#salesforce security
Explore tagged Tumblr posts
Text
Best Practices for Salesforce Security Awareness Training
Introduction
Cybersecurity isn’t just a technology issue—it’s a people issue. Despite Salesforce’s robust built-in security features, many breaches still stem from human error, like credential theft or misconfigured permissions. With Salesforce being a mission-critical system for many organizations, it's essential to ensure that every user understands how to protect data and follow secure practices.
The Salesforce security model provides the technical backbone for protecting information—offering fine-grained access controls, authentication protocols, and audit tools. But without adequate user training, these controls can be undermined. That’s why Salesforce security awareness training is not optional—it’s foundational.
Understanding the Salesforce Security Model
Core Components of the Salesforce Security Model
Salesforce’s layered security model includes:
Authentication and Identity: Tools like Single Sign-On (SSO) and Multi-Factor Authentication (MFA) protect access.
Authorization Controls: Role hierarchies, profiles, permission sets, and sharing rules determine who can see and do what.
Data Protection: Field-level security, encrypted data at rest and in transit, and IP restrictions.
Monitoring & Compliance: Tools like Salesforce Shield, Event Monitoring, and the Security Health Check help detect threats.
Why Security Awareness Is Integral to the Model
While these features are powerful, they are only as effective as the users behind them. Many breaches occur not from platform flaws but from end users falling for phishing scams or inadvertently exposing data. Training users on the nuances of the Salesforce security model is essential for reinforcing its effectiveness.
Why Organizations Need Salesforce Security Awareness Training
Rising Threat Landscape in Cloud CRMs
Cloud CRM platforms like Salesforce are prime targets for cybercriminals. Common threats include:
Phishing attacks that harvest login credentials
Session hijacking through unsecured devices or networks
Misuse of integration tools that open backdoors
Falling prey to these risks can trigger serious compliance violations under laws like GDPR, HIPAA, and CCPA.
The Role of End-User Behavior in Security
Many data incidents originate from user actions, such as:
Downloading datasets to unencrypted drives
Sharing reports with unauthorized parties
Weak password practices or password reuse
Training helps users understand how their actions impact the broader Salesforce security model and compliance posture.
Best Practices for Salesforce Security Awareness Training
Align Training with the Salesforce Security Model
Security awareness must mirror the technical controls in place. Focus on:
Understanding role-based access and permission sets
Encouraging use of MFA and strong authentication
Educating users on secure report sharing and export practices
Tailor Training Based on User Roles
A one-size-fits-all approach won’t work. Admins need deeper insight into security configuration, while Sales users need guidance on data handling and phishing. Role-specific training leads to better retention and application.
Simulate Real-World Threats During Training
Make the training actionable by simulating phishing attacks or unauthorized data access scenarios. Use tools like Salesforce’s own phishing simulation modules or third-party LMS platforms to reinforce learnings.
Create a Culture of Continuous Security Learning
Security awareness isn’t a one-time event. Reinforce knowledge through:
Microlearning modules
Gamified assessments
Certification-based incentives using Trailhead or custom LMS paths
Measuring the Effectiveness of Training Programs
Key Metrics to Track
Use the following indicators to measure impact:
Decline in phishing test failures
Increased MFA adoption rates
Improved reporting of suspicious activity
Feedback Loops and Iterative Improvements
Post-training surveys and feedback sessions help refine future content. Leverage Salesforce analytics dashboards to detect risky behavior patterns and adapt your training accordingly.
Tools and Resources to Support Training
Leverage Salesforce Native Tools
Salesforce Shield for encryption, monitoring, and audit trails
Health Check to assess and improve org security posture
Security Center for real-time visibility across instances
Third-Party Training Platforms and LMS Integration
Organizations can supplement internal training with SCORM-compliant content or integrate Salesforce-specific security modules from platforms like KnowBe4 or Infosec IQ.
Conclusion
When users understand their role within the Salesforce security model, they become active defenders of enterprise data. Technical defenses are essential—but without human vigilance, they remain incomplete. Embedding security awareness into your organizational culture isn’t just smart—it’s a business imperative.
Call to Action
Want to secure your Salesforce environment beyond just configuration? Start by empowering your people. Embed awareness into every interaction, aligned with the Salesforce security model.
Protect your platform. Train your users. Strengthen your future.
