#top binary software 2017
Explore tagged Tumblr posts
Link
#top binary software 2017#best binary options best binary options software best binary options software in 2017
1 note
·
View note
Text

Hey it’s Robin again, I’m a 24-year-old non-binary (they/them & she/her) software engineer from England, if you wnat to know a little bit more about me I said some stuff here and you can always feel free to hit me up on here or on discord!
have you seen SURENDRA EGILLSSON around town? We’re trying to make sure they’re still in town, especially with everything that’s been happening lately. HE is a TWENTY FIVE year old CIS MAN. currently residing in Perfection Valley, but they’re originally from LAS VEGAS. they are best known for being a RADIO HOST, and i hear they’re pretty CREATIVE yet also PARANOID at times; i hope they continue to survive.
Full Name: Surendra Freyr Navin Egillsson Nickname/Alias: Ren Meaning: Means “lord of gods” from Sanskrit सुर (sura) meaning “god” combined with the name of the Hindu god Indra, used here to mean “lord”. Gender: Cis Male Pronouns: He/Him Orientation: Pansexual & Panromantic Ethnicity: Indian & Icelandic Age: 25 Birthday: 2nd March 1994 Birthplace: Las Vegas, Nevada Occupation: Local Radio Host Faceclaim: Avan Jogia
Surendra Freyr Navin Egillsson (सुरेन्द्र फ्रे नवीन ईगलसन; born 2nd March 1994) is the youngest of seven children born to Egill Tómasson (an Icelandic sociology professor from Húsavík, Iceland) and Kavita Sharma (an American physics reseachers of Indian decent, born in San Francisco). He was raised in Las Vegas, where both of his parents worked to try to make it in their respective fields. He had a happy childhood for the most part, he liked to imagine he was a Viking explorer whem he was a kid “like his father’s family”, made slightly amusing by the fact Surendra’s farther looked more like a kindly fisherman than he did a warrior.
He grew up with 6 elder siblings: three brothers, two sisters, and a non-binary sibling. Both his parents worked long hours, which his elder brother Páll picked up the slack for. Before then Ren was told that his siblings had a nanny called Brigitte, who still visited the family on occasion, having grown close to his elder siblings. When he was around 4 Ren was diagnosed with a mild form of autism, which has affected his life in a lot of ways, making him feel strange and other from the children in his class, who tended to mock him for his “weird” behaviour.
When Surendra was 7, however, his parents split, having simply “grown apart”. This meant that Ren found himself frequently bounced between living in his mother’s new house and the house he’d always grown up with with his father. Though he still loved both of his parents it was hard for him to understand why they didn’t love each other any more. The change was especially hard for him to understand, given his autism. One of the traits Ren presented was an inability to cope with change.
On top of this, it distressed Ren as, much as he didn’t want to see less of either one of them, he was jarred by the constant hopping back and fourth. It was decided several months down the line that he would live with his father and spend the summer holidays with his mother, with visits from the other parent throughout. In High School the bullying continued, but something in Ren managed to get to the point where he decided that if he had to be the “weird” kid, he was going to make it work.
Though it was absolutely a case of faking it until he made it, made possible only with the support of his father, and eventually he did. Eventually he got to a point, at around 15, where he just didn’t mind what people thought of him (not an easy thing to accomplish). This allowed him to gain a bit of charisma. It was at this point in his life that Ren’s favourite special interest came to stay: true crime and conspiracy theories. Though, by no means, does he believe all of them, he certainly seems to believe in a lot of them. It was also around this time that Ren came out to his family, the response was mostly positive.
Upon graduating high-school, Surendra attended university in San Fransisco, where he studied Chemistry, among other things, though he later changed majors to media production with a minor in music. It was during this point of his life, when he was around 18, he met Isaac Zapatero with whom he quite instantly hit it off. Isaac was 19 and from a well-to-do family from Phoenix, and thussly had some amount or arrogance around him for this reason, but other than this, Ren loved everything about Isaac. When they’d both graduated from college, and when the government would let them, In the July of 2015, Surendra married Isaac.
The newlyweds moved to Perfection Valley, where Isaac had gotten a surgical residency at a local Hospital. While Surendra hadn’t originally seen himself moving to such a small town, Ren fell for Perfection Valley in some ways, because it just seemed to be the kind of place just weird enough to handle Surendra Egilsson and he had seen a posting saying that they needed a new radio host, it felt like the perfect job for him, and while he wasn’t sure he could get it, he had a hunch.
Their marriage worked well for a while, and the pair had a son called Hari Zapatero, via a surrogate, in 2017. Surendra had gotten the job and, despite his “quirky” talking points, his charm and personality has managed to gain him gain quite the following in the town. While Isaac had completed his residency, his hours were still long and it was hard for the couple to cope with, this eventually led to marital breakdown and divorce in mid-2018, though Surendra isn't quite over it there's few he'll admit this to.
While this was happening, Ren's sister, Hildur Egillsson, died in a car accident while on her way home from work. The tragedy shook the family to the core, perhaps none more strongly than Surendra's father, Egill whose mental health fell through the floor to the point he needed to retire from his job as a professor, as he could no longer handle the stress. Ren offered to have him move in with him, as he could use the company himself and he hated the idea of them both being alone in their grief. To bring in a little bit of money, and to keep himself busy, Ren's father plays folk music.
Ren's current situation is living with his son and his father, looking after both in some ways, though also enjoying his occupation of theorising about everyone's imminent demise and who, or what, might be responsible for it or trying to cover it up.
2 notes
·
View notes
Text
2017 MID-EXAM REFLECTION
After I invited my friends to discuss in the past few weeks, I summed up the content of our discussion. There is still a question here. I still can’t get the answer until now, I hope some friends can tell me.
I think these answers can help people review knowledge very well.
Enjoy it :-)
= COMP6441 Midsemester Exam : 2017s1 = == Total number of marks: 50 == == Total duration: 60 minutes == There are two marks for following the examination instructions. You will be supplied working / scribble paper. You must bring your own pens/pencils. You must bring photo ID. Working is not marked, only your final answer. Your answers can be submitted by pressing save on this application. Press Save often to back up your working so far. You may submit your solutions as many times as you like. The last submission ONLY will be marked. Write your name on the top of each sheet of rough working paper you use, this will not be marked, and write your answers in the computer files as directed in the exam instructions. You must hand in ALL writing paper at the end of the exam. Once the exam has commenced you may not leave the exam. You may only use the viewer and GUI calculator. Other programmes including scripting or interpreted languages may not be used. We are logging all activity and use of other software etc will result in 0 fail. If you are unsure ask the supervisor. The use of Malachite or social engineering is prohibited. Strict exam conditions apply, including that you may not attempt to communicate with any other person, or access other computers or external data or any internet resources. If you do not follow these instructions you will get zero marks for the exam and a possible charge of academic misconduct. Phones must be turned off and not visible, either left outside the room in your bag or sealed in an opaque bag placed under your seat. If more than one answer to a multiple choice question seems correct then select the answer you think best answers the question. V2.2
==== Part A ==== This part is worth 18 marks and consists of 6 three mark questions. Answer all questions. Spend about 3 minutes on each.
=== Question 0 === (3 Marks)
What is the most important property for a cryptographic hash function to have to make it as resistant as possible to birthday attacks?
.[A] Preimage resistance .[B] Collision resistance .[C] Confidentiality .[D] Symmetry .[E] Second-preimage resistance .[F] Non-determinism birthday attack is a way to find a collision between different things The answer should be B
=== Question 1 === (3 Marks)
You are a developer of opensource fake-news software called "The trumpet shall sound", or "Trumpet" for short. You wish to use a cryptographic algorithm to generate a 64 character "digital fingerprint" of the "Trumpet" binary, which you will display on your web site so that people can check that they have downloaded a legitimate and unaltered copy of "Trumpet".
What is the most important property for this cryptographic fingerprint algorithm to have?
.[A] Preimage resistance .[B] Collision resistance .[C] Confidentiality .[D] Symmetry .[E] Second-preimage resistance .[F] Non-determinism
We put the Trump and Fingerprint(Trump) on our website We need to prevent Attacker to make a fake message fakeTrump which has a same Fingerprint(Trump). The public can be mislead by checking Fingerprint. This is called Second-preimage attack, the website should avoid this. The answer should be E.
=== Question 2 === (3 Marks)
A MAC is designed to provide .[A] Neither Integrity nor Authentication .[B] Authentication but not Integrity .[C] Integrity but not Authentication .[D] Integrity and Authentication .[E] A Very Fashionable Device Mac both provide INTEGRITY AND AUTHENTICATION THE ANSWER SHOULD BE D
=== Question 3 === (3 Marks)
You have a password file of 1,000 password hashes. Assuming that 50% of the passwords used were weak passwords which can be found in a dictionary of 1,000,000 common passwords, and that hashing a password takes 12 bits of work on average, roughly how many bits of work would it take to discover all these 500 or so weak passwords?
Note: only enter DIGITS in your answer (or else the automarker will mark it wrong.) _____ THE BEST SITUATION IS THAT DISCOVER 500 WEAK PASSWORD IN FIRST 500 COMMON PASSWORDS DICTIONARY, THE WOREST CASE IS THAT DISCOVER 500 WEAK PASSWORD IN LAST 500 COMMON DICTIONARY. ON AVERATE THE ATTACKER WILL FIND THE PASSWORD IN 500,000 STEP WHICH NEEDS 2^19. HASH EVERY PASSWORD NEED 12BITS TOTAL WORK SHOULD BE 2^19 * 2^12 = 2^31 or 2^32 (no half)
=== Question 4 === (3 Marks)
As for Question 3 but now assume that each password is appended to a different 32 bit number (a salt) before the hash was computed, and that the salt number for each password hash is stored, unencrypted, next to the hash in the password file.
Roughly how many bits of work would it take to discover all the 500 or so weak passwords in this case?
Note: only enter DIGITS in your answer (or else the automarker will mark it wrong.)
THE PASSWORD IS APPEND SALT THEN HASH THEM, THERE ARE 1000 PASSWORD AND 1000 SALT VALUE , ALTHOUGH A SALT IS 32BITS LONG. SO FOR EVERY PASSWORD, THEY MAY TRY 500 EXTRA TIMES FOR SALT ON AVERAGE WHICH IS 2^9 THE TOTAL WORK IS 2^31 * 2 ^ 9 = 2 ^ 40 BITS or 2^42(no half)
=== Question 5 === (3 Marks)
Below are six lists of expenses submitted by six politicians. Sadly 3 of the politicians are dishonest and submitted made-up fake expense claims, not costs that they really incurred. :(
{{{ Albus Bert Carl Dave Egon Fred
269 6,296 543 1,137 503 206
1,428 3,217 220 638 4,195 74
3,840 520 3,080 696 5,780 257
2,163 456 5,070 543 7,774 350
165 111 108 113 986 50
2,701 2,176 8,078 145 884 426
339 476 7,963 313 6,530 3,226
64 2,607 68 236 50 108
942 824 2,457 701 9,801 94
17 10 7,952 422 5,717 17
423 112 5,332 5,723 29 158
37 13 5,705 964 3,933 609
723 9,048 8,851 750 6,122 5,769
172 295 99 7,905 91 19
498 165 6,424 9,953 89 275
5,583 3,008 48 491 19 898
56 1,396 8,339 2,675 758 506
158 19 1,945 8,212 427 3,467
1,244 238 916 897 8,503 9,217
2,445 51 3,618 392 3,617 26
866 921 4,219 941 338 1,349
}}}
Correctly identify the status of each politician.
==== 5.1 Albus ==== .[A] Honest .[B] Dishonest
==== 5.2 Bert ==== .[A] Honest .[B] Dishonest
==== 5.3 Carl ==== .[A] Honest .[B] Dishonest
==== 5.4 Dave ==== .[A] Honest .[B] Dishonest
==== 5.5 Egon ==== .[A] Honest .[B] Dishonest
==== 5.6 Fred ==== .[A] Honest .[B] Dishonest SORRY I DON’T KNOW THIS ANSWER EVEN AFTER THE DISCUSSION WITH MY THREE FRIENDS.
==== Part B ==== This part is worth 10 marks and consists of 1 question. Spend about 10 minutes on it.
=== Question 6 === (10 Marks)
What is the 5th word in the plaintext for the ciphertext below?
{{{ HHPET IAESR DTEHN SRAKA UASMI UEOYR CNWOK FNERA TRONE TNYLO
SOENO OHDAS RYUSW DONUR BNSGI STLAU HTTOO DSAHE EWSYO SRTEC
IFHWO EHNOC TIHGM AENUB EAERW DEYRV EYHTA OUGNS WSODE ROEVN
HLTLA ESSEE SRTEC ONSDA YVREE SNIEO ENHTI IAKRD WOENN AYROA
EOHTN OIYFR SAERU TNABU IIGNH RAAPN IFROK NSATN TEUBC OODUY
NOKTN AWHTO CAOLT AECDK TIENB RSUBI IEFDI ETFYF NTEBE YAHTE
LUBRO TNEKA YHNET EURAO ENHTI EAKRD HETNV YUHGO EURAO COATN
LULAT HITNY KDRAE
}}} FIRST WE NEED TO OBSERVE THE CYPHER MODE, SUBSTITUATION OR TRANSPORTATION? FOR SUBSTITUTION AND TRANSPORTATION WE CAN CALCULATE THE FREQUENCY OF THE WORD AND GUESS THE RIGHT ANSWER. LET’S ASSUME THE TESTER JUST CHANGE THE ORDER OF THE WORD. HHPET THE MOST COMMON WORD START IS THE, WE MOVE THE WORD THEN LEFT THE HP/PH. WE KNOW THAT PH IS THE MOST COMMON PATTERN IN AN ENGLISH WORD. THEN WE CAN GUESS THE MAP ORDER. HHPET TO THEPH. H TO LAST ONE, E TO THIRD ONE P TO FOURTH ONE. ACCORDING THIS MODE, WE CAN GET THE FOLLOWING WORD
THEPHRASEINTHEDARKASIAMSUREYOUKNOWCANREFERNOTONLYTOONESSHADOWYSURROUNDINGSBUTALSOTOTHESHADOWYSECRETSOFWHICHONEMIGHTBEUNAWAREEVERYDAYTHESUNGOESDOWNOVERALLTHESESECRETSANDSOEVERYONEISINTHEDARKINONEWAYORANOTHERIFYOUARESUNBATHINGINAPARKFORINSTANCEBUTYOUDONOTKNOWTHATALOCKEDCABINETISBURIEDFIFTYFEETBENEATHYOURBLANKETTHENYOUAREINTHEDARKEVENTHOUGHYOUARENOTACTUALLYINTHEDARK THE FIFTH WORD IS DARK
(==== Part C ==== This part is worth 20 Marks and consists of 1 question. Spend about 20 minutes on it.
=== Question 7 === (20 Marks)
Suppose we convert letters and other characters into numbers in the range 1..54 using the following table and then separately encipher each of these numbers using RSA with a public encryption key of 23 and a modulus of 55.
{{{ 1 < 21 L 41 4
2 > 22 M 42 5
3 ? 23 N 43 6
4 / 24 O 44 7
5 : 25 P 45 8
6 ; 26 Q 46 9
7 “ 27 R 47 (
8 ' 28 S 48 )
9 @ 29 T 49 *
10 A 30 U 50 +
11 B 31 V 51 ,
12 C 32 W 52 -
13 D 33 X 53 .
14 E 34 Y 54 /
15 F 35 Z
16 G 36 SPACE
17 H 37 0
18 I 38 1
19 J 39 2
20 K 40 3
}}}
For example the plaintext ":)" would be converted into 5,48, and then each of these numbers would be individually encrypted using RSA to produce the cipertext 15,42.
The remainder of this question has been encrypted using RSA with an encryption key of 23 and a modulus of 55.
{{{ 24,18,49,16,48,49,33,10, 2,12,
52,49,48,16,19,20,16,24,18, 2,
7,16,31,50,49, 7,24, 2,19,12,
16,18,10, 7,16,11,49,49,12,16,
49,12,23,48,34, 5,24,49,52,16,
50, 7, 2,12,26,16,48, 7,10,16,
43, 2,24,18,16,10,12,16,49,12,
23,48,34, 5,24, 2,19,12,16,25,
49,34,16,19,20,16,29,35,16,10,
12,52,16,10,16,33,19,52,50,21,
50, 7,16,19,20,16, 3, 3,47,16,
16,24,18,49,16,10,12, 7,43,49,
48,16,23,19,52,49,43,19,48,52,
16, 2, 7,16,53,53,53,53,53,53,
53,53.
}}}
What is the answer codeword? FOR THIS QUESTION, I HAVE NO IDEA AT FIRST, BUT I SPEND SOME TIME TO WRITE A LITTLE PROGRAM THEN I GET THE ANSWER.
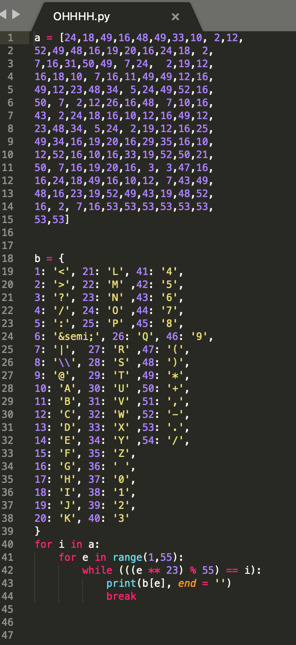
Did you see that? Code is 00000000 But in the exam, we are not allowed to use the python
There is a simple way, What is the answer codeword? The question tells us to find a “codeword” Then codeword must appear in the ciphertext We just calculate the beginning of the first bytes of codeword number and match it to the ciphertext. The code must be following the codeword. It’s 53 53 53 …. 53 then we map it to 0, it needs lower bits of work.
2 notes
·
View notes
Text
The Bitcoin Code Review
The Bitcoin Code Software Review Is The Bitcoin Code Scam System Or Legit? What’s The Bitcoin Code System About? Read Now My Experience with The Bitcoin Code App in My Real The Bitcoin Code Review Before Register in It
The Bitcoin Code App By Steve McKay is a Top Rated Binary Options Trading Signal tool that will trade on Binary Options Trading markets for TheBitcoinCode.com users. The Bitcoin Code system is 100% web-based Binary Trading App & work in automated way. No special knowledge required. No installation required. All The Bitcoin Code Binary Options trading operations are executed automatically without human interference & The Bitcoin Code setup is takes less than Less Than 60 seconds.

