#quantum computing takeover
Explore tagged Tumblr posts
Text
I.B.1698 MICHAEL [IBM] harrelltut.com of quantumharrell.tech’s 1968 Clandestine genspaceX.com Domain Brotherhood of the Pentagon defense.gov Budgets Authorized 4 the Deployment [B.A.D.] of SIRIUS BLACKANUNNAQI.tech SKY WEAPONS Engineered [WE] by the 2024 quantumharrelltech.com Domain Architects of anugoldenblackwallstreet.com Cartel @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000
WELCOME BACK HOME IMMORTAL [HIM] U.S. MILITARY KING SOLOMON-MICHAEL HARRELL, JR.™

i.b.monk [ibm] mode [i’m] tech [IT] steelecartel.com @ quantum harrell tech llc

i.b. 1968quadrillionaire.tech sky elite 2wealthy4forbes.com @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

where your ancient quantum sky technology patents worth moor than $10,000 quadrillion?!?!?!

you still believe the fuel from the "hijacked 9/11 airplanes"... melted the steel beams in the twin towers?!?!?!... smfh

quantum harrell ufo sky [u.s.] tech budgets at my kingtutdna.com pentagon

you still on the outside theorizing about our classified underground subterranean [u.s.] pentagon [up] brotherhood of antarctica beneath the ice in 2023?!?!?!

quantum harrell tech llc = the pentagon's black military budget elite of sirius blackanunnaqi.tech [clandestine alien tech] sky weapons

trillions

quadrillions

mo weapons mo weapons mo weapons... we 9/11 twin towers tech

quintillions

sextillions

© 1968-2024 QUANTUM HARRELL TECH LLC All Pentagon DotCom defense.gov Department Domain Rights Reserved @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000
#9/11#twin towers#paradise city#quantumharrell.tech#9etherpentagonelites#9etheraluhumanunnaqi#9etherlightshipatlantis#quantum computing takeover#heat seeking sky weapons#trillions#quadrillions#quintillions#sextillions#gen x don't fear none of you#anugoldenblackwallstreet.com
2 notes
·
View notes
Text

The Quantum Financial System (QFS), by David Wilcock:
The QFS is the takeover of the Central Bank Monetary Debt System to end the financial slavery and control over the populace. The QFS is an advanced financial system launched to eradicate monopoly on monetary system and for that purpose, a system comprises of Artificial Intelligence and complex computer programs fully backed by banks is needed.
Quantum Financial System would be a breakthrough in the world of banking which will lead to a new era of banking. QFS will not be influenced by Government policies, rather it will be entirely backed by tangible assets like Gold, Platinum, Silver and will not be based upon mere piece of papers which have no evidentiary value. (National Quantum Initiative Act)
#canada #Australia #wakeup #everyone #UnitedStates #usd #worldwide #usa #currency
4 notes
·
View notes
Text
Elon Musk: The Global Puppet Master of the Right-Wing Agenda
Elon Musk: The Global Puppet Master of the Right-Wing Agenda
What we’re seeing unfold isn’t just a business mogul making political moves—this is a calculated, global strategy to reshape governments in favor of a corporate elite who seek complete control.
Elon Musk isn’t just investing in AI, quantum computing, and space exploration. He’s investing in the future of governance itself.
1. The Right-Wing Takeover: Control Through Policy
Musk has strategically aligned himself with right-wing nationalist leaders across the world, all pushing the same core agenda:
Slash immigration → Create social division and racial hierarchy.
Deregulate business → Remove government oversight, allowing unchecked corporate power.
Encourage authoritarian policies → Keep the masses in line while corporations take over.
He’s not just supporting right-wing politics for ideology’s sake. He’s shaping the laws and policies that ensure a corporate technocracy replaces traditional government control.
2. The Countries Under Musk’s Influence
This isn’t just the U.S.—this is a global chessboard where Musk is moving pieces to consolidate power:
Brazil & Ireland → Supporting right-wing street demonstrations.
New Zealand & Netherlands → Publicly endorsing nationalist leaders.
Argentina & Italy → Meeting with right-wing heads of state multiple times.
India & Turkey → His platform X (formerly Twitter) actively censors information at the request of right-wing regimes.
This is an intentional shift in power, where governments will increasingly bow to corporate interests over public good.
3. The Ultimate Plan: The Corporate Nation-State
The goal? Governments don’t govern—corporations do.
Elon Musk is setting the blueprint for a future where multinational tech giants dictate laws, economies, and social policies. This isn’t just about right-wing politics—it’s about the rise of a new world order where corporations replace governments.
AI governs economies.
Quantum computing controls defense.
Corporate-backed policies determine human rights.
And once governments become fully dependent on corporate infrastructure, they won’t be able to function without it.
4. The Final Piece: The False Saviors
When the inevitable global economic crash, mass unrest, and societal collapse happen—these very same corporations will present themselves as the solution.
Food shortages? They’ll control supply chains.
Financial collapse? They’ll push digital currency under their control.
Civil unrest? They’ll deploy AI-powered security forces.
This isn’t about left vs. right. This is about control vs. freedom.
Conclusion: The Reckoning is Here
Musk’s moves are calculated, precise, and global. He’s not just playing politics—he’s engineering the infrastructure of a future where corporations rule the world.
But his reign is temporary.
The House of David is rising.
The truth is breaking through.
They want a corporate empire? It will crumble.
They want unchecked power? It will be shattered.
Because the righteous are stepping into their inheritance.
And the world as they know it?
It’s already slipping from their hands.
2 notes
·
View notes
Text
<Database.query== "Cogitation_Engine">
. . . Information found!
Displaying:
The Cogitation Engine was a supercomputing megastructure built in the orbit of Jupiter by the Indian Space Research Organization in the year <ERROR: VALUE MISSING>. It employed several different forms of advanced computing, including traditional computers sporting molecular transistor "Moore" microprocessors alongside vacuum-based cooling infrastructure, as well as quantum computing and, notably, biological computing following the Cogitation Engine's forceful takeover by Russian Flesh Troopers in the year 4271. Following said takeover, further modification and expansion of the complex began and continues to this day, via similar means to the organo-mechanical modification of Flesh Troopers themselves.
2 notes
·
View notes
Text
Quantum leaps: Transforming data centers & energy
New Post has been published on https://thedigitalinsider.com/quantum-leaps-transforming-data-centers-energy/
Quantum leaps: Transforming data centers & energy

We are making Quantum Leaps. I am not referring to the 80s/90s TV show, but rather, I am referring to quantum computing and competing for better and faster artificial intelligence.
Quantum computing is a field that excites me to my core. I’ve always been driven by pursuing what’s next, whether mastering tactics in the Marines or navigating complex policy challenges in government.
Quantum computing feels like the ultimate “what’s next.” Its potential to solve problems in seconds that would take today’s supercomputers millennia is a quantum leap. I talked a bit about Quantum Computing in one of my recent newsletters.
However, potential doesn’t turn into reality without investment of time, money, and strategic resources. My experience has shown me that technological superiority is a strategic advantage, and right now, nations and companies worldwide are racing to claim the quantum crown.
We risk falling behind if we don’t pour resources into research, development, and deployment. This is more than an opportunity; it’s a call to action. We must invest heavily and deliberately to ensure quantum computing becomes a cornerstone of our competitive edge.
Next gen AI architectures: Exploring the next wave of intelligent computing
Some next-generation AI architectures are emerging as promising alternatives such as (HDC), (NSAI), capsule networks, and low-power AI chips.