#salesforce security model#salesforce security#salesforce cloud#sfdc security model#security model in salesforce#sfdc security#data security in salesforce#security salesforce#salesforce data security#salesforce field level security#salesforce consultant
0 notes
Text
Elevate Your Career with Salesforce Certification
Salesforce Certification is a recognized credential that validates your expertise in Salesforce's CRM platform. Whether you're an administrator, developer, or marketer, earning this certification demonstrates your skills in managing Salesforce tools and solutions effectively. It helps you stand out in the competitive job market, boosts your earning potential, and opens doors to exciting career opportunities. With various certification paths, including Salesforce Administrator, Developer, and Consultant, there's a track for every professional goal. Gain a competitive edge by becoming a Salesforce-certified expert today!
0 notes
Text
I don't like that the dev community picks on people who are most fluent in Python, when the ChatGPT-using "vibe coders" are right there. At least Python babies are coding. Bully the non-coders instead.
#coding#programming#anyone that doesn't know 'vibe coding' means they asked ChatGPT to write code for them.#Same concept as 'I am a creative bc an LLM regurgitated an output for me'. 'I am an artist bc I told a machine to paint for me.'#programmer#I don't know if people even use that phrase anymore to be honest I feel like it's fallen out of use in favour of engineer or developer#ai bullshit#like. If they hire anyone that actually does know the first thing about coding in favour of a prompt engineer (so-called engineer)#they are going to realise—to costs to the tune of millions—that you can't 'vibe code' your way out of security vulnerabilities. Idiots.#I think we're a good few years out from that since anyone that still has a dev team (i.e. everyone; yes even Salesforce*) realises that#letting a text generator run your business would be MADNESS. That's not gonna happen until the AI snakeoil salesmen manage to gradually#lower everyone's standards of accuracy; security and objectivity. When that happens we're all fucked#(*https://www.salesforceben.com/salesforce-will-hire-no-more-software-engineers-in-2025-says-marc-benioff/#tl;dr salesforce snakeoi— CEO says no more software devs; our AI is sophisticated enough.#Balls it is.)#software engineering#programmer humor#etc etc
45 notes
·
View notes
Text

Summer Internship Program 2024
For More Details Visit Our Website - internship.learnandbuild.in
#machine learning#programming#python#linux#data science#data scientist#frontend web development#backend web development#salesforce admin#salesforce development#cloud AI with AWS#Internet of things & AI#Cyber security#Mobile App Development using flutter#data structures & algorithms#java core#python programming#summer internship program#summer internship program 2024
2 notes
·
View notes
Text

XfilesPro is transforming how organizations manage and protect documents within Salesforce by introducing a robust, enterprise-grade security framework. By combining features like advanced access controls, encrypted file storage, and seamless external sharing safeguards, XfilesPro ensures data confidentiality while enhancing user efficiency. Its dynamic integration with Salesforce workflows enables secure collaboration without compromising compliance, making it a reliable solution for regulated industries.
#Salesforce document security#Salesforce file security tool#data protection Salesforce#Salesforce data compliance
0 notes
Text
When Trusted Tools Turn Rogue: Hackers Exploit Salesforce App to Breach Global Firms
In a chilling revelation, Google has exposed a sophisticated cyber campaign where hackers are manipulating a Salesforce-related app to steal sensitive corporate data and extort companies. The attackers have successfully targeted organizations across Europe and the Americas by convincing employees to install a tampered version of Salesforce's Data Loader. This attack, tracked by Google's Threat Intelligence Group under the identifier UNC6040, underscores the growing vulnerabilities in enterprise software environments and the alarming ease with which cybercriminals can infiltrate even the most trusted digital infrastructures.

#Salesforce app breach#Google cyber threat report#UNC6040 hackers#Salesforce Data Loader attack#cyberattack global firms#enterprise software hack#cloud security breach#social engineering cybercrime#Google Threat Intelligence
0 notes
Text

Build secure and robust Salesforce applications with Lightning Web Components.
LWC leverages the latest web security standards and enforces strict security rules, minimizing vulnerabilities and protecting your data. Rest easy knowing your applications are shielded against common web threats.
#LWC #Salesforce #LightningWebComponents #Security #WebSecurity #DataProtection #SecureCoding #Cybersecurity #Trust
Build secure and robust Salesforce applications with Lightning Web Components.