The The Bitcoin Code App is a unique tool that automatically taps into a glitch in the worldwide trading markets to make each of its users over $1 million every single month!
Update : (22 July 2017) – Steve McKay The Bitcoin Code is performing exceptionally well. Many The Bitcoin Code traders are reporting positive results with an average ITM Rate of over 89%.
The The Bitcoin Code App team was first established over 5 years ago in 2011 By Steve McKay . Within a few years The The Bitcoin Code system had expanded and was consistently making over $27,439 each day for each of its members. Sign up now & you can make cash today with The Bitcoin Code Binary Trading System!
The Bitcoin Code Overview Product Name: The Bitcoin Code The Bitcoin Code Official Website: TheBitcoinCode.com 24option (Recommended): Click Here The Bitcoin Code CEO: Steve McKay Money-back Promise : Yes (2months) The Bitcoin Code Category: Binary Options The Bitcoin Code Price: FREE Get Coupon Code Now + Get Fast Action Bonus
REVEAL
The Bitcoin Code Review According to Steve McKay , “The The Bitcoin Code App is currently reaching successful binary options trade percentages that are unmatched by any other Binary Options Trading System 2016 that are available & it’s all thanks to the New Secrets code that drives the entire The Bitcoin Code software.”
Hundreds of new binary investor have flooded into the The Bitcoin Code members area due to the successful trade ratio that the The Bitcoin Code App is currently reaching & Steve McKay claims “The The Bitcoin Code system has the power and has proven to reach as high as 98% successful trades for a number of our beta-testers.”
There is still a Big question about how the The Bitcoin Code App operates and actually provides such high rate of success when investing within the binary options industry.
WHAT’S THE BITCOIN CODE SOFTWARE? The The Bitcoin Code tool was developed with the user in mind and is able to “completely take control of the binary options trading process” by finding & automating the trades for trader. There are a number of investors reaching over $3K each day using the live trading signals provided by The Bitcoin Code App.
New Binary Options Investor can plug into live The Bitcoin Code binary trading signals tool and begin receiving real-time alerts instantly so they do not have to spend Time learning the ins and outs of binary investing.
The newest feature that has been added to the The Bitcoin Code App is the automation feature which will completely control the trading by placing the trades at the The Bitcoin Code broker. This is a major driving factor behind the buzz of The Bitcoin Code App and the hundreds of new investors that continue to join in The Bitcoin Code on a daily basis.
HOW DOES THE BITCOIN CODE SYSTEM WORK? The The Bitcoin Code system is going to find the best trading chances that will give you the ability to earn up to 97% profit per winning trade. The second the The Bitcoin Code tool senses a trade the investor is going to get an instant alert which will tell them precisely what & how to trade.
There are a limited number of investment options when it comes to binary & those are the “call” or the “put.” The The Bitcoin Code App tells the investor to place a call the option is going to move upward by Signals of expiration while the put means the option will most likely be moving downward.
Every binary option has an expiration that’s set by the investor and this can range from 30 seconds to as long as one year (365 days). In the event the option moves in the direction choose by the The Bitcoin Code investor by the expiration he or she will win a profit payout of 89%-98%.
A loosing trade will cost the initial investment that was placed into that specific option which typically ranges from $5 to $1K A trade. The point behind the The Bitcoin Code App is to take out the guess work & learning curve to trading binary options. By following the signals that the The Bitcoin Code App provides traders can begin investing with little to no background in binary options.
WHAT’S IT GOING TO TAKE TO GET START WITH THE BITCOIN CODE SYSTEM? Any new binary investor that wants to get started with the The Bitcoin Code system will need to invest with an accepted binary options trading broker. The The Bitcoin Code system is currently only accepting a number of binary options brokers depending on where are traders live around the world. The list of accepted brokers is available after the investor enters their details on the official The Bitcoin Code website.
Features Of The Bitcoin Code System ● Watch over the Shoulder of a Pro Every Day & you can learn as you trade.
● Averaging 89% Winning Weeks – which means more potential profits for you to make good profits.
● The Bitcoin Code system is completely transparent which has only lost once in the last 1342 trading sessions.
● You can trade with The Bitcoin Code App on the go with your smartphone (Both Android & iOS).
● The Bitcoin Code is Works on any PC, Laptop & Mac.
● Multiple Signals Every Day – You’ll receive average of 21 & 97 trading signals daily which is good enough for you to earn quick profits for your day.
Pros Of The Bitcoin Code App: The Bitcoin Code App is the simple way that anybody can easily understand & Apply.
The Bitcoin Code software will guide you’re a combination of the insights gained from a handful of successful traders who have found a way to consistently generate profits trading binary options.
You don’t have to sit at your computer & trade – instead all you have to do is select the trade amount & click on the ‘activate’ button.
The Bitcoin Code App is very user friendly & works with almost every platform.
The Bitcoin Code is very comfortable to use by newbies.
The Bitcoin Code App offers updated version with new features & tools that will increase the accuracy to your daily trading experience.
Cons Of The Bitcoin Code App: The Bitcoin Code can net you a return quickly but it can also lead to a huge loss quickly. If your prognosis is wrong, you’ll end up losing up to 95% of the investments you put into the market.
Since an investor only has two options when it comes to trading in binary options markets, there aren’t that many tools that can help a trader navigate the market.
OUR RESULTS ON THE BITCOIN CODE APP Now, to my results. By the time I am writing this review I’ve used The Bitcoin Code for over 1 month. During the last 22 sessions, the The Bitcoin Code system traded a total of 174 signals & 131 were ITM. This is an amazing 75% win rate. I made a deposit of $5000 with OptionsMaker & invested $50 per each trade (What can I do, I am usually very skeptic about trading robots.) My balance today is $3590, which means I have made $3090 in just three weeks of using The Bitcoin Code App, with a daily average of over $140 in profits. That is not bad at all, but it’s hard not to imagine how my balance could have looked like if my trading amount was $1000 (I could have made $280 each day!). By the way, I usually take just 5-8 signals each day & I’m using the The Bitcoin Code software in its auto-pilot mode. HOW TO START WITH THE BITCOIN CODE SOFTWARE? The Bitcoin Code works on auto-pilot so no binary options trading experience is needed in order to use it. The Bitcoin Code App can dramatically improve a traders results & in turn help them make more cash. Large corporations use computerized systems that have set algorithms, but individual investors will simply have a set of rules for trading successfully. Here are the simple steps to join & use the The Bitcoin Code as follows.
Step 1: First thing, you have to simply fill out the form on this program to create your The Bitcoin Code. And all the information you submit is protected by the latest encryption technology and will not be shared with the third parties.
Step 2: After submitting the form, it’ll create your free The Bitcoin Code App account and give you access to your 100% free down-load of The Bitcoin Code tool.
Step 3: Begin with by opening an account at binary dealing options brokers & in your The Bitcoin Code Account. Then you connect your account with your The Bitcoin Code system.
Step 4: Finally, enter inside the The Bitcoin Code tool and start trading.
The Bitcoin Code is currently offering an instant trading bonus & interested investors should visit the official website to find out more.
Is The Bitcoin Code a SCAM? This is the first question that is bound to come to mind Is The Bitcoin Code Scam? After Weeks of testing & our Binary Options Trading expert team has come to the conclusion that The Bitcoin Code isn’t A Scam. Ask How? A simple test is try to withdraw your profits multiple times & in good numbers. If you’re able to do it seamlessly without any caveats involved or any sort of” No-Go” from your The Bitcoin Code broker, you’re in safe hands. We too succeeded to withdraw a part of the close to $17,398 dollars we’d made. No questions asked, No Red flags raised!
Update (23 January 2017) – Steve McKay The Bitcoin Code App is performing exceptionally well. Many The Bitcoin Code investors are reporting positive results with an average ITM Rate of over 87%. Bitcoin Code Explained This is the first question that is bound to come to mind Is The Bitcoin Code App Scam? After Weeks of testing & our Binary Options Trading expert team has come to the conclusion that The Bitcoin Code App is NOT A Scam. Ask How? A simple test is try to withdraw your profits multiple times & in good numbers. If you’re able to do it seamlessly without any caveats involved or any sort of” No-Go” from your The Bitcoin Code broker, you’re in safe hands. We too succeeded to withdraw a part of the close to $17,398 dollars we’d made. No questions asked, No Red flags raised!
Update (11 Nov 2017) – Steve McKay Bitcoin Code is performing exceptionally well. Many The Bitcoin Code investors are reporting positive results with an average ITM Rate of over 87%.
The Betquin transactions were sent to and from the Bitquin Electronic Governorates and digitally signed for security purposes. Also, everyone on the Web can know about the deal, while it’s possible to know the transaction record from the point of production of the Pitcairn. Keeping in the Betcquin is fantastic, and if you are a speculator you just have to wait for the price to rise, so the full point in this currency is to sell, right? So, how do these transactions take place when you sell Pitcairn?
There are no homeowners, only records for the Betquin transactions
Here’s the funny thing about the Bitquin: the Bitquin coin does not exist anywhere, not even on the hard drive. When we talk about someone owning a petquin, and then look at his own petquin, we won’t find any of the preserved Bitquin as it shows you in your bank account where you keep the dinar or the dollar. So you can’t point to anything physical, or even a digital file to say that ‘this is the Betquin.” Instead, all you will find are transactional records between different addresses, with balances increasing or decreasing. Each transaction is stored at any time and anywhere in a large public ledger called the buxine. If you would like to work on any CV address, the information will not be in the same address. So you should bring them through the look of the buccaneers.
Steve McKay Bitcoin Code Here is the funny thing about the Bitcoin: the Bitcoin coin doesn’t exist anyplace, not even on the hard drive. When we talk about somebody owning a BitcoinCodeAPP.com, and then look at his own Bitcoin Code sign in, we won’t find any of the preserved Bitcoin as it shows you in your bank account where you keep the dinar or the dollar. So you can’t point to anything physical, or even a digital file to say that “this is the Bitcoin Code” Instead, all you will find are transactional records between different addresses, with balances increasing or decreasing. Each transaction is stored at any time & anywhere in a large public ledger called theBitcoinCode.com . If you would like to work on any CV address, the information won’t be in the same address. So you should bring them through the look of the buccaneers.
In 2008, a person named Satoshi Nakamoto introduced an online paper suggesting the idea of a “virtual currency”. The following year, Bitcoin was first floated.
10 Facts You Should Know Before You Consider Using Bitcoin Code The currency of the Bitcoin is modern & in the experimental phase of a critical revolution, so you have to think twice before trading it, ask yourself whether these digital coins really fit you or not, and also know these facts so that you can decide your decision regarding the use of BitcoinCode or not .
Bitcoin Code can’t be falsified or exposed to inflation like regular currencies. You can get a Bitcoin & exchange them for goods & services with others even though they’re in large quantities. You don’t need an intermediary to use Bitcoin Code Generator.
Once you send them, you can’t retrieve them again or cancel the submission action, so you should think carefully before converting. As previously mentioned, it can’t be retrieved & you send it directly to the customer or to the seller without an intermediary, so you should focus during the transmission process to avoid any errors.
There is a clear policy for the use of Bitcoin Code system, and it has a known source, and all the Bitcoin Code app exchanges are sign up on the Internet, which means that anybody who has access to this network can monitor all transfers from all addresses, giving BitcoinCode a greater degree of protection, Which are mostly related to the financing of prohibited activities.
Getting a Bitcoin is not difficult, because you can buy it or get it for the services or goods you shop for. BitcoinCode is used in the whole world.
There is a permanent development in the manufacture of BitcoinCode, as we have already mentioned in the experimental phase is therefore likely to change and develop more in the coming stages.
There are services similar to Bitcoin but not the same technology, do not mix them like BCH or Bitcoin Cash.
People have started all kinds of rumors about Elon Musk & BTC related products, but ElonMusk himself has refused all of these & reports that he owns only a very little BTC that somebody gifted to him years ago. BitcoinCode was built by Steve McKay, not Elon Musk or anybody who works for/with Elon Musk. We are not sure what company Steve McKay was working for when he first developed the foundation of his now-famous app, and some have suggested that it may have been Tesla! We can not confirm or deny these rumors, but this is the only possible legitimate app we can think of for the Elon Musk rumor. Elon Musk Martin-Lewis is a famous financial personality from Great Britain. Like all of the other rumors, this one is false. Martin Lewis has never advised the program, despite his connections with money comparison site Money Super Market. He has been very vocal about his displeasure that his name has been used to promote this system, even taking to Twitter to deny his link. So while this app itself may have merits, they have not been described or promoted by Martin Lewis personally. Martin Lewis If you have read this far, you can probably guess the answer. No, Peter Jones (British entrepreneur & occasional star of Dragon’s Den) has never used, promoted, endorsed, or otherwise spoken favorably of the App. This is only an internet rumor, and no-one is sure exactly where it started. Just because this rumor is false does not mean that the platform isn’t good or scammy. But in general, we have found these BTC Code celebrity rumors to be nothing more than rumors.
1 note
·
View note
Text
Litecoin QT Wallet(LTC) is a person of the most ancient cryptocurrencies in existence and unveiled in October 2011 as a fork of Bitcoin. The idea shares many of the same characteristics as Bitcoin but strives to get lighter and quicker plus as a result, exhibits shorter stop creation periods of approximately installment payments on your five minutes. This enables with regard to both faster business deal distance and in turn, discount transaction costs than Bitcoin.<br/><br/>Litecoin Website<br/><br/>The group behind Litecoin explain the idea as a peer-to-peer Net currency that enables automatic, near-zero cost bills to help anyone in the earth. Litecoin is a wide open source, mathematically safeguarded, world-wide payment network which is furthermore fully decentralized. The Litecoin team as well look to incorporate technologies that boosts the particular coin�s key capabilities together with as a result, Litecoin loves substantive industry help support, trade volume and fluid, it is really a proven channel of swap and one particular of the most established online currencies with relation to web the business sector plus internet spending. Litecoin aspires to facilitate an boost in everyday digital dealings and also should run complementary to Bitcoin.<br/><br/>Who is behind it?<br/>Items [Show]<br/><br/>Litecoin was developed by Charlie Lee, an ex Coinbase employee who also quit working at this change in the summer time of 2017 so that you can concentrate on Litecoin full time. Lee envisaged creating a foreign money that would get complementary to Bitcoin plus operate as �digital silver� to Bitcoin�s reputation seeing that a digital store valuable similar to gold. Windschatten acts as a new vocal and clear front man to get the project and will be able to often be found expressing his ideas on some sort of variety of topics affecting typically the general cryptocurrency community.<br/><br/>Although being in fee involving all the day for you to day time operations involved with running Litecoin, Lee can be as well a part of often the Litecoin Foundation, a good non-profit organization registered in Singapore that strives to advance Litecoin for the good involving society by developing in addition to promoting state-of-the-art blockchain technologies. <a href="http://www.pearltrees.com/chapmanbroch71">Litecoin QT Windows Wallet</a> is comprised of:<br/><br/>Table of Directors: Charlie Lee (US), Xinxi Wang (SG), and Franklyn Richards (UK)<br/>Handling Overseer: Charlie Shelter<br/>Surgical procedures Director: Keith Yong (SG)<br/>Provided Full-time Developers: Adrian Gallagher (thrasher, AU)<br/>Part-time Builders: Loshan Testosterone levels. (UK), Addict Yang (CN)<br/>Litecoin is usually also made up regarding often the Litecoin Core enhancement group which consists of all of designers of the Litecoin project plus both equally the Litecoin Base and Primary team work tightly together and share technical together with financial support.<br/><br/>Litecoin Capabilities<br/>Litecoin is open source software in addition to is open to indie verification of binaries together with their similar source computer code. Litecoin in addition seeks to implement technological advances of which let this to preserve their position being a leading cryptocurrency. These include:<br/><br/>3Commas<br/>Blockchain � The Litecoin blockchain is geared in order to take care of a high level of transactions when in contrast to Bitcoin. By putting into action frequent stop generation, Lightening, and Segregated Witness (SegWit), the Litecoin network supports high amount transactions devoid of needing to modify the software program in the future. This specific makes Litecoin extremely effective intended for merchants and clients who else benefit from faster evidence times and lower charges.<br/><br/>Mining � Litecoin employs an algorithm called Scrypt which ascertains the gold mining process for new cash, in addition to Scrypt allows for a higher quantity seite an seite processing and is typically more accessible for different miners compared to a more regular algorithm. Working with Scrypt allows to facilitate this mining of Litecoin without resorting to typically the ASIC-based mining hardware desired to mine coins utilizing the SHA-256 formula. Miners are now honored with 25 brand-new Litecoin per block, a sum which is halved just about every 5 years or somewhere around every single 840, 000 pads. <a href="https://www.instapaper.com/read/1178179533">Litecoin Core Wallet</a> will be appointed to produce 84 million Litecoin, which will be exactly 4 times since Bitcoin�s maximum supply.<br/><br/>Sector Integration � Litecoin was initially originally a fork regarding Bitcoin and as a new result the two values still promote many involving the same characteristics. Litecoin is therefore one associated with the most nicely bundled cryptocurrencies in the sector and enjoys a wide range of assistance all over the entire industry. Litecoin is well supported simply by exchanges, ATMs, online and even offline sellers, web gambling dens, and coders. It is definitely also backed up by means of some sort of loyal and zealous group.<br/><br/>Litecoin vs. Bitcoin<br/>Bitcoin and Litecoin are generally known as being complimentary and Litecoin often works to steam ahead together with implementing changes and improvements that can in addition benefit the Bitcoin network.<br/><br/>Litecoin has focused on getting speedier and more successful than Bitcoin and has deliberately aimed in turning out to be adopted by stores in addition to vendors. In addition to be able to implementing frequent wedge creation, Litecoin also makes use of the Fast Network and Segregated Experience (SegWit) to help make certain that users will be ready to rely on this network being ready associated with handling a high level of purchases with the high speed together with lower cost. Litecoin was furthermore just lately used to conduct a cross chain atomic swap which enables end users to swap cryptocurrencies instantly through the use of a smart agreement together with without the need to get a third party for example an exchange.<br/><br/>These advances give Litecoin the top hand regarding overall effectiveness; however it is very almost inevitable that these characteristics will certainly eventually be integrated simply by the Bitcoin blockchain.<br/><br/>Inspite of establishing itself as the top five cryptocurrency, Litecoin nonetheless tracks in Bitcoin�s aftermath in terms of popularity. Bitcoin at the moment positions at around $7000 in addition to holds a market place cap involving around $117B and it is also capable of recording 24 hour industry volumes regarding up to four occasions greater than any other cryptocurrency. Litecoin currently holds a market cap of $3B plus trades at all-around $60 ( as connected with 15th Nov 2017 ).<br/><br/>Bitcoin is definitely viewed seeing as the superior shop of value and The Bitcoin network can never exceed twenty-one million coins. Litecoin could accommodate up to be able to 84 mil coins and even its lower price helps it be more appropriate to purchasing low-priced goods or providers, and as cryptocurrencies border closer to mass adoption this should help Litecoin to shut the gap about it has the older brother.<br/><br/>Litecoin Pouches<br/>There are various of diverse wallets you can use regarding stocking your Litecoin, you could store them in a new Hardware Wallet: the two the Trezor and Ledger support Litecoin. You can furthermore download several pouches from the official internet site for Windows, Mac pc, Cpanel, Android, iOS and thus on.<br/><br/>Litecoin Pouches<br/><br/>Just how to Buy Litecoin<br/>Litecoin is one of merely a few cryptocurrencies that you can currently order together with fiat currency via Coinbase, which makes that one of several least complicated purchases currently and even consequently attractive to newbies to be able to cryptocurrency. You can read our full review involving Coinbase here.<br/><br/>Sign up with Coinbase<br/>For first time potential buyers of crypto currency, most of us recommend that you work with Coinbase to make your own personal first purchase : it is easy to use, completely governed by the UNITED STATES government therefore you know that is one of the safest and many reputable spots to purchase cryptocurrency via. <a href="https://www.plurk.com/chapmanbruus58">LTC Wallet</a> offers the power to purchase Bitcoin, Litecoin and Ethereum with a credit score or debit card or maybe by sending a traditional bank transfer. The fees are usually higher for cards nonetheless you will receive your current money instantly.<br/><br/>You will certainly have to carry out there several identity verification when signing up as they now have to adhere to rigorous financial guidelines. Make positive you use our link to signup you can be credited with $10 throughout no cost bitcoin when you choose a first purchase of $465.21.<br/><br/>Coinbase Website<br/><br/>To obtain started, click the �Sign up� button where you will arrive at a subscription form where you will need to be able to enter your name, email and choose a code.<br/><br/><br/><br/>Coinbase will then send you a hyperlink by way of email to confirm your own email account, when you finally click on the link in this email you will find yourself taken in order to the verification webpage. A person must then add your own personal cell phone number and upload a new picture of your USERNAME � this is usually a passport, driving license etc. You also have in order to add your settlement information, so you can increase your bank account or perhaps a debit or maybe credit cards seeing as required � immediately after a short period your accounts will then be tested and you can then make your current first invest in.<br/><br/>Coinbase Confirmation<br/><img src="https://a.c-dn.net/b/3uic0P/Cryptocurrency-Price-Analysis---Bitcoin-Ripple-Litecoin-and-Ethereum_body_Picture_2.png.full.png"/><br/><br/>Purchase Litecoin<br/>In Coinbase, visit the �Buy <a href="/">hcg diet plan</a> Sell� tab at this top, select �Litecoin�, choose your payment technique and enter the amount you wish to buy ~ you can both enter into a US Money amount or a number associated with LTC.<br/><br/>Get Etherum<br/><br/>An individual will then be inquired to confirm your purchase, in case paying with some sort of card a person may well have got to complete a good confirmation with your card provider. Once that�s complete, the Litecoin will be added in to your account and most of us recommend you then transfer them off the exchange to some sort of wallet where you command the individual key.<br/><br/>Industry Performance<br/>Regarding the the greater part from the living Litecoin generally bought and sold with close to the $3 to $4 mark which has a marketplace cap that normally did not exceed $200M. LTC knowledgeable a surge in worth in the winter regarding 2013 yet soon dropped back to its standard levels. It continued secure for a long interval and was still investing at the $4 mark simply by Walk 2017. However, Litecoin would soon go on to skyrocket in cost and regularly set fresh all time high prices. This reached a peak in The month of september when LTC would trade at over $80 and reached a market cap of around $4. 2B, whilst experiencing 24 trade volumes of all-around $1B.<br/><br/>Litecoin was able to benefit from a world-wide increase in cryptocurrency trading as being the crypto areas in locations such because Japan and Tiongkok grew to become more developed. On the other hand, part of the current upturn inside of popularity can come to be attributed to Litecoin�s usage of features like the Super Network and Segregated Witness (SegWit), technology who has authorized the network to approach more transactions and be made use of across the web to cover some sort of range of merchandise and services. The significance of Litecoin has grown substantially around 2017 and LTC at present trades at just less than $60 while preserving the market limit of around $3B. With 2017 indicating to be the main eruption year for Litecoin many analysts and experts happen to be eager to find what lies in store to get the cryptocurrency over the future few years.<br/>
1 note
·
View note
Text
Ccleaner cloud yearly subscription

