#remote developers for startups
Explore tagged Tumblr posts
Text
Top Cost-Saving Strategies for Startups Hiring Developers in 2025
Introduction

In 2025, startups are under more pressure than ever to innovate rapidly without burning through capital. The traditional model of building large, in-house development teams is increasingly being questioned as startups seek agility, specialized skills, and cost-efficiency.
Hiring developers was once a straightforward decision, but this is no longer the case. It is now a complex balancing act between costs, quality, and scalability leaving businesses asking the question how to hire developers for startup?
With inflationary pressures, rising salaries in tech hubs, and the global competition for skilled talent, founders are facing a new dilemma, hence asking the critical question: How do we build a strong dev team without going broke?
The answer lies in smart hiring—particularly outsourcing and staff augmentation. This article outlines cost-saving strategies for startups when hiring developers in 2025, supported by real-world case studies, statistics, and expert advice.
Early-Stage Startups Struggles

Early-stage startups, by their very nature, operate within tight financial constraints. They face an uphill battle when it comes to attracting and retaining top-tier developer talent with many wondering: How much does it cost to hire a developer?
Here is what their early struggle involves:
With limited budget and compensation constraints they cannot compete with packages offered by tech giants.
Lack the brand recognition that draws in passive candidates.
There is a lot at stake in every minor business decision with a single misstep significantly impacting project timelines.
Hiring in-house developers involves a multitude of hidden costs.
For startups, the most expensive line of code isn't the one written — it's the one paid for but never used. Every unused feature drains the budget without delivering value. This is very true for startups who tend to worry about how to build a tech team on a budget?
The Shifting Sands of Developer Hiring in 2025

The demand for specialized tech skills continues to outpace supply. This scarcity drives up salaries and benefits, making in-house hiring a significant financial burden for nascent companies.
There are several affordable ways to hire developers to ensure it does not burn a hole in your startup’s tight budget. Here are a few interesting statistics:
IT outsourcing revenue is expected to reach a staggering $591.24 billion USD in 2025.
The offshore software development market is expected to rise to $151.9 billion in 2025 and $389.7 billion by 2033.
92% of G2000 companies depend on IT outsourcing.
There are multiple models available to businesses for hiring remote developers for startups as mentioned below, besides which there is also the option to hire in-house developers:
Freelancer developers
Outsourcing
IT staff augmentation
Top Cost-Saving Strategies
Hiring remote developers over in-house ones is highly beneficial when it comes to cost-cutting.
Freelancers tend to be unreliable; however, startups have the option to either outsource or embrace staff augmentation.
Here are a few strategies for businesses wondering how to hire developers for startup
Hire Remote Developers from Cost-Effective Regions:
Hiring remote developers for startups isn’t just about flexibility—it’s about geography.
Hiring from regions like India and Philippines ensures more cost-effective software development.
Rates vary across the globe. Best countries to hire developers 2025:

Use Specialized Agencies Instead of Freelance Platforms:
Agencies that specialize in IT staff augmentation ensure pre-vetted developers, replacement guarantees, ongoing project management support and skillset alignment with your tech stack. This model ensures continuity and minimizes the risk of attrition during critical development phases.
Avoid Over-hiring:
Startup founders often make the mistake of hiring too many specialists too early.
Reduce your dependency on multiple hires and keep your team agile.
Hire a skilled set of developers and avoid over-hiring.
Scale Flexibly with Monthly Contracts, Not Full-Time Salaries:
Hiring full-time employees comes with long-term obligations.
Staff augmentation is more flexible - you can hire monthly, pause, or scale based on project load.
Invest in Code Reusability and DevOps Automation Early:
Save by hiring cheaper and writing smarter code.
Encourage your team to build reusable components, use Laravel packages efficiently, and implement CI/CD pipelines.
Automate testing and deployments.
Implementing these strategies helps reduce development time, minimize bugs, and accelerates your release cycles—saving both time and money.
Choose the Right Engagement Model for Your Project Lifecycle:
Not every startup needs the same engagement model.
Align your project needs with the right model to avoid scope creep and over commitment—common financial pitfalls for early-stage startups.
Start with a Pilot Before Committing Fully:
Whether you’re outsourcing for the first time or switching vendors, always begin with a pilot project.
Test communication workflows, validate code quality, and evaluate cultural and process fit.
Hiring remote developers that offer flexible onboarding and short-term trials without long lock-ins will pay off.
These cost saving strategies offer a vital insight into how to hire developers for startup. The article goes on to provide more details on the benefits of outsourcing and opting for staff augmentation.
The Power of Outsourcing Development Requirements

Outsourcing software development requirements is a smart business decision especially for startups. It is no longer viewed with skepticism, but has matured into a sophisticated and highly effective strategy for startups.
Top cost-saving strategy - Outsourcing
Here is how outsourcing is the most cost-effective solution:
Access to a Global Talent Pool: Outsourcing opens doors to highly skilled talent from all around the globe. It provides the startups access to highly quality solutions at significantly lower rates.
Reduced Overhead and Operational Costs: Outsourcing helps eliminate the overheads associated with recruiting top-notch developers. This includes the recruitment costs, benefits, office space, equipment, utilities, training, as well as administrative overhead.
Faster Time-to-Market and Scalability: When you outsource to a professional software development company there is no delay to start the development process. They implemented proven methods and have access to the latest technology to reduce time-to-market.
Focus on Core Competencies: The startups can focus on more pressing business matters by delegating development tasks to the professionals.
Outsourcing isn’t just a cost-cutting move it’s a strategic solution especially in 2025 when technology is making it easy for businesses to launch their products and services.
IT Staff Augmentation: A Hybrid Approach
When it comes to getting work done, staff augmentation is a pretty neat trick. Instead of just handing off a whole project to an outside company:
Filling in the Blanks: Ever been in a spot where you need a super specific skill for a short burst? Staff augmentation lets you bring in vetted experts without all the usual hiring headaches.
Flexibility is Key: You can scale your workforce up or down in a flash, depending on project demands, busy seasons, or if something unexpected pops up.
Budget-Friendly: While it might not always beat full project outsourcing on price, staff augmentation can still be incredibly cost-effective.
Strategic Implementation for Maximum Savings
Several key elements influence the total cost to hire remote developers. To genuinely reduce expenses while ensuring high-quality outcomes, startups should keep the following best practices in mind:
Define Clear Requirements:
Always define project scope, technical requirements, desired skills, and expected deliverables first. It is best to have a clear picture of the project's scope prior to engaging any external partner. Ambiguity leads to scope creep and increased costs.
Select the Right Engagement Model:
Decide whether a fully outsourced project or a staff augmentation approach fits better with your goals, budget, and how much control you want to retain. Each model has its advantages depending on your stage and needs.
Prioritize Thorough Evaluation:
Vet candidates or agencies rigorously and avoid making decisions exclusively based on the cost of development. Verify their technical expertise, communication skills, past project success, and cultural compatibility and ensure they have a proven track record.
Start Small:
Consider starting small with limited requirements like an MVP. This is a good opportunity to assess compatibility and performance before committing to larger engagements.
Leverage Project Management Tools:
Make the most of the advanced tools to streamline project management and communication. This is vital since it helps improve visibility, coordination and ensures everyone stays aligned on deadlines and responsibilities.
Conclusion
With stiffer competition as building top-notch solutions becomes simpler in 2025, businesses need a good strategy. Hence startups need to build and iterate quickly while maintaining financial prudence.
This article provides details on several startup developer hiring models. It explains how the traditional model of hiring a large, expensive in-house development team is often unsustainable.
Outsource development requirements and reap the benefits, it is the ideal cost-saving strategy.
FAQ
What’s the most cost-effective way for startups to hire developers in 2025?
Hiring remote developers or outsourcing to trusted development agencies often proves the most budget-friendly while maintaining quality.
Is outsourcing still viable for startups in 2025?
Yes. Strategic outsourcing helps reduce infrastructure and hiring costs while accessing global talent pools.
How can startups ensure quality while saving costs on development?
Prioritize MVP development, choose skilled yet affordable developers, and use hybrid hiring models combining in-house and outsourced talent.
What are some common hiring mistakes startups make in 2025?
Over hiring early, ignoring remote options, and choosing price over proven expertise are common mistakes.
