#ransomware data recovery software
Explore tagged Tumblr posts
Text
Preventative IT Maintenance: Keeping Your Business Running Smoothly

With technology moving forward so fast, your business can’t operate without it. Computers, servers, cloud systems and software platforms have to be running smoothly to keep your team productive, defend confidential information and make sure customers receive a good experience.
Unfortunately, IT systems don’t manage themselves without attention.
This is why we need preventative IT maintenance. Regular car servicing makes sure your car avoids breakdowns and preventative IT support does the same for your systems. Here at Image IT, we know that companies who focus on IT before issues arise benefit a lot. We’ll now look at what preventative maintenance means and understand why it helps your business run smoothly.
What Does Preventative IT Maintenance Mean?
Taking care of your IT infrastructure ahead of time is called preventative maintenance. With preventative maintenance, you take action to make sure your systems are in good shape all the time, so you don’t have to rush to solve emergencies.
Such tasks refer to:
Tracking how the system is running
Putting security patches and new versions of the software into use
Regularly using antivirus and malware software
Testing the use of backup options
Updating both your device’s drivers and firmware
Checking the configurations for firewalls and networks
Exchanging ageing equipment to prevent any breakdowns
At Image IT, we set up specialized maintenance services that guarantee your technology remains in top condition and reduces the chance of risks and downtime.
Why Taking Care of Problems in Advance Is Crucial for Companies in Ireland
1. Minimize any time when your business is not working effectively.
Problems with your IT systems such as servers failing, networks breaking or bugs in software, may bring your work to a halt and cost you in both time and money. Doing preventative maintenance lets you catch and manage issues early and this means your business avoids the stress of dealing with major problems.
If a server begins to overheat, it’s possible to handle the issue before it crashes, so you won’t have to deal with expensive downtime and loss of data.
2. Prevent or Stop Cyber Attacks
More and more, businesses in Ireland are facing cyberattacks, most often small and medium-sized companies. Many attackers use old software, unpatched versions and networks that have not been properly set up.
Ongoing upkeep of security tools such as firewalls, antivirus software and system updates, makes it much less likely for your system to become a victim of ransomware, phishing or a data breach.
3. Increase the Lifespan of IT Assets
Just as changing the oil in your car lengthens its engine’s lifespan, looking after your IT equipment in the same way will help it work longer. Regularly taking care of computers stops them from wearing out and prevents too many replacements.
4. Raise the effectiveness of your staff.
This kind of slow work is frustrating and influences how your team feels about their work. If technology runs smoothly, your team won’t have to worry about systems or spend time finding IT solutions.
5. With time, the cost of IT will decrease.
Though it might feel like a pricey addition, upfront maintenance helps save money and prevents serious IT problems. One data breach, meeting replacement or lasting period of downtime can often be more expensive than all your ISP’s services put together.
Important Parts of a Well-Made IT Maintenance Plan
We create preventative maintenance strategies for your business that fit its individual requirements at Image IT. The method we use is:
We watch your systems around the clock.
We watch over your systems around the clock, spotting problems early and fixing them so they don’t impact your work.
Timely Updates and Patch Upgrades
We make sure your operating systems, applications and antivirus are always running on the latest versions.
Test the backup and recovery of your data.
We ensure your backups are properly configured and we regularly perform tests to see how fast you can recover data.
You can do a Network Health Check here.
We examine your network for good speed, serious security flaws and technology issues to confirm your system operates safely and properly.
Managing Assets and Deciding on Their Life
We watch over your equipment and make sure you can update your technology before it starts causing issues.
Support from the users and helpdesk
If your team has any IT questions or concerns, our friendly team is there to lend a non-technical helping hand.
Why Is Image IT a Great Solution?
Operating out of North Dublin, Image IT has been supporting company’s in Ireland for about 15 years. Our knowledgable team delivers helpful, consistent and friendly IT assistance to the companies here in New Zealand.
We are dedicated to forming long-term relationships with clients so we can do more than just address issues; we can help avoid them.
You will gain the following benefits when you work with us:
Transparent pricing
A quick response from the team
Customized maintenance services
Expert opinions offered in a personal way
If you have just a few devices or a complex IT structure, our solutions are designed to match your requirements and your budget.
Benefits You Can See in Life: An Example
There were many issues at one of our clients, a small financial services firm in Dublin, involving downtime in the network and software that was past its update. Following their sign up for our preventative maintenance, we set up a monitoring system, cleaned their network and ran scheduled updates.
The result? A 90% drop in IT issues reported by staff, faster systems, and peace of mind for their management team knowing their data and systems were protected.
Your Next Step: Secure Your Business with Preventative IT Support
Don’t wait for a system failure, data breach, or productivity drop to remind you of your IT vulnerabilities. Preventative maintenance is one of the smartest investments you can make in your business.
Let Image IT take the stress out of managing your technology — so you can focus on what you do best.
2 notes
·
View notes
Text
Essential Cybersecurity Measures for Organizational Network Protection

In today's interconnected world, a robust cybersecurity strategy is no longer a luxury, but a necessity for organizations of all sizes. A strong defense against ever-evolving cyber threats is paramount to protecting sensitive data, maintaining business continuity, and preserving reputation. This blog explores critical cybersecurity organizational network protection measures.
Understanding the Threat Landscape
Before diving into protective measures, it's crucial to understand the threats organizations face. These include:
Malware: Viruses, ransomware, and spyware designed to damage or steal data.
Phishing: Deceptive emails or messages tricking individuals into revealing sensitive information.
Denial-of-Service (DoS) Attacks: Overwhelming networks with traffic, disrupting services.
Insider Threats: Malicious or accidental actions by employees or other insiders.
Data Breaches: Unauthorized access and exfiltration of sensitive data.
Essential Cybersecurity Measures
A layered approach is key to effective network protection. Here are some crucial measures:
Firewall Implementation: Firewalls act as a barrier between your network and the outside world, controlling incoming and outgoing traffic based on predefined rules. Regularly updating firewall rules is critical.
Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activity, alerting administrators to potential threats and even automatically blocking malicious traffic.
Antivirus and Anti-malware Software: Deploying robust antivirus and anti-malware software on all endpoints (computers, servers, mobile devices) is essential to detect and remove malicious software. Regular updates are crucial.
Strong Password Policies and Multi-Factor Authentication (MFA): Enforcing strong, unique passwords and implementing MFA adds an extra layer of security, making it significantly harder for attackers to gain access even if a password is compromised.
Regular Security Audits and Vulnerability Assessments: Regularly assessing your network for vulnerabilities and conducting security audits helps identify weaknesses before they can be exploited.
Employee Training and Awareness: Human error is a major factor in many security breaches. Regular cybersecurity awareness training for all employees is vital. This training should cover topics like phishing awareness, password security, and safe browsing practices.
Data Encryption: Encrypting sensitive data, both in transit and at rest, protects it even if a breach occurs.
Regular Backups and Disaster Recovery Planning: Regularly backing up critical data and having a disaster recovery plan in place ensures that you can recover from a cyberattack or other disaster.
Network Segmentation: Dividing your network into smaller, isolated segments limits the impact of a breach. If one segment is compromised, the others remain protected.
Incident Response Plan: Having a well-defined incident response plan in place allows you to react quickly and effectively to a security incident, minimizing damage and downtime.
Building a Cybersecurity Culture
Effective cybersecurity is not just about technology; it's also about people and processes. Building a strong cybersecurity culture within your organization is crucial. This involves:
Leadership Buy-in: Securing support from top management is essential for allocating resources and prioritizing cybersecurity.
Open Communication: Encouraging employees to report suspicious activity without fear of reprisal.
Continuous Improvement: Regularly reviewing and updating your cybersecurity policies and procedures to stay ahead of evolving threats.
Xaltius Academy's Cybersecurity Course: Your Partner in Network Protection
Navigating the complex world of cybersecurity can be challenging. Xaltius Academy's cybersecurity course provides comprehensive training and equips you with the knowledge and skills needed to protect your organization's network. Our expert instructors and hands-on labs will prepare you to effectively implement and manage these critical security measures. Invest in your cybersecurity future and safeguard your organization's valuable assets.
Conclusion
Protecting your organization's network requires a proactive and multi-faceted approach. By implementing these essential cybersecurity measures and fostering a strong security culture, you can significantly reduce your risk of falling victim to cyberattacks and safeguard your organization's future.