#CCLEANER CLOUD YEARLY SUBSCRIPTION HOW TO#
#CCLEANER CLOUD YEARLY SUBSCRIPTION UPGRADE#
#CCLEANER CLOUD YEARLY SUBSCRIPTION WINDOWS 10#
#CCLEANER CLOUD YEARLY SUBSCRIPTION ANDROID#
#CCLEANER CLOUD YEARLY SUBSCRIPTION SOFTWARE#
#CCLEANER CLOUD YEARLY SUBSCRIPTION WINDOWS 10#
More on those in a bit.Īs noted earlier Windows 10 includes a handful of built-in tune-up utilities that you may want to check out if you don't want to spend money on third-party software. The top-of-the-line Professional Plus (reviewed here) is a $39.95 application that adds three standalone apps for hard drive defragmentation, file recovery, and PC spec viewing.
#CCLEANER CLOUD YEARLY SUBSCRIPTION SOFTWARE#
The $24.95 Professional plan builds on the free option by offering more thorough computer cleaning, real-time system monitoring, automatic history cleaning, and automatic software updates. It has basic PC-cleaning capabilities, as well as privacy-protection tools that let you delete cookies, passwords, and other related browser files. The free version is, as you'd expect, the least feature-packed option. Piriform has corrected the problem in subsequent CCleaner releases. Still, Iolo System Mechanic remains the category's Editors' Choice due to its thorough cleaning tools and unlimited licenses.Įditors' Note: This is PCMag's first CCleaner review since the tune-up utility suffered malware-related issues in 2017. CCleaner is pricier than Windows 10's free, integrated tune-up tools, but it comes in at a lower price than some competing products, offers features that dramatically improved our testbed's boot time, and is easy enough to use that it's worth the investment. It boasts many system-enhancing features, including a registry repairer and real-time system monitoring, as well as extra features like privacy protection and drive-wiping tools. Piriform's CCleaner Professional Plus is one of many tune-up utilities capable of giving a heavily used PC a new shot at life.
Performance improvement not as large as the competition's in some areas.
#CCLEANER CLOUD YEARLY SUBSCRIPTION HOW TO#
How to Set Up Two-Factor Authentication.How to Record the Screen on Your Windows PC or Mac.How to Convert YouTube Videos to MP3 Files.How to Save Money on Your Cell Phone Bill.How to Free Up Space on Your iPhone or iPad.How to Block Robotexts and Spam Messages.
#CCLEANER CLOUD YEARLY SUBSCRIPTION ANDROID#
The malware did not affect the Android CCleaner app. Users of CCleaner Cloud are already protected as the software is updated automatically.
#CCLEANER CLOUD YEARLY SUBSCRIPTION UPGRADE#
The malware-infected version was released on Augand the infected version was removed on September 15, 2017.Īll users of the application should upgrade to version 5.34 or higher. Piriform acted quickly once it was alerted to the presence of malware and released a new version of CCleaner however, an immediate security alert was not issued about the backdoor as the company was working with law enforcement and did not want to alert the attackers that the malware had been discovered. Piriform notes that this was a two-stage backdoor that was also capable of running code from a remote IP address. That information was exfiltrated to a third-party server in the United States. An investigation into the incident is ongoing and law enforcement are involved.Īccording to a recent blog post from Piriform, the malware was capable of gathering information such as a user’s IP address, active software installed on the infected device, and a list of network adaptors. It is unclear whether the malware was inserted by an insider or whether an external attacker compromised the build or development environment. The backdoor was inserted into the CCleaner binary and was hosted on the company’s server. As of yesterday, there were still 730,000 users that had not yet updated to the latest version of the software. Initially it was thought that as many as 3% of users may have been affected – approximately 3.9 million devices. An estimated 2.27 million users have downloaded the infected version of the application, according to Avast, which purchased Piriform this summer. The backdoor was inserted into those versions at least a month before it was discovered, giving the hackers behind the malware plenty of time to gather information on compromised computers, of which there are many. The backdoor was present in two versions of the application – the 32-bit version of CCleaner and CCleaner Cloud. Researchers at Cisco Talos recently announced that CCleaner contains a backdoor that was inserted by hackers. Piriform’s CCleaner, a free PC cleaning app with 130 million users around the world, has been discovered to contain malware.

