#The Importance of Updates and Patches for Server Security
Explore tagged Tumblr posts
Text
The Importance of Updates and Patches for Server Security
That’s an excellent topic. Here’s a clear explanation on the importance of updates and patches for server security, written in a professional style suitable for IT managers, business owners, or a general technical audience.
🔒 The Importance of Updates and Patches for Server Security
In today’s digital world, servers are the backbone of most business operations—powering websites, applications, databases, and entire networks. Keeping these servers secure is critical, and one of the simplest yet most powerful ways to protect them is by regularly applying updates and security patches.
🛡️ Why Are Updates and Patches So Important?
1️⃣ Fix Known Vulnerabilities
Every day, cybersecurity researchers and malicious hackers discover new software flaws—known as vulnerabilities—that could be exploited to break into systems.
Vendors release patches to close these security holes.
Without patching, your server is effectively running with unlocked doors, inviting cybercriminals in.
2️⃣ Prevent Malware & Ransomware Attacks
Many large-scale cyber attacks, including ransomware outbreaks, exploit unpatched systems.
Examples: WannaCry and NotPetya leveraged known Windows vulnerabilities that had patches available months before the attacks.
Keeping servers up to date significantly lowers the risk of these devastating incidents.
3️⃣ Protect Sensitive Data & Maintain Compliance
If your business handles sensitive information (like customer data, financial records, or healthcare data), patching helps:
Prevent data breaches that could damage your reputation and lead to legal penalties.
Maintain compliance with regulations such as GDPR, HIPAA, PCI-DSS, which often require up-to-date systems.
4️⃣ Improve System Stability & Performance
Patches aren’t only for security—many updates fix bugs that can cause crashes, improve performance, and add new features. This keeps your IT infrastructure running smoothly.
🚨 The Risks of Neglecting Updates
❌ Without Regular Patching🚀 With Regular PatchingHigh chance of malware & ransomware breachesReduced attack surfaceData theft, costly recovery, lost customer trustStrong compliance posturePotential non-compliance finesImproved system stability
⚙️ Best Practices for Server Patching
✅ Implement a patch management policy. Define when, how, and by whom patches are tested and applied.
✅ Use staging environments. Test patches in a staging or QA environment to catch issues before pushing to production.
✅ Automate updates where possible. Use patch management tools (like WSUS, Red Hat Satellite, Ansible, or Puppet) to streamline updates.
✅ Schedule regular maintenance windows. Plan updates during low-traffic times to minimize disruption.
✅ Monitor and audit. Keep records of applied patches for compliance and troubleshooting.
💡 Bottom Line
Applying updates and security patches is one of the most cost-effective ways to secure your servers. It protects your business from threats, ensures regulatory compliance, and keeps your systems running reliably.
Think of patching as locking the doors and windows of your digital infrastructure—essential, routine, and crucial for peace of mind.
✅ Need help creating a patch policy or choosing patch management tools? Let me know your environment (Windows, Linux, VMware, hybrid) — I can draft a simple action plan for you!

The Importance of Updates and Patches for Server Security
#The Importance of Updates and Patches for Server Security#Updates and Patches for Server Security#patch management process#Server Patch Management#servers secure#Server Patching#patch management policy
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Preventative IT Maintenance: Keeping Your Business Running Smoothly

With technology moving forward so fast, your business can’t operate without it. Computers, servers, cloud systems and software platforms have to be running smoothly to keep your team productive, defend confidential information and make sure customers receive a good experience.
Unfortunately, IT systems don’t manage themselves without attention.
This is why we need preventative IT maintenance. Regular car servicing makes sure your car avoids breakdowns and preventative IT support does the same for your systems. Here at Image IT, we know that companies who focus on IT before issues arise benefit a lot. We’ll now look at what preventative maintenance means and understand why it helps your business run smoothly.
What Does Preventative IT Maintenance Mean?
Taking care of your IT infrastructure ahead of time is called preventative maintenance. With preventative maintenance, you take action to make sure your systems are in good shape all the time, so you don’t have to rush to solve emergencies.
Such tasks refer to:
Tracking how the system is running
Putting security patches and new versions of the software into use
Regularly using antivirus and malware software
Testing the use of backup options
Updating both your device’s drivers and firmware
Checking the configurations for firewalls and networks
Exchanging ageing equipment to prevent any breakdowns
At Image IT, we set up specialized maintenance services that guarantee your technology remains in top condition and reduces the chance of risks and downtime.
Why Taking Care of Problems in Advance Is Crucial for Companies in Ireland
1. Minimize any time when your business is not working effectively.
Problems with your IT systems such as servers failing, networks breaking or bugs in software, may bring your work to a halt and cost you in both time and money. Doing preventative maintenance lets you catch and manage issues early and this means your business avoids the stress of dealing with major problems.
If a server begins to overheat, it’s possible to handle the issue before it crashes, so you won’t have to deal with expensive downtime and loss of data.
2. Prevent or Stop Cyber Attacks
More and more, businesses in Ireland are facing cyberattacks, most often small and medium-sized companies. Many attackers use old software, unpatched versions and networks that have not been properly set up.
Ongoing upkeep of security tools such as firewalls, antivirus software and system updates, makes it much less likely for your system to become a victim of ransomware, phishing or a data breach.
3. Increase the Lifespan of IT Assets
Just as changing the oil in your car lengthens its engine’s lifespan, looking after your IT equipment in the same way will help it work longer. Regularly taking care of computers stops them from wearing out and prevents too many replacements.
4. Raise the effectiveness of your staff.
This kind of slow work is frustrating and influences how your team feels about their work. If technology runs smoothly, your team won’t have to worry about systems or spend time finding IT solutions.
5. With time, the cost of IT will decrease.
Though it might feel like a pricey addition, upfront maintenance helps save money and prevents serious IT problems. One data breach, meeting replacement or lasting period of downtime can often be more expensive than all your ISP’s services put together.
Important Parts of a Well-Made IT Maintenance Plan
We create preventative maintenance strategies for your business that fit its individual requirements at Image IT. The method we use is:
We watch your systems around the clock.
We watch over your systems around the clock, spotting problems early and fixing them so they don’t impact your work.
Timely Updates and Patch Upgrades
We make sure your operating systems, applications and antivirus are always running on the latest versions.
Test the backup and recovery of your data.
We ensure your backups are properly configured and we regularly perform tests to see how fast you can recover data.
You can do a Network Health Check here.
We examine your network for good speed, serious security flaws and technology issues to confirm your system operates safely and properly.
Managing Assets and Deciding on Their Life
We watch over your equipment and make sure you can update your technology before it starts causing issues.
Support from the users and helpdesk
If your team has any IT questions or concerns, our friendly team is there to lend a non-technical helping hand.
Why Is Image IT a Great Solution?
Operating out of North Dublin, Image IT has been supporting company’s in Ireland for about 15 years. Our knowledgable team delivers helpful, consistent and friendly IT assistance to the companies here in New Zealand.
We are dedicated to forming long-term relationships with clients so we can do more than just address issues; we can help avoid them.
You will gain the following benefits when you work with us:
Transparent pricing
A quick response from the team
Customized maintenance services
Expert opinions offered in a personal way
If you have just a few devices or a complex IT structure, our solutions are designed to match your requirements and your budget.
Benefits You Can See in Life: An Example
There were many issues at one of our clients, a small financial services firm in Dublin, involving downtime in the network and software that was past its update. Following their sign up for our preventative maintenance, we set up a monitoring system, cleaned their network and ran scheduled updates.
The result? A 90% drop in IT issues reported by staff, faster systems, and peace of mind for their management team knowing their data and systems were protected.
Your Next Step: Secure Your Business with Preventative IT Support
Don’t wait for a system failure, data breach, or productivity drop to remind you of your IT vulnerabilities. Preventative maintenance is one of the smartest investments you can make in your business.
Let Image IT take the stress out of managing your technology — so you can focus on what you do best.
2 notes
·
View notes
Text
Trusted Cyber Crime Lawyer in Noida
Trusted Cyber Crime Lawyer in Noida
The advancement of digital technology has transformed how we communicate, transact, and work. However, it has also given rise to cybercrime — a pressing issue that affects individuals, businesses, and governments worldwide. In Noida, a bustling hub of technology and business, cybercrime is an ever-present threat. If you find yourself a victim of cybercrime, Advocate Deepak, a leading trusted cyber crime lawyer in Noida, is here to provide expert legal guidance and representation.
This article explores what cybercrime is, its types, safety tips to prevent it, and why Advocate Deepak is the best choice for tackling cybercrime cases in Noida.

What is Cyber Crime?
Cybercrime refers to illegal activities carried out using computers, digital devices, or networks. These crimes exploit technological vulnerabilities and target individuals, organizations, or governments. Cybercrime can cause financial losses, emotional distress, and reputational damage.
Understanding the nature and types of cybercrime is crucial for prevention and response.
Types of Cyber Crime
Cybercrime encompasses a wide range of activities, including but not limited to:
1. Hacking
Hacking involves unauthorized access to computer systems or networks. Hackers often aim to steal sensitive information, disrupt operations, or cause harm.
2. Phishing
Phishing is a fraudulent practice where attackers trick individuals into revealing personal information, such as passwords or credit card details, through fake emails or websites.
3. Identity Theft
Identity theft occurs when cybercriminals steal personal information to impersonate someone for financial or criminal purposes.
4. Ransomware Attacks
Ransomware is malicious software that encrypts a victim’s data and demands payment for its release. These attacks can paralyze businesses and organizations.
5. Cyberstalking
Cyberstalking involves the use of digital platforms to harass, intimidate, or monitor individuals, causing psychological distress.
6. Online Fraud
Online fraud includes scams like fake e-commerce websites, Ponzi schemes, and fraudulent investment opportunities.
7. Malware Attacks
Malware refers to software designed to damage, disrupt, or gain unauthorized access to systems. Common types include viruses, worms, and spyware.
8. Denial of Service (DoS) Attacks
DoS attacks flood a network or server with excessive requests, rendering it inaccessible to legitimate users.
9. Social Engineering
Social engineering manipulates individuals into divulging confidential information by exploiting trust or creating urgency.
