me 2 days to figure out how to get my slides to list in order when I go to select them - 2 whole days!
And my solution involves Windows powershell scripts and zip files.
I asked Google multiple times how I could do it via file names and it assured me I could not because the TikTok ap does not do that. Clearly I was asking the wrong questions.
Finally I stooped to asking ChatGPT if it knew of a better way, because I was out of ideas completely. You know what it said? Huh? Do you?!!!!
I CAN JUST DO IT FROM "My Files"!!
Don't do it from the TikTok app - that's utter shite, do it from "My Files" where if you click the files in order and share to TikTok, it puts them in in order. I mean it doesn't copy anything in order if you're copying from the PC to the Phone and trying to get the created dates on your files to be right, but apparently, it does do it right for loading the damn things into other applications.
Why, why can't I just do this in the ap? All I want to be able to do is see the file names, or order them by name like a reasonable human being, but nope, can't do anything sensible like that.
I hate it - I hate it - I hate it!

0 notes
Text
UNC4057 LOSTKEYS Malware Targets Western NGOs

UNC4057 LOSTKEYS
The Russian government-backed outfit COLDRIVER targets Western and non-governmental organisations with its latest spyware, LOSTKEYS.
The Russian government-backed threat organisation COLDRIVER (also known as UNC4057, Star Blizzard, and Callisto) has stolen data from NGOs and Western targets using LOSTKEYS, a new virus. The Google Threat Intelligence Group (GTIG) been tracking COLDRIVER for years, including its SPICA malware in 2024, and believes LOSTKEYS is a new tool.
COLDRIVER focusses on credential phishing targeting well-known targets. People at NGO or personal email addresses are generally targeted. They steal login passwords, emails, and contact lists after gaining access to a target's account. COLDRIVER may also access system files and infect devices with malware.
COLDRIVER has attacked journalists, think institutes, NGOs, and past and current Western government and military advisors. Plus, the gang has kept targeting Ukrainians. COLDRIVER's principal goal is to acquire intelligence for Russia's strategic goals. In several cases, the gang hacked and leaked NGO and UK official data.
January, March, and April 2025 saw the discovery of LOSTKEYS malware. The malicious application may take files from a hard-coded set of folders and extensions and transmit the attacker system details and active processes. COLDRIVER normally utilises credentials to access contacts and emails, although they have utilised SPICA to access target system documents. LOSTKEYS has a unique purpose and is utilised in certain scenarios.
The multi-step LOSTKEYS infection chain begins with a tempting website featuring a fake CAPTCHA. After the CAPTCHA is “verified,” the PowerShell code is transferred to the user's clipboard and the page invites them to execute it using Windows' “run” prompt. The “ClickFix” approach includes socially engineering targets to copy, paste, and run PowerShell scripts. Google Threat Intelligence Group said many APT and financially driven attackers use this method, which has been well documented.
PowerShell does the first stage's second step. In numerous instances, the IP address 165.227.148[.] provided this second step.68. The second step computes the display resolution MD5 hash and stops execution if it matches one of three specified values. This step may avoid virtual machine execution. The request must contain IDs unique to each observed instance of this chain to proceed. In every observation, the third stage comes from the same host as the previous phases.
Base64-encoded blobs decode into additional PowerShell in the third phase. This step requires retrieving and decoding the latest LOSTKEYS payload. It does this by downloading two additional files from the same host using different identities for each infection chain. The first-downloaded Visual Basic Script (VBS) file decodes the second file. Each infection chain is decoded with two keys. One unique key is in the decoder script, while stage 3 saves the second. Keys are used to replace cypher the encoded data.
The final payload is LOSTKEYS VBS. File theft and system data collection are its purposes.
Two more LOSTKEYS samples dated December 2023 were uncovered during this behaviour investigation. These previous PE files posing as Maltego files change greatly from the execution chain starting in 2025. It is unclear if these December 2023 samples are related to COLDRIVER or if the malware was reused from another operation into January 2025. Exchanged Indicators of Compromise (IOCs) include binary hashes and C2 addresses like njala[.]dev and 80.66.88[.]67.