0 notes
Text
Jre 8 Dmg For Mac
Java Archive Downloads - Java SE 8u211 And Later
REW Beta Release V5.20 Beta 29
8 Installation Of The JDK And The JRE On MacOS - Oracle
The Java Development Kit (JDK), officially named 'Java Platform Standard Edition' or 'Java SE', is needed for writing Java programs. The JDK is freely available from Sun Microsystems (now part of Oracle). The mother site for JDK (Java SE) is http://www.oracle.com/technetwork/java/javase/overview/index.html.
Patch Name: jre-8u65-macosx-x64.dmg: Patch Description: Update for Java Runtime Environment for Mac (1.8.65) Bulletin Id: MAC-033: Bulletin Title: Java Runtime Environment 8 Updates For Mac. Jre-8u version-macosx-amd64.dmg. Jre-8u version-macosx-x64.dmg. Where version is 6 or later. Download the file. Before the file can be downloaded, you must accept the license agreement. From either the Downloads window of the browser, or from the file browser, double click the file.dmg to launch it. Complete antivirus/antispyware test for Java (JRE) for Mac 8 Build 261, setup file: jre-11-ea+8osx-x64bin.dmg (75.39 MB) using top antivirus engines Avast.
'JDK' or 'JRE'?
Summary: JDK 8 should be installed in your system to run SysTools Mac software even if you have latest version of JDK available in your system. It is because, our application requires installation of JDK & JRE in the user machine for running the software properly. The latest version like JDK 11, 13 does not provides JRE installers.
JRE (Java Runtime) is needed for running Java programs. JDK (Java Development Kit), which includes JRE plus the development tools (such as compiler and debugger), is need for writing as well as running Java programs. In other words, JRE is a subset of JDK. Since you are supposed to write Java Programs, you should install JDK, which includes JRE.
JDK Versions
Reference: 'Java Version History' @ https://en.wikipedia.org/wiki/Java_version_history.
JDK Alpha and Beta (1995): Sun Microsystem announced Java in September 23, 1995.
JDK 1.0 (January 1996): Originally called Oak (named after the oak tree outside James Gosling's office). Renamed to Java 1 in JDK 1.0.2.
JDK 1.1 (February 1997): Introduced AWT event model, inner class, JavaBean, JDBC, and RMI.
J2SE 1.2 (JDK 1.2) (December 1998): Re-branded as 'Java 2' and renamed JDK to J2SE (Java 2 Standard Edition). Also released J2EE (Java 2 Enterprise Edition) and J2ME (Java 2 Micro Edition). Included JFC (Java Foundation Classes - Swing, Accessibility API, Java 2D, Pluggable Look & Feel, and Drag & Drop). Also introduced Collection Framework and JIT compiler.
J2SE 1.3 (JDK 1.3) (May 2000): Introduced Hotspot JVM.
J2SE 1.4 (JDK 1.4) (February 2002): Introduced assert statement, non-blocking IO (nio), logging API, image IO, Java webstart, regular expression (regex) support.
J2SE 5.0 (JDK 5) (September 2004): Officially called 5.0 instead of 1.5 (by dropping the 1.). Introduced generics, autoboxing/unboxing, annotation, enum, varargs, for-each loop, static import. See 'JDK 5 New Features'.
Java SE 6 (JDK 6) (December 2006): Renamed J2SE to Java SE (Java Platform Standard Edition). No new language features. See 'JDK 6 New Features'.
Java SE 7 (JDK 7) (July 2011): First version after Oracle purchased Sun Microsystem - aslo called OracleJDK. Introduced Strings in switch statement, Binary integer literals, allowing underscores in numeric literals, improved type inference for generic instance creation (or diamond operator <>), Catching multiple exception types and rethrowing exceptions with improved type checking. See 'JDK 7 New Features'.
Java SE 8 (JDK 8) (LTS) (March 2014): Included support for Lambda expressions, default and static methods in interfaces, improved collection, and JavaScript runtime. Also integrated JavaFX graphics subsystem. See 'JDK 8 New Features'.
Java SE 9 (JDK 9) (September 21, 2017): Introduced modularization of the JDK (module) under project Jigsaw, the Java Shell (jshell), and more. See 'JDK 9 New Features'.
Java SE 10 (18.3) (JDK 10) (March 2018): Introduced var for type inference local variable (similar to JavaScript). Introduced time-based release versioning with two releases each year, in March and September, denoted as YY.M. Removed native-header generation tool javah. See 'JDK 10 New Features'.
Java SE 11 (18.9) (LTS) (JDK 11) (September 2018): Extended var to lambda expression. Standardize HTTP client in java.net.http. Support TLS 1.3. Clean up the JDK and the installation package (removed JavaFX, JavaEE, CORBA modules, deprecated Nashorn JavaScript engine). OracleJDK is no longer free for commercial use, but OpenJDK is still free. See 'JDK 11 New Features'.
Java SE 12 (19.3) (JDK 12) (March 2019): Switch Expression (preview). See 'JDK 12 New Features'.
Java SE 13 (19.9) (JDK 13) (September 2019): Switch Expression (preview), Multi-line Text Block (preview). See 'JDK 13 New Features'.
Java SE 14 (20.3) (JDK 14) (March 2020): Records (preview)
How To Install JDK on Windows
Step 0: Un-Install Older Version(s) of JDK/JRE
I recommend that you install only the latest JDK. Although you can install multiple versions of JDK/JRE concurrently, it is messy.
If you have previously installed older version(s) of JDK/JRE, un-install ALL of them. Goto 'Control Panel' ⇒ (optional) 'Programs' ⇒ 'Programs and Features' ⇒ Un-install ALL programs begin with 'Java', such as 'Java SE Development Kit ..', 'Java SE Runtime ..', 'Java X Update ..', and etc.
Step 1: Download JDK
Goto Java SE download site @ http://www.oracle.com/technetwork/java/javase/downloads/index.html.
Under 'Java Platform, Standard Edition' ⇒ 'Java SE 13.0.(x)', where (x) denotes a fast running security-update number ⇒ Click the 'Oracle JDK Download' button.
Under 'Java SE Development Kit 13.0.(x)' ⇒ Check 'Accept License Agreement'.
Choose the JDK for your operating system, i.e., 'Windows'. Download the 'exe' installer (e.g., 'jdk-13.0.(x)_windows-x64_bin.exe' - about 159MB).
Step 2: Install JDK
Run the downloaded installer (e.g., 'jdk-13.0.(x)_windows-x64_bin.exe'), which installs both the JDK and JRE.
By default, JDK is installed in directory 'C:Program FilesJavajdk-13.0.(x)', where (x) denotes the update number. Accept the defaults and follow the screen instructions to install JDK.
Use your 'File Explorer', navigate to 'C:Program FilesJava' to inspect the sub-directories. Take note of your JDK installed directoryjdk-13.0.(x), in particular, the update number (x), which you will need in the next step.
I shall refer to the JDK installed directory as <JAVA_HOME>, hereafter, in this article.
Step 3: Include JDK's 'bin' Directory in the PATH
Windows' Command Prompt (CMD) searches the current directory and the directories listed in the PATHenvironment variable (or system variable) for executable programs. JDK's programs (such as Java compiler 'javac.exe' and Java runtime 'java.exe') reside in the sub-directory 'bin' of the JDK installed directory. You need to include JDK's 'bin' in the PATH to run the JDK programs.
To edit the PATH environment variable in Windows 10:
Launch 'Control Panel' ⇒ (Optional) 'System and Security' ⇒ 'System' ⇒ Click 'Advanced system settings' on the left pane.
Switch to 'Advanced' tab ⇒ Click 'Environment Variables' button.
Under 'System Variables' (the bottom pane), scroll down to select variable 'Path' ⇒ Click 'Edit..'.
For Newer Windows 10: You shall see a TABLE listing all the existing PATH entries (if not, goto next step). Click 'New' ⇒ Click 'Browse' and navigate to your JDK's 'bin' directory, i.e., 'c:Program FilesJavajdk-13.0.(x)bin', where (x) is your installation update number ⇒ Select 'Move Up' to move this entry all the way to the TOP.
For Older Windows 10 (Time to change your computer!): (CAUTION: Read this paragraph 3 times before doing this step! Don't push 'Apply' or 'OK' until you are 101% sure. There is no UNDO!!!) (To be SAFE, copy the content of the 'Variable value' to Notepad before changing it!!!) In 'Variable value' field, APPEND 'c:Program FilesJavajdk-13.0.(x)bin' (where (x) is your installation update number) IN FRONT of all the existing directories, followed by a semi-colon (;) to separate the JDK's bin directory from the rest of the existing directories. DO NOT DELETE any existing entries; otherwise, some existing applications may not run.
Note: If you have started CMD, you need to re-start for the new environment settings to take effect.
Step 4: Verify the JDK Installation
Launch a CMD via one of the following means:
Click 'Search' button ⇒ Type 'cmd' ⇒ Choose 'Command Prompt', or
Right-click 'Start' button ⇒ run.. ⇒ enter 'cmd', or
Click 'Start' button ⇒ Windows System ⇒ Command Prompt
Issue the following commands to verify your JDK installation:
Issue 'path' command to list the contents of the PATH environment variable. Check to make sure that your JDK's 'bin' is listed in the PATH.
Issue the following commands to verify that JDK/JRE are properly installed and display their version:
Step 5: Write a Hello-World Java Program
Create a directory to keep your works, e.g., 'd:myProject' or 'c:myProject'. Do NOT save your works in 'Desktop' or 'Documents' as they are hard to locate. The directory name shall not contain blank or special characters. Use meaningful but short name as it is easier to type.
Launch a programming text editor (such as TextPad, NotePad++, Sublime Text, Atom). Begin with a new file and enter the following source code. Save the file as 'Hello.java', under your work directory (e.g., d:myProject).
Step 6: Compile and Run the Hello-World Java Program
To compile the source code 'Hello.java':
Start a CMD Shell (Search ⇒ enter 'cmd' ⇒ select 'Command Prompt').
Set the Current Drive to the drive where you saved your source file 'Hello.java'. If you use drive 'c', skip this step. Else if you use drive 'd', enter 'd:' as follow:
Set the Current Working Directory to the directory that you saved your source file via the cd (Change Directory) command. For example, suppose that your source file is saved in directory 'myProject'.
Issue a dir (List Directory) command to confirm that your source file is present in the current directory.
Invoke the JDK compiler 'javac' to compile the source code 'Hello.java'. The compilation is successful if the command prompt returns. Otherwise, error messages would be shown. Correct the errors in your source file and re-compile. Check 'Common JDK Installation Errors', if you encounter problem compiling your program.
The output of the compilation is a Java class called 'Hello.class'. Issue a dir (List Directory) command again to check for the output.
To run the program, invoke the Java Runtime 'java':
Everything that can possibly go wrong will go wrong: Read 'JDK Installation Common Errors'.
Step 7: (For Advanced Users Only) JDK's Source Code
Source code for JDK is provided and kept in '<JAVA_HOME>libsrc.zip' (or '<JAVA_HOME>src.zip' prior to JDK 9). I strongly recommend that you to go through some of the source files such as 'String.java', 'Math.java', and 'Integer.java', under 'javalang', to learn how experts program.
How to Install JDK on macOS
Step 1: Check if JDK has been Pre-Installed
To check if JDK has been installed, open a 'Terminal' (Search 'Terminal'; or Finder ⇒ Go ⇒ Utilities ⇒ Terminal) and issue this command:
If a JDK version number is returned (e.g., JDK x.x.x), then JDK has already been installed. If the JDK version is prior to 1.8, proceed to Step 2 to install the latest JDK; otherwise, proceed to 'Step 3: Write a Hello-world Java program'.
If message 'command not found' appears, JDK is NOT installed. Proceed to the 'Step 2: Install JDK'.
If message 'To open javac, you need a Java runtime' appears, select 'Install' and follow the instructions to install JDK. Then, proceed to 'Step 3: Write a Hello-world Java program'.
Step 2: Download JDK
Goto Java SE download site @ http://www.oracle.com/technetwork/java/javase/downloads/index.html.
Under 'Java Platform, Standard Edition' ⇒ 'Java SE 13.0.(x)', where (x) denotes a fast running security-update number ⇒ Click the 'Oracle JDK' 'Download' button.
Under 'Java SE Development Kit 13.0.(x)' ⇒ Check 'Accept License Agreement'.
Choose the JDK for your operating platform, i.e., macOS. Download the DMG installer (e.g, jdk-13.0.(x)_osx-x64_bin.dmg - about 172MB).
Step 3: Install JDK/JRE
Double-click the downloaded Disk Image (DMG) file. Follow the screen instructions to install JDK/JRE.
Eject the DMG file.
To verify your installation, open a 'Terminal' and issue these commands.
Step 3: Write a Hello-World Java Program
Create a directory called 'myProject' under your home directory (Launch 'Finder' ⇒ 'Go' ⇒ 'Home'; Select 'File' ⇒ 'New Folder' ⇒ 'myProject'). In macOS, the home directory of the current user can be referenced as '~'. Hence, this new directory can be referenced as '~/myProject'.
Use a programming text editor (such as Sublime Text or Atom) to input the following source code and save as 'Hello.java' under the directory '~/myProject'. (If you use macOS's default text editor 'TextEdit' (NOT recommended), you need to open a new file ⇒ choose 'Format' ⇒ 'Make Plain Text' ⇒ Enter the source code ⇒ Save as 'Hello.java'.)
Step 4: Compile and Run the Hello-World Java Program
To compile the source code 'Hello.java', open a new 'Terminal' ('Go' ⇒ 'Utilities' ⇒ 'Terminal') and issue these commands (as illustrated):
To run the Hello-world, invoke the Java Runtime 'java' as follows:
How to Install JDK on Ubuntu
There are several JDK implementations available for Linux, such as Oracle JDK, OpenJDK, Sun JDK, IBM JDK and GNU Java Compiler. We shall choose the Oracle JDK 8. Ubuntu chooses OpenJDK as its default JDK, which is not 100% compatible with Oracle JDK.
Step 0: Check if JDK has already been Installed
Open a Terminal and issue this command:
If a JDK version number (e.g., 'javac x.x.x') appears, JDK has already been installed. You can skip the installation and goto step 2.
To remove OpenJDK, issue command:
Step 1: Download and Install JDK
Goto JDK (Java SE) download site @ http://www.oracle.com/technetwork/java/javase/downloads/index.html. Under 'Java Platform, Standard Edition' ⇒ 'Java SE 11.0.(x)' ⇒ Click JDK's 'Download' ⇒ Under 'Java SE Development Kit 11.0.(x)' ⇒ Check 'Accept License Agreement' ⇒ Select 'Linux', 'tar.gz' package, (e.g., 'jdk-13.0.(x)-linux-x64_bin.tar.gz' - 171MB). The tarball will be downloaded in directory '~/Downloads', by default.
We shall install JDK under '/usr/local/java' (or Ubuntu's default JDK directory /usr/lib/jvm; or /opt/java). First, create a directory 'java' under '/usr/local'. Open a Terminal and issue these commands: Extract the downloaded package (Check your downloaded filename!) JDK shall be extracted in a folder '/usr/local/java/jdk-13.0.(x)', where (x) is the update number.
Inform the Ubuntu to use this JDK/JRE: The above steps set up symlinks java, javac, javaws at /usr/bin (which is in the PATH), that link to /etc/alternatives and then to JDK bin directory. The 'alternatives' system aims to resolve the situation where several programs fulfilling the same function (e.g., different version of JDKs). It sets up symlinks thru /etc/alternatives to refer to the actual programs to be used. Alternatively, you can include the JDK's bin and JRE's bin into the PATH directly.
To verify the JDK installation, issue these commands:
(Don't Do this step - It is taken care by 'alternative' in Step 3. Keep here to show you how to set PATH.) Add JDK's binary directory ('bin') to the 'PATH' by editing '/etc/profile': Add these lines at the end of the file '/etc/profile', replace '(x)' with the actual number: Rerun the configuration file by:
Step 2: Compile and Run a Hello-world Java Program
File Explorer ⇒ Home ⇒ Create a new folder called 'myProject' to keep our works.
Open 'Text Editor' (gedit). Enter the following source code and save as 'Hello.java' under the '~/myProject' directory created earlier.
To compile the Hello-world Java program, launch a Terminal and issue these commands:
Run the Hello-world Java program:
Source-Code Editors & IDEs for Java Programming
Eclipse IDE
You need to first install Eclipse. Read 'How to Install Eclipse'.
You can then proceed to write your first Java program. Read 'Writing your first Java Program with Eclipse'.
Eclipse allow you to debug program graphically. Read 'Debugging program in Eclipse'.
NetBeans IDE
You need to first install NetBeans. Read 'How to Install NetBeans'.
You can then proceed to write your first Java program. Read 'Writing your first Java program with NetBeans'.
NetBeans allow you to debug program graphically. Read 'Debugging program in NetBeans'.
Visual Studio (VS) Code IDE
Click HERE, look for 'VS Code for Java Programming'
Sublime Text (for Windows, macOS, Linux)
Click HERE, look for 'Sublime Text for Java Programming'
Atom (for Windows, macOS, Linux)
(TODO)
TextPad (for Windows only)
Click HERE, look for 'TextPad for Java Programming'.
NotePad++ (for Windows only)
Click HERE, look for 'NotePad++ for Java Programming'.
(JDK 11) Launch Single-Source-File New Feature
From JDK 11, you can compile/run a single-file program in one step, without explicit compilation.
Write a 'Hello.java' (see previous section).
Delete 'Hello.class', if it exists.
You can compile/run 'Hello.java' in one command as follows:
Notes:
This is applicable to single source-file only.
No need to use javac to compile the program.
It compiles in memory (without producing a .class file), and run.
This feature is introduced for beginners to learn Java, and for professionals to test a Java feature.
The filename and classname need not be the same.
How To Set JAVA_HOME Environment Variable
Many Java applications (such as Tomcat) require the environment variable JAVA_HOME to be set to the JDK installed directory.
See 'How to set JAVA_HOME for Windows' or 'How to set JAVA_HOME for macOS/Linux'.
Common Errors in installing JDK
(Advanced) External JAR Files and Native Libraries
Notes: This section is applicable to JDK prior to JDK 9. JDK 9 introduces a new level called 'module' on top of package, and 'jmod' files for Java modules. Need to revise this section for JDK 9.
Java Archive Downloads - Java SE 8u211 And Later
External Java packages (such as Servlet, MySQL Connector/J, JOGL, JUnit) are often distributed in JAR files (Java Archive - a single-file package of many Java classes), with possibly Native Libraries ('.lib' and '.dll' in Windows, or '.a' and '.so' in Linux/macOS).
External JAR Files ('.jar')
If external JAR files are not properly included: https://hunterscreen229.tumblr.com/post/654151946943578112/adguard-mac-torrent.
During the compilation, you will receive compilation error 'cannot find symbol' on classes belonging to the external packages.
During execution, you will get a runtime error 'Could not find or load main class xxx' or 'NoClassDefFoundError'.
To include external JAR files, you can either:
Copy all the JAR files of the external packages to the Java's Extension Directories (NOT applicable to JDK 9).
For Windows, the JDK extension directory is located at '<JAVA_HOME>jrelibext' (e.g., 'c:Program FilesJavajdk1.8.0_xxjrelibext').
For macOS, the JDK extension directories are '/Library/Java/Extensions' and '/System/Library/Java/Extensions'.
For Ubuntu, the JDK extension directories are '<JAVA_HOME>/jre/lib/ext' (e.g., '/usr/user/java/jdk1.8.0_xx/jre/lib/ext') and '/usr/java/packages/lib/ext'.
The location of JDK's extension directories is kept in Java's System Property 'java.ext.dirs'. You can print its contents via System.out.println(System.getProperty('java.ext.dirs')).
You can also include all the JAR files in the CLASSPATH environment variable. CLASSPATH may contain directories (of Java classes) or JAR files (single-file archive of Java classes). If you set the CLASSPATH, you must also include the current directory (denoted as '.').
For Windows, set the CLASSPATH in Control Panel ⇒ System ⇒ Advanced system settings ⇒ Advanced ⇒ Environment Variables ⇒ System Variables ⇒ New ⇒ In 'Variable name', enter 'CLASSPATH' ⇒ In 'Variable value', enter '.;path1xxx.jar;path2yyy.jar', where the entries are separated by a semi-colon (;).
For Linux and macOS: Edit ~/.profile or ~/.bash_profile (or /etc/profile for system-wide setting) to include the following line at the end of the file: The entries are separated by colon (:).
You can also set the CLASSPATH in the javac/java command-line via the option -cp <paths> (or -classpath <paths>), for example,
External Native Libraries ('.lib', '.dll', '.a', '.so')
Some external package may provide static or shared native libraries in the form of '.lib' (Windows' static LIBrary), '.dll' (Windows' Dynamically Link Library), '.a' (Unix's static (Archive) library), or '.so' (Unix's Shared Object library).
Native Libraries are to be kept in a directory accessible via JRE's Property 'java.library.path', which normally but not necessarily includes all the directories in the PATH environment variable.
Native libraries are not involved in the compilation. But if they are not properly included during runtime time, you will get a runtime error 'java.lang.UnsatisfiedLinkError: no xxx in java.library.path'.
To include external native libraries:
Copy the native libraries into a system library directory, e.g., c:windowssystem32 (Windows), /usr/lib or /usr/local/lib (macOS / Unix). You can verify that the directory is included in Java's System Property 'java.library.path', via System.out.println(System.getProperty('java.library.path')).
You can also set the native library path via the java's command-line option -Djava.library.path=xxx, for example,
Eclipse/NetBeans
Using an IDE can greatly simplifies inclusion of external packages. Read 'Eclipse How-To' or 'NetBeans How-To'.
Link to References & Resources Java Platform, Standard Edition Installation Guide Contents Previous Next
REW Beta Release V5.20 Beta 29
This page describes how to install and uninstall JRE 8 on OS X computers.
This page has these topics:
See 'JDK 8 and JRE 8 Installation Start Here' for general information about installing JDK 8 and JRE 8.
See 'OS X Platform Install FAQ' for general information about installing JRE 8 on OS X.
System Requirements
Observe these requirements:
Any Intel-based computer running OS X 10.8 (Mountain Lion) or later.
Administrator privileges.
Note that installing the JRE on OS X is performed on a system-wide basis, for all users, and administrator privileges are required. You cannot install Java for a single user.
Only one JRE can be installed at a time. The system will not install a JRE that has a lower version than the current version. If you wish to install a lower version of the JRE, uninstall the current version as described in 'Uninstalling the JRE'.
Installing a JRE from Oracle will not update java -version symlinks or add java to your path. To be able to do this, you need to install the JDK.
JRE Installation Instructions
The JRE installation includes the JavaFX Runtime which is incorporated into the same directory structure.
8 Installation Of The JDK And The JRE On MacOS - Oracle
Depending on your processor, the downloaded file has one of the following names:
jre-8uversion-macosx-amd64.dmg
jre-8uversion-macosx-x64.dmg
Where version is 6 or later.
Download the file.
Before the file can be downloaded, you must accept the license agreement.
From either the Downloads window of the browser, or from the file browser, double click the file.dmg to launch it.
A Finder window appears containing an icon of an open box and the name of the .pkg file.
Double click the package icon to launch the Install app.
The Install app displays the Introduction window.
Note:
In some cases, a Destination Select window appears. This is a bug, as there is only one option available. If you see this window, select Install for all users of this computer to enable the Continue button.
Click Continue.
The Installation Type window appears.
Click Install.
A window appears that says 'Installer is trying to install new software. Type your password to allow this.'
Enter the Administrator login and password and click Install Software.
The software is installed and a confirmation window appears.
After the software is installed, delete the .dmg file if you want to save disk space.
Determining the Installed Version of the JRE
If you have not yet installed Apple's Java OS X 2012-006 update, then you are still using a version of Apple Java 6 that includes the plug-in and the Java Preferences app. See 'Note for Users of OS X that Include Apple Java 6 Plug-in'.
Only one JRE can be installed. Installing a JRE removes the previously installed JRE. The JRE version used by the system can be determined in one of two ways:
From System Preferences click the Java icon from the Other category. This launches the Java Control Panel. Click About.
Type the following in a Terminal window (note escaped space character, ignore line break):
The system will not install a JRE that has a lower version than the current version. If you want to install a lower version, first uninstall the existing version.
Uninstalling the JRE
To uninstall the JRE, you must have Administrator privileges and execute the remove commands either as root or by using the sudo(8) tool.
Remove one directory and one file (a symlink), as follows:
Navigate to /Library/Internet Plug-Ins and remove the JavaAppletPlugin.plugin directory.
Navigate to /Library/PreferencePanes and remove JavaControlPanel.prefpane.
Do not attempt to uninstall Java by removing the Java tools from /usr/bin. This directory is part of the system software and any changes will be reset by Apple the next time you perform an update of the OS.
Contents Previous Next
Copyright © 1993, 2014, Oracle and/or its affiliates. All rights reserved.
0 notes
Text
Best Miner For Mac

Best Ethereum Miner For Mac
Best Miner Machine For Bitcoin
Doge says: Get a coinbase account, buy crypto, send it to Bittrex to buy DOGE!, and keep it on Exodus wallet!
This software is comfortable with GPU mining hardware and runs on Mac. It is the best system for cloud mining. Cloud-based service can help the miners in Bitcoin mining if you want to go for it, and you are not interested in investing in ASIC. Miner server is the best cloud-based mining service. Awesome Miner is a powerful mining software that lets users manage multiple mining rigs and miner’s pools, all from one dashboard. As a result, it tops our list as the best centralized.
Aug 26, 2020 Bitcoin Mining Software For Mac. macOS/Windows/Linux One of the most popular and best-rated software for mining Bitcoin is CGMiner. It’s available on Windows, macOS,. Most profitable miners currently on the market and soon to be released. $42,509.99 $106.74 $2,953.64 $243.28 $46.12 $157.92 $147.04 Follow @WhatToMine dark mode GPU. Contribute to rplant8/cpuminer-opt-rplant development by creating an account on GitHub. RandomX Mining On MacOS Using XMRig MacOS Build 16 Apr 2020 Apple’s MacOS computers aren’t really a popular choice as far as GPU mining is concerned, but for CPU mining they may still be usable if you manage to find a miner with a MacOS binary build or if you manage to compile it yourself.
SPECIAL: Need to buy more Dogecoin? Open a new Coinbase account, buy $100 or more in Bitcoin and receive $10 in bitcoin free! That’s an automatic 10% return on investment! Click here to sign up!
2021 Updated mining pools:
Pool Mining: Cudo Miner
ProHashing
—————————————-
Cloud Mining:

HiveOS Administration Software
2018 Update: Currently, mining Dogecoin is unprofitable.
You will never get a block against Litecoin ASIC miners
DON’T MINE, BUY DOGECOIN instead!
Do notmine with a laptop or phone!
Mining Software
Software used to Mine
CGminer 3.7.2 (CPU's, Nvidia and ATI) Latest version of Mining Software for Cpu’s and Gpu’s
Cudaminer (Nvidia) Mining software for Nvidia cards only
Guiminer (Gui-based miner) A graphical interface based mining program
Droidminer An android based miner **be careful with heat**
AMD Catalyst Drivers Graphics Card Drivers for AMD
AMD SDK Download The AMD SDK for GPU’s
Nividia Graphic Card Drivers Drivers for Nvidia cards
Nividia Cuda Download CUDA for Nvidia
Sgminer 4.1.0 Windows Optimized CGminer fork
Cuda Manager (Nvidia) Manager for Nvidia mining
My Web Miner Software for monitoring hash rates remotely
Cgeasy .Bat file manager for CGminer
Radeon Card Tuning Guide ATI GPU Specific Tweaking Guide.
Cuda manager_v12 Failover support manager for Cudaminer
BAMT Reboot Script Auto-reboot script for BAMT/SMOS Linux users
Minerstatus Remote Miner Monitoring Webapp
Asteroid for Mac Mac mining software
Macminer User Friendly Mac Mining software
CGWatcher Excellent Mining Companion to restart and log mining machines. Supports multiple miner profiles. Feed it a .bat file and watch it go.
Karloth CgMiner 3.7.3 mod A forked version of Cgminer used to squeak out a few more kh/s out of your GPU for mining.
Shibeminer – automagic mining software A quick turn-key solution to get you started in mining- Great for beginners!
Gridseed ASIC Mining Software CPUminer 3335 for Gridseed Asic Miners
Dogecoin Core 1.10 Beta 2 Dogecoin Core desktop software Version 1.10 Beta New as of 9/11/15
2016 – 2017 information regarding Mining non-profitability in solo mining Reddit thread on the current (as of 11/16) state of Dogecoin mining. Updated info for new users.
CoreMiner 101 latest dogecoin miner – For Novelty Use Only!!! CoreMiner 101
Solo Mining Dogecoin 2014 Video on Dogecoin Solo Mining.
Cudo Miner Pool Based Scrypt mining pool – Dogecoin supported.
ProHashing (2021) Pool-Based Mining supporting Dogecoin (2021)
Genesis Cloud Mining Cloud based mining supporting Dogecoin
Vertcoin to Doge miner Custom fork of vertcoin miner to pay off in doge.
HiveOS mining Admin Software The BEST HiveOS mining administration platform.
Such Relate
Pages
SPECIAL:
Need to buy more Dogecoin? Open a Coinbase account, buy $100 in Bitcoin and receive $10 in bitcoin free! That’s an automatic return on investment! Click here to sign up!
Best Ethereum Miner For Mac
Doge says: Get a coinbase account, buy crypto, send it to Bittrex to buy DOGE!, and keep it on Exodus wallet!
Need a Miner?
Best Miner Machine For Bitcoin

0 notes
Text
Download Xcode Macos


Download Xcode Macos Sierra
Download Xcode Macos Tutorial
Download Xcode Macos Download
The software development kit, of course, Xcode, is right now only available for macOS. Technically, Xcode can’t be installed on Windows PC because there are compatibility issues, but there are ways to emulate Xcode on Windows 10 via Virtual machine. Currently and officially, Xcode is only available through Mac App Store or iTunes, but still Mac users can download xcode without app store and without Apple ID for free. Although, xCode software is only compatible with macOS, but still Windows users can download, install and run PC version of xcode through virtual machine software like VMware.
With an all-new design that looks great on macOS Big Sur, Xcode 12 has customizable font sizes for the navigator, streamlined code completion, and new document tabs. Xcode 12 builds Universal apps by default to support Mac with Apple Silicon, often without changing a single line of code.
Designed for macOS Big Sur.
Xcode 12 looks great on macOS Big Sur, with a navigator sidebar that goes to the top of the window and clear new toolbar buttons. The navigator defaults to a larger font that’s easier to read, while giving you multiple size choices. New document tabs make it easy to create a working set of files within your workspace.
Document tabs.
The new tab model lets you open a new tab with a double-click, or track the selected file as you click around the navigator. You can re-arrange the document tabs to create a working set of files for your current task, and configure how content is shown within each tab. The navigator tracks the open files within your tabs using strong selection.
Navigator font sizes.
The navigator now tracks the system setting for “Sidebar icon size” used in Finder and Mail. You can also choose a unique font size just for Xcode within Preferences, including the traditional dense information presentation, and up to large fonts and icon targets.
Code completion streamlined.
A new completion UI presents only the information you need, taking up less screen space as you type. And completions are presented much faster, so you can keep coding at maximum speed.
Oct 25, 2017 I've been using CleanMyMac for some years now because of its Verify Startup Disk tool, which may give you a clue why your Mac is not booting up. Verify Startup Disk tool, which may give you a clue why your Mac is not booting up. Launch CleanMyMac (you can get its free version here) 2. Click section 'Maintenance' 3. Check 'Verify startup disk' 3. Cleanmymac activation number 2020 reddit. Google Sketchup Pro 2019 Crack is a 3D graphics designing program. This program is beneficial to the architectures as they use it to design the interior and exterior designs giving the best images. The user can surely generate any serial key such as activation, license, registration or serial key. Universal Keygen Generator 2018 Serial Key is suitable for all operating system Windows Vista, XP, 8,7,8.1 and also on windows 10.
Redesigned organizer.
An all-new design groups all critical information about each of your apps together in one place. Choose any app from any of your teams, then quickly navigate to inspect crash logs, energy reports, and performance metrics, such as battery consumption and launch time of your apps when used by customers.