10. Cyberbullying
Cyberbullying involves using digital platforms to threaten, humiliate, or harm individuals, particularly vulnerable groups like children and teenagers.
Safety Tips to Prevent Cyber Crime
Preventing cybercrime requires a proactive and informed approach. Here are some essential tips to enhance your cybersecurity:
1. Use Strong Passwords
Create complex passwords with a mix of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable information like birthdays or names.
2. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security by requiring a secondary verification step, such as a code sent to your phone.
3. Be Wary of Phishing Attempts
Verify the authenticity of emails and messages before clicking on links or providing personal information. Look for signs of phishing, such as suspicious sender addresses or grammatical errors.
4. Keep Software Updated
Regularly update your operating system, applications, and antivirus software to patch vulnerabilities and enhance security.
5. Secure Your Wi-Fi Network
Protect your home or office Wi-Fi with strong passwords and encryption. Avoid using public Wi-Fi for sensitive transactions.
6. Back Up Data Regularly
Regularly back up important files to external drives or cloud storage. This ensures data recovery in case of ransomware attacks or system failures.
7. Monitor Financial Transactions
Review bank and credit card statements frequently to detect unauthorized transactions. Report any discrepancies immediately.
8. Limit Sharing Personal Information Online
Be cautious about sharing personal details on social media platforms. Cybercriminals can use this information for identity theft or social engineering attacks.
9. Install Reliable Security Software
Use reputable antivirus and anti-malware software to detect and prevent threats. Ensure the software is updated regularly.
10. Educate Yourself and Your Family
Stay informed about the latest cyber threats and educate your family members, especially children, about safe online practices.
Advocate Deepak: Your Trusted Cyber Crime Lawyer in Noida
When dealing with cybercrime, having a skilled and experienced lawyer is crucial. Advocate Deepak is a leading trusted cyber crime lawyer in Noida, specializing in providing legal solutions for cybercrime victims.

Why Choose Advocate Deepak?
Expertise in Cyber Laws Advocate Deepak possesses in-depth knowledge of India’s Information Technology Act and other relevant laws. This expertise enables him to handle complex cybercrime cases effectively.
Personalized Legal Strategies Every case is unique. Advocate Deepak provides tailored legal strategies to address the specific needs of his clients, ensuring the best possible outcomes.
Proficient Evidence Management Cybercrime cases often rely on digital evidence, such as IP logs, emails, or financial records. Advocate Deepak excels in collecting, analyzing, and presenting this evidence in court.
Proven Track Record With a history of successfully resolving cybercrime cases, Advocate Deepak has earned the trust and respect of his clients in Noida.
Preventive Legal Advice Beyond litigation, Advocate Deepak offers advice to help clients mitigate the risk of future cybercrimes through robust cybersecurity measures.
Services Offered by Advocate Deepak
Representation in cybercrime cases
Assistance with filing complaints with cybercrime cells
Legal support for hacking, phishing, identity theft, and ransomware cases
Guidance on data protection and privacy laws
Advisory on cybersecurity compliance for businesses
In today’s digital age, cybercrime poses a significant threat to individuals and organizations alike. Whether it’s identity theft, hacking, or online fraud, the consequences can be devastating. Advocate Deepak, a trusted cyber crime lawyer in Noida, is dedicated to helping victims navigate the complexities of cyber laws and achieve justice.
By understanding the types of cybercrime and implementing the safety tips provided, you can significantly reduce your risk of becoming a victim. If you do encounter a cybercrime issue, Advocate Deepak’s expertise and commitment make him the ideal choice to handle your case effectively. Protect your digital life by staying informed, vigilant, and prepared to seek professional legal assistance when needed.
2 notes
·
View notes
Text
Comparing Wordpress Hosting in the UK
When it comes to building a website, one of the most critical decisions you'll make is selecting a hosting provider. For those seeking a platform that combines flexibility, ease of use, and scalability, **WordPress hosting in the UK** is an excellent choice. In this blog post, we will delve into various aspects of WordPress hosting specifically tailored for the UK market, helping you make an informed decision.
What Is Wordpress Hosting and Why Is It Important?
**WordPress hosting** refers to a type of web hosting that is optimised specifically for WordPress websites. Unlike generic web hosting, WordPress hosting is tailored to enhance the performance, security, and management of WordPress sites. This optimisation can take various forms, including server configurations, caching mechanisms, and specialised support. The importance of WordPress hosting lies in its ability to provide a seamless and efficient website experience. A well-optimised hosting environment can significantly improve site speed, which is crucial for retaining visitors and achieving higher search engine rankings. In addition, WordPress hosting often includes built-in security features such as automatic updates, malware scanning, and SSL certificates, which help protect your site from cyber threats. Another critical aspect is the ease of management. Many WordPress hosting providers offer managed services, meaning they handle technical tasks like software updates, backups, and security patches. This allows website owners to focus more on content creation and business operations rather than technical maintenance. Managed hosting can be particularly beneficial for those who lack technical expertise or simply wish to save time. Furthermore, specialised support is a key benefit of WordPress hosting. Providers typically have support teams well-versed in WordPress, capable of resolving issues more efficiently than general hosting support. This can be a lifesaver when facing unexpected problems or needing guidance on optimising your site. Finally, WordPress hosting often comes with additional tools and features designed to enhance functionality, such as one-click installations, staging environments, and developer tools. These features make it easier to customise and extend your website according to your specific needs.
Key Features to Look for in a UK WordPress Hosting Provider
When selecting a WordPress hosting provider, focusing on specific features can ensure you get the best performance and reliability for your site. One of the top priorities should be **managed WordPress hosting**, which handles tasks like updates and backups, freeing you to concentrate on content creation. Additionally, **automatic backups** are essential, providing peace of mind that your data is secure and can be restored if needed. **Security features** should be high on your list, including SSL certificates, firewalls, and malware scanning to protect your site from various threats. Equally important is **scalability**, allowing your hosting solution to grow with your website without requiring a complex migration process. **Customer support** is another crucial feature. Opt for providers that offer 24/7 support, ensuring assistance is available whenever you need it. Look for support options like live chat, phone, and a comprehensive knowledge base to troubleshoot issues swiftly. Other valuable features include **staging environments** for testing changes safely before deploying them live, and **one-click installations** for easy setup. **Content Delivery Networks (CDNs)** and **SSD storage** can further enhance your site's speed and performance, particularly important for retaining visitors and improving SEO rankings.
Top WordPress Hosting Providers in the UK
Several reputable WordPress hosting providers operate in the UK, each offering unique features and benefits to cater to different needs: - **SiteGround**: Renowned for its stellar customer support and managed WordPress hosting options. SiteGround is ideal for users seeking reliable performance and ease of management. - **Bluehost**: Officially recommended by WordPress, Bluehost provides a user-friendly experience, making it an excellent choice for beginners. Their plans include automatic updates and robust security features. - **Kinsta**: A premium managed hosting provider that focuses heavily on performance and speed, utilising Google Cloud infrastructure. Kinsta's services are suited for high-traffic websites that require top-notch performance. - **WP Engine**: Known for its high performance, robust security measures, and comprehensive support. WP Engine offers advanced features like staging environments and developer tools, making it a strong option for professionals. - **Fasthosts**: A UK-based provider offering budget-friendly plans without compromising on support. Fasthosts provides scalable solutions suitable for both small and large websites, with options to upgrade as your needs grow. - **TsoHost**: Offers a range of plans including shared, VPS, and cloud hosting, designed to cater to diverse requirements. Their UK-based data centres ensure optimal speed and compliance with local regulations. These providers offer a variety of plans and features, allowing you to find a solution that fits your specific needs and budget.
Speed and Performance Considerations for UK Users
Website speed is a pivotal element influencing user experience and search engine optimisation (SEO) rankings. For users in the UK, opting for a hosting provider with servers located within the country can drastically improve loading times, as proximity to the server reduces latency. Beyond server location, other critical factors to consider include caching solutions and Content Delivery Networks (CDNs). Caching stores a version of your website so that it can be delivered faster to repeat visitors, while CDNs distribute your content across multiple global locations, ensuring quicker access for users regardless of their geographic location. Solid State Drives (SSDs) also play a crucial role by providing faster data retrieval compared to traditional Hard Disk Drives (HDDs). Look for hosting providers that offer advanced performance features such as PHP 7.x support, HTTP/2, and integrated caching mechanisms like Varnish or Memcached. These technologies can enhance the speed at which your website loads, improving overall user satisfaction. In addition, regular monitoring and performance analytics can help identify bottlenecks and areas for improvement. Many UK-based WordPress hosting providers include these tools in their plans, enabling you to make data-driven decisions to optimise your site's performance continuously. Focusing on these aspects ensures your website not only meets but exceeds the expectations of your UK audience, fostering better engagement and higher retention rates.
Understanding Security Features in UK WordPress Hosting
**Security is paramount when it comes to maintaining a reliable and trustworthy website. UK-based WordPress hosting providers often implement a range of robust security measures designed to protect your site from various cyber threats. Regular malware scans are essential, offering early detection and removal of malicious software that could compromise your website's integrity.** **DDoS protection is another critical feature, safeguarding your site against Distributed Denial of Service attacks, which aim to overwhelm your server with traffic, rendering it inaccessible. Automatic updates ensure that your WordPress software and plugins remain current, addressing potential vulnerabilities as soon as fixes are released.** **Firewalls serve as a barrier against unauthorised access, blocking malicious traffic and preventing attacks. Additionally, many hosting providers include intrusion detection systems to monitor and respond to suspicious activity in real time.** **Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of identification beyond just a password, making it significantly harder for attackers to gain access. SSL certificates are typically standard, encrypting data transmitted between your site and its visitors to protect sensitive information like login credentials and payment details.** **Finally, some providers offer security audits and vulnerability assessments, providing insights into potential risks and recommendations for improvement. These comprehensive security measures collectively enhance the safety and reliability of your WordPress site in the UK.**
Customer Support: Why Localised Support Matters
Access to localised customer support can make a significant difference when managing your WordPress site. Local support teams understand the unique challenges and requirements faced by UK-based websites, offering more tailored and effective assistance. They are also well-versed in local regulations, such as GDPR, ensuring that your website complies with legal standards. Language and time zone compatibility are additional benefits of localised support. When you encounter an issue, you can expect quicker response times and clearer communication, eliminating the frustration of language barriers and inconvenient support hours. This immediate assistance is invaluable, particularly in urgent situations where downtime could impact your business. Many UK hosting providers offer 24/7 support, giving you peace of mind that help is available whenever you need it. Whether through live chat, phone support, or an extensive online knowledge base, local support teams can resolve issues more efficiently. They are familiar with the specific needs and expectations of UK customers, which can result in more relevant and effective solutions. In addition, localised support often means a more personalised experience. UK-based providers typically have smaller support teams, allowing them to offer a higher level of customer service. This personal touch can make all the difference, especially for small businesses and individual site owners who may require more dedicated assistance.