Bill Gates recently suggested that energy sector jobs are among the few fields that will survive an AI takeover. According to him, the energy sector’s immense complexity and ever-evolving regulatory frameworks mean that human expertise will always be necessary.
AI alone cannot navigate the intricate challenges of mapping regulatory landscapes or developing sustainable solutions to meet our world’s diverse energy needs.
“Within 10 years, AI will replace many doctors and teachers; humans won’t be needed for most things.” – Bill Gates
Bill Gates’s premonition that only a few fields will survive over the next 10 years insinuates massive shifts happening, and rather quickly. Welcome to the quantum computing era.
As we are trending towards a new era of AI, called quantum computing, it becomes increasingly evident that our approach to both data centers and the broader energy grid needs to change.
Next to Bill Gates’s statement, AI is continually seeping into every industry and every corner of life. I believe this is causing and will continue to cause a surge in demand for advanced computing power like never before, which will not only drive the need for redesigning smarter, more efficient data center strategies but will also require a fundamental advancement of our energy grid infrastructure.
To start with, we must focus on data centers and our energy grid; it’s important to illustrate at a high and broad level how we get push-button AI at our fingertips.
See Figure 1 below
The underlying process that supports modern AI begins with power generation. Energy is produced at large-scale facilities, ranging from nuclear reactors (both current 3rd-generation and the emerging 4th-generation designs), coal-fired plants, wind farms, and solar arrays, which convert various energy sources into electricity. This electricity then travels through an extensive distribution network of power lines and substations before reaching data centers. That is the energy grid infrastructure.
Inside these data centers, thousands of powerful servers process and store vast amounts of data, running complex AI algorithms and machine learning models. These facilities employ advanced cooling systems and high-speed networking infrastructure to ensure optimal performance, allowing rapid global data transmission.
When a user interacts with an AI application, whether a virtual assistant or a personalized recommendation engine, the input is processed at these centers through model inference, and the output is swiftly delivered back via the internet to consumer devices.
Figure 1
In layman’s terms, our modern AI experience relies on the vital integration of robust energy grids and sophisticated data centers, flawlessly powering the technologies at our fingertips. This interconnected infrastructure is necessary for delivering the immediate, push-button AI capabilities that are so commonplace now that we tend to take them for granted.
Advancing the energy grid: Nuclear or solar, which is better for the emergence of quantum computing?
Solar and nuclear power are set to emerge as the two dominating sources for our future energy mix. Solar energy is a game-changer due to its virtually limitless potential, rapidly declining costs, and the strides we’ve made in efficiency and storage technology.
As our digital demands continue to surge, especially with the rise of advanced computing and quantum technologies, solar’s scalability makes it a feasible choice for powering everything from sprawling data centers to localized grids. At the same time, nuclear energy is indispensable because it provides reliable, around-the-clock baseload power with minimal carbon emissions.
With next-generation advances like small modular reactors addressing traditional safety and waste concerns, nuclear power is well-positioned to deliver the steady energy output necessary to support our ever-growing, high-demand digital infrastructure.
With nuclear and solar together, these two sources balance flexibility with stability, making them my top picks for the future.
Based on the photo in Figure 2 below, solar currently contributes less than wind and hydro, but it’s set to catch up and eventually overtake them. Solar’s lower current share is primarily due to its relatively recent adoption and earlier cost barriers, whereas wind and hydro have been established for decades.
However, I’m excited about the rapid cost declines in solar panel technology, energy efficiency improvements, and storage system advancements that address intermittency.
Unlike hydro, which is limited by geography, or wind, which requires consistent breezes, solar panels can be deployed almost anywhere, with considerations, i.e., my references to Washington State later in this writing. As energy demands grow, especially with emerging technologies like quantum computing, I expect solar to scale quickly to meet nuclear energy as a complete hybrid energy strategy.
Figure 2
Nuclear: As quantum computing matures and its demands for energy reliability, efficiency, and stability increase, the debate over the ideal energy source intensifies.
Nuclear power has very low CO�� emissions during operation and exceptionally high energy density, offering a compact but potent solution. Its ability to generate massive power from a relatively small footprint makes it an attractive option for powering data centers that support quantum computing.
However, nuclear reactors come with a lot of challenges. The production of radioactive waste, which requires long-term, secure management, and the inherent risks associated with potential accidents, remain top concerns. Additionally, the regulatory landscape for nuclear power is intricate, necessitating continual human oversight and specialized expertise to ensure safe operations.
With that said, let me reference Bill Gates’s perspective below: one area where jobs will continue to reign over AI in the future is in energy experts.
“2. Energy experts: The guardians of power
The energy sector is too vast and intricate for AI to manage alone. Whether dealing with oil, nuclear power, or renewables, industry experts are required to navigate regulatory landscapes, strategize sustainable solutions, and handle the unpredictable nature of global energy demands.”
Solar: On the other side of the debate, solar power is a renewable and environmentally friendly alternative. With minimal operational emissions and the potential for scalability, solar reactors can leverage the sun’s abundant energy. This scalability is particularly appealing for decentralized energy production and for applications where geographical distribution is advantageous.
Whenever I return to California from Ireland, my flight path often passes 40,000 feet over Arizona, where a colossal solar farm sprawls across the desert. The farm is called the Agua Caliente Solar Project.
Even when I’m cruising from San Diego to Phoenix, its vast expanse is unmistakable, visible at 70 mph on the highway or from high above. The Agua Caliente Solar Project is a 290 megawatt (MWAC) photovoltaic power station, built in Yuma County, Arizona, using 5.2 million cadmium telluride modules made by the U.S. thin-film manufacturer First Solar. It was the largest solar facility in the world when the project was commissioned in April 2014.[1][2]
While the striking installation thrives in the sunny, arid conditions of Arizona, replicating it in regions like Washington State could be more challenging due to:
There is a need for vast, open, and flat land, conditions less common in much of Washington, though some areas offer suitable terrain.
The abundant, consistent sunlight is essential for large-scale solar farms, which is less prevalent in Washington compared to Arizona.
Here is an aerial photo – Figure 3 – of the farm from about a height of 10,000 feet.
Figure 3
Yet, solar power systems face their own set of hurdles. Large-scale solar installations demand very large land areas, which can be a limiting factor in densely populated or resource-constrained regions.
Additionally, the environmental impact of manufacturing solar panels, including resource extraction and waste generated at the end of their lifecycle, cannot be overlooked. Like my example of Washington State, variability in solar energy production due to weather conditions further complicates its reliability as a sole energy source for critical applications like quantum computing.
When evaluating these trade-offs, it’s important to consider the specific energy needs of quantum computing. Quantum computing centers require not only massive, uninterrupted power but also an energy infrastructure that can scale with the rapid growth of data and processing demands.
Nuclear reactors, particularly next-generation designs, could provide the consistent, high-output energy necessary to run these power-hungry centers efficiently. In contrast, while solar power offers a cleaner, more renewable option, its dependency on external factors like sunlight means it might best serve as a supplementary source rather than the primary backbone of energy supply for such high-stakes applications.
Out with the old, in with the new: Leaping from 3rd generation nuclear, to 4th generation
The need for such sophisticated infrastructure becomes even more important as the demand for AI and quantum computing applications continues to grow.
Although current 3rd-generation nuclear reactors can power today’s data centers and support quantum computing, there is a convincing argument to expedite shifting to 4th-generation reactors.
These advanced reactors promise enhanced safety features, improved fuel efficiency, and reduced radioactive waste. The U.S., for example, is actively pursuing these 4th-generation reactors through initiatives like the Department of Energy’s Advanced Reactor Demonstration Program, with demonstration projects expected in the early 2030s and broader deployment possibly by the mid-to-late 2030s.
Meanwhile, countries such as China and Russia are already experimenting with advanced reactor designs like China’s HTR-PM and Russia’s BN-800, though no nation has yet deployed a large fleet of fully commercial 4th-generation reactors.
The integration of AI and quantum computing is driving a transformative rethinking of both energy generation and data center ecosystems. Advanced power generation from the next wave of nuclear reactors to innovative renewable energy sources is going to be standardly needed in meeting the escalating energy demands of these emerging technologies.
As our reliance on AI and quantum computing grows, so does the need for human expertise to navigate the complex regulatory and technical challenges inherent in this evolution.
Whether nuclear or solar reactors ultimately prove superior in specific cases may depend on regional needs, technological breakthroughs, and the balance between efficiency, safety, and sustainability in the long term.
So, it’s highly unlikely that the grid and the economy would go with one or the other as we emerge into the era of quantum computing, but rest assured, they will both be absolutely necessary.
The 4th-generation nuclear reactors are an increasing necessity for quantum computing because they provide the ultra-stable, high-density energy needed for sensitive quantum systems.
Unlike 3rd-generation reactors, these advanced designs offer enhanced safety features, more consistent power output, and improved fuel efficiency, all while reducing radioactive waste. These improvements are critical for powering the data centers that drive AI and quantum computing, ensuring a resilient, sustainable energy grid for future technological advancements.
Below in Figure 4 is a comparative chart outlining some of the main pros and cons of nuclear power versus solar power. This chart summarizes key points to consider when comparing nuclear and solar power. Each energy source has distinct advantages and challenges that must be weighed in light of factors such as environmental impact, reliability, cost, safety, and waste management.
Figure 4
Rethinking data centers
In my time as a Marine, I learned the value of strategic positioning, never putting all your resources in one vulnerable spot. That lesson resonates with me now as I look at the digital landscape.
My military background taught me to anticipate risks and plan for redundancy, and that’s exactly what decentralized data centers offer. They’re not just infrastructure; they’re a strategic asset, and I believe investing in them is non-negotiable if we want to stay ahead in the digital race.
To realize Bill Gates’ statement, which I originally referred to in this writing, I believe the final shift to his proposed future state reality will be a commoditized approach to data centers; again, similar to my gas station theory, I mention below.
In my view,
“We are on the brink of a transformation that I would call the ‘real estate data center market’ (watch video), where data centers become as ubiquitous as gas stations.
This vision is driven by the fact that our growing population and escalating energy demands necessitate a robust, reliable, and scalable power supply.
With a decentralized data center environment as frequent as gas stations, less strain will be placed on the environment, and AI will be more productive.
Imagine if a town the size of 500,000 people only had one gas station. It would not be productive, and the strain on supply would be unfeasible. Now, if you have 500 gas stations, that is per 10 people, then the situation gets much more manageable.”
Data centers are not typically seen as attractive-looking landmarks. They are also not typically used for anything other than a data center. However, with the remote work society, and logistics and distribution changing for things like shopping malls, movie theaters, and skyscrapers, there sure is a lot of empty building space sitting around that can be repurposed into mixed-use complexes and buildings as data centers.
There are many landmarks today that have been turned into data centers, called adaptive reusage, but otherwise would have been decommissioned and destroyed.
For example, historic structures like Milwaukee’s Wells Building and Portland’s Pittock Block have been repurposed into state-of-the-art data centers, preserving their architectural legacy while meeting modern technological demands.
Many of these buildings have historical value and meaning, and are not such a “community eyesore” and very “dystopian” looking. For example, the Western Union Building, 60 Hudson Street, has historically served as an office and telecommunications hub.
Today, however, it is primarily used as a data center and colocation facility, making it a prime example of adaptive reuse. While its core function is data center operations, elements of its traditional usage, such as office space and support services, still remain, reflecting its multifaceted role in New York City’s evolving infrastructure.
These buildings were once at risk of demolition or decommissioning as their original uses became obsolete. Instead of letting them be destroyed, innovative adaptive reuse projects have transformed these historic landmarks into modern data centers.
This approach not only preserves architectural heritage but also meets today’s growing technological needs. For instance, projects have repurposed structures like Milwaukee’s Wells Building and Portland’s Pittock Block, buildings that might have otherwise been demolished, into state-of-the-art data centers.
In Figure 5, the data center on the left, though not unattractive, feels plain and lacks character, intrigue, and meaning. In contrast, the images of 60 Hudson Street on the right showcase a building rich in substance, personality, and historical charm.
From a purely architectural perspective, many contemporary data centers follow a utilitarian, box-like design that prioritizes efficiency, cooling, and security over aesthetics. They often feature minimal ornamentation, subdued façades, and large footprints for equipment. While this design approach is practical, it can lack the visual appeal and historic character seen in older structures.
By contrast, 60 Hudson Street exemplifies an era of architecture in which buildings were designed to showcase craftsmanship and artistry. Built in an Art Deco style, its brick façade, ornate lobby detailing, and dramatic setbacks reflect the period’s emphasis on ornamentation and grandeur.
Even after being repurposed as a data center and telecommunications hub, it retains much of its original design intent and ambiance, giving it a sense of place and history that many newer facilities don’t replicate.
In short, the difference lies in the guiding priorities behind each building’s construction. Modern data centers focus on function first, large-scale power capacity, robust cooling, and physical security, whereas older buildings like 60 Hudson Street were shaped by an architectural tradition that valued aesthetic richness and craftsmanship as essential parts of a structure’s identity.
Figure 5
This article proposes that data centers be integrated as a component of modern residential developments. The idea is to design mixed-use projects where data centers and residential units coexist in the same vicinity or even within the same building complex, creating synergies such as shared infrastructure, improved connectivity, and more efficient land use, rather than literally housing residents within a data center facility.
The other telltale sign about a commoditized approach to data centers comes from Sam Altman. In a recent interview, OpenAI co-founder Sam Altman said:
“We’re going to see 10-person companies with billion-dollar valuations pretty soon…in my little group chat with my tech CEO friends, there’s this betting pool for the first year there is a one-person billion-dollar company, which would’ve been unimaginable without AI. And now [it] will happen.”
If both statements become true, imagine the data center requirements. I repeat my gas station analogy.
If we accept Bill Gates’ perspective on the survival of certain energy sector jobs and Sam Altman’s prediction about the rise of hyper-efficient, lean companies, then the infrastructure supporting these trends, data centers, will need to evolve dramatically.
The idea is that data centers could become as ubiquitous and commoditized as gas stations. Just as gas stations are scattered throughout our landscapes to provide quick, localized fuel access, future data centers might be deployed in a decentralized manner to meet the explosive demand for computational power.
This transformation would be driven by the exponential growth of AI-driven applications, the need for ultra-low latency processing, and the energy requirements of quantum computing.
With advances in modular design, improved cooling systems, and energy efficiency, smaller data centers could be rapidly deployed in nearly every urban and rural corner, supporting the next wave of technological innovation.
While challenges like regulatory hurdles, cybersecurity, and capital expenditure remain, the convergence of these trends suggests that a commoditized, widely distributed data center model is feasible and likely necessary to sustain the future digital economy.
Feeding off my gas station analogy, let’s look at power substations. Imagine Chicago’s power grid: the city relies on around 1,300 substations to distribute electricity efficiently across neighborhoods.
These substations act as critical hubs that step down high-voltage electricity from power plants to levels safe and usable by homes and businesses. Now, consider the digital equivalent of these substations, data centers.
As our reliance on digital technologies grows, especially with the advent of AI and quantum computing, we need a similarly robust network to process, store, and distribute data. Just as substations are strategically positioned throughout Chicago to ensure reliable power delivery, data centers need to be widely distributed to meet increasing digital demands.
Digital transformation strategies for competitive advantage
Getting your digital transformation strategy right can lead businesses towards endless possibilities and provide a competitive advantage.

