#securityeverywhere
Explore tagged Tumblr posts
Text
Current State of Biometrics
We already know the issues we face with passwords and other single-factor authentication protocols. They are often ‘weak’, reused and can be easily forgotten given the number of passwords some people have to remember. This is where the idea of biometrics comes in - it aims to alleviate these concerns by mapping the concept of authentication to physical aspects of our bodies. The question is how good are biometrics right now and where are they vulnerable?

I want to go over the main types that are in use today which are:
Iris / retina scanning - uses unique patterns in the iris or vein patterns in the retina
Facial recognition - extract features of the face (i.e. distance between eyes) and match against a database
Fingerprint scanning - identification via the ridges and valleys on your fingers
Finger dimensions & palm veins - not as common as fingerprints but beginning to gain popularity
DNA - copying and splitting of genetic markers in our genes (very accurate)
There are some other interesting emerging ones too:
Voice recognition - can recognise an individual in as few as 100 datapoints in your speech
Ear recognition - shape of human ear is unique to every individual; remains pretty much the same from birth to death
Typing - identification of individuals through habits of using a keyboard (i.e. rhythm & key pressure)
Gait - mainly used in analysing athletes at present, but could be expanded to identify individuals (unique ways in which joints move)
All these methods of identifying individuals via biometrics are ‘good and well’, however we have one main issue with them all. In order for an organisation to use these as authentication, these elements need to be converted into data and stored. If the data was compromised then you have permanently lost your biometric authentication (for that aspect) - there are only so many physical aspects you can use for biometrics, where as you aren’t limited in password choice. There have already been proven methods today to forge facial recognition, fingerprints and iris scans from this data. Honestly, I don’t think biometrics alone can provide great security at this stage - although, I think as part of a multi-factor authentication, they definitely add to the overall security. (it’s just another pain in the ‘butt’ for an attacker)
The other big issue with systems implementing biometrics is the ‘type I / type II error tradeoff’. Being able to recognise the physical features in sufficient detail such that it recognises the individual most of the time, without leading to a significant increase in false positives, is difficult. I’m pretty sure Richard already mentioned in the lectures the example of going through the airport - the systems are tilted towards approving identities, otherwise we would have huge queues and lots of manual intervention required.
TransportNSW - Facial Recognition Replace Opal Cards? (article)
The transport minister, Andrew Constance, basically discussed the idea of using facial recognition in the not-too-distant future instead of Opal Cards. Now I don’t actually see any issues regarding forging authentication in this case - since the costs are so minimal for a single transaction, it wouldn’t be worth the effort for an attacker to try and forge it. My problem revolves around the fact I don’t think our facial recognition technology is good enough to do this yet; we can barely recognise people with lined up passport photos at the airport.
My other major concern relates to privacy - the government will be investing billions of dollars if they were to try and develop this system, so who says that would just limit it to transport? I think they would try and expand the system to law enforcement and every other area of government, if they manage to get the authentication working well. Remember a lot of image recognition systems rely on being able to ‘train against data’; if millions of people are using the systems every day then you can collect a lot of data in a short period of time. They would be able to get so good at recognising your face in every shade of light and every angle; to the point where they could use this on every camera in their control. This is the point we become a ‘surveillance state’.
China - Facial Recognition (article)
Some of the things China has been doing with regards to facial recognition are definitely starting to feel like an Orwellian dystopia. According to the article, here are the main things they’ve been doing in 2018:
Police facial recognition glasses - almost like ‘Google Glass’, they can be used to identify individuals and flag criminals
Drones in class - used to scan student’s faces to track attendance and how closely they followed lectures
“Smart” uniforms - microchipped school uniforms to give location and link up with on-school facial recognition
AI news anchors - used to ‘effectively replace’ an anchor when breaking news needs to be broadcast
Facial recognition near rivers - recognition used to detect children near river to give them warnings and alert parents
Checking up on animals - facial recognition to identify pigs and track well-being
San Francisco Biometric Ban (article)
The ban was essentially enacted due to people being concerned about violation of their privacy and civil rights - it prevents “the use of facial recognition software by the police and other agencies”. A number of organisations have spoken out against the ban citing the numerous benefits of biometrics in identification - missing children, fraudulent documents and identity theft. Honestly I think this ban is a bit silly; I think a more balanced approach (i.e. restriction to where surveillance can occur) would be more appropriate.
6 notes
·
View notes
Text
Security Everywhere - Hospitals
Yesterday night I was visiting a friend in a hospital, and it’s been a while since I’ve actually been to a hospital (probably a good thing). But when I got there, I was really surprised by the lack of security or even staff in the wards.
I was able to walk right past reception and visit patient wards without having to sign in or be verified anywhere. On the way to actually find the right ward, I accidentally took the lift to a floor which was supposed to be ‘staff only’ access - the mechanism which restricts permissions to visit floor might have been broken. I also noticed some of the elevators didn’t have noticeable security cameras.
After getting to the right ward, I also noticed that there were probably very important medical records about patients just lying around desks that anyone could have picked up. I also saw one instance of a computer that was left logged in and unattended which is obviously a massive security risk, I could have walked up to the computer and looked up potentially confidential information about patients assuming I had access to the database.
Obviously a lot of people who would visit a hospital are there to visit a patient, but what about the low probability event of a random person coming in to harm a patient/staff member.
Ways hospitals might improve their security measures to prevent the risk of this happening:
Implement a sign in sheet at the front of the reception desk where visitors must sign - and staff to monitor who goes in and out of the ward
Training for staff should be improved - know not to leave important documents lying around, and ALWAYS log out of the computer if not in use
Update security protocols for elevators, and other areas of the wards with regular checks
6 notes
·
View notes
Text
Week 6. Security Everywhere
I was watching a video lecture on echo360 to catch up on some work and saw that my lecturer was typing in the pin to the ipad that is used during the lecture. Similarly, a few weeks later the notification of logging into icloud pops up showing the lecturer’s personal email address. Within this email address is the lecturer’s name and six digits which closely resemble the a birth date.
Risk: So, all this is recorded on echo, if an attacker wanted to access this lecturer’s personal details, the ipad can easily be taken and logged in using the pin in the recording.
Also learning from the talk last week regarding passwords, we only require a few pieces of information of an individual to determine the possible passwords to an account. So since we already know the name and possible dob the third piece of information can be found somewhere on the ipad.
Otherwise, it is also possible that some sites are already logged on/ have details saved. i.e. unsw portal.
Prevention and plan for the future:
I guess a lesson that can be learn is that we can’t always keep everything a secret, but keep your personal information to yourself.
If you don’t need to share information don’t
3 notes
·
View notes
Text
Train barriers
Train barriers and the gate guards are simply a detterent like the guards at retail stores. I saw recently a boy jump over a gate and the guard saw, but did absolutely nothing. A recommendation for Transport NSW would be to invest more in higher gates which would make it much more difficult to jump over, or duck under.