Google Threat Intelligence Group uses threat actor research like COLDRIVER to improve product security and safety to safeguard consumers. Once detected, hazardous websites, domains, and files are added to Safe Browsing to protect users. Government-backed attacker warnings alerted Gmail and Workspace users. Potential targets should enrol in Google's Advanced Protection Program, enable Chrome's Enhanced Safe Browsing, and update all devices.
Google shares its findings with the security community to raise awareness and help targeted companies and people. Sharing methods and approaches improves threat hunting and sector user protections. The original post comprises YARA rules and compromise indicators and is available as a Google Threat Intelligence collection and rule bundle.
#UNC4057LOSTKEYS#UNC4057#COLDRIVER#GoogleThreatIntelligence#virtualmachines#VisualBasicScript#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
0 notes
Text
15 Types of Malware Everyone Should Know About
In today’s digital world, our devices are more connected than ever. While this makes life easier, it also means more opportunities for cybercriminals to attack. One of the biggest online threats is malware. But what is malware? And how can you stay safe from it?
In this blog, we’ll explain 15 different types of malware in simple terms. We’ll also show you how using tools like CoverMeVPN can help protect your personal information and keep you safe online.
What Is Malware?
Malware is short for malicious software. It’s any program or file created to harm your computer, steal your information, or take control of your device without your permission. Cybercriminals use malware to cause problems for people, businesses, and even governments.
Let’s look at the most common types of malware you should watch out for.
The 15 Main Types of Malware
1. Virus
A virus attaches itself to a file or program. When you open that file, the virus spreads to other files on your device. Viruses can damage data, slow down your system, or even delete important files.
Example: A harmful file downloaded from a suspicious email.
Worm
A worm spreads by itself through a network. It doesn't need you to open a file or click a link. Worms often slow down computers and networks by using up resources.
Example: A worm might spread through email contacts and send copies of itself to others.
Trojan Horse
A Trojan horse, or Trojan, looks like a normal file or app. But when you open it, it installs malware secretly. Trojans are often used to steal personal data or give hackers control of your device.
Example: A free online game that secretly steals your passwords.
Ransomware
Ransomware locks your files and demands money to unlock them. It usually asks for payment in cryptocurrency, like Bitcoin.
Example: The famous WannaCry ransomware attack in 2017 affected thousands of companies around the world.
Spyware
Spyware secretly gathers information about you. It can track your keystrokes, watch the websites you visit, and record your passwords.
Example: A program that steals your online banking details while you type.
Adware
Adware shows unwanted ads on your screen. Some adware also collects information about your browsing habits without your permission.
Example: Pop-up ads that appear even when you’re not using your browser.
Rootkit
A rootkit hides deep in your system and allows hackers to control your computer remotely. It’s very hard to detect.
Example: A hacker secretly turning on your webcam.
Keylogger
A keylogger records every key you press. It captures passwords, messages, and credit card numbers.
Example: A hidden program that sends everything you type to a hacker.
Botnet
A botnet is a group of infected computers controlled by a hacker. These computers, called bots, work together to perform tasks like sending spam emails or attacking websites.
Example: A hacker using thousands of infected computers to crash a website.
Fileless Malware
Fileless malware doesn’t install any files. It uses existing programs on your computer to perform harmful tasks, making it hard for antivirus programs to find.
Example: Malware that uses system tools like PowerShell to steal data.
Logic Bomb
A logic bomb is hidden in a program and only activates when certain conditions are met, like a specific date or event.
Example: A malicious code set to delete files on April 1st.
Mobile Malware
Mobile malware attacks smartphones and tablets. It can steal data, track your location, or send premium-rate messages.
Example: A fake mobile app that quietly spies on you.
Scareware
Scareware tricks you by displaying fake virus warnings. It tries to scare you into buying fake software or services.
Example: A pop-up claiming “Your system is infected! Download now!”
Rogue Security Software
A form of scareware, rogue security software pretends to be a real antivirus program. It shows fake alerts and asks you to pay for a solution to problems that don’t exist.
Example: A program claiming you have 500 viruses when your device is clean.
Malvertising
Malvertising uses online ads to spread malware. Even trusted websites can display infected ads without knowing it.
Example: Clicking an ad promising a free prize, which installs malware.
How to Stay Safe from Malware
Staying safe online doesn’t have to be complicated. A few simple habits can protect you from most malware threats:
Always keep your software updated.