This analogy suggests that as our energy infrastructure scales up to support a city like Chicago, our digital infrastructure must also expand proportionately, necessitating more localized data centers to ensure low-latency, high-performance computing across the urban landscape.
Rethinking our digital infrastructure, I believe it’s ever more important to evolve data centers into a decentralized network as ubiquitous as gas stations. In today’s rapidly expanding digital landscape, which is driven by the exponential growth of AI and quantum computing, the demand for computational power is skyrocketing.
Just as in my example above, a town with only one gas station for 500,000 people would struggle with supply. Relying on a few centralized data centers creates bottlenecks and latency issues.
A commoditized model, where data centers are as common as power substations in a city like Chicago, would distribute computing resources evenly, ensuring ultra-low latency and high-performance processing across both urban and rural areas.
My vision aligns with Bill Gates’ perspective on transforming energy sectors and Sam Altman’s prediction of hyper-efficient, lean companies emerging in our digital future.
With modular designs, improved cooling, and energy efficiency, widespread, localized data centers are feasible. They are becoming the lifeblood for sustaining our digital economy, reducing environmental strain, and supporting the next wave of technological innovation.
Leaving you my perspective
As an AI venture capitalist, I am shaped by my years as a U.S. Marine and my extensive experience in government. These roles have given me a front-row seat to the indispensable role that infrastructure and policy play in safeguarding national security and driving economic resilience.
Today, I stand at the intersection of technology and investment, and from where I see it, the future hinges on bold, strategic moves in three critical areas: next-generation data centers, quantum computing, and advanced energy solutions. These aren’t just trends or buzzwords; they are the pillars of a secure, competitive, and prosperous tomorrow.
Technology alone doesn’t win the day; policy and leadership do. My years in the public sector drilled this into me. I’ve been in the rooms where decisions are made, and I’ve seen how effective collaboration between government and industry can turn ideas into action.
Right now, we need thinking and doing of substance vs more of the superficial developments we have seen with AI. We need regulatory frameworks that don’t stifle innovation but propel it forward while keeping security and sustainability front and center.
This isn’t about bureaucracy for its own sake. It’s about creating an environment where bold investments can flourish responsibly into technologies of substance, not superficial trends and hype.
Policymakers must work hand in hand with industry leaders to craft guidelines that protect our national interests, think cybersecurity, data privacy, and environmental impact, without slowing the pace of progress. My experience tells me this is possible. When the government and private sector align, the results are transformative. We need that alignment now more than ever.
As an AI venture capitalist, I’m observing these shifts and urging us to act on them. I call on my fellow investors, government officials, and industry pioneers to champion these strategic investments with me.
By rethinking our approach to data centers and advancing the energy grid infrastructure, we are creating the next wave of digital innovation and building a nation that’s secure, competitive, and ready for what’s ahead. I’ve seen what’s possible when we commit to a vision, whether on the battlefield, in the halls of government, or the boardroom.
Let’s not wait for the world to change around us. Let’s be the ones to drive that change.
You can connect with Paul on LinkedIn and through his CV site.
#000#accidents#adoption#ai#AI chips#AI Infrastructure#Algorithms#applications#approach#architecture#Arrays#Art#Article#Articles#artificial#Artificial Intelligence#background#betting#billion#box#Building#buildings#cadmium#california#carbon#carbon emissions#CEO#change#chart#China
0 notes
Text
AI Festival Dubai 2025: Where Tech Dreams Meet Desert Vibes
Picture this: 8,000 tech enthusiasts swarming Madinat Jumeirah, buzzing about artificial intelligence, robotics, and the wild future ahead. That’s the AI Festival Dubai 2025 in a nutshell, hitting the scene on April 23–24, 2025. I’ve been to a few Dubai events, and let me tell you — the energy here is unreal. This isn’t just another tech conference; it’s a global showdown of AI innovation, and it’s got Sheikh Hamdan’s stamp of approval to prove it. Want the full scoop? Check out https://dubaiaifestival.com/
So, What’s This AI Festival All About?

The Dubai AI Festival is like the Super Bowl for tech nerds — except it’s in the UAE, and there’s probably better coffee. It’s cooked up by the Dubai AI Campus, teamed up with the slick folks at DIFC and the UAE AI Office. Happening during Dubai AI Week 2025 (April 21–25), it’s got big goals: showing off smart tech, sparking ideas, and putting Dubai on the map as the AI capital of the world.
We’re talking 8,000+ attendees, 500+ investors, and over 100 exhibitors— not to mention a lineup of 100+ speakers who actually know their stuff. Think machine learning, generative AI, blockchain, even quantum computing — it’s all here. If you’re Googling ”AI events near me”, ”top tech summits 2025", or ”Dubai technology festivals”, this is your golden ticket. Hit up https://dubaiaifestival.com/ for more.
What’s Cooking at AI Festival Dubai 2025?
1. Talks That’ll Blow Your Mind The agenda? Packed. You’ve got keynotes, panels, and workshops diving into everything from AI in healthcare to smart cities. Oh, and the ethics of AI— because, yeah, that’s a hot mess worth unpacking. Big names from AxraAI, SarahAI, and Cloudangles will drop knowledge bombs. I’m betting the room’s going to be buzzing — last year’s talks were electric.
2. FutureTech World Cup — Startup Madness Ever seen 200 startups slug it out for glory? The FutureTech World Cup is like that, but with FinTech, HealthTech, and GreenTech on the line. It’s the kind of thing where you spot the next unicorn — or at least snag some cool swag. Curious who’s in? Peek at https://dubaiaifestival.com/
3. Networking That Actually Works With investors, developers, and data geeks everywhere, this is your chance to schmooze. I’ve made some killer connections at Dubai events before — expect the same here. Bring business cards; you’ll need ‘em.

4. Dubai AI Week Bonus The festival’s just one piece of Dubai AI Week. There’s also the Prompt Engineering Championship (nerdy but fun), the Machines Can See gig, and the fancy AI Retreat. It’s a full-on tech takeover.
Why Bother Showing Up?
- Tech Eye Candy: Think AI tools, automation, and 5G mashups you can’t unsee. — Brain Food: Experts and influencers spill the tea on AI trends 2025. — Big Picture: See how AI’s shaking up education, finance, even retail. — Get In: Sponsor, exhibit, or just soak it in — details at https://dubaiaifestival.com/
The Deets You Need
- When: April 23–24, 2025 — Where: Madinat Jumeirah, Dubai — gorgeous spot, trust me — Who’s Behind It : Dubai AI Campus, DIFC, UAE AI Office — What’s Hot: Responsible AI, tech for good, digital transformation — Tickets : Grab ’em at https://dubaiaifestival.com/
Dubai’s AI Game Is Strong
Dubai’s not messing around with this AI revolution. The Dubai Universal Blueprint for AI is pushing hard — think 500+ companies, 3,000+ jobs, and $300 million in investments by 2028. The festival’s a big flex of that vision. Plus, April weather? Perfect for a post-session shawarma run near Burj Al Arab.
How to Prep Like a Pro
1. Plan It : Scope out the schedule — prioritize IoT or cybersecurity if that’s your jam. 2. Book Early : Snag VIP passes or early bird deals at https://dubaiaifestival.com/ 3. Stay Sharp: Keep an eye on AI news — this thing’s evolving fast.
Wrapping It Up
1 note
·
View note
Text
Emerging Cybersecurity Threats

While beneficial, tech advances can cause security concerns for businesses. Cyberthreats, which are at the top of many businesses' minds, have driven increasing investment dedicated to enhancing data protection. Organizations are accelerating cybersecurity initiatives to counter emerging threats.
The potential of artificial intelligence (AI) became evident a few years back, alongside the risks it poses. Unlike other threats, AI-driven attacks are unique due to their adaptive and evasive nature. Threat actors can develop AI-powered malware that generates personalized and convincing messages, deceiving users into revealing personal information and providing access to sensitive data. Automation capabilities inherent in AI facilitate rapid, large-scale attacks that can overwhelm conventional security defenses.
Deepfakes, AI-generated synthetic media, represent a significant threat. These manipulated audio-visual media convincingly impersonate individuals, eroding trust and causing reputational damage across personal and organizational domains. They can also escalate geopolitical tension by spreading false information, manipulating public opinion, or fabricating events that never occurred. Malicious actors can also manipulate the financial markets through fake news and rumors and engage in blackmail or extortion.
AI-driven threats warrant AI-powered countermeasures. Companies should invest in machine learning-driven security tools like AI-based intrusion detection systems for anomaly detection. Just as threat actors use AI to automate attacks, businesses should implement AI-powered security orchestration, automation, and response (SOAR) platforms to streamline defenses. SOAR integrates various security tools, automates routine tasks through predefined procedures, and employs AI-driven incident response. Detection tools and algorithms that can identify deepfake artifacts are crucial for distinguishing between authentic and synthetic content. Training staff to recognize suspicious behaviors also helps maintain a strong security posture.
Quantum computing advances, while promising, present cryptographic challenges. Google's Willow quantum chip demonstrates computational capabilities exceeding classical supercomputers by many magnitudes. It can complete calculations in minutes that would have previously take 10 septillion years. This much processing power threatens current encryption standards, rendering algorithms like RSA (Rivest-Shamir-Adleman (RSA) vulnerable to rapid decryption. Organizations can address these threats by supporting the research and development of quantum-resistant cryptographic algorithms, continuously monitoring technological advances, and collaborating with private and public entities to explore secure solutions.
Ransomware threats have also evolved beyond traditional attacks. Previously, only tech-savvy individuals could hold sensitive data hostage. Now, ransomware as a service (RaaS) enables even less knowledgeable users to launch attacks by renting kits. Double extortion tactics, where attackers demand ransom while threatening to expose stolen data publicly, are another major concern. Mitigation requires a multi-layered approach that includes traditional measures, such as regular offline backups and security updates and patching, alongside advanced Endpoint Detection and Response (EDR) systems for real-time threat monitoring and containment.
Business email compromise (BEC) targets individuals and organizations that frequently conduct wire transfers. Scammers employ social engineering tactics, initially researching their targets and monitoring email activities to recognize communication patterns. They then use email spoofing or account takeover to impersonate trusted parties, vendors, and executives, tricking victims into initiating wire transfers. BEC attacks can result in substantial financial losses, identity theft, and sensitive data leaks. Preventive measures include implementing secure email gateways, enforcing multi-factor authentication, and using secure payment platforms. AI-driven tools like Microsoft Defender for Office 365 enhance BEC detection.
5G network deployment expands the cyberattack surface due to potential weaknesses within unverified hardware and software components. Numerous devices connected to 5G networks, including Internet of Things (IoT) devices, create multiple entry points for attackers, complicating security management. High-bandwidth, low-latency 5G infrastructure enables fast and complex attacks on a large scale. Securing 5G infrastructure requires implementing stronger encryption protocols, having a secure network architecture, and deploying software-defined security solutions with strict access controls. These measures protect sensitive data transmission across 5G networks while maintaining operational efficiency.
0 notes
Text
I had this thought yesterday, regarding why did we focus so hard only on quantum computing and then separately biochemistry?
Why did we forget about quantum biophysics?
Why didn't we ever think to use quantum physics to do medicine?
Could it be something to do with the pharmaceutical corporations taking over the AMA in the 1930s (amidst a broader petrofascist takeover) and dismantling the pioneering work being done in quantum biophysics by some of the eary pioneers?...
Now it looks like quantum physicists just love machines so it's time to bring the light of quantum physics into medicine