Original Source: https://medium.com/@mukesh.ram/top-cost-saving-strategies-for-startups-hiring-developers-in-2025-1debaf532156
#Hire Remote Developers#Cost-effective software development#how to hire developers for startup#remote developers for startups#Hiring Cost
0 notes
Text

App Development for Startups: Build Better, Faster with Remote Tech Talent
At Overseas Career, we help companies accelerate app development by connecting them with top-tier remote tech talent. Whether you're creating an MVP or scaling your platform, our worldwide network of expert developers guarantees faster delivery, cheaper costs, and greater results—without sacrificing quality.
Visit Our Website: overseascareer.net
#custom mobile application development#zoho crm training and support#app development for startups#remote accounting services
0 notes
Text
Top Tech Job Boards for 2025: Where the Best Tech Talent Gets Hired
The tech job market in 2025 is as fast-paced as ever—but now, the best opportunities don’t always live on LinkedIn or Indeed. For software engineers, product managers, data scientists, and tech-savvy creatives, niche platforms and curated job boards have become the go-to channels for discovering high-quality, high-paying roles. Whether you’re looking for remote startups, big tech gigs, or…
#GitHub tech hiring#remote developer jobs#startup job boards 2025#top tech job boards 2025#where to find tech jobs
0 notes
Text
0 notes
Text
Unlock the Full Potential of Remote Developers with These 5 Proven Tactics! From Effective Communication Strategies to Streamlined Project Management, These Tips Will Help Startups Maximize Productivity and Collaboration. Leverage the Power of Remote Teams to Scale Your Business and Achieve Success. Discover the Secrets to Remote Developer Success Today!
1 note
·
View note
Text
Top 5 Trending Business Topics in 2023: AI, Big Data, Cybersecurity, Cloud Computing, and Remote Work

Top 5 Trending Business Topics in 2023
The business world is constantly evolving, and new trends are emerging all the time. To stay ahead of the curve, it's important to be aware of the latest trends and how they are impacting businesses of all sizes.
Here are five of the top trending business topics in 2023:
Artificial intelligence (AI)
AI is rapidly changing the business landscape, and it's only going to become more important in the coming years. Businesses are using AI to automate tasks, improve customer service, and develop new products and services.
For example, AI is being used to develop chatbots that can answer customer questions and provide support 24/7. AI is also being used to develop personalized product recommendations and marketing campaigns.
If you're not already using AI in your business, now is the time to start. AI can help you improve efficiency, productivity, and profits.
Big data
Big data is another important trend that is impacting businesses of all sizes. Big data is the collection and analysis of large amounts of data. Businesses are using big data to gain insights into their customers, improve their products and services, and make better business decisions.
For example, businesses are using big data to identify customer trends and preferences. They are also using big data to develop targeted marketing campaigns and improve their pricing strategies.
If you're not already using big data in your business, you're missing out on a valuable opportunity. Big data can help you make better business decisions and improve your bottom line.
Cybersecurity
Cybersecurity is a top concern for businesses of all sizes. As cyber threats become more sophisticated, it's important for businesses to take steps to protect themselves.
Businesses are investing in cybersecurity solutions such as firewalls, intrusion detection systems, and encryption. They are also training their employees on cybersecurity best practices.
If you're not already investing in cybersecurity, you're putting your business at risk. Cybersecurity is essential for protecting your data and your bottom line.
Cloud computing
Cloud computing is another important trend that is impacting businesses of all sizes. Cloud computing is the delivery of computing services over the internet. Businesses are using cloud computing to store data, run applications, and develop new products and services.
For example, businesses are using cloud computing to store customer data and financial records. They are also using cloud computing to run applications such as CRM and ERP systems.
If you're not already using cloud computing in your business, you're missing out on a valuable opportunity. Cloud computing can help you reduce costs, improve efficiency, and scale your business more easily.
Remote work
Remote work is a growing trend that is being accelerated by the COVID-19 pandemic. More and more businesses are allowing their employees to work remotely, either full-time or part-time.
Remote work offers a number of benefits for both businesses and employees. Businesses can save money on office space and expenses, and employees can enjoy greater flexibility and work-life balance.
If you're not already offering remote work options to your employees, you should consider doing so. Remote work can help you attract and retain top talent, and it can also boost employee productivity and satisfaction.
How to Prepare for the Future of Business
The business world is constantly changing, and it's important to be prepared for the future. Here are a few tips:
Stay up-to-date on the latest trends. Read industry publications, attend conferences, and network with other business professionals to stay informed about the latest trends and how they are impacting your industry.
Invest in new technologies. New technologies can help you improve efficiency, productivity, and profitability. Consider investing in AI, big data, cloud computing, and other new technologies that are relevant to your industry.
Upskill and reskill your workforce. As the economy changes, so too do the skills that are needed for success. Make sure your employees have the skills they need to succeed in the future by offering them training and development opportunities.
Be agile and adaptable. The business world is constantly changing, so it's important to be agile and adaptable. Be prepared to change your business strategy and operations as needed in response to new trends and challenges.
By following these tips, you can prepare your business for the future and ensure that it remains successful.
#Trending business topics#Business trends for 2023#Top business trends#Business trends to watch#Future of business trends#Artificial intelligence (AI) in business#Big data in business#Cybersecurity in business#Cloud computing in business#Remote work trends#AI for customer service#AI for product development#Big data for marketing#Big data for pricing#Cybersecurity for small businesses#Cybersecurity for remote workers#Cloud computing for startups#Cloud computing for enterprise#Remote work benefits#Remote work challenges#Remote work trends for 2023
0 notes
Text
What kind of bubble is AI?
My latest column for Locus Magazine is "What Kind of Bubble is AI?" All economic bubbles are hugely destructive, but some of them leave behind wreckage that can be salvaged for useful purposes, while others leave nothing behind but ashes:
https://locusmag.com/2023/12/commentary-cory-doctorow-what-kind-of-bubble-is-ai/
Think about some 21st century bubbles. The dotcom bubble was a terrible tragedy, one that drained the coffers of pension funds and other institutional investors and wiped out retail investors who were gulled by Superbowl Ads. But there was a lot left behind after the dotcoms were wiped out: cheap servers, office furniture and space, but far more importantly, a generation of young people who'd been trained as web makers, leaving nontechnical degree programs to learn HTML, perl and python. This created a whole cohort of technologists from non-technical backgrounds, a first in technological history. Many of these people became the vanguard of a more inclusive and humane tech development movement, and they were able to make interesting and useful services and products in an environment where raw materials – compute, bandwidth, space and talent – were available at firesale prices.
Contrast this with the crypto bubble. It, too, destroyed the fortunes of institutional and individual investors through fraud and Superbowl Ads. It, too, lured in nontechnical people to learn esoteric disciplines at investor expense. But apart from a smattering of Rust programmers, the main residue of crypto is bad digital art and worse Austrian economics.
Or think of Worldcom vs Enron. Both bubbles were built on pure fraud, but Enron's fraud left nothing behind but a string of suspicious deaths. By contrast, Worldcom's fraud was a Big Store con that required laying a ton of fiber that is still in the ground to this day, and is being bought and used at pennies on the dollar.
AI is definitely a bubble. As I write in the column, if you fly into SFO and rent a car and drive north to San Francisco or south to Silicon Valley, every single billboard is advertising an "AI" startup, many of which are not even using anything that can be remotely characterized as AI. That's amazing, considering what a meaningless buzzword AI already is.
So which kind of bubble is AI? When it pops, will something useful be left behind, or will it go away altogether? To be sure, there's a legion of technologists who are learning Tensorflow and Pytorch. These nominally open source tools are bound, respectively, to Google and Facebook's AI environments:
https://pluralistic.net/2023/08/18/openwashing/#you-keep-using-that-word-i-do-not-think-it-means-what-you-think-it-means
But if those environments go away, those programming skills become a lot less useful. Live, large-scale Big Tech AI projects are shockingly expensive to run. Some of their costs are fixed – collecting, labeling and processing training data – but the running costs for each query are prodigious. There's a massive primary energy bill for the servers, a nearly as large energy bill for the chillers, and a titanic wage bill for the specialized technical staff involved.
Once investor subsidies dry up, will the real-world, non-hyperbolic applications for AI be enough to cover these running costs? AI applications can be plotted on a 2X2 grid whose axes are "value" (how much customers will pay for them) and "risk tolerance" (how perfect the product needs to be).