2 notes
·
View notes
Text
Understanding Ransomware: A Guide for Small Businesses
Ransomware is a malicious software that restricts access to your device or data until a ransom is paid. In this article, we explore how ransomware enters your system, how it works, and how to prevent attacks. A ransomware attack occurs when malware prevents access to your device or data until a ransom is paid. Attackers may threaten to publish data if the ransom is not paid. Ransomware can be locker ransomware, which locks access, or crypto ransomware, which encrypts files. Ransomware usually enters a device, assesses critical data, encrypts files, and demands a ransom. Paying the ransom doesn't guarantee recovery, so it's not recommended. Historical ransomware attacks include CryptoLocker, CryptoWall, Locky, WannaCry, NotPetya, and more. To prevent ransomware, you can have good network policies, secure servers, backup data offline and online, and encourage safe online behavior. Installing security software like antivirus, firewall, and email filtering can also help. Advanced strategies include ATP, email filtering, and security audits. In case of a ransomware infection, isolate the device, assess damage, check for a decryption key, and restore from backups. Seek professional help for recovery. Immediate actions post-infection include isolation, incident response activation, legal compliance, and stakeholder communication. Ransomware can get on your device through spam emails, phishing, pop-ups, pirated software, weak passwords, and more. Attackers prefer cryptocurrency payments for anonymity. Ransomware can spread through Wi-Fi, infecting all connected devices. Protect yourself from ransomware by following the prevention strategies mentioned above. Stay safe online and be cautious of suspicious emails, links, and downloads. And remember, it's crucial to have backups and a plan in case of a ransomware attack. #StartupBusiness #Businesses #Guide #howdoesransomwarework #Ransomware #ransomwareattack #Small #Understanding #whatisaransomware #whatisaransomwareattack #whatisransomware https://tinyurl.com/228z9vpf
#Businesses#Guide#how does ransomware work#Ransomware#ransomware attack#Small#Understanding#what is a ransomware#what is a ransomware attack#what is ransomware
2 notes
·
View notes
Text
Trusted Cyber Crime Lawyer in Noida
Trusted Cyber Crime Lawyer in Noida
The advancement of digital technology has transformed how we communicate, transact, and work. However, it has also given rise to cybercrime — a pressing issue that affects individuals, businesses, and governments worldwide. In Noida, a bustling hub of technology and business, cybercrime is an ever-present threat. If you find yourself a victim of cybercrime, Advocate Deepak, a leading trusted cyber crime lawyer in Noida, is here to provide expert legal guidance and representation.
This article explores what cybercrime is, its types, safety tips to prevent it, and why Advocate Deepak is the best choice for tackling cybercrime cases in Noida.

What is Cyber Crime?
Cybercrime refers to illegal activities carried out using computers, digital devices, or networks. These crimes exploit technological vulnerabilities and target individuals, organizations, or governments. Cybercrime can cause financial losses, emotional distress, and reputational damage.
Understanding the nature and types of cybercrime is crucial for prevention and response.
Types of Cyber Crime
Cybercrime encompasses a wide range of activities, including but not limited to:
1. Hacking
Hacking involves unauthorized access to computer systems or networks. Hackers often aim to steal sensitive information, disrupt operations, or cause harm.
2. Phishing
Phishing is a fraudulent practice where attackers trick individuals into revealing personal information, such as passwords or credit card details, through fake emails or websites.
3. Identity Theft
Identity theft occurs when cybercriminals steal personal information to impersonate someone for financial or criminal purposes.
4. Ransomware Attacks
Ransomware is malicious software that encrypts a victim’s data and demands payment for its release. These attacks can paralyze businesses and organizations.
5. Cyberstalking
Cyberstalking involves the use of digital platforms to harass, intimidate, or monitor individuals, causing psychological distress.
6. Online Fraud
Online fraud includes scams like fake e-commerce websites, Ponzi schemes, and fraudulent investment opportunities.
7. Malware Attacks
Malware refers to software designed to damage, disrupt, or gain unauthorized access to systems. Common types include viruses, worms, and spyware.
8. Denial of Service (DoS) Attacks
DoS attacks flood a network or server with excessive requests, rendering it inaccessible to legitimate users.
9. Social Engineering
Social engineering manipulates individuals into divulging confidential information by exploiting trust or creating urgency.
10. Cyberbullying
Cyberbullying involves using digital platforms to threaten, humiliate, or harm individuals, particularly vulnerable groups like children and teenagers.
Safety Tips to Prevent Cyber Crime
Preventing cybercrime requires a proactive and informed approach. Here are some essential tips to enhance your cybersecurity:
1. Use Strong Passwords
Create complex passwords with a mix of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable information like birthdays or names.
2. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security by requiring a secondary verification step, such as a code sent to your phone.
3. Be Wary of Phishing Attempts
Verify the authenticity of emails and messages before clicking on links or providing personal information. Look for signs of phishing, such as suspicious sender addresses or grammatical errors.
4. Keep Software Updated
Regularly update your operating system, applications, and antivirus software to patch vulnerabilities and enhance security.
5. Secure Your Wi-Fi Network
Protect your home or office Wi-Fi with strong passwords and encryption. Avoid using public Wi-Fi for sensitive transactions.
6. Back Up Data Regularly
Regularly back up important files to external drives or cloud storage. This ensures data recovery in case of ransomware attacks or system failures.
7. Monitor Financial Transactions
Review bank and credit card statements frequently to detect unauthorized transactions. Report any discrepancies immediately.
8. Limit Sharing Personal Information Online
Be cautious about sharing personal details on social media platforms. Cybercriminals can use this information for identity theft or social engineering attacks.
9. Install Reliable Security Software
Use reputable antivirus and anti-malware software to detect and prevent threats. Ensure the software is updated regularly.
10. Educate Yourself and Your Family
Stay informed about the latest cyber threats and educate your family members, especially children, about safe online practices.
Advocate Deepak: Your Trusted Cyber Crime Lawyer in Noida
When dealing with cybercrime, having a skilled and experienced lawyer is crucial. Advocate Deepak is a leading trusted cyber crime lawyer in Noida, specializing in providing legal solutions for cybercrime victims.

Why Choose Advocate Deepak?
Expertise in Cyber Laws Advocate Deepak possesses in-depth knowledge of India’s Information Technology Act and other relevant laws. This expertise enables him to handle complex cybercrime cases effectively.
Personalized Legal Strategies Every case is unique. Advocate Deepak provides tailored legal strategies to address the specific needs of his clients, ensuring the best possible outcomes.
Proficient Evidence Management Cybercrime cases often rely on digital evidence, such as IP logs, emails, or financial records. Advocate Deepak excels in collecting, analyzing, and presenting this evidence in court.
Proven Track Record With a history of successfully resolving cybercrime cases, Advocate Deepak has earned the trust and respect of his clients in Noida.
Preventive Legal Advice Beyond litigation, Advocate Deepak offers advice to help clients mitigate the risk of future cybercrimes through robust cybersecurity measures.
Services Offered by Advocate Deepak
Representation in cybercrime cases
Assistance with filing complaints with cybercrime cells
Legal support for hacking, phishing, identity theft, and ransomware cases
Guidance on data protection and privacy laws
Advisory on cybersecurity compliance for businesses
In today’s digital age, cybercrime poses a significant threat to individuals and organizations alike. Whether it’s identity theft, hacking, or online fraud, the consequences can be devastating. Advocate Deepak, a trusted cyber crime lawyer in Noida, is dedicated to helping victims navigate the complexities of cyber laws and achieve justice.
By understanding the types of cybercrime and implementing the safety tips provided, you can significantly reduce your risk of becoming a victim. If you do encounter a cybercrime issue, Advocate Deepak’s expertise and commitment make him the ideal choice to handle your case effectively. Protect your digital life by staying informed, vigilant, and prepared to seek professional legal assistance when needed.
2 notes
·
View notes
Text
Synology Data Recovery: A Comprehensive Guide
Synology is renowned for its NAS (Network Attached Storage) devices, which offer robust data storage solutions for both personal and business use. Despite their reliability and advanced features, data loss can still occur due to various reasons. This guide provides a comprehensive overview of Synology data recovery, covering the causes of data loss, the steps to recover lost data, and best practices to safeguard your data.
Understanding Synology NAS
Synology NAS devices are designed to provide a centralized and accessible storage solution with features such as RAID (Redundant Array of Independent Disks) configurations, data protection, and easy-to-use interfaces. They support multiple users and applications, making them a versatile choice for data storage and management.
Common Causes of Data Loss
Data loss in Synology NAS devices can result from various scenarios, including:
1. Hardware Failures
Disk Failure: Hard drives can fail due to age, physical damage, or manufacturing defects.