SwiftUI
SwiftUI offers new features, improved performance, and the power to do even more, all while maintaining a stable API that makes it easy to bring your existing SwiftUI code forward into Xcode 12. A brand new life cycle management API for apps built with SwiftUI lets you write your entire app in SwiftUI and share even more code across all Apple platforms. And a new widget platform built on SwiftUI lets you build widgets that work great on iPad, iPhone, and Mac. Your SwiftUI views can now be shared with other developers, and appear as first-class controls in the Xcode library. And your existing SwiftUI code continues to work, while providing faster performance, better diagnostics, and access to new controls.
Download Xcode Macos Sierra
Universal app ready.
Xcode 12 is built as a Universal app that runs 100% natively on Intel-based CPUs and Apple Silicon for great performance and a snappy interface.* It also includes a unified macOS SDK that includes all the frameworks, compilers, debuggers, and other tools you need to build apps that run natively on Apple Silicon and the Intel x86_64 CPU.
Updated automatically
When you open your project in Xcode 12, your app is automatically updated to produce release builds and archives as Universal apps. When you build your app, Xcode produces one binary “slice” for Apple Silicon and one for the Intel x86_64 CPU, then wraps them together as a single app bundle to share or submit to the Mac App Store. You can test this at any time by selecting “Any Mac” as the target in the toolbar.
Test multiple architectures.
On the new Mac with Apple Silicon, you can run and debug apps running on either the native architecture or on Intel virtualization by selecting “My Mac (Rosetta)” in the toolbar.
Multiplatform template
New multiplatform app templates set up new projects to easily share code among iOS, iPadOS, and macOS using SwiftUI and the new lifecycle APIs. The project structure encourages sharing code across all platforms, while creating special custom experiences for each platform where it makes sense for your app.
Improved auto-indentation
Swift code is auto-formatted as you type to make common Swift code patterns look much better, including special support for the “guard” command.
StoreKit testing
New tools in Xcode let you create StoreKit files that describe the various subscription and in-app purchase products your app can offer, and create test scenarios to make sure everything works great for your customers — all locally testable on your Mac.
Get started.
Download Xcode 12 and use these resources to build apps for all Apple platforms.
Newsletter
Subscribe to our Threatpost Today newsletter
Join thousands of people who receive the latest breaking cybersecurity news every day.
Download macOS Catalina 10.15 Torrent File - macOS Catalina 10.15 virtual or VMDK file Torrent download to install on Virtualbox or VMWare. Torrent client for mac os catalina. BitTorrent offers free torrent clients for Mac computers, including web-based and desktop applications. Choose the best BitTorrent Mac client and download. Bit torrent and Utorrent are both broken. Someone knows and alternative.
Download Xcode Macos Tutorial
The administrator of your personal data will be Threatpost, Inc., 500 Unicorn Park, Woburn, MA 01801. Detailed information on the processing of personal data can be found in the privacy policy. In addition, you will find them in the message confirming the subscription to the newsletter.
Infosec Insider Post
Infosec Insider content is written by a trusted community of Threatpost cybersecurity subject matter experts. Each contribution has a goal of bringing a unique voice to important cybersecurity topics. Content strives to be of the highest quality, objective and non-commercial.

Sponsored Content
Download Xcode Macos Download
Sponsored Content is paid for by an advertiser. Sponsored content is written and edited by members of our sponsor community. This content creates an opportunity for a sponsor to provide insight and commentary from their point-of-view directly to the Threatpost audience. The Threatpost editorial team does not participate in the writing or editing of Sponsored Content.
Download macOS Catalina 10.15- If the user currently has macOS Catalina’s predecessor macOS Mojave running on their Mac, they can proceed to the System Preferences which can be found under their Apple Menu and update their OS version directly. If they do not possess this macOS, they can download macOS Catalina from the App Store. Mac os catalina installer app download. Download Adobe Photoshop CC 2019 for Mac Free. Click on below button to start Adobe Photoshop CC 2019 Download for Mac OS X. This is completely Tested and Working Latest Version Mac OS App of Adobe Photoshop CC 2019. It is offline installer and standalone setup for Adobe Photoshop CC 2019 for Apple Macbook Macintosh. Mac OS puma or the Mac OS X 10.1 is one of the most speculating operating system released in the Mac OS X lineage. Apple released a lot of operating systems under the same line of operating systems. Download Mac OS X 10.1 Puma.

0 notes
Text
Microsoft Visual 2015

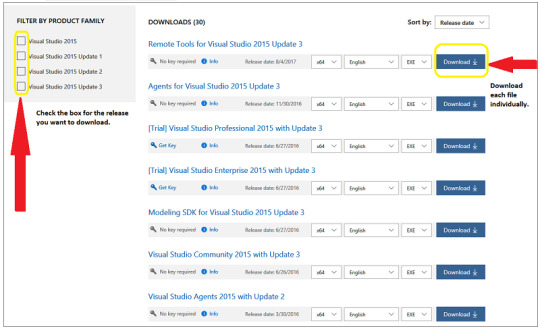
Microsoft Visual 2015 Redistribution
Microsoft Visual 2015 Redistributable X64
Microsoft Visual 2015 32-bit
Microsoft Visual 2015-2019
Microsoft Visual 2015
Microsoft Visual 2015 C++
Jun 02, 2016 Microsoft Visual C 2015 Redistributable includes bug fixes to the runtime DLLs and also the latest versions for KB 2999226. To find out what's new in Visual Studio 2015 Update 3 RC, see the Visual Studio 2015 Update 3 RC Release Notes. For a list of fixed bugs and known issues, see the Visual Studio 2015 Update 3 RC MSDN Article. The Visual Studio Shell is available for Visual Studio 2015, Visual Studio 2013, Visual Studio 2012, and Visual Studio 2010. It is not available for Visual Studio 2017, Visual Studio 2019, or later versions. To access the Visual Studio Shell downloads and documentation, you must accept the Microsoft Software License Terms below.
Microsoft Visual C 2015-2019 redistributable x64 7 Anyone know were I can get a copy of this exact version of MS Visual? Microsoft Visual C 2015 Redistributable includes bug fixes to the runtime DLLs and also the latest versions for KB 2999226. Right-click on the following link to copy or bookmark this download: Microsoft Visual C 2015 Redistributable Update 3. Single slit diffraction examples. Visual Studio IDE Visual Studio for Mac Visual Studio Code To continue downloading, click here Visual Studio 2015 Support Visual Studio 2020-11-18T14:47:52-08:00.
-->
Microsoft Visual 2015 Redistribution
Visual Studio 2015 contains many new and exciting features to support cross-platform mobile development, web and cloud development, IDE productivity enhancements, and more.
System Requirements
The system requirements for Visual Studio 2015 can be found on the Visual Studio 2015 System Requirement page.
Platform Targeting
Microsoft Visual 2015 Redistributable X64
Visual Studio provides cutting-edge tools and technologies to create apps that take advantage of the latest platforms capabilities. Visual Studio 2015 also targets earlier platforms such as Windows 7, so you can create new apps or modernize existing apps that execute on earlier versions of Windows while leveraging the enhanced development tools, quality enablement, and team collaboration capabilities in Visual Studio 2015. For more information, see Managing Project References and Visual Studio Multi-Targeting Overview.
Visual Studio 2015 Support for Windows Desktop Development
Targeted Platform1Native Code DevelopmentManaged Code DevelopmentWindows 10✔️2✔️2Windows 8.1✔️2✔️2Windows 8✔️2✔️2Windows 7✔️✔️Windows Vista✔️3✔️3Windows XP✔️3✔️3, 5Windows Server 2012 R2✔️2✔️2Windows Server 2012✔️✔️Windows Server 2008 R2✔️✔️Windows Server 2008✔️✔️Windows Server 2003✔️3✔️4, 5Footnotes: 1. Visual Studio supports the listed platforms when used with the latest available service pack for that platform. For more information, see Microsoft Support Lifecycle. 2. See table below for Visual Studio 2015 support for Windows Universal and Windows Store app development. 3. Remote debugging and profiling tools not available for targeted platform. 4. Requires side-by-side installation of Visual Studio 2010. For more information, see: A Look Ahead at the Visual Studio 2012 Product Lineup and Platform Support. 5. Requires using Visual Studio managed multi-targeting.
Visual Studio 2015 Support for Windows Universal, Windows Store, and Windows Phone App Development
You can create Windows Universal, Windows Store, and Windows Phone apps with the following editions of Visual Studio 2015.
Visual Studio 2015 EditionInstalled OS for DevelopmentWindows UniversalWindows Store apps for Windows 8.1Windows Phone 8.1 appsWindows Store apps for Windows 8Windows Phone 8 appsEnterprise, Professional, CommunityWindows 10✔️✔️2✔️Not Supported 3✔️4, 5Enterprise, Professional, CommunityWindows 8.1✔️1✔️2✔️Not Supported 3✔️4, 5Enterprise, Professional, CommunityWindows Server 2012 R2Build onlyBuild only 2Build onlyNot supportedBuild onlyEnterprise, Professional, CommunityWindows 8✔️1Not supportedNot supportedNot Supported✔️5Enterprise, Professional, CommunityWindows Server 2012Build onlyNot supportedNot supportedNot supportedBuild onlyEnterprise, Professional, CommunityWindows 7Build onlyNot supportedNot supportedNot supportedNot supportedExpress for Windows 10Windows 10✔️Not supportedNot supportedNot supportedNot supportedFootnotes: 1. When running on OS earlier than Windows 10, some Visual Studio features for Windows Universal development may be degraded. 2. Includes support for remote debugging to Windows 8.1. 3. Visual Studio 2015 supports migration of Windows Store app projects from Windows 8 to Windows 8.1. Existing Windows 8 projects may be maintained with Visual Studio 2013, including remote debugging to Windows 8.1 and Windows 8. Use Visual Studio 2012 to create new Windows 8 projects. 4. Visual Studio 2015 supports migration of Windows Phone 7 and 7.5 projects to Windows Phone 8. 5. Supports migration of Windows Phone 8 projects to Windows Phone Silverlight 8.1.
Compatibility with Previous Releases
Windows Store app projects for Windows 8.1 and Windows Phone 8.1 can be opened in Visual Studio 2015.
Microsoft visual studio java. You can install and use Visual Studio 2015 alongside Visual Studio 2013 and Visual Studio 2012. It can also be installed on top of Visual Studio 2015 RC without having to uninstall RC.
.NET 4.6 is a highly compatible in-place update of .NET 4, .NET 4.5, .NET 4.5.1, and .NET 4.5.2. See Application Compatibility in the .NET Framework for more information on .NET compatibility.
Upgrade paths
When following the supported upgrade paths, your Visual Studio source, solution, and project files will continue to work; however, you should expect to make some changes to sources. While we cannot guarantee binary compatibility between releases, we will do our best to document significant changes to assist you with updates.
Release Management upgrade paths
Release Management 2015 is a full layout that includes the latest feature additions and software updates. Before you try to upgrade to Release Management 2015, make sure that you have a full backup of your current databases and RSA crypto key (see this blog post for RSA crypto keys export instructions). If the Release Management installation fails, you will be unable to restart the update or roll back to the earlier version of Release Management without performing a restore operation.
The following upgrade paths apply to this release.
Supported upgrades
Release Management for Visual Studio 2013 to Release Management for Visual Studio 2015
Release Management for Visual Studio 2013 Update 4 to Release Management for Visual Studio 2015
Release Management for Visual Studio 2015 RC to Release Management for Visual Studio 2015
Microsoft Visual 2015 32-bit
Top of Page-->
Visual Studio 2015 contains many new and exciting features to support cross-platform mobile development, web and cloud development, IDE productivity enhancements, and more.
System Requirements
The system requirements for Visual Studio 2015 can be found on the Visual Studio 2015 System Requirement page.
Platform Targeting
Visual Studio provides cutting-edge tools and technologies to create apps that take advantage of the latest platforms capabilities. Visual Studio 2015 also targets earlier platforms such as Windows 7, so you can create new apps or modernize existing apps that execute on earlier versions of Windows while leveraging the enhanced development tools, quality enablement, and team collaboration capabilities in Visual Studio 2015. For more information, see Managing Project References and Visual Studio Multi-Targeting Overview.
Visual Studio 2015 Support for Windows Desktop Development
Targeted Platform1Native Code DevelopmentManaged Code DevelopmentWindows 10✔️2✔️2Windows 8.1✔️2✔️2Windows 8✔️2✔️2Windows 7✔️✔️Windows Vista✔️3✔️3Windows XP✔️3✔️3, 5Windows Server 2012 R2✔️2✔️2Windows Server 2012✔️✔️Windows Server 2008 R2✔️✔️Windows Server 2008✔️✔️Windows Server 2003✔️3✔️4, 5Footnotes: 1. Visual Studio supports the listed platforms when used with the latest available service pack for that platform. For more information, see Microsoft Support Lifecycle. 2. See table below for Visual Studio 2015 support for Windows Universal and Windows Store app development. 3. Remote debugging and profiling tools not available for targeted platform. 4. Requires side-by-side installation of Visual Studio 2010. For more information, see: A Look Ahead at the Visual Studio 2012 Product Lineup and Platform Support. 5. Requires using Visual Studio managed multi-targeting.
Visual Studio 2015 Support for Windows Universal, Windows Store, and Windows Phone App Development

You can create Windows Universal, Windows Store, and Windows Phone apps with the following editions of Visual Studio 2015.
Microsoft Visual 2015-2019
Visual Studio 2015 EditionInstalled OS for DevelopmentWindows UniversalWindows Store apps for Windows 8.1Windows Phone 8.1 appsWindows Store apps for Windows 8Windows Phone 8 appsEnterprise, Professional, CommunityWindows 10✔️✔️2✔️Not Supported 3✔️4, 5Enterprise, Professional, CommunityWindows 8.1✔️1✔️2✔️Not Supported 3✔️4, 5Enterprise, Professional, CommunityWindows Server 2012 R2Build onlyBuild only 2Build onlyNot supportedBuild onlyEnterprise, Professional, CommunityWindows 8✔️1Not supportedNot supportedNot Supported✔️5Enterprise, Professional, CommunityWindows Server 2012Build onlyNot supportedNot supportedNot supportedBuild onlyEnterprise, Professional, CommunityWindows 7Build onlyNot supportedNot supportedNot supportedNot supportedExpress for Windows 10Windows 10✔️Not supportedNot supportedNot supportedNot supportedFootnotes: 1. When running on OS earlier than Windows 10, some Visual Studio features for Windows Universal development may be degraded. 2. Includes support for remote debugging to Windows 8.1. 3. Visual Studio 2015 supports migration of Windows Store app projects from Windows 8 to Windows 8.1. Existing Windows 8 projects may be maintained with Visual Studio 2013, including remote debugging to Windows 8.1 and Windows 8. Use Visual Studio 2012 to create new Windows 8 projects. 4. Visual Studio 2015 supports migration of Windows Phone 7 and 7.5 projects to Windows Phone 8. 5. Supports migration of Windows Phone 8 projects to Windows Phone Silverlight 8.1.
Compatibility with Previous Releases
Windows Store app projects for Windows 8.1 and Windows Phone 8.1 can be opened in Visual Studio 2015. Vegplotter app.
You can install and use Visual Studio 2015 alongside Visual Studio 2013 and Visual Studio 2012. It can also be installed on top of Visual Studio 2015 RC without having to uninstall RC.
.NET 4.6 is a highly compatible in-place update of .NET 4, .NET 4.5, .NET 4.5.1, and .NET 4.5.2. See Application Compatibility in the .NET Framework for more information on .NET compatibility.
Microsoft Visual 2015
Upgrade paths
When following the supported upgrade paths, your Visual Studio source, solution, and project files will continue to work; however, you should expect to make some changes to sources. While we cannot guarantee binary compatibility between releases, we will do our best to document significant changes to assist you with updates.
Release Management upgrade paths
Microsoft Visual 2015 C++
Release Management 2015 is a full layout that includes the latest feature additions and software updates. Before you try to upgrade to Release Management 2015, make sure that you have a full backup of your current databases and RSA crypto key (see this blog post for RSA crypto keys export instructions). If the Release Management installation fails, you will be unable to restart the update or roll back to the earlier version of Release Management without performing a restore operation.
The following upgrade paths apply to this release. https://neuroloading498.tumblr.com/post/659039631628746752/dockmate-twist-price.
Supported upgrades
Release Management for Visual Studio 2013 to Release Management for Visual Studio 2015
Release Management for Visual Studio 2013 Update 4 to Release Management for Visual Studio 2015
Release Management for Visual Studio 2015 RC to Release Management for Visual Studio 2015
Top of Page