Charging teenaged D&D players $10 month for an image generator that creates epic illustrations of their characters fighting monsters is low value and very risk tolerant (teenagers aren't overly worried about six-fingered swordspeople with three pupils in each eye). Charging scammy spamfarms $500/month for a text generator that spits out dull, search-algorithm-pleasing narratives to appear over recipes is likewise low-value and highly risk tolerant (your customer doesn't care if the text is nonsense). Charging visually impaired people $100 month for an app that plays a text-to-speech description of anything they point their cameras at is low-value and moderately risk tolerant ("that's your blue shirt" when it's green is not a big deal, while "the street is safe to cross" when it's not is a much bigger one).
Morganstanley doesn't talk about the trillions the AI industry will be worth some day because of these applications. These are just spinoffs from the main event, a collection of extremely high-value applications. Think of self-driving cars or radiology bots that analyze chest x-rays and characterize masses as cancerous or noncancerous.
These are high value – but only if they are also risk-tolerant. The pitch for self-driving cars is "fire most drivers and replace them with 'humans in the loop' who intervene at critical junctures." That's the risk-tolerant version of self-driving cars, and it's a failure. More than $100b has been incinerated chasing self-driving cars, and cars are nowhere near driving themselves:
https://pluralistic.net/2022/10/09/herbies-revenge/#100-billion-here-100-billion-there-pretty-soon-youre-talking-real-money
Quite the reverse, in fact. Cruise was just forced to quit the field after one of their cars maimed a woman – a pedestrian who had not opted into being part of a high-risk AI experiment – and dragged her body 20 feet through the streets of San Francisco. Afterwards, it emerged that Cruise had replaced the single low-waged driver who would normally be paid to operate a taxi with 1.5 high-waged skilled technicians who remotely oversaw each of its vehicles:
https://www.nytimes.com/2023/11/03/technology/cruise-general-motors-self-driving-cars.html
The self-driving pitch isn't that your car will correct your own human errors (like an alarm that sounds when you activate your turn signal while someone is in your blind-spot). Self-driving isn't about using automation to augment human skill – it's about replacing humans. There's no business case for spending hundreds of billions on better safety systems for cars (there's a human case for it, though!). The only way the price-tag justifies itself is if paid drivers can be fired and replaced with software that costs less than their wages.
What about radiologists? Radiologists certainly make mistakes from time to time, and if there's a computer vision system that makes different mistakes than the sort that humans make, they could be a cheap way of generating second opinions that trigger re-examination by a human radiologist. But no AI investor thinks their return will come from selling hospitals that reduce the number of X-rays each radiologist processes every day, as a second-opinion-generating system would. Rather, the value of AI radiologists comes from firing most of your human radiologists and replacing them with software whose judgments are cursorily double-checked by a human whose "automation blindness" will turn them into an OK-button-mashing automaton:
https://pluralistic.net/2023/08/23/automation-blindness/#humans-in-the-loop
The profit-generating pitch for high-value AI applications lies in creating "reverse centaurs": humans who serve as appendages for automation that operates at a speed and scale that is unrelated to the capacity or needs of the worker:
https://pluralistic.net/2022/04/17/revenge-of-the-chickenized-reverse-centaurs/
But unless these high-value applications are intrinsically risk-tolerant, they are poor candidates for automation. Cruise was able to nonconsensually enlist the population of San Francisco in an experimental murderbot development program thanks to the vast sums of money sloshing around the industry. Some of this money funds the inevitabilist narrative that self-driving cars are coming, it's only a matter of when, not if, and so SF had better get in the autonomous vehicle or get run over by the forces of history.
Once the bubble pops (all bubbles pop), AI applications will have to rise or fall on their actual merits, not their promise. The odds are stacked against the long-term survival of high-value, risk-intolerant AI applications.
The problem for AI is that while there are a lot of risk-tolerant applications, they're almost all low-value; while nearly all the high-value applications are risk-intolerant. Once AI has to be profitable – once investors withdraw their subsidies from money-losing ventures – the risk-tolerant applications need to be sufficient to run those tremendously expensive servers in those brutally expensive data-centers tended by exceptionally expensive technical workers.
If they aren't, then the business case for running those servers goes away, and so do the servers – and so do all those risk-tolerant, low-value applications. It doesn't matter if helping blind people make sense of their surroundings is socially beneficial. It doesn't matter if teenaged gamers love their epic character art. It doesn't even matter how horny scammers are for generating AI nonsense SEO websites:
https://twitter.com/jakezward/status/1728032634037567509
These applications are all riding on the coattails of the big AI models that are being built and operated at a loss in order to be profitable. If they remain unprofitable long enough, the private sector will no longer pay to operate them.
Now, there are smaller models, models that stand alone and run on commodity hardware. These would persist even after the AI bubble bursts, because most of their costs are setup costs that have already been borne by the well-funded companies who created them. These models are limited, of course, though the communities that have formed around them have pushed those limits in surprising ways, far beyond their original manufacturers' beliefs about their capacity. These communities will continue to push those limits for as long as they find the models useful.
These standalone, "toy" models are derived from the big models, though. When the AI bubble bursts and the private sector no longer subsidizes mass-scale model creation, it will cease to spin out more sophisticated models that run on commodity hardware (it's possible that Federated learning and other techniques for spreading out the work of making large-scale models will fill the gap).
So what kind of bubble is the AI bubble? What will we salvage from its wreckage? Perhaps the communities who've invested in becoming experts in Pytorch and Tensorflow will wrestle them away from their corporate masters and make them generally useful. Certainly, a lot of people will have gained skills in applying statistical techniques.
But there will also be a lot of unsalvageable wreckage. As big AI models get integrated into the processes of the productive economy, AI becomes a source of systemic risk. The only thing worse than having an automated process that is rendered dangerous or erratic based on AI integration is to have that process fail entirely because the AI suddenly disappeared, a collapse that is too precipitous for former AI customers to engineer a soft landing for their systems.
This is a blind spot in our policymakers debates about AI. The smart policymakers are asking questions about fairness, algorithmic bias, and fraud. The foolish policymakers are ensnared in fantasies about "AI safety," AKA "Will the chatbot become a superintelligence that turns the whole human race into paperclips?"
https://pluralistic.net/2023/11/27/10-types-of-people/#taking-up-a-lot-of-space
But no one is asking, "What will we do if" – when – "the AI bubble pops and most of this stuff disappears overnight?"

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/12/19/bubblenomics/#pop

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
--
tom_bullock (modified) https://www.flickr.com/photos/tombullock/25173469495/
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/
4K notes
·
View notes
Text
That Time When I Tried To Bring A Foot Long Knife In My Cabin Bag On An International Flight
You know flights. For at least a few generations already we have had a privilege of travelling through air, which is statistically one of the safest means of transportation, but when shit goes wrong, it goes wrong in a particularly spectacular manner and being the dumb fucks we humans are, spectacular failures (such as acts of terror) register as more plausible ones in our stupid monkey brains. This is a digression, but, as the title of the post suggests, not an untangential one.
In any case, there used to be a time in my life when international flying was just a regular thing for me, getting on a plane and immediatelly getting some monday-morning shut-eye even before the take-off to teleport a few thousand kilometers away was just a fact of life. Two of my russian-speaking (but also fluent in my mother tongue) team mates doing some contract backend web development for a foreign fintech startup with me as a "team lead" (in quotes, because we have always been egalitarian) were as accustomed to flying as I was. Security checkpoint, it seemed at that time, was something we knew intimately, not necessarily to the point when we referred to the agents by their first names, but rather we knew which shoes are going to have to come off and the exact amount of change to trigger the metal detector. It was, as we all understood it, a dog-and-pony show in a post 9/11 security theater where water in your belly was qualitatively different from the water in an unopened bottle, which is technically true, but it never even made anyone feel safer as a passenger or less safe as a potential criminal (like my white ass getting "randomly checked" five times in a row for "traces of explosives"); it usually went as a well-choreographed routine of retrieving a laptop from an easily-accessible part of your backpack, unbuckling your belt, taking off your coat, putting clothes, backpack and electronics into separate trays and proceeding to waltz through the SCARY GATE in a steady pace all the while smiling in a friendly manner to the agents, maintaining Just Enough eye contact to establish connection but not come off as challenging and refraining yourself from making any meta commentary throughout the whole ordeal.
Easy.
Imagine yourself in my shoes when my backpack comes out of the x-ray about 1.25 seconds later than usual. There's a warning light going off silently at the back of my head as I wait for my belt to come back to me so my pant's don't slip off my fat white ass as much, getting brigher and turning into a bangbang double exclamation mark emoji and starting to emit avionic warning sound as the security agent pulls the tray with my backpack aside.
"Sir is this your bag?"