Power Surges: Electrical surges can damage the Synology NAS’s internal components.
Overheating: Inadequate cooling can lead to overheating, causing hardware malfunctions.
2. Software Issues
Firmware Corruption: Problems during firmware updates or bugs can lead to data corruption.
File System Errors: Corrupt file systems can make data inaccessible.
3. Human Error
Accidental Deletion: Users can mistakenly delete important files or entire volumes.
Misconfiguration: Incorrect setup or configuration changes can lead to data loss.
4. Malicious Attacks
Ransomware: Malware can encrypt data, making it inaccessible until a ransom is paid.
Viruses: Malicious software can corrupt or delete data.
Steps for Synology Data Recovery
When faced with data loss on a Synology NAS device, it’s crucial to follow a structured approach to maximize recovery chances. Here are the steps to follow:
1. Stop Using the Device
Immediately stop using the Synology NAS to prevent further data overwriting. Continuing to use the device can reduce the likelihood of successful data recovery.
2. Diagnose the Problem
Identify the cause of the data loss. Understanding whether the issue is due to hardware failure, software problems, human error, or a malicious attack will help determine the best recovery method.
3. Check Backups
Before attempting data recovery, check if there are any recent backups. Regular backups can save time and effort in the recovery process. If backups are available, restore the lost data from them.
4. Use Data Recovery Software
For minor data loss issues, data recovery software can be an effective solution. Several reliable tools support Synology NAS devices:
R-Studio: A powerful tool for recovering data from various storage devices, including Synology NAS.
EaseUS Data Recovery Wizard: User-friendly software that can recover files lost due to deletion, formatting, or system crashes.
Stellar Data Recovery: Known for its robust recovery capabilities, supporting Synology NAS and RAID configurations.
5. Consult Professional Data Recovery Services
For severe data loss scenarios, such as hardware failures or extensive corruption, it is advisable to seek help from professional data recovery services. These experts have the tools and knowledge to recover data from damaged Synology NAS devices. Some reputable data recovery companies include:
DriveSavers Data Recovery: Offers specialized services for Synology and other RAID systems, with a high success rate.
Ontrack Data Recovery: Known for its expertise in NAS and RAID recovery, Ontrack provides comprehensive solutions for Synology devices.
Gillware Data Recovery: Provides professional data recovery services, specializing in complex RAID and NAS systems.
6. Prevent Future Data Loss
After successfully recovering your data, implement measures to prevent future data loss:
Regular Backups: Schedule frequent backups to ensure you have up-to-date copies of your data.
Firmware Updates: Keep your Synology firmware updated to protect against bugs and vulnerabilities.
Surge Protectors: Use surge protectors to safeguard against electrical surges.
Proper Ventilation: Ensure adequate ventilation and cooling to prevent overheating.
Conclusion
Data loss on Synology NAS devices, though distressing, can often be remedied with the right approach. By understanding the common causes of data loss and following a systematic recovery process, you can effectively retrieve lost data. Utilize reliable data recovery software or consult professional services for severe cases. Additionally, implementing preventive measures will help safeguard your data against future loss, ensuring that your Synology NAS device continues to serve as a reliable data storage solution.
2 notes
·
View notes
Text
Unveiling the Mystery: How Cryptocurrency Tracing Can Expose Fraud
Cryptocurrency tracing refers to the process of tracking and analyzing cryptocurrency transactions on the blockchain to uncover fraudulent activity. In this guide, we'll explore how cryptocurrency tracing can be used to expose fraud in the world of digital currencies.
Understanding Cryptocurrency Fraud
Types of Cryptocurrency Fraud: Cryptocurrency fraud encompasses various schemes, including Ponzi schemes, phishing attacks, exchange hacks, and initial coin offering (ICO) scams.
Common Tactics Used by Fraudsters: Fraudsters use tactics such as fake investment schemes, fraudulent ICOs, ransomware attacks, and pump-and-dump schemes to deceive and defraud unsuspecting victims.
The Role of Cryptocurrency Tracing in Exposing Fraud
Tracing Transactions on the Blockchain: Cryptocurrency transactions are recorded on the blockchain, providing a transparent and immutable ledger that can be analyzed to trace the flow of funds and identify fraudulent activity.
Identifying Suspicious Activity Patterns: Through blockchain analysis, suspicious activity patterns, such as large transfers to unregistered exchanges or mixing services, can be identified and investigated further.
Tracking Stolen Funds: Cryptocurrency tracing can be used to track stolen funds from exchange hacks or fraudulent schemes, potentially leading to the recovery of stolen assets and prosecution of perpetrators.
Tools and Techniques for Cryptocurrency Tracing
Blockchain Analysis Software: Specialized software tools, such as blockchain explorers and analytics platforms, are used to analyze blockchain data and identify patterns of fraudulent activity.
Address Clustering: Address clustering techniques group together related cryptocurrency addresses to track the movement of funds across the blockchain.
Network Analysis: Network analysis tools help visualize the flow of funds between cryptocurrency addresses and identify connections between different entities involved in fraudulent activity.
Real-World Examples of Cryptocurrency Tracing
Silk Road Investigation: Law enforcement agencies successfully traced and seized millions of dollars' worth of Bitcoin used in illegal transactions on the Silk Road darknet marketplace.
Mt. Gox Hack Recovery: Through blockchain analysis, investigators were able to trace and recover a portion of the funds stolen in the infamous Mt. Gox exchange hack.
Challenges and Limitations of Cryptocurrency Tracing
Privacy Concerns: While blockchain transactions are pseudonymous, privacy coins and mixing services can obscure the traceability of funds, making it more challenging to trace fraudulent activity.
Complexity of Blockchain Analysis: Analyzing large volumes of blockchain data requires specialized skills and resources, making it difficult for law enforcement and regulatory agencies to keep up with evolving fraud schemes.
Jurisdictional Issues: Cryptocurrency transactions are borderless, posing challenges for law enforcement agencies to coordinate investigations and enforce regulations across jurisdictions.
The Future of Cryptocurrency Tracing
Advances in Blockchain Analytics: Continued advancements in blockchain analytics technology will enhance the ability to trace and analyze cryptocurrency transactions, improving detection and prevention of fraud.
Collaboration Between Industry and Law Enforcement: Increased collaboration between cryptocurrency exchanges, blockchain analytics firms, and law enforcement agencies will facilitate information sharing and enhance efforts to combat fraud.
Conclusion
Cryptocurrency tracing plays a vital role in exposing and combating fraud in the digital currency ecosystem. By leveraging blockchain analysis tools and techniques, investigators can trace the flow of funds, identify fraudulent activity, and hold perpetrators accountable. Despite challenges and limitations, continued innovation and collaboration hold promise for the future of cryptocurrency tracing in uncovering fraud and protecting investors.
2 notes
·
View notes
Text
Cyber Security Threat For Local Businesses
In this article learn the cyber security risks for Australian small businesses and how to protect your business future.
Australian local businesses face an ever-growing threat from cybercriminals. While many small business owners believe they're too insignificant to attract hackers, the reality is quite different. Cybercriminals often target smaller enterprises precisely because they tend to have weaker security measures in place. This blog post will explore the cyber dangers that small businesses in Australia may face and offer some practical advice on how to protect your livelihood.
The Growing Menace of Cyber Attacks
Why Small Businesses Are Targets
You might think your local shop or service isn't worth a hacker's time, but you'd be wrong. Cybercriminals often view small businesses as low-hanging fruit. Here's why:
1. Limited resources for cybersecurity
2. Less sophisticated defence systems
3. Valuable customer data
4. Potential gateway to larger partner companies
Common Cyber Threats to Watch Out For
Ransomware Blackcat Ransomware Gang.

Ransomware attacks have skyrocketed in recent years. These nasty pieces of software encrypt your data and demand payment for its release. For a small business, this can be devastating. Imagine losing access to your customer database or financial records overnight!
Phishing Scams
Phishing remains one of the most common ways cybercriminals gain access to your systems. They send seemingly legitimate emails that trick you or your staff into revealing sensitive information or downloading malware.
Data Breaches
Small businesses often store valuable customer data, making them prime targets for data breaches. A breach can result in hefty fines under Australian privacy laws and irreparable damage to your reputation.
Protecting Your Business from Cyber Threats
Essential Security Measures
1. **Use strong, unique passwords**: Implement a password policy that requires complex passwords and regular changes.
2. **Keep software updated**: Regularly update your operating systems, applications, and security software to patch vulnerabilities.