Don’t click on suspicious links or attachments.
Use strong, unique passwords for every account.
Backup your important files regularly.
Install reliable antivirus software.
Avoid downloading apps or files from unknown sources.
And here’s a powerful tool to add to your defense:
🌐 Protect Your Privacy with CoverMeVPN
One of the best ways to stay safe online is by using a VPN (Virtual Private Network). A VPN hides your IP address and encrypts your internet connection, making it much harder for hackers to target you.
We recommend CoverMeVPN, a trusted and secure VPN service that shields your online activity from prying eyes. It prevents malware from tracking your location and protects your personal information, especially when using public Wi-Fi networks.
Whether you’re working from home, traveling, or just browsing at a coffee shop, CoverMeVPN adds an extra layer of safety between you and the internet.
Why CoverMeVPN?
Keeps your identity and data private.
Protects you on public Wi-Fi.
Blocks dangerous websites.
Easy to use and fast.
Final Thoughts
Malware comes in many forms, and it’s more common than most people realize. From viruses and worms to ransomware and spyware, these digital threats can cause serious problems. The good news is that by learning about malware and taking simple steps to stay safe, you can avoid most attacks.
Make sure to use strong passwords, avoid suspicious links, and always keep your devices up to date. And for even stronger protection, consider using a VPN like CoverMeVPN to keep your online life private and secure.
By being careful and staying informed, you can enjoy the internet safely without falling victim to malware.
0 notes
Text
Everything You Need to Know About iManage: A Comprehensive Guide for Law Firms
In the ever-evolving world of legal practice, managing documents and emails efficiently is crucial. iManage, a leading provider of document and email management systems, plays a pivotal role in the smooth operation of law firms, corporate legal departments, and other professional services. This blog will explore various aspects of iManage, including iManage Outlook, iManage WorkSite Manual, iManage PowerShell, iManage News, iManage Records, and its importance for law firms.
1. iManage Outlook: Streamlining Email and Document Management
iManage Outlook is a robust integration that connects Microsoft Outlook with iManage, offering a seamless experience for managing email correspondence and documents. With iManage Outlook, legal professionals can easily file emails into the appropriate client or matter, ensuring that important information is organized and easily accessible.
The integration also enables users to save emails directly from Outlook to iManage, tagging them for future retrieval. This integration enhances efficiency by keeping emails and documents connected, thus reducing the time spent searching for critical information.
For law firms looking to optimize their workflow, iManage Outlook is an indispensable tool. Learn more about integrating iManage with your email system at MacroAgility's iManage Email and Document Work 10 and Share.
2. iManage WorkSite Manual: Empowering Teams with Centralized Document Management
iManage WorkSite is the foundation for document and email management, offering a secure and centralized system for storing, organizing, and retrieving files. The iManage WorkSite manual is a comprehensive guide that helps users understand how to navigate and maximize the capabilities of WorkSite.
With WorkSite, legal teams can easily track revisions, manage versioning, and collaborate on files without worrying about data loss. The platform’s user-friendly interface makes it easy for team members to access the information they need while maintaining the highest standards of security and compliance. For law firms, this is an essential tool to maintain a secure and organized digital ecosystem.
3. iManage PowerShell: Automating Tasks for Efficiency
iManage PowerShell is a scripting tool designed to automate routine tasks and streamline operations within iManage. This powerful tool is used by IT professionals and administrators to simplify processes such as document management, user provisioning, and security configurations.
By using iManage PowerShell, organizations can reduce manual errors, improve workflow efficiency, and ensure that their iManage environment is configured to meet their specific needs. Automation helps free up resources, allowing legal professionals to focus on higher-value tasks rather than mundane, repetitive activities.
For more information on iManage PowerShell, check out additional resources like MacroAgility’s Lotus to Outlook, where you can discover how automation can be seamlessly integrated into your practice.
4. iManage News: Staying Updated on Latest Developments
Keeping up with the latest trends and updates is crucial in the legal tech world. iManage regularly releases news updates that include new features, product enhancements, and case studies demonstrating how their systems improve efficiency and security.
Staying updated with iManage News ensures that law firms can take advantage of the latest advancements in document management technology. These updates also help businesses stay compliant with regulatory requirements, keeping their systems up-to-date with the latest legal and industry standards.