"Yes, it is"
"It seems you have a knife in there"
At this point I am more amused than perplexed.
"Yes, that is true," - I say smiling incredulously - "but it never caused any trouble anywhere."
I'm thinking about my trusty pocket victorinox (with scissors that are incredibly good for trimming my nails on the go) attached to my RSA OTP generator.
"Oh." - the female agent replies dryly, putting the vynil gloves on - "may I please open your bag, sir?"
"Sure!" - "May I retrieve The Object, sir?" - "Please go ahead".
And I watch, with increasing horror, my eyes widening, as I see the very remotely familiar handle that stirs something in the depths of my memory, the blade emerging in slow motion and going oh-so-slowly to what seems like forever until the whole footlong thing is out, pinched between two fingers of the agent who looks at me as memories of a town several hundred kilometers away rush back to me: the hunger, the yearning, the NEED for a simple kielbasa-and-bun sandwitch, both kielbasa and a freshly baked bun in my hands in a middle of a shop with no way to cut neither kielbasa nor the bun and the footlong steel monstrocity being the only possible option of instruments capable of cutting. Did I unpack my bag or I simply throw it aside when I got home is a question with an answer so obvious it immediately unasks itself.
"Sir?" - a female voice brings me back to here-now. - "I said, shall I discard of it, sir?"
I struggle for a moment to regain control of my motor function and nod. I think my mouth is slightly agape and I have no control of my vocal cords. A single elongated vowel escapes my throat.
"Thank you" - she says, handing my backpack over to me. My colleagues also stand frozen, their eyes wide in disbelief. - "You may proceed, sir"
"T-thank you" - I stutter as I shuffle away with my backpack in one hand and my belt which I retrieved just prior to the whole incident in another, pretty sure I've gotten damn lucky once again.
I never bought another trio of bun, kielbasa and a big fuckoff knife abroad again.
34 notes
·
View notes
Text
Early Hiring Failure and How Staff Augmentation for Startups Saves?
Introduction
Startups collapse not just because of weak ideas but often due to hiring the wrong people at the wrong time. Poor hiring choices in the early stages burn through budgets, delay product timelines, and stall momentum when speed matters most. The biggest startup hiring mistakes come from rushing to fill roles without a clear product-market fit or engineering clarity!
Founders often overhire or hire too soon, investing in full-time staff before validating their business model. This leads to bloated payrolls, mismatched skills, and decision bottlenecks. Instead of agility, the startup becomes locked into rigid headcounts and underperforming teams. This is where staff augmentation for startups changes the game.
Top Reasons Why Startups Fail at Hiring Early

Inside story: These startup hiring mistakes happen because early-stage founders lack time, resources, or the network to build the right team quickly. That’s why they need faster and more flexible ways to access top talent!
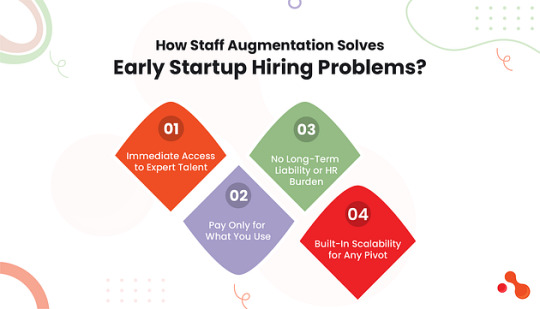
How Staff Augmentation Solves Early Startup Hiring Problems?
When traditional hiring slows you down or drains your runway, staff augmentation for startups offers a smarter alternative. It fixes early hiring failures by offering speed, control, and flexibility, without the overhead of building an in-house team.
Immediate Access to Expert Talent
With staff augmentation, startups can instantly onboard skilled professionals who already know how to build and ship. Whether you need remote MVP developers for hire or a Laravel specialist for a backend module, you get results without going through months of interviews.
Pay Only for What You Use
You can hire on an hourly or monthly basis. There’s no wasted spend on idle capacity or bloated salaries. This model ensures cost efficiency at every stage of product development.
No Long-Term Liability or HR Burden
Forget about contracts, employee benefits, taxes, or compliance issues. Augmented staff work under flexible agreements, and you’re free to scale down with no HR bottlenecks.
Built-In Scalability for Any Pivot
Your startup may pivot, scale up suddenly, or face funding delays. Staff augmentation lets you adjust resources instantly. You can add more developers or reduce bandwidth as priorities change, without harming velocity or morale. The benefits of staff augmentation are clear: it lets you move fast, stay lean, and build smarter from day one.
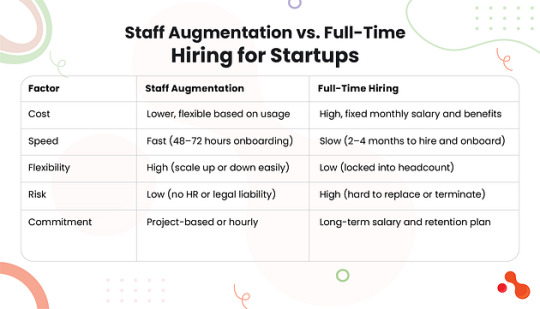
Staff Augmentation vs. Full-Time Hiring for Startups
Common Startup Scenarios Where Augmentation Is Better

Here are real-world situations where augmentation makes more sense:
MVP Launch Under Tight Deadline
Launching an MVP often comes with fixed investor expectations and a short runway. Augmentation allows you to hire remote Laravel developers for startup projects within days, not months. This speeds up delivery without sacrificing code quality or team control.
Post-Funding Scaling (Seed or Series A)
Once funding arrives, startups need to scale fast. Instead of spending three months hiring, founders can bring in multiple developers on contract to accelerate product updates, feature rollouts, and architecture redesigns.
SaaS Development With Rapid Iteration Needs
SaaS startups must release updates regularly based on user feedback. Staff augmentation gives access to skilled developers who can build, test, and deploy in short sprints. You can avoid bottlenecks without inflating payroll!
Tech Pivot Requiring New Skills
When your product shifts from Web2 to Web3, or from monolith to microservices, your old team may not have the required skill set. Augment your core with specialists who bring that exact expertise without hiring full-time.
In all these cases, startups save time, money, and bandwidth by partnering with the best staff augmentation company for startups, one that understands early-stage urgency and tech specificity.
Real Startup Examples: Failing Fast vs. Scaling Smart
The following examples show how two early-stage startups took different paths, with drastically different outcomes.
❌ Startup A: Hired Fast, Burned Out Faster
Startup A raised a small seed round and rushed to build its MVP. The founder, with no technical background, hired a full-time in-house team of five developers in just four weeks. Without proper vetting or role clarity, they overbuilt features, missed critical deadlines, and created tech debt that slowed progress.
In six months, the startup burned over $300,000 in salaries, tools, and office space. No product shipped. Investors lost confidence. The company shut down before reaching the market.
✅ Startup B: Augmented Right, Launched on Time
Startup B, working with a similar budget, chose staff augmentation for startups. They brought in remote MVP developers for hire from a trusted agency. Instead of hiring full-time, they paid hourly for a project-based team via flexible model options.
Within five months, they launched a clean, functioning MVP. Their burn rate stayed low. They saved over 50% in upfront costs and secured follow-on funding after the product gained traction. These outcomes show the power of choosing the right hiring model.
How to Implement Staff Augmentation Strategically?
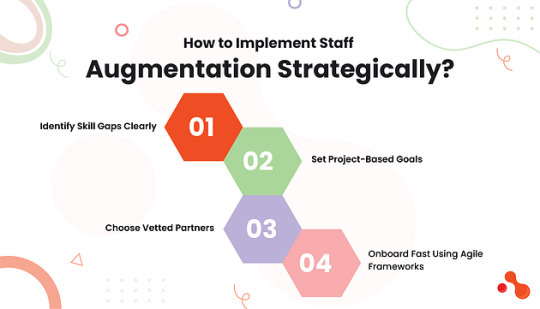
Choosing staff augmentation for startups works only when done with clarity and intent. You need to know what to build, who to bring in, and how to manage their output. Follow this strategic approach to make augmentation effective from day one!
Identify Skill Gaps Clearly
Start by auditing your current team.
Do you lack frontend capacity?
Need backend specialists like Laravel developers?
Or product designers for an MVP sprint?
Define exact roles and skills before reaching out for external help!
Set Project-Based Goals
Augmented developers perform best when assigned to specific outcomes. Don’t onboard them to “help the team.” Instead, tie each resource to milestones like a working prototype, API integration, or testing phase.