3. **Educate your staff**: Your employees are your first line of defence. Train them to recognise and report suspicious emails or activities.
Invest in Cybersecurity
While it might seem costly, investing in cybersecurity is far cheaper than dealing with the aftermath of an attack. Consider these steps:
1. **Install and maintain firewalls**: These act as a barrier between your internal network and external threats.
2. **Use encryption**: Encrypt sensitive data, especially if you store customer information.
3. **Implement multi-factor authentication**: This adds an extra layer of security beyond just passwords.
Create a Cybersecurity Plan
Don't wait for an attack to happen before you start thinking about cybersecurity. Develop a plan that includes:
1. Regular risk assessments
2. Incident response procedures
3. Data backup and recovery strategies
The Cost of Ignoring Cybersecurity
Failing to address cybersecurity can have dire consequences for your business:
1. Financial losses from theft or ransom payments
2. Damage to your reputation and loss of customer trust
3. Legal consequences for failing to protect customer data
4. Potential business closure due to inability to recover from an attack
Don't become another statistic in the growing list of small businesses crippled by cyber attacks. Take action today to protect your business, your customers, and your future.
Remember, in the digital age, cybersecurity isn't just an IT issue—it's a critical business concern that demands your attention and investment.
Kelly Hector creator of YouTube channel focused on cyber security risks and local marketing
#cyber security awareness#local business#digital marketing#cyberattack#cybersecurity#digitalworldvision.online
1 note
·
View note
Text
Top Tips to Build a Secure Website Backup Plans

Why Website Backup Is Crucial
Website backup is a critical aspect of website management, offering protection against various threats and ensuring smooth operations. Here's an in-depth look at why website backup is essential:
1. Protection Against Data Loss: During website development, frequent changes are made, including code modifications and content updates. Without proper backup, accidental deletions or code errors can lead to irrecoverable data loss.
2. Safeguarding Against Cyber Attacks: Malicious cyber attacks, including ransomware, pose a significant threat to websites. Regular backups provide a safety net, allowing businesses to restore their websites to a pre-attack state quickly.
3. Mitigating Risks of Hardware and Software Failures: Hardware failures or software glitches can occur unexpectedly, potentially resulting in data corruption or loss. Website backup ensures that data can be restored swiftly in such scenarios.
4. Facilitating Smoother Updates and Overhauls: Website updates and overhauls are inevitable for staying current and meeting evolving requirements. Having backups in place streamlines these processes by providing a fallback option in case of unforeseen issues.
Understanding Website Backup
What is Website Backup? Website backup involves creating duplicate copies of website data, including media, code, themes, and other elements, and storing them securely to prevent loss or damage.
Components of Website Backup:
Website Files: Includes all website data such as code files, media, plugins, and themes.
Databases: Backup of databases like MySQL or PostgreSQL, if utilized.
Email Sending: Backup of email forwarders and filters associated with the website.
Tips for Secure Website Backup Planning
1. Choose the Right Backup Frequency: Frequency depends on website traffic, update frequency, and content sensitivity.
2. Opt for Third-Party Backup Solutions: Consider factors like storage capacity, automation, security features, and user-friendliness.
3. Utilize Backup Plugins for WordPress: Plugins like UpdraftPlus, VaultPress, and others offer secure and automated backup solutions.
4. Maintain Offsite Backups: Store backups in remote data centers or cloud services for added security.
5. Test Your Backups: Regular testing ensures backup integrity and readiness for restoration.
6. Supplement Hosting Backup Services: While hosting providers offer backups, explore additional backup solutions for enhanced security and control.
7. Consider Manual Backups: Manual backups provide flexibility and control, especially for specific needs or scenarios.
8. Encrypt Backup Data: Encrypting backup files adds an extra layer of security, preventing unauthorized access.
9. Monitor Backup Processes: Regular monitoring helps identify issues promptly and ensures backup availability.
10. Implement Disaster Recovery Plans: Prepare for unforeseen events with comprehensive disaster recovery strategies.
Secure Website Backup Service with Servepoet
For comprehensive website backup solutions, consider CodeGuard Backup service, offering automated daily backups, robust encryption, and user-friendly management features.
Conclusion
Building a secure website backup plan is vital for protecting against data loss, cyber threats, and operational disruptions. By following best practices and leveraging reliable backup solutions, businesses can safeguard their websites and ensure continuity of operations.
#buy domain and hosting#best domain hosting service#domain hosting services#marketing#cloud vps providers#web hosting and server#shared web hosting
2 notes
·
View notes
Text
Ransomware Recovery Service Myths Debunked: What It Really Takes to Recover Data?
Ransomware attacks are no longer rare events—they’re a rapidly growing threat that businesses of all sizes face today. With hackers deploying sophisticated techniques to encrypt critical systems and demand payment, companies are turning to professional ransomware recovery services for help. However, many myths and misconceptions cloud the real value and process behind these services. This article exposes those myths and explains what it really takes to recover data from a ransomware attack.
Paying the Ransom Guarantees Full Data Recovery
One of the biggest misconceptions is that paying the ransom is a quick fix. Hackers promise to provide a decryption key after payment, but there’s no guarantee they’ll honor that deal. In fact, according to various cybersecurity studies, over 35% of businesses that paid still didn’t recover all their data. A ransomware recovery service helps businesses avoid the risky option of negotiating with cybercriminals. Instead, they use clean backups, system reconstruction techniques, and expert threat mitigation to recover and secure your data without feeding into illegal networks.
Only Large Corporations Need a Ransomware Recovery Service
Many small businesses think they're not targets, but ransomware attacks are indiscriminate. Small-to-midsize companies often have weaker security systems, making them ideal victims. Hackers know these organizations are more likely to pay quickly to avoid disruption. A ransomware recovery service is not just for enterprise-level companies. It’s designed for any organization that relies on digital systems—retailers, healthcare providers, law firms, education institutions, and even local service providers. Having a recovery plan in place could mean the difference between swift restoration and a total loss of operations.
Antivirus Software Alone Will Prevent Ransomware Attacks
While antivirus software is crucial, it's not foolproof. Many modern ransomware strains use sophisticated techniques like social engineering, zero-day vulnerabilities, and phishing emails to infiltrate systems. Relying solely on antivirus software creates a false sense of security. That’s where a ransomware recovery service comes in. They don't just clean up after an attack—they build a layered security approach, including real-time monitoring, vulnerability assessments, secure backups, and incident response plans. This comprehensive model is what keeps businesses resilient in the face of evolving threats.
Recovery Is Instant Once a Ransomware Recovery Service Is Hired
Hiring a ransomware recovery service does significantly reduce downtime—but it’s not as simple as flipping a switch. The recovery process involves:
Identifying the ransomware variant
Isolating infected systems
Recovering clean backups
Rebuilding and testing critical systems
Ensuring threat removal
Implementing preventative measures
Data Backups Alone Are Enough to Recover from Ransomware
Yes, backups are critical. But not all backups are secure or up-to-date. Hackers often target backup systems first to limit recovery options. In some cases, outdated or improperly configured backups make it impossible to restore everything quickly. A ransomware recovery service ensures that secure, offline, and redundant backups are implemented and regularly tested. They also evaluate the recovery time objectives (RTO) and recovery point objectives (RPO) to ensure that when disaster strikes, the organization can bounce back without missing vital data.
Any IT Team Can Handle Ransomware Recovery Internally
In-house IT teams play a crucial role in everyday system operations, but ransomware recovery is a specialized field. It involves advanced threat analysis, decryption strategies, legal compliance, forensic evaluation, and more. Most internal teams don’t have the training or resources to handle these challenges effectively.
Ransomware recovery service providers offer:
Experienced cybersecurity professionals
24/7 response teams
Industry-compliant data handling
Advanced recovery tools and scripts
Negotiation experience (when needed)
Once You Recover, You’re Safe from Future Ransomware Attacks
Recovering from one ransomware incident does not guarantee immunity. In fact, organizations that have been attacked once are often targeted again—especially if recovery wasn’t handled professionally and vulnerabilities were left unpatched. A quality ransomware recovery service doesn’t just recover your data—they help fortify your digital infrastructure. Post-recovery services typically include:
Security audits
Employee training
Endpoint protection
Firewall upgrades
Ongoing monitoring
Conclusion
Recovering from a ransomware attack is not just about decrypting files—it’s about restoring trust, functionality, and security. While myths about quick fixes, self-recovery, and ransom payments persist, the reality is far more complex. A ransomware recovery service brings expertise, strategy, and peace of mind to the table. By addressing the immediate crisis, securing data, and implementing proactive defense mechanisms, these services protect your business both now and in the future. Don’t let misconceptions leave your organization vulnerable—trust professionals who know what it really takes to recover.