Pricing: Getting the Best Value for Your Money
When evaluating pricing for **WordPress hosting in the UK**, it's essential to balance cost with value. While a lower price can be enticing, scrutinise the features and services included. Assess factors such as storage capacity, bandwidth limits, and the quality of customer support provided. Some providers offer introductory rates that increase upon renewal, so be aware of long-term costs. Look for packages that include essential features like SSL certificates, automatic backups, and security enhancements without additional charges. Compare different providers to ensure you're not missing out on critical functionalities. Some hosting companies offer flexible payment plans, such as monthly or annual billing, which can help manage your budget more effectively. Additionally, consider any hidden fees that may arise, such as charges for exceeding bandwidth or additional storage. By carefully analysing these elements, you can find a hosting solution that offers both affordability and comprehensive support, ensuring you get the best return on your investment.
Scalability and Flexibility of UK Hosting Providers
As your website evolves, having a hosting provider that supports scalability and flexibility becomes paramount. UK hosting providers often offer plans that can be easily upgraded to accommodate increased traffic, storage, and other resource demands. This capability is crucial for businesses anticipating growth, ensuring that your site can handle higher visitor numbers without performance issues. Look for providers that offer seamless upgrade paths, allowing you to enhance your plan without experiencing downtime or complex migration processes. Flexible hosting solutions often include options like VPS (Virtual Private Server) and dedicated hosting, which provide more control and resources compared to shared hosting environments. This flexibility allows you to adjust your hosting environment to meet changing needs effectively. Many UK hosting providers also offer pay-as-you-go models, enabling you to add resources like bandwidth and storage as required, without committing to higher-tier plans upfront. This approach is particularly beneficial for seasonal businesses or websites that experience fluctuating traffic levels. Additionally, some providers offer features like auto-scaling, which automatically allocates more resources during traffic spikes to maintain optimal performance. Finally, ensure that your hosting provider supports various integrations and plugins, allowing you to extend your website's functionality as needed. This adaptability can be a significant advantage, providing the tools necessary to grow and enhance your site over time.
The Importance of Data Centres and Server Locations in the UK
For websites targeting a UK audience, the location of data centres is a critical factor that directly impacts performance. Hosting your site on servers located within the UK can drastically reduce latency, leading to faster load times for local visitors. This proximity to the server ensures that data travels a shorter distance, which can significantly enhance the user experience. Local data centres also play a crucial role in compliance with GDPR regulations. UK-based data centres are more likely to adhere to local data protection laws, providing an added layer of security for your website’s data. This is particularly important for businesses that handle sensitive customer information, ensuring that data is stored and processed within legal frameworks. Additionally, having data centres in the UK means that your hosting provider can offer more reliable support tailored to your specific needs. Localised infrastructure allows for quicker response times in case of technical issues, ensuring that your site remains operational with minimal downtime. This can be especially beneficial during peak traffic periods when site performance is paramount. Lastly, the environmental impact of data centres should not be overlooked. Many UK hosting providers are adopting green energy solutions to power their data centres, aligning with broader sustainability goals and reducing carbon footprints. This not only supports environmental initiatives but also enhances your brand's commitment to sustainability.
Specialised WordPress Hosting Options Available in the UK
For WordPress users with specific needs, several UK hosting providers offer specialised hosting options. **WooCommerce hosting** is designed for e-commerce sites, providing features that enhance speed, security, and transaction handling. This type of hosting often includes pre-installed WooCommerce plugins, optimised server configurations, and dedicated support for online stores. **Multisite hosting** is another specialised option, ideal for users managing multiple WordPress sites from a single dashboard. This solution simplifies the management process, offering a centralised control panel to handle updates, backups, and other administrative tasks across all sites. **Staging environments** are crucial for those who wish to test changes or new features without affecting their live site. These environments allow users to create a copy of their site to experiment safely before deploying updates, ensuring that any potential issues can be resolved beforehand. Additionally, some providers offer **developer-focused hosting** with advanced tools such as SSH access, Git integration, and customisable server settings. These features cater to developers who require a high degree of control over their hosting environment, enabling them to tailor their setup to specific project needs. By offering these specialised options, UK WordPress hosting providers cater to a diverse range of requirements, making it easier for users to find a solution that aligns with their unique needs.
User Experience: How UK Providers Enhance Usability
UK hosting providers focus heavily on enhancing usability to ensure a seamless experience for their users. Many offer intuitive control panels like cPanel or custom-built dashboards that simplify website management tasks. These interfaces often feature drag-and-drop functionalities, making it straightforward for users to upload files, manage domains, and configure email settings without needing technical expertise. Providers frequently include one-click installations for WordPress and other popular applications, streamlining the setup process. This feature allows users to launch their websites quickly without grappling with complex configurations. Additionally, many UK hosting companies offer extensive knowledge bases, video tutorials, and community forums, providing valuable resources for troubleshooting and site optimisation. For ongoing site maintenance, automated tools such as backup services and update notifications are commonly integrated. These tools ensure that sites remain secure and up-to-date with minimal manual intervention. Enhanced usability extends to performance monitoring features, enabling users to track metrics like site speed and uptime easily. Real-time analytics help identify potential issues before they impact the user experience, allowing for prompt resolution. By prioritising these user-friendly features, UK hosting providers make website management accessible, even for those with limited technical skills.
Case Studies: Success Stories from UK-Based WordPress Sites
The success of UK-based websites using WordPress hosting is evident through various case studies. Take "The Independent," a leading news outlet that utilises WordPress for its robust content management system. By leveraging advanced caching solutions and Content Delivery Networks (CDNs), they've optimised their site speed and user experience, accommodating millions of daily visitors efficiently. Another notable example is "Graze," the snack subscription service that has scaled its e-commerce operations seamlessly with specialised WooCommerce hosting. The integration of automatic backups, SSL certificates, and tailored support has allowed them to maintain a secure and efficient online store, boosting customer trust and engagement. Local educational institutions like "University of Oxford" have also benefitted from WordPress hosting. Utilising features such as staging environments and managed hosting services, they have created dynamic, user-friendly portals that cater to students and faculty alike. Small businesses like "BrewDog," a craft beer company, have taken advantage of developer-focused hosting to customise their websites extensively. This flexibility has enabled them to create unique, engaging online experiences that align with their brand identity. These examples demonstrate the diverse capabilities of WordPress hosting in the UK, catering to various industries and needs effectively.
Environmental Impact: Green Hosting Options in the UK
As environmental concerns take centre stage, many UK hosting providers are adopting eco-friendly practices to reduce their carbon footprint. These green hosting solutions often involve using renewable energy sources, such as wind or solar power, to operate data centres. Energy-efficient hardware and cooling technologies further minimise energy consumption, ensuring a more sustainable operation. Providers like GreenGeeks and Eco Web Hosting have made significant strides in this area, offering services that not only perform well but also contribute positively to the environment. Some companies even participate in carbon offset programmes, planting trees or investing in renewable energy projects to balance out their emissions. Additionally, hosting companies may implement policies to reduce waste, such as promoting digital documentation over printed materials and encouraging remote work to cut down on travel emissions. By choosing a green hosting provider, you can support these environmental initiatives, aligning your website with broader sustainability goals.
Final Thoughts: Choosing the Best WordPress Hosting for Your Needs
Selecting the best WordPress hosting in the UK can be a daunting task, given the myriad of options available. However, focusing on key aspects such as performance, security, customer support, and scalability can streamline your decision-making process. Performance is vital; ensure the provider offers advanced caching solutions, SSD storage, and local data centres to optimise loading times. Security should not be compromised, so look for features like SSL certificates, firewalls, and regular malware scans. Customer support is another crucial factor, particularly localised support that understands UK-specific challenges and regulations. 24/7 availability and multiple support channels can provide peace of mind and quick resolutions to any issues. Scalability is essential for future growth. Opt for a provider that offers seamless upgrade paths and flexible resource allocation to accommodate increasing traffic and storage needs. Specialised hosting options, such as WooCommerce hosting for e-commerce sites or developer-focused hosting, can offer additional benefits tailored to your specific requirements. Finally, consider the environmental impact. Green hosting options not only benefit the planet but can also enhance your brand's sustainability credentials. By weighing these factors carefully, you can find a WordPress hosting solution that aligns perfectly with your goals and ensures a smooth, secure, and efficient online presence.
#web hosting#cheap web hosting#hosting#managed wordpress hosting#website hosting#wordpress hosting#businesss#online businesses#cheap website hosting#online
2 notes
·
View notes
Text
Software of the Week: WingetUI / UniGetUI
Keeping all of the programs on your computer up to date is important for security reasons; just ask LastPass, the disgraced password manager that got hacked because an employee's personal computer was running an old version of Plex Media Server. The particular vulnerability that the hackers exploited had been patched almost 3 years earlier, but because the employee never bothered to update Plex, he never got the fix.
Every month that you leave software on your computer un-patched is time in which hackers may discover the vulnerability and start using it to attack computers. But how on earth can you even figure out which of your programs need updates? Doing that one by one takes forever, and THEN you still have to actually install those updates.
This is where software updaters are essential. On Windows, SUMO used to be among the best programs for the job, but it was discontinued in early 2024. I've been searching for a replacement for a while now, and I finally settled on WinGetUI (soon to be known as UniGetUI). A LOT more detail and some tips are under the readmore!