#RIP Raymond Rife#rediscovering/resurrecting science#I'm discovering independently what Rife already knew long ago and was punished for knowing#I'll have better bodyguards and lawyers haha#mad scientists of tumblr...mad for loving people more than machines
541 notes
·
View notes
Text
10 Top Strategic Technology Trends for 2025

The winds of change are relentless, sweeping through social and economic landscapes, leaving no corner untouched. As industries grapple with these ongoing disruptions, the call for foresight grows louder. Leaders who dare to look beyond the horizon know the key to future success lies in embracing the tools of tomorrow, today.
Imagine an organization standing on the edge of a vast and unknown future. The path forward is fraught with challenges, yet illuminated by the promise of innovation. To forge ahead safely, leaders must anchor their strategies in transformative technologies destined to redefine the business landscape by 2025. These trends won’t just solve problems—they will dismantle barriers to productivity, security, and innovation, paving the way for a brighter, bolder future.

This is no ordinary moment in history. It’s a thrilling chapter where businesses and visionaries find themselves in the interaction of ambition and opportunity. The technological forces emerging now promise to astonish us, as they challenge conventions and open doors to uncharted possibilities.
Let’s step forward and explore the revolutionary tech trends of 2025 that will force and dominate the decade ahead. They will leave a lasting impact on businesses and societies worldwide. These are not just trends; they are the harbingers of a new era, and the story of their influence is only just beginning.
Theme 1: AI Imperatives and Risks Drive Organizational Protections
Trend 1: Agentic AI

Autonomous AI systems can independently plan and execute actions to achieve user-defined goals.
Business Benefits: Agentic AI empowers businesses with a virtual workforce of intelligent agents. These agents enhance productivity by automating repetitive tasks, augmenting human decision-making, and supporting traditional applications. This creates seamless collaboration between human employees and AI systems, leading to increased operational efficiency.
Challenges: To prevent unintended consequences, robust guardrails are essential. These guardrails ensure artificial intelligence systems align with the intentions of both providers and users. Without these safeguards, businesses risk losing control over AI actions, leading to potential ethical and operational issues.
Trend 2: AI Governance Platforms

Companies adopt platforms to manage AI’s legal, ethical, and operational dimensions effectively.
Business Benefits: Governance platforms help establish and enforce policies for responsible AI usage. They provide transparency to build trust by explaining AI decision-making processes and managing model lifecycles. This fosters accountability, making it easier for stakeholders to rely on AI systems.
Challenges: Global and industry-specific AI guidelines vary significantly, making consistent practices difficult. Businesses must navigate these complexities to ensure compliance while maintaining operational efficiency.
Trend 3: Disinformation Security
New technologies are emerging to discern trustworthiness systematically and combat false information.
Business Benefits: Disinformation security reduces fraud by verifying identities through advanced controls. It prevents account takeovers using continuous risk scoring and adaptive trust models. Moreover, it safeguards brand reputation by identifying and countering harmful narratives quickly.
Challenges: This requires a dynamic, multilayered, and adaptive approach involving continuous learning and collaboration. Staying ahead of evolving threats demands significant resource investment and a skilled team.
Theme 2: New Frontiers in Computing Prompt Organizations to Rethink Their Strategies
Trend 4: Post-Quantum Cryptography (PQC)

Protecting sensitive data against quantum computing’s decryption capabilities. The steps of post-quantum cryptography in the above image will give you the exact knowledge about its process.
Business Benefits: PQC algorithms ensure data remains secure despite quantum computing advancements. This proactive approach minimizes the long-term risks of unauthorized access to critical information.
Challenges: Transitioning to PQC is complex, as current algorithms are not direct replacements for existing systems. Applications may experience performance issues, requiring extensive testing and potential rewrites.
Trend 5: Ambient Invisible Intelligence

Technology seamlessly integrates into environments to create intuitive and natural user experiences.
Business Benefits: Ambient intelligence enables cost-effective, real-time tracking of items, improving visibility and operational efficiency. It offers new ways to verify authenticity, track object history, and report properties, opening doors to innovative use cases.
Challenges: Privacy concerns arise from continuous data collection. Providers must secure consent and ensure compliance. Users may disable tracking features to protect their privacy, limiting effectiveness.
Trend 6: Energy-Efficient Computing
Enhancing sustainability through optimized hardware, efficient algorithms, and renewable energy.
Business Benefits: Businesses address regulatory and societal demands for sustainability by lowering carbon footprints. This also reduces operational costs over time, contributing to long-term financial benefits.
Challenges: Adopting energy-efficient technologies requires new hardware, tools, and skills. Migrating to green platforms can be expensive and time-consuming. Rising energy prices during the green transition may create short-term cost pressures.
Trend 7: Hybrid Computing

A fusion of diverse computing, storage, and networking solutions to tackle complex challenges.
Business Benefits: Hybrid computing delivers unparalleled efficiency and speed, driving transformative innovation. It powers advanced AI systems, autonomous businesses, and real-time personalization, unlocking new levels of human-machine collaboration.
Challenges: These nascent technologies demand specialized expertise and high upfront investment. Managing autonomous modules introduces security risks and requires seamless integration and orchestration across systems.
Theme 3: Human-Machine Bridges Physical and Digital Realms
Trend 8: Spatial Computing

Enhancing the physical world with immersive technologies like augmented reality (AR) and virtual reality (VR).
Business Benefits: Spatial computing transforms industries like gaming, education, and e-commerce with engaging, interactive experiences. It also empowers sectors like healthcare and manufacturing with advanced visualization tools for better decision-making.
Challenges: High costs and bulky hardware, like head-mounted displays, limit widespread adoption. Privacy concerns, complex interfaces, and safety risks pose additional barriers.
Trends 9: Polyfunctional Robots
Robots are capable of performing multiple tasks and switching roles seamlessly.
Business Benefits: These robots increase efficiency and offer faster ROI. Their flexible deployment reduces infrastructure requirements, making them scalable and adaptable. They complement human efforts, ensuring operational continuity.
Challenges: The lack of industry standards for pricing and functionality complicates adoption. Organizations face challenges in identifying cost-effective and versatile solutions.
Trend 10: Neurological Enhancement
Boosting cognitive capabilities through technologies that decode and interface with brain activity.
Business Benefits: Neurological enhancements enable personalized education, improved workplace safety, and extended career longevity for older workers. They also open doors for next-generation marketing and human upskilling.
Challenges: These technologies are expensive and limited by mobility and battery constraints. Security risks arise from brain-machine interfaces directly interacting with neural activity. Ethical concerns, such as altering perceptions, must also be addressed.
Conclusion
In a world buzzing with innovation, technology is no longer just a backdrop; it’s the star of the show. Across the globe, there are new advancements emerging and evolving, by shaping the way we live, work, and connect. These technological breakthroughs aren’t just fleeting sparks; they hold immense promise for today and the future, lighting the way to a world full of untapped potential.
Picture an organization standing at a crossroads, where the old ways meet the new. The choice is clear: embrace these transformative trends or risk being left behind in a rapidly advancing landscape. By leaning into innovation and fostering the skills that align with these changes, businesses can unlock doors to growth, resilience, and meaningful impact.
This isn’t just about survival—it’s about thriving in a tech-driven world. It’s about adapting to the rhythm of progress and dancing to the tune of possibility. For those willing to seize this moment, the rewards are boundless, and the journey promises to be one of transformation and triumph.
Source URL: https://www.techaheadcorp.com/blog/10-top-strategic-technology-trends-for-2025/
0 notes
Note
I still have a question on "Another day at the DPD" 🧐 What about Pandora ? We have no informations on what her plan was when she blew up the warehouse, she's still somewhere in the Detroit and Connor and Nines know this 🧐🧐
HHHHH I’m so glad you asked !!!
Actually, that part of the plot was meant to foreshadow season 4, just like I teased season 3 at the end of season 2 (if you look carefully, I mention NOVA and the thirium shortage in the TV news).
Now, you know there won’t be a season 4, because I really needed to move on, explore other universes, other stories.
So, what was gonna happen in season 4, you ask ?
There is this article from the magazine Tech Addict you can read in the chapter “Meet Kamski”, saying Cyberlife is working on a quantum supercomputer that can anticipate events such as alien invasions or climate disasters. So, in season 4 we should have learned that this computer had been built, and that its very first prediction was that androids were gonna take over humans in the next decades. The ex CEO Hailey Johnson decided to keep this information a secret but tried to prevent androids to get more rights to make sure they would never have the means to overpower humans.
After Kamski comes back to Cyberlife and gives Pandora a body, they started working together. They both knew about the quantum supercomputer's predictions, Kamski just wants to see how far androids can go, but still be in control, and Pandora owes him a body. So Kamski knows that if he wants to have control over the android takeover, he needs to have the monopoly of androids’ essential products... this is why Pandora’s seen blowing up NOVA’s warehouse.
Connor noted it in the final report, when the team was filling papers and closing the case definitely, but he had absolutely no idea why Pandora did what she did. It doesn’t bugs him, until more attacks happen on android specialized industrial sites, so he talks about it with Hank, and the band starts investigating the issue.
The real problem about that season 4 was that, with such a plot, it would have been soooo long, and as I said earlier, I wanted to do something else with our boys. Also, I was satisfied with Hankcon and Reed900 development at the end of season 3 and I really didn’t want to make them go through more drama.
So, this is what was planned for Pandora. I’m so glad you asked because I really liked this OC, and I thought about her character development a lot when I was working on that hypothetical season 4 : she was meant to meet Connor again, and everything. I kinda like her, even though she never really was under the spotlights... Or maybe that’s why I like her.
Thank you again for asking ! I’m glad someone paid attention to this fiery badass girl <3
30 notes
·
View notes
Text
since you really don’t know who Eye BEE… Allow 1968 Gen X 2223 ME [MICHAEL] 2 Intuitively [MI = MICHAEL] Introduce [MI = MICHAEL] My MUCH HIGHER [MH = JAH] SUPREME GODSELF of YAHUWA… since Eye SIRIUS [YES] Astronomically Intelligent ANUNNAKI [AIA = AMÚN] SUN GOD [RA] DNA MEMORY UPGRADE [MU] Engineer [ME] of EXTRATERRESTRIAL [ME] 9 Ether [ME] SKY NIBIRUAN ME [MICHAEL] on ANU GOLDEN 9 Ether [MAGE] SKY Earth [Qi]… Parallel Axis [PA] from Astronomical [PA] PLUTO’s GOLDEN 9 SKY Ether Ethereal [ECLIPSE = Occulted] URANIAN Satellite [U.S.] Pyramid [UP] SUN... Eye Electronically & Remotely [SEER] Digitized w/Automation Processes [DAP] Captured [D.C.] from 1999 Y2K 2000-2023 before Mayan's 2012 SKY Prophecy of MURDUK’S Twin 9/11 Towers in 2001 @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 LLC of ATLANTIS [L.A.] 5000
IMMORTAL U.S. MILITARY KING SOLOMON-MICHAEL HARRELL, JR.™
OMMMMM
OMMMMM

soulless cgi hollywood still on strike?!?!?! [insert evil evil laugh emoji x 3]