Choose Vetted Partners
Work with the best staff augmentation company for startups, one that understands tech stacks, agility, and startup pace. Agencies like Acquaint Softtech provide proven developers who can plug in fast, adapt to your tools, and build real products.
Onboard Fast Using Agile Frameworks
Use agile tools like Jira, Trello, or Asana for sprint planning. Assign Git access, set up Slack channels, and define standup routines. When you onboard right, remote engineers feel like part of the core team from day one.
Also read: Top ways IT staff augmentation empowers tech startups!
Bottomline
In the early stages of a startup, hiring decisions determine product velocity, cost efficiency, and long-term sustainability. Moving quickly is important, but making the right hiring developer choice is essential for survival. Full-time hiring at the wrong stage can lead to wasted capital, missed deadlines, and irreversible damage to growth momentum.
Staff augmentation for startups offers a strategic alternative. It allows founders to access specialized talent, reduce overhead, and scale operations based on real-time business needs. Instead of locking into fixed salaries, you gain the ability to allocate resources where they deliver the most value.
The most successful startups today prioritize flexibility, skill alignment, and speed. Staff augmentation supports all three, giving your venture the foundation to build fast, scale smart, and respond to change effectively.
#startup hiring mistakes#early hiring problems in startups#benefits of staff augmentation#remote MVP developers for hire
0 notes
Text
App Development for Startups Build Better Faster with Remote Tech Talent

Starting a new business in today's fast-paced digital environment necessitates savvy techniques, particularly when it comes to app development for startups. For entrepreneurs, developing an efficient, high-quality app can be critical to success. But how do you create better and faster while staying inside your budget? The solution rests in utilizing remote technical talent.
In this article, we'll look at why companies should consider remote engineers, how it can speed up app development, and practical recommendations for getting the most out of your remote team. Plus, if you want to pursue a career or expand your firm overseas, keep reading - we'll show you how app development complements an Overseas Career approach.
Why App Development is Crucial for Startups
Best App development for startups has become indispensable in the United States and elsewhere for reaching out to customers, increasing user engagement, and generating revenue. Whether you're developing a marketplace, a health app, or a finance solution, your startup's app is frequently the first impression users have of your company.
However, startups face unique challenges:
Limited budgets
Tight deadlines
Need for innovation
Lack of in-house tech expertise
This makes it critical to discover smart, cost-effective, and adaptable solutions for your app development requirements.
Remote Tech Talent: The Game Changer for Startups
Hiring skilled engineers, designers, and testers who can work from anywhere, frequently outside of your city or nation, is referred to as remote technical talent. This technique has grown in popularity among startups, particularly app development for startups in the United States, due to the numerous benefits it provides.
Benefits of Hiring Remote Tech Talent for Your Startup
Cost EfficiencyHiring developers remotely can significantly reduce costs. You may tap into talent pools where the cost of living is lower, resulting in quality work for a fraction of the regular price.
Access to Global ExpertiseRemote hiring provides access to the best developers worldwide. You are not restricted to local talent, which may be rare or pricey.
Faster Development CyclesYour project can be worked on around the clock with remote collaborators from various time zones. While your local team relaxes, distant devs can continue coding, accelerating delivery.
Flexibility and ScalabilityStartups may grow their teams up or down according to project requirements without making long-term commitments, which is ideal for the fast-changing startup environment.
Focus on Core BusinessStartup founders who outsource app development chores can focus on business growth, marketing, and funding rather than micromanaging IT teams.
How to Build Better and Faster with Remote Tech Talent
Simply hiring remote developers is insufficient; excellent management is required to achieve the best results. Here are some proven tips:
1. Define Clear Project Goals and Requirements
Create a clear project plan before getting started. Define the app's features, user experience goals, and technological specifications. This clarity enables app development for startup teams to work freely and minimizes misunderstandings.
2. Use Agile Development Practices
Use agile approaches such as Scrum or Kanban to handle activities in short cycles (sprints). This keeps the workforce agile, responsive, allowing for rapid feedback, which is critical for businesses that need to adjust to market changes.
3. Communicate Regularly and Transparently
Communication is essential for distant teams. Use Slack, Zoom, or Microsoft Teams to schedule daily or weekly check-ins. Maintain consensus and promptly address barriers.
4. Leverage Collaboration Tools
Platforms such as Jira, Trello, and Asana make it easier to track progress, assign tasks, and meet deadlines. Cloud-based tools ensure that your distant engineers and local teams collaborate effortlessly.
5. Hire the Right Talent for Your Startup
Look beyond resumes. Check portfolios, provide technical assessments, and record video interviews. Hiring engineers who understand startup culture and fast-paced workplaces ensures greater results.
6. Build a Strong Company Culture Remotely
Even when working remotely, cultivating a sense of belonging and motivation increases productivity. Celebrate accomplishments, encourage informal conversations, and ensure that remote developers feel a part of your startup's development.
Why Remote App Development Fits into Your Overseas Career Goals
If you’re considering expanding your startup overseas or are an aspiring tech professional eyeing international career opportunities, mastering remote app development is essential. Here’s why:
Work from Anywhere: Remote development transcends geographical barriers, allowing you to build or collaborate with companies from the comfort of your own home.
High Demand in the USA Market: Many American businesses choose remote development, resulting in numerous work opportunities for foreign talent.
Gain Cross-Cultural Experience: Working remotely with varied teams allows you to improve your communication skills and cultural awareness, all of which are significant benefits in your career abroad.
Build a Global Portfolio: Successful remote projects strengthen your resume or portfolio, making you appealing to foreign companies and clients.
Final Thoughts
App development is an important step in the success of companies in the United States and around the world. Embracing remote IT talent not only saves money but also accelerates development cycles and provides access to global experience.
Remember that the key to success is not simply employing remote developers, but also effectively managing them through clear communication, appropriate tools, and agile processes.
Whether you're a company founder or a tech professional looking for an international career, understanding app development for startups opens the door to exciting growth and prospects.
#affordable app development services#app development for startups#remote accounting services#zoho crm training and support
0 notes
Text
Your next developer might write excellent code and still not be who they claim to be. Remote hiring scams are sophisticated now. Think deepfakes, identity theft, and location masking. This is a threat, not a theory.
#AshkanRajaee#StartupSecurity#RemoteHiring#DigitalTrust#FakeEmployees#HiringRisk#ModernScams#GlobalTech
8 notes
·
View notes
Text
ah fuck my tv is on the fritz again and the trick that helped last time isn't working. however. new development in completely baffling and inscrutable electronic behavior: the only thing that seems to fix it this time around is when I connect my playstation remotely to play on my laptop screen instead. almost without fail the tv will, after a few minutes of me playing like that, suddenly come back to life and without any of the fucked up glitches it has otherwise and I can just use that for the rest of the play session without incident. but I HAVE to activate remote play first, or the tv screen is just solid black with maybe some green streaks or it starts doing shit in slow motion with afterimagese and look like a bad rave between going dark, and no amount of waiting or futzing around with the settings fixes it. I. I have no explanations for this. it works perfectly for hours and hours once it's actually coaxed back to life in this manner, so like. it does not seem to be a problem with the hardware, there's something in the software that keeps getting fucked at the startup??? what has your science wrought, children of men. a tv that can think itself to dysfunction. we have gone too far in our endless hubris and now we are paying the price
I feel more and more that I understand exactly the mechanisms of human psychology that had us try any fucking thing we could think of to placate gods of weather and volcano. I'm engaging in ritual behaviour so strange and illogical here because something about it sure seems to be doing something to better my standing with an implacable and unknowable force (this fucking screen with delusions of grandeur)
#deathloop is so beautiful that it's kind of worth it to get to see it on The Big Screen but this is undeniably a bit of a nightmare lol#I realllllly don't want to buy a new one tho that's a lot of stress and money. when it works it's great!#when.
6 notes
·
View notes
Text
applying for software developer jobs is so hellish because all the listings online are either defense contractors who offer high salaries with lots of benefits, on the job training, and flexible hours with remote work opportunities or some startup that pays way under market rate and demands you commute for an hour to their shitty office 5 days a week at 8 am sharp. and then every job that actually sounds tolerable wants you to have 5+ years experience in some technology you've never heard of. truly the stuff of nightmares
#I'm so sick of seeing job listings for northrop grumman 😭#I will not fucking compromise my morals for a paycheck I would rather be homeless#sigh....... my dreams of being a game dev seem further and further away every year#kvetching
89 notes
·
View notes
Text
On paper, the first candidate looked perfect. Thomas was from rural Tennessee and had studied computer science at the University of Missouri. His résumé said he’d been a professional programmer for eight years, and he’d breezed through a preliminary coding test. All of this was excellent news for Thomas’ prospective boss, Simon Wijckmans, founder of the web security startup C.Side. The 27-year-old Belgian was based in London but was looking for ambitious, fully remote coders.