Details:
Purpose: Provide a unified frontend for multiple package managers on Microsoft Windows to simplify installing and updating software
OS Supported: Windows 10, 11
Installer Size: 76 MB
Country of Origin: Catalonia/Spain
Languages Supported: 16 languages fully, 24 partially
License: Freeware
Download Link: https://www.marticliment.com/wingetui/
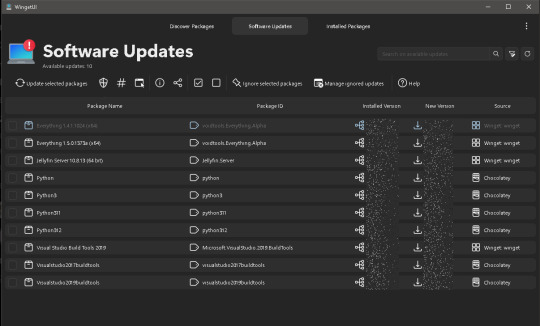
A LOT more detail and some tips are under the readmore!
Winget ("WIN-get") is the name of Microsoft Window's new-ish package manager, a program that itself takes care of installing and updating other software for you. Linux and Unix have had built-in package managers for decades, but Windows has been sorely lacking on that front until just recently. Winget provides the ability to install and update software, but it's a command line utility, meaning you have to type text into a command prompt in order to get winget to do anything for you.
WinGetUI is essentially just a nice interface using winget in the background; it shows you which programs you have installed, which ones have updates available, and it will even install the updates for you. That last part was a game changer for me personally as it saves me a lot of time (I have a LOT of programs and libraries installed on my computer).
The best part is the developer has added support for other package managers too. Computer language SDKs often come with their own package managers for downloading the little libraries that you can bundle with code that you write, and WinGetUI now supports most of them: npm, pip, .NET Tool, Chocolatey, scoop, Powershell Gallery, and it can even list software installed from the Steam shop or the Microsoft Store (though it can't update those ones for you). Incidentally, this is why the name is changing from WinGetUI to UniGetUI; it now supports a lot more package managers than just winget.
WinGetUI can even help you migrate software to a new computer. Simply install WinGetUI on your old computer, export a list of all of the software you have installed, then install WinGetUI on your new computer and import that list and then click install. You'll probably have to babysit it for a while because Windows will prompt you to give admin access to the installers that need it, but hey. At least you don't have to write down all the software you have and download and install each one by hand.
I do want to highlight that Microsoft is still working out the kinks in winget. Windows has existed for a long time and provided a lot of freedom in how you could install software. Multiple companies have made their fortunes just by providing custom installer software for Windows (InstallShield and NSIS being prime examples), so Microsoft has their work cut out for them trying to get all the different software manufacturers to list their software in the winget directory AND standardize their installers.
As such, you may run into issues like these:
WinGetUI lists a program you installed manually and tries to update it via winget; the installer succeeds, but because those installation methods are different, you end up with 2 copies of the software installed in different locations
WinGetUI fails to update a program because the hash of the downloaded installer doesn't match the hash that winget says it should have. This is usually a developer error
WinGetUI fails to determine whether some programs have updates available or not
WinGetUI downloads an installer/updater but it fails to run because it detects that the installation methods for that program are different (manual install vs. winget install)
Almost all of these can be resolved by uninstalling the manually installed version and reinstalling it using winget, either from the command line or just from WinGetUI. Once you do that one-time operation, the winget package manager (and by extension WinGetUI) should be able to handle everything from there on out. It will only get better too as winget usage becomes more common among software developers.
#software of the week#windows software#mine#wingetui#winget#package managers#microsoft windows#cybersecurity
3 notes
·
View notes
Text
What are the best Plesk reseller hosting services?
Plesk Web Hosting uses a Plesk control panel to let you handle all aspects of your website hosting requirements, including DNS records, email addresses, domain names, and more. Plesk is an easy-to-use control panel that guarantees website security, automates server tasks, and supports both Linux and Windows hosting. Plesk is best suited for you if you need to manage your multiple customer accounts seamlessly and automate your admin functions.

Plesk reseller hosting: What is it?
In order to meet the requirements of individuals and businesses that want to administer multiple websites on a single platform, the Plesk reseller hosting platform offers a solution that is not only effective but also flexible. This particular hosting option is going to be highly appealing to web designers, web developers, and businesses that want to provide hosting services to their consumers but do not want to deal with the hassle of managing individual accounts.
Regardless of whether you handle a small number of domains or a large portfolio of websites, the user-friendly interface and wide feature set of Plesk make it simple to streamline your web hosting operations. This is true regardless of the magnitude of your website portfolio. This article will give you the knowledge you need to make decisions that are based on accurate information by delving into the most significant features, benefits, and best hosting service providers of Plesk reseller hosting.
The advantages of Plesk reseller hosting-
The Plesk reseller hosting platform offers a plethora of benefits, which makes it an enticing option for online professionals who have extensive experience in the field. One of the most important aspects of this product is the fact that it has a user-friendly design, which makes it simpler to manage a variety of websites and accounts.
Customers have the ability to effortlessly manage databases, email accounts, and domains with the help of Plesk, which features an interface that is simple to use. Furthermore, the reseller plans include support for an unlimited number of domains. This enables resellers to provide their customers with the most affordable hosting pricing possible for multi-domain publishing operations.
Using this cloud management platform comes with a number of important benefits, one of which is the complete security measures that are built into Plesk. These features include firewalls, intrusion detection, and antivirus protection. These qualities assist in the safety of websites against the dangers that can be found on the internet.
As an additional benefit, Plesk is compatible with a wide range of applications and extensions, which enables customers to customize their hosting environment to meet the specific needs of their businesses.
Plesk reseller hosting gives resellers the ability to create unique hosting packages, efficiently allocate resources, and deliver dependable services to their customers. This is made possible by the usage of Plesk. As a consequence of this adaptability, scaling and expanding the hosting business is a far simpler process.
Features of Plesk reseller hosting-
Security features
Plesk reseller hosting has many security tools to protect your hosting environment. Firewalls in Plesk prevent unwanted access and cyberattacks. The software also supports SSL certificates for encrypted server-client communication. Intrusion detection and prevention systems in Plesk monitor for suspicious activity and automatically mitigate threats.
Antivirus and anti-spam capabilities are incorporated to safeguard your email services from dangerous assaults and undesirable information. Regular security updates and patches are provided to maintain the system's security against current vulnerabilities. Plesk lets you create user roles and permissions to restrict authorized users' access to sensitive control panel areas.
User-friendly interface
One of the major characteristics of Plesk reseller hosting is its user-friendly interface. Plesk's control panel is simple and efficient, even for web hosting beginners. Domain management, email configuration, and database administration are easily accessible from the dashboard. As a complete WordPress site update, security, and management solution, the WordPress Toolkit improves user experience. Users may manage their hosting environment right away, thanks to this simplified UI.
Plesk lets users customize the dashboard to their preferences and workflow. Additionally, the responsive design guarantees that the interface is accessible and functioning across many devices, including PCs, tablets, and smartphones. The Plesk reseller hosting interface makes managing multiple websites and customer accounts easy and boosts productivity.
Performance and reliability
Performance and reliability are key to Plesk reseller hosting. Compared to typical shared hosting, reseller hosting offers better scalability and control, making it a more powerful choice for managing several websites. User satisfaction and SEO rankings depend on fast loading times and high uptime, which the platform optimizes. Plesk optimizes server performance with smart caching and resource management. Plesk websites perform well even during traffic spikes with minimal downtime.
Plesk also enables load balancing and clustering to spread traffic between servers. Having no single server bottleneck improves dependability. The platform’s solid architecture also features automatic backups and restoration capabilities, providing peace of mind that your data is safe and can be retrieved promptly in case of an incident. These performance and stability characteristics make Plesk reseller hosting a reliable alternative for administering several websites, giving your clients continuous service.
Expanding your company's reseller hosting operations-
Scaling your services
Growing your business requires scaling your Plesk reseller hosting services. Start by evaluating your current resource utilization and discovering any restrictions in your existing configuration. To handle traffic and data storage, you may need to modify your hosting plan or add servers as your client base expands. Plesk lets you add CPU, memory, and bandwidth to customer accounts for easy scaling. Load balancing and clustering can also evenly distribute traffic across servers for better performance and reliability.
Consider broadening your service offerings by introducing new features such as better security solutions, premium assistance, or specialized hosting plans for specific sectors. To match client needs and industry developments, regularly review and update hosting packages. Scaling your services efficiently lets you accommodate customer growth while retaining performance and dependability.
Effective marketing strategies
Effective marketing strategies are crucial for expanding your Plesk reseller hosting business. Determine your target audience—small businesses, bloggers, or e-commerce sites—and personalize your marketing to them. Explain Plesk reseller hosting benefits in blog posts, tutorials, and guides. This draws customers and establishes your hosting authority. Social networking can expand your audience. To develop trust, provide updates, promotions, and client testimonials.
Email marketing campaigns with unique discounts or new features can also be beneficial. To increase your website's exposure to search engines, you should also spend money on search engine optimization or SEO. To draw in organic traffic, use keywords such as Plesk reseller hosting. In order to broaden your reach, lastly, think about forming alliances or working together with web developers and agencies. By putting these marketing ideas into practice, you can increase your clientele and income dramatically.
For better value, bundle
Another efficient strategy to expand margins and stand out is by combining domains with critical web services. Besides delivering additional value to your consumer, bundling also boosts the average order value, which is vital in a market with intrinsically tiny per-product margins.
Web hosts frequently purchase SSL certificates, DDoS protection, email services, and CDNs as part of bundles. Although popular, these products are highly competitive. Besides bundling products, you might offer specialist products like DMARC or VPN services that your competitors may not offer.
Improving customer satisfaction
Enhancing customer experience is important to the success of your Plesk reseller hosting business. Start by giving your clients an easy-to-use control panel for managing their websites, email, and other services. Comprehensive documentation and tutorials can help clients solve common problems on their own. Give customers several support channels, including live chat, email, and phone, and answer questions quickly. Call clients by name and understand their needs.
Request feedback via surveys or direct communication to identify areas for improvement. Furthermore, providing value-added services like performance optimization, security upgrades, and automated backups can greatly enhance the general clientele experience. Providing customers with information about upgrades, new features, and maintenance plans fosters openness and confidence. By focusing on client satisfaction, you may develop long-term connections and drive favorable word-of-mouth referrals.
