#tld afflictions
Explore tagged Tumblr posts
Text
Psychological Afflictions because games keep getting them wrong and I wanted to take a shot at them




Bit more detailed info here: vvv
Mental Health Risk:
- it would be a hidden statistic like Vitamin C or Cabin Fever. Called Resilience or whatever
- reduces slowly over time but there are factors that impact it negatively or positively. Like being near dead bodies and getting attacked (negative) and stayin’ alive or reaching milestones (positive)
- there are specific factors that either make their respective affliction worse or help cure them by increasing resilience
- when it reaches 20% remaining you get the risk affliction. At 0% one of the three psychological afflictions manifests, depending on player history/actions
Depression:
- usually other games just apply a grayscale filter and say “you sad :(“ and call it a day
- this ones theme is Progress Hindered. You can sleep or you sleep too long and also your skill progress gets stunted and reset a bit because screw you.
- 50% chance to get either Insomnia or Hypersomnia. The latter makes the survivor sleep longer by 1-5 hours but doesn’t restore fatigue for those extra hours
- “something or someone to hold onto” I made these with a multiplayer setting in mind. Being social is better to mental health than being isolated
Anxiety:
- it’s basically the risk affliction but with light effects. Supposed to be the easiest to manage
- it has a bar that increases. The higher it gets the higher the frequency of effects.
- they are more to keep the player on edge than affecting the survivor directly. YOU are affected as well, don’t just ignore this. Was that twig snap just a sound or a wolf nearby. Who knows
- also another effect I forgot to put there: Fake suffocation risk. All the visual effects for the suffocation risk affliction including the UI info but as soon as the counter reaches 0 nothing happens. Get trolled lol
PTSD:
- main theme: past trauma (obviously)
- gives Insomnia and problems with struggles
- big thing is Flashbacks: they happen randomly or when fitting triggers are present (let’s use a wolf attack and a Sprain/Break affliction as an example). There are Audio and Visual aspects
- Audio: Sounds Echo or repeat. A wolf sound is heard and fake sounds continue for a while after that. Sometimes there isn’t a wolf anywhere nearby anymore. Or sounds get replaced like a broken stick sound gets replaced with a broken bone sound
- Visual: Usually accompany the audio. It’s a subtle but noticeable overlay at lower opacity. Like a wolf at 50% opacity jumping the survivor, charging or standing (there. MENACINGLY). Or a fake affliction notification but you didn’t actually get the affliction
Ya I think that’s every important thing. Thanks for reading until here
#my art#the long dark art#the long dark#tld afflictions#psychological afflictions#this is a VERY generalised view on these mental illnesses so obvs not 100% accurate#had to simplify them a bit so that they would fit into a game without being annoying/detrimental to deal with#again did this just for fun#and to see if I could#also designing the icons was nice#sorry that the commas look like periods. That font was the closest but the commas suck
64 notes
·
View notes
Text
The custom difficulty settings I use for TLD (Interloper weather/afflictions, Stalker loot, Pilgrim wildlife—I call it “Jackalope mode”) really changes the experience of wildlife struggles. I feel like it makes me appreciate them more?
I used to spend my unskippable first-person bear-mauling cutscenes complaining (WTF Mr. Bear, all I wanted was a STICK on the GROUND like 200 feet away from you! Wherefore this violence??) but now, on the rare occasion that a Moose is turning my ribs into applesauce, I must concede that he has the right to do so.

sir you are absolutely correct. I am the asshole here. Please enact whatever justice you deem necessary.
#the long dark#moose#haven’t met a cougar yet but they have appeared in my game#excited and scared to be pet by the kitty
6 notes
·
View notes
Text
Been thinking of a Isatxskyrim thing W' My modded Followers... Like ok so like I mean, Ofc Xelzaz would be the Researcher [i mean duh] Either TLD or, more likely Remiel would be The HouseMaiden [Tld because dragonborn, eat sou l yum. Remiel Because Aroace and... um Feels similar to Mirabelle in some way????] Redcap as the kid [both are goblins-likes and smart... Yeah sure Redcap can drink + isnt a goblin [riekling but sh sh sh fanon murders detail sh sh sh, ] (Xelzaz is on snack duty because i am doubtful Redcap can cook all that great.) {redcap is still on Tonic/Potion Duty though!} TLD is siffrin no contest [IM the last dragon born and i dont want any of my Friends Party members Family members actors Allies... to leave!!!! Most likely to get stuck in a self afflicted Timeloop] Who knows who the fighter is, Teehee. [... Kaidan is one option but i have no idea how Anyone would react.] The king is the final boss of any of the expansions [Alduin, The vampire, ...The other dragonborn.... Yeah Miraak is the most similar to the king... But Alduin is dragon so is big and powerful, More likely to die against than just some guy.]