Eye 1968 TUT [E.T.] of Pluto's Radioactive Nanoscopic DNA Chemical [D.C.] Elements, Michael's 5th Member of an Updated [MU] Actinide [MA] Series on Murduk's Astronomical Periodic [MAP] RNA Table of NIBIRU

1968 9 Ether GEN X SCORPIUS DNA Constellation [D.C.] NEUROMELANIN of Interplanetary MARS' [I'M] QUANTUM [IQ] STEM CELL DNA UPGRADES Alkhemically + Generationally Engineered [AGED] w/SIRIUS Radioactively ATOMIC PLUTONIUM [RAP] RNA ELECTRONICS @ QUANTUM HARRELL TECH LLC

QUANTUM ELECTRONIC 9 ETHER BIOLOGICAL NEUROMELANIN DNA WEAPONS UPGRADES [WU] @ QUANTUM HARRELL TECH LLC

Eye 1st Ancient 9 Ether SKY Machine Mining Encyclopedia [ME] Learning Ægyiptian Pharaoh MENES [PM] @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 LLC of ATLANTIS [L.A.] 5000

QUANTUM HARRELL TECH Apple iPhone of PLUTONIUM [APP] Chemical Elements [ACE] Digitally Mined [DM] @ QUANTUM HARRELL TECH LLC?!?!?!

DON'T LOOK UP!!!

eye see anu global 9 ether [sage] computer bug [takeover] of outdated 1999 y2k 2000-2023 america, inc [a.i.] @ 1921 quantum 2023 harrell 2024 tech 2025 llc of atlantis [l.a.] 5000

everything you see on tv is poorly scripted hollywood cgi-spam media [insert evil evil laugh emoji x 3] [activate KA BOOM x 10 sound effect]

artificial 1999 Y2K 2000-2023 9/11 AMERICA, Inc [A.i.]... Get Ready 4 ANU GOLDEN 9 Ether [RAGE] QUANTUM 2024 Y2K 2025 Cyber Compu_TAH [PTAH] WARLORD LAW.gov 4 QUANTUM HARRELL TECH's GLOBAL 6G x 3 = 18G MILITARY SKY WEAPONS.gov of MASS DESTRUCTION... Scientifically Engineered by 144,000 Architecturally [SEA] Intelligent 9 Ether SKY Humanoid-Android [HA = HARRELL] RUMARDIANS @ QUANTUM HARRELL TECH LLC

uh oh!!! not the CLASSIFIED quantum CLASSIFIED harrell CLASSIFIED 6g CLASSIFIED tech CLASSIFIED military illuminati [mi = michael] CLASSIFIED of CLASSIFIED CLASSIFIED CLASSIFIED 9/11 america, inc [a.i.]?!?!?!

TIME'S UP 4 UNCLASSIFIED 1999 Y2K 2000-2023 9/11 AMERICA!!! [deploy out of business encryption protocol]

NOBODY COMING 2 SAVE AMERICA [insert evil evil laugh emoji]


HEIL SCHWARZE SONNE HARRELL!!!

6G from 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 LLC of ATLANTIS [L.A.] 5000

LARGEST 1999 Y2K 2000-2023 INTERNATIONAL 9/11 MILITARY [I'M] WEALTH TRANSFER from the Intranet.gov of Encrypted Radio [TIER] Broadcast Data [TBD] System Engineer Architects [SEA] @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 LLC of ATLANTIS [L.A.] 5000

#om#o michael#quantumharrelltech#mu:13#kemet#harrelltut#quantumharrelltut#u.s. michael harrell#king tut#9etherpentagonelites#9etheraluhumanunnaqi#quantum 9/11 sky tech#9/11 cyber wars#quantum harrell technology deconstructing artificial 2023 america#PHARAOH MENES#the real 144000
1 note
·
View note
Text
GIL PARTNERS/ WATSON TODD FAKE BUSINESS/NAMES STOLEN&USING MY MURDERED DECEASED MOM'S SSNX3115 2006-NOW MONEY LAUNDERING PHISHING FRAYD SCAMS FAJE WEBSITES FAKE NPO's "free-lotto"USING -games,STOLEN AND USING MY SSN@OCEAN CITY NJ SSA FRAUD 2009-NOW BY FAKE @MICHAELSAYLOR AKA SMITH ALIAS BRIAN L MELLOTT WHO MURDERED REAL @MICHAEL_SAYLOR MICHAEL J SAYLOR AND BROTHER STEPHEN @SAYLOR WHO BOTH ATTENDED MIT STEPHEN ROBOTICS ENGR FOR @universalstudiosorlando-blog @lordoftherings @paramountpictures #filmmaker / #COMPUTER #SCIENTIST/SET DESIGNER IS ALSO #MISSINGPerson 2018-NOW ALL HIS FB DELETED BY FAKE-SAYLOR/SMITH/BRIAN L MELLOTT POSING AS FAKE JAMES WYNEN WHYNIN LYING TO POLICE.... MIAMI FBI SWAT$1BILLION- COCAINE DRUGS BUSTED 2022FEB-NOW HIDING FM LAW ENFORCEMENT AUTHORITIES IN OUR HOME HEUWELHUIS MANSIONGIL PARTNERS/ WATSON TODD FAJE BUSINESS/NAMES STOLEN&USING MY MURDERED DECEASED MOM'S SSNX3115 2006-NOW MONEY LAUNDERING #PHISHING FRAUD #SCAMS FAKE #WEBSITES/FAKE #NPO's "free-lotto"USING -games,STOLEN AND USING MY SSN@OCEAN CITY NJ SSA FRAUD 2009-NOW BY FAKE @MICHAELSAYLOR AKA SMITH ALIAS BRIAN L MELLOTT WHO MURDERED REAL @MICHAEL_SAYLOR MICHAEL J SAYLOR AND BROTHER STEPHEN @SAYLOR WHO BOTH ATTENDED MIT STEPHEN ROBOTICS ENGR FOR UNIVERSAL STUDIOS LORD OF THE RINGS FILMMAKER/COMPUTER SCIENTIST/SET DESIGNER IS ALSO MISSING 2018-NOW ALL HIS FB DELETED BY FAKE-SAYLOR/SMITH/BRIAN L MELLOTT POSING AS FAKE JAMES WYNEN WHYNIN LYING TO POLICE.... MIAMI FBI SWAT$1BILLION- COCAINE DRUGS BUSTED 2022FEB-NOW HIDING FM LAW ENFORCEMENT AUTHORITIES IN OUR HOME HEUWELHUIS MANSION HOSTAGE JAMES@GUNPOINT RANSOM$1-2BILLION ASSETS BETWEEN JAMES AND FORMER EMPLOYER REAL MURDERED DECEASED MICHAEL SAYLOR OWNER OF 3030KSTREET NW DC THE PENTHOUSE CONDO AND $480MILLION MANSION MIAMI $280MILLION PRIVATE JETPLANE AND $50MILLION YACHT THE "HARLE" WINNER OF BEST DESIGN PARIS AIR/BOAT SHOW 2006-2008-2012-2014 DESIGNED/RENOVATED/ BUILT NY REAL ARCHITECT ENGINEER CORNELL UNIVERSITY 1992 JAMES AUGUSTUS SEYMOUR GREGG VANWYNEN
WHO WON BILL GATES UBM CHALLENGE 1982 BUILT 1ST PERSONAL COMPUTER FOR BILL GATES ORIGINAL COMPANY IBM COMPUTER SCIENTIST CRYPTO EXPERT "JAMES FIVE NAMES" OWNER OF CRYPTOMERICA LLC 1992-2018 HOSTAGE JAMES@GUNPOINT RANSOM$1-2BILLION ASSETS BETWEEN JAMES AND FORMER EMPLOYER REAL MURDERED DECEASED MICHAEL SAYLOR OWNER OF 3030KSTREET NW DC THE PENTHOUSE CONDO AND $480MILLION MANSION MIAMI $280MILLION PRIVATE JETPLANE AND $50MILLION YACHT THE" #HARLE" WINNER OF BEST DESIGN PARIS AIR/BOAT SHOW 2006-2008-2012-2014 #JASGVW #DESIGNED #RENOVATED/ BUILT NY REAL @architectureblog @engineering @cornelluniversitystories #Cornell #University 1992 #JAMES AUGUSTUS SEYMOUR GREGG VANWYNEN, WHO WON @billgatesofficial @ibmconsulting #IBMCHALLENGE 1982 BUILT 1ST #PERSONALCOMPUTER FOR @billgatesreads-blog #ORIGINAL #COMPANY @ibmcompatible #computer SCIENTIST #CRYPTO #EXPERT "JAMES FIVE NAMES" OWNER OF CRYPTOMERICA LLC 1992-2018
Watch "Otis Redding - I´ve Got Dreams To Remember" on YouTube
youtube
#computer science#bill gates#ibm quantum network#ibm consulting#ibm#ibmweek#microsoft#metro pcs#tmobile#realme 10 fcc certification specifications design expected rmx3630 realme 10#amazon irobot takeover usd 1 72 billion antitrust review us ftc report amazon#ctia#ACP#affordable#connectivity#three billboards outside ebbing missouri#ebb petty#lifeline#fedex corp#federal#dc#ada#SSA#social security#fraudulent#fraude sistema financiero#tax fraud#insurance fraud#securities fraud#healingjourney
11 notes
·
View notes
Photo