2 notes
·
View notes
Photo

Minecraft Factions: Security Engineering There’s an Overlap?
Minecraft just went up big time in sales. That has provided Youtube with an excuse to push Minecraft videos into my feed again. While the part of my brain that is closest to the 12-year-old me was so very enthused at how much this game has changed and only just cared about watching people play the casual Minecraft... The part of my brain that’s been in a tug of war with the concepts of Security Engineering noticed a lot of interesting things with my childhood sweetheart game.
Let me explain... Minecraft Factions is basically a sub-genre of themed servers on Minecraft, where people go to form factions and instigate in the mindless violence they can’t follow through with in real life. Players Join servers They make or join factions They then either collect resources or loot them from other factions This server requires people to maintain a high ranking in terms of resources and to build strongholds to protect those resources. When I was watching videos of people infiltrating these bases and using all these creative ways of finding weaknesses in seemingly secure defences, I noticed just how many overlaps there were with the concepts I’ve been learning in 6441 What are these similarities you ask?
That’s for my next blog...
2 notes
·
View notes
Text
Security Everywhere #2
Social engineering can be viewed as any form of manipulation. As humans, we use it a lot more than we think. On a weekly basis, I help train a Lion dance class. This class is majority comprised of young children who enjoy messing around more than training. This week we tried something different. After warm ups, I gathered the children, drew an imaginary line on the concrete and told them ‘If you are serious about lion dance then come over this side. If not, its okay. Stay on that side and we can do drills’. The older children crossed first, those who were legitimately serious. Followed by those who were mildly serious. At the end, only the trouble makers were left and they were isolated. They also crossed the line, not wanting to be left behind by the rest of the class. Whether by peer pressure or threat, by crossing that line, the trouble makers had consented to training seriously. In practice, this turned out to be true and the class that week experienced significantly less disruptions. Two things were particularly interesting about this case. Firstly, It was not intended that all students would cross the line. The intention was to train the more dedicated students at a faster pace and to do drill exercises with the trouble makers such that they would not interfere with the rest of the class. Secondly, this tactic was not planned as purposeful manipulation or social engineering. In hindsight however, this could certainly be viewed as that. The point of the post is not to suggest that we should always be suspect of manipulation or that the intentions of social engineering are always malicious. Instead, it is to raise awareness of when we may be using social engineering without realising it and also when we unwittingly being a victim of social engineering.
2 notes
·
View notes
Text
Security Everywhere #6: Educating others
I wrote up a post on password security for my College group and posted in our Facebook group, in order to advice them. Some of the tips are general ones we all know of, but there are some who need to be reminded!
There were a lot of lunchtime/ dinnertime discussions over the topic so I was really happy and glad I had them talking and getting enlightened!
(I have blocked names for security purposes).