LWC leverages the latest web security standards and enforces strict security rules, minimizing vulnerabilities and protecting your data. Rest easy knowing your applications are shielded against common web threats.
#LWC #Salesforce #LightningWebComponents #Security #WebSecurity #DataProtection #SecureCoding #Cybersecurity #Trust
#LWC#Salesforce#LightningWebComponents#Security#WebSecurity#DataProtection#SecureCoding#Cybersecurity#Trust
0 notes
Text
#salesforce#salesforce cloud#CRM#CRM platform#customer service#Features of Salesforce#manage customer interactions#Service Cloud#Marketing Cloud#Commerce Cloud#Einstein AI#Analytics Cloud#Community Cloud#Mobile App#Operational Efficiency#Scalability#Security
0 notes
Text
Salesforce Security: Advanced Strategies Unlocked
youtube
0 notes
Text
Learn effective Salesforce backup strategies to protect your business data and ensure seamless recovery in case of data loss.
#Salesforce backup#data recovery guide#Salesforce strategies#secure business data#Salesforce data protection
0 notes
Text
Salesforce Role Hierarchy Best Practices for Data Visibility
Establishing a robust role hierarchy is essential for ensuring accurate data visibility and security in any Salesforce implementation. The role hierarchy is a key component of the broader Salesforce security model, which governs how records are accessed across the organization. While the role hierarchy doesn’t grant additional access beyond the organization-wide defaults (OWDs), it allows users higher in the hierarchy to view, edit, and report on all data owned by or shared with users below them.
Here are some best practices to help you design an effective Salesforce role hierarchy for optimal data visibility and security:
1. Align Roles with Business Structure
Your role hierarchy should reflect your organization's actual reporting structure. By mirroring your business units and management lines, you create a framework that supports logical data access while reducing the risk of unauthorized visibility.
2. Keep It Simple and Scalable
Avoid over-complicating the role structure. A complex hierarchy may lead to performance issues and difficulties in managing access. Instead, create a streamlined hierarchy that supports current needs and can easily be scaled as the organization grows.
3. Use Roles and Profiles Together
Roles manage record-level access, while profiles handle object-level permissions. To maintain data integrity, ensure that each user’s role complements their profile settings. This dual-layered approach strengthens your Salesforce security strategy.
4. Leverage Permission Sets for Flexibility
Instead of creating new roles for every exception, use permission sets to grant additional access where necessary. This helps avoid role explosion and keeps the hierarchy clean.
5. Control Visibility with OWD and Sharing Rules
Set your organization-wide defaults (OWDs) to the most restrictive settings, then open access through role hierarchy and sharing rules. This approach adheres to the principle of least privilege, ensuring users see only what they need.
6. Regularly Review and Audit Roles
As business needs change, roles may become outdated or redundant. Schedule periodic audits to ensure the hierarchy still aligns with organizational goals and compliance requirements.
Final Thoughts
A well-structured role hierarchy is not just about data visibility—it’s a cornerstone of the Salesforce security model. By combining roles with profiles, sharing rules, and permission sets, organizations can ensure secure, scalable, and efficient access control. Staying aligned with best practices helps prevent data leaks, simplifies reporting, and strengthens user trust across the Salesforce ecosystem.
0 notes
Text
Top Salesforce Security Best Practices to Protect Your Data

Ensuring robust Salesforce security is vital for safeguarding sensitive business data. Start with role-based access controls to restrict unauthorized access. Use multi-factor authentication (MFA) for enhanced login security. Regularly update permissions and audit logs to identify vulnerabilities. Encrypt data both at rest and in transit to prevent breaches. Leverage Salesforce Shield for advanced monitoring and protection. Periodic security training for users also mitigates human error. Adopting these Salesforce security best practices ensures a secure, compliant, and reliable CRM environment.