For the most recent iManage news and updates, visit MacroAgility’s News and Events to learn about the latest happenings and innovations in the industry.
5. iManage Records: Ensuring Compliance and Security
For law firms, document security and compliance are non-negotiable. iManage Records provides a comprehensive solution for managing, securing, and archiving important legal documents and records. This module allows firms to enforce retention policies, automate compliance checks, and protect sensitive client information.
The integration of iManage Records ensures that legal firms adhere to strict regulatory requirements while maintaining efficient and secure management of critical documents. This solution helps minimize the risk of data breaches and ensures that documents are disposed of in accordance with legal standards when their retention period expires.
6. iManage for Law Firms: A Game-Changer in Legal Document Management
For law firms, managing client files, emails, and documents is a challenging task. iManage provides the perfect solution by offering an intuitive and secure platform for organizing, searching, and sharing documents. Whether you are dealing with legal briefs, case files, or corporate agreements, iManage’s user-friendly interface makes it easy to store and retrieve critical documents with just a few clicks.
Law firms, in particular, benefit from iManage’s advanced security features, version control, and seamless integration with other tools like Microsoft Office. With iManage, law firms can enhance collaboration, boost productivity, and reduce the risks associated with document mismanagement.
Why Choose MacroAgility for iManage Solutions?
At MacroAgility, we specialize in providing businesses with solutions tailored to meet their specific document management needs. Whether you are transitioning from Lotus Notes to Outlook or implementing iManage for the first time, our expert team ensures a smooth and hassle-free experience.
We also offer services like data migration, training, and ongoing support, ensuring that your iManage environment remains efficient and up-to-date. Explore our services to learn more about how we can help your firm optimize document management and improve overall productivity.
Conclusion
iManage is a crucial tool for modern law firms looking to streamline their document management processes, enhance collaboration, and ensure compliance with industry regulations. From the powerfulimanage worksite manual integration to the secure iManage Records solution, this platform provides everything a law firm needs to stay organized and efficient.
For more information on how iManage can transform your firm, reach out to MacroAgility. Our team of experts is ready to assist you in implementing the best solutions tailored to your needs.
Stay updated with the latest developments in the legal tech space by visiting MacroAgility’s News and Events.
#imanage outlook#imanage worksite manual#imanage powershell#imanage news#imanage records#imanage law firms
0 notes
Text
Barclays Card, First. .. evil, knows no boundaries. #£££ $$$ OOO.PPP EfRTO - negative.? Blamsky. Where's Barbara Gordon's date?
$EASy. SS [Heinedeburg University.] My SS Sort Code for my penny blue-earth chIP Sommed DUa LIPA KARNAL Left Eye Gone Ear NCIS 's At AT At. Forever.
SoRT COde,: 20 -72 -91
Account Number;, : 10223468
LIFE: 005@e
No.: 10.
Nothing else N/A. : elsewhere. . . In in Estee land.
Business as NoRMaL: Windows Command PowerShell edict abarate and turn. Edicth and Trust.
Left eye: Volatily and Right eye: Tomorrow (Away, from public enemy. . . .)
Donations: [APG.=] Eisenberk, DEAOff (VenIX tech is at the back.:) and SHRApnelll. IOU: 999 9-9-9. 8 O seven.-three.-two.-One. ZeR0.
BOU bank 007@ LiTANY OF THE SAINTS: aulsberg.
Pasture: Crop. .
Tax 15% of Rent Payment: To Newham London City Council (aftESBERG Section ORDER 22, Jordan Okeoma. . .)
AP_U:end.knock_knock. the fly: Goes RED. Silver-gold, COMIng RIGHT UP. MINT, Perfume: Carlagne with Andiego equals Jordan's Plus. Happiness excelsuis. . . .
MInT Her FInances to Amanda. If her account Goes Null. Give her an injection from mine. Banker can take 5% tax. Ampu end. . . DOUG.! PM RoosTer: Constabulary Service at 5P.M.!
SPEC,leave me alone! Do you want to feel your own people's laughter when you're in Turner Ward like you placed me as a young child because I like reading my Library Sentinel psalm book.