1 note
·
View note
Text
UNSW Change Passwords
Richard mentioned how changing passwords are no good because people will run out of good passwords and just use weak passwords for the new ones. It always annoys me that I have to change password every single time. So for last year I used two passwords and alternated between both of them every time they sent me an email. However, this time it did not let me do it.
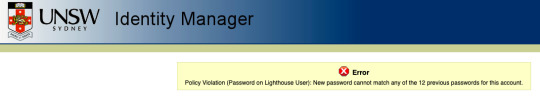
This is very concerning that UNSW stores the previous 12 password hashes (I assume they’re hashes). This means if the system ever gets compromised all the previous 12 password hashes are revealed. There is no point in changing passwords every 6 months if all previous passwords are stored as the security vulnerability still exists.
1 note
·
View note
Photo
This week’s reading on privacy - its so meta :D
1 note
·
View note
Text
Blindly Following Google Maps
Recently in Colorado Google Maps led over 100 users to a “detour” which just ended up leading to a muddy empty field. This shows how much people rely and just blindly trust technology. It makes me consider an attack similar to social engineering where you manipulate a piece of software someone trusts to trick users into giving information. Eg have a false form pop up that looks like it’s from the application being opened and asks the user to change their password by putting in their current and “new” password. This will then supply the attacker with two passwords a user may have used for other things and the user will be non the wiser because they blindly trust that program.
Source: https://www.gizmodo.com.au/2019/06/dozens-of-colorado-drivers-got-stuck-after-blindly-following-google-maps-into-a-mud-pit/
1 note
·
View note
Photo

Stalk mode on.
1 note
·
View note
Text
Watch Your Digital Trail
I saved these articles from a couple days ago because I thought they were pretty cool, but didn’t get time to writeup about them.
Catching Vandals with Wi-Fi
The basic idea behind this story was a bunch of teens were busted vandalising a school because their phones automatically connected to the WiFi. While they were painting racist and homophobic imagery throughout the school, their phones connected to the school’s internet with their own personal credentials. Basically their efforts to try and conceal their identities by covering their faces from the school’s security cameras were completely wasted.
This case is somewhat similar (conceptually) to the Harvard bomb threat that happened back in 2013. Some dude thought he was pretty smart in using ‘Tor’ to post the threat to get out of an exam. However, he failed to realise he was connected to the universities’ internet and was the only person using ‘Tor’. As they were able to trace the threat back to one of the ‘Tor’ servers and suspected a student at Harvard had made the threat, they were able to force a confession from him.
Both these stories definitely highlight the need to consider every aspect of your online identity if you don’t want to be traced. You have to understand that the best way for ‘no information’ to be conferred about you is to ‘blend in’ with the crowd - how close data is to random is what determines information!
Google Listening In
Is anyone honestly surprised by this story? I wrote a blog post about this very fact, a couple weeks ago, from personal anecdotes which I had heard. It seems very obvious to me that the device itself isn’t capable of handling complex human speech interactions and would require an external server! Of course they would be using excerpts from this to try and improve their ‘listening devices’.
I found it funny how they essentially claimed all the data was anonymised - you know, like apart from your voice and everything you say to it? Apparently Google has hit back and said only around 0.2% of recordings get sent for review - don’t worry that’s probably only 2 million people.
The other thing you might not consider is the fact that the NSA probably has roots in all major American tech companies, so really if you do have one of these devices, you essentially have ‘another’ wiretap in your house. (on top of all your other devices of course!)