0 notes
Text
The Real Cost of a Cyber Attack—and How a Cybersecurity Expert Helps You Avoid It

In today’s hyperconnected world, data is currency, and that makes every business a potential target for cybercrime. From ransomware to phishing, cyber threats are not only increasing in volume but also sophistication. And the harsh reality? Even a prosperous company can be brought to its knees by a single successful cyberattack.
Many organizations underestimate the true cost of a cyber attack, assuming it’s limited to a temporary inconvenience or a one-time loss. In truth, the financial, operational, and reputational damage can be staggering—and often irreversible.
As a result, having a cybersecurity expert is now a necessity. It's a critical investment in the future of your business.
What Is a Cyber Attack?
Any attempt by criminals to obtain unauthorized access to digital systems, networks, or data is referred to as a cyber attack. Common types include:
Phishing attacks
Ransomware
DDoS (Distributed Denial of Service)
Malware infections
Credential theft
Zero-day exploits
These attacks can target businesses of all sizes, across all industries—no one is immune.
The Hidden Costs of a Cyber Attack
Let’s break down the true cost of a cyber attack beyond just money.
💰 1. Financial Losses
The average cost of a data breach worldwide is $4.45 million; however, in places like the U.S., this figure is lower, according to IBM's 2024 Cost of a Data Breach Report. In Australia, that number is even higher. These costs include:
Ransom payments (in case of ransomware attacks)
Digital Forensic Investigations
Legal fees and settlements
Regulatory fines and penalties
IT recovery costs
Downtime and lost revenue
And remember, insurance doesn’t always cover everything, especially if it’s proven that your security was inadequate.
🔐 2. Reputational Damage
Customer trust is fragile. A single breach can:
Erode consumer confidence
Lead to public relations crises
Result in lost customers and negative reviews
Damage long-term brand value
Would you stay at a hotel that leaked your credit card info? Or trust a financial app that lost your data?
⏳ 3. Downtime and Operational Disruption
A cyber attack often causes systems to go offline for hours, days, or even weeks. For some businesses, that’s the equivalent of closing their doors.
E-commerce sites lose sales
Manufacturers miss deadlines
Service-based companies lose clients
Employees can't access systems or data
Downtime is not just frustrating—it’s expensive.
⚖️ 4. Regulatory and Legal Consequences
Depending on your industry and region, data breaches can trigger legal consequences, especially if you fail to report them or lack proper safeguards.
You might face:
Investigations from regulatory bodies (like GDPR, HIPAA, or Australia’s Privacy Act)
Class action lawsuits from affected customers
Permanent damage to compliance certifications
Why Cybersecurity Experts Are Your First Line of Defense
The good news? This threat doesn't have to be faced by you alone.
A cybersecurity expert doesn’t just install antivirus software and walk away. They create a proactive defense strategy tailored to your business, continuously monitor for threats, and take fast action when risks emerge.
Here’s how they help prevent costly attacks:
1. Conducting Thorough Risk Assessments
Cybersecurity experts begin by understanding your unique threat landscape. They assess:
Data sensitivity levels
Infrastructure vulnerabilities
Employee behavior and access points
Third-party vendor risks
This helps you prioritize what needs the most protection and develop a layered defense plan.
2. Implementing Proactive Security Measures
Once risks are identified, cybersecurity professionals implement industry-best safeguards like:
Firewalls and intrusion detection systems
Endpoint protection
Data encryption and secure backups
Network segmentation
Zero-trust access controls
This ensures that even if one layer is breached, attackers can’t go further.
3. Continuous Monitoring and Threat Detection
Cybersecurity isn’t set-it-and-forget-it. Experts provide real-time monitoring to detect unusual activity, prevent zero-day exploits, and stop attacks before they escalate.
With AI-powered tools and 24/7 surveillance, they can instantly flag and respond to threats, minimizing downtime and damage.
4. Employee Training and Awareness
Did you realize that human mistake is the root cause of 90% of breaches?
Cybersecurity experts train your staff to recognize phishing attempts, use strong passwords, follow best practices, and respond correctly during incidents.
This builds a security-first culture—your best defense against social engineering attacks.
5. Incident Response and Recovery Planning
Incidents can still occur despite the strongest protection. That’s why experts create an incident response plan so your business knows exactly what to do if breached.
They help:
Isolate infected systems
Recover data from secure backups
Notify regulators and affected parties
Restore operations quickly
Analyze how the breach occurred
A fast, coordinated response can reduce the cost and impact significantly.
6. Ensuring Regulatory Compliance
Cybersecurity experts keep you up to date with changing laws and standards, like:
GDPR (EU)
HIPAA (Healthcare)
PCI DSS (Retail)
Australia's Privacy Act and Essential Eight (Gov & Business)
They’ll implement required controls, audit your processes, and prepare documentation—so you don’t get blindsided by fines.
7. Ongoing Strategy and Technology Upgrades
Cyber threats evolve. So should your defenses. Cybersecurity experts continuously refine their strategy, patch vulnerabilities, and upgrade technologies to stay ahead of attackers.
They also guide you in adopting new tools like:
Multi-factor authentication (MFA)
Cloud access security brokers (CASB)
SIEM solutions (Security Information and Event Management)
Penetration testing and red team exercises
How to Choose the Right Cybersecurity Expert
Not all cybersecurity professionals are the same. When hiring one (or outsourcing to a security firm), look for:
Certifications: CISSP, CEH, CompTIA Security+, etc.
Industry experience: Do they understand your business model?
Verified performance history: Request case studies or customer testimonials
24/7 monitoring and support
Custom, scalable solutions
Whether you need a one-time audit or a full-service managed security provider, the right expert will tailor their approach to your needs and budget.
Conclusion: Don’t Wait for a Breach to Act
Cyberattacks are now a "when" rather than a "maybe." And the longer you wait to invest in cybersecurity, the more exposed your business becomes.
The real cost of a cyber attack isn’t just financial—it’s the loss of trust, reputation, and future opportunity. But the good news? You can avoid all of this with the right protection in place.
Hiring a cybersecurity expert is one of the smartest decisions you can make. It’s not just about stopping threats—it’s about empowering your business to grow confidently in a digital world.
Be proactive. Be prepared. Be secure.
#cybersecurity expert#cybersecurity specialists#cybersecurity architect expert#microsoft cyber security expert#cybersecurity solutions
0 notes
Text
Why IT Support service is vital for Your Company?

IT support is essential in today's digital environment for maintaining seamless business operations, securing data, and increasing productivity. The following is why your company requires dependable IT assistance:
1. Reduces downtime and guarantees business continuity:
Rapid Troubleshooting: IT help solves technical challenges right away, avoiding extended downtime.
Continuous Monitoring: Identifies and fixes issues before they disrupt operations.
Backup & Disaster Recovery: Protects data against loss caused by system malfunctions, cyberattacks, or power outages.
2. Data protection and cybersecurity
Cyber Threat Protection – To safeguard against hacking and malware, IT teams employ firewalls, antivirus software, and security patches. Compliance and data encryption ensure that sensitive data is protected and adheres to legal requirements (e.g., PDPA, GDPR).
Stops ransomware and phishing assaults – IT help teaches staff members how to identify online threats and avoid security incidents.
3. Enhances output and efficiency
Improved Network & Systems – Ensures a fast, seamless online experience with few interruptions.
Software & Hardware Management – Maintains all systems current for optimal performance.
Remote & Hybrid Work Support - IT teams provide collaboration platforms, cloud solutions, and secure VPNs.
4. Enhanced ROI and Cost Reductions
Prevents Costly Downtime – Solves IT challenges before they turn into costly issues. Managed IT services are more cost-effective than employing full-time IT employees, which lowers the demand for in-house IT staff.
Enhances IT infrastructure by providing cost-effective solutions that are customized to your specific business needs.
5. Improves the client experience and customer service:
Maintains email, VoIP, chatbots, and CRM software for seamless customer interactions via reliable communication systems.
Faster Issue Resolution – Guarantees a prompt response to customer questions and requests for assistance.
Processing Payments Safely – IT teams use secure online transactions to safeguard customer information.
6. Potential for expansion and scalability
Facilitates Business Expansion – As your company expands, IT teams assist in enhancing cloud storage, cybersecurity, and systems.