Best Plesk reseller hosting service providers-
MyResellerHome
One of the most well-known resale hosts is MyResellerHome. Every reseller plan from MyResellerHomecomes with a free domain broker and a free domain name for life. MyResellerHome has a great name for being innovative, dependable, and safe. This is important when you agree to be a reseller for a long time with a company. It is known to release new versions of PHP and MySQL faster than other hosts. With white-label billing, you can give your customers this benefit. A free WHMCS and cPanel license comes with most of MyResellerHome’s Hosting reselling plans.
AccuWebHosting
AccuWebHosting takes the tried-and-true approach of giving shared Linux reseller accounts cPanel and shared Windows reseller accounts Plesk. Although AccuWebHosting has a lot of great features like shared Linux and Windows servers and Windows VPS servers, dealers really like the company's hardware, data center engineering, and customer service.
ResellerClub
ResellerClub's plans come with the Plesk control panel, and you can choose from three different registration options: WebAdmin, WebPro, or WebHost. Business owners who want to run a shared Windows server environment can get Windows reseller products that come with an endless number of Plesk control panels.
InMotionHosting
In its reseller hosting plans, InMotion Hosting gives you a free WHMCS license. These plans use the same NVMe SSD hardware that a lot of users swear by. At InMotion Hosting, there are four main levels of reseller bills that go up to 100 cPanel licenses.
Conclusion-
When looking for the best Plesk reseller hosting, stability, performance, scalability, and support are crucial. Each hosting provider has unique characteristics, and choosing one that meets your demands can greatly impact your reseller business. After careful consideration, MyResellerHome is the best Plesk reseller hosting option. MyResellerHome is the top Plesk reseller provider, giving you the tools and resources to succeed in the hosting industry with its powerful infrastructure, excellent customer service, and extensive range of reseller-focused features.

Janet Watson
MyResellerHome MyResellerhome.com We offer experienced web hosting services that are customized to your specific requirements. Facebook Twitter YouTube Instagram
1 note
·
View note
Text
Discovering the Best Reseller Hosting with WHMCS Integration
In the fast-evolving landscape of web hosting, finding the perfect reseller hosting solution with seamless WHMCS integration can be a game-changer for businesses aiming to streamline their operations. At l3webhosting.com, we understand the significance of a robust hosting infrastructure coupled with WHMCS capabilities. In this article, we delve into the intricacies of WHMCS integration, uncovering why it's crucial for reseller hosting success.
Understanding WHMCS Integration
What is WHMCS?
WHMCS, or Web Host Manager Complete Solution, is a comprehensive client management and billing platform designed for web hosting businesses. It serves as the backbone for automating various tasks, including invoicing, ticketing, and provisioning, ensuring a seamless experience for both providers and clients.
Why WHMCS Integration Matters
Automated Billing and Invoicing: WHMCS simplifies the billing process, automating recurring payments, and generating invoices effortlessly. This not only saves time but also reduces the chances of errors, fostering a reliable financial system.
Client Management: Efficient client management is the cornerstone of successful reseller hosting. WHMCS provides a centralized platform to manage clients, their accounts, and support requests, allowing for a streamlined and organized workflow.
Product Provisioning: With WHMCS, reseller hosting providers can automate the provisioning of hosting accounts. This means faster and more efficient delivery of services, enhancing the overall client experience.
Unveiling the Best Reseller Hosting with WHMCS Integration
Features to Look For
When on the quest for the best reseller hosting with WHMCS integration, consider the following features:
Scalability: A top-notch reseller hosting solution should offer scalability to accommodate the growth of your business. Look for providers that allow seamless upgrades to higher resource plans as your client base expands.
Server Performance: Speed and reliability are paramount. Opt for a hosting provider that ensures optimal server performance, minimizing downtime and providing a smooth experience for your clients.
WHMCS Compatibility: Ensure that the hosting provider's infrastructure is fully compatible with the latest WHMCS version. This guarantees a hassle-free integration, eliminating any potential compatibility issues.
WHMCS Integration at l3webhosting.com
At l3webhosting.com, we pride ourselves on offering reseller hosting solutions that seamlessly integrate with WHMCS, providing our clients with a powerful and user-friendly experience. Here's why our WHMCS integration stands out:
Zero Configuration Hassles: Our reseller hosting plans come with pre-configured WHMCS setups, eliminating the need for intricate manual configurations. You can focus on your business while we take care of the technicalities.
24/7 Technical Support: Our dedicated support team is available around the clock to assist with any WHMCS-related queries or issues. We understand the importance of prompt and effective support in the dynamic world of web hosting.
Regular Updates: We stay ahead of the curve by ensuring our WHMCS integration is always up to date. This guarantees access to the latest features, security patches, and enhancements, keeping your hosting environment secure and efficient.
Conclusion
In the realm of reseller hosting, choosing a provider with impeccable WHMCS integration can make all the difference. At l3webhosting.com, our commitment to delivering top-tier hosting solutions, coupled with seamless WHMCS integration, positions us as the ideal choice for businesses seeking excellence in their hosting endeavors.
2 notes
·
View notes
Text
How to Build a Safe and Secure Digital Wallet

In today’s digital era, convenience and efficiency are driving the shift towards cashless transactions, and digital wallets have become an essential part of our daily lives. As these digital wallets store sensitive financial information, it is crucial to prioritize security and safety during their development. In this blog, we will explore the key elements necessary to build a safe and secure digital wallet, ensuring users’ confidence and trust in your platform.
Strong Authentication Mechanisms: A robust authentication system is the foundation of a secure digital wallet. Implement multi-factor authentication (MFA) to require users to provide multiple forms of identification before accessing their accounts. MFA may include a combination of passwords, biometric data (fingerprint, facial recognition), and one-time passwords (OTP) sent to registered mobile numbers or email addresses. This layered approach significantly reduces the chances of unauthorized access.
Encryption and Data Protection: Protecting sensitive user data is paramount in a digital wallet’s security. Utilize strong encryption algorithms to secure data both at rest and during transmission. Adopt industry-standard encryption protocols like SSL/TLS to safeguard communication between the app and backend servers. Additionally, never store plain-text passwords or sensitive information in the database; instead, use strong hashing techniques.
Regular Security Audits and Penetration Testing: Frequent security audits and penetration testing are essential to identify vulnerabilities and weaknesses in your digital wallet’s infrastructure. Engage with qualified security professionals to conduct thorough assessments and address any discovered issues promptly. Regular testing ensures your platform remains resilient against emerging threats and hacker attempts.
Secure Development Practices: Adopt secure development practices from the outset to build a strong security foundation. Train your development team on secure coding practices, ensuring they follow the latest OWASP guidelines. Implement code reviews and conduct regular security awareness training to ensure everyone involved understands the importance of security in the development lifecycle.
End-to-End Encryption for Transactions: Ensure that all transactions, whether online or in-store, are encrypted end-to-end. This encryption prevents unauthorized parties from intercepting and manipulating sensitive transaction data, such as credit card details or personal identification numbers.
Regular Software Updates: Stay vigilant in updating your digital wallet application and backend servers with the latest security patches and software updates. Outdated software can expose your platform to known vulnerabilities, making it an easy target for cyberattacks. Enabling automatic updates can streamline this process and keep your app’s security up to date.
Secure Storage of Payment Information: When storing payment information, follow Payment Card Industry Data Security Standard (PCI DSS) compliance guidelines. If possible, avoid storing cardholder data and instead utilize tokenization or outsourcing payment processing to certified third-party providers. This approach minimizes the risks associated with storing sensitive financial information.
User Education and Awareness: Promote user education and awareness about digital wallet security best practices. Educate users about the risks associated with phishing attacks, using unsecured Wi-Fi networks, and sharing sensitive information with unknown sources. Regularly communicate security updates and tips to ensure users can safeguard their accounts effectively.
Building a safe and secure digital wallet is a critical responsibility for any fintech company. By adopting strong authentication mechanisms, encryption, and secure development practices, you can create a robust platform that users can trust. Regular audits, updates, and user education play pivotal roles in keeping the digital wallet ahead of emerging threats.
Remember, security is an ongoing process, and a proactive approach is essential to maintaining a trusted and reliable digital wallet in an ever-evolving digital landscape.
1 note
·
View note
Text
Cloud-Based ERP vs On-Premise ERP: Which Is Better for Abu Dhabi SMEs?
Selecting the right ERP (Enterprise Resource Planning) deployment model is one of the most important decisions for small and medium-sized enterprises (SMEs) in Abu Dhabi.
Should you choose Cloud-based ERP or On-premise ERP?
Both options offer powerful tools to manage finance, HR, sales, inventory, and operations. But they come with different costs, security requirements, and scalability benefits.
This guide breaks down the pros and cons of each model—so you can make the best choice for your UAE business.
✅ What Is Cloud-Based ERP?
Cloud ERP is hosted on the vendor’s servers and accessed over the internet. Your business pays a subscription fee and typically accesses the system via a browser or mobile app.
Key features:
Hosted on secure, remote servers
Accessible from anywhere
Vendor handles maintenance and updates
✅ What Is On-Premise ERP?
On-premise ERP is installed on your company’s own servers and infrastructure. Your business buys licenses up-front, manages the system internally, and is responsible for maintenance and security.
Key features:
Installed locally on company servers
Full control over data and system
Customizable, but higher upfront cost
⚖️ Cost Comparison
💰 Cloud ERP Abu Dhabi
✅ Lower upfront costs (subscription-based pricing) ✅ Predictable monthly/annual fees ✅ No need for expensive on-site hardware ✅ Vendor handles updates and maintenance
Best for: Startups and SMEs wanting affordable, scalable solutions without large capital investment.
💰 On-Premise ERP UAE
✅ High upfront costs for licensing, servers, infrastructure ✅ Ongoing costs for IT staff, upgrades, maintenance ✅ No recurring subscription fees (one-time license, with optional support contracts)
Best for: Larger companies with existing IT teams and budgets for infrastructure.