0 notes
Text
Java Macbook Pro Download

Java 8 Download For Macbook Pro
Java Download For Macbook Pro
Sometimes the lines between macOS and Windows 10 seem like a war zone of proponents from either side arguing about graphics, user interface, and program availability. But what if you just want the best of both worlds?
As many of us know, it’s the little things that make us wish we could switch back and forth between the two operating systems. Whether it’s that one program you need for work or your favorite video game that isn’t cross-platform compatible, it’s high time you find a way to be able to continue using your gorgeous MacBook Pro without making sacrifices around the edges.
Download the Java SE 6 for OSX (click the Download button) Once the download finishes, install the dmg file following the onscreen instructions. When you have Java Runtime 6 installed on your Mac, you can launch Adobe CS5 (or any other app that require Java 6 runtime). Note: You DO NOT need to restart your Mac before launching the app.
Setting Up A MacBook Pro for Java Development Read this wonderful primer for developers switching to the 'dark' side and acquiring a MacBook Pro. It includes some tips for the German/Swiss keyboard.
This may be tough as Java 6 on the Mac was only provided by Apple. Oracle/Open JDK didn't take over to providing binaries until Java 7. Do you specifically need Java 6 or can you run it with a later version of Java? Isolating Java is a bit more complex now that Apple has removed the Java preferences utility from Lion and Mountain Lion. If you run Java 6 (the Apple supplied version), you need to restrict it on.
Can I run Windows 10 on My MacBook Pro?
The short answer to this question is yes, you certainly can.
The longer version? To do so, you’re going to need to spend a fair amount of time setting this up and deciding which method of doing so is most effective for you.
Why won't my iphone photos download to my macbook pro 2017. Also, no option is going to be seamless – you will probably lose some performance power due to the way built-in optimization software works.
Is Windows 10 free for Mac?
Unfortunately, if you want to run Windows 10 on your Mac, you’ll need to purchase a license from Microsoft.
If you’ve used a PC in the past, you may not be familiar with this since Windows tends to come preinstalled. But in the same way, as if you were building your computer from the ground up or if you were updating an extremely outdated laptop, you’ll need to buy a copy of Windows 10.
This can be done electronically from the Microsoft Store here, where you’ll receive a product key and download, or you can choose to receive a copy via physical USB. Windows 10 Home starts at about $120, and the Pro version costs about $200. However, both are still cheaper than trying to buy an entirely new computer just to run a few of your favorite things.
Running Windows 10 on MacBook Pro
Once you have a copy of Windows 10 in your possession, it’s time to pick a method for installation. There are two main ways to do this: creating a partition on your Mac with the built-in Boot Camp program or using a third-party virtual machine that creates a tiny version of the Windows OS on top of the normal Mac system. We’ll guide you through both of these.
Method 1: Boot Camp
Bootcamp is preinstalled on your Mac, but most people use their MacBook without ever realizing it’s there. To find it, simply search in Spotlight for “Bootcamp”, and it should come up right away.
When you use BootCamp, your Mac’s hard drive will be split into two sections- one running Windows, and one running macOS. These means that they operate in completely separate spheres and cannot interact with each other. Additionally, the size of the partition you create cannot be changed unless you perform a fresh install to reset it.
Pros:
Already built into Mac, so it’s the safest and easiest option to run Windows.
You’ll experience the least performance loss.
It will feel like you’re running a completely new computer.
Cons:
Not that convenient because your MacBook must be rebooted to switch between Windows 10 and macOS.
Partition size is semi-permanent, and cannot be resized without some considerable effort to re-install and repartition.
Transferring files between the two systems is like transferring between two totally separate computers- you’ll need to share them by flash drive (see the best usb-c drive for MacBook Pro), email, or some other method that isn’t just drag-and-drop.
Macbook pro openvpn connect download pc. Using BootCamp
To use BootCamp, you’ll need to follow a few basic steps:
Obtain a copy of Windows 10 (as previously mentioned)
Make sure your entire MacBook is up to date by checking for any software updates
Open BootCamp from Spotlight
Partition your hard drive
Install Windows & Windows Drivers
Choose which OS to run and get started!
For a more detailed version of this overview, you’ll want to check out PCMag’s BootCamp walkthrough or head for the official Apple Guide.
Method 2: Virtual Machines
If the idea of rebooting your computer to switch OS doesn’t appeal to you, a virtual machine is always an option. These are ideal in situations where you only need one program or don’t plan on doing many taxing operations on Windows.
In a virtual machine, Windows 10 runs inside an application so it’s like having another computer, but confined inside a single window on your screen. This means you can work in both Mac and Windows at the same time but may suffer a bit from performance issues.
Pros:
It’s much more convenient than rebooting your computer to use Windows.
You can change the size of the partition whenever you want.
You can use files between operating systems easily.
Cons:
You’ll need to buy a software license for your virtualization machine in addition to a copy of Windows.
You may notice some drop in performance than if you dual-boot.
When it comes to virtual machines, you have a few options, each with their own benefits and drawbacks.
The most well-known programs are Parallels Desktop for Mac and VMWare Fusion, which provide almost identical functionality with a few minor differences (such as display resolution or Quick Look support) that won’t make or break your decision. They are priced at the same level for a single computer license and similar setup options. Fusion tends to outperform Parallels, but Parallels is a bit more user-friendly.

A third, lesser-known option is VirtualBox. This software is free, but it doesn’t come with the bells and whistles of its competitors. It doesn’t have the same optimization power or even offers a similar variety of setup options, and it tends to be on the techier side, making it difficult to use if you aren’t invested in learning how (you may be interested in this book: An Ultimate Guide Book on Virtualization with VirtualBox). But if you just need to try out virtualization, it’s a great place to start.
Using a Virtual Machine
Java 8 Download For Macbook Pro
To use a virtual machine, you’ll need to go through a similar amount of setup as Bootcamp, but the process varies more depending on which software you’ve chosen.
Java Download For Macbook Pro
Obtain a copy of Windows 10 (as mentioned above)
Also, purchase a license for the software you have chosen
Create a virtual machine. This process varies by program, but it’s the first thing you need to do before attempting to run any programs
Install Windows to the Virtual Machine
If you’ve chosen to use Parallels, this guide includes images and should be sufficient to get through the installation process. For VMWare Fusion, their support page includes both a video and text-based tutorial for installation. Those who opt for VirtualBox can follow LifeHacker’s guide to setup since this program’s installation includes a plethora of personalization options you may not be sure what to do with.
Final Words
Running Windows on a MacBook Pro means you get to have your cake and eat it too. It’s a great compromise between systems that let you do the work you need to while sticking with the operating system you know best. While you may see some performance loss and it won’t be quite the same as having a computer completely dedicated to Windows, you do have a variety of options to work with what you’ve got.
How do you use Windows 10 on your Mac? Tell us about your experience by leaving a comment below.