0 notes
Text
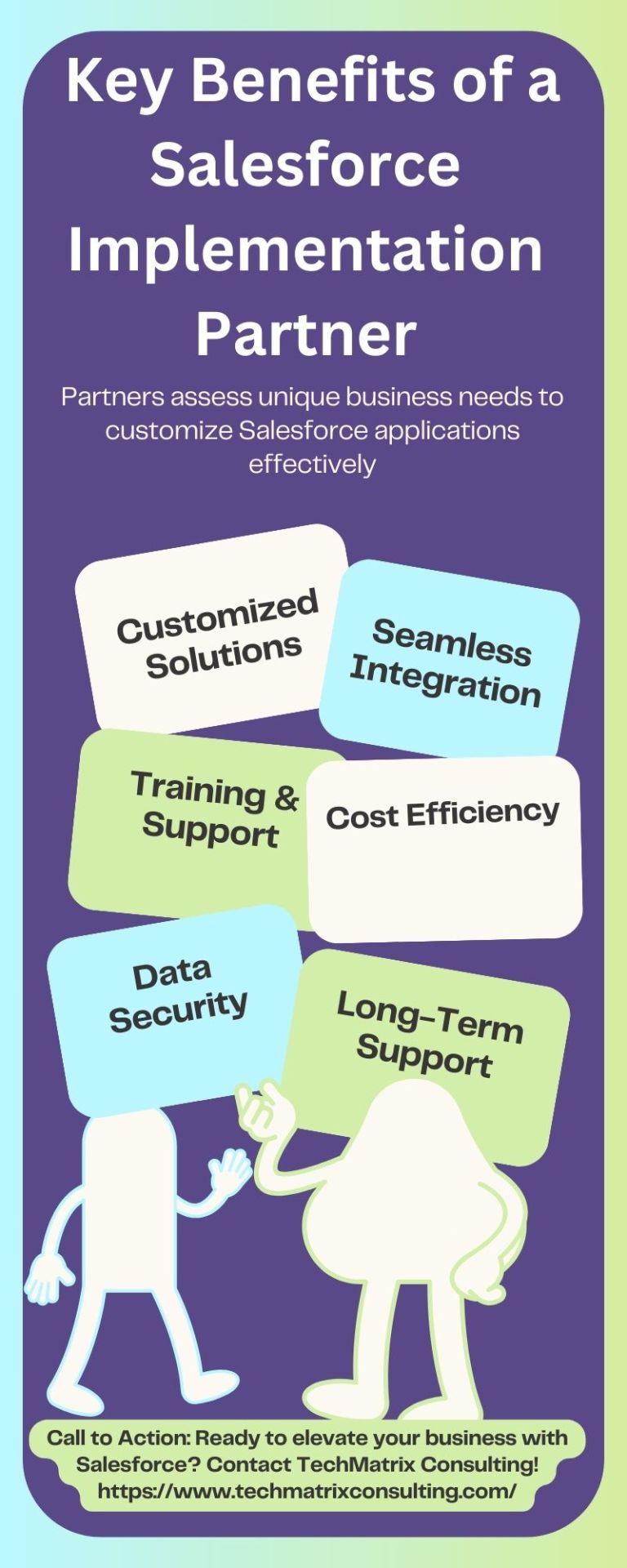
Discover the benefits of working with a certified Salesforce Implementation Partner. From tailored solutions and seamless integration to enhanced data security and scalability, learn how partnering with experts like TechMatrix Consulting can drive your business success. With global experience, 500+ projects, and a dedicated team, TechMatrix ensures smooth implementation and long-term support for your Salesforce needs.
#Salesforce Implementation Partner#certified Salesforce partner#Salesforce consulting services#TechMatrix Consulting Salesforce#Salesforce integration#benefits of Salesforce partner#Salesforce expert support#Salesforce solutions provider#Salesforce CRM implementation#Salesforce consulting firm#choosing Salesforce partner#top Salesforce partners#Salesforce partner benefits#Salesforce data security#Salesforce scalability
0 notes
Text

Mydocify - Streamlined Document Management Software for Businesses
Mydocify is a powerful document management software that helps businesses efficiently organize, store, and retrieve files. Experience seamless document collaboration, version control, and enhanced security with Mydocify’s cloud-based solution.