⚖️ Scalability and Flexibility
🌐 Cloud ERP
✅ Easily add new users or modules ✅ Quickly scale up or down as your business grows ✅ Ideal for multi-location businesses in Abu Dhabi and the UAE
Example use case: A retailer expanding from Abu Dhabi to Dubai can instantly add branches to the ERP without new servers.
🏢 On-Premise ERP
✅ Scaling requires buying and installing new hardware ✅ Adding users/modules often needs IT involvement ✅ More time-consuming for multi-site expansion
Example use case: A manufacturing company with a single, secure location may not need rapid scaling.
⚖️ Security Considerations
🌐 Cloud ERP
✅ Vendors provide advanced, enterprise-grade security ✅ Regular security patches and updates ✅ Data backup and disaster recovery included
UAE consideration: Ensure the provider complies with UAE data hosting and privacy requirements. Some vendors offer local data centers.
🏢 On-Premise ERP
✅ Full control over data storage and security policies ✅ Must manage own backups, patches, and security monitoring ✅ May suit businesses with sensitive data (e.g. government contractors)
UAE consideration: Some industries require strict data residency—on-premise can guarantee local data storage.
⚖️ Customization
🌐 Cloud ERP
✅ Highly configurable but sometimes less customizable at code level ✅ Limited changes to core system to maintain compatibility with updates
Best for: Businesses that want best practices out-of-the-box without deep customization.
🏢 On-Premise ERP
✅ Deep, code-level customization possible ✅ Fully tailored to business workflows
Best for: Complex industries with unique processes or legacy integrations.
⚖️ Compliance and Local Regulations
✅ Both cloud and on-premise solutions can support UAE VAT compliance, Arabic language interfaces, and local reporting standards.
However:
Cloud vendors must guarantee data residency (some UAE businesses require data stored locally).
On-premise ERP gives maximum control for meeting industry-specific compliance needs.
✅ Which Is Better for Abu Dhabi SMEs?
✅ Choose Cloud ERP if:
You want low upfront cost and predictable fees
Need easy remote access and scalability
Prefer minimal IT maintenance
Have straightforward, standardized workflows
✅ Choose On-Premise ERP if:
You need maximum data control and local storage
Have strict industry compliance requirements
Require deep, custom-built features
Have existing IT infrastructure and budget
📌 Final Thoughts
No one-size-fits-all answer exists. The best ERP for Abu Dhabi SMEs depends on your goals, budget, industry, and regulatory requirements.
At Emirtech Technology, we help UAE businesses evaluate, implement, and support both Cloud-based and On-premise ERP solutions.
📞 Ready to Choose the Right ERP for Your Business?
Contact Emirtech Technology today for a free consultation. ✅ We’ll help you weigh the options and deploy the ERP that’s best for you.
0 notes
Text
Server Management: A Complete Guide for Businesses
In today’s digital-first world, server management is a critical aspect of maintaining a reliable, secure, and high-performing IT infrastructure. Whether you’re running a small business website or a large-scale enterprise application, efficient server management ensures smooth operations, minimizes downtime, and enhances security.
What is Server Management?
Server management refers to the process of monitoring, maintaining, and optimizing servers to ensure they operate efficiently. This includes hardware and software management, security updates, performance tuning, and troubleshooting.
Key Components of Server Management:
Hardware Monitoring – Checking CPU, RAM, disk usage, and temperature. Software Updates – Applying OS patches, security fixes, and application updates. Security Management – Firewalls, intrusion detection, and malware protection. Backup & Disaster Recovery – Regular data backups and recovery plans. Performance Optimization – Load balancing, caching, and resource allocation. User & Access Control – Managing permissions and authentication.
Why is Server Management Important?
Prevents Downtime – Proactive monitoring reduces unexpected crashes. Enhances Security – Protects against cyber threats and data breaches. Improves Performance – Optimized servers ensure faster response times. Cost Efficiency – Reduces hardware failures and unnecessary expenses. Compliance – Helps meet industry regulations (GDPR, HIPAA, etc.).
Types of Server Management
1. On-Premises Server Management
Managed in-house by an IT team.
Full control over hardware and software.
Higher upfront costs but more customization.
2. Cloud Server Management
Managed via cloud providers (AWS, Azure, Google Cloud).
Scalable, flexible, and cost-effective.
Requires expertise in cloud platforms.
3. Hybrid Server Management
Combines on-premises and cloud servers.
Balances security, performance, and cost.
4. Managed Hosting Services
Outsourced to third-party providers.
Ideal for businesses without an IT team.
Best Practices for Effective Server Management
Automate Routine Tasks – Use scripts for backups, updates, and monitoring. Monitor Server Health – Tools like Nagios, Zabbix, or Prometheus help track performance. Implement Strong Security – Use firewalls, SSL certificates, and regular audits. Schedule Regular Backups – Ensure data recovery in case of failures. Optimize Resource Usage – Balance workloads to prevent bottlenecks. Document Configurations – Maintain logs for troubleshooting and audits.
Top Server Management Tools
🛠 Monitoring: Nagios, SolarWinds, Datadog 🛠 Automation: Ansible, Puppet, Chef 🛠 Security: Fail2Ban, Snort, Wazuh 🛠 Backup: Veeam, Acronis, Rsync
In-House vs. Outsourced Server Management
AspectIn-HouseOutsourcedCostHigher (hardware & staff)Pay-as-you-goControlFull controlLimited customizationExpertiseRequires skilled IT teamManaged by expertsScalabilityLimited by hardwareHighly scalable
When Should You Consider Professional Server Management?
Your business is growing, and server demands are increasing.
You lack an experienced IT team.
Security and compliance are top priorities.
Frequent downtime is affecting operations.
Final Thoughts
Effective server management is crucial for business continuity, security, and performance. Whether you manage servers in-house or outsource to experts, following best practices ensures a stable and secure IT environment.
Need help managing your servers? Consider managed hosting or cloud solutions to streamline operations and focus on growing your business!
0 notes
Text
MikroTik Wholesale Distributor UAE: Your Gateway to Reliable Networking Solutions
As a leading MikroTik distributor Africa, many businesses rely on authorized distributors to procure authentic MikroTik routers, switches, and accessories. These distributors not only provide a comprehensive product range but also offer valuable technical support, ensuring that clients can deploy their networks efficiently. Whether you are setting up a small office network or managing an extensive service provider infrastructure, partnering with a reputable MikroTik wholesale distributor UAE guarantees access to the latest technology and reliable supply chains.
MikroTik Router Setup Dubai: Simplifying Network Configurations
Setting up MikroTik routers in Dubai is straightforward when following proper configuration procedures. MikroTik routers are popular for their flexibility, advanced features, and affordability, making them suitable for various applications—from small businesses to large enterprises.
To begin with, ensure you have access to the MikroTik RouterOS interface, which is typically managed via WinBox or through a web browser. The basic steps for MikroTik router setup Dubai include:
Initial Access: Connect your computer to the MikroTik router via Ethernet. Use WinBox or access the router’s default IP address (usually 192.168.88.1) through a web browser.
Login Credentials: Use the default username and password (admin/admin) or the credentials provided by your distributor.
Configure Basic Settings: Assign IP addresses, set up DHCP servers, and configure interfaces based on your network architecture.
Security Measures: Change default passwords, enable firewalls, and set up VPNs if necessary to secure your network.
Advanced Features: Utilize MikroTik’s features such as QoS, VLANs, or hotspot configurations to optimize network performance.
For those unfamiliar with MikroTik's complex configurations, consulting with a professional or referring to detailed guides can streamline the process. Many MikroTik distributor Africa and MikroTik wholesale distributor UAE offer technical support and training to facilitate smooth deployments in Dubai and across the region.
MikroTik Router Configuration Dubai: Best Practices
Proper MikroTik router configuration Dubai involves understanding your network's specific requirements and tailoring the setup accordingly. Here are some best practices:
Segmentation: Use VLANs to segment different parts of your network for security and performance.
Bandwidth Management: Implement QoS policies to prioritize critical applications.
Monitoring: Enable logging and use MikroTik’s monitoring tools to track network health and troubleshoot issues proactively.
Regular Updates: Keep your RouterOS firmware up-to-date to benefit from security patches and new features.
Backup Configurations: Always save configurations before making significant changes to prevent data loss.
Many MikroTik distributors in Dubai and Africa offer pre-configured devices or professional configuration services, ensuring your network is optimized from the start.
Why Choose a Reliable MikroTik Distributor?
Partnering with a trusted MikroTik wholesale distributor UAE or MikroTik distributor Africa is vital for ensuring genuine products, competitive pricing, and ongoing support. Authorized distributors provide access to the latest MikroTik hardware, software updates, and technical assistance, which are essential for maintaining a secure and efficient network.
In summary, whether you're setting up a small office in Dubai or managing a large network across Africa, understanding MikroTik router setup Dubai and MikroTik router configuration Dubai is critical to success. Reliable distribution channels are equally important to guarantee you receive authentic equipment and expert support.
0 notes
Text
Siebel CRM 25.5 Update: What You Need to Know
The world of customer relationship management doesn’t stand still—and neither does Oracle’s Siebel CRM. With its continuous delivery model, Siebel keeps evolving every month to ensure businesses run faster, smoother, and smarter. In May 2025, Oracle released Siebel CRM 25.5, a version that, while not feature-heavy, is essential for maintaining a solid, optimized system. So, what does this update bring? Should you upgrade? And how can you make the most of it?
Let’s break it all down.

Why 25.5 Matters—Even Without Major New Features
Let’s be upfront—Siebel CRM 25.5 doesn’t bring major new modules or flashy user interface changes. But here’s why that’s actually a good thing.
This release is maintenance-driven—focusing entirely on bug fixes, performance refinements, and stability improvements. In an enterprise CRM world, these "behind-the-scenes" enhancements are just as important (if not more) than new features. Because here's the thing, when systems are running mission-critical processes, even the smallest glitch can snowball into major disruption. An update like 25.5 helps prevent that.
Oracle’s Continuous Delivery Model: A Quick Refresher
If you're new to Siebel's update rhythm, here’s a quick snapshot.
Oracle adopted a continuous delivery model for Siebel CRM back in 2018. Since then, a new update rolls out every month, each labelled as a version—like 25.1 for January 2025, 25.2 for February, and so on. With 25.5 being the 83rd update since the model began, it reflects Oracle’s commitment to ongoing, incremental innovation.