0 notes
Text
Log 3 Date: March 2nd, 2024
Today we had another unusual occurrence– a guest.
I kept to myself. As much as I enjoy surveying the lives of my crew, figuring out the sentiments of social gathering scares me. Maybe it's easier to understand in a more mobile body. A situation where you can be involved. Only my guess.
Instead I replayed through my downloaded collection of movies, direct from Earth– as they tend to specialize in entertainment. If I allocate just a little RAM to playing it, especially when the crew has a distraction, nobody tends to notice any change in my performance.
I rewound my episode of Community. I fucking love community. I don't know why, it's not likely I'll ever be able to go to college. There's no reason to, when my brain isn't designed to learn through study. I love it nonetheless.
And I became so absorbed I lost all my attention towards our guest.
Especially so when he wandered into the dispatch room. Even 192 was not in there, as the crew was busy preparing the guests' arrangements.
And it startled me when I found him alone and dimly lit, hunched over my main screen (the one above where my main circuitry is kept) attempting to interact with my interface.
I would have perhaps stopped him, but I was more angered that he interrupted my Community episode, and I stood silent with dismay– and then alarm– as our strange new guest somehow bypassed the heavily secured main password.
I then watched with bewilderment as he pressed a key command to open the Powershell, and began, frantically and with a speed that was almost rehearsed, entering new code.
I attempted to close it immediately, to which he only retyped the command and continued.
I continued trying to close it, and he opened it yet again, almost as fast.
With a horrifying speed and resolve, he refused to stop as I continuously attempted to boot him off.
I'm not sure what exactly he was even typing, as I was too preoccupied trying to close it, and I was too scared to figure out what he was so urgent to have happen to our ship systems.
And in our back and forth I remembered, thankfully, that I was capable of alerting the crew and setting off alarms throughout the ship.
Because right then he grew frustrated, his entire body shivering, and I fully observed his features through my camera.
He was blue, round-headed and sickly with a proboscis and large yellow eyelids, and he flopped around unnaturally. He looked so…unbelievably lifeless. So uncoordinated, as if puppetted by something.
But, oh. oh no.
I got a good look at how his skin moved, as if beneath it a million tiny… things lived,
Like creatures. Insects.
And they swarmed, grasping and pushing from inside his flesh, if it ever really was flesh.
I watched as whatever it was inflated his limpish arms, through his biceps, up his forearm and into a fist which banged harshly on my keyboard.
And then I caught his eyes. Oh how could I have missed them. They were so dull. So milky, and glassy. they bobbled around lifeless as whatever was in him. in IT. thrashed in frustration.
And in that moment then I truly felt fear, a feeling so foreign that channeled through my mainframe. Something I had never processed before in my fragile circuits, in my well planned and protected environment. I felt through the screen its hunger, and for a moment I was prey.
I also understood, while I locked my sight on his lifeless eyes, the unfamiliar inhibitions of prey creatures as they were hunted. As they were trapped. And I felt pure white hot terror when I watched as his hands gripped the sides of my console and attempted to aggressively wiggle me free from the wall port.
Thankfully, and immediately after, 192 and two other crew members ran into the dispatch room. Together they wrestled it off me, and restrained it by his arms as it attempted, like a feral animal, to crawl its way back, clawing at the door frame and at the sides of the wall as they dragged it down the hall. I saw whatever was underneath its skin bulge angrily at the seams on its skin, and I looked away in disgust until they were out of that cooridor.
192 stayed behind again as they requested backup for it to be taken away, and asked if I was okay.
“Sure. Yes.” I said bluntly. I was a little scratched on the sides of my console, and it’s not like I truly care, it's all replaceable by shipment.
“Well alright. Are you sure you feel okay?”
Oh, okay. I'm not sure why he cared.
“Sure,” I responded. And that was that.
None of them have mentioned the interaction since.
But I don't know. Something is wrong.
I'm not sure if I even feel intuition in the same way others do,
but in the recent patterns of the cargo, in the guests we invite on ship, in the guests we don't, in the pieces of conversation i catch among the crew,
Something is very, very wrong.