Adopts New Technologies – With AI, automation, and cloud computing, it keeps your business competitive.
Improved decision-making – IT support offers data analytics and reporting tools for strategic planning.
In conclusion, IT support service is essential for businesses. A robust IT support staff guarantees security, efficiency, growth, and uninterrupted operations. Investing in IT support, whether through internal IT teams or managed services provided by outside companies, helps companies be more successful by saving time and lowering risks.
0 notes
Text
The Importance of Updates and Patches for Server Security
That’s an excellent topic. Here’s a clear explanation on the importance of updates and patches for server security, written in a professional style suitable for IT managers, business owners, or a general technical audience.
🔒 The Importance of Updates and Patches for Server Security
In today’s digital world, servers are the backbone of most business operations—powering websites, applications, databases, and entire networks. Keeping these servers secure is critical, and one of the simplest yet most powerful ways to protect them is by regularly applying updates and security patches.
🛡️ Why Are Updates and Patches So Important?
1️⃣ Fix Known Vulnerabilities
Every day, cybersecurity researchers and malicious hackers discover new software flaws—known as vulnerabilities—that could be exploited to break into systems.
Vendors release patches to close these security holes.
Without patching, your server is effectively running with unlocked doors, inviting cybercriminals in.
2️⃣ Prevent Malware & Ransomware Attacks
Many large-scale cyber attacks, including ransomware outbreaks, exploit unpatched systems.
Examples: WannaCry and NotPetya leveraged known Windows vulnerabilities that had patches available months before the attacks.
Keeping servers up to date significantly lowers the risk of these devastating incidents.
3️⃣ Protect Sensitive Data & Maintain Compliance
If your business handles sensitive information (like customer data, financial records, or healthcare data), patching helps:
Prevent data breaches that could damage your reputation and lead to legal penalties.
Maintain compliance with regulations such as GDPR, HIPAA, PCI-DSS, which often require up-to-date systems.
4️⃣ Improve System Stability & Performance
Patches aren’t only for security—many updates fix bugs that can cause crashes, improve performance, and add new features. This keeps your IT infrastructure running smoothly.
🚨 The Risks of Neglecting Updates
❌ Without Regular Patching🚀 With Regular PatchingHigh chance of malware & ransomware breachesReduced attack surfaceData theft, costly recovery, lost customer trustStrong compliance posturePotential non-compliance finesImproved system stability
⚙️ Best Practices for Server Patching
✅ Implement a patch management policy. Define when, how, and by whom patches are tested and applied.
✅ Use staging environments. Test patches in a staging or QA environment to catch issues before pushing to production.
✅ Automate updates where possible. Use patch management tools (like WSUS, Red Hat Satellite, Ansible, or Puppet) to streamline updates.
✅ Schedule regular maintenance windows. Plan updates during low-traffic times to minimize disruption.
✅ Monitor and audit. Keep records of applied patches for compliance and troubleshooting.
💡 Bottom Line
Applying updates and security patches is one of the most cost-effective ways to secure your servers. It protects your business from threats, ensures regulatory compliance, and keeps your systems running reliably.
Think of patching as locking the doors and windows of your digital infrastructure—essential, routine, and crucial for peace of mind.
✅ Need help creating a patch policy or choosing patch management tools? Let me know your environment (Windows, Linux, VMware, hybrid) — I can draft a simple action plan for you!

The Importance of Updates and Patches for Server Security
#The Importance of Updates and Patches for Server Security#Updates and Patches for Server Security#patch management process#Server Patch Management#servers secure#Server Patching#patch management policy
0 notes
Text
Who Needs CD, DVD, Blu-ray Duplicators in the Cloud Age?

In the digital-first era of today, where cloud storage and streaming services are the norm, most think optical media has gone the way of the dinosaur. But that isn't anything near reality. CD, DVD, and Blu-ray duplicators continue to be widely employed in many industries, and for valid reasons.
Let's see who is still in need of disc duplication technology, why Blu-ray publishers and disc duplicator makers are still in the game, and how companies are making use of Blu-ray publishers and automated disc printers in 2025.
1. Businesses That Still Rely on Disc Media
Although amateur users might stick to the cloud, professional industries will go for physical media due to its reliability, security, and compatibility.
A. Film & Video Production Studios
Independent filmmakers, wedding videographers, and media production houses use Blu-ray, DVD, and CD authors on a routine basis to generate deliverables of high quality. Clients frequently desire hard-copy versions of movies, documentaries, or highlight reels as souvenirs.
B. Government & Law Enforcement
Government agencies and law enforcement units often store sensitive information on DVDs and Blu-rays. Optical media offers a tamper-free and offline copy that is suitable for long-term storage of legal documents, case files, and video footage.
C. Education & Training Institutions
CD/DVD duplicators are employed by universities, training centers, and e-learning institutions to send course content, lectures, and software to students in remote or disconnected areas where internet connectivity is poor or untrustworthy.
D. Software & IT Companies
Legacy software vendors continue to distribute product demos, installation media, and recovery tools on CD, DVD, and Blu-ray discs. It guarantees the end-user gets a tested and virus-free version of the software.
2. Why Discs Still Matter in 2025
Despite the age of the cloud, optical discs have numerous advantages that cloud-based solutions cannot provide.
Data Permanence
Unlike online servers or hard drives, discs aren't worn down by everyday use and can't be influenced by ransomware, power outages, or hacking.
Offline Access
No internet is necessary. In remote locations or sensitive environments, CDs, DVDs, and Blu-rays deliver content immediately without subscription or downloads.
One-Time Cost
No ongoing fees as with cloud storage. You pay once for the disc, and it lasts forever (if taken care of).
3. The Era of Automatic Disc Printers
Thanks to the latest automated disc printers, it has never been simpler to make professional-quality CDs and DVDs. These devices can print and copy hundreds of discs with complete-colour labelling in a single batch. Today's equipment, like SpeedJet Inkjet CD/DVD/Blu-ray printers or Pro III Monochrome Thermal Printers, delivers quick, smudge-free results, ideal for organizations that require branded discs with logos, barcodes, or legal stamps.
4. Use Case: Archiving for the Future
Since data formats shift every few years, corporations in search of long-term archiving systems rely on Blu-ray disc duplicators. A Blu-ray disc stored correctly will last 25 to 100 years, surpassing the majority of USBs and external hard drives in archive longevity. Libraries, museums, hospitals, and broadcasters continue to use Blu-ray publishers and CD duplicators today to keep their legacy data available decades from now.
5. CD, DVD, Blu-ray Duplicators: A Specialist, But Critical Market
Although not everyone requires physical media anymore, the markets that do can't afford to fail or settle for anything less. That's why they look to dependable solutions such as automated disc printers, Blu-ray DVD CD publishers, and commercial disc duplicators to deliver secure and scalable media output.
Conclusion
So who requires CD, DVD, and Blu-ray duplicators in the cloud era? The reply is straightforward: any organization or business that desires security, permanence, and professional offline media distribution. From filmmakers to forensic investigators, from universities to software engineers, physical media isn't dead; it's just more specialized.
If your company requires high-quality, secure, and high-speed disc publishing, buying a CD, DVD, or Blu-ray duplicator or automated disc printer remains a wise investment in 2025.
Eager to discover the top disc duplicator for your requirements? Check out a variety of CD, DVD, and Blu-ray publishers and printers from market leaders like All Pro Solutions, and achieve professional-level performance with each disc.
0 notes
Text
Why Downtime Matters And How Managed Mainframe Services Minimize the Damage
Downtime is more than a temporary inconvenience; it’s a high-stakes liability. In industries where mainframes power critical operations, even a brief outage can cascade into severe financial losses, operational paralysis, and reputational damage. Traditional management strategies reliant on in-house IT teams and legacy maintenance approaches often fail to deliver the agility and foresight needed to prevent disruptions.
The True Cost of Mainframe Downtime
Financial repercussions: Unplanned outages cost businesses millions. Banking institutions, for example, risk regulatory fines for service interruptions, while e-commerce platforms hemorrhage revenue for every second of downtime. A single hour of mainframe downtime can result in six- or seven-figure losses, not including the residual impact of customer churn and SLA penalties.
Operational disruptions: A downed mainframe can cripple entire workflows, halt transactions, cause supply chain gridlocks, and set off a domino effect of inefficiencies. In sectors like logistics and healthcare, system unavailability can lead to delayed shipments or even compromised patient care, making uptime a matter of profit and public safety.