The benefit is you get improvements continuously, rather than waiting for large annual releases that can be costly and complex to adopt.
What’s Inside Siebel CRM 25.5?
While 25.5 isn’t about introducing new tools or major functionality, it still brings several key enhancements you shouldn’t ignore:
Performance Fixes
Minor glitches and inefficiencies can drain productivity over time. 25.5 includes refinements that speed up transactions, UI responsiveness, and background processes.
Security Patches
System security is non-negotiable. This update ensures any vulnerabilities discovered in recent months are patched, reducing the risk of exploits or breaches.
Stability Enhancements
Database interactions, integration flows, and workflow engines all benefit from increased reliability—especially important if you're using custom scripts or third-party integrations.
How Should You Approach This Update?
You might be thinking, “If it’s just fixes, do I really need to update right now?”
Short answer: yes—but strategically.
Here’s a step-by-step approach to rolling out Siebel CRM 25.5 effectively:
1. Review the Release Notes
Head to Oracle’s official support portal or documentation centre and thoroughly review what’s included in 25.5. Pay attention to:
Resolved bugs
Known issues
component-specific changes (e.g., Marketing, Service, CTI)
2. Test in a Sandbox Environment
Don’t rush straight to production. Test in a non-live sandbox that mirrors your customized environment. Validate that:
Your scripts and workflows still function as expected
Third-party integrations behave normally
Key reports and dashboards load correctly
3. Build a Rollout Plan
Once you're confident in testing, plan your rollout:
Schedule the update during off-peak hours
Prepare rollback procedures, just in case
Alert key users about changes (even if minimal)
4. Train Your Staff If Needed
Even if functionality hasn’t changed, performance and behaviour might feel different—especially for power users. A brief walkthrough or internal update can smooth the transition.

Looking Ahead: What Comes After 25.5?
Though 25.5 is a maintenance release, Oracle has hinted at feature-rich updates in the pipeline for future versions. Some anticipated developments for Siebel CRM 25.6 and beyond include:
Updates to the Approval Manager installer
Enhancements to Email Marketing Server deployment
Streamlined deployment processes
Extended support for OpenUI customizations
By staying current with maintenance updates like 25.5, you’ll be ready to embrace these enhancements without delays or compatibility concerns.
Why You Shouldn’t Skip Maintenance Releases
Here’s a common trap, many businesses delay updates because there’s "nothing new" they can see. But skipping minor versions often leads to technical debt, where:
Bug fixes pile up
Compatibility with browsers or middleware breaks
Security patches are missed
And then? You’re forced into a larger, more expensive upgrade later—often under pressure. Regular updates like 25.5 keep your CRM lean, secure, and future-ready.
Partner Spotlight: BriskWinIT Solutions Can Help
Upgrading Siebel—no matter how small the update—takes planning and precision. That’s where BriskWinIT Solutions comes in. As a trusted partner in Siebel CRM implementation, upgrades, and managed support, we help businesses like yours:
Assess the impact of new releases
Apply updates with minimal disruption
Customize features to suit evolving business needs
Provide proactive monitoring and issue resolution
Whether you need a full upgrade or just assistance testing 25.5 in your environment, BriskWinIT Solutions is here to support every step.
Is Siebel CRM Still Worth It in 2025?
Great question—and one we hear often. Despite the rise of modern CRMs, Siebel remains a powerhouse for many industries, especially in telecom, financial services, public sector, and utilities. Because of its,
Robust process automation
Deep industry-specific customization
Scalability for large, complex organizations
Offline capabilities for field service
And with Oracle’s ongoing commitment to updates (like 25.5), Siebel continues to evolve with modern architecture, cloud integrations, and Open UI flexibility.
What You Can Do Next
Here are a few questions to help guide your next move:
Are you currently on Siebel 25.4 or earlier?
Have you tested the 25.5 release in a sandbox?
Is your IT team prepared for continuous delivery processes?
Do you have a roadmap for upcoming monthly updates?
If any of these questions give you pause, it may be time to review your upgrade strategy—or bring in expert help.
Final Thoughts: Maintenance is Momentum
Siebel CRM 25.5 might not make headlines, but it does something more important, it keeps your CRM ecosystem strong, secure, and scalable. In an enterprise environment, success often hinges on the little things—fewer bugs, faster processes, better security. This update delivers all of that and more.
So don’t wait for a big feature drop to take action. Let 25.5 be your reminder that maintenance updates are a key part of digital growth.
Need help with your Siebel upgrade strategy?
BriskWinIT Solutions is ready to support your CRM journey—whether you're upgrading, customizing, or just getting started. Let's make Siebel work smarter for your business. Reach out to BriskWinIT Solutions today — and take the next step with confidence.
0 notes
Text
Security Best Practices in Custom Website Development
In today’s digital age, your website is more than just a virtual business card — it’s a powerful platform that interacts with users, stores sensitive data, and supports business operations. As a leading custom website development company, Kwebmaker understands the critical importance of security in every phase of website development.
Custom websites are tailored to meet specific business needs, but with customization comes the responsibility of ensuring airtight security. Below are the top security best practices that Kwebmaker implements in custom website development projects to protect businesses and their users.
1. Secure Code Practices
The foundation of any secure website lies in its code. Our developers follow secure coding guidelines and frameworks to prevent common vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). Regular code reviews and automated scanning tools help us identify and fix security issues early in the development cycle.
2. HTTPS and SSL Encryption
Every website developed by Kwebmaker comes with HTTPS and SSL encryption by default. These protocols ensure that all data transferred between the user and the server remains encrypted and protected from eavesdropping and tampering.
3. Authentication and Authorization Controls
We implement strong user authentication protocols such as two-factor authentication (2FA), password strength enforcement, and session timeout mechanisms. Role-based access control (RBAC) is also configured to ensure users only access the data and features they are authorized to use.
4. Regular Security Updates and Patch Management
As a proactive custom website development company, Kwebmaker ensures that all third-party libraries, CMS platforms, and frameworks are regularly updated. Security patches are applied promptly to avoid any known vulnerabilities being exploited.
5. Data Validation and Sanitization
User inputs are thoroughly validated and sanitized on both the client and server sides to prevent malicious code from compromising the system. This prevents injection attacks and ensures data integrity throughout the application.
6. Database Security
Kwebmaker secures databases through encryption, access control, and optimized query design to prevent data leaks and minimize risks. Sensitive data such as passwords and personal information is stored using robust hashing and encryption techniques.
7. Secure File Uploads
File uploads are common in many custom websites, but they pose a security risk if not handled properly. We enforce strict file validation, limit file types, and scan for malware to ensure only safe files are stored on the server.
8. Backup and Disaster Recovery
Our websites are built with disaster recovery in mind. Regular automated backups and secure storage allow us to recover quickly from data loss, breaches, or system failures — giving our clients peace of mind.
9. Security Testing and Monitoring
Before launch, every custom website undergoes rigorous security testing, including penetration testing and vulnerability scanning. Post-launch, continuous monitoring tools are used to detect suspicious activity in real time.
Conclusion
Security is not a one-time task — it’s an ongoing commitment. At Kwebmaker, we go beyond just building custom websites. As a trusted custom website development company, we build secure digital experiences that empower businesses to grow confidently in the digital landscape.
Looking to build a secure, scalable website tailored to your business? Contact Kwebmaker, your reliable custom website development company, today!
To Know More: https://kwebmaker.com/services/best-custom-website-design-development-services-agency-in-india/

0 notes
Text
What Makes VPS Hosting A Cost-Effective Hosting Solution
Nothing is more thrilling than putting up a new website and then seeing it take off and succeed. After the website takes off and becomes popular, you'll see a rise in sales as well as thousands of daily visitors. Purchasing affordable VPS hosting is similar to renting a specific area on a shared space that is yours alone. Every shared area on the physical server is separate from the others, has its operating system, and can execute any app that is compatible with it. Supporting an expanding website is of utmost importance.

VPS service is essential to the growth of a business and contributes to an increase in traffic. In the continually evolving and quickly expanding digital landscape, where every company is fighting to have a solid online presence. And individuals are working hard to incorporate the touch-basing idea into every part of their lives. Through social media, they may stay in touch with friends, family, and loved ones and order nearly anything, including food, electronics, everyday necessities, and gadgets. Businesses now need websites due to the digital expansion, which means they also need stable, dependable, and affordable hosting providers.
VPS hosting: what is it?
One of the many virtual servers that can be built on a single physical server is a virtual private server or VPS. Because you use a portion of the physical server, it's similar to shared hosting. But with VPS, you get a lot more resources than you would with shared hosting. Unlike shared hosting, each virtual private server is capable of running its operating system, which gives you more flexibility to install any software you might require for your website. Despite the shared environment in which VPS operates, user activity has no bearing on performance. It wouldn't be incorrect to compare VPS hosting to a miniature dedicated server.
What Features Make VPS Hosting an Extremely cost-effective Business Solution?
The most significant benefit of selecting affordable VPS hosting can be financial savings. The cost of VPS plans is significantly less than that of dedicated hosting options. When you join up for a VPS hosting, you are likely to receive nearly identical services to those of dedicated hosting, but at significantly lower costs.
You can be certain of receiving the best web hosting security, dependability, and assistance when you choose a reputable and trustworthy host.
The most scalable choices for expanding any organization are VPS plans. Some businesses begin with simple blogs or static web pages. Cheap shared hosting plans can be used to maintain these. Shared hosting, however, won't provide you with the adequate resources that an e-commerce website requires. Therefore, cheap shared web hosting is best suited for start-ups and smaller companies with tighter budgets. Because they cannot provide sufficient resources at cheap prices, therefore, virtual private servers are an affordable and best option.
Different kinds of VPS hosting exist:
VPS hosting services may be a suitable choice for your company since they provide a solid mix of price and flexibility. The best VPS hosting providers provide bandwidth, RAM, and storage on both managed and unmanaged plans.