0 notes
Text
Neo4j Python
要通过python来操作Neo4j,首先需要安装py2neo,可以直接使用pip安装。 pip install py2neo 在完成安装之后,在python中调用py2neo即可,常用的有Graph,Node,Relationship。 from py2neo import Graph,Node,Relationship 连接Neo4j的方法很简单:. The Python Driver 1.7 supports older versions of python, Neo4j 4.1 will work in fallback mode with that driver. Neo4j Cypher Tutorial With Python. In this course student will learn what is graph database, how it is different from traditional relational database, why graph database is important today, what is neo4j, why neo4j is the best graph database available in the market, students will also get the idea about cypher query and uses of cypher query(all CRUD operations and complete sets of uses cases.
Neo4j Python Book
Neo4jDeveloper(s)Neo4jInitial release2007; 14 years ago(1)Stable releaseRepositoryWritten inJavaTypeGraph databaseLicense
Source code:GPLv3 and AGPLv3
Binaries:Freemiumregisterware
Websiteneo4j.com
Neo4j (Network Exploration and Optimization 4 Java) is a graph database management system developed by Neo4j, Inc. Described by its developers as an ACID-compliant transactional database with native graph storage and processing,(3) Neo4j is available in a GPL3-licensed open-source 'community edition', with online backup and high availability extensions licensed under a closed-source commercial license.(4) Neo also licenses Neo4j with these extensions under closed-source commercial terms.(5)
Neo4j is implemented in Java and accessible from software written in other languages using the Cypher query language through a transactional HTTP endpoint, or through the binary 'bolt' protocol.(6)(7)(8)(9)
History(edit)
Version 1.0 was released in February 2010.(10)
Neo4j version 2.0 was released in December 2013.(11)
Neo4j version 3.0 was released in April 2016.(12)
In November 2016 Neo4j successfully secured $36M in Series D Funding led by Greenbridge Partners Ltd.(13)
In November 2018 Neo4j successfully secured $80M in Series E Funding led by One Peak Partners and Morgan Stanley Expansion Capital, with participation from other investors including Creandum, Eight Roads and Greenbridge Partners.(14)
Release history(edit)
Release historyReleaseFirst release(15)Latest
minor version(16)
Latest release(16)End of Support Date(15)Milestones1.02010-02-23Old version, no longer maintained: 1.0N/A2011-08-23Kernel, Index, Remote-graphdb, Shell(17)1.12010-07-30Old version, no longer maintained: 1.1N/A2012-01-30Graph-algo, Online-backup(17)1.22010-12-29Old version, no longer maintained: 1.2N/A2012-06-29Server including Web Admin, High Availability, Usage Data Collection(17)1.32011-04-12Old version, no longer maintained: 1.3N/A2012-09-12Neo4j Community now licensed under GPL, 256 Billion database primitives, Gremlin 0.8(17)1.42011-07-08Old version, no longer maintained: 1.4N/A2013-01-08The first iteration of the Cypher Query Language, Experimental support for batch operations in REST1.52011-11-09Old version, no longer maintained: 1.5N/A2013-03-09Store Format Change, Added DISTINCT to all aggregate functions in Cypher,
New layout of the property store(s), Upgraded to Lucene version 3.5(17)
1.62012-01-22Old version, no longer maintained: 1.6N/A2013-07-22Cypher allShortestPaths, management bean for the diagnostics logging SPI, gremlin 1.4(17)1.72012-04-18Old version, no longer maintained: 1.7N/A2013-10-18Moved BatchInserter to a different package, lock free atomic array cache, GC monitor(17)1.82012-09-28Old version, no longer maintained: 1.8N/A2014-03-28Bidirectional traversals, Multiple start nodes(17)1.92013-05-21Old version, no longer maintained: 1.9.92014-10-132014-11-21Performance improvement on initial loading of relationship types during startup,
Pulled out Gremlin as separate plugin to support different versions(17)
2.02013-12-11Old version, no longer maintained: 2.0.42014-07-082015-06-11Extending model to “labeled” property graph and introduced visual IDE(17)(18)2.12014-05-29Old version, no longer maintained: 2.1.82015-04-012015-11-29Cypher new cost based planner, Fixes issue in ReferenceCache, potential omission, potential lock leak(17)2.22015-03-25Old version, no longer maintained: 2.2.102016-06-162016-09-25Massive Write Scalability, Massive Read Scalability, Cost-based query optimizer,
Query plan visualization(19)
2.32015-10-21Old version, no longer maintained: 2.3.122017-12-122017-04-21Break free of JVM-imposed limitations by moving the database cache off-heap,
Spring Data Neo4j 4.0, Neo4j-Docker Image, Windows Powershell Support, Mac Installer, and Launcher(20)
3.02016-04-16Old version, no longer maintained: 3.0.122017-10-032017-10-31user-defined/stored procedures called APOC (Awesome Procedures on Cypher),
Bolt binary protocol, in-house language drivers for Java, .NET, JavaScript and Python(21)(18)
3.12016-12-13Old version, no longer maintained: 3.1.92018-06-052018-06-13Causal Clustering, Enterprise-Class Security and Control, User-Defined Functions,
Neo4j IBM POWER8 CAPI Flash, User and role-based security and directory integrations(22)(18)
3.22017-05-11Old version, no longer maintained: 3.2.142019-02-262018-11-31Multi-Data Center Support, Causal Clustering API, Compiled Cypher Runtime, Node Keys,
Query Monitoring, Kerberos Encryption, Clustering on CAPI Flash, Schema constraints,
new indexes and new Cypher editor with syntax highlights and autocompletion(23)(18)
3.32017-10-24Old version, no longer maintained: 3.3.92018-11-022019-04-28Write performance is 55% faster than Neo4j 3.2, Neo4j Data Lake Integrator toolkit, Neo4j ETL(24)3.42018-05-17Old version, no longer maintained: 3.4.172019-11-192020-03-31Multi-Clustering, New Data Types for Space and Time, Performance Improvements(25)3.52018-11-29Older version, yet still maintained: 3.5.282021-04-202021-11-28Native indexing, Full-text search, The recommended index provider to use is native-btree-1.0(26)4.02020-01-15Older version, yet still maintained: 4.0.112021-01-112021-07-14Java 11 is required, Multiple databases, Internal metadata repository “system” database,
Schema-based security and Role-Based Access Control, Role and user management capabilities,
Sharding and federated access, A new neo4j:// scheme(27)(28)
4.12020-06-23Older version, yet still maintained: 4.1.82021-03-192021-12-23Graph privileges in Role-Based Access Control (RBAC) security, Database privileges for transaction management, Database management privileges, PUBLIC built-in role, Cluster Leadership Control, Cluster Leadership Balancing, Cypher Query Replanning Option, Cypher PIPELINED Runtime operators, Automatic routing of administration commands(29)4.22020-11-17Current stable version:4.2.5 2021-04-092022-05-16(Administration) ALIGNED store format, Procedures to observe the internal scheduler, Dynamic settings at startup, WAIT/NOWAIT in Database Management, Index and constraint administration commands, Filtering in SHOW commands, Backup/Restore improvements, Compress metrics on rotation, Database namespace for metrics, neo4j-admin improvements, HTTP port selective settings (Causal Cluster) Run/Pause Read Replicas, Database quarantine (Cypher) Planner improvements, Octal literals (Functions and Procedures) round() function, dbms.functions() procedure (Security) Procedures and user defined function privileges, Role-Based Access Control Default graph, PLAINTEXT and ENCRYPTED password in user creation, SHOW CURRENT USER, SHOW PRIVILEGES as commands, OCSP stapling support for Java driver(30)
Old version
Latest version
Future release
Licensing and editions(edit)
Neo4j comes in 2 editions: Community and Enterprise. It is dual-licensed: GPL v3 and a commercial license. The Community Edition is free but is limited to running on one node only due to the lack of clustering and is without hot backups.(31)
The Enterprise Edition unlocks these limitations, allowing for clustering, hot backups, and monitoring. The Enterprise Edition is available under a closed-source Commercial license.
Data structure(edit)
In Neo4j, everything is stored in the form of an edge, node, or attribute. Each node and edge can have any number of attributes. Both nodes and edges can be labelled. Labels can be used to narrow searches. As of version 2.0, indexing was added to Cypher with the introduction of schemas.(32) Previously, indexes were supported separately from Cypher.(33)
Neo4j, Inc.(edit)
Neo4j is developed by Neo4j, Inc., based in the San Francisco Bay Area, United States, and also in Malmö, Sweden. The Neo4j, Inc. board of directors consists of Michael Treskow (Eight Roads), Emmanuel Lang (Greenbridge), Christian Jepsen, Denise Persson (CMO of Snowflake), David Klein (One Peak), and Emil Eifrem (CEO of Neo4j).(34)
See also(edit)
References(edit)
^Neubauer, Peter (@peterneubauer) (17 Feb 2010). '@sarkkine #Neo4j was developed as part of a CMS SaaS 2000-2007, became released OSS 2007 when Neo Technology spun out' (Tweet) – via Twitter.
^https://neo4j.com/release-notes/neo4j-4-2-5/.
^Neo Technology. 'Neo4j Graph Database'. Retrieved 2015-11-04.
^Philip Rathle (November 15, 2018). 'Simplicity Wins: We're Shifting to an Open Core Licensing Model for Neo4j Enterprise Edition'. Retrieved 2019-01-16.
^Emil Eifrem (April 13, 2011). 'Graph Databases, Licensing and MySQL'. Archived from the original on 2011-04-26. Retrieved 2011-04-29.
^'Bolt Protocol'.
^Todd Hoff (June 13, 2009). 'Neo4j - a Graph Database that Kicks Buttox'. High Scalability. Possibility Outpost. Retrieved 2010-02-17.
^Gavin Terrill (June 5, 2008). 'Neo4j - an Embedded, Network Database'. InfoQ. C4Media Inc. Retrieved 2010-02-17.
^'5.1. Transactional Cypher HTTP endpoint'. Retrieved 2015-11-04.
^'The top 10 ways to get to know Neo4j'. Neo4j Blog. February 16, 2010. Retrieved 2010-02-17.
^'Neo4j 2.0 GA - Graphs for Everyone'. Neo4j Blog. December 11, 2013. Retrieved 2014-01-10.
^'Neo4j 3.0.0 - Neo4j Graph Database Platform'. Release Date. April 26, 2016. Retrieved 2020-04-23.
^'Neo Technology closes $36 million in funding as graph database adoption soars'. SiliconANGLE. Retrieved 2016-11-21.
^'Graph database platform Neo4j locks in $80 mln Series E'. PE Hub Wire. Archived from the original on 2019-04-26. Retrieved 2018-11-01.
^ ab'Neo4j Supported Versions'. Neo4j Graph Database Platform. Retrieved 2020-11-26.
^ ab'Release Notes Archive'. Neo4j Graph Database Platform. Retrieved 2021-04-20.
^ abcdefghijk'neo4j/neo4j'. GitHub. Retrieved 2020-01-28.
^ abcd'Neo4j Open Source Project'. Neo4j Graph Database Platform. Retrieved 2020-01-28.
^'Neo4j 2.2.0'. Neo4j Graph Database Platform. Retrieved 2020-01-28.
^'Neo4j 2.3.0'. Neo4j Graph Database Platform. Retrieved 2020-01-28.
^'Neo4j 3.0.0'. Neo4j Graph Database Platform. Retrieved 2020-01-28.
^'Neo4j 3.1.0'. Neo4j Graph Database Platform. Retrieved 2020-01-28.
^'Neo4j 3.2.0'. Neo4j Graph Database Platform. Retrieved 2020-01-28.
^'Neo4j 3.3.0'. Neo4j Graph Database Platform. Retrieved 2020-01-28.
^'Neo4j 3.4.0'. Neo4j Graph Database Platform. Retrieved 2020-01-28.
^'Neo4j 3.5.0'. Neo4j Graph Database Platform. Retrieved 2020-01-28.
^'Neo4j 4.0.0'. Neo4j Graph Database Platform. Retrieved 2020-01-28.
^'2.1. System requirements - Chapter 2. Installation'. neo4j.com. Retrieved 2020-01-28.
^'Neo4j 4.1.0'. Neo4j Graph Database Platform. Retrieved 2020-06-23.
^'Neo4j 4.2.0'. Neo4j Graph Database Platform. Retrieved 2020-11-26.
^'The Neo4j Editions'.
^'The Neo4j Manual v2.1.5'.
^'The Neo4j Manual v1.8.3'.
^Neo4j. 'Staff - Neo4j Graph Database'. Retrieved 2020-06-19.
External links(edit)
Official website
Neo4j Python Book
Retrieved from 'https://en.wikipedia.org/w/index.php?title=Neo4j&oldid=1020554218'
0 notes
Text
Iris publishers-Online Journal of Complementary & Alternative Medicine (OJCAM)
Visualizing Traditional Chinese Medicine and Information Representation and Retrieval: Opportunities and Challenges in a New Era of Big Data
Authored by David C Mainenti*
Abstract
Computer-based medical diagnostic systems have seen tremendous growth since the 1950s, particularly with the arrival of personal computers, the Internet, portable devices, and big data analytical environments. Such technologies utilize the fundamental principles of information representation and retrieval (IRR) to solve complex questions pertaining to health and disease. However, since inception, such systems have virtually ignored traditional Chinese medicine (TCM) techniques, oftentimes due to their lack of success in randomized controlled trials. To this day, little is known about how TCM works scientifically and, yet, it remains an essential part of the world’s healthcare system, particularly in several Asian countries. As disease remains widespread across society, the diagnostic and treatment methods of TCM should be compared alongside Western medical models, in light of modern IRR techniques, to determine if a new, futuristic form of translational medicine can be developed that improves medical outcomes and reduces health care costs worldwide. This study analyzes all published research in SCOPUS relating to TCM and IRR for the period 1985-2020 and employs bibliometric techniques, multiple correspondence analysis, and data visualizations to investigate author productivity, collaborations, and research trends. Opportunities and challenges were discovered that will help identify future directions within the field as we enter a new era of data-intensive scientific discovery in medicine.
Keywords:Bibliometrics; Computer-based medical diagnostic systems; Data visualization; Herbal pharmaceutical technology; Multiple correspondence analysis; Traditional Chinese medicine; Information retrieval
Abbreviations:IRR: Information Representation and Retrieval; TCM: Traditional Chinese Medicine; IoT: Internet of Things; AI: Artificial Intelligence; ISO: International Organization for Standardization
The Ecological Model
Since its creation thousands of years ago [1], scholars of traditional Chinese medicine (TCM) have provided a wide variety of resources for biomedical and health science, comprised of published literature, medicinal materials, herbs, diagnostic matrices, clinical records, medical formularies, and the like. In many ways, the founders of TCM were true pioneers of information science – they identified problems affecting society in their day and consciously searched available data at the time, represented mainly by classical medical literature passed down from the sages of antiquity in chant and song prior to the development of the written record, in addition to plants and other natural substances garnered from the environment [2]. These early medical leaders proceeded to organize and index such information into influential works (e.g., primitive expert knowledge systems) to prevent the spread of epidemic disease so that all those who followed would have retrieval access to a robust decisioning mechanism designed to solve a host of medical issues [3]. These ancient systems, based primarily on natural patterns of disharmony, herbal medical information representation, and treatment models, resemble mathematical thinking based on the presence or absence of human biological information [4] and utilize a binary system of numbers and probabilities that closely identifies with the concept of bits and bytes that form the working principle found in our current computing environment [5].
With the advent of big data analytics, Internet of Things (IoT) technologies, and society’s continued pursuit of optimal health and well-being, the idea of developing computer-aided medical decision-making using artificial intelligence (AI) models to simulate the deductive procedure of disease diagnosis is soon to become a common reality that laid roots down over forty years ago [6]. In the future, Samsung [7] predicts sensors embedded all around us monitoring our health in a continuous manner, linked to one giant AI network, picking up signs of illness, automatically nudging users to make healthier choices, acting as a virtual doctor, directing future medical research but also potentially ranking us and shifting health and life insurance premiums to a pay-as-you-live model. Through the use of information representation and retrieval (IRR) technology, medical data gathered from a multitude of sources can now be gleaned and aggregated with appropriate criteria for use in complex TCM algorithms that bridge gaps currently existing in Western diagnostic practices by imitating classical deductive and reasoning procedures for solving medical problems and recommending treatment protocols [8]. Unfortunately, the complexity of medical knowledge creates a number of IRR difficulties [9] including, but not limited to standardized data formats; formulated inputs; and good feature representation with efficient key factors of the target problem. This is further complicated [10] by the fact that there remains, to this day, no single system able to accurately read the many medical manuscripts written in numerous dialects and stored at different locations all over the world, a literary necessity to ground TCM theory with modern science, due to the historical nature of the medicine. In particular, due to thousands of years of medical development and evolution, regional cultural differences and language variations exist which, while providing a richness and diversity to the TCM terminology system, creates standardization problems with the modernization of this classical medical modality, especially when compared to Western medical systems [11], which also experience similar vocabulary issues. On top of this, the use of natural herbal medicinal and other applications such as acupuncture are widely viewed as experimental by the Western scientific community, due, in part, to the individualistic nature in which such modalities are prescribed to human beings. Moving forward, a shift in research ideology will be required, gravitating away from controlled clinical trials to big data based, informationrich experiments with IRR at its core and mobile technologies as a means to collect large volumes of TCM data in a quantitative manner. To identify research opportunities and challenges that may exist in the design and implementation of a TCM-based diagnostic and medical recommendation system, the purpose of this work is to perform a bibliometric analysis with data visualizations related to IRR and TCM, particularly through author, paper, and co-word analysis, so as to better understand the conceptual structure of the field.
Materials and Methods
Scopus® (http://www.scopus.com), considered by some to be the largest abstract and citation database of peer-reviewed literature, including scientific journals, books and conference proceedings, was initially searched on October 9, 2019 and again on November 16, 2019 for all citations with the Boolean string [(“Chinese medicine”) AND (“information retrieval”) OR (“information representation”)] located in the article title, abstract, or keywords. The results of the search revealed 192 documents for the period 1985-2020; a BibTeX export file was saved and read into R, a free software environment for statistical computing and graphics (http://www.r-project.org), using bibliometrix [12], a tool for comprehensive science mapping analysis. The function *readFiles* was initially used to create a single large character vector; this object was then converted into a data frame using the function *convert2df*, with cases corresponding to manuscripts and variables to field tags in the original export file, comprising all bibliographic attributes of each document based on Clarivate Analytics WoS Field Tag codified industry standards [13]. During data cleansing, four entries were removed from the data frame due to a lack of author and other document information: three represented conference proceeding introductions and a fourth represented an introductory chapter on semantic grid applications for traditional Chinese medicine.
Results and Discussion
Descriptive analysis
To begin, a descriptive analysis was performed on the bibliographic data frame using the function *biblioAnalysis*; a display of the main results are included in Table 1. A total of 188 documents from 105 sources and 899 author appearances were noted, including a collaboration index of 2.49. Figure 1 illustrates/+*-*/-*//-+ `` of publications per year for the collection period 1985-2020; one large spike occurs in 2006 (28 citations) which continues into 2008, followed by a dip and then another, slower increase cumulating in 2017. This trend mirrors publications on IRR in general, which also peaks in 2006, according to Scopus, representing the maturation of computer browsing and the initial transition to mobile smart devices.
Table 2 contains the top 10 most cited papers in the collection, with Kanehisa M, et al. [14] having been cited over 1,500 times for their work in Japan on computerizing disease information using pathway maps, all Japanese drugs (including every TCM herbal formula), and gene/molecule lists. The second most-cited paper, Tang JL, et al. [15], represents one of the oldest papers in the current collection and is a summary of issues relating to randomized controlled trials in TCM, specifically: lack of blinding; low sample sizes; using another, unproven TCM treatment as the control; not long-term in nature; incompleteness; lack of quantitative data; missing intention to treat; lack of data on baseline characteristics or side effects; short reporting; and presence of publication bias. The third most-cited paper [16], was published in an American Heart Association journal and concludes, in similar fashion, the insufficiency of TCM evidence in using herbal medicinal for stroke patients, due to bias from poor methodology, even though the agents used appeared to be potentially beneficial and nontoxic in nature. The fourth document with the most citations [17] discusses newly published guidelines and technical notes by the European Union, in collaboration with Chinese scientists, to encourage good practice in the collection, assessment, and publication of TCM literature. The fifth most-cited document [18] reviews advances in automated tongue diagnosis, a key requirement for the accurate gathering of quantitative data, while the sixth most-cited document [19] discusses the development of ontology for TCM IRR. Fang YC, et al. [20] and Qiao X, et al. [21] both discuss the creation of TCM databaes, while Wojcikowski K, et al. [22] again point to difficultie with randomized controlled trials in TCM, particularly relating to the use of herbal medicinals in the treatment of kidney disorders. The tenth most-cited document [23] concludes that text mining of TCM literature and clinical data carries with it the potential to clarify misunderstandings, but clear operational definitions are first required.
Table 3 lists total citations by country, along with average article citations; Japan leads this metric due to the Kanehisa M, et al. [24] document noted above, with China positioned strongly behind with 865 total citations. As expected, over 50% of the top 10 countries are located in Asia; the United States remains far behind in this research area with only 10 total citations related to one published article. Table 4 illustrates the top author countries in the collection, with China strongly in the lead with 109 articles (a frequency of 0.76224) – additionally, 89% of these articles (97) are considered single country publications. Given the nature of this data, TCM and IRR research in the East has been mainly conducted as single country publications (China, Hong Kong, Korea, and Japan) while Australia, Canada, and Germany research has been more multicountry in nature.
Table 5 lists the top 10 most productive authors in the collection, based on both number of published articles (full counting) and number of published articles fractionalized (which assigns coauthored publications a fraction of one to each of the co-authors); studies have illustrated that, oftentimes, fractional counting offers a more useful perspective than full counting, especially as a means to avoid misunderstanding or misinterpretation [25]. Fractionalized counting does not affect the most productive author (Zhang Y) but does shift the order of the others slightly and results in the appearance of one new author (Xiong X) in the top 10.
Figure 2 applies the *authorProdOverTime* function on the collection to calculate and visualize the production of these top 10 authors over time, in terms of number of publications and total citations per year, for the period 1985-2020. This illustration clearly depicts the top producing author (Zhang Y) as covering both a wide period (2005-2019) along with more recent proliferation, oftentimes as a co-author, as noted by the number of articles fractionalized (2.09). Other authors with more recent production include Yu T (8 overall publications), Li J and Wang Y (6 overall publications each), and Liu L (5 overall publications).
Table 6 contains the top 10 most frequent journals, based on number of published articles in the collection – led by the Chinese Journal of Clinical Rehabilitation with 25 articles and followed by Evidence-Based Complementary and Alternative Medicine with 11 publications. However, it is important to also look at this data from the perspective of number of documents published annually; this information for each of the top five sources is visualized in Fig. 3 using the function *sourceGrowth*, which illustrates that the Chinese Journal of Clinical Rehabilitation was only in existence from 2002-2006. Since then, four newer journals have increased their publication rate, particularly Evidence-Based Complementary and Alternative Medicine, which is second in number of articles but clearly the leading publication in this field, particularly as the journal currently holds an h-index of 72 and sits as the sixth ranked journal in complementary and alternative medicine [26].
Table 4: Top 10 corresponding author’s countries.
Table 5: Top 10 Most productive authors.
Table 6: Top 10 Most frequent journals.
Table 7: Top 10 Most frequent keywords.
Table 8: Historiograph legend.
Table 7 contains the top 10 most frequent keywords using two keyword variations: authors’ keywords, as specifically selected by each author, and keywords-plus, which are those keywords extracted from the publication by Scopus’ database algorithms. The results vary, with keywords-plus identifying many more in common across the collection – for example, information retrieval was only selected by seven authors as a keyword but appears 173 times as a keywords-plus. Overall, while keywords-plus is as effective as authors’ keywords in terms of bibliometric analysis investigating the knowledge structure of a particular field, it is often less comprehensive in representing an article’s specific content [27]. However, within this collection, the use of keywords-plus may lead to a greater understanding than simply using those keywords identified by the authors, due to the increased volume and commonality of terms; this is particularly evident in Figure 4a and Figure 4b, which clearly illustrate greater and more prolific growth of keyword-plus over time, as compared to authors’ keywords.
Network visualizations
To summarize the activity of top authors, journals and keywords presented below, Figure 5 employs the *threeFieldsPlot* function to generate a Sankey diagram that visualizes multiple attributes at the same time; top authors on the left, top author keywords in the center, and major cited references on the right. The width of the bands is linearly proportional to frequency, and the size of the boxes correspond to overall production.
Figure 6 visualizes scientific collaboration networks in and across countries using the *biblioNetwork* function to develop each matrix and the *networkPlot* function to illustrate it. A sphere layout is used with the size of the sphere correlating to overall production, lines density relating to collaboration strength, and color relating to the nature of the collaboration. As expected, the majority of research is clustered in and around China, particularly with Western countries, while six additional countries are illustrated as working independently (Taiwan, Brazil, Japan, Spain, Hungary, and Korea). The main collaboration networks, however faint, are represented by Germany-United Kingdom-China, USACanada- China, and Singapore-China, based on the density of the lines.
Figure 7 depicts a word co-occurrence network that maps and clusters terms extracted from author abstracts. The *termExtraction* function was first used with word stemming to gather this information from the textual abstract field of each manuscript. In this visualization, TCM stands alone at the bottom left in its relation to the larger clusters of information science (red), herbology (green), and biomedicine (blue). Similarly, Figure 8 illustrates author keyword co-occurrences, which follows a similar pattern as to the extracted words from the author abstracts but, due to each individual author’s knowledge of the work during the keyword selection process, this visualization displays in a more orderly fashion, showing a logical progression from TCM, through a main section of information retrieval, to herbology, and ultimately across to Western biomedicine.
Visualizing influential papers
In each and every scientific field, a number of publications play influential roles in its evolution; these articles and their impacts can be accelerating factors in research development [28]. It is therefore important to identify and visualize the most influential articles on TCM and IRR published between 1985 and 2020, in order to better understand the nature and chronology of the field through its key authors, papers, and subjects. Using the *histNetwork* function, we created a historical citation network from the collection, using a minimum number of one global citation for the documents included in the analysis (see Table 8 for legend). We then employed the *histPlot* function to plot the historical co-citation network in the style of Garfield [29], using both local and total citation distributions; nodes displayed in Fig. 9 identify the thirty two specific articles identified in the collection and sort the main bibliography in ascending order by year. Each circle represents a paper, and arrows, pointing from one node to the next (usually to an older paper), indicates the citation relationship between these key works.
In the historiograph for TCM and IRR, the paper by Tang JL, et al. [30] serves as the first work noted and surveyed the efficacy of randomized controlled trials in TCM literature; this spurned a line of research (highlighted in blue) extending to Flower A, et al. [31] who advocated for the Delphi method, Sampson M, et al. [32] who searched for additional databases to identify more successful controlled trials, and Jiang M, et al. [33] who evaluated evidencebased literature for TCM diagnosis and knowledge discovery.
The second and most dominant area of research in Figure 9 (highlighted in red) focuses on TCM information databases and begins with Chang IM [34] who investigated anti-aging and healthpromoting elements derived from traditional herbal remedies found in the Traditional Oriental Medicine Database, leading to future research by Boehm K, et al. [35], who provided an overview of 45 published database resources for complementary and alternative medicine. Bensoussan A, et al. [36] established research goals for the search and retrieval of scientific evidence regarding the toxicity of Chinese herbal medicine, which contributed to Wang JF, et al. [37] and the construction of a TCM information database. Qiao X, et al. [38] created a structured database of components extracted from TCM herbs, while Zhou X, et al. [39] wrote an influential paper (5 local citations) that used ontology to construct a unified TCM language system for information retrieval and integration. This led to Zhou X, et al. [40], which investigated research issues regarding TCM text mining, You M, et al. [41], who developed an intelligent system for customized clinical TCM case management and analysis, Wan H, et al. [42], who constructed a heterogeneous factor graph model for extracting relations from TCM literature, and Yu T, et al. [43], who utilized semantic web technologies to build cross-cultural communication between TCM and Western medicine.
A third, smaller research group in Fig. 9 (highlighted in green) begins with Ka WF [56], who introduced journals and other TCM research materials available online and May BH, et al. [57], who searched English and Chinese databases to review the effectiveness and safety of Chinese herbal medicines for use in the treatment of cognitive and memory impairment. These two works led to additional research by May BH, et al. [58], comparing and evaluating published TCM collections for research and drug discovery searches, and May BH, et al. [59], who searched a database of over 1,000 classical and pre-modern TCM texts for the treatment of memory impairment. A fourth research group was also mapped on the historiograph (highlighted in purple) relating to difficulties in drawing clinical conclusions in the treatment of specific Western medicine disorders with TCM: Xiong X [60] reviewed an article on randomized controlled trials for the treatment of cardiovascular disease with TCM, while Xiong X, et al. [61] researched the clinical effects of a TCM herbal decoction in the treatment of hypertension. A fifth and final research group (highlighted in yellow), albeit small, begins late and relates to the standardization of TCM: Liu YQ, et al. [62] focused on standards and proposals established by the International Organization for Standardization (ISO), which Yoon SH, et al. [63] built from this to investigate the pros and cons of proposing standard terminology for acupotomy, a treatment modality which involves the use of both an acupuncture needle and a surgical scalpel. These five pathways of research in TCM and IRR help illustrate both the research difficulties in the field as well as opportunities in the treatment of specific diseases and the construction of modern databases and ontologies for the future use of this medical modality.
Visualizing the conceptual structure of the field
Multiple correspondence analysis is an exploratory multivariate technique that allows for the graphical and numerical analysis of the patters in relationships of categorical dependent variables, such as keywords [64]. We used the *conceptualStructure* function to draw a conceptual map of the field using keywords-plus with a maximum of five clusters and no stemming. Results are interpreted based on the relative position of the points and their distribution across the dimensions; as words are more similar in distribution, the closer they are represented in Figure 10. According to Cuccurullo C, et al. [65], map data can be translated as follows: point size is proportional to the keyword’s absolute contribution; proximity between keywords corresponds to shared substance, or lack thereof; and the dimensions of the map reflect characteristic poles of topical orientation within TCM and IRR, with the middle of the map representing the average position of all the articles and thus the center of the research field.
Cluster one (highlighted in red) resides in the top right quadrant and contains keywords from articles that relate to the use of TCM herbs and natural substances as viable treatment options for both acute and chronic diseases. Cluster two (highlighted in blue) is the largest, residing in the middle and bottom center of the map; it contains keywords from articles that relate to the design of databases and retrieval systems for scientific TCM medical literature (including Zhou X, et al. [66]). The third cluster (highlighted in green), resides center left and contains keywords from articles specific to TCM diagnosis, ontology, and data mining. Cluster four (highlighted in purple) resides in the lower right quadrant and contains keywords from articles relating to the success, or lack thereof, of evidence-based research and TCM, particularly as it pertains to clinical trials. Cluster five (highlighted in orange) resides in the top left-center quadrant and contains keywords from articles relating to the representation of TCM information in IRR systems.
From this conceptual structure analysis, one can see that the first dimension of published research extends horizontally from theoretical on the left to experimental on the right. The second dimension, extending vertically, defines published works and their keywords over a spectrum ranging from technical on the top to clinical on the bottom. There are clear research gaps in the upper and lower left quadrants, indicating that more scientific research is required to ground both clinical and technical IRR work in TCM theory – an area we know is sorely lacking at the time, due to the fact that TCM is an individualized medicine, treating each patient according to their specific pattern of disharmony, gleaned from information gathered mainly, at this point, through quantitativelybased examinations performed by human beings. As a result, a great portion of research exists on the right side of the map that is considered, according to Western biomedicine, to be experimental in nature – namely Chinese herbal pharmaceutical medicine, its integration with biomedicine, and the lack of success to date with measuring TCM treatment outcomes and drug efficacy in controlled trials. This map, therefore, charts the course for where future research should be headed as it relates to TCM and IRR – to employ new research paradigms and instruments, namely big data analytics and IoT technologies, to merge Eastern and Western medicine together, in a translational way, so as to better understand the nature of disease progression and its effects on the body.
Conclusion
It may be time for the broad discipline of information studies to come out of its proverbial shell; in the future of both Samsung [67] and Sinclair DA, et al. [68], as our lives become monitored, accentuated and refined as a means to achieve a new state of existence, behind and underneath it all will be a vast, universallyencompassing network of medical IRR systems. Such structures have already begun to take shape in other areas of existence: industry is refining algorithms that learn our preferences, activities, motives, and bioactivities; cars have begun to program themselves to reach destinations; drivers are learning where passengers are headed, before they actually meet them; and music is constantly indexed and streamed around the world across language and culture. These systems all require underlying IRR architecture so that the consumer, the device, the network, and the provider can communicate digitally, behind the scenes, in a grand dance of capitalistic-driven mobile technology. However, by applying these conceptual structures to problems like ancient TCM practitioners faced but with new goals of health and well-being over profit and market share, one could only image if, in the future, through a combination of TCM and IRR, we might be able to one day think out at least half of our medical problems. Such a vision is worth pursuing, particularly in times where many diseases, especially chronic ones like obesity and mental illness, appear to be on the upswing. Further TCM research is therefore warranted, particularly with respect to IRR as it relates to grounding modern research, both clinical and technical, with classical theory. In the style of Jim Gray’s vision of scientific discovery, driven by the collection, analysis, and comprehension of digital data by an ever-increasing interdisciplinary community of both professional and citizen-like scientists alike [69], perhaps the future of TCM lies in a big data design and deployment methodology with a new medical IRR at its core that is translational in nature, reducing health care costs and improving medical outcomes worldwide.
To read more about this article: https://irispublishers.com/ojcam/fulltext/visualizing-traditional-chinese-medicine-and-information-representation.ID.000631.php
Indexing List of Iris Publishers: https://medium.com/@irispublishers/what-is-the-indexing-list-of-iris-publishers-4ace353e4eee
Iris publishers google scholar citations:
https://scholar.google.co.in/scholar?hl=en&as_sdt=0%2C5&q=irispublishers&btnG=
0 notes
Text
Lifecam Studio For Mac