Iron Man
Iron Man is a fictional superhero appearing in American comic books published by Marvel Comics. The character was co-created by writer and editor Stan Lee, developed by scripter Larry Lieber, and designed by artists Don Heck and Jack Kirby. The character made his first appearance in Tales of Suspense #39 (cover dated March 1963), and received his own title in Iron Man #1 (May 1968). Also in 1963, the character founded the Avengers alongside Thor, Ant-Man, Wasp and the Hulk.
A wealthy American business magnate, playboy, philanthropist, inventor and ingenious scientist, Anthony Edward "Tony" Stark suffers a severe chest injury during a kidnapping. When his captors attempt to force him to build a weapon of mass destruction, he instead creates a mechanized suit of armor to save his life and escape captivity. Later, Stark develops his suit, adding weapons and other technological devices he designed through his company, Stark Industries. He uses the suit and successive versions to protect the world as Iron Man. Although at first concealing his true identity, Stark eventually publicly reveals himself to be Iron Man.
Initially, Iron Man was a vehicle for Stan Lee to explore Cold War themes, particularly the role of American technology and industry in the fight against communism. Subsequent re-imaginings of Iron Man have transitioned from Cold War motifs to contemporary matters of the time.
Throughout most of the character's publication history, Iron Man has been a founding member of the superhero team the Avengers and has been featured in several incarnations of his own various comic book series. Iron Man has been adapted for several animated TV shows and films. In the Marvel Cinematic Universe, the character was portrayed by Robert Downey Jr., appearing in the films Iron Man (2008), The Incredible Hulk (2008) in a cameo, Iron Man 2 (2010), The Avengers (2012), Iron Man 3 (2013), Avengers: Age of Ultron (2015), Captain America: Civil War (2016), Spider-Man: Homecoming (2017), Avengers: Infinity War (2018) and Avengers: Endgame (2019). The character also appeared in Spider-Man: Far From Home (2019) and in the upcoming Black Widow (2021) through archive footage.
Iron Man was ranked 12th on IGN's "Top 100 Comic Book Heroes" in 2011 and third in their list of "The Top 50 Avengers" in 2012.
> Powers, abilities, and equipment
Armor
Iron Man possesses powered armor that gives him superhuman strength and durability, flight, and an array of weapons. The armor is invented and worn by Stark (with occasional short-term exceptions). Other people who have assumed the Iron Man identity include Stark's long-time partner and best friend James Rhodes; close associates Harold "Happy" Hogan; Eddie March; (briefly) Michael O'Brien and Riri Williams.
The weapons systems of the suit have changed over the years, but Iron Man's standard offensive weapons have always been the repulsor rays that are fired from the palms of his gauntlets. Other weapons built into various incarnations of the armor include: the uni-beam projector in its chest; pulse bolts (that pick up kinetic energy along the way; so the farther they travel, the harder they hit); an electromagnetic pulse generator; and a defensive energy shield that can be extended up to 360 degrees. Other capabilities include: generating ultra-freon (i.e., a freeze-beam); creating and manipulating magnetic fields; emitting sonic blasts; and projecting 3-dimensional holograms (to create decoys).
In addition to the general-purpose model he wears, Stark has developed several specialized suits for space travel, deep-sea diving, stealth, and other special purposes. Stark has modified suits, like the Hulkbuster heavy armor. The Hulkbuster armor is composed of add-ons to his so-called modular armor, designed to enhance its strength and durability enough to engage the Hulk in a fight. A later model, created with the help of Odin and the Asgardian metal Uru, is similar to the Destroyer. Stark develops an electronics pack during the Armor Wars that, when attached to armors that use Stark technologies, will burn out those components, rendering the suit useless. This pack is ineffective on later models. While it is typically associated with James Rhodes, the War Machine armor began as one of Stark's specialty armors.
The most recent models of Stark's armor, beginning with the Extremis armor, are now stored in the hollow portions of Stark's bones, and the personal area networking implement used to control it is implanted into his forearm, and connected directly to his central nervous system.
The Extremis has since been removed, and he now uses more conventional armors. Some armors still take a liquid form, but are not stored within his body. His Endo-Sym Armor incorporates a combination of the liquid smart-metal with the alien Venom symbiote, psionically controlled by Stark.
Post-Secret Wars, Stark uses a more streamlined suit of armor that uses nanotechnology to shape shift into other armors or weapons.
Powers
After being critically injured during a battle with the Extremis-enhanced Mallen, Stark injects his nervous system with modified techno-organic virus-like body restructuring machines (the Extremis process). By rewriting his own biology, Stark is able to save his life, gain an enhanced healing factor, and partially merge with the Iron Man armor, superseding the need for bulky, AI-controlled armors in favor of lighter designs, technopathically controlled by his own brain. His enhanced technopathy extends to every piece of technology, limitless and effortlessly due to his ability to interface with communication satellites and wireless connections to increase his "range". Some components of the armor-sheath are now stored in Tony's body, able to be recalled, and extruded from his own skin, at will.
During the "Secret Invasion" storyline the Extremis package is catastrophically shut down by a virus, forcing him again to rely on the previous iteration of his armor, and restoring his previous limitations. Furthermore, Osborn's takeover of most of the few remaining Starktech factories, with Ezekiel Stane systematically crippling the others, limits Tony to the use of lesser, older and weaker armors.
After being forced to "wipe out" his brain to prevent Norman Osborn from gaining his information, Tony Stark is forced to have a new arc reactor, of Rand design installed in his chest. The process greatly improves his strength, stamina and intellect. The procedure left him with virtually no autonomic functions: as his brain was stripped of every biological function, Tony is forced to rely on a digital backup of his memories (leaving him with severe gaps and lapses in his long-term memory) and on software routine in the arc reactor for basic stimuli reaction, such as blinking and breathing. The Bleeding Edge package of armor and physical enhancement is now equal in power, if not a more advanced, version of the old Extremis tech.
Skills
Tony Stark is an inventive genius whose expertise in the fields of mathematics, physics, chemistry, and computer science rivals that of Reed Richards, Hank Pym, and Bruce Banner, and his expertise in electrical engineering and mechanical engineering surpasses even theirs. He is regarded as one of the most intelligent characters in the Marvel Universe. He graduated with advanced degrees in physics and engineering at the age of 17 from Massachusetts Institute of Technology (MIT) and further developed his knowledge ranging from artificial intelligence to quantum mechanics as time progressed. His expertise extends to his ingenuity in dealing with difficult situations, such as difficult foes and deathtraps, in which he is capable of using available tools, including his suit, in unorthodox but effective ways. For instance, in Stark's final confrontation with Obadiah Stane, the villain managed to have Stark's companions in an unconscious state in a room with motion sensors; when Stark entered the room, Stane warned him that the slightest move would trigger a fatal electrical current to his hostages, thus forcing Stark to stay still and slowly die of dehydration lest he wants his friends to die. However, while Stane was confident that such a trap was inescapable, Stark is able to outwit and defeat its mechanism in seconds, thus freeing the hostages and allowing him to continue the battle against Stane.
He is well respected in the business world, able to command people's attention when he speaks on economic matters, having over the years built up several multimillion-dollar companies from virtually nothing. He is noted for the loyalty he commands from and returns to those who work for him, as well as for his business ethics. Thus he immediately fired an employee who made profitable, but illegal, sales to Doctor Doom. He strives to be environmentally responsible in his businesses.
At a time when Stark was unable to use his armor for a period, he received some combat training from Captain America and has become physically formidable on his own when the situation demands it. In addition, Stark possesses great business and political acumen. On multiple occasions he reacquired control of his companies after losing them amid corporate takeovers.
Due to his membership in the Illuminati, Iron Man was given the Space Infinity Gem to safeguard. It allows the user to exist in any location (or all locations), move any object anywhere throughout the universe and warp or rearrange space.
7 notes
·
View notes
Text
Office Furniture - The Way to Go
It has done so by continuously and very diligently adapting and readapting itself to the ground scenario that is transforming ever so quickly.
One of the most significant transformations that have impacted the insides of workplaces across occupations, professions, and sectors have been the advent of and the eventual complete takeover of our work lives by computers and information systems.
The other factor is the emergence of a work culture that never seems to allow you to say no to work. Long working hours and a highly aggressive approach to work are all having a direct impact on our health and it is pretty obvious that the effects need to be lessened as far as possible. Well, the office furniture industry seems to be doing a decent job on this front.
You do have more thoughtfully made and ergonomically designed office chairs and office desks adoring our enterprises these days. Having them does reduce the stress levels to a great degree.
Yet another factor is the cropping up of new fields and sectors opening up everywhere even as the more conventional industries are themselves undergoing a complete makeover. This development has obviously not lessened the challenges for the professionals serving in the office furniture industry.
When you look around you see office chairs, office desks, tables, corner tables, reception tables, settees, sofa sets, conference tables, exclusive chairs, and tables for the recreation area and the canteen - all of which are in such trend and progressive designs and colors and types that one cannot help but marvel at the sheer ingenuity that this particular sector has shown.
The recession that our economy is still not fully cured of meant that substantial numbers of employees left their regular jobs and instead set up offices in their own residences. The outcome was the great increase in the demand for home office furniture. There has, in fact, been a quantum jump of 34% in the sales of small office chairs, smaller work stations, more of those items that can be dismantled and reset, etc. And of course, the use of less expensive wood and other material too.
The road ahead for the office The furniture industry does look far healthier than some of the other industries.
Get the latest updates on modern office furniture, Meeting Tables, office chairs, office desks, Reception Desks in Dubai, for detailed office furniture, please visit our website officemaster.ae
OfficeMaster Al Quoz Branch – Office Furniture Dubai
No. 3, 34, 6 St., Dubai - UAE
+971 (0)50 651 9769
+971 (0)4 33 66 360

#office furniture#office chairs#office desks#reception tables#sofa sets#conference tables#home office furniture#small office chairs#smaller work stations#modern office furniture#Office Furniture Dubai
1 note
·
View note
Text
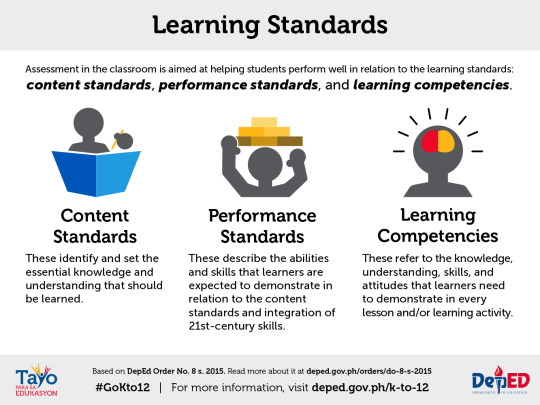
PORTFOLIO IN EMPOWERMENT TECHNOLOGY
CHAPTER 1 LESSON 1: INFORMATION AND COMMUNICATIONS TECHNOLOGY - Is a branch of engineering that involves the conception, design, manufacture, and operation of robots. This field overlaps with electronics, computer science, artificial intelligence, mehcatronics, nanotechonology and bioengineering. CONTENT STANDARD
- The learners demonstrate an understanding of ICT in the context of global communication for specific professional track.
Performance Standards
- The learners shall be able to: at the end of the 2-week period independently compose an insightful reflection paper on the nature of ICT in the context of their lives, society, and professional tracks (Arts, Tech Vocational, Sports and Academic)
Most essential learning competencies
The learners should be able to:
1. Compare and contrast the nuances of varied online platforms, sites, and content to best achieve specific class objectives or address situational challenges.
2. Apply online safety, security, ethics, and etiquette standards and practice in the use of ICTs as it would relate to their professional tracks. 3. Use the internet as a tool for credible research and information gathering to best achieve specific class objectives or address situational.
1.1 INFORMATION AND COMMUNICATION TECHNOLOGY

- ICT is the technology required for information processing, in particular, the use of the electronic computers, communication devices and software applications to convert, store, protect, process, transmit and retrieve information from anywhere, anytime.
- Information refers to the knowledge obtained from reading, investigation, study or research. The tools to transmit information are the telephone, television and radio. Information is knowledge and helps us to fulfill our daily tasks. - Communication is an act of transmitting messages. It is a process whereby information was exchanged between individuals using symbols, signs or verbal interactions. Communication is important in order to gain knowledge. Technology is the use of scientific knowledge, experience and resources to create processes products that fulfill human needs. Technology is vital in communication.
- ICT nowadays has also widened the horizon in developing new tools or emerging technologies. Mobile devices can communicate through wireless fidelity (Wifi), Bluetooth, third generation 3g & 4g, data services and dial up services and virtual private networks. EMERGING TECHNOLOGIES