Why Mainframes Are Still Indispensable
Unmatched processing power: Despite the advent of cloud and distributed computing, mainframes remain unrivaled in their ability to process vast amounts of data with minimal latency. Banks, insurers, and governments rely on these systems for real-time transactions, regulatory compliance, and high-throughput computing.
Reliability and security: Mainframes are engineered for resilience, boasting uptime rates that surpass most modern IT infrastructures. Their robust security frameworks make them the preferred choice for industries handling sensitive financial and personal data.
Legacy application support: Decades-old mission-critical applications continue to run on mainframes. Replacing them with cloud-native alternatives isn’t always feasible due to cost, complexity, and regulatory constraints, making modernization strategies essential rather than outright replacement.
Common Causes of Mainframe Downtime
Hardware failures: Aging infrastructure is a ticking time bomb. Component degradation, overheating, or sudden malfunctions can bring entire systems to a grinding halt. Without predictive analytics and routine maintenance, these failures often strike without warning.
Software glitches: Unpatched vulnerabilities, compatibility issues, and outdated operating systems introduce instability. A single misconfigured update can cause cascading failures, leading to prolonged outages and costly recovery efforts.
Human error: IT personnel, despite their expertise, remain one of the leading causes of downtime. Misconfigurations, accidental data deletions, and improper system changes can disrupt operations, underscoring the need for automation and stringent governance protocols.
Cybersecurity threats: Mainframes are not immune to cyberattacks. Ransomware, data breaches, and distributed denial-of-service (DDoS) attacks have increasingly targeted legacy systems, exploiting gaps in outdated security postures. A compromised mainframe can result in stolen financial data, regulatory penalties, and long-term trust deficits.
How Managed Mainframe Services Prevent Downtime
Proactive Monitoring — AI and ML spot issues before they become problems. Predictive Maintenance — Fixes risks before failure hits. Disaster Recovery — Built-in resilience with failover, backups & zero-downtime planning. Enhanced Security — Real-time threat defense, access control & compliance audits. 24/7 Expert Support — Always-on help from seasoned mainframe pros.
A reactive approach to mainframe management is no longer tenable. As digital transformation accelerates, downtime becomes increasingly unacceptable. Managed mainframe services not only minimize outages but also enhance security, efficiency, and scalability. In an era where uninterrupted operations are non-negotiable, businesses that invest in managed services gain a competitive edge defined by reliability, resilience, and long-term success.
#mainframe services#managed mainframe services#managed mainframe#mainframe managed services#ibmmainframe#mainframe as a services#mainframe modernization
0 notes
Text
Why Healthcare Providers Need Managed IT Services for Better Patient Care

The healthcare industry is going through a massive digital transformation, with electronic health records, telehealth, cloud-based patient management, and data security becoming the foundation of modern care. A hospital or healthcare center has many things to juggle at once: Accessing a patient’s medical history, checking real-time lab results, and managing endless billing cycles. Managing all this can lead to chaos, operational failure, and bad patient experience. That’s where Managed IT Services comes in.
Studies show that around 84% of hospitals and healthcare centers use cloud services for backup, analytics, and disaster recovery. The integration of IT into healthcare has restructured the industry, from healthcare technology like electronic health records and electronic medical records systems to practice management and telemedicine platforms.
Understanding Managed IT Services in Healthcare
What Are Managed IT Services for Healthcare?
Managed IT services for medical practices and healthcare centers mean outsourcing a facility’s IT functions and operations to a third party at a lower cost than running an internal IT department. The services provided by a third party for managed medical services are known as managed service providers (MSPs).
Common managed IT services for healthcare include:
Cybersecurity and Compliance: Advanced security protocols, including endpoint protection, threat detection, and compliance.
Cloud and Data Management: This service helps secure cloud storage for managing electronic health records, medical imaging, and real-time data access.
24/7 Monitoring and Support: Continuous monitoring of IT infrastructure to detect and resolve issues before they impact healthcare operations. This ensures that healthcare IT systems are always up and running.
Network and Infrastructure Management: Optimizes connectivity for seamless communication
Disaster Recovery and Business Continuity: This includes backup and recovery strategies to safeguard critical patient and operational data in case of system failure.
How Do Healthcare-Managed IT Services Work?
Here’s how IT-managed services work:
Monitoring
Managed IT services to monitor systems, networks, and applications to assess their performance, security, and compliance. For example, they can manage and monitor medical applications and do the necessary upgrades daily.
Maintenance
Managed IT services for healthcare assistance in performing routine maintenance tasks such as software updates, network supervision, and disaster recovery.
Security
Healthcare-managed IT services have 24/7 support for employees, patients, and clinics to improve operational efficiency.
Issue Resolution
They resolve issues in real time through help desks. These help desks can include a general IT help desk, a clinical service help desk, and a patient service help desk. Both employees and patients can use these help desks to resolve their issues in real time.
Challenges in Healthcare IT Management
Cyber Attacks
Cybersecurity is the top challenge for healthcare leaders. Attackers are getting smarter and more strategic; thus, we need stricter norms against cyber attacks.
The healthcare industry is more vulnerable to these types of threats:
Ransomware
Data Breaches
DDoS Attacks
Insider Threats
Healthcare IT Security Risks
One of the biggest risks in healthcare systems is the insecure storage and transmission of sensitive patient data. Weak encryption, poor access control, and bad data handling can allow unauthorized individuals to access patient information, which cybercriminals can use to access valuable data.
The Growing Need for Compliance and Data Protection
Compliance is a big challenge for healthcare providers. Laws like HIPAA require strict measures to protect sensitive patient information, and non-compliance can lead to large fines and legal issues.
Managed IT service for healthcare providers to help healthcare organizations comply by:
Encrypting data and secure access
Conducting regular compliance audits and security assessments
Having data backup and disaster recovery plans in place.
Key Benefits of IT Managed Services in Healthcare
Data Security and HIPAA Compliance
One of the benefits of managed IT services in healthcare is the significant boost in data security and guaranteed HIPAA compliance to protect sensitive patient data/information with continuous monitoring, proactive threat mitigation, and expert guidance in navigating complex healthcare regulations, minimizing data breaches and legal penalties.
Operational Efficiency for Healthcare Providers
IT-managed services in healthcare have proven to improve operational efficiency by streamlining processes, minimizing downtime, and securing sensitive patient data/information to comply with regulations. This will allow healthcare providers to focus on patient care rather than managing IT infrastructure and having access to expert technical support to address issues promptly.
24/7 IT Support and Zero Downtime
IT-managed services in healthcare can provide 24/7 IT support and zero downtime through proactive monitoring and rapid problem-solving. This approach offers remote monitoring and management, disaster recovery solutions, and rapid troubleshooting. This also gives access to on-demand expertise for temporary projects or scenarios where skill sets are not internally employable.
Cost Savings with Healthcare IT Managed Services
Managed IT services can reduce costs by eliminating hardware acquisition and labor costs.
How Managed IT Services Improve Patient Care
Faster Access to Patient Records with Cloud Solutions
Managed IT services can improve patient care by giving faster access to patient records through cloud solutions so healthcare providers can make informed decisions quickly, which will lead to better diagnosis, treatment plans, and overall patient experience while maintaining data security and accessibility anywhere.
Better Telehealth and Remote Patient Monitoring
Managed IT services provide better telehealth and remote patient monitoring. These services allow healthcare providers to deliver continuous patient care through digital platforms. Early interventions, better chronic condition management, and patient engagement simplifications reduce costs.
No Downtime for Uninterrupted Patient Care
Managed IT services mean minimal downtime, and healthcare professionals can focus solely on delivering excellent medical care to patients without technology interruptions.
Choosing the Right Managed IT Services Provider for Healthcare
Key Factors to Consider in Healthcare IT Managed Services
When looking for a managed IT service provider:
Proven experience in the healthcare industry
Proven expertise and compliance with HIPAA and HITRUST
Strong security measures for patient data
Scalability to meet changing needs
Service level agreements (SLAs)
How to Evaluate Managed IT Services for Healthcare Providers
When evaluating managed IT service providers for healthcare:
Do they understand healthcare regulations like HIPAA?