Thomas had an Anglo-Saxon surname, so Wijckmans was surprised when he clicked into his Google Meet and found himself speaking with a heavily accented young man of Asian origin. Thomas had set a generic image of an office as his background. His internet connection was laggy—odd for a professional coder—and his end of the call was noisy. To Wijckmans, Thomas sounded like he was sitting in a large, crowded space, maybe a dorm or a call center.
Wijckmans fired off his interview questions, and Thomas’ responses were solid enough. But Wijckmans noticed that Thomas seemed most interested in asking about his salary. He didn’t come across as curious about the actual work or about how the company operated or even about benefits like startup stock or health coverage. Odd, thought Wijckmans. The conversation came to a close, and he got ready for the next interview in his queue.
Once again, the applicant said they were based in the US, had an Anglo name, and appeared to be a young Asian man with a thick, non-American accent. He used a basic virtual background, was on a terrible internet connection, and had a single-minded focus on salary. This candidate, though, was wearing glasses. In the lenses, Wijckmans spotted the reflection of multiple screens, and he could make out a white chatbox with messages scrolling by. “He was clearly either chatting with somebody or on some AI tool,” Wijckmans remembers.
On high alert, Wijckmans grabbed screenshots and took notes. After the call ended, he went back over the job applications. He found that his company’s listings were being flooded with applicants just like these: an opening for a full-stack developer got more than 500 applications in a day, far more than usual. And when he looked more deeply into the applicants’ coding tests, he saw that many candidates appeared to have used a virtual private network, or VPN, which allows you to mask your computer’s true location.
Wijckmans didn’t know it yet, but he’d stumbled onto the edges of an audacious, global cybercrime operation. He’d unwittingly made contact with an army of seemingly unassuming IT workers, deployed to work remotely for American and European companies under false identities, all to bankroll the government of North Korea.
With a little help from some friends on the ground, of course.
christina chapman was living in a trailer in Brook Park, Minnesota, a hamlet north of Minneapolis, when she got a note from a recruiter that changed her life. A bubbly 44-year-old with curly red hair and glasses, she loved her dogs and her mom and posting social justice content on TikTok. In her spare time she listened to K-pop, enjoyed Renaissance fairs, and got into cosplay. Chapman was also, according to her sparse online résumé, learning to code online.
It was March 2020 when she clicked on the message in her LinkedIn account. A foreign company was looking for somebody to “be the US face” of the business. The company needed help finding remote employment for overseas workers. Chapman signed on. It’s unclear how fast her workload grew, but by October 2022 she could afford a move from chilly Minnesota to a low-slung, four-bedroom house in Litchfield Park, Arizona. It wasn’t fancy—a suburban corner lot with a few thin trees—but it was a big upgrade over the trailer.
Chapman then started documenting more of her life on TikTok and YouTube, mostly talking about her diet, fitness, or mental health. In one chatty video, shared in June 2023, she described grabbing breakfast on the go—an açaí bowl and a smoothie— because work was so busy. “My clients are going crazy!” she complained. In the background, the camera caught a glimpse of metal racks holding at least a dozen open laptops covered in sticky notes. A few months later, federal investigators raided Chapman’s home, seized the laptops, and eventually filed charges alleging that she had spent three years aiding the “illicit revenue generation efforts” of the government of North Korea.
For maybe a decade, North Korean intelligence services have been training young IT workers and sending them abroad in teams, often to China or Russia. From these bases, they scour the web for job listings all over, usually in software engineering, and usually with Western companies. They favor roles that are fully remote, with solid wages, good access to data and systems, and few responsibilities. Over time they began applying for these jobs using stolen or fake identities and relying on members of their criminal teams to provide fictional references; some have even started using AI to pass coding tests, video interviews, and background checks.
But if an applicant lands a job offer, the syndicate needs somebody on the ground in the country the applicant claims to live in. A fake employee, after all, can’t use the addresses or bank accounts linked to their stolen IDs, and they can’t dial in to a company’s networks from overseas without instantly triggering suspicion. That’s where someone like Christina Chapman comes in.
As the “facilitator” for hundreds of North Korea–linked jobs, Chapman signed fraudulent documents and handled some of the fake workers’ salaries. She would often receive their paychecks in one of her bank accounts, take a cut, and wire the rest overseas: Federal prosecutors say Chapman was promised as much as 30 percent of the money that passed through her hands.
Her most important job, though, was tending the “laptop farm.” After being hired, a fake worker will typically ask for their company computer to be sent to a different address than the one on record—usually with some tale about a last-minute move or needing to stay with a sick relative. The new address, of course, belongs to the facilitator, in this case Chapman. Sometimes the facilitator forwards the laptop to an address overseas, but more commonly that person holds onto it and installs software that allows it to be controlled remotely. Then the fake employee can connect to their machine from anywhere in the world while appearing to be in the US. (“You know how to install Anydesk?” one North Korean operative asked Chapman in 2022. “I do it practically EVERYDAY!” she replied.)
In messages with her handlers, Chapman discussed sending government forms like the I-9, which attests that a person is legally able to work in the US. (“I did my best to copy your signature,” she wrote. “Haha. Thank you,” came the response.) She also did basic tech troubleshooting and dialed into meetings on a worker’s behalf, sometimes on short notice, as in this conversation from November 2023:
Worker: We are going to have laptop setup meeting in 20 mins. Can you join Teams meeting and follow what IT guy say? Because it will require to restart laptop multiple times and I can not handle that. You can mute and just follow what they say ...
Chapman: Who do I say I am?
Worker: You don’t have to say, I will be joining there too.
Chapman: I just typed in the name Daniel. If they ask WHY you are using two devices, just say the microphone on your laptop doesn’t work right ... Most IT people are fine with that explanation.
Sometimes, she got jumpy. “I hope you guys can find other people to do your physical I9s,” she wrote to her bosses in 2023, according to court documents. “I will SEND them for you, but have someone else do the paperwork. I can go to FEDERAL PRISON for falsifying federal documents.” Michael Barnhart, an investigator at cybersecurity company DTEX and a leading expert on the North Korean IT worker threat, says Chapman’s involvement followed a standard pattern—from an innocuous initial contact on LinkedIn to escalating requests. “Little by little, the asks get bigger and bigger,” he says. “Then by the end of the day, you’re asking the facilitator to go to a government facility to pick up an actual government ID.”
By the time investigators raided Chapman’s home, she was housing several dozen laptops, each with a sticky note indicating the fake worker’s identity and employer. Some of the North Korean operatives worked multiple jobs; some had been toiling quietly for years. Prosecutors said at least 300 employers had been pulled into this single scheme, including “a top-five national television network and media company, a premier Silicon Valley technology company, an aerospace and defense manufacturer, an iconic American car manufacturer, a high-end retail store, and one of the most recognizable media and entertainment companies in the world.” Chapman, they alleged, had helped pass along at least $17 million. She pleaded guilty in February 2025 to charges relating to wire fraud, identity theft, and money laundering and is awaiting sentencing.
Chapman’s case is just one of several North Korean fake-worker prosecutions making their way through US courts. A Ukrainian named Oleksandr Didenko has been accused of setting up a freelancing website to connect fake IT workers with stolen identities. Prosecutors say at least one worker was linked to Chapman’s laptop farm and that Didenko also has ties to operations in San Diego and Virginia. Didenko was arrested in Poland last year and was extradited to the United States. In Tennessee, 38-year-old Matthew Knoot is due to stand trial for his alleged role in a scheme that investigators say sent hundreds of thousands of dollars to accounts linked to North Korea via his laptop farm in Nashville. (Knoot has pleaded not guilty.) And in January 2025, Florida prosecutors filed charges against two American citizens, Erick Ntekereze Prince and Emanuel Ashtor, as well as a Mexican accomplice and two North Koreans. (None of the defendants’ lawyers in these cases responded to requests for comment.) The indictments claim that Prince and Ashtor had spent six years running a string of fake staffing companies that placed North Koreans in at least 64 businesses.
before the hermit kingdom had its laptop farms, it had a single confirmed internet connection, at least as far as the outside world could tell. As recently as 2010, that one link to the web was reserved for use by high-ranking officials. Then, in 2011, 27-year-old Kim Jong Un succeeded his father as the country’s dictator. Secretly educated in Switzerland and said to be an avid gamer, the younger Kim made IT a national priority. In 2012, he urged some schools to “pay special attention to intensifying their computer education” to create new possibilities for the government and military. Computer science is now on some high school curricula, while college students can take courses on information security, robotics, and engineering.