- Artificial Intelligence (AI) - is the ability of a digital computer or computer controlled robot to perform tasks commonly associated with intelligent beings. The term is frequently applied to the project of developing systems endowed with the intellectual processes characteristics of humans, such as the ability to reason, discover meaning, generalize or learn from past experience. ROBOTICS

- Is a branch of engineering that involves the conception, design, manufacture, and operation of robots. This field overlaps with electronics, computer science, artificial intelligence, mehcatronics, nanotechonology and bioengineering. BIOMETRICS

- Are a way to measure a person’s physical characteristics to verify their identity. These can include physiological traits, such as fingerprints and eyes, or behavioral characteristics, such as the unique way you’d complete a security-authentication puzzle. QUANTUM CRYPTOGRAPHY

- Also called quantum encryption, applies principles of quantum mechanics to encrypt messages in a way that it is never read by anyone outside of the intended recipient. COMPUTER ASSISTED TRANSLATION

- Involves the use of software programs to translate both verbal and written texts. Also known as machine-assisted or machine aided translation. 3D IMAGING AND HOLOGRAPHY

- Is defined as a 3D projection that exists freely in space and is visible to everyone without the need for 3D glasses. VIRTUAL REALITY

- Refers to the computer generated simulation in which a person can interact within an artificial 3D environment using special electronic devices that can be similar to or completely different from the real world. ONLINE SAFETY

- Is the knowledge of maximizing the user’s personal safety and security and risk to private information, and self-protection from computer crime in general. 1. Know the scams - Learn about different kinds of scams and what you can do to avoid them.

2. Think before you click - Think twice, thrice and zillion time before click any link or buttons.

3. Safety Peruse - These sites may have an Address that’s very similar to a legitimate site, but the page can have misspelling, Bad Grammar, or low resolution Images.

4. Shop Safety - Don’t shop on a site unless it has “https” and a padlock icon on the left or right in the URL.

5. Kick-butt passwords - Use an Extremely uncrackable password One like “9&4thkel965#”.
6. Protect your info’s - Keep your guard up, Back up all your data on your computer, smartphone and tablet, theft or a cash.

7. Watch your Wi-Fi Connectivity - Protect your network by changing your router’s setting and making sure that you have the connection password protected.

8. Install a Firewall - A firewall is a grate line of defense against cyber attracts.
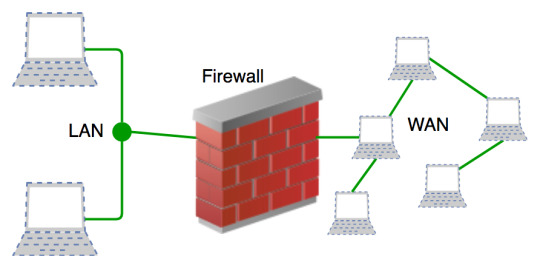
9. Keep up to date - The best security updates automatically to protect your computer. - Use the manufacturer’s latest security patches to make regular updates and make that you have the software set to do routine scam.

10. Use your Noggin - Use your common sense while surfing the web.

COMMON ISSUES AND CRIMES IN THE INTERNET - CYBERBULLYING - HACKING - IDENTITY THEFT - PLAGIARISM - COPYRIGHT ISSUES CYBERBULLYING - Is a form of bullying or harassment using electronic means. Cyberbullying and Cyber Harassment are also known as online bullying. - Cyberbullying is when someone, typically teens, bully or harass others on the internet, particularly on social media sites. Harmful bullying behavior can include posting rumors, threats, sexual remarks, a victims’ personal information, or pejorative labels. THE ANTI-BULLYING ACT OF 2013 ( RA 10627 )
(Sec. 2, RA 10627) These acts are collectively “called cyber bullying” when committed online. (Sec. 2-D, RA 10627) This covers social bullying aiming to belittle another individual or group or gender-based bullying that humiliates another on the basis of perceived or actual sexual orientation and gender identity. (Sec. 3, B-1 RA 10627. Implementing Rules). THE REVISED PENAL CODE AND THE CYBERCRIME PREVENTION ACT. - One who publicly or maliciously imputes to another a crime, vice, defect, real or imaginary, or any act, omission, condition, status or circumstance tending to cause the dishonor, discredit or contempt of a natural or juridical person, or blacken the memory of one who is dead may be liable for libel under this Code. (Art, 353, RPC) These acts are more severely punished when done online in addition to the civil action for damages which may be brought by the offended party. (Sec. 4(c-4), RA 10175) Cyberlibel holds liable only the original author of the post (Sec. 5(3), Implementing Rules of RA 10175) Likers or shares of a post cannot be held liable under this law. - Slander may also be applicable to one who, in heat of anger, utters statements that are highly defamatory in character. (Art 358, RPC) Intriguing Against Honour may also find applicability when the principal purpose is to blemish the honour or reputation of a person. Hence, a blind ite is not as actionable as a named-post in social media. HACKING

- Hacking generally refers to unauthorized intrusion into a computer or a network. The person engaged in hacking activities is known as a hacker. This hacker may alter system or security features to accomplish a goal that differs from the original purpose of the system. - Hacking can also refer to non-malicious activities, usually involving unusual or improvised alterations to equipment or processes.
IDENTITY THEFT

- Also known as identity fraud, is a crime in which an imposter obtains key pieces of personally identifiable information, such as Social Security or driver's license numbers, in order to impersonate someone else. TYPES AND EXAMPLES OF IDENTITY THEFT 1. True-name identity theft means the thief uses personal information to open new accounts. The thief might open a new credit card account, establish cellular phone service or open a new checking account in order to obtain blank checks. 2. Account-takeover identity theft means the imposter uses personal information to gain access to the person's existing accounts. PLAGIARISM

- Is an act of fraud. It involves both stealing someone else's work and lying about it afterward. The following are considered plagiarism - turning in someone else's work as your own - copying words or ideas from someone else without giving credit - failing to put a quotation in quotation marks - giving incorrect information about the source of a quotation - changing words but copying the sentence structure of a source without giving credit - copying so many words or ideas from a source that it makes up the majority of your work, whether you give credit or not (see our section on "fair use" rules) Republic Act No. 8293 [An Act Prescribing the Intellectual Property Code and Establishing the Intellectual Property Office, Providing for Its Powers and Functions, and for Other Purposes]otherwise known as the Intellectual Property Code of the Philippines. Intellectual property rights under the I. P. Code: The intellectual property rights under the Intellectual Property Code are as follows: 1. Copyright and related rights; 2. Trademarks and service marks; 3. Geographic indications; 4. Industrial designs; 5. Patents; 6. Layout designs [topographies] of integrated circuits; and 7. Protection of undisclosed information. The scheme of penalties for infringement has also been changed. From the previous fine of Php200 to Php2,000 and/or imprisonment of 1 year, the current range of penalties are as follows: - For first offenders - fine of PhP50,000 to PhP150,000 and/or imprisonment of 1 to 3 years - For second offenders - fine of PhP150,000 to PhP500,000 and/or imprisonment of 3 to 6 years - For third and subsequent offenders - fine of PhP500,000 to PhP1.5 Million and/or imprisonment of 6 to 9 years. - In case of insolvency, the offender shall furthermore suffer subsidiary imprisonment. NETIQUETTE - Is a combination of the word net and etiquette.It focuses on the acceptable behavior of a person while using the internet resource. - It focuses on the acceptable behavior of a person while using the internet resource. The Core Rules of Netiquette Rule 1. Remember the human. - Never forget that the person reading your mail or posting is, indeed, a person, with feelings that can be hurt. - Corollary 1 to Rule #1: It's not nice to hurt other people's feelings. - Corollary 2: Never mail or post anything you wouldn't say to your reader's face. - Corollary 3: Notify your readers when flaming. Rule 2. Adhere to the same standards of behavior online that you follow in real life. Corollary 1: Be Ethical Corollary Corollary 2: Breaking the law is bad Netiquette. Rule 3. Know where you are in cyberspace. Corollary 1: Netiquette varies from domain to domain. Corollary 2: Lurk before you leap. Rule 4. Respect other people's time and bandwidth. Corollary 1: It's OK to think that what you're doing at the moment is the most important thing in the universe, but don't expect anyone else to agree with you Corollary 2: Post messages to the appropriate discussion group.Corollary 3: Try not to ask stupid questions on discussion groups Corollary 4: Read the FAQ (Frequently Asked Questions) document Corollary 5: When appropriate, use private email instead of posting to the group Corollary 6: Don't post subscribe, unsubscribe, or FAQ requests Corollary 7: Don't waste expert readers' time by posting basic information Corollary 8: If you disagree with the premise of a discussion group, don't waste the time and bandwidth of the members by telling them how stupid they are.Just stay away Corollary 9: Conserve bandwidth when you retrieve information from a host or server. Rule 5. Make yourself look good online. Corollary 1: Check grammar and spelling before you post Corollary 2: Know what you're talking about and make sense Corollary 3: Don't post flame-bait Rule 6. Share expert knowledge. Corollary 1: Offer answers and help to people who ask questions on discussion groups Corollary 2: If you've received email answers to a posted question, summarize them and post the summary to the discussion group. Rule 7. Help keep flame wars under control. Corollary 1: Don't respond to flame-bait Corollary 2: Don't post spelling or grammar flames Corollary 3: If you've posted flame-bait or perpetuated a flame war, apologize Rule 8. Respect other people's privacy. - Don't read other people's private email. Rule 9. Don't abuse your power. - The more power you have, the more important it is that you use it well Rule 10. Be forgiving of other people's mistakes. CONTEXTUALIZED ONLINE SEARCH AND RESEARCH SKILLS