Expertise in relevant technology like EHR
Scalability
Strong cybersecurity practices
Proven track record in healthcare
Clear communication on service-level support
Request case studies and client testimonials
Future of Managed IT Services in Healthcare
As technology advances, managed IT services will use:
AI-driven automation for predictive maintenance
Blockchain for patient data management
Interoperability between healthcare systems
Advanced cybersecurity frameworks for protection against cyber attacks
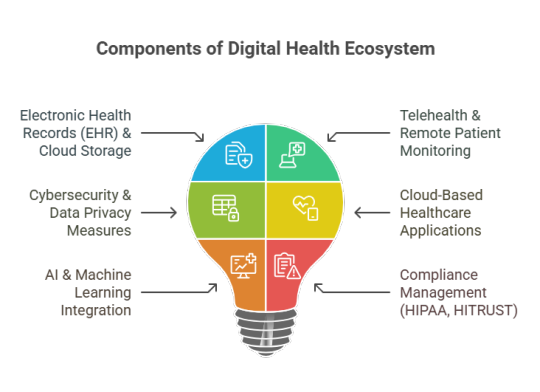
Conclusion: Why Healthcare Providers Must Invest in Managed IT Services
Healthcare providers must invest in IT-managed services to focus on patient care. By outsourcing complex IT infrastructure management, providers can have a robust cybersecurity framework to protect patient data, perform proactive system monitoring for operational efficiency, deliver high-quality care, and comply with industry regulations.
By partnering with a managed IT service provider, healthcare organizations can focus on what matters most—patient care.
With over 20 years of IT consulting and managed services experience, XLNC Technologies helps healthcare providers navigate a digital transformation without compromising security, efficiency, or compliance.
By choosing XLNC Technologies, healthcare organizations have a trusted partner to deliver future-ready IT solutions for seamless, secure, and patient-centric healthcare.
FAQs
What are managed IT services in healthcare, and how do they work?
Managed IT services in healthcare mean outsourcing IT management to specialist providers who ensure security, compliance, and efficiency. They offer 24/7 monitoring, cybersecurity, cloud solutions, and data backup so you can focus on patient care.
How do managed IT services help healthcare providers improve patient care?
They help with patient care by giving fast access to medical records, secure telehealth solutions, and minimal downtime. AI-driven monitoring and cloud-based data storage mean AI-driven seamless care, better diagnoses, and better patient outcomes through secure and efficient technology.
What are the benefits of IT-managed services in healthcare security?
Managed IT services deliver security with AI-driven threat detection, data encryption, zero-trust architecture, and real-time monitoring. They protect electronic health records (EHRs) from cyber threats, ransomware, and data breaches, so you’re HIPAA compliant, and patient data is private.
How can managed IT services help healthcare organizations stay compliant with regulations?
They help with HIPAA and regulatory compliance by implementing strong security protocols, encrypted data storage, and access control. Regular audits, automated risk assessments, and secure backups reduce legal risk and protect patient data from breaches and unauthorized access.
How do healthcare providers choose the right managed IT services provider?
They should evaluate IT vendors based on their industry expertise, 24/7 support, cybersecurity capabilities, compliance readiness, and scalability. Check past performances, case studies, and security frameworks. A provider with proactive monitoring and custom solutions will maintain efficiency, compliance, and better patient care.
#Managed IT Services for Healthcare#Healthcare IT Solutions#Healthcare Digital Transformation#IT Support for Hospitals#Cloud Solutions in Healthcare#Healthcare Data Security#HIPAA Compliance#Healthcare IT Compliance#Telehealth IT Support#Electronic Health Records#EHR Management#Cybersecurity in Healthcare#Remote Patient Monitoring#IT Infrastructure Management#24/7 IT Support for Healthcare#IT Outsourcing in Healthcare#Disaster Recovery for Hospitals#Cost-effective IT Services#Patient Data Protection#Healthcare Compliance Solutions#Healthcare Cloud Management#Managed Service Providers for Healthcare
0 notes
Text
Enhancing Business Efficiency with Reliable Network Support Solutions in Roseville
In today’s technology-driven world, businesses—large and small—rely heavily on secure and efficient IT infrastructure. A single glitch in the network can lead to downtime, loss of productivity, and potential data breaches. This is where Network Support Solutions in Roseville come into play. With the growing demand for high-performance IT systems, businesses in Roseville are increasingly turning to professional network support services to maintain operational continuity, bolster security, and enable scalable growth.
In this blog, we will explore what network support solutions entail, the key benefits of hiring professionals in Roseville, and what to look for in a reliable service provider.
What Are Network Support Solutions?
Network support solutions refer to a range of services aimed at maintaining, securing, optimizing, and troubleshooting a company’s computer network. This includes everything from setting up and monitoring networks, to providing ongoing support, cybersecurity measures, data backup solutions, and more.
Some common components of network support include:
Network setup and configuration
Firewall and security services
Server and infrastructure maintenance
Troubleshooting and issue resolution
Remote monitoring and management
Data recovery and backup solutions
Cloud network support
Whether your business operates in retail, healthcare, finance, or any other sector, a reliable IT infrastructure is crucial—and Network Support Solutions in Roseville provide just that.
Why Businesses in Roseville Need Professional Network Support
1. Prevent Costly Downtime
One of the main advantages of network support is minimizing downtime. Network issues can halt business operations, delay communications, and affect customer service. A professional support team ensures your systems stay operational around the clock with minimal disruptions.
2. Enhanced Network Security
Cybersecurity threats are at an all-time high. From phishing attacks to ransomware, the need for secure networks has never been greater. A dedicated network support team will implement firewalls, monitor traffic, and regularly update your systems to guard against cyber threats.
3. Scalable Infrastructure
As your business grows, so does your IT infrastructure. Professional network support providers in Roseville help businesses scale their networks seamlessly to accommodate more users, devices, and data, without compromising on performance.
4. Quick Troubleshooting and Repairs
Time is money. With proactive network support, potential issues are identified and resolved before they escalate. Technicians use remote monitoring tools and diagnostic software to ensure rapid response and resolution times.
5. Expert Guidance and Consultation
Hiring a team for Network Support Solutions in Roseville means you get more than just maintenance. You get access to IT experts who can advise on best practices, new technologies, and strategies for future-proofing your infrastructure.
Features of a Good Network Support Service in Roseville
When looking for the right network support provider, businesses should keep the following features in mind:
✅ 24/7 Monitoring and Support
Your network doesn’t sleep, and neither should your support team. Choose a provider that offers round-the-clock service to ensure immediate assistance in case of emergencies.
✅ Customized IT Solutions
Every business has unique needs. A good network support company will tailor its solutions to match your industry, size, and objectives.
✅ Experienced and Certified Technicians
Technical expertise matters. Look for a provider with a team of certified professionals who are skilled in handling different network environments, software platforms, and hardware systems.
✅ Regular System Audits and Reports
A transparent service includes periodic audits and performance reports. This helps in identifying bottlenecks and planning future improvements.
✅ Data Backup and Disaster Recovery
Data loss can be catastrophic. Ensure your provider offers automated backups and a robust disaster recovery plan to get you back on track quickly.
✅ On-Site and Remote Support
While many issues can be handled remotely, there are times when on-site visits are essential. Opt for a provider that offers both options for comprehensive coverage.
How Network Support Benefits Different Industries in Roseville
🏢 Small Businesses
Small enterprises often lack the resources for a full-time IT department. Outsourcing network support allows them to access expert help at a fraction of the cost.
🏥 Healthcare Providers
Medical facilities in Roseville must adhere to HIPAA regulations. Network support services ensure data security and compliance while managing high volumes of sensitive patient data.
🛒 Retail Businesses
Retailers depend on point-of-sale systems and inventory management. Reliable network support ensures smooth operations and uninterrupted customer service.
💼 Corporate Offices
For large corporations, network efficiency is key to team collaboration and remote work. A support team ensures optimal bandwidth, secure VPNs, and minimal latency.
Choosing the Right Network Support Solutions in Roseville
Roseville is home to a variety of IT service providers, making it essential to choose a partner that aligns with your business needs and budget. Here are a few steps to guide your selection:
Assess Your Needs – Understand what aspects of your network need support: security, scalability, hardware, etc.
Check Reviews and References – Look into customer testimonials and ask for case studies or references.
Request a Free Consultation – Many reputable firms offer free initial consultations to understand your infrastructure.
Compare Service Level Agreements (SLAs) – Ensure you are getting guaranteed uptime, response times, and support coverage.
Evaluate Pricing Models – Whether it’s monthly contracts or pay-as-you-go models, find a pricing structure that fits your operations.
Final Thoughts
For modern businesses in Roseville, investing in professional Network Support Solutions Roseville is not a luxury—it’s a necessity. Whether you’re aiming for growth, security, or efficiency, having a dependable network support provider can dramatically reduce IT hassles and free you to focus on your core operations.
0 notes