#document management software#salesforce document management#Document Workflow#Secure and Efficient File Organization#marketing#branding
0 notes
Text
Salesforce Marketing Cloud Solutions for Any Size Business
Whether running a small business or managing a larger enterprise, the Salesforce Marketing Cloud has something in store for you. The powerful platform was designed to help businesses of all sizes easily connect with their customers through personalized marketing interactions at scale. Offering tools for social media, email, advertising, and customer engagement, the Marketing Cloud allows you to…
#Customer Journey Mapping#Email Marketing Automation#Lead Scoring and Nurturing Salesforce#Marketing Cloud#Marketing Cloud AI#marketing cloud for enterprise#Marketing Cloud for Small Business#marketing cloud for smb#Marketing Cloud Personalization#Marketing Cloud Security Compliance#Marketing for Medium Sized Enterprises#Salesforce AI#Salesforce blog#Salesforce Marketing Cloud Solutions for Any Size Business#sfdc fan boy#sfdcFanBoy
0 notes
Text
Top 5 Customer Identity And Access Management Software Of 2024

You see, CIAM or Customer Identity & Access Management, functions much like the Sorting Hat. It examines an individual's identity against their unique credentials stored in a database, ensuring the person is who they claim to be (no Polyjuice Potion here!) and keeping impostors out of the system.
CIAM Software also categorizes users into their appropriate "house" (access level) based on their roles, preferences, and previous interactions. However, unlike the Sorting Hat, CIAM Software continually monitors user journeys, adjusting permissions as needed to ensure the right people access the right resources at the right times, while keeping out impostors.
So, read on for the top 5 Customer Identity And Access Management Software of 2024!
Customer Identity And Access Management (CIAM) is a security strategy that allows organizations to securely manage their customers’ identities to control their access to applications, portals, and services. CIAM solutions offer a digital security layer in customer interactions, empowering users to secure their identities and data while managing their security preferences.
Customer Identity And Access Management (CIAM) Software simplifies this approach by streamlining the sign-up and log-in process for online applications and services. This helps in protecting data privacy, defending against identity theft and other types of fraud, as well as managing account profiles and security settings. Moreover, the solution helps businesses improve the customer experience while complying with data privacy mandates such as the GDPR.
Last year, we covered the top CIAM solutions of 2023. To find out about this year's top options, read on and explore the top 5 Customer Identity And Access Management Software of 2024!
Top 5 Customer Identity And Access Management (CIAM) Software Of 2024
CIAM Software provides businesses with features such as customer registration, self-service account management, consent and preference management, single sign-on (SSO), multi-factor authentication (MFA), access management, data access governance, identity proofing, identity orchestration, fraud mitigation, and more, to deliver seamless and secure customer experiences. Pretty cool, right?
So, here are the top 5 Customer Identity And Access Management Software of 2024 – in no particular order!
Tool 1: WSO2 Identity Server
Founded in August 2005 and headquartered in Mountain View, California, United States, WSO2 began as an open-source middleware company and now offers suites for application development, SaaS, and IAM solutions. With over 900 employees, serving major clients such as Nutanix, Jaguar, Vodafone, Honda, and Cisco, WSO2 has secured over 1 billion identities. The company has also won several awards, including being named a Customers’ Choice in the Gartner Peer Insights Voice of the Customer report in 2023. Pretty cool, WSO2!
WSO2 Identity Server, new to our list, excels in customer identity and access management with its open-source platform that helps secure applications for individuals, enterprise customers, citizens, and more. It offers robust features such as single sign-on (SSO), multifactor authentication (MFA), and identity federation to ensure seamless, secure, and streamlined user experiences. The platform also offers scalable features for passwordless logins, data privacy compliance, enterprise SSO, role-based access management, and contextual authentication.
Moreover, WSO2 Identity Server provides a wide range of APIs and SDKs to help businesses develop custom deployments that easily integrate with existing systems. This solution is compatible with cloud-based IDaaS, on-premises, or private cloud and comes in three variants – B2B, B2C, and G2C – enabling secure identity and access management for diverse customer sets. WSO2 can easily help organizations optimize customer data security, leading to more engaging experiences!
Tool 2: IBM Security Verify
Who hasn’t heard of IBM? Founded in 1911 and headquartered in Armonk, New York, United States, IBM employs roughly 300,000 people globally, serving major clients such as Apple, NASA, Ford, and Cisco. IBM has received numerous industry accolades, including winning 16 awards from Comparably in 2023, ranging from Best Company for Diversity to Happiest Employees. Impressive, IBM!
IBM Security Verify, making its debut on our list, is notable for its advanced security and AI-driven features for customer identity and access management. The CIAM solution offers adaptive authentication, identity analytics, and risk-based access control to ensure customer data is always protected. Moreover, IBM Security Verify creates a consistent, frictionless authentication experience across all business applications, ensuring customers have a smooth experience at every touchpoint.