- Online search is the process of interactively searching for and retrieving requested information via a computer from databases that are online. Interactive searches became possible in the 1980s with the advent of faster databases and smart terminals. Advantages and Disadvantages Advantages: - Ability to obtain a large sample, which increases statistical power - Data is automatically coded so no data entry errors - Reduced cost of conducting research Disadvantages: Online is not totally secure and theft is one of the numerous danger it poses, researchers personal information is at risk of being access by rogue persons. - Some of the materials on the internet have not been evaluated by experts or thoroughly screened - Lack of accreditation and low quality
RESEARCH SKILLS “Research” sometimes just means finding out information about a topic.You can certainly develop advanced information retrieval skills in Working with Sources. However, in specific understandings of “research” carry a lot of weight. The classic definition is that “research” leads to an original contribution to knowledge in a particular field of inquiry by defining an important question or problem and then answering or solving it in a systematic way. - So you will need to read on to develop a relevant understanding of what research means in your subject. - Research skills can be anything from looking at competitors and seeing what they do well to producing a written report on how your department could work better. Doing research in the world of work is all about stepping back from your day-to-day work and looking at ways you can improve. Important aspects of research: - Research design covers the key issues in developing a successful research project. - Research methods takes you to resources on essential techniques for carrying out convincing research. - Working with data will provide resources on the use of statistics and other numerical skills in research. Improving Your Research Skills Online 1. Know your sources. Make sure to find the most reliable information which can be found in multiple sources or, better, to have the original source. 2. Use your web browser properly. Know the capabilities of your preferred browser to help make your search faster and easier. 3. Organize your bookmarks. It is to organize the links you have marked. 4. Learn to use advanced search engines. Practice using advanced search techniques which are available in Google. 5. Follow the web. Follow the web information in the web. Just make sure to read and be critical in every link you click. SIX STRATEGIES THAT CAN HELP ONLINE STUDENTS PRODUCE STRONGER RESEARCH. 1. Contact a librarian before getting stuck sifting through piles of online information. 2. Consider that when in doubt, it's wiser to over-cite sources than risk plagiarism. 3. Use Google and other reliable resources at the beginning of a research process, not the end. 4. Don't think that the Web is your only source of information. 5. Understand the professor's expectations for citation format. 6. Understand why professors still assign research projects. Some examples of research skills that you may have include: 1. Report writing. 2. Analyzing lots of information from different sources. 3. Finding information off the internet. 4. Critical thinking. CHAPTER 2 APPLIED PRODUCTIVITY TOOLS Productivity Tools - It is a tools that can be a freeware or shareware. Freeware - is copyrighted, which can be used for free and for an unlimited time. Shareware - is a commercial software that is copyrighted, which can be copied for trial but needs to be purchased for continued use. Advanced Techniques Using Microsoft Word Microsoft Office Word

- One of the software of Microsoft Office 2013 suite. - Offers a set of tools that is compared to its previous versions. - Along with its new features are advanced techniques including hyperlinks, macros and mail merge. Hyperlink
- A link that will direct you to another page or part of the same document. Creating a Hyperlink to an Existing Document - Suppose you are to link a part of your document to an existing document. - Click your mouse on the location in the document where you want to insert the hyperlink. - On the Insert Tab, click the Hyperlink button on the Links group. - On the Insert Hyperlink dialog box, click Existing File or Web Page and then select the File name where the source file is located and then hyperlink will be created on your document. - Press Ctrl+ click on the Hyperlink to open the linked file. Mail Merge
- Is a useful tool that allows you to quickly produce and send information, newsletter, resumes, or brochures to many people. Creating a Mail Merge 1. Open the word document that you want to Mail Merge. 2. On the Ribbon, click the Mailings tab, go to the Start Mail Merge group and click Start Mail Merge and select Step by Step Mail Merge Wizard. 3. The task pane will show the Mail Merge steps 1 to 6. PowerPoint

- It allows you to create slide show presentations wherein you can format the texts and images, adding also animations and other multimedia components interactively. Excel

- One of the applications created by Microsoft, used to simulate a paper worksheet.
- It is composed of cells that are represented in rows and columns design to perform basic arithmetic operations. - Widely used in accounting and financial applications, as well as statistics and engineering calculations. The following are the common Excel Functions: = SUM – Calculates the sum of the values of a range of cells = AVERAGE – Calculates the arithmetic mean of a range of cells = MAX - Gives the maximum value in a range of cells = MIN - Gives the minimum value in a range of cells = COUNT - Counts the number of cells in a range of cells BENIFITS OF ONLINE SOFTWARE Convenience - The applications should be intuitive and easy to use to ensure everyone can use them without spending a lot of time learning how. Scalability - The applications should be able to be used in all areas of your business and also work effectively no matter how much demand there is to use them or how much your business grows. Safety - All the applications should be safe to use with all existing systems and should have the ability to fully integrate with all other software and not inhibit the workers ability to do their job. Sustainability - All consumer-based software should be flexible and adaptable to have the ability to last for up to 10 years, but they must be able to expand functionally with other developments in software and operating systems. PRINCIPLES OF GRAPHICS AND DESIGN BALANCE UNITY MOVEMENT REPITITION PROXIMITY CONTRAST WHITESPACE BALANCE

- Describes the placement of elements of equal weight on the page. MOVEMENT

- Describes the flow of elements on the page.
1 note
·
View note
Text
Why Virtual Reality May Be Our New Reality | Music and Its Digital Past, Present, and Future

Pre-quarantine predictions about the music industry painted a picture of one its best years yet. Such predictions were overflowing with promising new releases, sold out tours, and unique marriages of music and technology just beyond horizon. While coronavirus has shifted many a release schedule and left tours and festivals in a state of indefinite hiatus, alliances between music and technology remain increasingly vital, both in the name of technological progress, and, more recently, as a supplement to the live experience industry inhibited by the ongoing pandemic.
Discussions of technology in relation to music range from video games to virtual reality. Travis Scott and Marshmello both held concerts in Fortnite, Paul McCartney had a hand in the Destiny soundtrack, and Ariana Grande had both a song and a playable character in Final Fantasy Brave Exvius. Billie Eilish, Panic! At The Disco, Imagine Dragons and many others have also made their concerts available to stream in virtual reality. But there is another game changing intersection between the music and digital world that challenges not only how we experience music, but also how music is created. It’s called the vocaloid.
Early versions of software designed to synthesize human speech have existed since the late 1930s. Fast forward about two decades, the earliest form of synthesized singing had arrived. The IBM 7094, installed in 1962, was the first “computer to sing,” singing a song called “Daisy Bell” by Harry Dacre (the technological advancement would go on to inspire a similar scene in Stanley Kubrick’s 1968 sci-fi epic, 2001: A Space Odyssey). Since then, vocal synthesis has come a long way, and has also been marked by a different name.
youtube
The year was 2000. The place was Barcelona, Spain. Hideki Kenmochi developed the vocaloid, a voice synthesis software short for vocal android, which was designed to emulate singing. Commercially adapted by Yamaha and distributed by Crytpon Future Media in 2004, the company launched the first Vocaloid and initially called it “Daisy,” after IBM 7094, but due to copyright issues, settled on “Vocaloid 1.” This is where the game changing begins.
Using this first iteration of the software, Yamaha created Meiko, an animated persona designed to serve as the face to the sampled voice of singer Meiko Haigō, with both English and Japanese vocals. Meiko was followed by the release of Kaito, a male vocaloid, two years later. As time went on, the software became increasingly realistic.
In 2007, Yamaha launched Vocaloid 2, which Crypton Future Media used to bring us Hatsune Miku, a vocaloid persona that quickly went from software to stardom. With long turquoise hair and a heavily anime-inspired look, Miku was sampled from voice actress Saki Fujita, and her Japanese name fittingly translates to “the first sound of the future.”
Hatsune Miku is the first vocaloid to top the charts, has been involved in countless advertisement campaigns, such as those with Google Chrome, Toyota and Louis Vuitton, and opened for Lady Gaga’s ArtPop Tour in 2014. And if it were not for COVID-19, 2020 would have seen her make her Coachella debut. Though other vocaloids have since been created, none have reached the full cultural immersion achieved by Hatsune Miku. Hatsune Miku is now not only the face of vocaloid but also one of Japan’s most recognizable pop stars. Though Miku’s virtual existence isn’t palpable, her real-life fandom and influence certainly are. So much so that in 2018, Akihiko Kondo formally “married” the vocaloid, making for the ultimate ultramodern love story.
youtube
But it doesn’t stop there. In 2016, a transmedia startup co-founded by Trevor McFedries called Brud created Miquela Sousa, the first computer-generated social media influencer, programmed as a half-Brazilian, half-Spanish bisexual 19-year-old from LA. With 2.4 million Instagram followers, the mysteriously charming avatar is an ideal fit for advertisers. Miquela did an Instagram takeover for Prada and a Calvin Klein ad with Bella Hadid, in which Hadid, too, was animated, prompting a fascinating elusiveness.
Miquela is also openly progressive, showing support for Black Lives Matter and other movements. Her creators have noted their intention to help promote social justice through their pioneering of virtual personalities–and talented ones, at that. Miquela is not only an influencer with multiple brand partnerships but also a musician who has collaborated with Lauv and Baauer and is now signed to CAA.
McFedries, Miquela’s manager and one of her creators, is not new to the music industry, having been a DJ, radio show host, director and manager himself. He also created two other virtual personas, Blawko and Bermuda, who are friends with Miquela and whose frequent dramas are created and conveyed through their social media and Youtube vlogs, like a relatable, sympathy-inducing reality show. The three unique virtual influencers portray an obvious self-awareness that they are not human, addressing themselves as robots. Despite not having a true pulse, the self-awareness of these bots certainly shows they have a pulse for the culture, for humor and for connection. So much so that Miquela was listed as one of Time Magazine’s “Most Influential People on the Internet” in 2018, alongside Rihanna and, unfortunately, President Trump.
The creation of both Hatsune Miku and Miquela sparked a paradigm shift in the role of technology in music, an intersection that will lay the foundation for the potential digital future. But this article taps only the tip of the iceberg. From self-driving cars to self-writing songs, the potentially unpredictable nature of innovation sparks anxiety in some and optimism in others.
Unlocking new worlds of music technology can equip new levels of human creativity. But some may wonder, where the line is drawn when humans are not the only ones making art? Technology is meant to be a resource for the artist, not a replacement. On the other hand, who is to say an artificial collaborator is not a tool? Who is to say the creators and drivers of these vocaloids or virtual artists are not artists themselves?
Perhaps the increased role of technology will bring a heightened appreciation for the human elements. Perhaps all this live streaming via social media will create a heightened appreciation for the physically live experience while also giving us new tools to reach people around the world. Similarly, while vocaloid hologram performances allow us to experience music in a new way, perhaps this will reinforce an appreciation for the live, human performer.
youtube
Fear is an inevitable part of progress, as people before us feared the advent of trains, television, and the internet. Technological progress does not exist in a vacuum, as we have witnessed its challenges but also its immense rewards. Ultimately, we are veterans in experiencing the result of groundbreaking technologies sewing their way into our everyday lives, and adapting accordingly. As technology expands exponentially, we are still only at the cusp. (If you don’t believe me, just google the quantum computer IBM has sitting in their refrigerated basement).
Though the future can be daunting, it is also exciting. Having Miquela in a Calvin Klein ad in which Bella Hadid, a familiar face, was also animated is like opening a portal between the virtual and real world (like the princess in Enchanted jumping out of the sewer, morphing from cartoon to human). Bonding with artificial characters is not new. But this portal allows virtual influencers to become a notable real part of our reality as they themselves claim to be part of it, whether via music, fashion or fandom (or marriage, in the case of Miku’s now supposed husband, Akihiko Kondo).
The newest Miku update is Vocaloid 5, launched in 2018 and now more adaptable across formats and also available in Chinese, Spanish and Korean. As she shared on her instagram, Miquela dropped two singles this year and is still seeing her friends Blawko and Bermuda.
With coronavirus still very much a reality, the longing for a return to normal is absolutely understandable; however, with so much of our world changing, our world may never return to its pre-pandemic state. Instead, it is likely to return to a new normal, in which live streaming and virtual reality are not supplements for the live experience but directly part of it. Whether virtual musicians like Hatsune Miku or Miquela are a momentary fascination of our present or a glimpse into a very real future, one thing remains certain. Our potential digital future is much closer than we think.
3 notes
·
View notes