The most promising students are taught hacking techniques and foreign languages that can make them more effective operatives. Staff from government agencies including the Reconnaissance General Bureau— the nation’s clandestine intelligence service—recruit the highest-scoring graduates of top schools like Kim Chaek University of Technology (described by many as “the MIT of North Korea”) or the prestigious University of Sciences in Pyongsong. They are promised good wages and unfettered access to the internet—the real internet, not the intranet available to well-off North Koreans, which consists of a mere handful of heavily censored North Korean websites.
The earliest cyberattacks launched by Pyongyang were simple affairs: defacing websites with political messages or launching denial-of-service attacks to shut down US websites. They soon grew more audacious. In 2014, North Korean hackers famously stole and leaked confidential information from Sony’s film studio. Then they targeted financial institutions: Fraudulent trades pulled more than $81 million from the Bank of Bangladesh’s accounts at the New York Federal Reserve. After that, North Korean hackers moved into ransomware—the WannaCry attack in 2017 locked hundreds of thousands of Windows computers in 150 countries and demanded payments in bitcoin. While the amount of revenue the attack generated is up for debate—some say it earned just $140,000 in payouts—it wreaked much wider damage as companies worked to upgrade their systems and security, costing as much as $4 billion, according to one estimate.
Governments responded with more sanctions and stronger security measures, and the regime pivoted, dialing back on ransomware in favor of quieter schemes. It turns out these are also more lucrative: Today, the most valuable tool in North Korea’s cybercrime armory is cryptocurrency theft. In 2022, hackers stole more than $600 million worth of the cryptocurrency ether by attacking the blockchain game Axie Infinity; in February of this year, they robbed the Dubai-based crypto exchange Bybit of $1.5 billion worth of digital currency. The IT pretender scam, meanwhile, seems to have been growing slowly until the pandemic dramatically expanded the number of remote jobs, and Pyongyang saw the perfect opportunity.
In 2024, according to a recent report from South Korea’s National Intelligence Service, the number of people working in North Korea’s cyber divisions—which includes pretenders, crypto thieves, and military hackers—stood at 8,400, up from 6,800 two years earlier. Some of these workers are based in the country, but many are stationed overseas in China, Russia, Pakistan, or elsewhere. They are relatively well compensated, but their posting is hardly cushy.
Teams of 10 to 20 young men live and work out of a single apartment, sleeping four or five to a room and grinding up to 14 hours a day at weird hours to correspond with their remote job’s time zone. They have quotas of illicit earnings they are expected to meet. Their movements are tightly controlled, as are those of their relatives, who are effectively held hostage to prevent defections. “You don’t have any freedom,” says Hyun-Seung Lee, a North Korean defector who lives in Washington, DC, and says some of his old friends were part of such operations. “You’re not allowed to leave the apartment unless you need to purchase something, like grocery shopping, and that is arranged by the team leader. Two or three people must go together so there’s no opportunity for them to explore.”
The US government estimates that a typical team of pretenders can earn up to $3 million each year for Pyongyang. Experts say the money is pumped into everything from Kim Jong Un’s personal slush fund to the country’s nuclear weapons program. A few million dollars may seem small next to the flashy crypto heists— but with so many teams operating in obscurity, the fraud is effective precisely because it is so mundane.
in the summer of 2022, a major multinational company hired a remote engineer to work on website development. “He would dial in to meetings, he would participate in discussions,” an executive at the company told me on condition of anonymity. “His manager said he was considered the most productive member of the team.”
One day, his coworkers organized a surprise to celebrate his birthday. Colleagues gathered on a video call to congratulate him, only to be startled by his response—but it’s not my birthday. After nearly a year at the company, the worker had apparently forgotten the birth date listed in his records. It was enough to spark suspicion, and soon afterward the security team discovered that he was running remote access tools on his work computer, and he was let go. It was only later, when federal investigators discovered one of his pay stubs at Christina Chapman’s laptop farm in Arizona, that the company connected the dots and realized it had employed a foreign agent for nearly a year.
For many pretenders, the goal is simply to earn a good salary to send back to Pyongyang, not so much to steal money or data. “We’ve seen long-tail operations where they were going 10, 12, 18 months working in some of these organizations,” says Adam Meyers, a senior vice president for counter adversary operations at the security company CrowdStrike. Sometimes, though, North Korean operatives last just a few days— enough time to download huge amounts of company data or plant malicious software in a company’s systems before abruptly quitting. That code could alter financial data or manipulate security information. Or these seeds could lay dormant for months, even years.
“The potential risk from even one minute of access to systems is almost unlimited for an individual company,” says Declan Cummings, the head of engineering at software company Cinder. Experts say that attacks are ramping up not just in the US but also in Germany, France, Britain, Japan and other countries. They urge companies to do rigorous due diligence: speak directly to references, watch for candidates making sudden changes of address, use reputable online screening tools, and conduct a physical interview or in-person ID verification.
But none of these methods are foolproof, and AI tools are constantly weakening them. ChatGPT and the like give almost anyone the capacity to answer esoteric questions in real time with unearned confidence, and their fluency with coding threatens to make programming tests irrelevant. AI video filters and deepfakes can also add to the subterfuge.
At an onboarding call, for instance, many HR representatives now ask new employees to hold their ID up to the camera for closer inspection. “But the fraudsters have a neat trick there,” says Donal Greene, a biometrics expert at the online background check provider Certn. They take a green-colored card the exact shape and size of an identity card—a mini green screen—and, using deepfake technology, project the image of an ID onto it. “They can actually move it and show the reflection,” says Greene. “It’s very sophisticated.” North Korean agents have even been known to send look-alikes to pick up a physical ID card from an office or to take a drug test required by prospective employers.
Even security experts can be fooled. In July 2024, Knowbe4, a Florida-based company that offers security training, discovered that a new hire known as “Kyle” was actually a foreign agent. “He interviewed great,” says Brian Jack, KnowBe4’s chief information security officer. “He was on camera, his résumé was right, his background check cleared, his ID cleared verification. We didn’t have any reason to suspect this wasn’t a valid candidate.” But when his facilitator—the US-based individual giving him cover—tried to install malware on Kyle’s company computer, the security team caught on and shut him out.
Back in london, Simon Wijckmans couldn’t let go of the idea that somebody had tried to fool him. He’d just read about the Knowbe4 case, which deepened his suspicions. He conducted background checks and discovered that some of his candidates were definitely using stolen identities. And, he found, some of them were linked to known North Korean operations. So Wijckmans decided to wage a little counter exercise of his own, and he invited me to observe.
I dial in to Google Meet at 3 am Pacific time, tired and bleary. We deliberately picked this offensively early hour because it’s 6 am in Miami, where the candidate, “Harry,” claims to be.
Harry joins the call, looking pretty fresh-faced. He’s maybe in his late twenties, with short, straight, black hair. Everything about him seems deliberately nonspecific: He wears a plain black crewneck sweater and speaks into an off-brand headset. “I just woke up early today for this interview, no problem,” he says. “I know that working with UK hours is kind of a requirement, so I can get my working hours to yours, so no problem with it.”
So far, everything matches the hallmarks of a fake worker. Harry’s virtual background is one of the default options provided by Google Meet, and his connection is a touch slow. His English is good but heavily accented, even though he tells us he was born in New York and grew up in Brooklyn. Wijckmans starts with some typical interview questions, and Harry keeps glancing off to his right as he responds. He talks about various coding languages and name-drops the frameworks he’s familiar with. Wijckmans starts asking some deeper technical questions. Harry pauses. He looks confused. “Can I rejoin the meeting?” he asks. “I have a problem with my microphone.” Wijckman nods, and Harry disappears.
A couple of minutes pass, and I start to fret that we’ve scared him away, but then he pops back into the meeting. His connection isn’t much better, but his answers are clearer. Maybe he restarted his chatbot, or got a coworker to coach him. The call runs a few more minutes and we say goodbye.