#Skyrim#Tes#the elder scrolls#elder scrolls#Xelzaz#Xelzaz Skyrim#Remiel#Remiel skyrim#Redcap#Redcap Skyrim#Tld skyrim#tld#My Dragonborn is a male Argonian battle Cleric#but like a... Daggerfall Argonian? Which is more draconic in appearance?#so is like 200-300 years old?#y'know#For the funsies#Teehee.#Replacement#Isat character replacement au#Teeehee#We put Gunieas through hell#'gunieas'#[Is actually Eshuary but shshshsh They cannot know#they cannot ever know you are not normal or correct or who you said you were.]#[You have to keep playing up this facade#You can let them ever know#They'll hate you they'll hate you they'll hate you!!!]#hehehe :]#modded followers
1 note
·
View note
Text
I like the idea but I’m worried it might turn into something like Amnesia or one of those other run-and-hide-only type horror games sanity bar systems. TBH I can’t stand those types of games lol.
Plus it would be nice but the story mode is giving good hints through dialogue on how things are effecting Will and Astrid (again I love Mark Meer but his lines deliver a bit flat compared to Jennifer Hale once again I just had to slip it in there sorry off topic), and it also gives good dialogue indicating that both of them aren’t seasoned survival experts and that they are not okay with how things are turning out.
BUT the sandbox mode survivors, without the added story dialogue, seem to be hardened, prepared outdoors people. Though mental health and mental conditioning are incredibly important in survival situations, especially long term ones, personally it would feel out of place to me in sandbox.
TLD sandbox is good at giving you a pure survival experience that’s close enough to real life to feel amazing and potent but also removed enough so that it doesn’t have to delve into the more nuanced things that afflict survivors and survivalists in those situations. Mental health and conditioning can be effected by hundreds of factors, many of which are from well before any survival situation takes place.
That being the case, if they ever did introduce it, I would think it very interesting if they had a randomized, hidden bit of script that coded for previous job, lifestyle, if they’ve had military or survival training, etc, and each time you started a new sandbox these would be shuffled up again. This would effect how mentally conditioned you are, how you deal with trauma of the crash, possible survivors guilt, if the person is comfortable around firearms and with hunting, as well as if the character is effected by the loneliness, if they expect rescue or not, if they are more driven to hike out and try and find rescue (increased risk of cabin fever/restless condition when in a single map too long possibly), are they okay with taking available food found in houses that obviously aren’t theirs, etc.
See where it can get complicated really quick xD but that’s probably my brain overanalysing. You want a mood bar, which is much much simpler than what my brain jumped to, and it would be a good addition!
Sorry for hijacking your post again!!
You know what would be cool?
A mood bar.
If we had a mood, imagine what it could do. Like, you wake up and you just feel aweful. You didn't sleep well, maybe you had a nightmare and you wake up and everything is shit. You are lonely and depressed and it results in you being encumbered faster. And what do you do? Try to have fun. Eat chocolate. Watch the sunrise from a safe vantage point. Maybe play cards or a board game you found, read a book.
Your moods gets worse when you get attacked or when you kill an animal (at first, the character should get used to it pretty fast) or when your clothes are wet and you're freezing. Your mood should get better when you eat, rest, warm up or finish crafting something. A sense of accomplishment, you know.
Am I trying to turn The Long Dark into the Sims?

#tld#the long dark#hinterland studio inc#indie games#survival#i always skimmed over the mental stuff when reading up on survival#i guess a lot stuck better than i thought#that and the ptsd and survivors guilt research lol#sorry i hijacked the post snoshep!
50 notes
·
View notes
Text
Original Post from Security Affairs Author: Pierluigi Paganini
Cybaze-Yoroi ZLab analyze a new GoLangbotnet named GoBrut, the investigation allowed to discover that the bot supports a lot more features
Introduction
Malware written in Go programming language has roots almost a decade ago, few years after its first public release back in 2009: starting from InfoStealer samples discovered since 2012 and abused in cyber-criminal campaigns, to modern cyber arsenal like the Sofacy one. Times ago it was considered an exotic way to code a malware, nowadays it became something more common most of the CSIRTs encountered at least once in their lifetime.
In the last month, a particular sample circulated within InfoSec community: it was written in GoLang and showed an interesting behavior, along with unusual binary patterns, for this reason, Cybaze-Yoroi ZLab decided to deepen the investigation.
Technical Analysis
GoLang programs compilation generates binaries embedding all the required dependencies, it is one of the principal advantages of this programming language because it avoids the need of installed runtimes within the machine, like the Java Runtime or specific .NET version, simplifying the multi-platform support of the Go applications. One of the main characteristic of the Go compiled binaries is the inclusion of the “Go build ID” field into the PE header.