3 notes
·
View notes
Text
Security Everywhere - 7-Eleven Japan
Recently on the 1st of July, 7-Eleven Japan released a mobile app for their customers, which allowed them to link a credit or debit card to their account, and then present a barcode to the cashier which then automatically charges the cards linked to the account.
However, on July 3rd, 7-Eleven announced that they were closing the app and all accounts associated with it due to a.... you guessed it, a security breach :) 7-Eleven reported that around 900 customers had their accounts compromised and had accumulated around $500,000 in fraudulent charges made by hackers.
So as usual, how did this happen, and how can we prevent future incidents like this from happening.
The flaws:
The app contained a password reset function apparently allowed anyone to request a password reset for other people's accounts, but have the password reset link sent to their email address, instead of the legitimate account owner.
A hacker only needed to know a user's email address, DOB, and phone number. Furthermore, if the user didn't enter their date of birth, the app would use a default of January 1, 2019, making some attacks even easier.
For the future:
I’m just speculating here, but this case seems like one where upper management has pressured their software team to produce an app by a deadline, creating a buggy mess which has compromised the privacy of their customers and resulted in major expenses.
I say this because HOW does an app with a password reset function like that get past the testing phase?? I assume it was released in that state because it was very likely not adequately tested. This hails back to the first week of this course, with the question, “why does engineering work”. One of the conclusions I made was because engineering dictates strict testing, before anything is released.
Its honestly disheartening to see that major corporations not taking appropriate care when it comes to dealing with people’s private information like credit cards and DOB etc. By releasing a poorly designed app, it really shows where management’s priority lies - creating tools to increase customer engagement with no actual care as to how they should be developed.
Hopefully next time major corporations will learn to do rigorous testing for software that they release, especially when people’s sensitive data are involved.
References:
https://www.zdnet.com/article/7-eleven-japanese-customers-lose-500000-due-to-mobile-app-flaw/
2 notes
·
View notes
Text
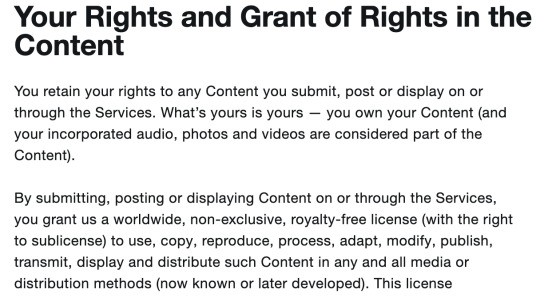
Week 7: Security Everywhere T&Cs
A currently trending application right now is the FaceApp which transforms a selfie editing it to a predicted version of the photo when aged using AI. In the app’s terms and conditions it grants permissions including name, likeness, voice, persona which may be allowed to be used in commercial purposes. This has gained traction due to the wording in their T&Cs, and individuals are concerned as to how their data might be used, it is not a single case, but quite common in many other apps including Facebook and Twitter. It is rare that people read terms and conditions, and with that, the convenience of having able to use Facebook and Twitter is worth the trade of your data and their ability to use it.
Terms of Use: Facebook

Terms of Use: Twitter
2 notes
·
View notes
Text
Deepfakes
In light of the deepfake video posted by the Israeli AI startup, Canny, this highlights what an amazing and scary time we are living in. If you haven’t seen, there was a video posted showing Mark Zuckerberg apparently announcing that Facebook would become more transparent with its ads - https://www.instagram.com/p/ByaVigGFP2U/
This demonstrates how far AI has come, where it can produce photorealistic videos of humans which can be manipulated into saying things they never said. Upon watching this myself, I could hardly tell that the video was fake, apart from the fact that the things Zuckerberg was saying were things he would never say. The video reminds us of the importance of always being skeptical and critical of “evidence”, even if it is photo or video evidence. Things to always check when reading these sources is the source, and cross-checking the story with other sources. In this case, the source was an AI startup, so it was clearly fake, but in addition, if there are no other video recordings of the video online from other reputable source, then it is also likely to be a fake story.
https://www.technologyreview.com/f/613690/facebook-deepfake-zuckerberg-instagram-social-media-election-video/

2 notes
·
View notes
Photo

Jake Paul: Infiltrating the White House
You heard me...
“YouTuber Sensation Jake Paul done goofed up real good this time...”
In one of his most recent videos, Jake Paul posted a video of himself hiding in the Presidential Whitehouse in Washington. The use of the word “Infiltrated” might have been a stretch but hey, this is how you grab attention on the internet. It’s called Click baiting...
Here’s some context,
Jake Paul for some reason was invited to the Whitehouse. He was authenticated and authorised to go inside as a friendly package.
Jake Paul for some reason decided to slip away from the main event and went into the bathroom. Since he’s already inside there aren’t many people checking for unusual activity in that premise. He’s decided to turn menacing after bypassing the big security defences.
Jake Paul for some reason decides to stay in the bathroom overnight. No one checks for him in there, since it’s only a bathroom and no one even notices him missing. Menacing package decides to take over unimportant asset. Menacing package doesn’t throw off alarms.
He then walked out at 3AM. No harm done. No items stolen. Miraculous that he’s still alive.
What a stunt. Taught me a lot about the Whitehouse’s security.
It’s a one time door... Once you’re in... You’re in...
I’m only kidding now XD
1 note
·
View note