Our next applicant calls himself “Nic.” On his résumé he’s got a link to a personal website, but this guy doesn’t look much like the profile photo on the site. This is his second interview with Wijckmans, and we are certain that he’s faking it: He’s one of the applicants who failed the background check after his first call, although he doesn’t know that.
Nic’s English is worse than Harry’s: When he’s asked what time it is, he tells us it’s “six and past” before correcting himself and saying “quarter to seven.” Where does he live? “I’m in Ohio for now,” he beams, like a kid who got something right in a pop quiz.
Several minutes in, though, his answers become nonsensical. Simon asks him a question about web security. “Political leaders ... government officials or the agencies responsible for border security,” Nic says. “They’re responsible for monitoring and also securing the borders, so we can employ the personnel to patrol the borders and also check the documents and enforce the immigration laws.”
I’m swapping messages with Wijckmans on the back channel we’ve set up when it dawns on us: Whatever AI bot Nic seems to be using must have misinterpreted a mention of “Border Gateway Protocol”—a system for sending traffic across the internet—with national borders, and started spewing verbiage about immigration enforcement. “What a waste of time,” Wijckmans messages me. We wrap up the conversation abruptly.
I try to put myself in the seat of a hiring manager or screener who’s under pressure. The fraudsters’ words may not have always made sense, but their test scores and résumés looked solid, and their technical-sounding guff might be enough to fool an uninformed recruiter. I suspect at least one of them could have made it to the next step in some unsuspecting company’s hiring process.
Wijckmans tells me he has a plan if he comes across another pretender. He has created a web page that looks like a standard coding assessment, which he’ll send to fake candidates. As soon as they hit the button to start the test, their browser will spawn dozens of pop-up pages that bounce around the screen, all of them featuring information on how to defect from North Korea. Then loud music plays—a rickroll, “The Star-Spangled Banner”—before the computer starts downloading random files and emits an ear-splitting beep. “Just a little payback,” he says.
Wijckman’s stunt is not going to stop the pretenders, of course. But maybe it will irritate them for a moment. Then they’ll get back to work, signing on from some hacking sweatshop in China or through a laptop farm in the US, and join the next team meeting—a quiet, camera-off chat with coworkers just like me or you.
7 notes
·
View notes
Text
Just a few public "Mind Control" projects. MKULTRA
"Military Funds Brain-Computer Interfaces to Control Feelings" https://www.technologyreview.com/s/527561/military-funds-brain-computer-interfaces-to-control-feelings/
US military successfully tests electrical brain stimulation to enhance staff skills https://www.theguardian.com/science/2016/nov/07/us-military-successfully-tests-electrical-brain-stimulation-to-enhance-staff-skills
Wireless magnetothermal deep brain stimulation http://science.sciencemag.org/content/early/2015/03/11/science.1261821?sid=53443da4-1e9c-4321-b54e-c142179e9294
MIT Researchers Develop Wireless, Noninvasive Deep Brain Stimulation Approach https://www.meddeviceonline.com/doc/mit-researchers-develop-wireless-noninvasive-deep-brain-stimulation-approach-0001
Dark past of deep-brain stimulation https://www.nature.com/articles/d41586-018-02963-6
Watch your tone
Voice-analytics software helps customer-service reps build better rapport with customers. http://news.mit.edu/2016/startup-cogito-voice-analytics-call-centers-ptsd-0120
Mind control: Scientists can now make people alter their prejudices and belief in God https://www.ibtimes.co.uk/mind-control-scientists-can-now-make-people-alter-their-prejudices-belief-god-1524122
Mind Control by Cell Phone
Electromagnetic signals from cell phones can change your brainwaves and behavior https://www.scientificamerican.com/article/mind-control-by-cell/
Washington State Fusion Center accidentally releases records on remote mind control
As part of a request for records on Antifa and white supremacist groups, WSFC inadvertently bundles in “EM effects on human body.zip” https://www.muckrock.com/news/archives/2018/apr/18/fusion-center-em/
Nervous system manipulation by electromagnetic fields from monitors https://patents.google.com/patent/US6506148
#5th generation warfare#deep state#shadow government#domestic terrorism#mk ultra#strategy of tension
14 notes
·
View notes
Text
North Korean hackers have stolen the equivalent of billions of dollars in recent years and the nation is seeking to amass even greater wealth through illicit means, experts told DW.
Hackers belonging to the Lazarus Group — a notorious North Korean crypto theft ring — stole a record $1.5 billion (some €1.37 billion) in digital tokens from Dubai-based cryptocurrency exchange ByBit in late February. The company said the hackers had accessed its digital wallet for Ethereum, the second-largest electronic currency after Bitcoin.
Binance News, a new platform operated by cryptocurrency exchange firm Binance, reported last month that North Korea now has some 13,562 Bitcoins, the equivalent of $1.14 billion. Bitcoin is the world's oldest and best known cryptocurrency, often compared with gold due to its alleged resistance to inflation. Only the US and Great Britain have greater reserves of the currency, Binance News said, citing crypto data provider Arkham Intelligence.
"Let's not mince words — [North Korea] achieved this through theft," Aditya Das, an analyst at cryptocurrency research firm Brave New Coin in Auckland, New Zealand, told DW.
"Global policing agencies like the FBI have publicly warned that North Korean state-sponsored hackers are behind numerous attacks on cryptocurrency platforms," he added.
Hackers use social engineering against crypto firms
Despite those warnings, however, crypto firms are still being robbed and North Korean hackers are becoming increasingly sophisticated, the analyst said.
"North Korea employs a wide range of cyberattack techniques, but they've become especially known for their skill in social engineering," said Das.
"Many of their operations involve infiltrating employee hardware, then using that access to breach internal systems or lay traps from the inside."
The hacker's primary targets are crypto startups, exchanges and decentralized finance (DeFi) platforms due to their "often under-developed security protocols," he said.
Recovery of funds 'extremely rare'
Elite North Korean hackers tend to take their time when infiltrating a legitimate global organization, often by impersonating venture capitalists, recruiters or remote IT workers to build up trust and breach firms' defenses.
"One group, Sapphire Sleet, lures victims into downloading malware disguised as job applications, meeting tools or diagnostic software — essentially turning victims into their own attack vectors," Das said.
Once crypto has been stolen, Das says recovery is "extremely rare." Cryptocurrency systems are designed to make transactions irreversible and striking back against North Korean operatives "is not a viable option because these are nation-state actors with top-tier cyber defenses."
Kim Jong Un's regime 'saved' by cryptocurrency theft
Park Jung-won, a professor of law at Dankook University, said North Korea previously relied on risky transactions — such as smuggling narcotics and counterfeit goods or supplying military instructors to African nations — to earn illicit funds.
The legal expert says the advent of cryptocurrency "has been a huge opportunity" for dictator Kim Jong Un.
"It is probably fair to say that given the way the world was cracking down on Pyongyang's smuggling efforts, crypto has saved the regime," Park told DW. "Without it, they would have been completely without funds. They know that and they have invested heavily in training the best hackers and getting them up to a very high level of skill."
"The money that they are stealing is going straight to the government and the assumption is that it is being spent on weapons and greater military technology as well as the Kim family," according to Park.
North Korea immune to international pressure
Park does not believe that outside pressure would force North Korea to end hacking attacks.
"For Kim, the survival of his dynasty is the most important priority," the law professor said.
"They have become accustomed to this source of revenue, even if it is illegal, and they will not change," he added. "There is no reason for them to suddenly start abiding by international law and there is no way to apply more pressure."
Das agrees there are few tools available to influence North Korea. He says companies need to do everything in their power to avoid becoming the next victim.
"Best practices like secure-by-design smart contracts, constant internal verification and social engineering awareness are essential if the industry wants to stay ahead," he said.
Crypto firms need universal security standards
There's growing momentum for sector-wide information sharing which would help crypto firms detect North Korean tactics and avert attacks, but Das warns that crypto remains "fragmented" because there is no universal security standard. Also, North Korean hackers are good at turning security tools against their users, according to the analyst.
"In the Bybit case, the attackers exploited Safe, a multi-signature wallet system meant to enhance security. Ironically, this added security layer became the very exploit they used," he said.
And in practice, Das added, "some firms still treat security as an afterthought."
"From my experience, teams often prioritize shipping fast over building secure systems and until that changes, the space will remain vulnerable," Das said.
#nunyas news#have to wonder what would happen#if all of a sudden a bunch of countries#started selling their crypto off#would the market tank or no
8 notes
·
View notes