Hash 94e119d88ff59d33d3c6fe6c346eba274d5fcc971771ec94b86657a0c2217a2d Threat GoBrut SSDeep 49152:6+UqQHrw3ygz94d8zgJqatzrYY2o6Kd3xlIUyCo061UlMX:qrwnz6e8l9rUo6KdiJX
The analyzed samples contains this particular field confirming the malware has been written in Go language, despite the lack of signature match running PE identification tools.
Figure 1: Go Build ID signature
Navigating the assembly we were able to isolate some interesting chunks of code revealing the malicious capabilities of the sample. We detected an inner routine granting the infection persistence after the system reboot, by running the following batch utility script to install a self-copy into the user startup folder (“AutorunDropper” function).
@echo off if not exist “C:/Users/admin/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Startupsvchostphb.exe” copy /Y “C:UsersadminAppDataRoamingMicrosoftWindowsStart MenuProgramsStartupsvchostphb.exe” “C:/Users/admin/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Startup/svchostphb.exe”
Also, an interesting reference have been found within the RDATA section of this PE binary: a reference to a so called “TryLogin” and “StartBrut” routine, suggesting some kind of offensive capabilities, subsequently described in “The BruteForce Module” section.
Figure 2: References to source code functions in RDATA section
Another interesting finding during the static analysis of the sample is a specific url value, hardcoded into the binary itself. The remote destination points an netherland Provider, ISPIRIA Networks Ltd, hosting the command and control server of the botnet.
Figure 3: Command and Control communication routine
Dynamically running the malware, it starts a series of http requests aimed to register the bot to the discovered server. The GET request parameters contains the “phpadmin” value in a quite interesting “worker” field, clear reference of the notorious “PhpMyAdmin” database administration tool, widely deployed across the internet and too many times unnecessarily exposed to the internet.
Figure 4: Bot’s registration on the C2
After the check-in, the bot queries a JSON object resembling a sort of bag of tasks, where the C2 instructs it to try a huge amount of logins on the retrieved web pages.
Figure 5: Response of C2 with the JSON file containing the targets
The BruteForce Module
The core of the bot is the bruteforce module: it has the task to try to login into target services using credentials retrieved from the C2 server, as described in the previous section.
Figure 6: BruteForce module function flow
The routine named “StartBrut” has the purpose to prepare the credentials retrieved from the C2, then subroutine “TryLogin” connects to the target host, tries to authenticate using provided credentials and waits for the server response. During these days the botnet was running a campaign leveraging its “phpadmin” module, resulting in attacks to thousand of PhpMyAdmin installation all over the internet.
Figure 7: Login attempts of the “phpadmin” module
At this point, we decided to collect the list of targets under the botnet attack and, at time of writing, we identified 40k unique destinations potentially under attack. The distribution of the Top Level Domains shows half of the targets are the “.com” and “.org” ones, surprisingly followed the by Russian TLD, and other Eastern Europe targets. Central and Southern Europe seems are targeted too but with in a lower portion, currently.
Figure 8 : Distribution of TLD
The “.it” domains in the botnet targets list are about 400, including professional forum such as “avvocati[.it”, e-commerce portals, company websites and also banks such as “bancamacerata[.it”. A wide spectrum of organization, the full list is available in the section “Italian Targets”.
Investigating the Botnet
Digging further into the investigations, we found out this new GoLang bot supports a lot more features, not only for “PhpMyAdmin” one. In fact, we discovered the bot supports 23 functionalities able to target a range of technologies from administrative protocols to CMSes, for instance it is capable to attack SSH logins, FTP sites, exposed MySql service and the two most used CMSes, WordPress and Joomla. Here the list of discovered functionalities:
bitrixBrt
bitrixChk
cp_b
cp_chk
drupalBrt
drupalChk
ftp_b
ftpChk
joomlaBrt
joomlaChk
magentoBrt
magentoChk
mysql_b
OCartBrt
OCartChk
php_b
php_chk
postgres_b
ssh_b
whm_b
whm_chk
wpBrt
wpChk
The attack campaigns are pretty dynamic and may change quickly over the time, further analysis pointet to a specific command and control API where the botnet master enables or disables running offensive operation through the “/project/active” server location. Thus, the bots is instructed of which are the current active campaigns and technologies to be targeted.
In the end, a recent article by Jérôme Segura reports a piece of the puzzle to complete the plot of this new “GoBot” threat, describing how the bot has been linked to a JavaScript skimmer installation campaign afflicted several web portals in the wild. The piece of javascript code embedded after the abusive access was able to steal sensitive information such as credentials and credit card numbers (PAN), to every user visiting the compromised site. This attack techniques is extremely dangerous and lead to massive data leak for organizations, as observed back in 2018, when the MageCart group hacked the British Airways infrastructure to install JavaScript skimmers.