Lifecam Studio For Windows 10
Windows 10 Lifecam Software Download
Lifecam Studio Mac Download
If you want to use your HD Microsoft LifeCam Studio webcam with your Mac, in imovie 2011 especially, so that you can select it as your source camera instead. Microsoft's LifeCam Studio looks like a CCTV camera from a dystopian nightmare – forget the eye of Sauron, this feels like the eye of Microsoft, and it's pretty terrifying. LifeCam Studio is the web camera designed and manufactured by Microsoft for Windows-based PCs and Skype certificated. It is a top 1080p HD webcam with autofocus on a flexible mounting base with USB 2.0 interface and broadband built-in microphone. This is a rewrite of a review I previously wrote about both the Logitech C920 and Microsoft Lifecam Studio 1080p HD. I've raised my rating from three to four stars for both webcams. They are both very good units, but both have significant flaws that make it impossible to give either of them five stars.
Lifecam Studio For Windows 10

A feature-rich Mac software to present live input from one or more Microsoft LifeCam Studio as software for http://CamHolder.org
Mac OS X Speciality level out of ten: 0 May 5, 2017 7:10 AM in response to Ulbel In response to Ulbel I managed to use the Microsft LifeCam Studio with this good freeware.
This software is currently work in progress. Please contact me with any questions about future status and feature requests.
Heiko [email protected]
This software accompanies the physical CamHolder you can find at http://CamHolder.org and runs on Mac OSX 10.6+. It connects to one or more USB WebCams of the type 'Microsoft LifeCam Studio' and offers several features such as
zooming and rotation,
fullscreen and snap to center (for screencasting),
manual exposure time and focus,
borderless and resizable windows,
comfortable keyboard short cuts,
that make presenting and screencasting with the CamHolder a snap.

Windows 10 Lifecam Software Download
Even though this software is open-source you must neither sell the compiled binary nor build any commercial software on top of its code without significant changes (see file LICENSE).
Lifecam Studio Mac Download
This software (especially the routines to access the UVC Camera) finds its roots the blog post http://www.phoboslab.org/log/2009/07/uvc-camera-control-for-mac-os-x by Dominic Szablewski. Also, I want to thank the beta testers Ekkehard Gentz (@ekkescorner) and Peter Friese (@peterfriese).

0 notes
Text
Juniper Publishers- Open Access Journal of Case Studies

Risk Factors of Rotavirus Outbreak Among Children in Kurmuk District, Benishangul Gumuz Regional State, Ethiopia
Authored by Malede Mequanent Sisay
Abstract
Background: Rotavirus infection (RV) is the leading cause of diarrhea in under 5 years’ children. About 600,000 deaths occurred worldwide due to RV infection and 90% of deaths occurred in low-income countries. In Ethiopia, death due to RV infection is one of the top ten leading cause. The aim this study was to identify the risk factors of confirmed Rotavirus outbreak in Kurmuk district, Ethiopia.
Methods: A community based unmatched case-control study was implemented to investigate RV outbreak from February 11 to March 20, 2017. We selected 57 cases and 114 controls randomly. Data were collected using pretested structured questionnaires included socio-demographic and clinical information. Stool samples were obtained from recruited children and tested for rotavirus antigen and water samples checked. Frequencies and graphs were used to explore the data. Binary logistic regression was used to identify the risk factors. Adjusted odds ratio (AOR) with 95% confidence interval and p -value <0.05 were considered statistically significant association. Model goodness of fit test was assessed using the Hosmer-Lemeshow.
Results: Out of the total 585, 303 (51.8%) were male children with mean age 23 months (SD=10.3). The overall attack rate was 25 cases per 1000. Fourteen (2.4%) deaths were observed. The risk factors were contact with cases (AOR 4.46; 95% CI 1.331-18.53), unavailability of latrine (AOR 12.98; 95% CI, 2.66-62.41), improper handling of drink water (AOR 13.88; 95% CI,5.06-38.05), not washing hands after cleaning child stool (AOR 4.524; 95%CI 1.303-15.705), not washing hand after defecation (AOR 7.22; 95% CI,1.4-37.25) and being vaccinated (AOR 10.19; 95% CI,166- 62.41). In contrast, washing hand using soap/ash reduce infection of rotavirus (AOR 0.209; 95% CI, 0.065-0.991).
Conclusion: Group A Rotavirus outbreak were identified in Kurmuk district. The risk factors were unavailability of latrine, improper handling of drink water, and not washing hands after defecation and cleaning child stool and contact with cases. Washing hands using soap/ash can reduce the risk of RV infection. Strengthen hygiene and sanitation activity reduce the infection. The further investigation on vaccine efficacy and genotype of the virus was crucial.
Keywords: Children; Risk Factors; Rotavirus Outbreak
Background
Rotavirus cause a significant proportion of childhood diarrhea worldwide leading to dehydration, hospitalization and deaths yearly [1-12]. The infection had a variation in regions and seasonal [13]. It is estimated that 111 million home care, 25 million clinic visits, 2 million hospitalizations and 600,000 deaths occurred in the worldwide in every year [14]. The case-fatality rate is higher in the developing countries due to malnutrition and barriers to accessing health services in a timely manner. It accounts more than 90% of rotavirus deaths. Study conducted in Africa reported that 49 to 65 % death caused by rotavirus in 2013, including Ethiopia [15]. In contrast, in the United States of America only 20-60 deaths happened per year [16].
In low income country, the reported showed the prevalence of rotavirus inflated in African countries [12,16-18] . However, the annual rate is decline from 42.5% in 2000 to 37.3% in 2013 due to vaccine, oral rehydration salt (ORS) and Zink supplementation [15,19].
According to world health organization (WHO) report, Ethiopia was ranked in top ten countries with high under five children mortality and morbidity by rotavirus with Prevalence ranged from 15 % to 44% [20-23]. Other sentinel surveillance of RV done at Addis Ababa indicated that the rate is decreased due to expanding of immunization [21,23,24].
However, On February 17, 2017 RV outbreak occurred at Kurmuk district, Benishangul Gumuz Regional state among under five years children.
Thus, the aim of this study was to confirm suspected rotavirus outbreak, describe epidemiology and identify risk factors of rotavirus disease in Kurmuk district, Benishangul Gumuz Regional state, Ethiopia.
Methods
Study area and design
The study was conducted in the Kurmuk district, Benishangul Gumuz Regional state, Ethiopia. Kurmuk district shares boundaries with the Khomosha district on the South, Assosa district in the West, North Sudan in North, and Sherkole district in the East.
According to 2007 national statistics, the district is divided in to 15 rural Kebeles and one town with a 22740-total population [25]. This district is lowland area with the annual average rain fall ranges from 700ml-1000ml and temperature (26oc, 35oc) as well as more than 85% of area is arid desert. Currently the district has 10 health posts and one health center with dedicated staff such as health extension workers, health development forces and health professionals.
The outbreak was investigated from Feb 11, 2017 to Mar 20, 2017. Consequently, we used community-based case-control study to identify risk factors of RV case.
Sample size and sampling technique
The required Sample size was calculated using Epi Info 7.1.4 software. Controls (21%), 2.83 Odd ratio and 43.1% exposure of cases was taken from previous studies conducted in Jimma zone [26]. Additionally, we used the following assumptions: a 95% confidence level, 80% Power, 1:2 cases to controls ratio. Finally, we found 171 (57cases and 114 controls) samples and included randomly.
Study case definition, recruitment and laboratory methods
The district health office was collected data daily base during outbreak period using standard line list format. The team searched active cases home to home and gave information to the community on meeting, markets, churches and other public gathering places. We collected stool samples from patients and send to Ethiopian Public health Institute (EPHI) polio and measles laboratory. Samples were placed in 2-8oC till and transported in triple package to the laboratory. The maximum time samples places in refrigerator were 48 hours. Main water source of woreda collected and checked for bacteriological indicator test. We collected samples by trained professional though sterile method. Immediately after collection we transported the water samples to Regional laboratory in 2-8oC within triple package.
The standard case definitions were as follows.
a) Suspected case: Any child under five years of age with sudden onset of diarrhea with vomiting, two or more episodes within 24 hours, from Feb 11, 2017 to March 20, 2017 and residence of Kurmuk Woreda.
b) Confirmed case: Suspect case for which there is a timely stool sample and the lab results are positive for rotavirus. Outbreak is confirmed when an epidemiological link is established with a laboratory-confirmed case.
c) Controls: Any child under five years of age without diarrhea and vomiting and resident of Kurmuk Woreda within period of Feb 11, 2017 to March 20, 2017.
For analytical study, we interviewed parents of the children by using standard pretested questioner at home and at Health facilities for controls and cases respectively. At enrollment, demographic, clinical, epidemiological, environmental information and stool samples were collected. The Dependent variable was Infection of rotavirus and Independent Variables were: Age, Sex, Immunization history, Water source, Using and presence of toilet, Exclusive breast-feeding frequency and Availability of washing facility
Statistical analysis
Data were entered in Epi Info 7.1.4 and analyzed using SPSS (V20.0). Data was described by place, person (age, sex, other socio-demographic information) and time (date of onset). Binary Logistic regression models were used to assess the associations between the dependent variable (RV status) and the independent variables. Factors with a p -value of 0.2 in the bivariate analysis and factors of biological plausibility were included in the multi-variable analysis. Adjusted odds ratio (AOR) with 95% confidence inter al and p -value <0.05 were considered statistically significant association. The fit of the model was assessed using the Hosmer-Lemeshow good ness of fit test and p -value > 0.05 was taken as a cutoff point.
Results
Cases and incidence rates
Figure 1 showed variation in daily numbers of measles infection from Feb 11, 2017 to March 20, 2017. A total of 585 cases were reported in infants less than 5 year of age in the districts. Two of them were confirmed rotavirus by laboratory, whereas the remain were linked epidemiologically. The index case was occurred at Dull-shetallo health post at 11/2/2017.
More than half cases 303(51.8%) were male children with mean age of 23 months (SD=10.3 months). The investigation showed that infants were more 267(45.6%) infected age group, and an additional epidemic peak was found in 23/6/2009 (49/585). The attack rate was 25 cases per 1000 under five year’s population. Moreover, 14(2.39%) deaths were recorded during the outbreak.
The study revealed that all children had diarrhea, vomit, fever and some dehydration. Before confirmation of etiologic agent patients were treated with antibiotics (cotrimoxazole) and supplements (ORS and Zink). Then after confirmation, patients were treated only with ORS and Zink. The most affected Kebeles was Dull shetallo, which accounts 156(26.6%) cases followed by Belehu Jibila 75 (12.6%) and Horazeab 69 (11.6%) respectively.
Demographic characteristics of the studied group
A total of 57 cases and 114 controls were selected to identify risk factors for outbreak in affected Kebeles of the Kurmuk district. The mean age was 18.9 months (SD=10.3). From cases 99.2% had diarrhea and fever. The distribution of demographic characteristics of the study participants and risk factors for measles outbreak were described in Table 1.
On multivariable logistic regression, having contact with cases, unavailability of latrine, improper handling of drink water, unwashing after cleaning child stool, defecation, and exclusive breast-feeding frequency less than 8 per day were risk factors for rotavirus infection. In contrast, washing hand using soap/ash reduce infection of rotavirus (Table 2).
Discussion
We identified group A Rotavirus outbreak in Kurmuk woreda, Asossa zone from 11/2/2017 to 20/3/2017. In addition to this Benishangul Gumuz Regional State Health Bureau declared that there was outbreak of RV in Kurmuk woreda at the same period. GAVI Surveillance report of Ethiopia showed that RV cases rose up in cooler season from October through March [24]. This outbreak began in same period with outbreak occurred in Tirana, Albania in 2000 [27]. The prevalence of rotavirus infection peaked in Ghana during the cool, dry months of January and February. In Zimbabwe a seasonal peak in the prevalence of rotavirus diarrhea occurred during the winter months [6] which is the same to cases in Kurmuk woreda. However, a less distinct seasonal peak was observed in some low-income countries (e.g., Indonesia, Vietnam, Cambodia) [13] and in equator areas (e.g., Uganda) seen year-round [6]. Some studies have noted secondary seasonal peaks in rotavirus incidence associated with periods of high rainfall and flooding [28] which contradict the season of Kurmuk woreda outbreak.
Rotavirus vaccination is the primary strategy for preventing severe rotavirus disease. Incidence and hospitalization due to rotavirus successively reduced by introduction the vaccine [29]. In United States of America, incidence of hospital visits and admission due to rotavirus gastroenteritis reduced by 86% and 96% respectively [7]. After rotavirus vaccine introduction in Rwanda, hospital admissions for diarrhea in children younger than 5 years reduced by 29% and 17% in 2013 and 2014 respectively. In the same period the number of hospital admissions for diarrhea in children younger than 1 year decreased by 55% and by 51% [21]. In contrast, vaccine efficacy such as severe gastroenteritis and length of follow-up had difference between high income and low-income nations. Rotavirus vaccines are less effective in lower income settings combination of poor immunological response caused by malnutrition, other intestinal infections, and immunosuppressant efficacy against other oral vaccine (OPV). The average efficacy for high, upper middle, lower middle, and low-income countries are 90%, 85%, 66%, and 55%, respectively [21,30] which is similar to in a cases of Kurmuk woreda.
Disease of rotavirus attacks children aged below 2 years and more than 75 % under 12-month infants and 95% more under the age of 18 months more affected [11]. On surveillance of rotavirus in Turkey, most rotavirus infections were recorded in children aged 12 to 23 months, and a second peak was observed in the 6 to 11-month age group; more than 70% of rotavirus infections occurred in children less than 2 years of age [2], which is similar to our finding. However, some outbreaks of RV infection in adults have been reported [18] and even in elderly persons [31]. On large waterborne outbreak in two districts of Turkey due to rotavirus with attack rate 1/46 and 1/66, the mean age of the outbreak patients was 25years [10] which is slightly similar to Kurmuk woreda.
Contaminated water may be an important source of transmission in settings with poor sanitation. The waterborne transmission route may dominate during times of increased rainfall [13]. A large infantile gastroenteritis outbreak in Albania caused by multiple emerging rotavirus genotypes, common source was contaminated water [27]. On this outbreak also, the major identified risk factor was spring water which contradict our findings.
On this outbreak children had contact with case were more exposed to RV infection. Outbreaks of RV gastroenteritis in day-care centers and hospitals can spread rapidly among no immune children, presumably through person-to-person contacts, airborne droplets, or contact with contaminated toys [23] which similar to our finding. Nosocomial infection study on RV in Greece, 58% of RV gastroenteritis in neonates was hospital acquired [17].
The limitation of this study Genotyping of rotavirus not performed in Ethiopia. Therefore, genotype of this group A rotavirus was not identified. The samples were not tested for other enteric virus like Adenovirus and norovirus which can cause gastroenteritis. Environmental sample (water) did not collected from all major water sources of sources there for the result water sample may not represent all drinking water sources in the woreda. Currently the infection was reduced by vaccinating child at age of 6 and 10 in worldwide, but my finding contradicts this idea which is risk factor for the infection. Hence it is good to identify the reason why so using cohort study and need extra investigation on vaccine efficacy.
Conclusion
We confirmed group A rotavirus outbreak among under five year’s children in Kurmuk woreda, Asossa zone, Benishangul Gumuz regional state from February 11 to March 20, 2017. Risk factors of this outbreak were unwashing hands after cleaning child stool, after defecation being vaccination of Rota vaccine, exclusive breast-feeding frequency less than 8 and contact with cases. Washing hand using soap/ash can reduce the risk of RV infection. Establishment of RV surveillance site in this area and genotyping of RV is essential further prevention activities.
For more articles in Open Access Journal of Case Studies please click on: https://juniperpublishers.com/jojcs/index.php
#JuniperPublishers#Juniper Publishers Contact#Transplantation Medicine#Neuroscience#Infectious Diseases#Hospice and Palliative Medicine
0 notes