Managed VPS hosting
Managed VPS hosting is beneficial for site owners with fewer staff or less technical expertise. IT specialists reduce your workload with managed VPS hosting by maintaining your server and looking after your virtual server. What to anticipate from a web hosting provider is as follows:
Initial server setup: To set up the server, you must follow a few procedures while launching your website on a VPS, such as installing your operating system, applications, control panel, and server software. A managed host will handle this.
Updates: In a similar vein, you will be taken care of for all application and OS updates, as well as continuous server optimization.
Security patches: Security updates for your operating system and essential server software are installed and updated on your behalf.
Monitoring: Keeps an eye out for early indicators of malicious attacks and hardware breakdown.
Automated backups: You can restore your website to a previous version in case something goes wrong.
Find out what degrees of management your VPS hosting company offers by contacting them.
Cost vs. flexibility is the trade-off between managed and unmanaged hosting. Of course, unmanaged services are significantly less expensive than managed plans, but there's a catch: in order to keep a server safe from potential threats and operating properly, you either need to be an expert in technology or be ready to pay someone who is.
Unmanaged VPS hosting
When you use an unmanaged virtual private server (VPS), your web hosting provider installs the operating system, and you, the site owner, control the server's numerous components, including:
Installing programs, maintaining software updates, and using your control panel.
Deploying security patches, addressing error messages, and keeping an eye out for security concerns.
You won't receive much, if any, assistance from your host in the event of an outage or hardware malfunction.
Configuration, upkeep, and any upgrades you may wish to see for your server.
You assume all responsibility for configuring backup services for your website.
It is advised for website owners with technical expertise to do this.
Reasons why VPS is the best choice for growing websites?
Cost-Effectiveness:
The primary goal of expanding businesses is to reduce their IT expenses and achieve maximum cost-effectiveness. Expanding business want to save money on paying for a dedicated server when their website doesn't require one. In this case, VPS hosting offers a cost-effective and capacity-efficient intermediate alternative between shared and dedicated hosting. Affordable VPS hosting is ideal for newly established websites and provides you with a good idea of how cost-effective it is.
Better Performance:
Organizations decide to migrate their websites to a dedicated virtual private server (VPS) due in large part to the VPS's evident performance advantages over shared servers. Your website will need more resources as it gets bigger in order to manage the increased traffic. However, while utilizing a shared solution, additional resources are only sometimes available. Other websites housed on the same server may also affect the performance of your website, causing issues like poor loading times and website outages. You won't have to worry about the server's capacity to accommodate additional website visits when you use cheap VPS hosting because you have dedicated resources.
Easily Scalable:
The scalability of best VPS hosting is another important advantage. With shared hosting, you have limited access to resources, and it could be challenging to scale up as your website grows. However, when your website traffic rises and your needs expand, you can quickly scale up your CPU, RAM, disk space, and bandwidth with a VPS. Your website will always have the resources it needs to function at its best, thanks to this scalability.
Dedicated resources:
To put it occasionally, certain software might not function, which could cause webpages to load slowly. Growing websites, particularly business websites, are not supported in this environment. A physical server is shared while using a virtual private server (VPS), yet each VPS is assigned specific resources that are not available for use by any other nearby server.
Customizable Server:
The best virtual private servers (VPS) offer greater flexibility and may be tailored to meet the needs of your website better. Because the server is shared with other websites, when you utilize shared hosting, you have less control over it, which might become problematic as your website expands. It is helpful to install custom software or configure the server environment, and a VPS can be fully customized to meet the needs of your particular application. If you require assistance with setup, a hosting company can assist you.
Strong security:
One of the most important things that any website owner should have been excellent security. Cheap VPS hosting is safer and more dependable than shared hosting. Typically, the VPS operates in a separate, segmented virtual environment. The host installs the necessary software layers to allocate specific areas of the server to you. While shared hosting is secure as well, there are instances where using the same server presents challenges. With VPS hosting, you may scale the server to meet your business needs and enhance its security at any moment. Your VPS account will never be impacted in any way by malware infecting another VPS account on the server.
Managed Service:
By switching from a shared server, you can investigate your alternatives for managed hosting. With a fully managed VPS hosting plans, you can concentrate on other facets of your company while a group of professionals takes care of your server management. Your website will always be up and operating because the VPS hosting provider will handle everything, including software installations, security, server maintenance, and backups. The ongoing support you get will help prevent common problems when your business grows, and more people visit your website.
Complete Access:
Despite sharing the same physical server, a cheap VPS hosting plan is separate from other accounts and gives you greater control over your partition. You will have full access to all resources and files on the operating system when you use VPS. There is complete administrative control with VPS plans. This lets you install and run other software, as well as configure and customize your server to your liking. It also gave you more access to your website so you could test apps more successfully and experiment with more complex coding. Although single-use dedicated server hosting is also accessible, virtual private server (VPS) hosting is more significant.
Conclusion:
VPS hosting services are important for clients whose websites and enterprises are expanding quickly. With affordable VPS hosting, you may obtain the best performance at the most reasonable prices. Thus, go with best VPS hosting right now if you own a developing website, have a small capital commitment, and wish to maintain control over all of your hosting requirements.

Janet Watson
MyResellerHome MyResellerhome.com We offer experienced web hosting services that are customized to your specific requirements. Facebook Twitter YouTube Instagram
1 note
·
View note
Text
Fortifying Your Online Presence Top Web Security Solutions to Protect Your Digital Assets
In today’s digital landscape, a strong online presence is essential but it also comes with significant security risks. Cyber threats like hacking, data breaches, malware, and phishing attacks can compromise your website, damage your brand, and result in financial loss. That’s why implementing robust web security solutions is more critical than ever. From firewalls and SSL certificates to DDoS protection and real-time threat monitoring, these tools safeguard your digital assets and ensure safe, uninterrupted access for your users. In this blog, we’ll explore the top web security that help protect your website, preserve user trust, and maintain your online integrity.
The Importance of a Secure Web Infrastructure
A strong web security solutions infrastructure forms the foundation of digital security. It includes secure hosting environments, updated server software, and properly configured networks. Without these basics, even the most advanced security tools can fall short. A secure infrastructure protects your website from vulnerabilities that hackers often exploit, such as outdated scripts or weak configurations. Regular updates, server patches, and backups ensure stability and reduce the risk of cyberattacks. Web security begins with building on a solid base one that supports all other layers of protection. By prioritizing infrastructure security, businesses can prevent breaches and safeguard their digital presence from the ground up.
SSL Certificates and HTTPS Encryption
Secure Sockets Layer (SSL) certificates are essential for encrypting data transmitted between a user’s browser and your website. By enabling HTTPS, SSL ensures that sensitive information like passwords, credit card numbers, and personal details remain private and secure. This encryption protects your users from man-in-the-middle attacks and builds trust by displaying the padlock icon in browsers. Moreover, search engines like Google favor HTTPS-enabled sites, giving you an SEO advantage. Installing an SSL certificate is one of the easiest and most effective ways to boost web security. It’s a critical first step in establishing credibility and protecting user data online.
Web Application Firewalls for Real-Time Protection
A Web Application Firewall acts as a shield between your website and incoming traffic, filtering out malicious requests before they reach your server. Detect and block threats like SQL injection, cross-site scripting, and file inclusion attacks in real time. They are especially valuable for businesses that handle sensitive customer data or rely on e-commerce platforms. Whether cloud-based or hardware-driven, WAFs can be customized to fit specific security needs, offering scalable protection. Implementing a WAF not only enhances website security but also ensures smoother performance and increased uptime making it a key component in a comprehensive web security strategy.
DDoS Protection to Maintain Website Availability
Distributed Denial of Service attacks aim to overwhelm your website with traffic, causing downtime and disrupting operations. These attacks can last for hours or even days, costing businesses significant revenue and damaging customer trust. protection services work by identifying and filtering malicious traffic while allowing legitimate users uninterrupted access. They use advanced algorithms, load balancing, and traffic scrubbing to neutralize the threat before it impacts your site. Implementing a reliable mitigation solution is essential for maintaining availability, especially for high-traffic websites. It ensures business continuity and resilience against one of the most common and disruptive cyber threats.
Malware Detection and Removal Tools
Malware can silently infiltrate your website, stealing data, redirecting traffic, or damaging your brand’s reputation. Regular malware scanning and automatic removal tools are crucial for identifying and eliminating harmful code. These solutions monitor files, plugins, and content management systemweb security solutionss for suspicious activity or unauthorized changes. Infected sites not only lose visitors but may also be blacklisted by search engines. By using trusted malware detection software, you can act swiftly to contain threats and restore your website’s integrity. Early detection prevents more serious breaches and gives your visitors confidence that your site is safe and secure to browse.
Secure Authentication and Access Controls
Unauthorized access is a major cybersecurity risk, especially for websites with multiple users or administrative roles. Implementing strong authentication methods like two-factor authentication, biometric logins, and role-based access controls helps prevent breaches caused by weak or stolen passwords. Limit access to sensitive areas of your site based on user roles and regularly review permissions to minimize vulnerabilities. Secure login protocols not only protect internal data but also reduce the risk of backdoor entry by cybercriminals. By tightening access controls and using advanced authentication, you can significantly enhance the security of your web environment and protect it from internal and external threats.
Regular Security Audits and Vulnerability Assessments
Security isn’t a one-time setup it’s an ongoing process. Regular audits and vulnerability assessments are essential to identify new risks and ensure all defenses are up to date. These evaluations involve checking for outdated plugins, scanning for open ports, testing input fields for injection flaws, and assessing access logs. Cybersecurity experts use both automated tools and manual penetration testing to uncover weaknesses before attackers do. Regular assessments help prioritize fixes, maintain compliance with regulations, and provide peace of mind. Staying proactive with security audits ensures that your website adapts to the ever-changing threat landscape and remains fortified against potential breaches.
Conclusion
In today’s ever-evolving digital landscape, protecting your website and data is more important than ever. Implementing robust web security solutions such as SSL encryption, firewalls, DDoS protection, malware detection, and secure authentication ensures your digital assets remain safe from cyber threats. Regular security audits and tailored protection strategies not only enhance user trust but also keep your business compliant and resilient. With the right tools and proactive measures, you can confidently fortify your online presence and prevent costly disruptions. In a world where online threats never rest, staying vigilant and secure is the key to long-term digital success and peace of mind.
0 notes