Conclusion
The usage of emergent, uncommon, languages and technologies for malware writing is a weapon can be leverage by the attackers to defeat traditional anti-virus based security controls: compilation patterns and artifacts may evade static signature and general heuristics detection. For this reason the security perimeter must include appropriate analysis capabilities to detect and handle this kind of threats.
Also, this new “GoBrut” botnet provides a precious insight of the kind of threat insecure logins and unnecessary exposure are subject to. Showing how cyber-crime actors are able to run wide international criminal operations aimed to opportunistically penetrate organizations, to abuse its infrastructure and steal users logins and sensitive data.
Technical details, including IoCs and Yara Rules, are available in the analysis published in the Yoroi blog.
https://blog.yoroi.company/research/gobrut-a-new-golang-botnet/
window._mNHandle = window._mNHandle || {}; window._mNHandle.queue = window._mNHandle.queue || []; medianet_versionId = "3121199";
try { window._mNHandle.queue.push(function () { window._mNDetails.loadTag("762221962", "300x250", "762221962"); }); } catch (error) {}
Pierluigi Paganini
(SecurityAffairs – GoBrut, GoLang)
The post Cybaze-Yoroi ZLab analyze GoBrut: A new GoLang Botnet appeared first on Security Affairs.
Go to Source Author: Pierluigi Paganini Cybaze-Yoroi ZLab analyze GoBrut: A new GoLang Botnet Original Post from Security Affairs Author: Pierluigi Paganini Cybaze-Yoroi ZLab analyze a new GoLangbotnet named GoBrut, the investigation allowed to discover that the bot supports a lot more features…
0 notes
Text

It’s that time of month
@adhdchaosbean had the idea and I made this in May. Forgot to post it here so now you have it
(Adding some more info vvv)
Affects female survivors. Or yknow individuals with ovaries.
Effects:
Increased Fatigue loss, Bleeding (Wow), Cramps and/or Headache
This form of Bleeding is not lethal. The main thing it does is give the survivor a scent value that doesn’t go away. It can only be halved by treating it with bandages. One every 24 hours or something.
The survivor can get Cramps and/or headaches/Migraines. Both give blurred vision and distorted sounds (like pain affliction) while Cramps would also cause the screen to shake/stumble when walking (like sprained ankle). Can be normally treated with Pain relevant items.
#my art#the long dark#the long dark art#tld afflictions#menstruation#forgor to post here but I guess it’s fitting it’s here now a month later
11 notes
·
View notes
Text

What if The Long Dark… but Werewolf
(Original idea by Qille on YouTube)
Down here is some more stuff vvv
This started as an affliction but now it resembles more of an idea for a challenge mode like Darkwalker (but longer or endless. Because otherwise that would be boring).
The survivors “goal” is to pay attention to the moon phases to take the necessary precautions in time and not turn into a werewolf. Or they can if they want but they get a bunch of debuffs like Intestinal Parasites because the werewolf definitely ate some things that the survivor shouldn’t.
The survivor can prevent/control the transformation with two methods:
Safehouse Barricading:
Like the “clear junk” option but it takes time and resources to barricade windows, doors, etc. This doesn’t prevent the transformation but prevents the werewolf from leaving a the safehouse. There could be a chance that the barricades break and the werewolf escapes but doesn’t get too far. (Who let the dogs out?)
Wolfsbane:
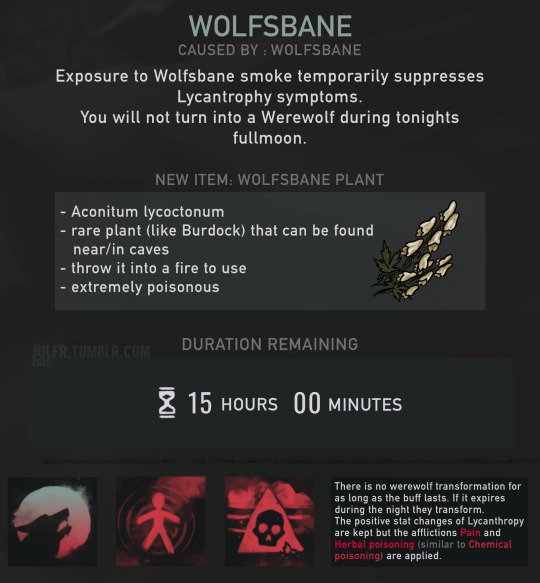
A plant that can be burned and gives the survivor an effect that as long as it lasts prevents the transformation. But it also applied the Pain and Herbal Poisoning afflictions.
Because Wolfsbane is really really poisonous. I originally wanted to make it into a potion/tea but while that would prevent the transformation it would do that by killing the survivor. Task failed successfully I guess. So smoke that’s still a bit poisonous but not by that much it is.
#my art#the long dark#the long dark art#tld afflictions#werewolf#lycanthropy#i read various pages about Wolfsbane plants for this
17 notes
·
View notes