With robust integration capabilities that support diverse environments, spanning cloud, on-premises, and hybrid infrastructures, IBM Security Verify helps build an enterprise-wide identity fabric that eliminates identity silos. Further, AI-driven analytics provide real-time threat detection based on users’ behaviors and biometrics to help protect from identity-based attacks such as Account Takeover (ATO). IBM Security Verify also enhances the overall security posture, offers a user-friendly interface, and comprehensive reporting tools to efficiently manage and monitor access policies.
Tool 3: Frontegg
Frontegg, an end-to-end user management solutions provider, was founded in 2019. With a modest team of fewer than 100 employees and headquarters in Tel Aviv, Israel, Frontegg serves clients such as Talon, Siemens, Cider, and Vial. It has received several recognitions, including winning the Best Software Award for Security Products category by G2 in 2023. Always at the front, Frontegg!
Frontegg, making its second consecutive appearance on our list, distinguishes itself in the CIAM space with a developer-centric platform featuring comprehensive user management capabilities. Besides seamless integration and rapid deployment, Frontegg offers extensive features such as social login, SSO, MFA, APIs, and open-source SDKs, providing businesses with everything they need to ensure a secure and frictionless user experience.
Frontegg’s user-friendly interface enables developers to quickly customize and integrate identity and access management features into their applications. Its modular architecture allows businesses to tailor, modify, and scale their CIAM capabilities as needed. With real-time monitoring and analytics, Frontegg provides actionable insights for authentication, authorization, security management, and observability, leading to comprehensive IAM coverage. No wonder Frontegg is a popular choice for organizations looking to enhance their customer data management!
Tool 4: Salesforce Platform
Salesforce, a leading cloud software company, was founded in 1999 and is headquartered in San Francisco, California, United States. Employing roughly 80,000 people globally, Salesforce serves major brands such as Amazon, Adidas, Coca-Cola, Walmart Inc., and more. The company has won several accolades, being ranked as the #1 CRM provider by IDC in the 2024 Worldwide Semiannual Software Tracker for the 11th consecutive time. How cool is that!
Salesforce Platform, new to our list, boasts CIAM capabilities integrated into its popular CRM ecosystem, offering a seamless and secure user experience. Key CIAM features include single sign-on, MFA, identity federation, and user lifecycle management, ensuring comprehensive management of user identity and access. Its integration with Salesforce CRM provides a unified view of customer data, access levels, roles, and more, enhancing context-based security capabilities.
The scalable architecture supports large-scale deployments, securing identities for employees, partners, and customers from a unified solution. Its intuitive user interface simplifies managing access policies and integrating third-party applications. Additionally, Salesforce’s advanced analytics and reporting tools provide deep insights into user behavior across the ecosystem, helping organizations optimize their identity management and security strategies.
Tool 5: Okta Customer Identity
Founded in 2009 and headquartered in San Francisco, California, United States, Okta employs over 5,800 people, serving clients such as Apple, Mitsubishi Heavy Industries, MGM Resorts International, and Albertsons. Okta has won several awards and recognitions, most recently being named the Google Cloud Technology Partner of the Year for Productivity and Collaboration in 2024. That’s pretty sweet, Okta!
Okta Customer Identity, making its first appearance on our list, offers extensive cloud-based CIAM features such as SSO, MFA, adaptive authentication, and user security management. Its cloud-native architecture ensures high availability and scalability, supporting millions of customer interactions seamlessly. Okta Customer Identity’s advanced security features, such as threat detection and response, Okta AI, progressive profiling, adaptive MFA, and more, provide robust protection against identity-related threats.
The platform’s intuitive interface and comprehensive APIs simplify third-party integrations and the management of identity services across various applications and ecosystems. Okta Customer Identity also enhances compliance with regulatory requirements and personal data protection laws to ensure customer information remains secure. With its powerful features, Okta Customer Identity can help organizations enhance customer security and user experiences!
Conclusion
There you have it, folks!
Choosing an ideal Customer Identity and Access Management Software is crucial for safeguarding customer data, complying with data security regulations, and enhancing the end-user experience. With the best Customer Identity And Access Software, you can streamline identity management, eliminate identity theft, secure user actions, boost customer loyalty, and foster higher trust in your brand.
However, remember that every business has unique customer management requirements. Make sure you choose a tool that addresses your unique needs. Happy CIAM-ing!
0 notes