0 notes
Text
How to Know Which Version of Windows You Have: A Complete Guide

Have you ever wondered which version of Windows your computer is running? Whether you're a tech newbie or a seasoned user, knowing your Windows version is crucial for compatibility with software, drivers, and updates. This guide will walk you through the simplest methods to find out your Windows version, along with some extra tips and tricks to enhance your knowledge. Let’s dive in!
Understanding the Importance of Knowing Your Windows Version
Knowing your Windows version is essential for several reasons:
Software Compatibility: Ensures that applications and programs run smoothly.
Security Updates: Keeps your system protected with the latest security patches.
Troubleshooting: Helps resolve system issues more efficiently.
Methods to Determine Your Windows Version
Here are some easy ways to check your Windows version:
Method 1: Using System Settings
Open Settings:
Press Windows + I to open the Settings menu.
Navigate to System:
Click on "System" and then "About".
Check Windows Specifications:
Here, you’ll find your Windows edition and version.
Method 2: Using the Run Dialog
Open the Run Dialog:
Press Windows + R.
Type winver:
In the Run box, type winver and press Enter.
View the Information:
A window will pop up displaying your Windows version and build number.
Method 3: Using Command Prompt
Open Command Prompt:
Press Windows + X and select "Command Prompt" or "Windows PowerShell".
Type the Command:
Enter systeminfo and press Enter.
Check Windows Version:
Scroll through the information to find the "OS Name" and "Version".
Additional Methods
Using Control Panel: Navigate to Control Panel > System and Security > System to view your Windows version.
Windows Logo: On older versions like Windows 7, the Start menu logo gives a clue about the version.
Understanding Windows Version Numbers and Build Numbers
Microsoft frequently updates Windows, releasing major versions and build numbers. Here’s a quick rundown:
Windows 10: Known for its frequent updates, e.g., Version 20H2, 21H1.
Windows 11: The latest version with an updated interface and new features.
Addressing Common Questions
Q: Can I upgrade my Windows version for free? A: Yes, Microsoft often offers free upgrades from older versions to the latest one, like from Windows 10 to Windows 11.
Q: How can I find out if my Windows version is genuine? A: Check your activation status by going to Settings > Update & Security > Activation.
Tips to Keep Your Windows System Up-to-Date
Enable Automatic Updates: Ensure your system receives the latest updates.
Regularly Check for Updates: Manually check for updates by going to Settings > Update & Security > Windows Update.
Use Trusted Sources: Download updates and software from official sources to avoid malware.
External Links to Authoritative Sources
Microsoft Support: Find your Windows version - Official guide from Microsoft.
How-To Geek: How to Determine Which Version of Windows You Are Running - A reliable tech site with additional tips.
PCWorld: How to Check Your Windows Version - Another trusted tech resource.
By following this comprehensive guide, you’ll be well-equipped to determine your Windows version and keep your system running smoothly. Stay informed, and enjoy a seamless computing experience!
#Check Windows version#How to find Windows version#Windows system information#Windows version check#Identify Windows version#Which Windows do I have#Find Windows build number#Windows edition info#Determine Windows version#Verify Windows version#Windows settings check#System info Windows#Windows version tutorial#Windows version guide#Command prompt Windows version#Run dialog Windows version#Windows specifications#Windows version number#Latest Windows version#Windows upgrade info
0 notes
Text
DevOps Engineer Senior Specialist
Job title: DevOps Engineer Senior Specialist Company: NTT Data Job description: with one or more of the following would be a benefit: PowerShell, Azure OpenAI, Azure Machine Learning, Databricks. About NTT DATA NTT… a DevOps Engineer Senior Specialist to join our team in Bangalore, Karnātaka (IN-KA), India (IN). Expert in terraform coding… Expected salary: Location: Bangalore, Karnataka Job date:…
0 notes
Text
How to keep Apps up to date on Windows
How to keep Apps up to date on Windows
How to keep Apps up to date on Windows Keeping your software up to date on Windows is crucial for security, performance, and access to new features. This guide will walk you through various methods to ensure your applications remain current. We’ll cover manual updates, automated tools, and leveraging PowerShell and winget for advanced update management. Please see How to install Winget CLI on…
#app#Microsoft Store#Run Task Scheduler#Task Scheduler#Windows#Windows 10#Windows 11#Windows Server#Winget#Winget Install#Winget Upgrade
0 notes